Viscous honeypot system and interaction method thereof
A honeypot, sticky technology, applied in the field of network security, can solve the problems of deception failure, downtime, increase hacker vigilance, etc., to achieve the effect of increasing difficulty, reducing network load, and improving survivability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
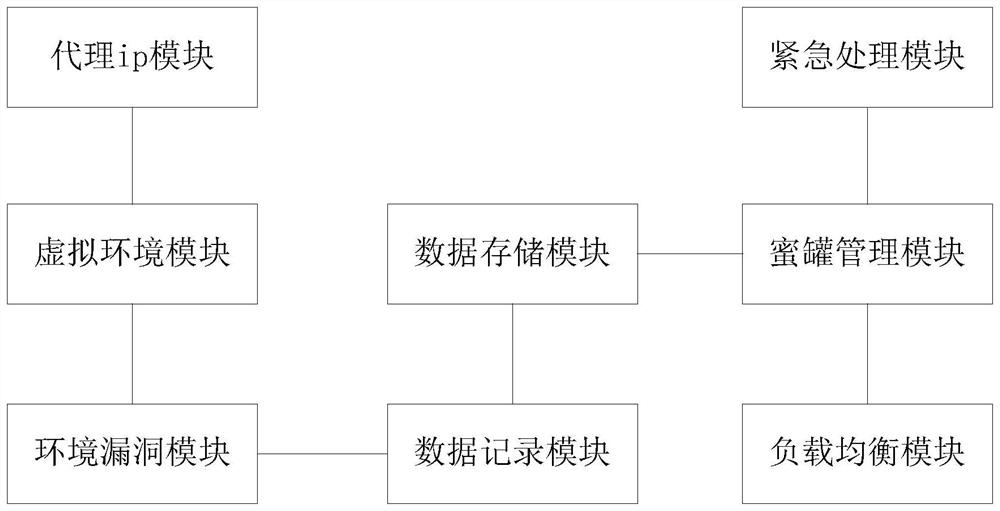
[0027] A sticky honeypot system such as figure 1 As shown, the following modules are included:
[0028] The agent ip module is used to assign the agent ip address to the virtual machine to build a new virtual environment; the agent ip module mainly includes the agent ip pool built by the cloud platform.
[0029] The virtual environment module is used to build a system environment image to simulate the real business system environment according to the proxy ip address; the virtual environment module includes a vmware virtual machine, a Docker container based on a vmware virtual machine, and a Debian system built in a Docker container.
[0030] The environmental vulnerability module is used to build a vulnerable intranet asset architecture and web business architecture in the system environment; the intranet asset architecture includes databases and SSH services, Telnet services, and SMTP services with weak password vulnerabilities; the web business architecture includes files w...
Embodiment 2
[0039] Embodiment 2 is a sticky honeypot system interaction method based on Embodiment 1, including:
[0040] 1) In the form of proxy ip, assign the proxy ip address to the virtual machine to build a new virtual environment;
[0041] 2) Build a system environment image in the new virtual environment to simulate the real business system environment;
[0042] 3) Build a vulnerable intranet asset structure and Web business structure in the system environment;
[0043] 4) Redirect the port of the vulnerable architecture in the honeypot system from iptables to the port of the real business environment;
[0044] 5) Record and store the operation records when the attacker infiltrates, the operation records include the ip address used, the attack duration and sensitive operation commands;
[0045] 6) At the same time, monitor the system environment, and analyze, process and display the monitoring data;
[0046] 7) According to the real-time situation of the system environment, the ...
Embodiment 3
[0048] In this embodiment 3, on the basis of embodiment 1, the honeypot system of embodiment 1 is deployed in a real business environment. The virtual environment module uses the ip address provided by the agent ip module to create a new virtual machine in the real environment, and the The Docker container is used in the machine to complete the deployment of the virtual business environment. Because the Docker container has a faster startup time, is good at handling the concentrated burst of server usage pressure, and can be elastically scaled and rapidly expanded, it is suitable for the construction of a virtual business environment. Build a Debian image in a Docker container. Debian is an open source system with Linux as the kernel. Compared with other Linux systems, it has stronger stability, faster and easier memory management and security protection. Debian is used to complete the honeypot system Build, in the environment vulnerability module, enable the SSH service, Telne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com