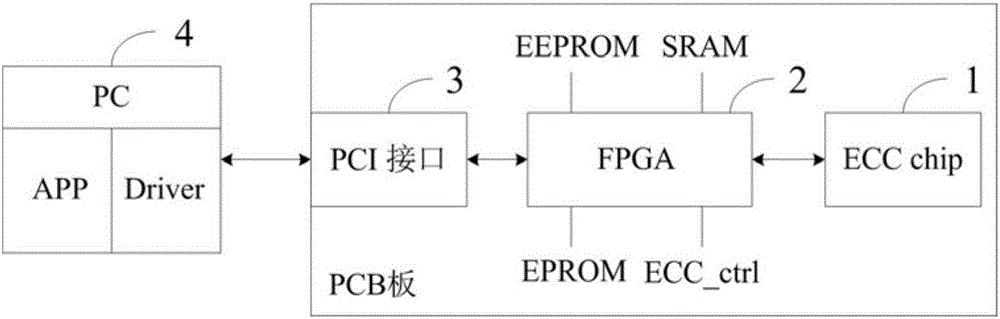
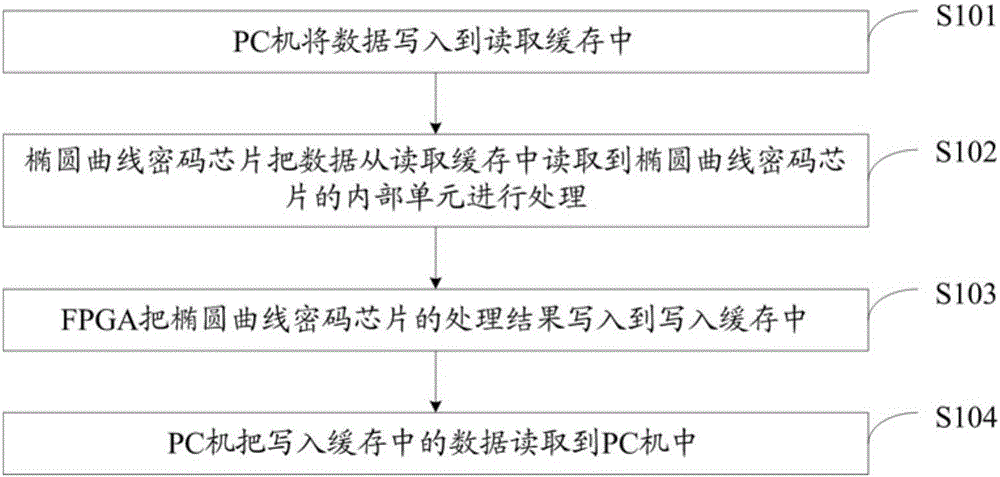
Elliptic curve cipher chip device and system, and data cache control method
A technology of elliptic curve cryptography and control methods, which is applied in the field of elliptic curve cryptography chip devices, can solve the problem of fewer control schemes, and achieve the effect of improving data throughput
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
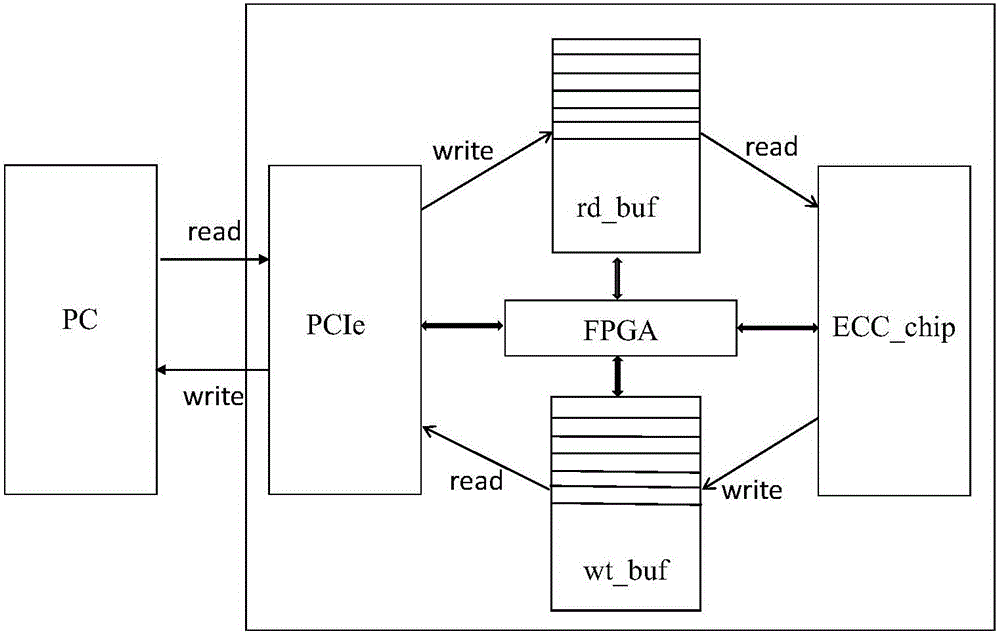
[0073] In this embodiment, the read cache is defined as rd_buf, the PC write pointer is h_p, the elliptic curve cryptographic chip read pointer is h_ptr, the synch_bit_up register group is used for reading the synchronous bit register group, and the synch_bit_up register group uses a group of data lengths Divided as a unit, the synch_bit_up register group synchronization flag rd_buf:
[0074] Such as Figure 5-6 As shown, before the PC sends data each time, it first checks whether the flag bit of the synch_bit_up register group corresponding to the h_p pointer is empty. The marked position of the register bank is valid;
[0075] When the FPGA detects that the mark bit of the synch_bit_up register group corresponding to the h_ptr pointer is valid, the FPGA reads the data from the rd_buf to the internal unit of the elliptic curve encryption chip for processing, and then makes the mark position of the synch_bit_up register group corresponding to the h_ptr pointer empty .
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com