Information processing method, system and device for enhancing access security
A device and dynamic device technology, applied in the field of information security, can solve the problem of no multi-dynamic device verification shared code, etc., to prevent man-in-the-middle attacks and integrity damage, ensure consistency, and improve the effect of security level
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
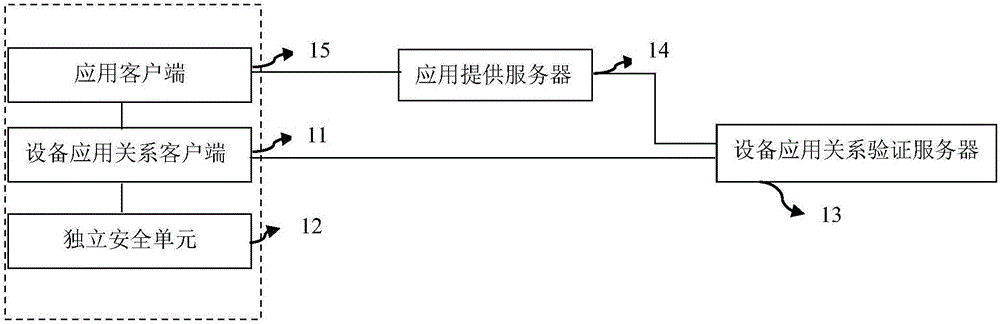
[0157] Such as figure 1 As shown, it is a schematic structural diagram of an information processing system provided by an embodiment of the present invention, including a device application relationship client 11, an independent security unit 12, a device application relationship verification server 13, an application providing server 14, and an application client 15, wherein:
[0158] Device application relationship client 11 refers to the general term for all software collections that run on the user end device to provide user applications with the service of initiating device access credentials, local information security encryption and decryption services, verification and signature functions, and provide UI exchanges with users at the same time , responsible for working directly with the security independent unit, communicating with the device application relationship verification server, assisting or directly generating keys, updating; providing security authentication o...
Embodiment 2
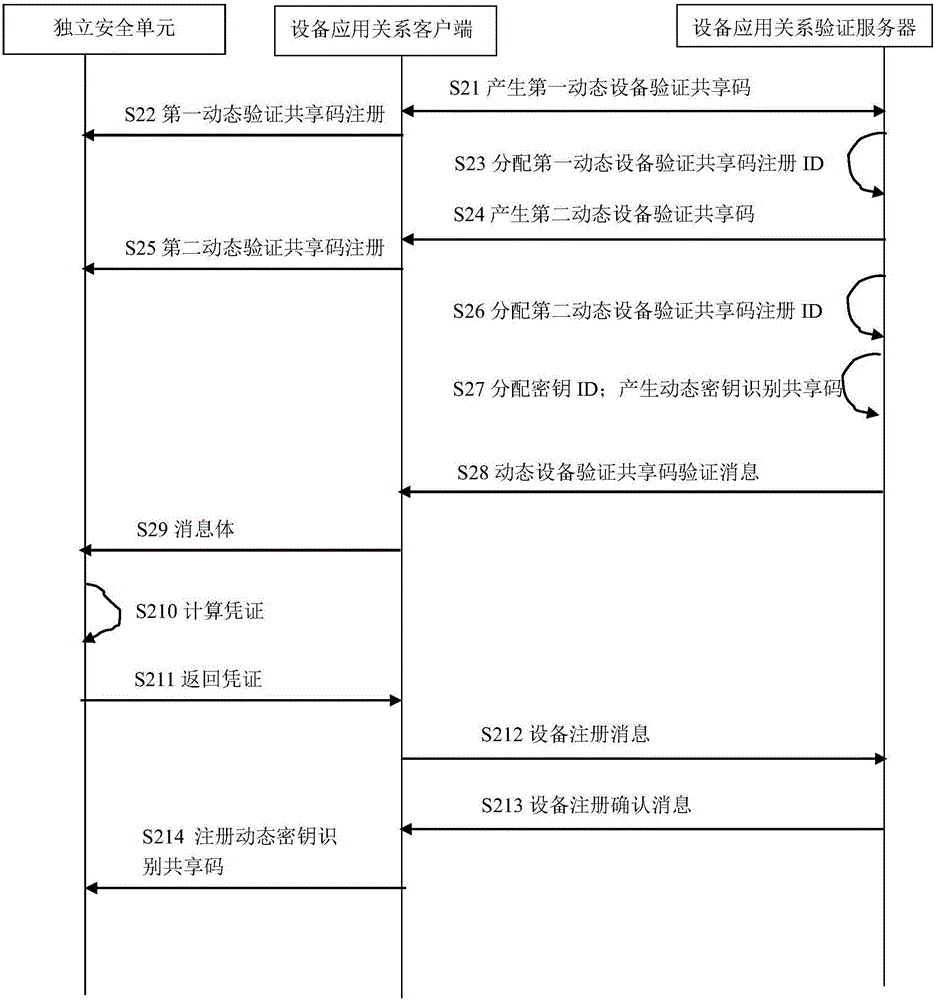
[0164] In specific implementation, such as figure 2 In the figure is the flow chart of device application relationship client registration described in the embodiment of the present invention;
[0165] Step S21 generates the first dynamic device verification shared code, and step S24 generates the second dynamic device verification shared code. The shared code generation algorithm can use the ECDH algorithm, the Diffie-Hellman key exchange algorithm, or the reliable delivery of the RSA key; better use ECDH algorithm can obtain higher calculation efficiency and shorter key length under the same security level;
[0166] Steps S21 and S25 need to calculate and save the key seed information on the device application relationship client and the independent security unit, and then generate the final key based on the seed information as the first dynamic device verification shared code and the second dynamic device verification shared code ;
[0167] Method 1: The device applicati...
Embodiment 3
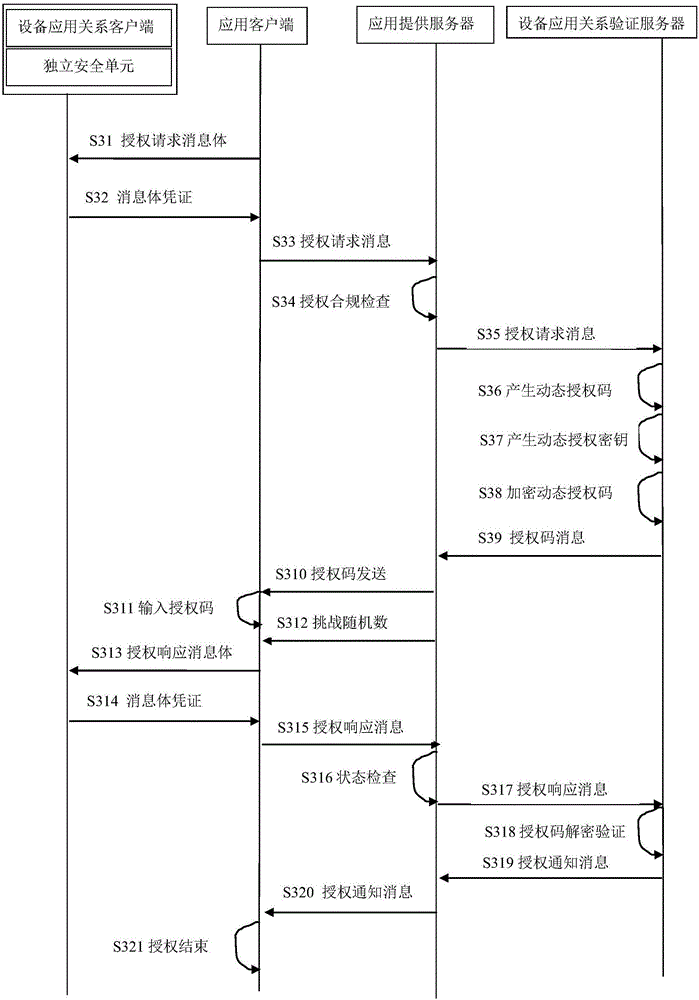
[0189] The present invention can be used for verification of device application relationship of public network Internet users, user access device and application relationship verification;
[0190] Such as image 3 It is an email application account authorization application relationship client device process:
[0191] During specific implementation, the email application client only talks to the device application relationship client,
[0192] Step S31 calculates the message body certificate, and the device application relationship client uses such as figure 2 Steps S210, S211, and S212 complete the calculation of the requested message body certificate, return the M certificate to the application client through S32, and the email application client uses this certificate as the current message authentication part to be included in the S33 authorization request message;
[0193] During specific implementation, the information in the authorization request message in steps S33...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com