Analogue biological immunological mechanism invasion detecting method
A technology of intrusion detection and biological immunity, applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problems of uncertainty, difficulty in providing statistical models, ambiguity, etc., and achieve the effect of strong robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
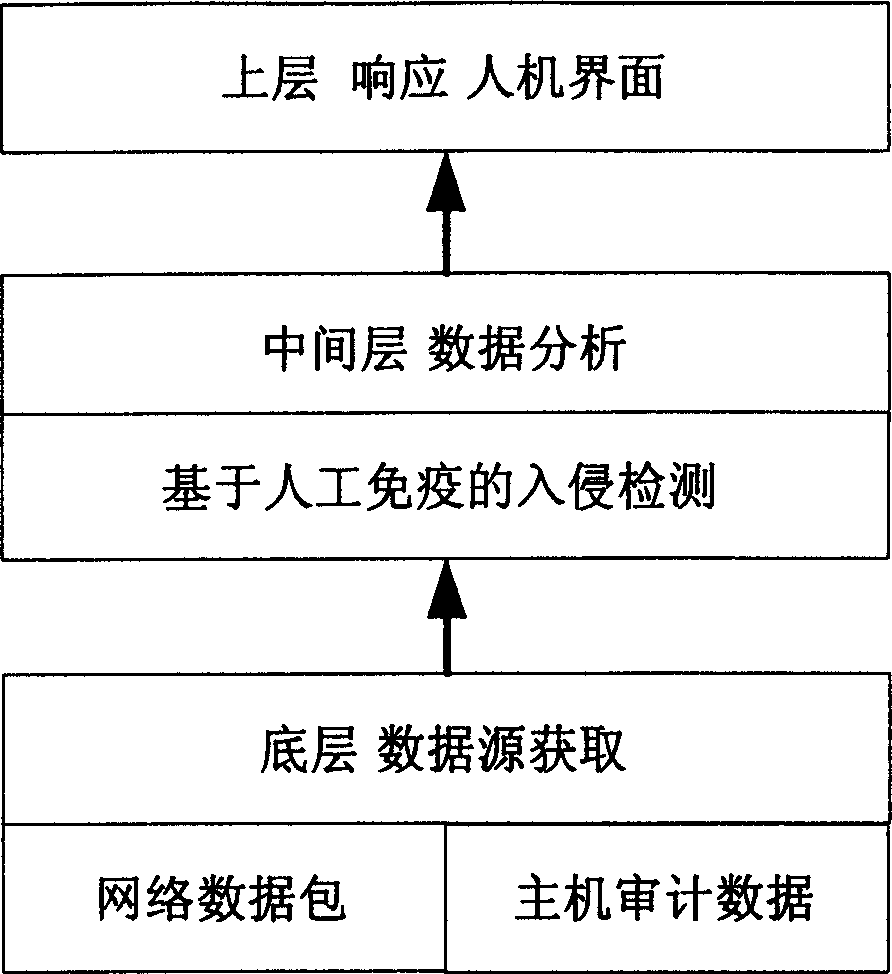
[0033] The detection method is an intelligent method, such as figure 1 As shown, its data analysis is relatively independent from the underlying data source acquisition layer and the upper application system presentation layer, and can be applied to abnormal detection of various data sources, including host audit data sources and network packet data sources.
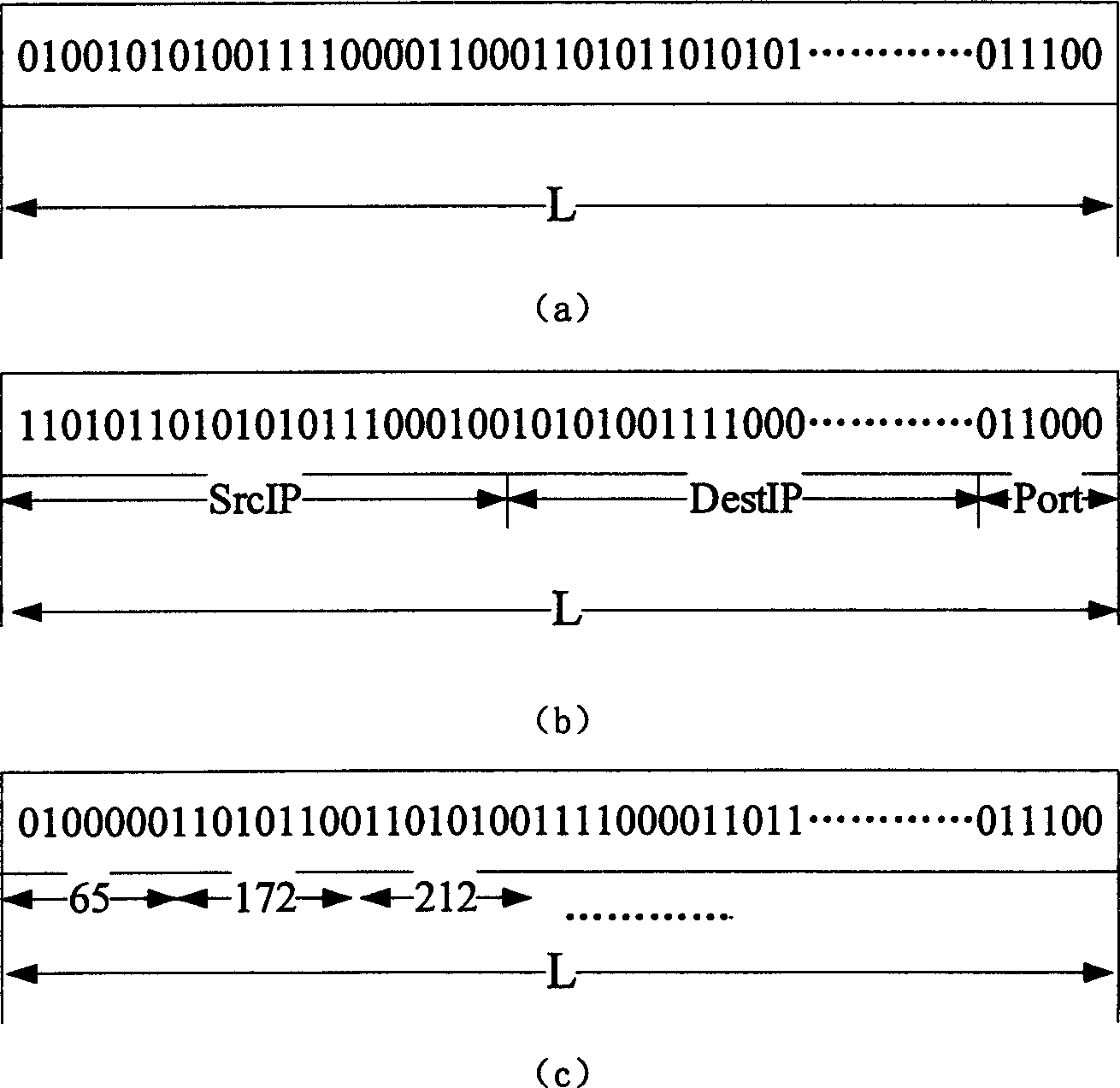
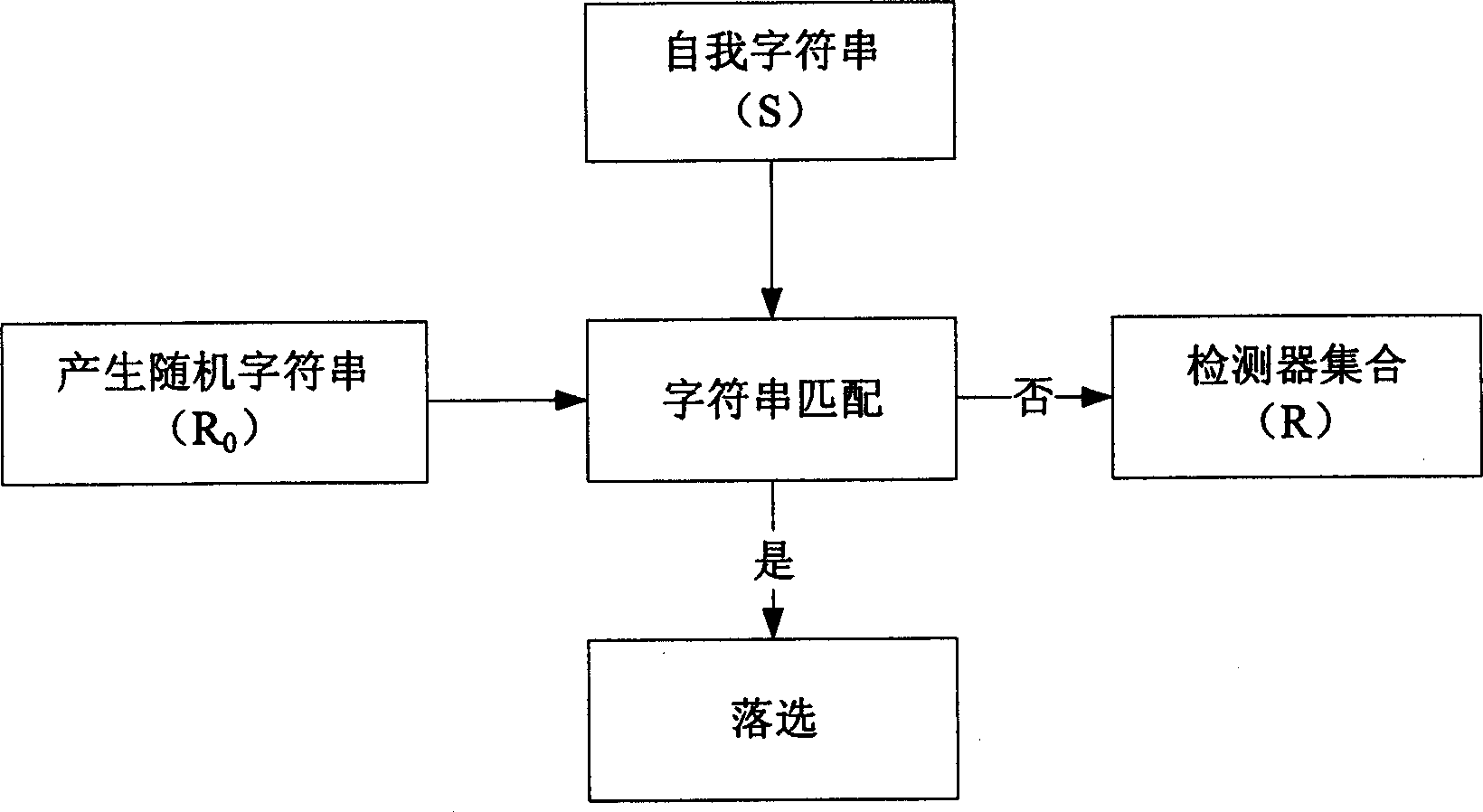
[0034] The invention includes the system architecture of the intrusion detection system, the specific functions of each component, the workflow of the intrusion detection, and the data collection, pattern expression, feature extraction and matching rules in the detection algorithm adopted.
[0035] The general architecture of an intrusion detection system is figure 1 As shown, it can be roughly divided into three layers: data source acquisition at the bottom layer, data analysis at the middle layer, and man-machine interface and response at the upper layer. There are two main sources of underlying data sources: network ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com