Data cross-blockchain access control method and system in multi-blockchain scene, equipment and terminal
An access control and data access technology, applied in transmission systems, electrical components, etc., can solve the problems of complex implementation, poor performance, and inability to effectively share information on the chain, and achieve the effect of ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
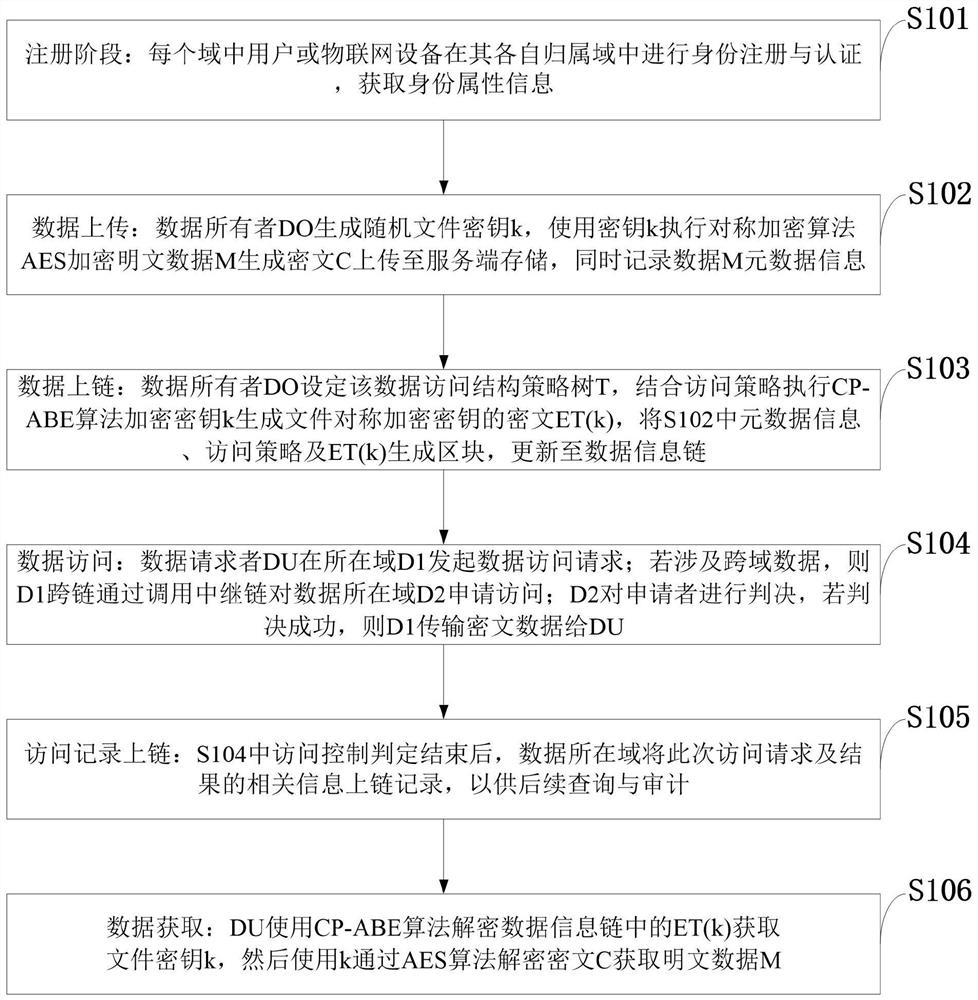
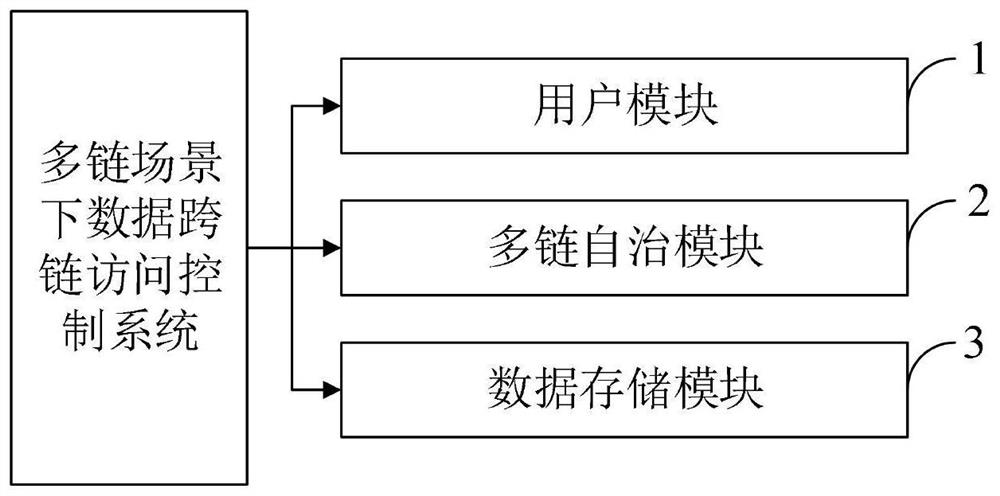
[0094] The data cross-chain access control system provided by the embodiment of the present invention includes:
[0095] The user module, which is composed of user entities, is the actual participant of data calls, and is used for user identity registration, accessing data and uploading data.
[0096] A multi-chain autonomous module composed of multiple autonomous domains (domain, D) is responsible for user identity registration and attribute issuance, as well as key generation and distribution for attribute encryption, and records data information at the same time. Each domain has its own independently maintained data Information chain and access record chain.
[0097] The data storage module is composed of a cloud service provider (cloud service provider, CSP) and other IoT devices with powerful computing power and large storage capacity, responsible for data storage and download services.
[0098] The user module provided by the embodiment of the present invention includes a...
Embodiment 2
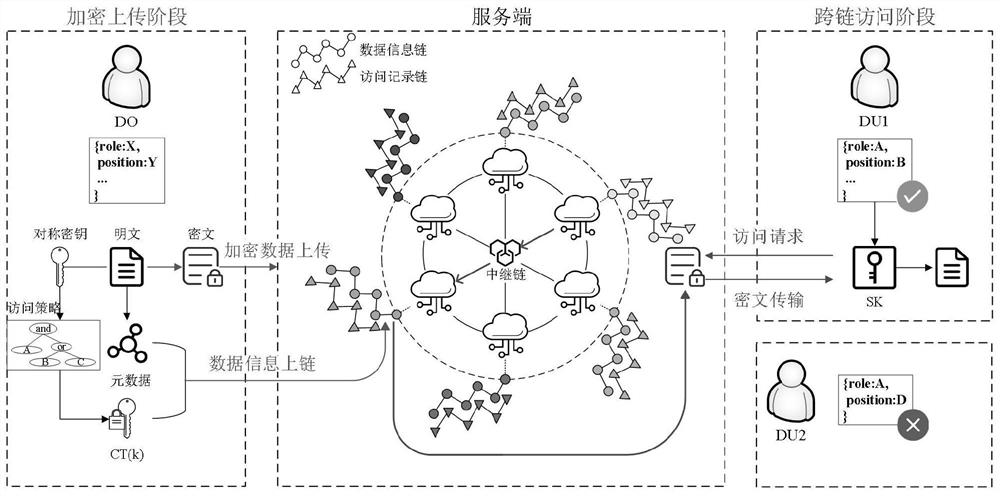
[0104] like Figure 5 As shown, a schematic diagram of cross-domain attribute mapping of the data cross-chain access control method provided by the embodiment of the present invention. In this model, ciphertext policy-based attribute-based encryption CP-ABE is used in each domain for data access control. The resource attributes of each domain are divided into general attributes and mapping attributes. The general attributes represent universal attributes in each domain, such as Name, gender, age, etc.; the mapped attribute represents a local attribute that is only applicable to this domain and requires attribute mapping when calling across domains. When accessing data across chains, the chain where the data resides completes the policy attribute mapping through the relay chain. When a user in any of the autonomous domains D1 sends a cross-chain access request to the autonomous domain D2, the attributes in the autonomous domain D2 can be mapped to the domain D1 through the rel...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com