Trusted authentication system and method for network transactions
A network transaction and authentication system technology, applied in the field of network transaction trusted authentication, can solve the problems of unpredictable behavior that cannot be discovered and handled in time, and user identity credibility that infringes on the interests of users, so as to ensure reliability and security, Good scalability, flexible and convenient deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] (case)
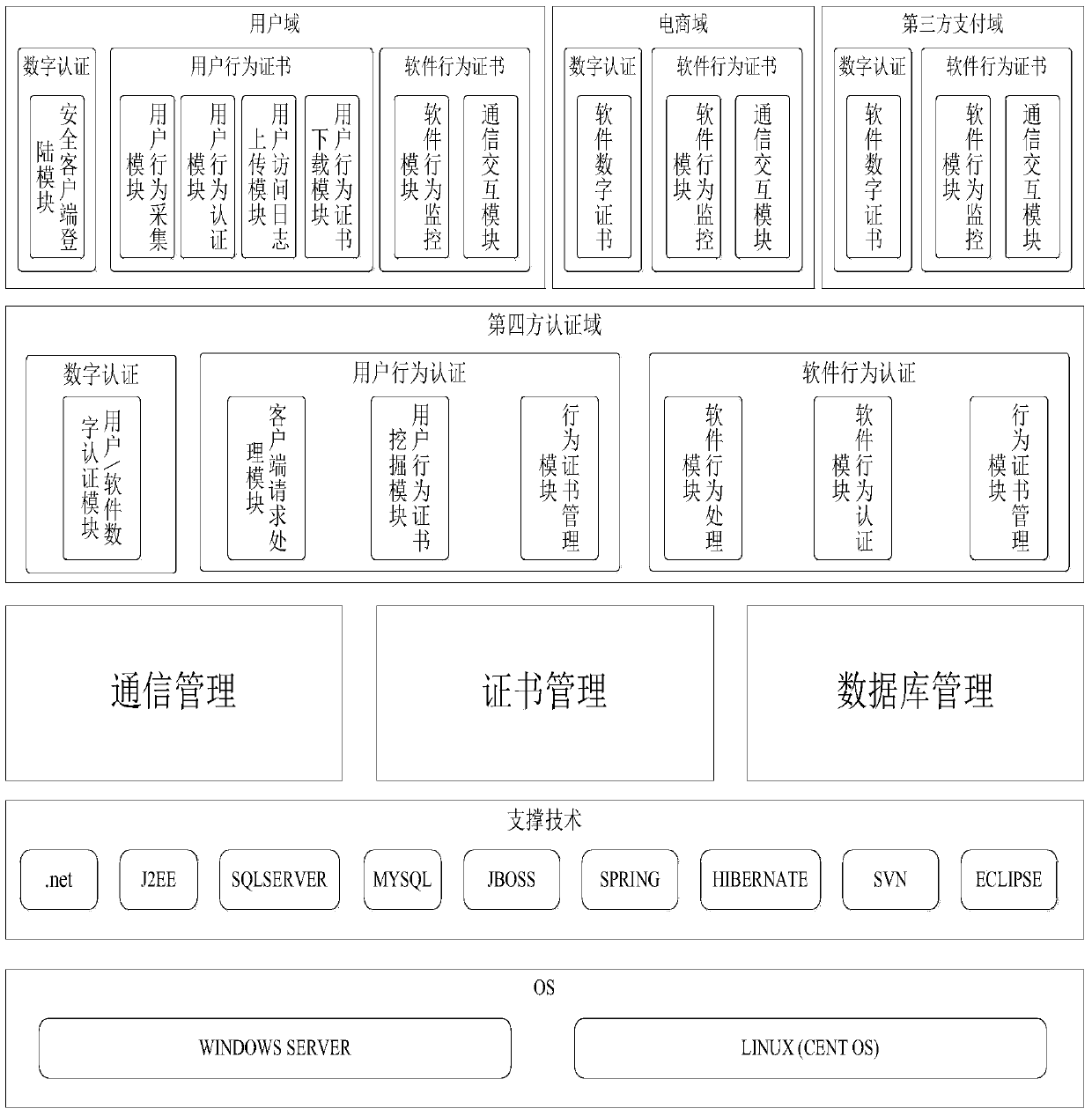
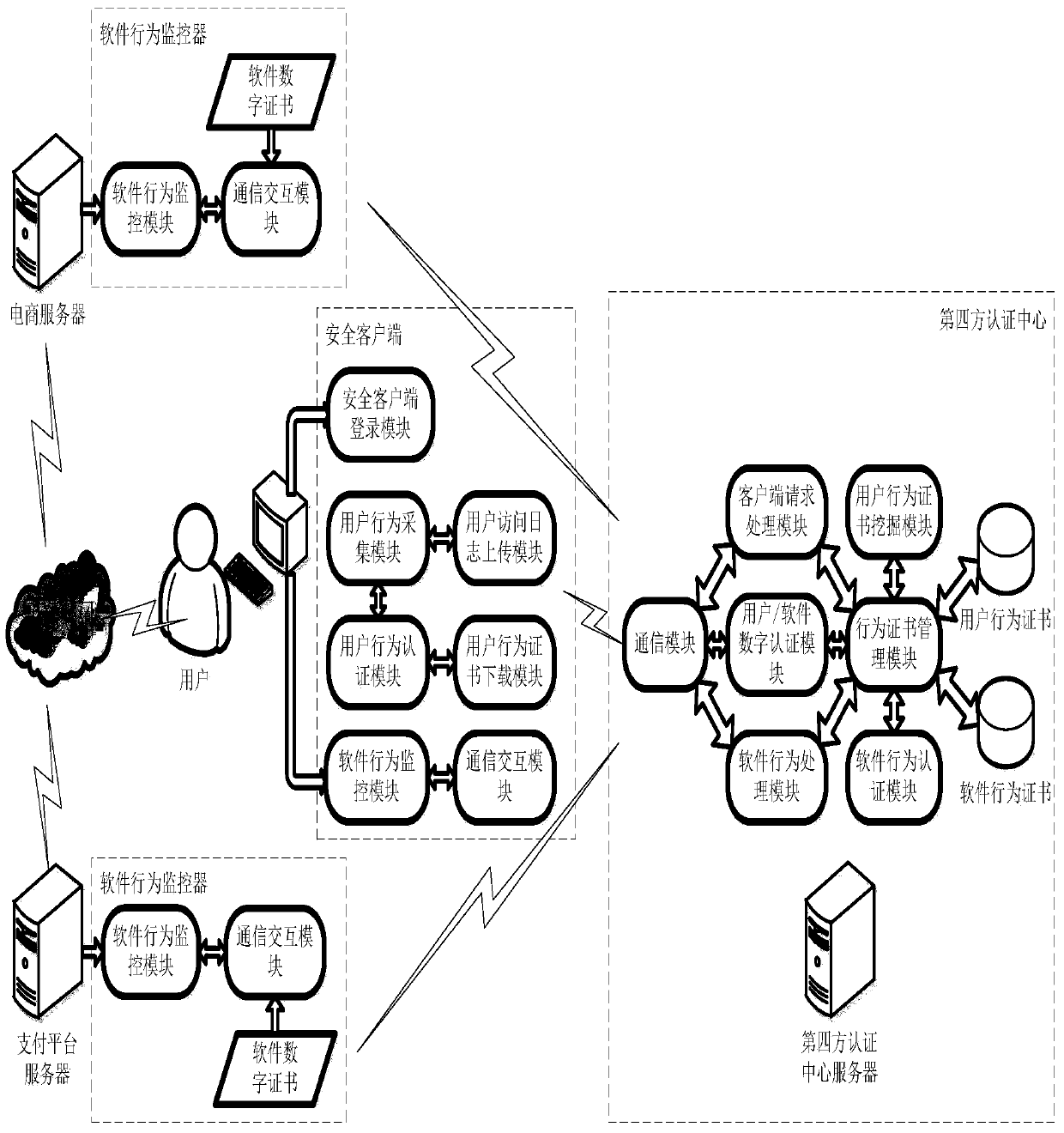
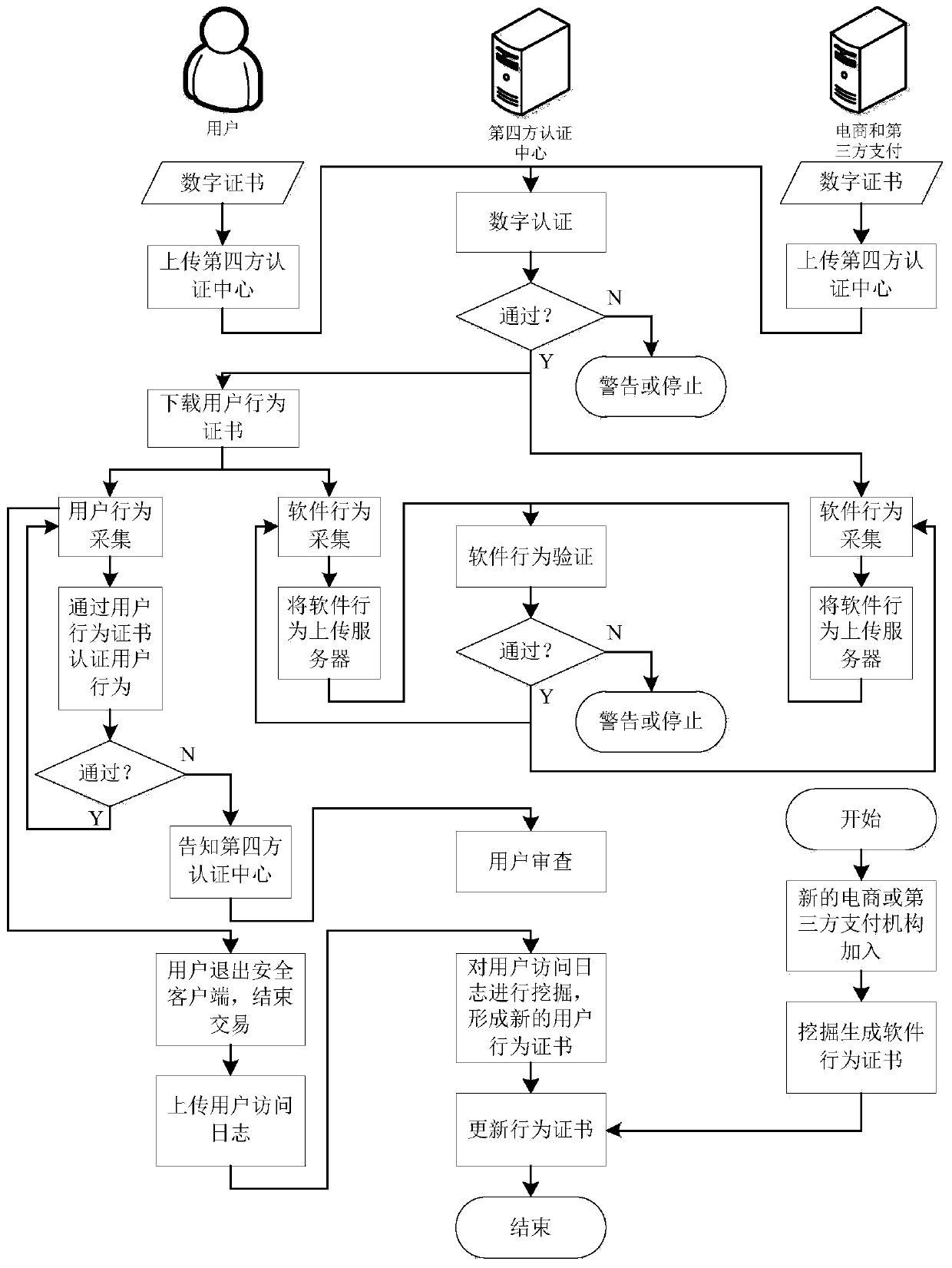
[0020] Network transaction trusted authentication system architecture diagram, such as figure 1 shown.
[0021] Such as figure 1 As shown, the bottom layer of the network transaction trusted authentication system supports two mainstream operating systems, Windows and Linux, so it can be deployed on both Windows and Linux systems, and has good cross-platform capabilities. Supporting technologies include .net, J2EE, SqlServer, MySql, JBoss, SPRING, and HIBERNATE, etc., providing good support for upper-layer application development. Above the supporting technology are three relatively low-level basic management modules, namely communication management module, certificate management module and database management module. The communication management module is mainly responsible for encapsulating the network communication function according to the specific requirements of this system, providing communication services such as data exchange for the upper layer, and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com