Efficient protocol client vulnerability mining method and system
A vulnerability discovery and client-side technology, applied in the transmission system, electrical components, etc., can solve the problems of inability to streamline data packet collection, lack of versatility, timeout limit, etc., to improve the ability to resist zero-day vulnerability attacks, enhance The ability to hide vulnerabilities, the effect of improving efficiency and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to make the purpose, technical solutions and advantages of the embodiments of the present invention clearer, the present invention will be described in detail below in conjunction with the accompanying drawings.
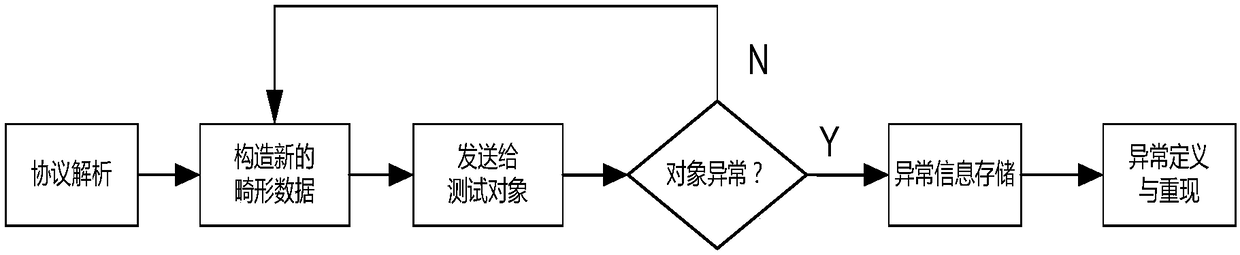
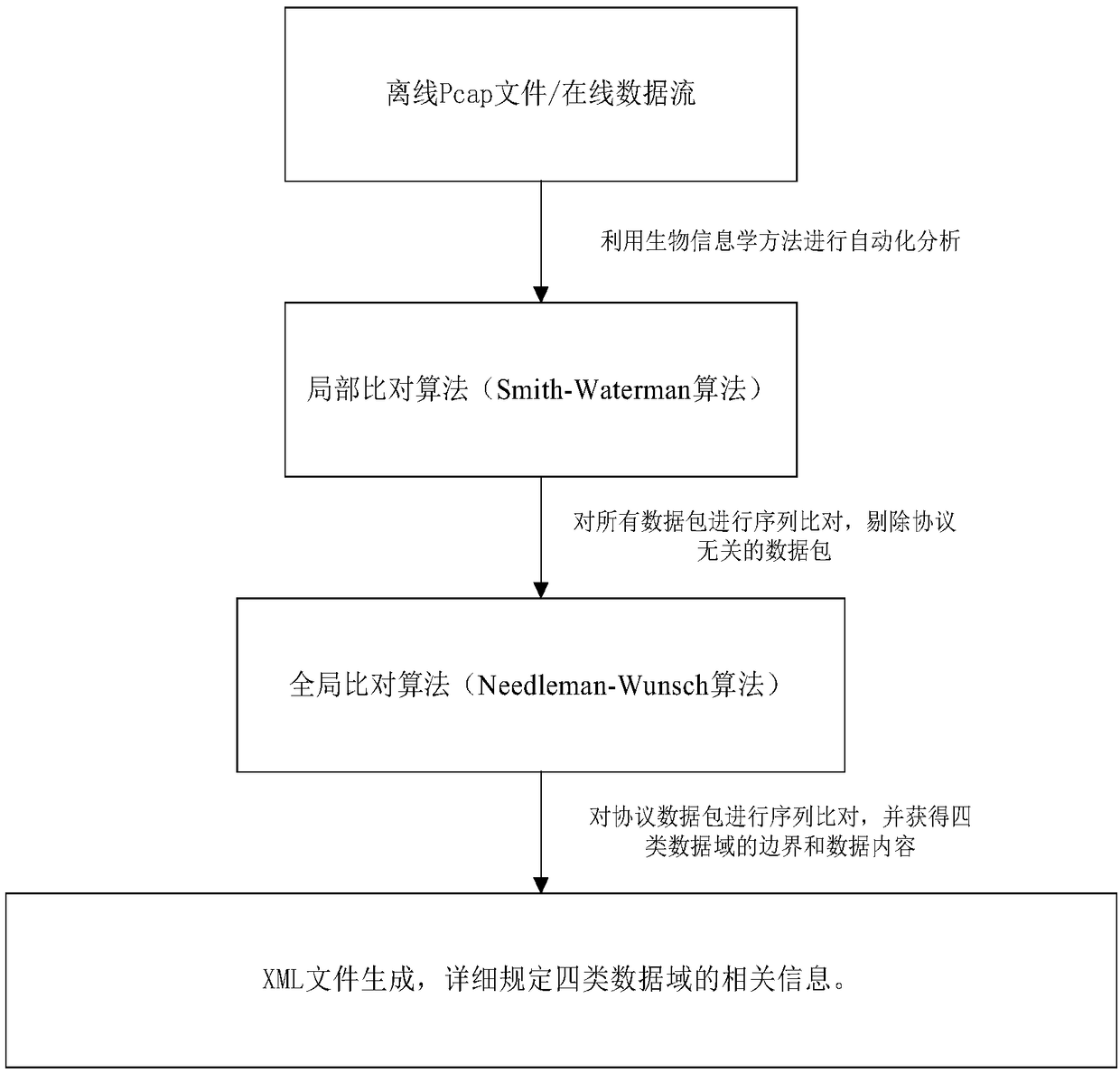
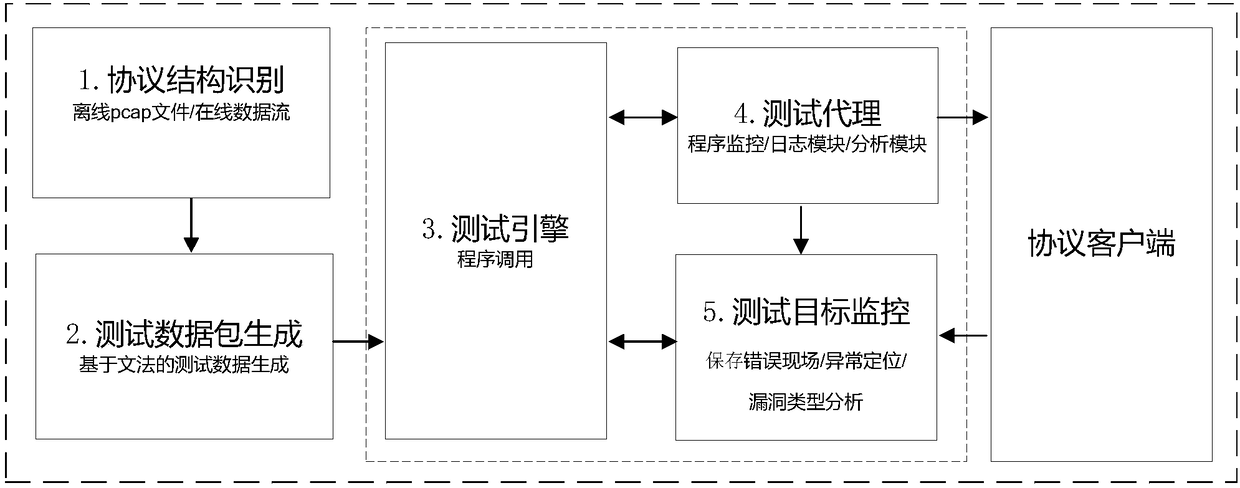
[0030] Such as figure 1 As shown, the efficient protocol client vulnerability discovery system of the present invention first analyzes the protocol data packets, and divides the protocol packets into four types: session-related data fields, data packet length data fields, fixed data fields, Fuzzy test the data domain, and obtain the data domain boundary and data content of the protocol, and then use different processing methods for different data domains according to the obtained data domain division: session-related data domain, according to the rules of the specific protocol under test. Change; packet length data field, obtained by recalculation in the constructed test packet; fixed data field, which remains unchanged in all data packets; fuzzy test...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com