Block chain-based 5G unmanned aerial vehicle cross-domain identity authentication method, system and terminal
A technology of identity authentication and drones, applied in the field of drones, can solve problems such as sensitive data leakage, single-node identity authentication server service paralysis, failure to meet authentication security requirements, etc., achieve strong flexibility, solve single-node failures and Distributed denial of service attack, low latency effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
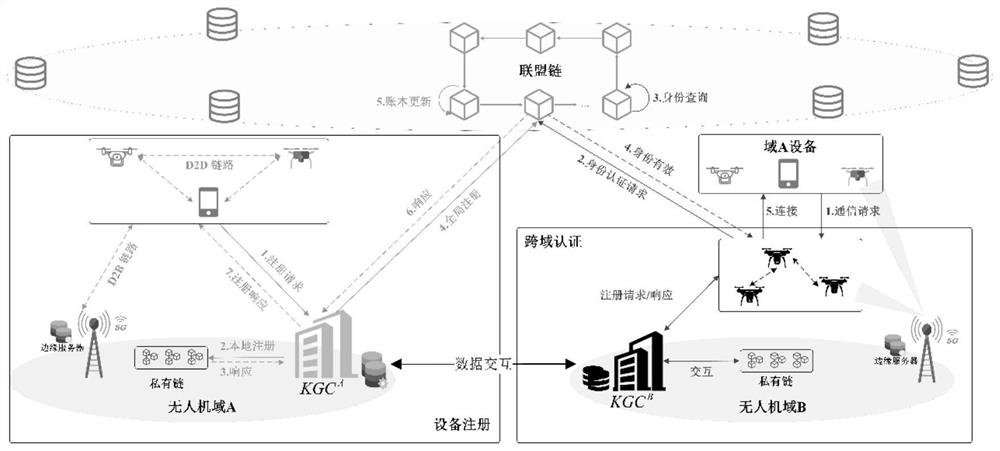
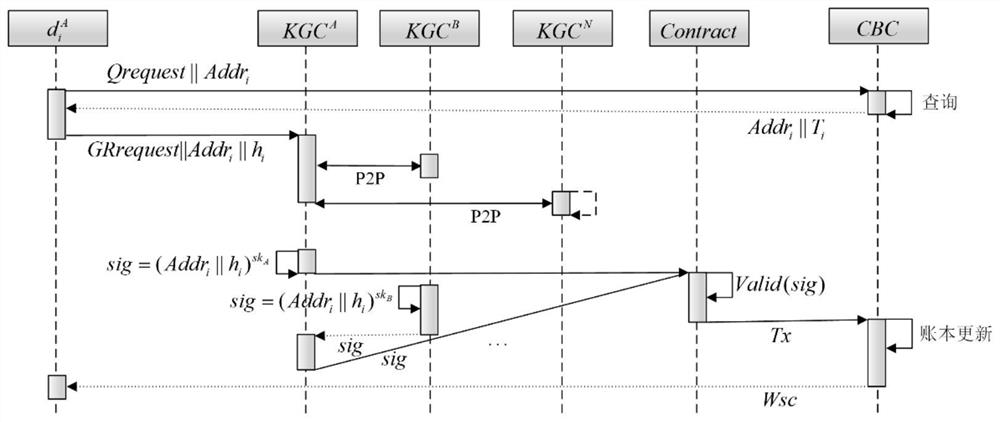
[0055] Embodiment 1: A blockchain-based 5G UAV cross-domain identity authentication method, such as figure 1 As shown in , it is specifically realized by the four steps of system initialization, identity management, session key negotiation, and identity authentication.
[0056] It should be noted that the key generation center and the edge server in this embodiment are both configured as a server, and the key generation center and the edge server cooperate to form a domain administrator, who is responsible for the enterprise manager of the drone and the maintenance of the alliance chain. The role of the operator is responsible for the management of equipment in the domain and the establishment and maintenance of blockchain nodes.
[0057] 1. System initialization
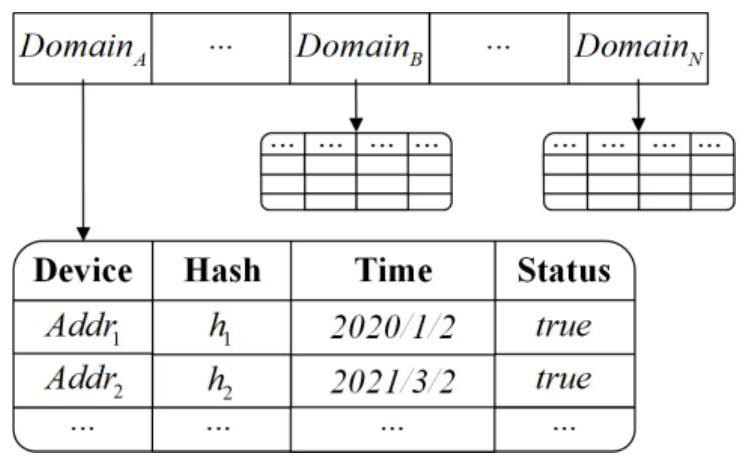
[0058] System initialization includes domain initialization, KGC initialization, private chain construction, alliance chain construction, and deployment of smart contracts.
[0059] 1. Domain initialization, the K...
Embodiment 2
[0119] Example 2: A blockchain-based 5G UAV cross-domain identity authentication system, such as figure 1 As shown, it includes multiple UAV domains and alliance chains formed by deploying smart contracts. Each drone domain is configured with a unique key generation center, an edge server, private chain, and multiple domain devices. Domain devices are connected through D2D link network communication, and domain devices and servers are connected through D2B link network communication. Domain devices include but are not limited to drones, smart terminals, etc.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com