A Chaos Encryption Method and System Based on 3D Probabilistic Forming
A chaotic encryption and probability technology, applied in the field of optical communication transmission, can solve the problems of laser synchronization performance and bandwidth not meeting requirements, large available bandwidth, etc., and achieve the effect of good encryption effect, large key space, and large flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
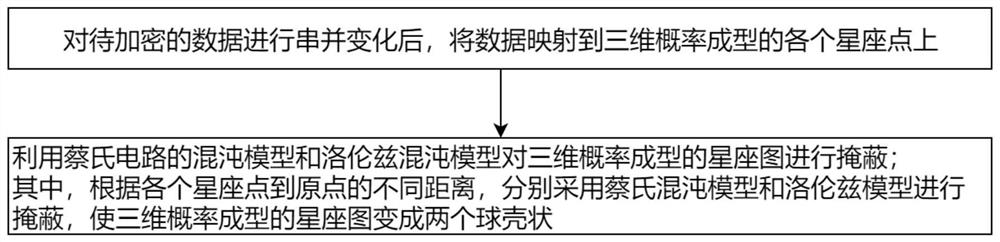
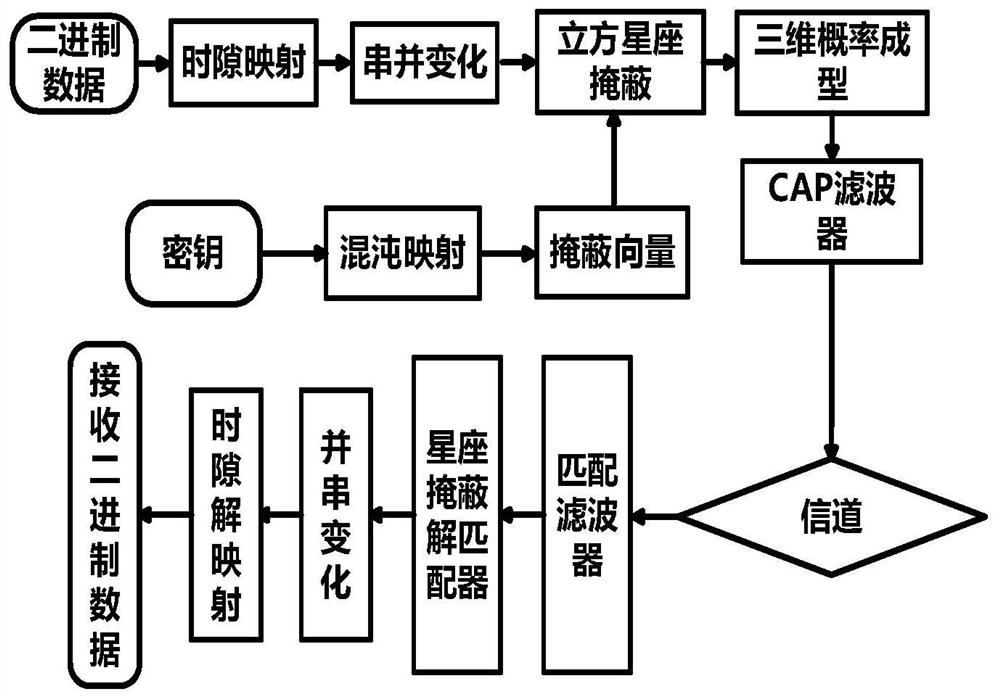
[0070] combine figure 1 , the present invention proposes a chaotic encryption method based on three-dimensional probability shaping, and the chaotic encryption method comprises the following steps:
[0071] S1, after serial-parallel transformation of the data to be encrypted, map the data to each constellation point formed by three-dimensional probability.
[0072] S2, using the Chaos model of Chua's circuit and the Lorentz Chaos model to mask the constellation diagram formed by the three-dimensional probability.
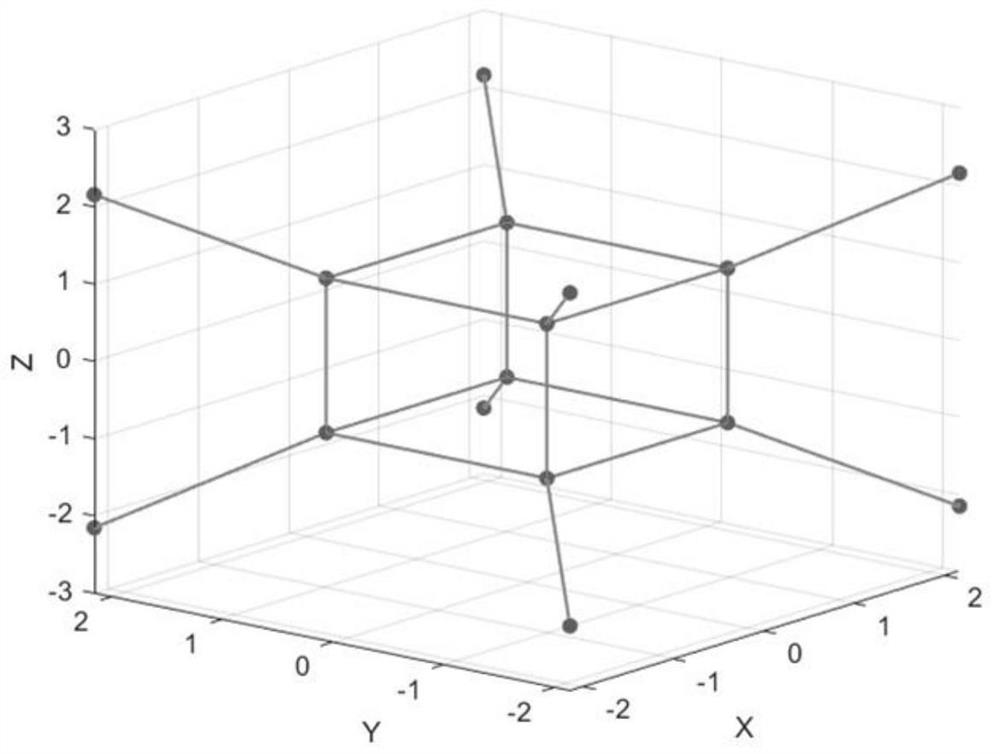
[0073] Among them, according to the different distances from each constellation point to the origin, the Chua's chaotic model and the Lorentz model are used for masking, so that the constellation diagram formed by the three-dimensional probability becomes two spherical shells.
[0074] The invention performs serial-parallel transformation and constellation mapping on the original binary data, performs constellation masking, and uses three-dimensional probability sh...
specific Embodiment 2
[0108] The system structure diagram of one of the chaotic encryption methods based on three-dimensional probability shaping is shown in Fig. Figure 8 Shown: A CW laser with a wavelength of 1551.72 nm is used as the light source, and we use the raw bitstream of length 8192 for further mapping, masking and filtering. The whole algorithm part is realized by digital signal processing in MATLAB, and a 50Gs / s digital-to-analog converter (DAC) is used to generate electrical signals. The resulting encrypted signal is electro-optically modulated with the light source in a modulator to generate an optical signal. An optical filter (OF) is used for slicing, resulting in optical SSB modulation. Then, the optical signal enters a 25km single-mode fiber for transmission after passing through an erbium-doped fiber amplifier. At the receiving end, a variable optical attenuator (VOA) is placed behind the fiber for bit error rate (BER) measurements. The optical signal is directly detected by...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com