Data security leakproof self-save system and method, readable memory medium and device
A data security and anti-leakage technology, which is applied in the field of data security anti-leakage self-rescue system, can solve the problems of being unable to prevent security attacks using new software vulnerabilities and preventing data leakage, etc., and achieve the effect of facilitating centralized maintenance and preventing theft or attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
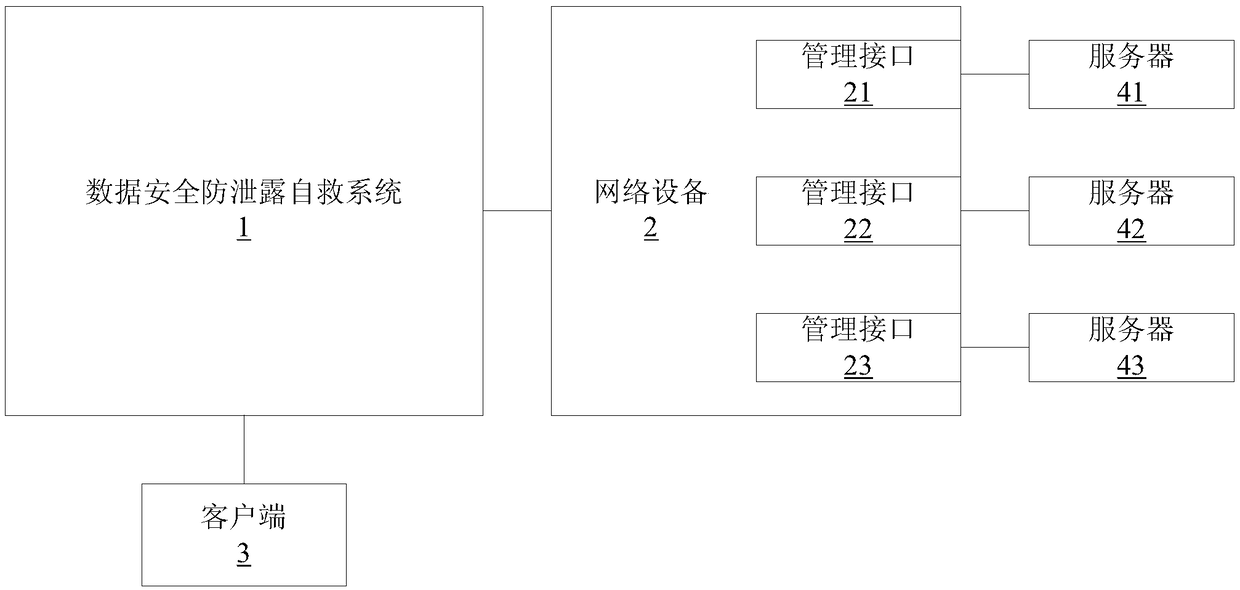
[0046] This embodiment provides a data security anti-leakage self-rescue system, which is communicatively connected to at least one network device and at least one client, and at least one server is connected to the network device; the data security anti-leakage self-rescue system includes:
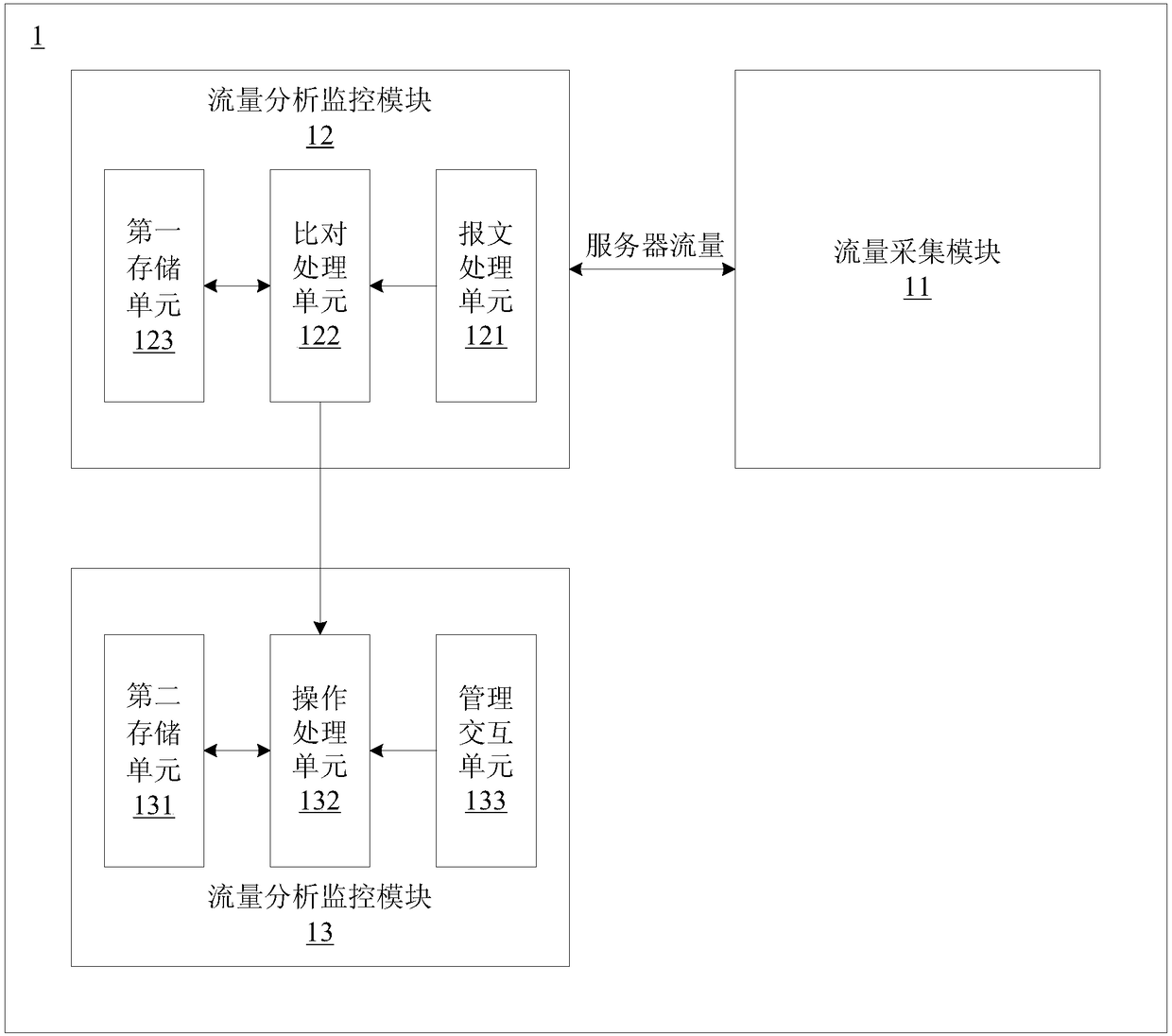
[0047] A traffic collection module, connected to the network device, for copying the server traffic passing through the network device, and forwarding the server traffic;
[0048] A traffic analysis and monitoring module, configured to receive the server traffic, extract network key feature content from the server traffic, and search for network attack features from the key feature content to determine whether a network attack occurs;
[0049] A control module, configured to form attack information when the traffic analysis, monitoring and monitoring module finds that there is a network attack on the server, and send the attack information and the processing selection corresponding to the ...
Embodiment 2
[0071] This embodiment provides a self-rescue method for data security leakage prevention, which is applied to a communication network including at least one network device connected to at least one server; the data security leakage prevention self-rescue method includes:
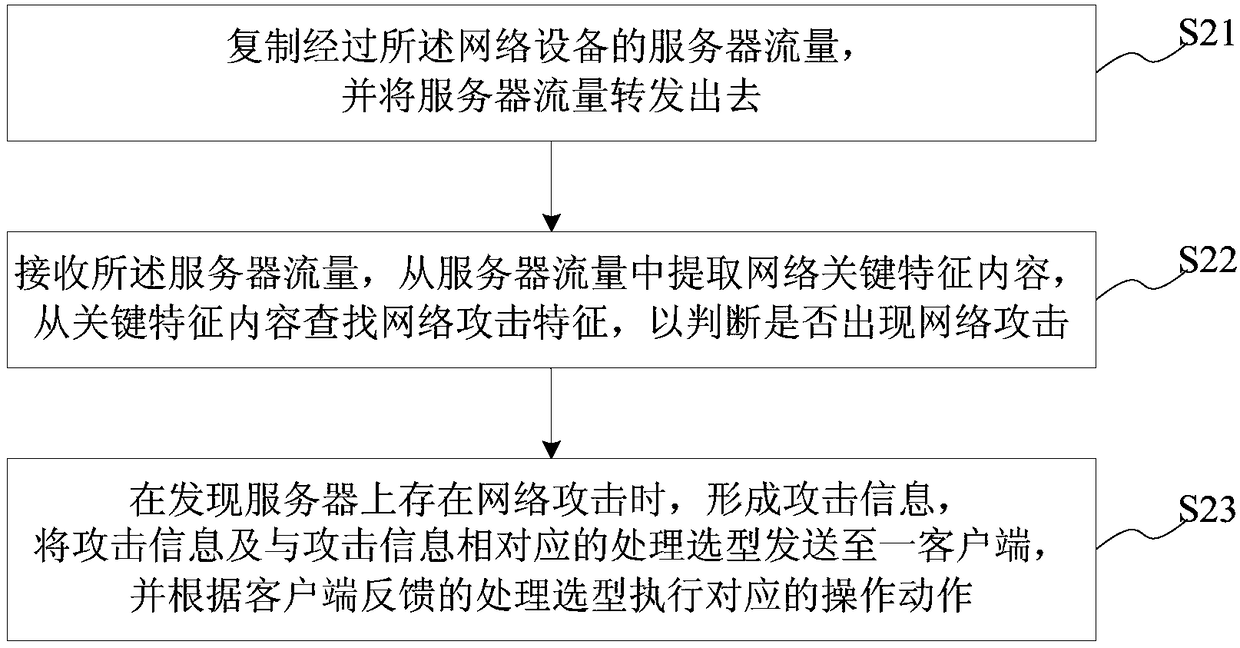
[0072] Step 1, copying the server traffic passing through the network device, and forwarding the server traffic;
[0073] Step 2, receiving the server traffic, extracting network key feature content from the server traffic, and searching for network attack features from the key feature content to determine whether a network attack occurs;
[0074] Step 3: When it is found that there is a network attack on the server, form attack information, send the attack information and the processing selection corresponding to the attack information to a client, and select the processing according to the feedback from the client Execute the corresponding action.
[0075]The data security leakage prevention self-rescue ...
Embodiment 3
[0092] This embodiment provides a device, which includes: a processor, a memory, a transceiver, a communication interface, and a system bus; the memory and the communication interface are connected to the processor and the transceiver through the system bus and complete mutual communication, and the memory is used for The computer program is stored, the communication interface is used to communicate with other devices, the processor and the transceiver are used to run the computer program, so that the device performs the steps of the above data security leakage prevention and self-rescue method.
[0093] The system bus mentioned above may be a Peripheral Component Interconnect (PCI for short) bus or an Extended Industry Standard Architecture (EISA for short) bus or the like. The system bus can be divided into address bus, data bus, control bus and so on. For ease of representation, only one thick line is used in the figure, but it does not mean that there is only one bus or on...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com