Simulation platform and method based on IEEE802.1X security protocol of EAP
A technology of security protocol and simulation platform, applied in the field of simulation platform of IEEE802.1X security protocol, can solve the problem of no security authentication, single data receiving and forwarding function of wireless node, and seamlessly solve the problem of roaming access authentication. The effect of ensuring integrity and solving security authentication problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
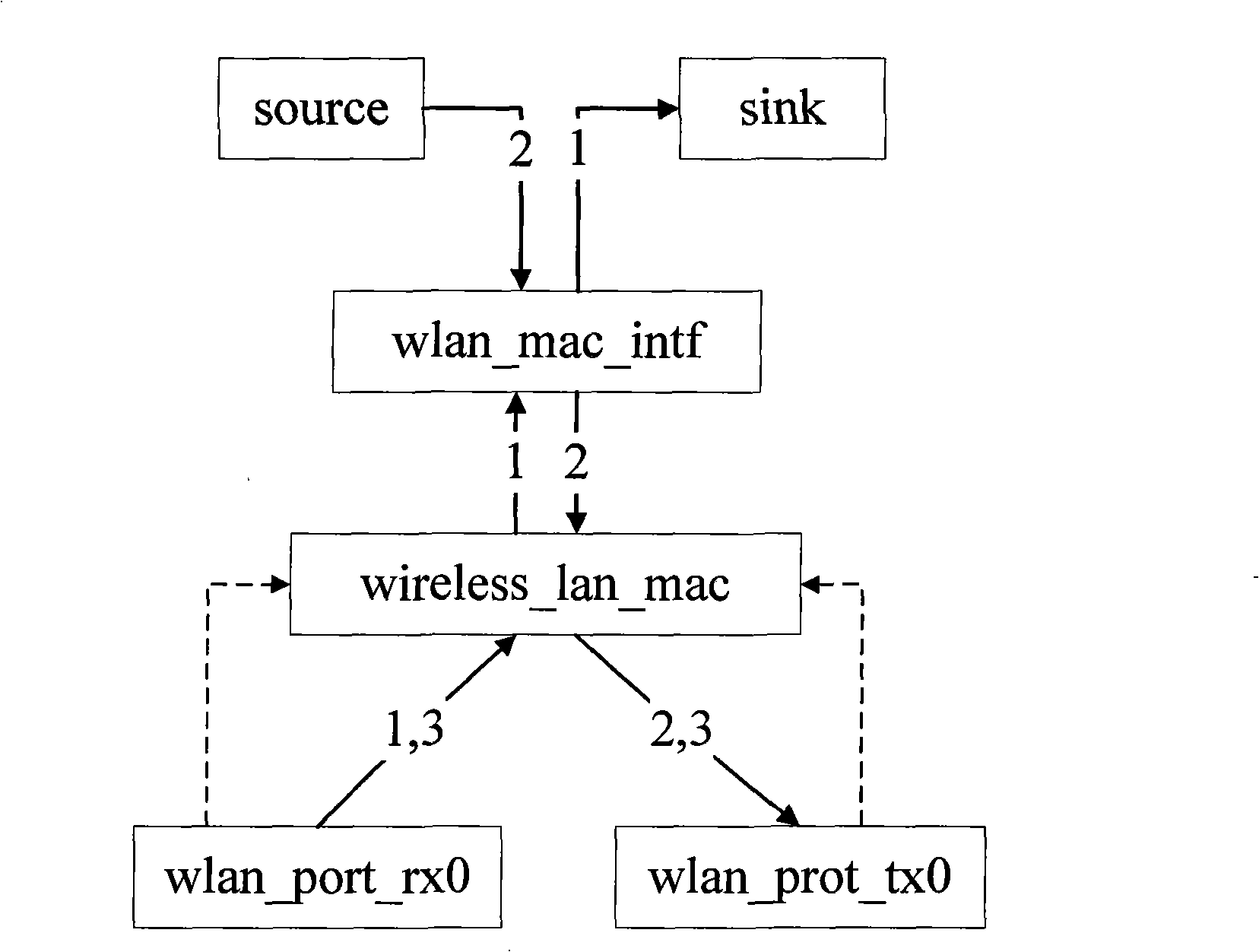
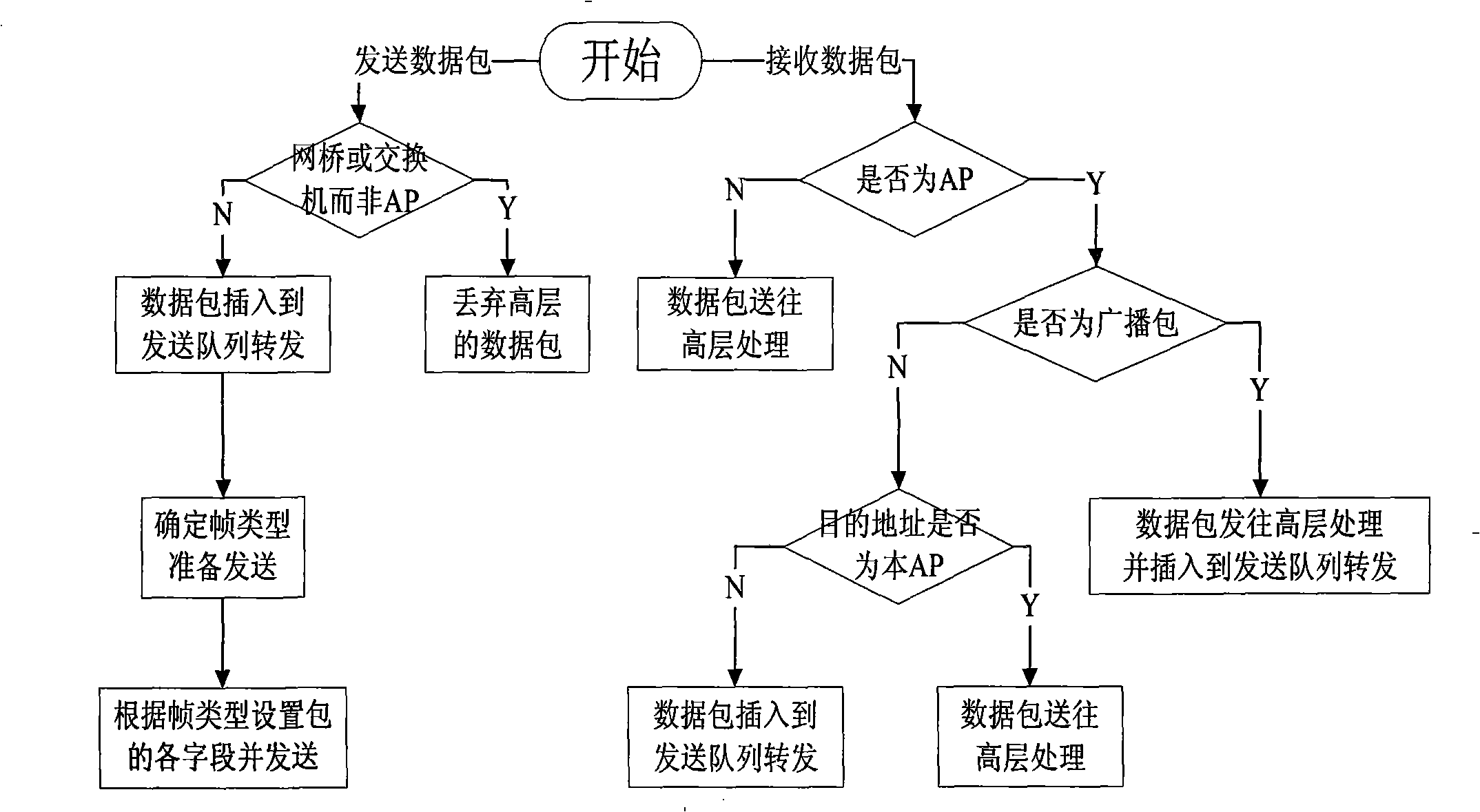
[0087] see figure 1 , the wireless node model consists of 6 process models, 6 data packet streams, and two statistical lines. Among them, the source and sink modules simulate the application layer, and the physical layer consists of the receiver wlan_port_rx0 and the transmitter wlan_port_tx0, which are responsible for receiving data packets sent by other nodes and sending data packets to other nodes. The two modules wlan_mac_intf and wireless_lan_mac simulate MAC media access The control layer; the wlan_mac_intf module is responsible for determining the target address; the wireless_lan_mac module is responsible for the fragmentation, encapsulation, queuing, and transmission of application layer data packets, and decapsulates, assembles, and transmits fragments received and forwarded by the physical layer to the application layer , while detecting collisions and forwarding packets.
[0088] The present invention improves the wireless_lan_mac module in the wireless node, adds ...
Embodiment 2
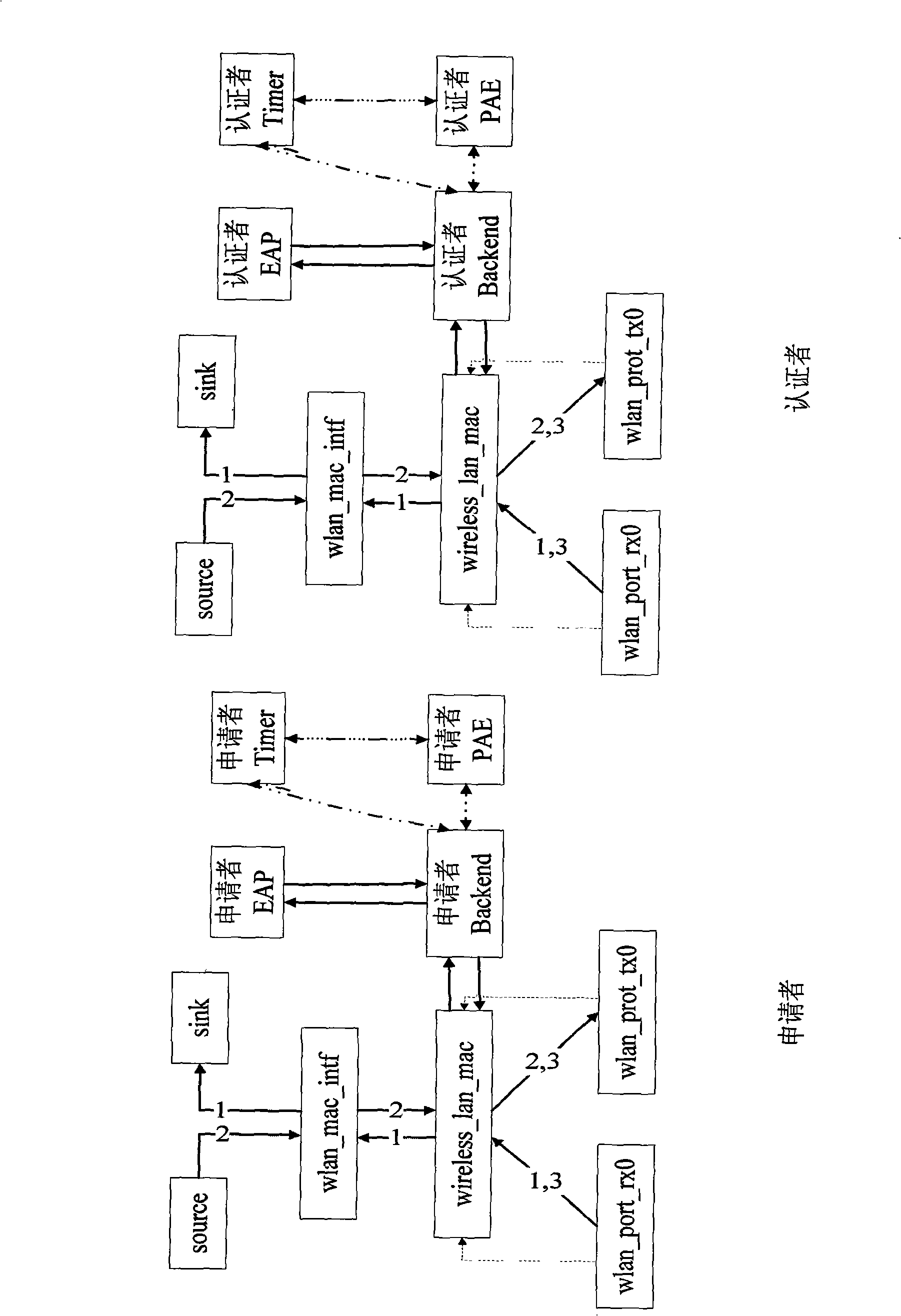
[0090] Overall composition is the same as embodiment 1, see image 3 .
[0091] The EAP authentication module is divided into two different roles: applicant and authenticator. In the applicant, implement the eap_supp module; in the authenticator, implement the eap_auth module; the two are connected to the network through their respective Backend background state machine and wireless_lan_mac module to realize mutual communication. OPNET's original wireless nodes do not distinguish between authenticators and applicants, see figure 1 composition. Wireless nodes can be regarded as both authenticators and applicants. There is only data communication between nodes, and there is no authentication process. See figure 2 .
[0092] In the simulation process, the present invention combines the authenticator and the authentication server into one, that is, the access point AP inside a basic service set BSS completes the function of the authentication server, and does not need to forw...
Embodiment 3
[0094] Overall composition is the same as embodiment 2, see image 3 .
[0095] The IEEE802.1X protocol is to solve the problem of Ethernet access authentication. It is not specially designed for WLAN, but it allows it to be used in a shared medium, so this protocol can be applied to IEEE802.11 WLAN that supports port-based network access control in the structure. The invention can obtain the equivalent model of IEEE802.1X finite state machine in OPNET through equivalent transformation, thereby ensuring the correctness of the established protocol model state machine in design. Confusion between model versions is avoided. We choose three state machines for equivalent transformation to complete the port control function in the authentication process, among which the Backend background state machine is mainly used for background authentication; the Port Timer port timer state machine is used for timeout control; the PAE port access entity module is used for port control.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com