Instruction-driven commercial password special processor system
A processor system, commercial encryption technology, applied in the architecture with a single central processing unit, electrical digital data processing, instruments, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] In order to more clearly illustrate the specific embodiments of the present invention or the technical solutions in the prior art, the following will briefly introduce the drawings that need to be used in the description of the specific embodiments or the prior art.
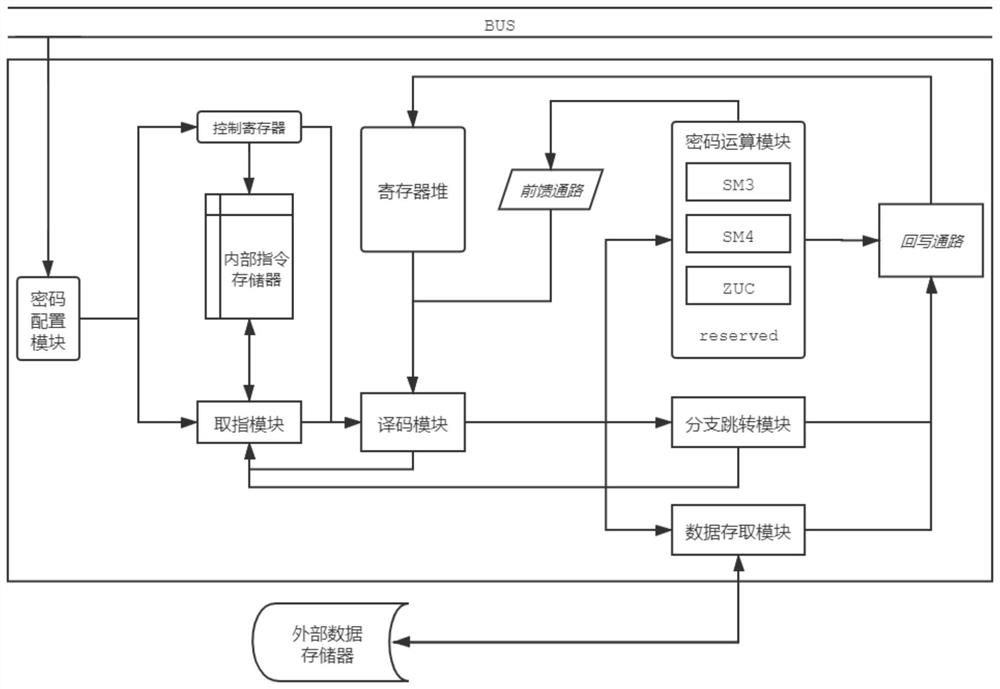
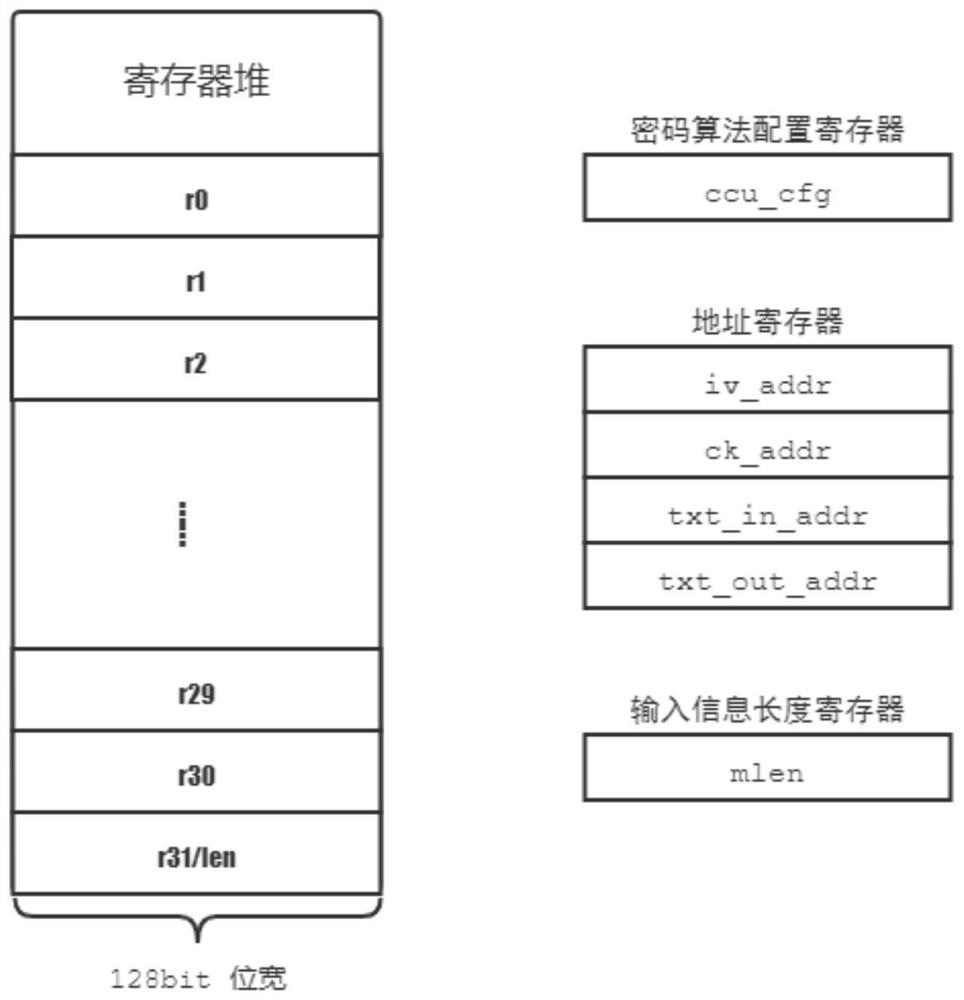
[0046] refer to figure 1 and figure 2 , an instruction-driven commercial cryptographic processor system, designed corresponding instructions for the SM3 cryptographic hash algorithm, SM4 block cipher algorithm and ZUC Zu Chongzhi sequence algorithm announced by the State Cryptography Administration of China, and also pre-programmed for other new cryptographic algorithms. The coding space is reserved, and it has certain scalability.
[0047] available from figure 1 It can be seen in the figure that when the special processor for encryption and decryption needs to be woken up, the central processing unit needs to write the cryptographic algorithm configuration information into the control register of the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com