Quantum key negotiation method, quantum key negotiation system, quantum digital signature method and quantum digital signature system
A quantum key agreement and key technology, which is applied in quantum digital signature method, quantum key agreement method, and system fields, can solve the problems of low efficiency and lack of practicability of digital signatures, and achieve large-scale deployment, high efficiency and Practical, practical effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
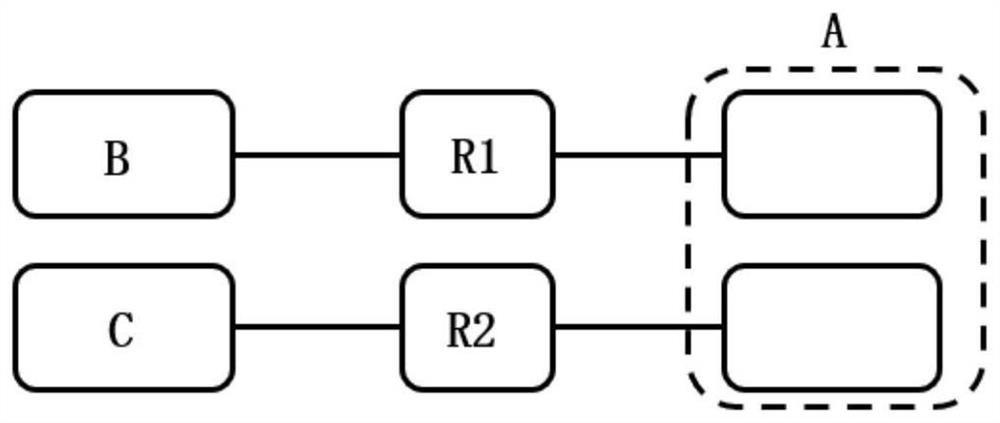
[0052] This embodiment exemplarily provides a quantum key agreement system, a sender A, a receiver B, and an untrusted relay R1.
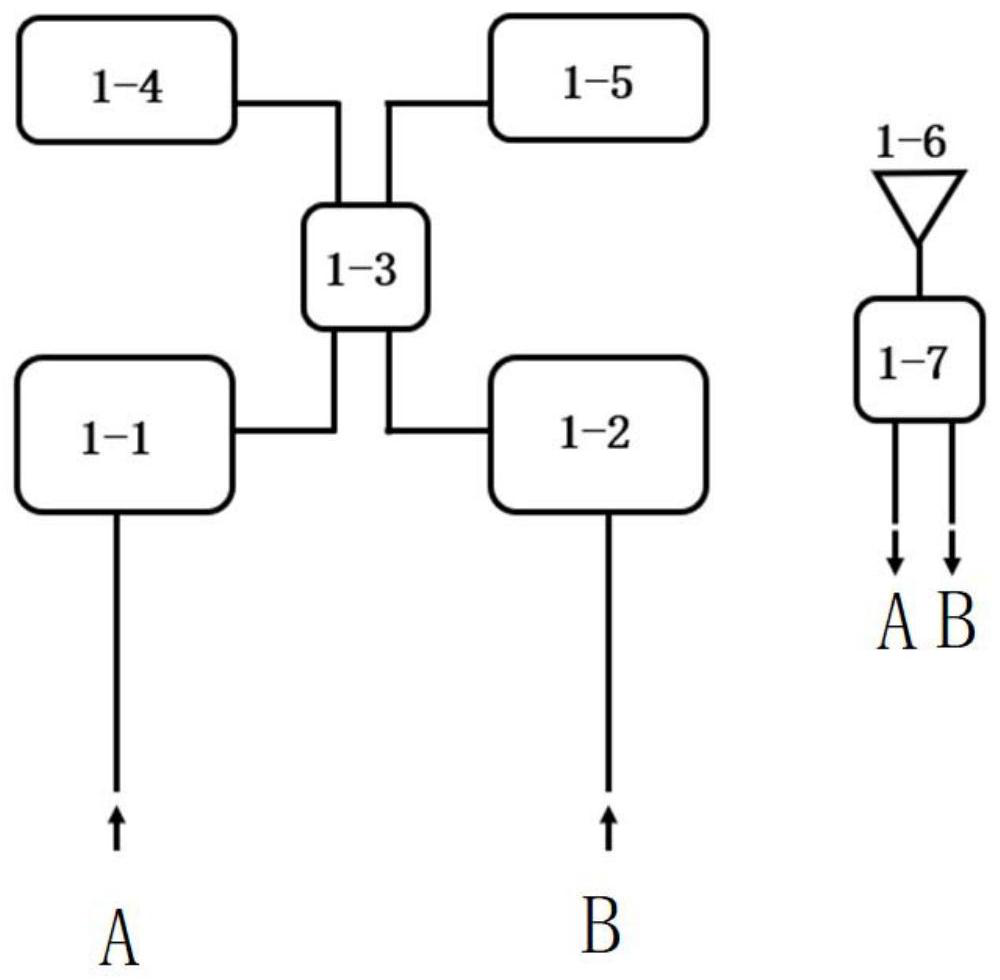
[0053] The internal structure of the untrusted relay is as follows figure 1 As shown, it includes a first signal stabilization module 1-1, a second signal stabilization module 1-2, an interference module 1-3, a first detector 1-4, a second detector 1-5, and a main laser module 1-6 and beam splitting modules 1-7.
[0054] figure 1 Among them, the first signal stabilization module 1-1 and the second signal stabilization module 1-2 have the same function, and both are used to increase the interference stability of the quantum signal. In this embodiment, we choose dense wavelength division multiplexing (hereinafter referred to as DWDM), electronically controlled polarization controller (hereinafter referred to as EPC), polarization beam splitter and superconducting nanowire single photon detector (hereinafter referred to as SNSPD) to form this module...
Embodiment 2
[0072] In this embodiment, on the basis of the quantum key agreement system described in Embodiment 1, a quantum key agreement method is proposed, which specifically includes the following steps:
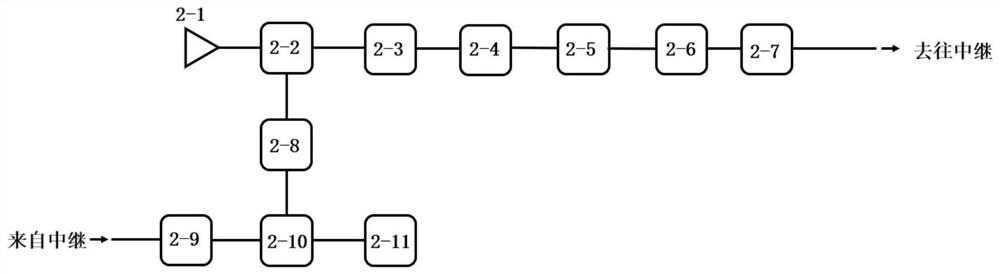
[0073] (1) Injection locking: the CW laser at the untrusted relay R1 is used as the main laser module 1-6, and the CW laser is generated as the seed light. The seed light is divided into two beams through the polarization maintaining beam splitter, and the two beams of seed light reach A and B respectively through the long-distance optical fiber channel. After the seed light reaches A and B, it is first amplified by EDFA, filtered by FBG through the circulator, and then filtered by DWDM, and then passed through EPC and polarization beam splitter. The transmission output port of the polarization beam splitter is connected to the circulator, and the reflection output port is connected to the The optical power meter adjusts the EPC according to the detection result of the optical power...
Embodiment 3
[0082] This embodiment further proposes a quantum digital signature method based on the key agreement method described in Embodiment 2, which method includes the following steps:
[0083] 1) A puts the S in his hand 1 and S 2 xor get
[0084] 2) A from S A Selecting the first key whose length is n is used to generate a hash function based on a linear feedback shift register;
[0085] 3) A obtains an n-bit random number locally, and uses the n-bit random number to generate an n-order irreducible polynomial in the GF(2) field.
[0086] First, each bit of the n-bit random number corresponds to the coefficient of each item in the polynomial except the highest term in turn to generate an n-order polynomial in the GF(2) field, and the coefficient of the highest term is 1. For example, the random number is (a n-1 , a n-2 ,...,a 1 , a 0 ), then the generated polynomial is p 1 (x)=x n +a n-1 x n-1 +…+a 1 x+a 0 . Preferably, only when a 0 =1, the generated polynomial m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com