Individual cryptoprotective complex
A complex and individual technology, applied in the payment system, digital data protection, payment system structure, etc., can solve the problem that the PC card cannot be used to realize various functions, the card cannot determine the object of confidential communication, and the key replacement cannot be established, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
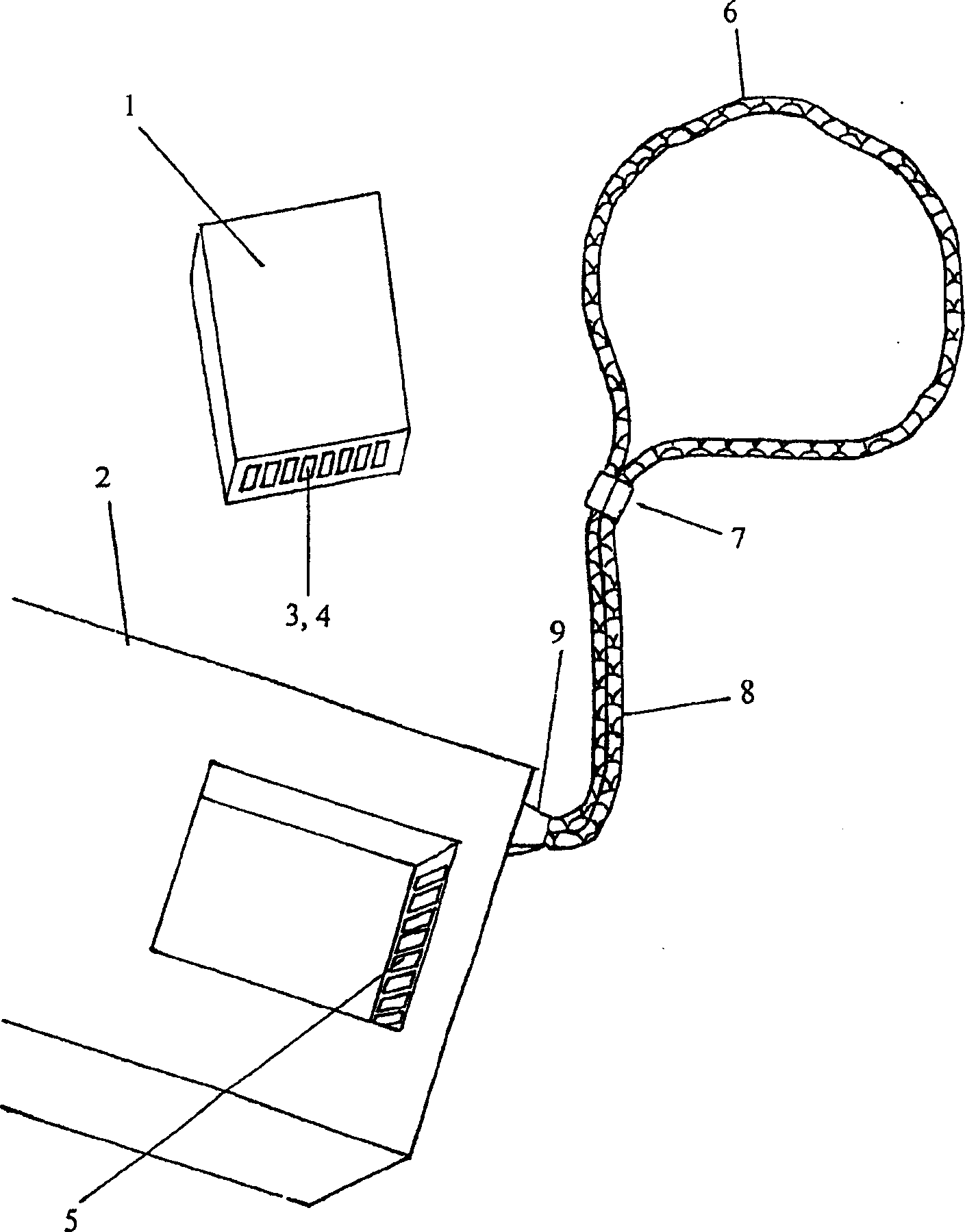
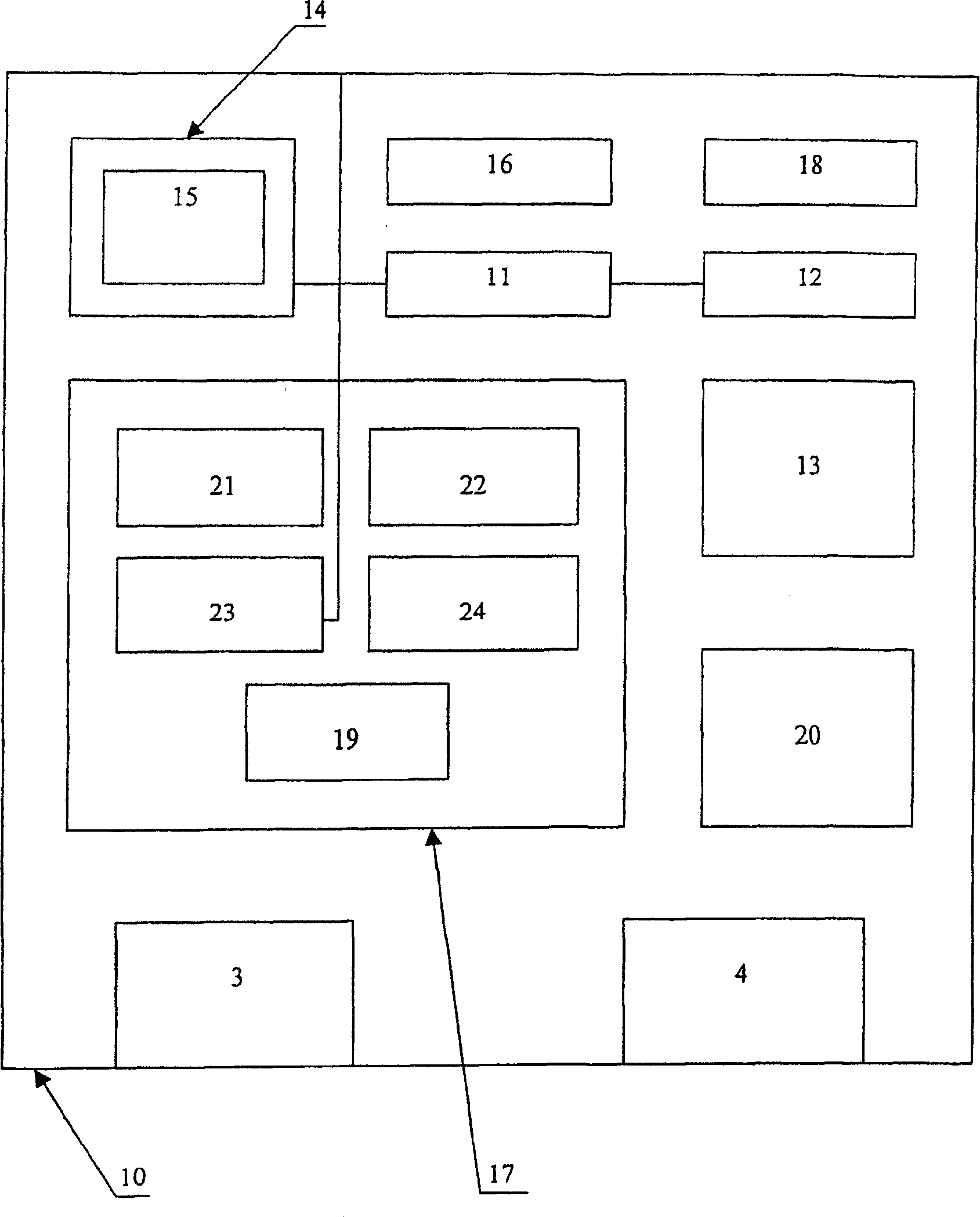
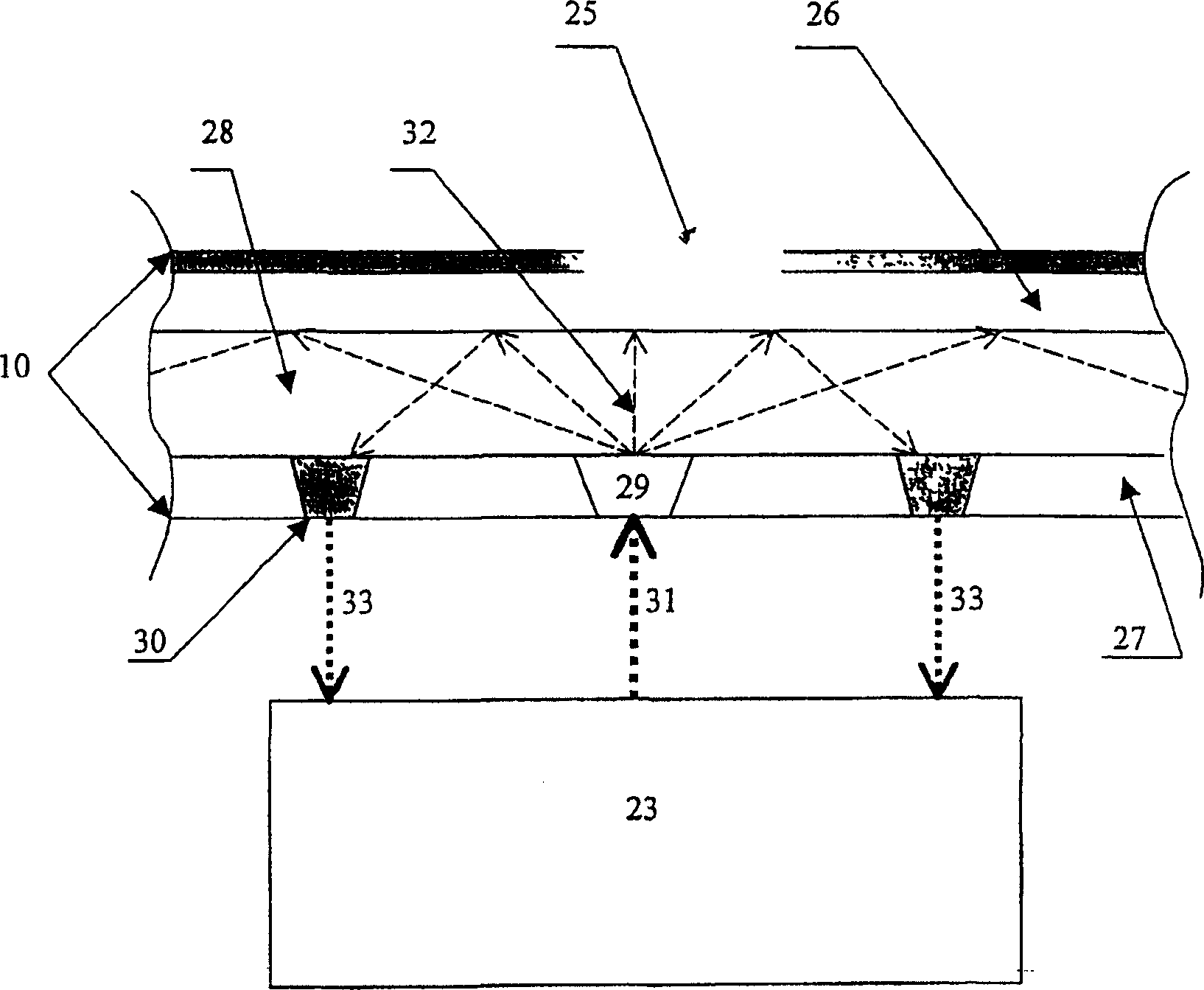
[0078] A personal security complex formed in accordance with the present invention works as follows. User connects box 1 ( figure 1) and terminal 2, additionally activating the box by supplying a job start signal. The activated box outputs a user access permission request to the user. By means of the terminal device 2, the user enters his or her identification data, and the box checks the entered identification data with the user's previous input and saves it in the PROM 13 ( figure 2 data in ). In the case of consistent data, the box continues to work. In order to simplify and speed up the additionally working user identification procedure in the execution of secure operations, the user should connect the identification wristband 6 and the fixed sensor by means of wires 8 , said wristband being worn on the user's hand by means of a latch 7 . After successfully identifying the user for the first time, the box checks for the presence of the connected identification wristba...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com