Method for Controlling and Recording the Security of an Enclosure
a technology for controlling and recording enclosures, applied in process and machine control, program control, instruments, etc., can solve the problems of difficult code burning after the device has been manufactured, difficult to program non-volatile memory, and interrupt the manufacturing process, so as to improve security, facilitate manufacturing, and be more reliable to operate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
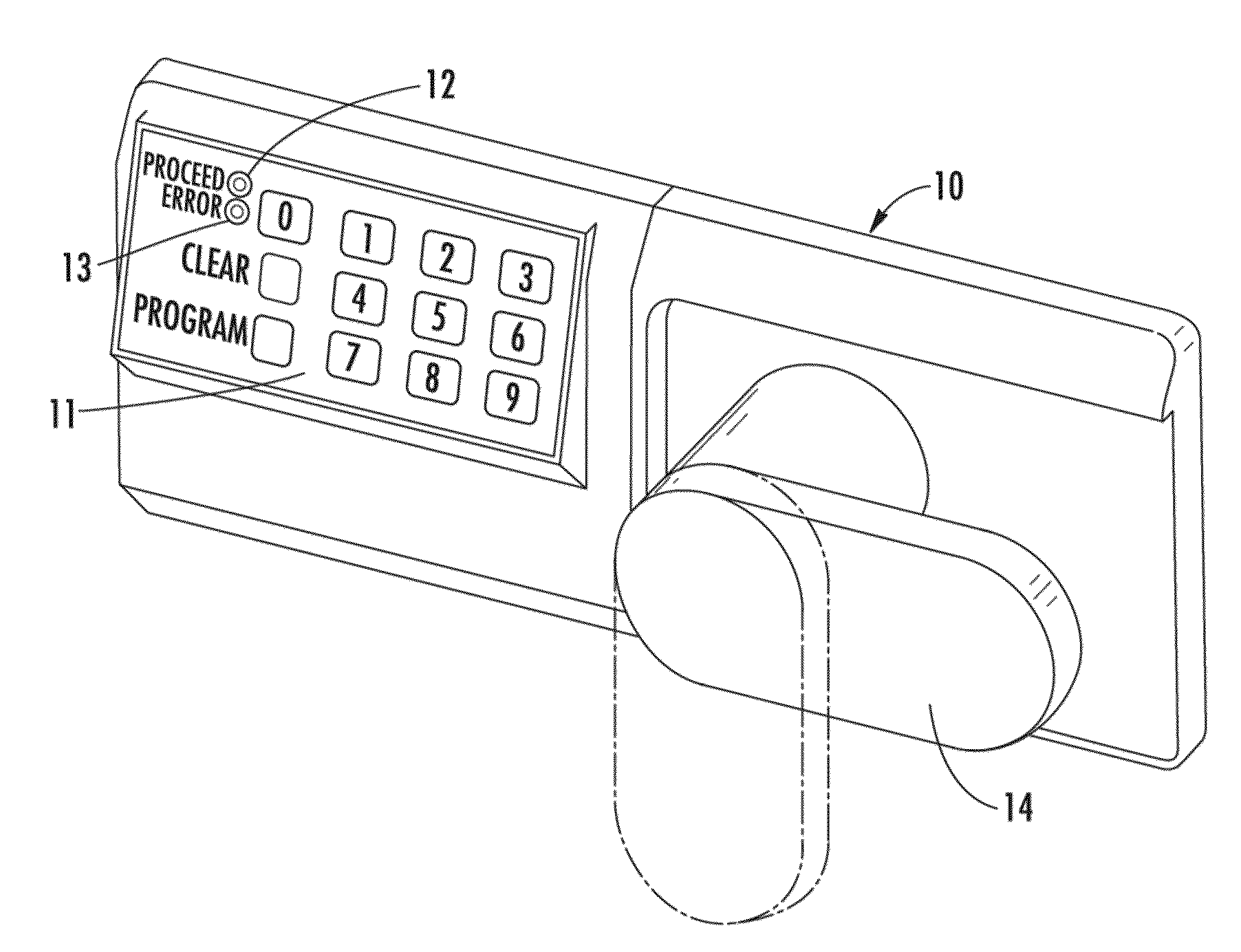
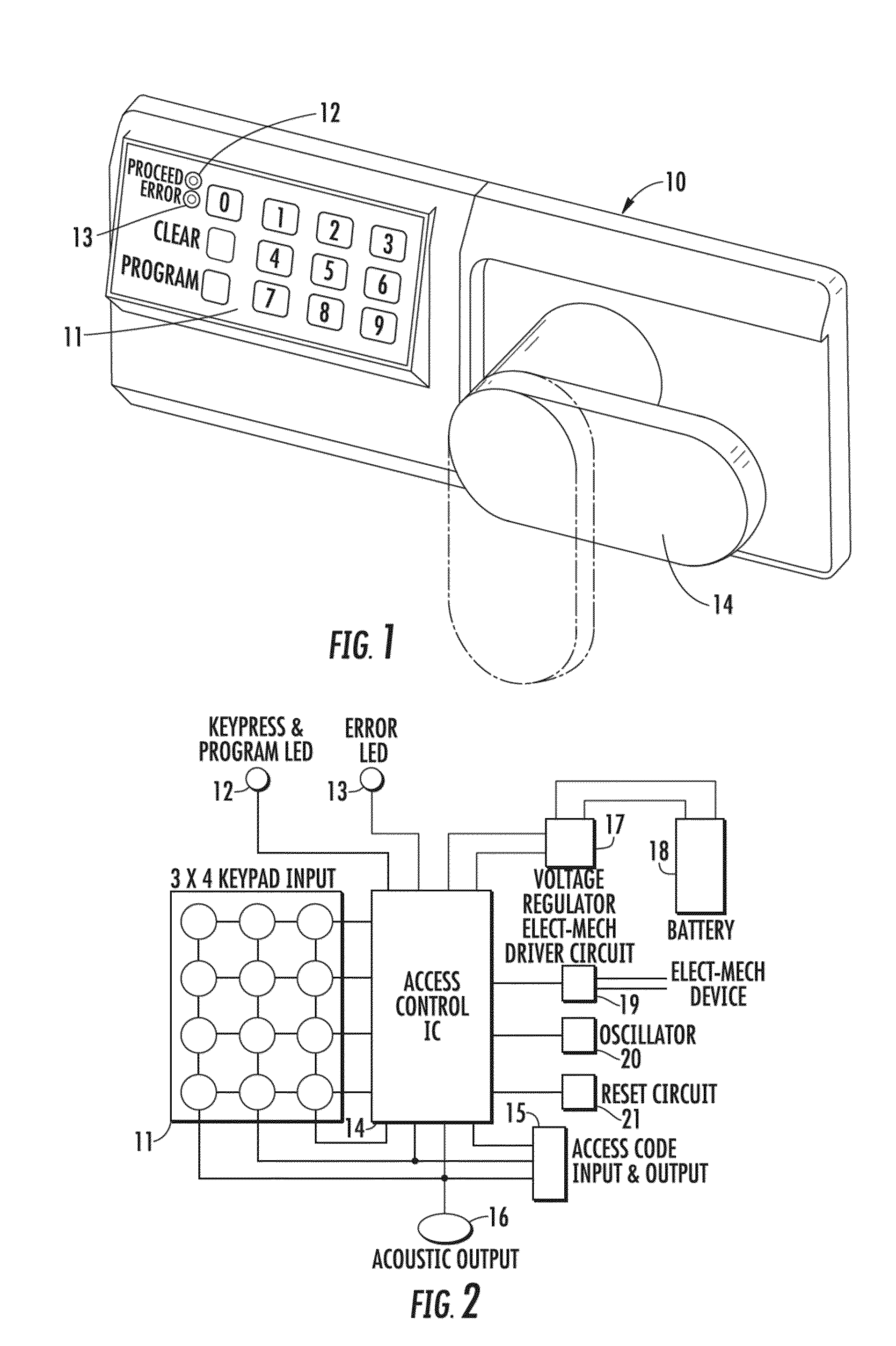
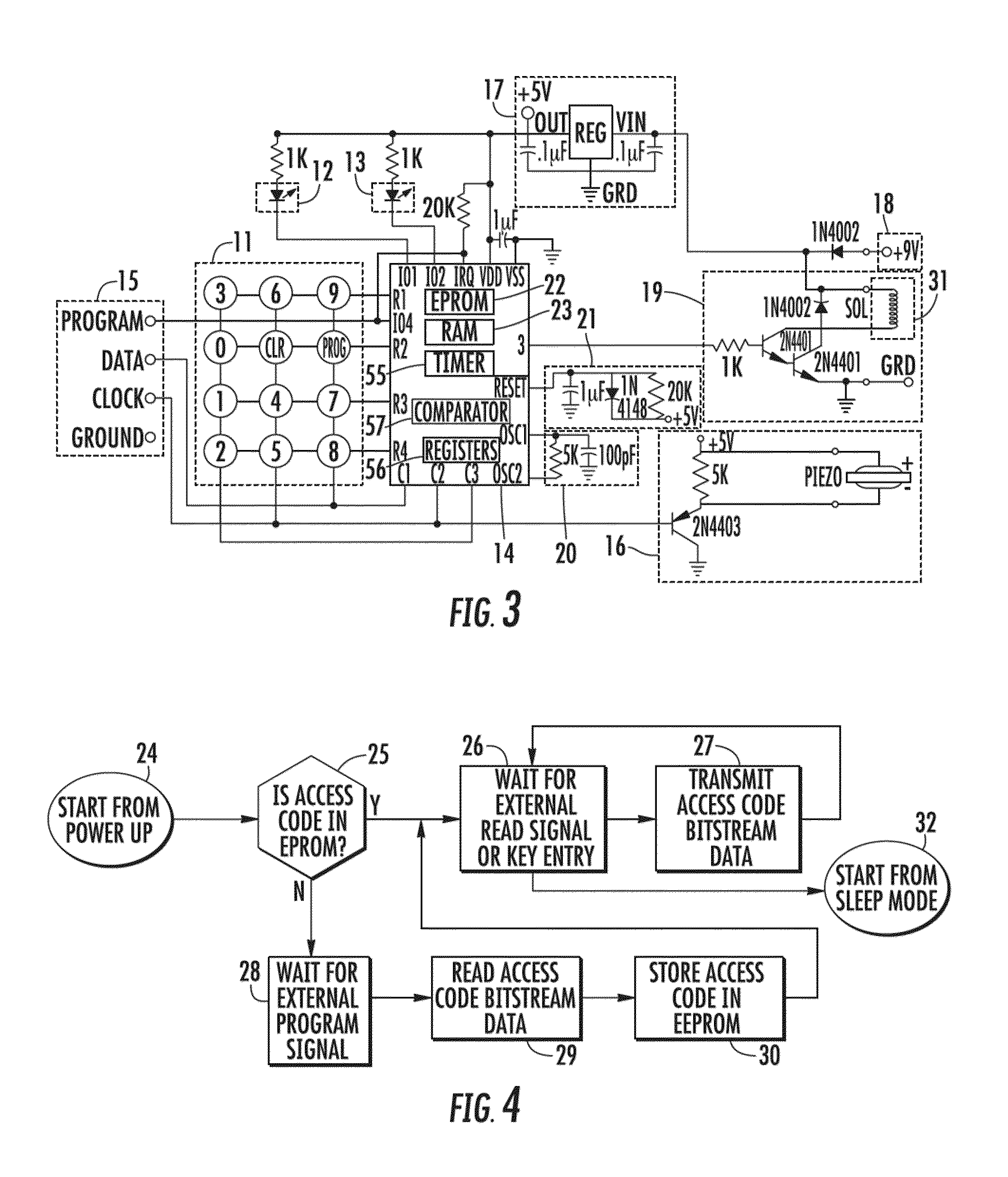
[0126]In an embodiment, an electronic system and method is provided for controlling access of devices. For instance, some devices operating in the field are in a relatively unsecured environment, and it is necessary to control the access or usage of the devices so that they are not accessed by unauthorized persons or that they are not used at unauthorized times or places. The devices that may be advantageously controlled using the system and method of the invention include, for example, safes, appliance devices such as vending machines, coolers, fountain drink dispensers, etc., power tools used in construction sites, shipping containers, and many other types of devices. It will be appreciated that the above list is meant only to provide some examples and is by no means intended to limit the applicability of the invention.
[0127]Referring to the drawings, there is shown in FIG. 1 an illustrative electronic access control device 10 having a keypad 11, light emitting diodes (LEDs) 12 an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com