Ciphertext storage and ciphertext retrieval open cloud method and system
A cloud service and ciphertext technology, applied in the field of information security, can solve problems such as weak key management functions, easy data leakage, and abuse of authority by cloud service providers, so as to improve data security protection and privacy protection capabilities, and various encryption algorithms , the effect of a simple calling method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0090] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments, but the scope of the present invention is not limited in any way.
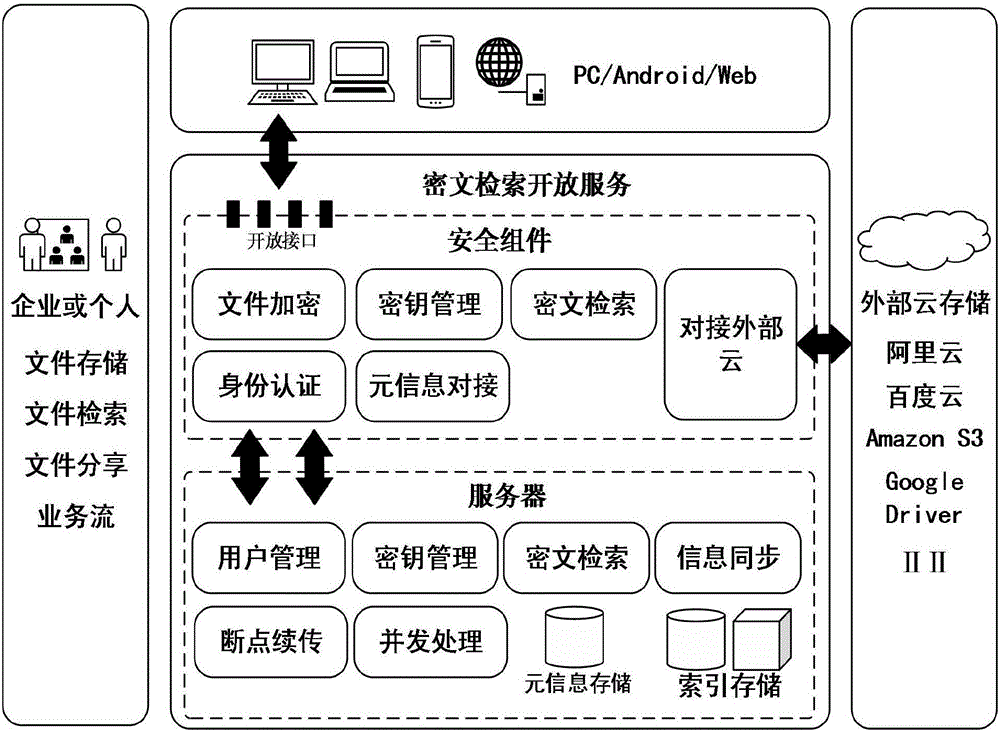
[0091] This embodiment adopts as figure 1 The shown ciphertext storage and ciphertext retrieval open cloud service method and system structure include a security component, a server connected to the security component, the security component establishes a connection with the server through the network, and the security component establishes a connection with a third-party cloud storage server through the network .
[0092] Security components include file encryption and decryption module, key management module, ciphertext retrieval module, external cloud connection module, identity authentication module and meta information connection module;
[0093] The file encryption and decryption module and the ciphertext index module are used to perform encryption and decryption...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com