Patents
Literature
82results about "Alarms with occupancy stimulation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
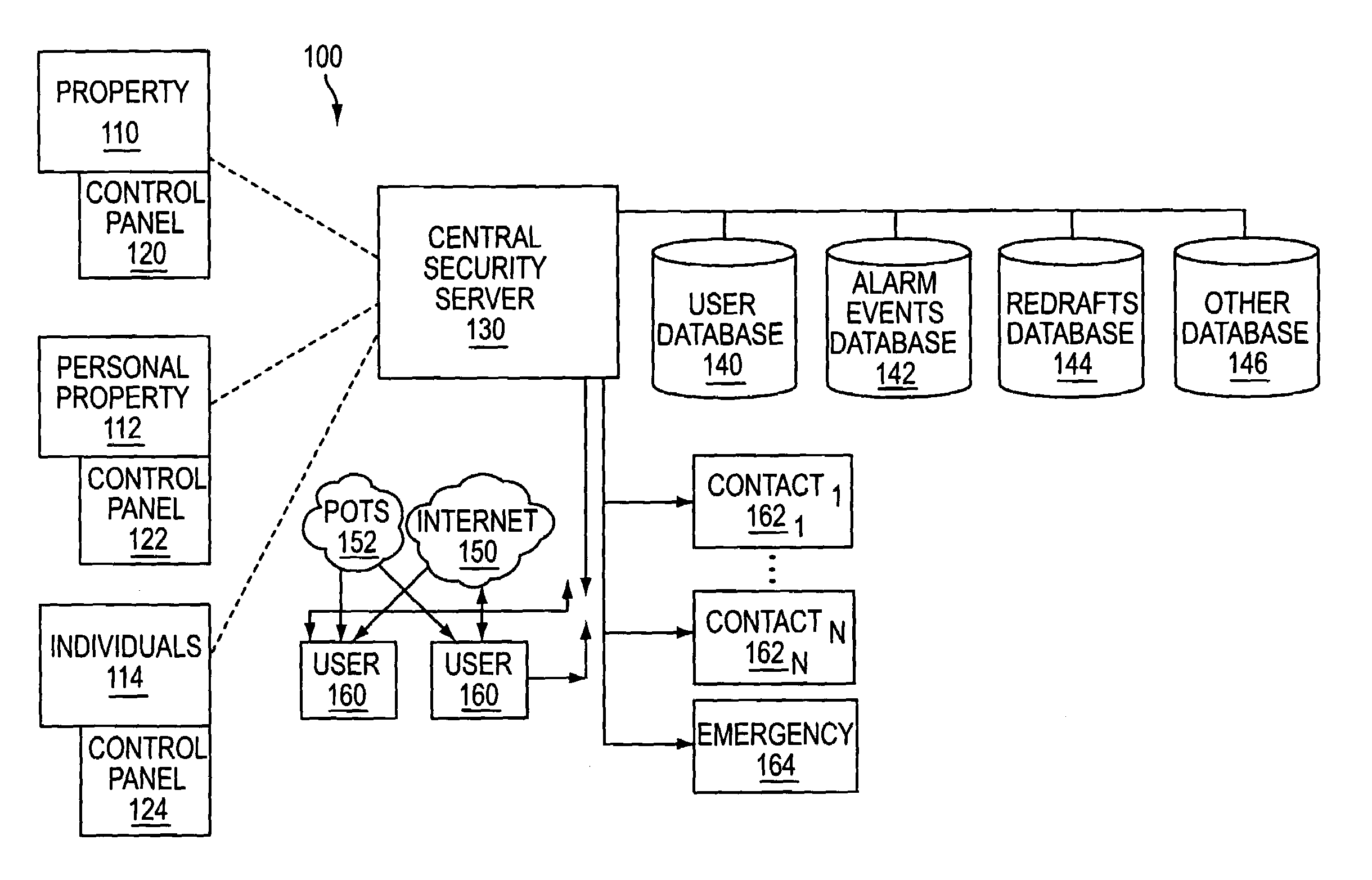
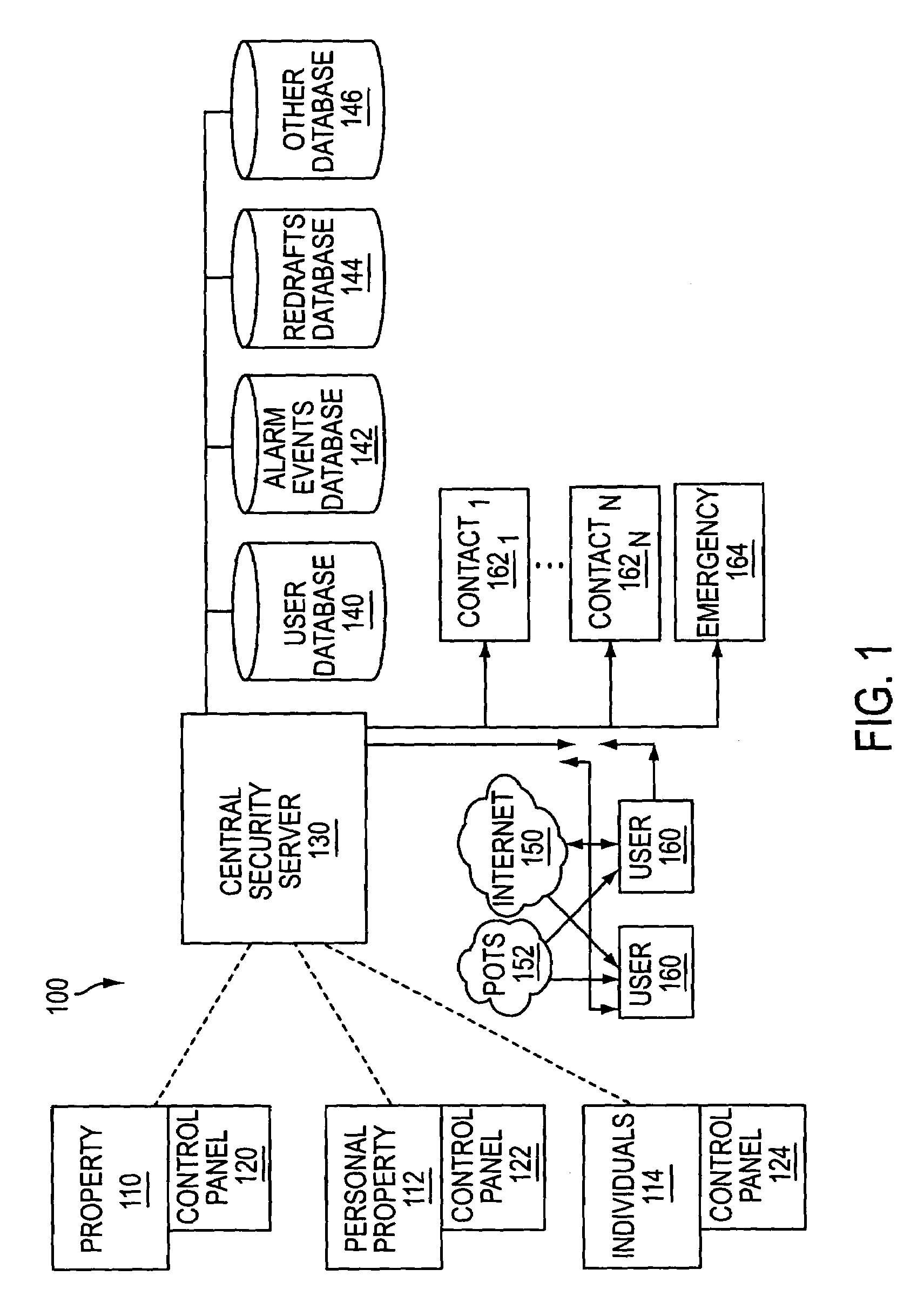
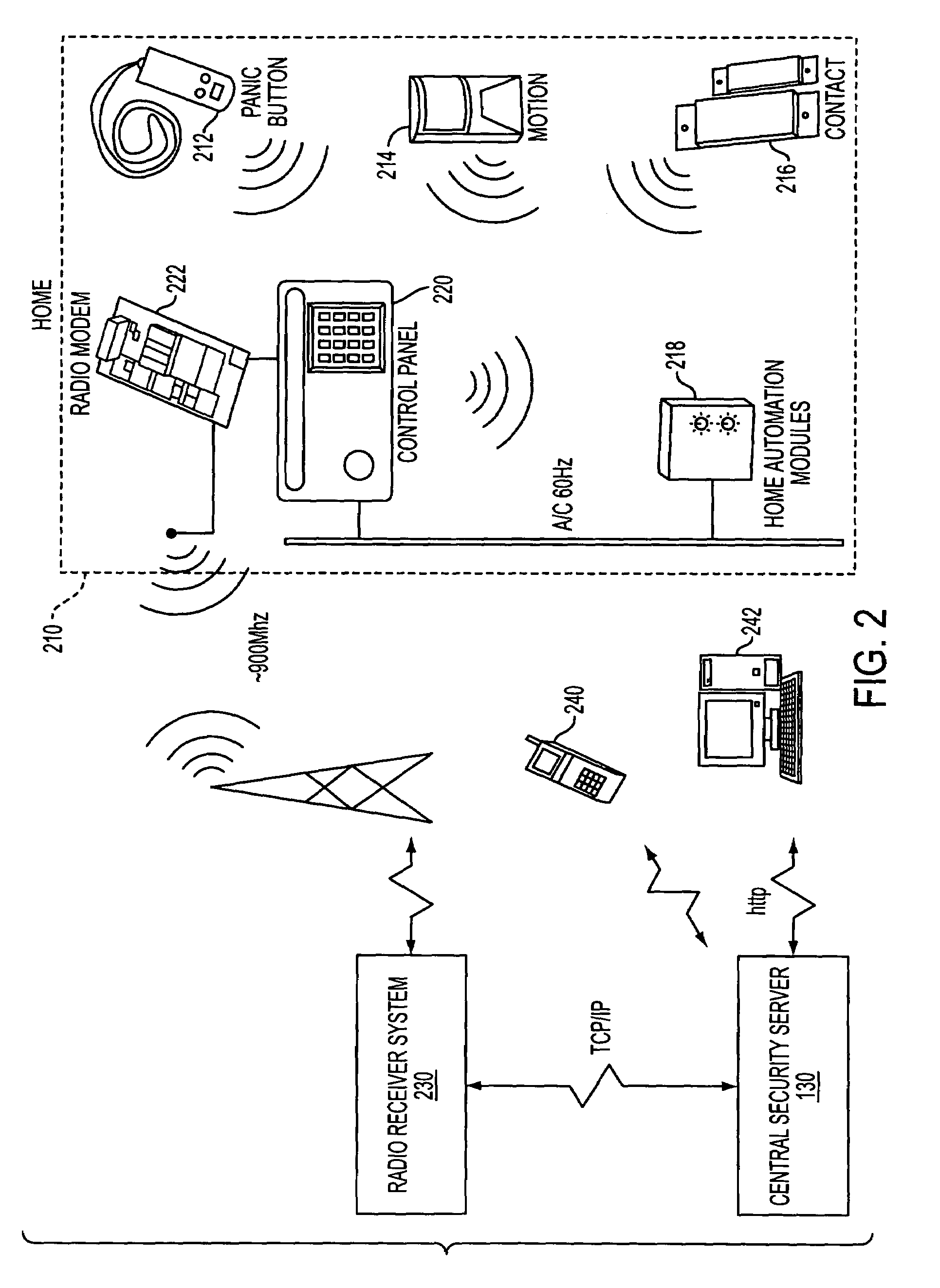
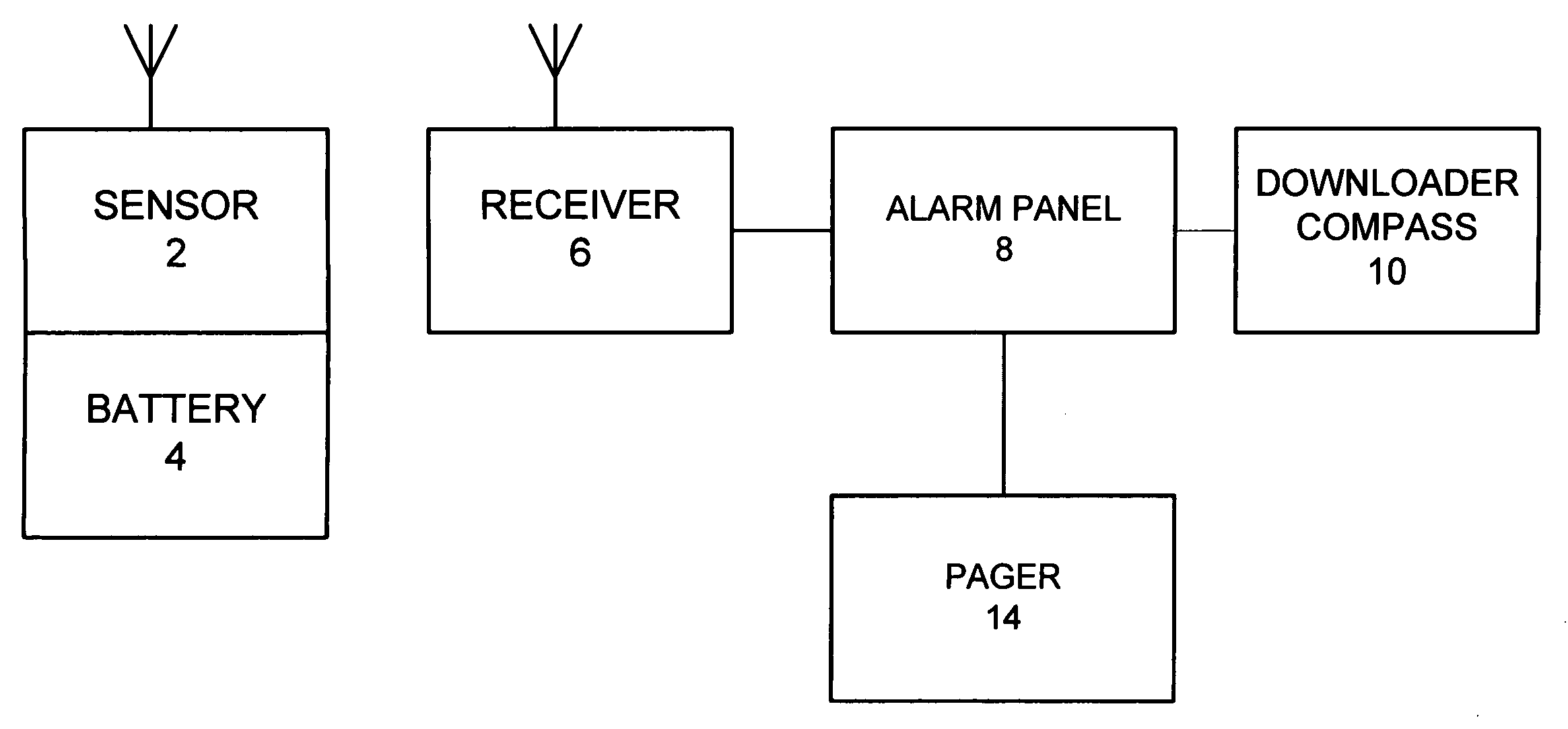
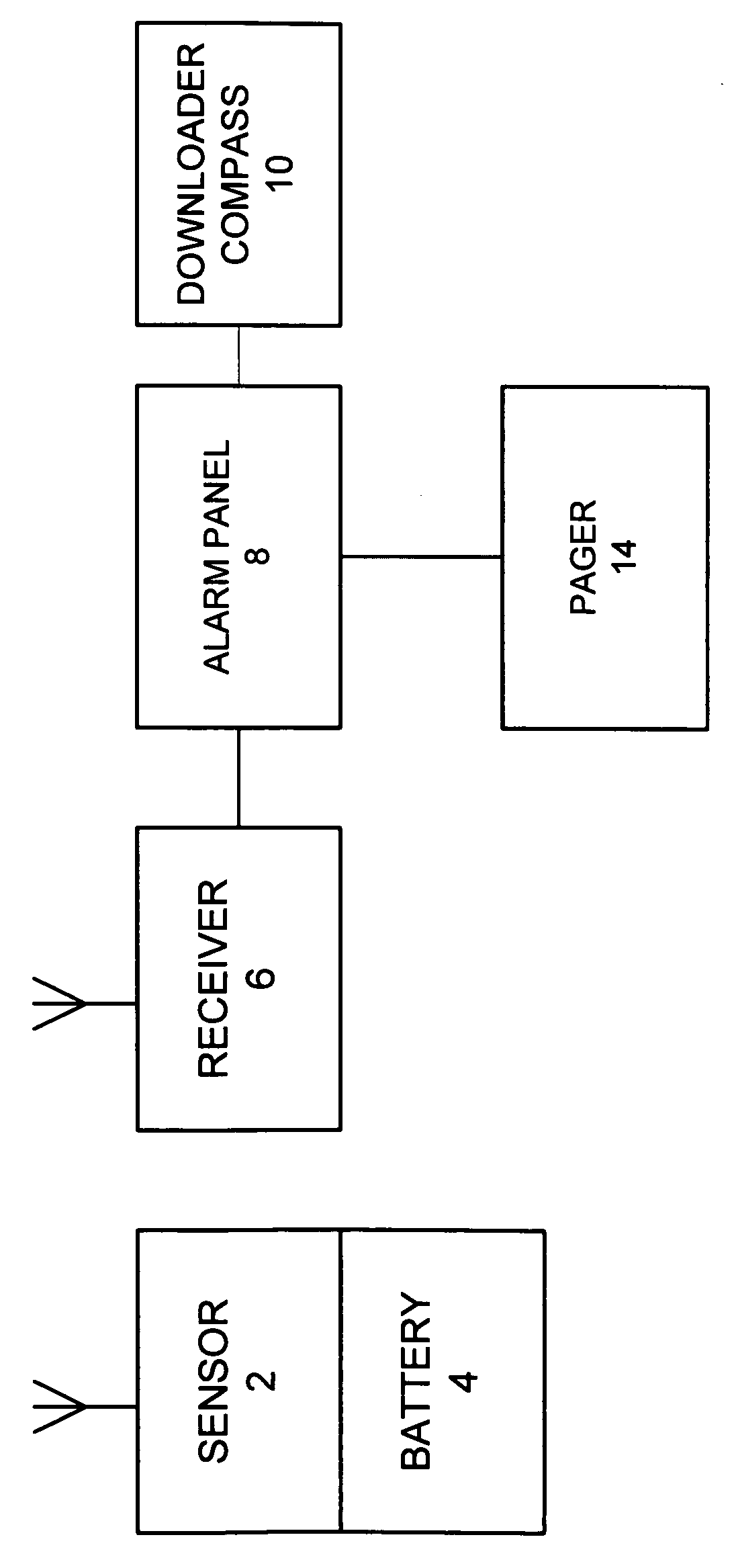
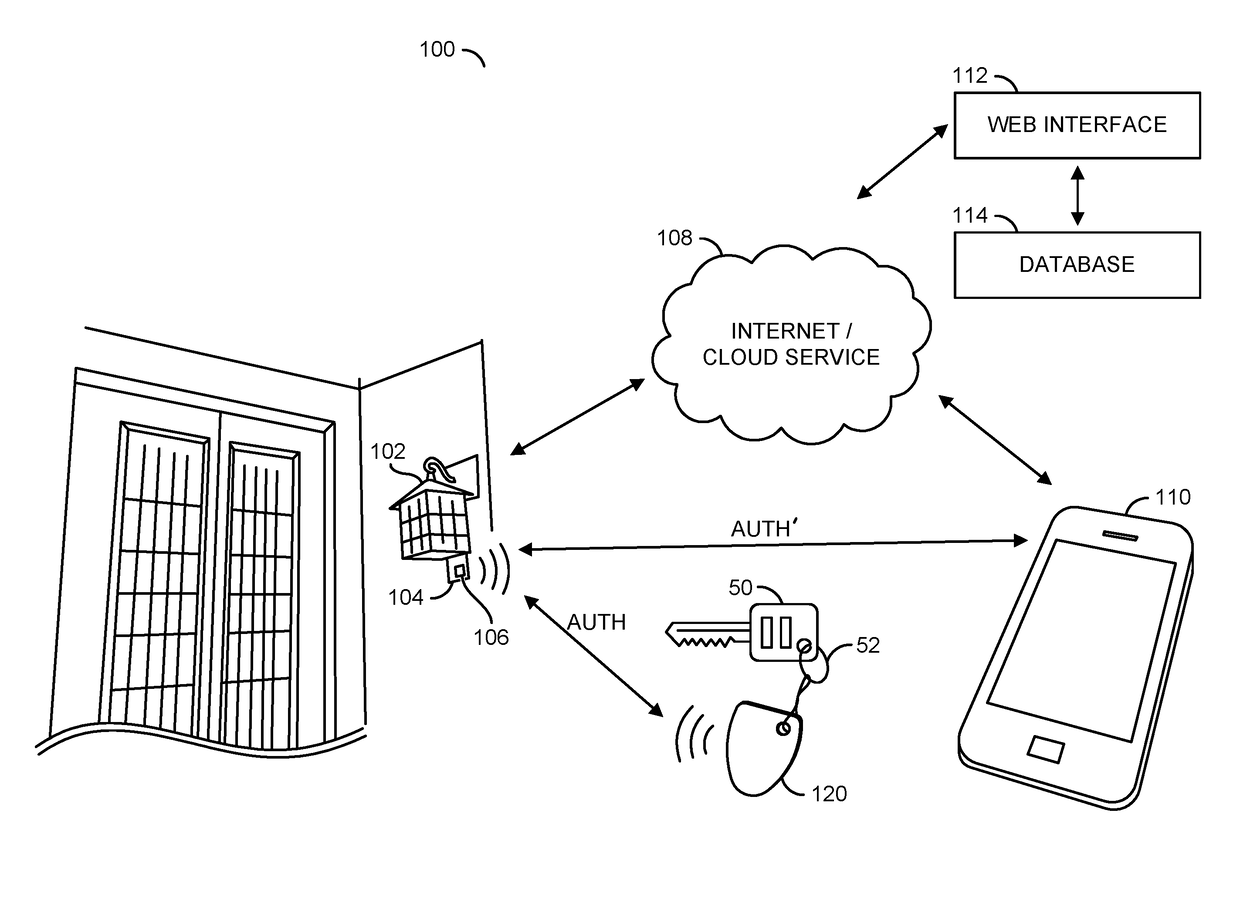
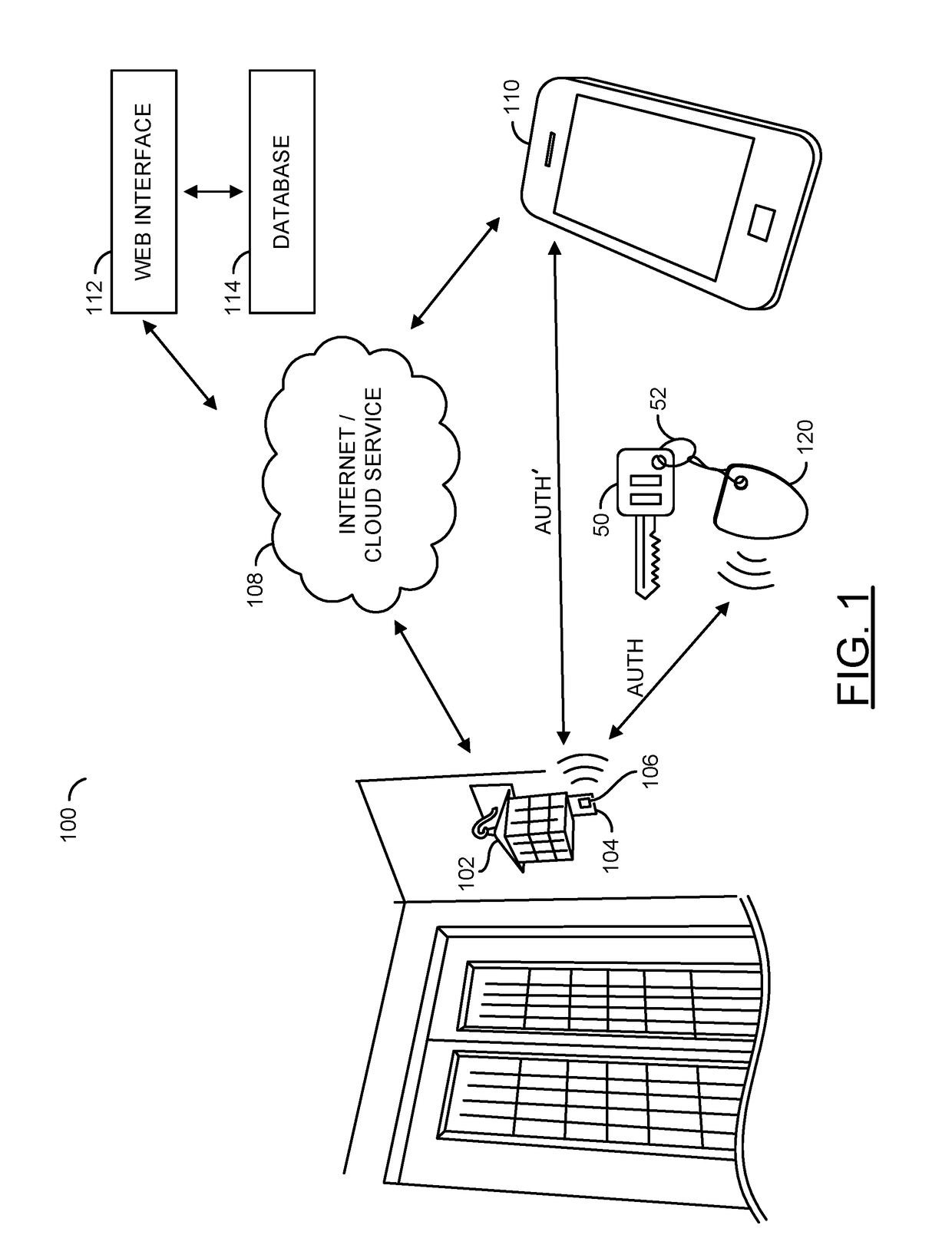
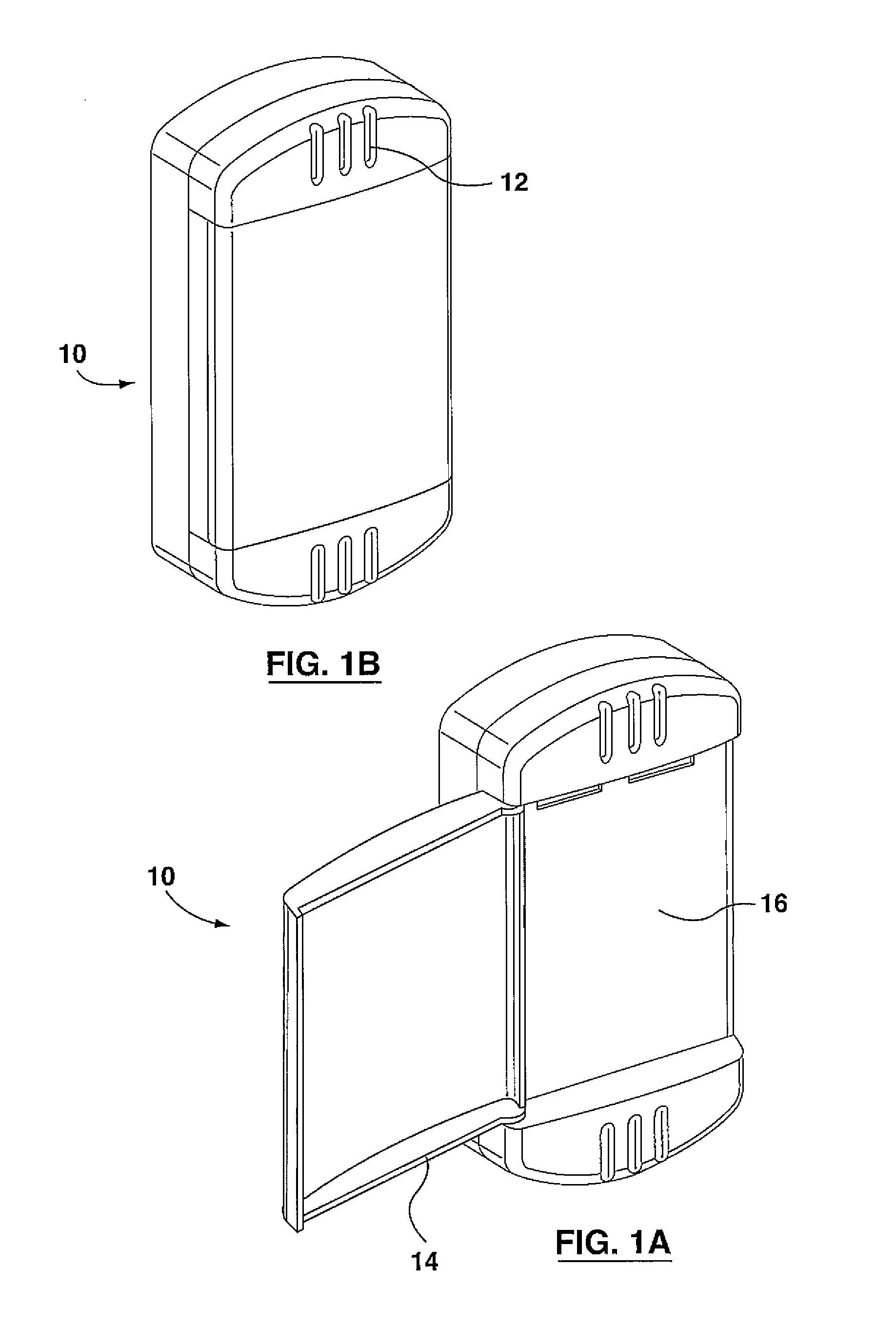
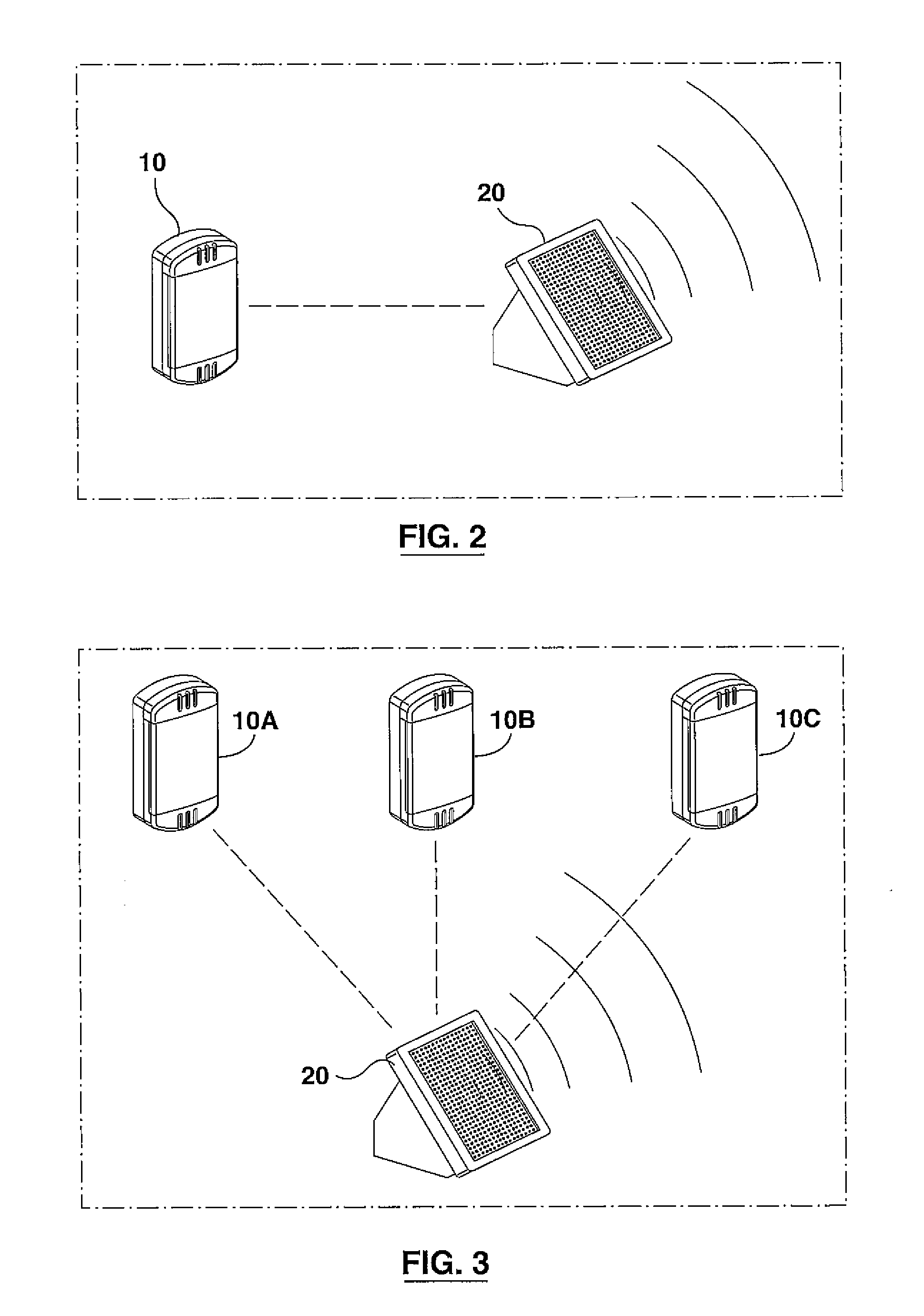
System and method for connecting security systems to a wireless device
InactiveUS7113090B1Electric signal transmission systemsMultiple keys/algorithms usagePersonalizationMonitoring system
The present invention provides a personal security network where an individual's system or systems of security devices may be connected to a central security network. The central security network of the present invention may monitor a system's status and alert the individual when an alert situation occurs. The present invention provides a security network where a user may set up personalized alarms and alert services; identify various methods of contact; order at which to be contacted; individuals and entities to be contacted; type of situations to be alerted of and other relevant security and other information. The present invention may further provide a personalized web interface where authorized individuals may view current and historical security device status. A user may generate personalized reports based on aggregated historical data based on various user-defined factors. The reports may be displayed to the user in various formats, such as maps, graphs, statistics, and others.
Owner:ALARM COM INC
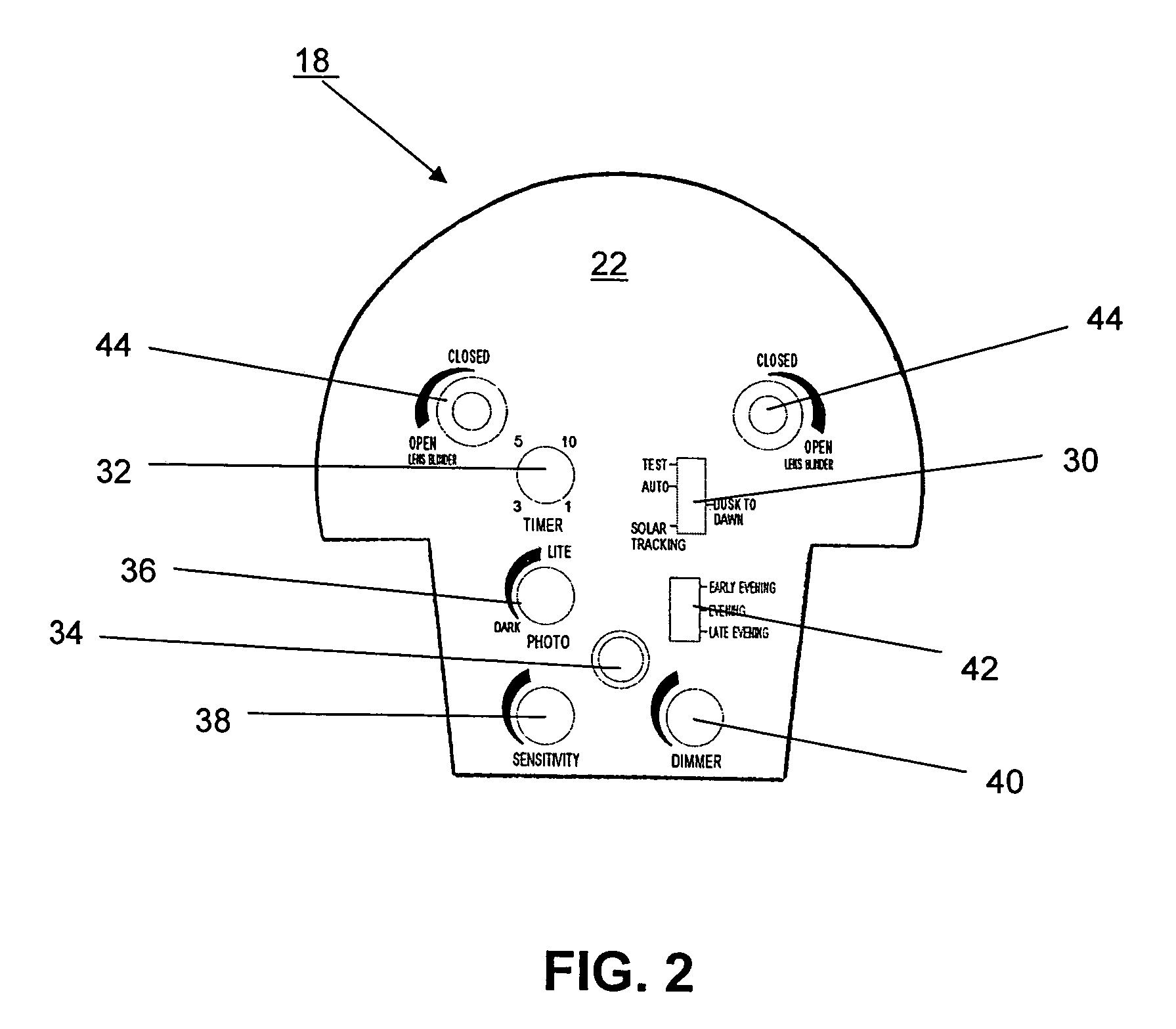
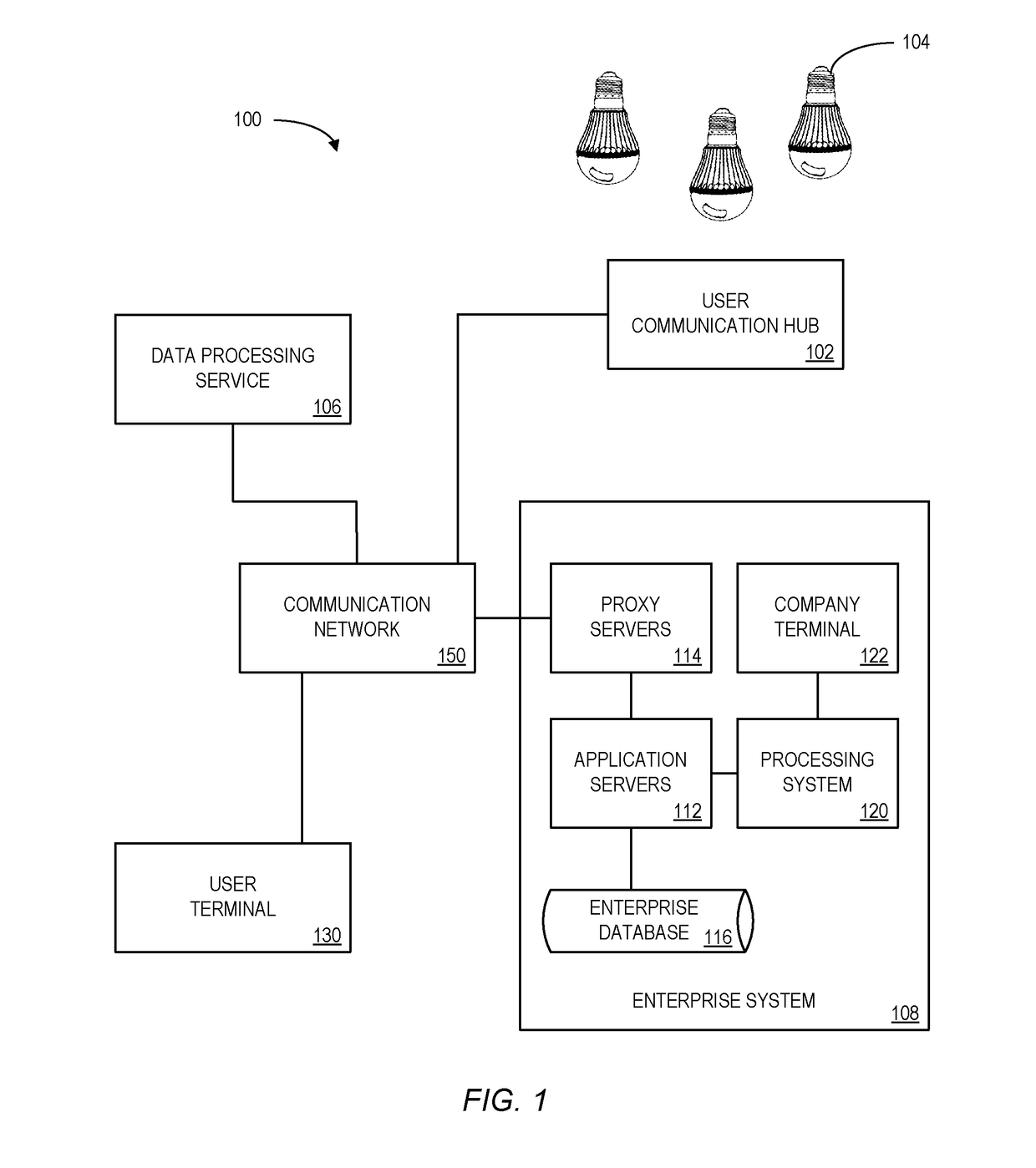
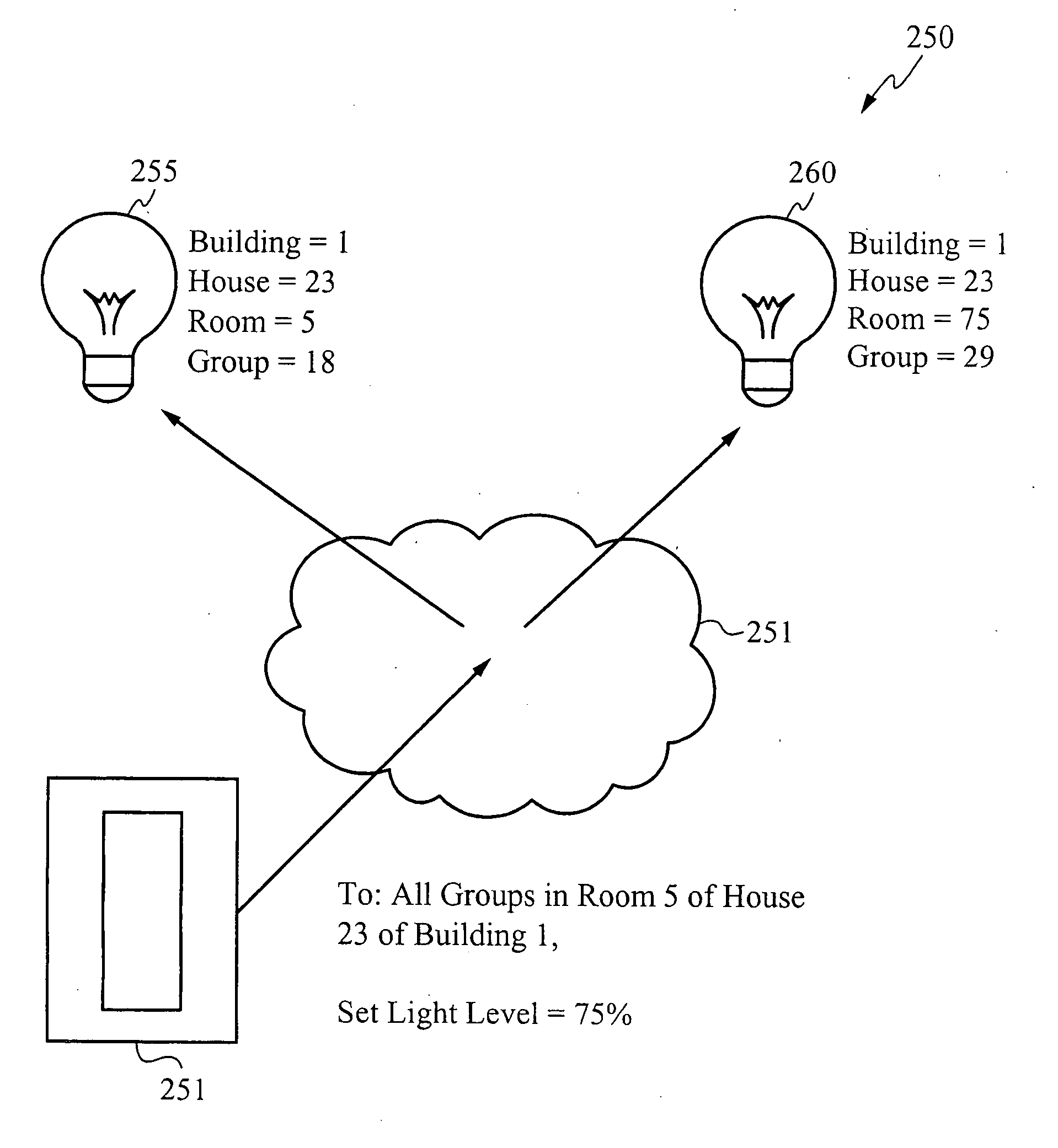
Location-based addressing lighting and environmental control system, device and method
ActiveUS7889051B1Less bandwidthAttenuation bandwidthElectric signal transmission systemsMultiple keys/algorithms usageLight equipmentControl system
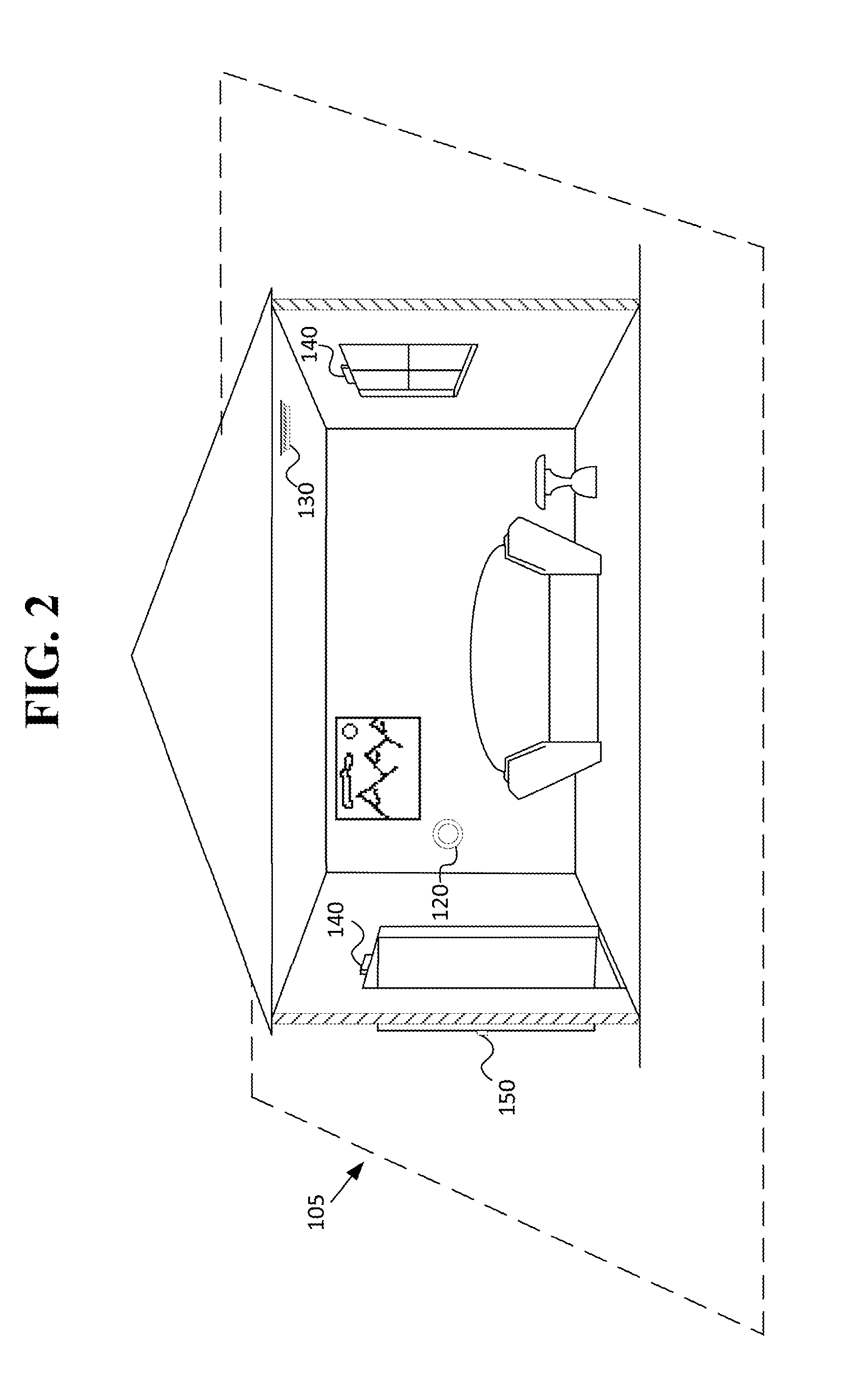
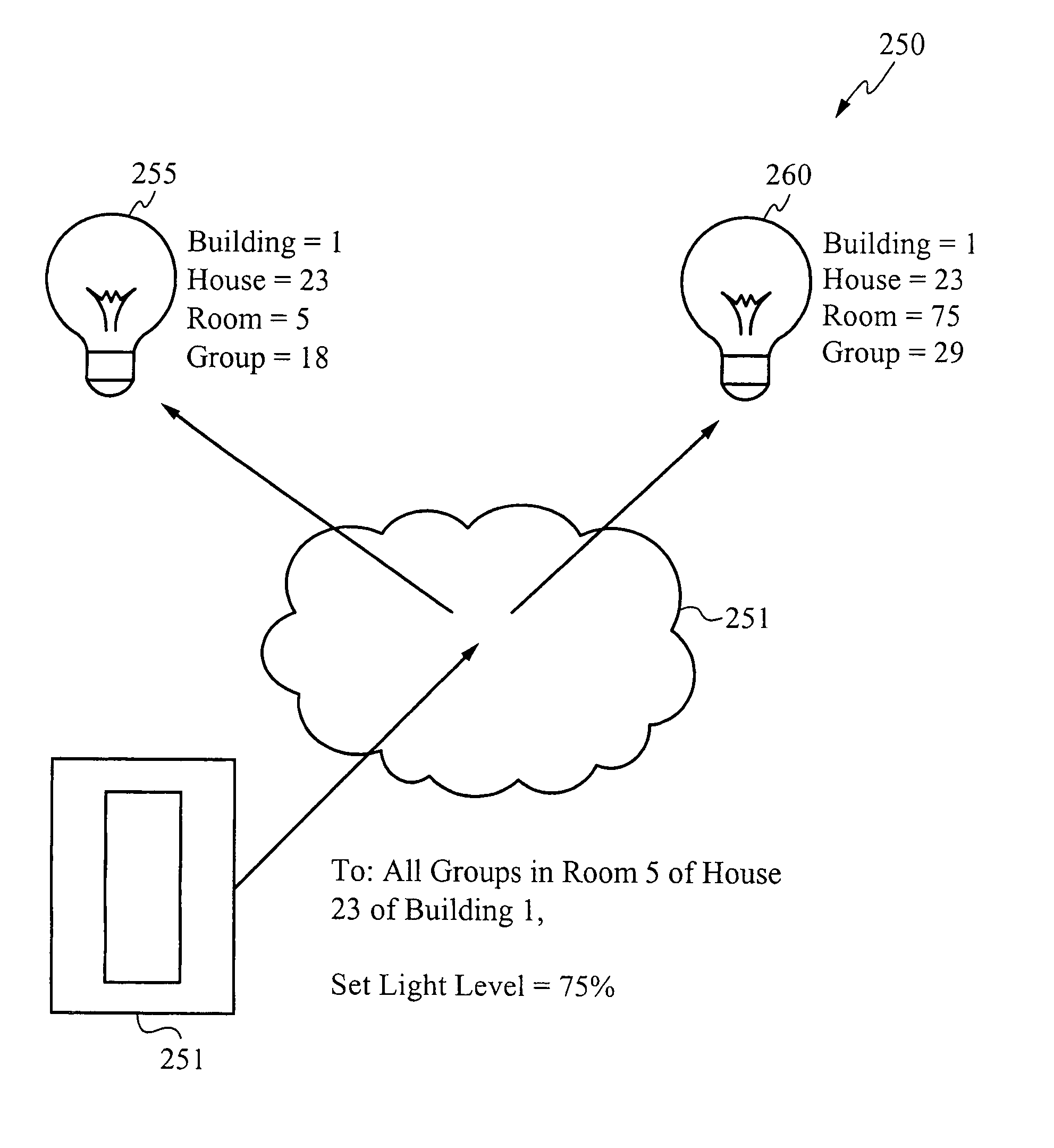
Location-Based Addressing (LBA) is a method of controlling and commissioning networked lighting devices. The lighting devices communicate over a wireless network using radio frequency communication protocols. The lighting devices are commissioned or grouped based on their respective locations in a building floor plan or a building architecture. The lighting devices are commissioned to respond to radio frequency communications that correspond to their respective locations. This imposed location-based architecture reduces the amount of transmitted data required to control the lighting devices and, thus, reduces the radio bandwidth required to control the lighting devices. In other words, controlling devices “multicast” instructions and controlled devices “listen” for instructions and act only upon instructions that correspond to their respective location. Hand shaking or two-way communication between the controlling devices and the controlled devices is not required.
Owner:THE WATT STOPPER
Nighttime-controlled lighting system
A time-controlled security lighting system records the length of nighttime and is capable of automatically adjusting for seasonal nighttime hours. The time duration between the initial nighttime darkness and the light of dawn, as sensed from the prior day by a photocell, is measured and recorded in memory. As the surrounding area becomes dark, the lighting system is activated to provide the illumination for the area. The duration of illumination is determined based on a predetermined fraction of the recorded length of nighttime from the previous night. The control system can adjust the duration of illumination according the recorded nighttime durations from the previous night. The control system can also adjust the level of illumination based on the signals from a motion detector, where the lights are set at a higher brightness for a predetermined amount of time upon detection of motion.
Owner:CORDELIA LIGHTING
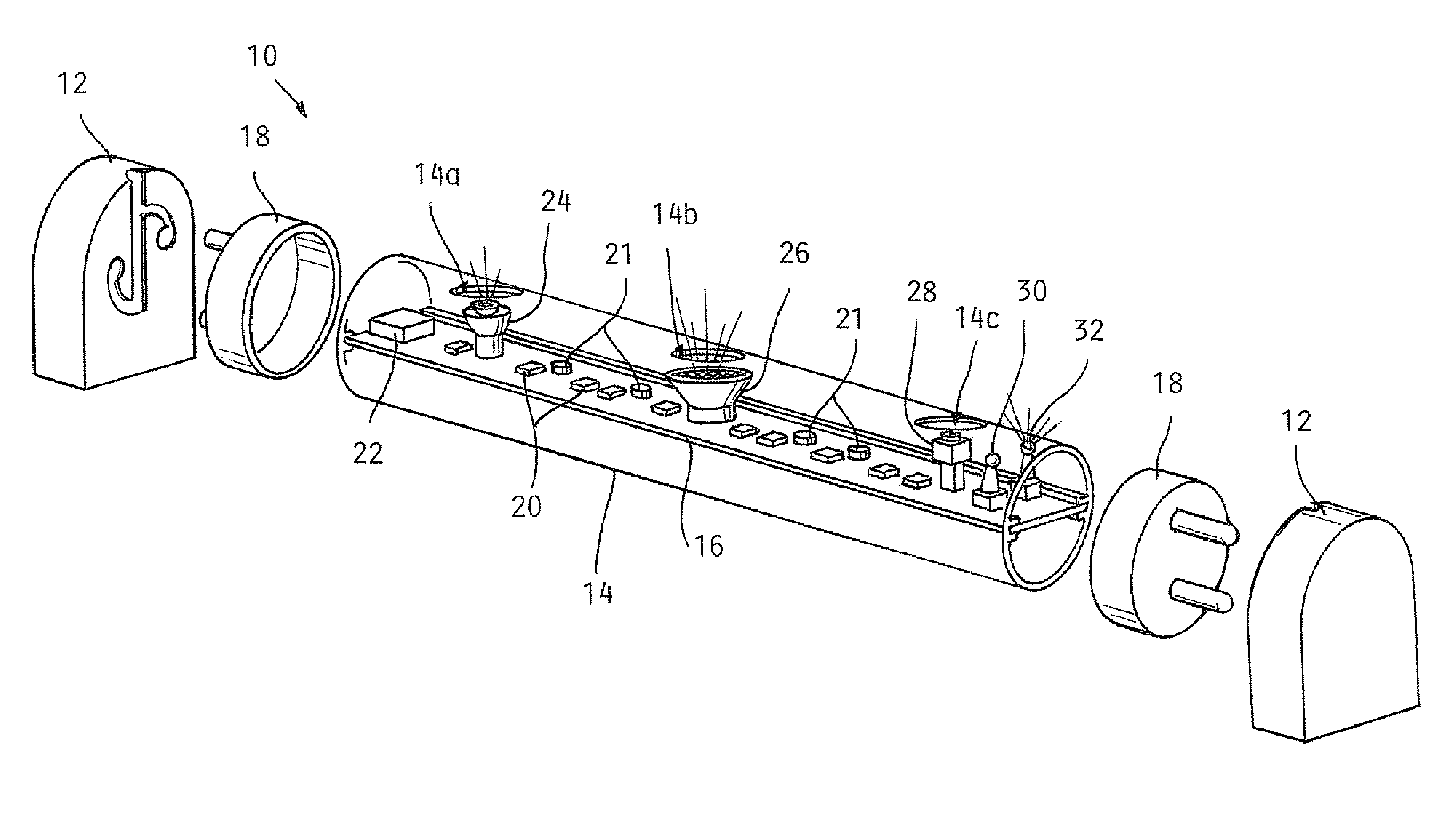
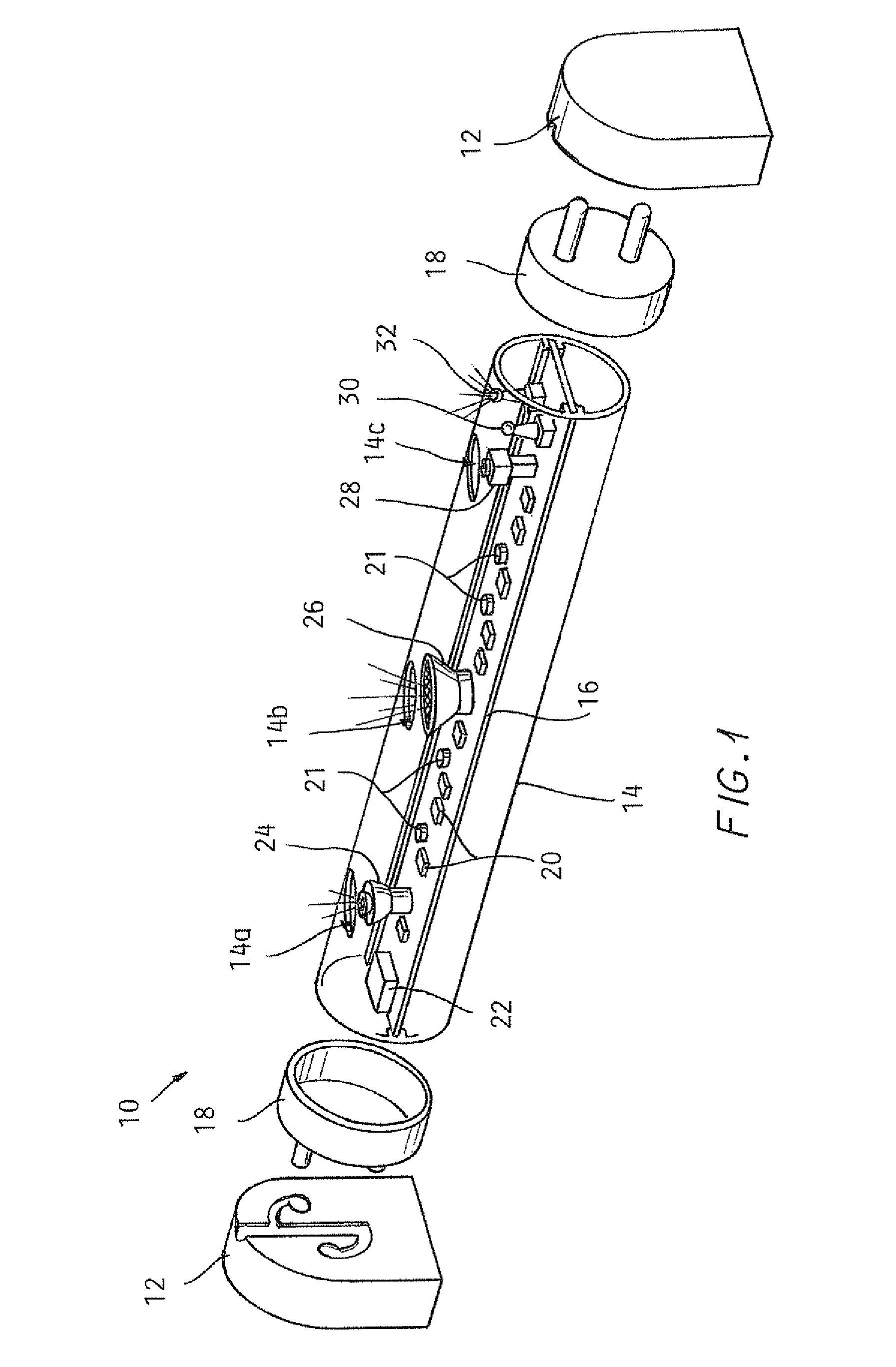
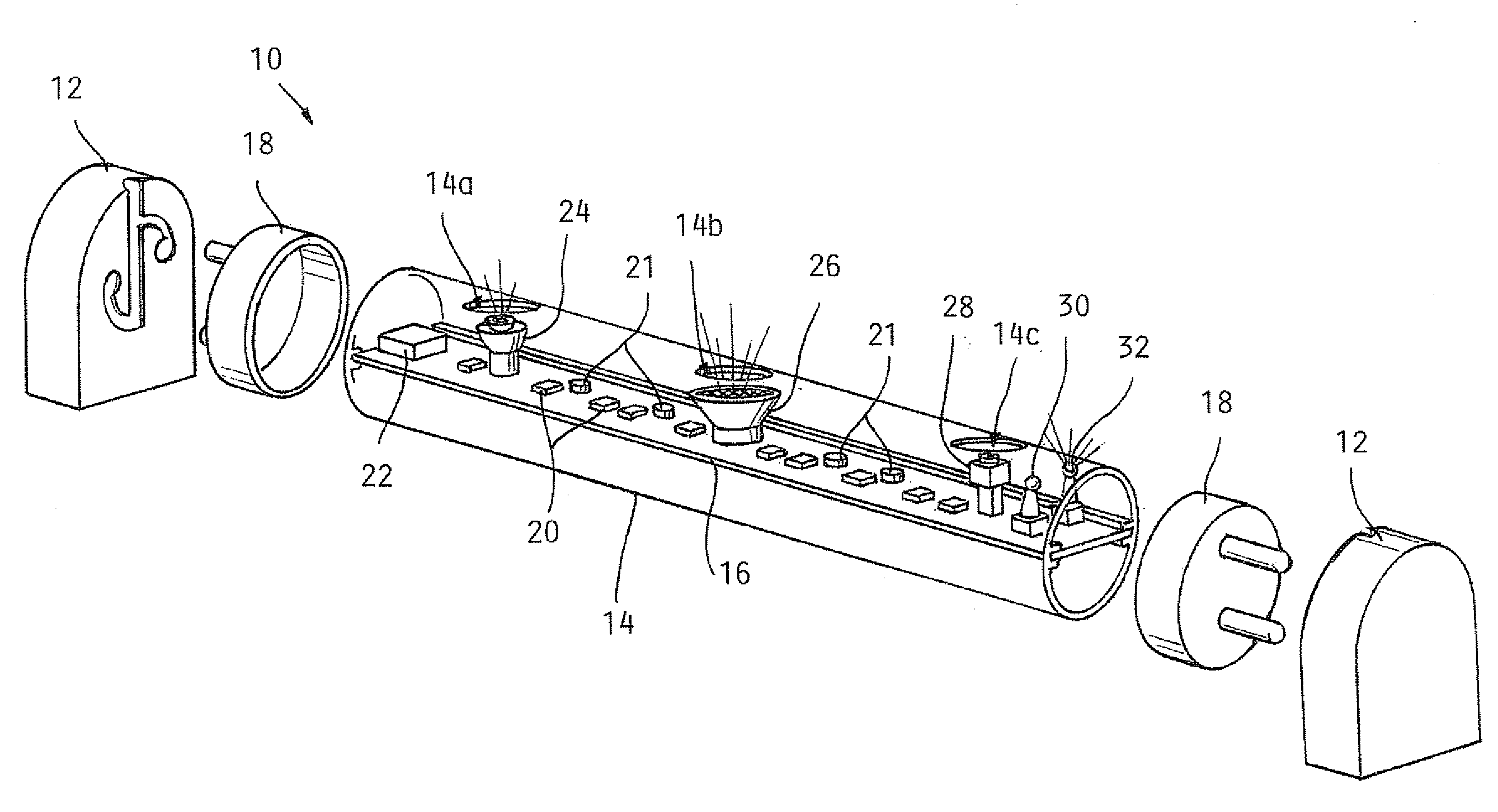
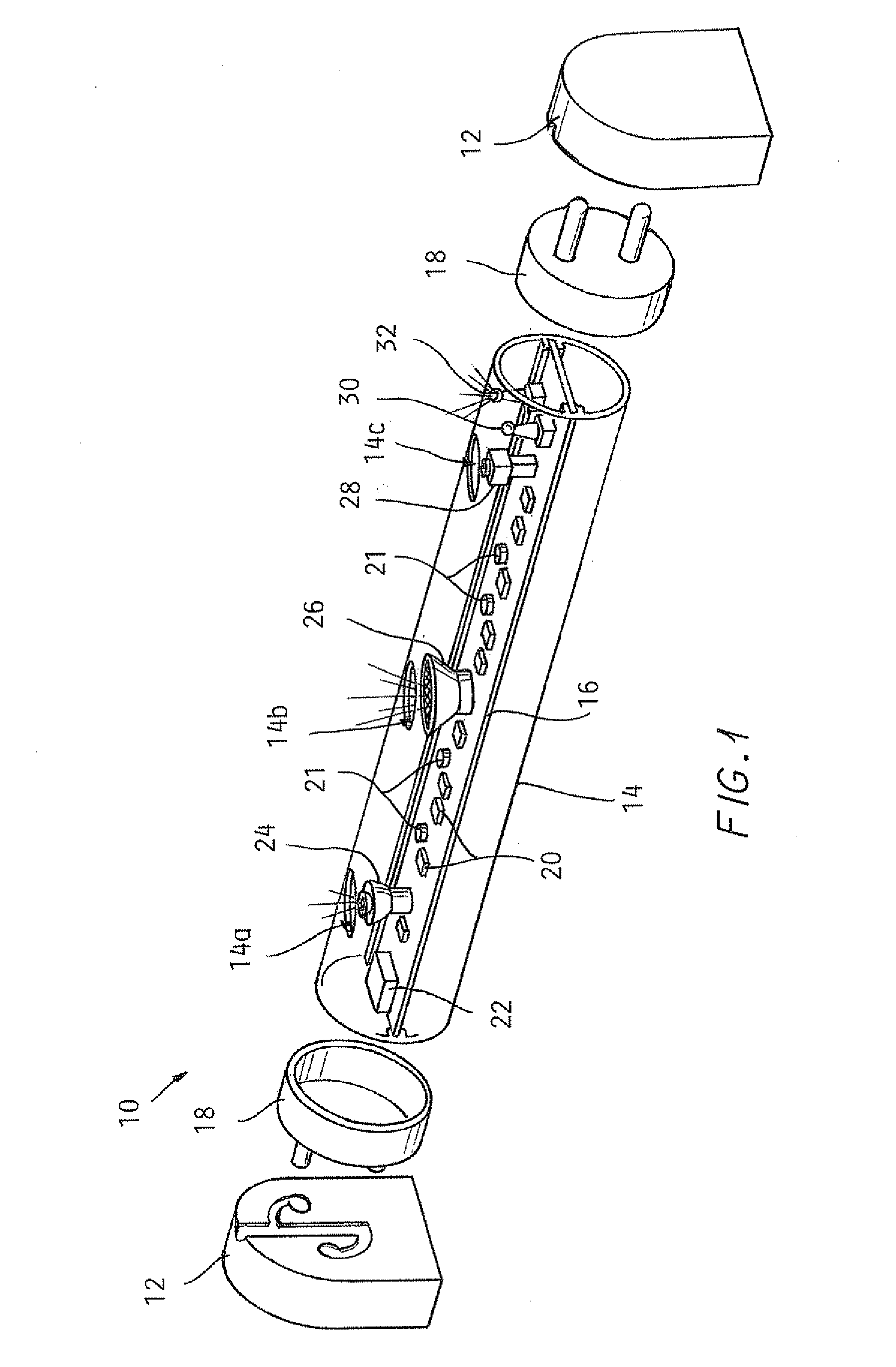
Lighting including integral communication apparatus
A lighting and communication system for use in a standardized light fixture is provided. The lighting and communication system includes a light source and a communication apparatus including at least one of an audio device and a camera. At least one electrical connector configured for physical and electrical connection to the standardized light fixture is included, and the at least one electrical connector is electrically connected to the light source and the communication apparatus.
Owner:ILUMISYS
Lighting including integral communication apparatus
A lighting and communication system for use in a standardized light fixture is provided. The lighting and communication system includes a light source and a communication apparatus including at least one of an audio device and a camera. At least one electrical connector configured for physical and electrical connection to the standardized light fixture is included, and the at least one electrical connector is electrically connected to the light source and the communication apparatus.
Owner:ILUMISYS
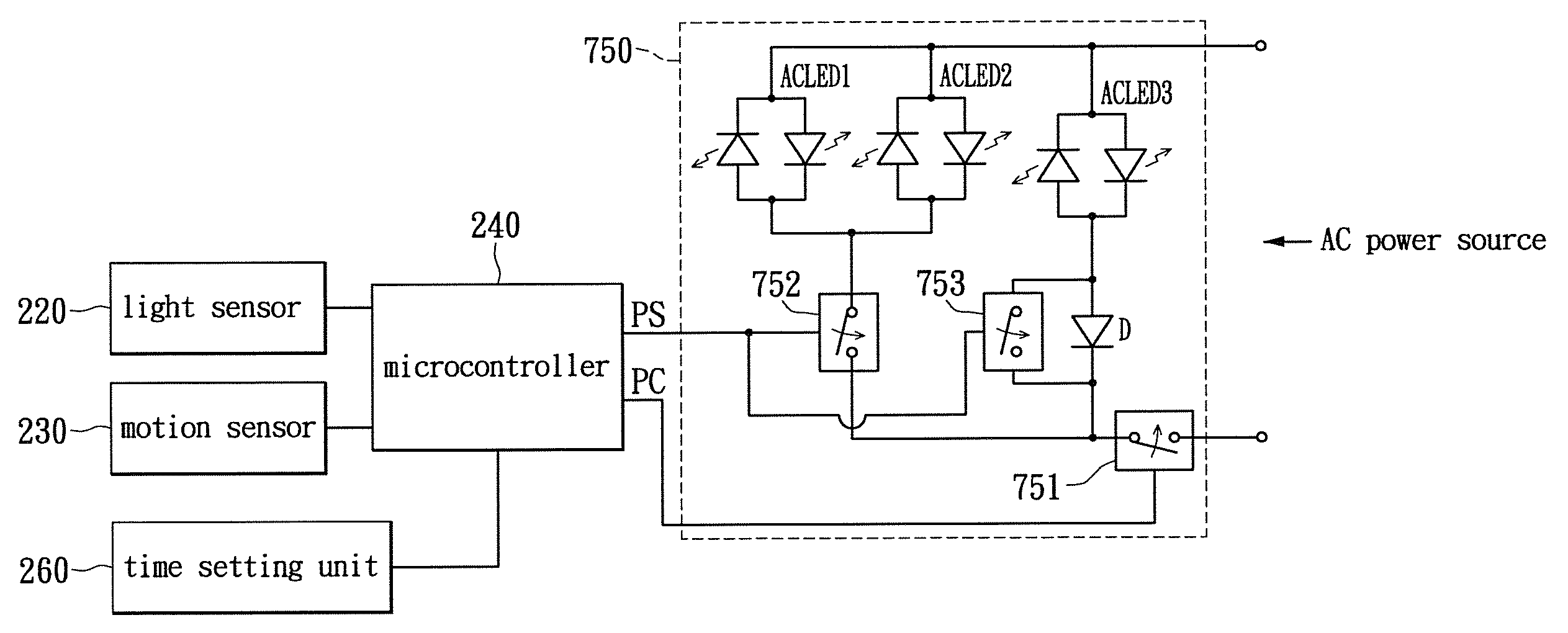
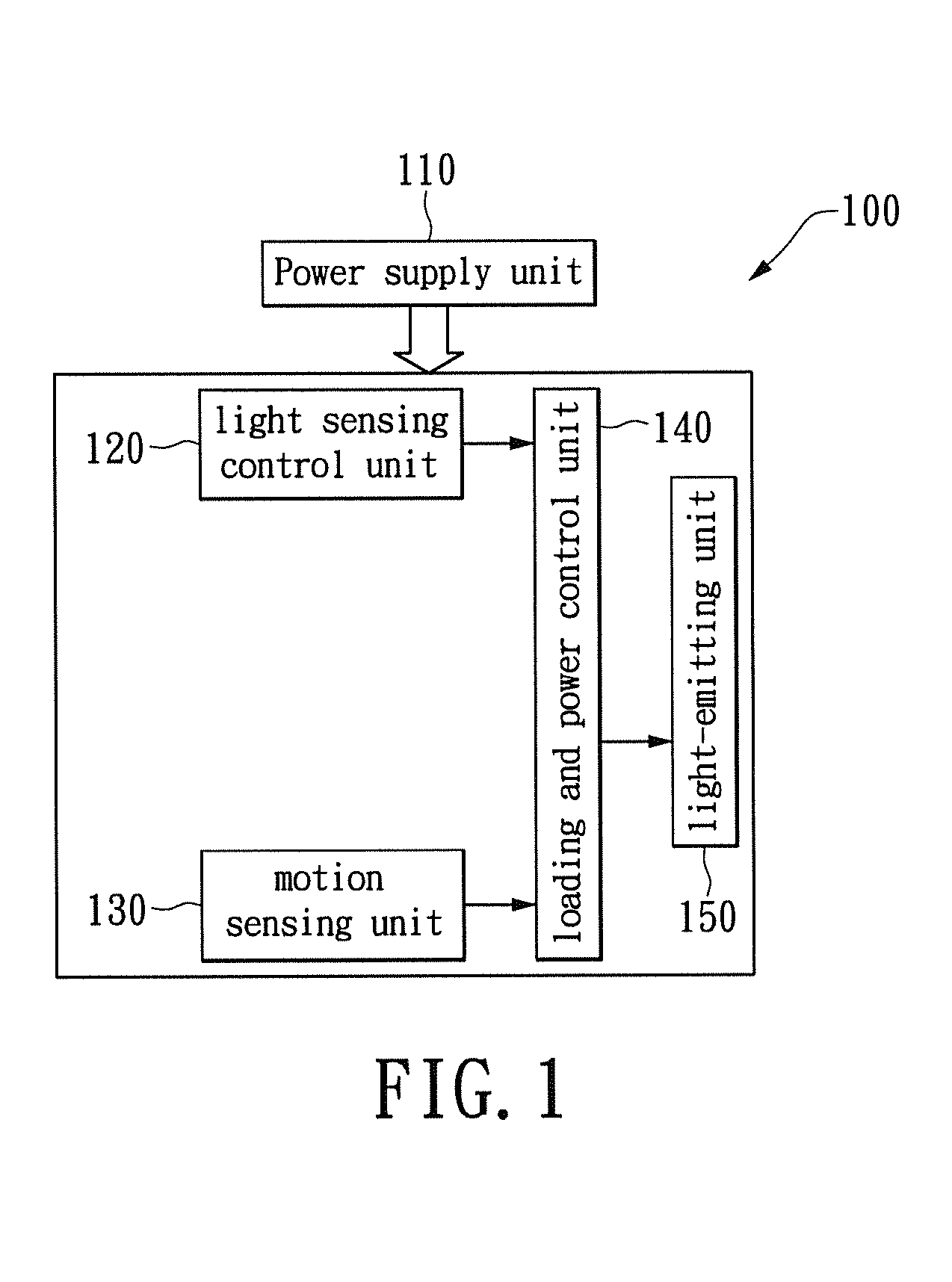
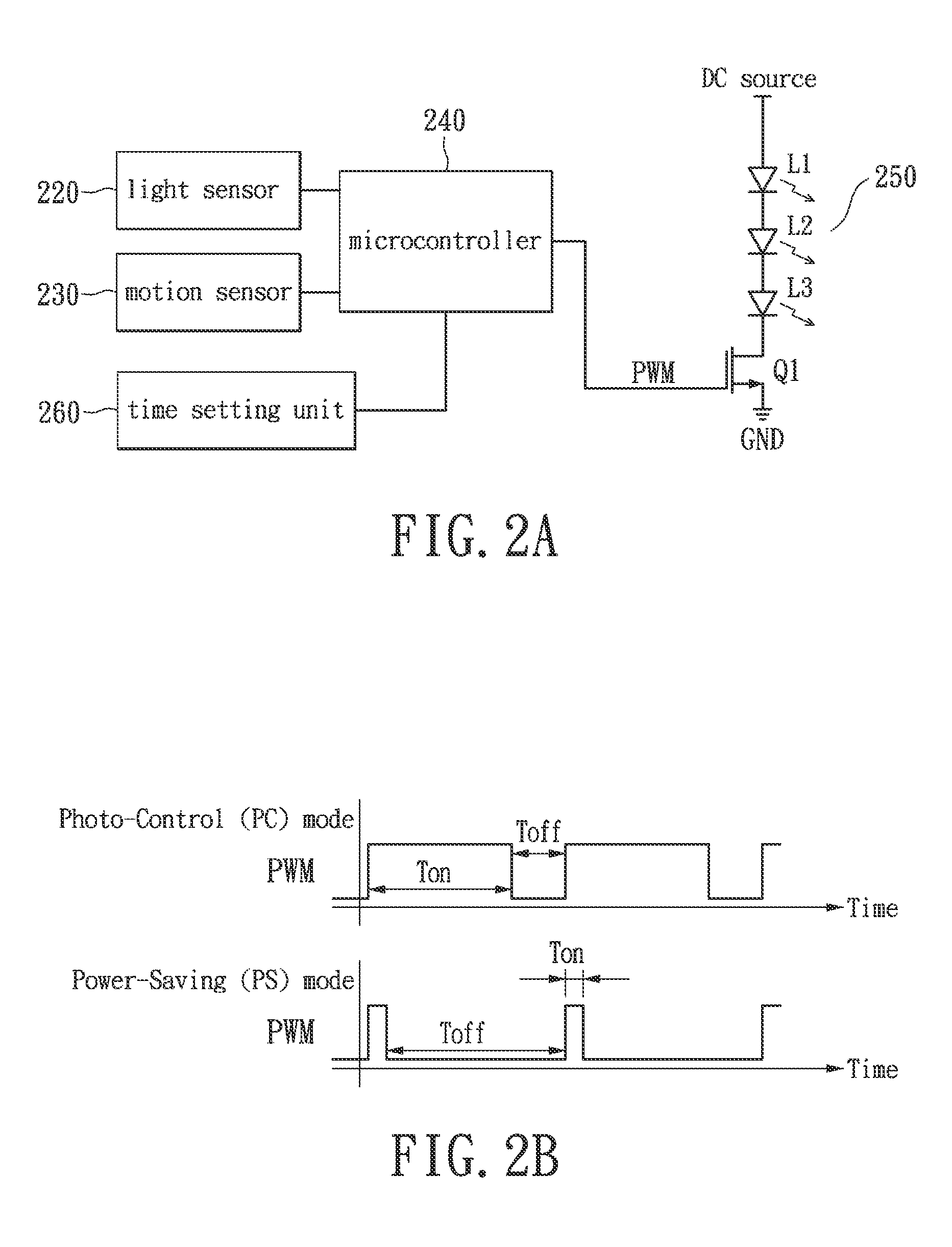
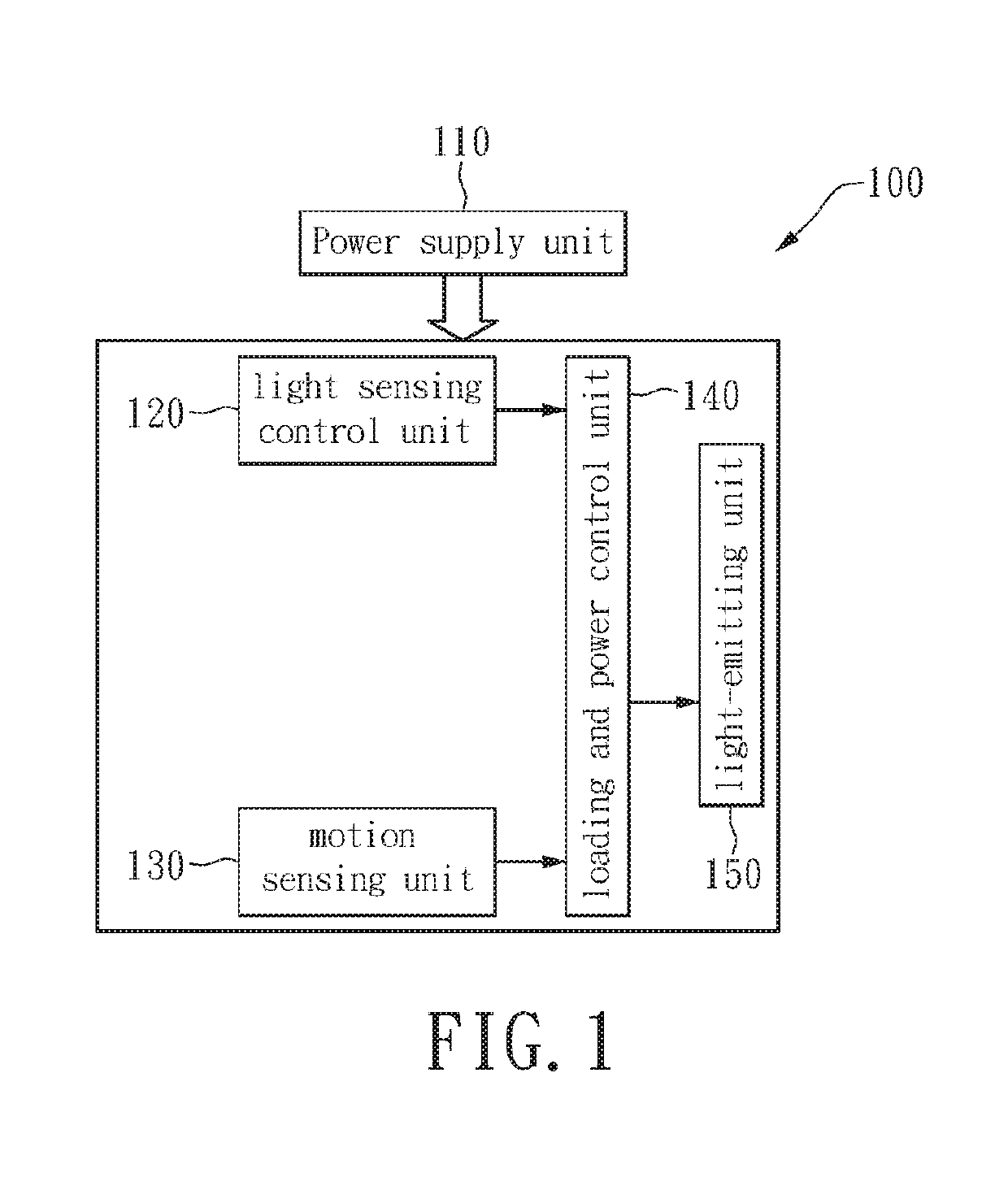
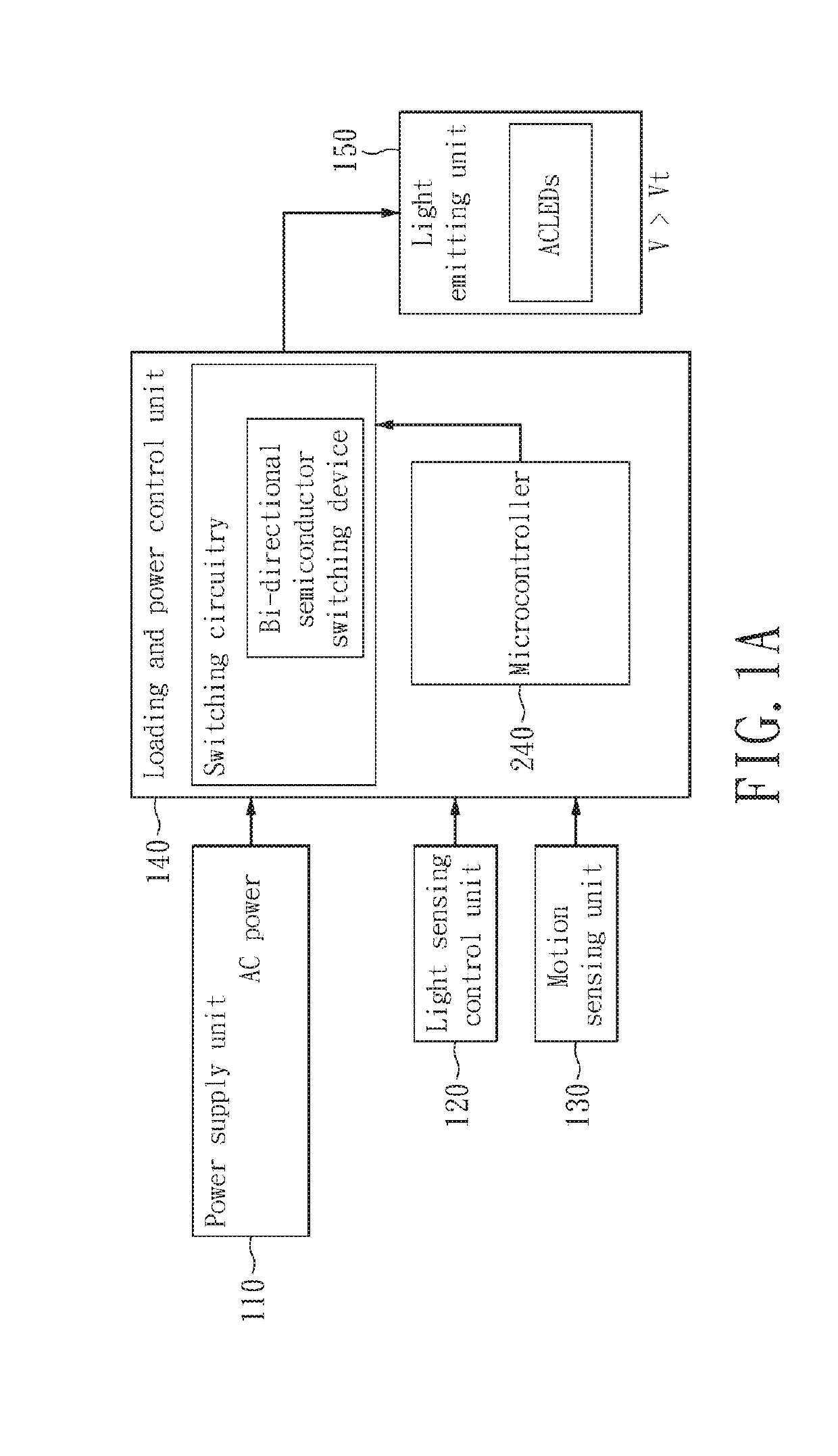
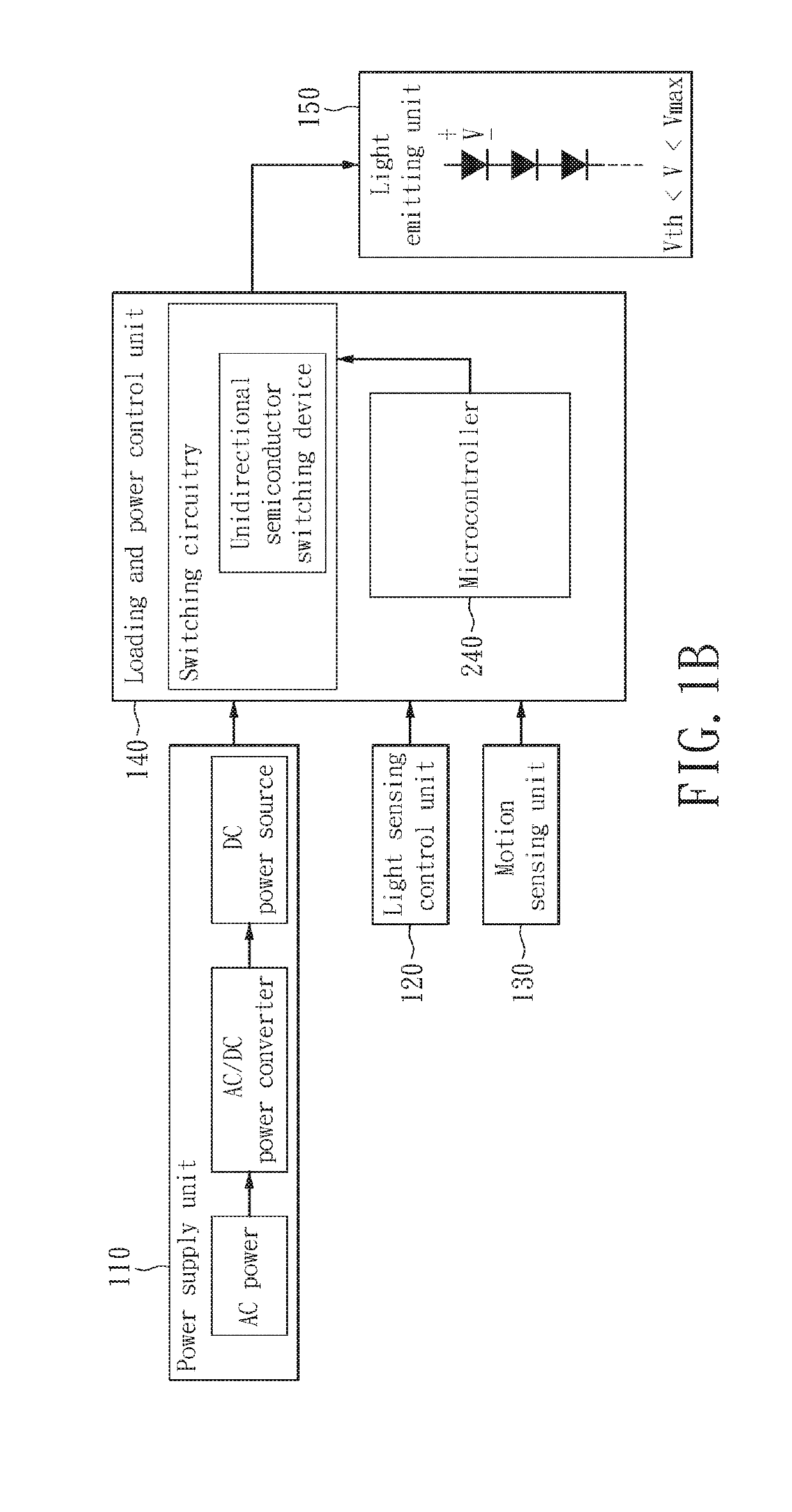
Two-level LED security light with motion sensor
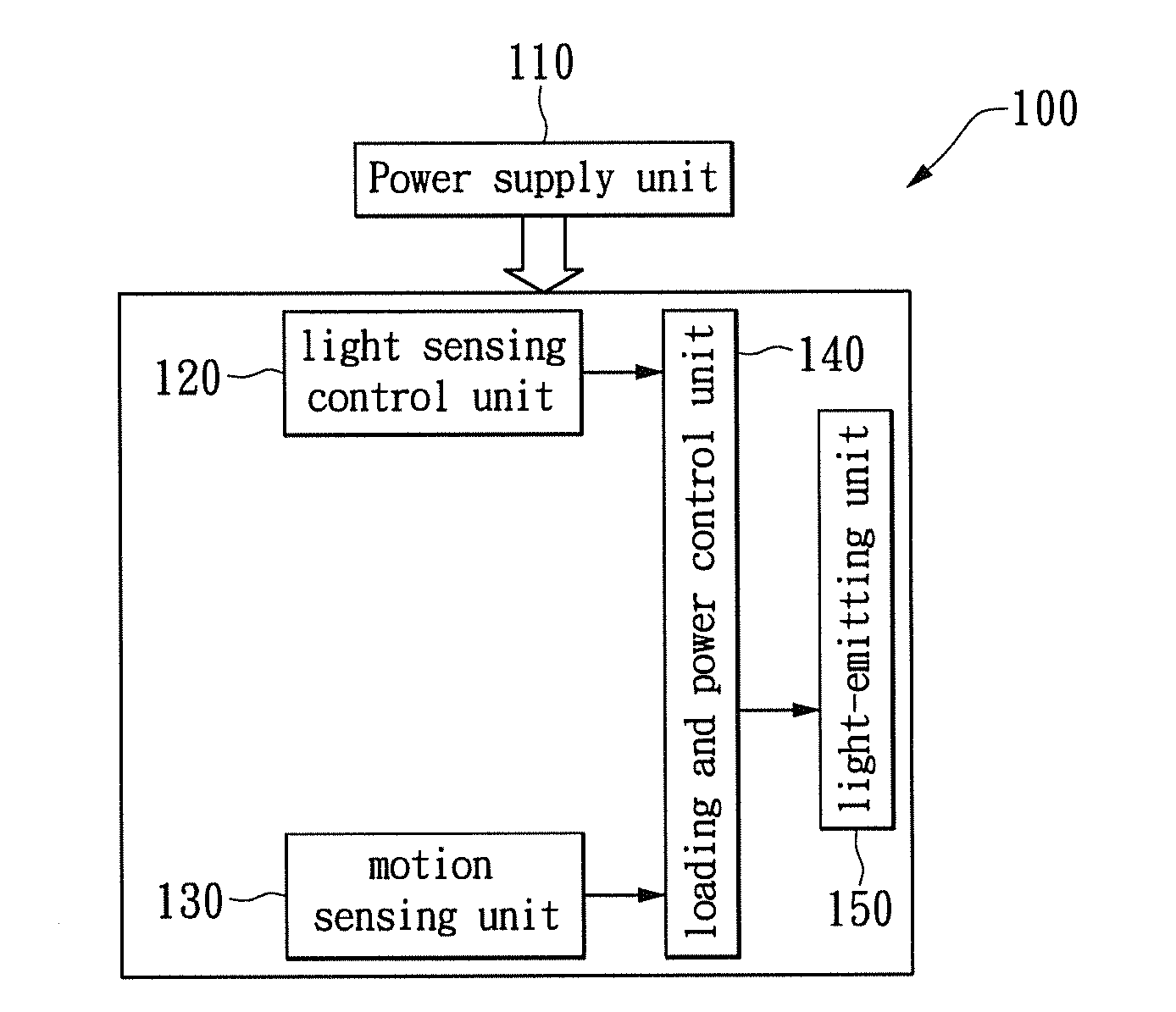
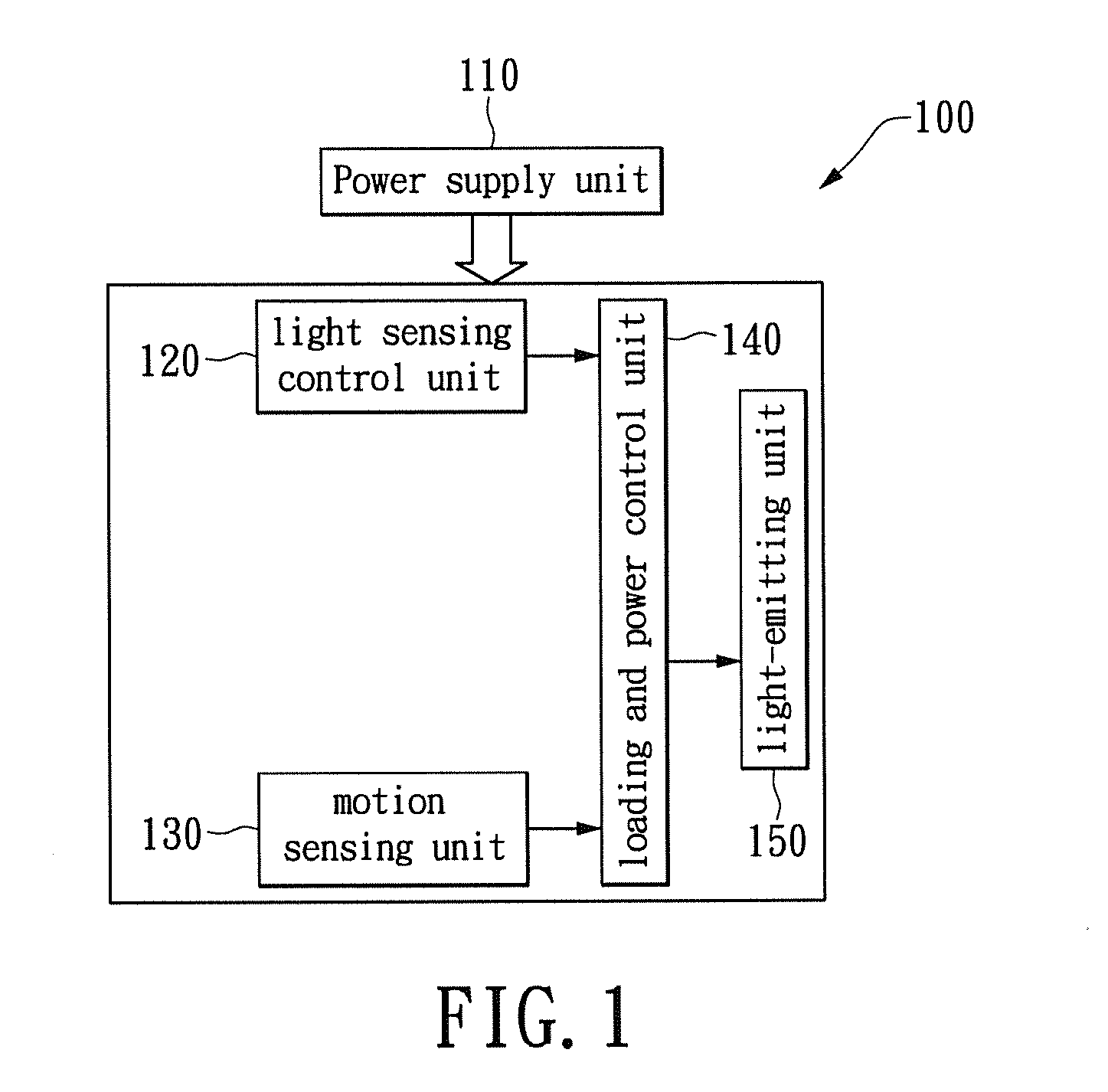
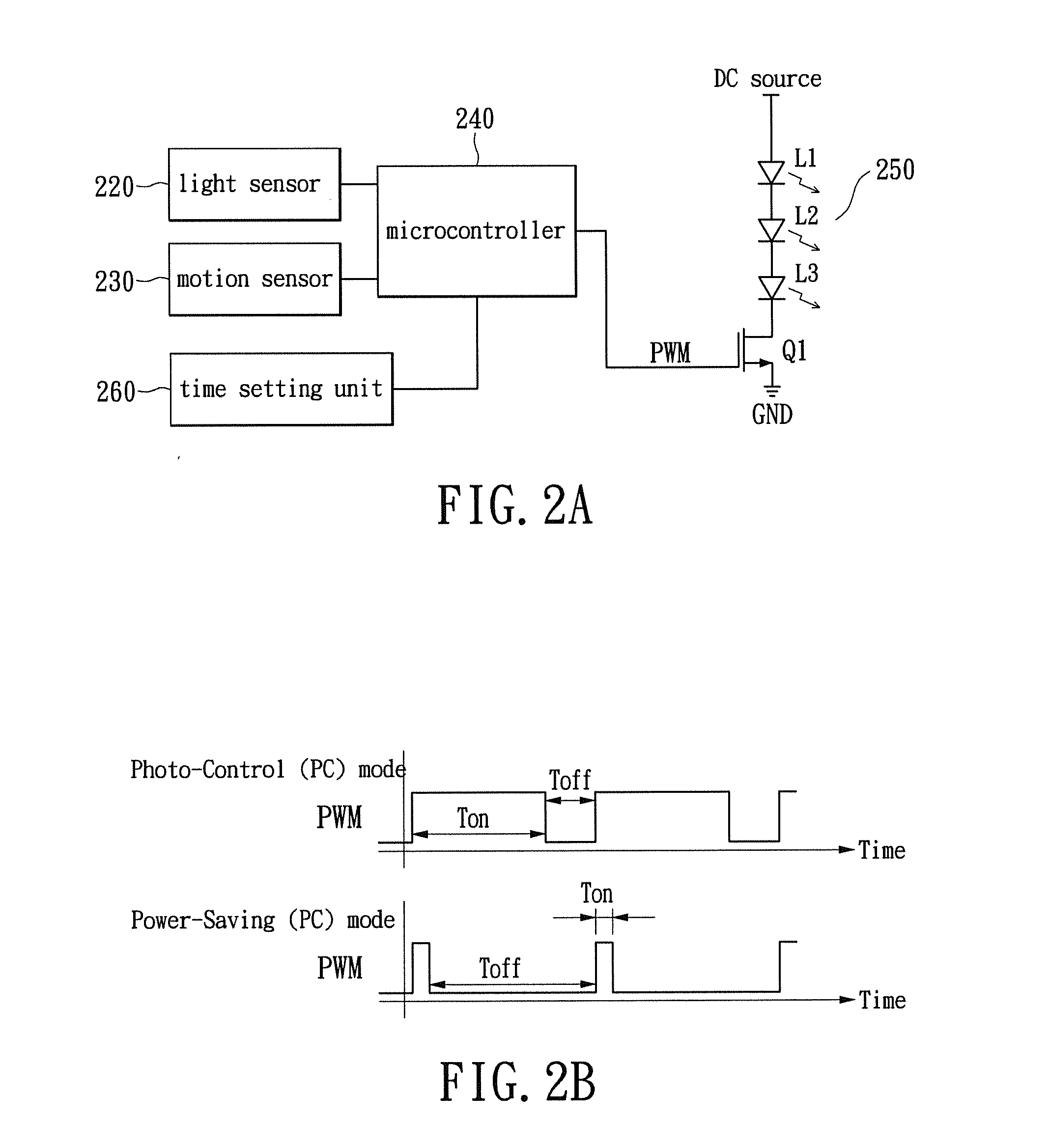
ActiveUS20130049610A1Save energyBatteries circuit arrangementsAlarms with occupancy stimulationLight sensingMotion sensing
A two-level LED security light with a motion sensor. At night, the LED is turned on for a low level illumination. When the motion sensor detects any intrusion, the LED is switched from the low level illumination to a high level illumination for a short duration time. After the short duration time, the LED security light returns to the low level illumination for saving energy. The LED security light includes a power supply unit, a light sensing control unit, a motion sensing unit, a loading and power control unit, and a lighting-emitting unit. The lighting-emitting unit includes one or a plurality of LEDs which may be turned-on or turned-off according to the sensing results from the light sensing control unit. When the motion sensing unit detects an intrusion, the illumination of the LED security light can be immediately turned on to the high level to scare away the intruder.
Owner:VAXCEL INT
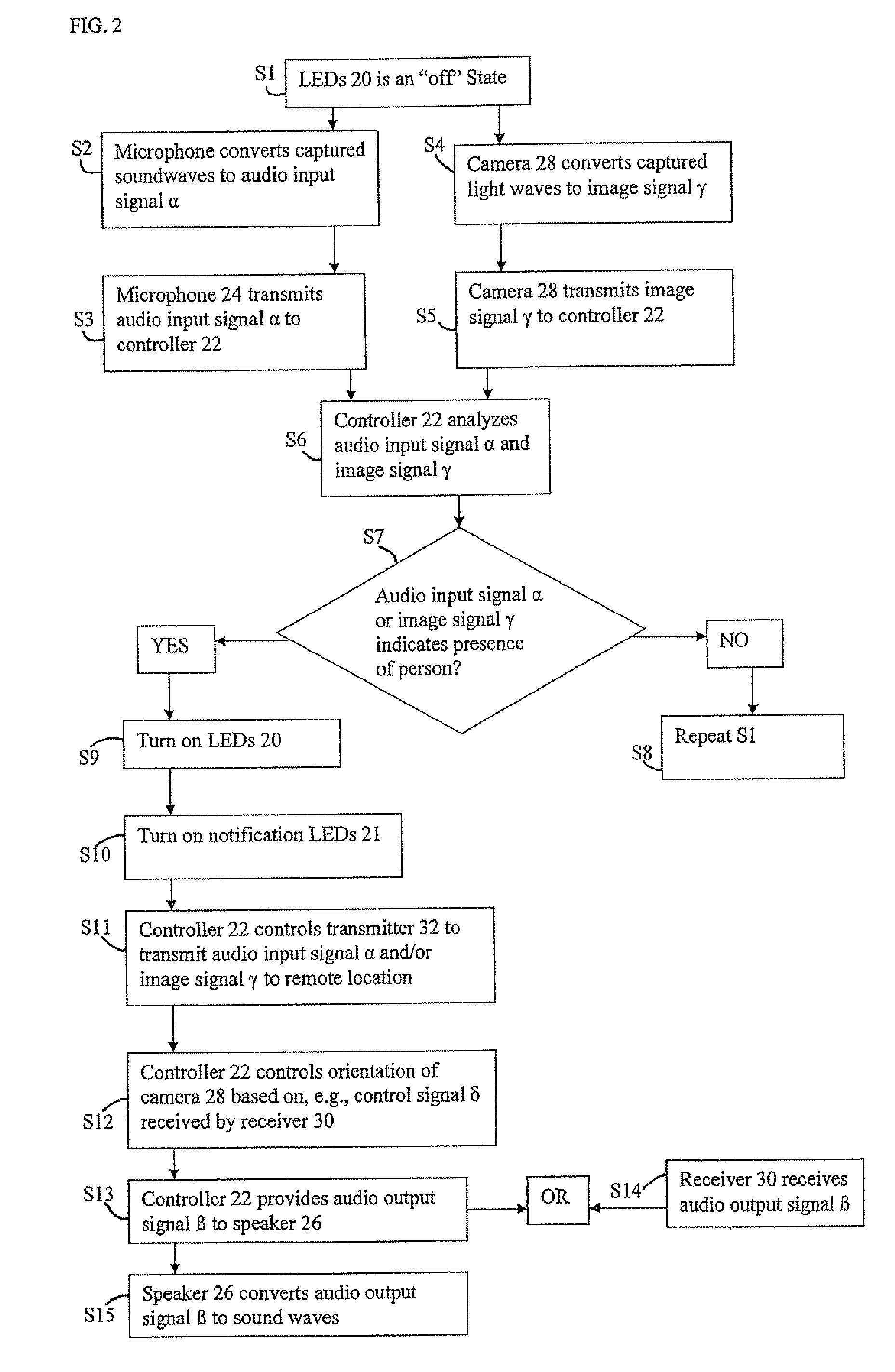
Virtual Presence after Security Event Detection
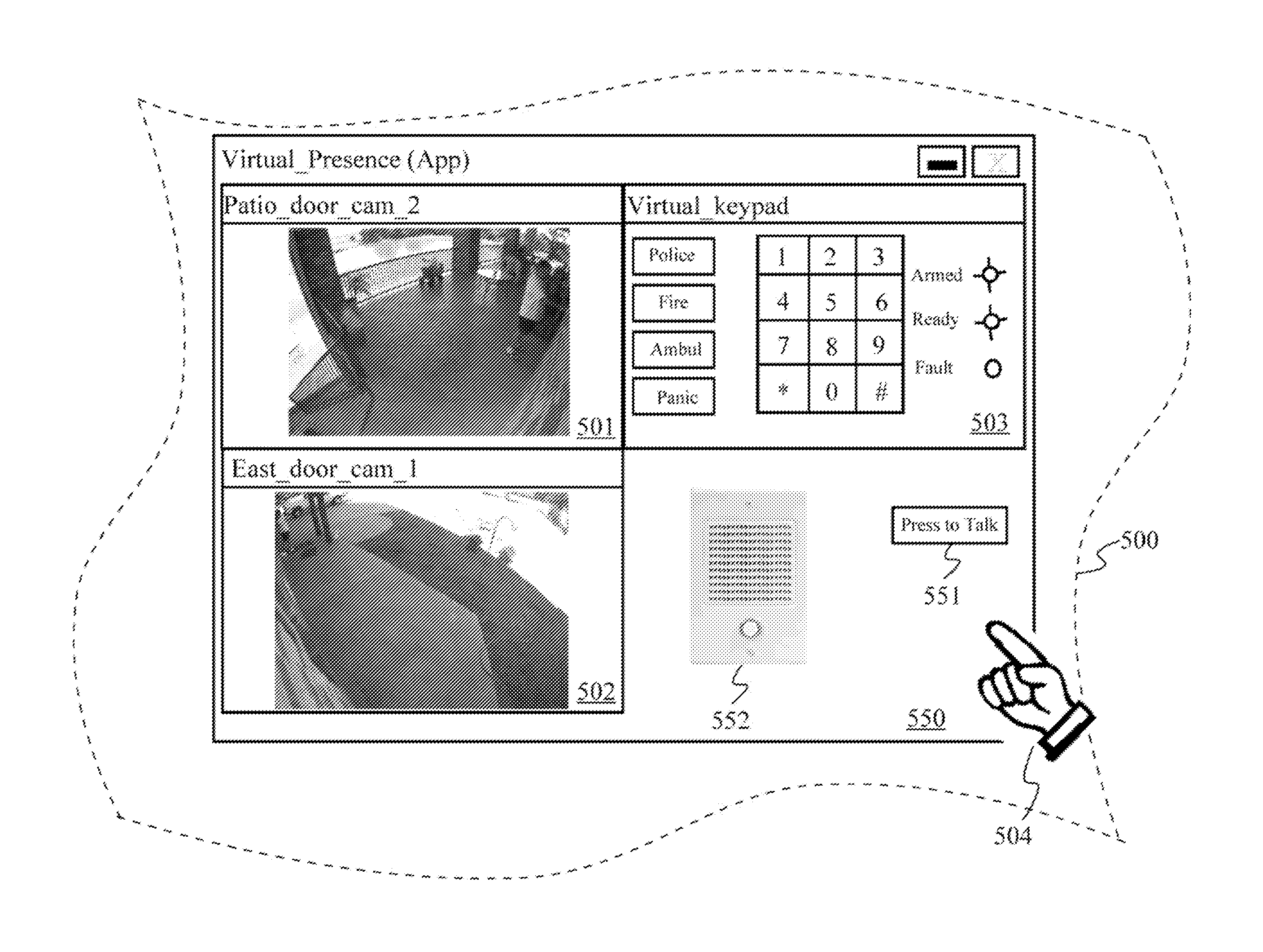
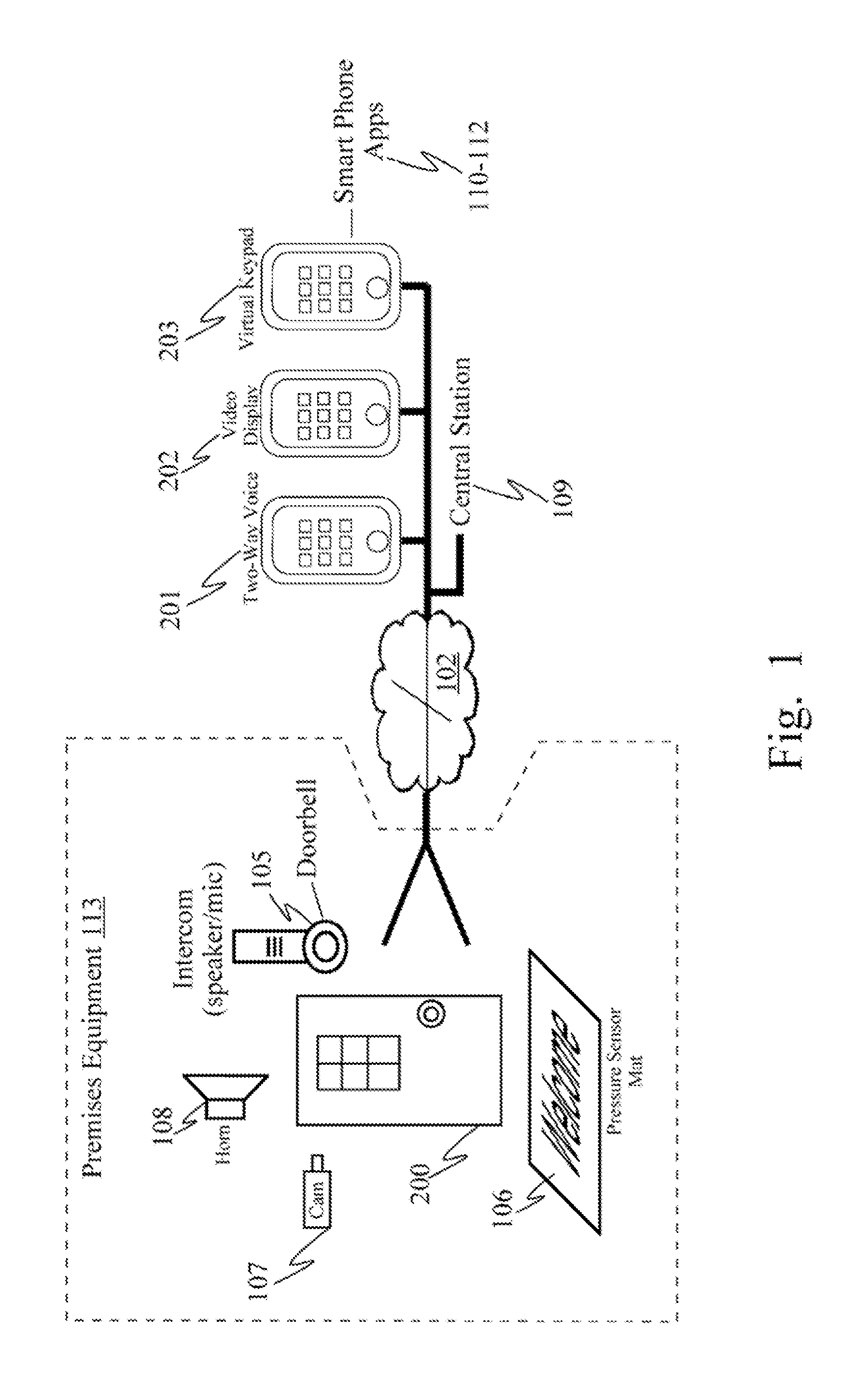
InactiveUS20120001755A1Provides illusionAlarms with occupancy stimulationElectric testing/monitoringTwo-way communicationIntercom
A virtual presence of an resident or owner of a monitored premise (home, office, etc.) is provided by automatic detection of the presence of a visitor, automatic establishment of a video feed to a remote device of the resident or owner, and automatic establishment of two-way audio communications between the remote device and a door intercom at the monitored presence. Using the video feed and the two-way communications, the resident or owner can communicate to the visitor as if the resident or owner were actually in the monitored presence viewing the visitor through a peep-hole or security camera, thereby providing the illusion to the visitor that the premise is actually occupied. Additionally, the resident or owner is provided a remote capability to activate an alarm or disarm and alarm, according to the conditions of the visit and the user's wishes.
Owner:CONRADY RICHARD PAUL
Systems and methods of intrusion detection
ActiveUS20160189496A1Burglar alarm by openingAlarms with occupancy stimulationEngineeringEmbedded system
Owner:GOOGLE LLC
Two-level LED security light with motion sensor
ActiveUS8866392B2Save energyBatteries circuit arrangementsAlarms with occupancy stimulationLight sensingMotion sensing
A two-level LED security light with a motion sensor. At night, the LED is turned on for a low level illumination. When the motion sensor detects any intrusion, the LED is switched from the low level illumination to a high level illumination for a short duration time. After the short duration time, the LED security light returns to the low level illumination for saving energy. The LED security light includes a power supply unit, a light sensing control unit, a motion sensing unit, a loading and power control unit, and a lighting-emitting unit. The lighting-emitting unit includes one or a plurality of LEDs which may be turned-on or turned-off according to the sensing results from the light sensing control unit. When the motion sensing unit detects an intrusion, the illumination of the LED security light can be immediately turned on to the high level to scare away the intruder.
Owner:VAXCEL INT
Subliminal audio burglar deterrent
The present invention is directed to a subliminal audio burglar deterrent device IP and system wherein a subliminal message is created and broadcast using techniques to unconsciously cause a burglar to mistakenly perceive the presence of a human or an animal in the space being protected.
Owner:HAWKES GARY J +1
Internet protocol security camera connected light bulb/system
ActiveUS9654678B1Implemented cost-effectivelyTelevision system detailsImage analysisInternet protocol suiteElectricity
Owner:KUNA SYST
Vacation mode security system and method
InactiveUS20060181401A1Eliminate delaysFrequency-division multiplex detailsAlarms with occupancy stimulationEngineeringSecurity system
A security system for protecting a building which includes at least a first sensor and an alarm panel that includes a microprocessor and memory, said alarm panel having an armed mode, a disarmed mode and a vacation mode, said armed mode and said vacation mode differing with respect to the response to events occurring within the associated building. The invention also includes the method for protecting a building which includes providing at least a first sensor, providing an alarm panel that includes a microprocessor and memory, and providing the security system, normally the alarm panel with features that include an armed mode, a disarmed mode and a vacation mode. The armed mode and the vacation mode differ with respect to the response to events occurring within the associated building.
Owner:HONEYWELL INT INC
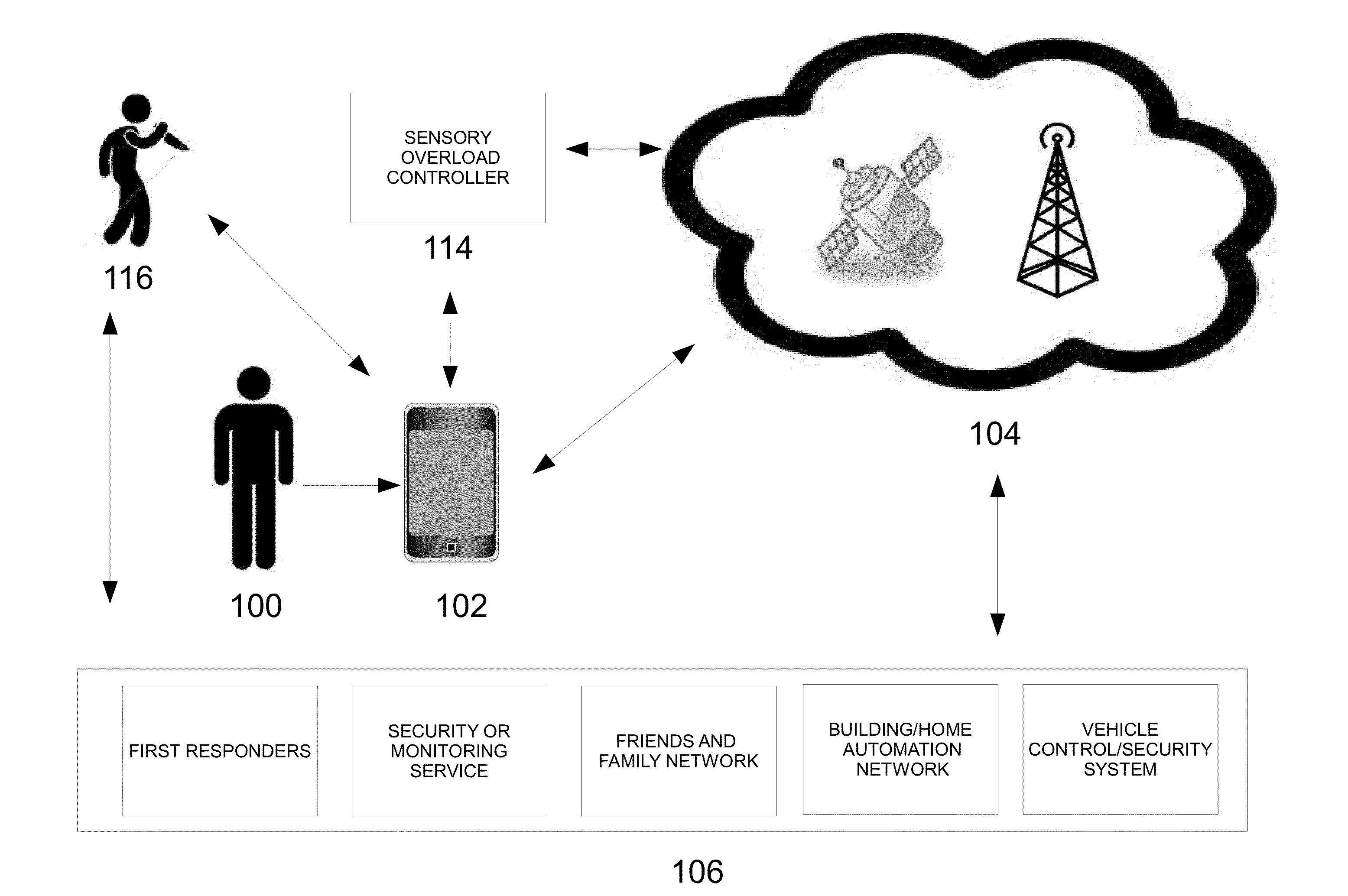
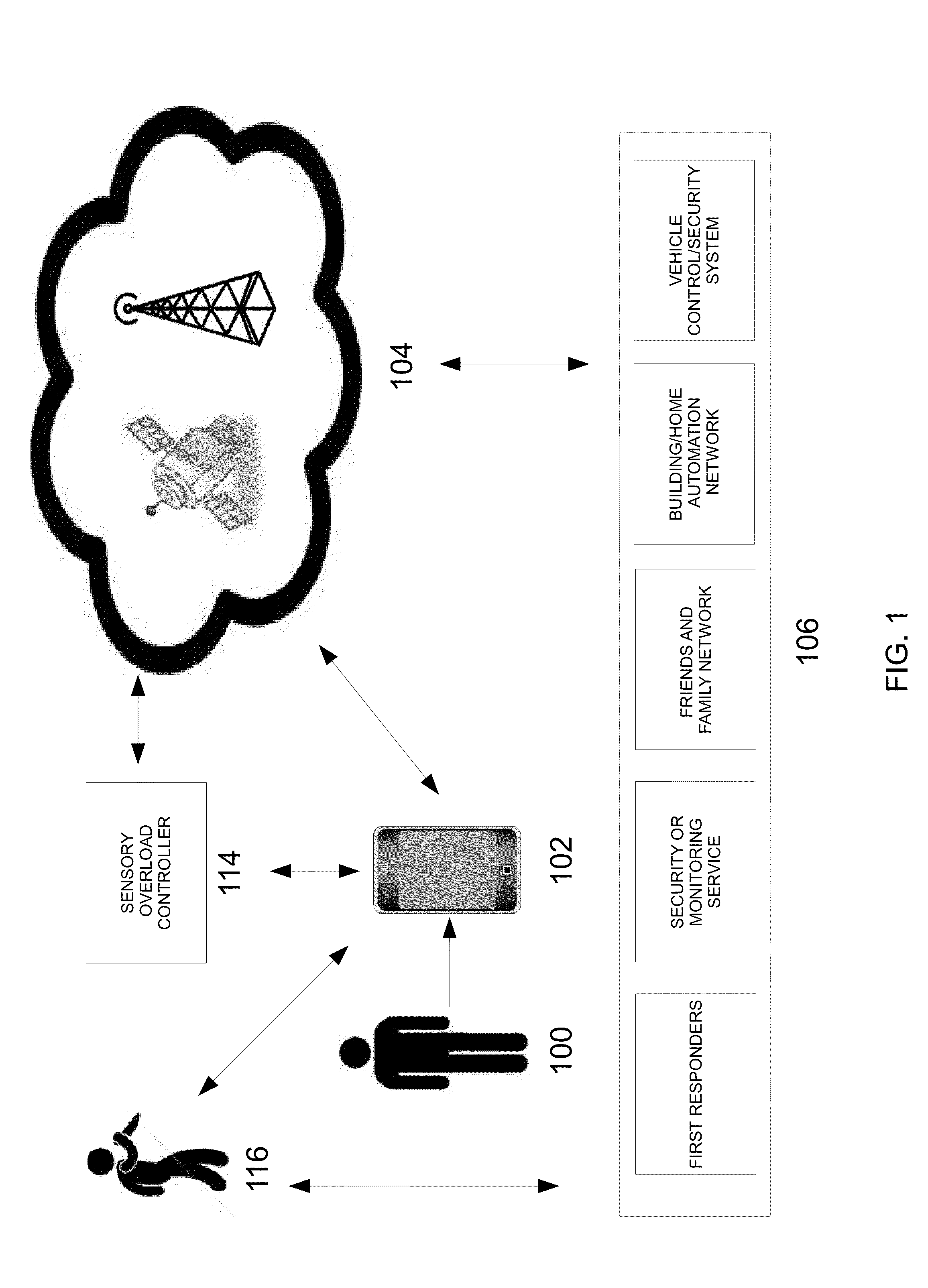
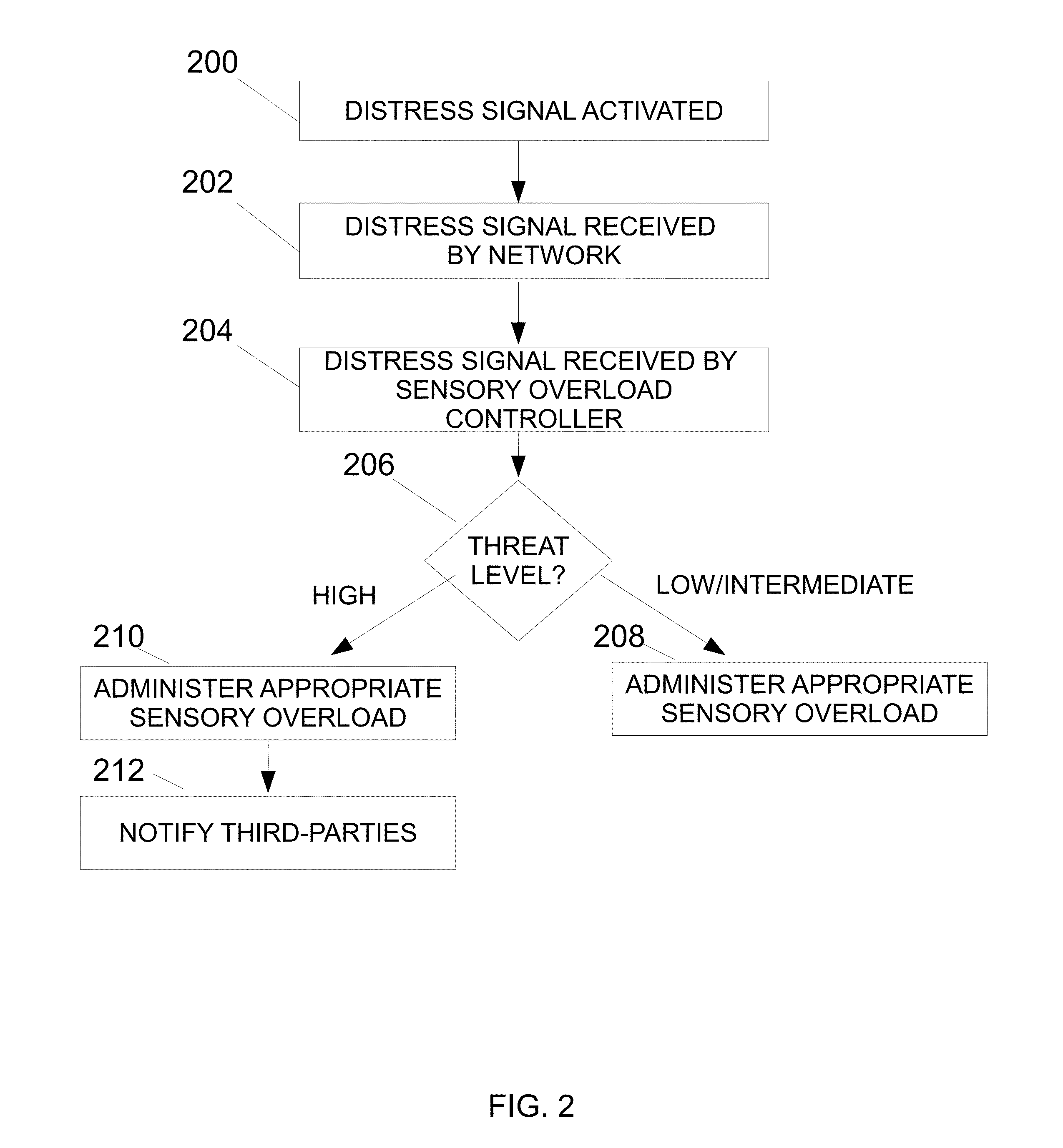
Systems and methods utilizing sensory overload to deter, delay, or disrupt a potential threat
InactiveUS20130088352A1Reduce intensityInterfere with requirementAlarms with occupancy stimulationOODA loopEngineering
The present invention applies OODA Loop (for observe, orient, decide, and act) and Defense and Delay concepts to its processes, by observing and reacting to unfolding threatening events more rapidly than potential perpetrators, thereby disorienting, dazing, and confusing perpetrators before they act, or before they cause additional harm. A sensory overload controller is used to initiate various events that can disturb a perpetrator's thought process, thereby deterring, delaying, and distracting perpetrators, and disrupting or decreasing the intensity of a potential criminal act.
Owner:AMIS DAVID
Internet protocol security camera connected light bulb/system
ActiveUS9143741B1Implemented cost-effectivelyImage analysisElectric circuit arrangementsInternet protocol suiteComputer module
The present invention concerns an apparatus comprising an antenna module and a control module. The antenna module may be configured to connect and send data to a local network and a mobile handheld device through a wireless connection. The control module may be configured to provide (i) a physical connection to the antenna module, (ii) a power source to an external device, and (iii) a camera sensor to capture still and motion pictures and sounds of a surrounding environment of the apparatus. The pictures may be sent as the data through the wireless connection or through a mobile handheld device.
Owner:KUNA SYST
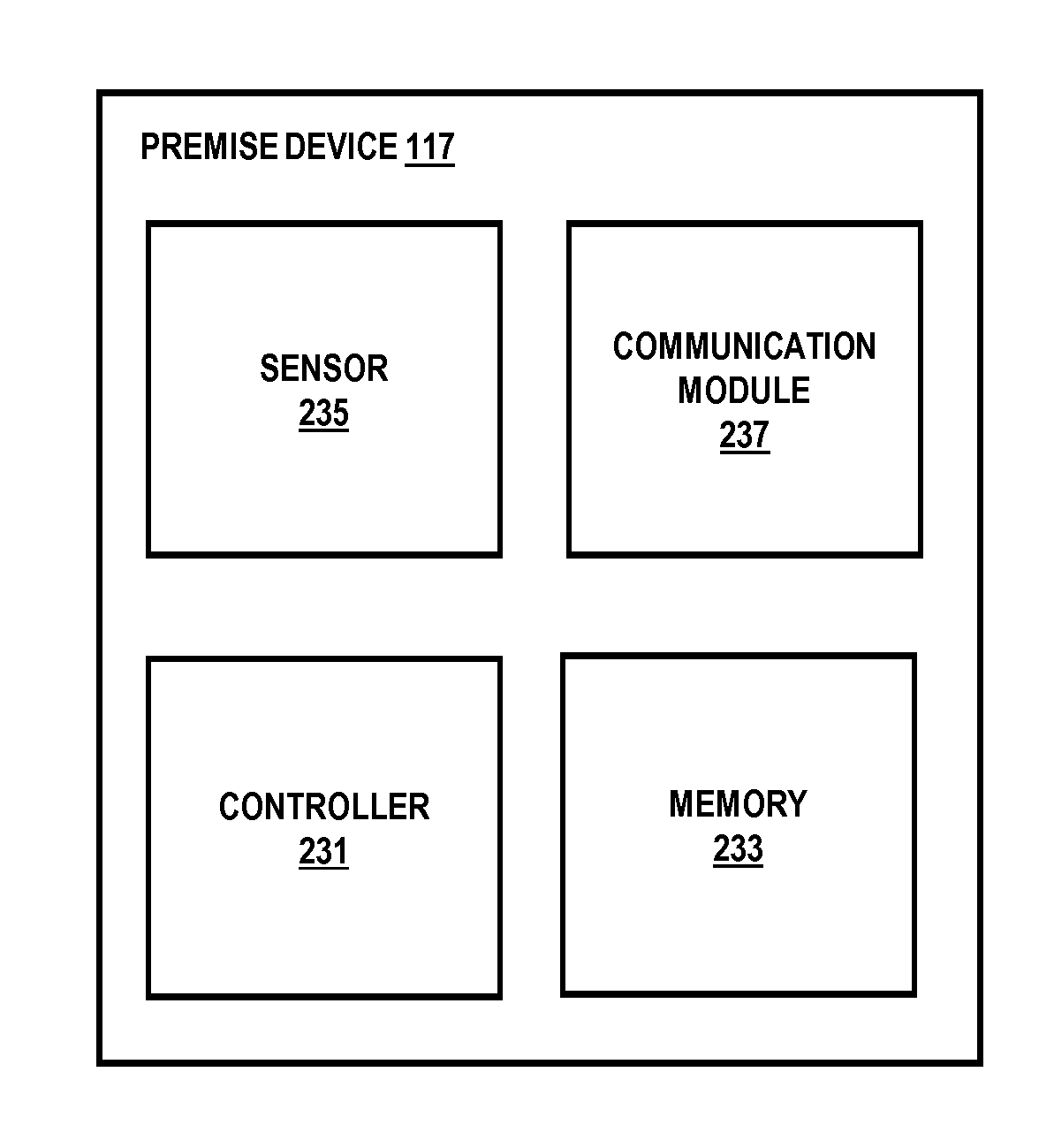
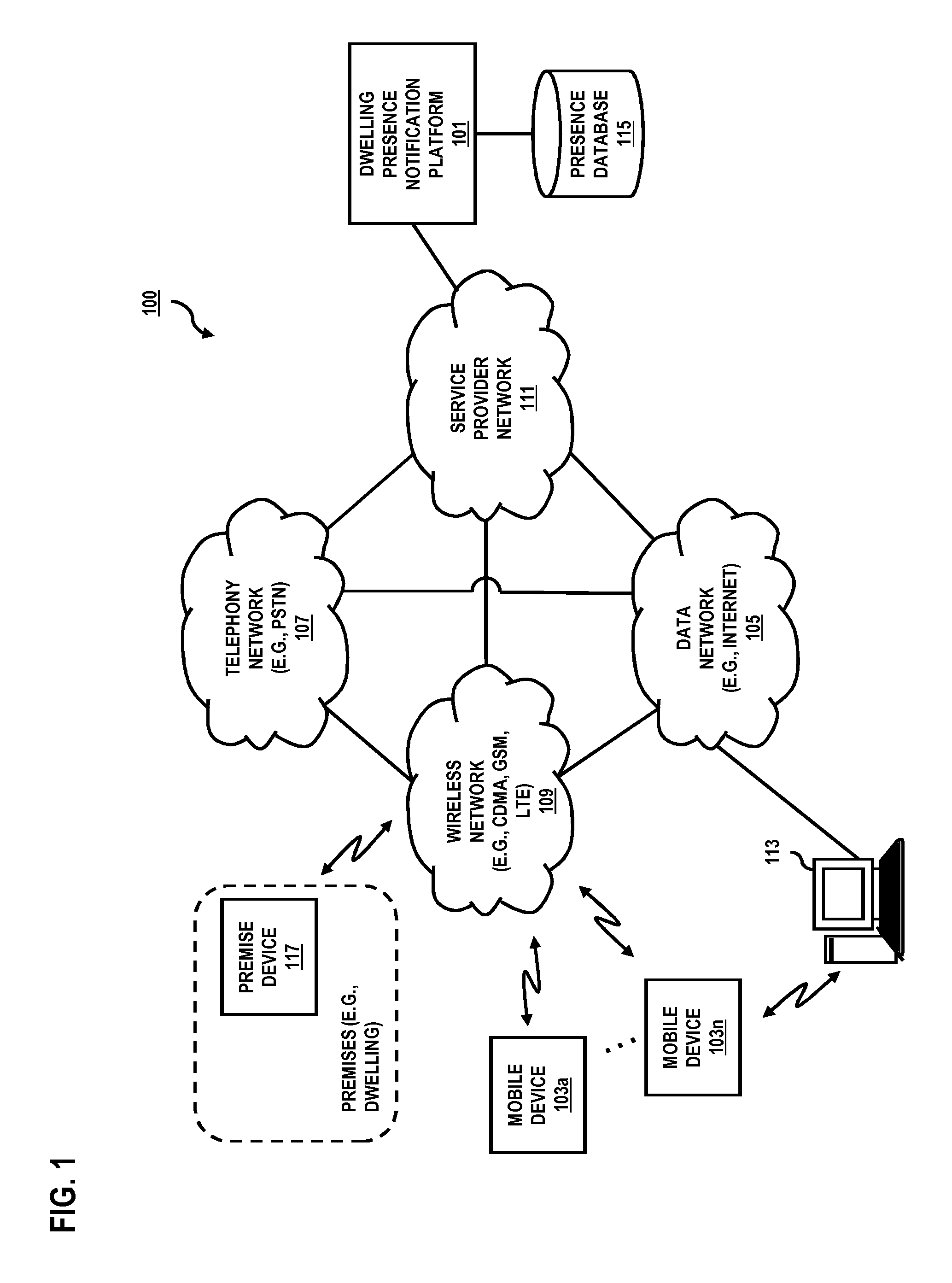
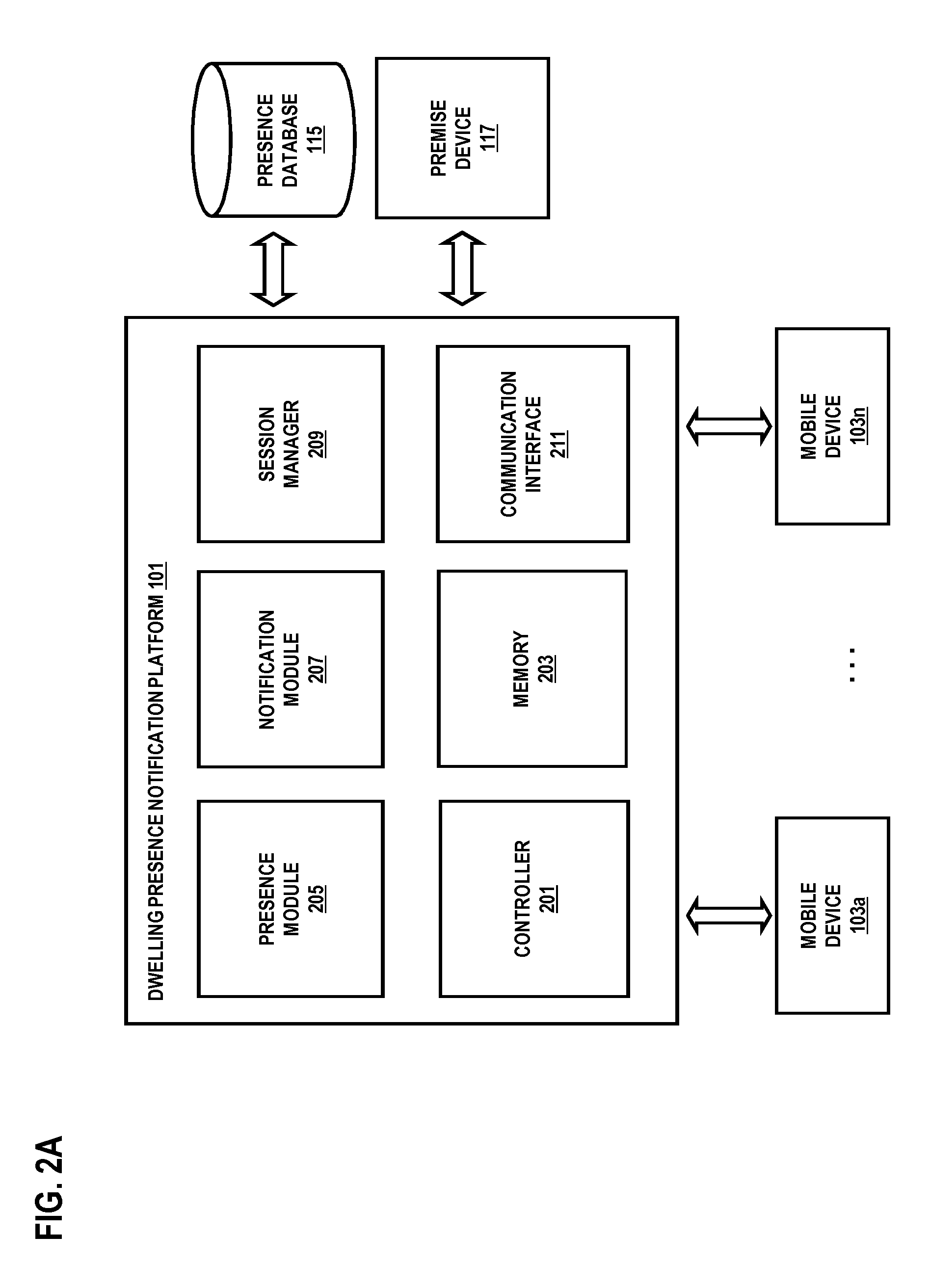
Method and system for providing presence-based communication over a cellular network for a dwelling
ActiveUS20130049954A1Alarms with occupancy stimulationServices signallingRegistration statusProviding presence
An approach for providing presence-based communication over a cellular network for a dwelling is described. A notification message is received over a wireless network to a mobile device associated with a user, wherein the notification message indicates generation of a presence indication signal by a device within a premise of the user. A registration status of the mobile device with the notification service is determined. The notification message is forwarded to the mobile device based on the registration status.
Owner:VERIZON PATENT & LICENSING INC
System and method to protect users via light fixture networks
InactiveUS20170098354A1Transmission systemsAlarms with occupancy stimulationCommunication deviceElectronic messaging
According to some embodiments, information may be received about at least one user associated with a light fixture network having a plurality of light fixtures each equipped with a wireless communication device. Based on the information about the at least one user, a protection feature may be determined to be applied via the light fixture network. The system may then dynamically collect and monitor an appropriate parameter from a sensor associated with at least one of the light fixtures in the light fixture network. Responsive to this monitoring, it may be automatically arranged for at least one electronic message to be transmitted.
Owner:LINKBEE LLC
Location-based addressing lighting and environmental control system, device and method
ActiveUS20110068900A1Less bandwidthAttenuation bandwidthCircuit arrangementsAlarms with occupancy stimulationLight equipmentControl system
Owner:THE WATT STOPPER
Multifunction portable security system
InactiveUS20070252720A1Alarms with occupancy stimulationSignalling system detailsEngineeringControl circuit
A security system and method for warning a potential intruder. One example system includes detector configured to detect the presence of a potential intruder within close proximity to the security system. At least one warning device is also configured to communicate warning signals to the potential intruder. The example system further includes a control circuit configured to cause the warning devices to automatically communicate a series of warning signals in a progressive manner to the potential intruder. Each subsequent warning signal becomes more severe than the last warning signal, and each subsequent warning signal is typically only provided if the potential intruder is detected by the detector within a predetermined time window since the communication of a previous warning signal.
Owner:U S SAFETY & SECURITY
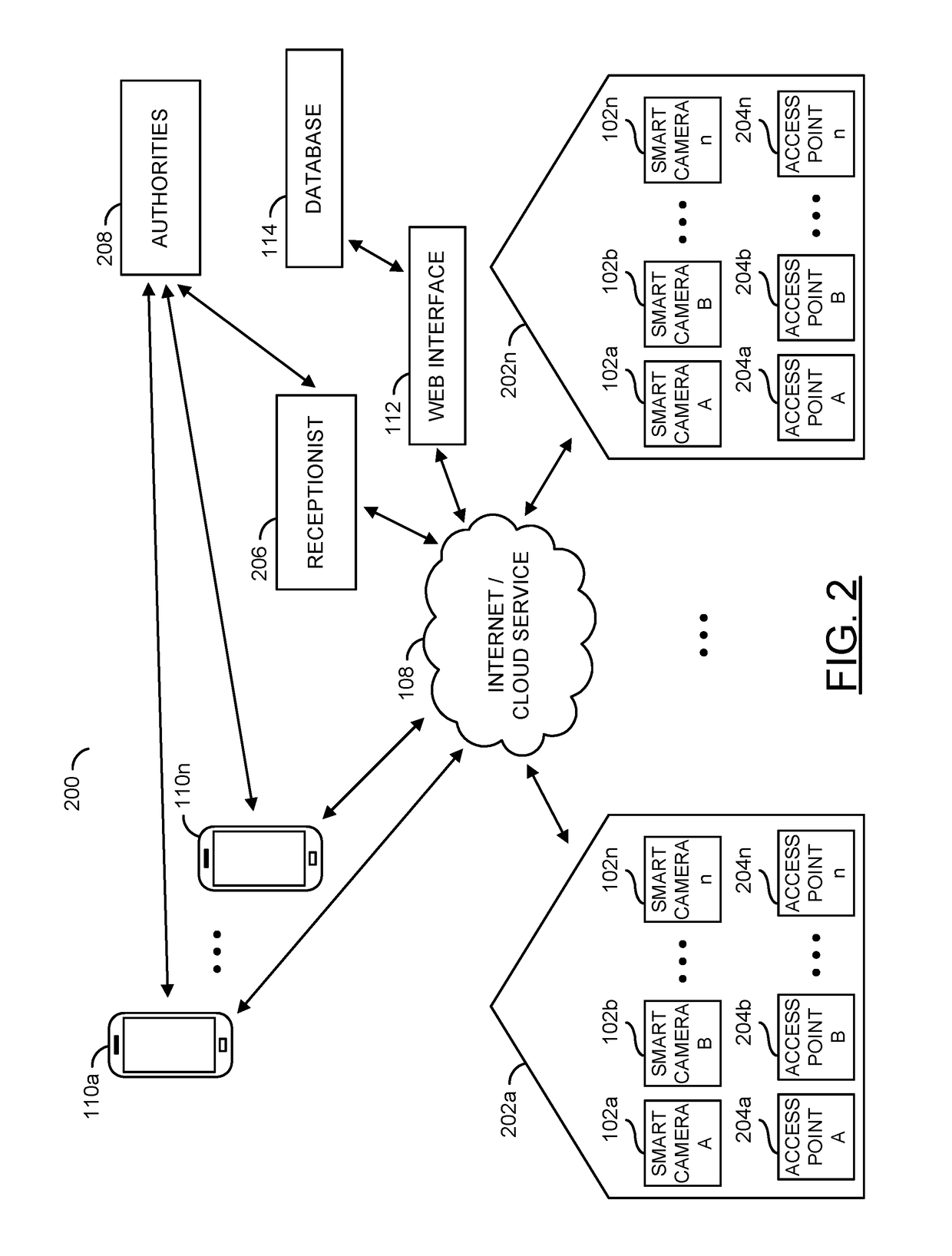
eReceptionist and eNeighborhood watch system for crime prevention and/or verification
ActiveUS9728077B1Alarms with occupancy stimulationAlarms with smoke/gas/colored-powderComputer hardwareComputer science
A system comprising a camera sensor, a circuit and an identification device. The camera sensor may be configured to generate video data of an environment. The circuit may be configured to (A) communicate with a network through a wireless connection, (B) provide an electrical connection to (i) a plurality of components and (ii) the camera sensor and (C) enable at least one of (i) the components and (ii) the camera sensor in response to an authentication signal. The identification device may be configured to generate the authentication signal. The plurality of components may be configured to implement a virtual receptionist. The video data may be transmitted to the network. The authentication signal may be transmitted using the network. The notifications may be generated by the components.
Owner:KUNA SYST
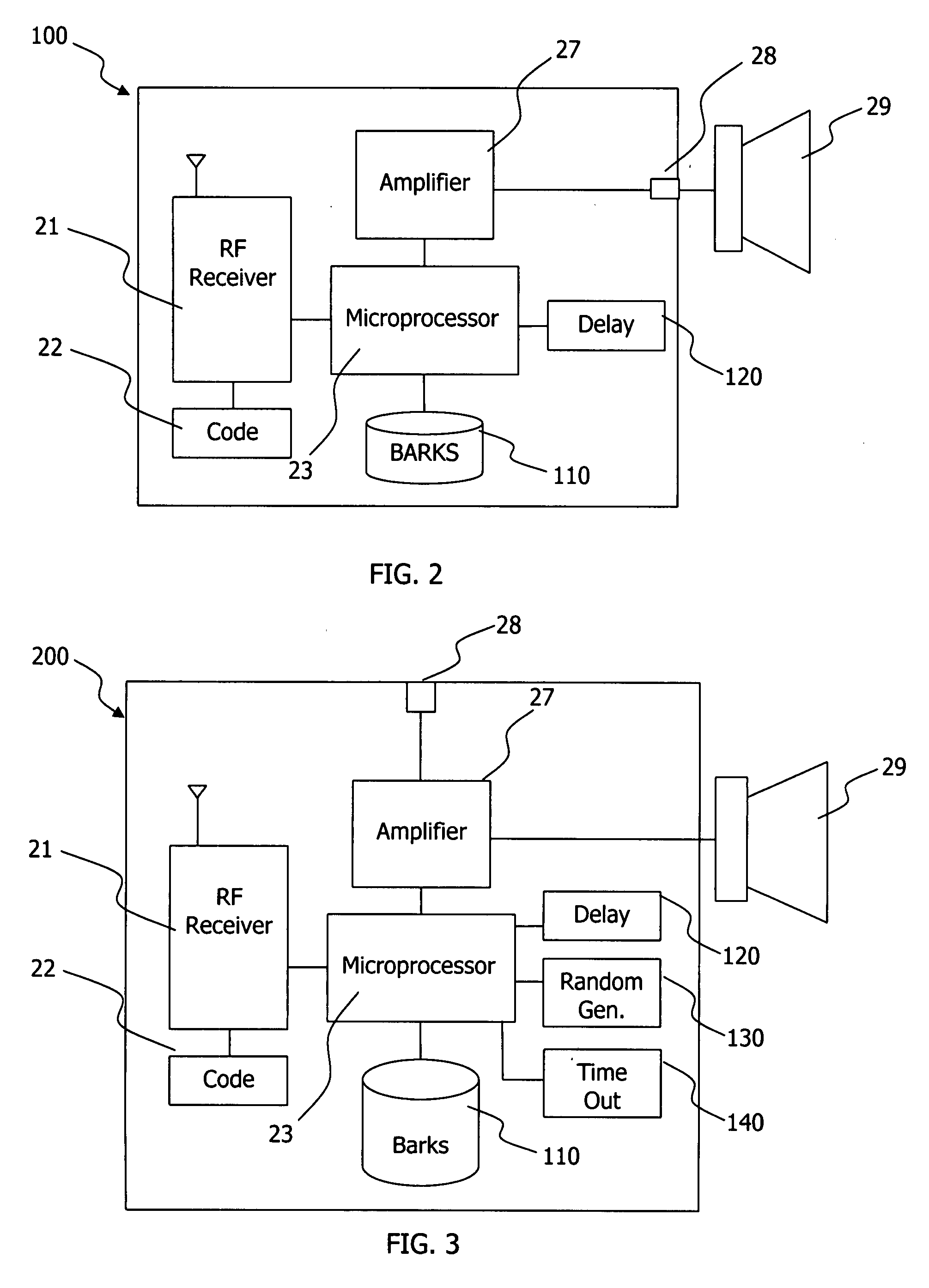
Wireless dog barking alarm system
InactiveUS20120293329A1Alarms with occupancy stimulationBurglar alarm mechanical vibrations actuationEngineeringLoudspeaker
The present invention is an alarm system that includes at least one base unit operable to detect sound levels and to transmit a signal to cause an alarm response, such as emission of media that may be the sound of one or more dog barks. The media may be emitted through one or more applicable broadcasting device, such as through a speaker, and may be the sound of one or more dog barks. The broadcasting device and base units may be configured to function collectively to create a realistic deterrent effect. Other alarm responses may be part of the system, such as electronic device warning messages, turning on a light, etc. The alarm responses and the general operation of the system may be set by a user, either through the base unit or by other remote input means (e.g., a fob unit or other electronic device).
Owner:CUNNINGHAM JAMES VERNON +4
Home Security System With Automatic Context-Sensitive Transition To Different Modes
ActiveUS20160189526A1Burglar alarm by openingAlarms with occupancy stimulationOperation modeEngineering
A home security system may infer a mode of operation based on indications it receives regarding a user's behavior. The disclosed implementations provide for a vacation mode of operation that defines a response for a security event that differs from the response that would be provided by the home security system for the same security event if it operated in another mode such as an away mode.
Owner:GOOGLE LLC
Location-based addressing lighting and environmental control system, device and method
ActiveUS8796958B2Less bandwidthAttenuation bandwidthCircuit arrangementsAlarms with occupancy stimulationLight equipmentControl system
Location-Based Addressing (LBA) is a method of controlling and commissioning networked lighting devices. The lighting devices communicate over a wireless network using radio frequency communication protocols. The lighting devices are commissioned or grouped based on their respective locations in a building floor plan or a building architecture. The lighting devices are commissioned to respond to radio frequency communications that correspond to their respective locations. This imposed location-based architecture reduces the amount of transmitted data required to control the lighting devices and, thus, reduces the radio bandwidth required to control the lighting devices. In other words, controlling devices “multicast” instructions and controlled devices “listen” for instructions and act only upon instructions that correspond to their respective location. Hand shaking or two-way communication between the controlling devices and the controlled devices is not required.
Owner:THE WATT STOPPER
Lifestyle security light
ActiveUS20190141812A1Save energyBatteries circuit arrangementsAlarms with occupancy stimulationCommunication interfaceDual mode
A security light technology to configure an automatically setting timer used for selecting and operating a light-on duration activated by a motion sensor is disclosed. The disclosed uses a shutoff transition mode to eliminate a hassle or hardship caused by an unexpected “shutoff” of illumination. The shutoff transition mode also serves a communication interface between the motion sensor and an occupant remaining in a detection space such that the occupant can interrupt the shutoff transition mode. The disclosed uses a software algorithm to detect and learn the motion characteristics of occupants in the detection space and thereby to automatically set a timer to operate the light-on duration triggered by a motion intrusion. The disclosed also teaches a dual mode motion sensing light configured with a short timer to manage a pathway illumination and a long timer to manage an occupancy illumination bridged by the shutoff transition mode.
Owner:VAXCEL INT
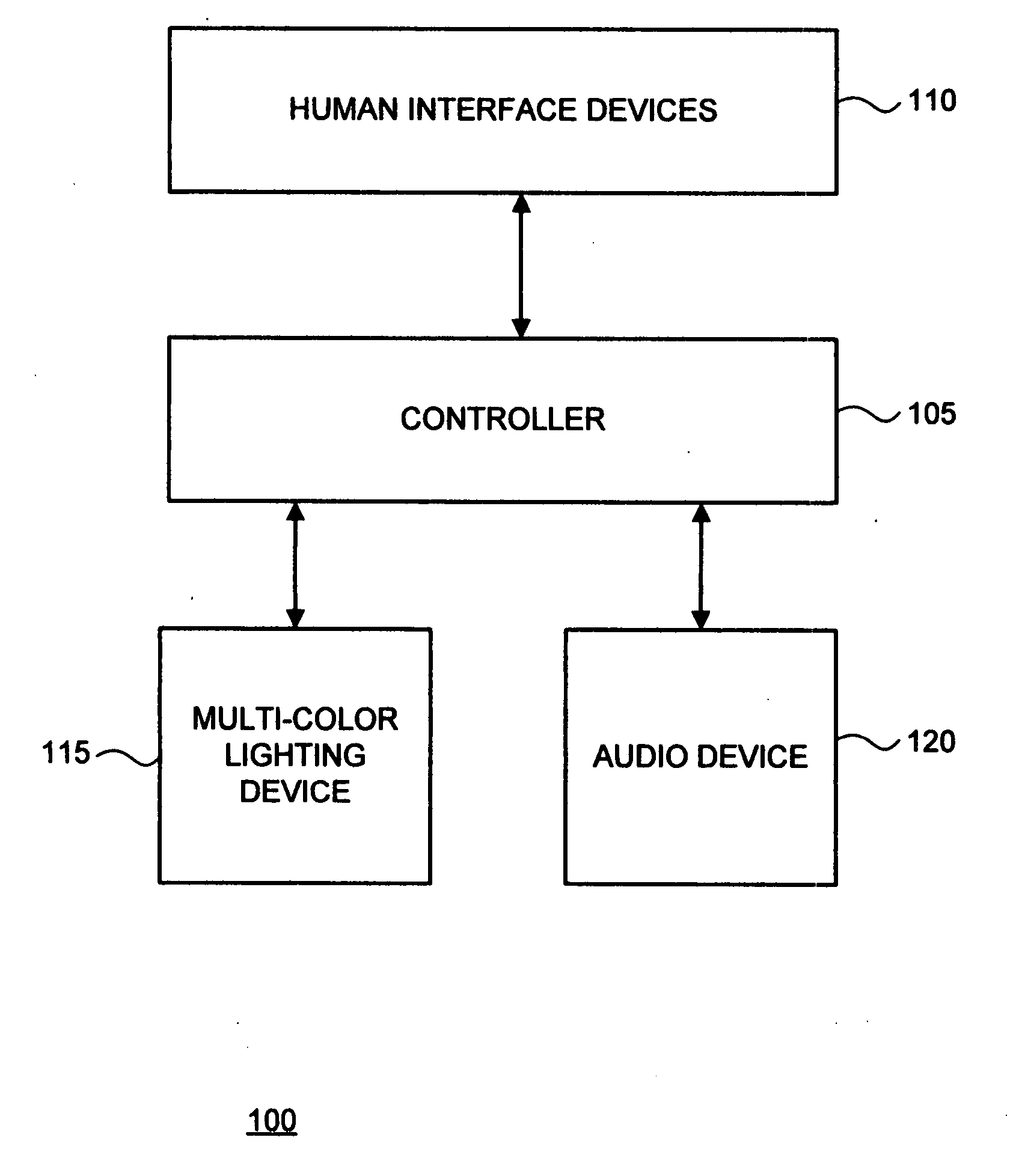
Intrusion deterrence system and method
InactiveUS20090109051A1Avoid premature mortality riskLow powerAlarms with occupancy stimulationSignalling system detailsPhysical securityLight equipment
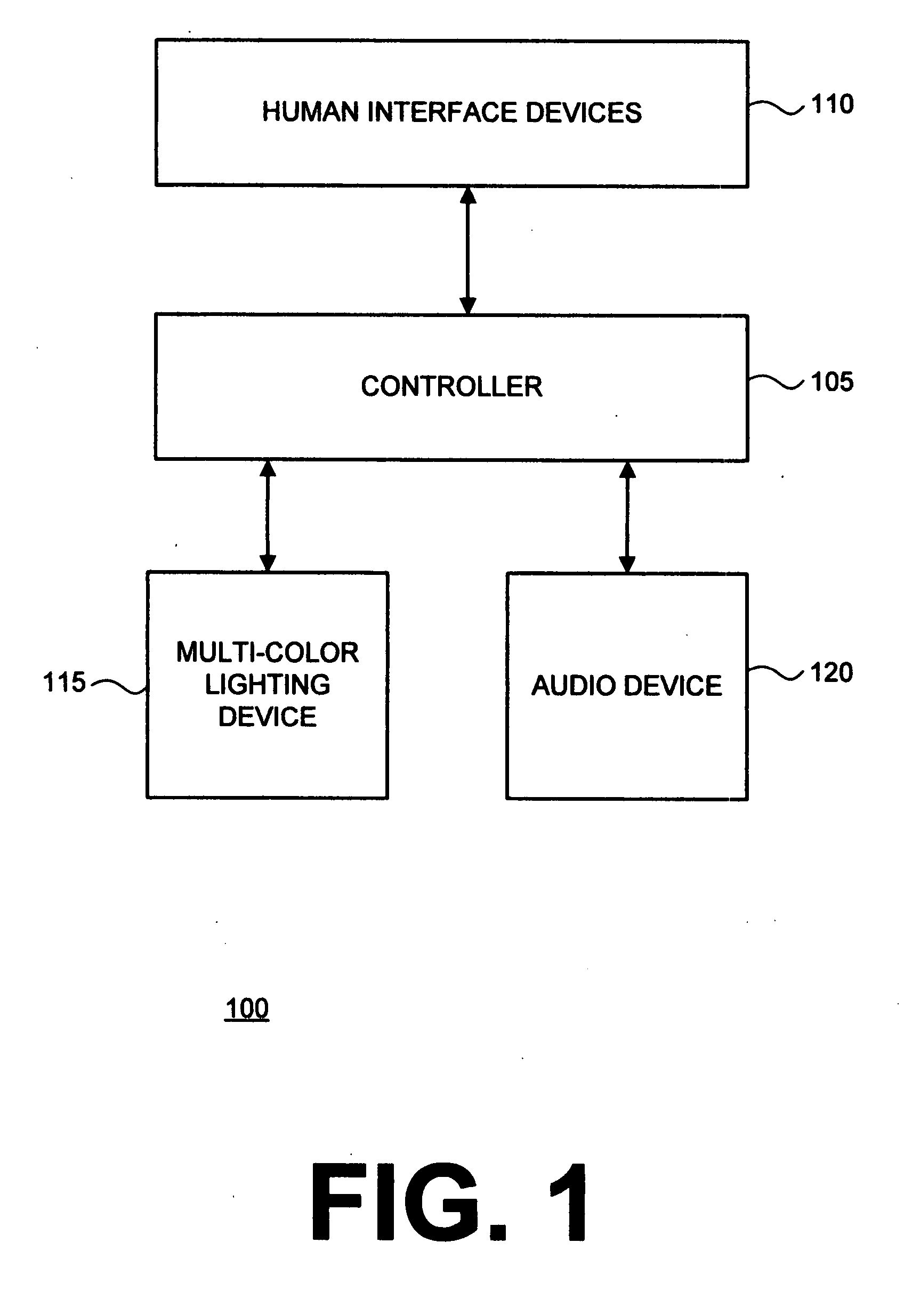
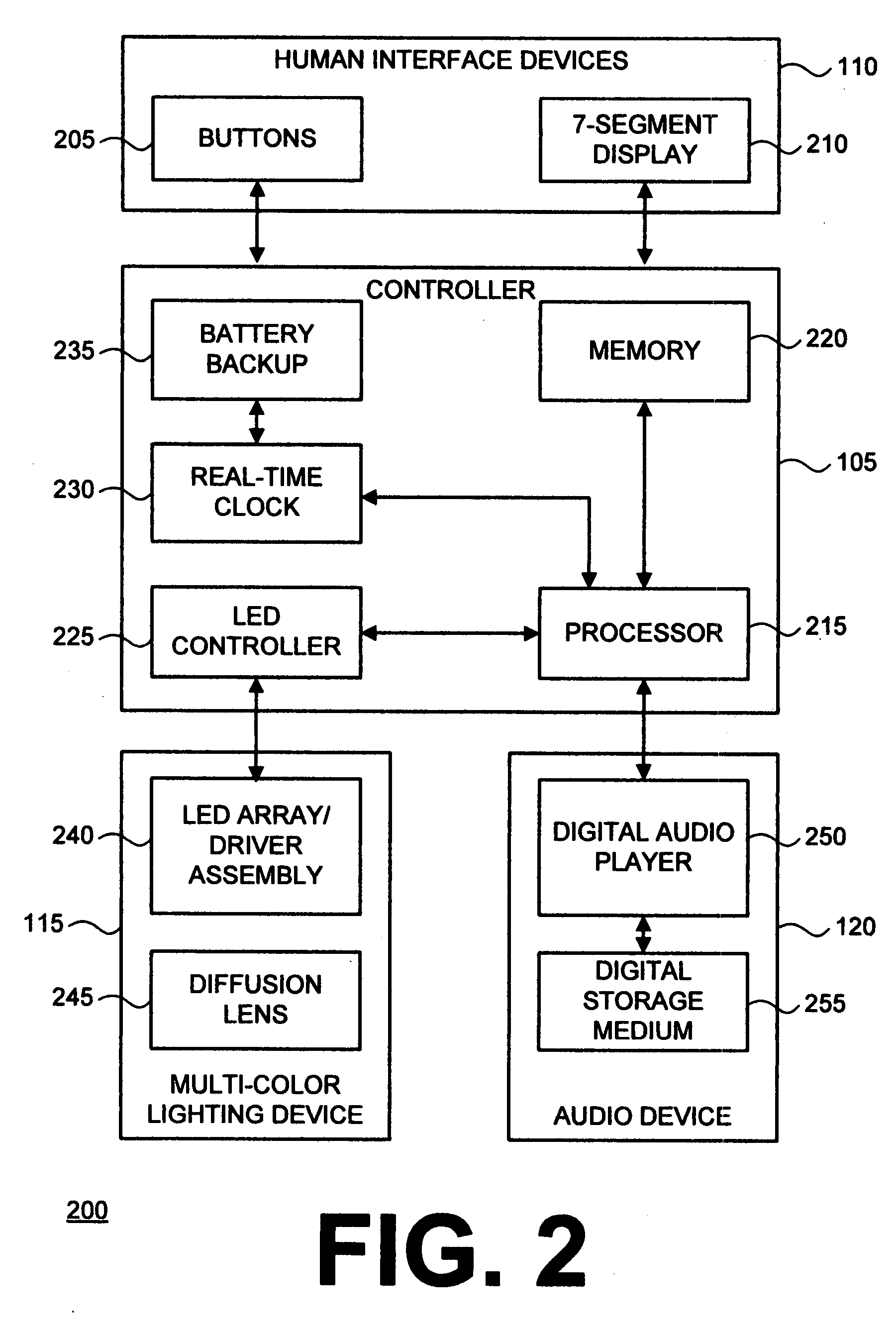
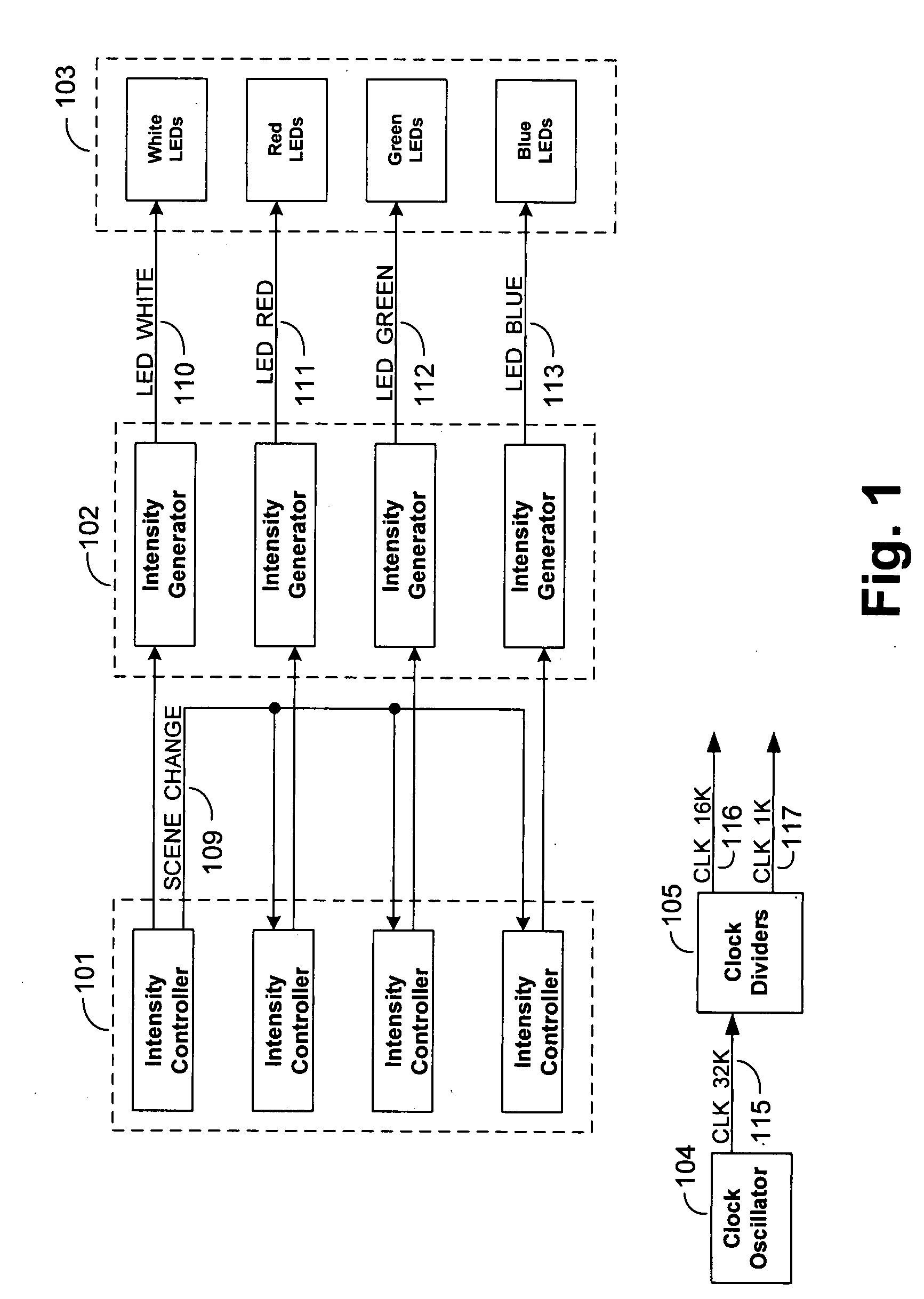
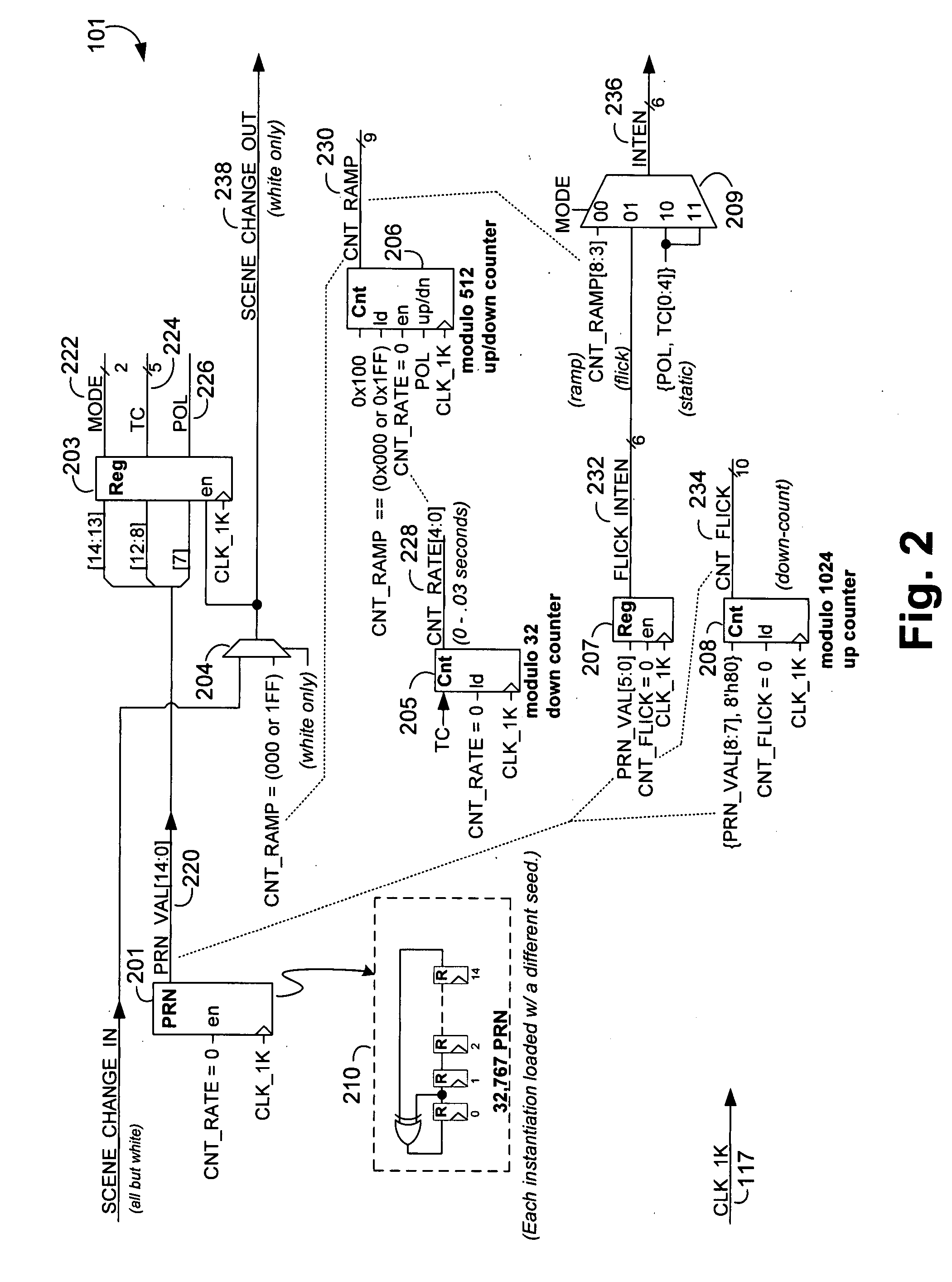
The invention relates generally to physical security, and more particularly, but without limitation to systems and methods that simulate television operation, and thus occupancy, for the purpose of deterring intrusion into a building. Embodiments of the invention control a multi-color lighting device, such as a Light Emitting Diode (LED) array, in a way that simulates light that is output from an operational TV screen. In embodiments of the invention, the multi-color lighting device may also simulate light that is output from a table lamp or other white light source. An audio device may also be used in combination with, or in the alternative to, the multi-color lighting device.
Owner:BODDEN JEFFREY
Dog bark door bell notification and personal protection system
InactiveUS20080309509A1Operation is disabledAlarms with occupancy stimulationSignalling system detailsDoorbellAudio power amplifier
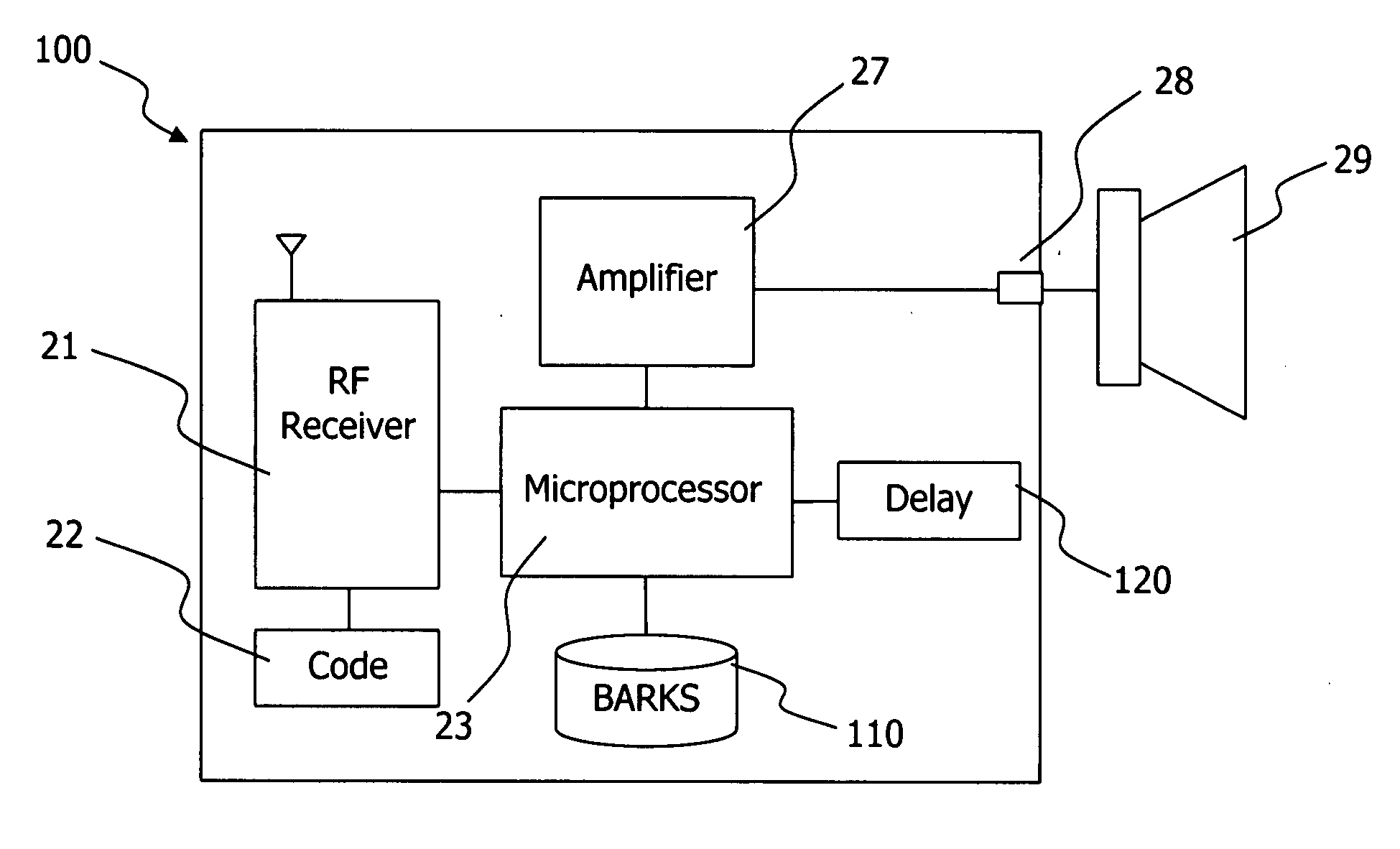
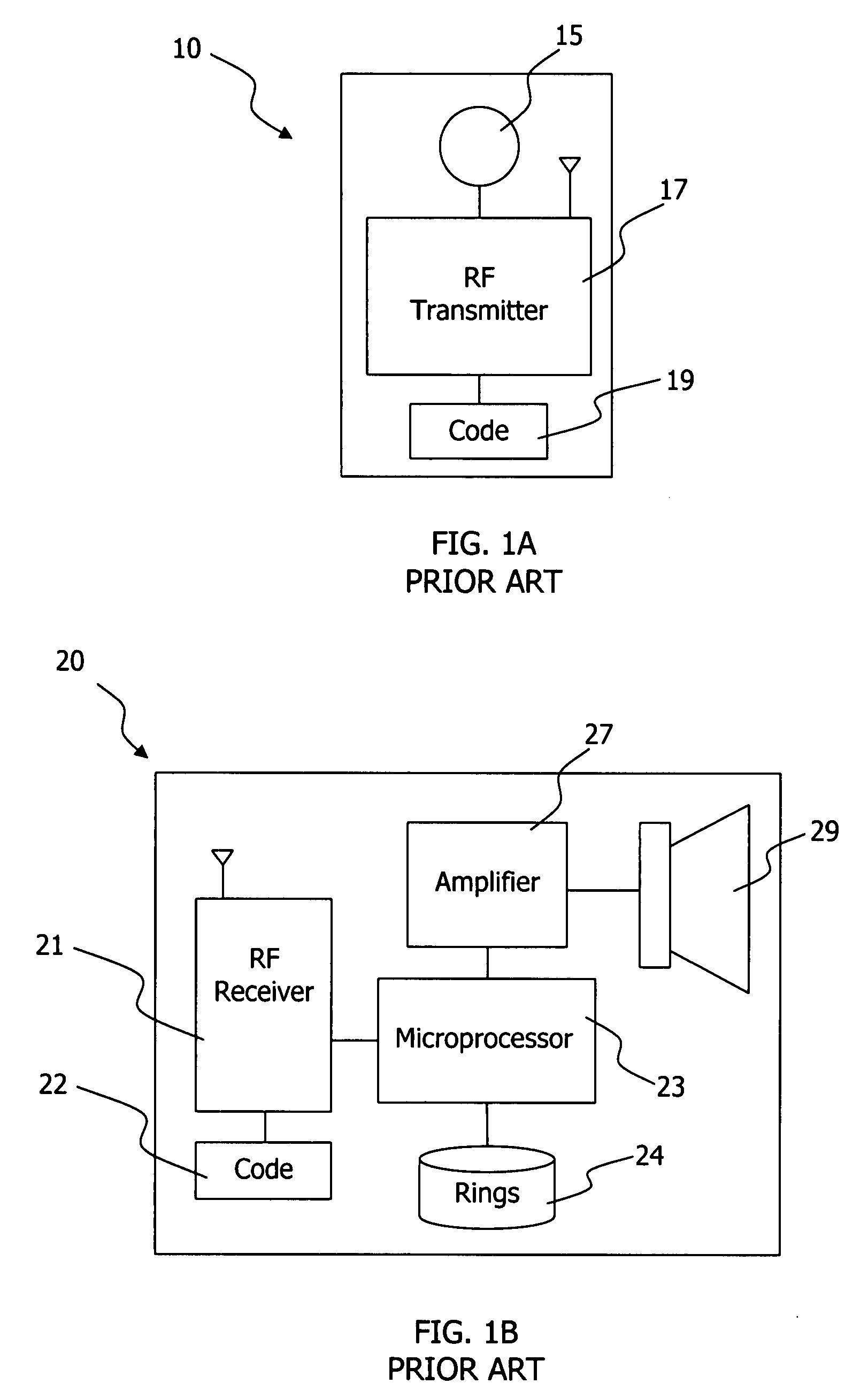
A door bell notification and personal protection system includes a warning notification module adapted to recognize at least one of a door bell notification from a door bell ringer or emergency transmission signal from a wireless transmitter and thereafter provide a recognition signal to a microprocessor. The microprocessor is adapted to retrieve dog barking sounds stored in a memory and provide the dog barking sounds to at least one of an amplifier or radio frequency transmitter after the microprocessor receives the recognition signal from the warning notification module. Dog barking sounds can be broadcasted using the wireless transmitter. A delay module can enable processing with a delay time after first receipt of the recognition signal. A random module can enable random retrieval of various dog barking sounds from memory for processing. A time out module can disable operation of the microprocessor at a set time after recognition signal receipt.
Owner:ORTIZ MELISENDRO T +1
Device for Simulating Human Activity in an Unoccupied Dwelling
ActiveUS20060186740A1Rotary current collectorBoards/switchyards circuit arrangementsElectricityBiological activation
The present invention is a thermally activated electrical switch for use in simulating human activity. The invention is features dual heat sources enclosed in a thermally isolated chamber within the invention. Since the activation of the switch is dependent upon the ambient temperature of the environment, it opens and closes at sufficiently random intervals to simulate human activity. This embodiment includes the use of a photoelectric sensor to further vary timing of the switch actuation.
Owner:THE MILETTI GRP
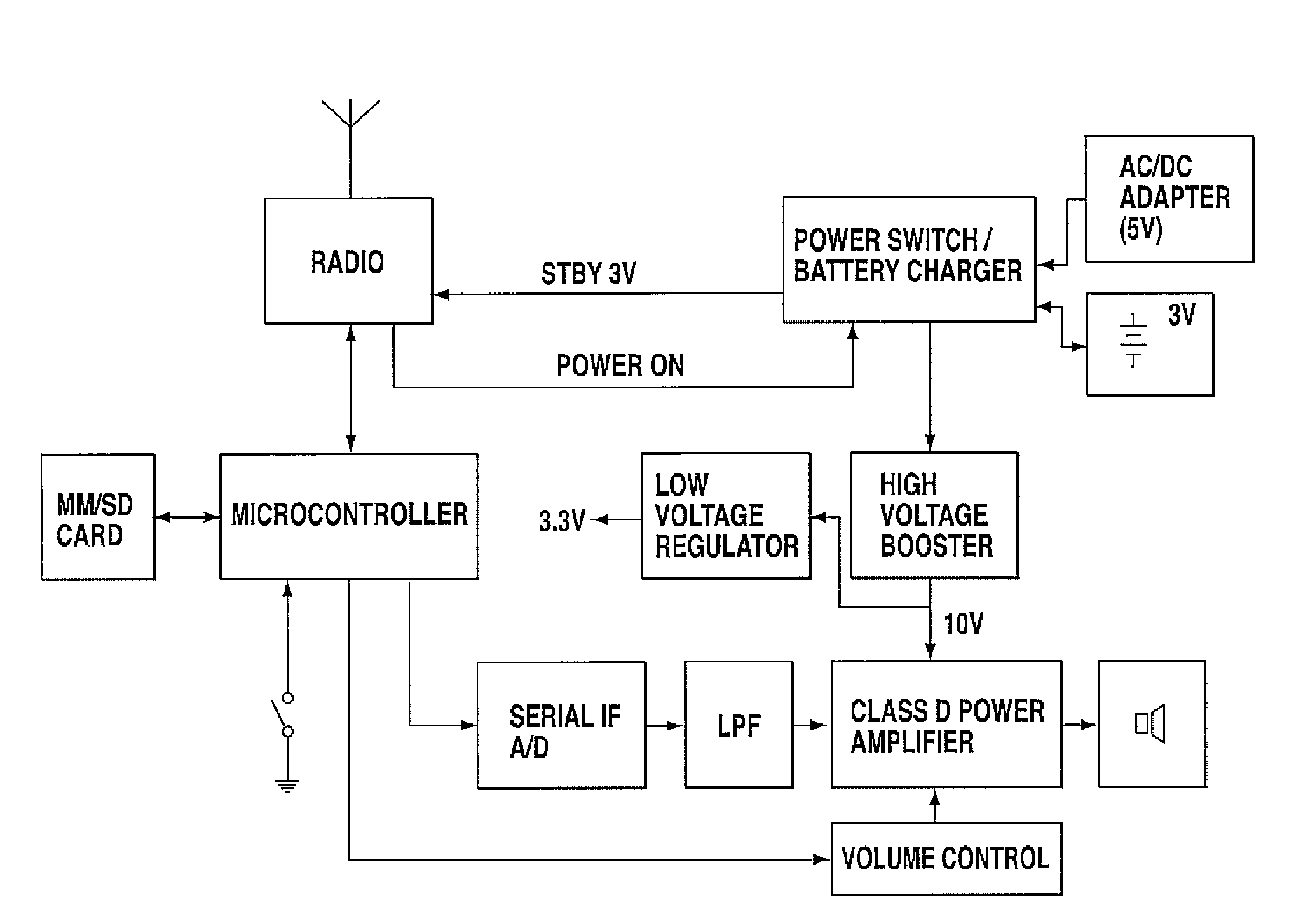
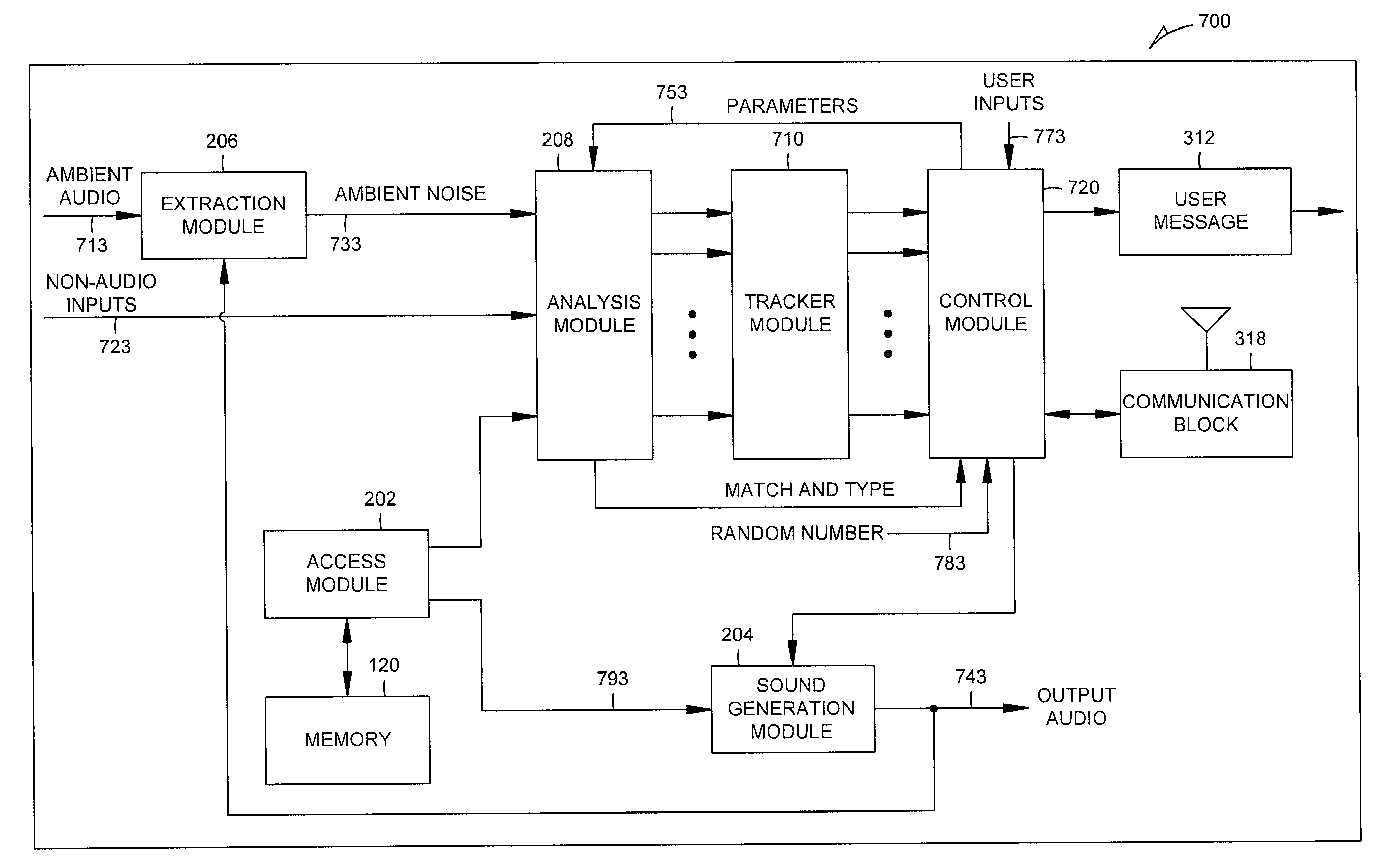
Ambient audio transformation modes
A method and device for transforming ambient audio are provided. Example embodiments may include monitoring ambient audio proximate to a sound processing device located in an environment. The device may receive a selection from a user interface. The selection may comprise one of a number of available first selections, each available first selection identifying one of multiple transformation modes. The device may access memory to obtain transformation audio and process the transformation audio, based on the ambient audio and the selection. The device may also use the transformation audio to provide modified output audio for propagation into the environment.
Owner:ADAPTIVE SOUND TECH
Security television simulator
ActiveUS20080186256A1Energy efficiencyEasy to useStatic indicating devicesAlarms with occupancy stimulationRandom combinationCable television
Method and apparatus for simulating an operating television for the purpose of deterring potential intruders by providing the appearance that one or more occupants are at home. Realistic simulation of a television is accomplished via perceived random combinations, amplitudes, colors, and durations of television program scene modes, these scene modes comprised of fades, swells, flicks, and static periods. Efficient, reliable, and inexpensive super-bright LEDs serve as light sources.
Owner:HYDREON CORP
Vehicle safety apparatus
InactiveUS7505843B2Prevent theftEnsure safetyPortable emergency signal deviceDigital data processing detailsVehicle safety
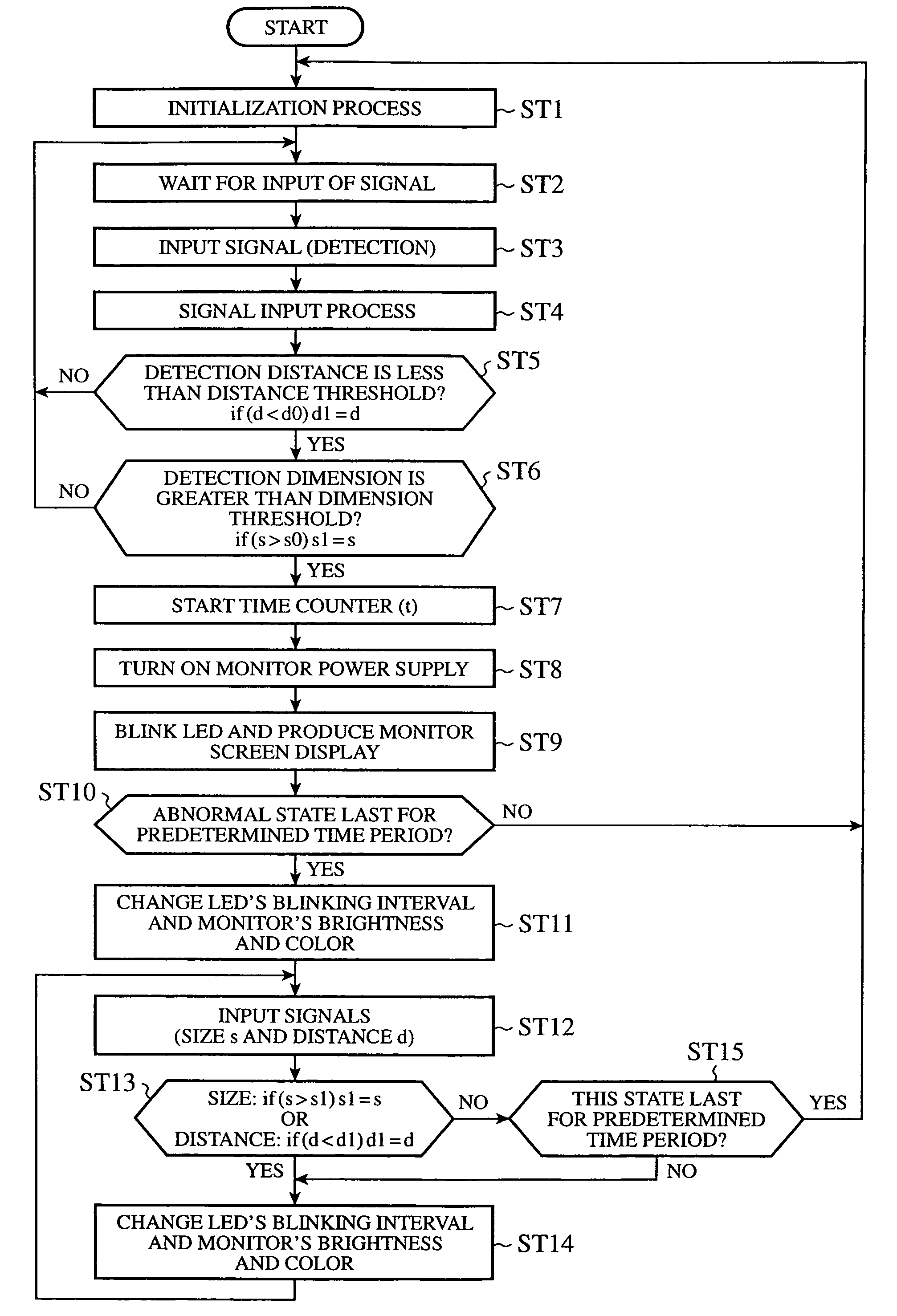
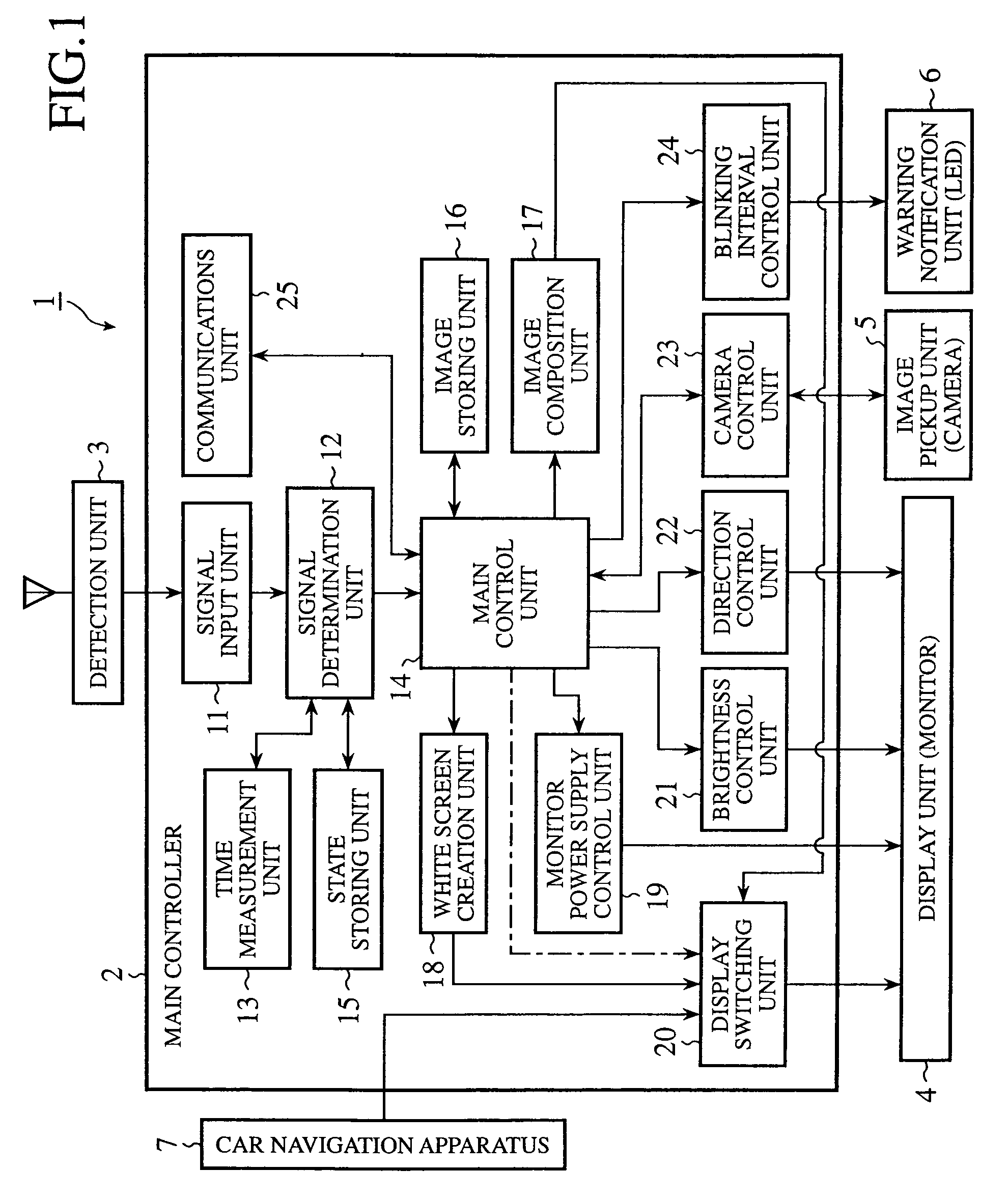
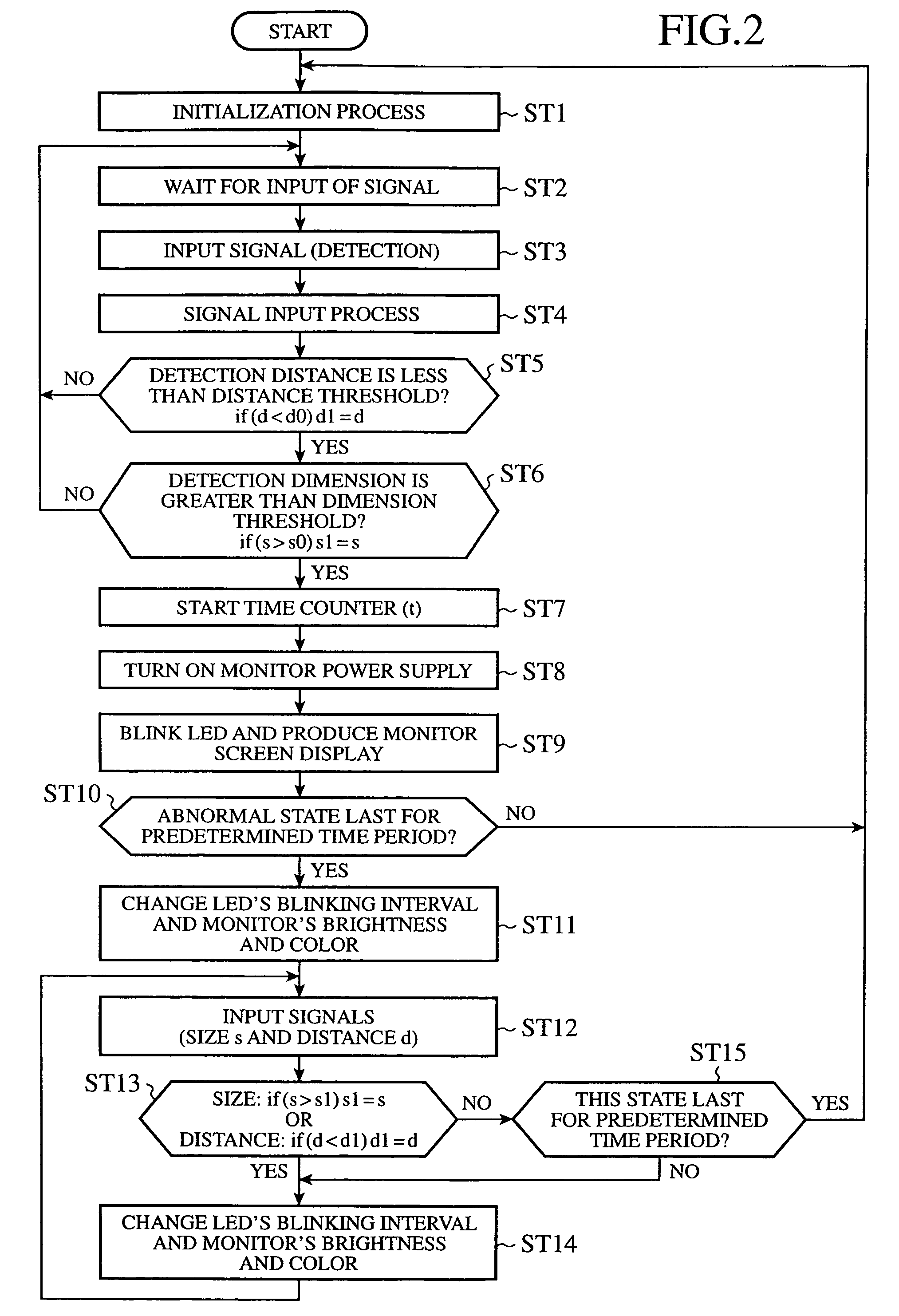
When a detection unit (3) detects an approach of an object to a vehicle in which a vehicle safety apparatus is mounted, a main controller (2) determines whether a positional relationship between the vehicle and the detected object reaches a predetermined positional one. The main controller (2) can start a warning unit according to a determination result obtained thereby, and can issue a warning before the vehicle gets damaged.
Owner:MITSUBISHI ELECTRIC CORP
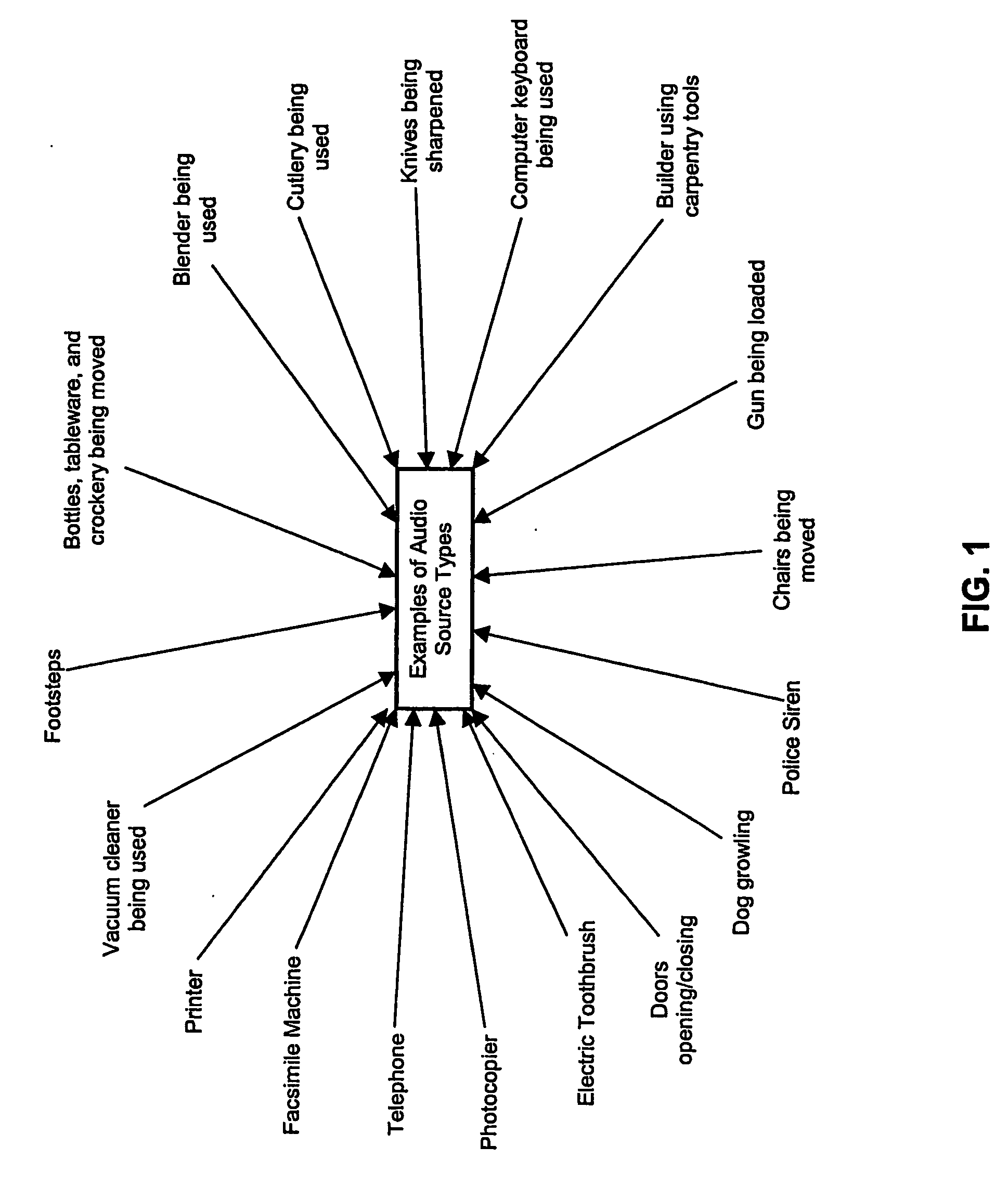
Sound effects security application for smartphone
InactiveUS20150080057A1Alarms using portable personal devicesAlarms with occupancy stimulationDisplay deviceVisual perception
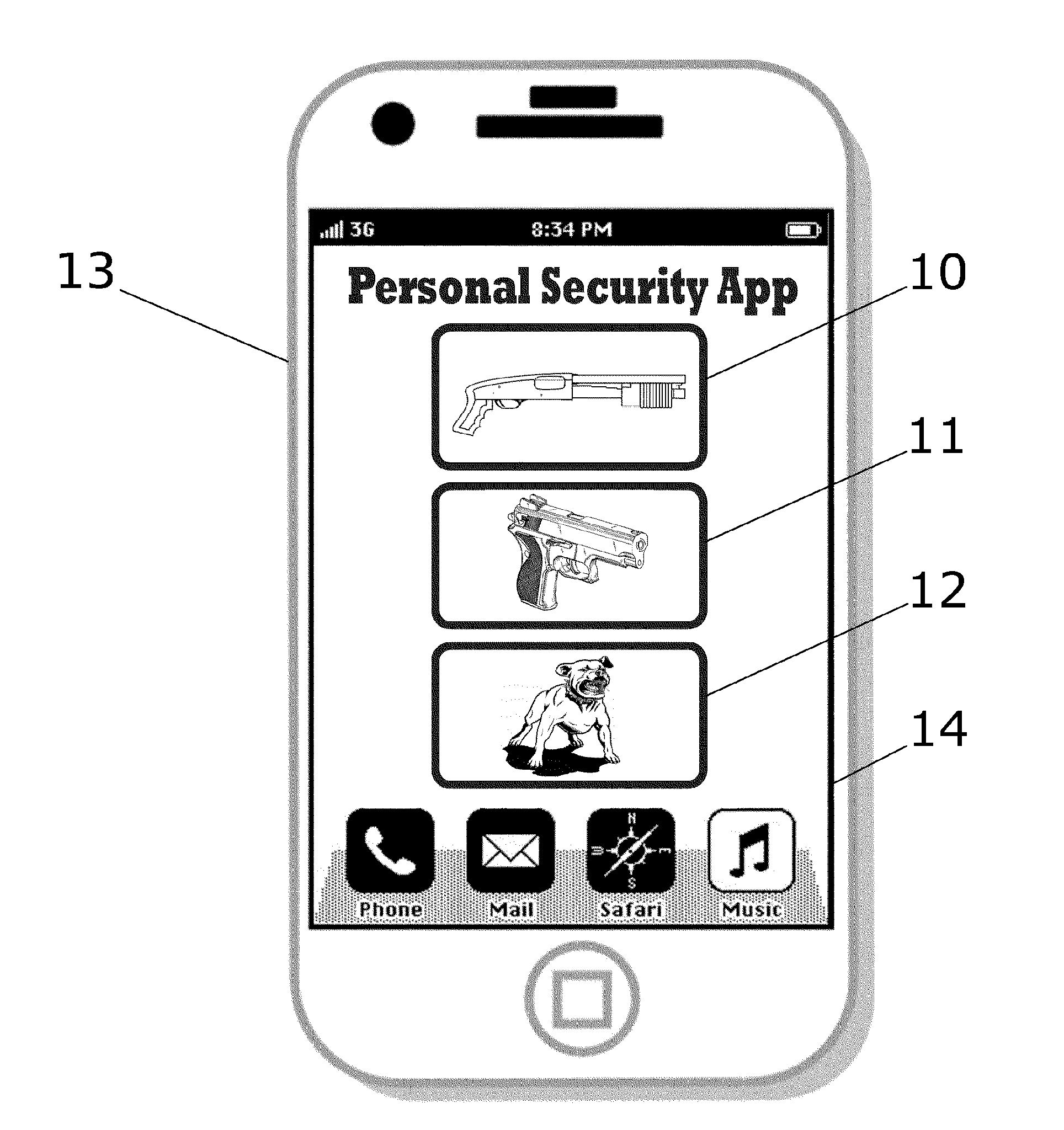
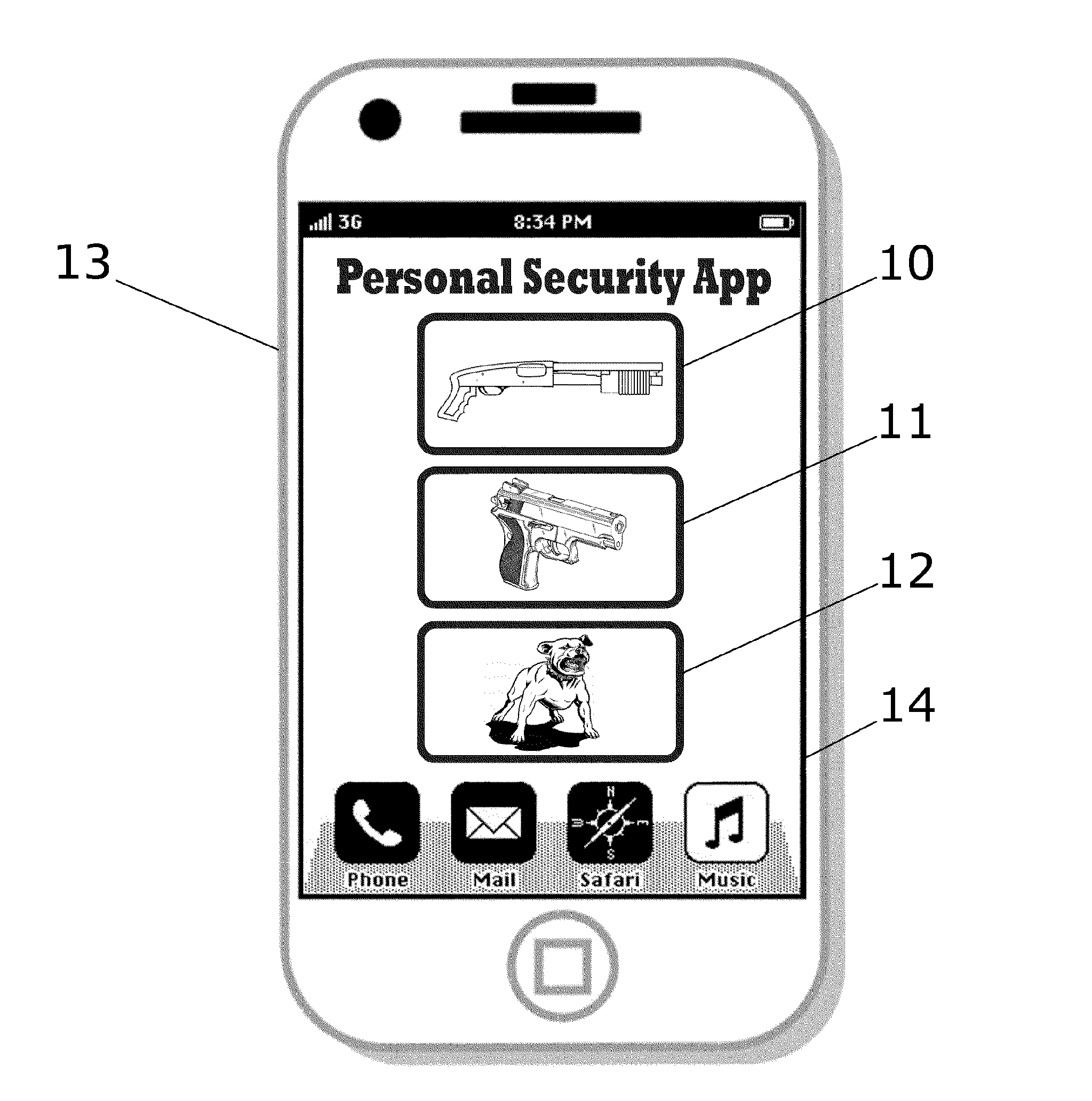
A sound effects security application for a smartphone provides icons on the visual display that are linked to sound effect audio files simulating a handgun being loaded, a shotgun jacking a fresh shell into the chamber, a barking dog, a piercing alarm and other similarly alarming sounds. The intended result of the sound is to cause intruders to hesitate before continuing to enter the premises.
Owner:ADAMS REBECCA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com