Patents
Literature
73 results about "Internet traffic engineering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Internet traffic engineering is defined as that aspect of Internet network engineering dealing with the issue of performance evaluation and performance optimization of operational IP networks. Traffic engineering encompasses the application of technology and scientific principles to the measurement, characterization, modeling, and control of Internet traffic [RFC-2702, AWD2].
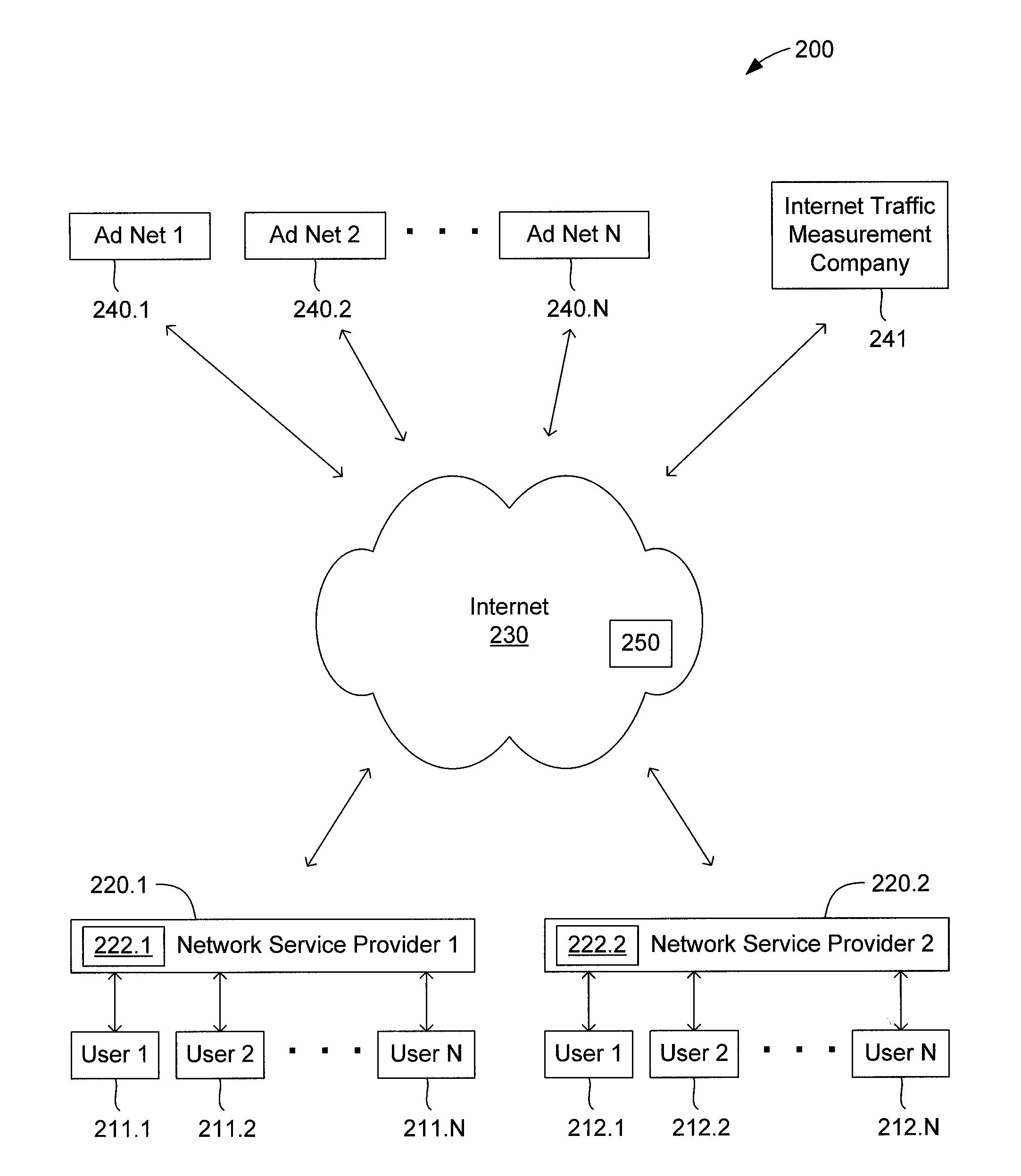
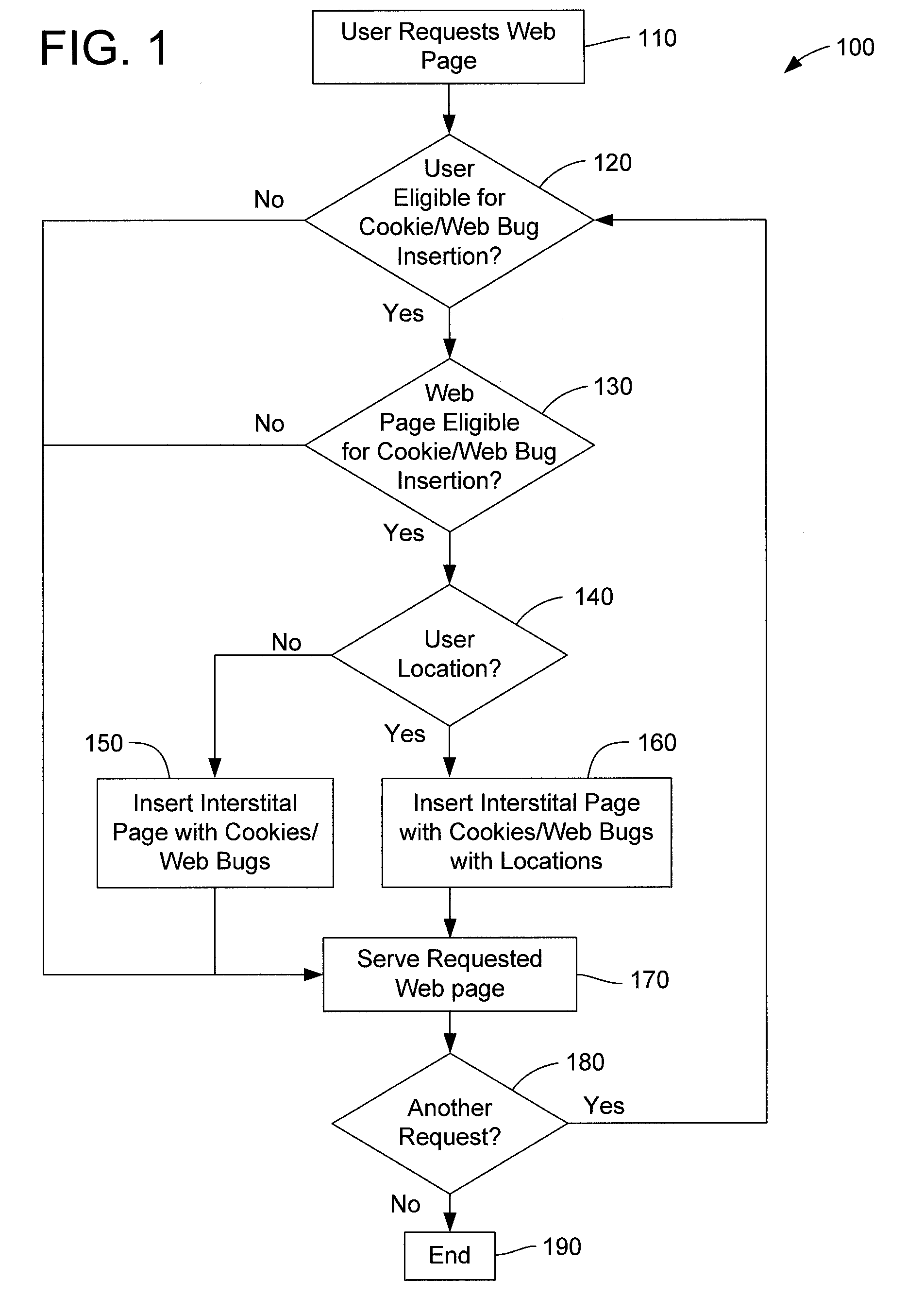
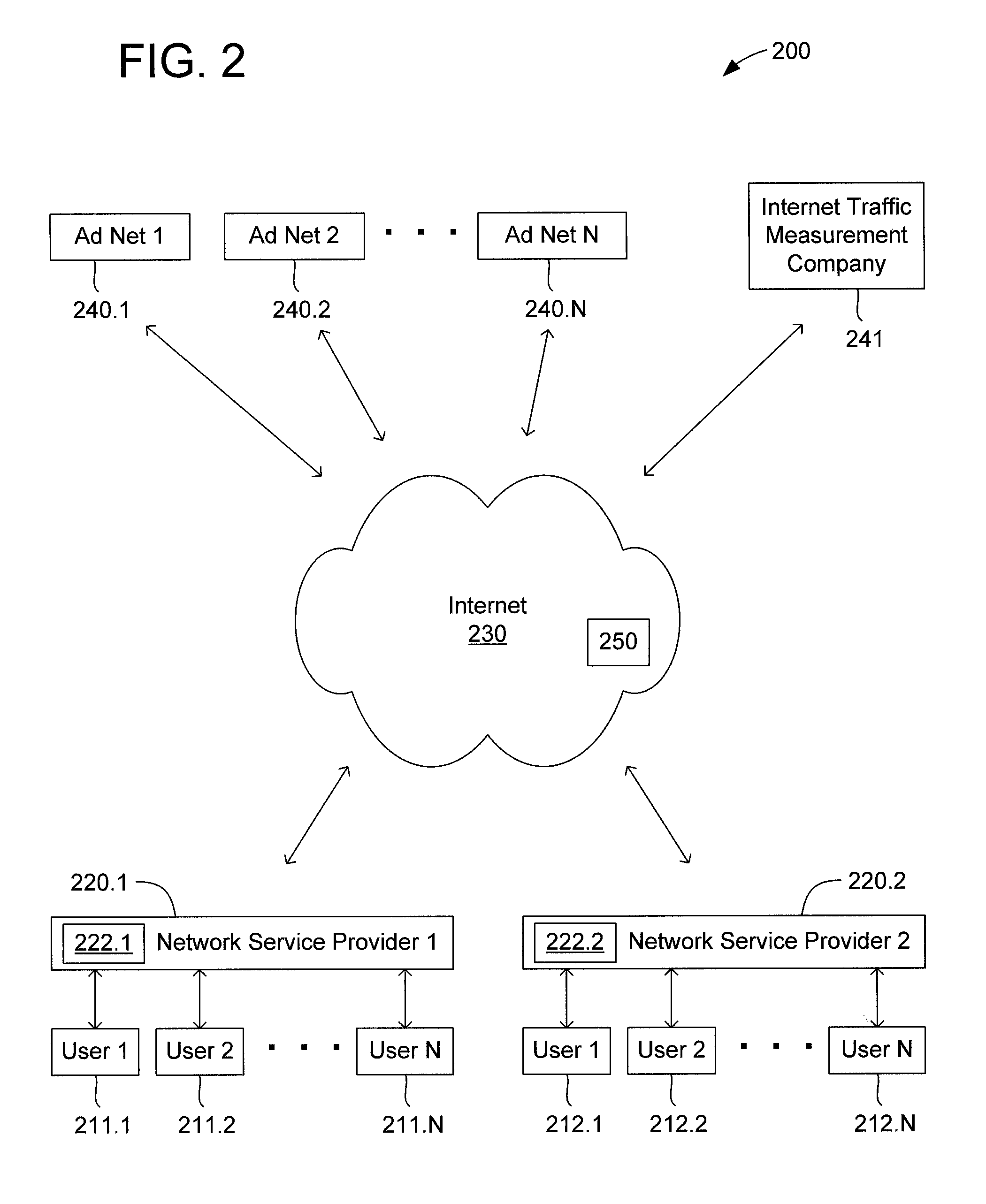
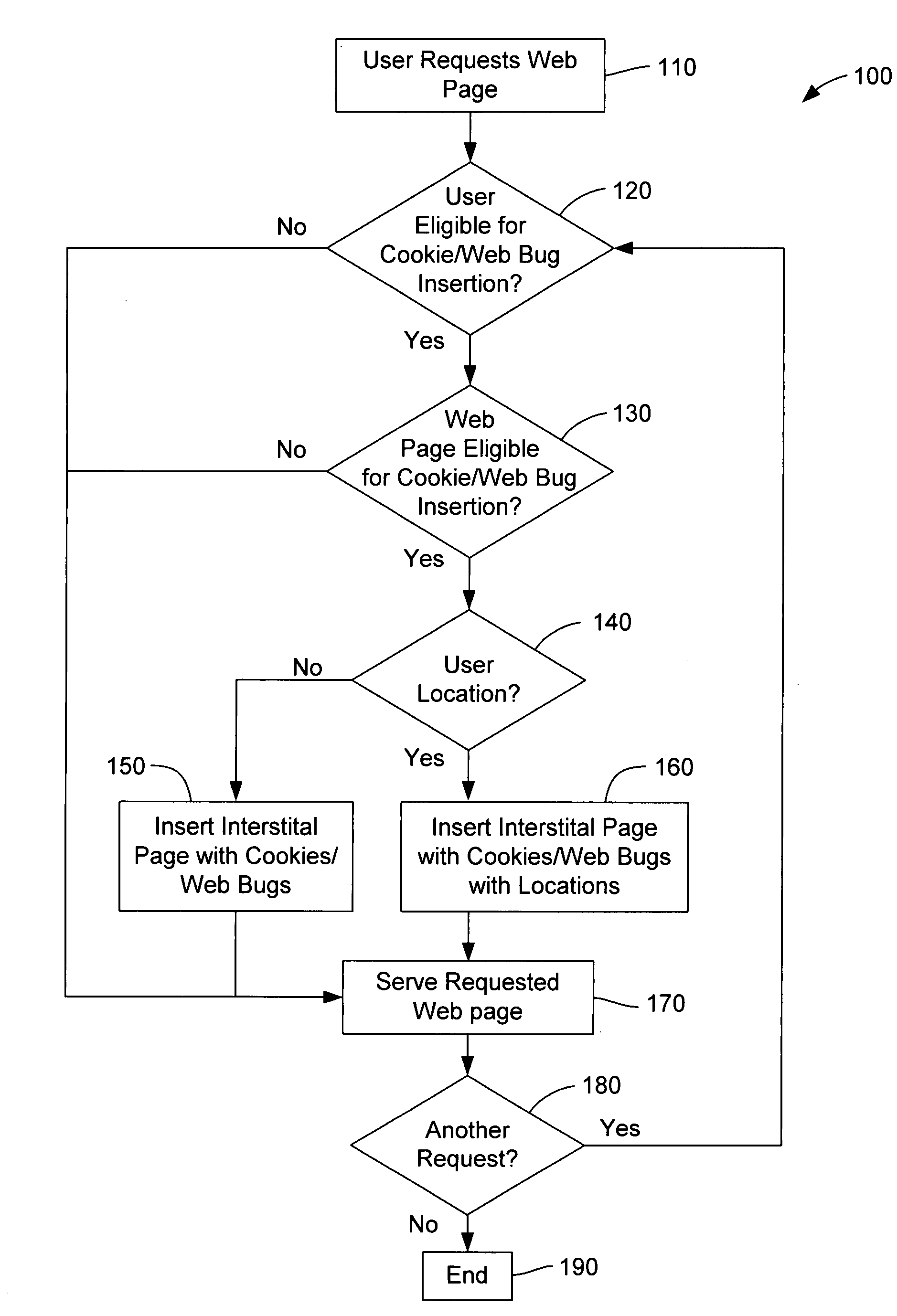
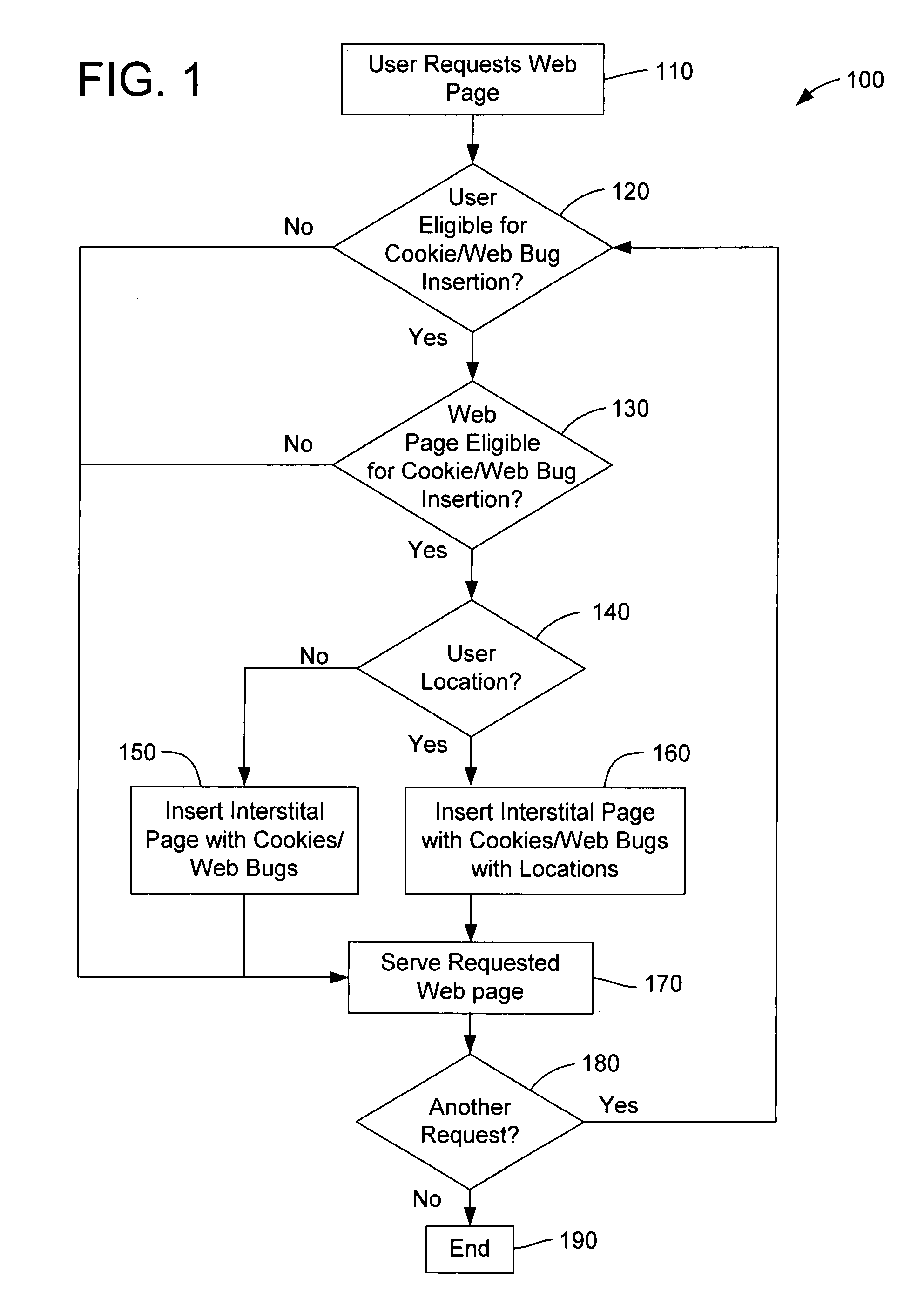
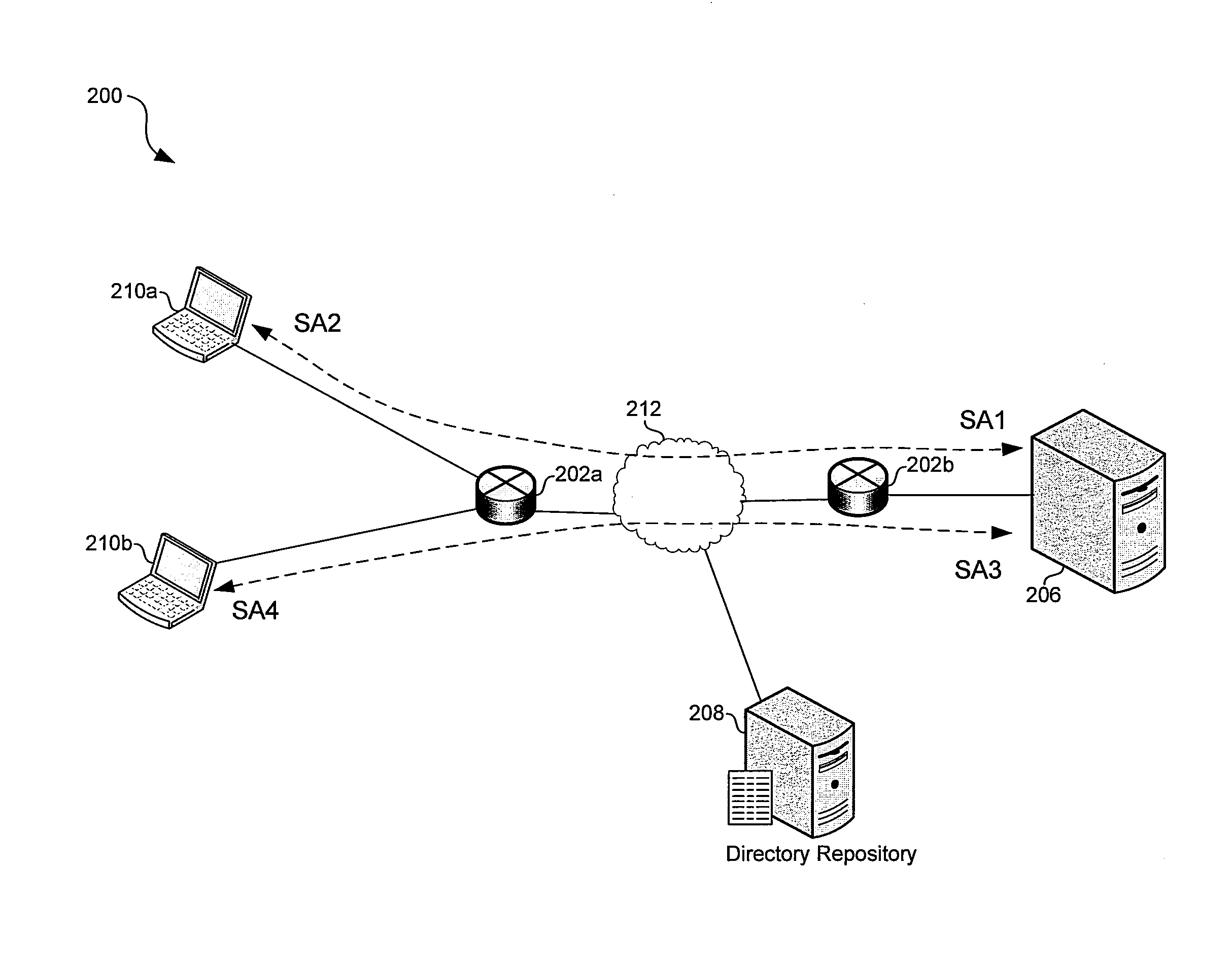
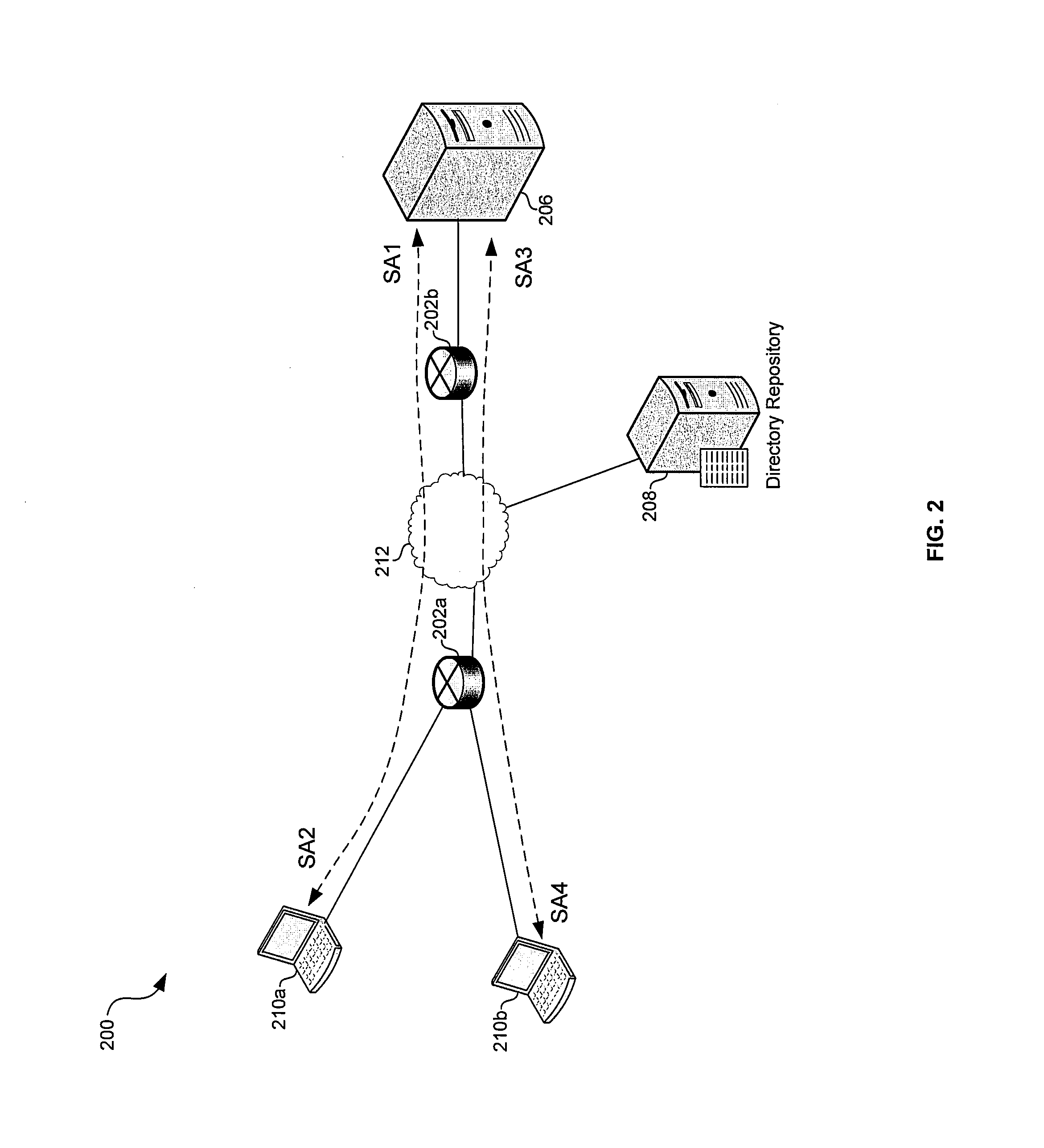
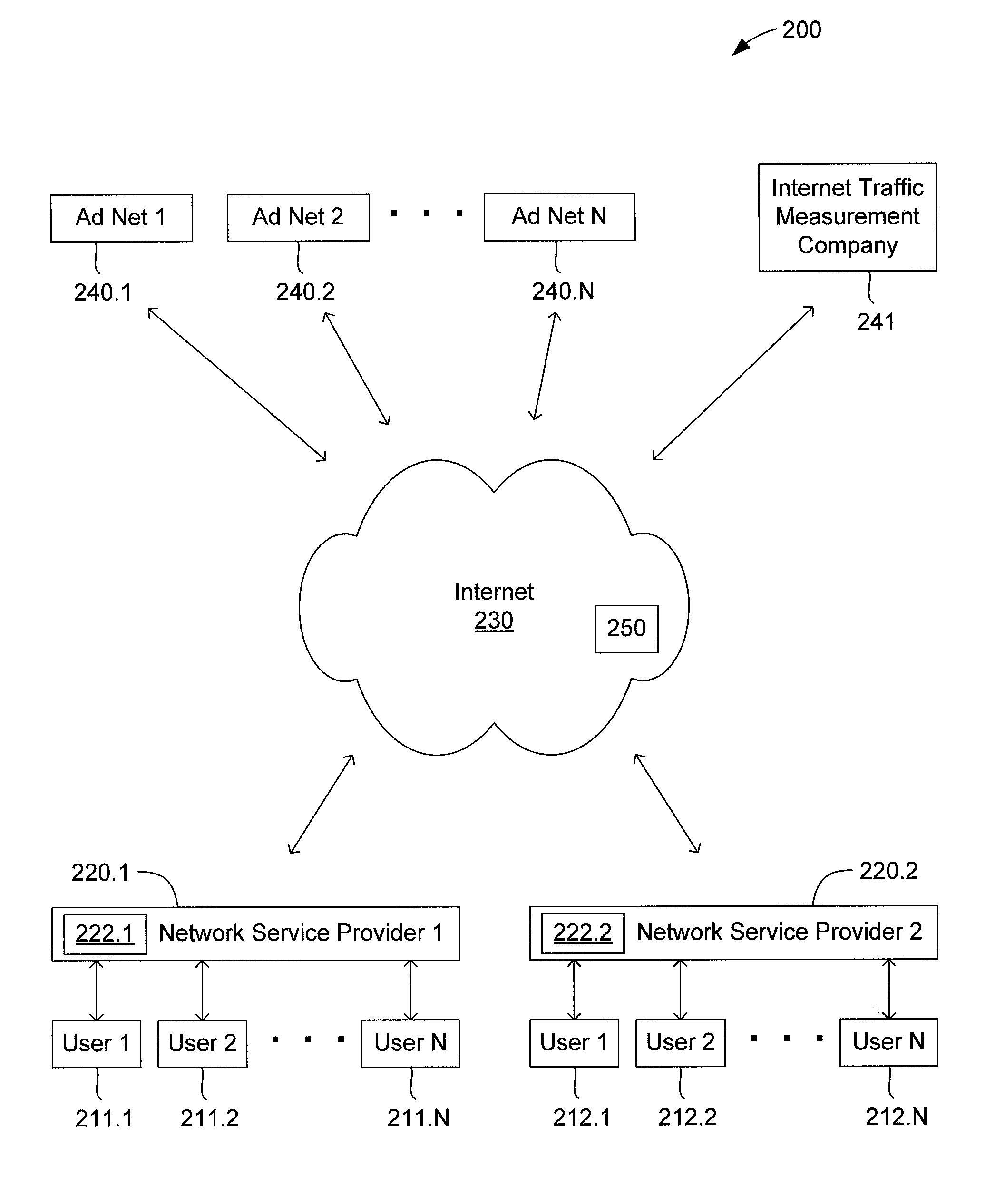
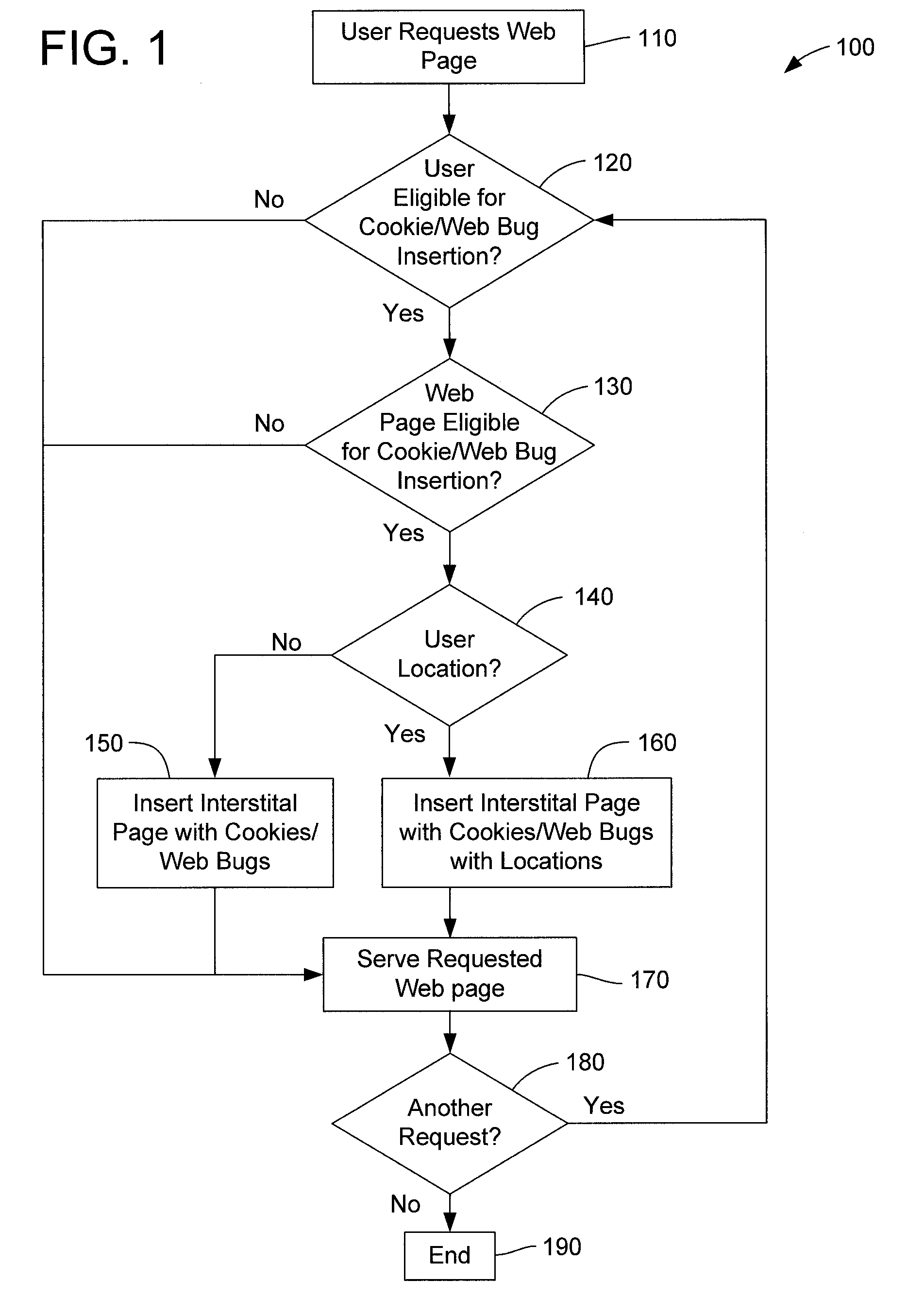
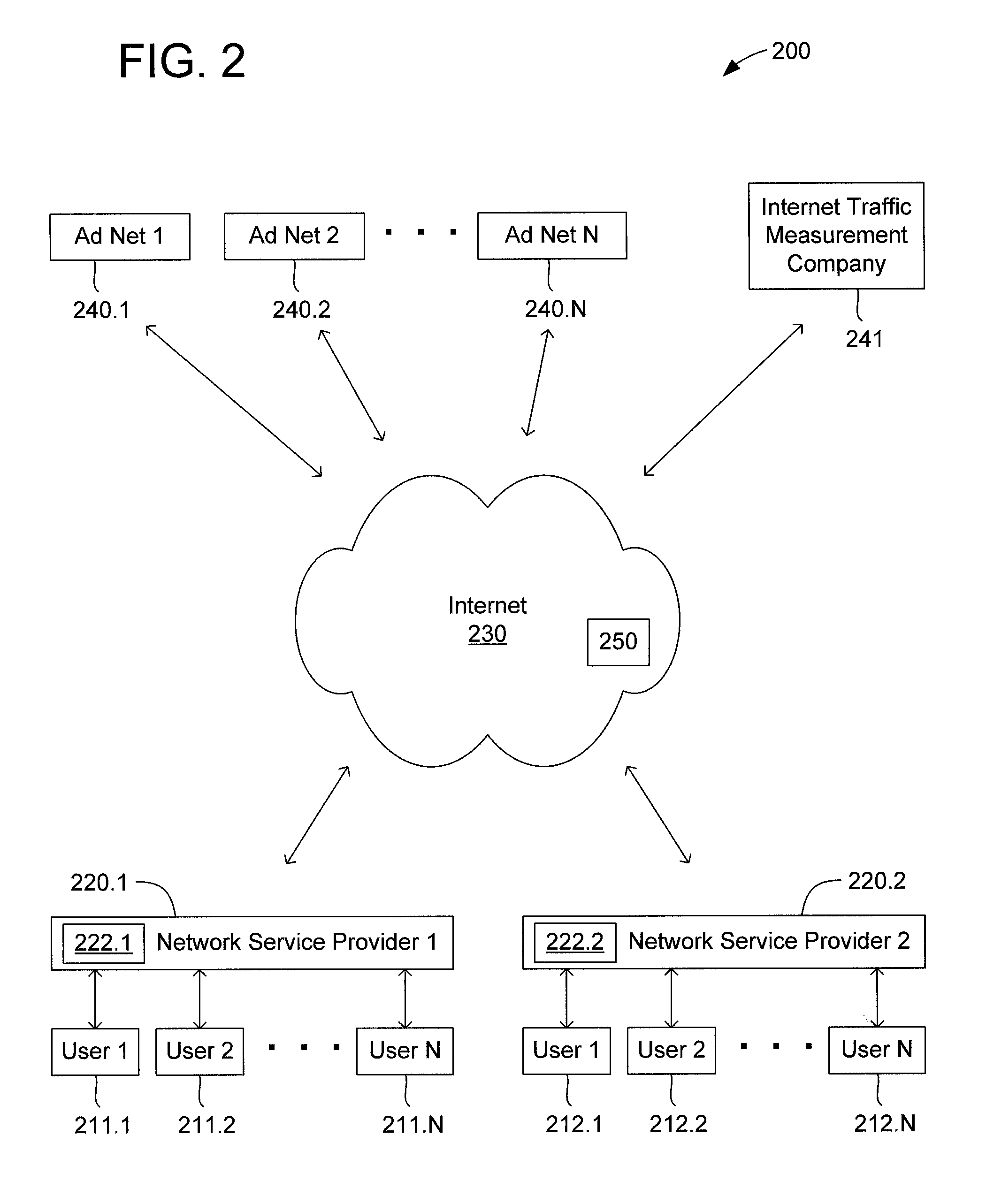
Method and apparatus for internet traffic monitoring by third parties using monitoring implements
InactiveUS20090177771A1Error preventionFrequency-division multiplex detailsInternet traffic engineeringThird party
Disclosed is an internet traffic monitoring method. In the method, a first packet, sent from a user client, having a web content request meeting certain monitoring selection criteria is detected. Upon detection of the first packet, a second packet is forwarded to the user client. The second packet has a redirection with a fabricated web content request to a monitoring web page including at least one monitoring implement.
Owner:FRONT PORCH
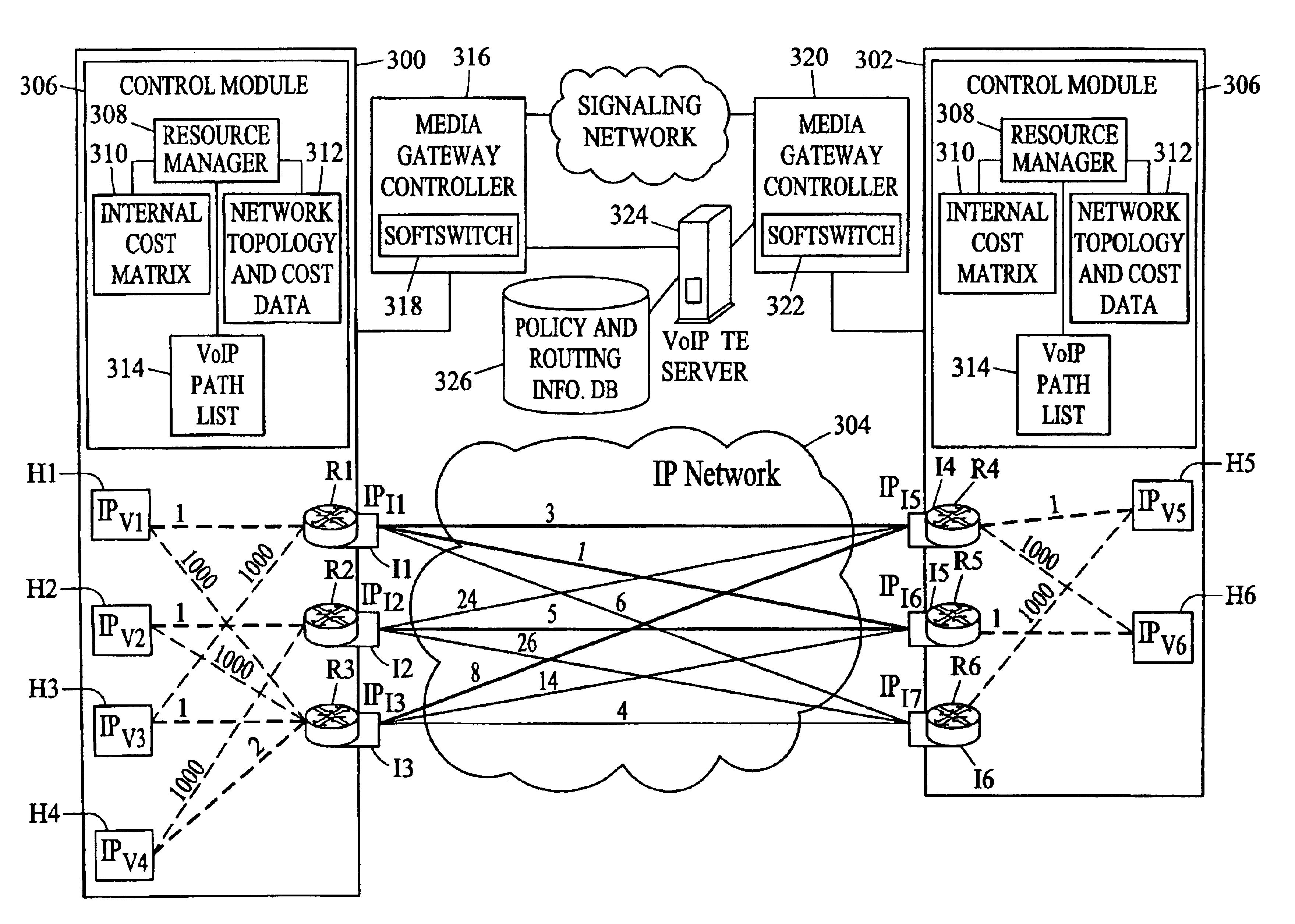
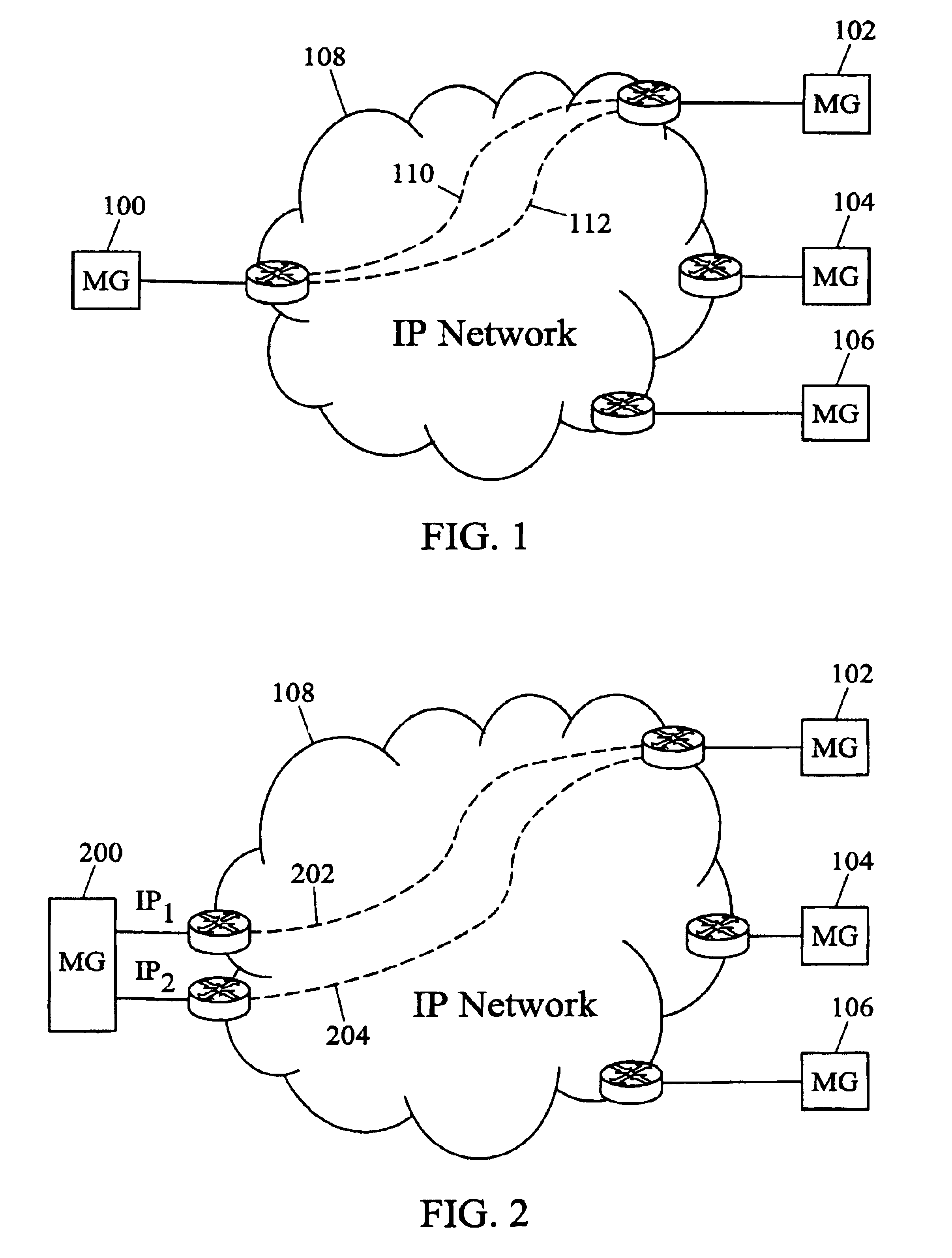
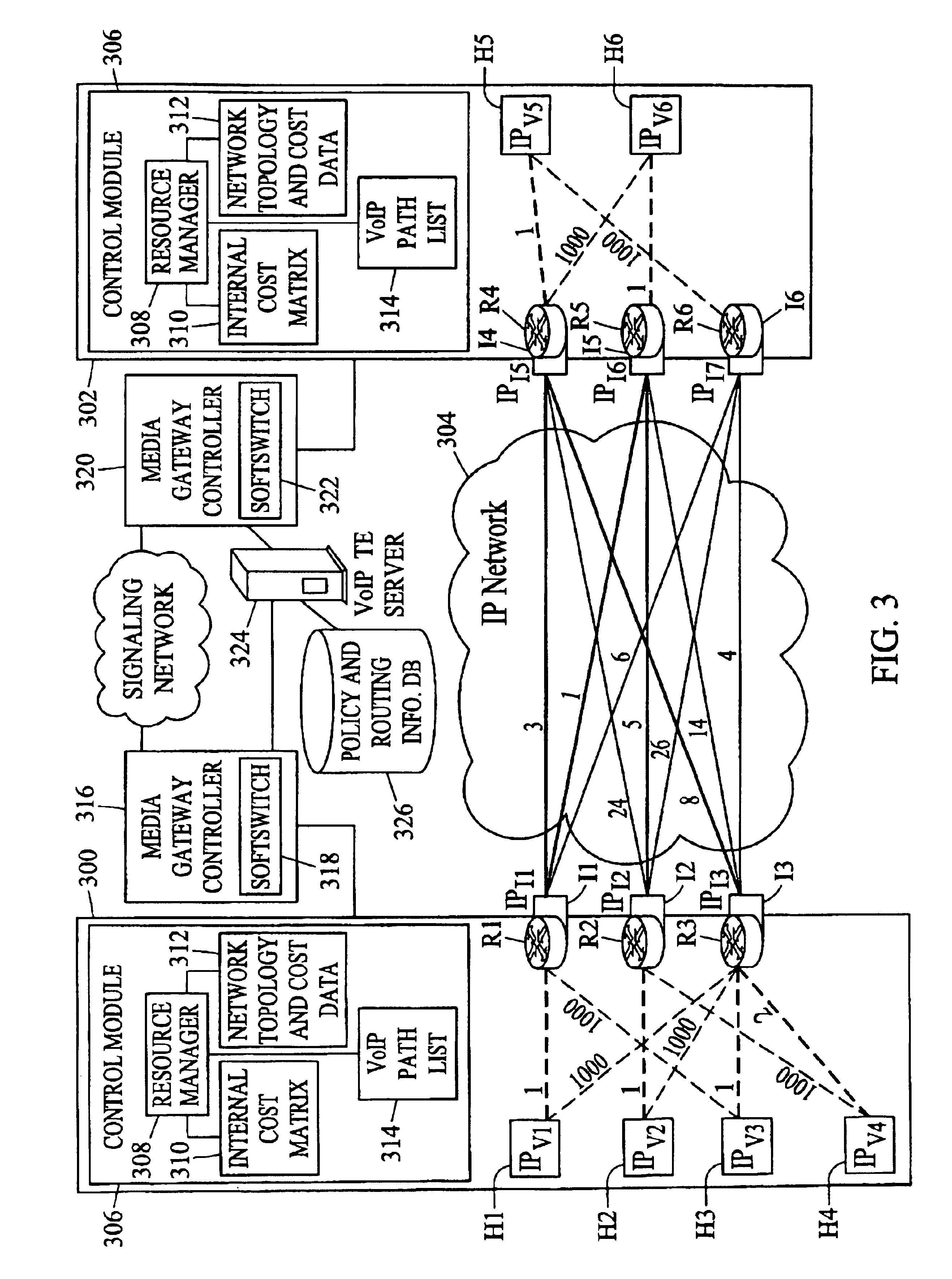
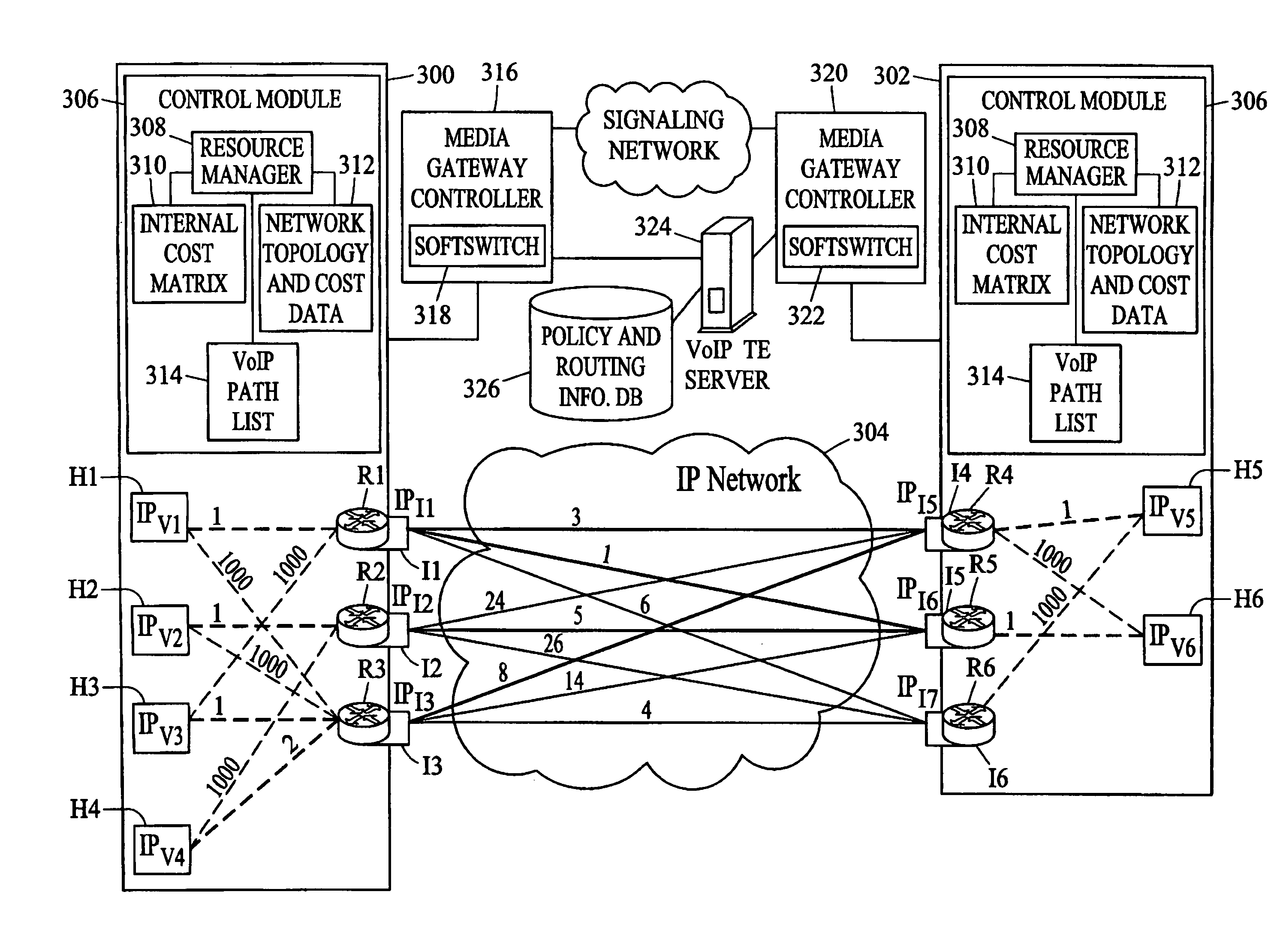
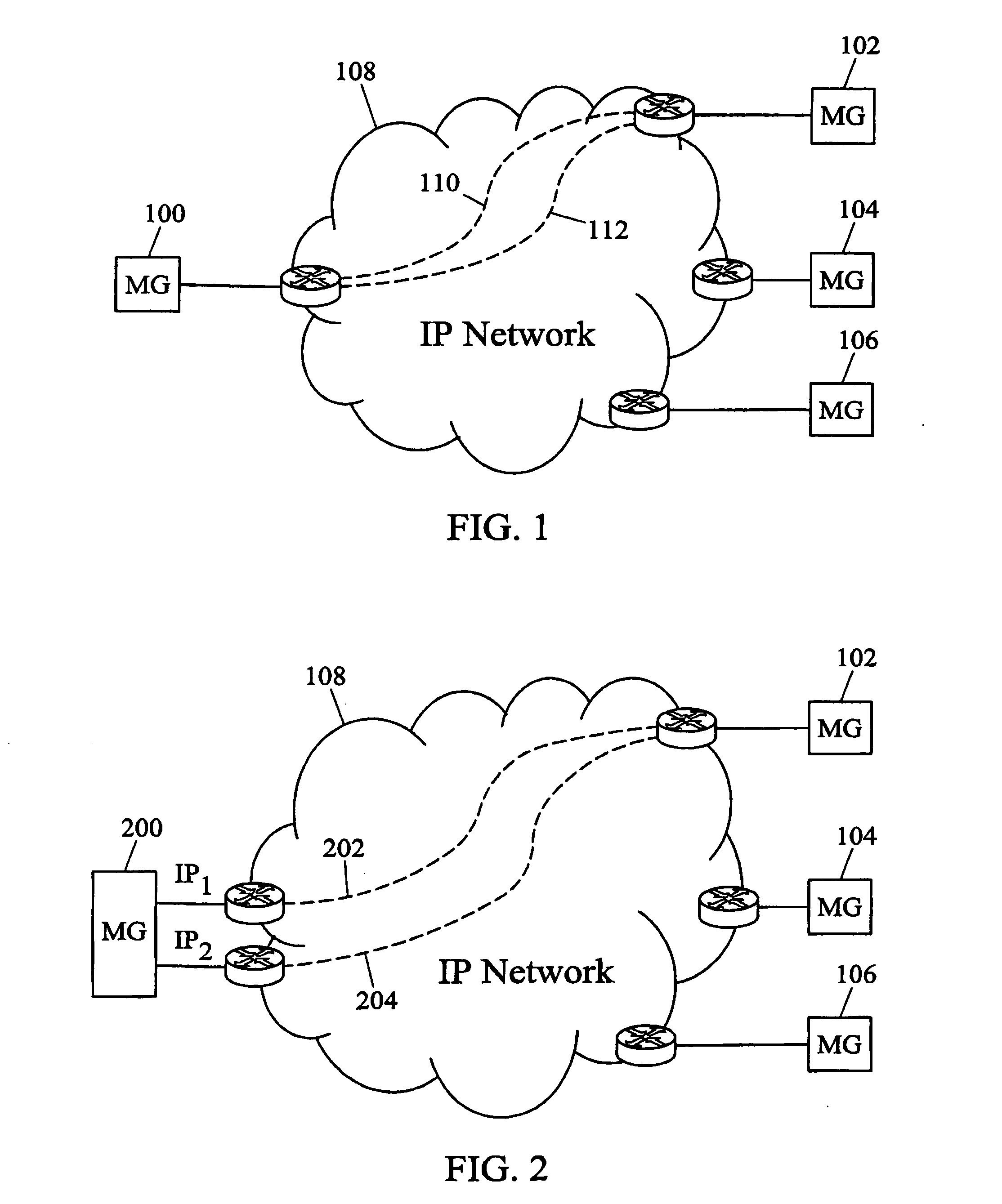
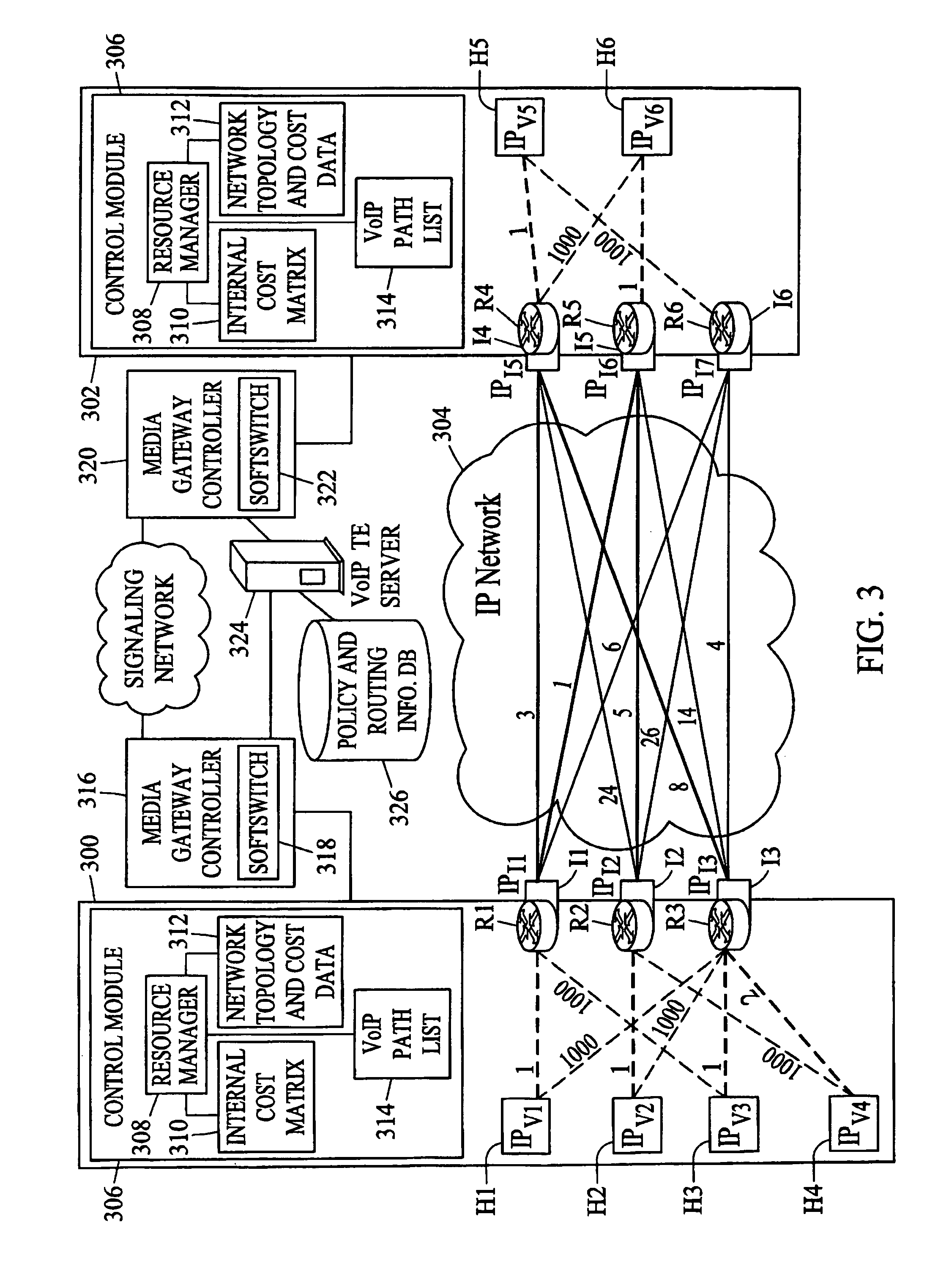
Methods, systems, and computer program products for voice over IP (VoIP) traffic engineering and path resilience using network-aware media gateway
InactiveUS6956820B2End-to-end network resilienceError preventionTransmission systemsInternet traffic engineeringRouting table
Methods and systems for providing voice over IP traffic engineering and path resilience using a network-aware media gateway are provided. In a media gateway, voice over IP hosts are assigned a first set of IP addresses. Network interfaces in the media gateway are assigned a second set of IP addresses that differ from the first set of IP addresses. Per-interface routers advertise reachability information from at least one of the voice over IP hosts via multiple interfaces and participate in network routing protocols to generate per interface routing tables. Voice over IP path lists may be generated based on the per interface routing tables. Internal costs may be assigned to the associations between the voice over IP hosts and the interfaces based on traffic engineering criteria.
Owner:GENBAND US LLC
Methods, systems, and computer program products for voice over IP (VOIP) traffic engineering and path resilience using network-aware media gateway
ActiveUS20050083844A1Provide flexibilityEnd-to-end network resilienceError preventionTransmission systemsInternet traffic engineeringRouting table
Methods and systems for providing voice over IP traffic engineering and path resilience using a network-aware media gateway are provided. In a media gateway, voice over IP hosts are assigned a first set of IP addresses. Network interfaces in the media gateway are assigned a second set of IP addresses that differ from the first set of IP addresses. Per-interface routers advertise reachability information from at least one of the voice over IP hosts via multiple interfaces and participate in network routing protocols to generate per interface routing tables. Voice over IP path lists may be generated based on the per interface routing tables. Internal costs may be assigned to the associations between the voice over IP hosts and the interfaces based on traffic engineering criteria.
Owner:GENBAND US LLC
Method and apparatus for internet traffic monitoring by third parties using monitoring implements
InactiveUS20090019148A1Multiple digital computer combinationsTransmissionInternet traffic engineeringThird party
Disclosed is an internet traffic monitoring method that includes a network service provider analyzing an HTTP transaction involving an internet user client. The network service provider responds to the HTTP transaction by forwarding, to the internet user client, an interstitial web page including a monitoring implement. After forwarding the interstitial web page to the internet user client, the network service provider forwards web content, originally associated with the HTTP transaction, to the internet user client.
Owner:FRONT PORCH
Traffic matrix computation for a backbone network supporting virtual private networks
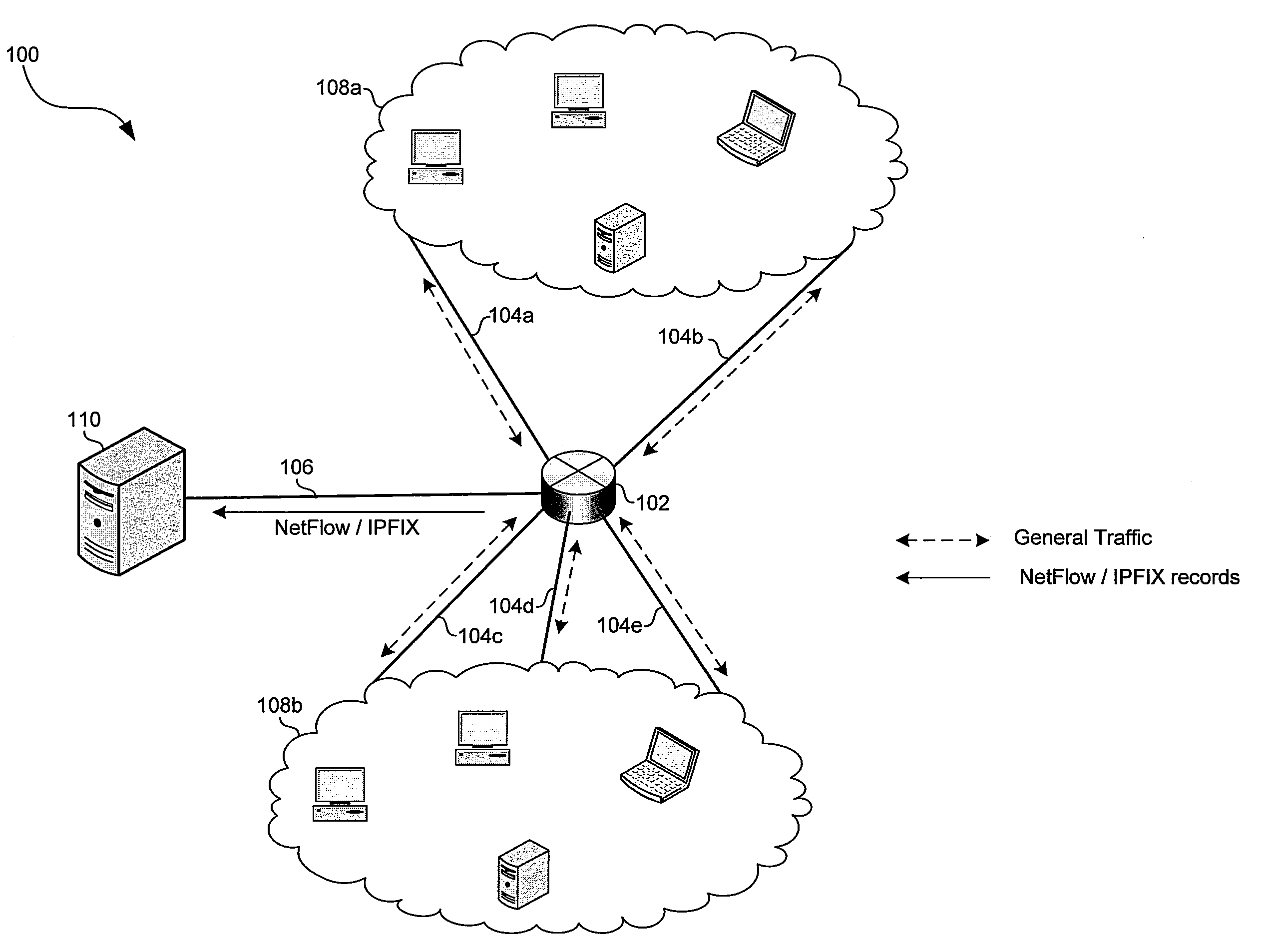
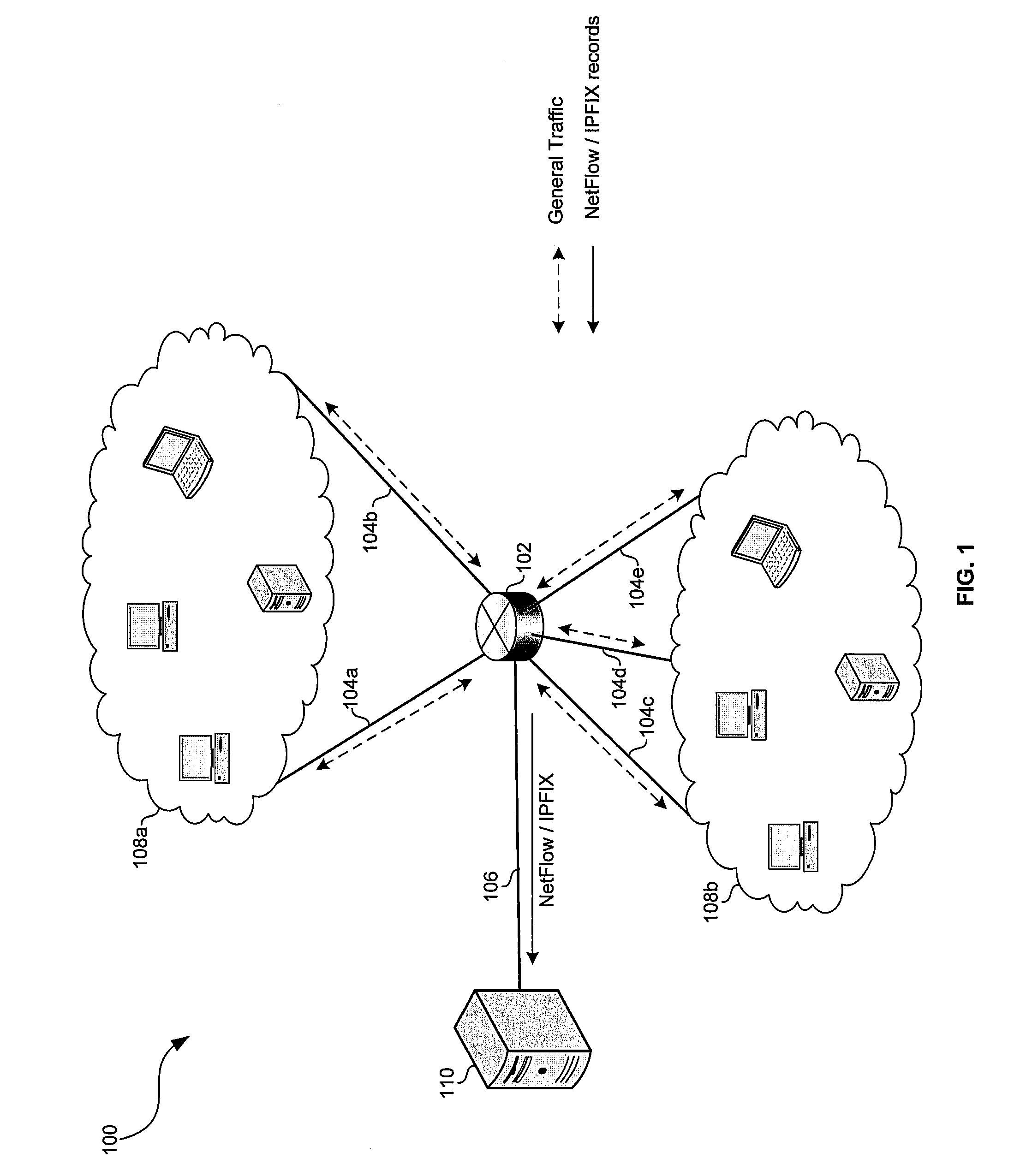
InactiveUS7027396B1Shorten the timeView accuratelyError preventionTransmission systemsTraffic capacityInternet traffic engineering
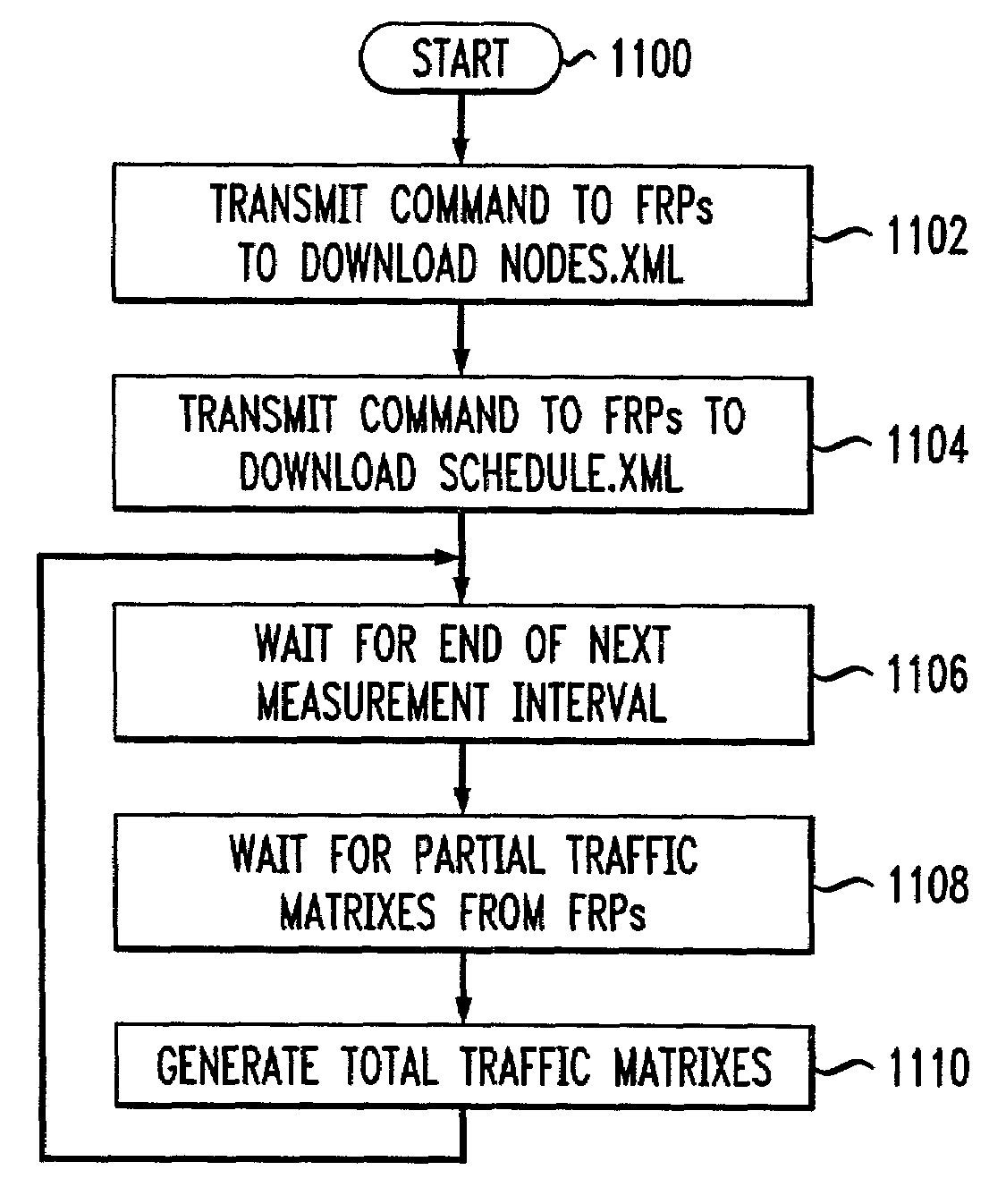
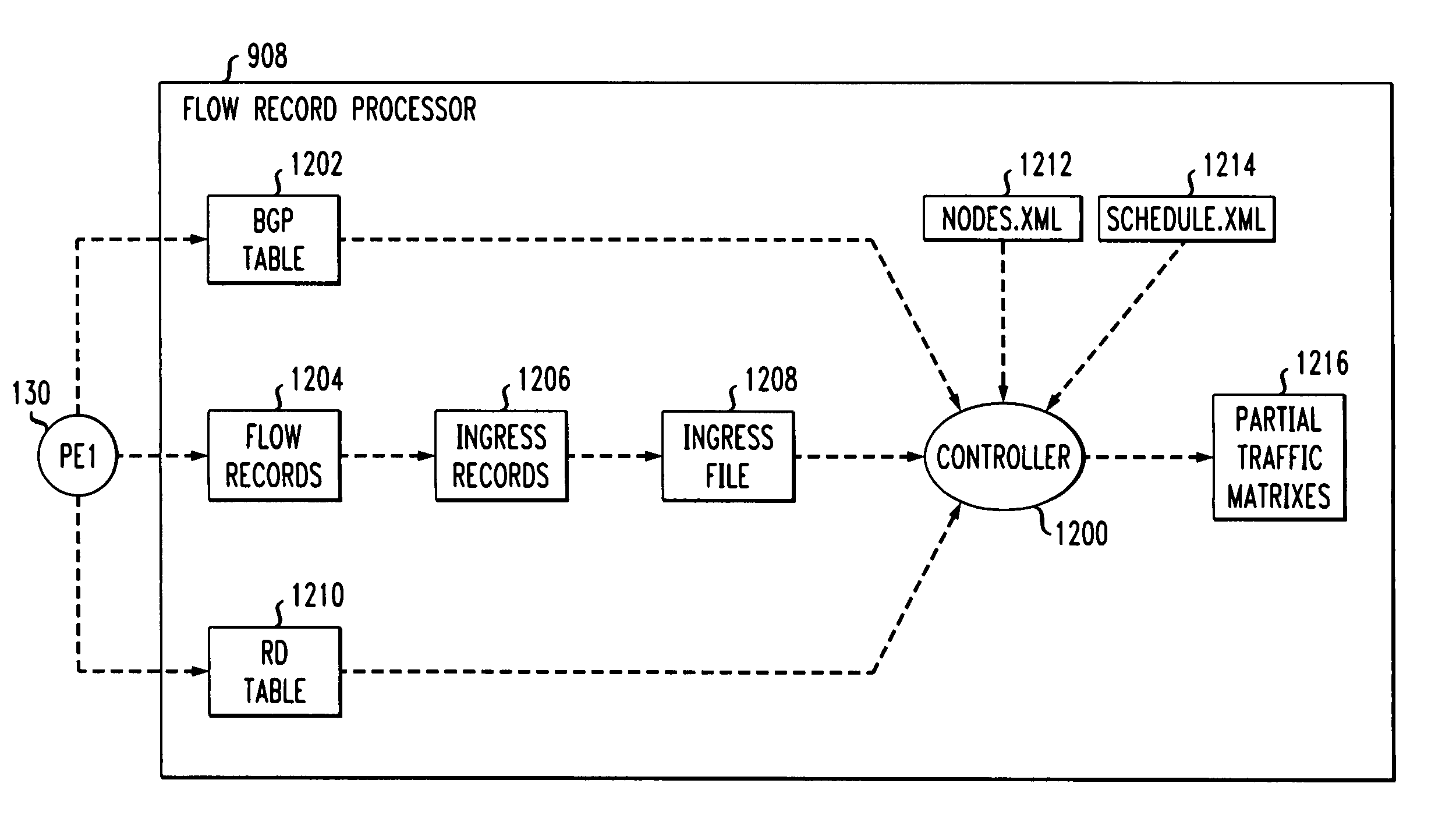
This invention provides a more effective method for capacity planning and traffic engineering of packet networks that connect Virtual Private Network (VPN) sites. A distributed architecture efficiently computes traffic matrixes that show the number of bytes and / or packets exchanged among provider edge (PE) routers and / or service nodes. Each PE router in a service node is exports flow records to a Flow Record Processor (FRP) in the same location. The FRPs use these records in conjunction with configuration data extracted from the PE routers to compute partial traffic matrixes. The partial traffic matrixes are uploaded to a Matrix Generator to create a total traffic matrix. The total traffic matrix is essential input for capacity planning or traffic engineering tools.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Method and apparatus for traffic engineering in shortest path bridged networks
ActiveUS20120076014A1Error preventionFrequency-division multiplex detailsTraffic capacityInternet traffic engineering
A method and apparatus for diverting traffic in a communications network are disclosed. According to one aspect, the invention provides a communications network with a first node and a second node. Connecting these two nodes is a first set of intermediate nodes on a first path (the true shortest path) and a second set of intermediate nodes on a second alternate path. At a first node, a first processor determines whether a packet arriving at the first node must transit the second node. If so, the base virtual local area network (VLAN) identifier (VID) of the packet is replaced by a first VID, and the packet is transmitted along the second path through the second set of intermediate nodes to the second node. At the second node, a second processor determines whether a packet arriving at the second node must transit the first node. If so, the base VID of the packet is replaced by a second VID different from the first VID and different from the base VID, and the packet is transmitted along the second path through the second set of intermediate nodes to the first node.
Owner:CIENA
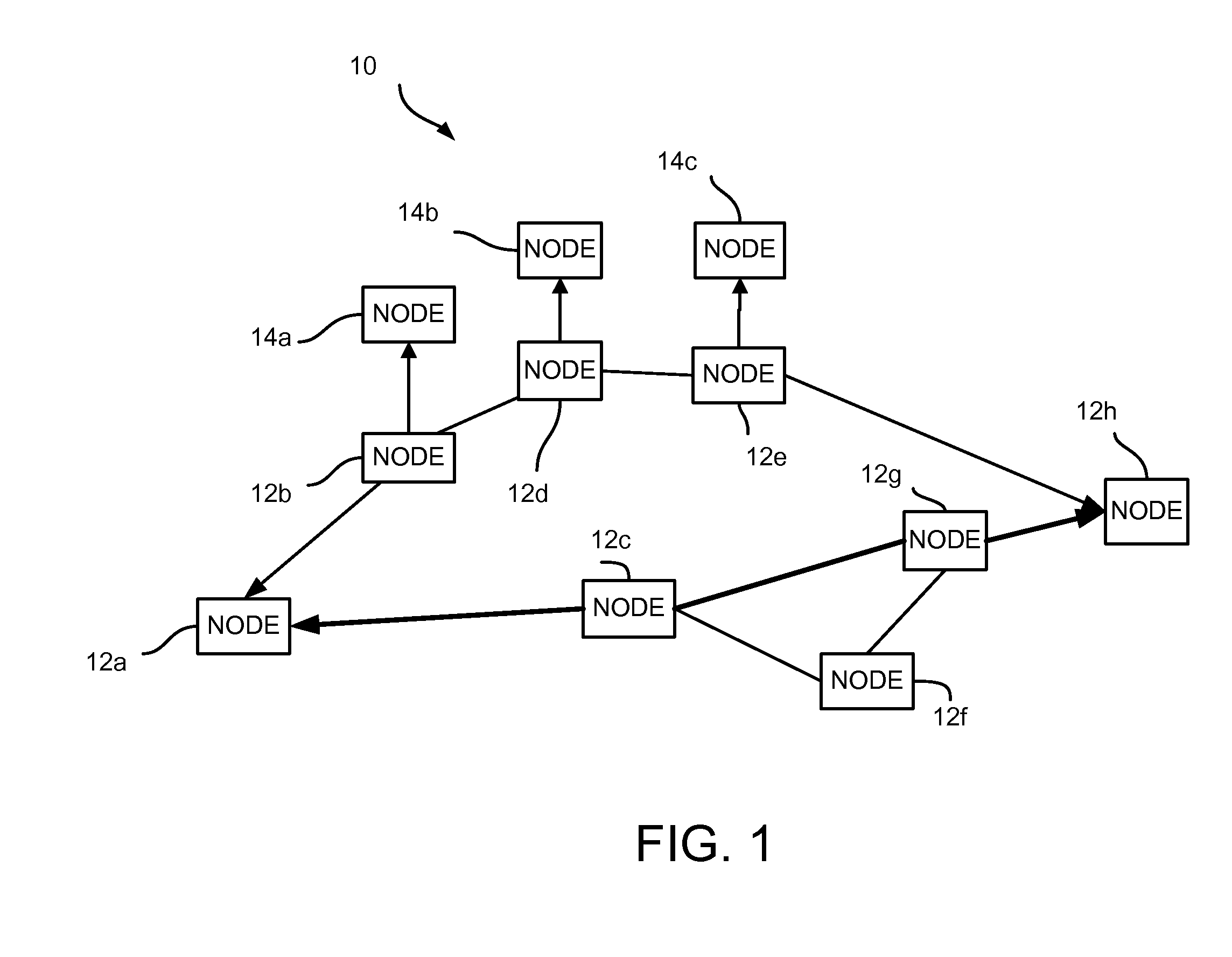
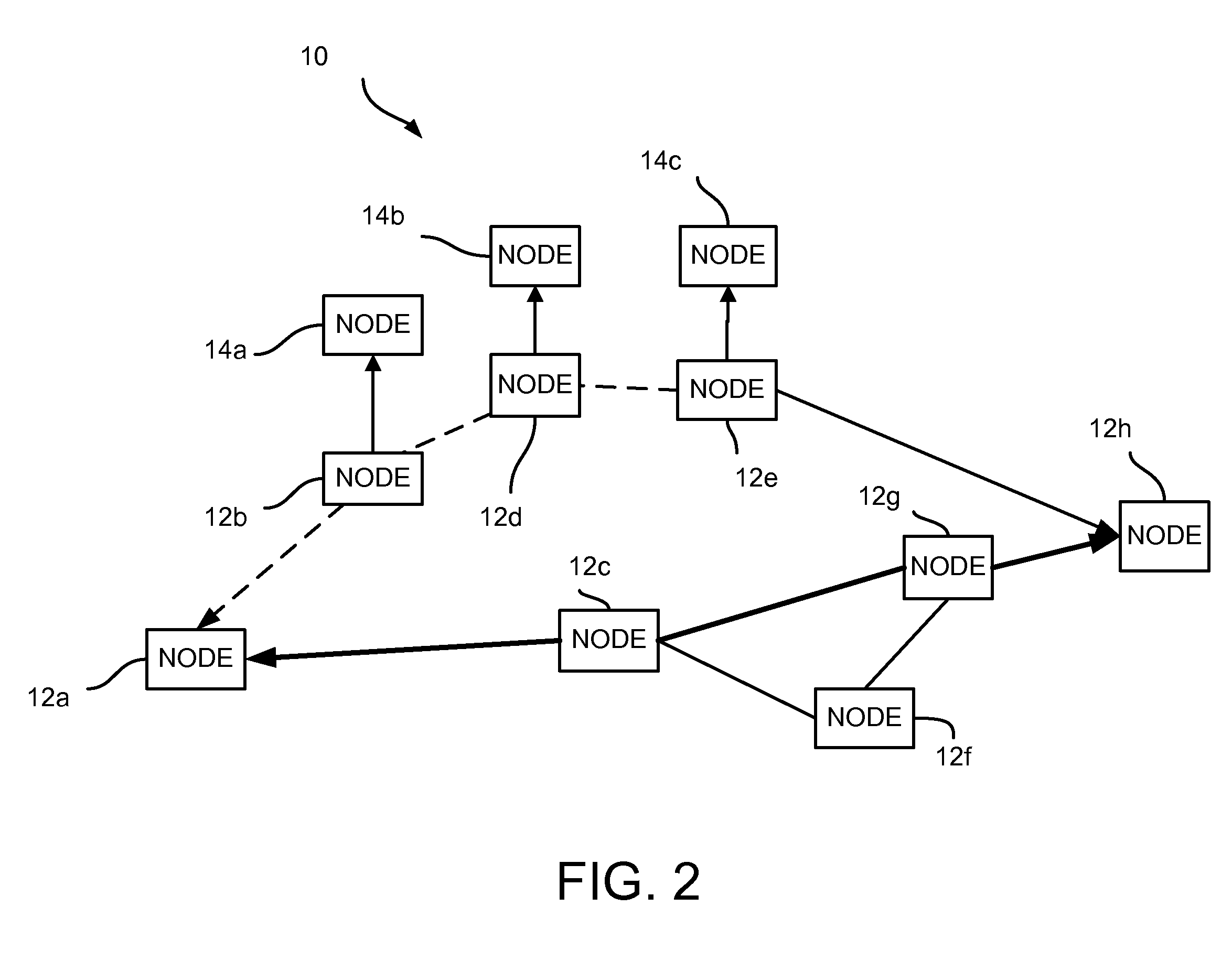
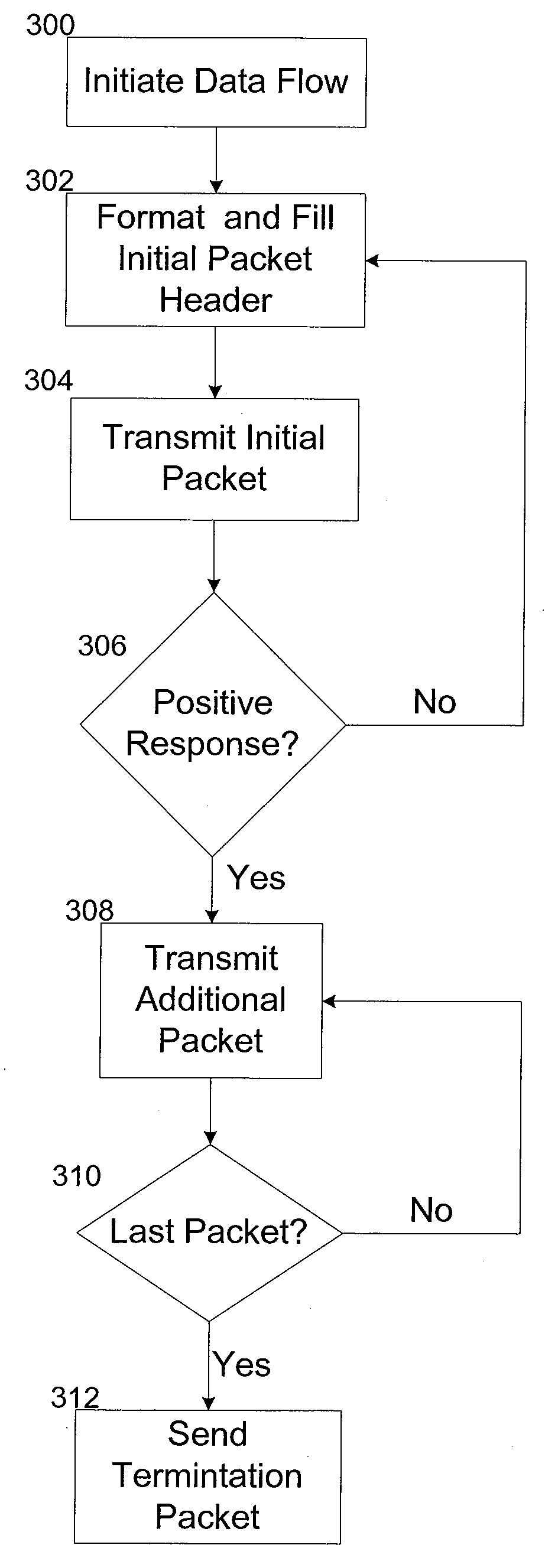
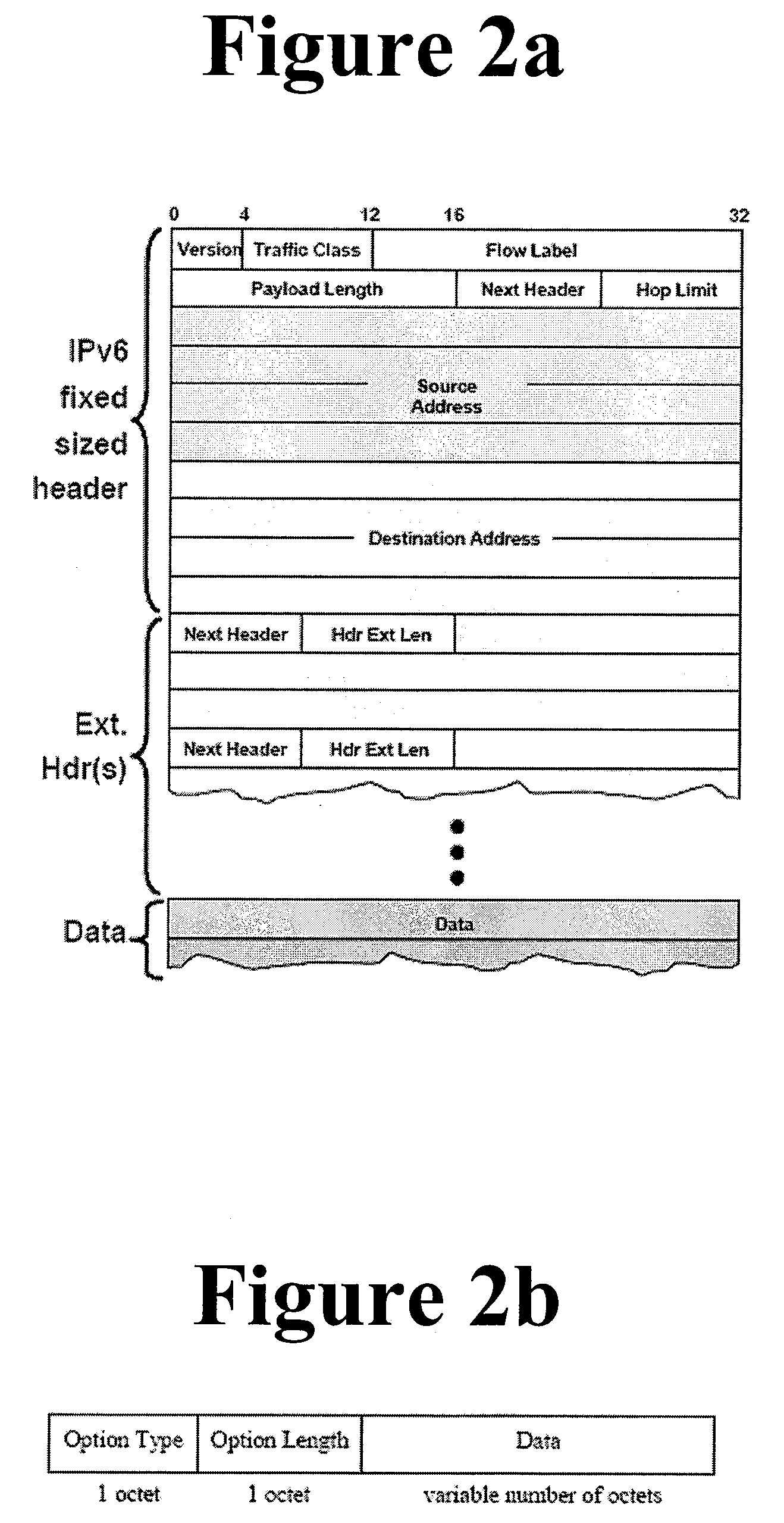
TRAFFIC ENGINEERING AND FAST PROTECTION USING IPv6 CAPABILITIES
InactiveUS20080159288A1Error preventionFrequency-division multiplex detailsInternet traffic engineeringQuality of service
The present invention provides a method for traffic engineering and fast protection of individual data flows using capabilities supported by IPv6. By utilizing IPv6 extension headers and flow labels a specific network route based upon quality of service (QoS) requirements of a data flow can be selected by a source node. Once a route meeting the QoS requirements of the data flow is selected, a source node can insert the route in an initial packet header and force the flow along the corresponding network path. The source and intermediate nodes cache the route and the flow label selected for a data flow. For subsequent packets, the flow label is used by intermediate nodes to determine the next hop along the route. In the event of a failure, an intermediate node can force the insertion of a new route (along with the original flow label) in the next packet belonging to the failed data flow so that, as the packet is forwarded toward the destination, intermediate nodes on this new path can cache the route and the corresponding flow label. This new route is then used to continue forwarding the data flow to the destination node.
Owner:LUCENT TECH INC
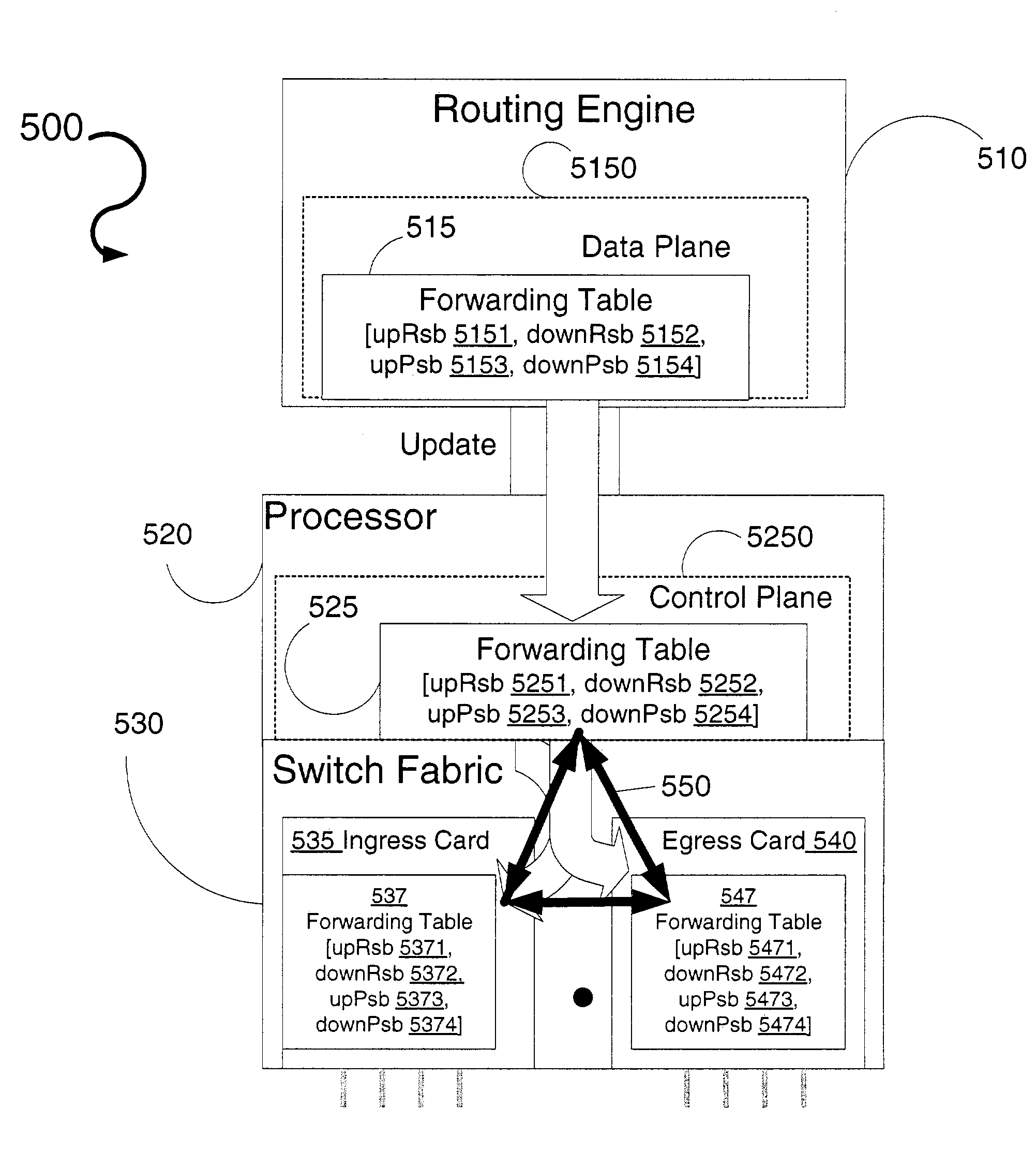
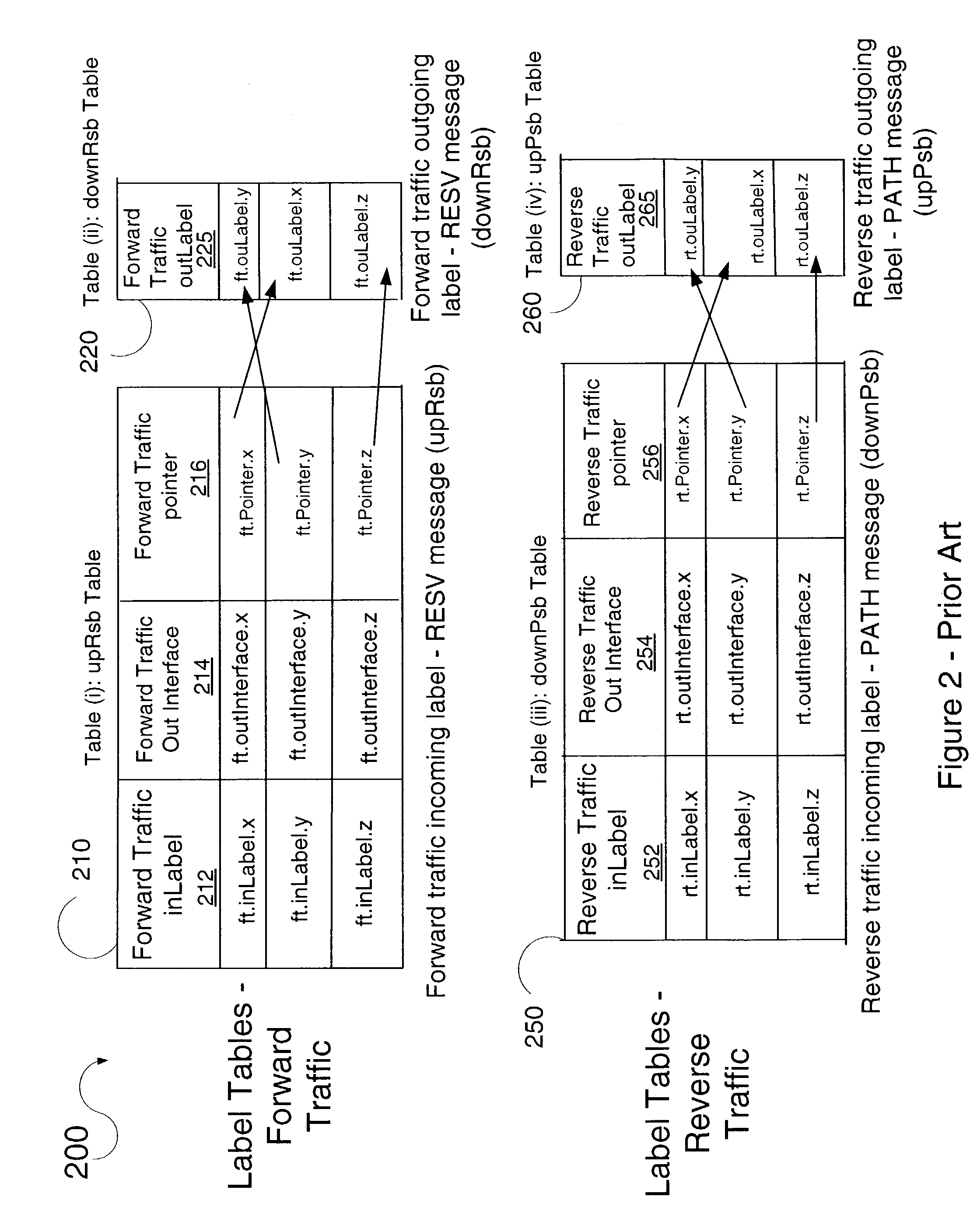
System and method for distributed resource reservation protocol-traffic engineering (RSVP-TE) hitless restart in multi-protocol label switching (MPLS) network
A system of hitless restart in a network, where at least one node in the network provides routing control distributed among ingress ports (ingress cards) and egress ports (egress cards), is disclosed. With distributed routing control, each ingress card has its own routing-control software and each egress card has its own routing-control software. When the routing-software at an ingress port or an egress port of a node is restarted, current connections traversing a restarting ingress card or a restarting egress card continue to function normally during a restart period without data loss. The disclosed system is tailored to a multi-protocol label switching (MPLS) network employing distributed-resource-reservation-protocol traffic engineering (RSVP-TE). The system relies on messaging between ingress card control planes, ingress card data planes, egress card control planes, and egress card data planes of a restarting node.
Owner:RPX CORP +1
Method and system for traffic engineering in secured networks
ActiveUS20080115203A1User identity/authority verificationComputer security arrangementsTraffic capacityInternet traffic engineering
Aspects of a method and system for traffic engineering in an IPSec secured network are provided. In this regard, a node in a network may be authenticated as a trusted third party and that trusted third party may be enabled to acquire security information shared between or among a plurality of network entities. In this manner, the trusted third party may parse, access and operate on IPSec encrypted traffic communicated between or among the plurality of network entities. Shared security information may comprise one or more session keys utilized for encrypting and / or decrypting the IPSec secured traffic. The node may parse IPSec traffic and identify a flow associated with the IPsec traffic. In this manner, the node may generate and / or communicate statistics pertaining to said IPSec secured traffic based on the flow with which the traffic is associated.
Owner:AVAGO TECH INT SALES PTE LTD
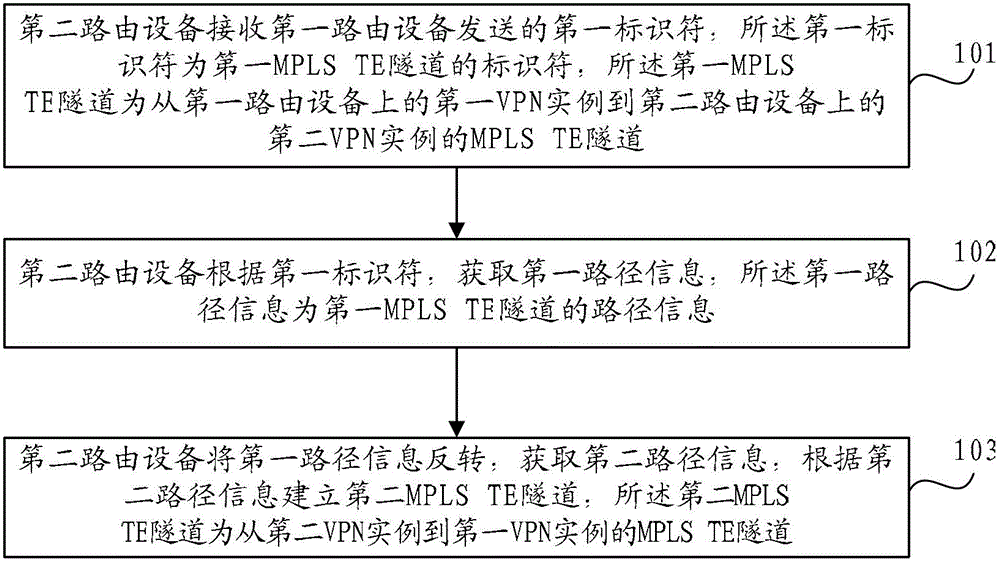
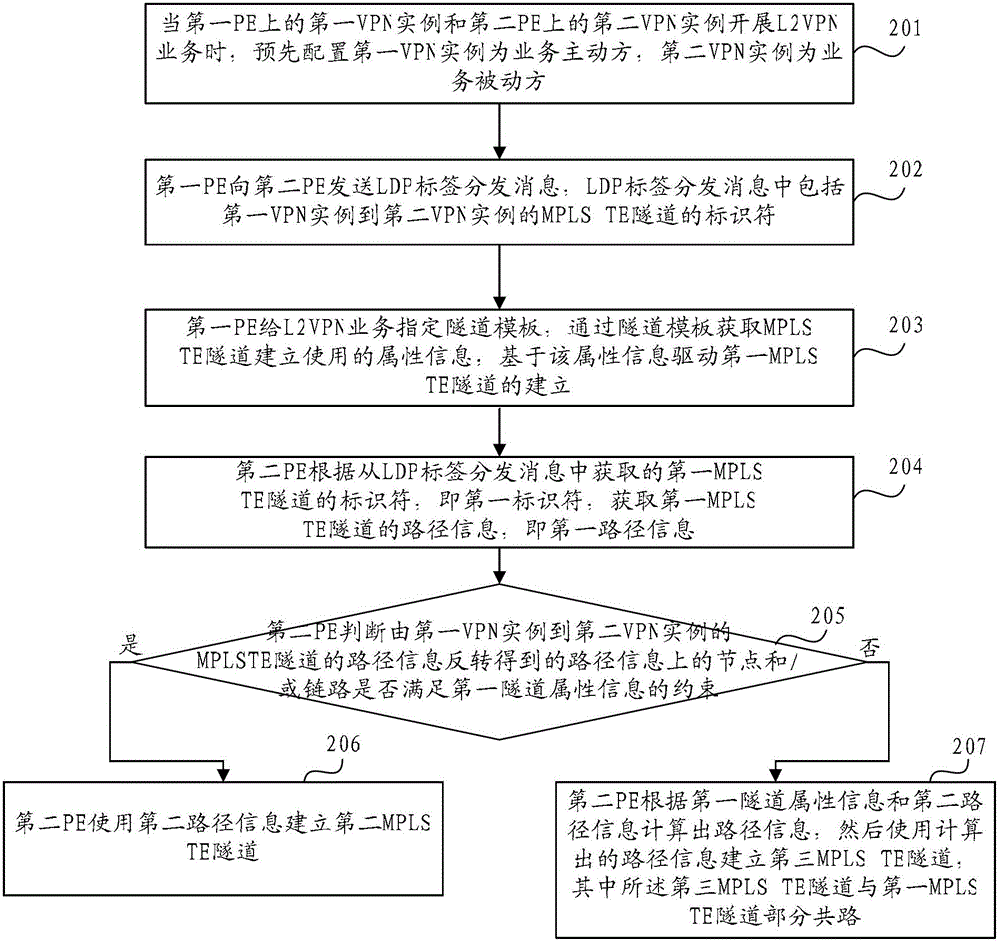
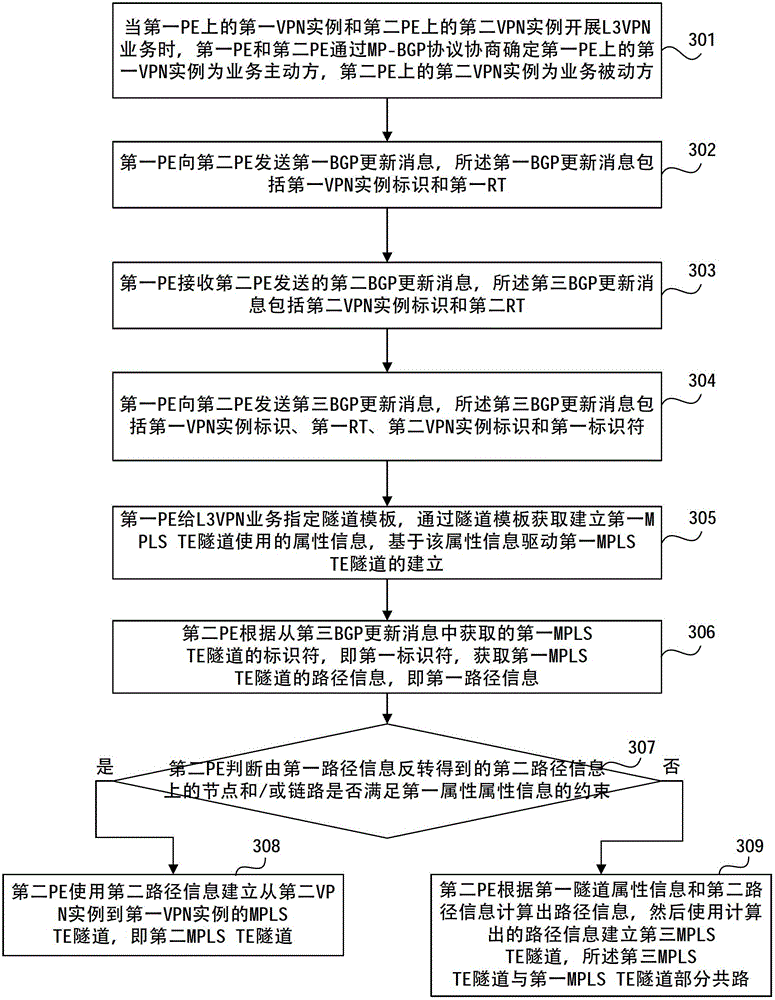
Multi-protocol label switching (MPLS) traffic engineering (TE) tunnel building method and device
The embodiment of the invention provides a multiprotocol label switching traffic engineering tunnel building method and device. The tunnel building method comprises the following steps: a first router device receives identifiers of an MPLS (multi-protocol label switching) TE (traffic engineering) tunnel from the first VPN (virtual private network) embodiment to the second VPN embodiment, sent by the first router device; and according to the identifiers, a second router device obtains the path information of the MPLS TE tunnel from the first VPN embodiment to the second VPN embodiment, and an MPLS TE tunnel from the section VPN embodiment to the first VPN embodiment is established on the basis of the obtained path information, so that the forward and backward bidirectional tunnels share the same path completely or partially, and thus the problems caused by no path sharing in BFD (bidirectional forwarding detection) are solved.
Owner:HUAWEI TECH CO LTD
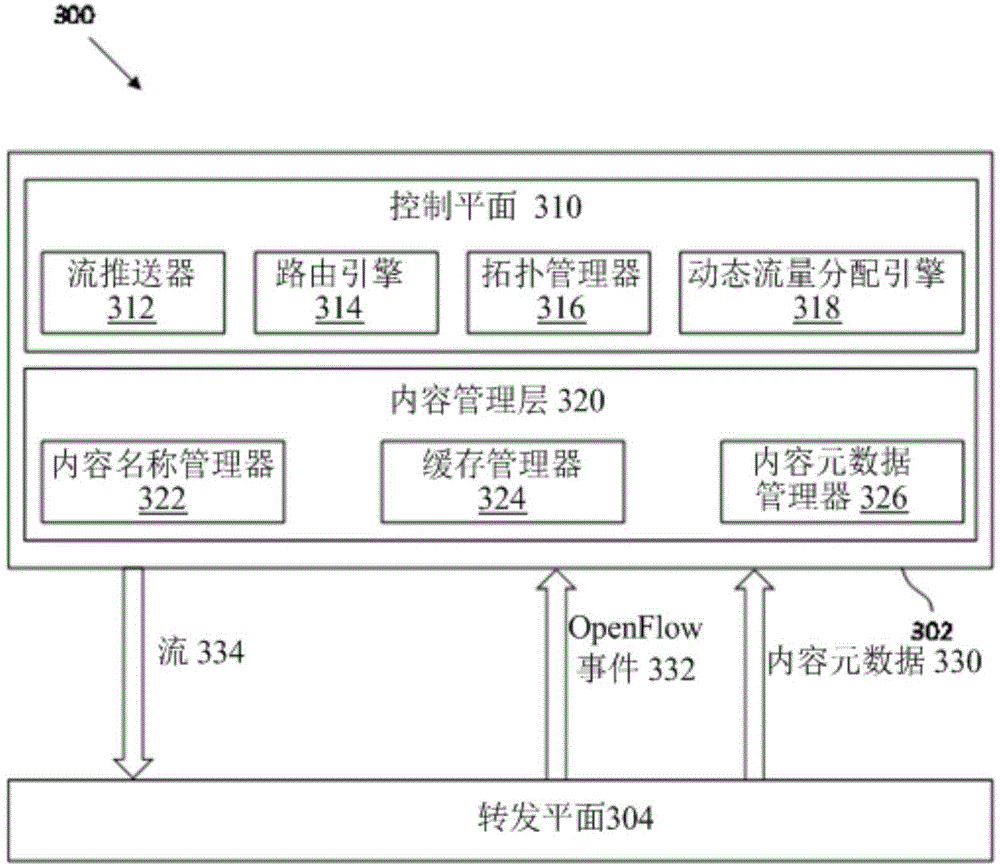
Content based traffic engineering in software defined information centric networks
A method implemented by a network controller, the method comprising obtaining metadata of a content, wherein the content is requested by a client device, allocating one or more network resources to the content based on the metadata of the content, and sending a message identifying the allocated network resources to a switch to direct the content to be served to the client device, wherein the switch is controlled by the network controller and configured to forward the content to the client device using the allocated network resources.
Owner:HUAWEI TECH CO LTD
Processing method for periodic line resource information of traffic engineering
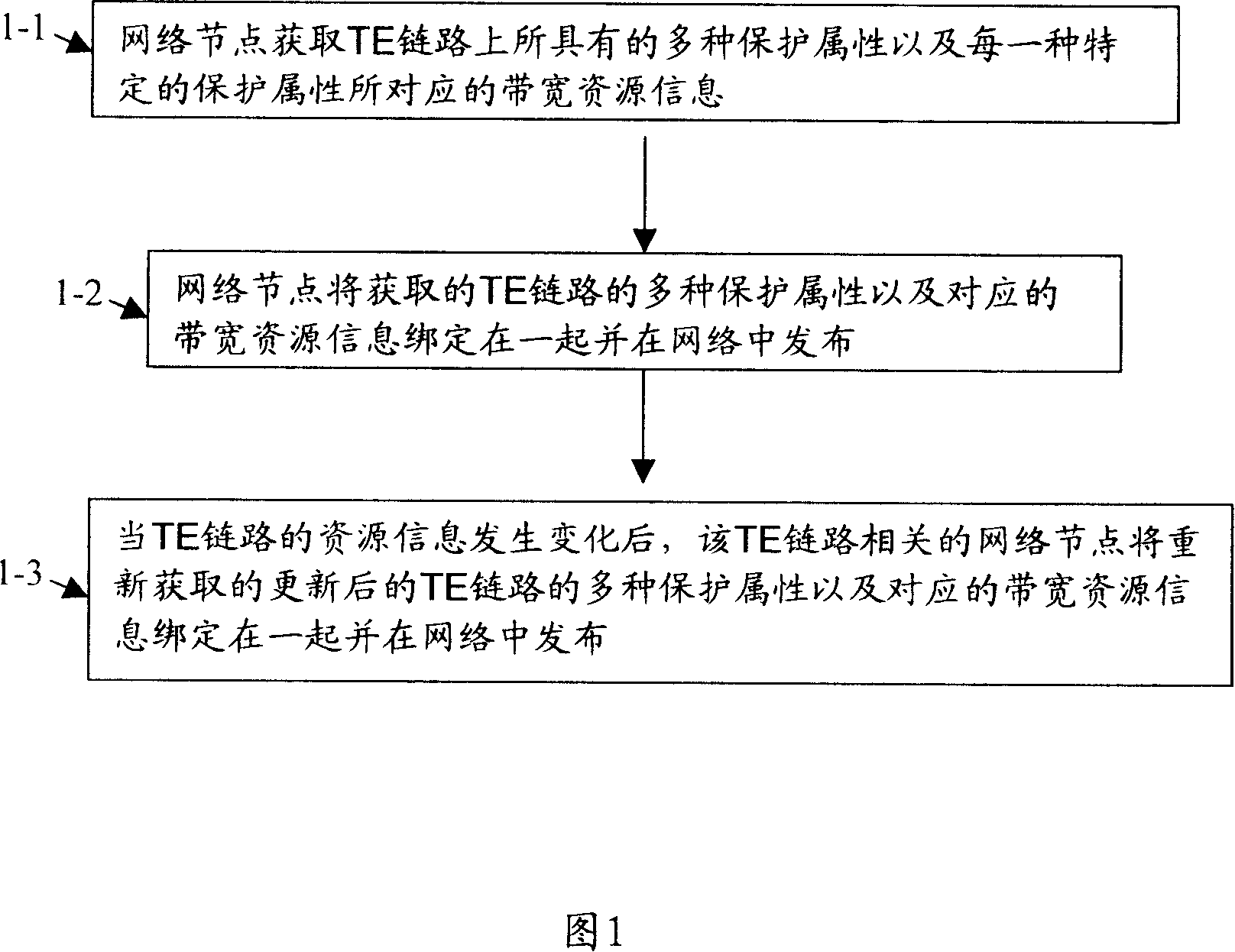
InactiveCN101155064AFlexible handlingUpdate protectionData switching networksInternet traffic engineeringTraffic capacity
The invention provides a processing method of a flow engineering link resource information. The said method comprises: a network node obtaining a great variety of protection attributes and corresponding bandwidth resource information of TE link; the network node issuing a great variety of protection attributes and corresponding bandwidth resource information of TE link. All the network nodes can obtain whole network TE link resource information to make a control plane adequately compatible with a great variety of protection rearranging technique of a transferring plane.
Owner:HUAWEI TECH CO LTD
Method and apparatus for internet traffic monitoring by third parties using monitoring implements
Disclosed is an internet traffic monitoring method. In the method, a first packet, sent from a user client, having a web content request meeting certain monitoring selection criteria is detected. Upon detection of the first packet, a second packet is forwarded to the user client. The second packet has a redirection with a fabricated web content request to a monitoring web page including at least one monitoring implement.
Owner:FRONT PORCH
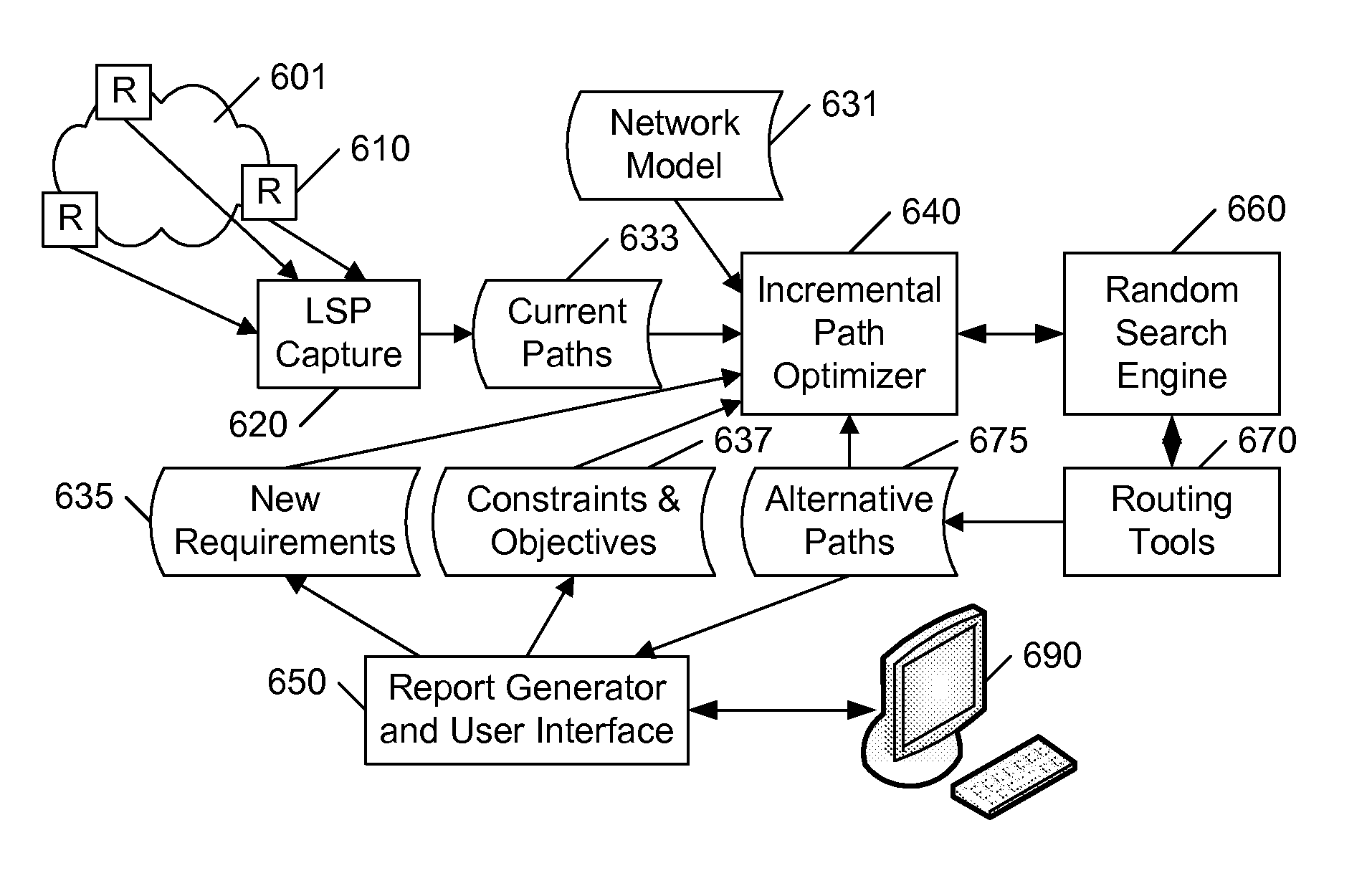
Controlled incremental multi-protocol label switching (MPLS) traffic engineering
ActiveUS20080175150A1Facilitates taskImprove network performanceError preventionFrequency-division multiplex detailsTraffic capacityInternet traffic engineering
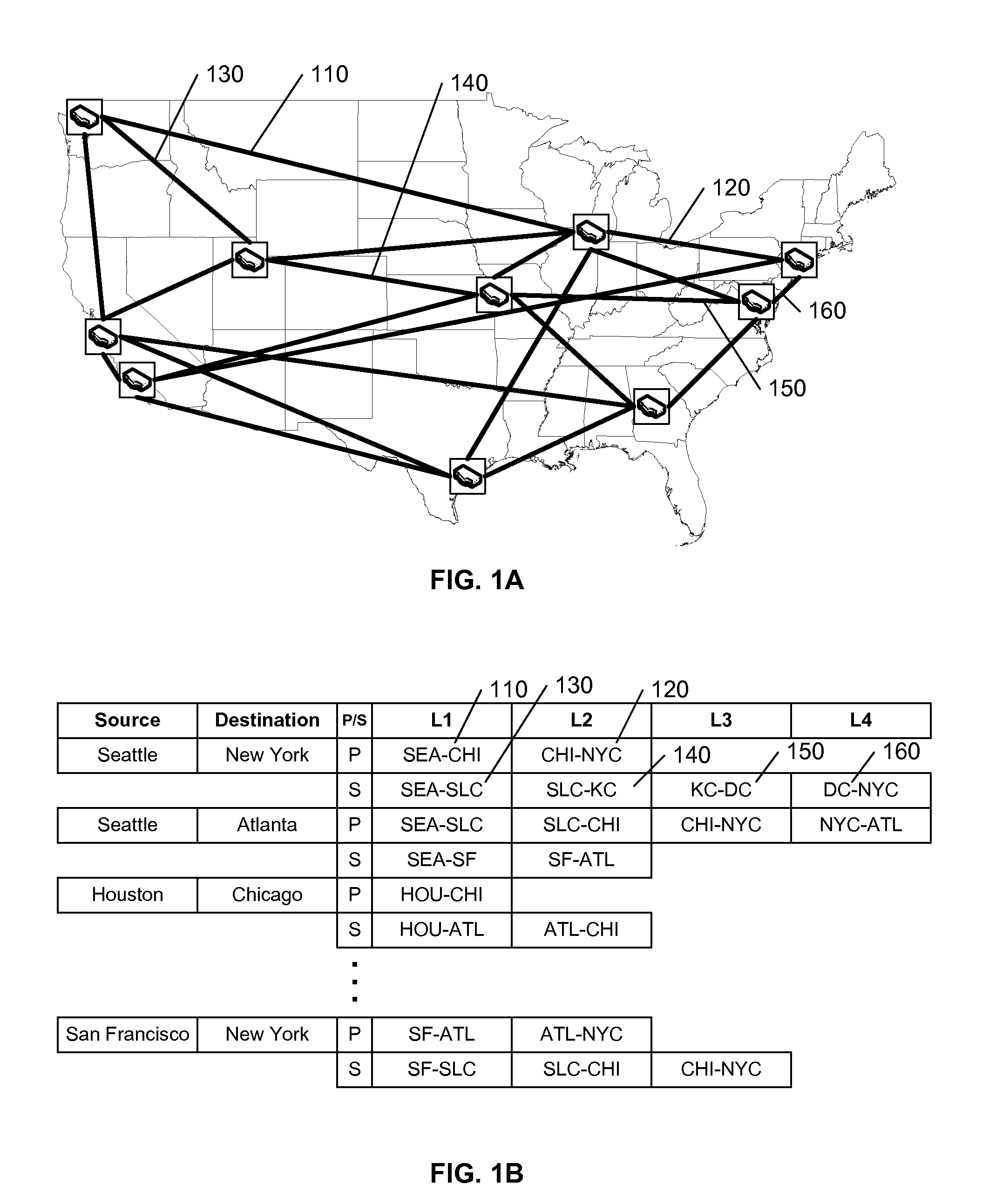
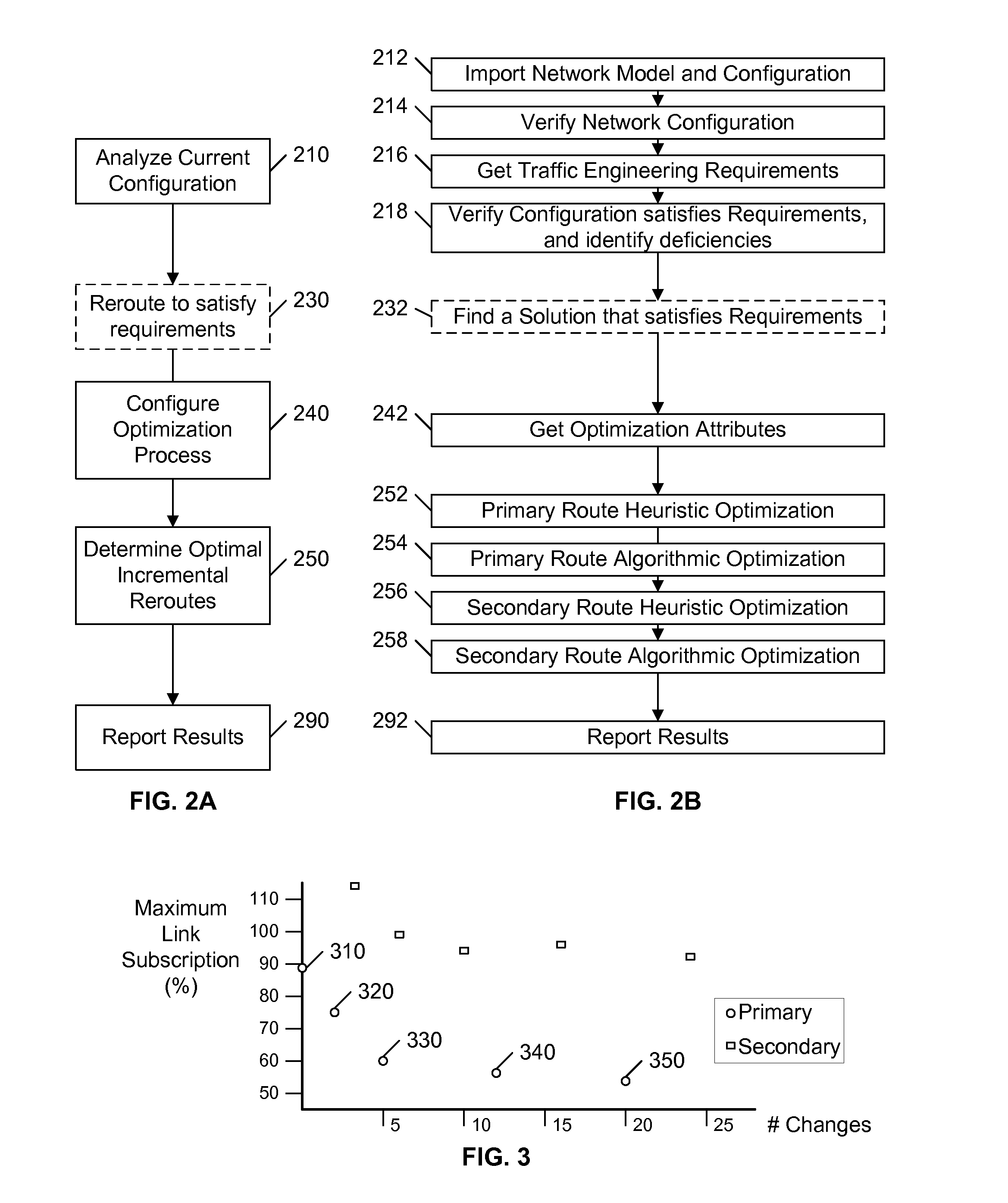
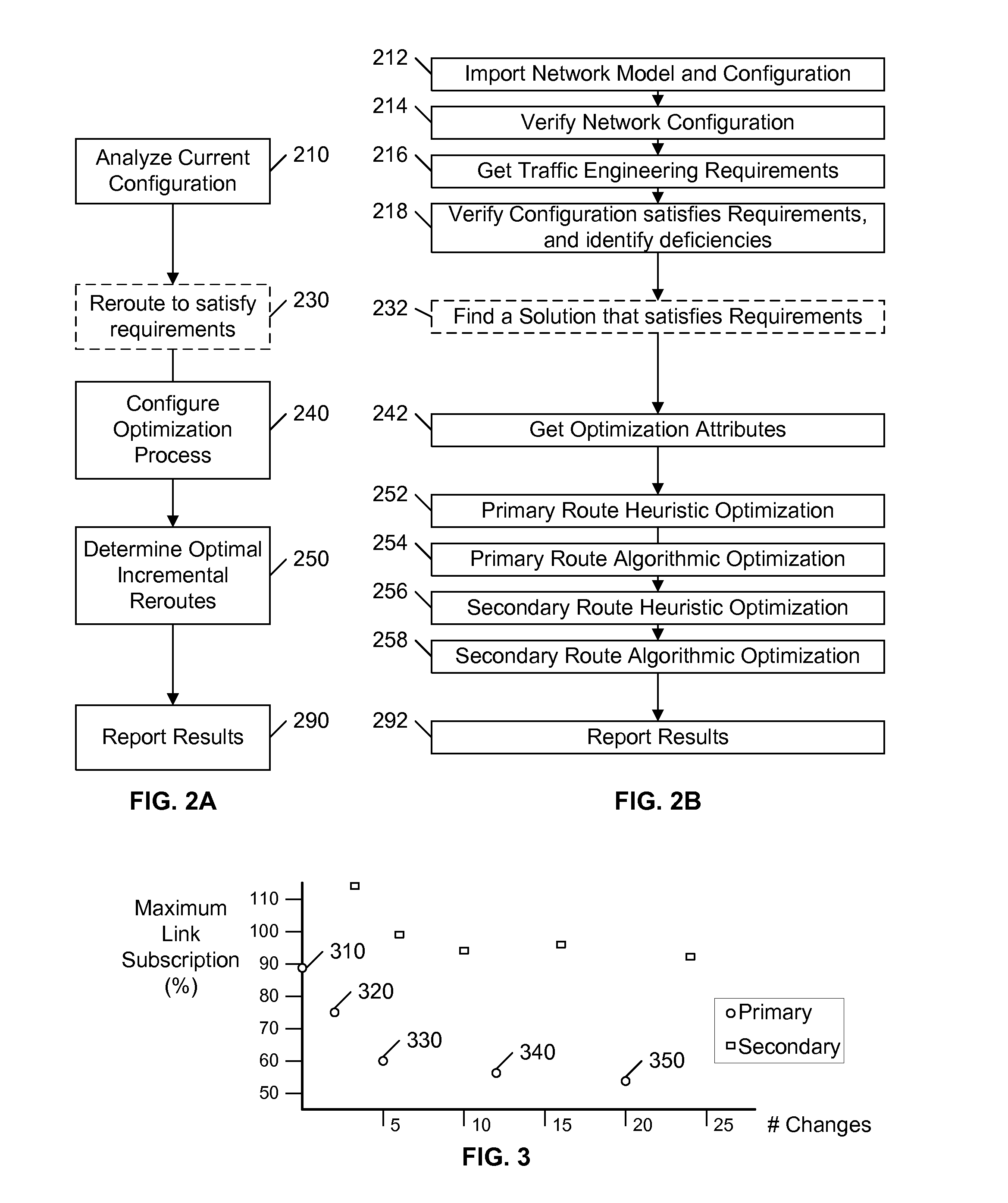
An existing network configuration is assessed, and potential changes to the existing configuration are identified that provide the greatest incremental improvements to the performance of the network. In a preferred embodiment, the user of the system identifies the maximum number (N) of changes that may be implemented in an existing network, and the system provides a set of possible reconfigurations, each requiring fewer than N changes. The user is presented a display of the potential improvement provided by each set as a function of the number of changes in the set, so that the relative incremental gain can be easily visualized. The objective function of the optimization may include conventional load-balancing objectives, or other objectives, such as a global minimization of path lengths.
Owner:RIVERBED TECH LLC
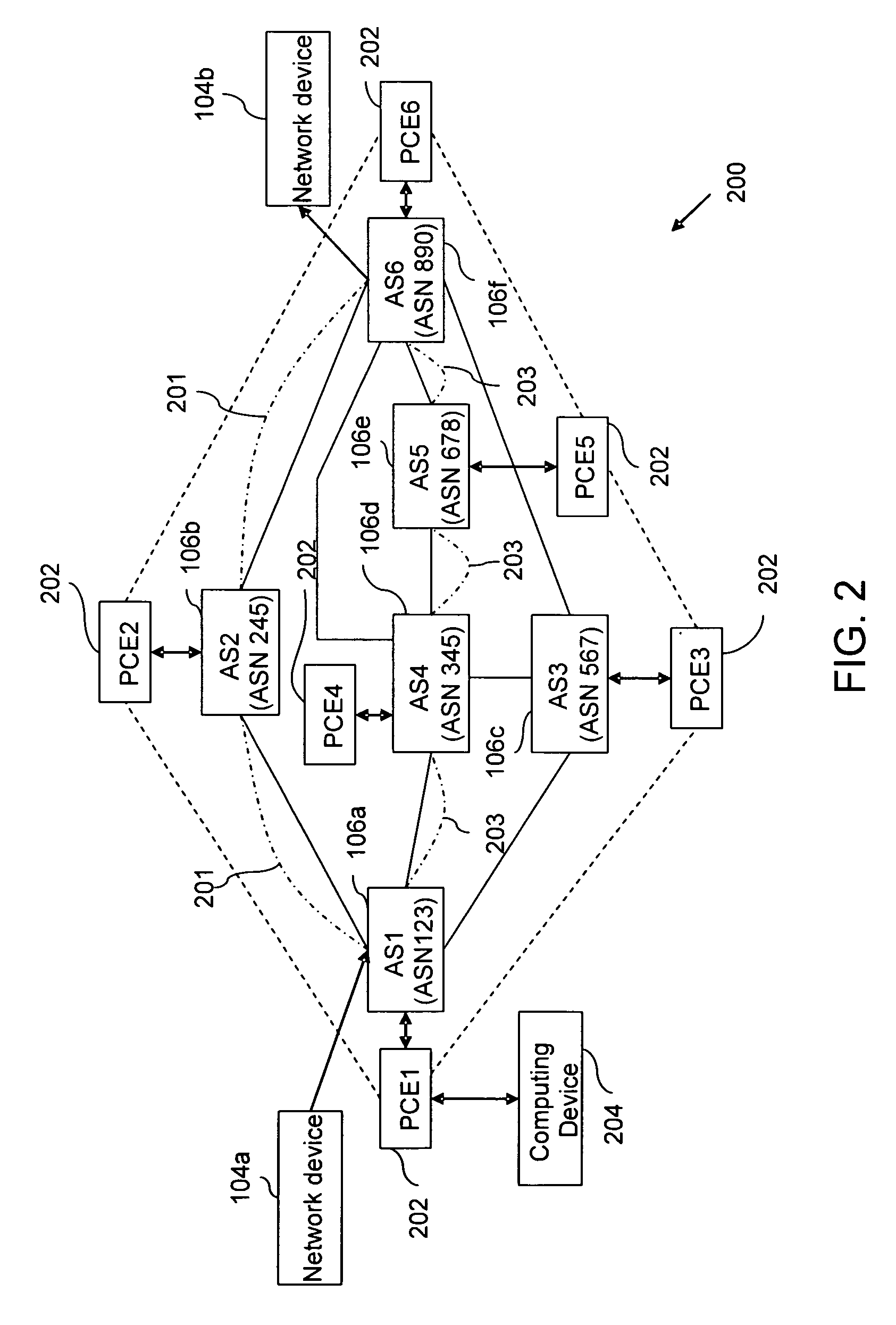
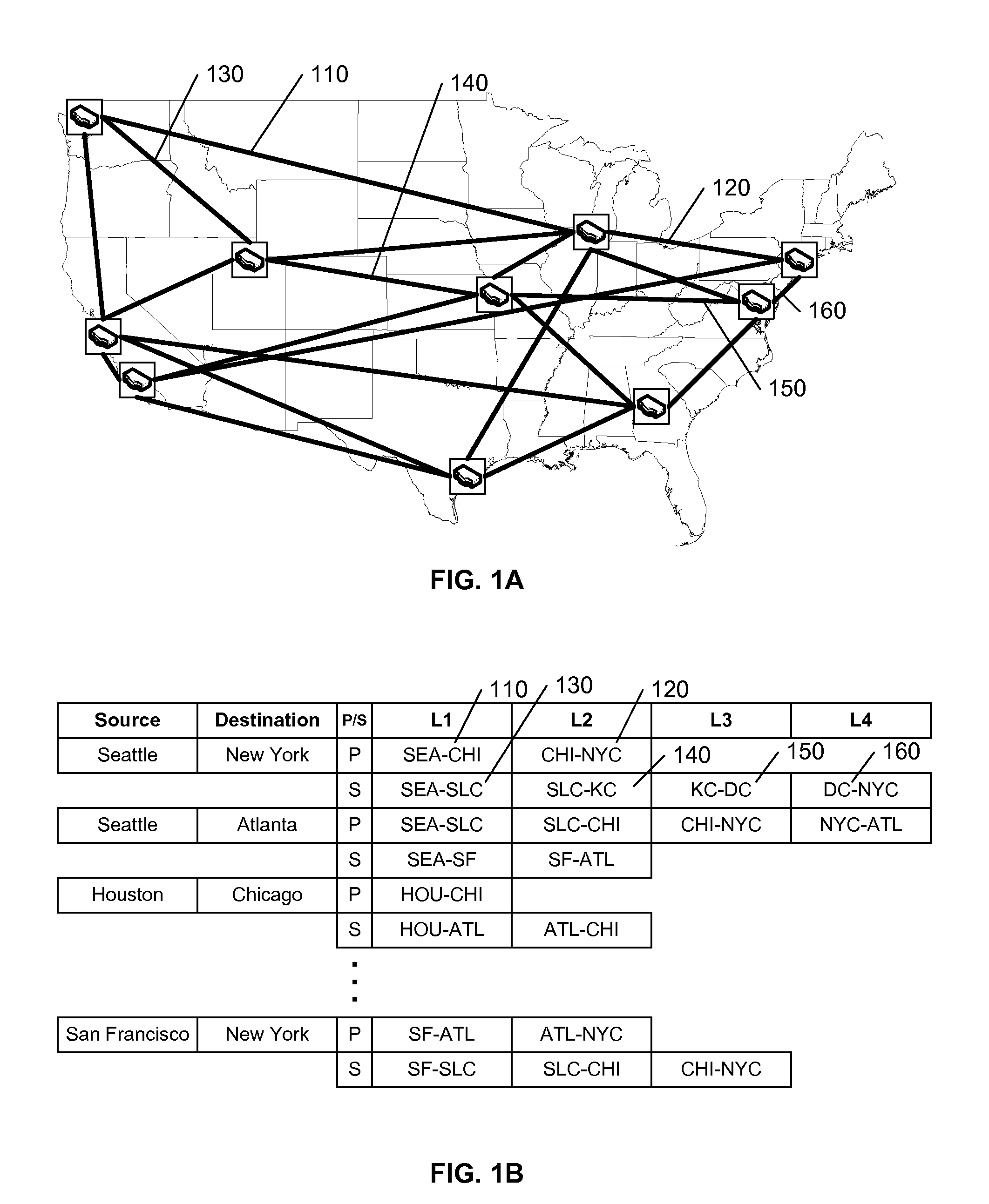
Method and system for computing as-disjoint inter-as traffic engineering-label switched paths (TE-LSPs)
ActiveUS20080049751A1Data switching by path configurationInternet traffic engineeringTopology information
Methods and systems have been provided for constructing autonomous system (AS)-disjoint Traffic Engineering LSPs for load-balancing and protection purposes using AS-Level topology information in a network. The constructed network paths through a plurality of domains may be disjoint or partially disjoint.
Owner:CISCO TECH INC
Offline optimization for traffic engineering with segment routing
InactiveCN107548545AData switching by path configurationTraffic capacityInternet traffic engineering
Owner:ALCATEL LUCENT SAS
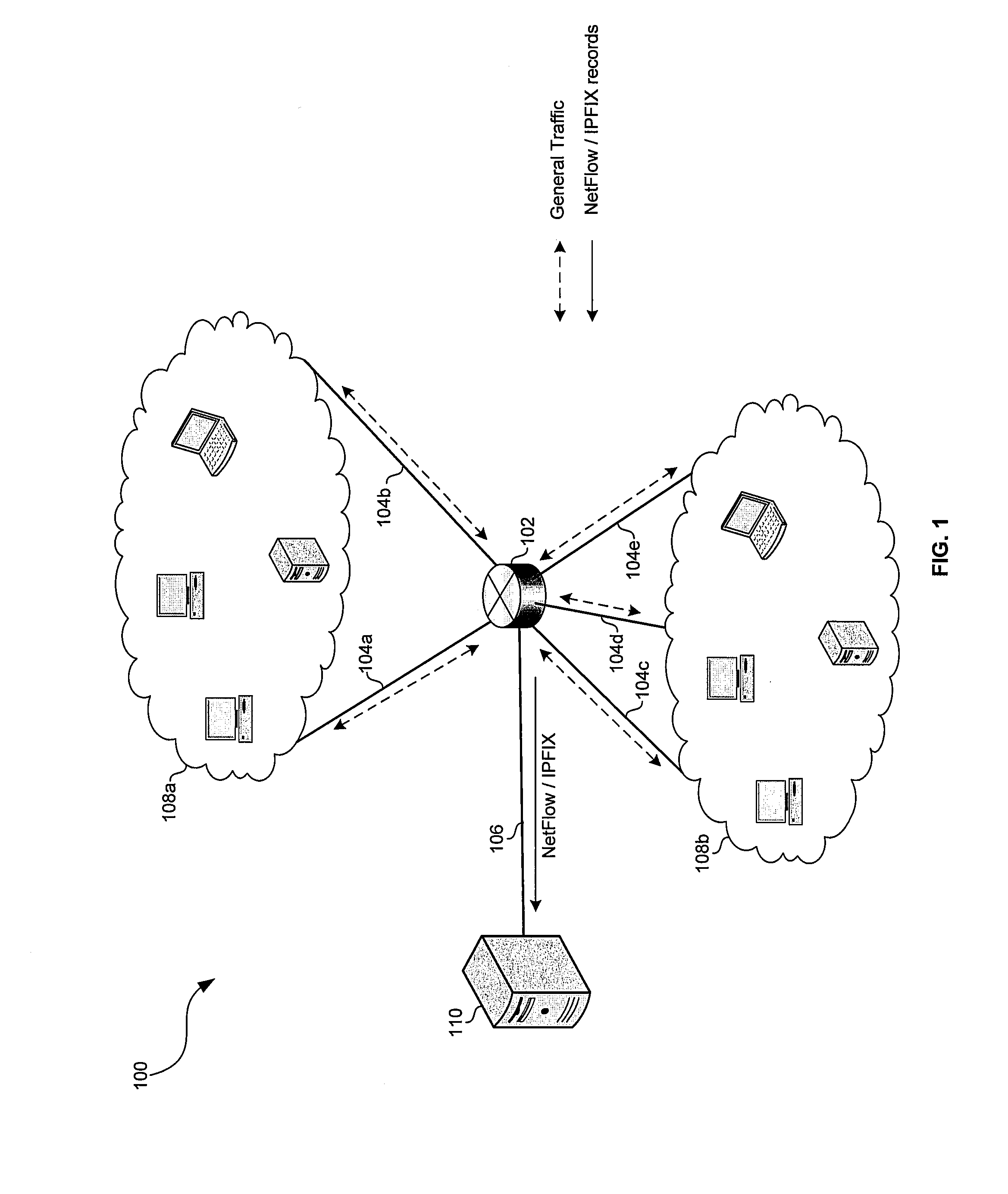
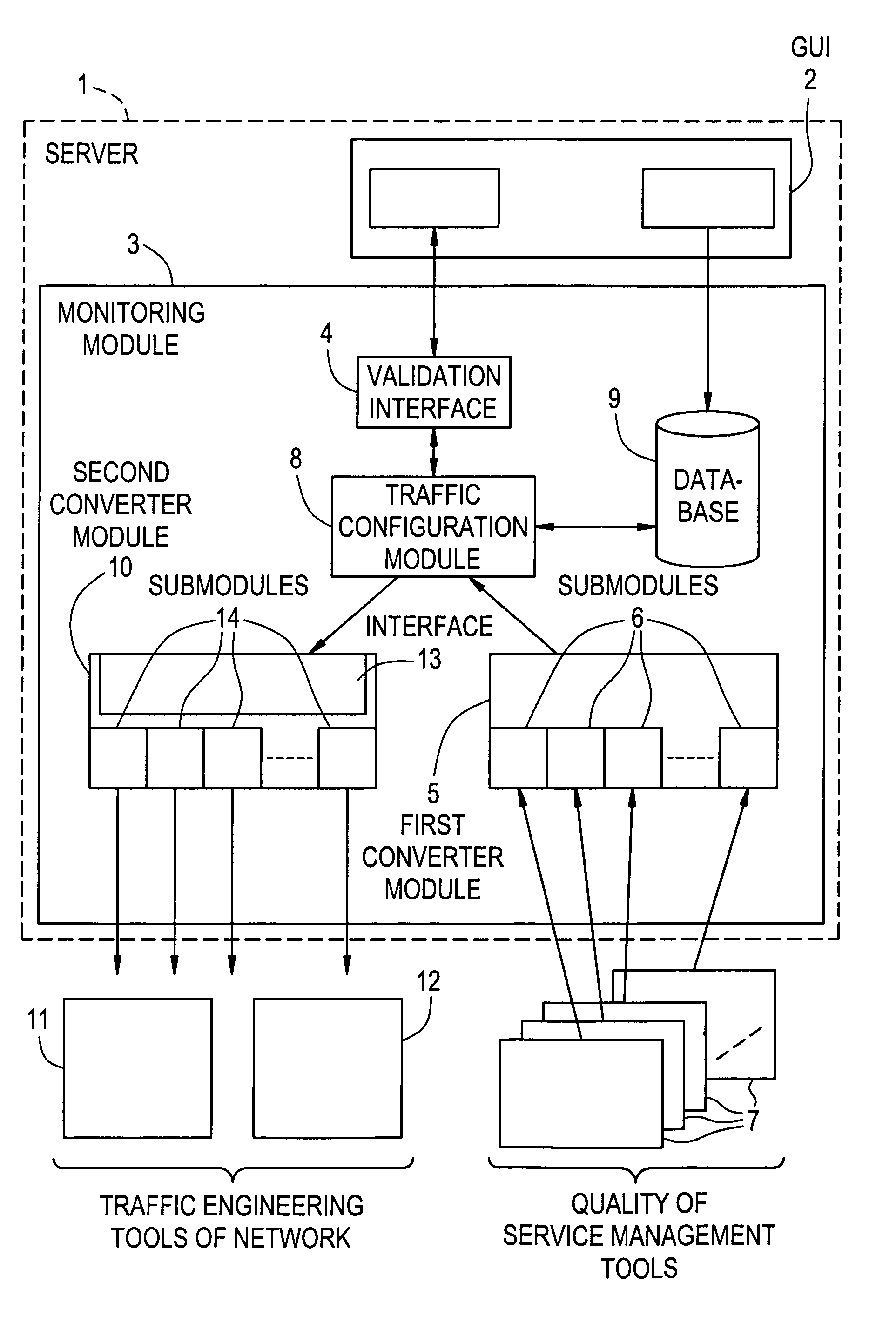
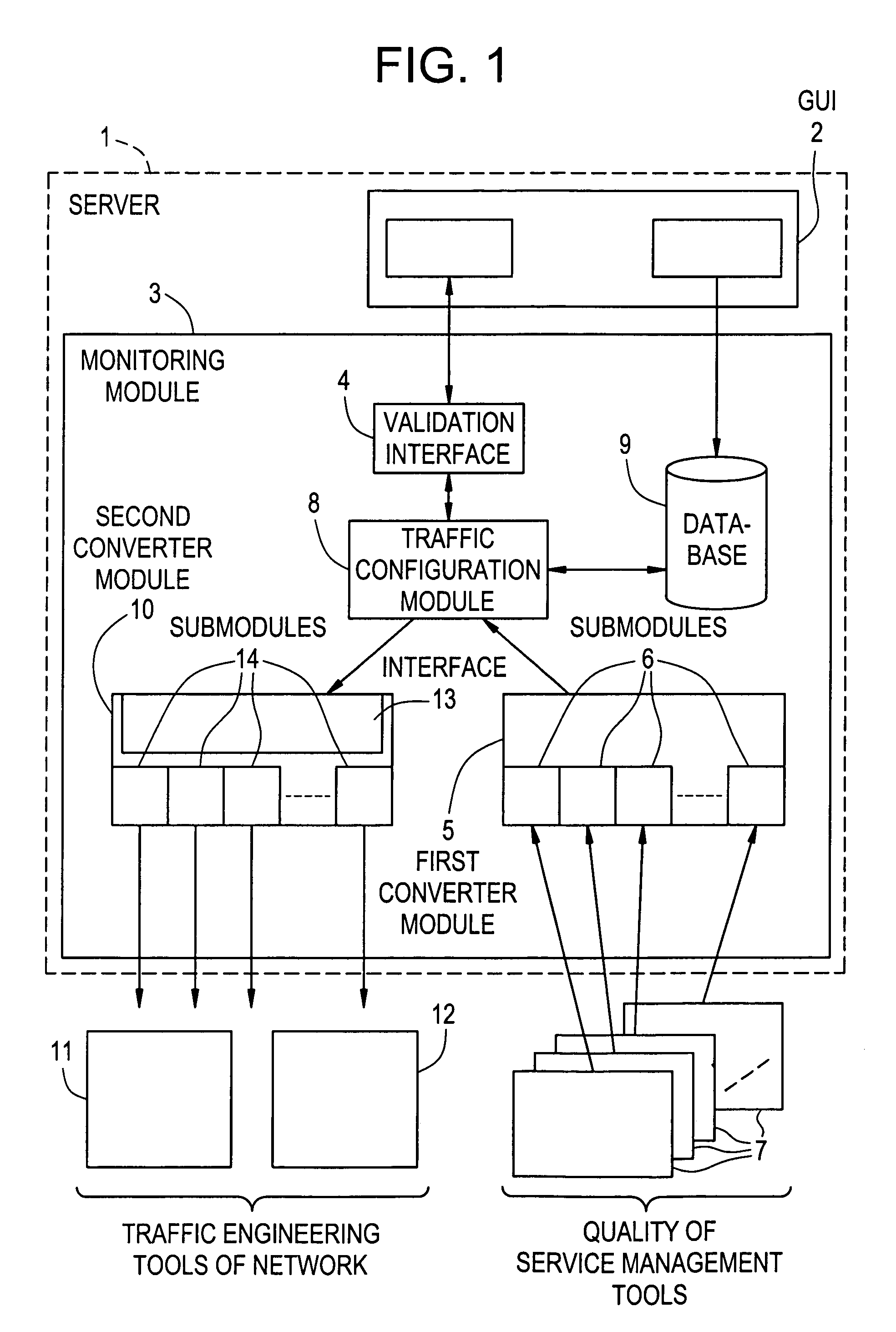
Device for and a method of monitoring service data for automated traffic engineering in a communications network
InactiveUS7050946B2Computer controlError detection/correctionTraffic capacityInternet traffic engineering
A device for monitoring service data for controlling traffic engineering modules (11, 12) and delivered by management modules (7) of a communications network. The device comprises i) a memory (9) for storing rules each defined by at least one condition representative of an event in the network associated with one of the traffic engineering modules (11, 12) and at least one action representative of at least one command to be executed by the associated module and ii) monitoring means (3) adapted, on receiving service data designating an event, to extract from the memory (9) at least one of the rules corresponding to the event and to deliver each command representative of the action associated with the condition representative of the event to the traffic engineering module (11, 12) associated with that event in the extracted rule.
Owner:ALCATEL LUCENT SAS
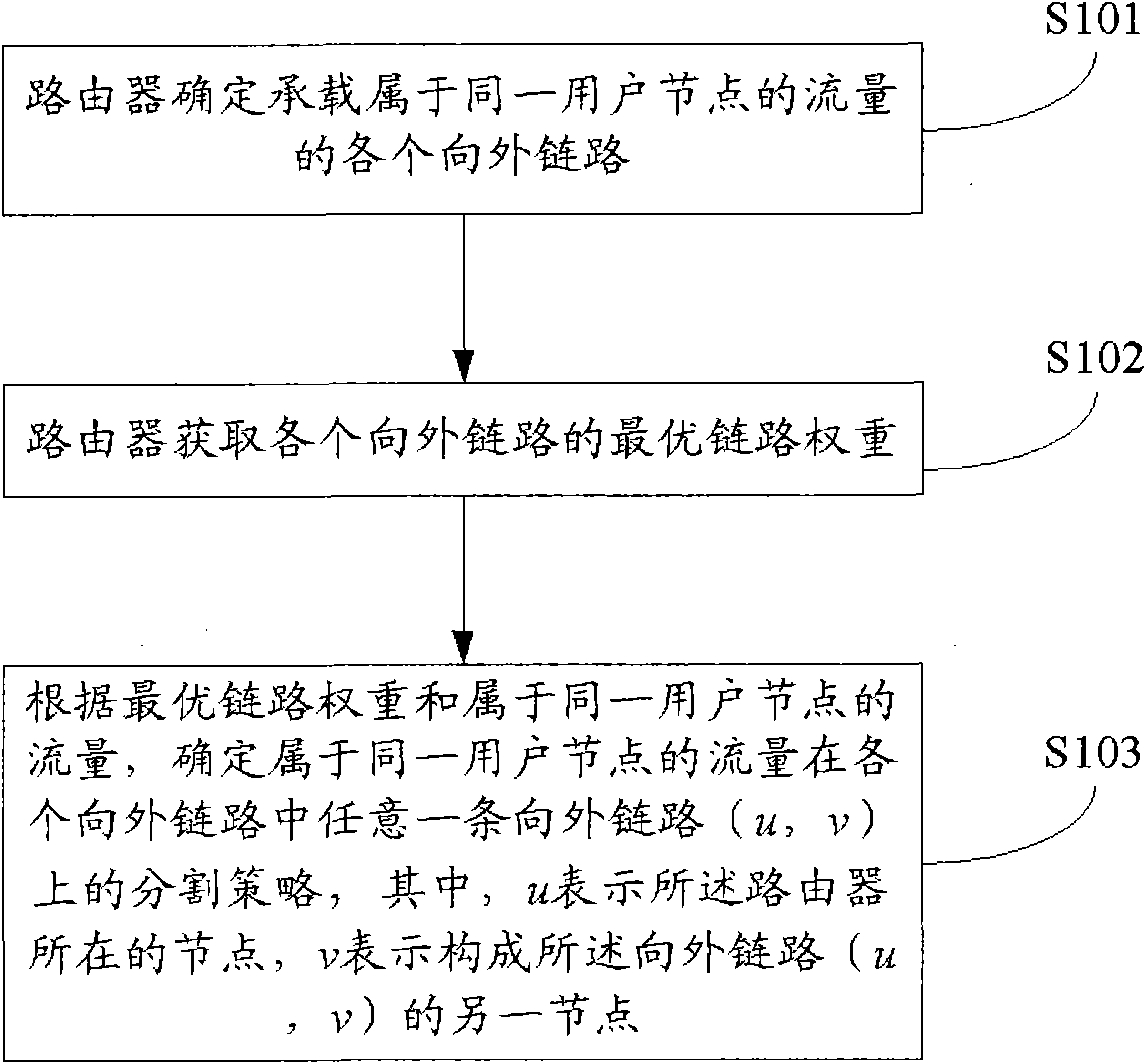
Traffic engineering and server selection joint optimization method, system and related equipment
InactiveCN102136998AReduce delivery volumeShort timeData switching networksTraffic capacityInternet traffic engineering
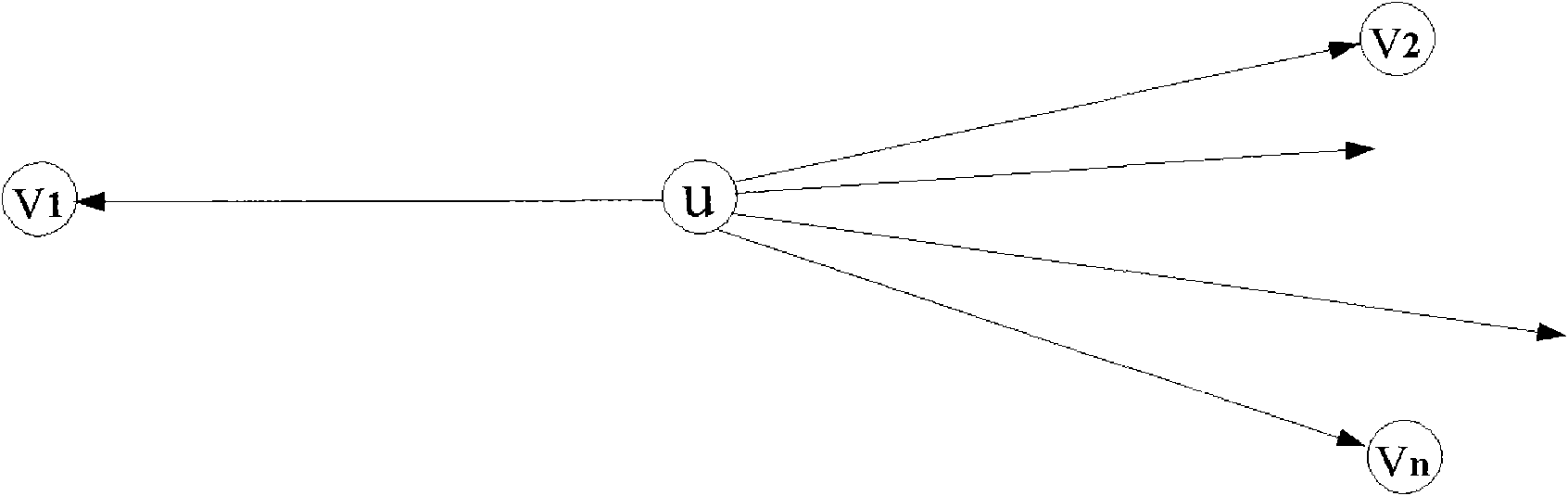
The embodiment of the invention provides a traffic engineering and server selection joint optimization method, a traffic engineering and server selection joint optimization system and related equipment. An optimal solution is calculated by utilizing a small amount of information in a relatively shorter convergence time on the premise of not disclosing key bottom-layer network information to a content provider (CP) by an instant service provider (ISP). The method comprises that: a router determines each outgoing link bearing traffic belonging to the same user node; the router acquires optimal link weights of each outgoing link; and the router acquires determines a division strategy of the traffic belonging to the same user node on any outgoing link (u,v) in the outgoing links according to the optimal link weights and the traffic belonging to the same user node. In the method, the system and the related equipment, calculation is not required to be performed for a plurality of turns, so the amount of transmitted information is greatly reduced, the convergence time of the system is shortened, time consumption is low generally, and the traffic division determining efficiency is higher.
Owner:HUAWEI TECH CO LTD
Method and device for differentiating service traffic engineering
InactiveCN101594289AEasy to distinguishReduce business riskEnergy efficient ICTNetworks interconnectionTraffic capacityDifferentiated services
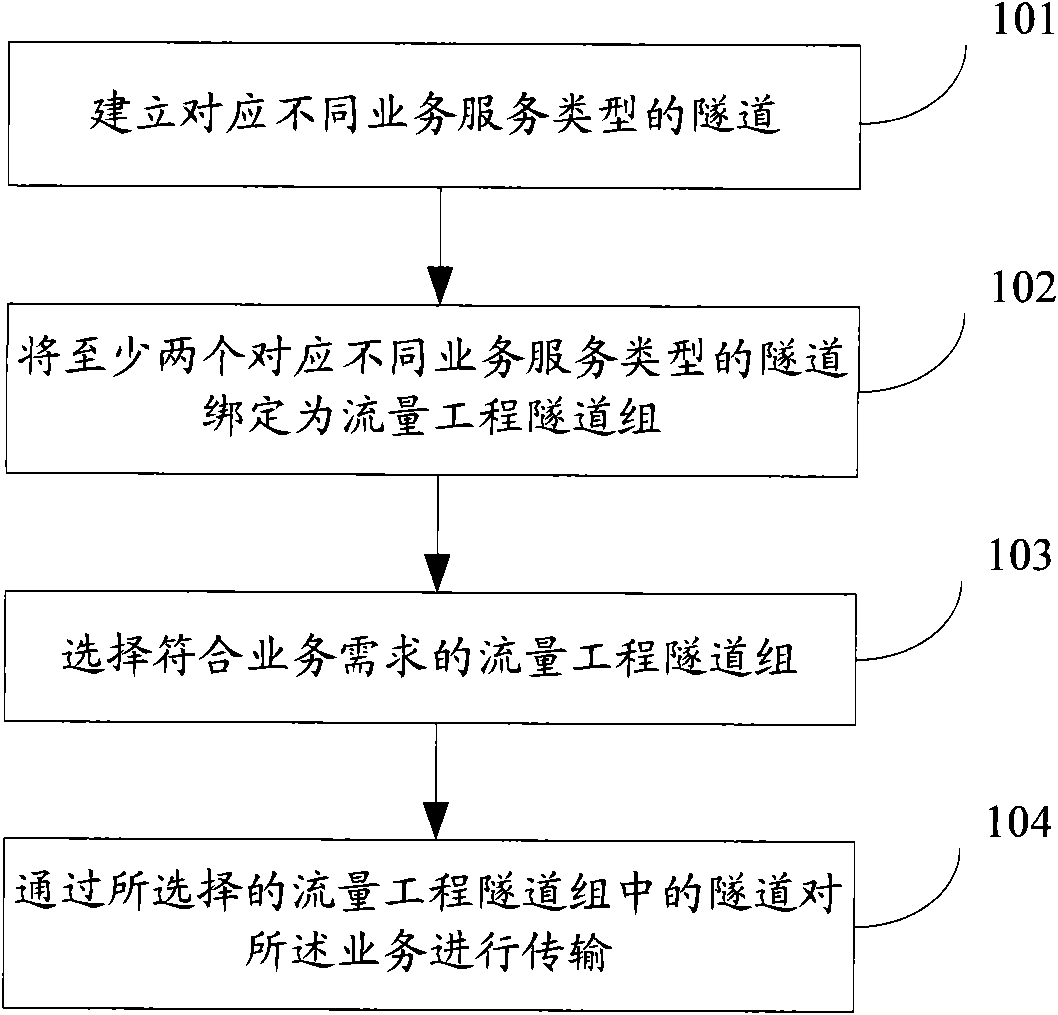
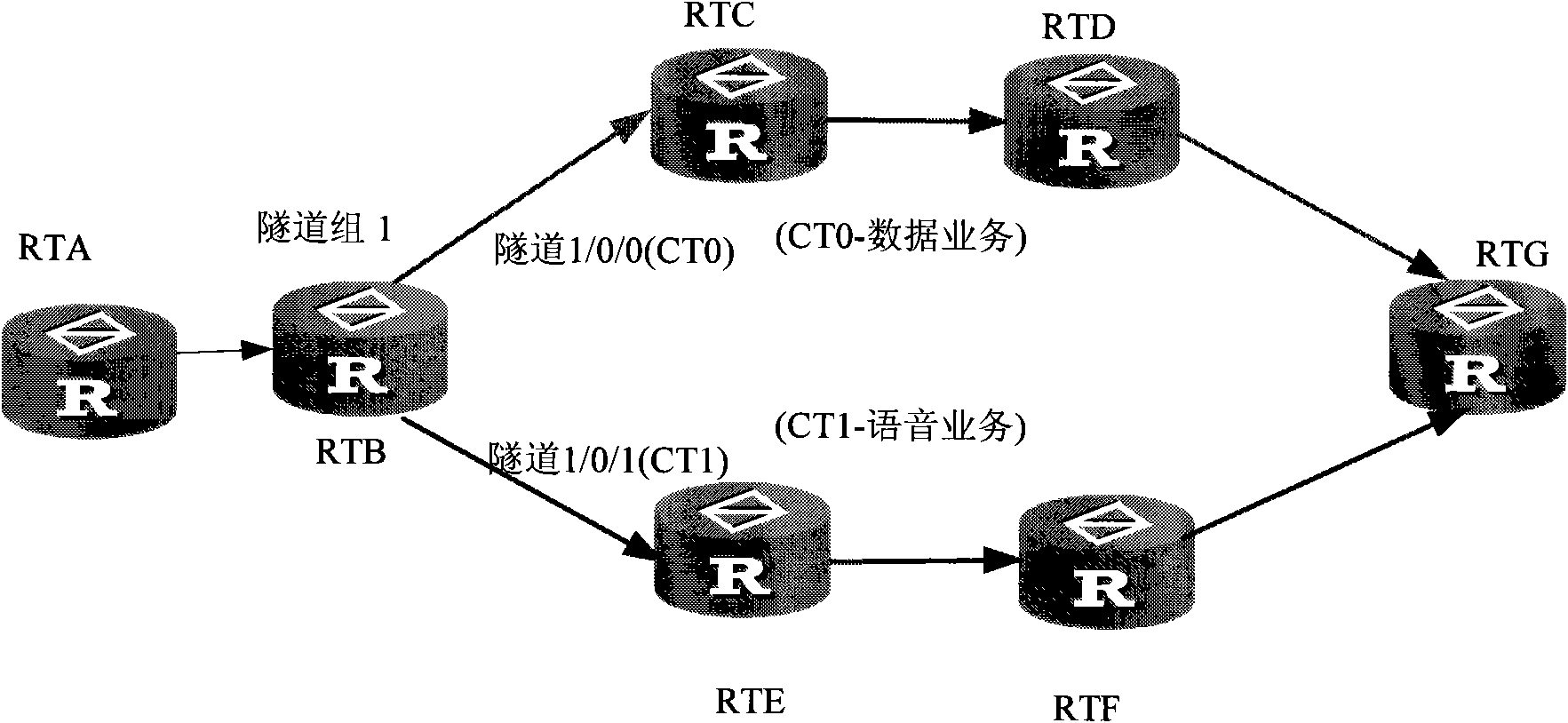
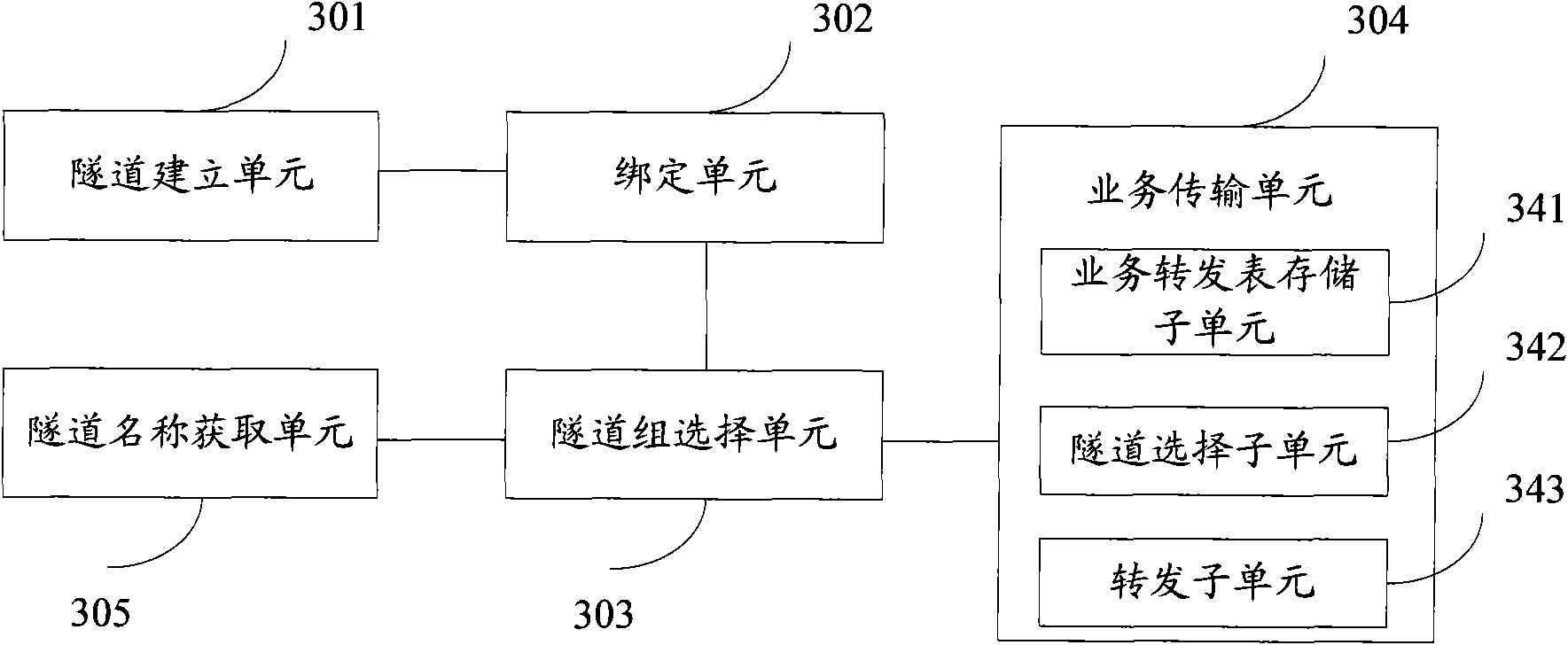
The invention discloses a method and a device for differentiating service traffic engineering. The method comprises the following steps: bonding at least two tunnels corresponding to different service types into a traffic engineering tunnel group; selecting a traffic engineering tunnel group in accordance with the service needs when services are needed transmitting; enabling different service traffics to enter different tunnels of the traffic engineering tunnel group and transmitting the services by the tunnels in the traffic engineering tunnel group. The invention can be utilized to simply and conveniently differentiate service traffic engineering without expanding the prior protocols and can lower the service danger.
Owner:HUAWEI TECH CO LTD
Method, apparatus and system for deploying TE tunnel of traffic engineering
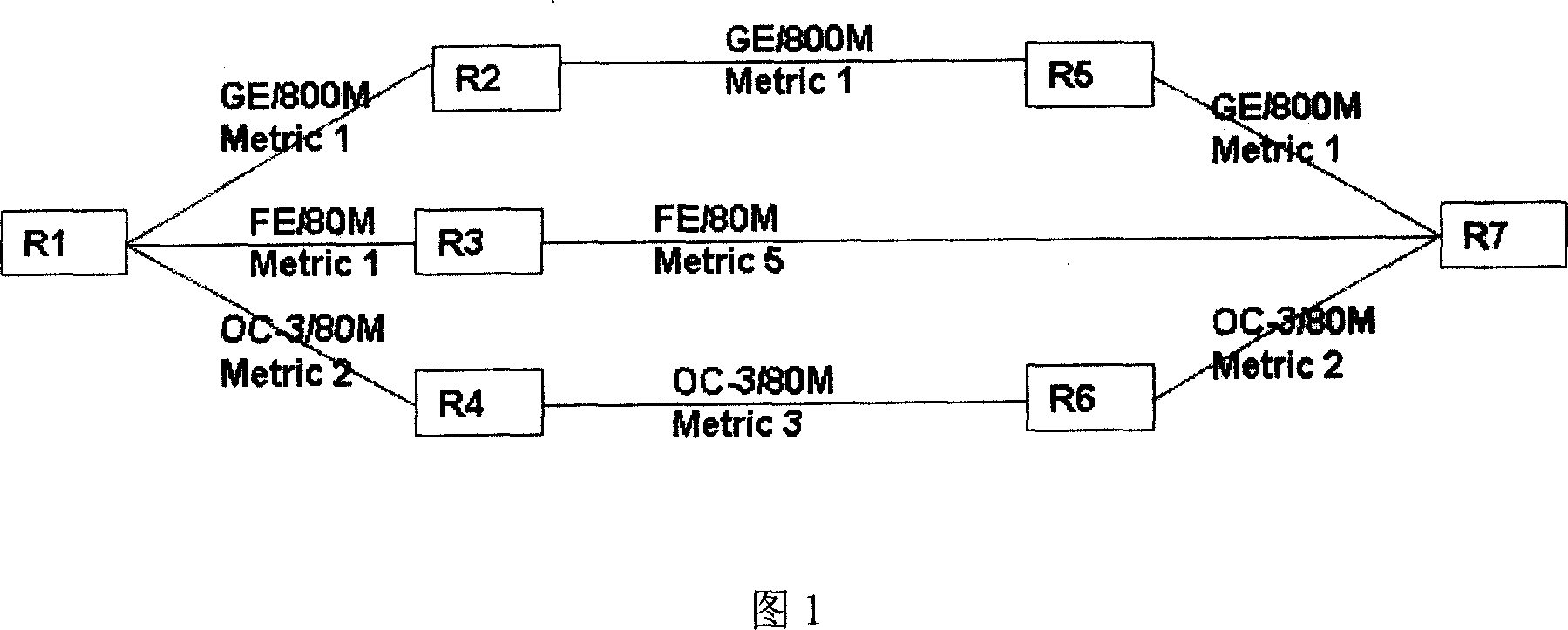
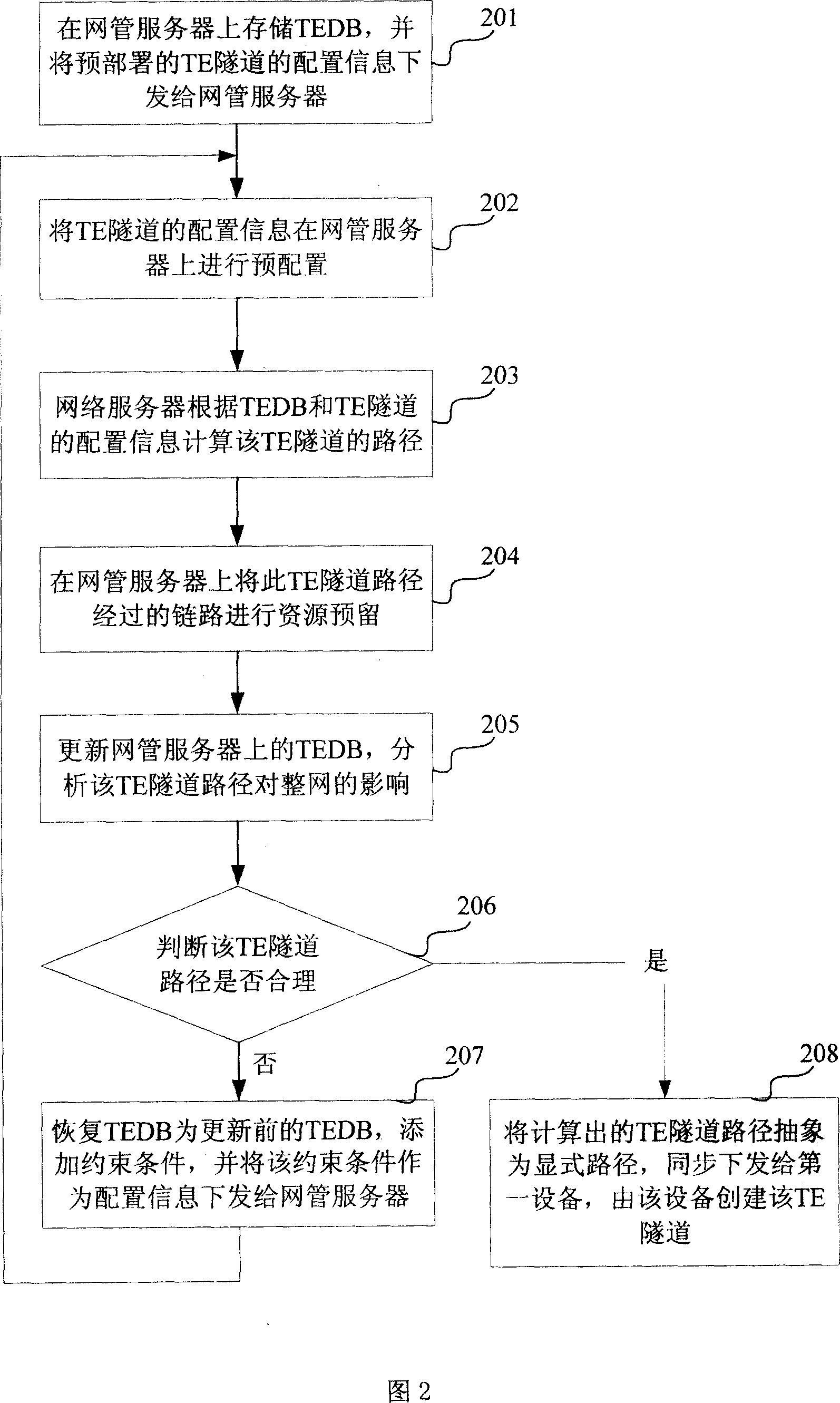
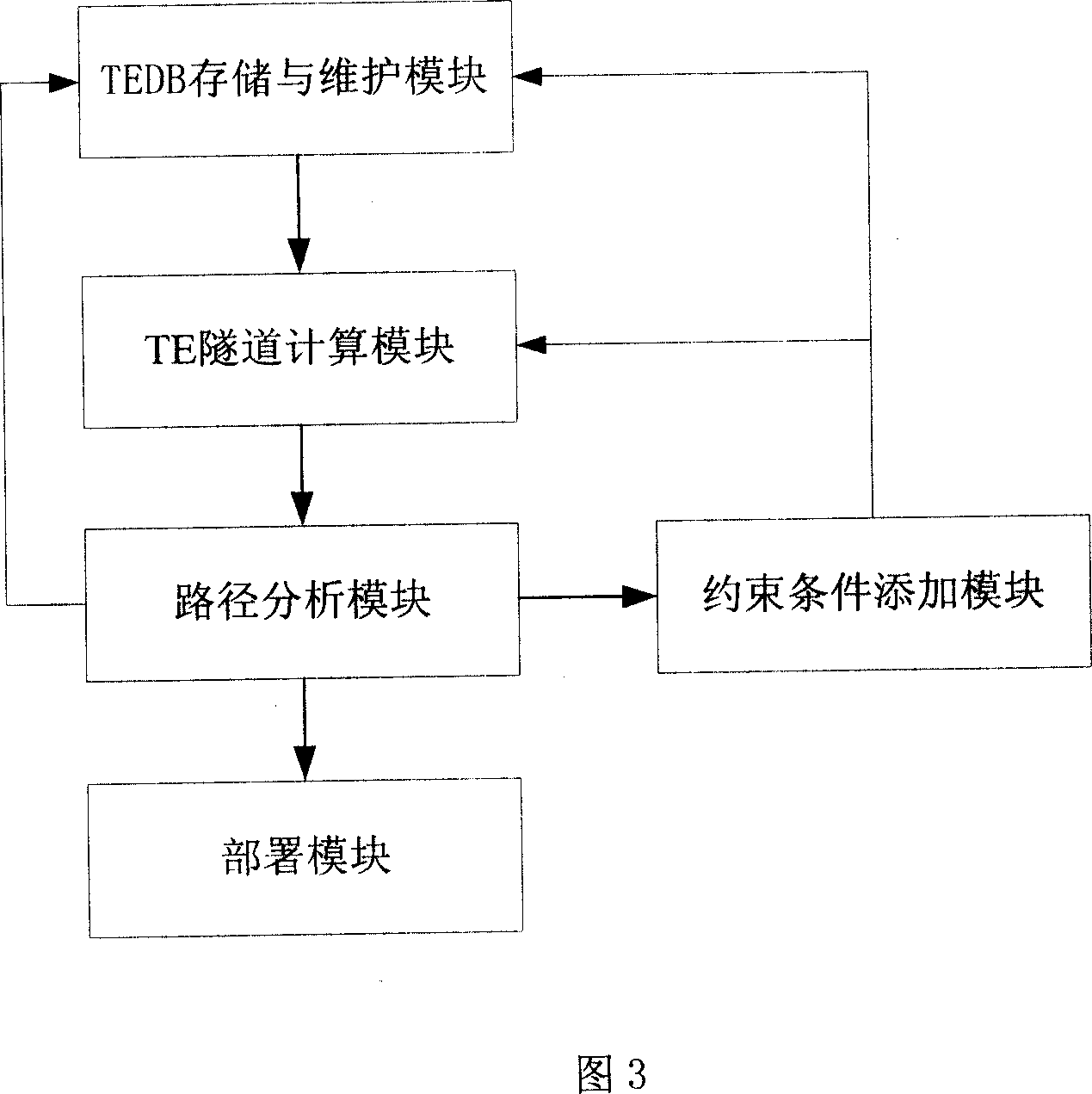
InactiveCN101014006ASupport protection applicationUse flexibilityNetworks interconnectionInternet traffic engineeringUsability
The invention provides one method, device and system to distribute flow engine channel in network communication field, which comprises the following steps: storing TEDS and set information on servo and computing TE channel path and analyzing whether it is proper, if not, adding binds for new path till it is proper and sending the distribution information to next device. The invention provides one device to distribute the channel, which comprises TEDB memory and sustain module, TE channel computation module, path analysis module and bind adding module and distribution module. The invention also provides one system composed of servo and device.
Owner:HUAWEI TECH CO LTD
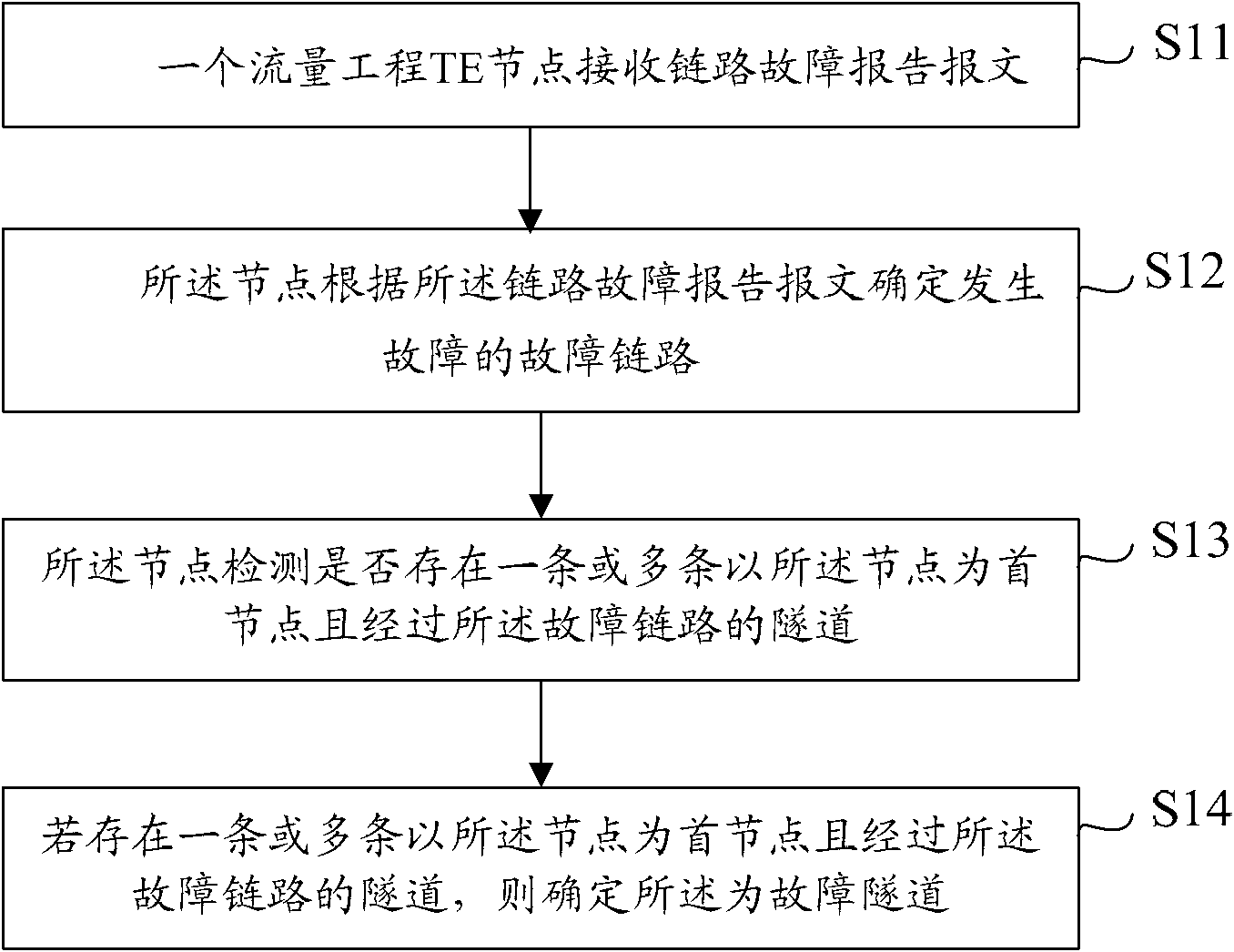
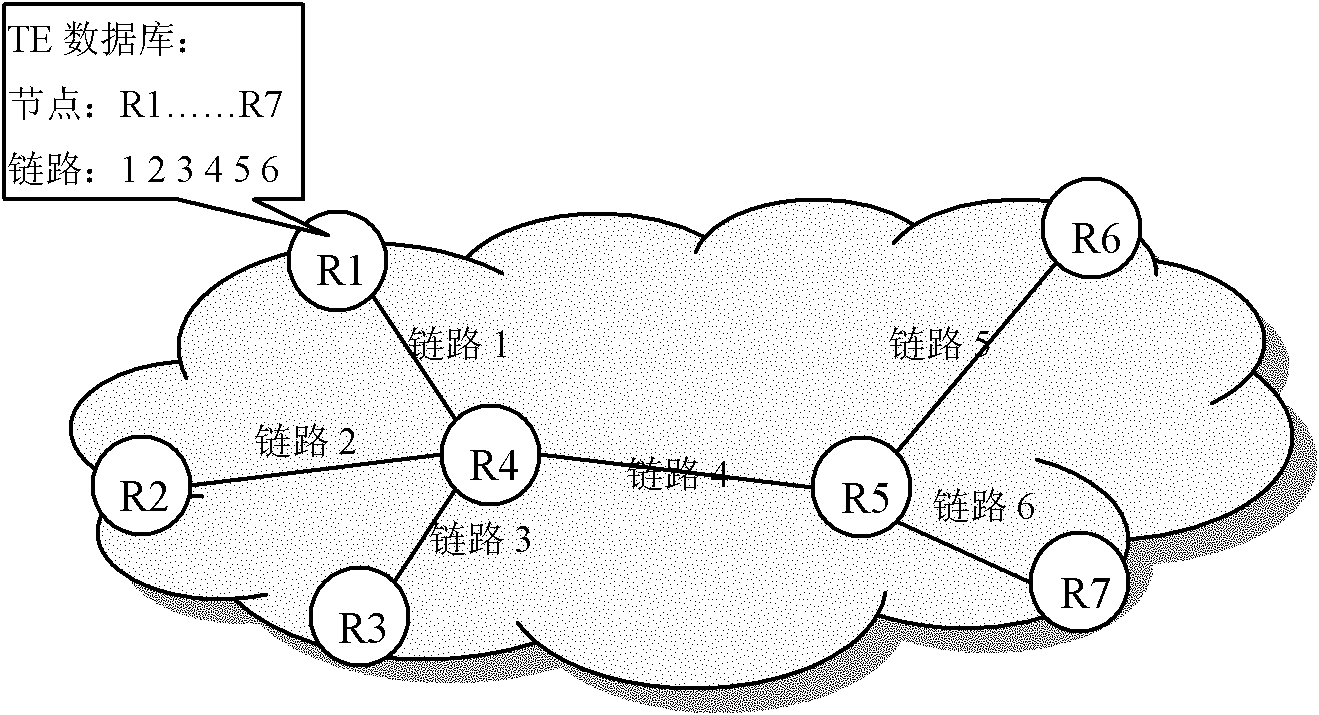
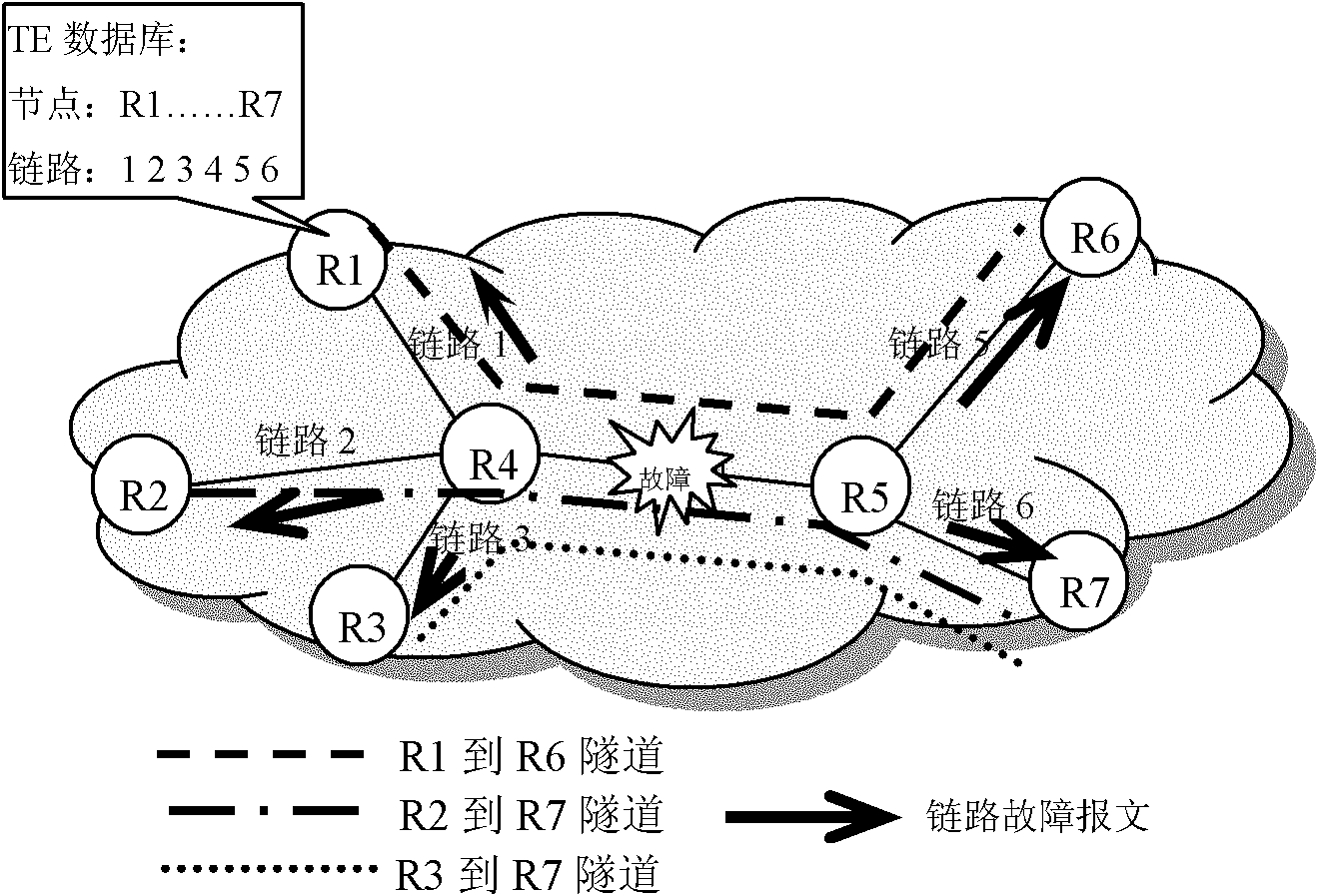
Method for detecting tunnel faults and traffic engineering (TE) node
The embodiment of the invention provides a method for detecting tunnel faults and a traffic engineering (TE) node. In the method, a TE node receives a link fault report message; the node determines a fault link having a fault in accordance with the link fault report message; the node inspects whether one or more tunnels which take the node as the head node and pass through the fault link exist or not; and if so, determining the tunnel(s) to be a fault tunnel(s). According to the embodiment of the invention, the TE node can detect all fault tunnels once without judging the fault tunnels one by one until a fault notification of every tunnel is received. Therefore, compared with the prior art, the TE node can detect fault tunnels in time in a network with a large number tunnels.
Owner:HUAWEI TECH CO LTD
Controlled incremental multi-protocol label switching (MPLS) traffic engineering
ActiveUS7639609B2Efficient and effective useImprove survivabilityError preventionTransmission systemsInternet traffic engineeringTraffic capacity
An existing network configuration is assessed, and potential changes to the existing configuration are identified that provide the greatest incremental improvements to the performance of the network. In a preferred embodiment, the user of the system identifies the maximum number (N) of changes that may be implemented in an existing network, and the system provides a set of possible reconfigurations, each requiring fewer than N changes. The user is presented a display of the potential improvement provided by each set as a function of the number of changes in the set, so that the relative incremental gain can be easily visualized. The objective function of the optimization may include conventional load-balancing objectives, or other objectives, such as a global minimization of path lengths.
Owner:RIVERBED TECH LLC
Method and device for selecting transmission path based on traffic engineering
ActiveCN109561028AAvoid congestionReduce congestionNetworks interconnectionInternet traffic engineeringTraffic capacity
The invention discloses a method and device for selecting a transmission path based on the traffic engineering, which relates to the technical field of communication and is used for solving a problemof link congestion caused by improper selection of the transmission path. The method comprises the steps of determining candidate paths between source and destination nodes of a VPN (Virtual Private Network) service in the network according to constraints of the traffic engineering, wherein the constraints of the traffic engineering include that the bandwidth margin of each link in the candidate paths is greater than or equal to the required bandwidth of the VPN service; determining a selection value of each candidate path according to path ranking information, wherein path ranking informationincludes the bandwidth margin of each link in the candidate paths and the hop count or length of the candidate paths; and determining a transmission path between the source and destination nodes of the VPN service from the candidate paths according to path determination information, wherein the path determination information includes the selection value of each candidate path.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Traffic matrix computation for a backbone network supporting virtual private networks
This invention provides a more effective method for capacity planning and traffic engineering of packet networks that connect Virtual Private Network (VPN) sites. A distributed architecture efficiently computes traffic matrixes that show the number of bytes and / or packets exchanged among provider edge (PE) routers and / or service nodes. Each PE router in a service node is exports flow records to a Flow Record Processor (FRP) in the same location. The FRPs use these records in conjunction with configuration data extracted from the PE routers to compute partial traffic matrixes. The partial traffic matrixes are uploaded to a Matrix Generator to create a total traffic matrix. The total traffic matrix is essential input for capacity planning or traffic engineering tools.
Owner:AT&T INTPROP II L P
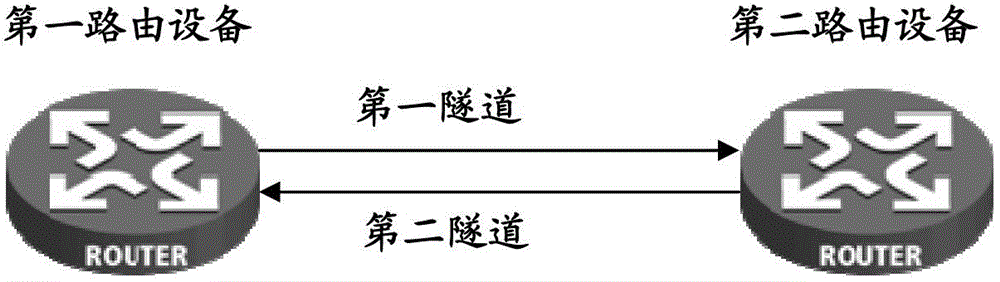
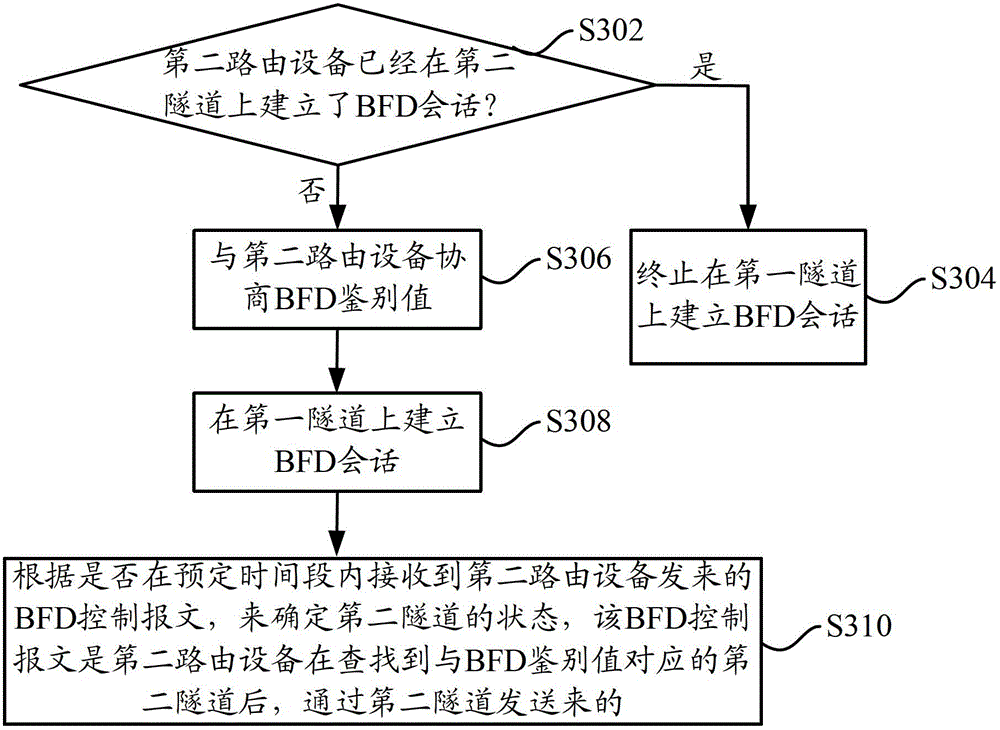
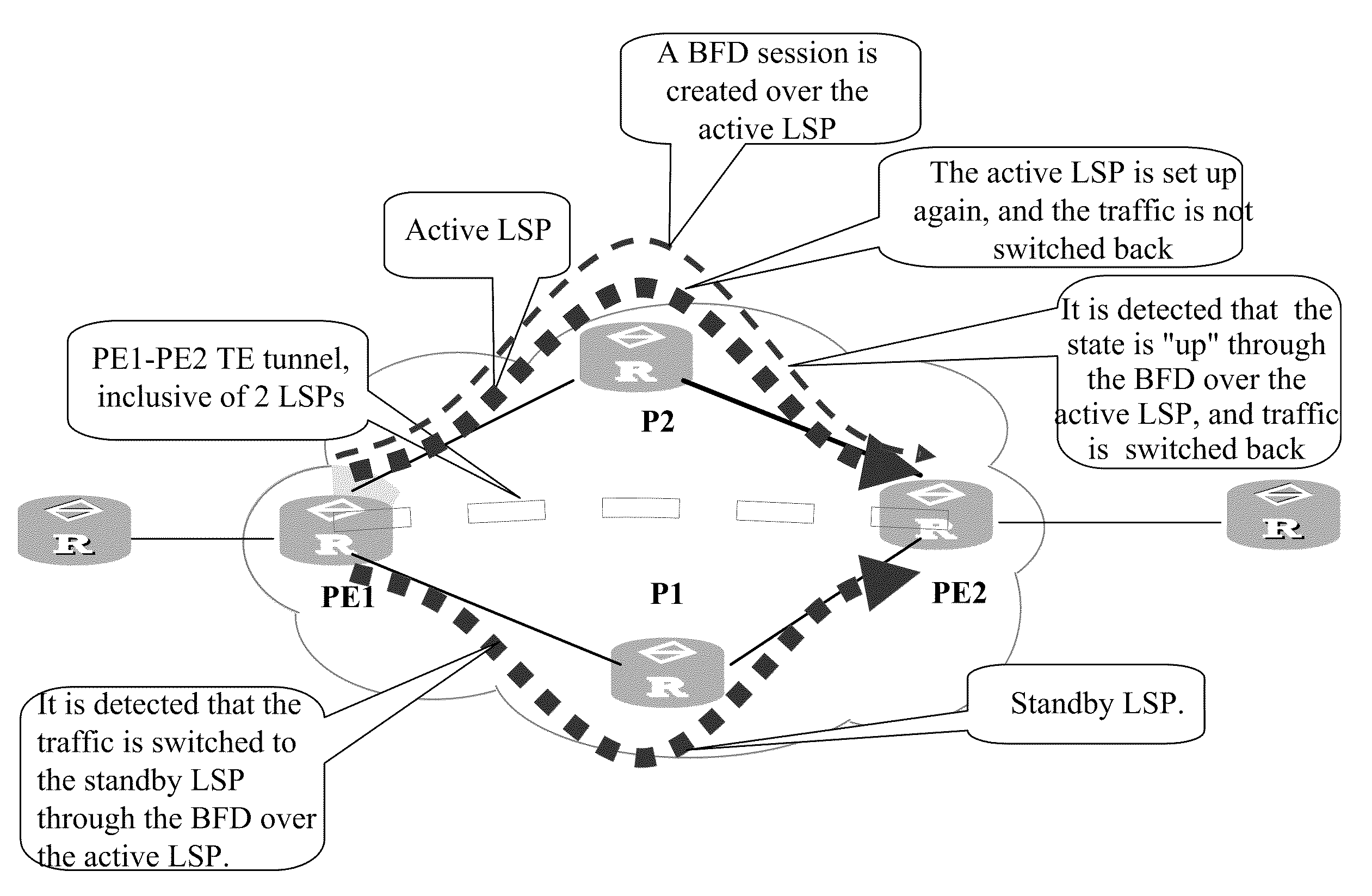
Bi-directional forwarding detection (BFD) method of multiple protocol label switching (MPLS) traffic engineering (TE) bi-directional tunnel and routing equipment
ActiveCN102752143ASave session resourcesEfficient detectionNetworks interconnectionInternet traffic engineeringTelecommunications
The invention discloses a bi-directional forwarding detection (BFD) method of a multiple protocol label switching (MPLS) traffic engineering (TE) bi-directional tunnel and routing equipment. The method comprises following steps that first routing equipment judges whether second routing equipment establishes a BFD session on a second tunnel or not, and the first routing equipment stops establishing the BFD session on a first tunnel if the second routing equipment establishes the BFD session on the second tunnel; if the second routing equipment does not establish the BFD session on the second tunnel, the first routing equipment consults a BFD discrimination value with the second routing equipment and establishes the BFD session on the first tunnel after being successful in consultation, and a corresponding relation between the second tunnel and the negotiated BFD discrimination value is stored on the second routing equipment; and in the BFD detection process of the MPLS TE bi-directional tunnel, the first routing equipment determines a status of the second tunnel on the basis of whether receiving a BFD control message transmitted by the second routing equipment within a preset time period or not, and the BFD control message is transmitted through the second tunnel after the second routing equipment finds the second tunnel corresponding to the BFD discrimination value.
Owner:XINHUASAN INFORMATION TECH CO LTD
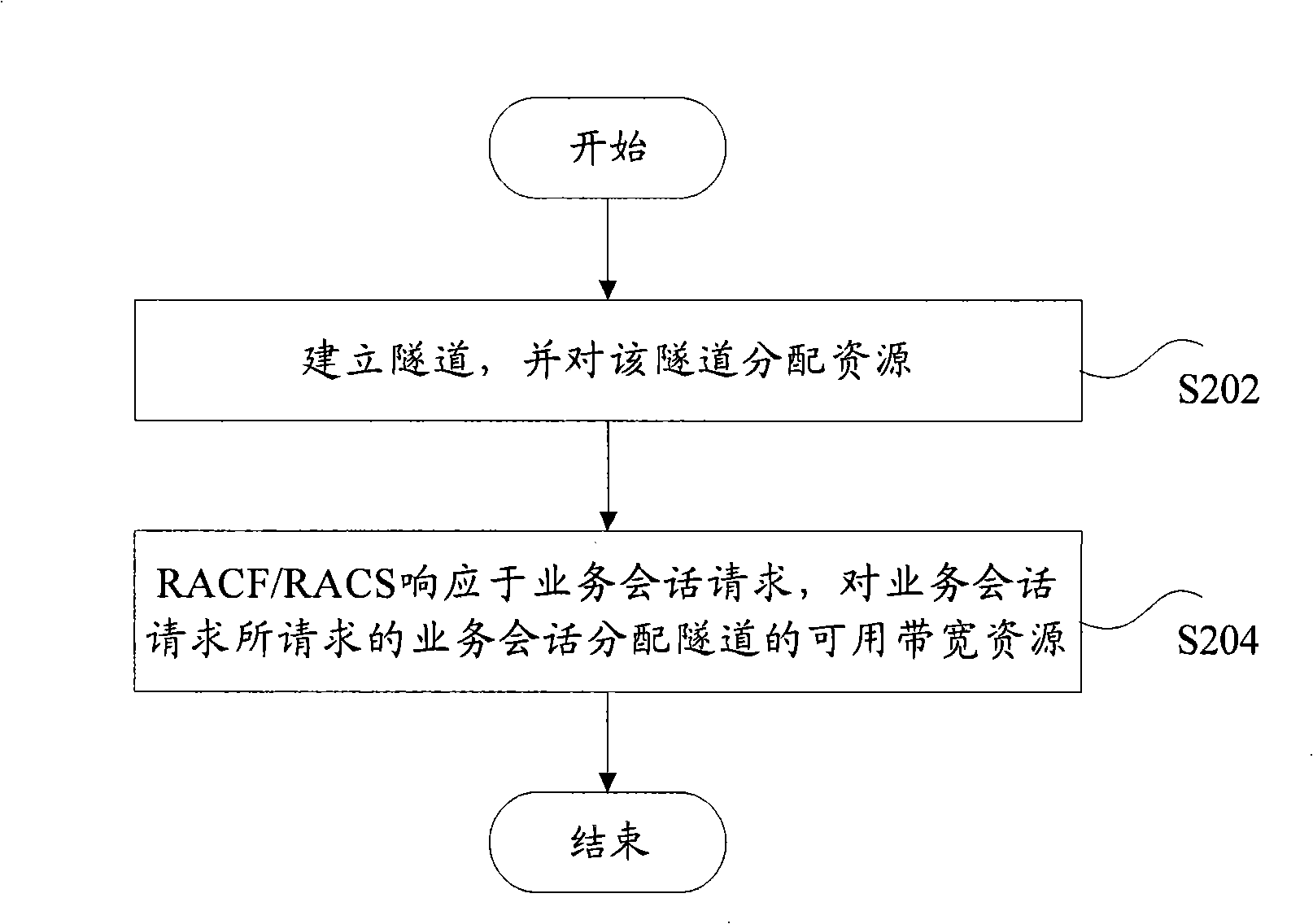
Distribution method of tunnel resource in multiple protocol label switch/traffic engineering
InactiveCN101286941AImprove distribution efficiencyNetworks interconnectionInternet traffic engineeringTraffic capacity
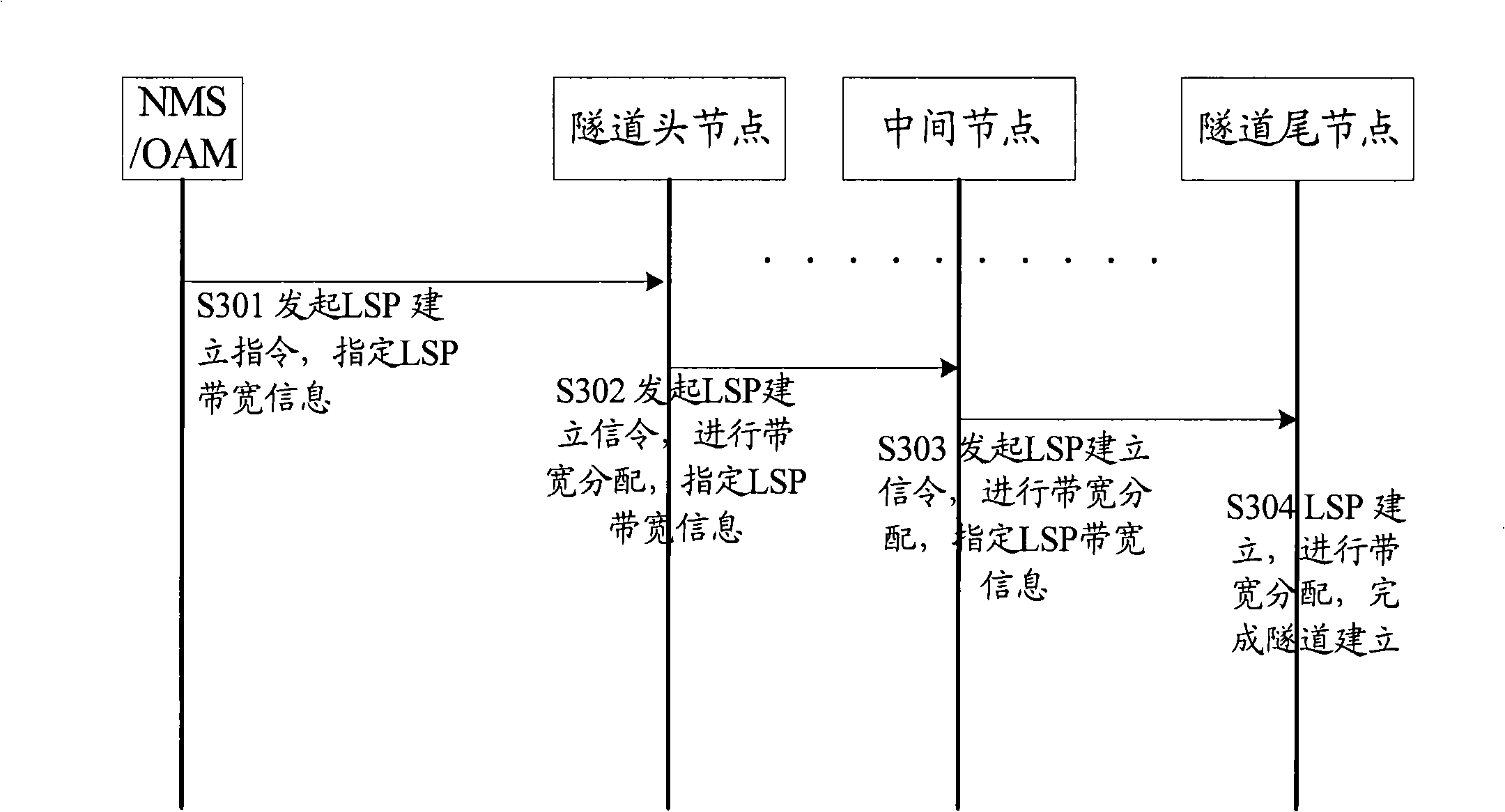
The invention discloses a distribution method for multi-protocol label switching / traffic engineering tunnel resource which comprises the steps that: after the establishment of a tunnel, a resource admission control function entity or a resource admission control subsystem responses to a service dialogue request and distributes available bandwidth recourses of the tunnel to the service dialogue requested by the service dialogue request; under the condition that the available bandwidth resources are insufficient to carry out the service dialogue requested, the resource admission control function entity or the resource admission control subsystem rejects the service dialogue. The technical proposal of the method of the invention determines the relationship among NMS / OAM and MPLS / TE tunnel establishment and RACF / RACS bandwidth resource distribution, thereby improving the efficiency of resource distribution.
Owner:ZTE CORP
Method and device for realizing traffic engineering in multi-home and multi-address space network
ActiveCN101552714ACapable of traffic engineeringData switching networksTraffic capacityInternet traffic engineering
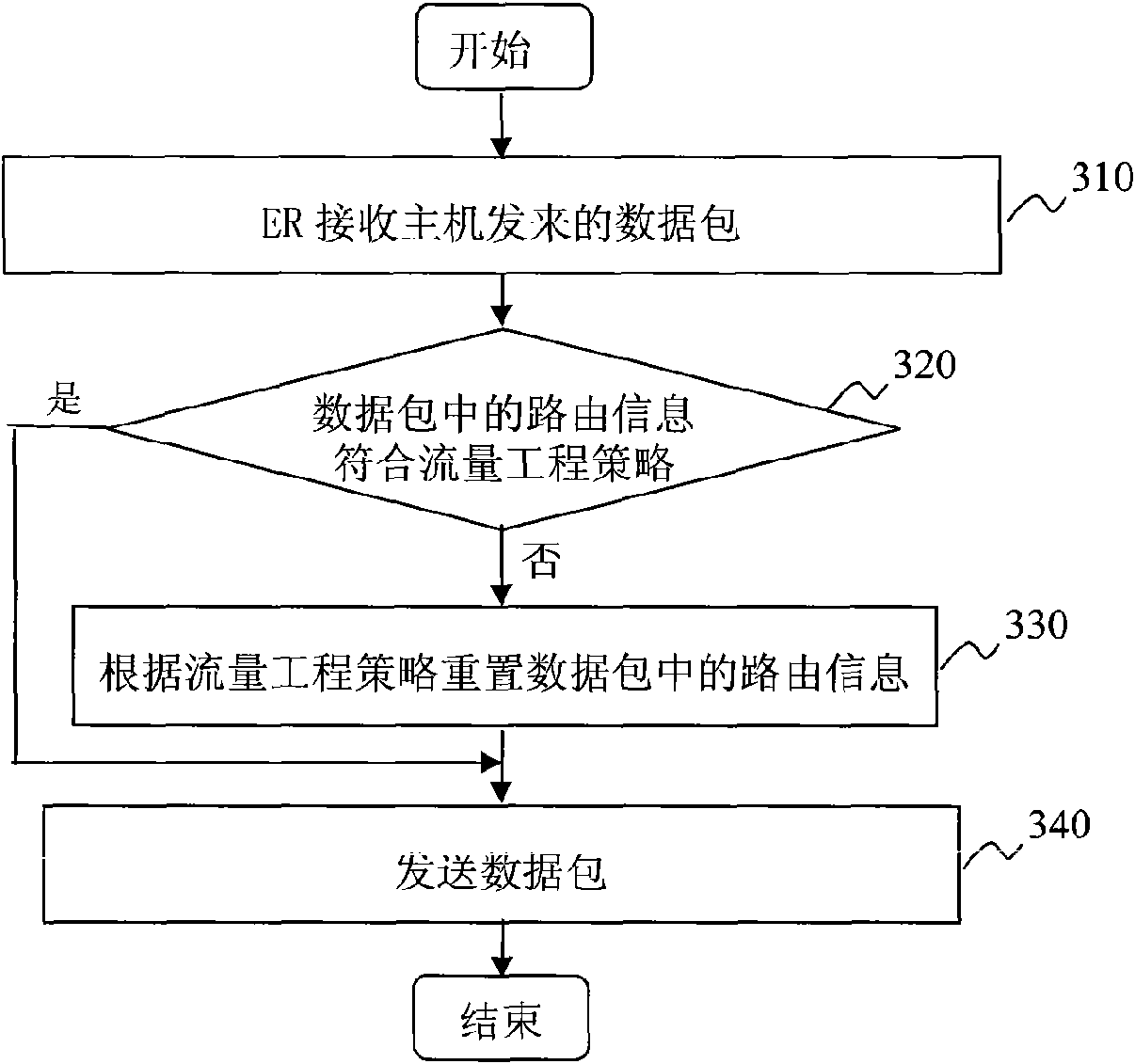
The invention provides a method and a device for realizing traffic engineering in a multi-home and multi-address space network, which relates to the communication field. The method provided by the embodiment of the invention for realizing traffic engineering in a multi-home and multi-address space network comprises the following steps: receiving a first data packet transmitted to a second host from a first host, wherein the first data packet carries first routing information which corresponds to a first position domain; judging whether the first routing information accords with the traffic engineering policy or not; resetting the first routing information to be second routing information according to the traffic engineering policy when the first routing information does not accord with the traffic engineering policy, wherein the second routing information corresponds to a second position domain; and transmitting a second data packet carrying the second routing information. The method and the device provided by the embodiment of the invention enable the multi-home and multi-address space network to have the traffic engineering ability at the network level.
Owner:HUAWEI TECH CO LTD
Method and system for traffic engineering in secured networks
ActiveUS8418241B2Multiple digital computer combinationsProgram controlInternet traffic engineeringTraffic capacity
Aspects of a method and system for traffic engineering in an IPSec secured network are provided. In this regard, a node in a network may be authenticated as a trusted third party and that trusted third party may be enabled to acquire security information shared between or among a plurality of network entities. In this manner, the trusted third party may parse, access and operate on IPSec encrypted traffic communicated between or among the plurality of network entities. Shared security information may comprise one or more session keys utilized for encrypting and / or decrypting the IPSec secured traffic. The node may parse IPSec traffic and identify a flow associated with the IPsec traffic. In this manner, the node may generate and / or communicate statistics pertaining to said IPSec secured traffic based on the flow with which the traffic is associated.
Owner:AVAGO TECH INT SALES PTE LTD
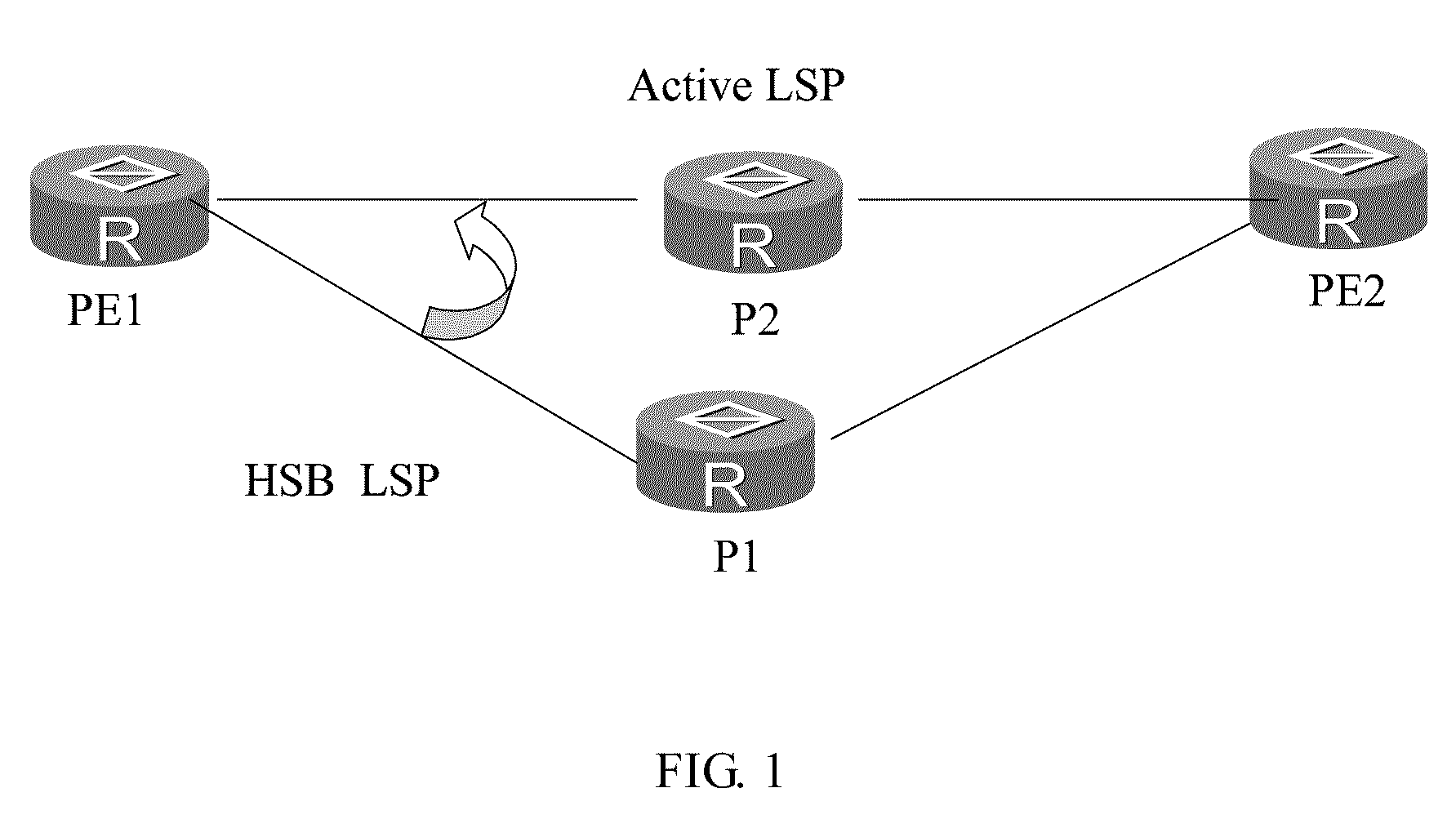
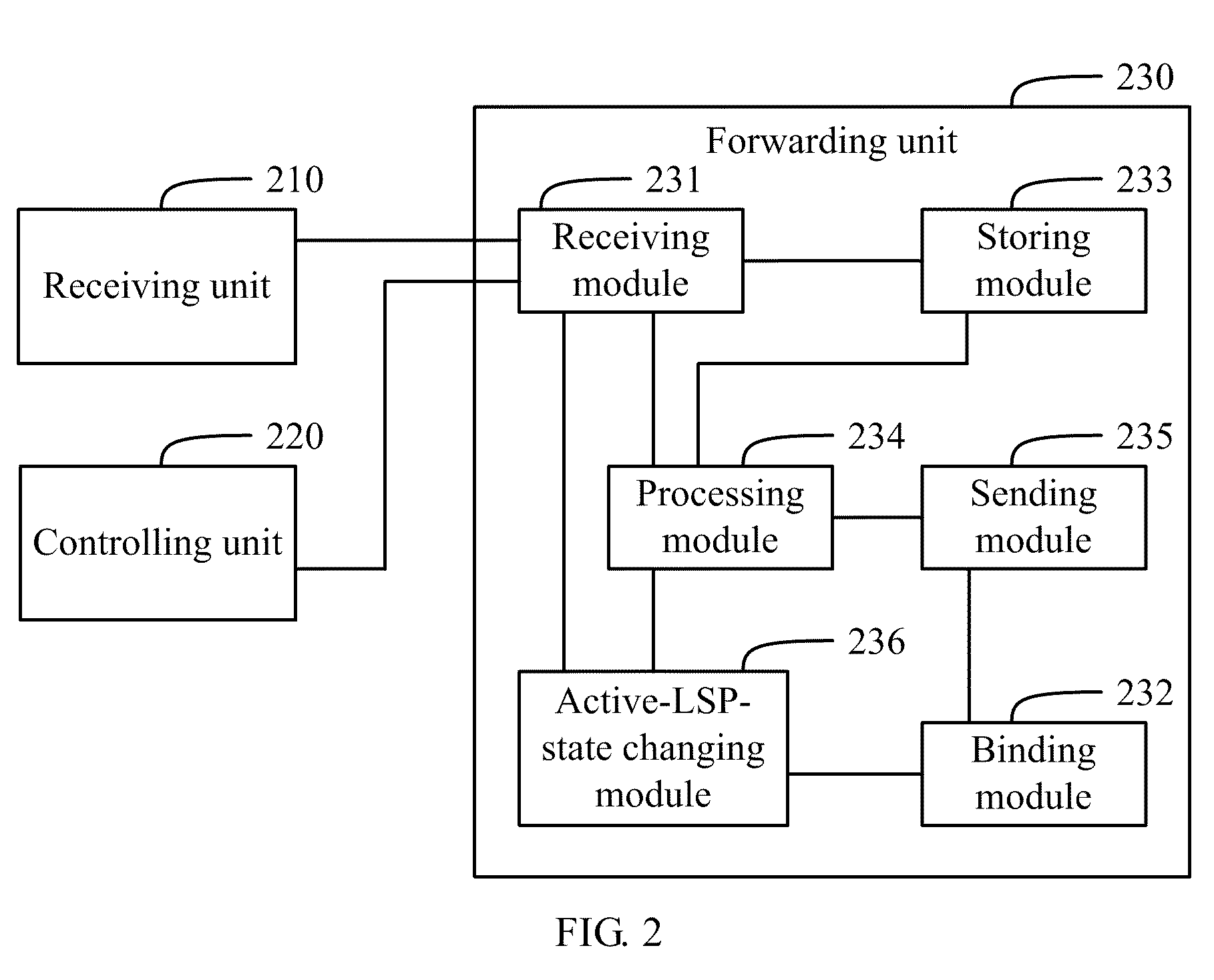
Method, device, and system for traffic switching in multi-protocol label switching traffic engineering
ActiveUS8565098B2Reduce traffic lossImprove user experienceError preventionTransmission systemsInternet traffic engineeringTraffic capacity
A method, device, and system for traffic switching in Multi-Protocol Label Switching Traffic Engineering (MPLS TE) are disclosed. The method includes: transmitting traffic over a standby Label Switching Path (LSP) after detecting fault of an active LSP; detecting that the forwarding entry on the active LSP is delivered completely after the fault of the active LSP is rectified; and switching the traffic to the active LSP, and transmitting the traffic over the active LSP. The present invention ensures that the forwarding entry on the active LSP is delivered completely, and prevents packet loss and traffic loss in the case of switching the traffic back from the standby LSP to the active LSP, thus improving the user experience and enhancing the network availability and stability.
Owner:HUAWEI TECH CO LTD
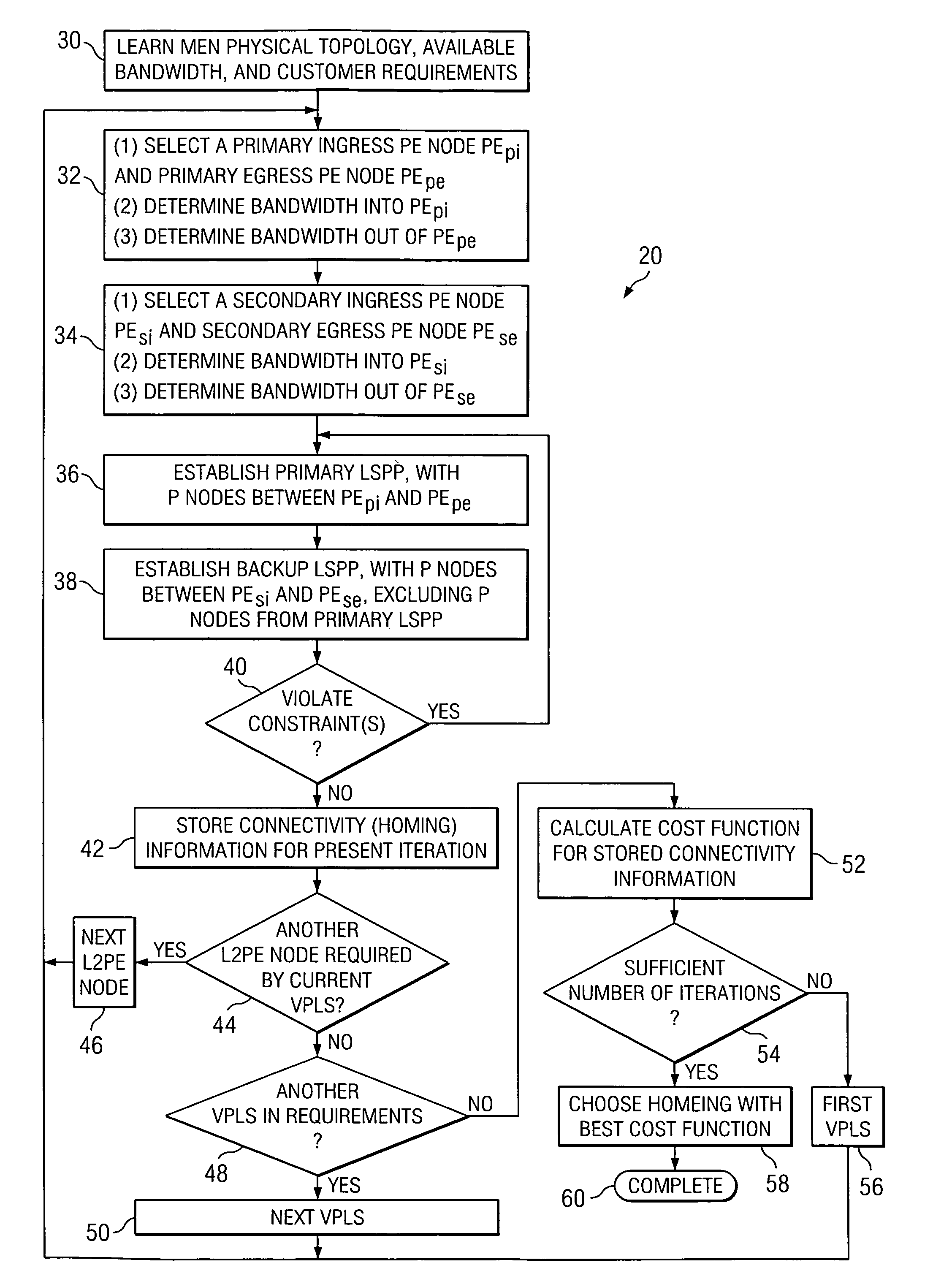
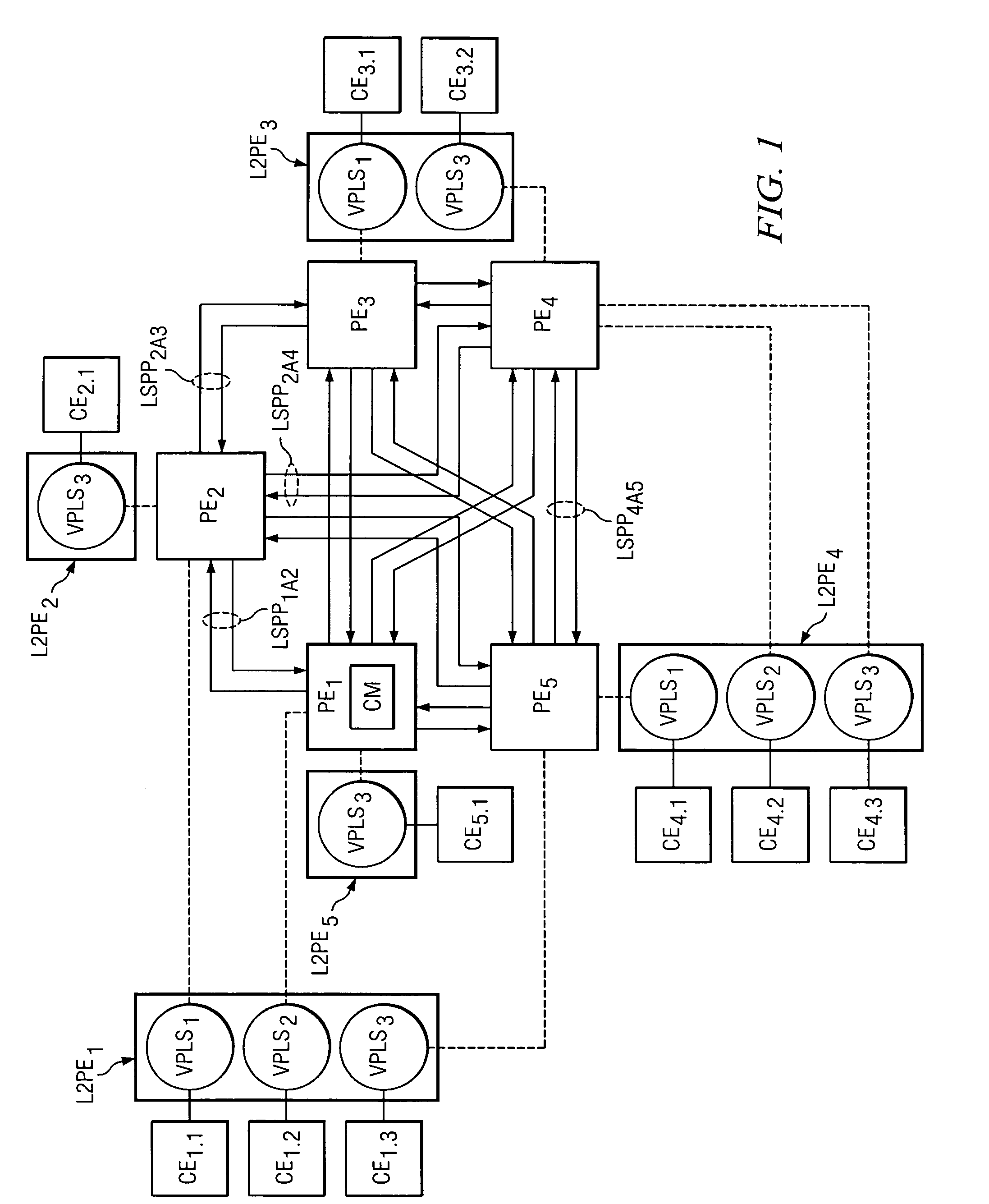
Method for traffic engineering in a multi-homed virtual private local area network service
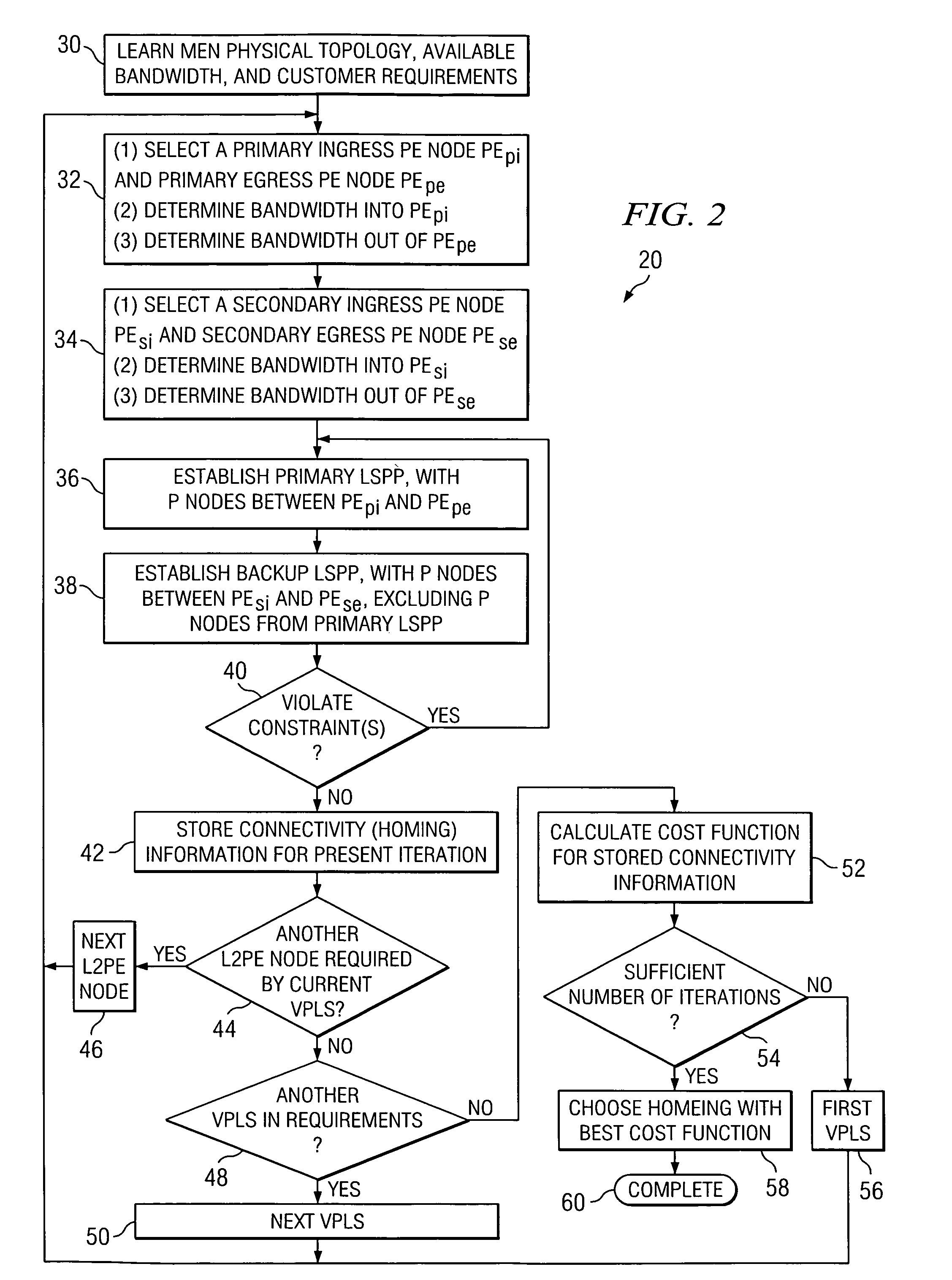
InactiveUS7484010B2Error preventionFrequency-division multiplex detailsTraffic capacityInternet traffic engineering
A processing device (CM) programmed to determine homing paths for a plurality of virtual private local area network services in an Ethernet network comprising a plurality of PE nodes. The processing device is programmed to perform the steps of computing (32-48) a plurality of sets of different homing configurations, computing (52) a cost function for each set of different homing configurations in the plurality of sets of different homing configurations, and selecting (58) a set of homing configurations from the plurality of sets of different homing configurations in response to a respective computed cost function.
Owner:ALCATEL LUCENT SAS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com