Image-tampering detection and recovery method based on energy-domain semi-fragile watermarking
A technology for fragile watermarking and tampering detection, applied in image data processing, image data processing, instruments, etc., can solve the problems of unable to restore images and blind detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0069] This embodiment adopts the static image grayscale picture LENA as the watermark carrier picture, in this example,
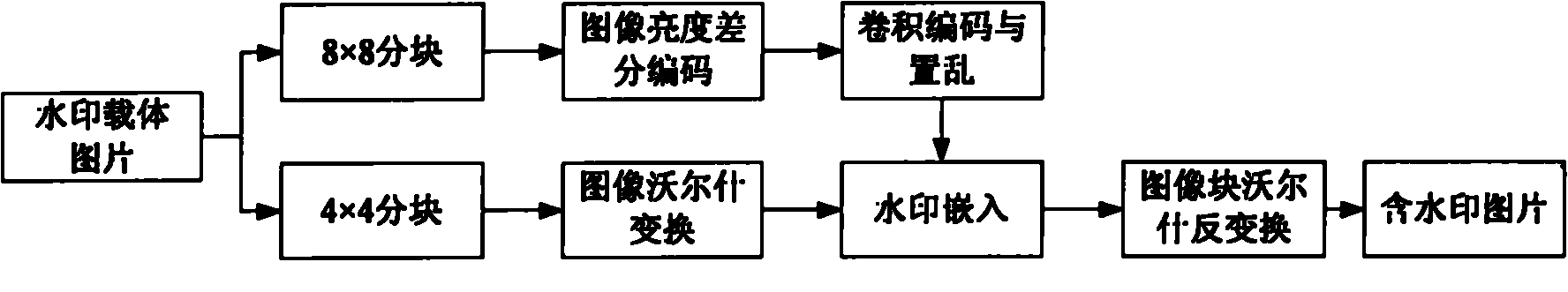
[0070] Step 1: see figure 2 , the watermark carrier picture LENA is divided into blocks with a size of 8×8, and the absolute difference in brightness between adjacent image blocks is calculated as the watermark content. Represented by two binary bits. Use the convolutional code (12, 1, 2) to perform convolutional coding on all the obtained watermark contents. The convolution code is formed into a matrix, and the scrambling result is formed by repeated diagonal scanning to obtain the embedded bit value. The watermark carrier image is divided into blocks with a size of 4×4, and Walsh-Hadamard transform is performed on each block ( figure 2 Walsh transform for short), the transformation formula is F=H M ×f×H N , where the transformation matrix is
[0071] H ′ 8 = 1 ...
Embodiment 2
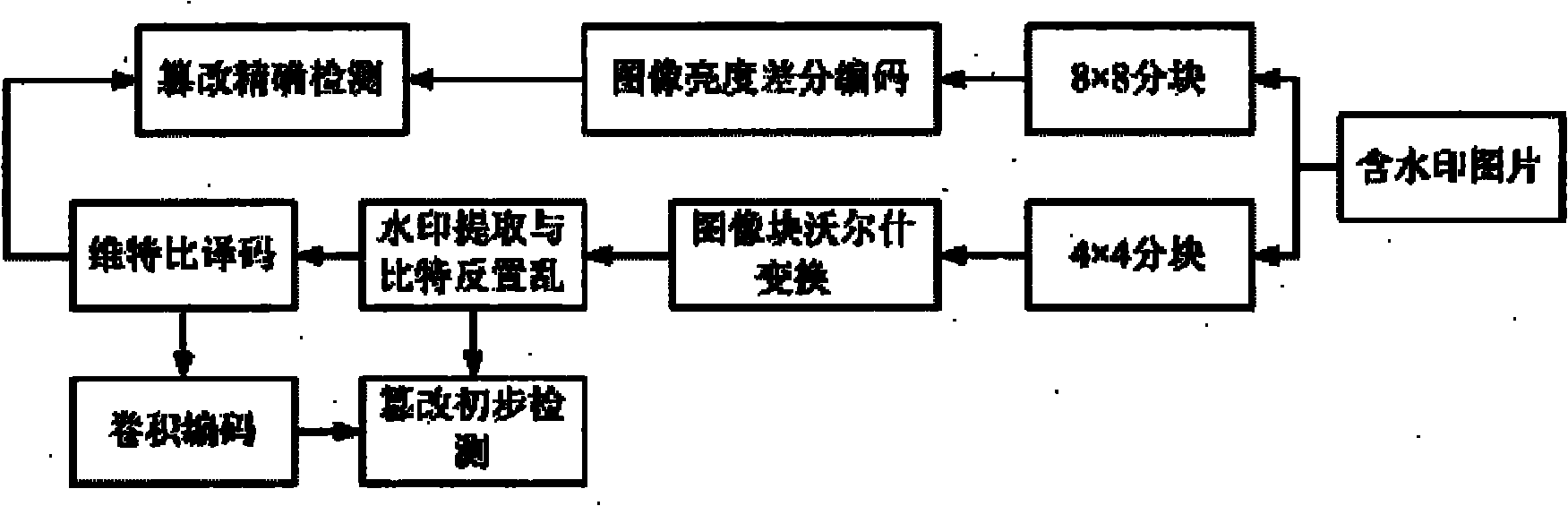
[0099] Apply the above method to a 512×512 grayscale (color) image named airplane as a watermark carrier image, and add another airplane above the original image airplane (such as Figure 5 .a). In order to precisely locate the location of image tampering, the size of the block is 4×4. Apply the image to the above tamper detection pipeline. The results of tamper detection are as follows Figure 5 As shown in .b, the area where the image has been tampered with can be clearly seen; the results of accurate detection are as follows Figure 5 As shown in .c, the restoration result of the original image is as follows Figure 5 .d.
Embodiment 3
[0101] This method is applied to LENA pictures for lossy compression attack test. The experimental effect picture is as follows Image 6As shown, from the point of view of actual effect, take Δq=17 and then list them in various situations, including: JPEG85%, 65%, 40%, 25% quality, JPEG2000 compression ratios are 10:1, 15:1 respectively , 20:1 tampering detection results, and restore the original image of the tampered area, the results are as follows Image 6 shown.
[0102] The above experiments use typical test pictures to test the invention from the aspects of watermark construction and embedding, static image tampering detection and restoration, etc., thus proving the effectiveness of the method.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com