Method and system for effectively identifying machine access behavior
A machine and behavior technology, applied in the field of effective identification of machine access behavior, can solve the problems of high threshold setting requirements, low universality, and low cost, and achieve the goal of alleviating high detection costs, high recognition accuracy, and reducing detection costs Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0069] In order to make the purpose, technical solution and advantages of the present application clearer, the present application will be further described in detail below in conjunction with the accompanying drawings and embodiments. It should be understood that the specific embodiments described here are only used to explain the present application, and are not intended to limit the present application.
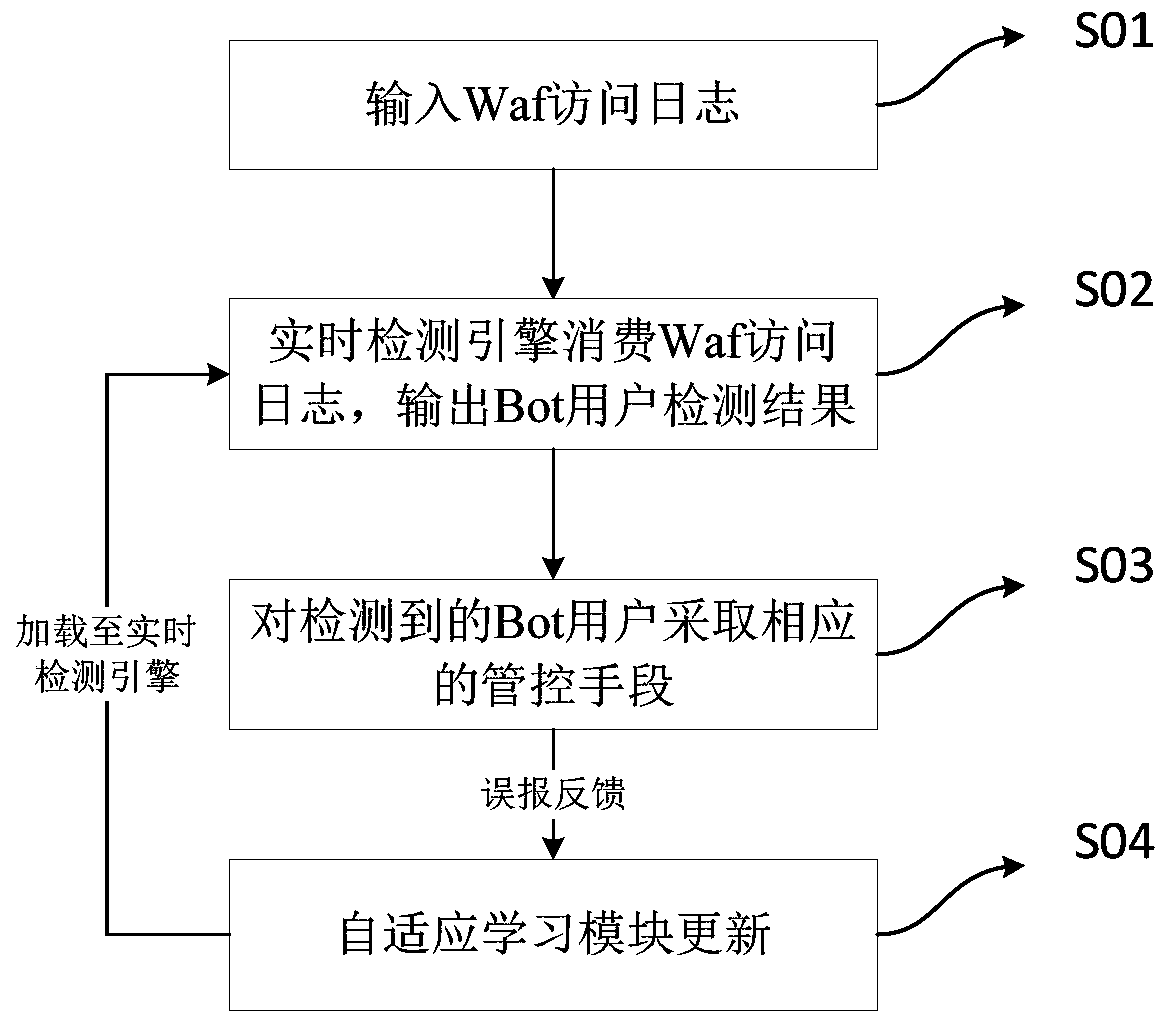
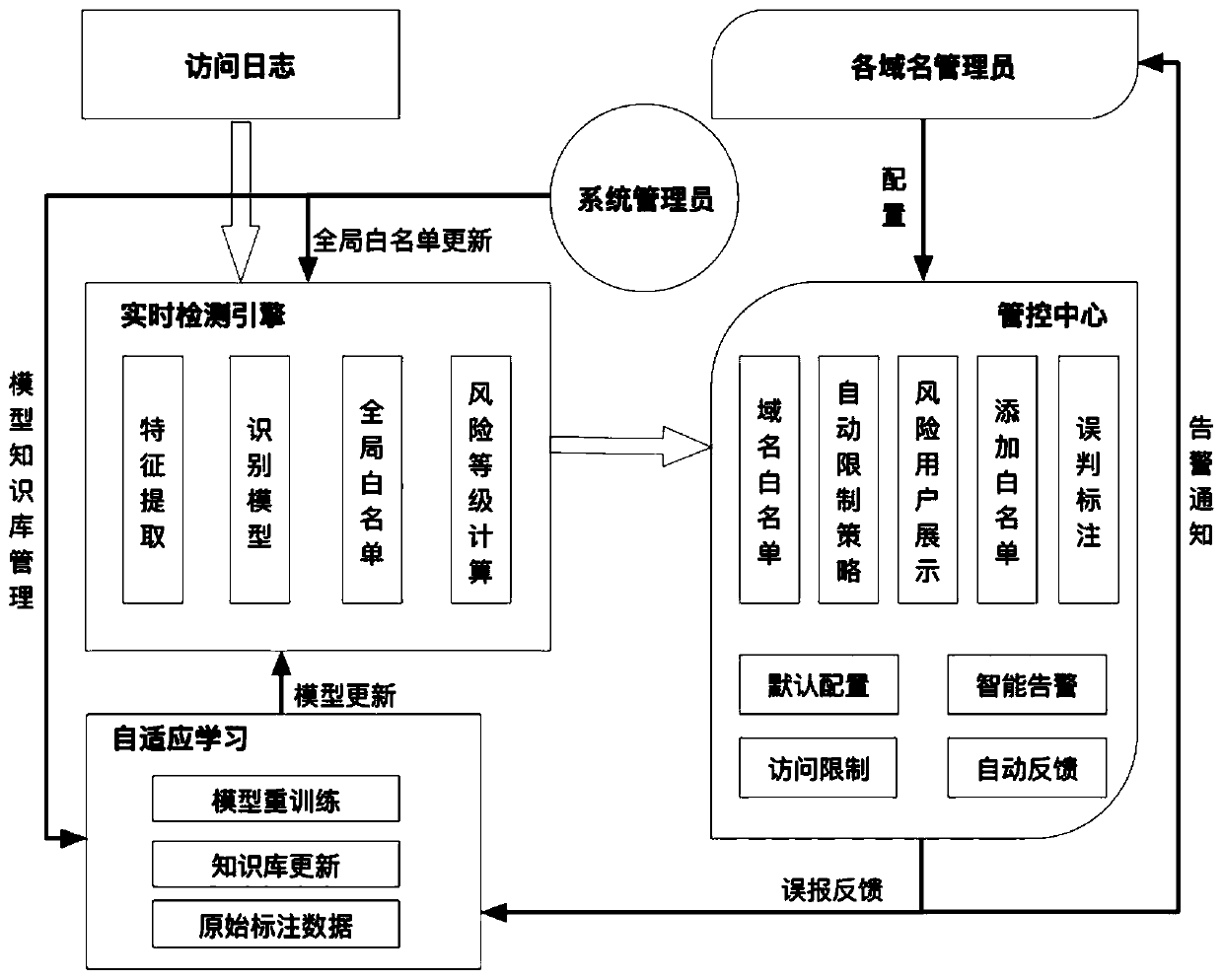
[0070] In one embodiment, combined with figure 1 and figure 2 , provides a method for effectively identifying machine access behavior, which includes:
[0071] Step S01, input Waf access log;
[0072] Step S02, the real-time detection engine consumes the Waf access log, and outputs the machine access behavior Bot user to the control center;
[0073] Here, Waf access logs include access behaviors of normal users and Bot users, and consuming Waf access logs refers to analyzing and processing Waf access logs to distinguish and identify Bot users.
[0074] Step S03, the d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com