Soft puf based on camellia encryption algorithm
An encryption algorithm and ciphertext technology, applied in computing, computer security devices, and key distribution, can solve the problems of low uniqueness and randomness of microprocessor PUF, low difficulty in cracking microprocessor PUF, unfavorable chip authentication, etc., and achieve Avoid instability, good uniqueness and randomness, and high security effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
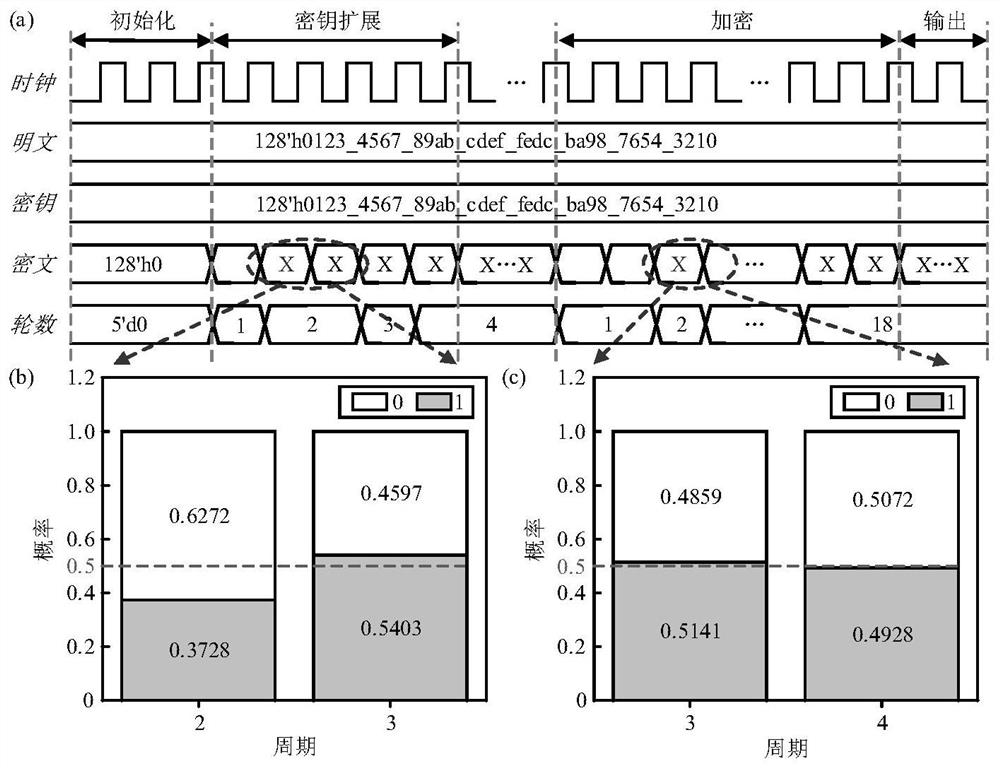
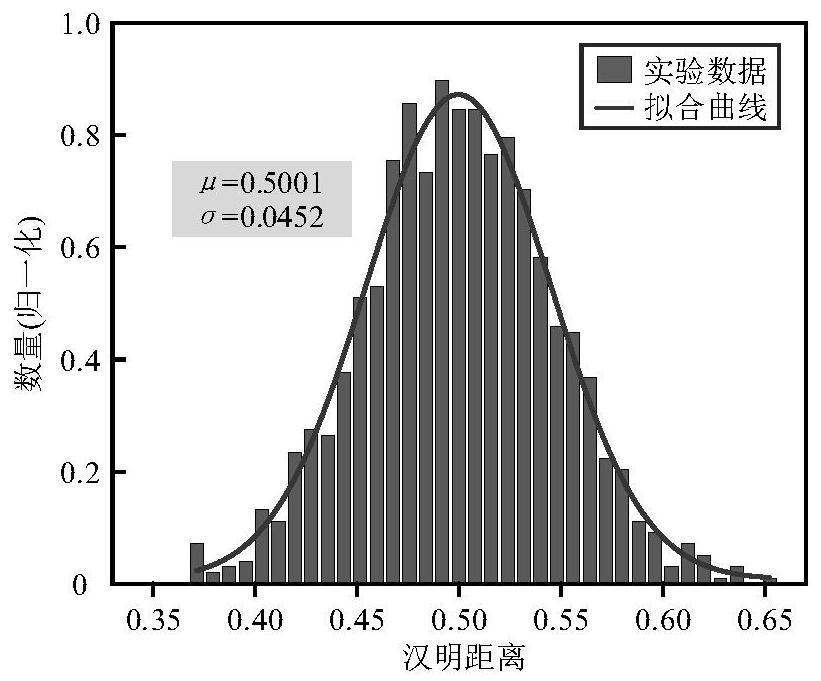
[0032] Embodiment: A soft PUF based on Camellia encryption algorithm, including a hardware platform, the hardware platform is a 128-bit Camellia encryption algorithm hardware circuit, and the 128-bit Camellia encryption algorithm hardware circuit has the following ports: used for inputting a 128-bit key signal K 1 (128-bit binary data) 128-bit key input port key_in[0]-[127], used to input 128-bit plaintext signal P 1(128-bit binary data) 128-bit plaintext input port data_in[0]-[127], clock input port clk, 128-bit ciphertext output port data_out[0]-[127]; 128-bit Camellia encryption algorithm hardware circuit 128-bit subkey k is pre-stored in 1 , 128-bit subkey k 2 and timing path information, 128-bit subkey k 1 and 128-bit subkey k 2 They are 128-bit binary data, and 128-bit subkey k 1 and 128-bit subkey k 2 different from each other, timing path information including critical path delay T path and 128 timing paths directly related to the 128-bit ciphertext output port d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com