Smart power grid user access authorization method
A smart grid and smart power technology, applied in the field of smart grid user access authorization, can solve the problems of easy theft of user privacy and sensitive information, inconvenient system and business expansion, lack of strict authentication and encryption, etc., to help the network life cycle. and energy control, improving simplicity and scalability, reducing the probability of being cracked
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The embodiments of the present invention are described in detail below, and examples of the embodiments are shown in the accompanying drawings. The embodiments described below with reference to the accompanying drawings are exemplary and are only used to explain the present invention, but should not be construed as an explanation of the present invention. limit.
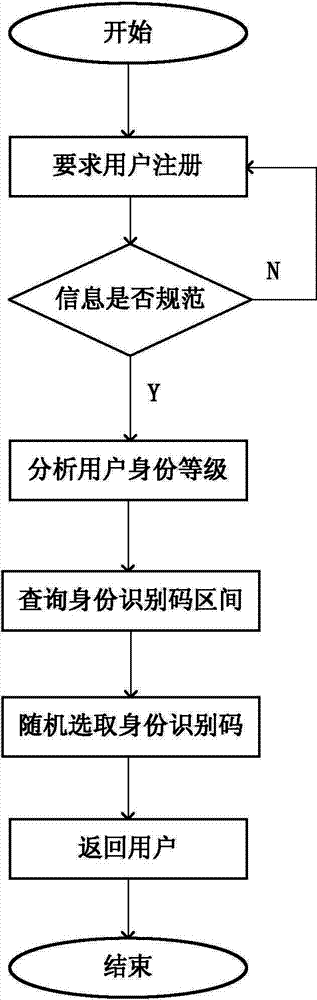
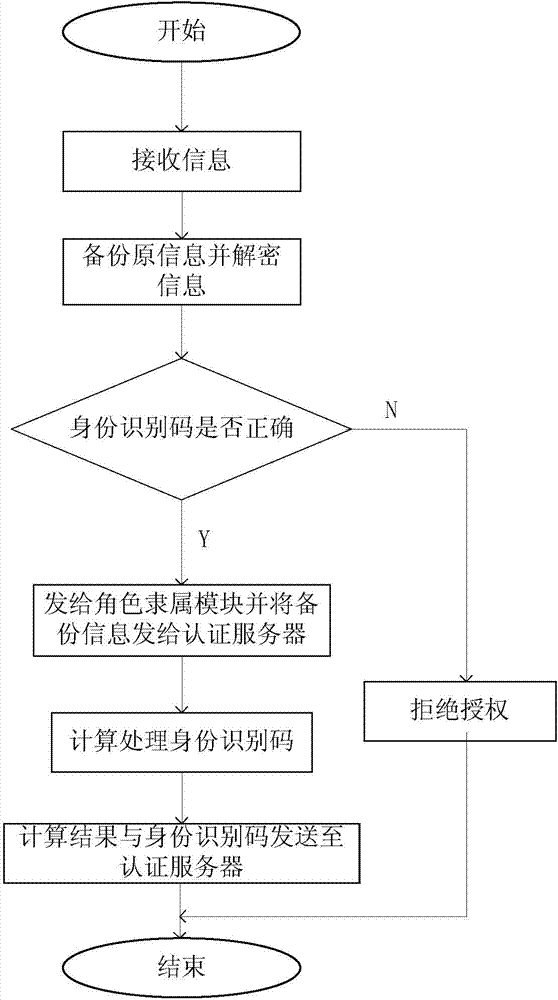
[0047] The invention provides a data security transmission method in a body area network system, in particular a smart grid user access authorization method, which includes the following steps:
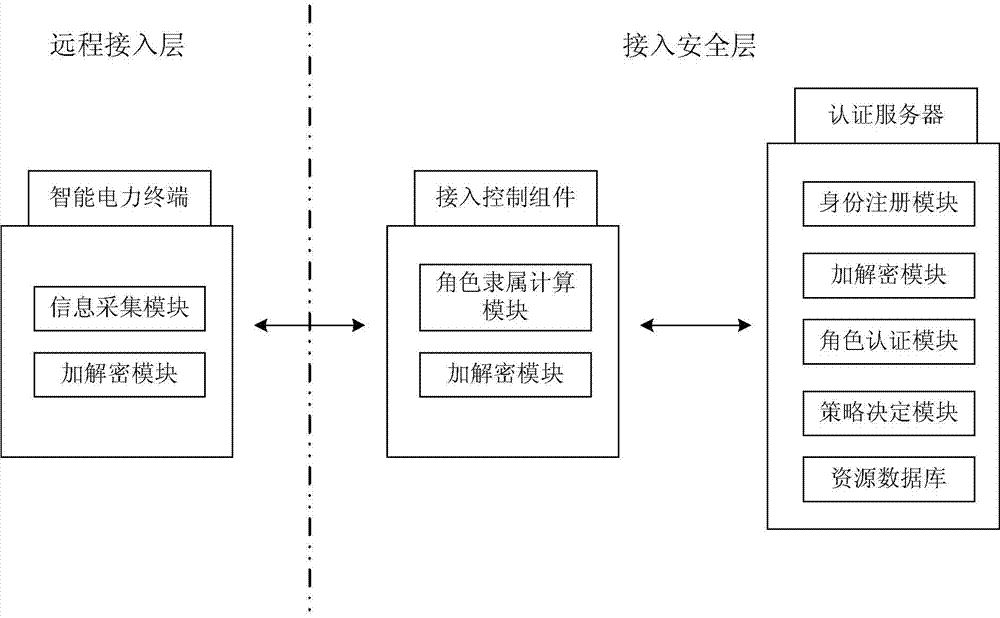
[0048] The first step: deploy the smart grid security access system according to the hierarchical structure, the remote access layer is the smart power terminal, the access security layer is the access control component, the access control component and the authentication server; after the smart power terminal completes the security access authentication The authority credential information is sent to the access contr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com