Polymorphic computational system and method in signals intelligence analysis
a computational system and signal intelligence technology, applied in the field of reconfigurable computing platforms, can solve the problems of not having the time or ability to do such coding, requiring significant amounts of time to write, and not reaching the full potential of this technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
SIA-Imagery
[0267]Signals intelligence analysis, and the solutions and solution fragments described above, are not limited to encryption / decryption. Indeed, they may extend to any other area in which incoming data is reviewed for the existence of a pattern. The incoming data may be, for example, a stream of satellite imagery containing pictures of suspected military equipment in opposition forces territory. With the abundance of satellites and other forms of information-gathering equipment, millions of digital images may be generated every hour. The traditional approach to SIA would transmit such images to a centralized location for analysis. The traditional approach uses a centralized location partly because it is easier to keep a central location secure. This centralized approach suffers a drawback, however, in that the time required for the transmission and central analysis may literally mean the difference between life and death. A satellite image showing an advancing troop trans...
example embodiment
Abstraction and Behavioral Models
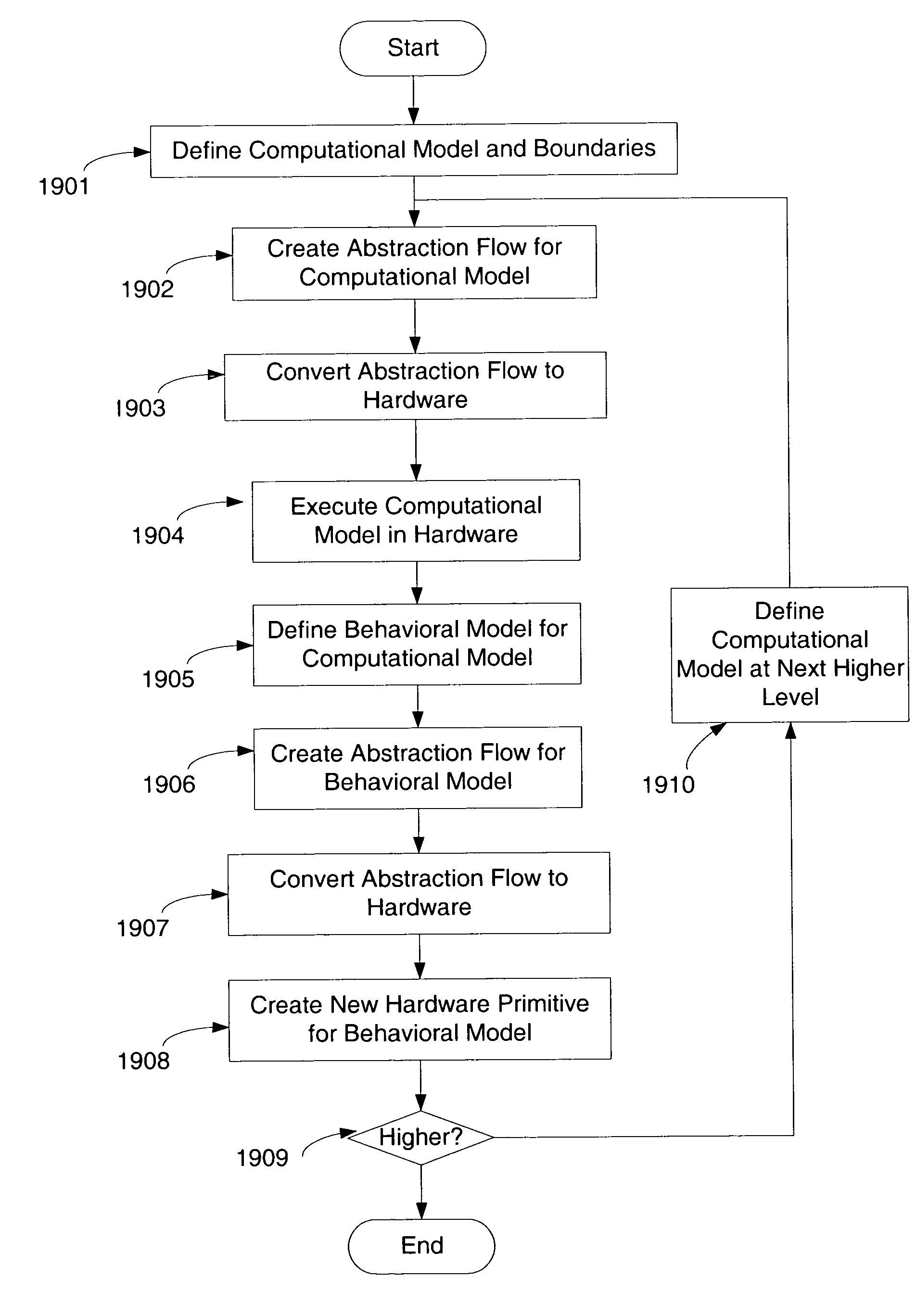
[0276]FIG. 19 illustrates a flow diagram for another example embodiment and use of the present invention. The power and ease-of-use offered by various embodiments described above enable the simulation and modeling of various computational problems. For example, in step 1901, a user may define a computational model and its boundaries. Computational models are common throughout the research community, and are used to define a near-infinite variety of behaviors such as planetary orbits, gene sequencing, thermal conductivity, etc. For ease of explanation, the present discussion will use the following simplified computational model (although it will be understood that the teachings described herein may be applied to any computational model):
[0277]∫0πsin(x+41)
[0278]The boundaries for a computational model represent the outer limits for the variables appearing in the computational model. In the illustrated example, the model is bounded by defining the val...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com