Trusted network architecture based on identity
A network architecture, trusted technology, applied in the field of information security, can solve problems such as difficult implementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
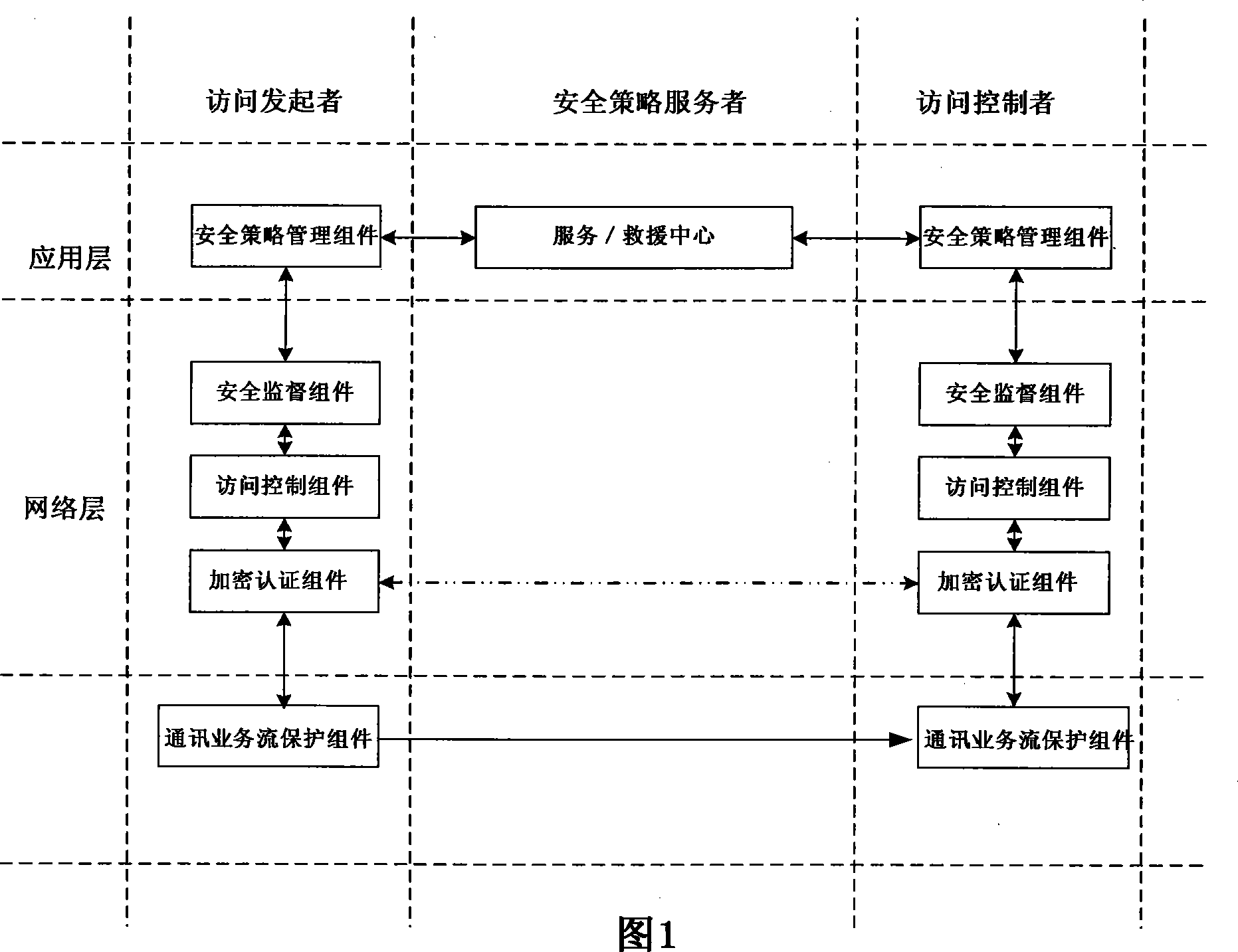
[0047] The trusted network architecture of the present invention will be further described below in conjunction with the drawings and embodiments. Embodiment 1. Device-centric trusted network architecture
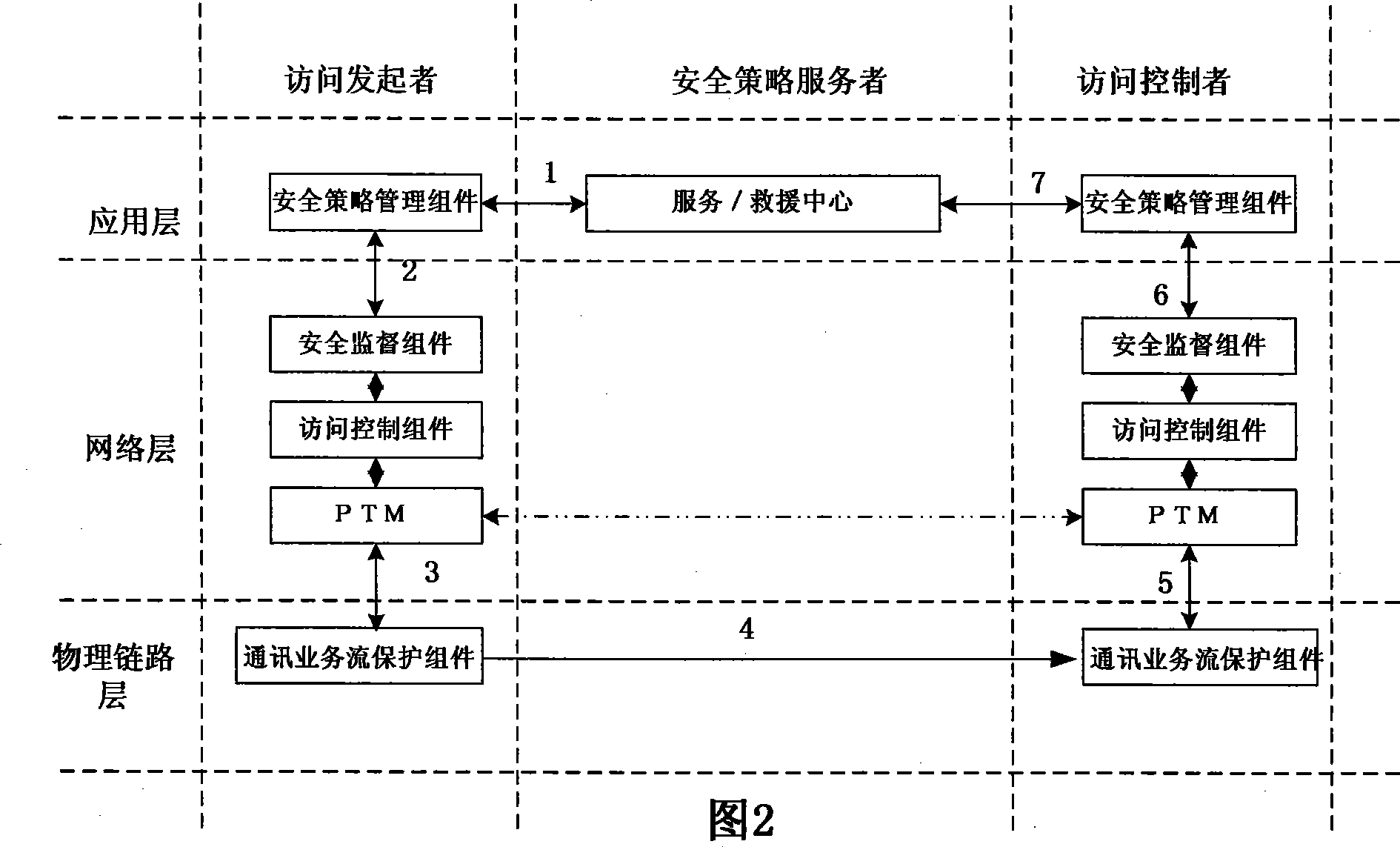
[0048] The device-centered trusted network architecture is shown in Figure 2. In this trusted network architecture, all network terminals and hosts adopt a hardware motherboard structure with a PTM trusted computing module, and the system software is equipped with security policy manager components, Security supervision and mandatory access control components form a trusted network architecture composed of trusted computing terminals, trusted hosts and security policy servers.
[0049] In the initial state, users with trusted terminals must register at the security policy service provider registration center, and then they can access the trusted network, and automatically obtain the latest security policies and virus protection technologies from the security policy service ...
Embodiment 2
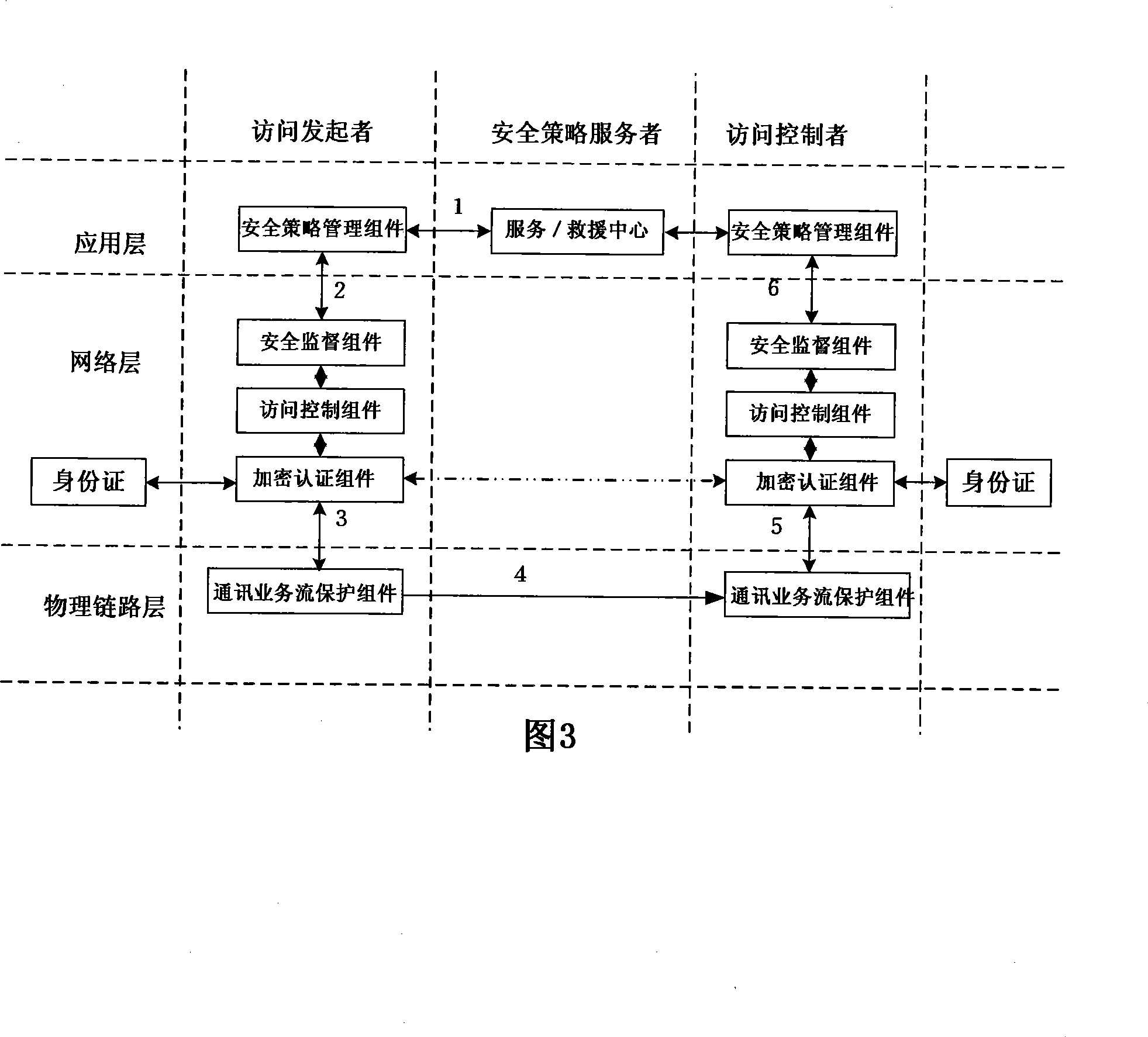
[0068] Embodiment 2, human-centered trusted network architecture
[0069] This embodiment is shown in Figure 3. The difference between it and Embodiment 1 is that in the trusted network of this mode, all terminals do not need to be replaced with computers equipped with a trusted computing module PTM, but adopt post-installed security component software and separate When the network ID card is separated from the terminal, the terminal is an ordinary computer. When the network ID card is inserted into the USB or sensor interface of the computer, the ordinary terminal becomes a trusted terminal. This design and layout is to support user mobility and compatibility with existing network infrastructure and users' computers, so that users can enjoy the security and convenience brought by trusted networks at the lowest cost.
[0070] The implementation process of the human-centered trusted network architecture will be described in detail below with reference to FIG. 3 .
[0071] In t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com