Secret communication method based on fractional Fourier transform order multiplexing
A fractional-order Fourier and secure communication technology, applied in the field of communication, can solve problems such as the inability to maintain the security and legality of the network environment, the inability to effectively prevent the transmission of illegal information, and the inability to locate the location of the attack source. Information security and social security, reducing the probability of data leakage, improving the effect of security and legality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
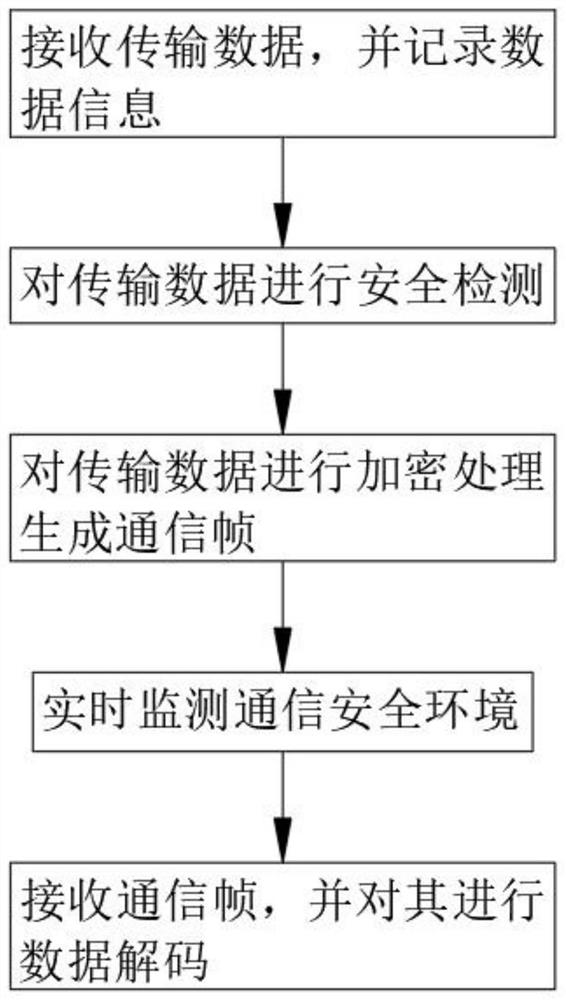
[0041] Refer figure 1 , A confidential communication method based on the multiplexing of the fractional Fourier transmissive sequence, the present embodiment mainly discloses a monitoring and analysis method:
[0042] Receive transfer data, and record data information: The transmission module receives the transmission data sent by the user, collects its related information, and classifys the collected, and constructs the encrypted record table, and record each group information.
[0043] Specifically, first, the transmission module collects information of the data type, data length, and data size of the transmitted data, and enters the encrypted record table, each group information record is completed, the transmission module is time to receive the transmitted data, respectively. Collect, and mark it as a transmission time, and record it in an encrypted record table.
[0044] Safety detection for transmission data: The transmission data sent by the user is monitored, analyzed and ...
Embodiment 2
[0053] Refer figure 1 A confidential communication method based on the scalletary flourishing leaf transform order, except that the above embodiment is the same as the above embodiment, the present embodiment mainly discloses an analytical treatment method:
[0054] Real-time monitoring of communication security environments: real-time monitoring of communication frame transmission environments, and analyzes external attack behaviors, and positioning the source of IP addresses and feeds back to the staff.
[0055] Specifically, when the communication frame is attacked during the transmission process, the firewall is started to defend the attack data, and confirm the attack source IP address through the firewall, communicate with the GPS satellite, and grab the IP address location area image At the same time, the real address of the grabbed is given to the staff, and the alert information is transmitted to the relevant unit. When the firewall cannot block external data invasion, th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com