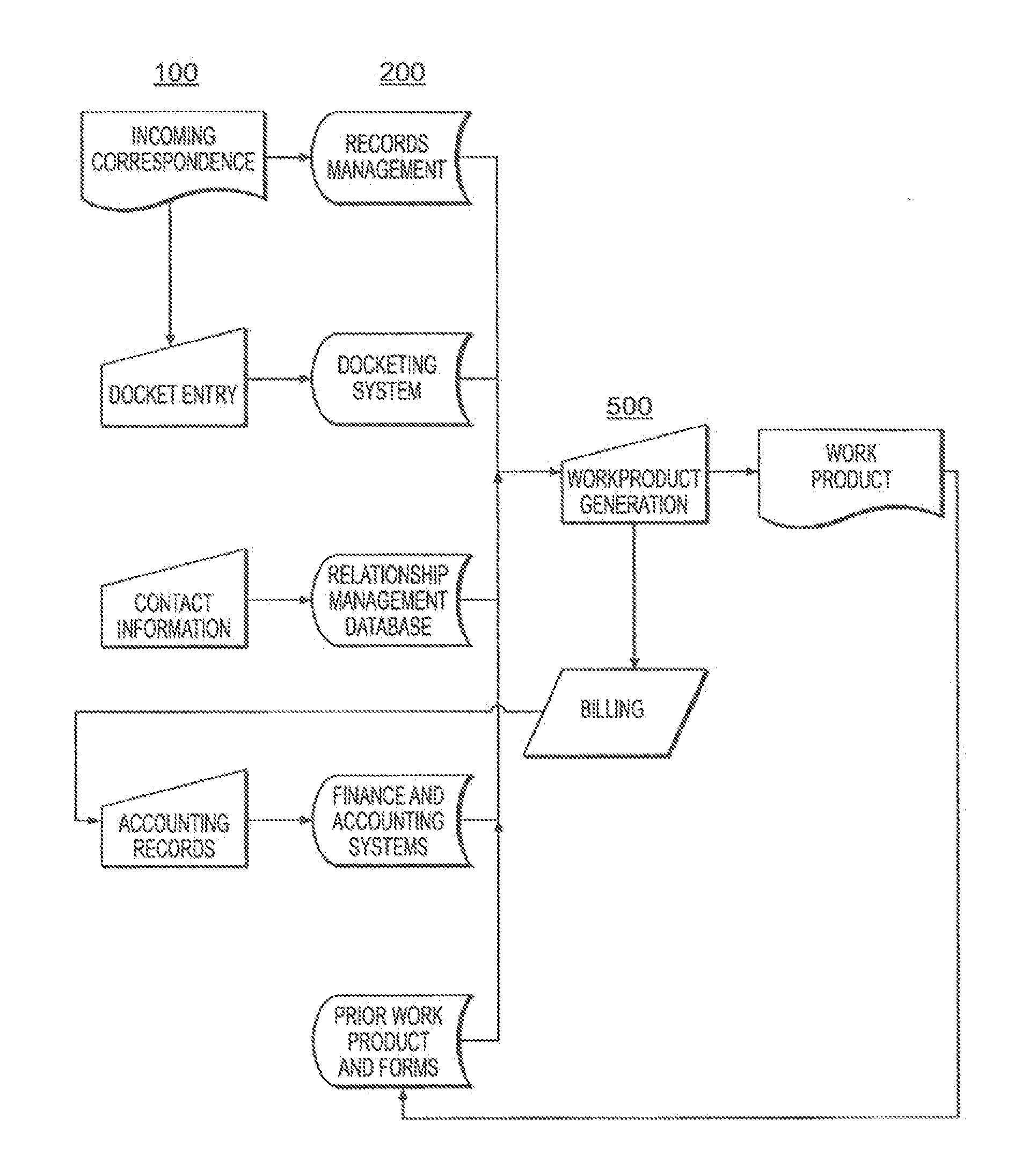
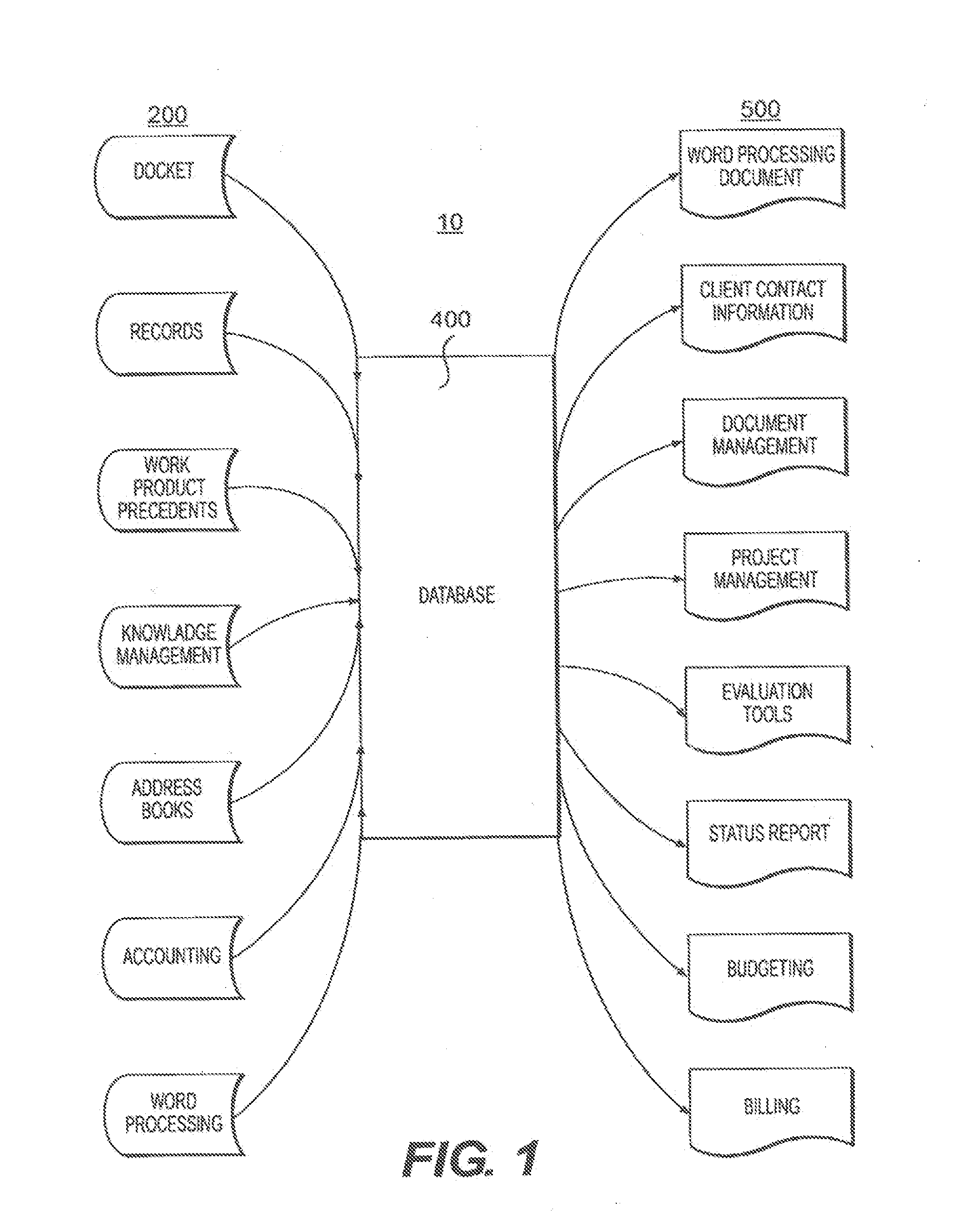
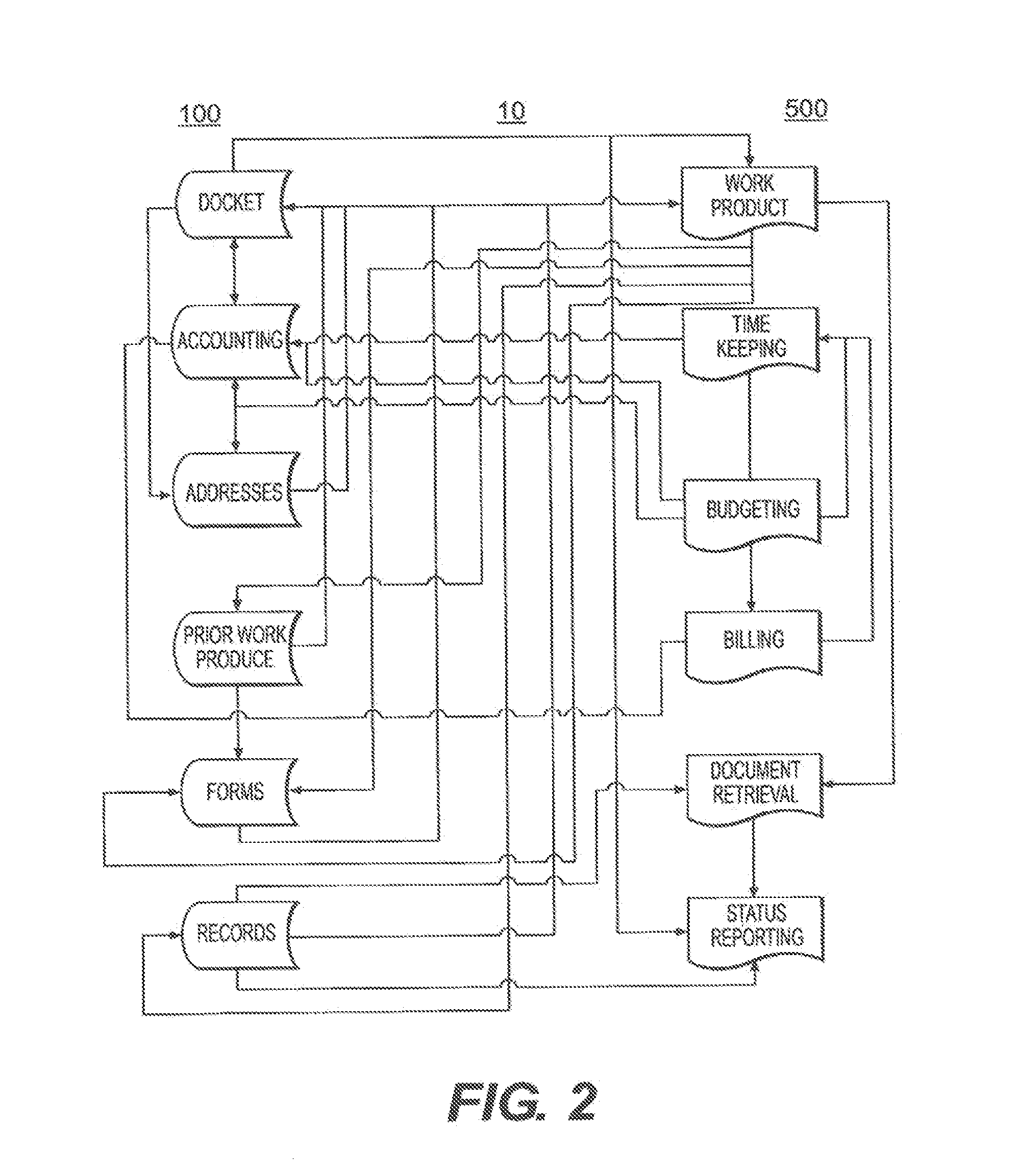
These applications are not adapted to, and in many instances, are not capable of, cooperating or communicating with one another.
The architecture of computer networks has compounded the difficulties of managing these disparate systems.
Apart from the substantial challenges this imposes on network managers and systems administrators, it has made the ready transferability of data between components more difficult, if not impossible.
Typically the data was maintained in a format that was proprietary and, in some cases, exclusive to the
single application, or at least not readily portable to other applications.
While these restrictions help preserve the security, integrity, and reliability of the data, they impair the transferability of the data.
Yet, these systems generally remain: proprietary; rigid in their formatting; and rigid in their ability to transfer or exchange information with other
software applications and to accept related
project management and / or financial information.
Extranets remain complex and limited in their functionality.
Web-based systems have not resolved the fundamental problem that pertinent data is stored in multiple inconsistent formats.
The rigidity of most docketing systems, however, impairs or prevents the data from being readily exchanged with other applications.
Consequently, data is typically manually transferred (
cut and pasted) or simply key-entered repeatedly in each application in which it is needed, presenting multiple additional opportunities for errors and
data corruption.
As a result, the same intended address now resides in multiple locations in the firm's
computer network, each likely being different and possibly containing incorrect and inconsistent information, style, and formatting.
At each point where it was entered or used, time is wasted in reentering the same information.
At each
entry point, there are new opportunities for additional errors being introduced.
Yet, while the data may be portable between the applications to a greater or lesser degree, incompatibilities remain, that have resulted in corruption or loss of the data, or general protection faults.
For example, errors and inconsistencies frequently result between Palm databases, Notes databases, and relationship management databases that purport to contain the same information.
The data is not reliably transferred between them in practice, due to
software flaws and / or incompatibilities.
Moreover, the undue complexity of these systems makes them difficult for even sophisticated users to use competently.
In Applicant's experience, these problems extend to all of the types of data used in a professional service(s) practices.
Even these limited applications, however, encountered substantial problems in transferring data from one application to another prior to the present invention.
Docketing and accounting systems have generally been even more problematic with respect to the portability and / or application-independence of their data.
In a professional services setting, such as law and / or
medicine,
centralized database applications have generally been disfavored for several reasons.
First, the cost and complexity of these types of integration projects have been prohibitive.
Second, the rapid evolution of hardware and software further contraindicate the massive investment required for centrally integrated databases.
Third, the distributed nature of professional services, as well as security concerns, teach away from massive integration in a professional services setting.
Thus, there has long been an unresolved need for secure, reliable, simple data transfer between applications.
Prior known approaches have failed to meet this long-felt and unresolved need, particularly in a professional service(s) setting.
Professional service(s) markets, therefore, have had to rely on either
mass-marketed software applications that are not adapted to their particular needs, and / or customized and / or proprietary solutions that are expensive, complex, and limited in their flexibility and adaptability.
This results in duplication in
purchasing and training, while only certain programs or features of each application are actually used.
Rather, each software application is typically written in a different, and incompatible,
proprietary format.
These proprietary formats are generally not compatible with other software applications.
In practice, however, this was not the case.
Transferring data was cumbersome,
time consuming, and required manual intervention and conversion, typically, with specialized assistance from personnel specifically trained in the
proprietary software.
Such incompatibilities regularly cause catastrophic failures.
Nor has the advent of Windows XP and other operating systems resolved these problems.
This marketing simply underscores the failure of prior known approaches to resolve this fundamental and long-felt need.
Moreover, Windows XP continues to suffer faults with a “
Task List” interface provided to terminate the offending application(s).
In reality,
mass marketed business
application software of the type used in professional services practices has come nowhere near achieving these levels of reliability.
This is wasteful and introduces multiple opportunities for error in
data entry, maintenance, and retrieval.
Typically, the more powerful the tool, the more rigorous the training requirements.
PC-based network systems have fostered the proliferation of incompatible, proprietary applications software.
These proprietary systems have resulted in: maintenance problems; undue complexity in systems architecture and design; excessive network systems support requirements; the need for duplicate copies of applications software; increased systems maintenance; increased cost; impaired access to data; increased
training time and expense; diversion of professional time to non-productive uses; and, ultimately, impairment of access to the information needed to run the practice or business.
Training time must be balanced against the value of upgrades, which sap even more resources.
New technologies have enabled greater productivity, yet, have done little to guide that effort in a productive manner.
Automation alone does not make an organization more efficient or productive.
Lack of Maturity of the
Software Industry
Nor do large-scale software integration projects offer a viable alternative.
And some three quarters of all large systems are ‘operating failures’ that either do not function as intended or are not used at all.
These include a pervasive lack of quality and repeated systems failures suffered by various software systems.
Among the
software engineering failures Gibbs chronicles are: the baggage
handling system at Denver International Airport; the loss of the Clementine
space probe; the State of California's attempt to merge its driver and vehicle registration systems; the unsuccessful attempt to force the expansion of American Airline's successful “Sabre”
reservation system to integrate hotel and car reservation bookings; the Federal
Aviation Administration's replacement of it's
air traffic control software with its failed “Advanced
Automation System;” and other spectacular failures.
Nor have distributed
systems approaches proved successful in overcoming the lack of maturity of the software industry.
In addition to the problems presented by
order of magnitude growth every decade, undue complexity, lack of adequate
documentation, and failure to integrate successive stages of evolution of a software product, the stresses imposed by “distributed systems” are substantial.
Often systems
crash because they fail to expect the unexpected.
. . .’ The complexity and
fragility of these systems
pose a major challenge.” / d.
Gibbs emphasizes the lack of discipline and professionalism in the software industry.
Although some researchers are addressing practical, repeatable solutions, most of the industry is not.
Although Microsoft Corporation prides itself that its software is “beta-tested” by tens of thousands of users, this system is expensive, inefficient, and, ultimately, ineffective.
Most software developers cannot and do not secure even this ineffective, level of
exposure.
The result is a continuing
stream of defective and faulty products.
Unfortunately, these advances generally have not been adopted by producers of
mass-market software, the type of software typically used in a business or professional service(s) setting.
It continues to encounter substantial resistance among the companies, managers, and engineers who produce these software products.
One glaring example of the lack of professionalism in
software development is the presence of “Easter Eggs” in mass-marketed software programs.
The
consumer is not offered the option to reject these deliberate and extraneous bits of software.
One expert in
computer security, Ross Anderson, at Cambridge University in Britain, has stated: “Easter Eggs are a telling symptom of
poor quality control at many software companies . . . . Purchasers are right to be concerned; the great majority of computer-security failures result from the opportunistic exploitation of vulnerabilities that are discovered by chance.
Although researchers are investigating several promising approaches, these approaches are not yet generally accepted.
Significant technical and cultural barriers remain to the success of these approaches.
There is no
accommodation to integrate or accept data from the types of distributed applications that are otherwise used in a medical office, or to transfer information maintained in an office's legacy systems.
Whitmyer's approach, however, enables corruption of the data in the docket by enabling potentially incorrect or unauthorized information to be added to the docketing
database.
The LawPack product did not fit within
Hummingbird's core business strategy and
Hummingbird announced in late 2001 that it was phasing out the LawPack product.
Although
XML has won widespread support in recent years from Internet standard bodies such as the
World Wide Web Consortium, it too has drawbacks, namely: astonishing complexity {Id. at 26) and the impracticality of metatagging the entire contents of a page.
Although
XML is beginning to address the issue of transferability of data in the context of web search engines, it is a limited approach and has not been applied among the various software applications within a
machine to enhance the transferability of data within an application or between applications.
These standards have not found their way back into the PC or office network environment to help resolve the basic problem of transferring information between incompatible application software platforms within the same computing device or network.
Nor have these approaches yet been applied to distributed networks serving professional services markets.
Yet, these too are saddled with the drawbacks of undue complexity and being proprietary and, therefore, less flexible and more rigid that desired.
Although PKI (
Public Key Infrastructure) systems, employing digital certificates are also gaining ground, particularly in banking and
telecommunications, they are similarly complex, rely on
third party involvement, and are not ‘well-adapted to use within an internal network to commoditize data between applications.
Its ability is limited, at present.
This is primarily due to restraints on access and the lack of generally accepted standards for data formatting.
None provided data in a substantially application-independent or portable fashion.
Moreover, none of the prior known approaches have resolved the unmet need to facilitate the transfer of data between outside professional service providers and their clients.
 Login to View More
Login to View More  Login to View More
Login to View More