Network traffic data analysis method and system
A technology of network traffic and network flow, applied in digital transmission systems, transmission systems, data exchange networks, etc., can solve the problems of poor generalization performance, low detection rate, and reduced false alarm rate of network security anomaly detection technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
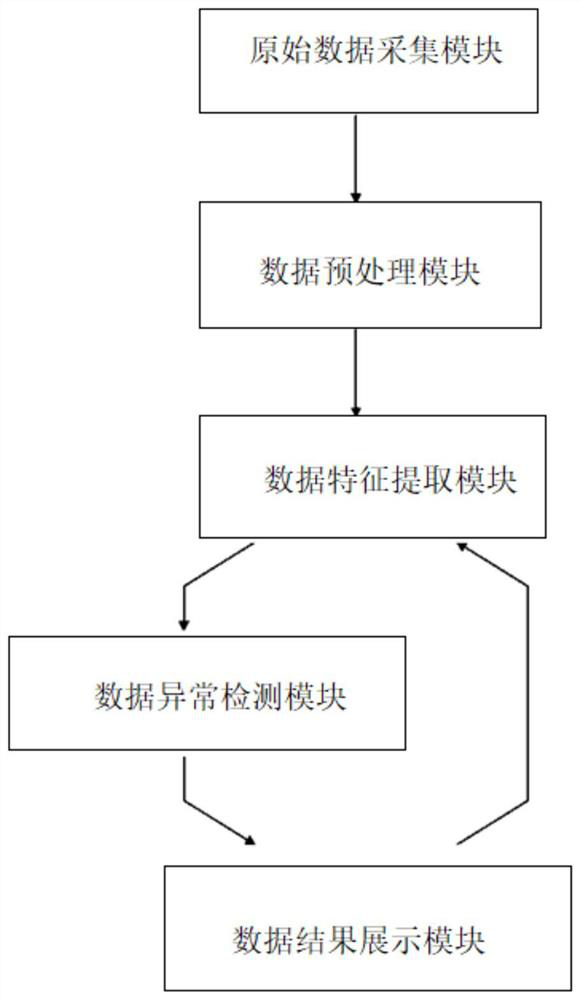
[0088] The present invention will be further described now in conjunction with accompanying drawing.
[0089] The present invention proposes a method for abnormality detection of network traffic data, the method comprising:
[0090] Step 1) Grab raw network traffic data in real time;
[0091] Specifically, an open source tool is used to capture the original network traffic data from the network environment in real time, and save it as a file in PCAP format; in this embodiment, the TCPDUMP tool is mainly used to capture the original network traffic data from the network environment in real time ;
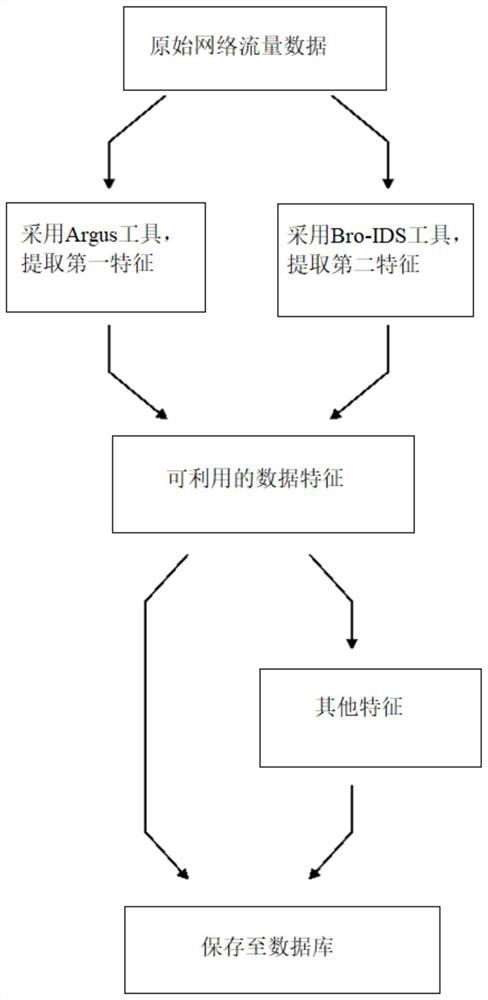
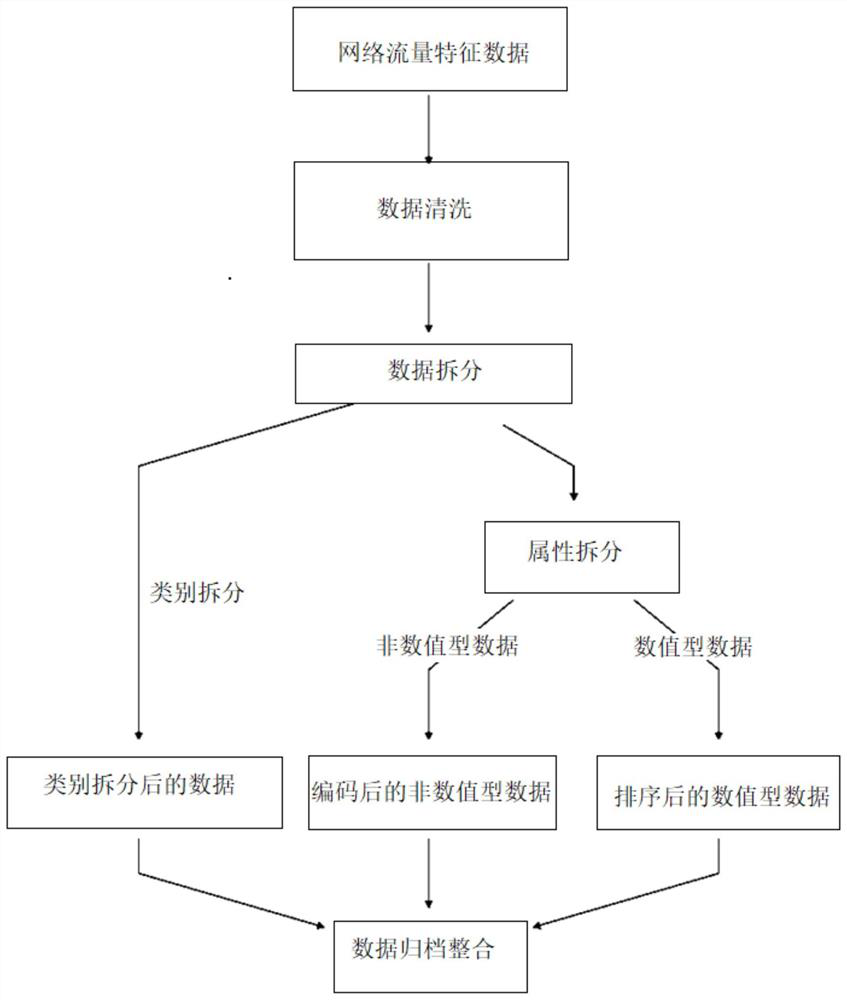
[0092] Step 2) extracting available data features from the obtained original network traffic data, and obtaining network traffic feature data;
[0093] Specifically, such as figure 2 As shown, the Argus tool is used to extract the first feature from the obtained original network traffic data, and the first feature includes: source IP address, source port number, target IP address...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com