Data verification system
A data verification and verification system technology, applied in the information field, can solve the problems of data security impact, data authenticity impact, and the authenticity of verification results cannot be guaranteed, so as to save space and prevent tampering.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
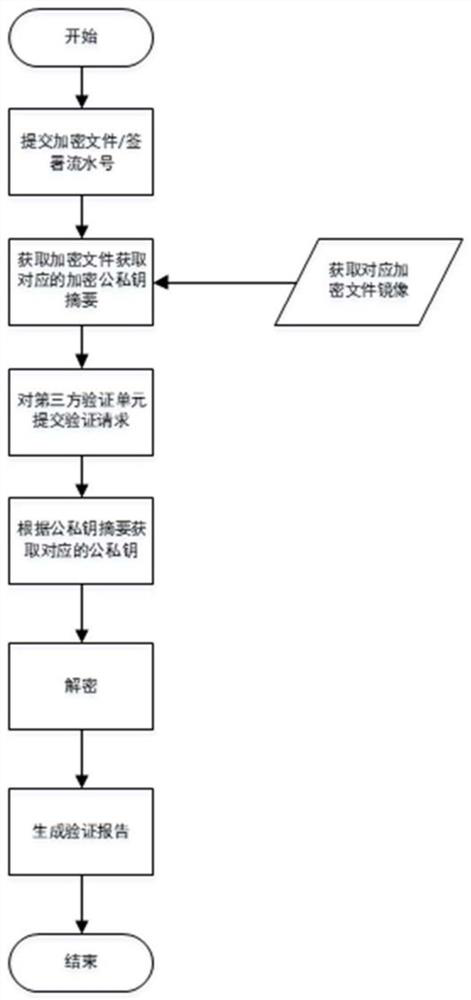
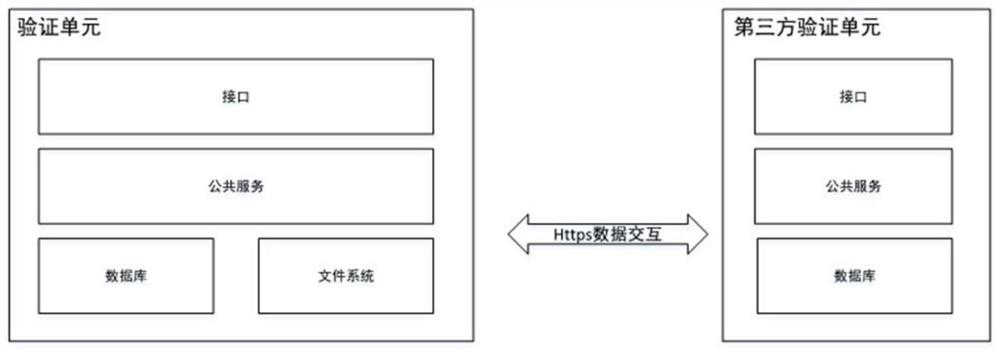
[0045] A data verification system includes a verification unit, a third-party verification unit and a terminal. The terminal includes a first interface module and a first public service module.
[0046] The verification unit includes a second interface module, a second public service module, a second database module and a second file system module.
[0047] The third-party verification unit includes a third interface module, a third public service module and a third database module.
[0048] Preferably, a third database module with encryption function is used.
[0049] The first public service module receives the encrypted data provided by the user and the serial number corresponding to the encrypted data.
[0050] The second database module stores plaintext data, including keys, key digests, and encrypted data image digests, and the second file system module stores ciphertext data, including encrypted data images.
[0051] Preferably, the second database module stores the p...
Embodiment 2
[0073] A data verification system includes a verification unit, a third-party verification unit and a terminal. The terminal includes a first interface module and a first public service module.
[0074] The verification unit includes a second interface module, a second public service module, a second database module and a second file system module.
[0075] The third-party verification unit includes a third interface module, a third public service module and a third database module.
[0076] Preferably, a third database module with encryption function is used.
[0077] The first public service module receives the encrypted data provided by the user and the serial number corresponding to the encrypted data.
[0078]The second database module stores plaintext data, including keys, key digests, and encrypted data image digests, and the second file system module stores ciphertext data, including encrypted data images.
[0079] The third database module stores plaintext data, inc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com