Communication security maintenance device based on power edge gateway equipment
An edge gateway and communication security technology, applied in internal/peripheral computer component protection, instrument, character and pattern recognition, etc., can solve problems such as cost limitation, interference operation, missing and missing data judgment, etc., and achieve good adaptability and scalability Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
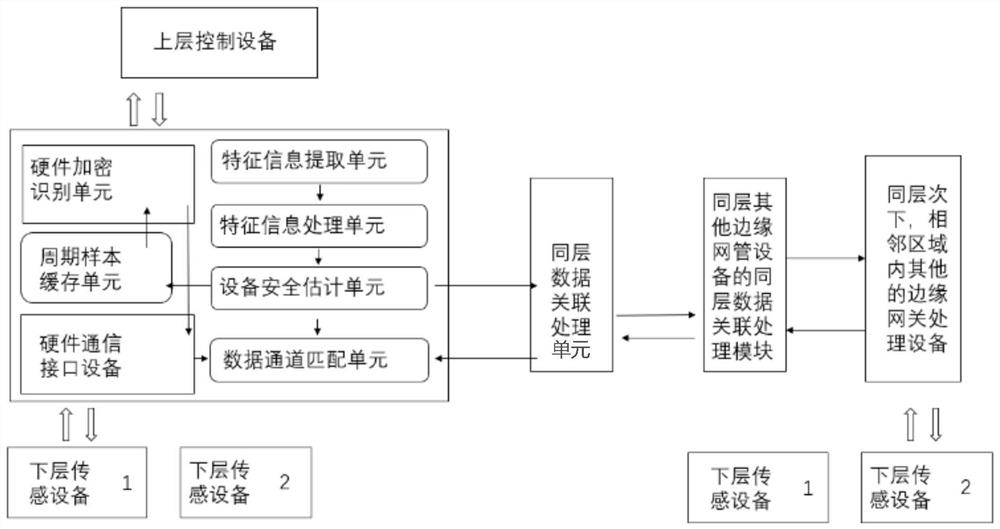
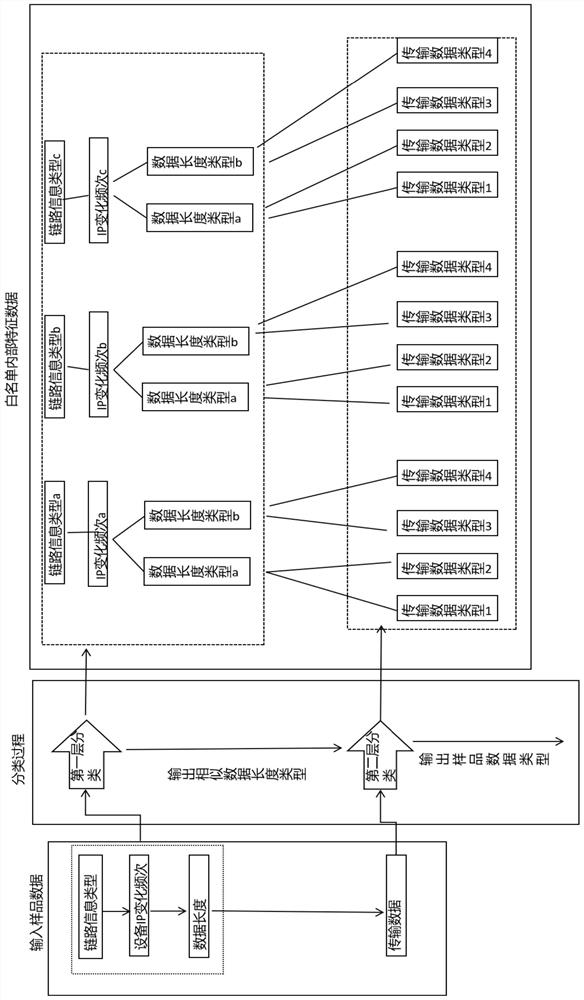
[0046] It should be noted that the connections mentioned below mean the construction of data channels to generate information exchange, which are mostly part of algorithms and have nothing to do with the actual module structure. It should be noted that the improved functions of the present invention are mainly realized by algorithm codes, and its specific execution functions are convenient to adjust, so here only the relevant units whose functions are simply classified are used as replacements.
[0047] As the practical application carrier of edge computing, edge gateways are widely used, but there are also data security issues. The present invention realizes the unique i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com