Method for effectively improving hardware Trojan activation probability
A hardware Trojan and probabilistic technology, applied in the direction of instruments, electronic digital data processing, platform integrity maintenance, etc., can solve the problems that the chip has no protection measures against hardware Trojans, does not have the ability to resist Trojans, and rare activation conditions, etc. The method is simple Ease of implementation, increased activation, and reduced verification time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
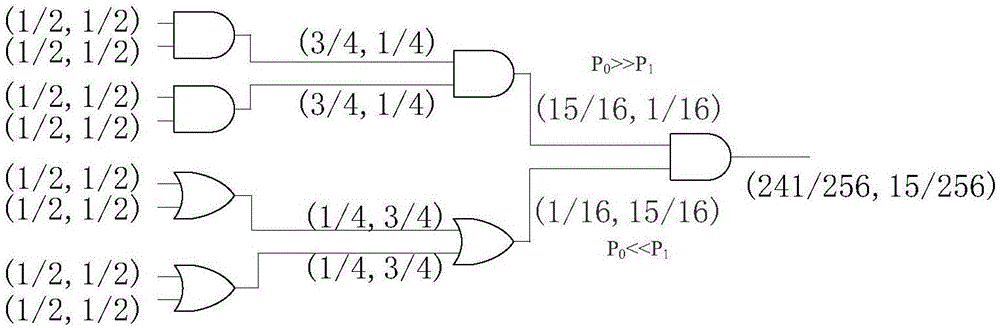
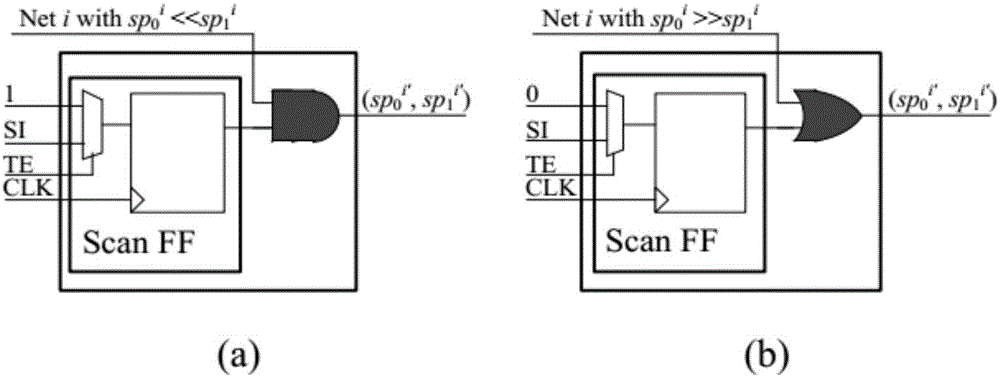
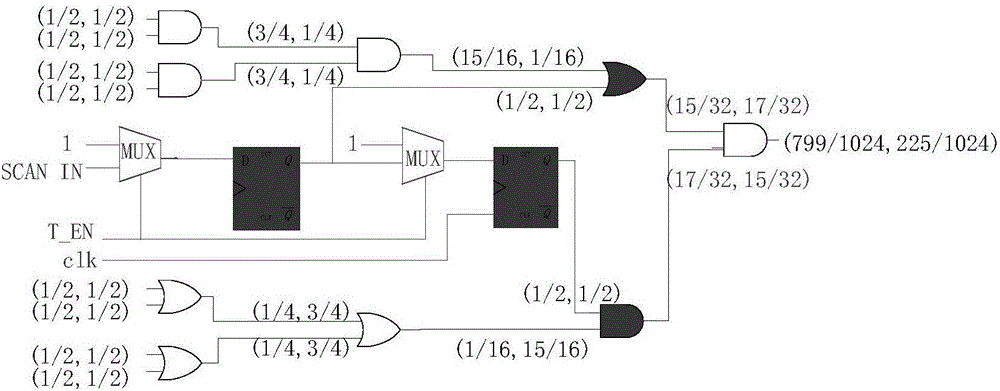
[0031] The present invention utilizes the idea of safety design, analyzes the circuit structure and node activity of the original circuit design on the basis of the virtual scanning trigger, implants a specific structure in the low-activity node according to the threshold probability, and removes the low-activity node in the circuit, Improve the circuit activity of the original design and the activation rate of the hardware Trojan horse, greatly reduce the randomness and uncertainty of the hardware Trojan horse activation, effectively shorten the activation time of the hardware Trojan horse, and improve the detection rate of the hardware Trojan horse to a certain extent.
[0032]With the development of semiconductor deep submicron technology, the number of chip integrated devices has increased exponentially with Moore's Law, the scale of chips has become larger, the functions of chips have become more and more, and the internal circuit structure has become more and more comple...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com