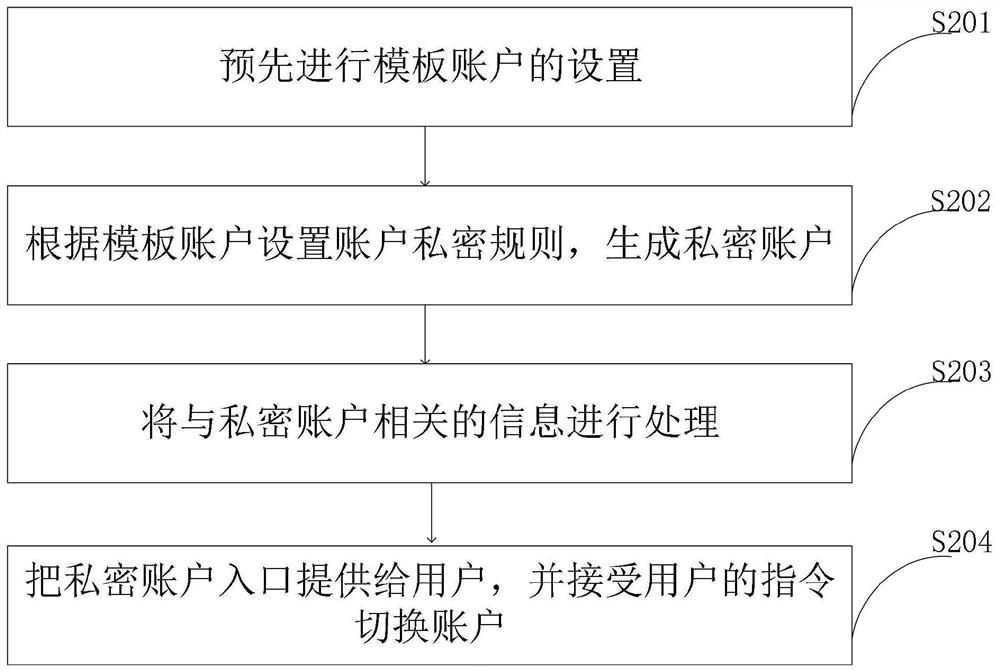
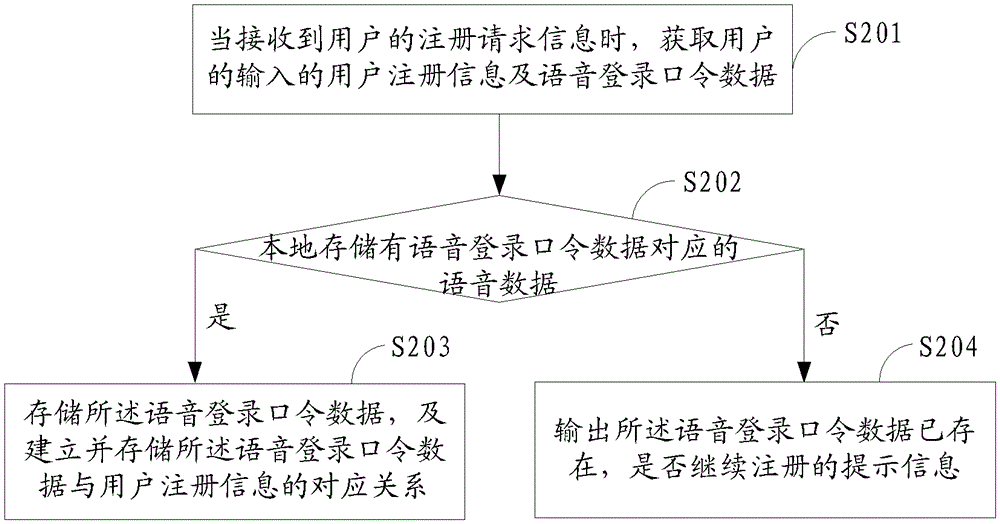
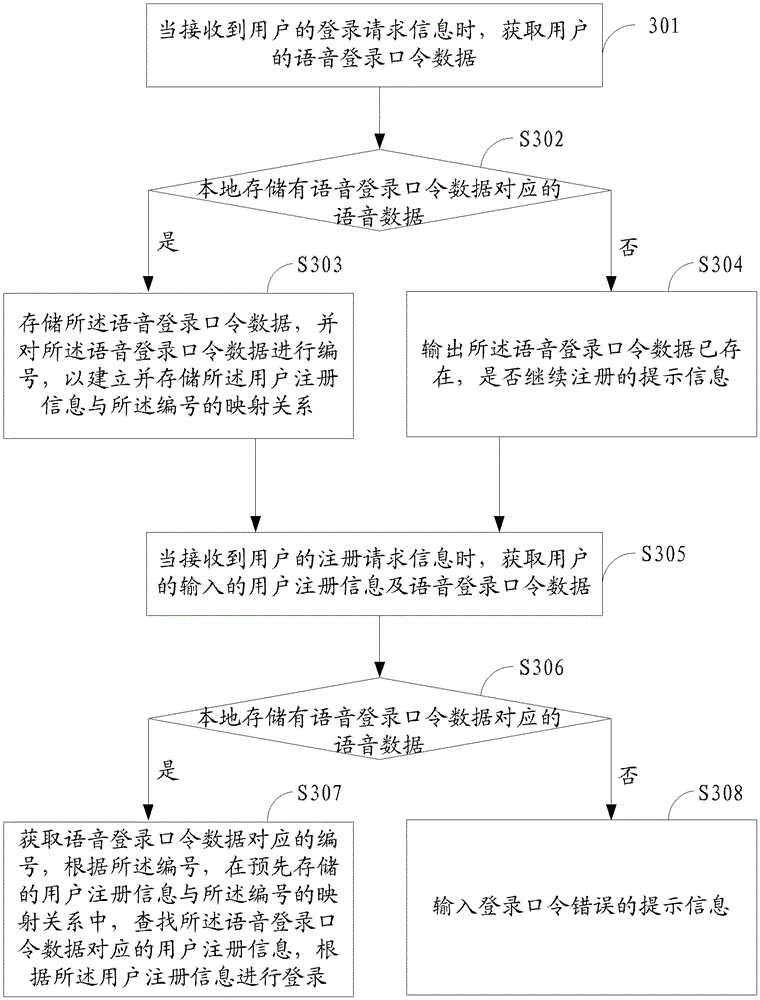
Patents
Literature
40results about How to "Login implementation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
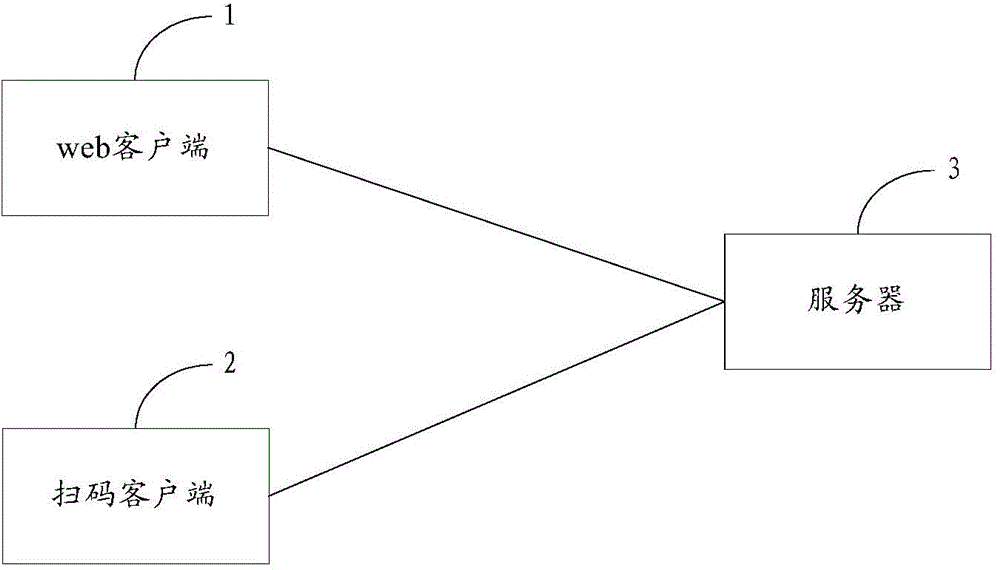
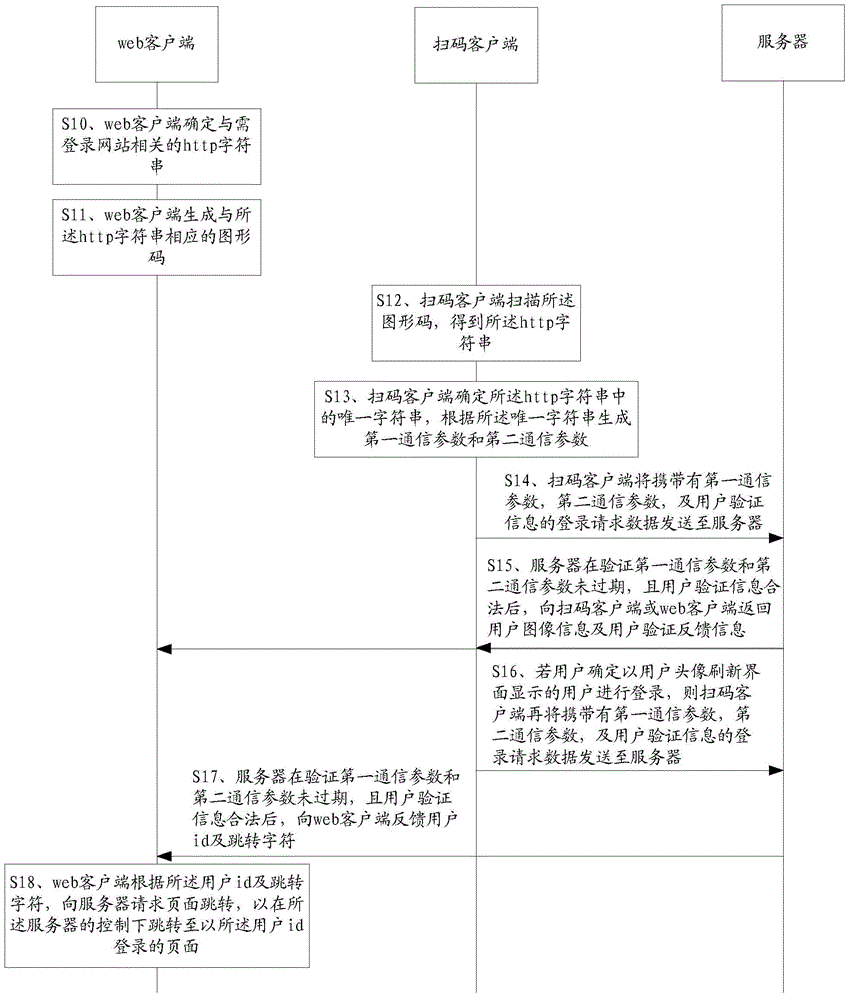
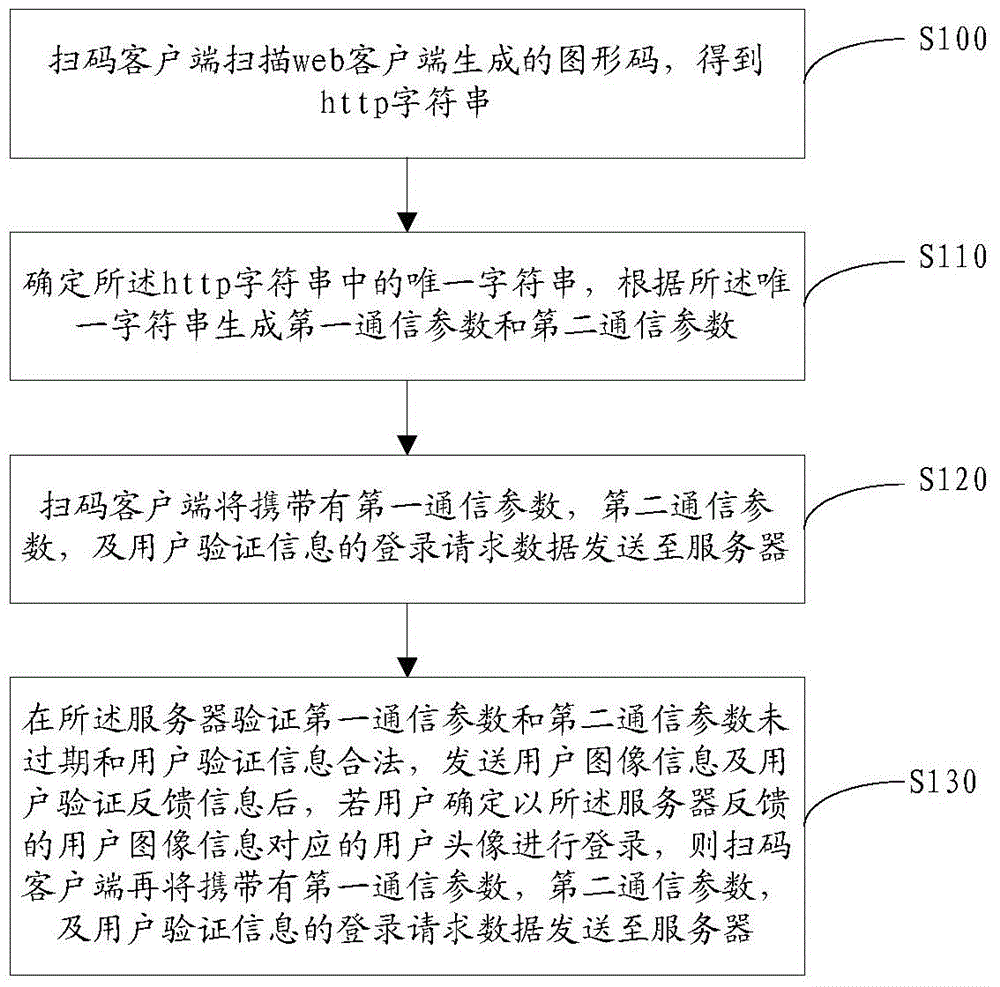
Website login method, code-scanning client and server
The invention provides a website login method, a code-scanning client and a server. The website login method comprises the following steps: the code-scanning client scans a graphic code generated by a web client to obtain http character strings; the sole character string in the http character strings is determined to generate a first communication parameter and a second communication parameter; login request data carrying the first communication parameter, the second communication parameter and user authentication information is sent to the server; after the server validation passes, if a user determines that login is performed through a user head portrait corresponding to user image information fed back by the server, the code-scanning client sends the login request data to the server, so that the server can conveniently feed back user id and skip characters to the web client after passing of one more validation to enable the web client to skip to a page for login through the user id. According to the invention, the user can log in a website through scanning a graphic code, so that the user operation is greatly reduced, and the security of the user account and login password is improved.
Owner:ZHENGZHOU XIZHI INFORMATION TECH
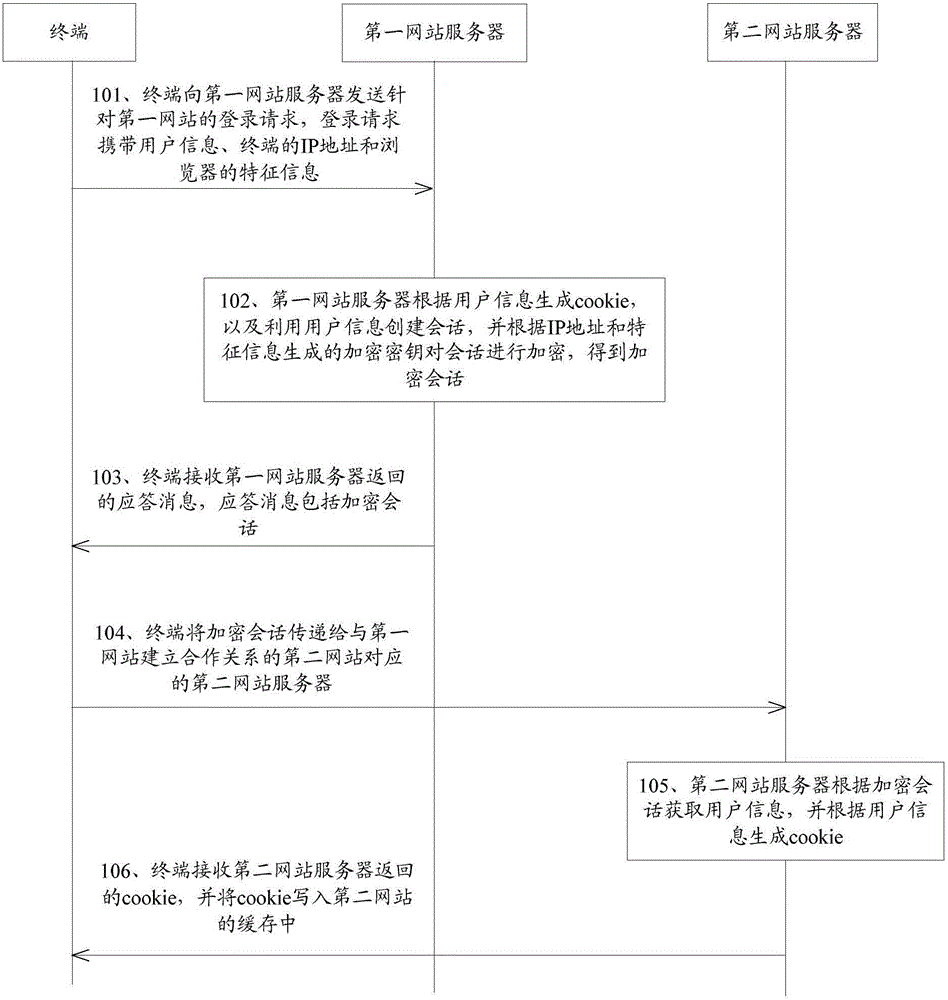
Cross-website login method, terminal and website server
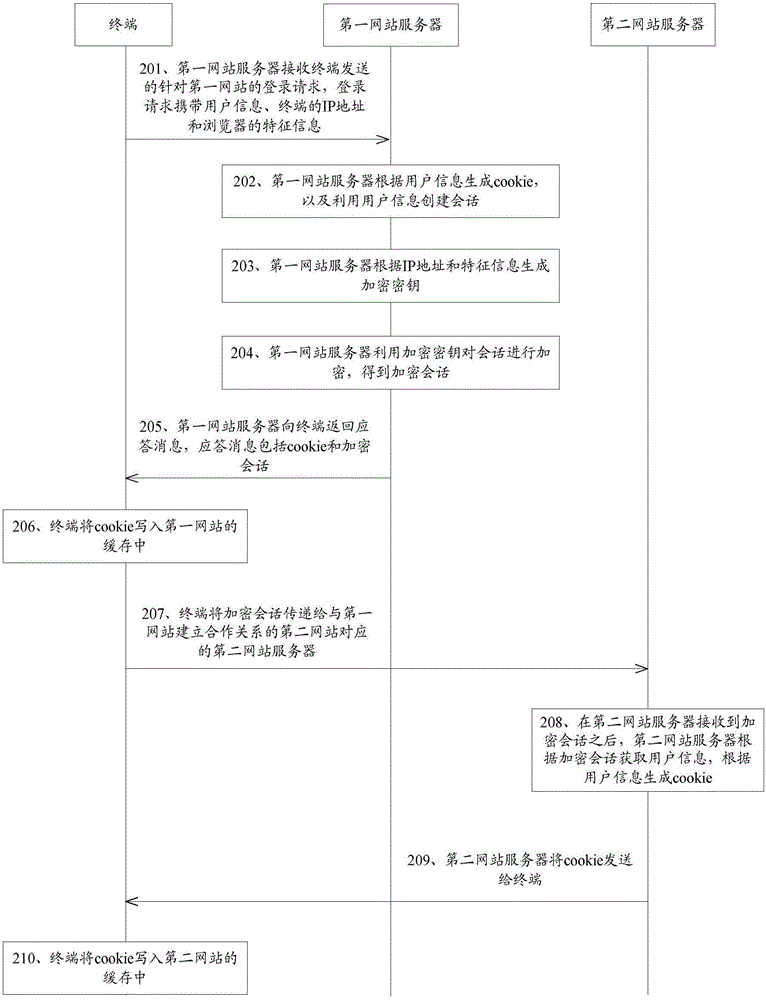
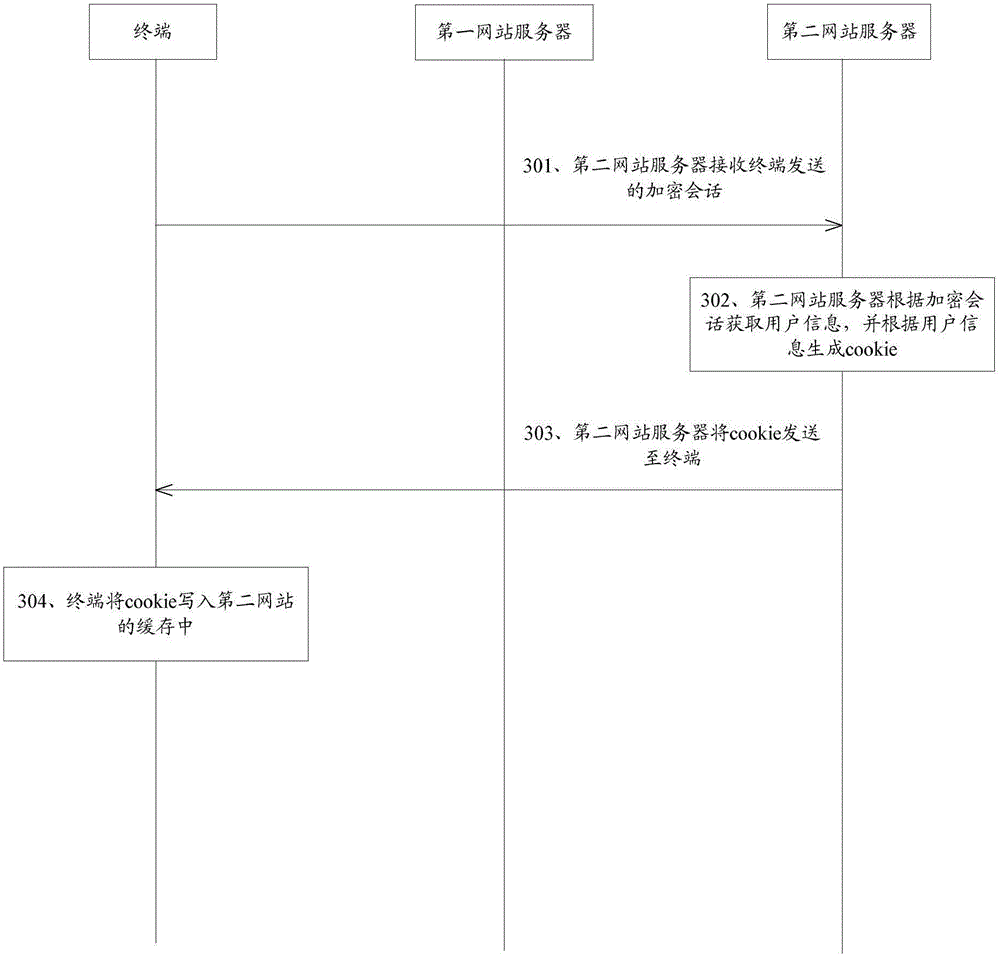
The embodiment of the invention discloses a cross-website login method, a terminal and a website server. The method comprises that the terminal sends a login request specific to a first website to a first website server, wherein user information, the IP address of the terminal and feature information of a browser are carried in the login request; the first website server produces cookie according to the user information, establishes a session by using the user information and encrypts the session, thus obtaining the encrypted session; the terminal receives a response message returned by the first website server, wherein the response message comprises the encrypted session; the terminal transmits the encrypted session to a second website server, wherein the second website server corresponds to a second website which establishes cooperative relationship with the first website; the second website server obtains the user information according to the encrypted session and produces the cookie according to the user information; and the terminal receives the cookie returned by the second website server and writes the cookie in the cache of the second website. Through application of the embodiment of the method, the terminal and the server, cross-website login of different domain names can be realized.
Owner:SHENZHEN GIONEE COMM EQUIP
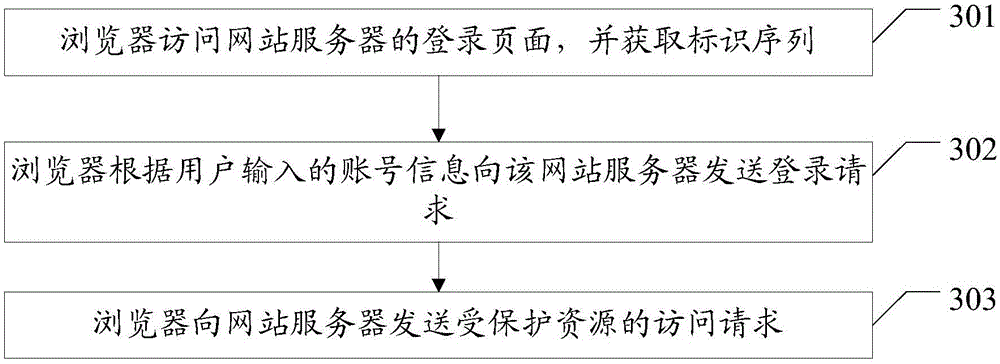
Session method, web server and browser
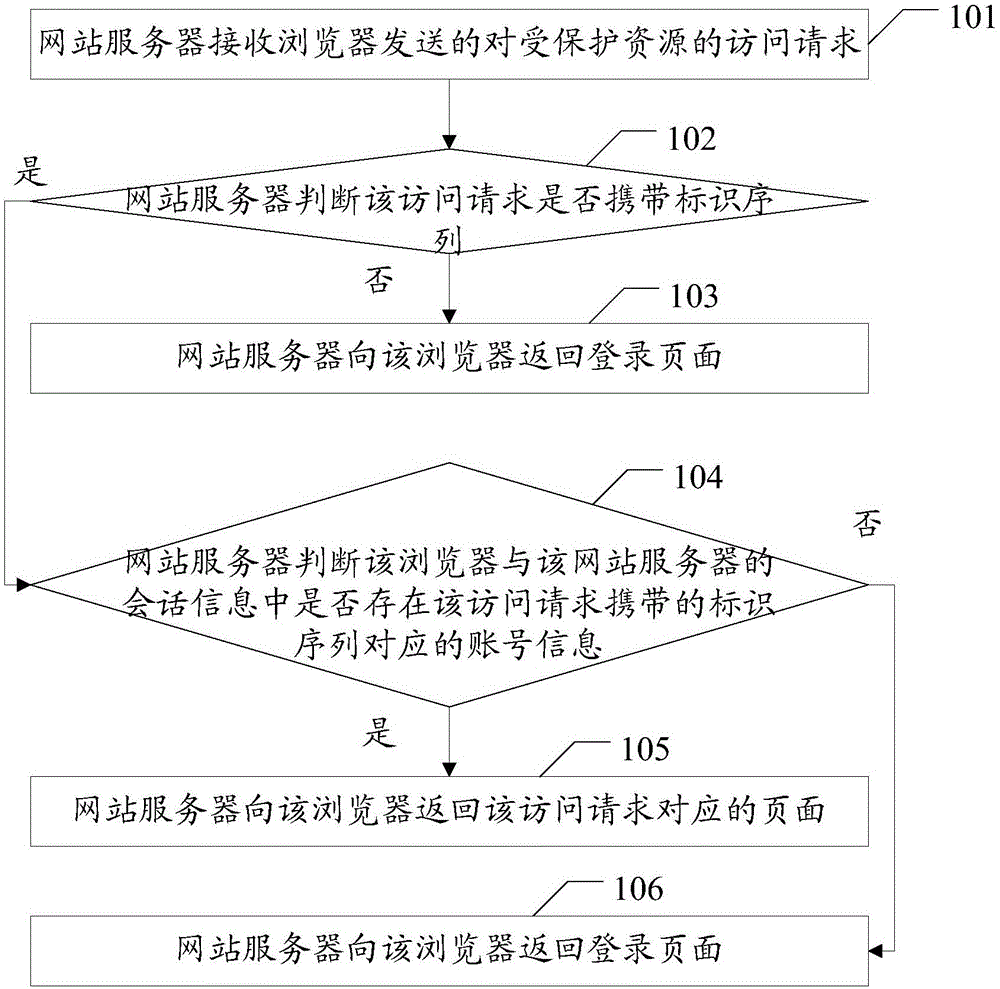
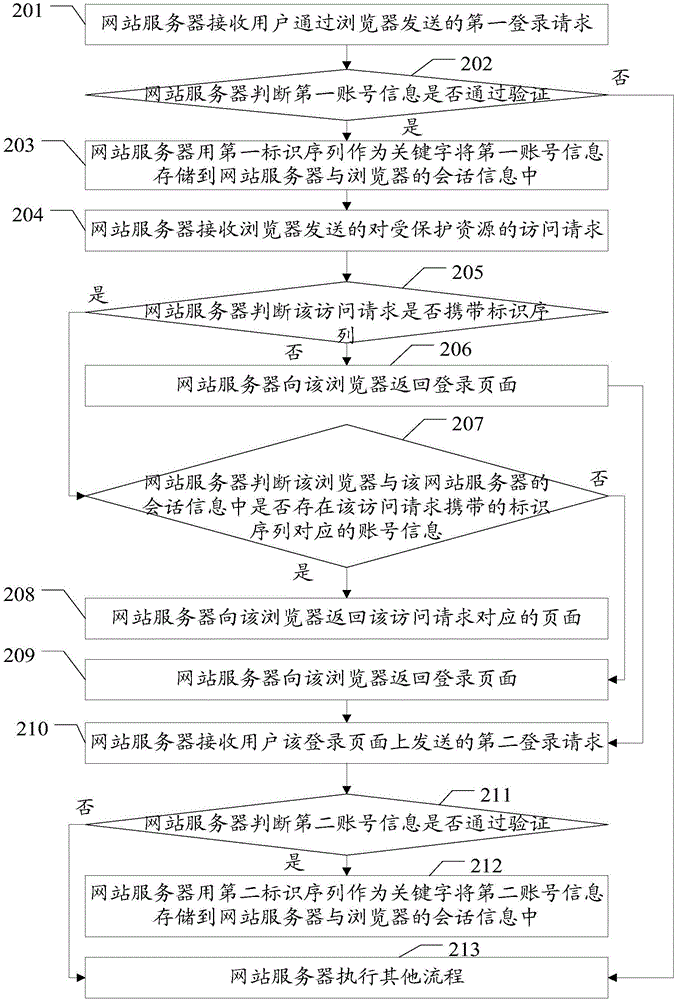
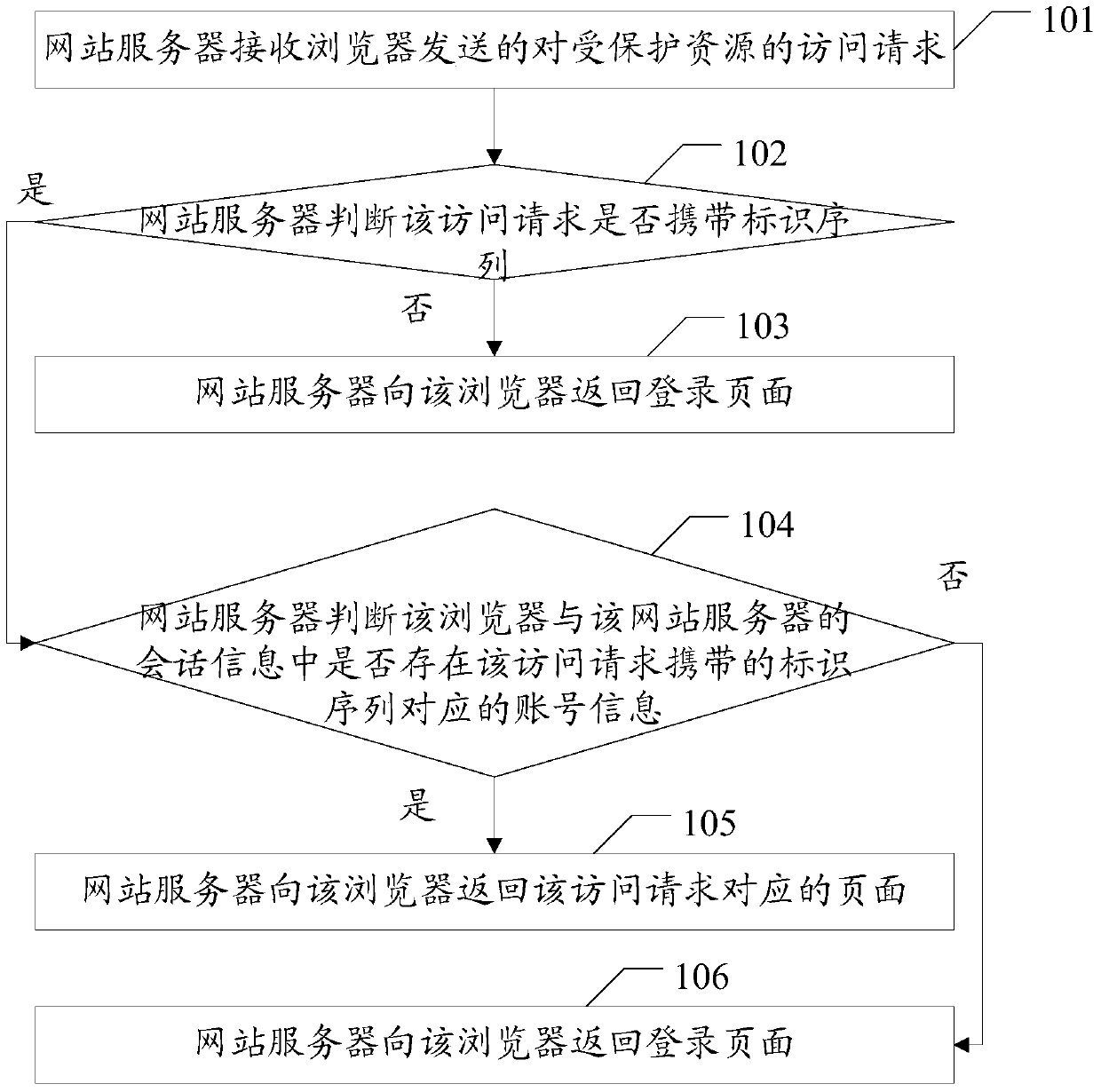
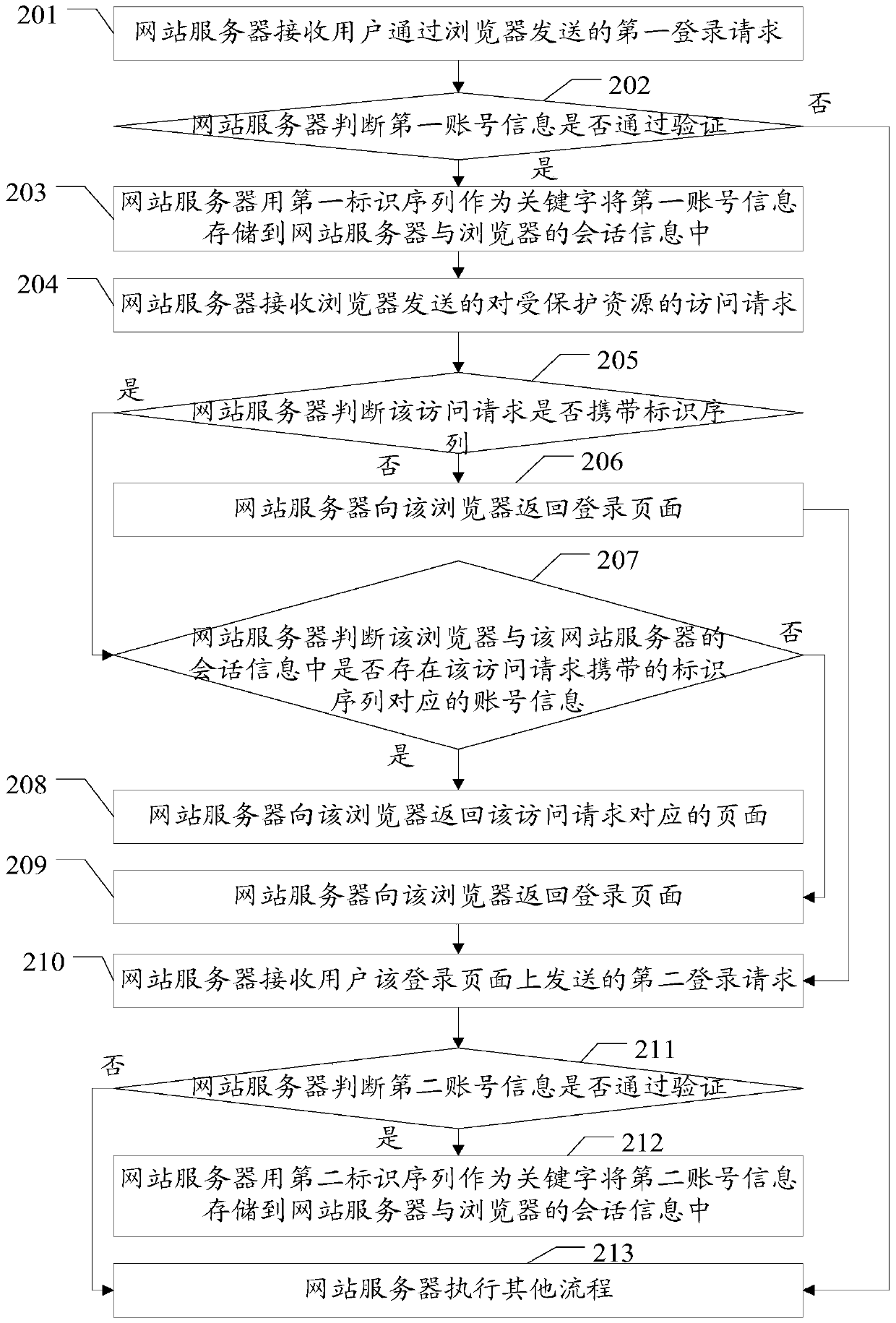
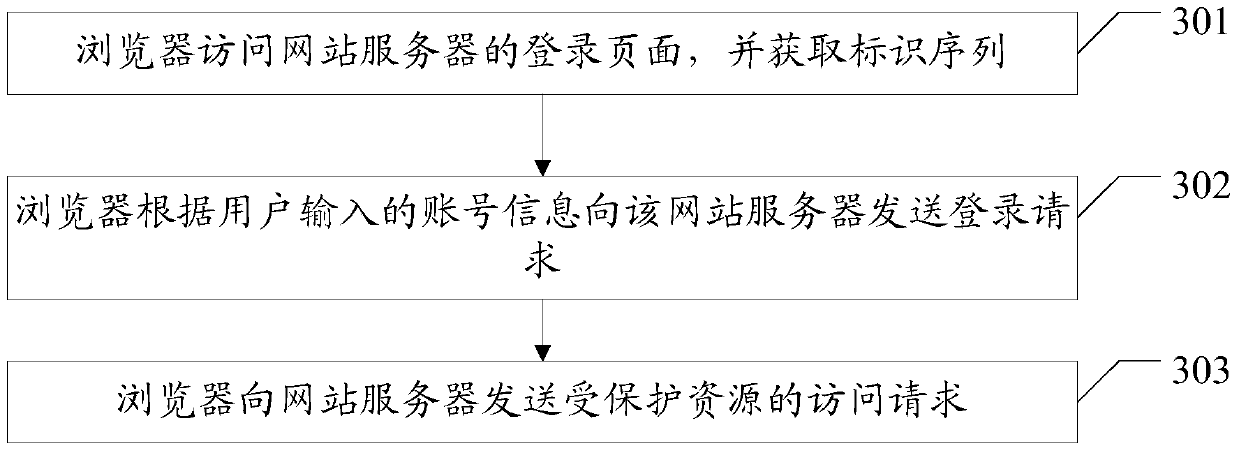
Embodiments of the invention disclose a session method, a web server and a browser, which are used for implementing login of a plurality of users in a plurality of tabs of a browser. The method in the embodiments of the invention comprises the following steps that the web server receives an access request for protected resources, which is sent by the browser, wherein the protected resources are only visited by legal registered users; the web server judges whether the access request carries an identification sequence, wherein the identification sequence is generated by the web server or the browser when the browser visits a login page of the web server; if the access request does not carry the identification sequence, the web server returns the login page to the browser; if the access request carries the identification sequence, the web server judges whether account information corresponding to the identification sequence carried by the access request exists in session information of the browser and the web server; if yes, the web server returns a page corresponding to the access request; if no, the web server returns the login page. The embodiments of the invention also disclose the web server and the browser, which are used for implementing login of a plurality of users in a plurality of tabs of the browser.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
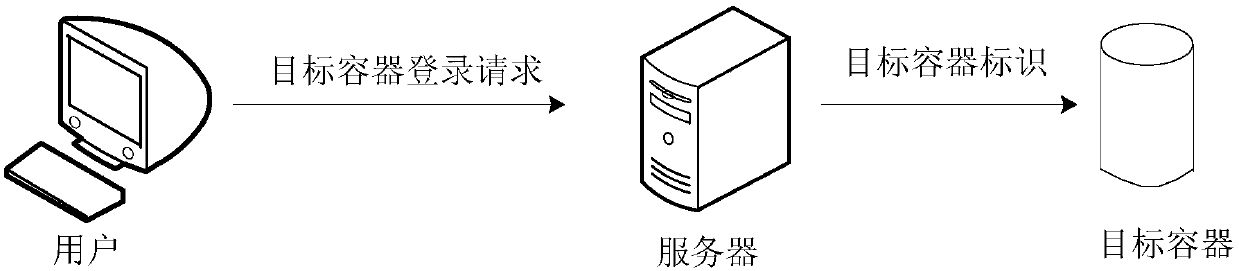
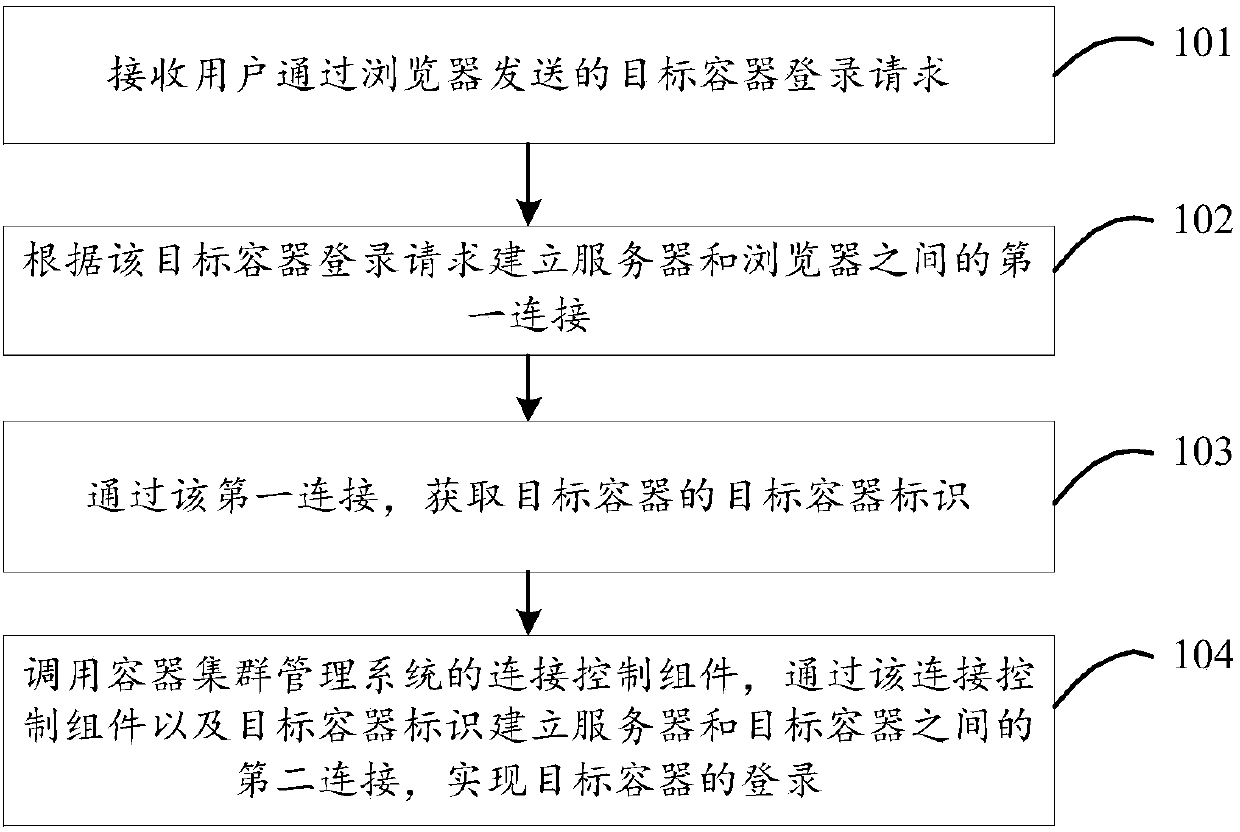
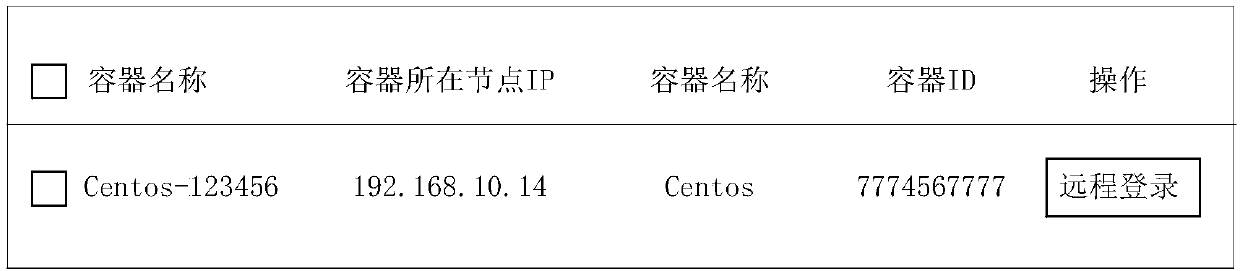
Container login method and device, and storage medium
ActiveCN109525624ALogin implementationEasy to operateProgram controlTransmissionOperating systemManagement system
Embodiments of the invention disclose a container login method and device, and a storage medium. The method comprises the steps that when a target container login request sent by a user through a browser is received, a first connection between a server and the browser is established according to the target container login request; through the first connection, a target container identifier of a target container is obtained; and a connection control component of a container cluster management system is called, and a second connection between the server and the target container is established through the connection control component and the target container identifier, so that the login of the target container is realized. The operation of logging in the target container by the user can be simplified.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
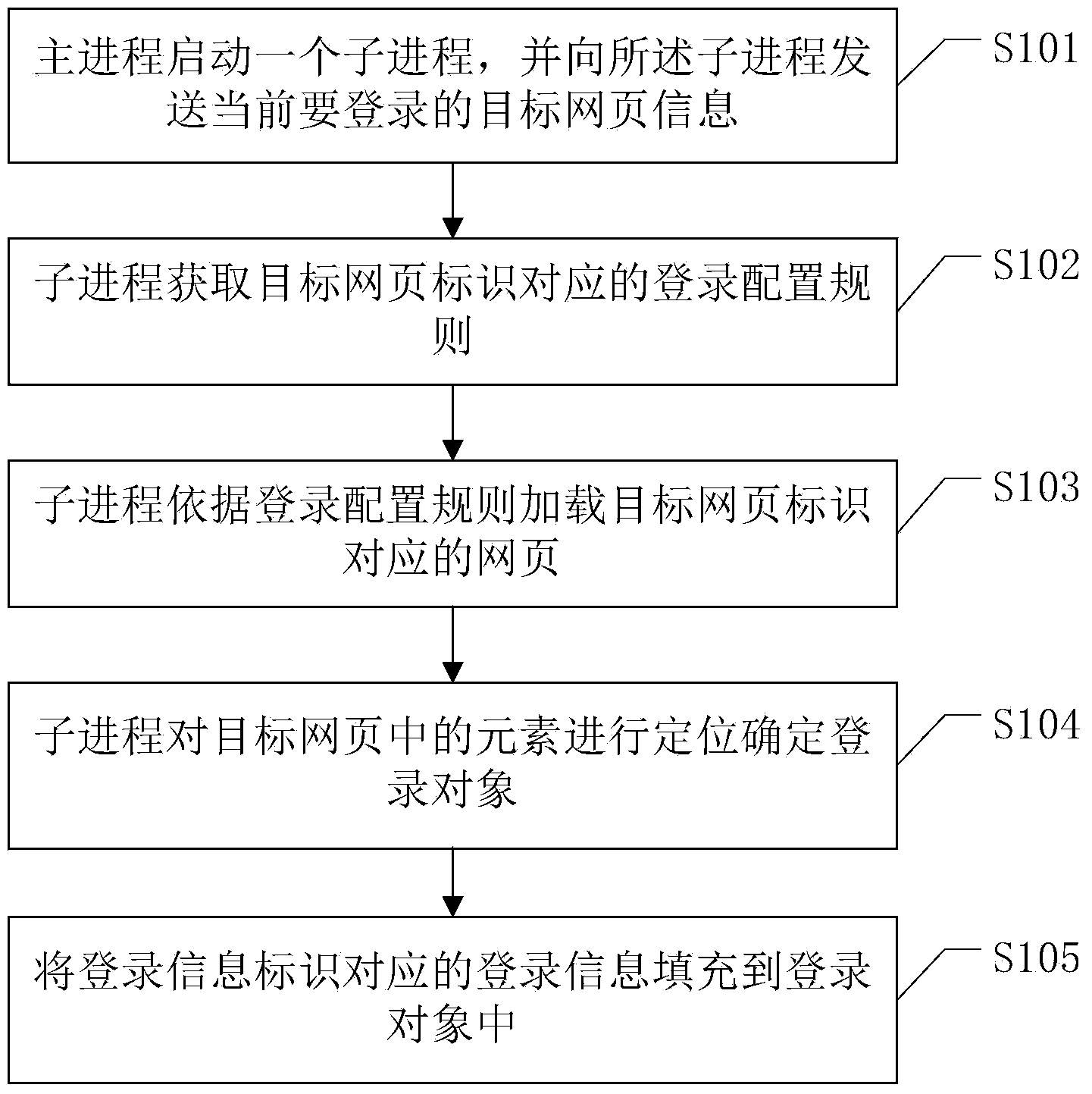
Method and device for logging in web page
The invention discloses a method and a device for logging in a web page. The method comprises the steps as follows: a host process starts a sub-process and sends information of the target web page to be logged in currently to the sub-process; the sub-process obtains a login configuration rule corresponding to a target web page identifier; the sub-process loads the target web page corresponding to the target web page identifier according to the login configuration rule; the sub-process locates elements in the target web page so as to determine a login object; and login information corresponding to a login information identifier is filled in the login object. The step that the sub-process loads the target web page corresponding to the target web page identifier according to the login configuration rule specifically comprises the steps as follows: the target web page corresponding to the target web page identifier is loaded; whether the login configuration rule includes a dynamic library interception step or not is judged, and if the login configuration rule includes the dynamic library interception step, a dynamic link library corresponding to the target web page is intercepted. Compared with form filling login methods in the prior art, the login method has the advantage that a user can use a plurality of different account numbers and passwords to log in one website simultaneously.
Owner:BEIJING QIHOO TECH CO LTD
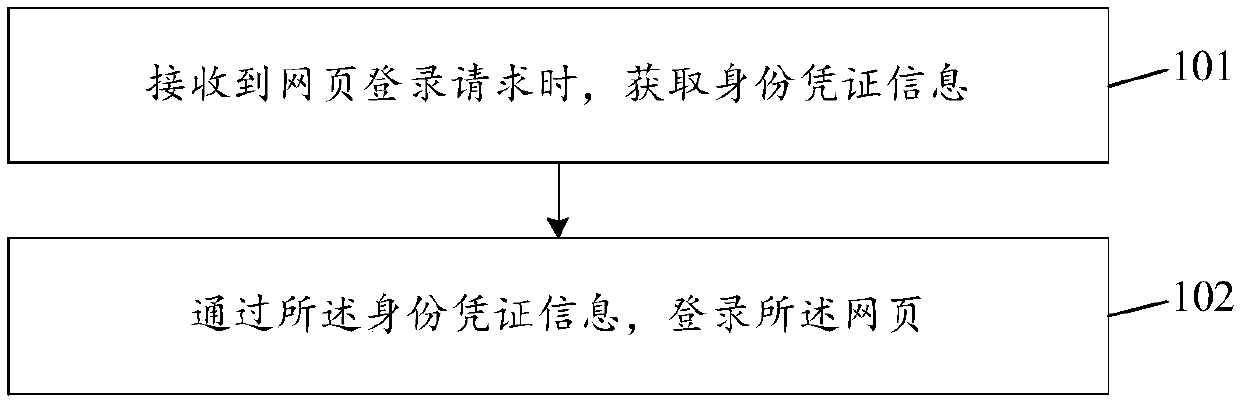
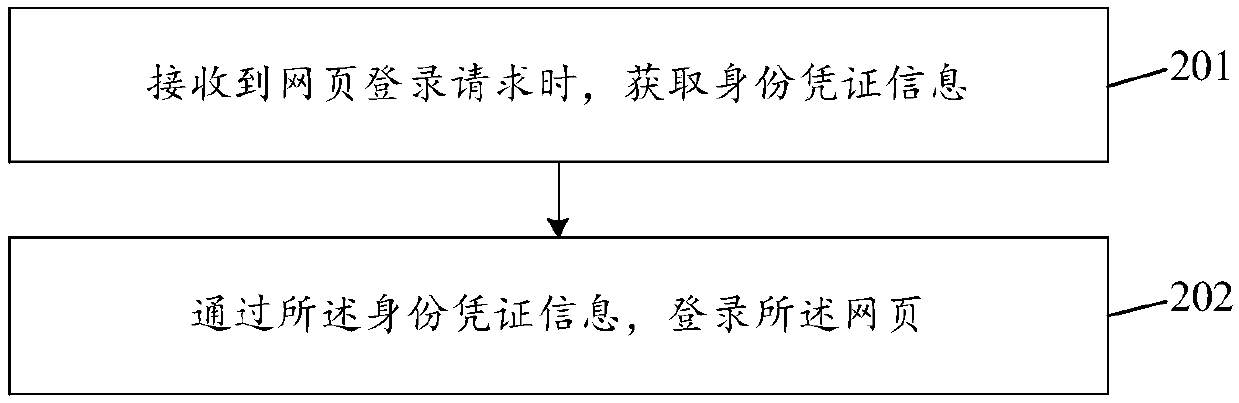
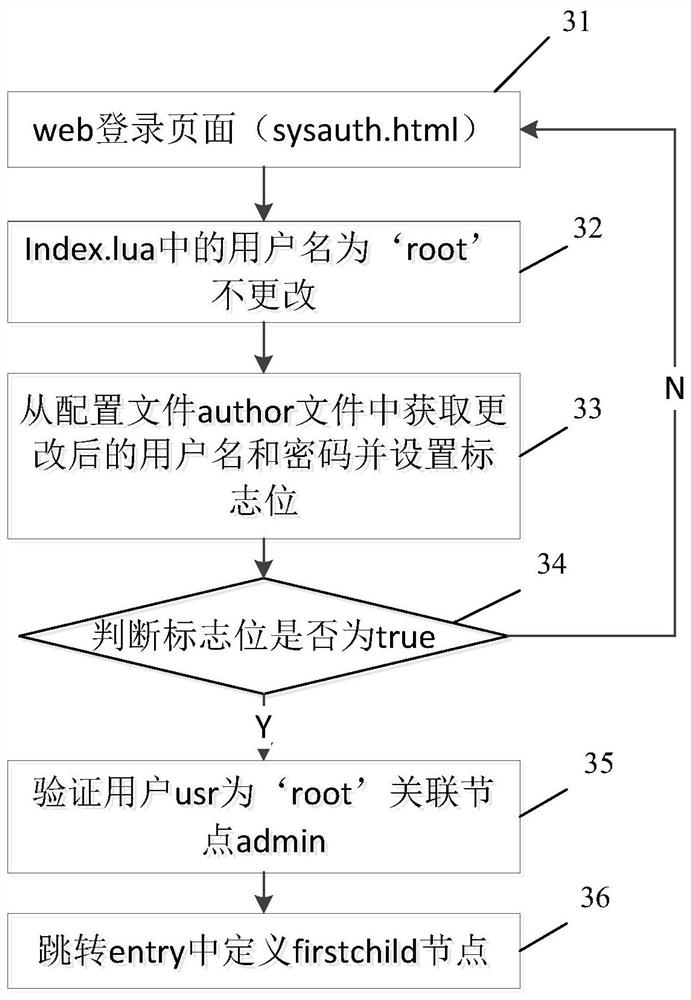
Webpage data crawling method and device and webpage login method and device
PendingCN110968760ALogin implementationAvoid restrictionsWeb data indexingTransmissionWeb siteInternet privacy
The invention discloses a webpage data crawling method and device, a webpage login method and device, relates to the technical field of networks, and mainly aims to solve the problem that crawling ofwebpage data in websites is extremely easy to fail. The method comprises the steps that when a crawling request is received, identity certificate information is obtained, and the identity certificateinformation is generated according to a user name and a password when a user logs in a webpage; logging in the webpage through the identity certificate information; and after logging in the webpage, crawling webpage data in the webpage. The invention is suitable for crawling the data in the website through the crawler.
Owner:BEIJING GRIDSUM TECH CO LTD
Charging control system and method for self-service equipment
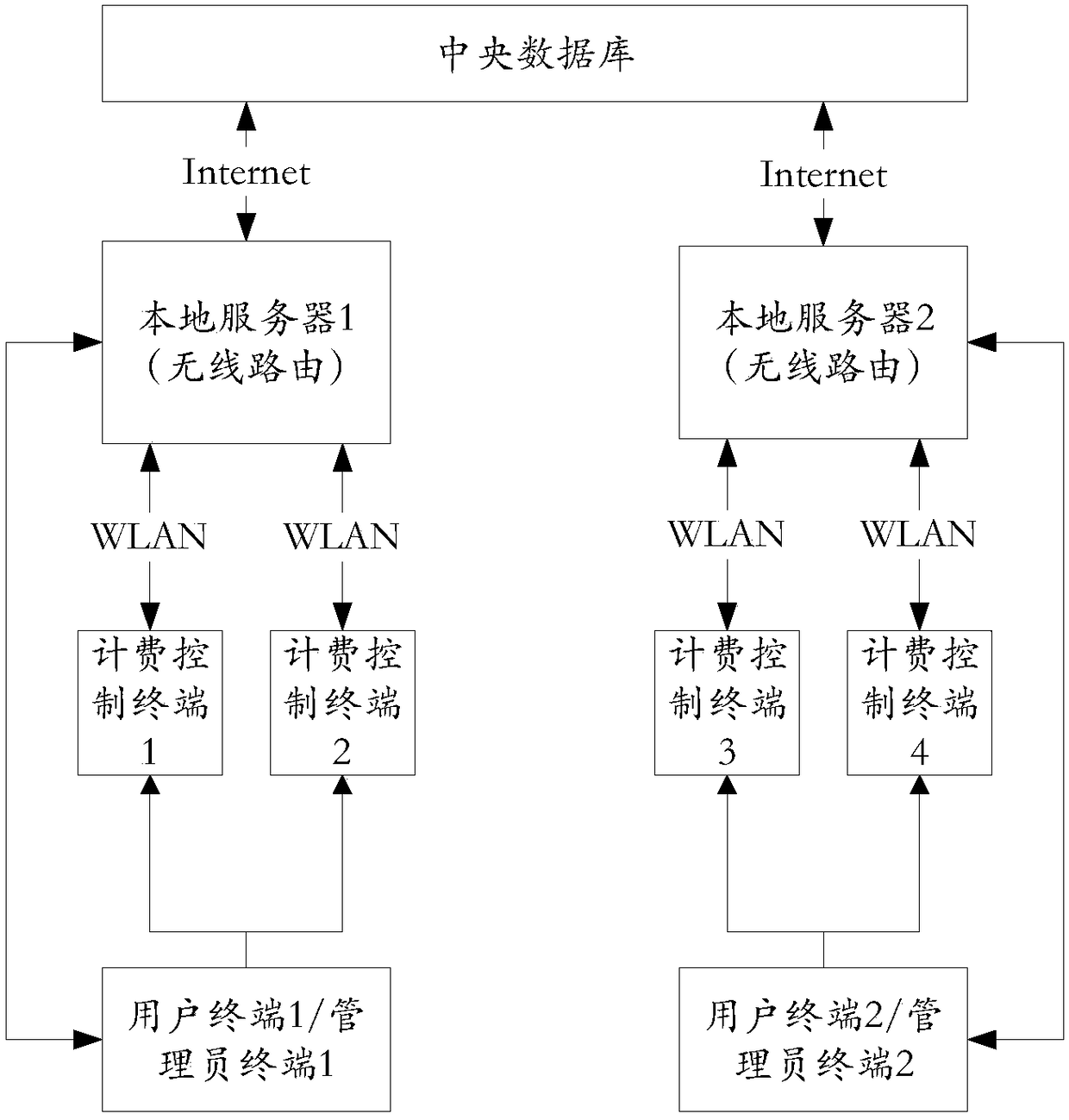
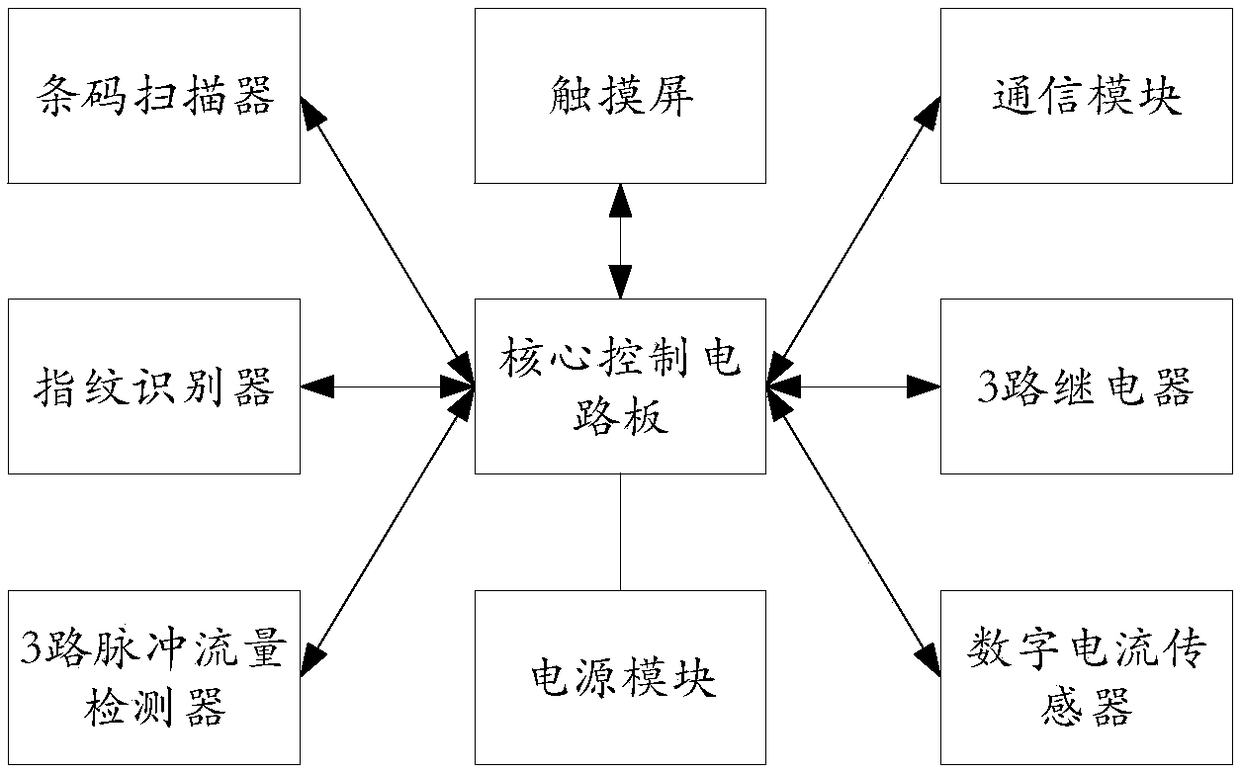
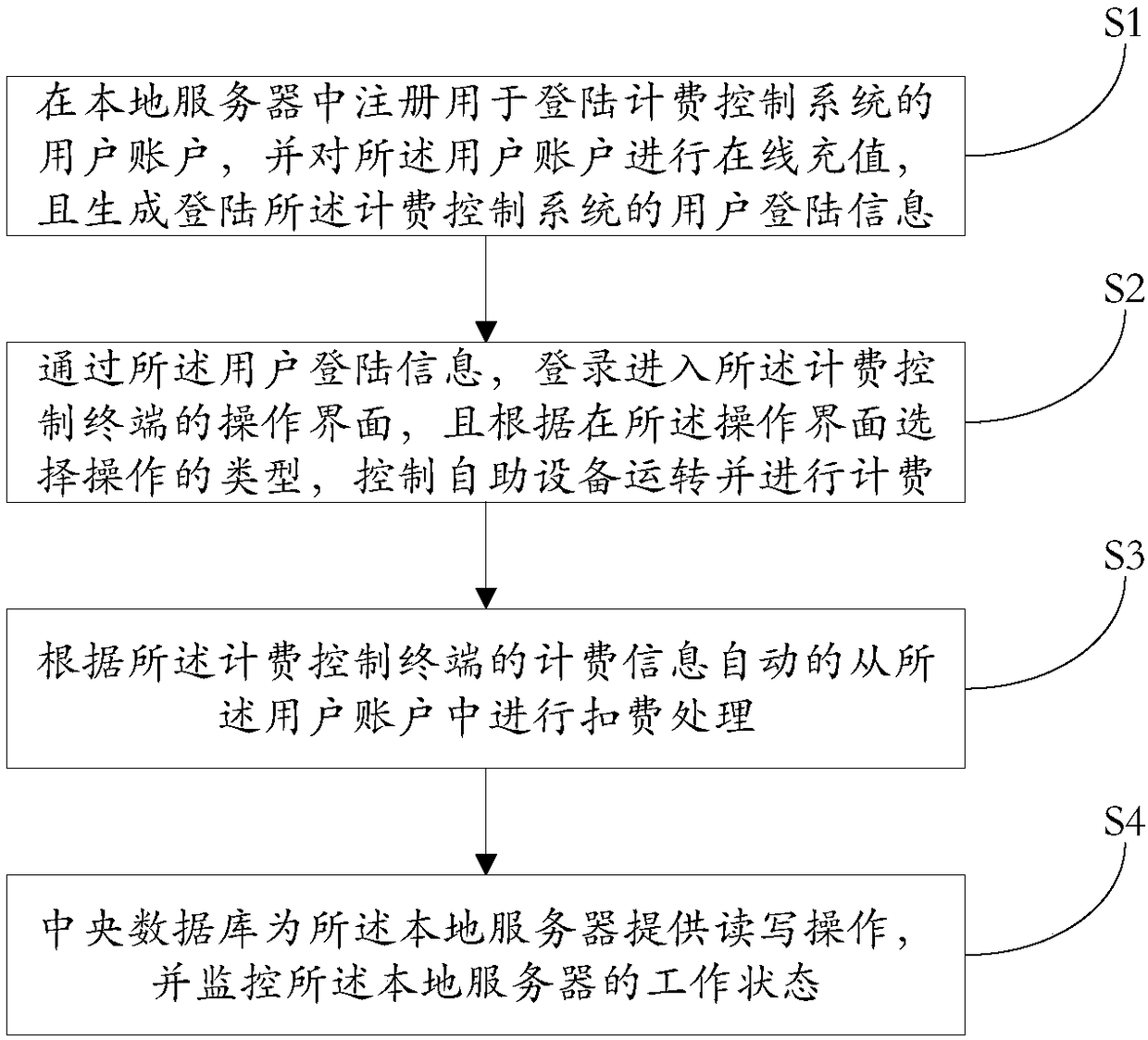
PendingCN108428125AConvenient paymentFlexible login methodsPayment architectureApparatus for meter-controlled dispensingMonetary AmountControl system
The invention relates to a charging control system and method for self-service equipment. The system comprises a user terminal, a plurality of charging control terminals and a local server; the user terminal is used for registering a user account for logging in to the charging control system in the local server, recharging the user account online and generating user login information of logging into the charging control system; each charging control terminal is used for entering an operation interface of the charging control system through the user login information, controlling the self-service equipment to run according to an operation type selected on the operation interface and conducting charging; the local server is used for monitoring and managing the charging control terminals andautomatically deducting amount from the user account according to charging information of the corresponding charging control terminal. According to the system, through account self-creation and account login, the corresponding charging control terminal achieves charging control over the self-service equipment, the charged amount is deducted from the account online, the amount payment is quick andconvenient, and the system can adapt to various different application scenarios.
Owner:唐晓冬
Double-factor authentication security supervisor login system and method
The invention relates to a double-factor authentication security supervisor login system and method. Login plugin is installed in the security supervisor, unique identification is transmitted to a server, the server generates verification information according to the unique identification and returns the verification information to the security supervisor, the security supervisor displays the verification information as a two-dimensional code, a user terminal scans the two-dimensional code to verify the verification information, a server receives a verification request of the user terminal, when the request is matched with the account and verification information of the security supervisor in the server, the security supervisor is marked as verification passing, a verification passing state is transmitted to the security supervisor, and the security supervisor receives the verification passing state to finish login. By the double-factor authentication security supervisor login system and method, extra hardware is not required, double passwords do not need to be memorized, complicated rules do not need to be set, the cost is low, hardware such as USB key is omitted, double-factor login complexity degree is reduced, and the cost of the safety technology is reduced.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
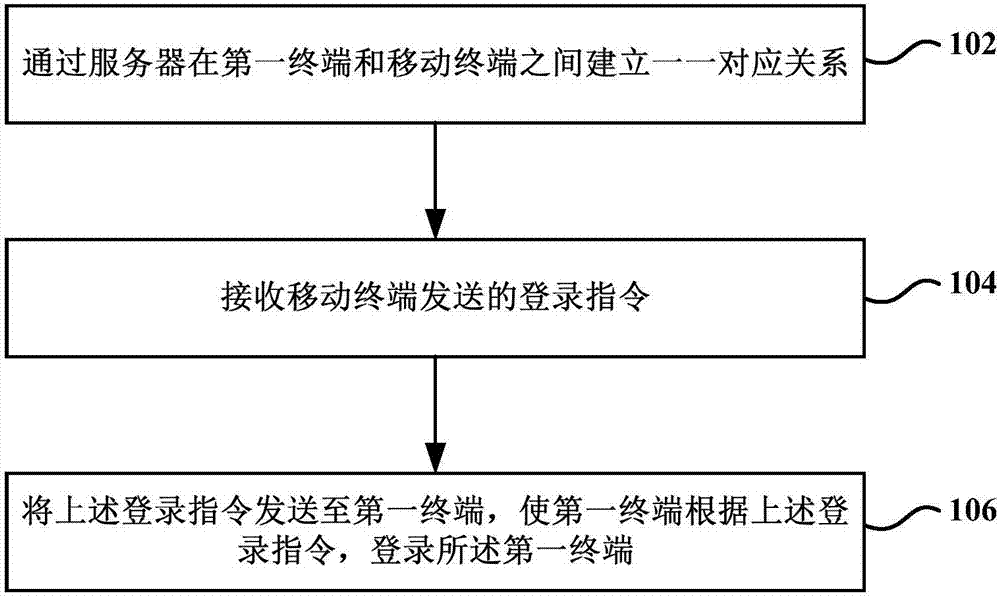
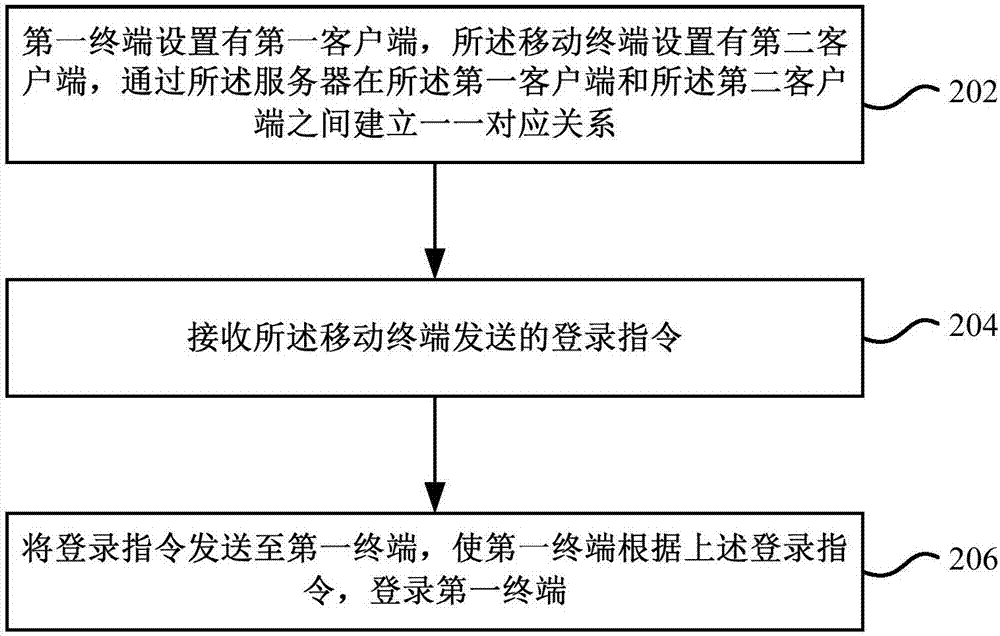
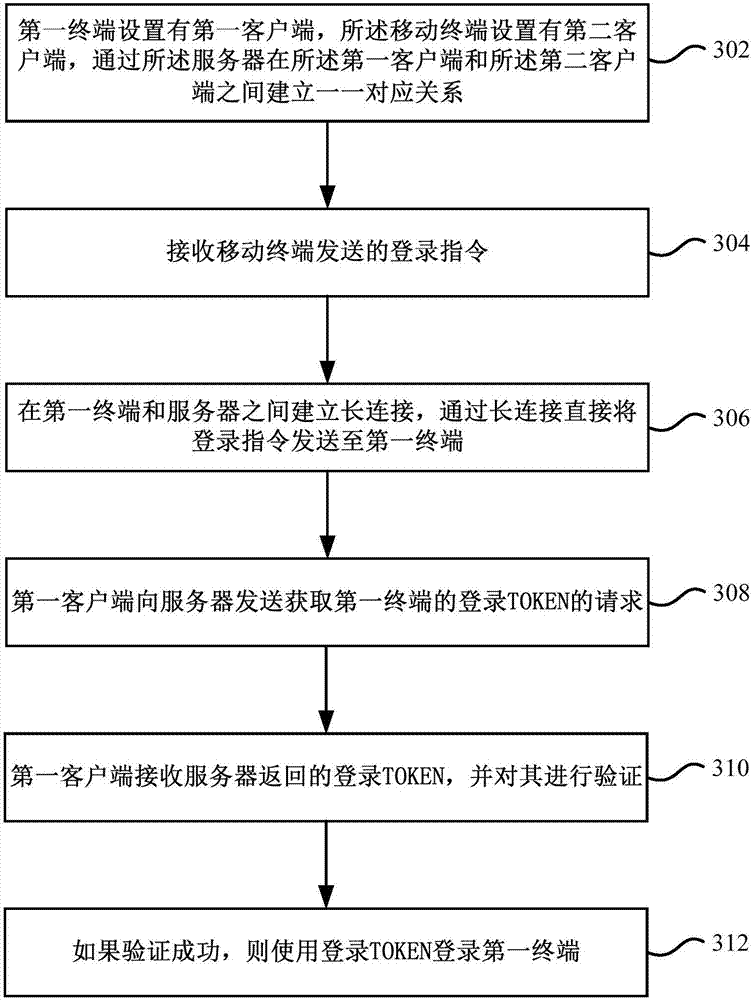
Terminal login method and system
The invention provides a terminal login method and system. The terminal login method comprises the following steps: establishing a one-to-one correspondence relationship between a first terminal and a mobile terminal by a server; receiving a login instruction sent by the mobile terminal; and sending the login instruction to the first terminal, so that the first terminal logs in the first terminal according to the login instruction. Based on the terminal login method and system provided by the invention, during the login of the terminal, a user does not need to manually input login information and only needs to establish the one-to-one correspondence relationship between the mobile terminal and the to-be-logged in terminal, and the login of the terminal can be realized by performing simple operations on the mobile terminal, thereby greatly improving the user experience.
Owner:BEIJING QIHOO TECH CO LTD
Application account login method and system based on ciphertext Hash retrieval
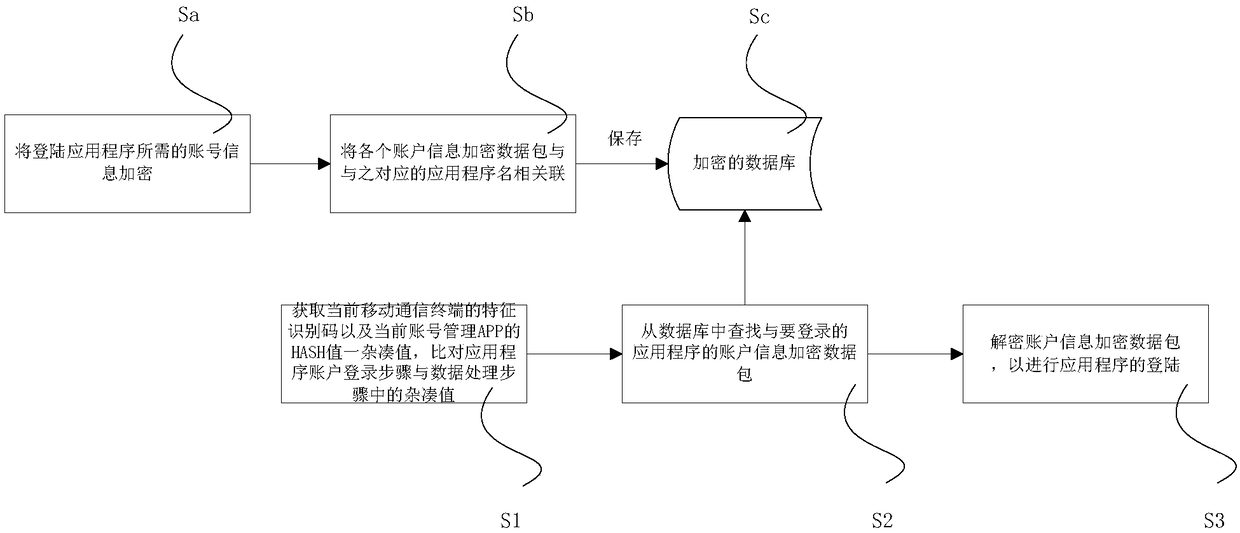
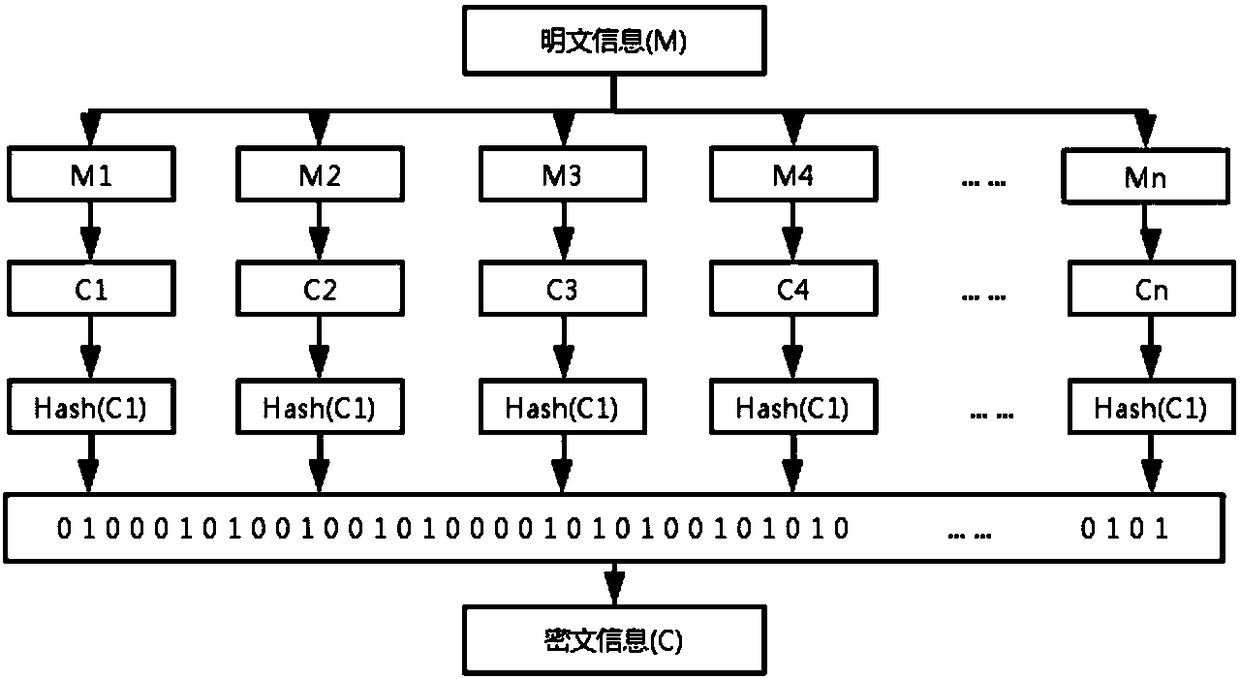
InactiveCN108390753ARealize functionImplement double encryptionEncryption apparatus with shift registers/memoriesUser identity/authority verificationTaskbarCiphertext
The invention discloses an application account login method and system based on ciphertext Hash retrieval. The method includes the following steps: encrypting account names, passwords and other information in a mobile phone login process by using an SQLCipher technology, binding the encrypted information to a mobile phone identification code to establish an account library, and further realizing the function that the accounts and passwords are automatically classified and retrieved and automatically input during login; enabling a user to save account information in a classification mode basedon applications, encrypting the account information through a mobile phone feature code and master key related information by using an SMS4 encryption algorithm and a Hash algorithm, and then saving the information in a database to realize the double encryption of the data and database. After entering the system to turn on an application login mode, the function resides in a taskbar, when the userclicks the automatic entry function in the taskbar, the system calculates and retrieves a Hash value of a data character combination ciphertext in the background and merges the value into a characterstring, and then the corresponding account information can be retrieved by using the character string, the account login based on ciphertext Hash retrieval can be achieved, and the scheme of the invention is simple in operation and convenient in management, and has high security.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
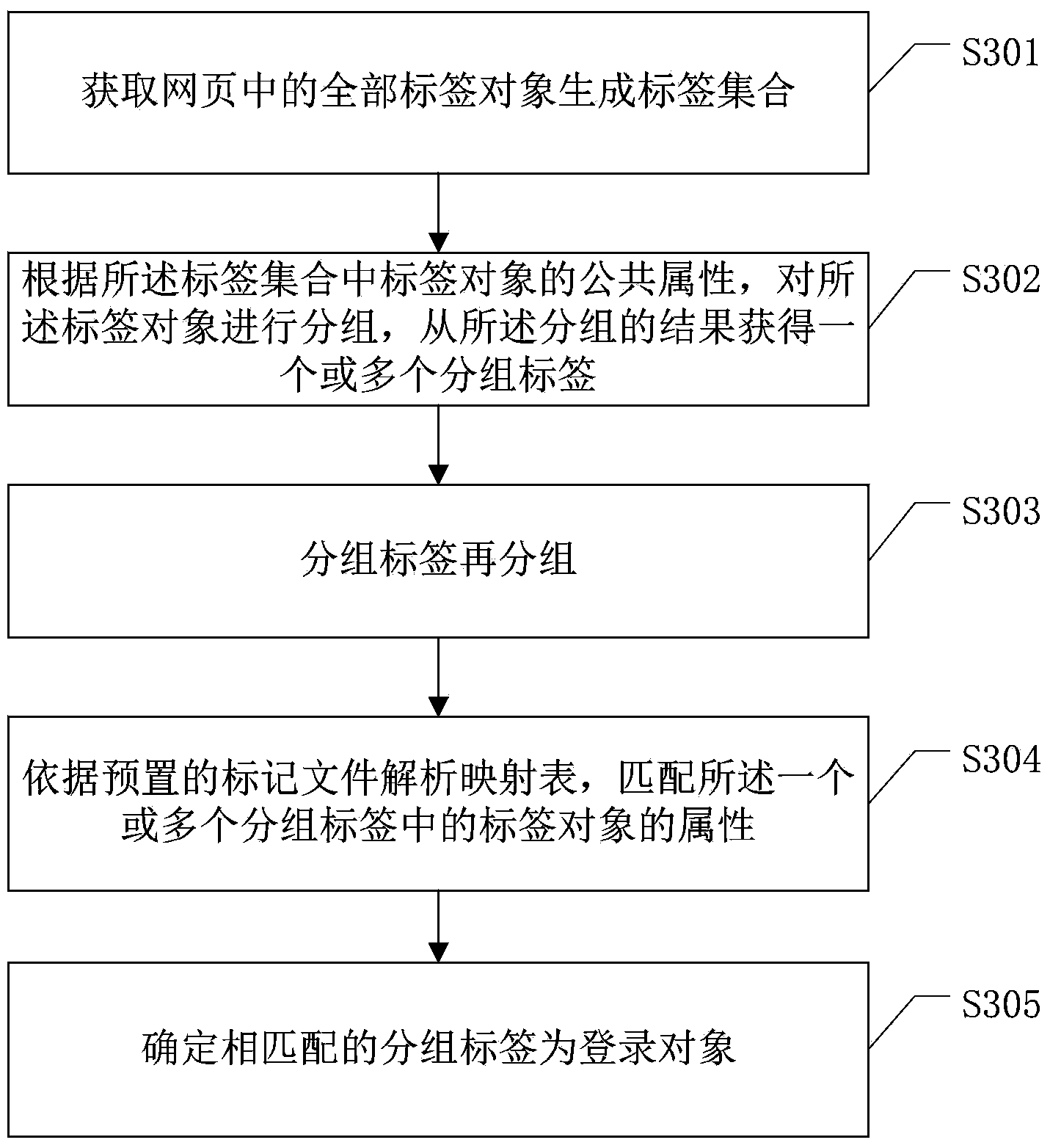
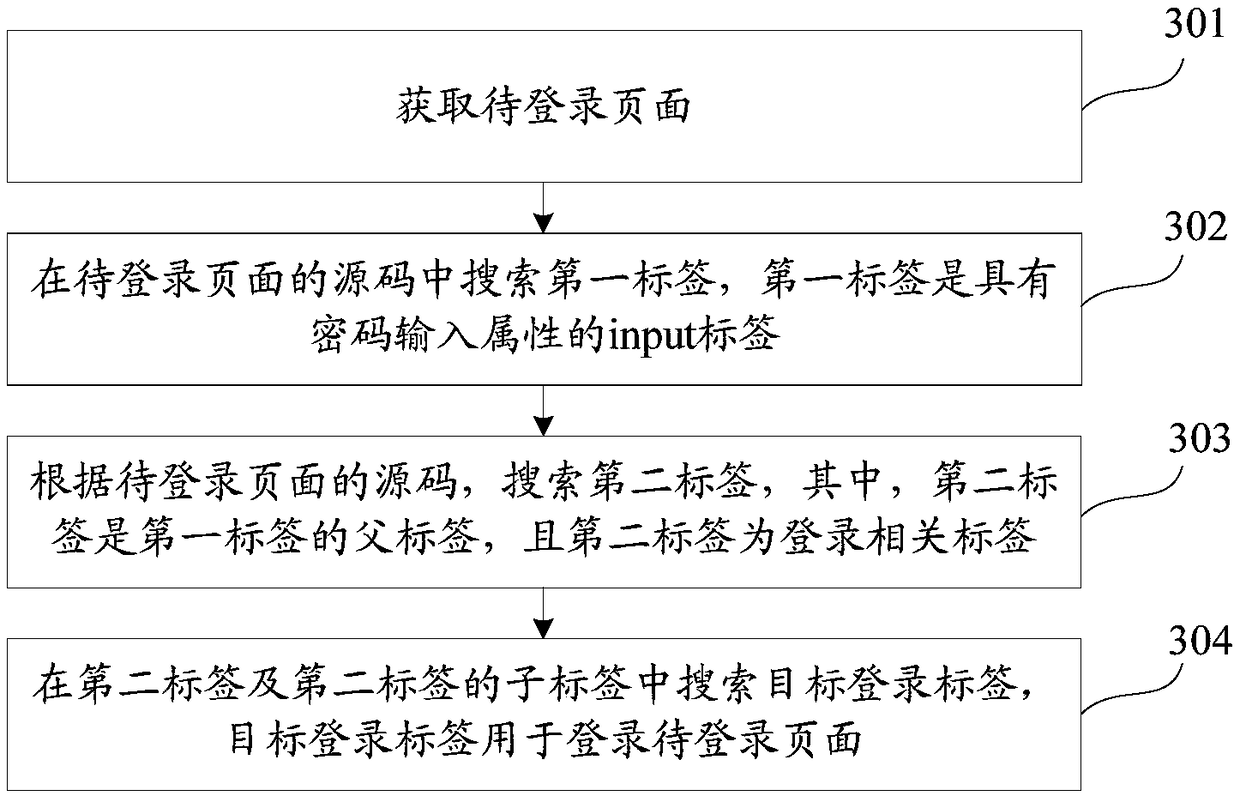
Webpage login method and device and readable storage medium
ActiveCN109246069ALogin implementationImprove login speedUser identity/authority verificationWeb data queryingPasswordSource code
The invention discloses a webpage login method and device and a readable storage medium. The method comprises the steps: searching for a first label in the obtained source codes of a page to be loggedin, wherein the first label is an input label with the password input attribute; searching for a second label correlated with the log-in according to the source codes of the page to be logged in after the first label with the password input attribute is searched in the source codes of the page to be logged in because an account and a password generally appear in the same row or column through combining with the common design of a page, wherein the second label is the parent label of the first label; searching for a target login label for logging in the page to be logged in from the second label and a son label of the second label, thereby achieving the webpage login, increasing the login speed of the webpage, and increasing the success rate of the webpage login.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
Resource calling method, resource calling device, client and business server
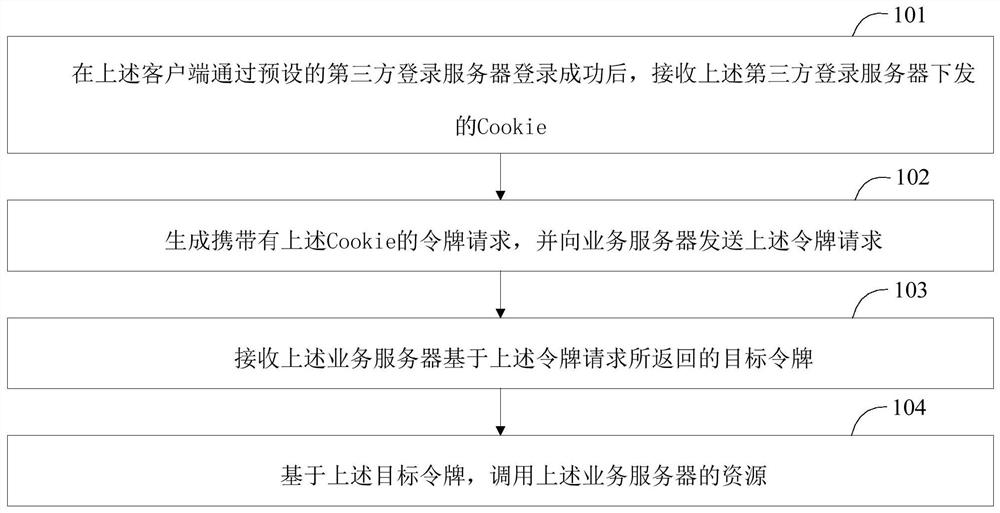
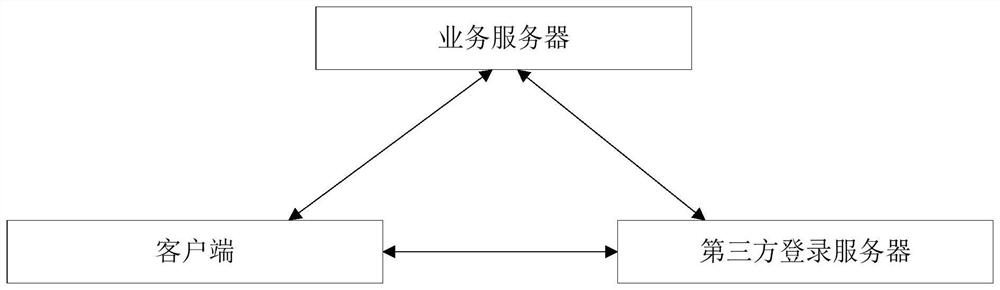
ActiveCN111371811AReduce Design ComplexityGuarantee data securityTransmissionData securityThird party
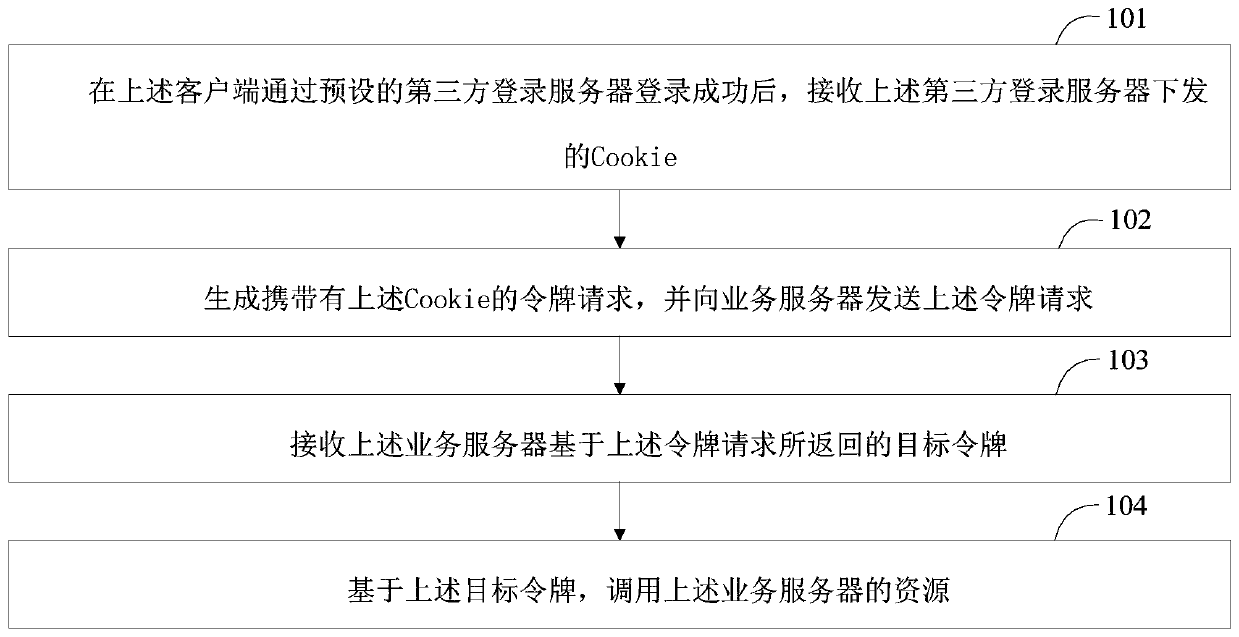
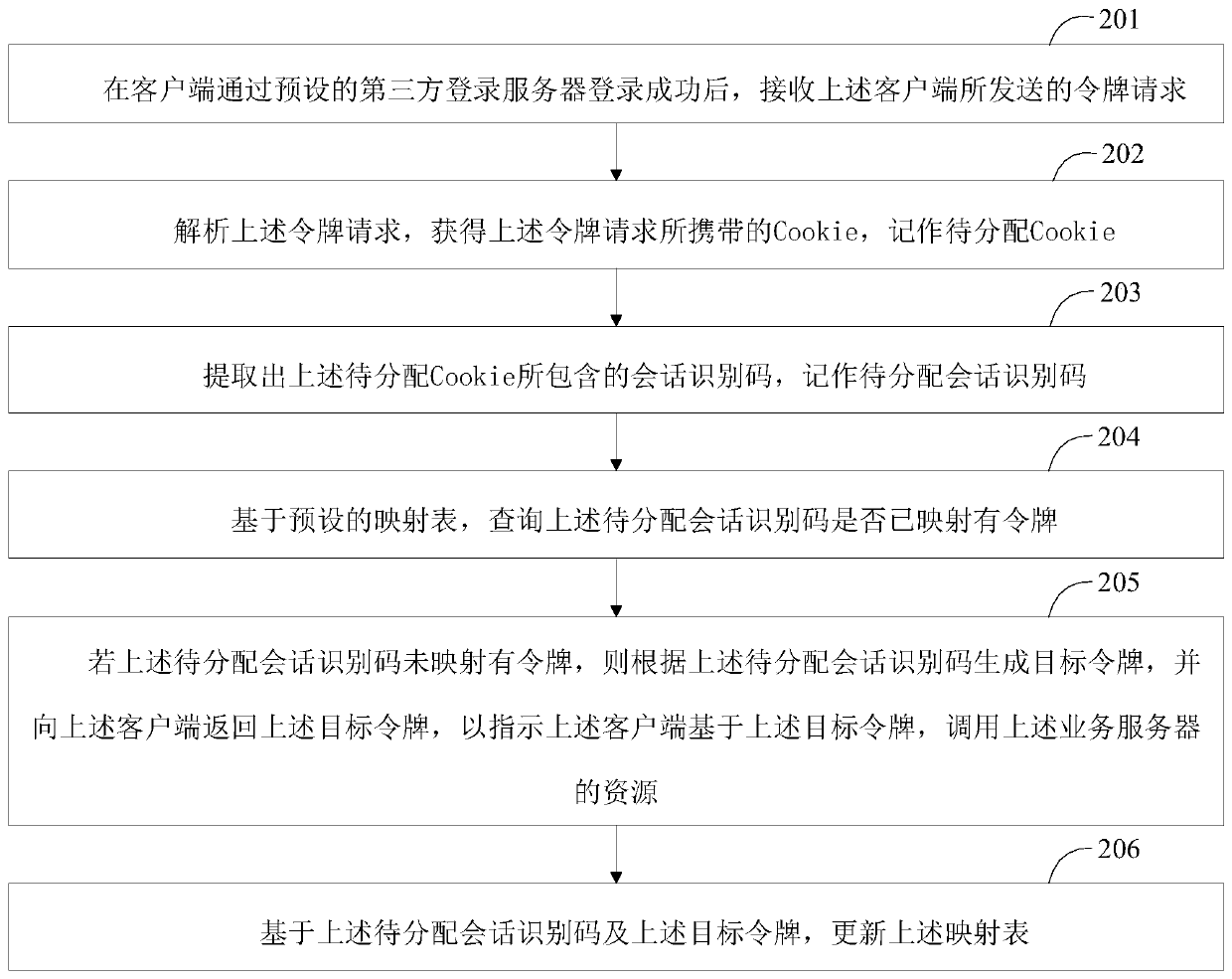
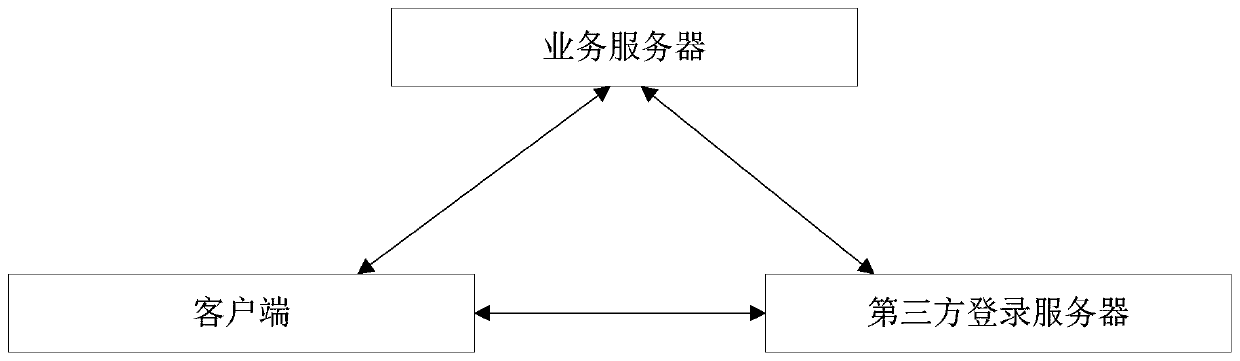
The invention discloses a resource calling method, a resource calling device, a client and a business server, and the method comprises the steps: receiving Cookie issued by a third-party login serverafter the client logs in successfully through the preset third-party login server, and enabling the Cookie to comprise a session identification code; generating a token request carrying the Cookie, and sending the token request to a service server; receiving a target token returned by the service server based on the token request, the target token being generated by the service server according toa session identification code contained in the Cookie; and calling resources of the service server based on the target token. Through the scheme of the invention, the login function can be extractedfrom the service server, so that the client logs in the service server through the third-party login server, and the data security of the service server is still ensured while the design complexity ofthe service server is reduced.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Cross-application login method and device, equipment and medium
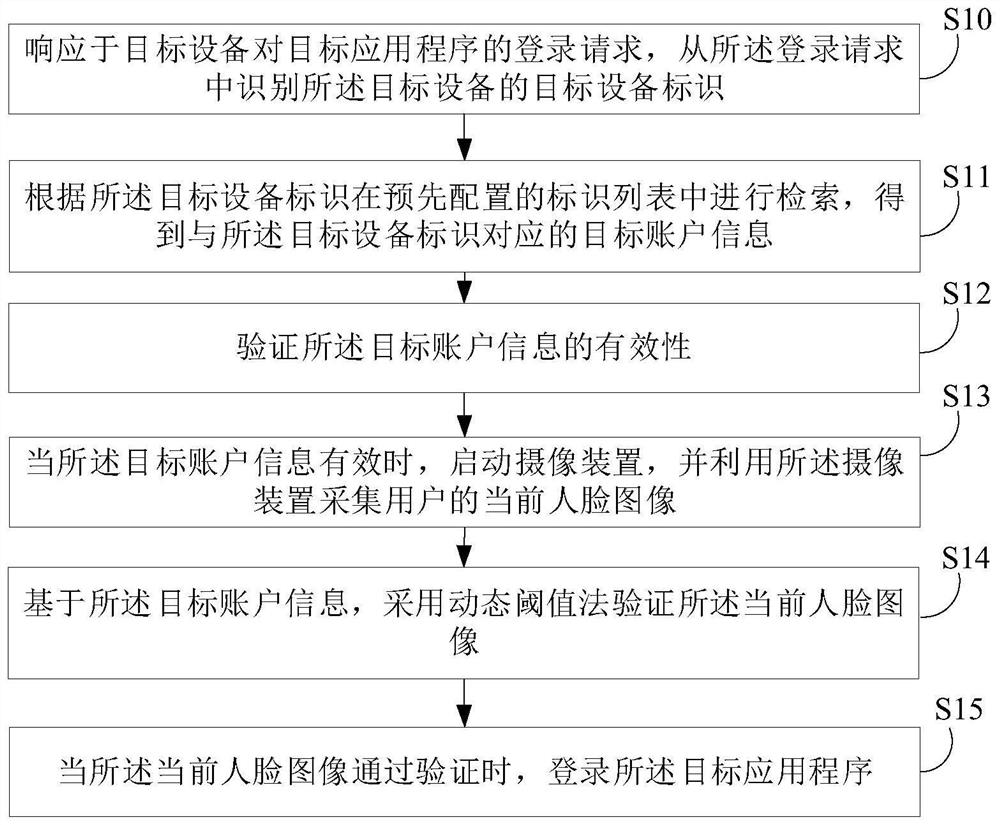
PendingCN112287318AEnsure safetyLogin implementationCharacter and pattern recognitionDigital data authenticationComputer hardwareApplication procedure
The invention relates to the field of artificial intelligence, and provides a cross-application login method and apparatus, a device and a medium, which can perform retrieval in an identifier list according to a target device identifier to obtain target account information corresponding to the target device identifier, so as to ensure that the target account information corresponding to the targetdevice identifier can be stored in the same group or the same organization. The equipment identifiers of one piece of equipment on different application programs are consistent, verifying the validity of the target account information, acquiring the current face image of the user by utilizing the camera device when the equipment identifiers are valid, verifying the current face image by adoptinga dynamic threshold method based on the target account information, and logging in the target application program when the equipment identifiers pass the verification; therefore, the related information of face authentication can be called through the unified equipment identifier to implement face login, the login security is ensured, cross-application login among different applications in the same organization is realized, and the login efficiency is improved. In addition, the invention also relates to a blockchain technology, and the identification list can be stored in the blockchain node.
Owner:PING AN TECH (SHENZHEN) CO LTD
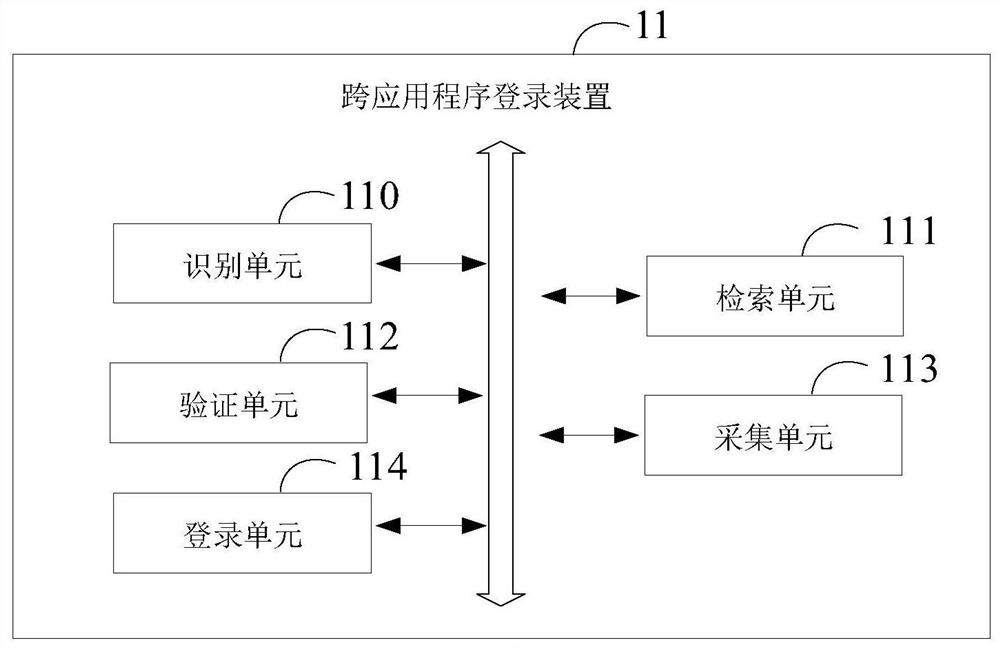
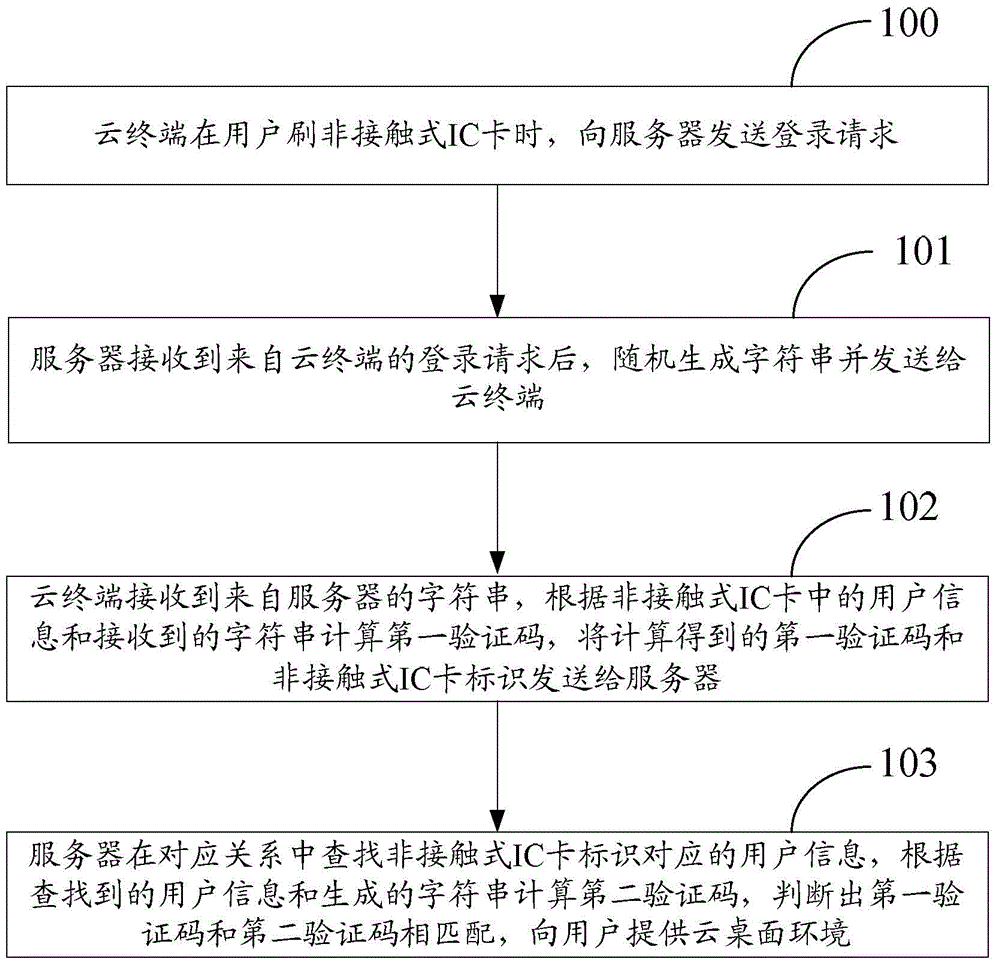
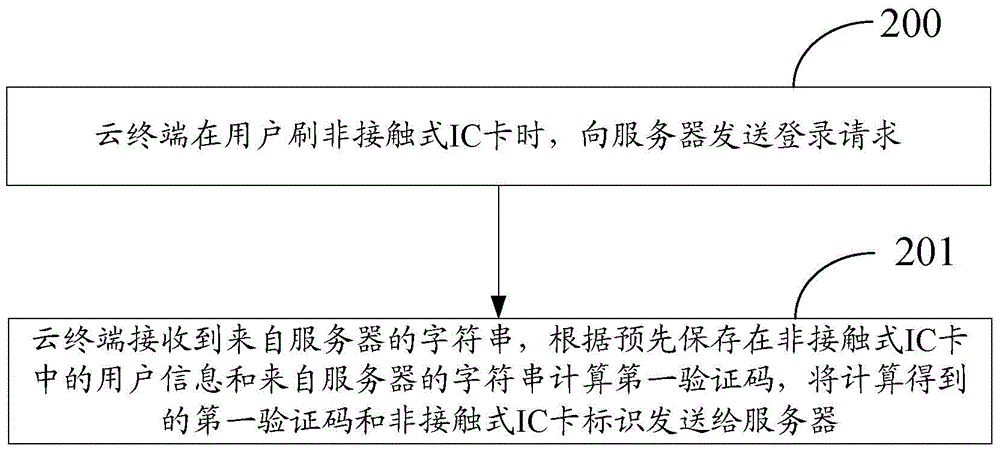
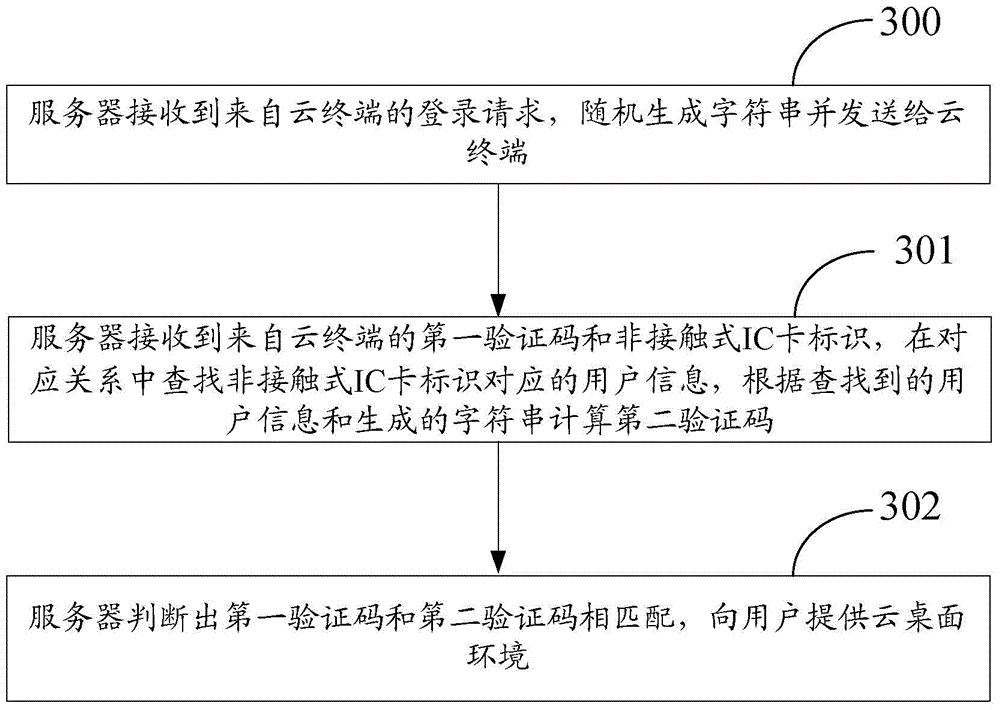
Method and device for logging in to cloud desktop
The invention discloses a method and a device for logging in to a cloud desktop. The method comprises steps: when a user swipes a contactless IC card, a cloud terminal sends a login request to a server; after the server receives the login request from the cloud terminal, a character string is generated randomly and sent to the cloud terminal; the cloud terminal receives the character string from the server, a first verification code is calculated according to the user information in the contactless IC card and the received character string, and the calculated first verification code and the contactless IC card identifier are sent to the server; and the server looks for the user information corresponding to the contactless IC card identifier in a corresponding relation, a second verification code is calculated according to the found user information and the generated character string, whether the first verification code and the second verification code are matched is judged, and a cloud desktop environment is provided for the user. According to the scheme of the invention, as long as the user swipes the contactless IC card, login of the cloud desktop can be realized, the user does not need to input a username and a password, login of the cloud desktop can be simply and quickly realized, and the user experience is thus improved.
Owner:ZTE CORP
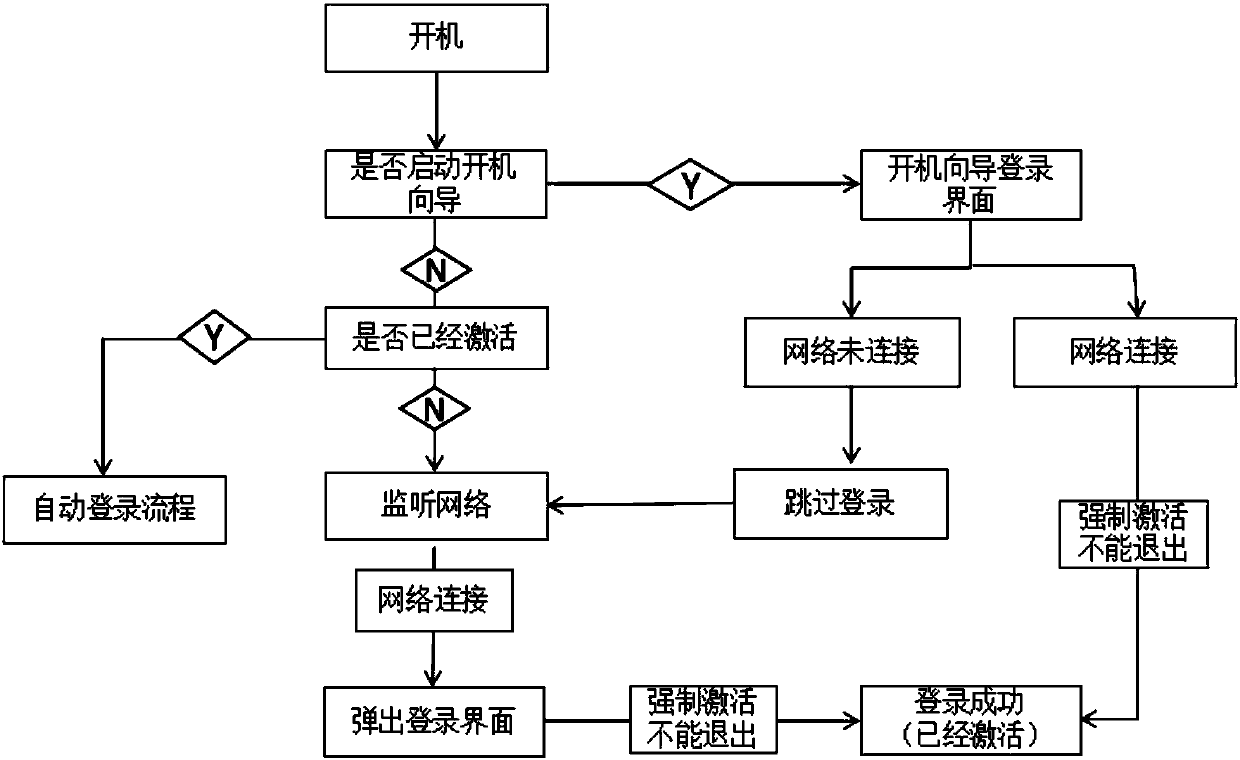
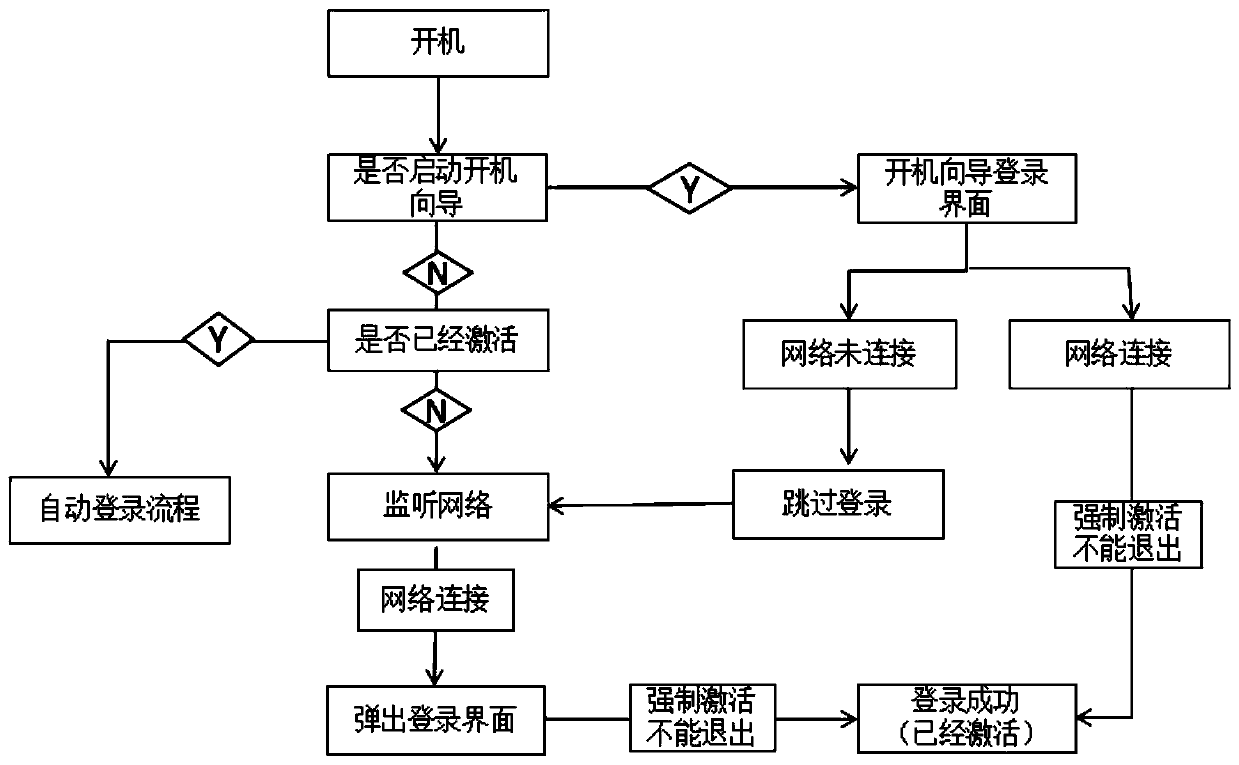
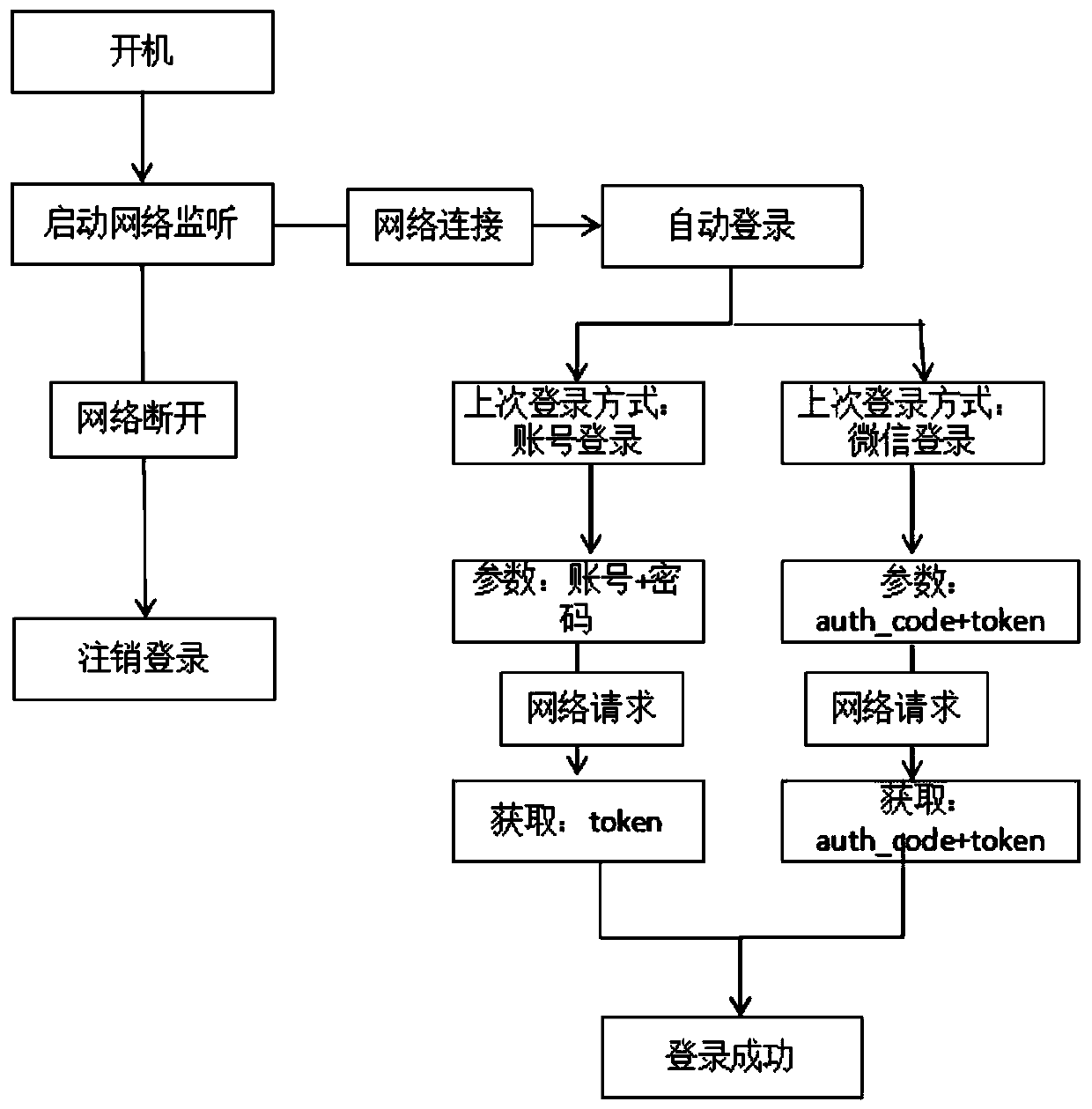
Method for activating intelligent television accounts in forced manner
ActiveCN107872728AEasy to useGuaranteed loginSelective content distributionNetwork connectionBiological activation
The invention relates to the field of intelligent televisions, and discloses a method for activating intelligent television accounts in a forced manner. The method includes steps of a, entering startup guide when televisions are started up if the televisions are started up for the first time, entering a step b, or entering a step c if the televisions are not started up for the first time; b, displaying television account login interfaces in the startup guide and entering the step c; c, judging whether the television accounts are already activated or not, entering account automatic login processes if the television accounts are already activated, or entering a step e if the television accounts are not activated; d, judging whether current networks are connected or not, forcing users to activate the accounts if the current networks are connected, skipping the login interfaces if the current networks are not connected and entering the step e; e, monitoring the television networks, poppingout the television account login interfaces if network connection is monitored, and forcing the users to activate the accounts. The method has the advantages that account registration of the television users can be increased by the aid of forced activation mechanisms, and the activeness of the user accounts can be guaranteed.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
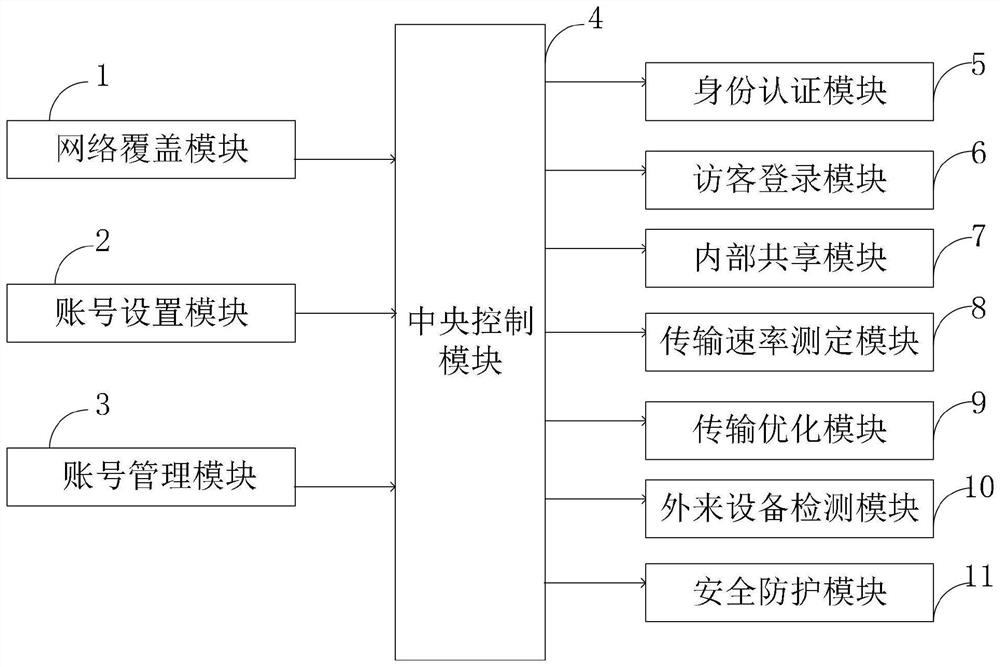
Wireless communication system and method based on Femto architecture
PendingCN111970700AMeet network needsLogin implementationTransmissionSecurity arrangementFemto-Engineering
The invention belongs to the technical field of wireless communication. The invention discloses a wireless communication system and method based on a Femto architecture. The wireless communication system based on the Femto architecture comprises a network coverage module, an account setting module, an account management module, a central control module, an identity authentication module, a visitorlogin module, an internal sharing module, a transmission rate measurement module, a transmission optimization module, an external device detection module and a safety protection module. According tothe system, the private account and the public account are set through the account setting module, and the accounts are selected as required, so that the network use requirements of families and visitors can be met; the identity authentication module and the visitor login module are arranged, so that identity authentication of family members and visitors can be realized, account login is realized,and information sharing is safer; the wireless communication system provided by the invention is realized on the basis of Femto, has multiple functions, is simple in communication method and good insafety, and can effectively protect user information.
Owner:YANCHENG INST OF TECH
Electronic device voice login method, system and television
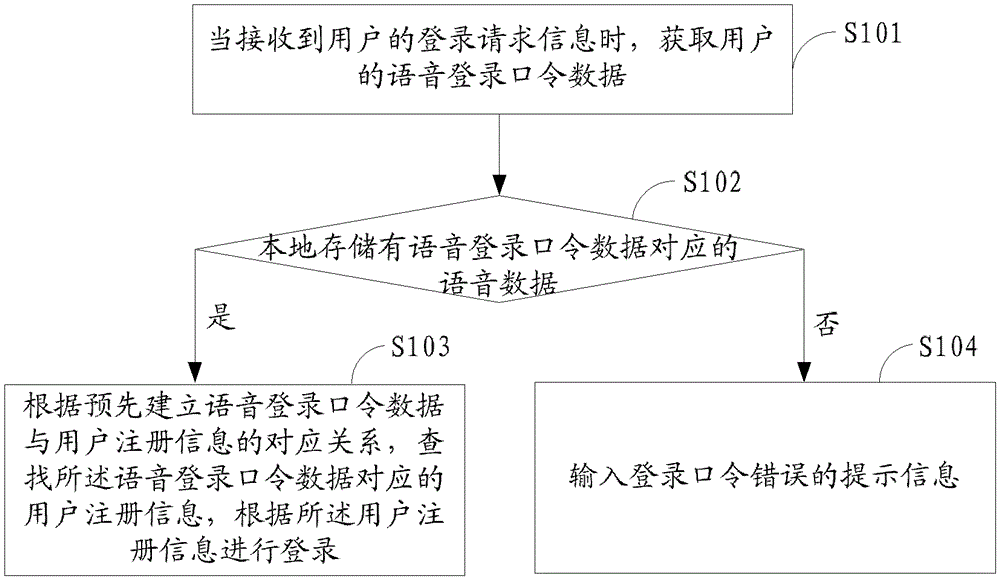
ActiveCN102710602BImprove experienceLogin implementationSpeech recognitionTransmissionComputer hardwareSpeech sound
The invention is applicable to the technical field of televisions, and provides a voice login method and a voice login system for electronic equipment, and a television. The method comprises the following steps of: receiving login request information of a user so as to acquire voice login command data of the user; judging whether voice data corresponding to the voice login command data is locally stored; if the voice data corresponding to the voice login command data is locally stored, looking up user register information corresponding to the voice login command data according to a preestablished corresponding relation between the voice login command data and the user register information; and if the voice data corresponding to the voice login command data is not locally stored, inputting prompt information of a login command error. According to the method and the system, an electronic equipment user can directly input the voice login command data through voice, so that the user can log in the electronic equipment; the login process is simple and convenient; the user does not need to execute complicated operation; and the user experience is improved.
Owner:SHENZHEN SKYWORTH RGB ELECTRONICS CO LTD
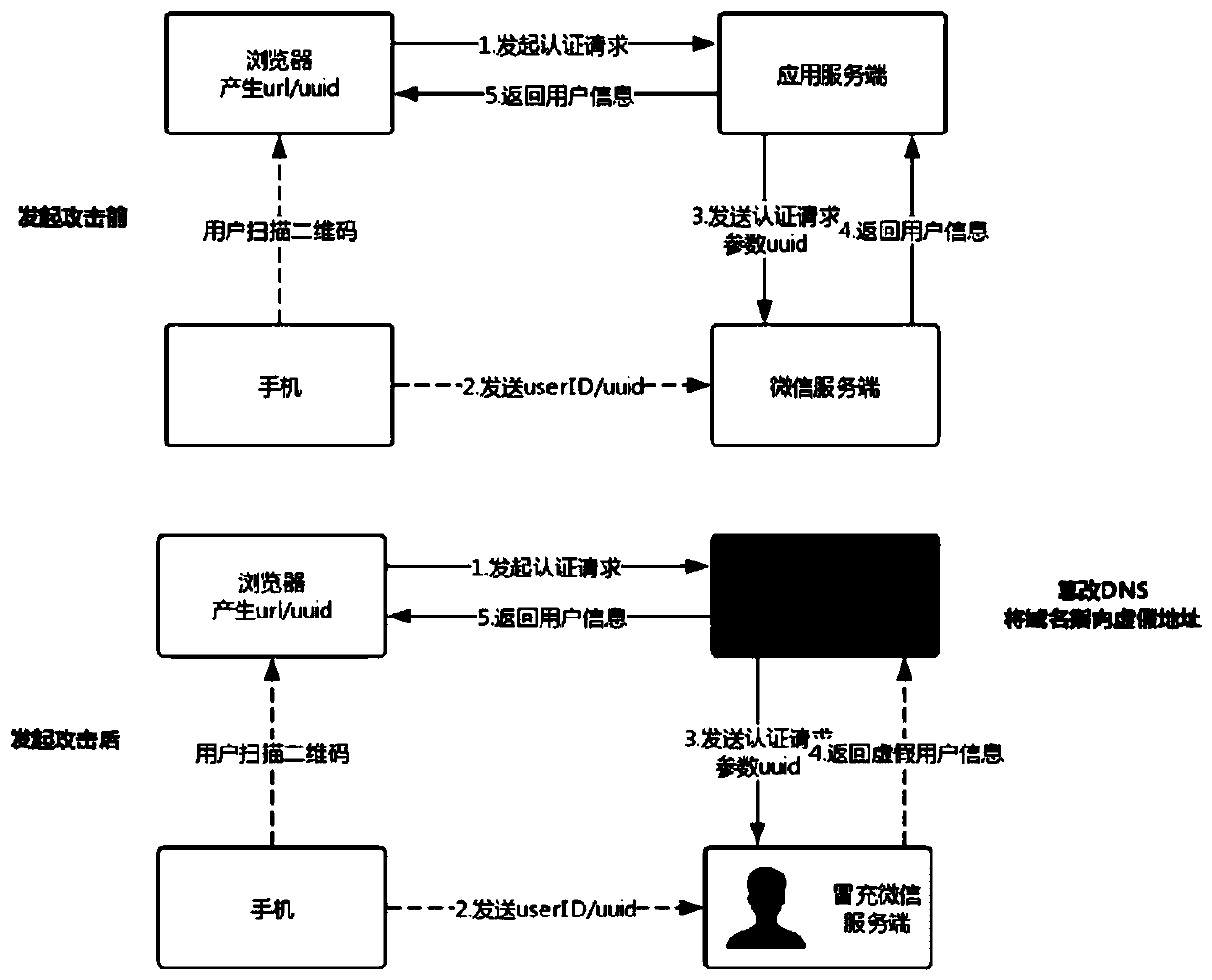
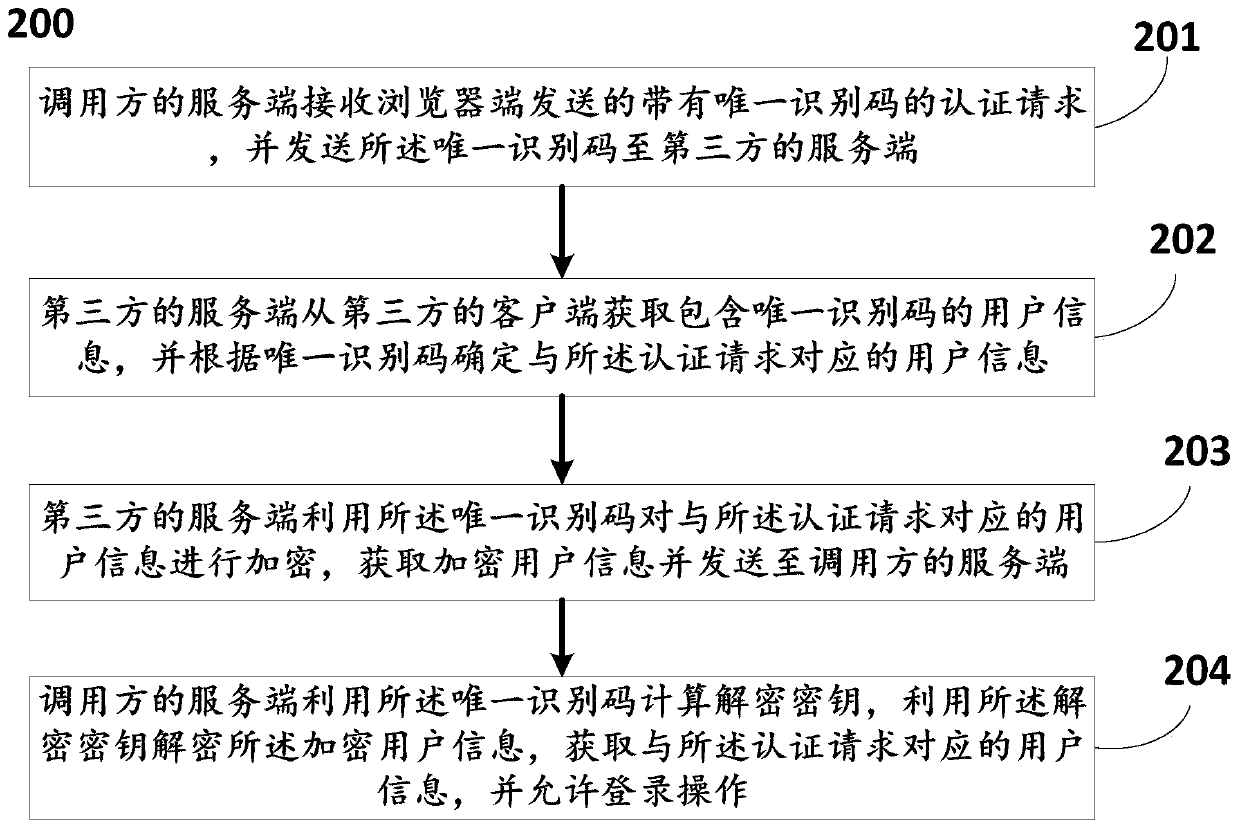
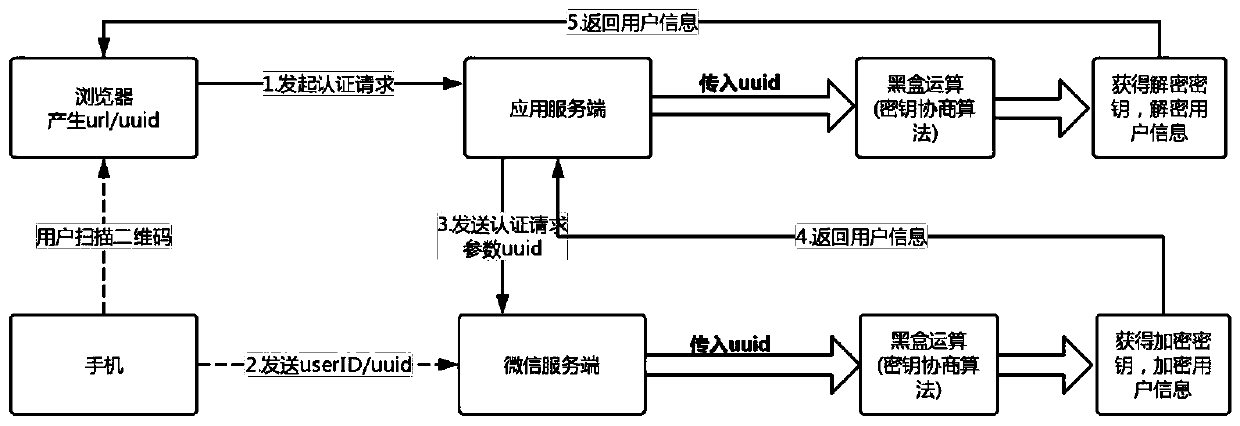
Secure login method and system based on third-party authorization
The invention discloses a secure login method and system based on third-party authorization, and the method comprises: a server side of a calling party receiving an authentication request which is transmitted by a browser side and is provided with a unique identification code, and transmitting the unique identification code to a server side of a third party; the server of the third party acquiringuser information containing the unique identification code from the client of the third party, and determining the user information corresponding to the authentication request according to the uniqueidentification code; the server of the third party encrypting user information corresponding to the authentication request by using the unique identification code, acquiring encrypted user information and sending the encrypted user information to the server of the calling party; and the server of the calling party using the unique identification code to calculate a decryption key, using the decryption key to decrypt the encrypted user information, obtaining the user information corresponding to the authentication request, and allowing login operation. According to the invention, the user information is encrypted and decrypted in a symmetrical encryption mode, so that the security is greatly improved, and the authenticity and reliability of the user identity information are ensured.
Owner:AEROSPACE INFORMATION
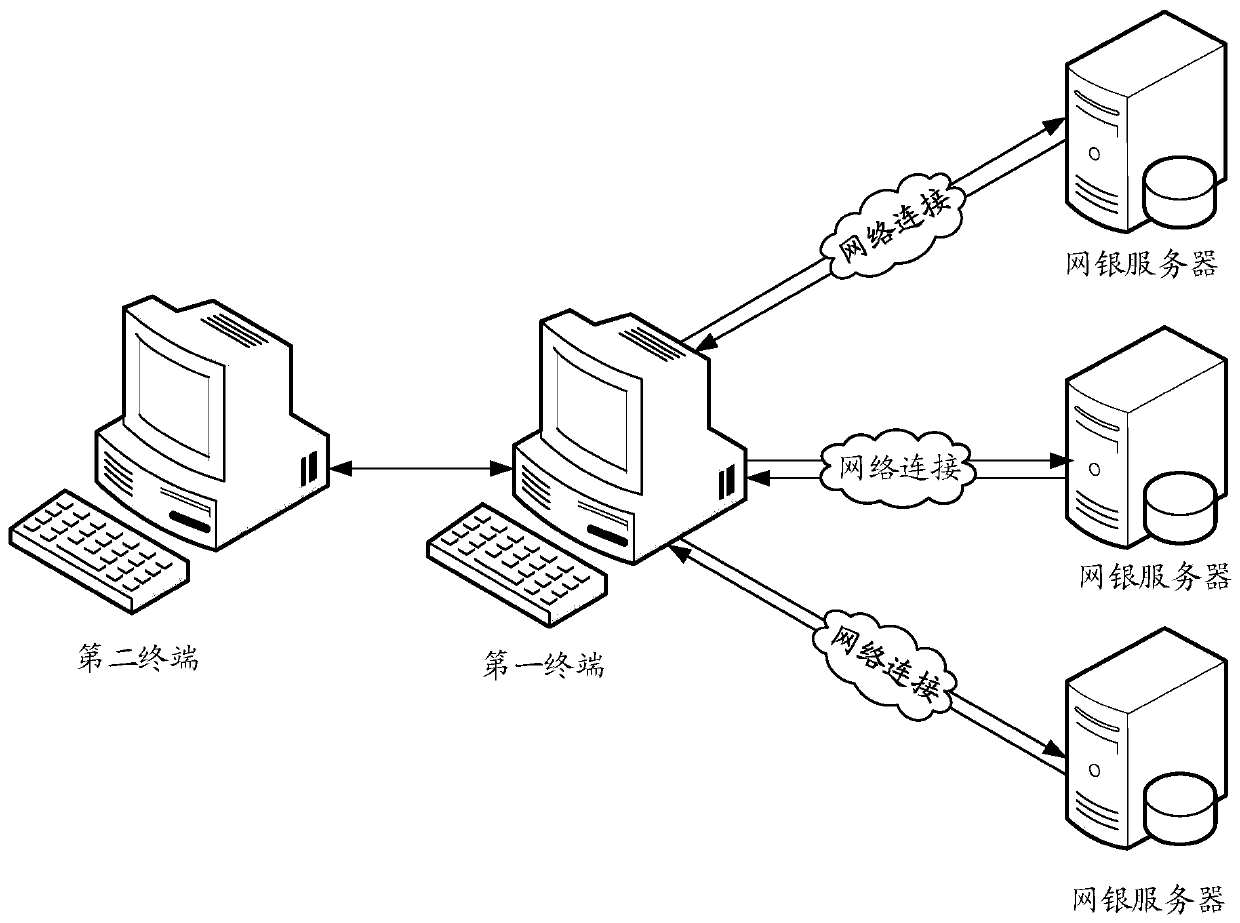
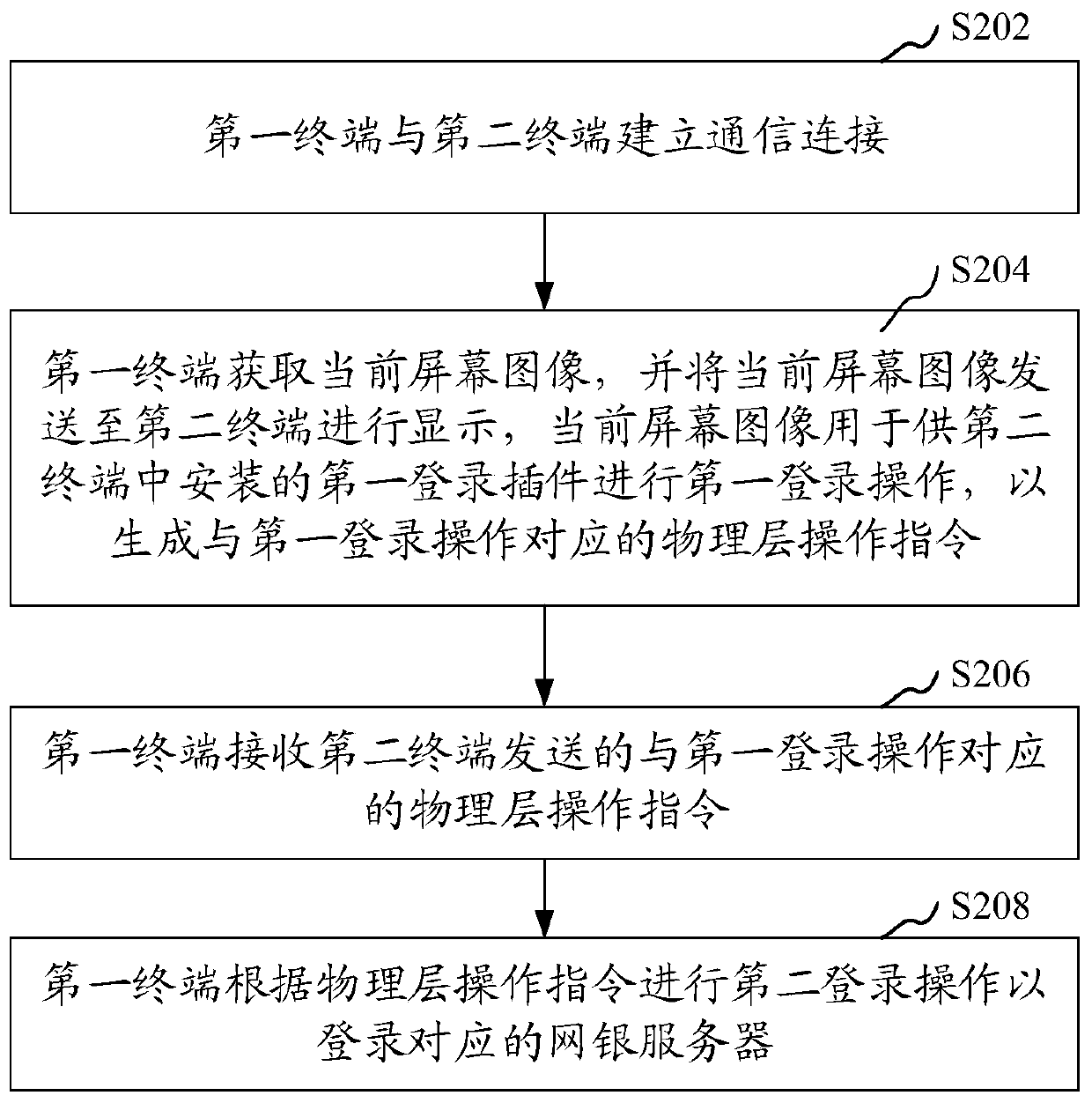
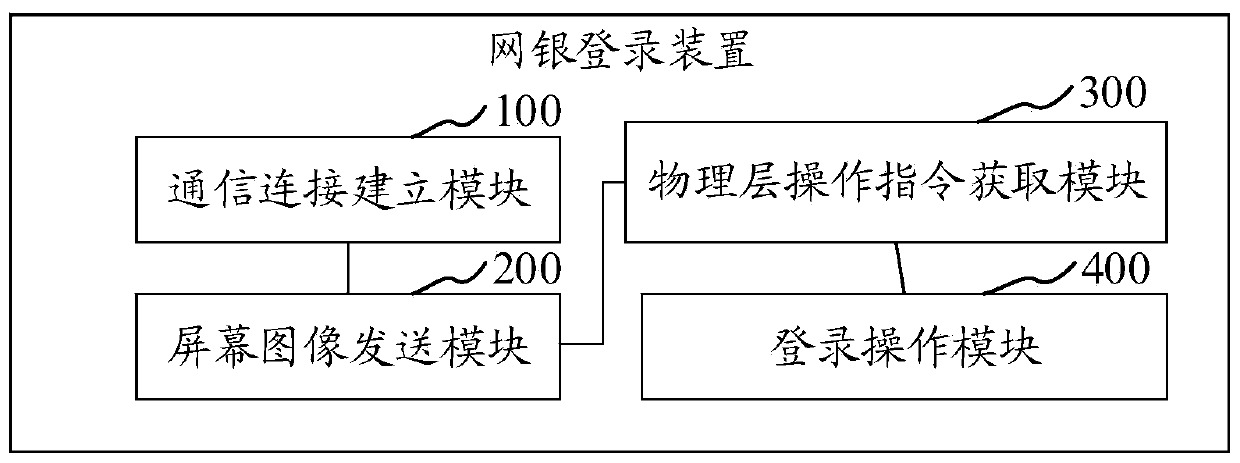
Online banking login method, device, computer equipment and storage medium
ActiveCN108171027BLogin implementationDigital data authenticationPayment circuitsSoftware engineeringPhysical layer
The invention relates to an E-bank login method, device, computer equipment and a storage medium. The method comprises the steps that a first terminal and a second terminal build communication connection; the first terminal obtains a current screen image, the current screen image is sent to the second terminal for display, the current screen image is used for a first login plug-in installed in thesecond terminal for performing a first login operation to generate a physical layer operation instruction corresponding to the first login operation; the first terminal receives the physical layer operation instruction corresponding to the first login operation sent by the second terminal; and the first terminal perform a second login operation according to the physical layer operation instruction to log in a corresponding E-bank server. According to the method, the operation instruction sent by the second terminal to the first terminal is the physical layer operation instruction, thus the physical layer operation instruction can not be recognized as a non-human operation, thereby achieving E-bank login and laying a foundation for the subsequent E-bank download.
Owner:深圳平安综合金融服务有限公司
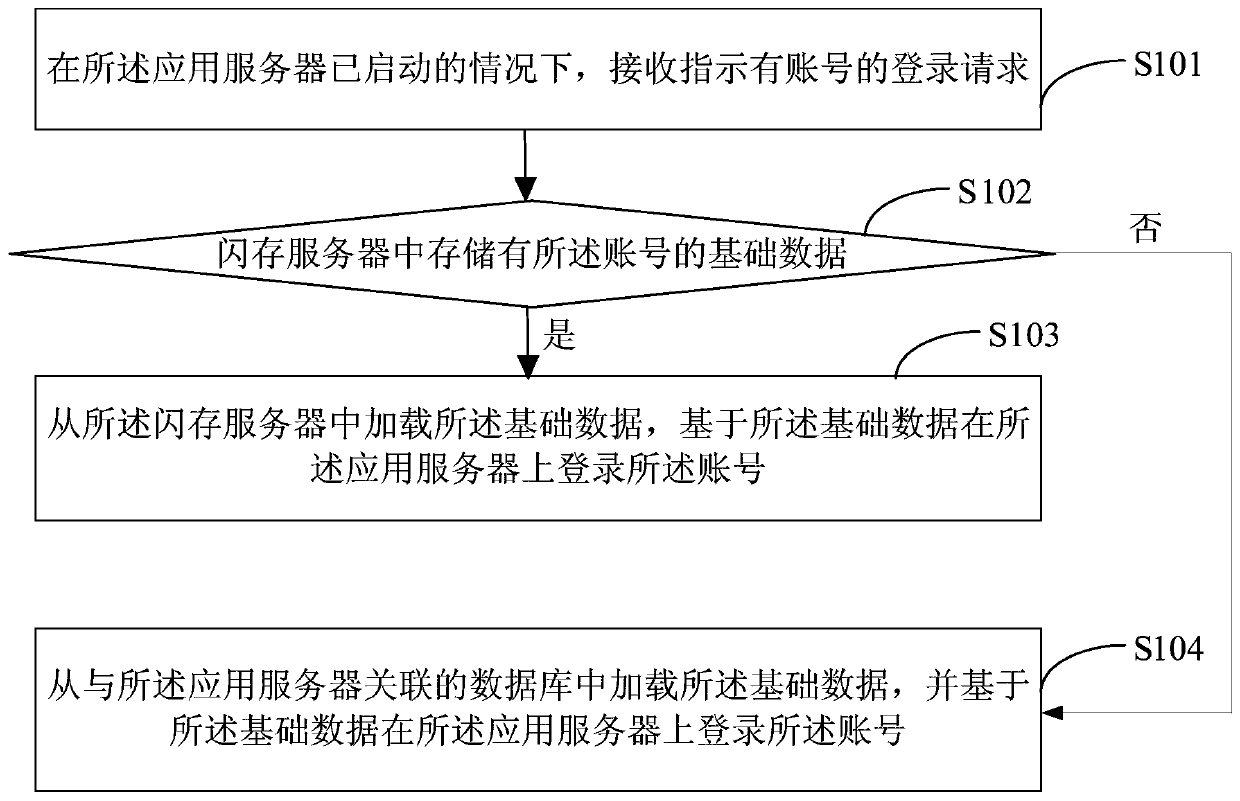
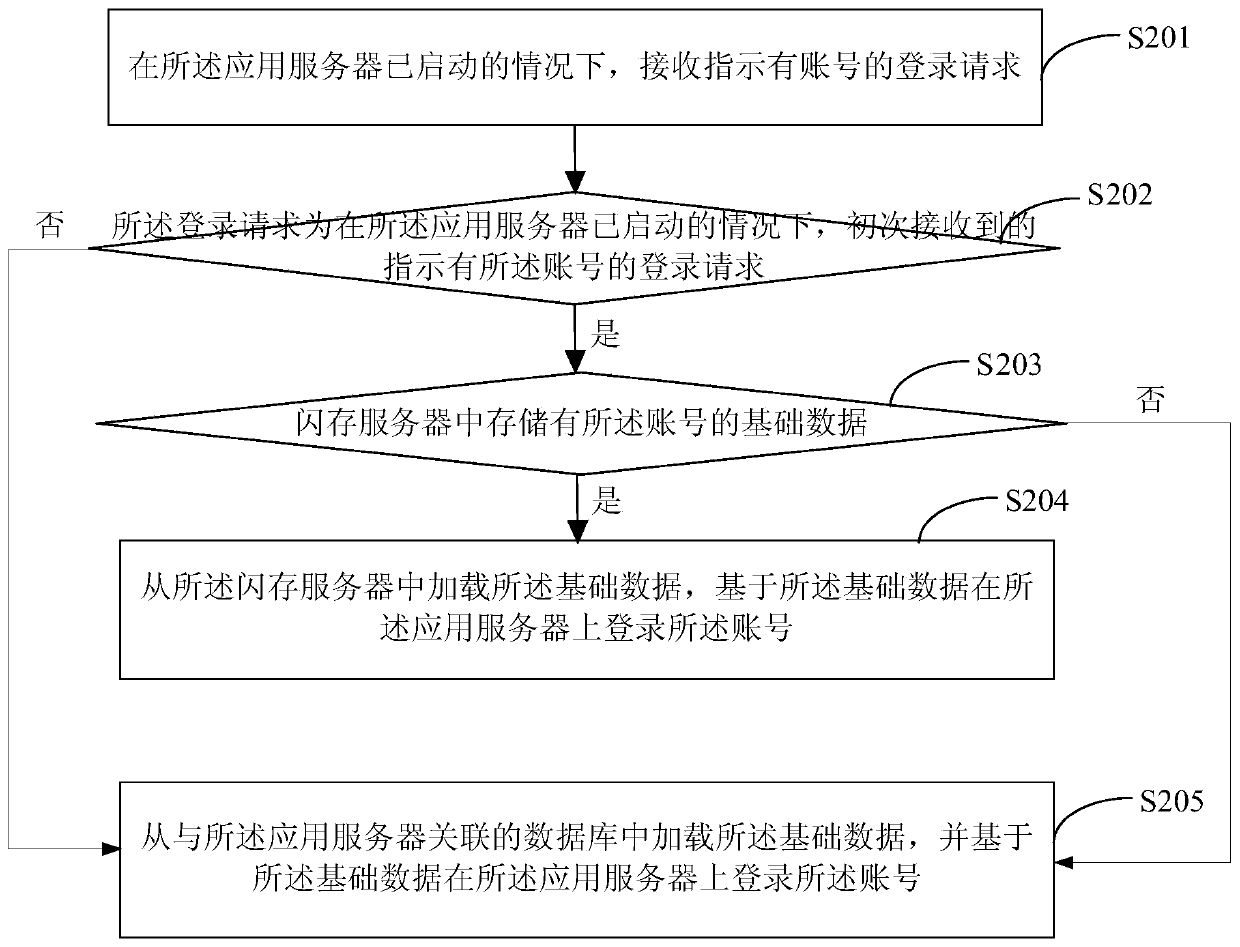
A login method, device and system
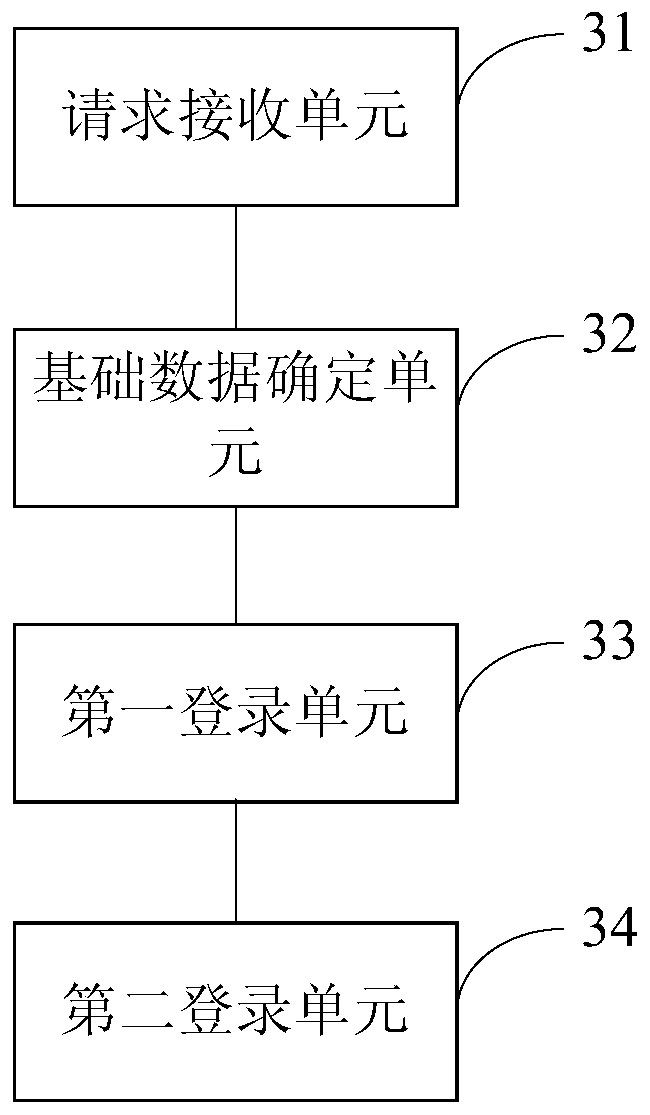
ActiveCN107172086BLogin implementationReduce update maintenance timeTransmissionApplication serverEngineering
The embodiment of the present application provides a login method, by receiving a login request indicating that there is an account when the application server is started; determining whether the basic data of the account is stored in the flash memory server; if so, loading the basic data from the flash memory server, Log in the account on the application server based on the basic data; if not, load the basic data from the database associated with the application server, and log in the account on the application server based on the basic data (the basic data is the last time the account logged out of the application server, the application server The data uniquely corresponding to the account stored in the database) method, so that the latest account basic data can be loaded from the flash server / database to realize account login, thereby avoiding only the basic data of the online account when the application server is updated and maintained. The situation stored in the database achieves the purpose of logging in to the application server on the basis of reducing the update and maintenance time of the application server.
Owner:BEIJING AMAZGAME AGE INTERNET TECH CO LTD
Method and system for realizing account synchronization between multiple platforms, and electronic device
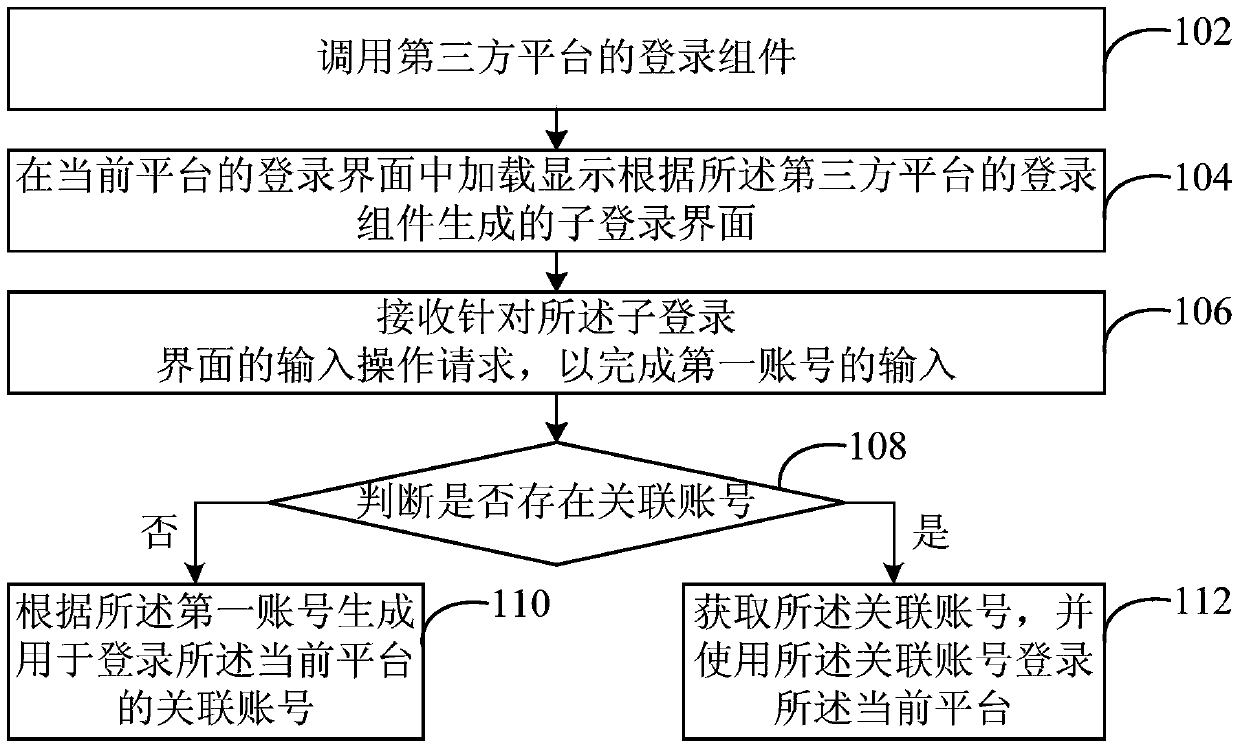
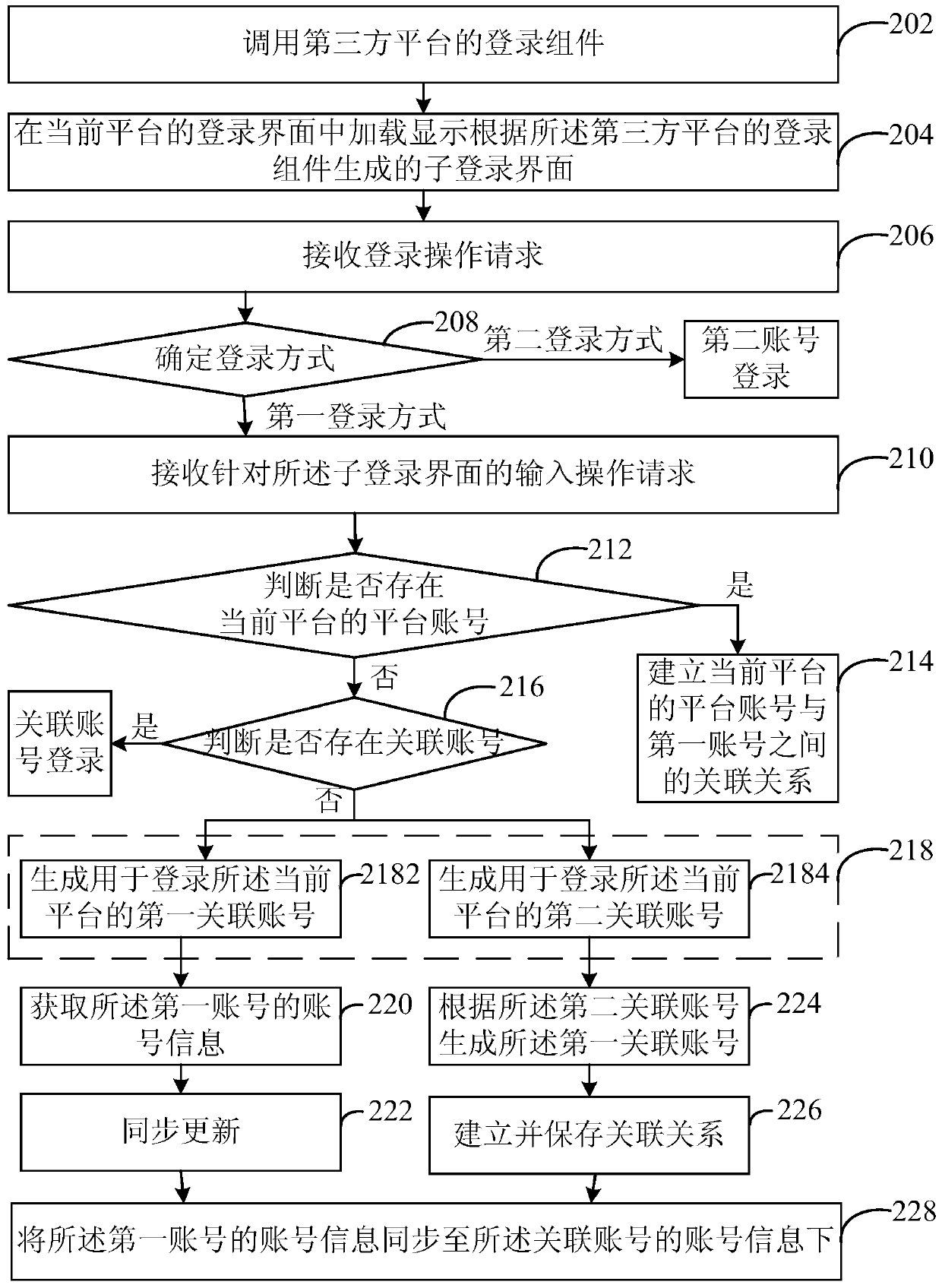
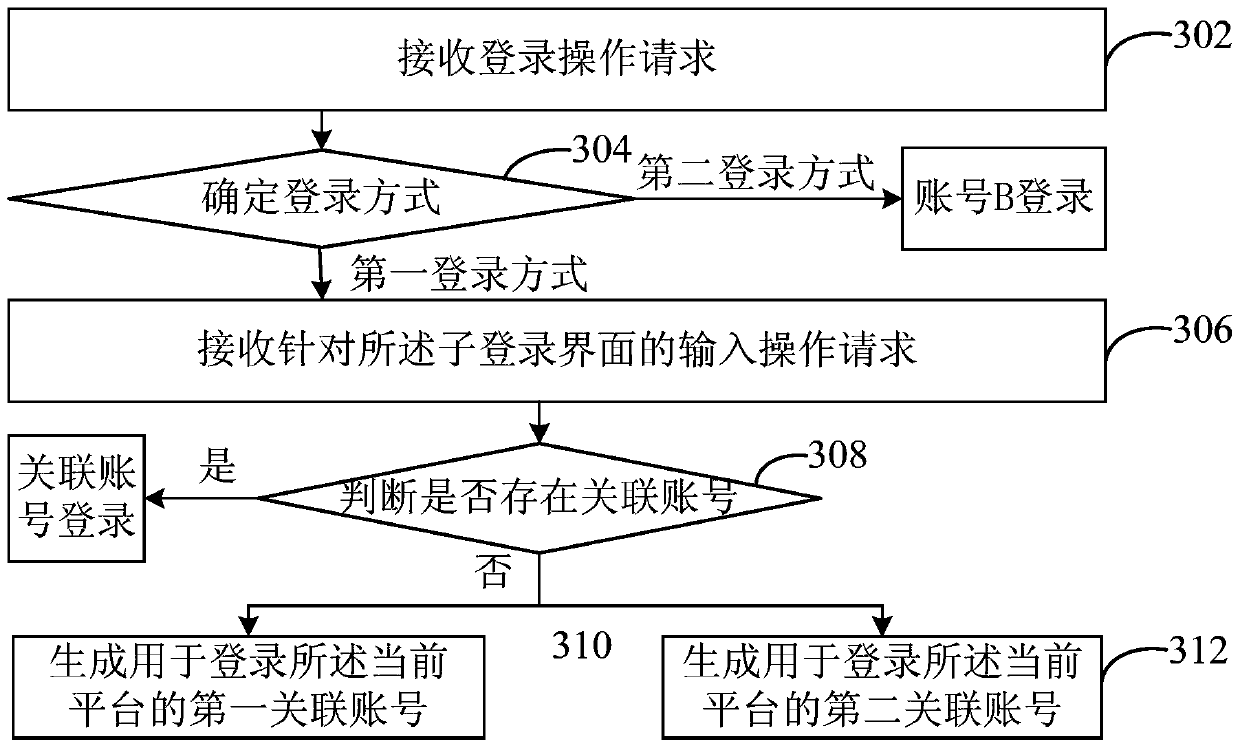
ActiveCN104580451BRealize shared synchronizationEasy to manageTransmissionThird partyMultiple platform
The invention discloses a method and system for achieving account number synchronization among multiple platforms, and an electronic device. The method comprises the steps of calling a login assembly of a third-party platform; loading and displaying a child login interface generated according to the login assembly of the third-party platform in a login interface of a current platform; receiving an input operation request aiming at the child login interface to finish input of a first account number, wherein the first account number is the platform account number of the third-party platform; judging whether a related account number related to the first account number exists in the current platform or not; if not, generating a related account number used for logging in the current platform according to the first account number so as to log in the current platform through the related account number. The method and system for achieving account number synchronization among the multiple platforms, and the electronic device solve the problem that account numbers are not synchronous.
Owner:BEIJING QIHOO TECH CO LTD
The method of realizing the forced activation of the smart TV account
ActiveCN107872728BIncrease the number of registrationsReduce stepsSelective content distributionNetwork connectionStart up
The invention relates to the field of intelligent televisions, and discloses a method for activating intelligent television accounts in a forced manner. The method includes steps of a, entering startup guide when televisions are started up if the televisions are started up for the first time, entering a step b, or entering a step c if the televisions are not started up for the first time; b, displaying television account login interfaces in the startup guide and entering the step c; c, judging whether the television accounts are already activated or not, entering account automatic login processes if the television accounts are already activated, or entering a step e if the television accounts are not activated; d, judging whether current networks are connected or not, forcing users to activate the accounts if the current networks are connected, skipping the login interfaces if the current networks are not connected and entering the step e; e, monitoring the television networks, poppingout the television account login interfaces if network connection is monitored, and forcing the users to activate the accounts. The method has the advantages that account registration of the television users can be increased by the aid of forced activation mechanisms, and the activeness of the user accounts can be guaranteed.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
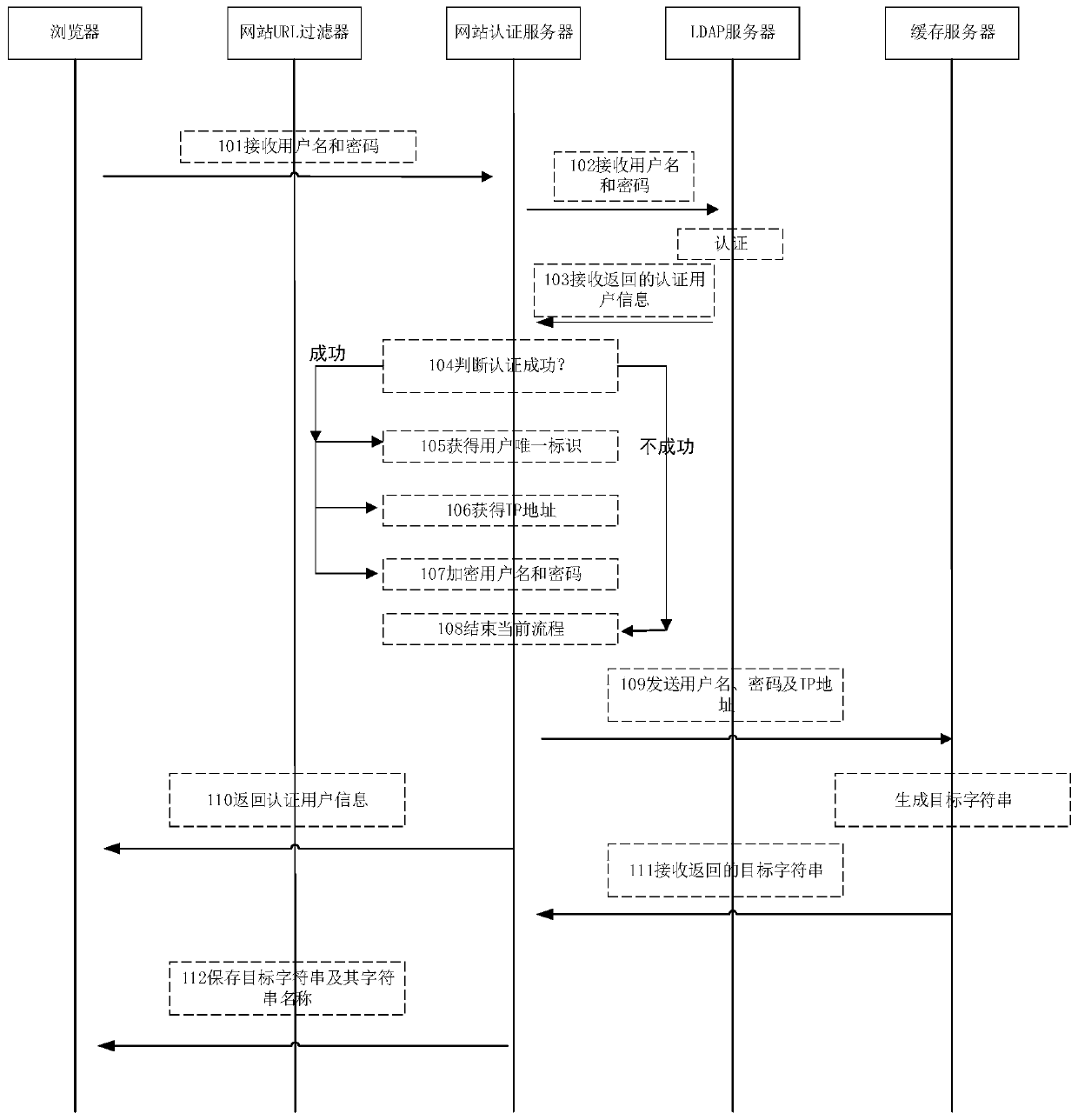
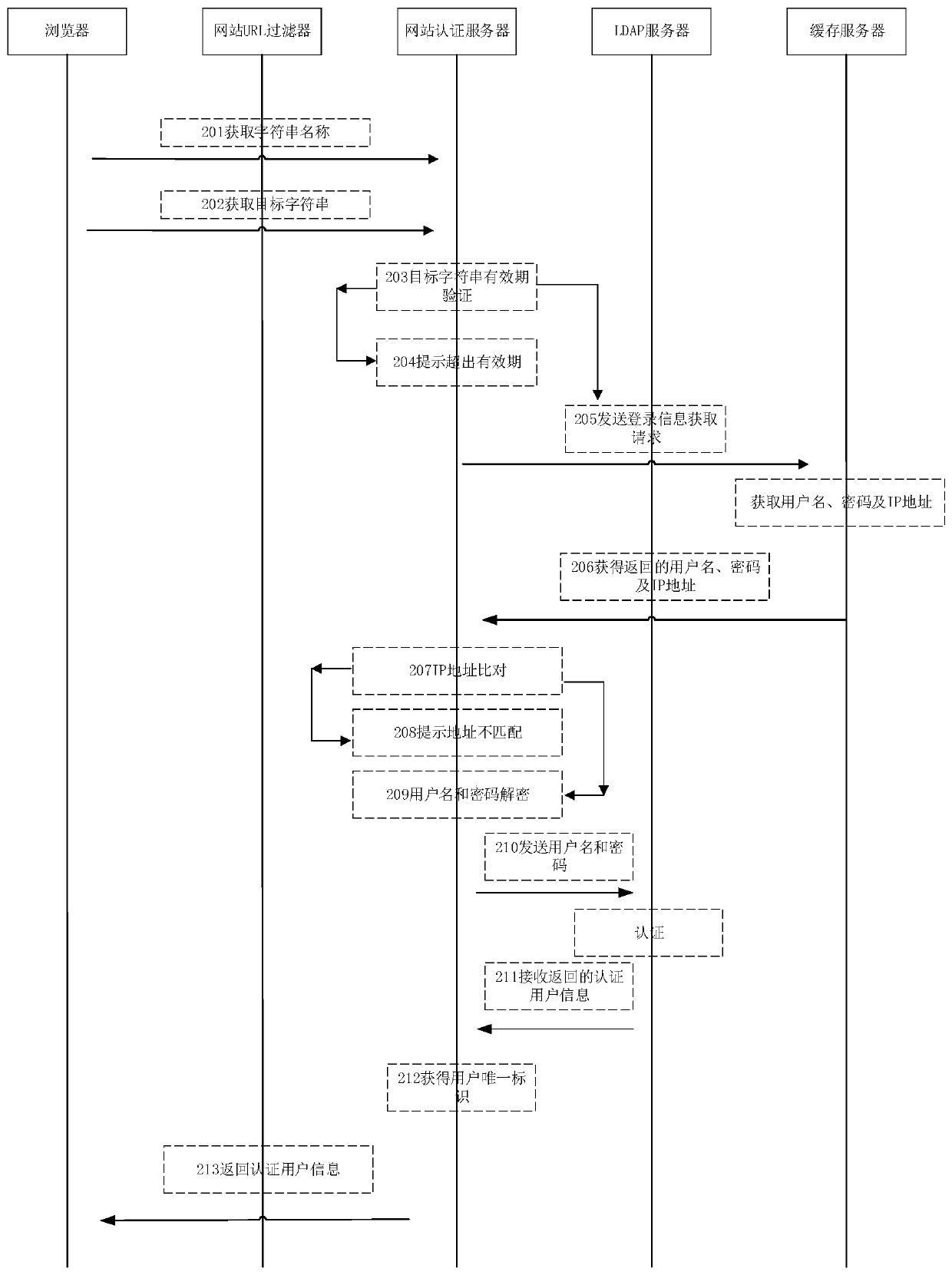
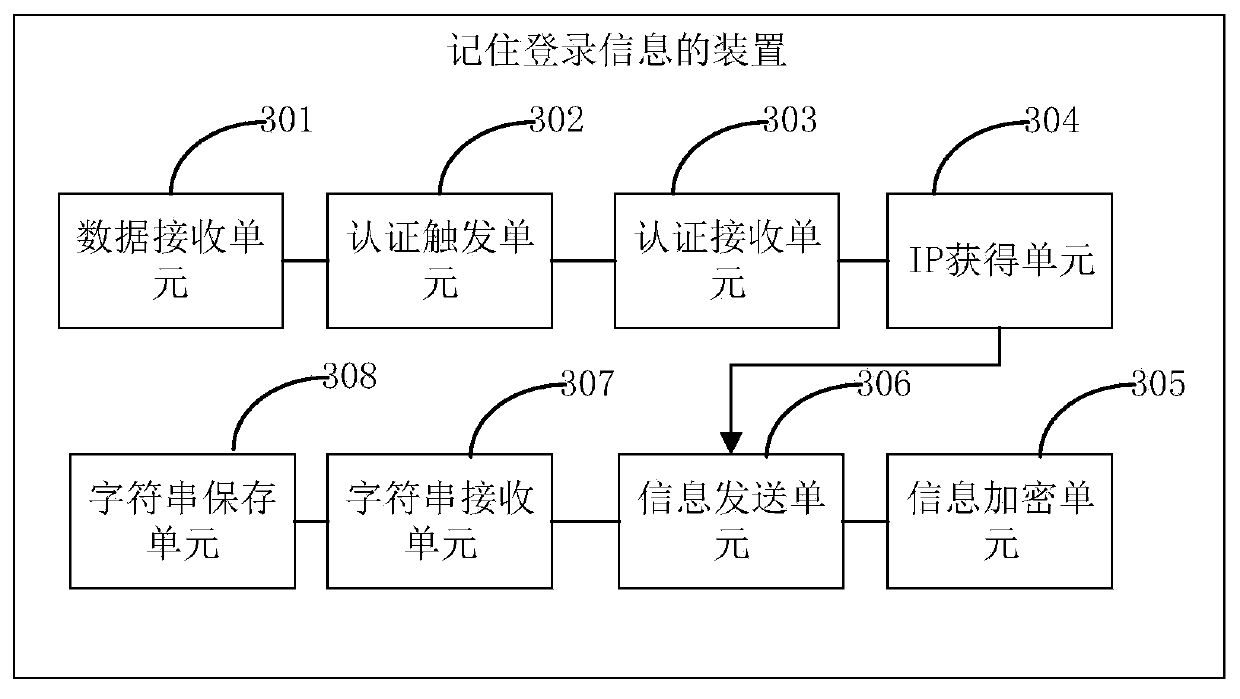
Method and device for remembering login information, login control method and device
This application discloses a method and device for remembering login information. The method includes: receiving the user name and password; sending the user name and password to the LDAP server to generate authentication user information; receiving the authentication user information returned by the LDAP server; When successful, send the user name and password to the cache server, and the cache server generates the target string; receives the target string returned by the cache server; saves the target string and its string name in the browser cache. This application sends the user name and password to a cache server that is different from the browser cache, and after the corresponding target string is generated in the cache server, it only needs to save the target string corresponding to the user name and password in the browser cache. The login information can be recorded, avoiding the situation where the login information is exposed in plain text by directly storing the user name and password in the browser cache, and ensuring the security of the account.
Owner:NEUSOFT CORP
Game weak network test analysis platform
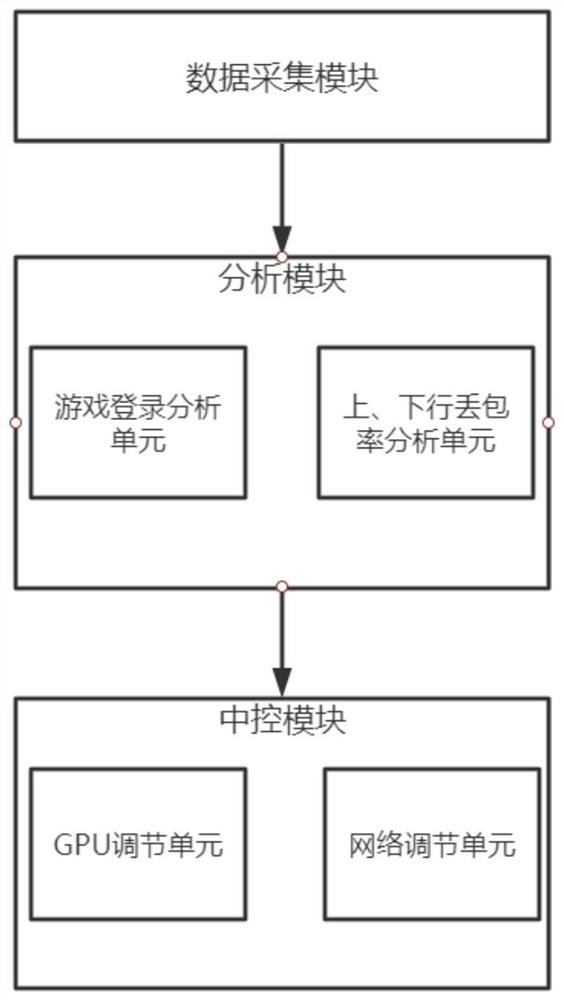
PendingCN114146417ASave hassle and timeFaster login timesProcessor architectures/configurationVideo gamesImage resolutionData processing
The invention relates to the technical field of network testing, in particular to a game weak network testing and analyzing platform, which comprises a data acquisition module, a data processing module and an analysis module, the analysis module is connected with the data acquisition module and is used for analyzing the entity information acquired by the data acquisition module and acquiring current game login state parameters; the central control module is connected with the data acquisition module and is used for adjusting the analysis result of the analysis module; according to the method, the GPU ratio of each login process is judged based on several specific continuous processes of game login so as to accurately determine the login obstacle of a certain determined link of game login, firstly, the animation frame rate and the animation resolution are reduced, on one hand, login in a low-obstacle environment can be rapidly realized by adopting the mode, and on the other hand, the login obstacle of a certain determined link of game login can be accurately determined by adopting the animation frame rate and the animation resolution. By dividing each determination link, preparation can be made for subsequent detection and judgment of uplink and downlink packet loss rates.
Owner:GUANGZHOU YINHAN TECH CO LTD
Method and device for page support multi-user login in MVC framework
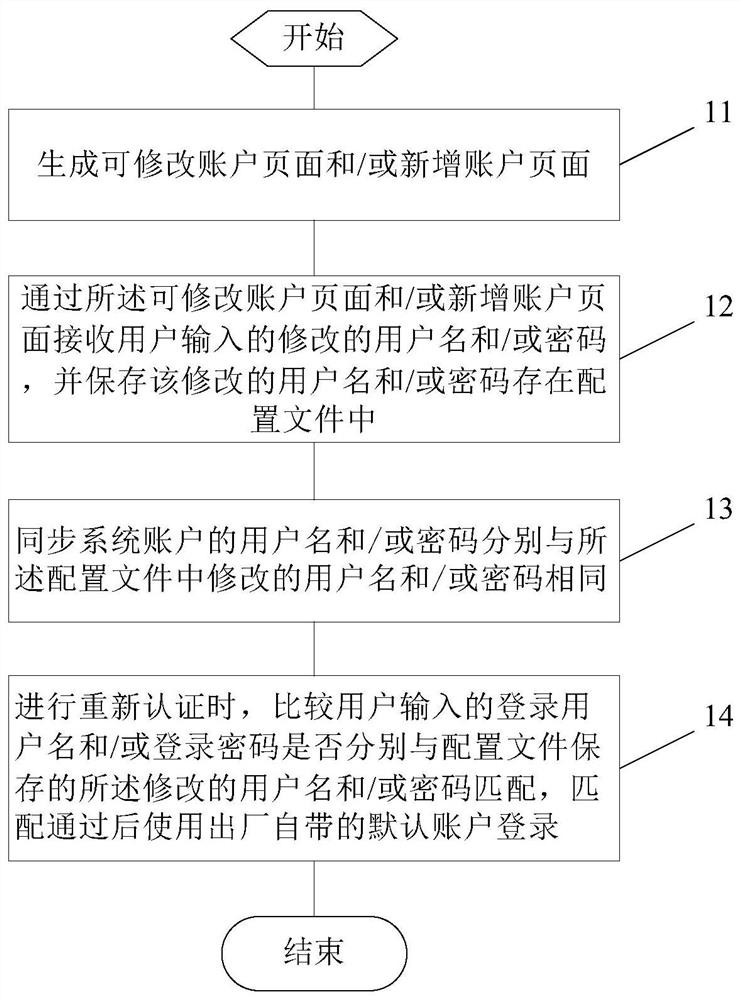
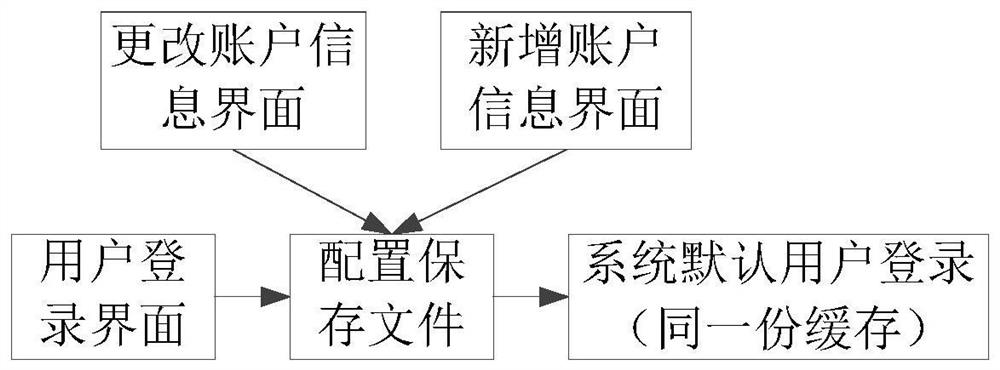
ActiveCN106487806BLogin implementationImproved first-time login access efficiencyTransmissionPasswordUser input
The embodiment of the invention provides a method and a device for supporting multi-user login in a webpage in an MVC framework. The method comprises steps of: generating a correctable account webpage and / or a new account webpage; receiving a modified user name and / or a password input by a user through the correctable account webpage and / or the new account webpage, and storing the modified user name and / or the password in a configuration file; synchronizing the user name and / or the password of a system account to be the same as the modified user name and / or the password in the configuration file; during re-authentication, comparing whether the user name and / or the password input by the user is matched with the modified user name and / or the password in the configuration file; and after the matching passes, using a factory default account to log in the webpage. According to the invention, multi-user login is achieved without increasing cache of a buffer; authority-based management for user grades is achieved; and the login and visit efficiency for the first time of a switched user is improved.
Owner:浙江安吉椅业科技有限公司
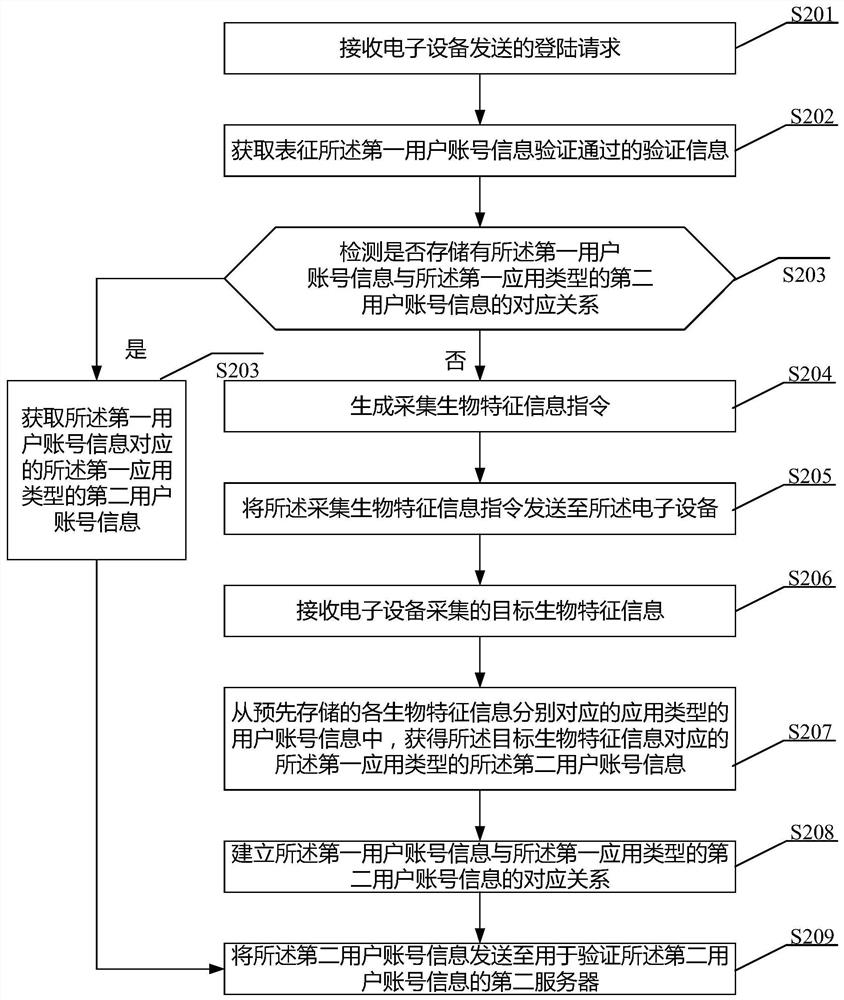
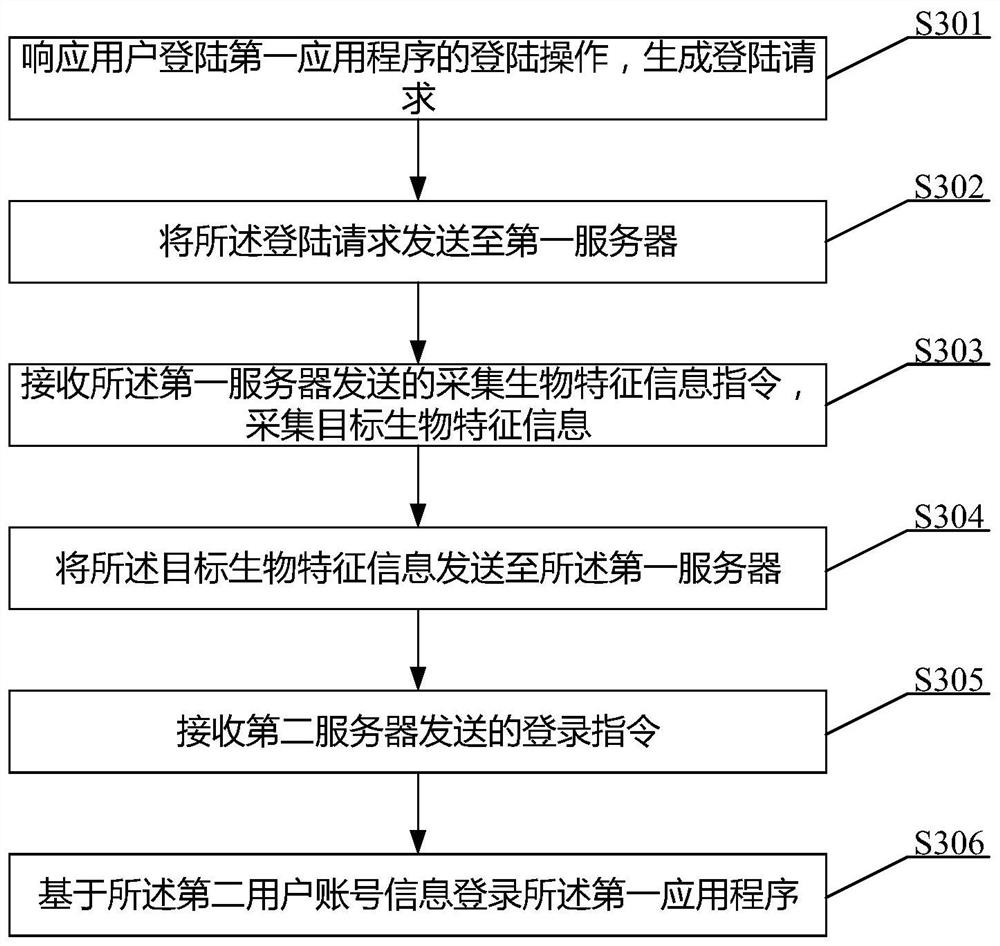
Single sign-on method, first server and electronic equipment
The invention provides a single sign-on method, a first server and electronic equipment. The method comprises the steps that: a sign-on request transmitted by the electronic equipment is received, wherein the sign-on request comprises a first application type and first user account information; a first server firstly detects whether second user account information of a first application type corresponding to the first user account information is stored or not; if the second user account information is not stored, the first server generates a biological characteristic information collection instruction and sends the same to the electronic equipment; the electronic equipment sends collected target biological characteristic information to the first server; the first server can obtain the second user account information of the first application type corresponding to the target biological characteristic information, so that the electronic equipment logs in a first application program basedon the second user account information. Therefore, the purpose of logging in the first application program by utilizing the first user account information can be achieved under the condition that thecorresponding relationship between the first user account information and the second user account information is not set in advance.
Owner:BANK OF CHINA
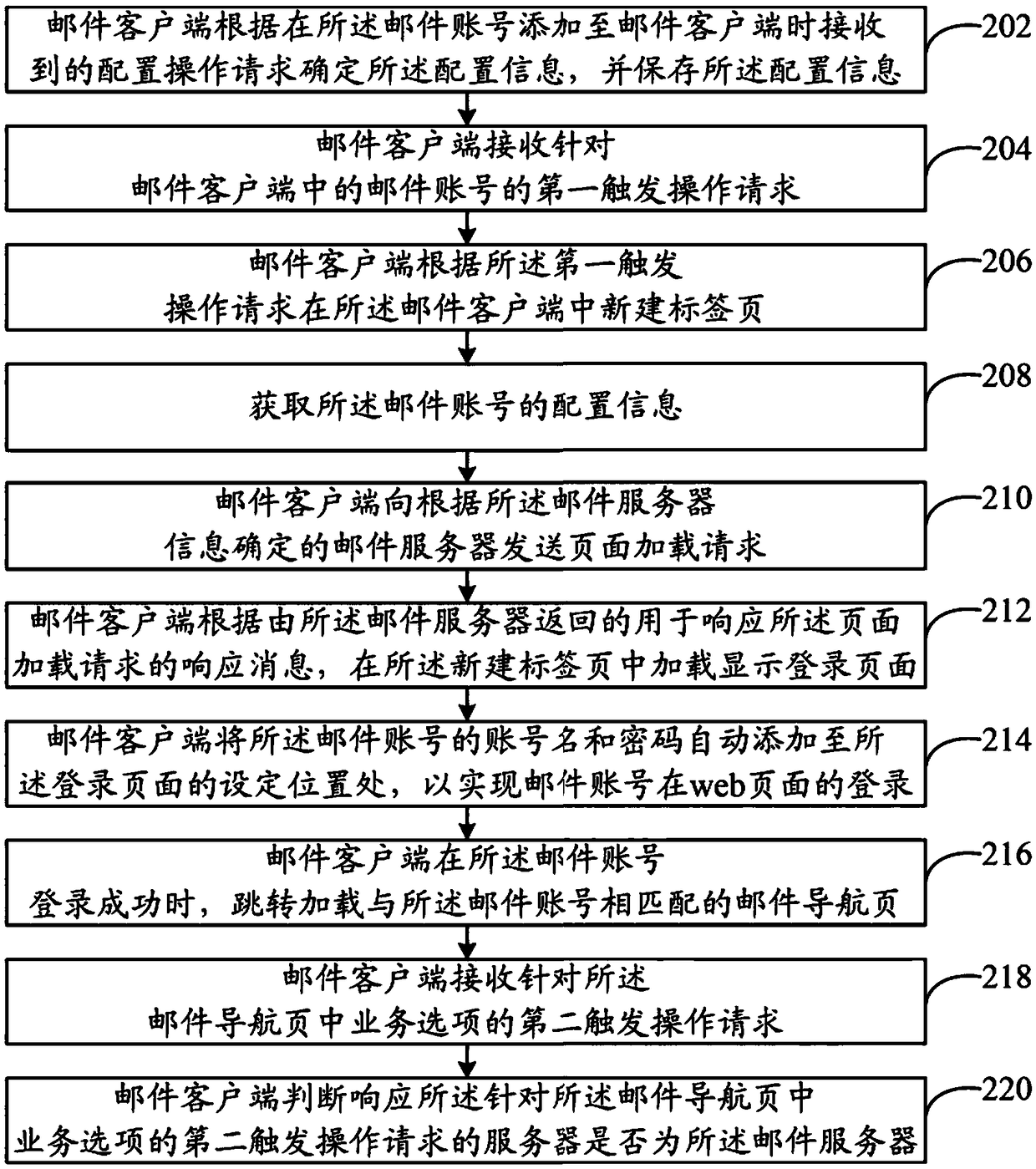
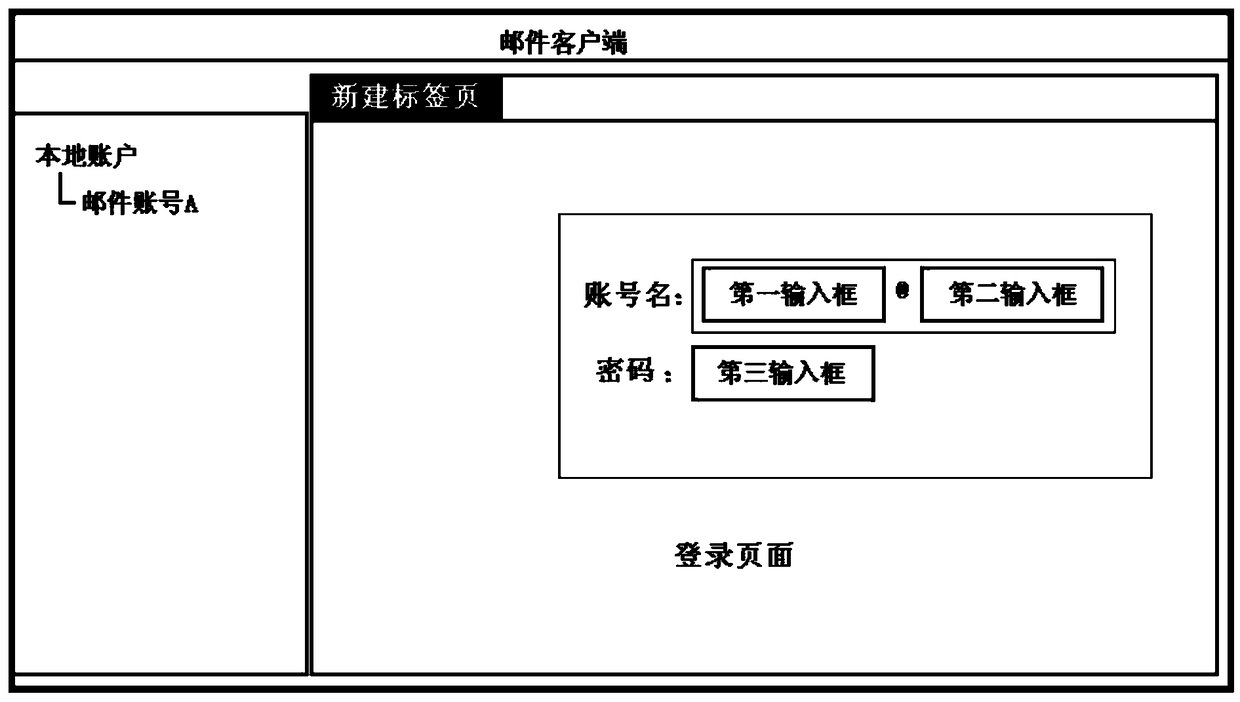
Mail account login method and mail client
ActiveCN104539613BLogin implementationImprove login efficiencyData switching networksMail surveyPassword
The invention discloses a mail account log-in method and a mail client side. The method comprises the steps that a first trigger operation request for a mail account in the mail client side is received; a label page is built in the mail client side according to the first trigger operation request; configuration information of the mail account is obtained, wherein the configuration information comprises mail server information and the account name and passwords of the mail account; a page loading request is sent to a mail server determined according to the mail server information; a log-in page is loaded and displayed in the newly-built label page according to response information, responding to the page loading request, returned by the mail server; the account name and the passwords of the mail account are automatically added to the set positions of the log-in page, so that login of the mail account on the web page is achieved. The mail account log-in method solves the problems that the mail client side is poor in interaction, and information is hard to share.
Owner:BEIJING QIHOO TECH CO LTD
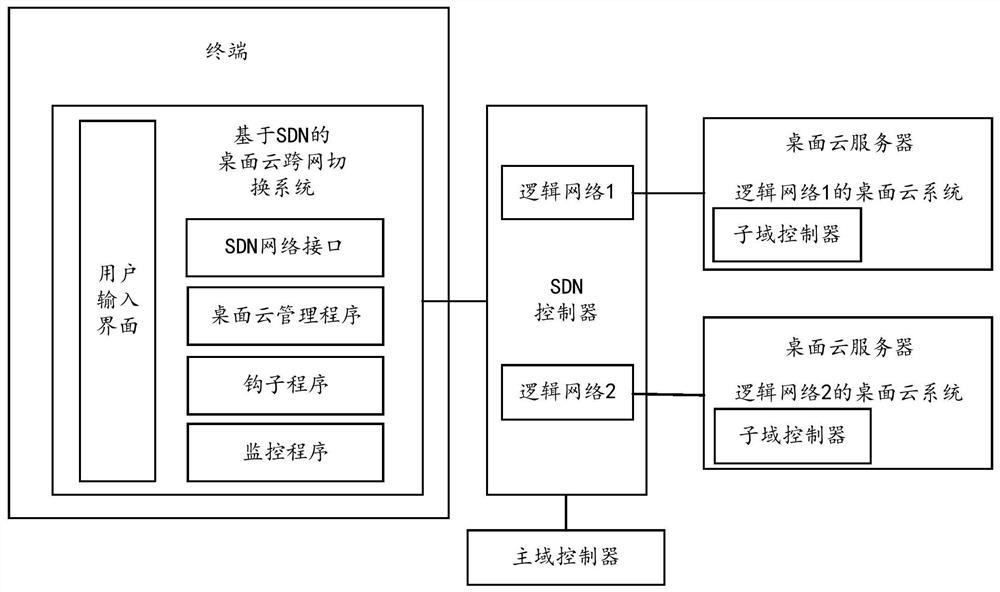
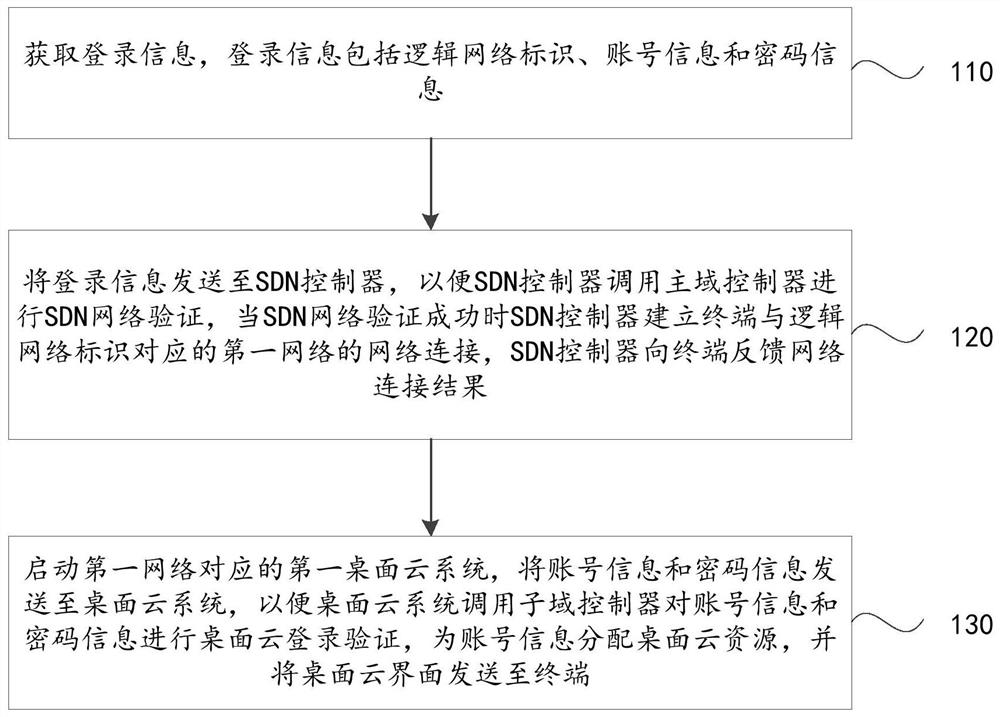
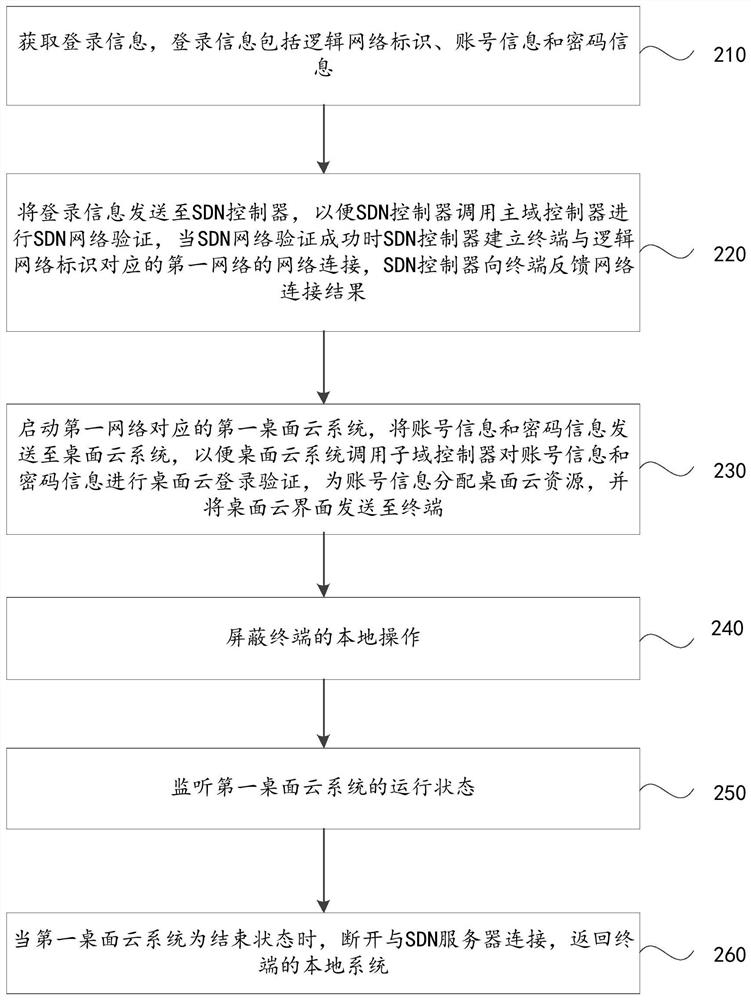
Desktop cloud login method, terminal, sdn controller and system based on software-defined network sdn
ActiveCN109302414BLogin implementationImprove resource utilizationTransmissionWeb authenticationCloud systems
The embodiment of the present application discloses a desktop cloud login method, terminal, SDN controller and system based on software-defined network SDN. When the authentication is successful, start the desktop cloud system, and the desktop cloud system will verify the login information of the desktop cloud login, and then can automatically perform SDN network authentication and desktop cloud login verification after obtaining the login information once, without the need for the user to enter the password multiple times, and then perform network switching When logging in, the login of the SDN network and the desktop cloud can be realized more quickly, and the utilization rate of system resources can be improved.
Owner:山西省农村信用社联合社
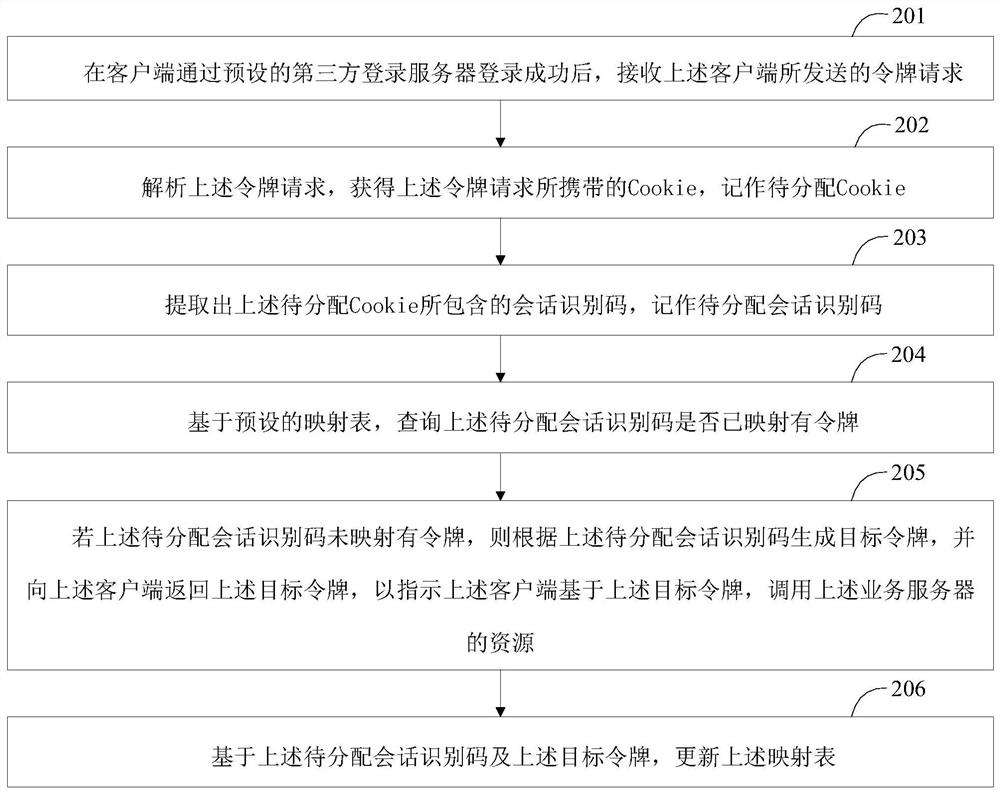
A resource call method, resource call device, client and business server
ActiveCN111371811BReduce Design ComplexityGuarantee data securitySecuring communicationThird partyEngineering
This application disclosed a resource call method, resource call device, client and business server. Among them, this method includes: after the client passed the client through the preset third -party login server login, receiving the third -party login server issuedCookie, wherein the Cookie contains session recognition code; generates token requests with Cookie, and sends to the business server toThe target token, where the target tokens are generated by the business server based on the session recognition code contained in the cookie; based on the target token, the resources of the business server are called.Through this application plan, the login function can be pulled away from the business server, so that the client can log in to the business server through a third -party login server. While reducing the design complexity of the business server, it still guarantees the data security of the business server.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Session Methods, Web Servers, and Browsers
The embodiment of the invention discloses a session method, a website server and a browser, which are used to realize the login of multiple users in multiple tabs of a browser. The method in the embodiment of the present invention includes: the website server receives the access request to the protected resource sent by the browser, and the protected resource is a resource that can only be accessed by legally registered users; judging whether the access request carries an identification sequence, and the identification sequence is the browser accessing the website server The login page is generated by the website server or browser; if it is not included, the login page is returned to the browser; if it is included, it is judged whether there is an account corresponding to the identification sequence carried in the access request in the session information between the browser and the website server information; if it exists, return the page corresponding to the access request; if it does not exist, return the login page. The embodiment of the invention also discloses a website server and a browser, which are used to realize the login of multiple users in multiple tabs of a browser.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com