Independent transparent security audit protection method facing real-time database
A security auditing and database technology, applied in the fields of digital data protection, electronic digital data processing, computer security devices, etc., can solve the problems of weak misoperation control ability, few real-time databases, no security restriction protection and auditing system, etc. Improve overall performance and the effect of efficient access control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
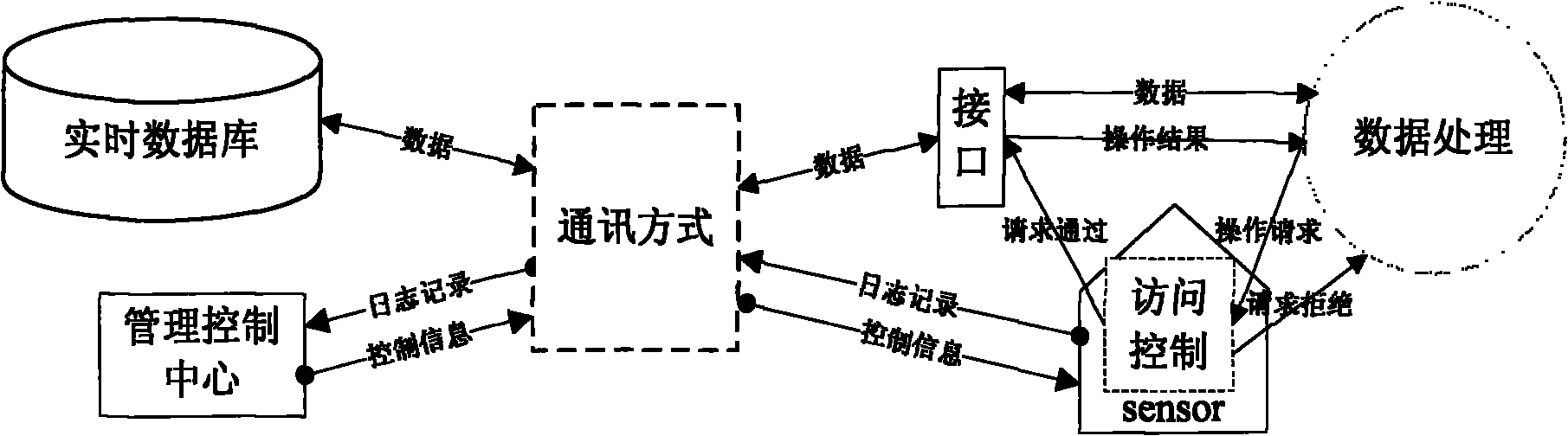
[0038] figure 1 A schematic diagram of adding transparent security audit protection to real-time database is given.
[0039] Before the security audit is added, the application system can directly access the real-time database through the interface, and its operation is not subject to any restrictions, which is very dangerous for applications with high data confidentiality, such as figure 1 The data flow shown in black letters.
[0040] After adding security audit, its function is divided into two parts: management control center and listener, such as figure 1 Color accented section shown. The management control center is generally started together with the real-time database, and is mainly responsible for management configuration, log reading and writing and processing, interface support, etc. By default, access control and auditing are turned off, and they need to be turned on by security administrators and audit administrators. In addition, the system administrator can ...
Embodiment 2
[0054] Embodiment 2 mainly describes the access control method suitable for real-time database
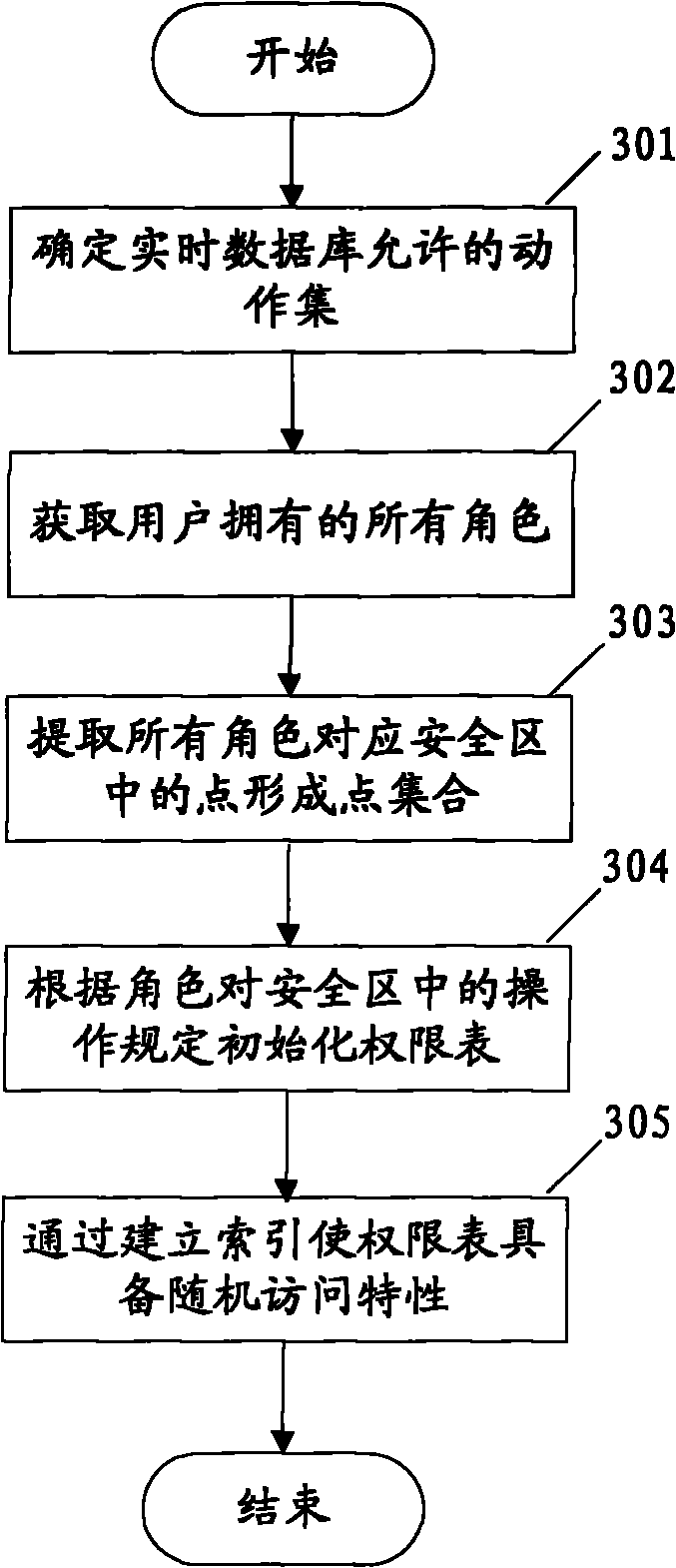
[0055] image 3 Construct a flowchart for the two-dimensional permission table in Example 2
[0056] Step 301, determine the action set of the system as a column of the authority table.
[0057] Step 302, obtaining the roles owned by the user.
[0058] Step 303, get the security zone involved by the user from the role, merge all the points in the security zone as the user-related object, as the row of the permission table;
[0059] Step 304, obtain the user's executable operations on the midpoint of the security zone from the role, set the corresponding position in the juxtaposition table to 1, and set the corresponding position to 0 for unexecutable operations;
[0060] Step 305, after the table is created, the point ID is used as the key value to establish a row-level Hash index for the two-dimensional permission table. The hash function adopts the divide-and-leave method, and...
Embodiment 3
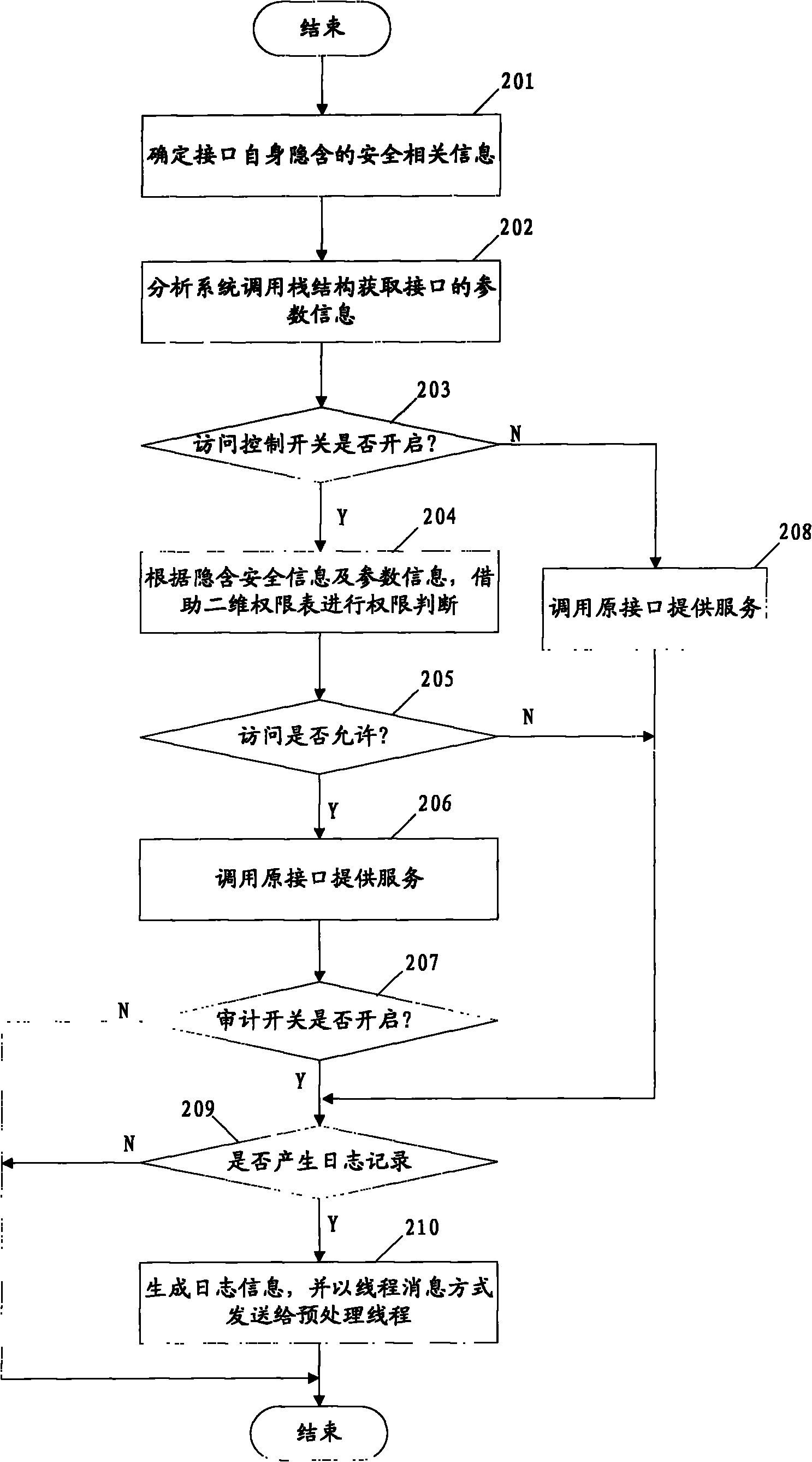
[0066] Figure 5 Schematic diagram of the process of log record generation, processing, and storage.
[0067] Step 501, converting the parameter information, operation execution results, and known information acquired in the security protection function into an integer form, wherein the object is represented by id, the action is represented by position, and the type data number is stored;
[0068]Step 502, map the log record to a 64-bit integer by bit operation, use two unsigned integers to store, the specific format is: the main information of the low 32-bit record log, from high to low are object ID, action ID , operation result, event type, object type and alarm level; the upper 32 bits record the operation error code, and the error information can be obtained through the error code.
[0069] Step 503, after the original record is generated, send the log data to the log preprocessing thread in the form of thread message data parameters through the thread message passing me...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com