Method to scan a forensic image of a computer system with multiple malicious code detection engines simultaneously from a master control point
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
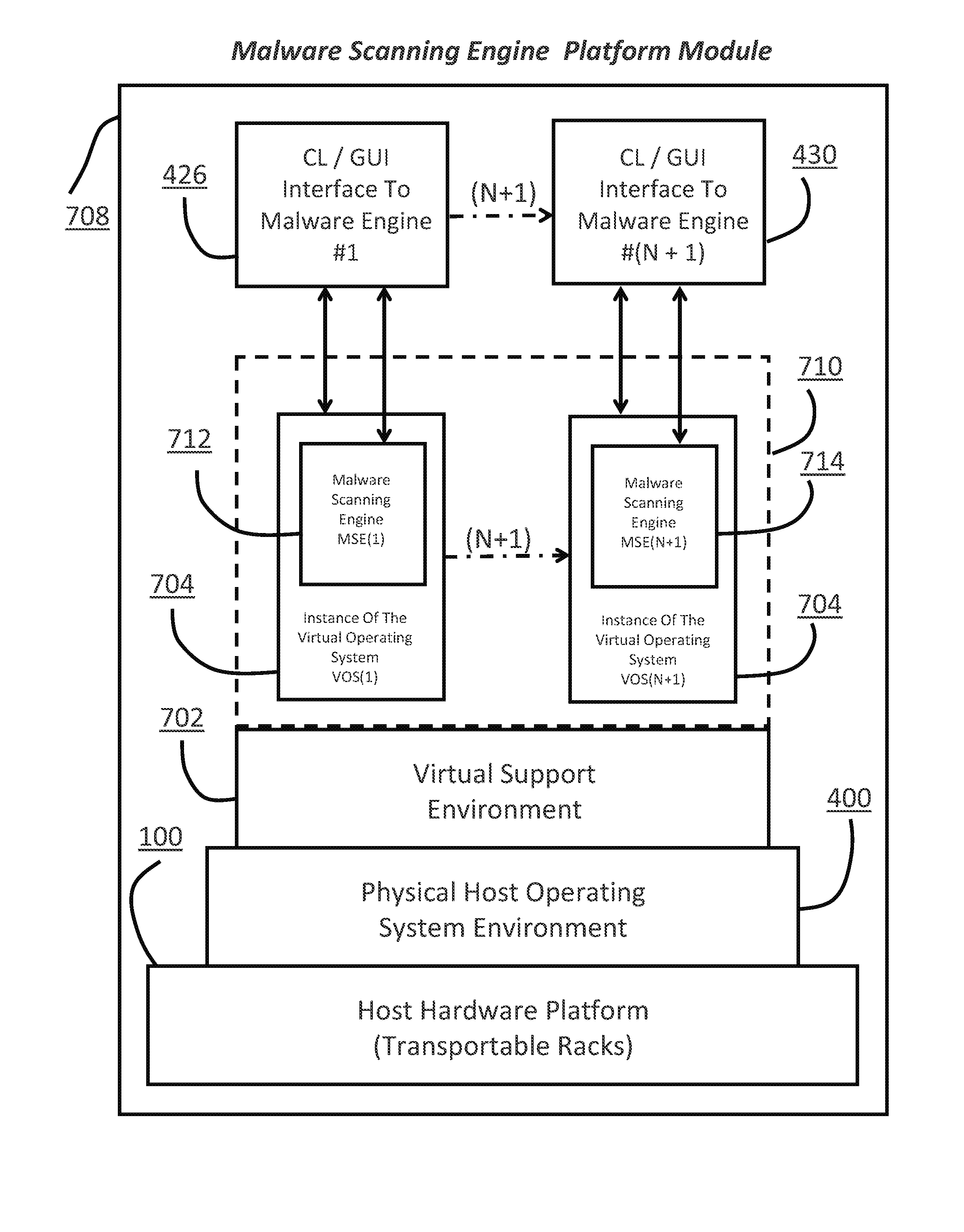
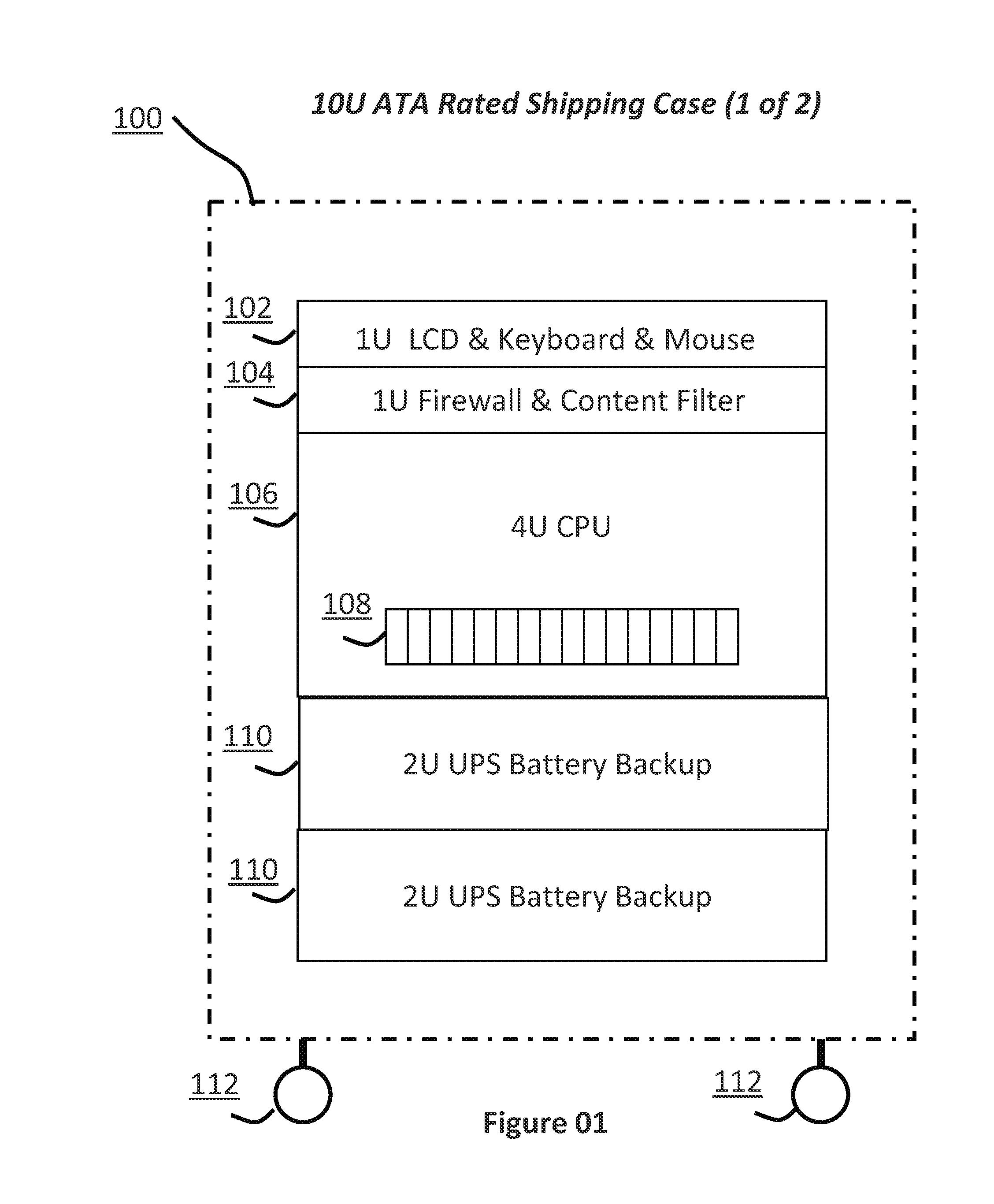
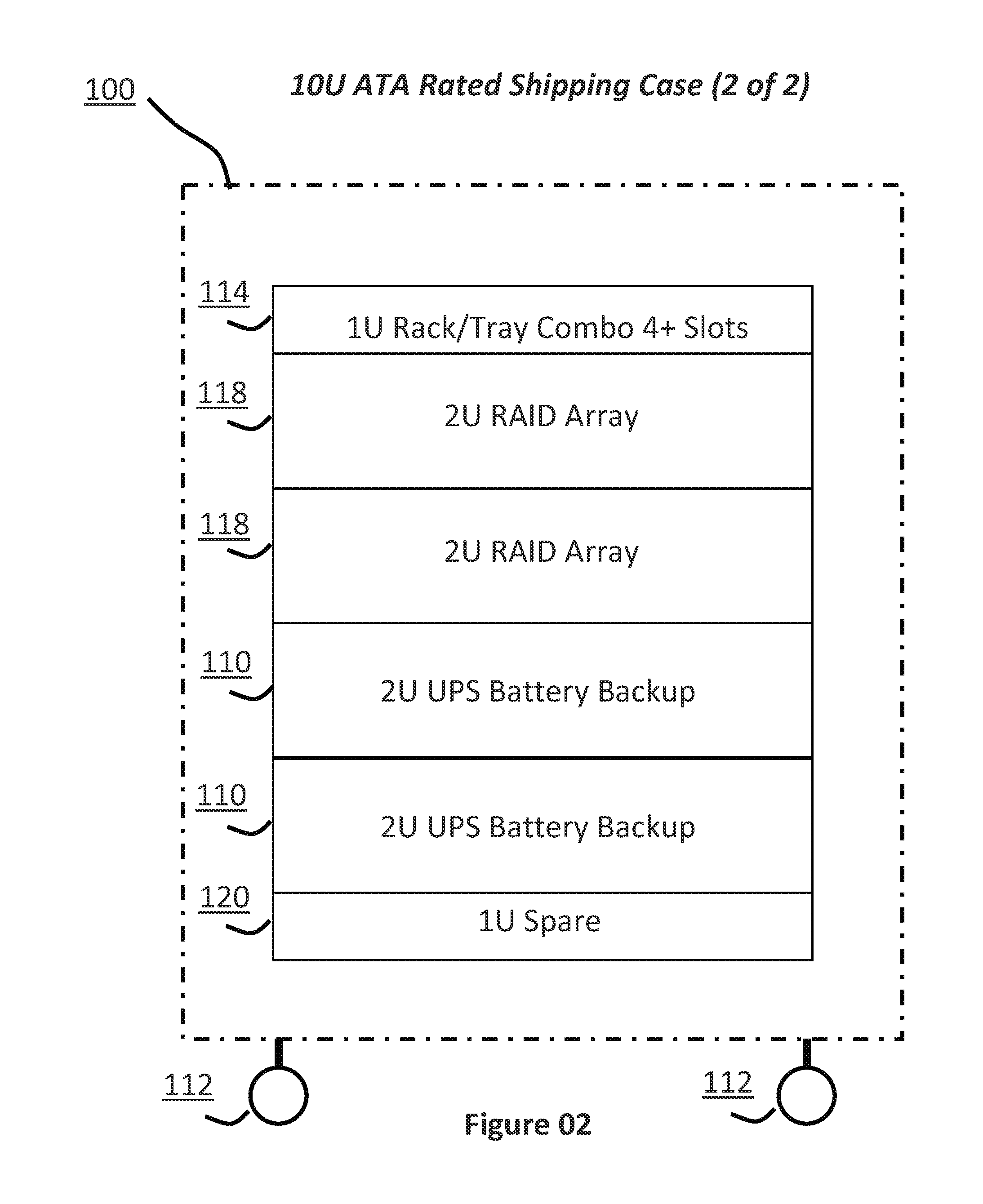
[0066]The present invention is a system, process and method that allows duplicate bit-by-bit forensic images of a computer system's hard drive or the live acquisition of RAM / Flash memory to be scanned with multiple malware engines simultaneously from a master control point dashboard. Moreover, the present invention is configured to be a portable solution such that it can be shipped, via common carriers, to client locations whose privacy policies prevent sensitive data from being taken off-site. More specifically, the present invention provides a process whereby the files and data on computer system storage devices, in the form of forensic images, can be scanned simultaneously from a virtual environment with multiple commercial or open source malware detection applications in a time period that is substantially less than if the scanning was performed sequentially. In addition, the present invention has the ability, via authored scripts and executable programs created, to collect rele...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com