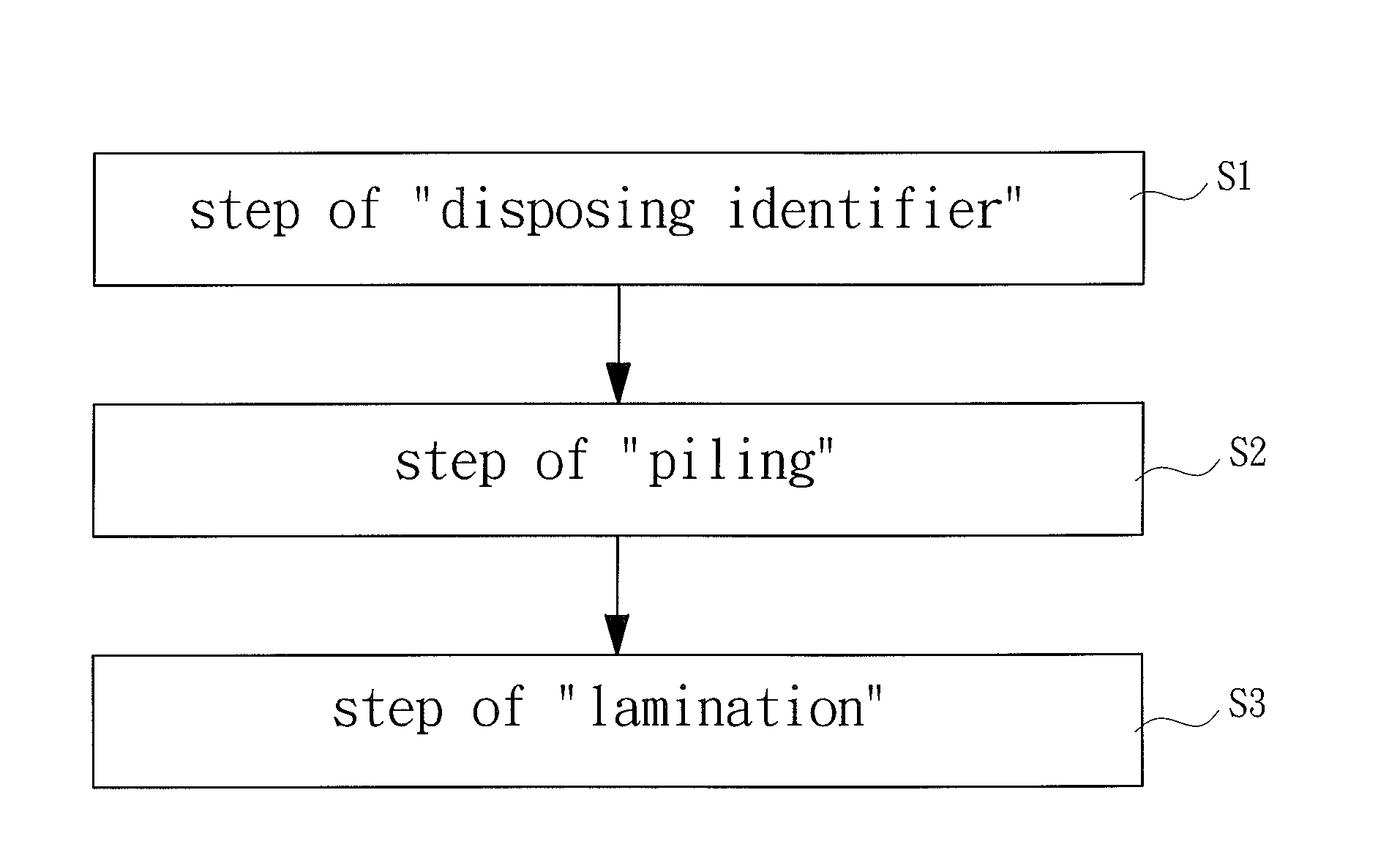
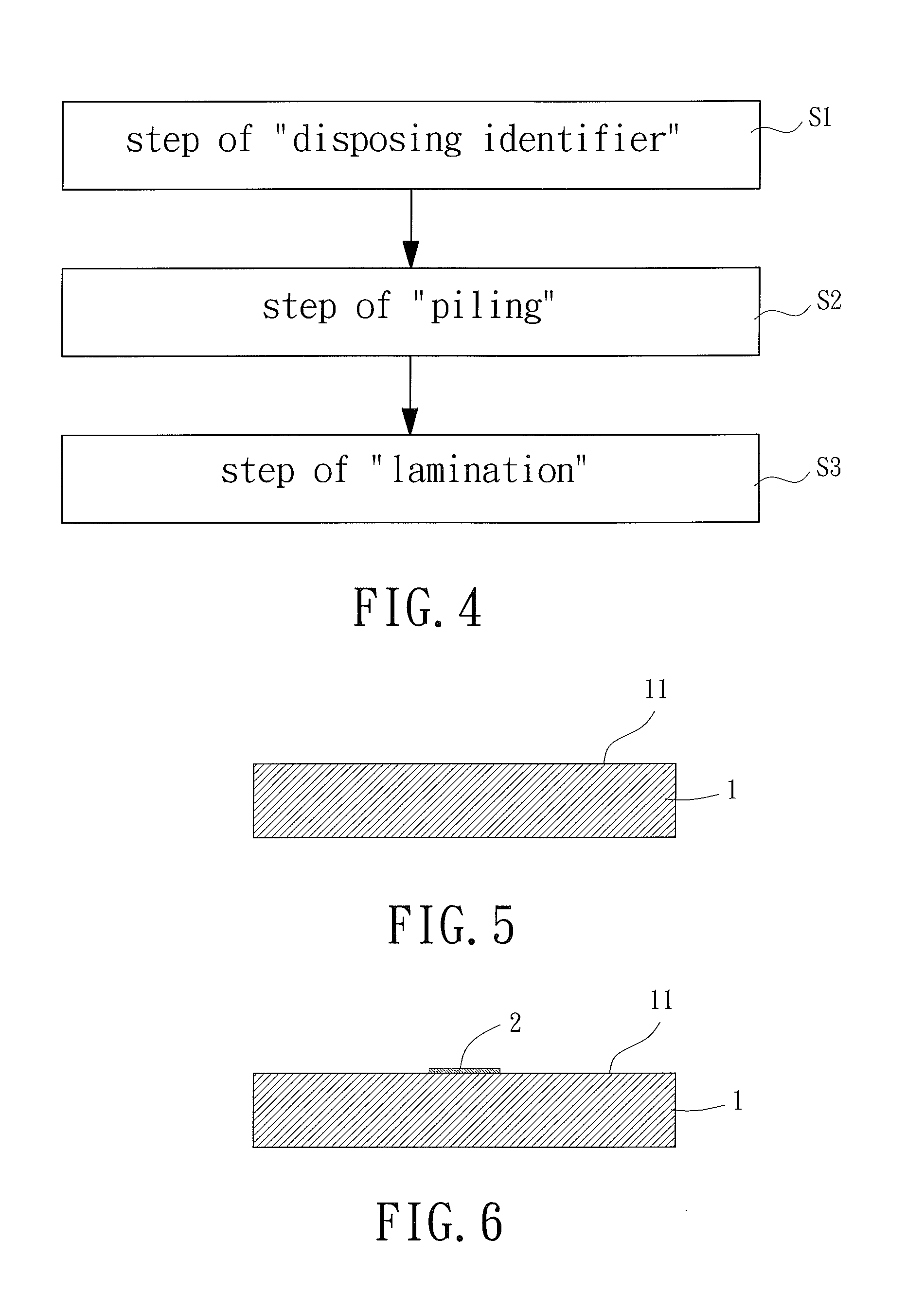
Patents
Literature
30 results about "Primary Identifier" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Primary identifiers. A primary identifier is a single attribute that is assigned as the primary key. You must specify one primary item identifier for the enterprise to facilitate data exchange and avoid duplicate resolutions.
Secure mobile payment system
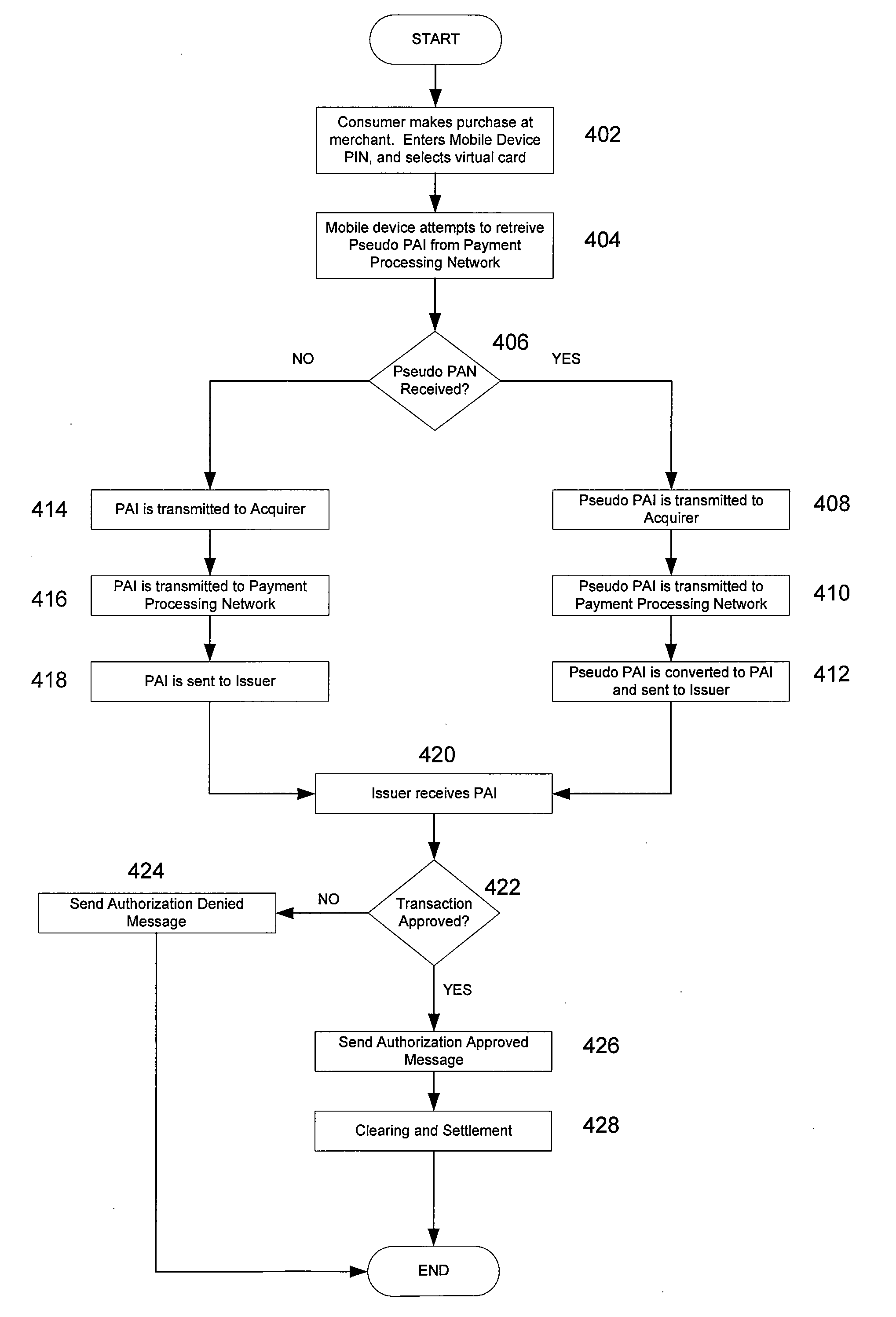
The present invention provides a method for conducting a transaction that includes receiving a pseudo account identifier that corresponds to a primary account identifier. The pseudo account identifier may be received at a portable wireless device and may be generated by a remote server computer. The portable wireless device can receive the pseudo account identifier over a first network and provide the pseudo account identifier to an access device. The access devices generally comprises a reader that can receive the pseudo account identifier, and thereafter send a message to request authorization of a transaction. The authorization request message may include the pseudo account identifier and is sent to a payment processing network. The authorization request message is sent to the payment processing network over a second network. The payment processing network may then process the authorization message and return a response that indicates if the transaction is authorized or not.
Owner:VISA INT SERVICE ASSOC
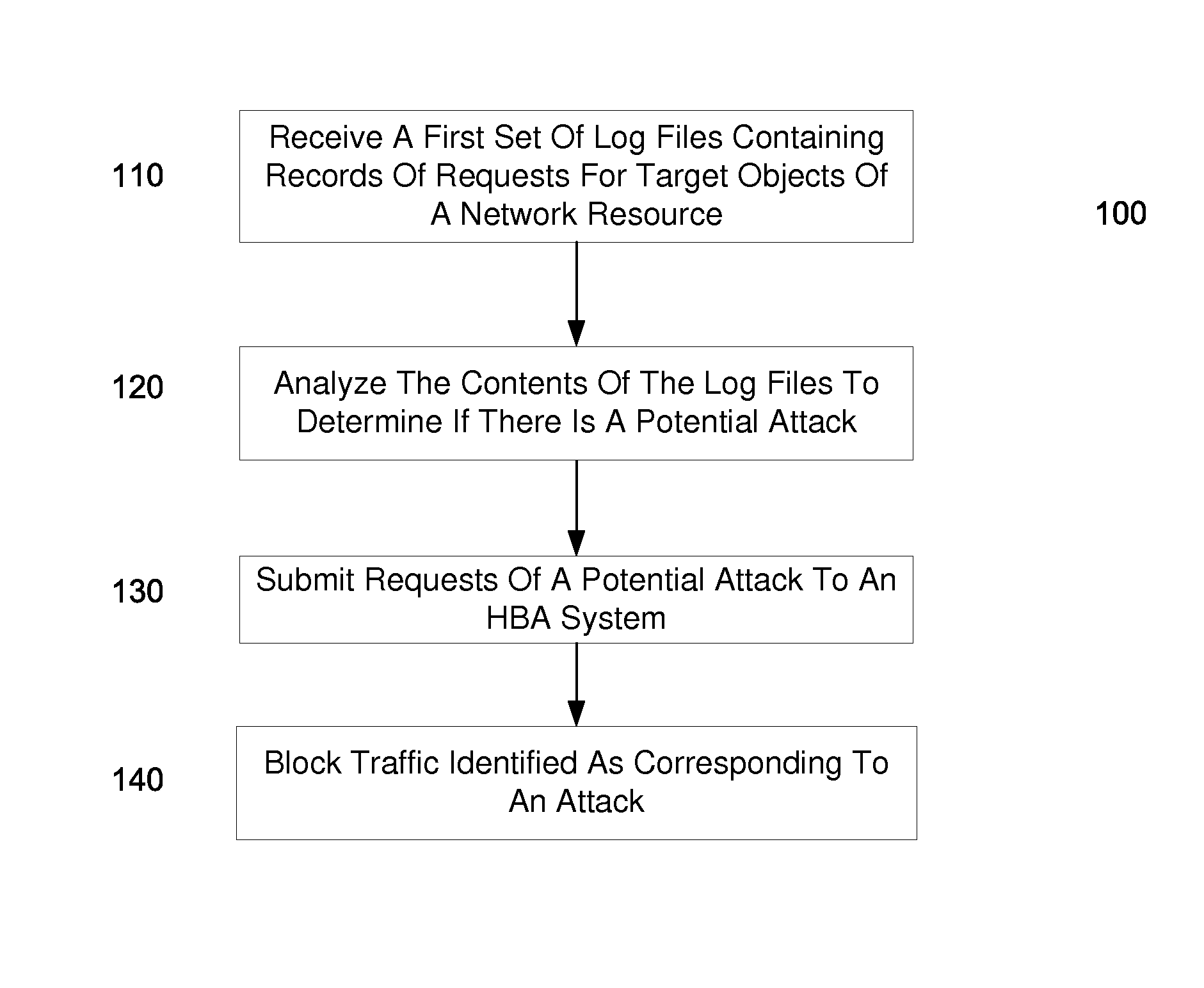
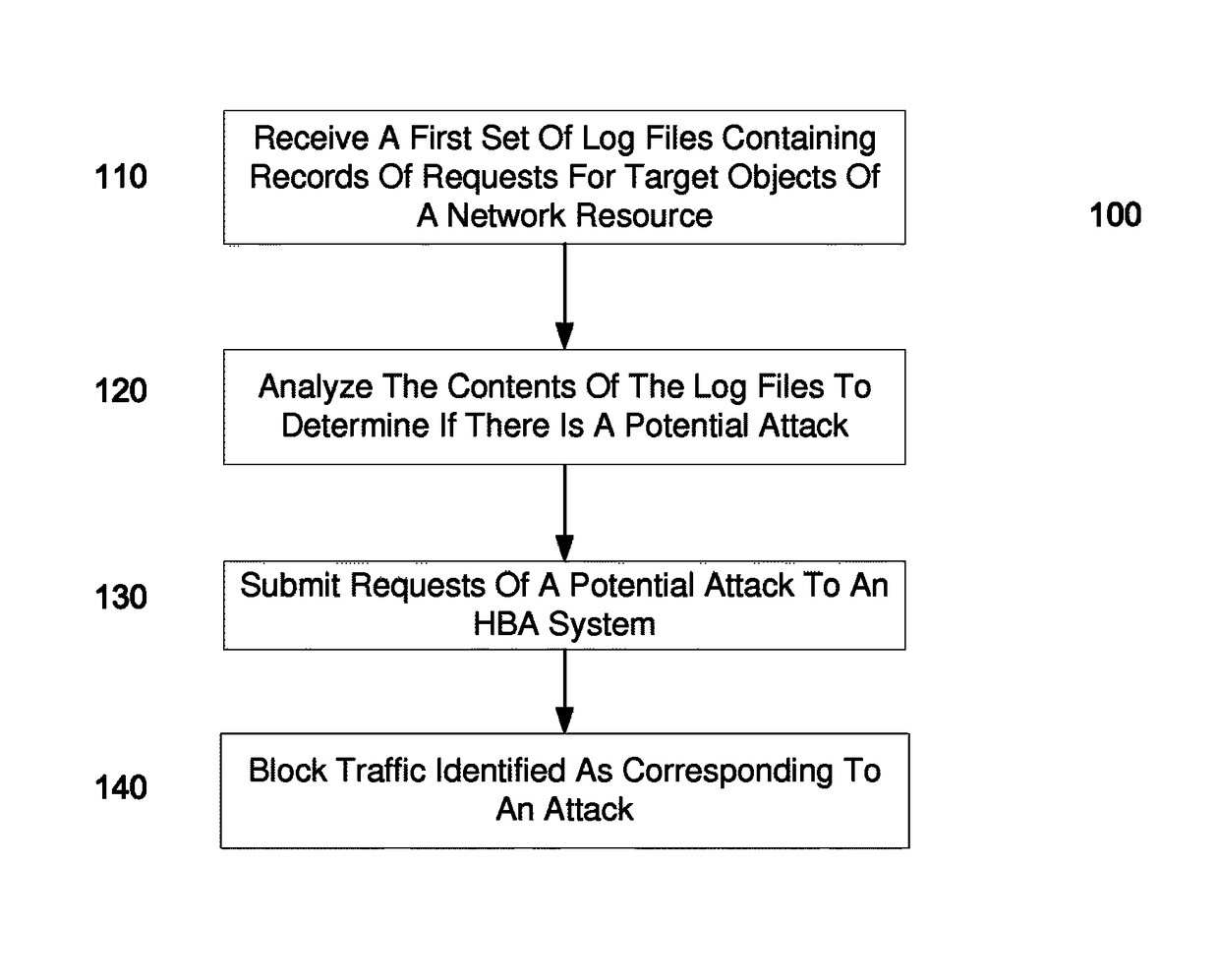
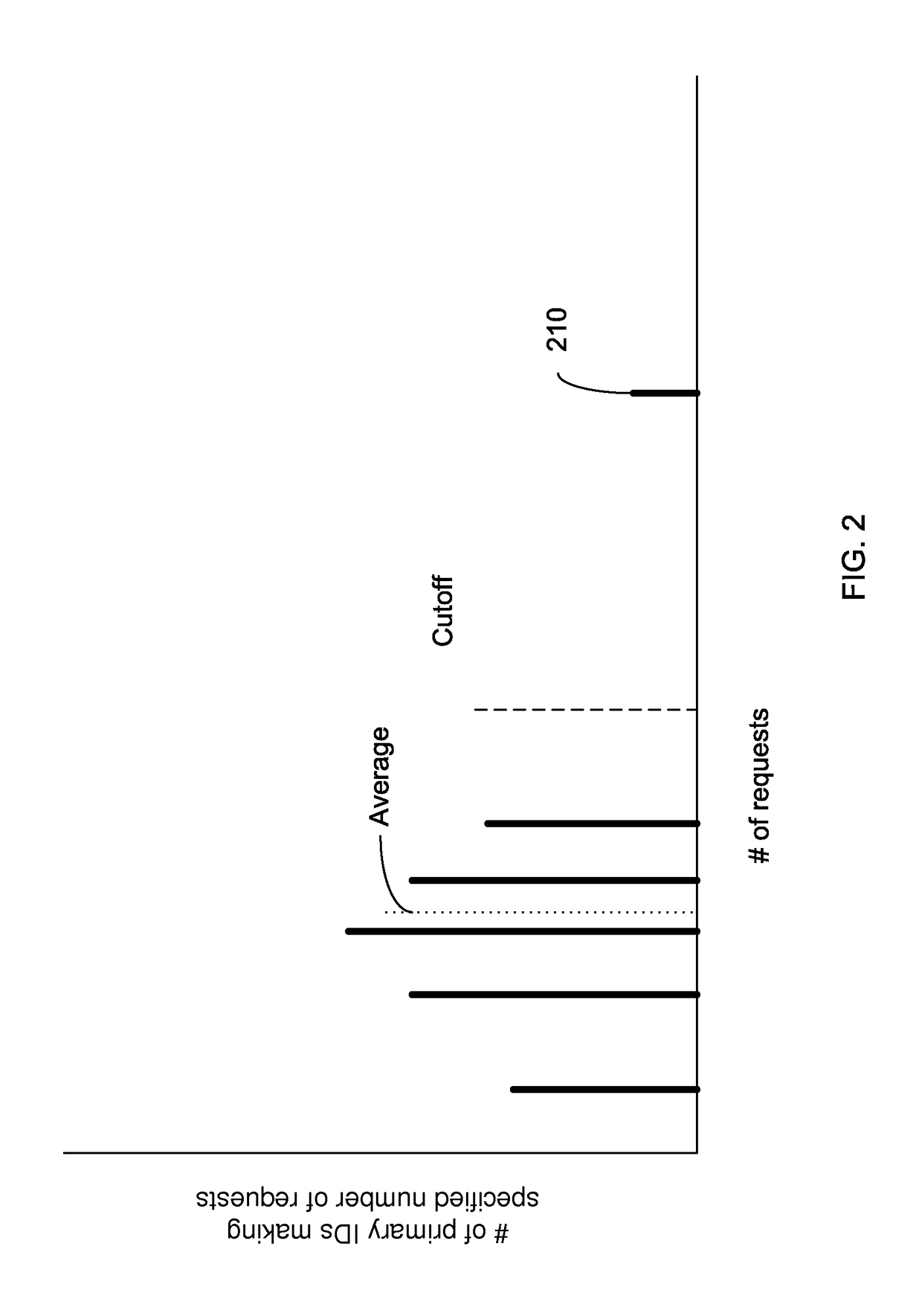
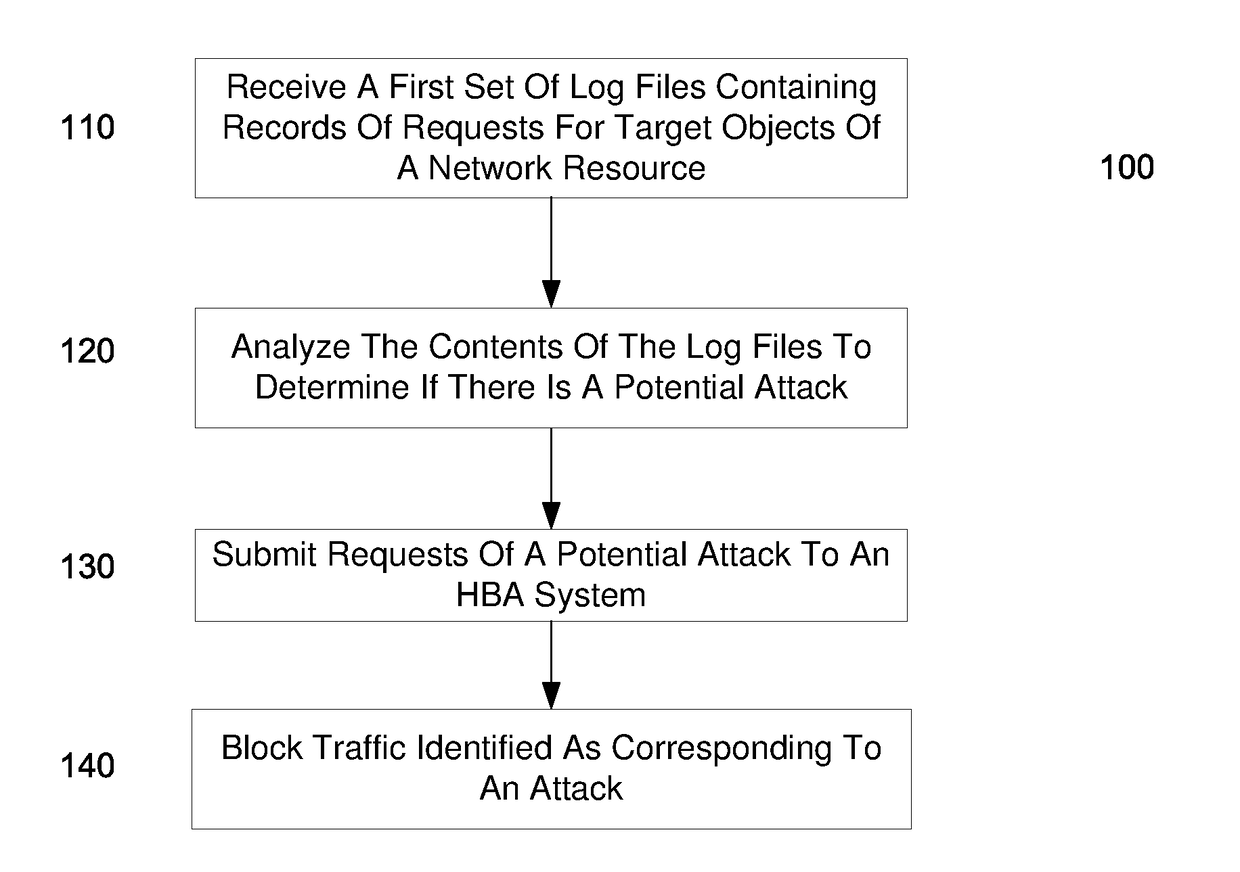
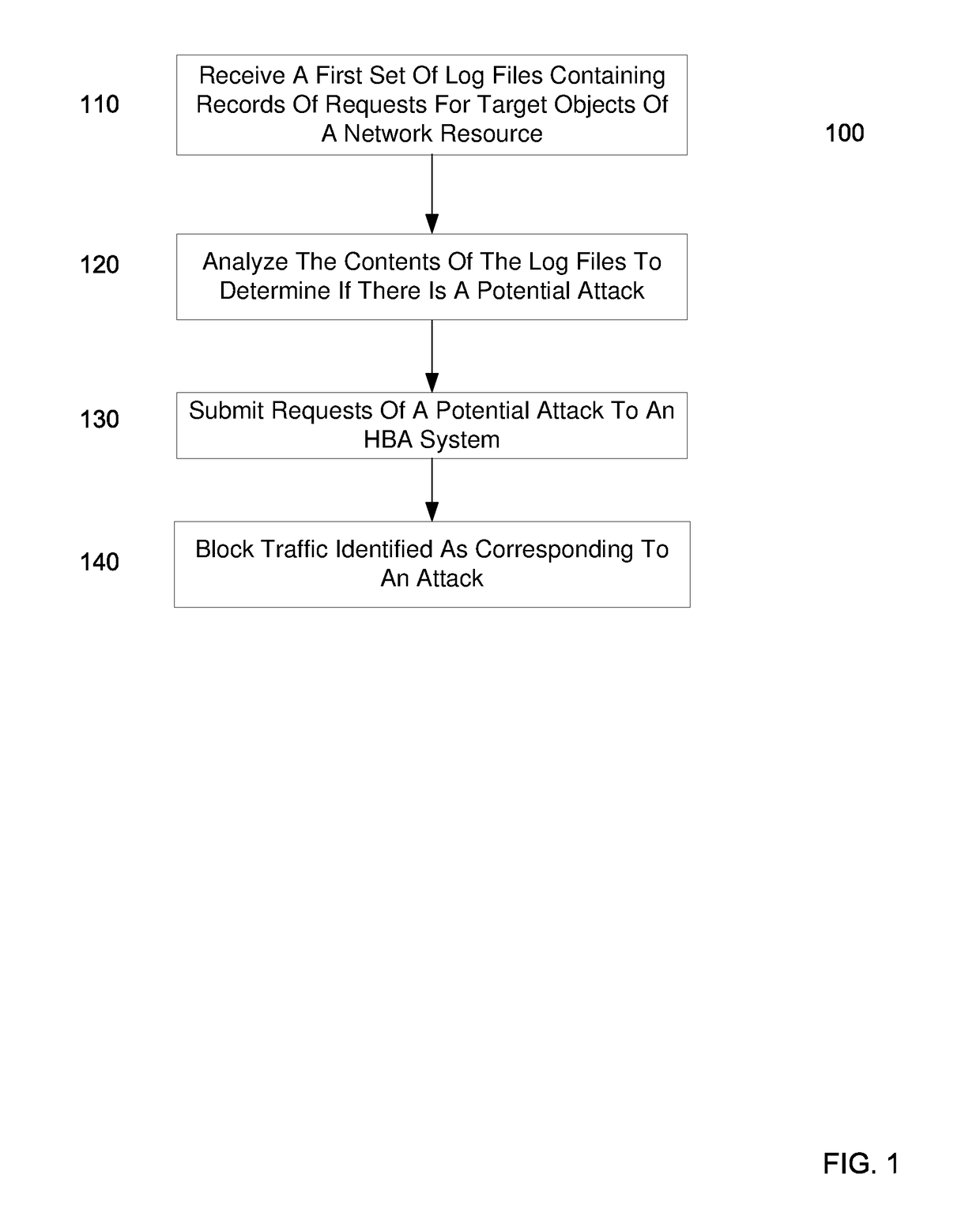
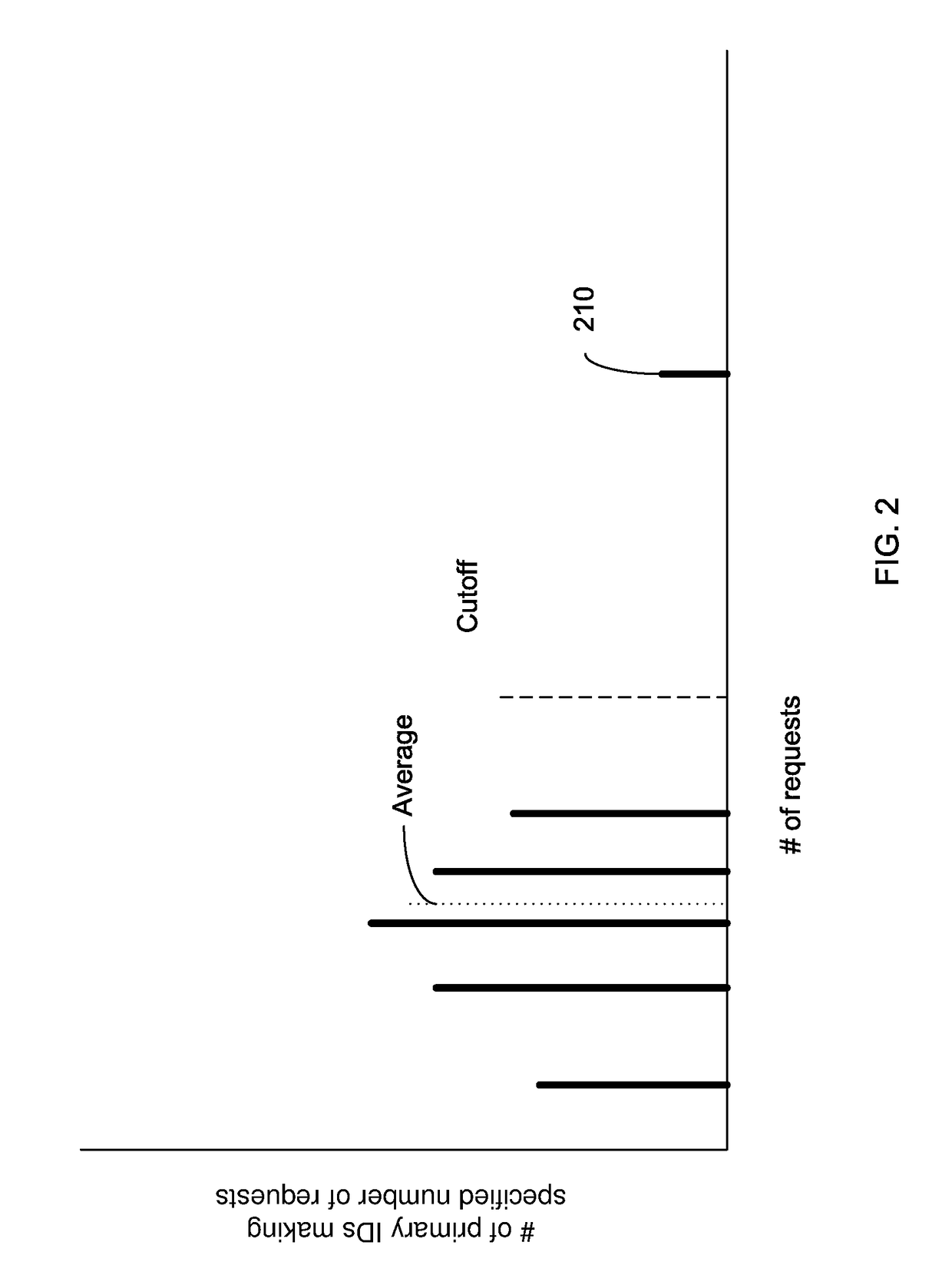
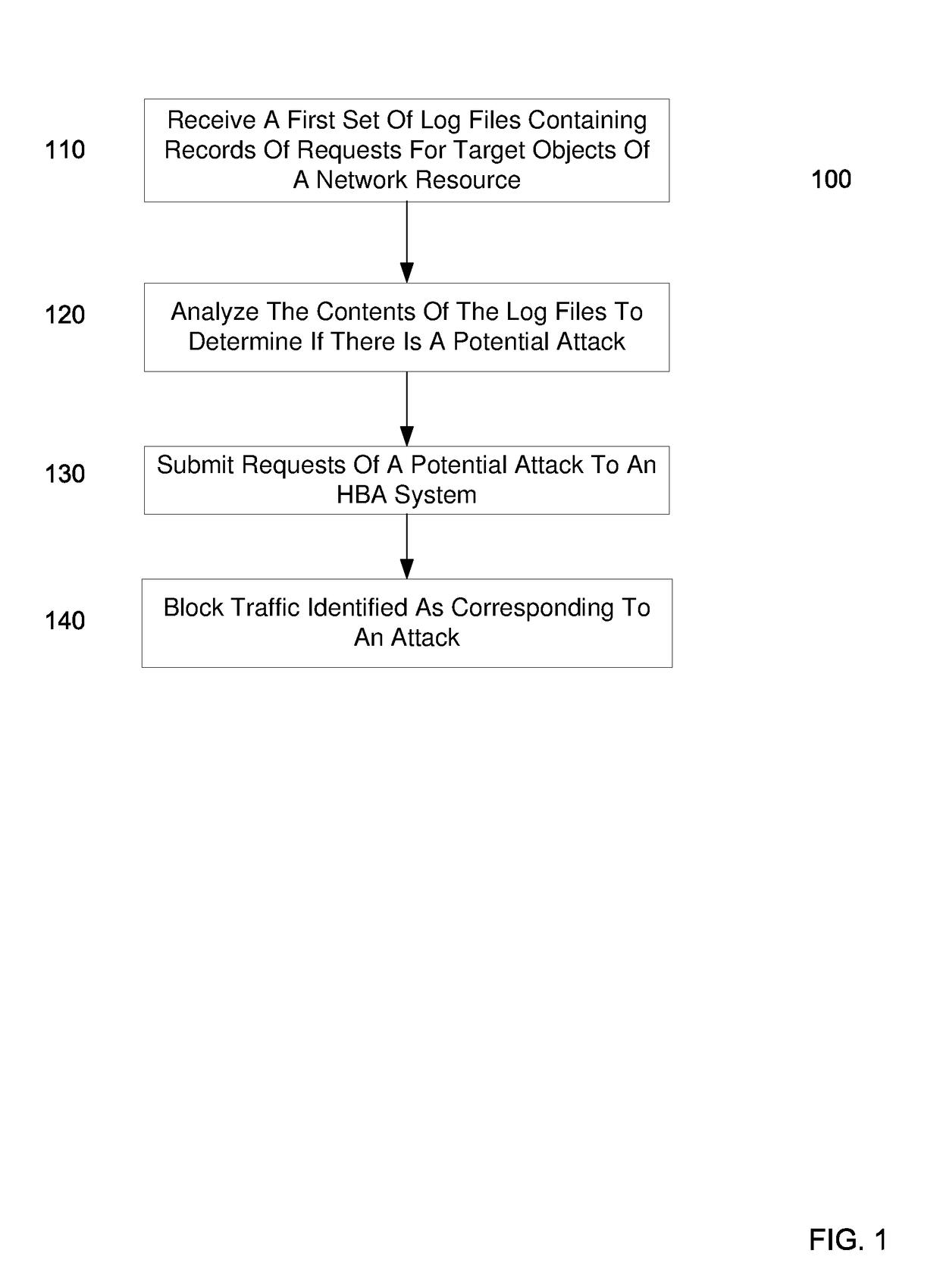
Identifying a potential DDOS attack using statistical analysis
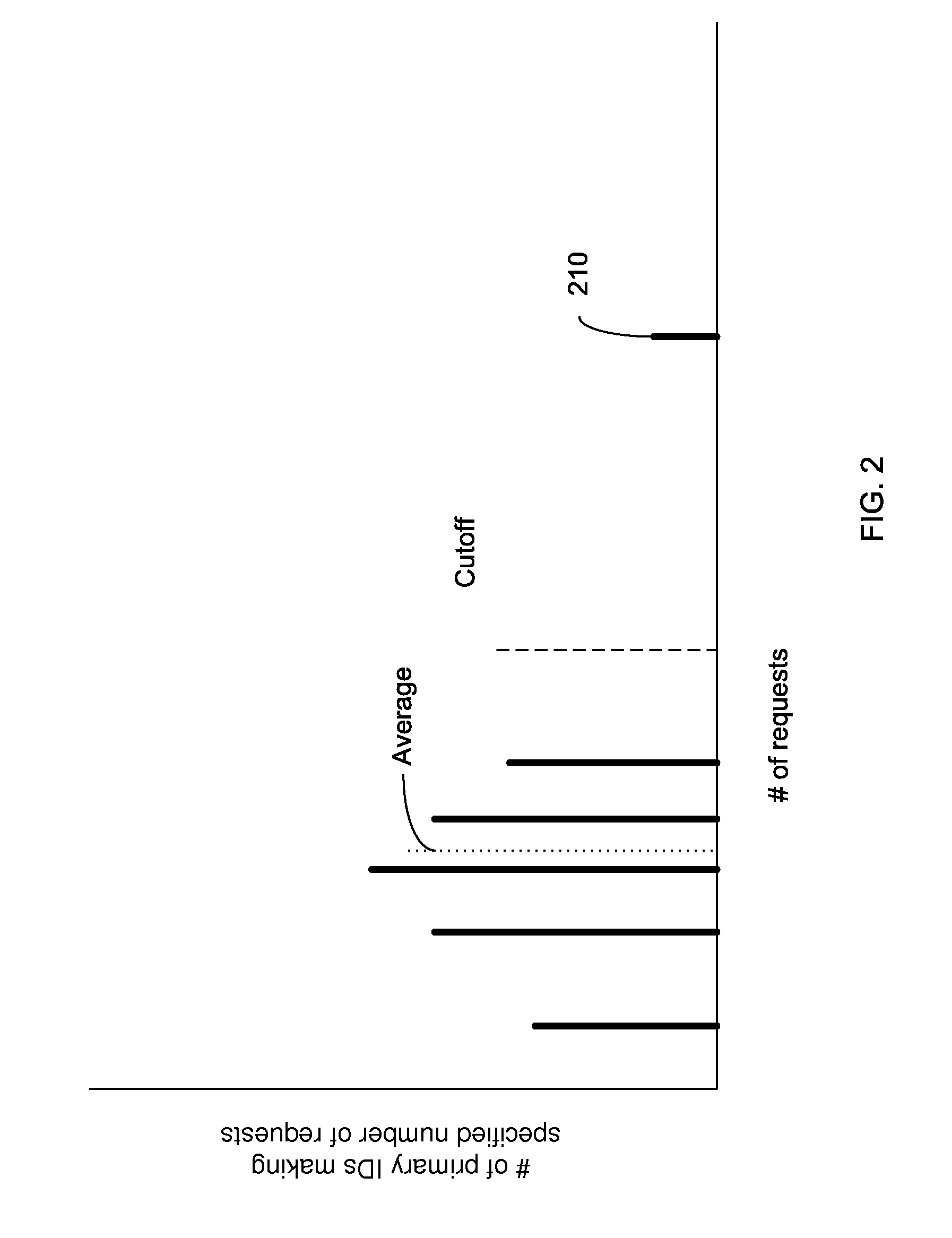
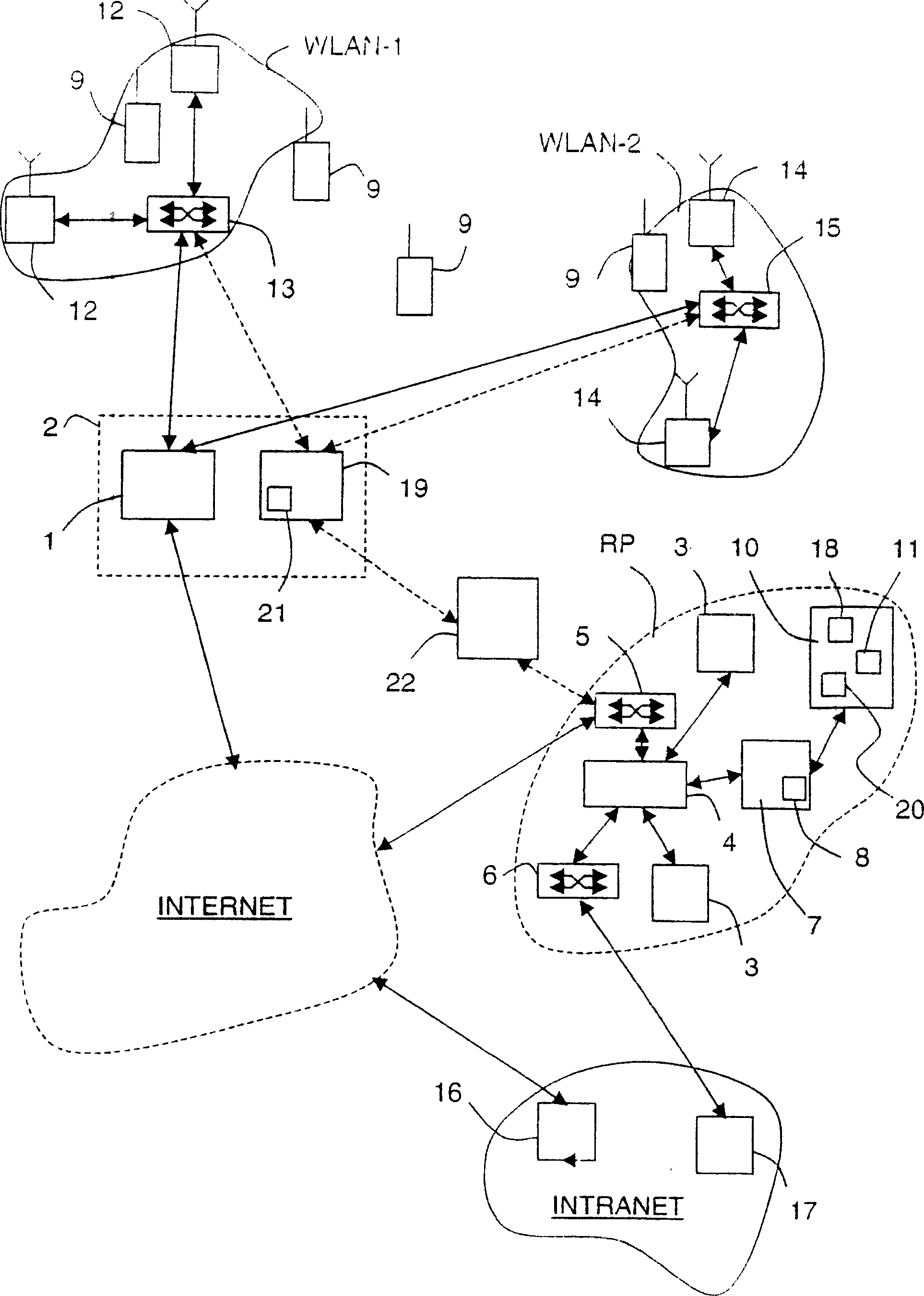
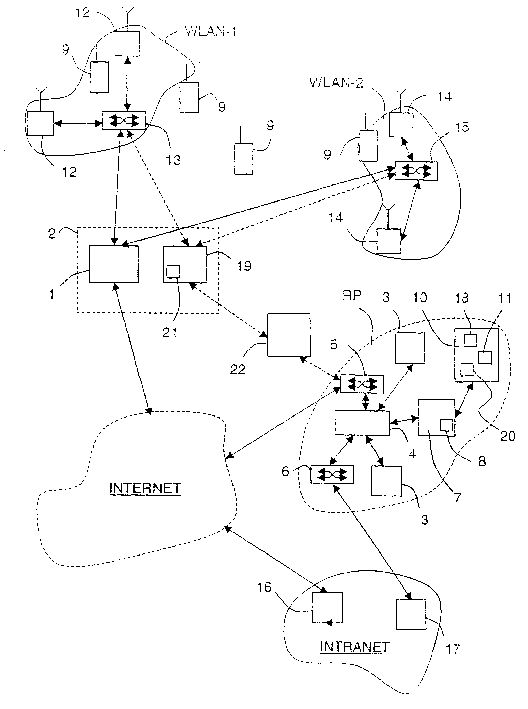
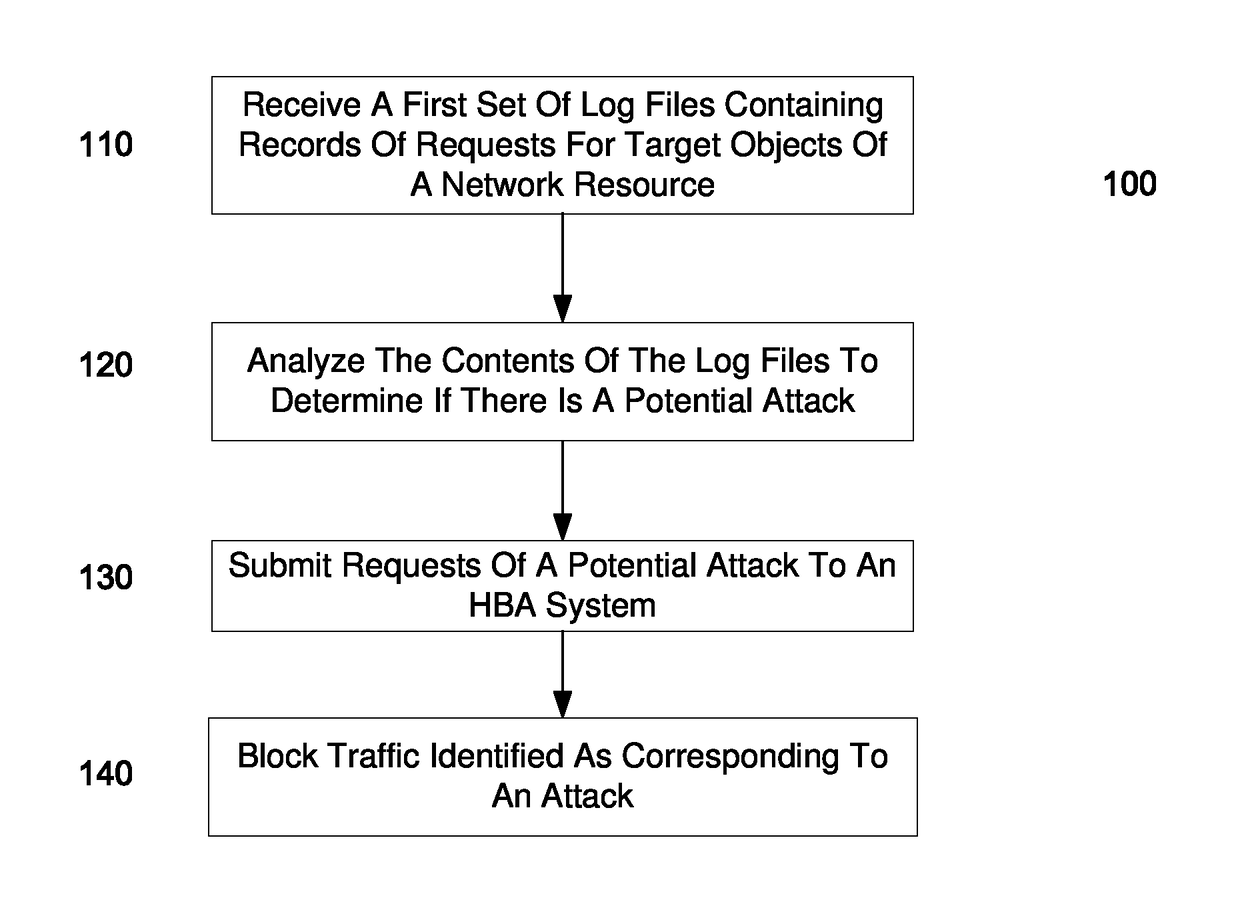
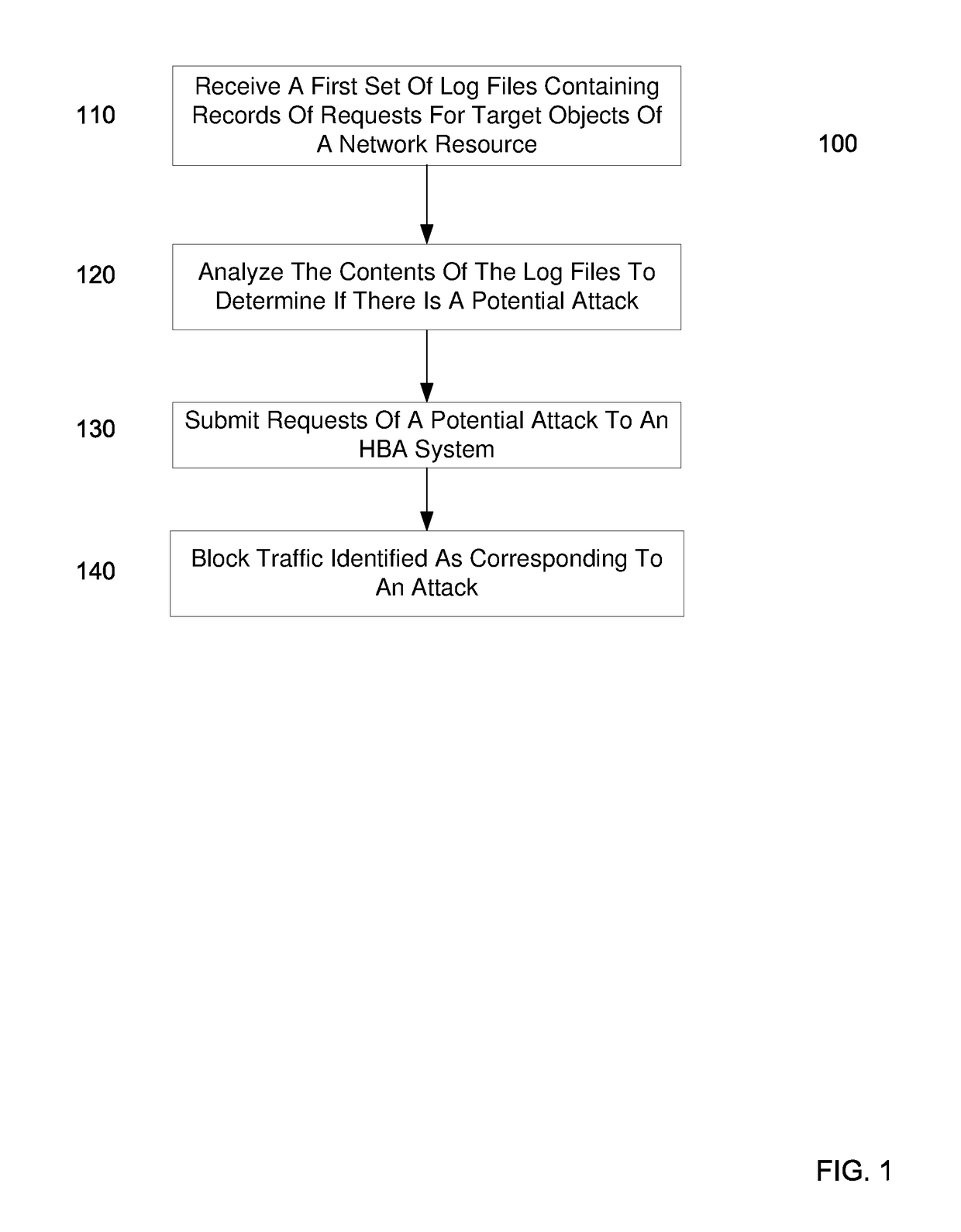
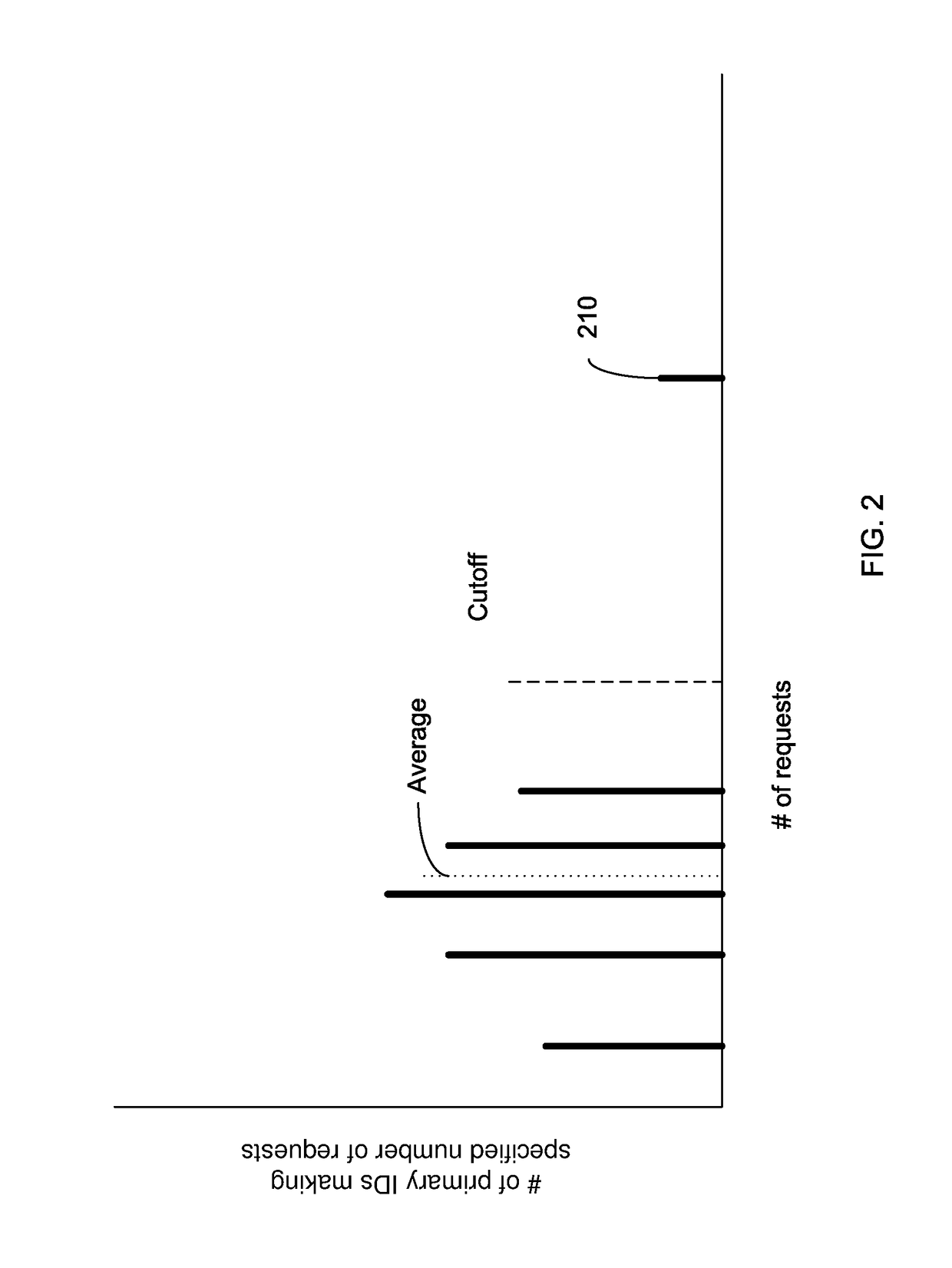
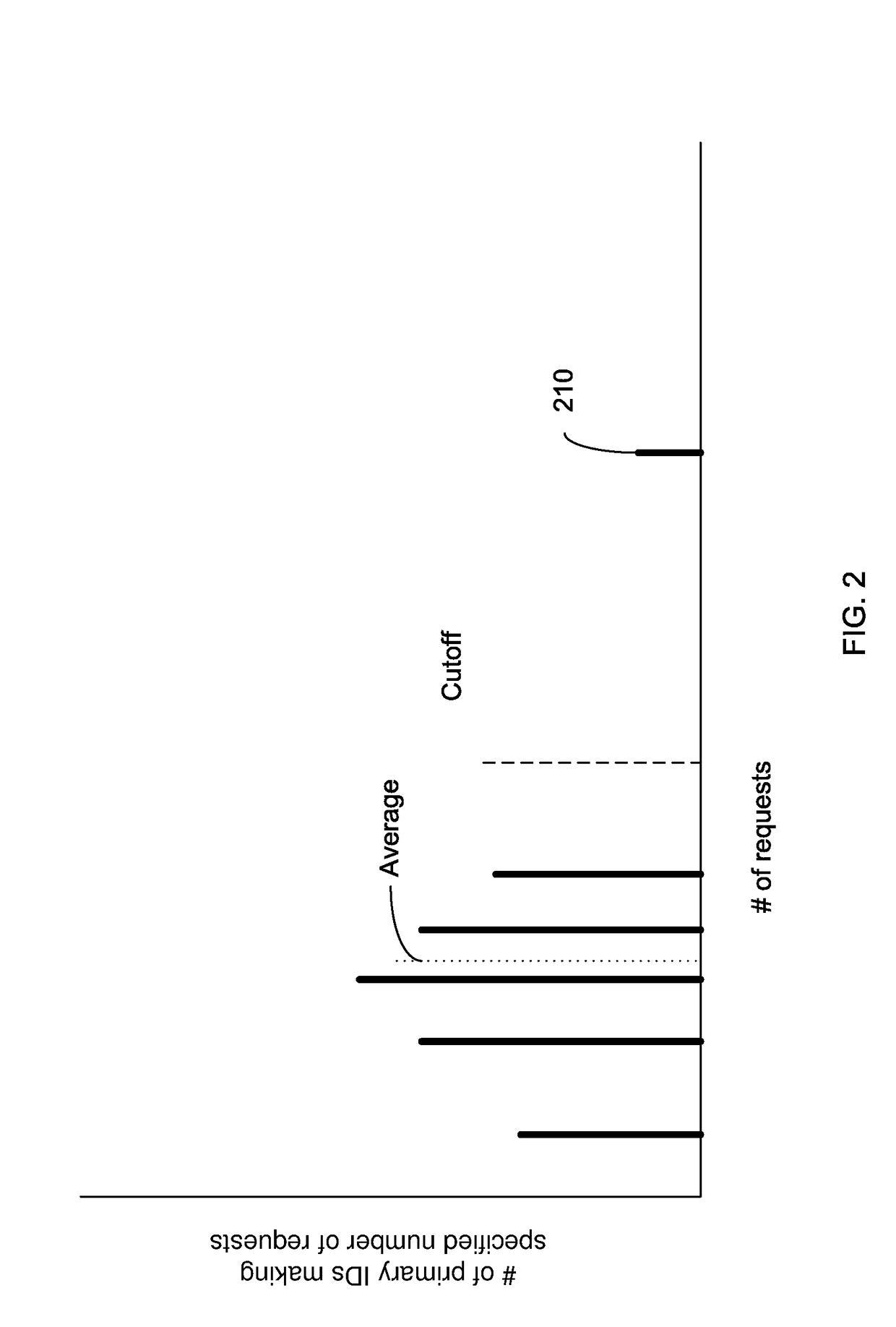
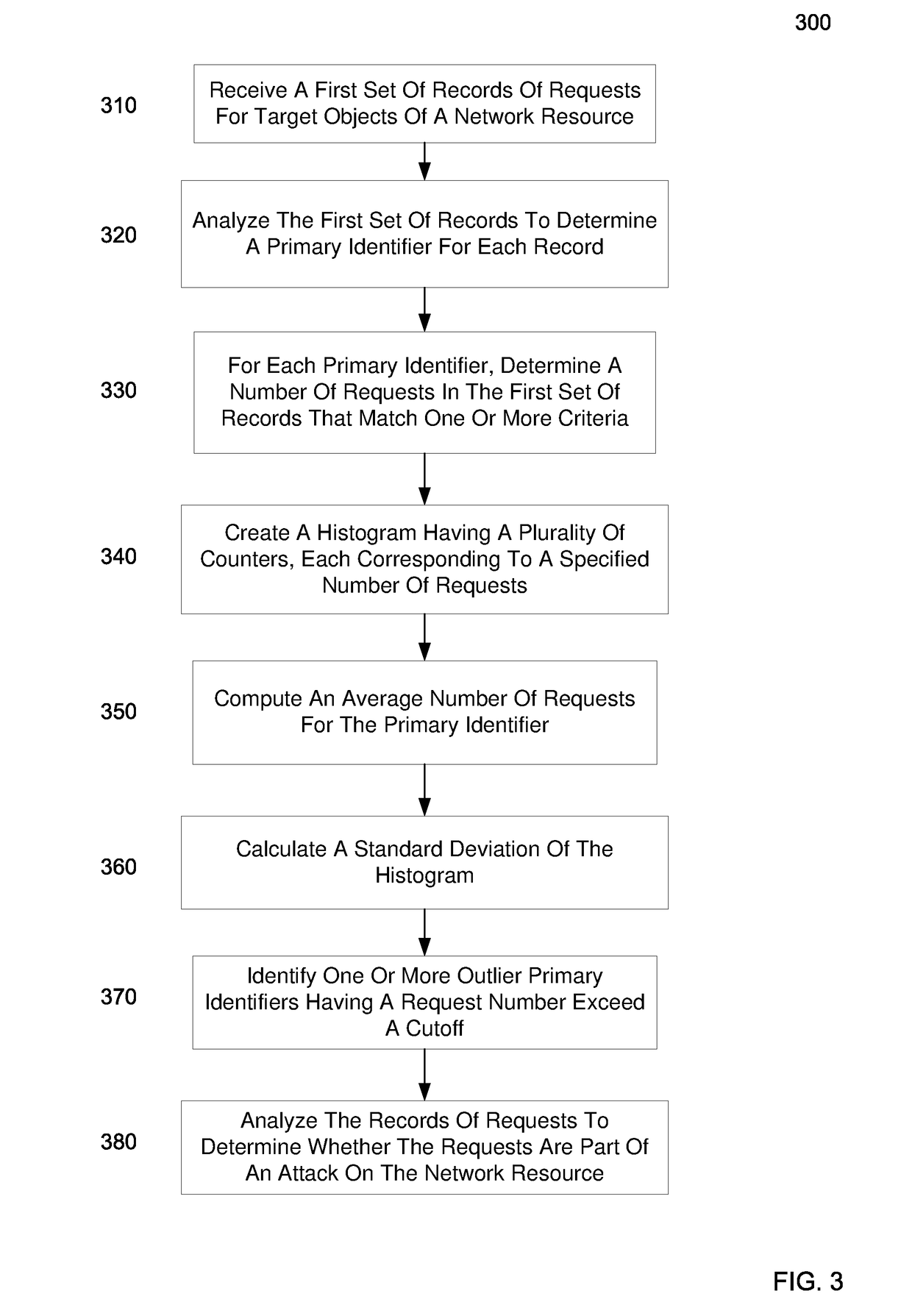
Embodiments can identify requests that may be tied to a DDOS attack. For example, the primary identifiers (e.g., a source address) of requests for a network resource (e.g., an entire website or a particular element of the website) can be tracked. In one embodiment, a statistical analysis of how often a particular source address (or other primary identifier) normally makes a request can be used to identify source addresses that make substantially more requests. A normal amount can correspond to an average number of request that a source address makes. According to some embodiments, a system can use statistical analysis methods on various request data in web server logs to identify potential attacks and send data concerned potential attacks to an HBA system for further analysis.
Owner:LEVEL 3 COMM LLC
Method and device for access control to a wireless local access network
A device is dedicated to controlling access to wireless communications local area networks having a local coverage area included in a main coverage area of a main communications network equipped with mobile communications device positioning means. The device having management means connected to the positioning means and adapted i) to compare the positions of at least some of the mobile devices to those of the local areas, in order to select the primary identifiers of the mobile devices substantially positioned in said local areas, and ii) to send a messaging server of the main network instructions including the primary identifier of each mobile device selected, in order for it to send them a message telling their users that they can connect to the local area network in whose local area they are placed.
Owner:NOKIA TECHNOLOGLES OY
System And Method For Technique Document Analysis, And Patent Analysis System
InactiveUS20090132496A1Improve convenienceReduce system resourcePatent retrievalSpecial data processing applicationsPrimary IdentifierDocument analysis
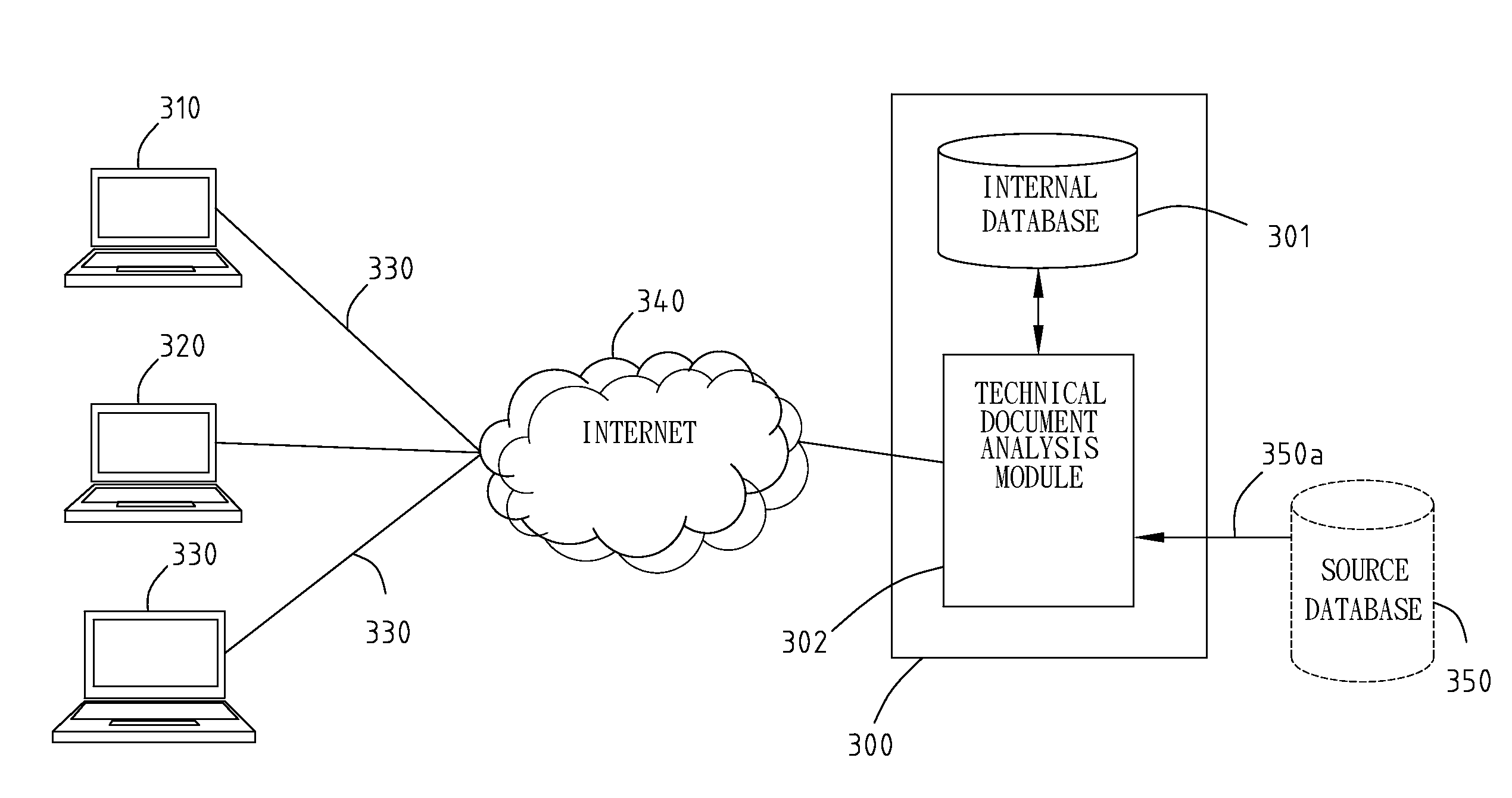
Disclosed is a system and method for technical document analysis. The system comprises an internal database and a technical document analysis module. The technical document analysis module links with at least an original database, and may fetch the original data from the original database and analyzes the original data. The partial data of the original data with regularity and preliminary index act as primary identifiers. According to the relationship between the other part of the original data and the primary identifiers, the original data are converted into a plurality of sub-data. After being compared with the contents of the relationship database, the whole sub-data may be stored in the relationship database or only their renew portion may be stored in the internal database.
Owner:IND TECH RES INST +1
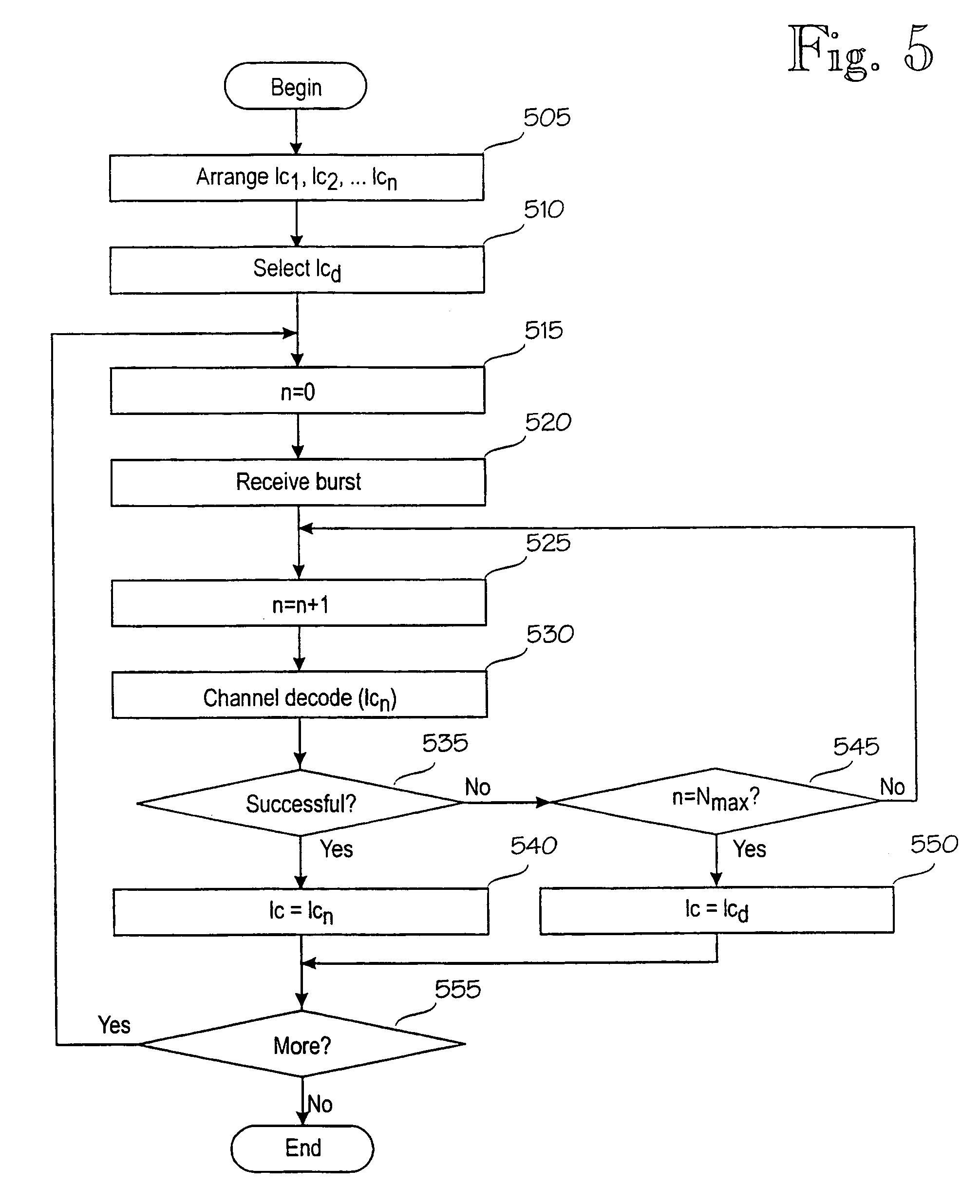
Method and equipment for identifying a logical channel
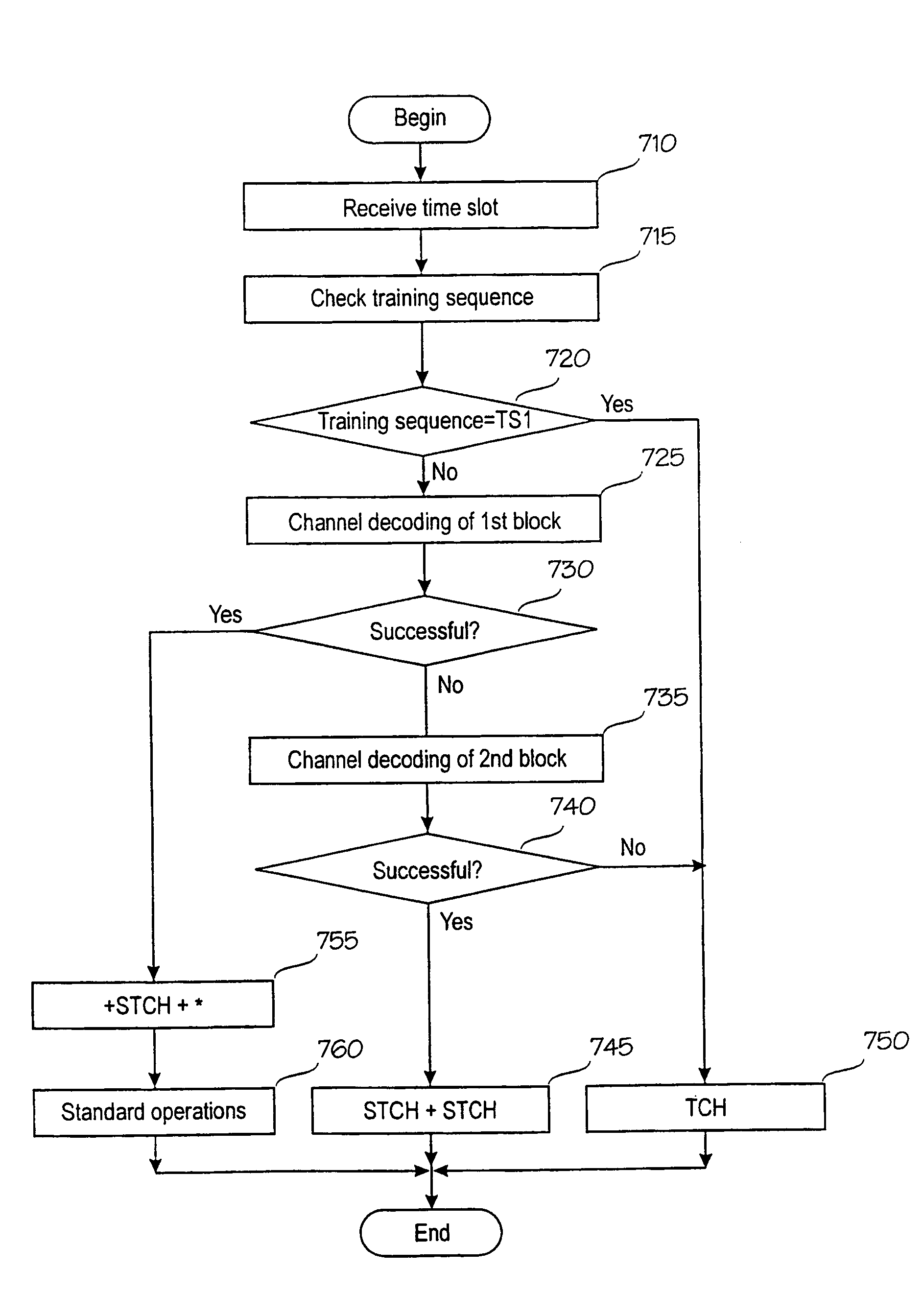
InactiveUS7133421B1Increase capacityError preventionTime-division multiplexPrimary IdentifierCommunications system
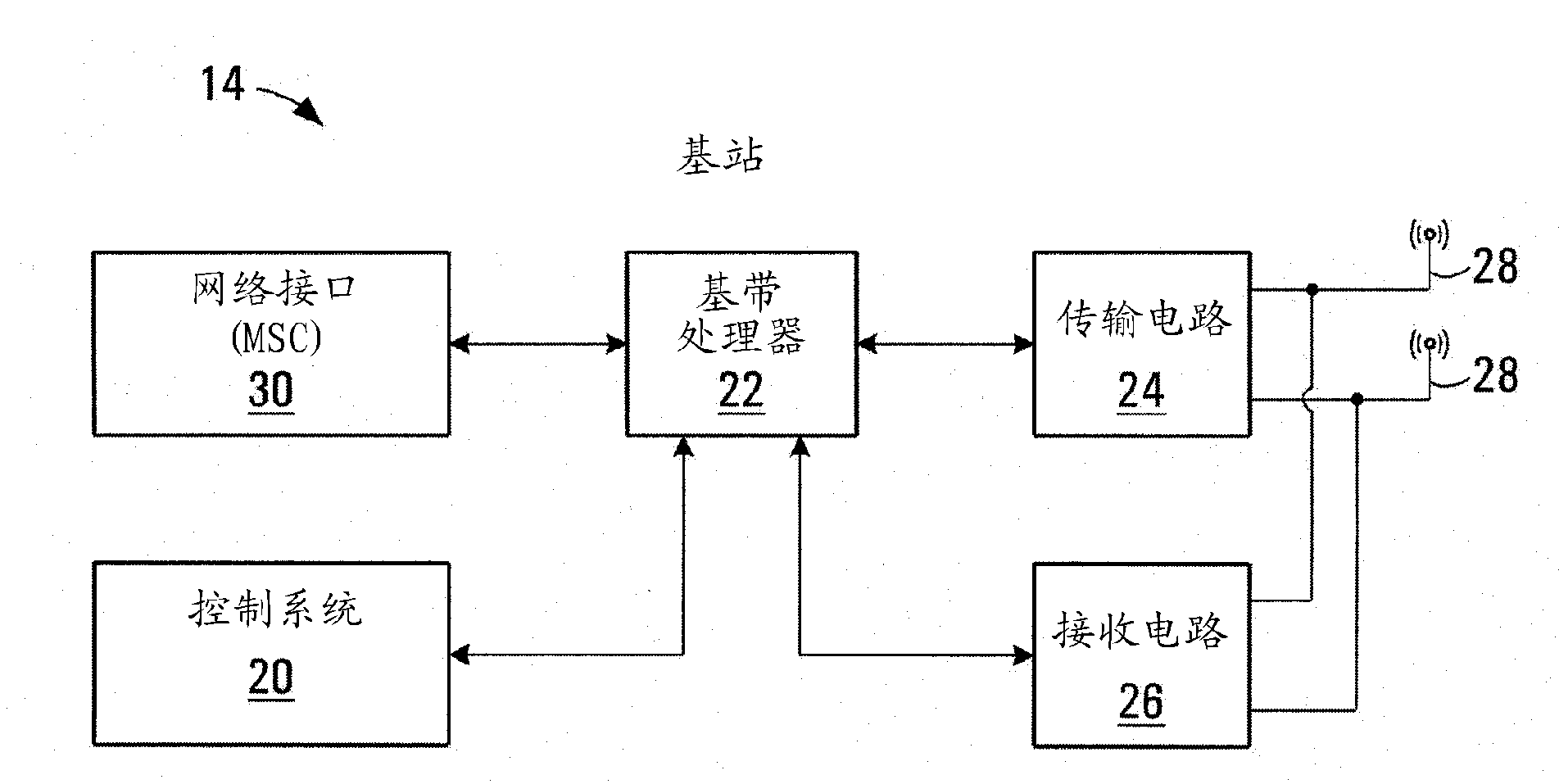
A method and an equipment implementing the method that allow a logical channel, to which a received burst relates, to be identified with certainty also in demanding operational circumstances. A logical channel relating to a time slot is identified by applying channel decoding. The identification can be a primary identification or a confirming identification taking place after a primary identifier the time slot comprises, preferably a bit map, has been interpreted. If identification based on channel decoding contradicts identification based on the bit map, a receiver can be arranged to indicate logical channel information on the basis of the channel decoding, for instance by changing the bit map, when selected criteria are met, to a bit map conforming to the logical channel identified on the basis of the channel decoding. The invention significantly improves the performance of a receiver of a mobile communications system because a considerable part of misinterpretations relating to the logical channel are avoided.
Owner:CASSIDIAN FINLAND
Codebook restructure, differential encoding/decoding and scheduling
InactiveUS20110122811A1Network traffic/resource managementWireless commuication servicesPrimary IdentifierWireless transmission
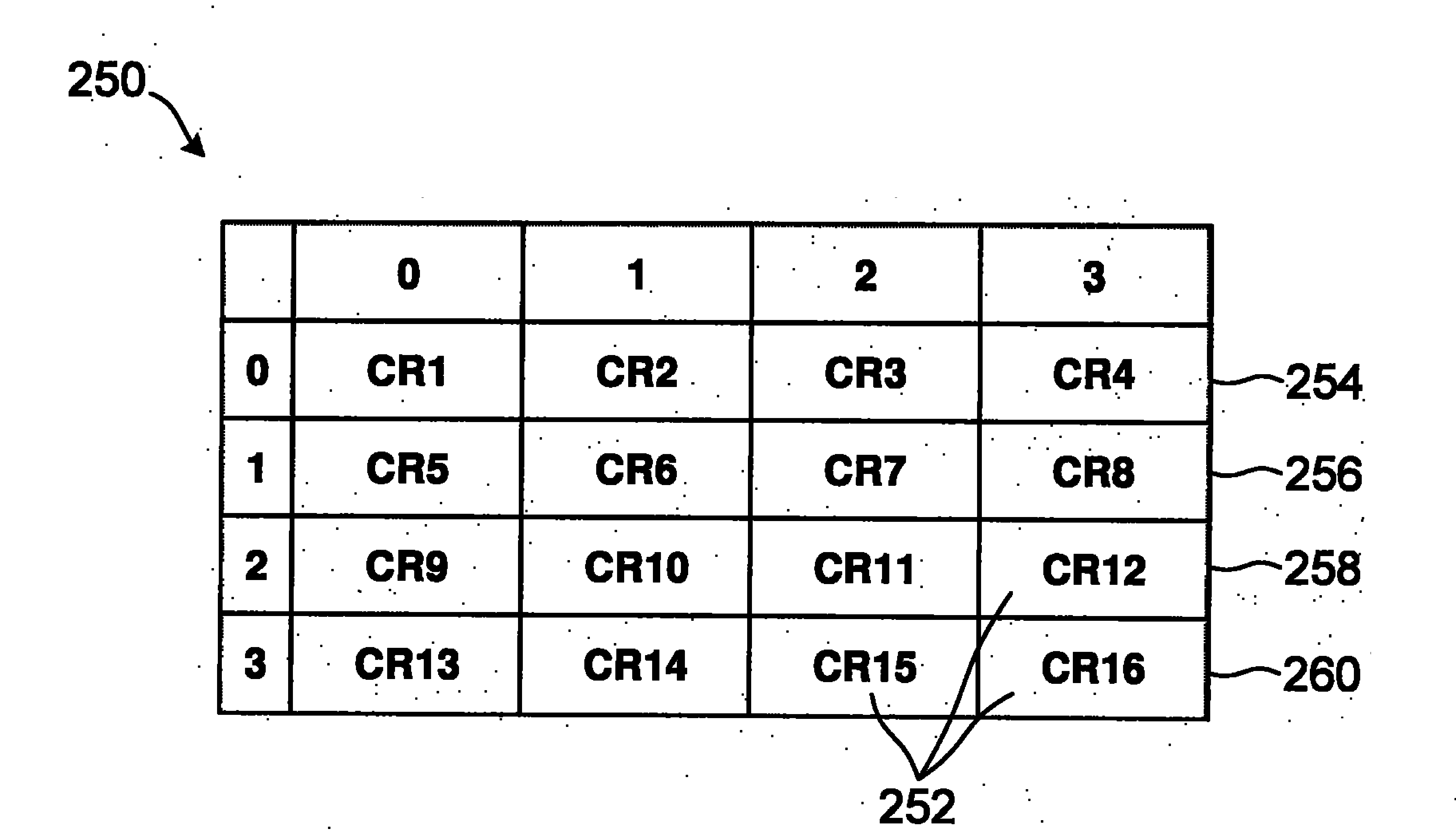
A method and apparatus for feedback of channel information characterizing a wireless transmission between a base station and a mobile station. The method involves, at the base station, locating in a codebook of predetermined channel responses a predetermined channel response identified by: a primary identifier identifying a cluster associated with a channel response generated by a mobile station; and a differential identifier identifying channel response member within the cluster identified by the primary identifier. The predetermined channel responses are grouped in a plurality of clusters in accordance with a correlation criterion, each cluster including a plurality of predetermined channel response members. The method also involves generating a control signal for controlling transmissions to the mobile station in accordance with the located predetermined channel response. A method and apparatus for feedback of channel information characterizing a wireless transmission between a mobile station and a base station are also disclosed.
Owner:APPLE INC
Identifying a potential DDOS attack using statistical analysis
Embodiments can identify requests that may be tied to a DDOS attack. For example, the primary identifiers (e.g., a source address) of requests for a network resource (e.g., an entire website or a particular element of the website) can be tracked. In one embodiment, a statistical analysis of how often a particular source address (or other primary identifier) normally makes a request can be used to identify source addresses that make substantially more requests. A normal amount can correspond to an average number of request that a source address makes. According to some embodiments, a system can use statistical analysis methods on various request data in web server logs to identify potential attacks and send data concerned potential attacks to an HBA system for further analysis.
Owner:LEVEL 3 COMM LLC
Identifying a potential ddos attack using statistical analysis
Owner:LEVEL 3 COMM LLC
Method of providing services to remote private terminals and an associated device
InactiveUS7139377B2Interconnection arrangementsSpecial service for subscribersPrimary IdentifierPrivate network
A method is disclosed of providing services to private terminals belonging to a private network including a private database which contains primary identifiers of the private terminals associated with first data representative of services to which the private terminals have access within the private network and which can be connected to a public network including an intelligent platform and connected to the private network. The method includes a first step in which there is stored, at an address accessible to the intelligent platform, second data representative of at least a portion of the private database and, at an address of the public network, third data representative of the primary identifier of each private terminal, of the associated private network, and of the intelligent platform having access to the second data of the private network. In a second step, if a private terminal sends a service request over the public network, the third data associated with the primary identifier of the requesting private terminal is extracted, after which the data of the request is compared to the second data designated by the extracted third data to authorize or not the platform designated by the extracted third data to implement the required service.
Owner:RPX CORP
Method and device for access control to a wireless local access network
Owner:ALCATEL LUCENT SAS
Identifying a potential DDOS attack using statistical analysis
Embodiments can identify requests that may be tied to a DDOS attack. For example, the primary identifiers (e.g., a source address) of requests for a network resource (e.g., an entire website or a particular element of the website) can be tracked. In one embodiment, a statistical analysis of how often a particular source address (or other primary identifier) normally makes a request can be used to identify source addresses that make substantially more requests. A normal amount can correspond to an average number of request that a source address makes. According to some embodiments, a system can use statistical analysis methods on various request data in web server logs to identify potential attacks and send data concerned potential attacks to an HBA system for further analysis.
Owner:LEVEL 3 COMM LLC
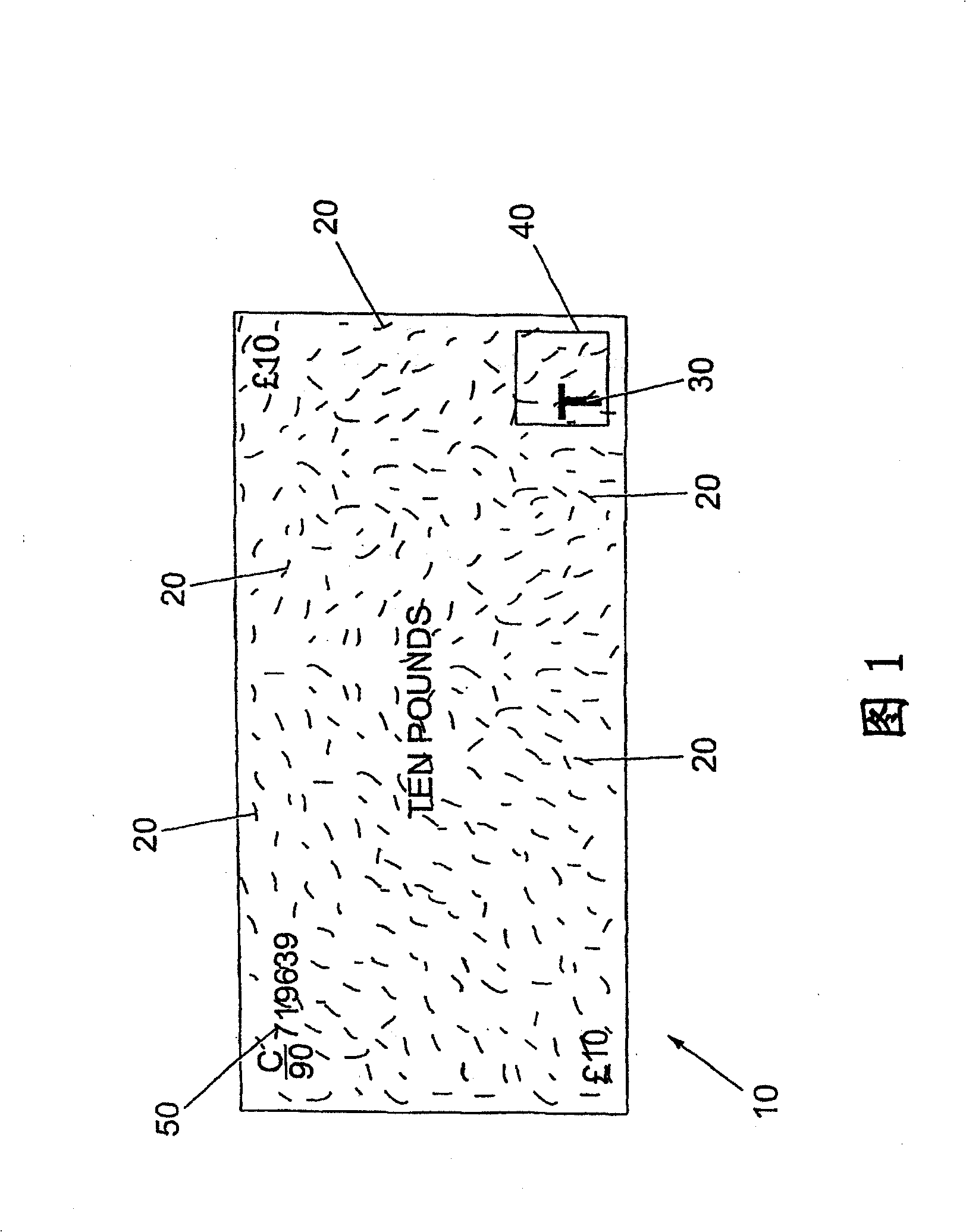
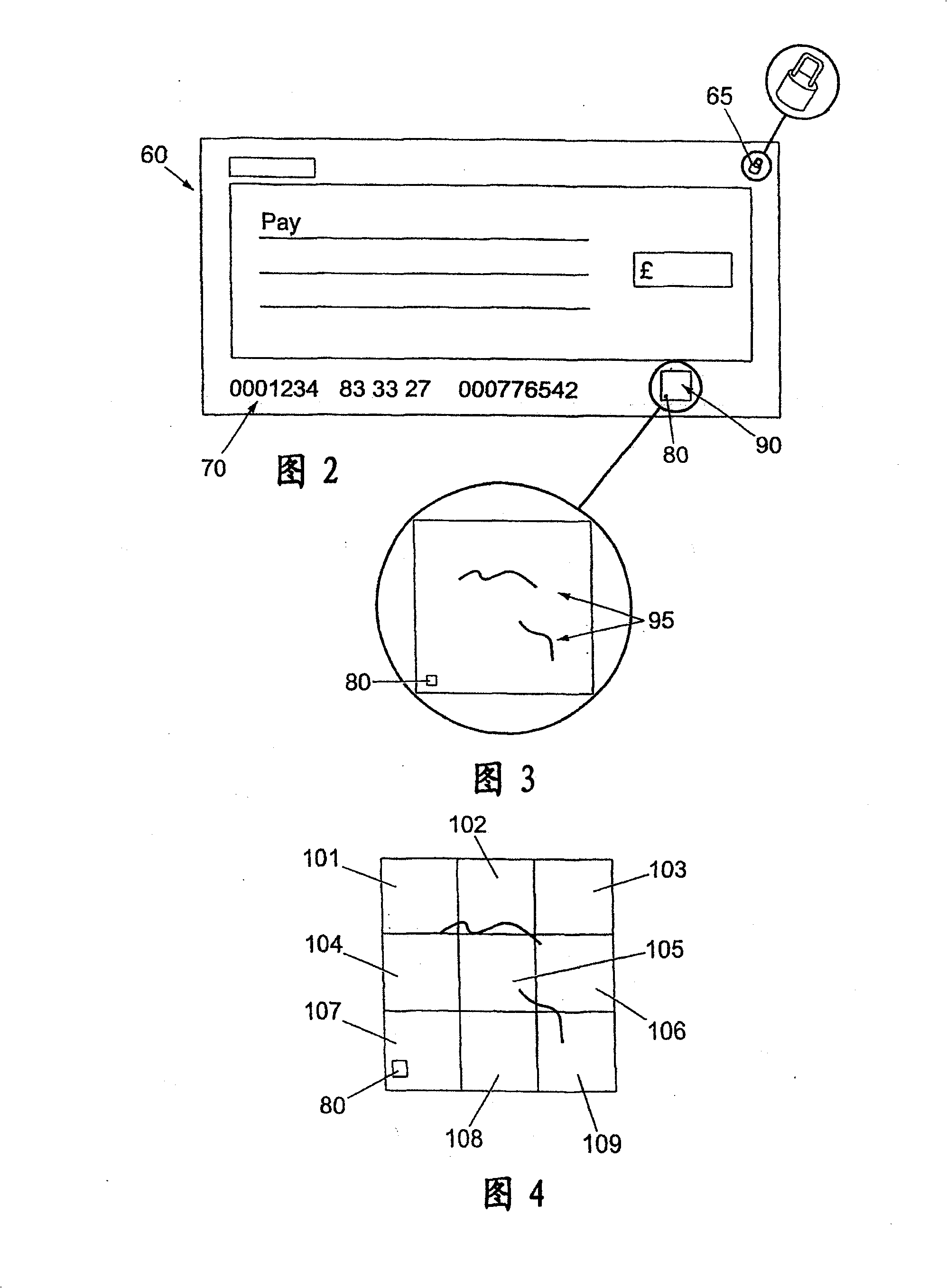
Apparatus and method for identifying an object having randomly distributed identification elements
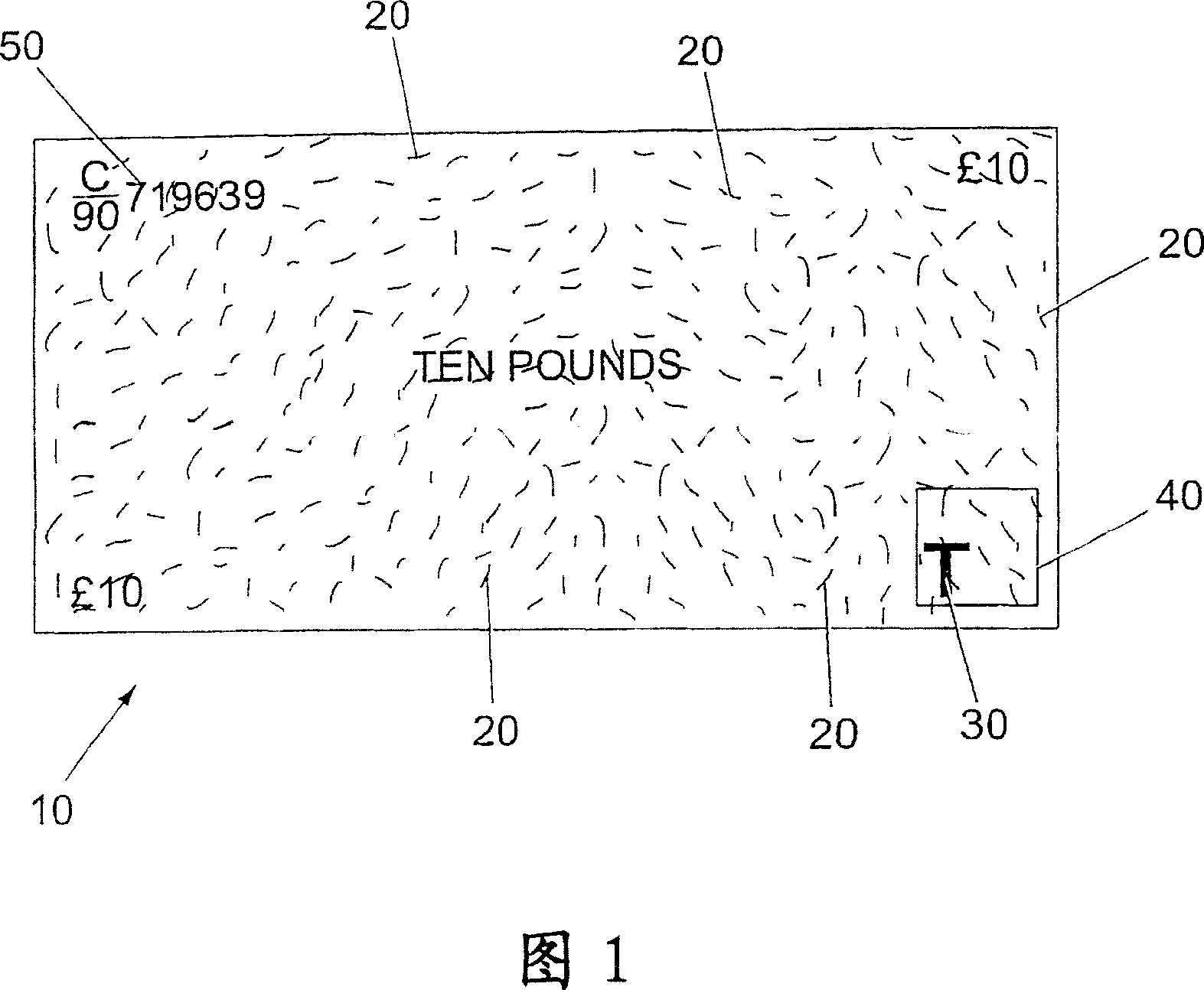
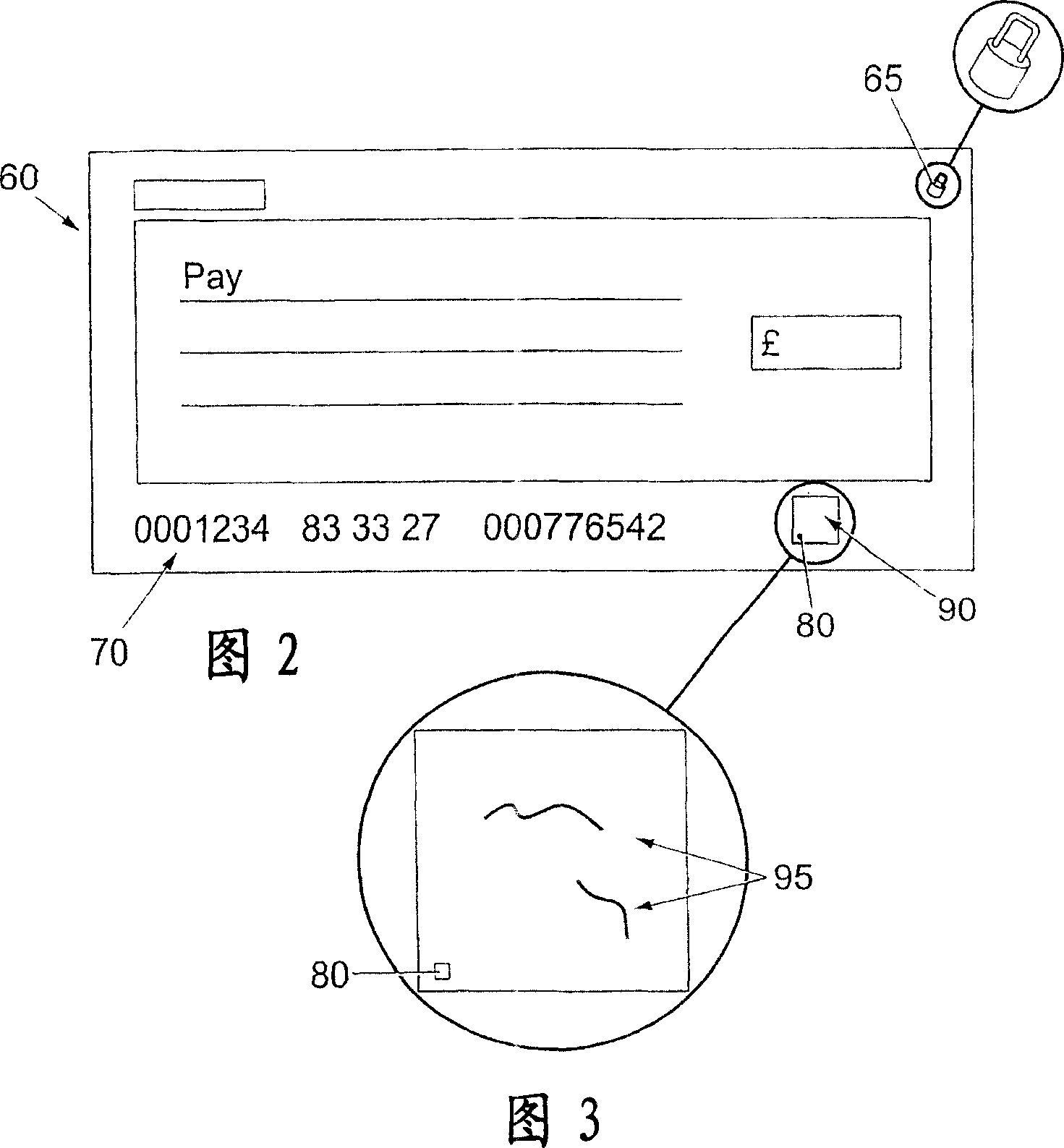
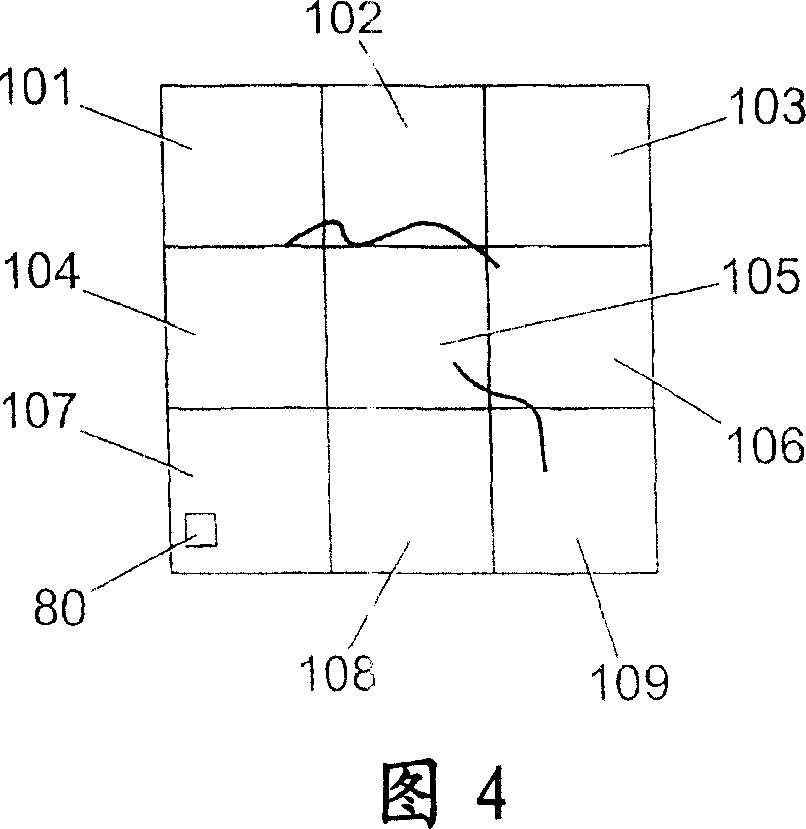
A method for verifying the authenticity of an object, e.g. a bank note or a cheque, is described. The object is provided with a primary identifier in the form of a plurality of identification elements embedded in the object. The identification elements are visually detectable when illuminated by infrared or ultraviolet electromagnetic radiation but are visually indistinguishable from the rest of the object when illuminated with visible light. The object has a reference point in the form of a printed symbol defining an area of the object in which at least some of the identification elements are provided. The method includes the step of identifying a sub-area of the object defined by the reference point, and recording information relating to the positions of the identification elements in the sub-area relative to the reference point. A detector that can be used to carry out this method is also described.
Owner:TULLIS RUSSELL PAPERMAKERS
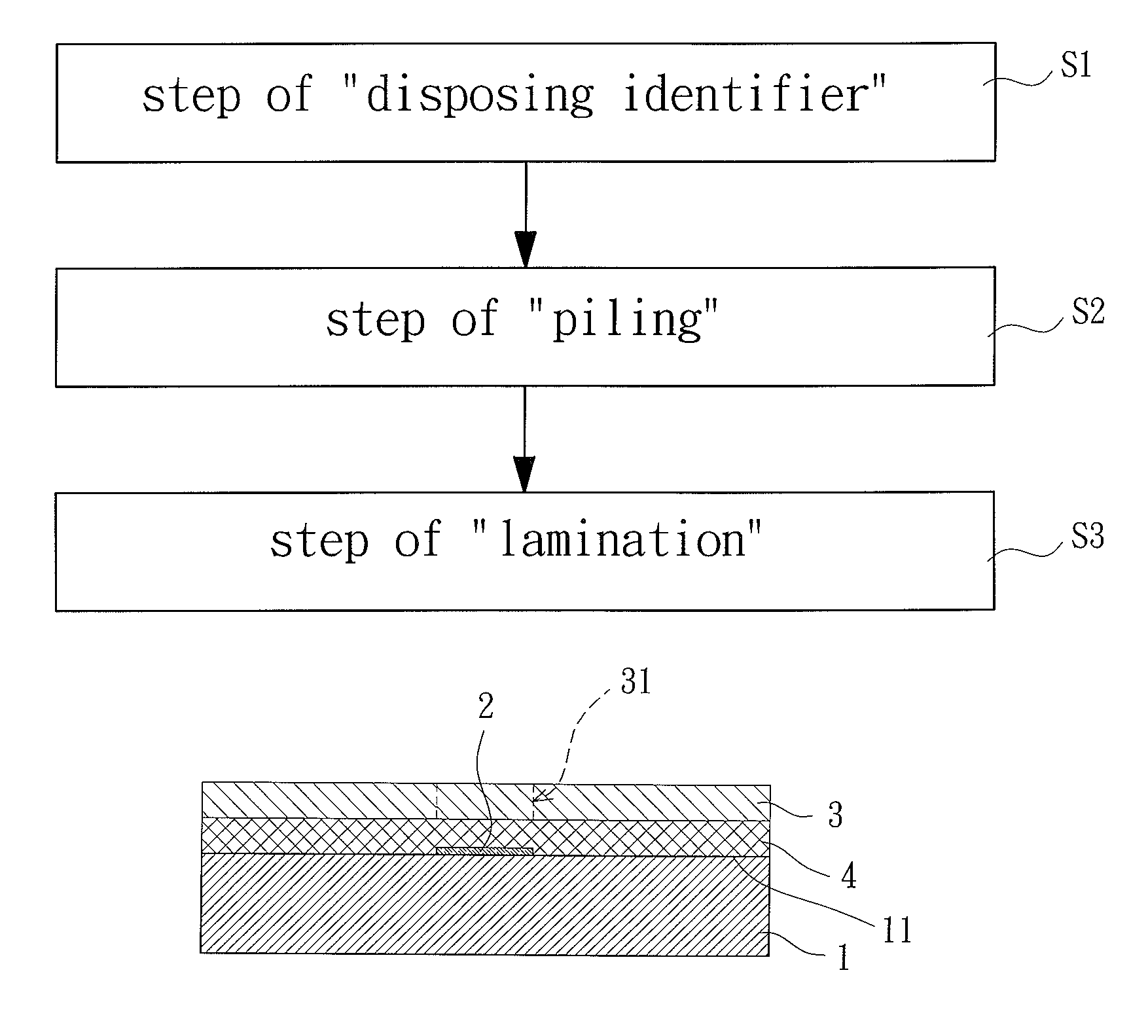
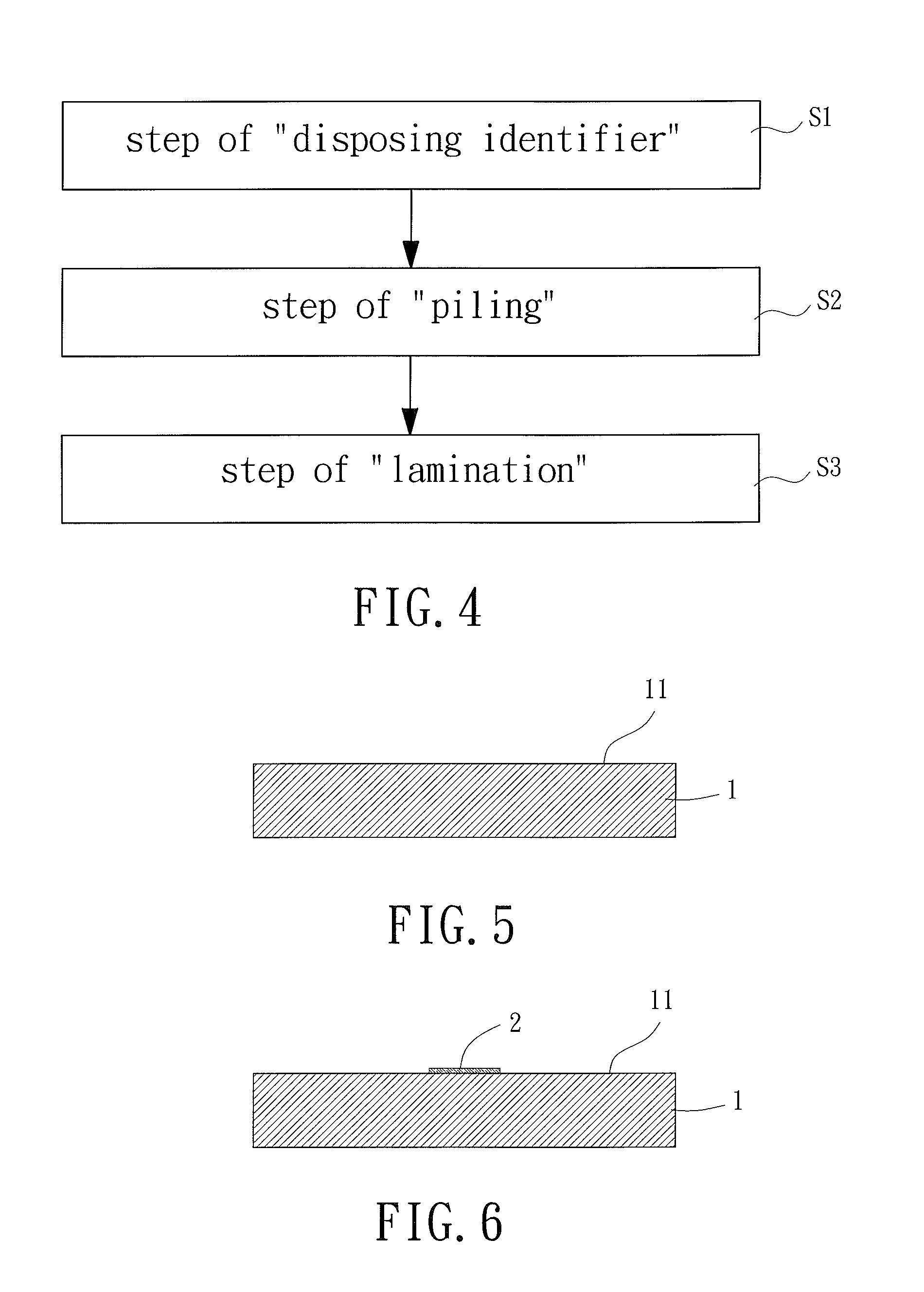
Manufacturing Method of Identifiable Print Circuit Board
ActiveUS20110265321A1Effective monitoringElectrical connection printed elementsElectrical apparatus contructional detailsPrimary IdentifierEngineering
Owner:WUS PRINTED CIRCUIT
Identifying a potential ddos attack using statistical analysis
Embodiments can identify requests that may be tied to a DDOS attack. For example, the primary identifiers (e.g., a source address) of requests for a network resource (e.g., an entire website or a particular element of the website) can be tracked. In one embodiment, a statistical analysis of how often a particular source address (or other primary identifier) normally makes a request can be used to identify source addresses that make substantially more requests. A normal amount can correspond to an average number of request that a source address makes. According to some embodiments, a system can use statistical analysis methods on various request data in web server logs to identify potential attacks and send data concerned potential attacks to an HBA system for further analysis.
Owner:LEVEL 3 COMM LLC
Real-time creation method for virtual channel link of avionics system
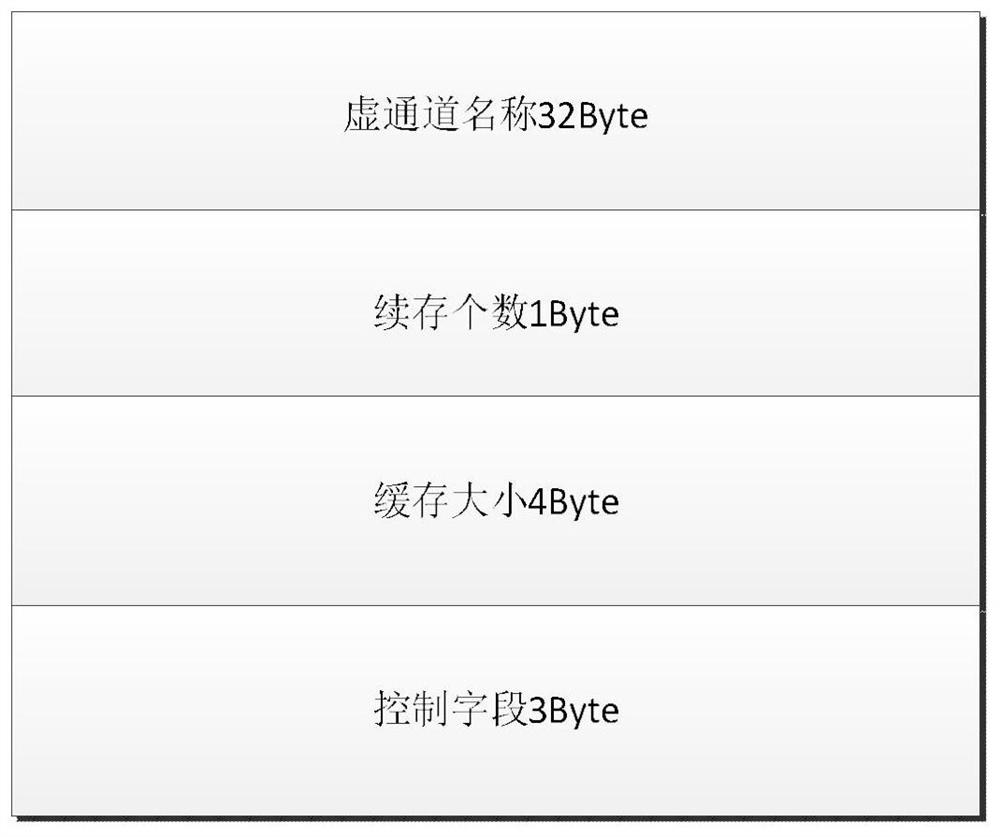
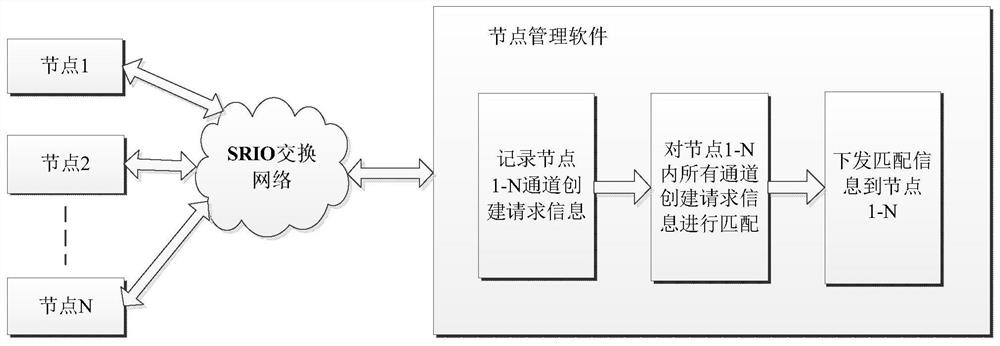
ActiveCN111600810AImprove real-time performanceSave human effortData switching networksElectric digital data processingComputer networkPrimary Identifier
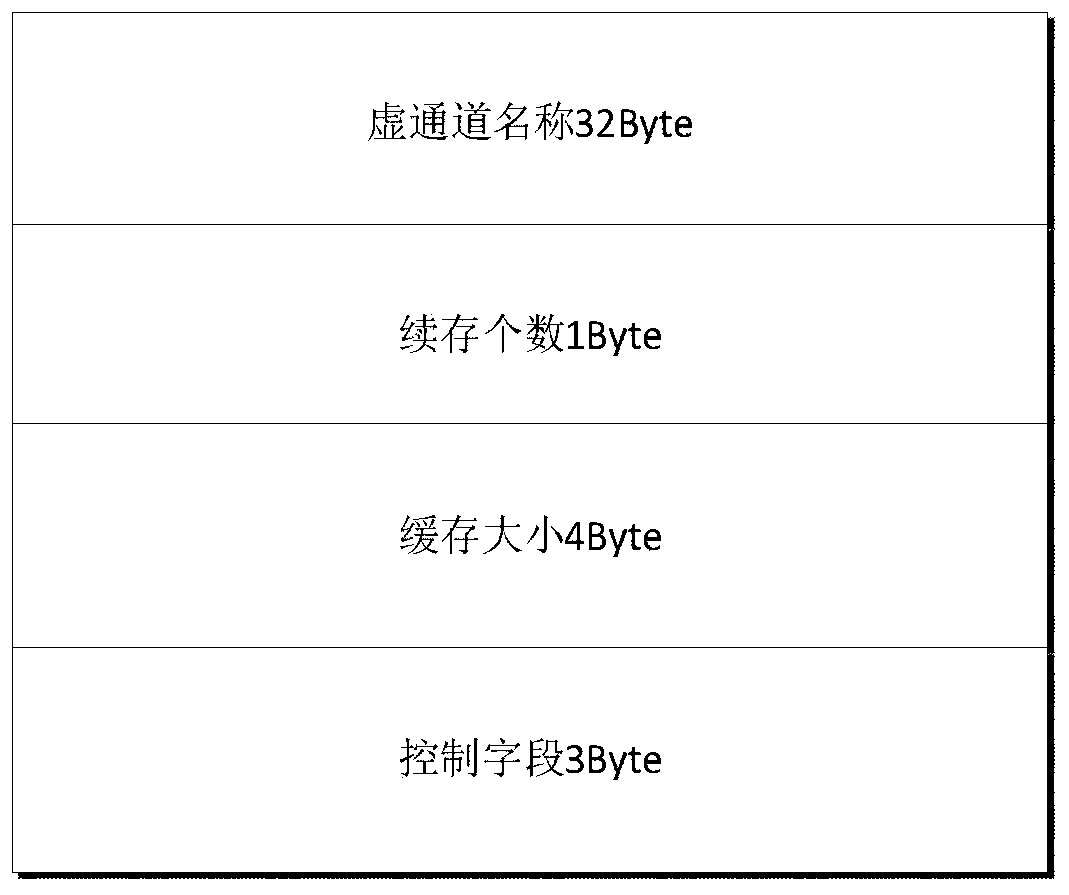
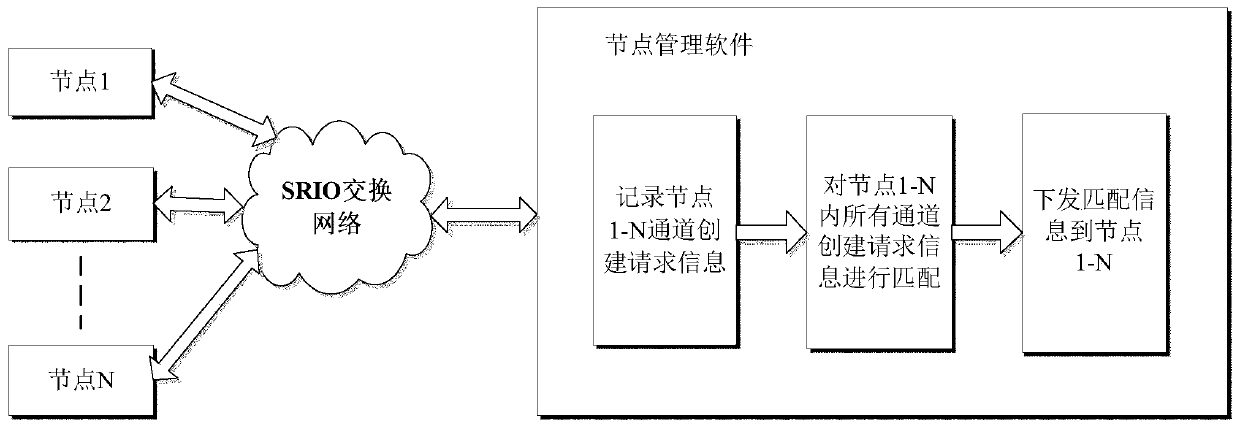
The invention discloses a real-time creation method for a virtual channel link of an avionics system, and aims to provide a virtual channel link creation method which is simple, reliable, rapid, flexible and low in complexity. The invention is realized through the following technical scheme: the method comprises the following steps: based on a high-speed serial RapidIO bus, sending a virtual channel link creation request to node management software, taking a channel name as a primary identifier of a virtual channel link between the nodes of the two communication parties, and injecting the virtual channel name and virtual channel related parameters of the nodes of the two communication parties through an external micro control unit (MCU) or each communication node debugging interface; then,after the node management software stores the virtual channel creation request information initiated by each communication node, matching the consistency of the related parameters of the receiving party and the transmitting party; and according to a consistency judgment result, issuing the virtual channel related configuration information to the related communication nodes, waiting for each related node to return an acknowledgement character ACK signal, and determining whether virtual channel link creation work is completed or not.
Owner:10TH RES INST OF CETC
Manufacturing method of identifiable print circuit board
ActiveUS8595925B2Electrical connection printed elementsElectrical apparatus contructional detailsPrimary IdentifierElectrical and Electronics engineering
Owner:WUS PRINTED CIRCUIT
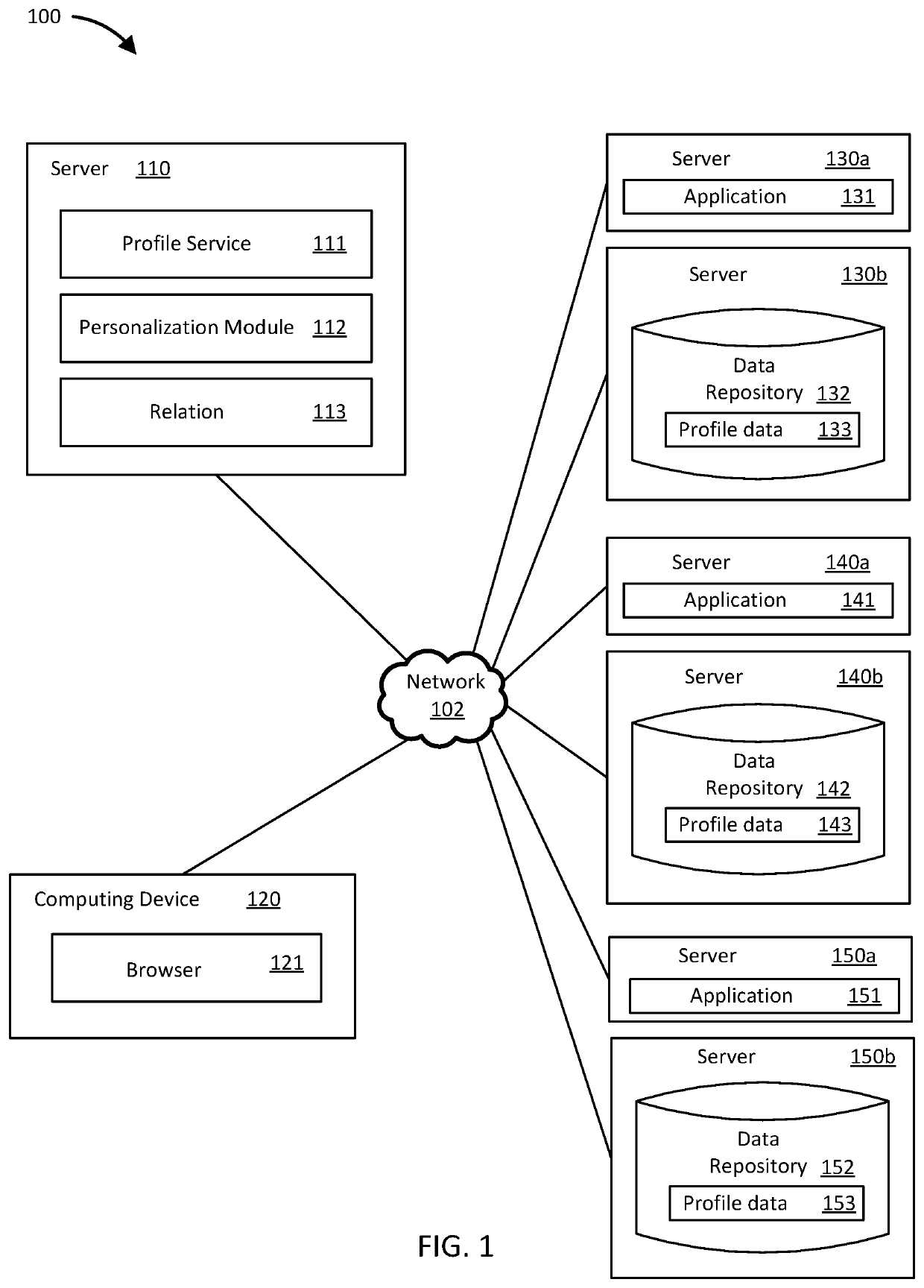
System for data consolidation across disparate namespaces
PendingUS20210037086A1Public key for secure communicationUser identity/authority verificationData packRelational system
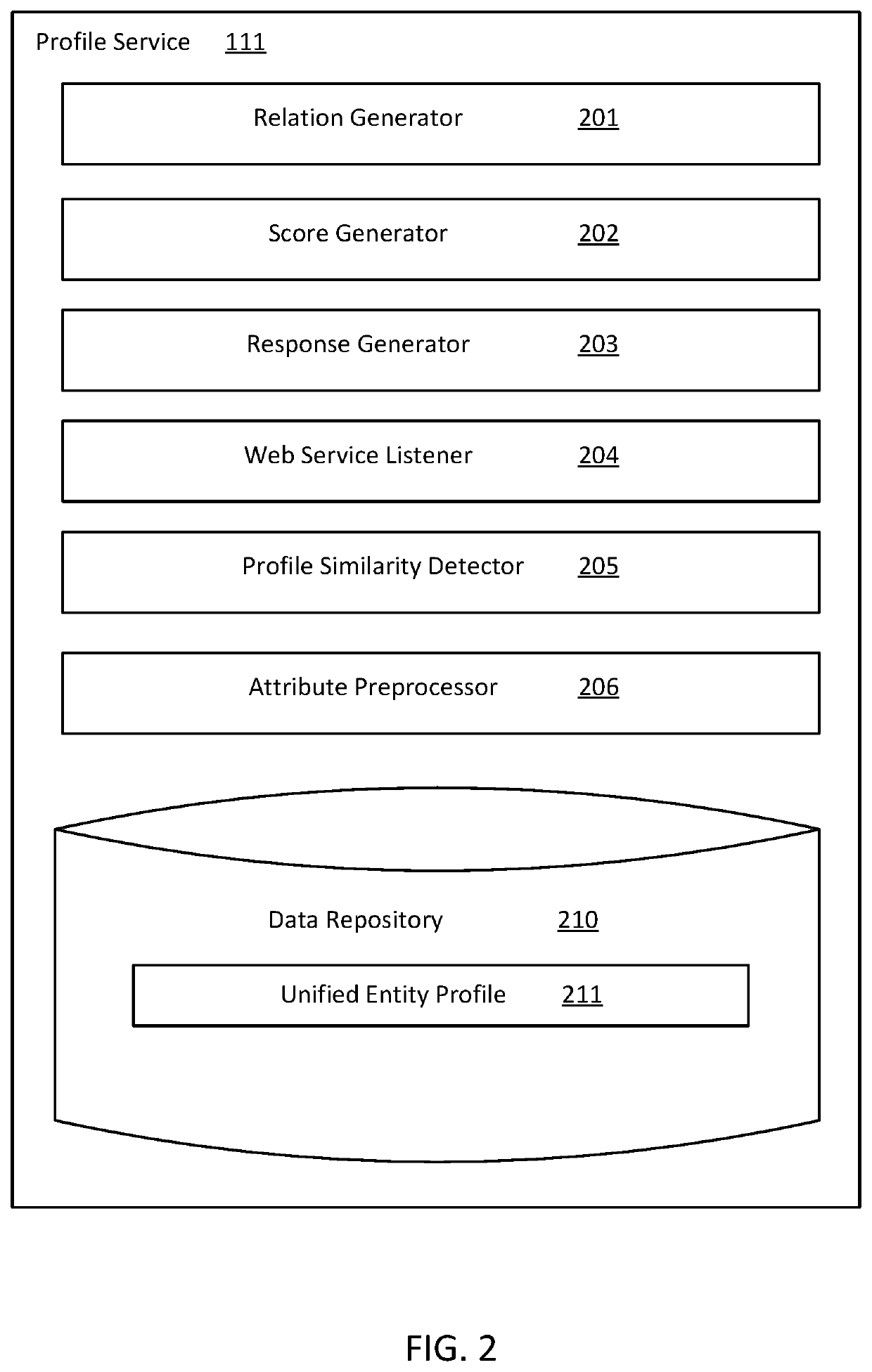
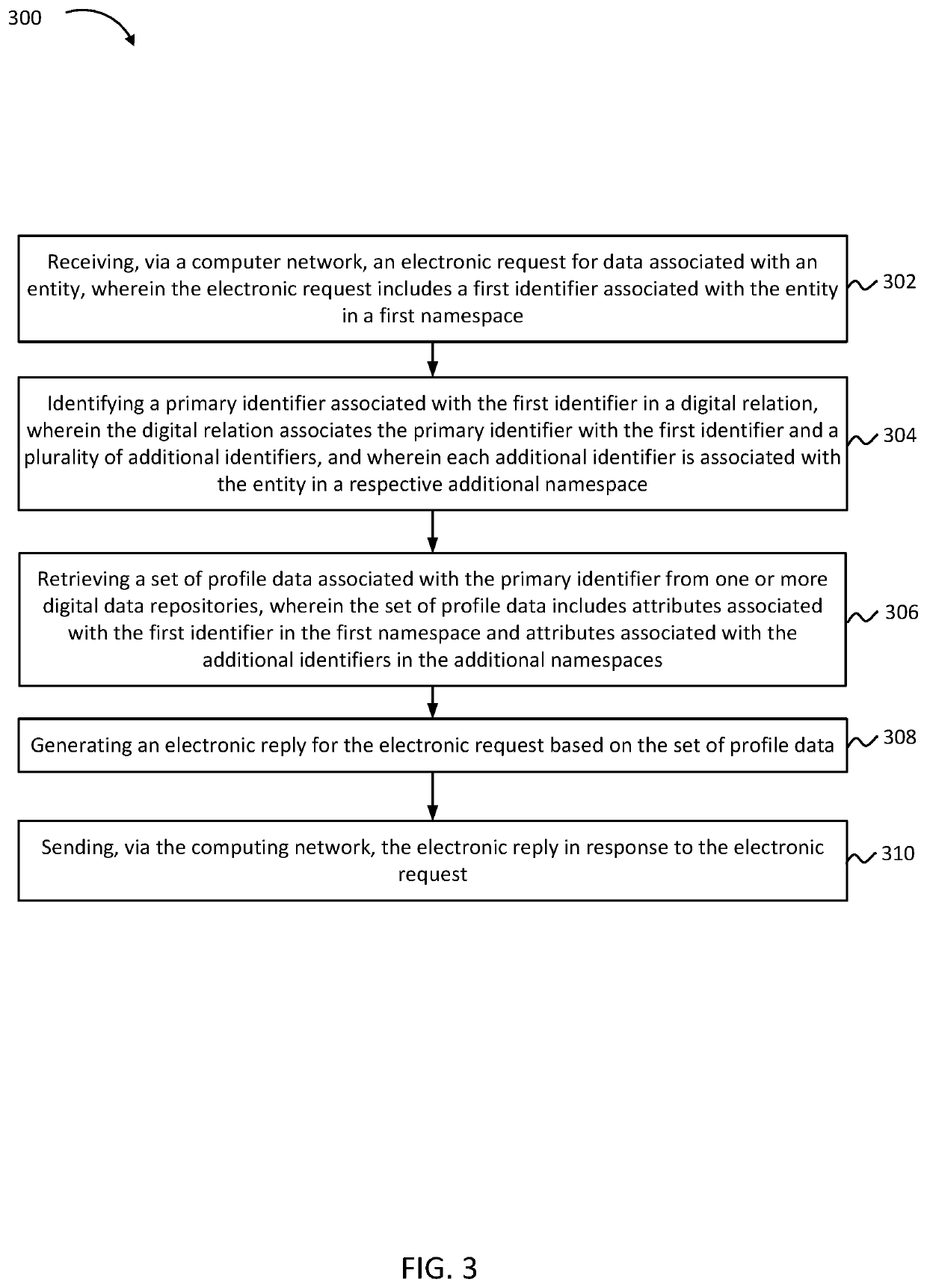
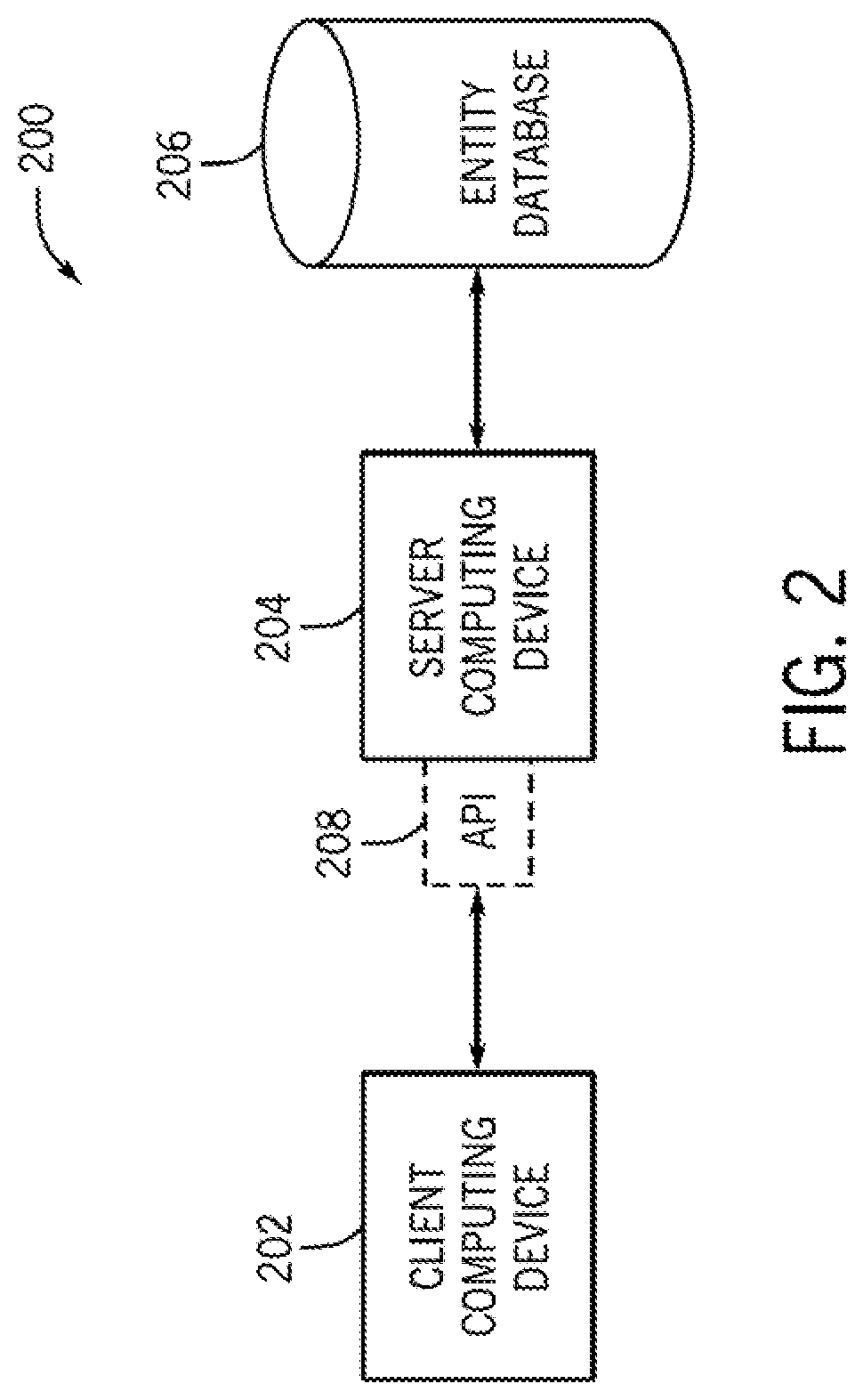
Embodiments presented herein provide systems and methods for unifying data that is stored in disparate namespaces. A system described herein receives an electronic request for data associated with an entity. The electronic request includes a first identifier of the entity in a first namespace. The system includes a digital relation that maps the first identifier to a primary identifier. The system determines additional identifiers that map to the primary identifier in the relation. The additional identifiers are associated with the entity in respective additional namespaces. The system retrieves a consolidated set of profile data associated with the primary identifier, including attributes of the entity within the first namespace and attributes of the entity within the additional namespaces. The system generates an electronic response to the electronic request based on the consolidated set of profile data and sends the response to an application that submitted the electronic request.
Owner:INTUIT INC
System and method for associating multiple logins to a single record in a database
ActiveUS20200401721A1Resolve ambiguityDatabase updatingDigital data protectionPrimary IdentifierMatch algorithms
A method for resolving ambiguity in computer data includes processing a record creation request transmitted from a computing device. The record creation request includes entity creation data and a login key. The login key includes a primary identifier and a password. The method also includes executing a matching algorithm with a selectable combination of the entity creation data at an entity database to identify a single entity record matching a selectable combination of the record creation request. The single entity record is linked to multiple different login keys. The method also includes updating one or more attributes of the single entity record with the entity creation data. Further, the method includes storing session data created during a session associated with the login key by using the login key to segregate the session data in the entity database, and linking the session data to the single entity record.
Owner:MAIN SEQUENCE TECH INC
Real-time creation method of virtual channel link in avionics system
ActiveCN111600810BImprove real-time performanceSave human effortData switching networksElectric digital data processingComputer networkPrimary Identifier
Owner:10TH RES INST OF CETC
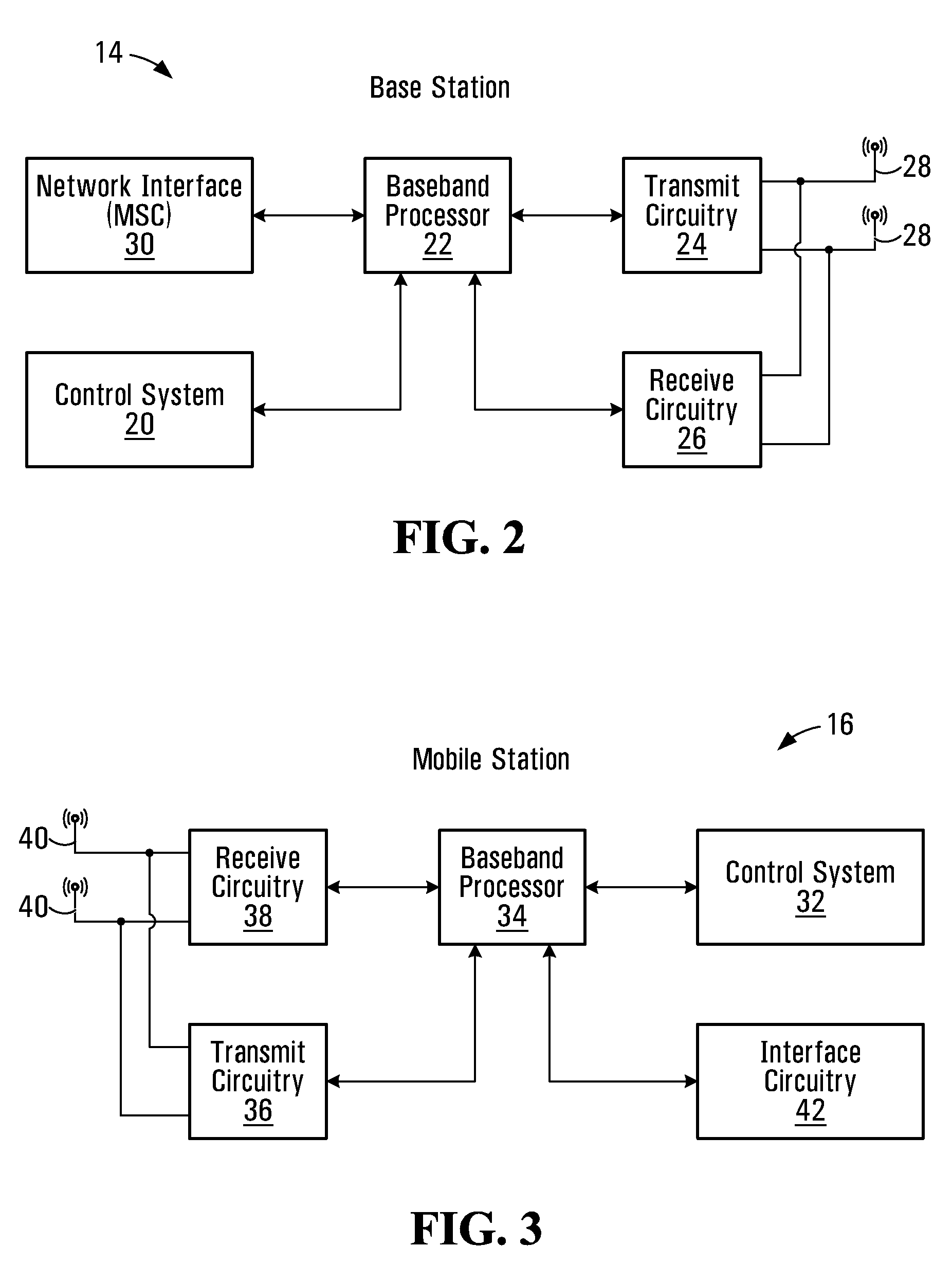
Method for channel information feedback, basestation device and mobile station device
There is disclosed a method for feedback of channel information characterizing a wireless transmission between a base station and a mobile station over a communications channel. The method involves: receiving a primary identifier identifying a cluster associated with a channel response generated by a mobile station; receiving a differential identifier identifying channel response member within the cluster identified by the primary identifier; locating in a codebook of predetermined channel responses a predetermined channel response identified by said primary identifier and said differential identifier, the predetermined channel responses in the codebook being grouped in a plurality of clusters in accordance with a correlation criterion, each cluster including a plurality of predetermined channel response members; and generating a control signal for controlling transmissions to the mobile station in accordance with said located predetermined channel response.
Owner:APPLE INC
Transaction application with a tokenized identifier
PendingUS20220012734A1Reduce power consumptionImprove battery lifeAcutation objectsFinancePrimary IdentifierEngineering
A Digital Transaction Processing Unit (DTPU) including a plurality of transaction applications operable for a digital transaction with a Digital Transaction Device (DTD), each of the plurality of transaction applications being associated with a tokenised primary identifier.
Owner:XARD GRP PTY LTD
Mobile phone provided with a secured identification system
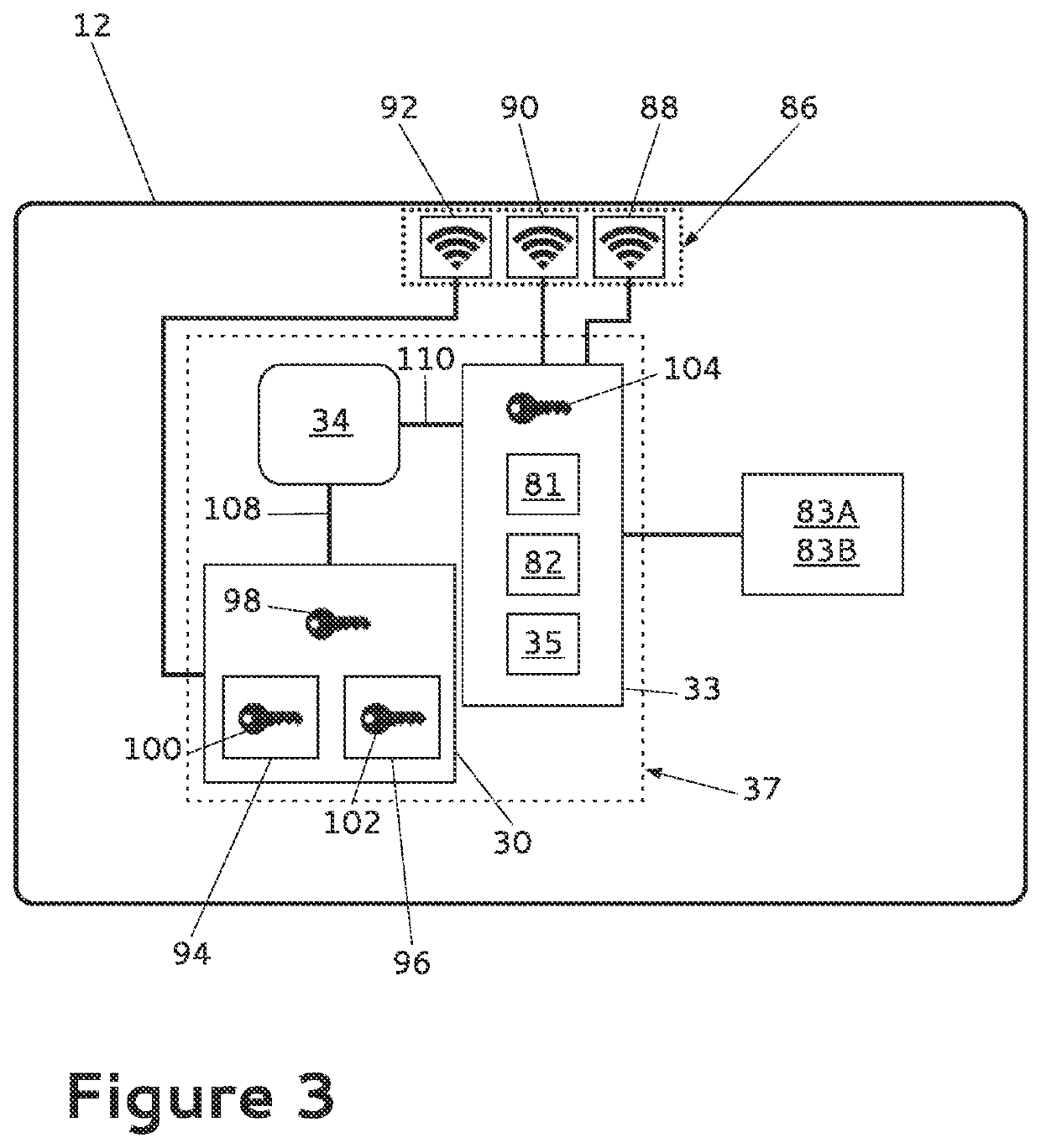
InactiveUS8666369B2Significant securingEasy to useUnauthorised/fraudulent call preventionEavesdropping prevention circuitsPrimary IdentifierUniform resource locator
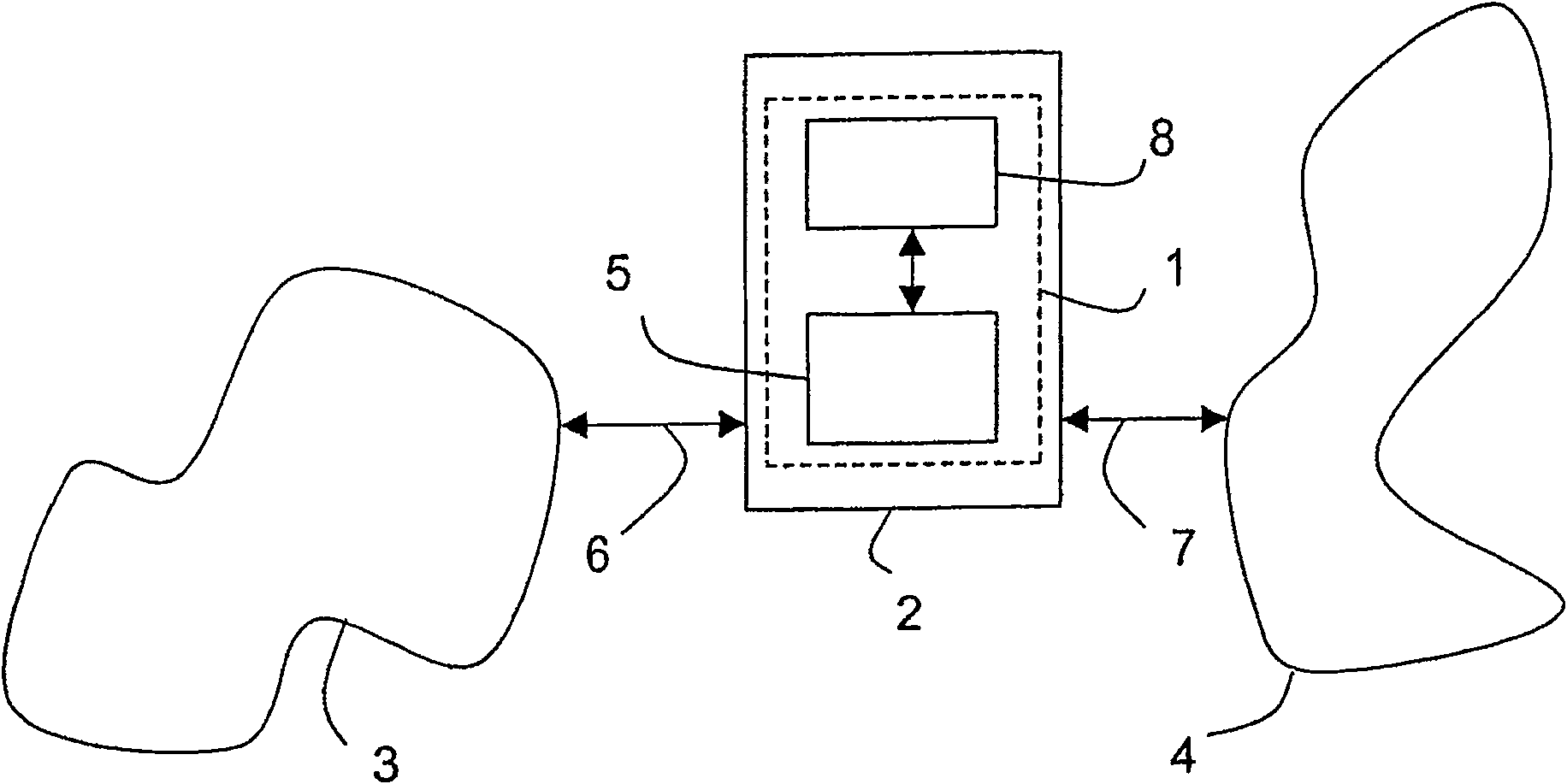
A mobile phone of the type including a connection, able to allow the connection to a webpage with a particular URL, the connection to said webpage requiring the entry of a particular identifier specific to said webpage, a first storage able to store, in a database, the particular identifiers, each associated with a corresponding webpage.The mobile phone also includes a trigger able to systematically and automatically trigger, after the entry of a particular identifier, the implementation of a selector for choosing a primary identifier shared by all webpages requiring that a particular identifier be entered, if no primary identifier has been chosen yet, and a second storage able to store a security datum depending on the primary identifier after the entry of the primary identifier.
Owner:MYRIAD GROUP
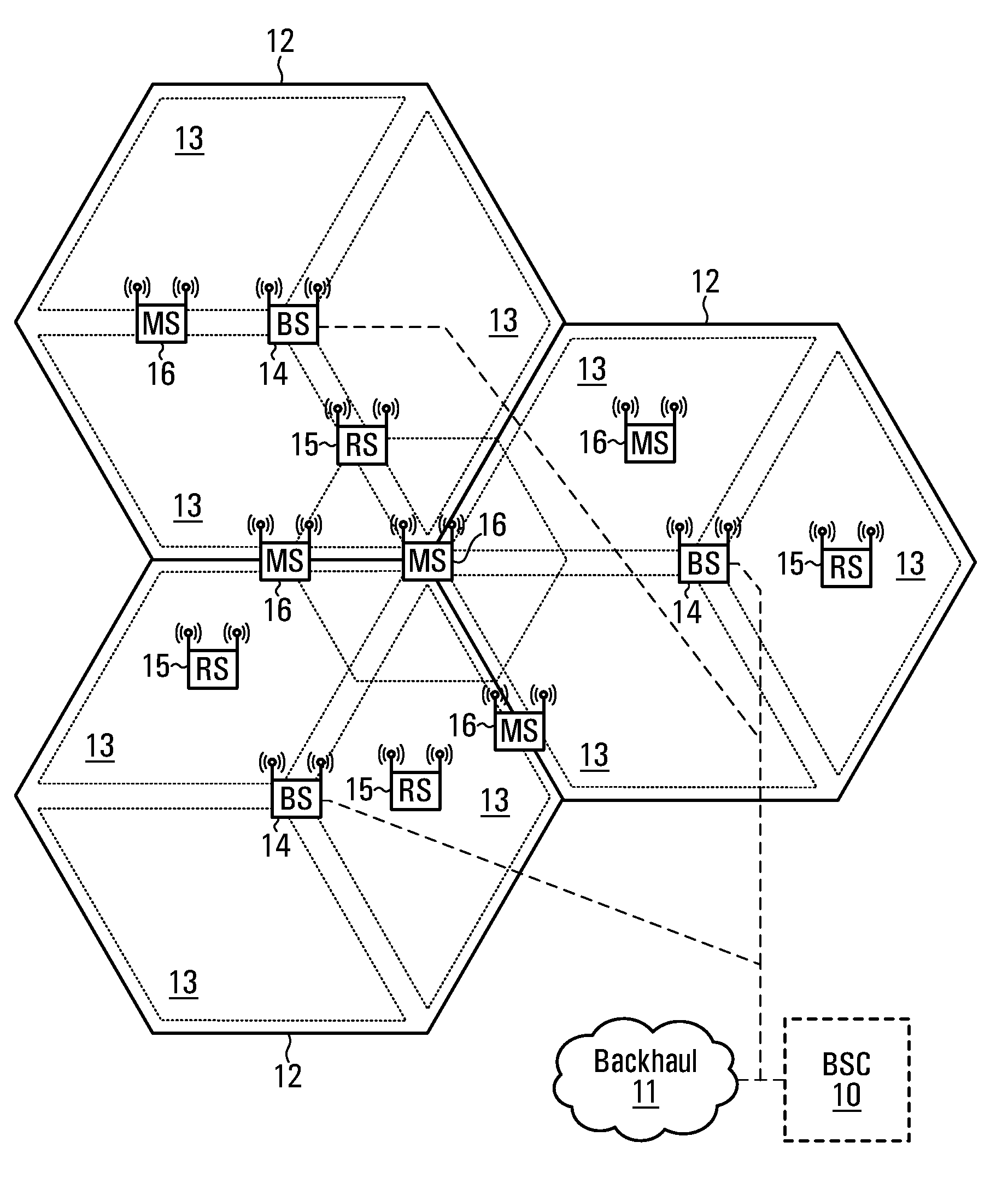
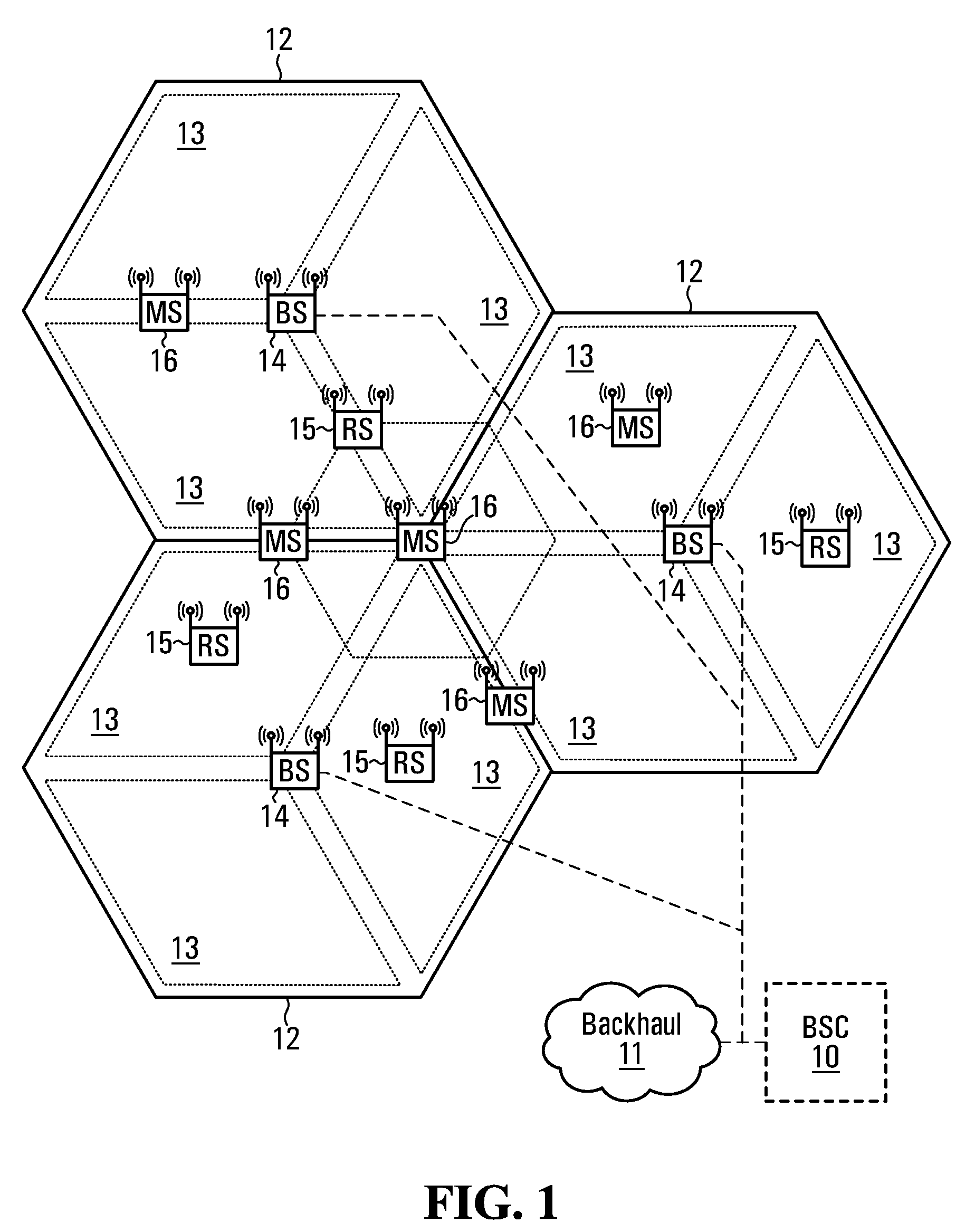
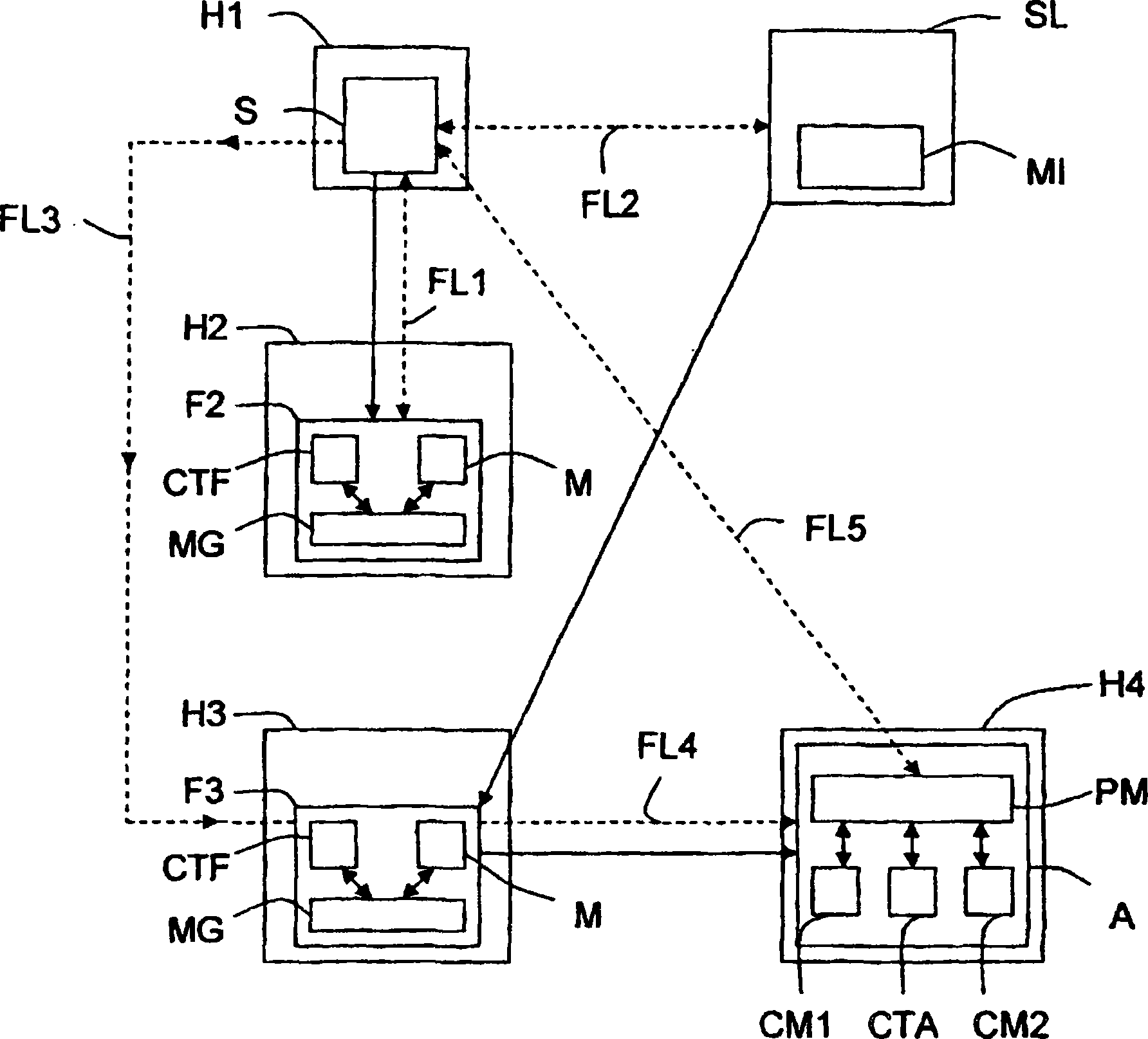
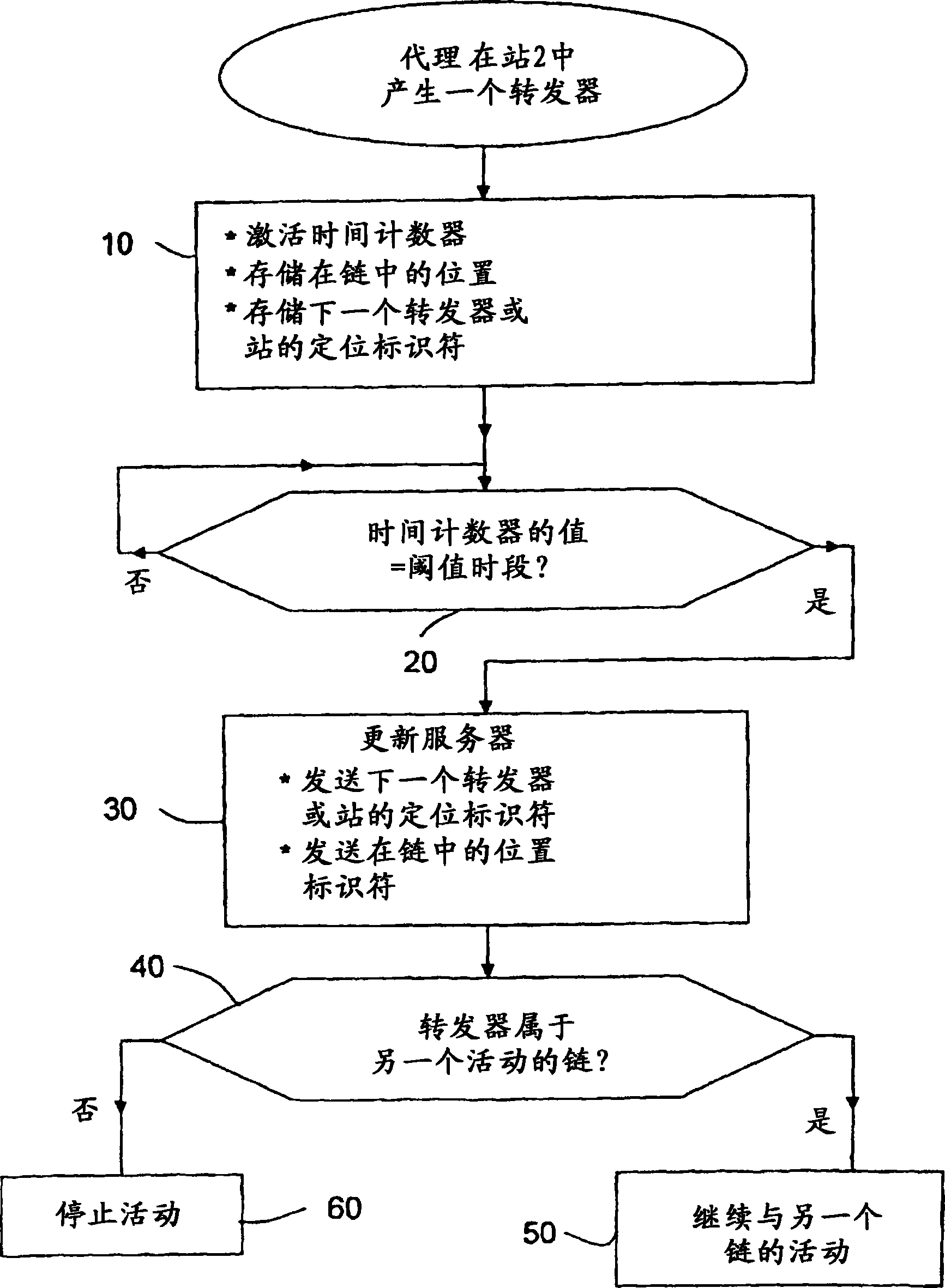
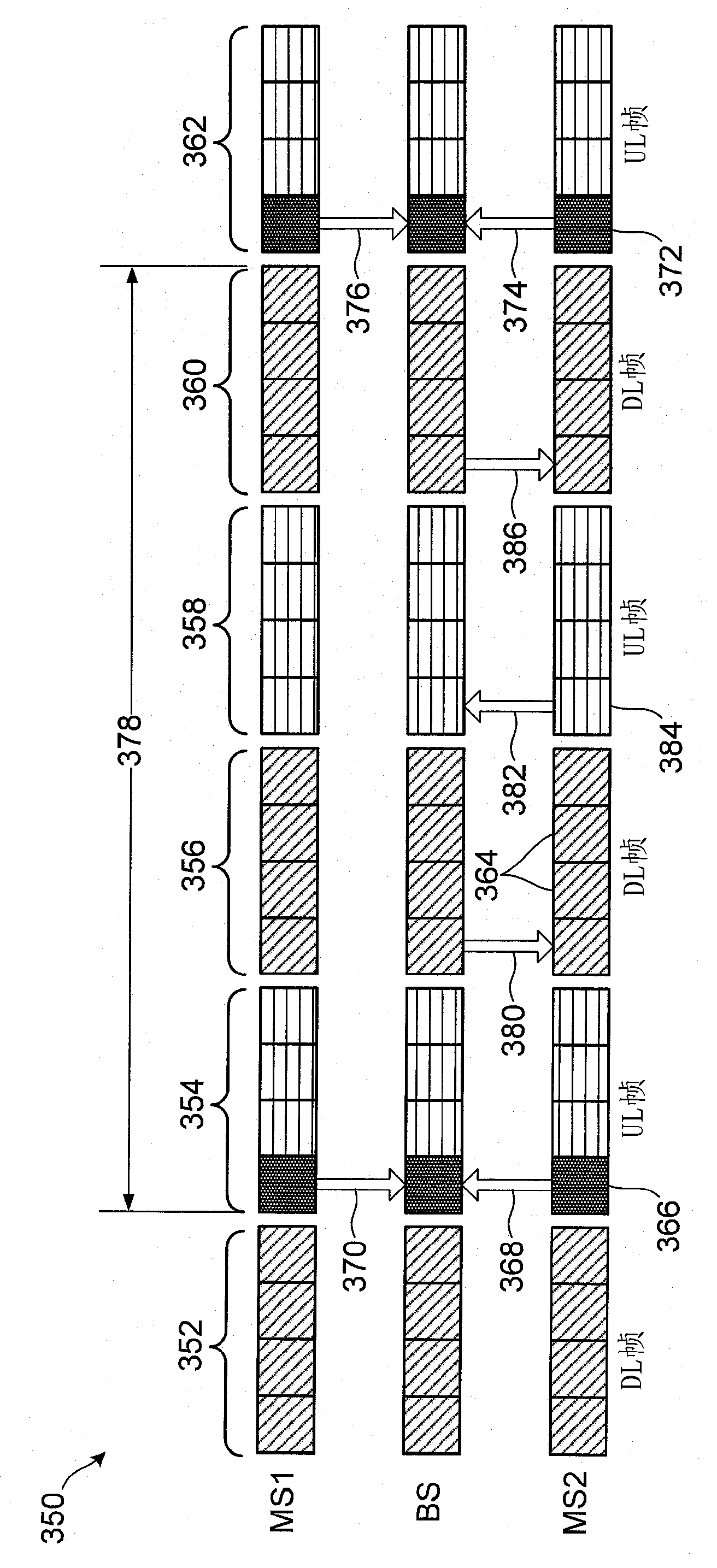
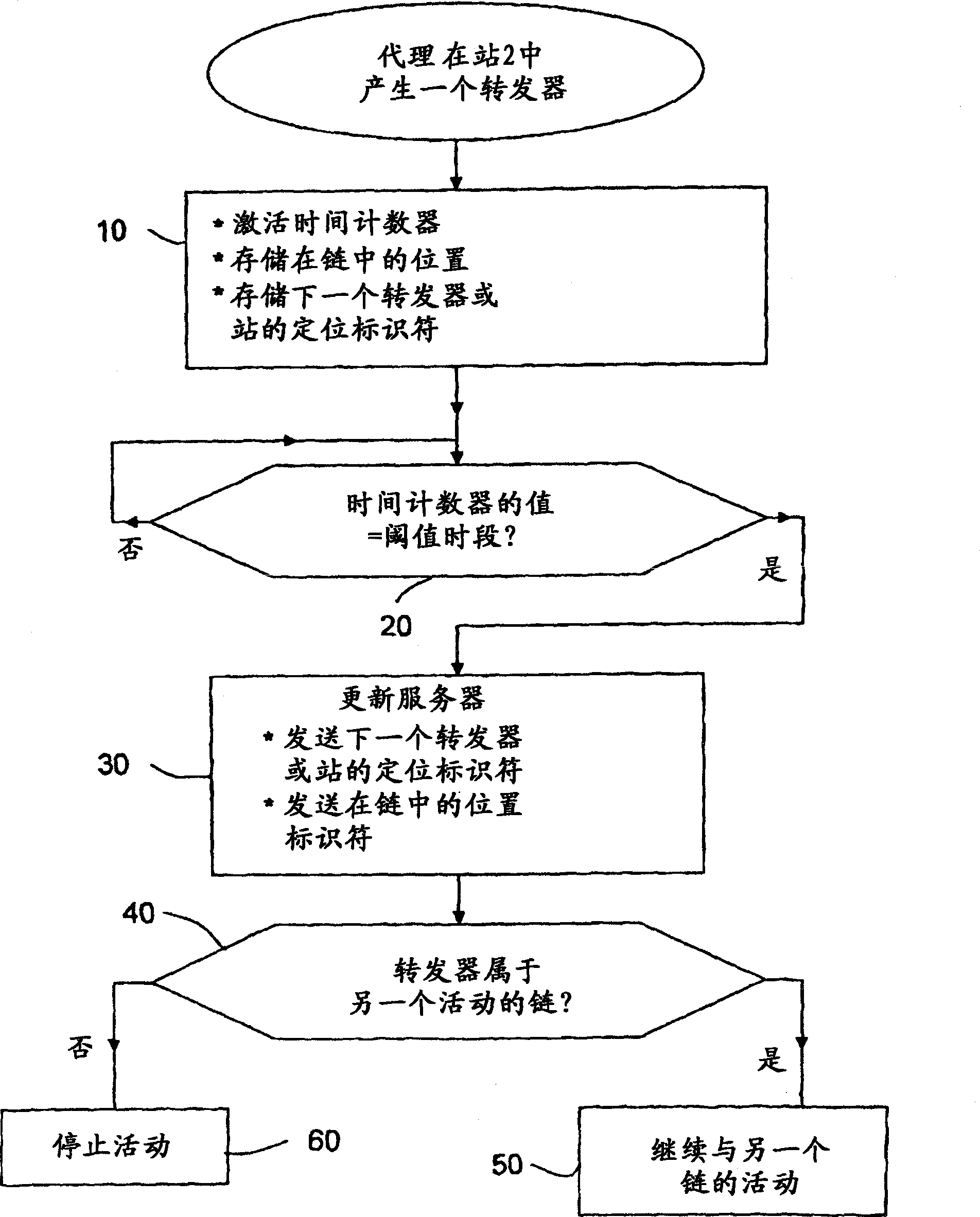
Method of locating mobile communicating objects within a communications network, comprising the transmission of location identifiers by repeaters and server updates
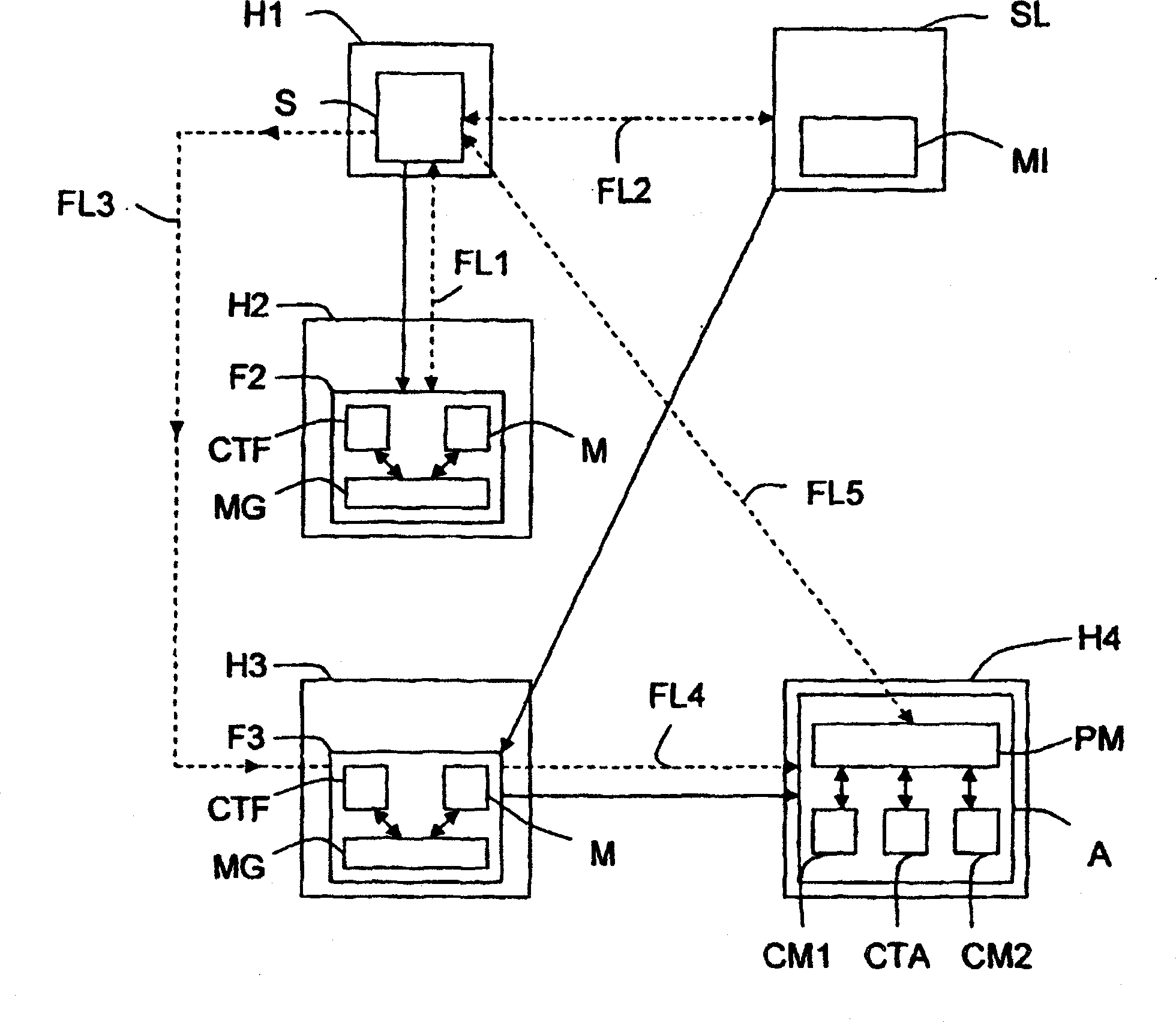
ActiveCN1868168AData switching by path configurationSecuring communicationPrimary IdentifierBroadcast communication network
The invention relates to a mobile communicating object (A) belonging to a communications network and comprising processing means (PM). According to the invention, when a communication has been established with another communicating object (S) belonging to the network, the aforementioned processing means generate a repeater (Fi) at each site (Hi) through which they pass. Moreover, when the repeater is generated, the processing means associate a timing counter (CTF) therewith and configure said repeater such that: (i) it can store an identifier that is representative of the location of the next repeater (F(i+1)) or site (H(i+l)) in the chain of repeaters to which it belongs; and (ii) at the end of a selected duration of time, it transmits the location identifier of the next repeater (F(i+1)) or site (S(i+l)) to at least one location server (SL) in the network, so that it stores said identifier together with the primary identifier of the mobile object (A). Preferably, once a repeater has addressed the location identifier, the relay activity thereof is terminated and, if the repeater does not belong to another chain, it is removed so that it no longer consumes resources.
Owner:INRIA NATIONAL INSTITUTE FOR RESEARCH IN COMPUTER SCIENCE AND CONTROL +1
Method of providing primary identity of a base station and associated wireless terminal and base station
Methods may be provided for operating a wireless terminal (UE) in a wireless communication network. In response to receiving the request for the primary identity of the wireless terminal's non-serving base station, a transmission to the wireless terminal's non-serving base station may be initiated using a random access channel RACH configuration (1505). A random access response RAR may be received (1507) from the non-serving base station. Additionally, the random access response can be received with the primary identity of the non-serving base station, and the random access response can be in response to transmission using a RACH configuration. The primary identity of the non-serving base station may be sent (1509) to nodes in the wireless communication network other than the non-serving base station.
Owner:TELEFON AB LM ERICSSON (PUBL)
Mobile phone provided with a secured identification system
InactiveUS20120164977A1Significant securingEasy to useUnauthorised/fraudulent call preventionEavesdropping prevention circuitsPrimary IdentifierUniform resource locator
A mobile phone of the type including a connection, able to allow the connection to a webpage with a particular URL, the connection to said webpage requiring the entry of a particular identifier specific to said webpage, a first storage able to store, in a database, the particular identifiers, each associated with a corresponding webpage.The mobile phone also includes a trigger able to systematically and automatically trigger, after the entry of a particular identifier, the implementation of a selector for choosing a primary identifier shared by all webpages requiring that a particular identifier be entered, if no primary identifier has been chosen yet, and a second storage able to store a security datum depending on the primary identifier after the entry of the primary identifier.
Owner:MYRIAD GROUP
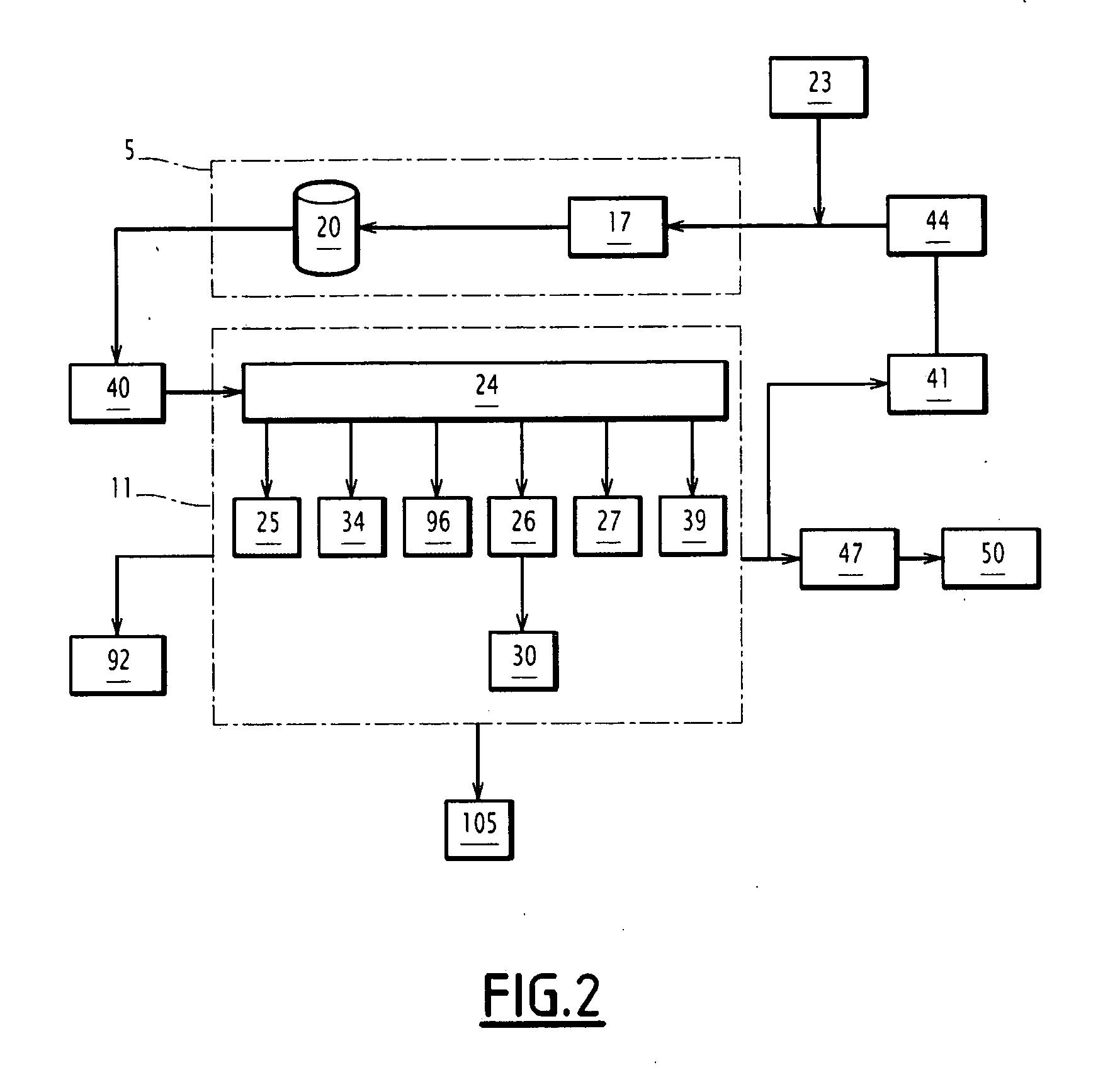
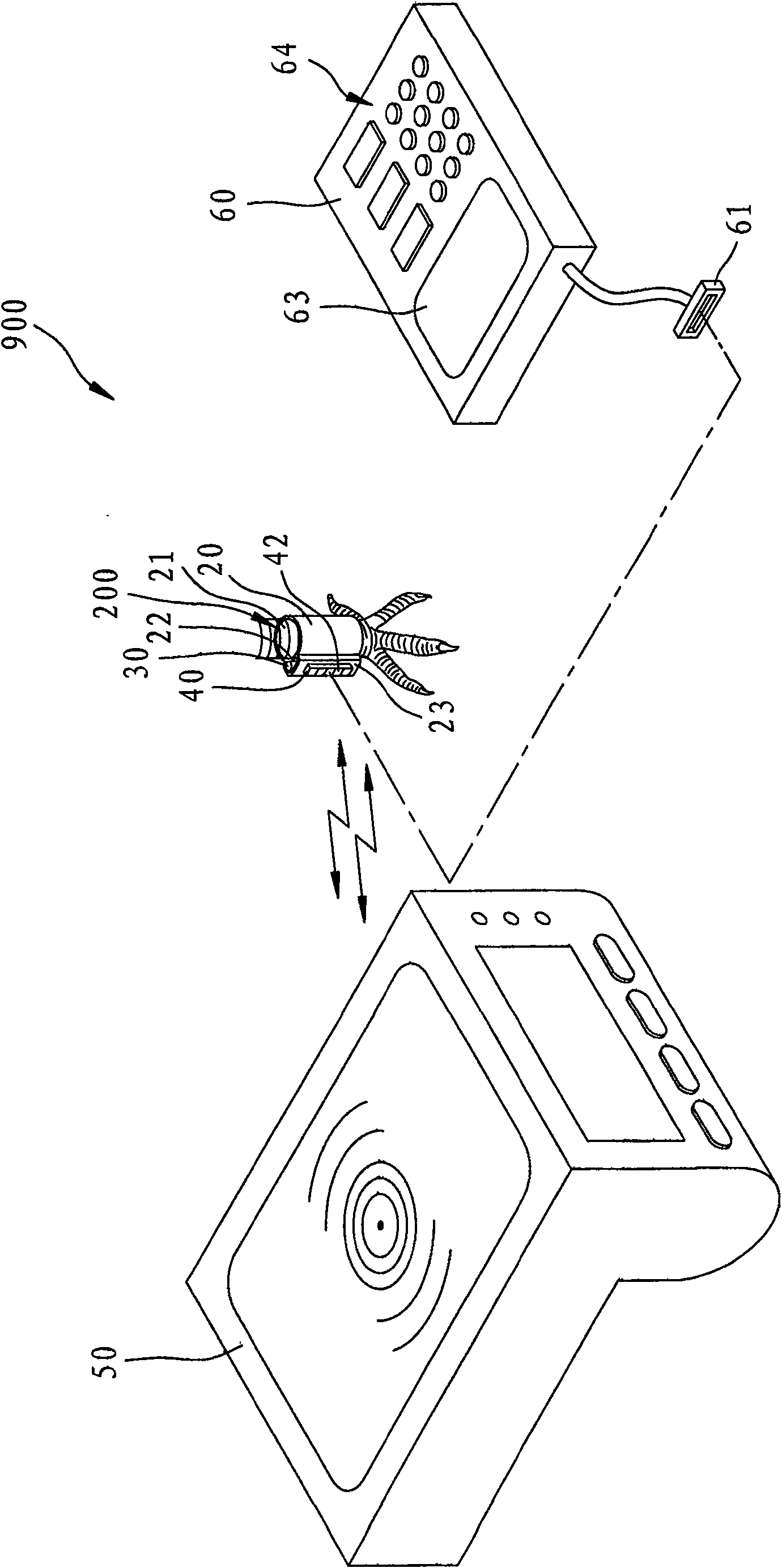
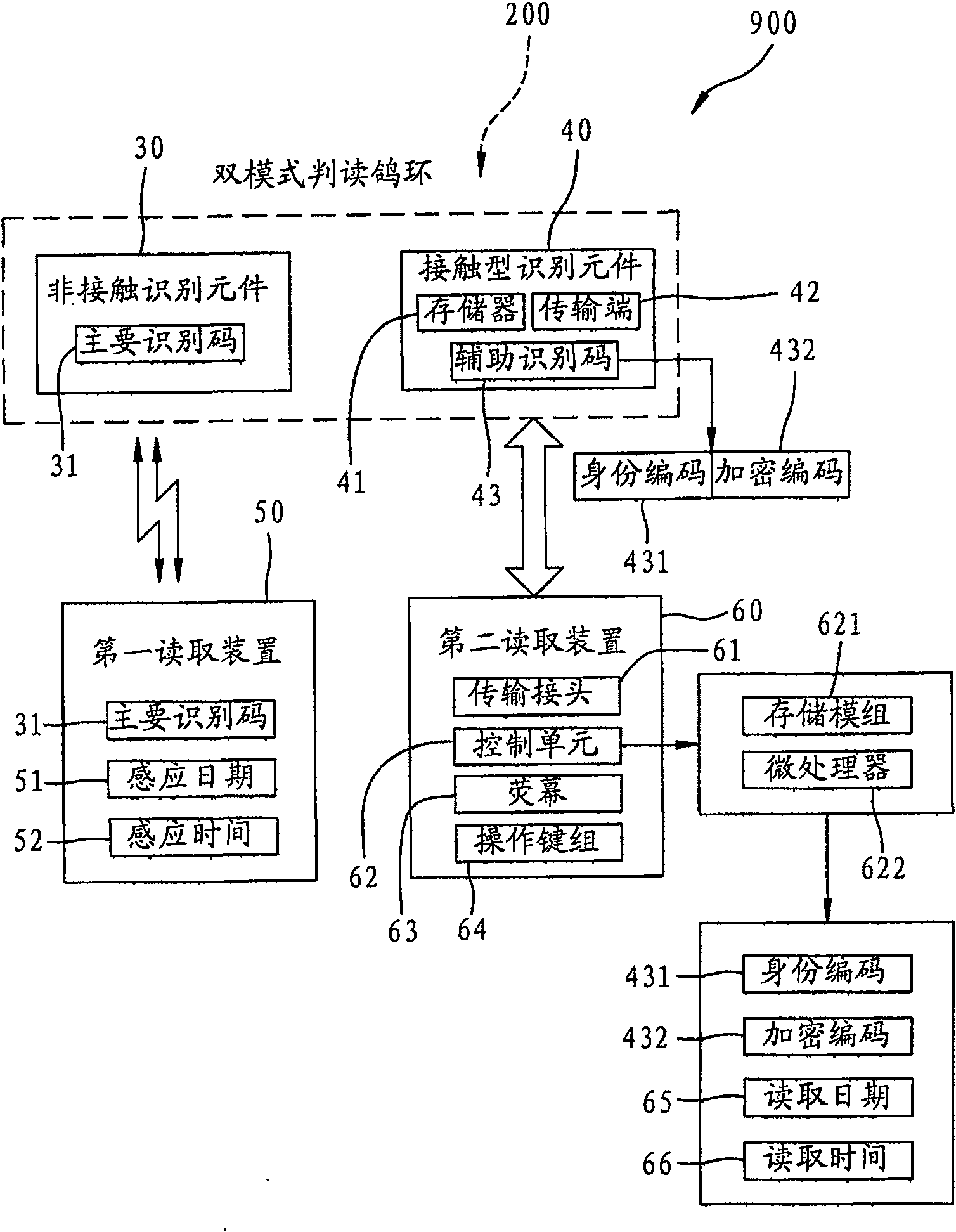
Double-mode interpretation pigeon loop and double-mode identification system of race pigeon
InactiveCN100562891CAvoid return time situationsMake up for the lack of knowing the identity of the pigeonSensing record carriersRecord carriers used with machinesPrimary IdentifierProject Pigeon
The invention relates to a dual-mode interpretation and identification system for pigeon rings and racing pigeons. The dual-mode reading pigeon ring is intended to be attached to a pigeon to provide identification of the pigeon, and includes a non-contact identification element with a primary identification code built in, and a contact with a secondary identification code built-in Type identification element. The system also includes a first reading device and a second reading device. The first reading device reads the primary identification code through a non-contact induction method. The second reading device reads and updates the auxiliary identification code by contacting and connecting with the contact identification element, and encrypts the encoded content. In this way, the owner can judge the identity of the pigeon through the double identification method of non-contact and contact, thereby improving the accuracy, uniqueness and security of judging the identity of the pigeon.
Owner:黄廷彰
Codebook restructure, differential encoding/decoding, and scheduling
A method and apparatus for feedback of channel information characterizing a wireless transmission between a base station and a mobile station over a communications channel. The method involves, at the base station, receiving a primary identifier identifying a cluster associated with a channel response generated by a mobile station, receiving a differential identifier identifying channel response member within the cluster identified by the primary identifier, and locating in a codebook of predetermined channel responses a predetermined channel response identified by the primary identifier and the differential identifier. The predetermined channel responses in the codebook are grouped in a plurality of clusters in accordance with a correlation criterion, each cluster including a plurality of predetermined channel response members. The method also involves generating a control signal for controlling transmissions to the mobile station in accordance with the located predetermined channel response. The method also involves, at the mobile station, determining a channel response for at least one carrier frequency received at the mobile station, and locating in a codebook of predetermined channel responses a predetermined channel response that is a closest match to the determined channel response, causing the mobile station to transmit a primary identifier identifying a cluster associated with the located predetermined channel response to the base station, and causing the mobile station to transmit a differential identifier identifying the located predetermined channel response member within the cluster identified by the primary identifier.
Owner:APPLE INC
Device for managing data filters
InactiveCN100550893CNetwork connectionsElectric digital data processingPrimary IdentifierWord processing
Owner:ALCATEL LUCENT SAS
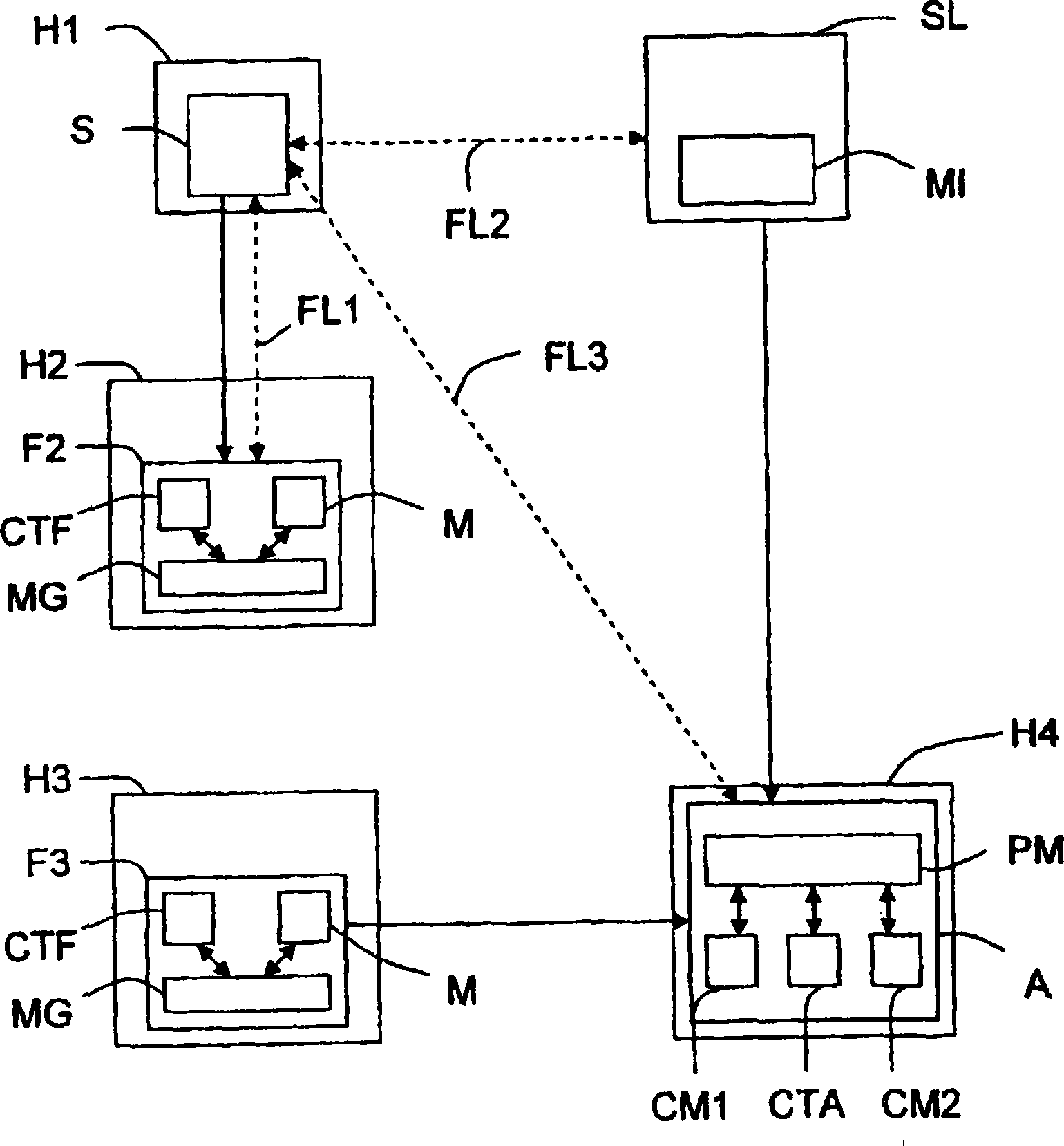
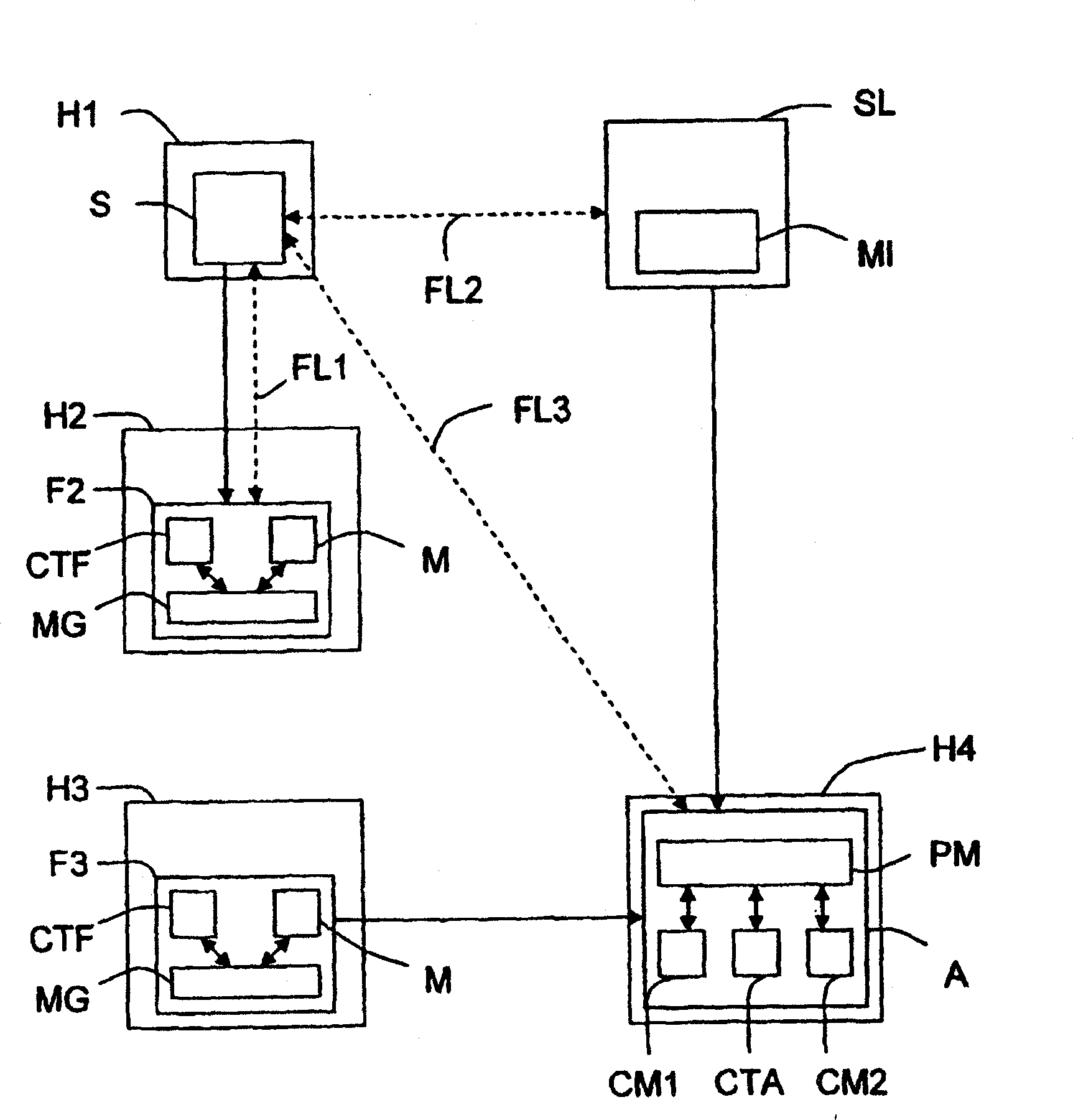
Method of locating mobile communicating objects within a communications network
ActiveCN1868168BData switching by path configurationSecuring communicationPrimary IdentifierCommunication device
The invention relates to a mobile communicating object (A) belonging to a communications network and comprising processing means (PM). According to the invention, when a communication has been established with another communicating object (S) belonging to the network, the aforementioned processing means generate a repeater (Fi) at each site (Hi) through which they pass. Moreover, when the repeater is generated, the processing means associate a timing counter (CTF) therewith and configure said repeater such that: (i) it can store an identifier that is representative of the location of the nextrepeater (F(i+1)) or site (H(i+l)) in the chain of repeaters to which it belongs; and (ii) at the end of a selected duration of time, it transmits the location identifier of the next repeater (F(i+1)) or site (S(i+l)) to at least one location server (SL) in the network, so that it stores said identifier together with the primary identifier of the mobile object (A). Preferably, once a repeater hasaddressed the location identifier, the relay activity thereof is terminated and, if the repeater does not belong to another chain, it is removed so that it no longer consumes resources.
Owner:INRIA NATIONAL INSTITUTE FOR RESEARCH IN COMPUTER SCIENCE AND CONTROL +1
Apparatus and method for identifying an object having randomly distributed identification elements
A method for verifying the authenticity of an object, e.g. a bank note or a cheque, is described. The object is provided with a primary identifier in the form of a plurality of identification elements embedded in the object. The identification elements are visually detectable when illuminated by infrared or ultraviolet electromagnetic radiation but are visually indistinguishable from the rest of the object when illuminated with visible light. The object has a reference point in the form of a printed symbol defining an area of the object in which at least some of the identification elements are provided. The method includes the step of identifying a sub-area of the object defined by the reference point, and recording information relating to the positions of the identification elements in the sub-area relative to the reference point. A detector that can be used to carry out this method is also described.
Owner:TULLIS RUSSELL PAPERMAKERS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com