DRM (digital rights management) system based on distributed keys
A security device and mobile terminal technology, applied in the field of DRM system, can solve problems such as performance bottlenecks, achieve the effect of reducing resource requirements, reducing costs, and eliminating performance bottlenecks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
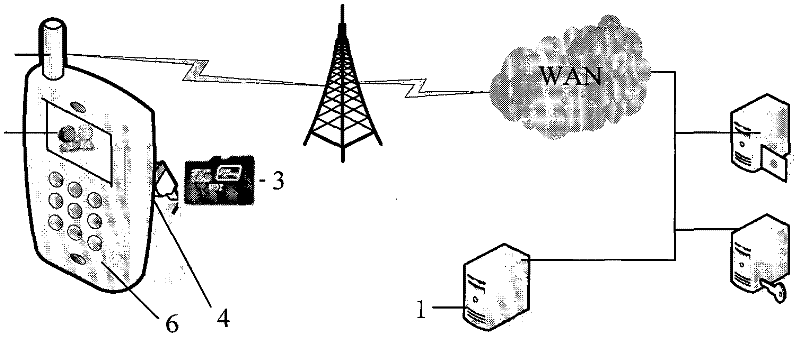
[0027] Embodiment 1: a control device for DRM, such as figure 1 Shown, comprise the client terminal 2 that is installed on mobile terminal 6 and communicate with server 1 and be arranged on the safety device 3 that has IC card function and TF card interface in mobile terminal 6, it also includes and carries out communication contact with client terminal 2 The mobile terminal 6 is provided with a TF card interface 4 connected to the security device 3 and a mobile network interface 5 communicating with the server 1 on the mobile terminal 6. The security device 3 adopts the smart TF card of Shenzhen Longsys Electronics Co., Ltd., which supports mobile payment function; when the client 2 connects to the security device 3 and enters the password, it switches to the hardware protection state and monopolizes resources such as SDIO, keyboard, mouse, touch screen and input pen. , to prevent viruses from stealing security information by controlling the operating system application progr...
Embodiment 2
[0028] Embodiment 2: a control device for DRM, such as figure 1 Shown, comprise the client terminal 2 that is installed on mobile terminal 6 and communicate with server 1 and be arranged on the safety equipment 3 that has IC card function and SDIO interface in mobile terminal 6, it also comprises the client terminal 2 that communicates with client terminal 2 The mobile terminal 6 is provided with an SDIO interface 4 connected to the security device 3 and a mobile network interface 5 communicating with the server 1 on the mobile terminal 6; the security device 3 adopts the smart SD card of Shanghai Putian Research Institute and supports mobile payment functions; 2. Switch to the hardware protection state when connecting the security device 3 and entering the password, and monopolize resources such as SDIO, keyboard, mouse, touch screen and stylus to prevent viruses from stealing security information by controlling the operating system application programming interface.
Embodiment 3
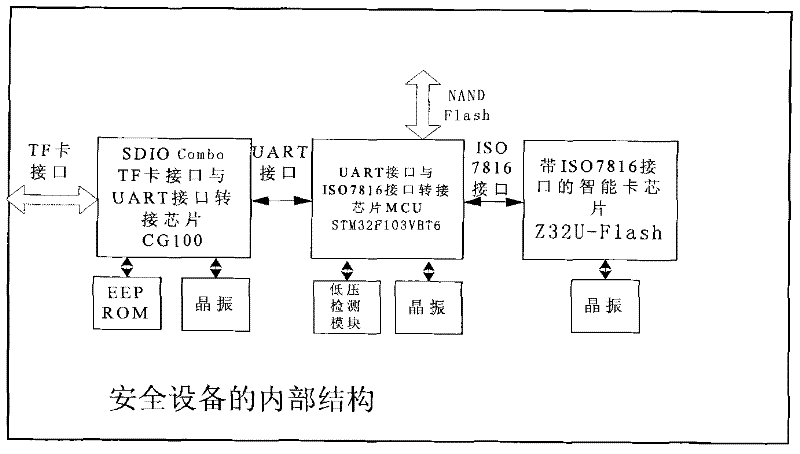
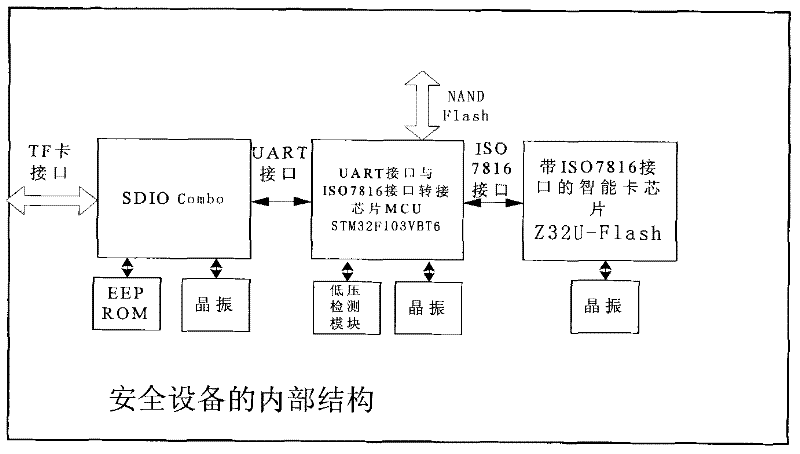
[0029] Embodiment three: a kind of security device for DRM system, such as figure 2As shown, the chip ATmega 16L is the control chip of the system, and the security module uses the Z32U-Flash series 32-bit security encryption chip of Shenzhen Zhongxing Integrated Circuit Design Co., Ltd., which conforms to the ISO1786 1-3 protocol, the working voltage is 5V, and is driven by a 3.579545MHz active The crystal oscillator provides the clock, and the reset and I / O ports of the card are controlled by ATmega 16L. The SDIO Combo chip is used as a bridge chip to complete the communication between the Z32UF and the smartphone. The CG100 used is a low-power TF card data communication transceiver chip produced by C-Guys that supports SDIO 1.0. Using its high-speed UART (HS-UART ) interface communicates with the serial port of ATmega 16L. The client sends the information to Z32U-Flash through SDIO Combo to complete data encryption, decryption, digital signature and safe storage. NAND Fl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com