TBM key parameter intelligent control system and method
A technology of intelligent control and key parameters, applied in earth-moving drilling, mining equipment, mining equipment, etc., can solve the problems of untimely model update, inability to realize data closed-loop management, low data transmission efficiency, etc., to achieve a virtuous cycle, improve Effects of data quality and transmission efficiency, rich scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
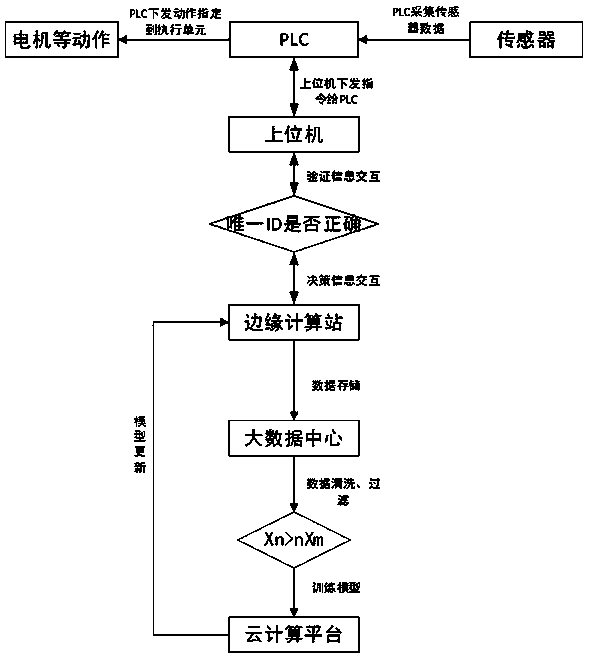
[0036] Embodiment 1: A kind of TBM key parameter intelligent control method, such as figure 1 shown, including the following steps:
[0037] S1, the PLC reads the data of the upper computer and establishes the unique identification ID of the upper computer;
[0038] PLC is connected with several host computers, and each host computer has at least one hard disk, and each hard disk has its own hard disk serial number X, PLC reads a hard disk serial number X of the host computer, and then uses MD5 The encryption algorithm processes the hard disk serial number X to obtain the machine code Y, and then intercepts the last N digits of the machine code Y as the unique identification ID of the host computer. In this embodiment, N=12; different hard disks have different hard disk serial numbers No. X, so the unique identification ID of each host computer is different.
[0039] The upper computer is equipped with dual network cards, one network card is used to communicate with the PLC,...
Embodiment 2
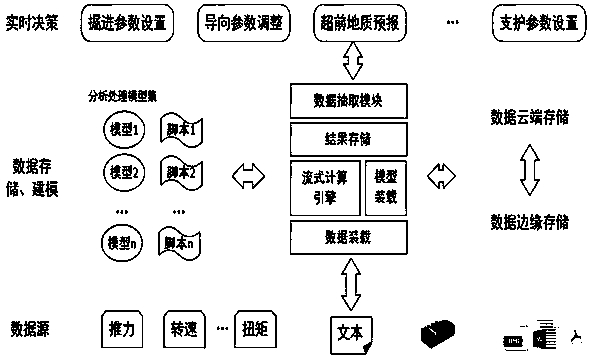
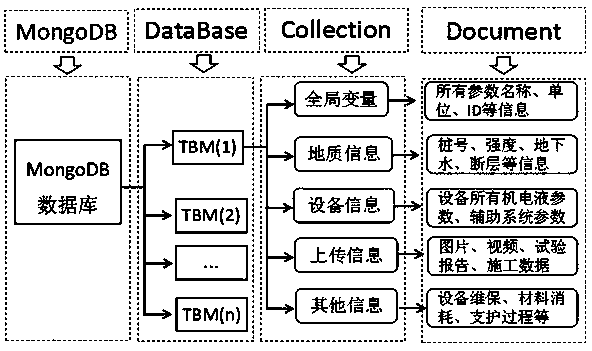
[0078] Embodiment 2: A TBM key parameter intelligent control system, including PLC, host computer, edge computing station and cloud computing platform, PLC is used as the execution unit, the host computer and PLC are connected, relevant parameters can be set through the host computer, and through PLC adjustment, the PLC collects relevant excavation data through the sensor on the shield machine and sends it to the host computer; the edge computing station stores the risk alarm model of the shield jamming machine, the risk alarm model of the cutterhead jamming machine, the rock mass perception model and the auxiliary driving model, the edge computing station is connected with the host computer, and the edge computing station is used to process the data received by the host computer, and store the processed data synchronously in the big data center; the edge computing station calls relevant The model calculates the optimal value of TBM key parameters, and adjusts the key parameter...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com