Patents
Literature
41results about "Postage metering system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
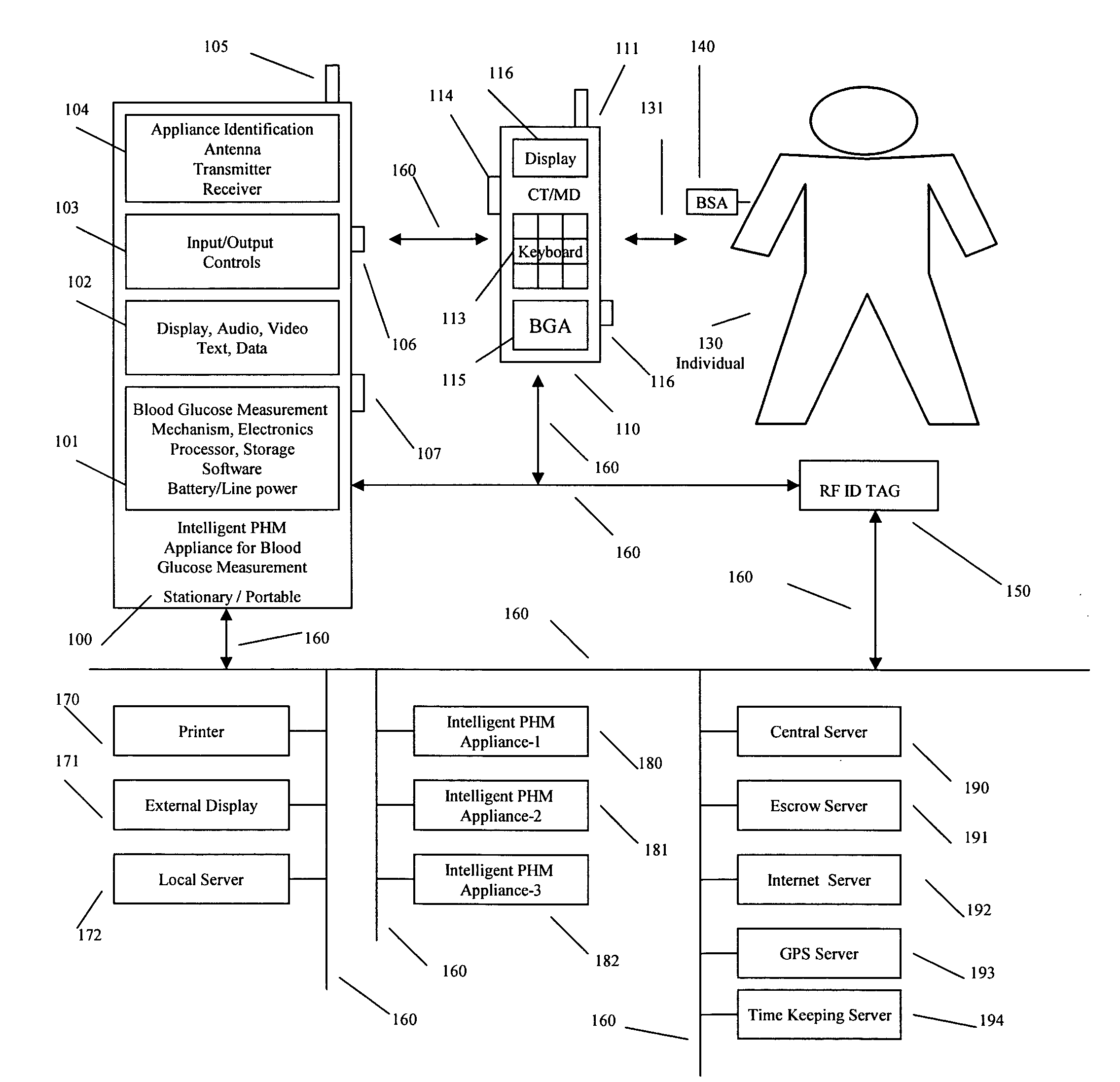
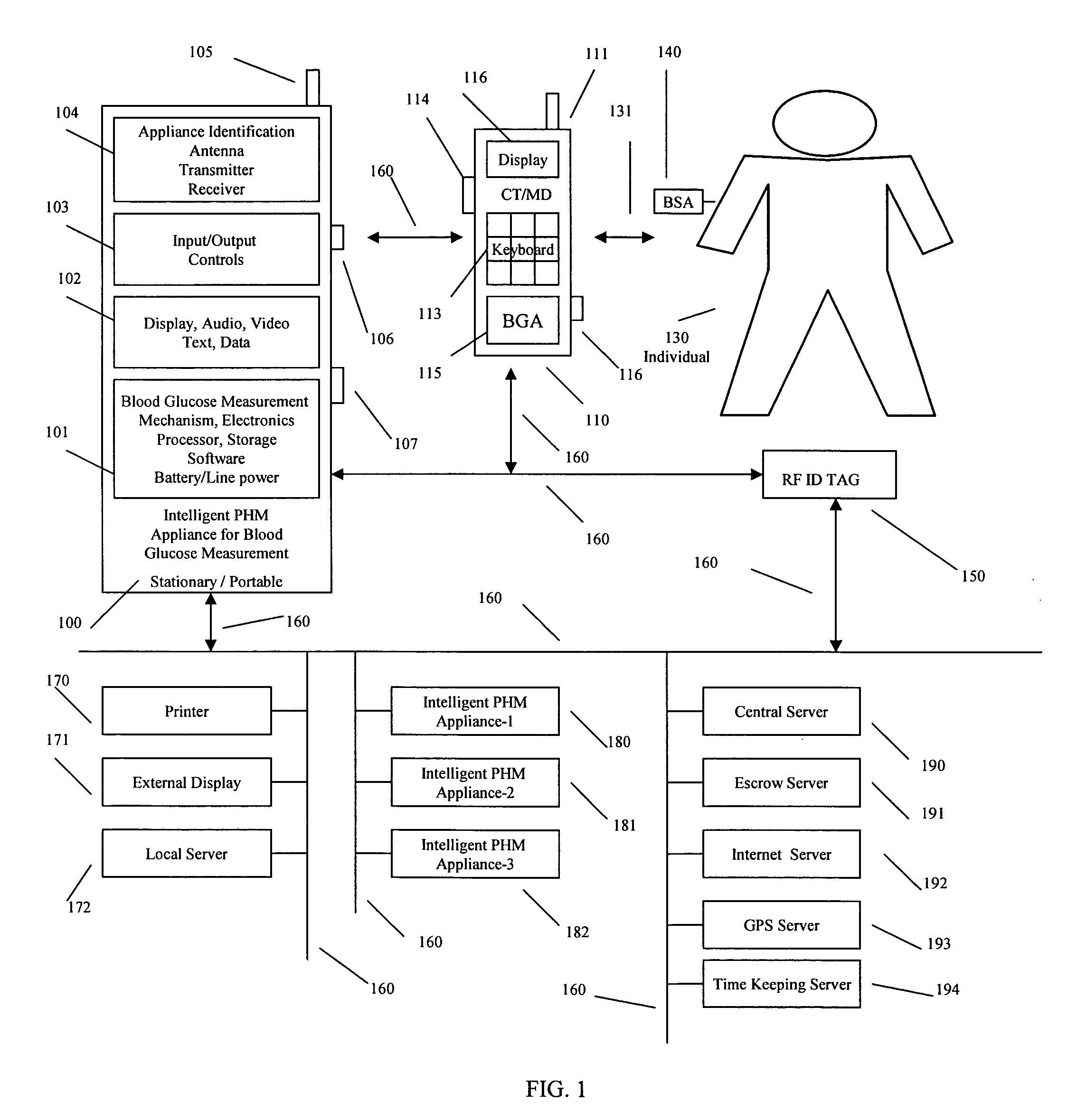
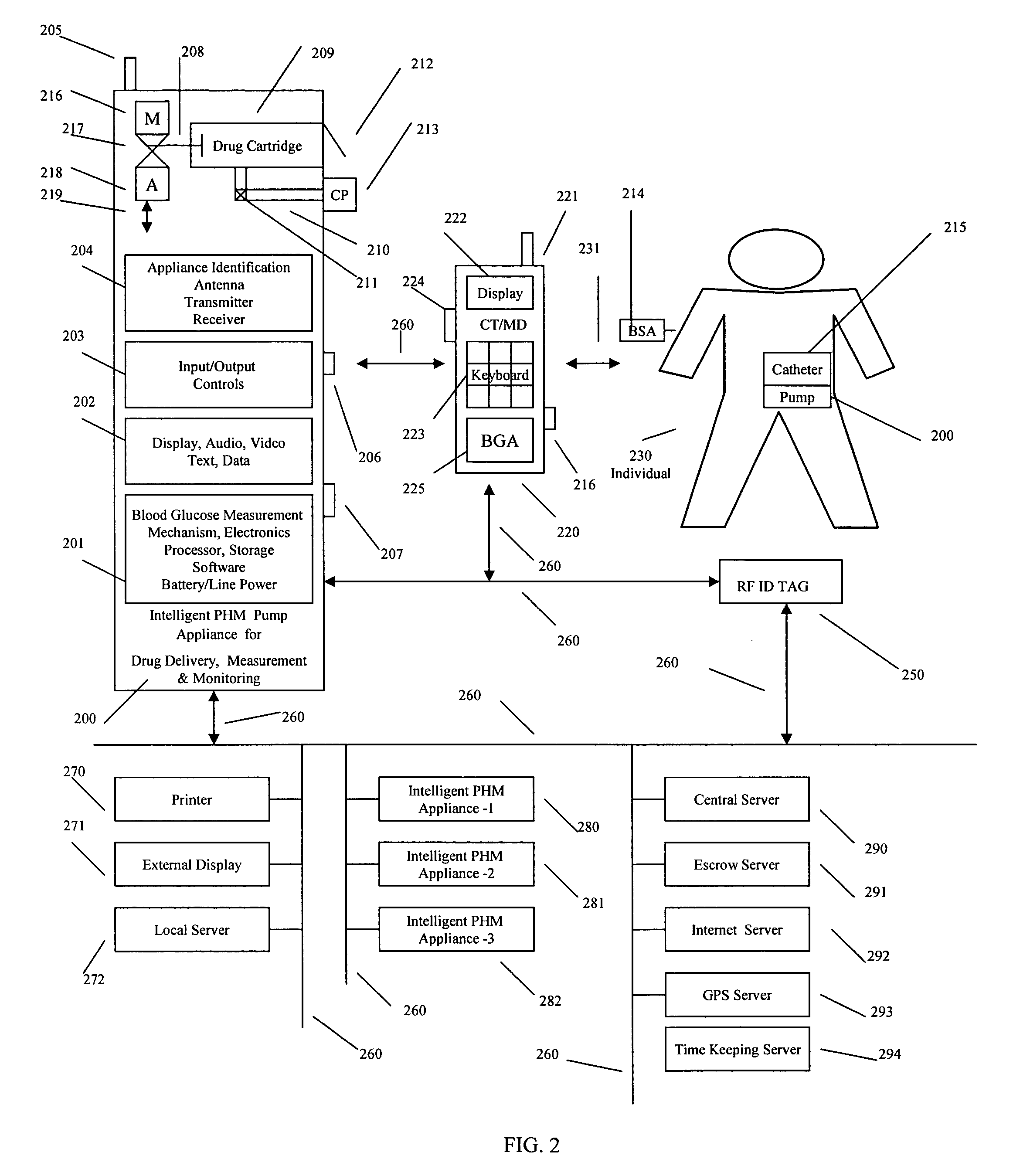
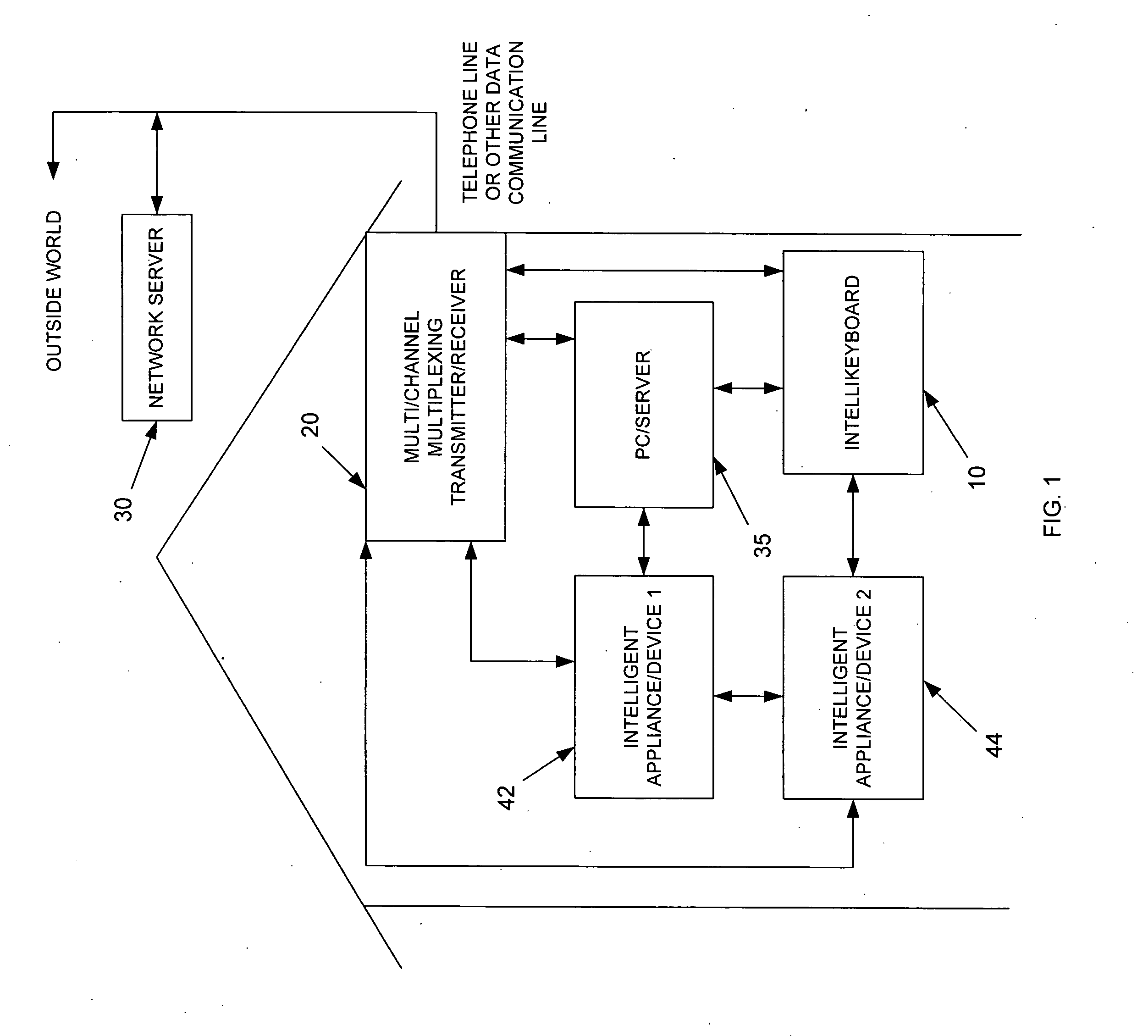
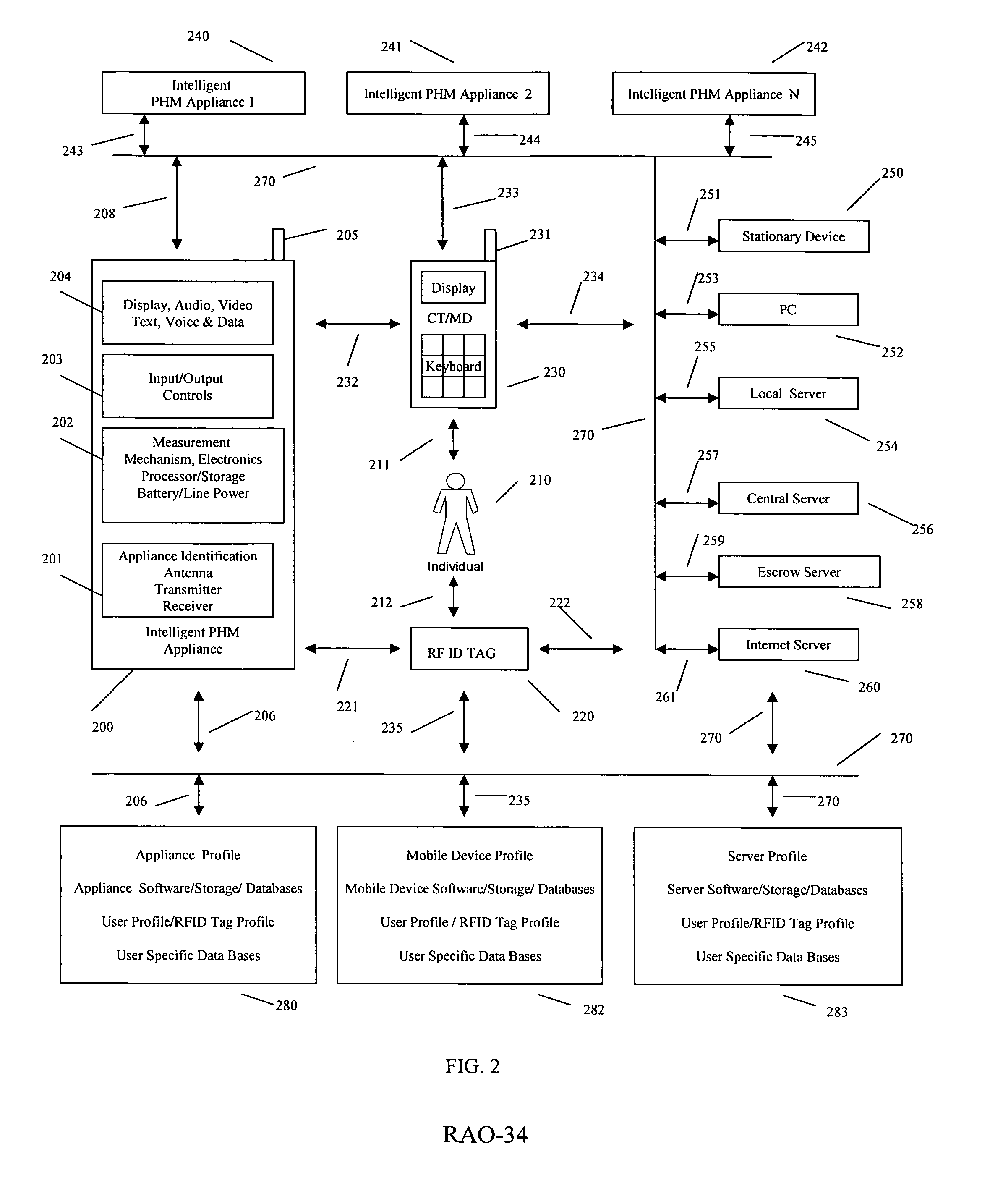
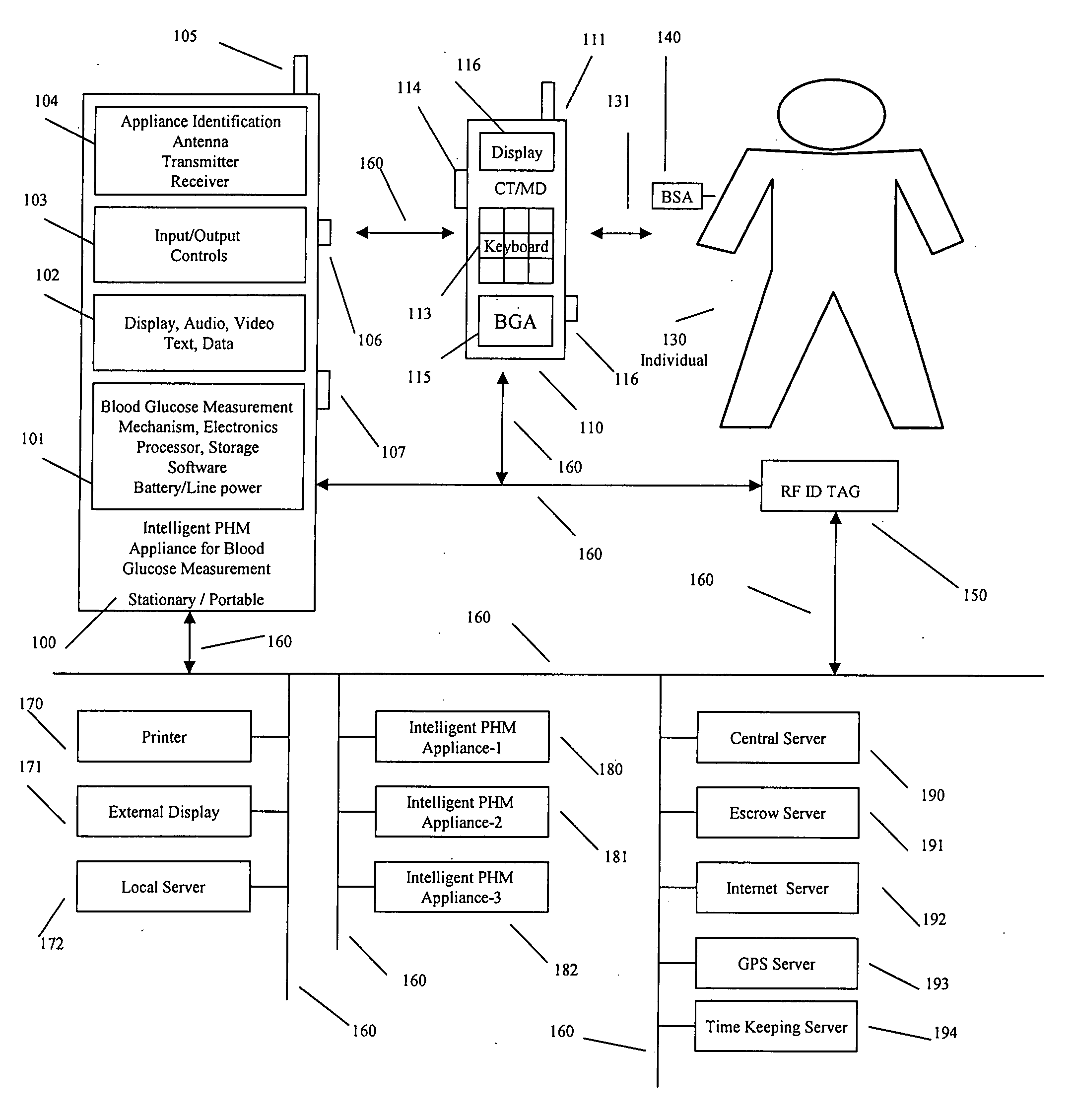
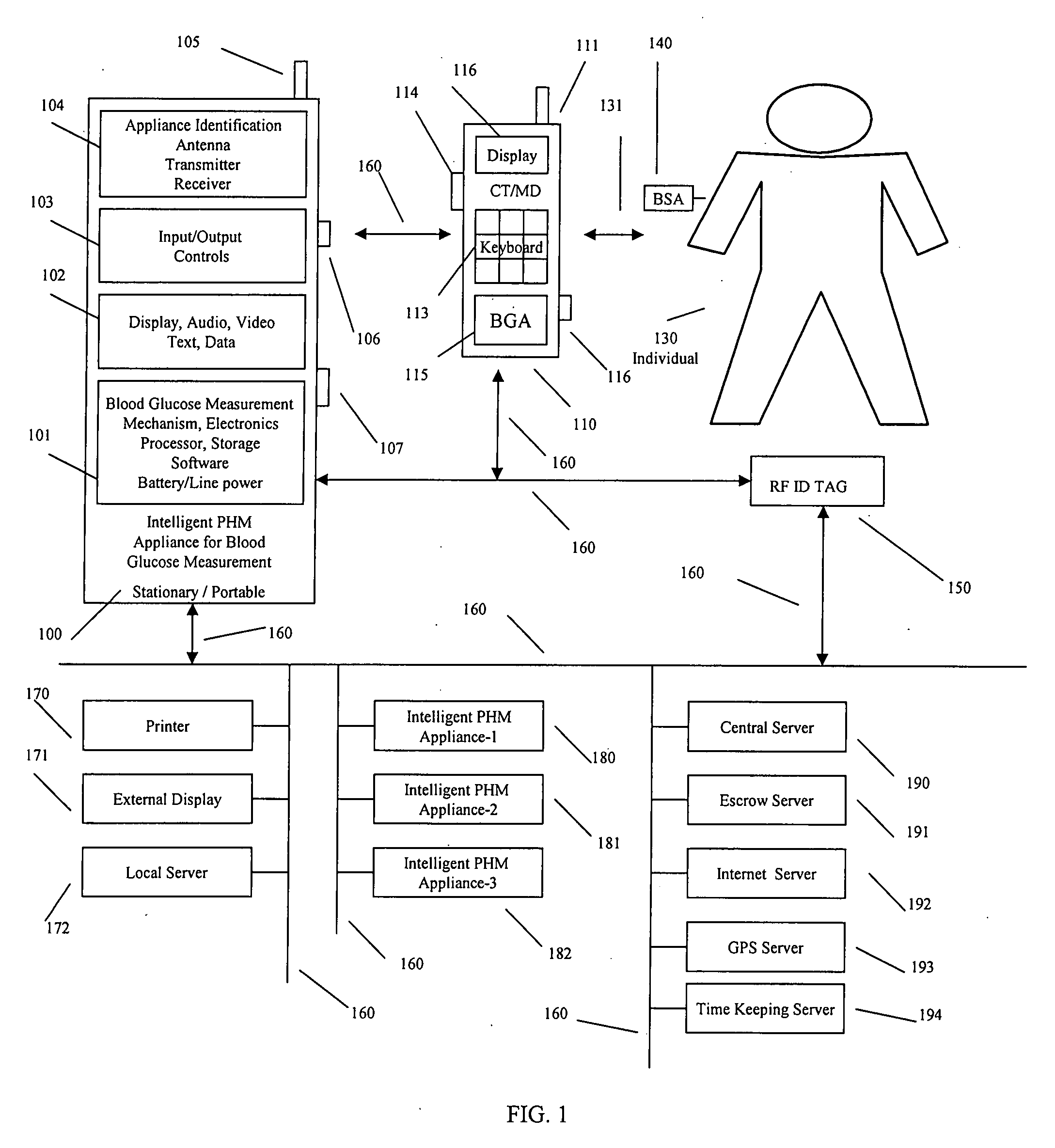
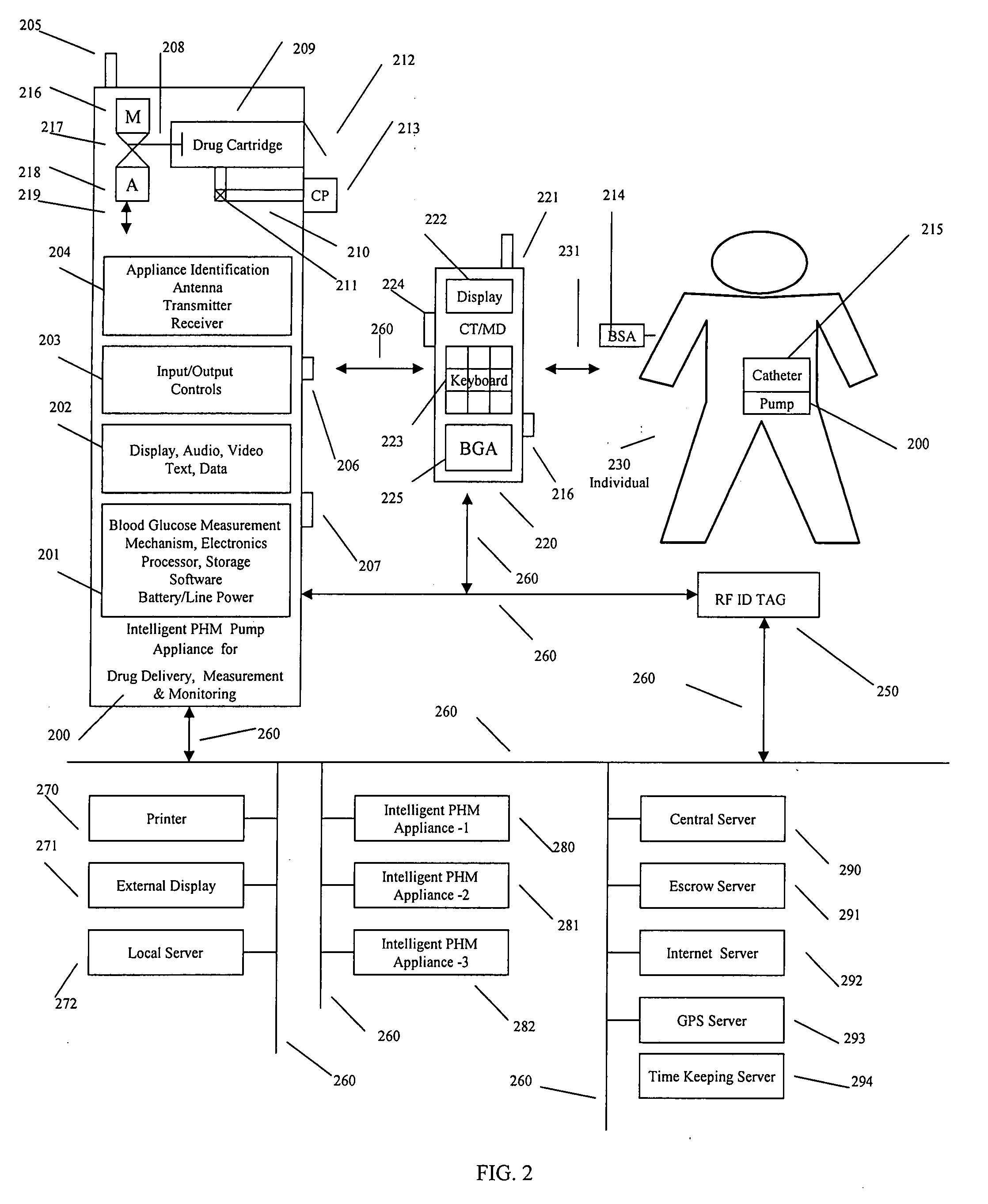
Intelligent personal health management appliances for the measurement and monitoring of health factors and controlled delivery of drugs
InactiveUS20080139907A1Precise positioningPointing accuratelyPhysical therapies and activitiesElectrotherapyDiseaseDiabetes mellitus
A system, method and apparatus for real time measurement and monitoring of various personal health parameters including controlled delivery of drugs / medications by intelligent pump appliances, intelligent inhalation appliances and intelligent skin patch appliances used in a standalone manner or in a wired or wireless networked configuration, in conjunction with various peripheral devices, other intelligent appliances, servers, RF ID Tags and stationary / mobile devices. The intelligent appliances relate to the measurement, monitoring and delivery of insulin / other drugs for the treatment of diabetes and other diseases. The method also additionally includes the application of intelligent appliances for pain management including visualization of organs and body locations exhibiting pain.
Owner:IP HLDG LLC
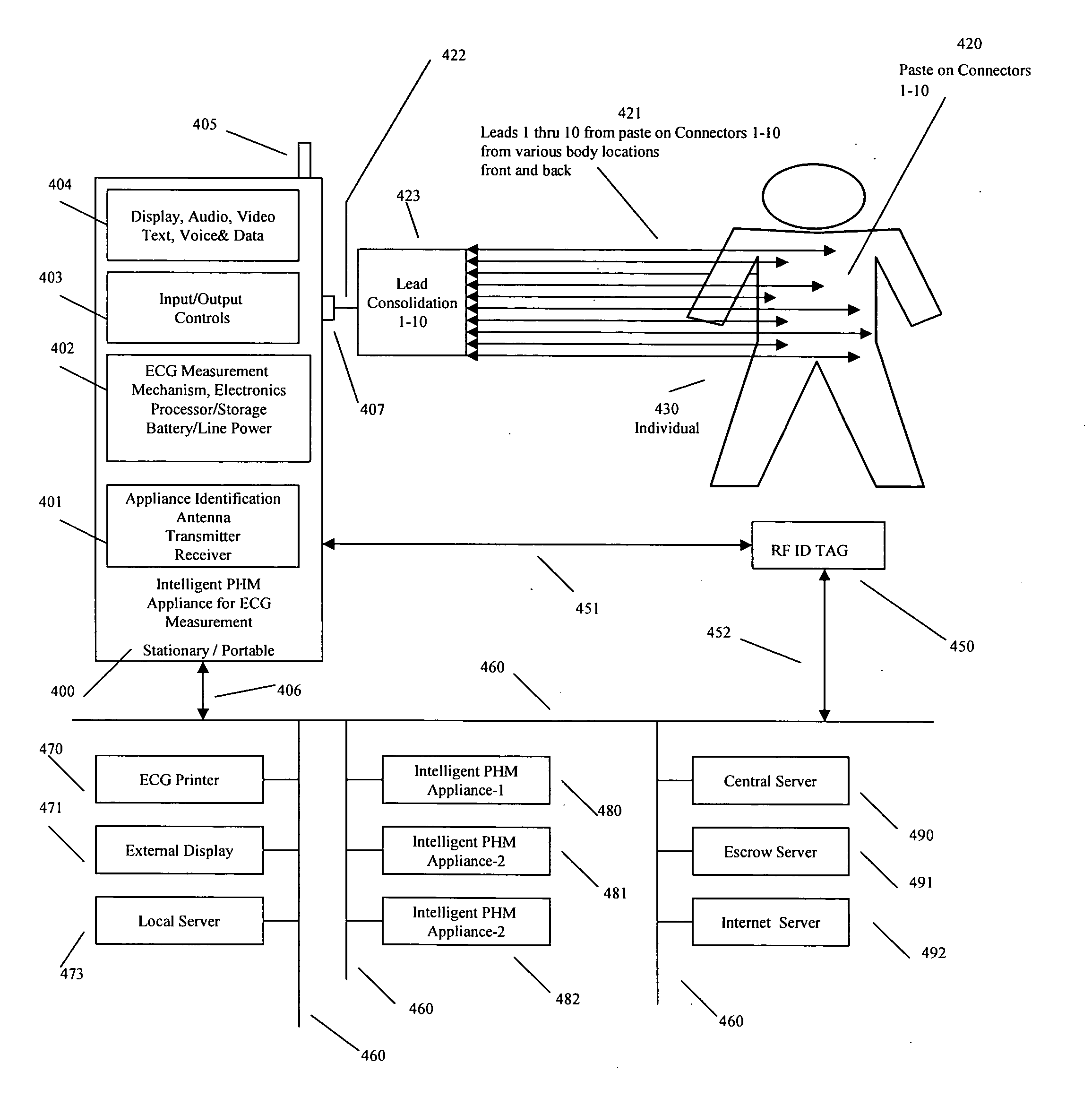
Electronic skin patch for real time monitoring of cardiac activity and personal health management
InactiveUS20120191147A1Physical therapies and activitiesDrug and medicationsCardiac activityCellular telephone
A novel wearable electronic skin patch sensor device configured for the real time acquisition, processing and communicating of cardiac activity and other types of biological information within a wired or wireless network is disclosed. A system level scheme for networking the sensor device with client devices that include intelligent personal health management appliances, cellular telephones, PDAs, portable computers, personal computers, RFID Tags and servers is disclosed. The sensor device and the system enable distributed processing, archival and correlation of the biological information with biometrics, gastronomic information, user profiles and health factors that include height, weight, blood pressure and physical activity facilitating real time personal health management at any time and any place.
Owner:IP HLDG LLC
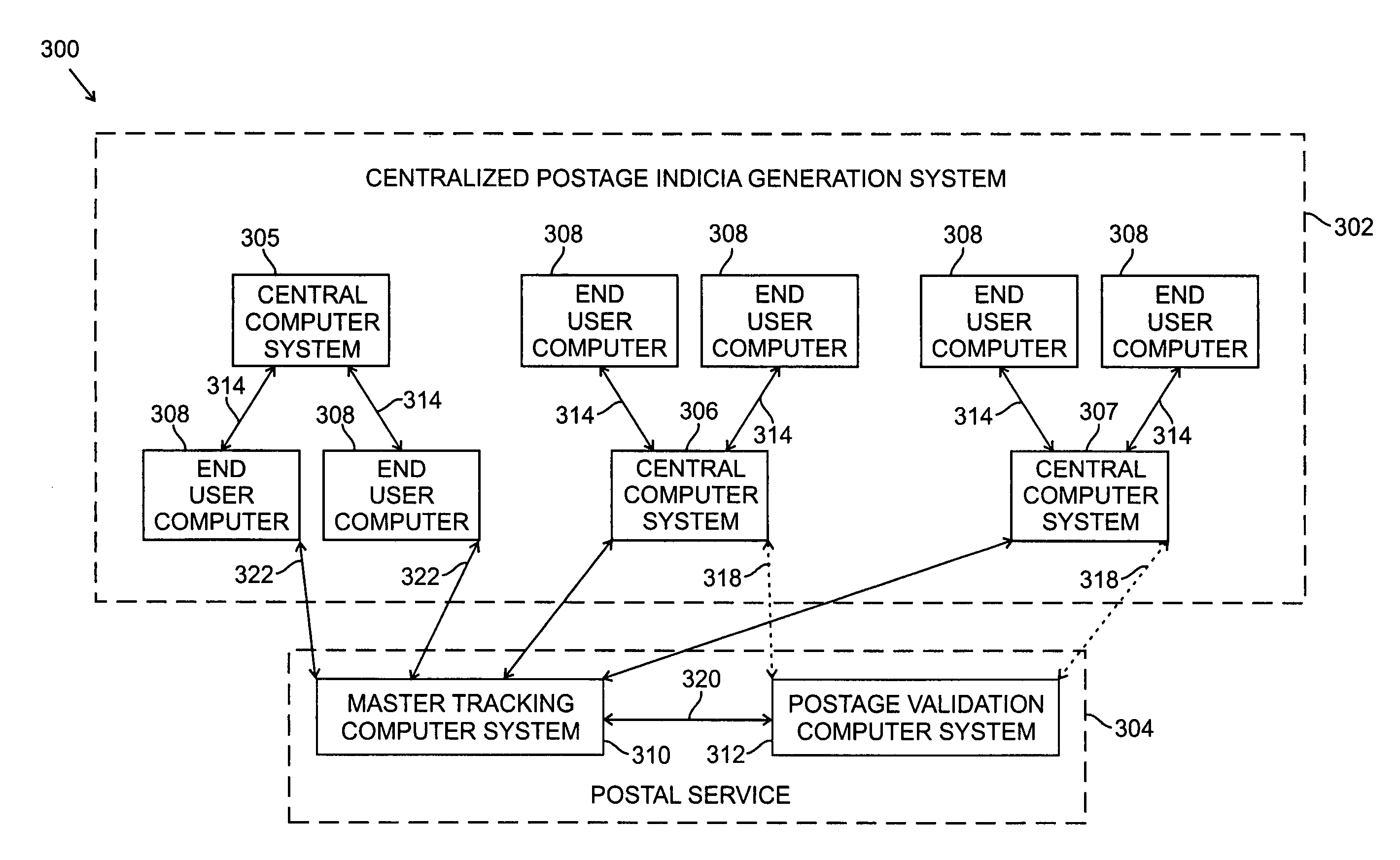
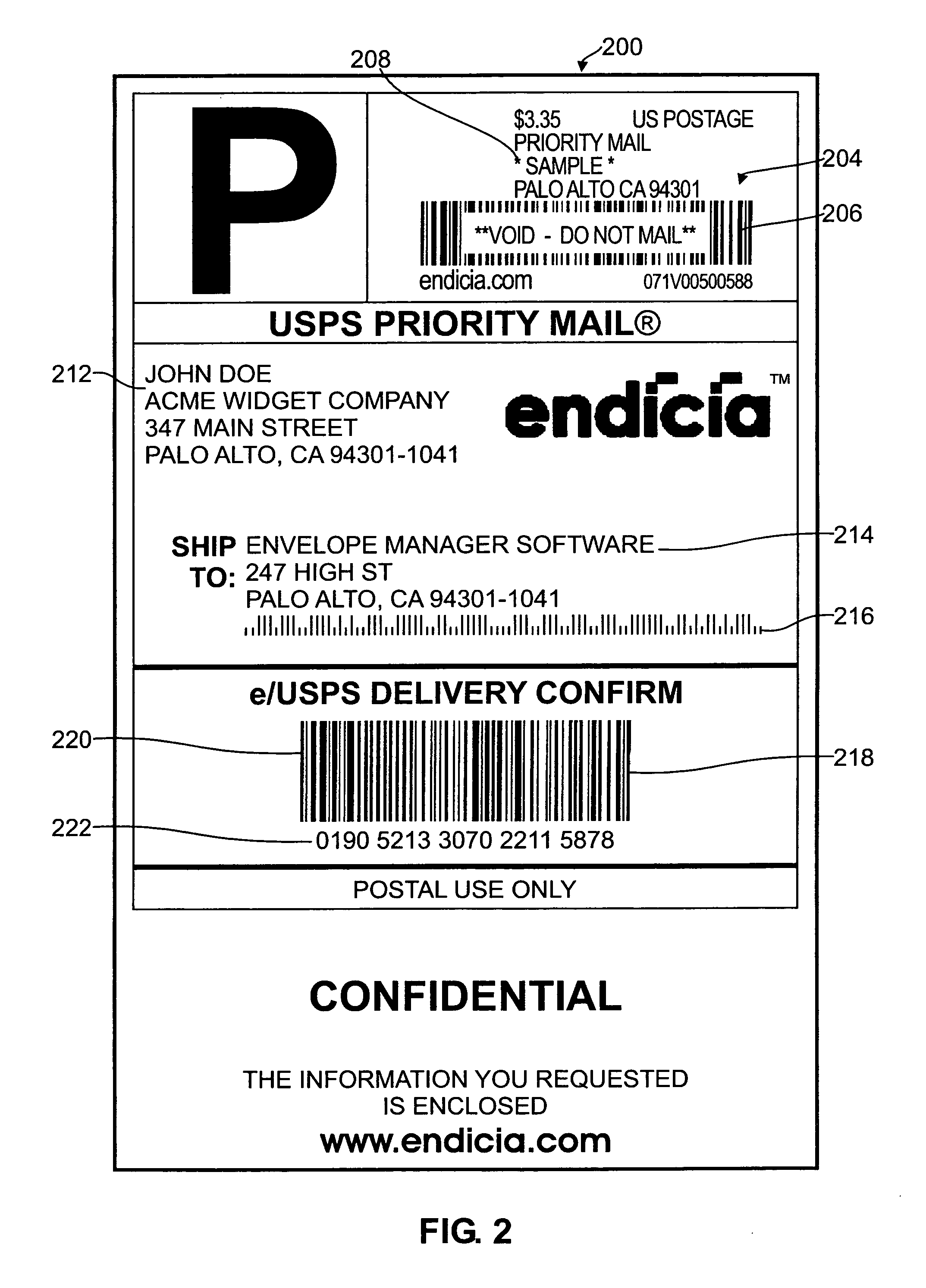
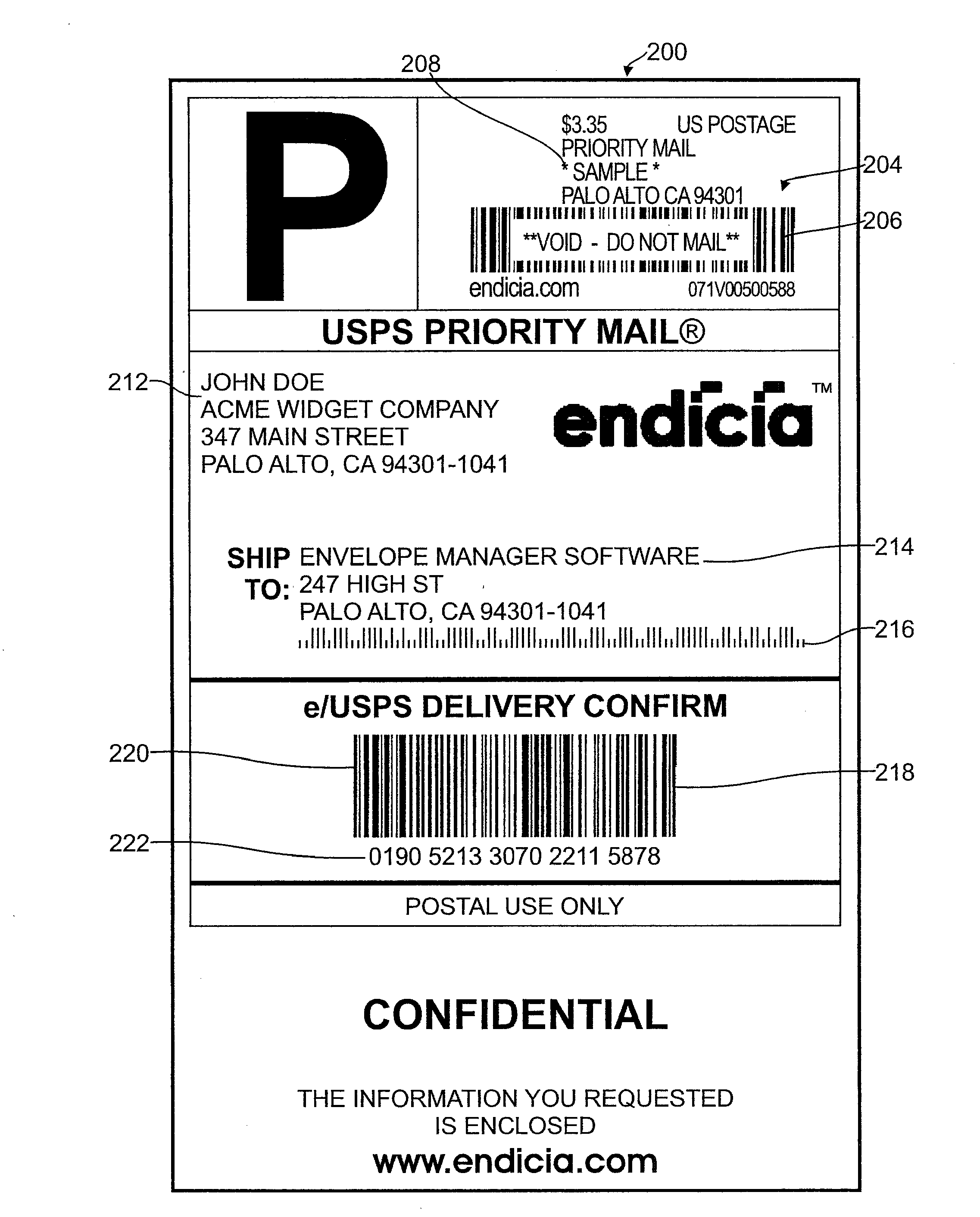
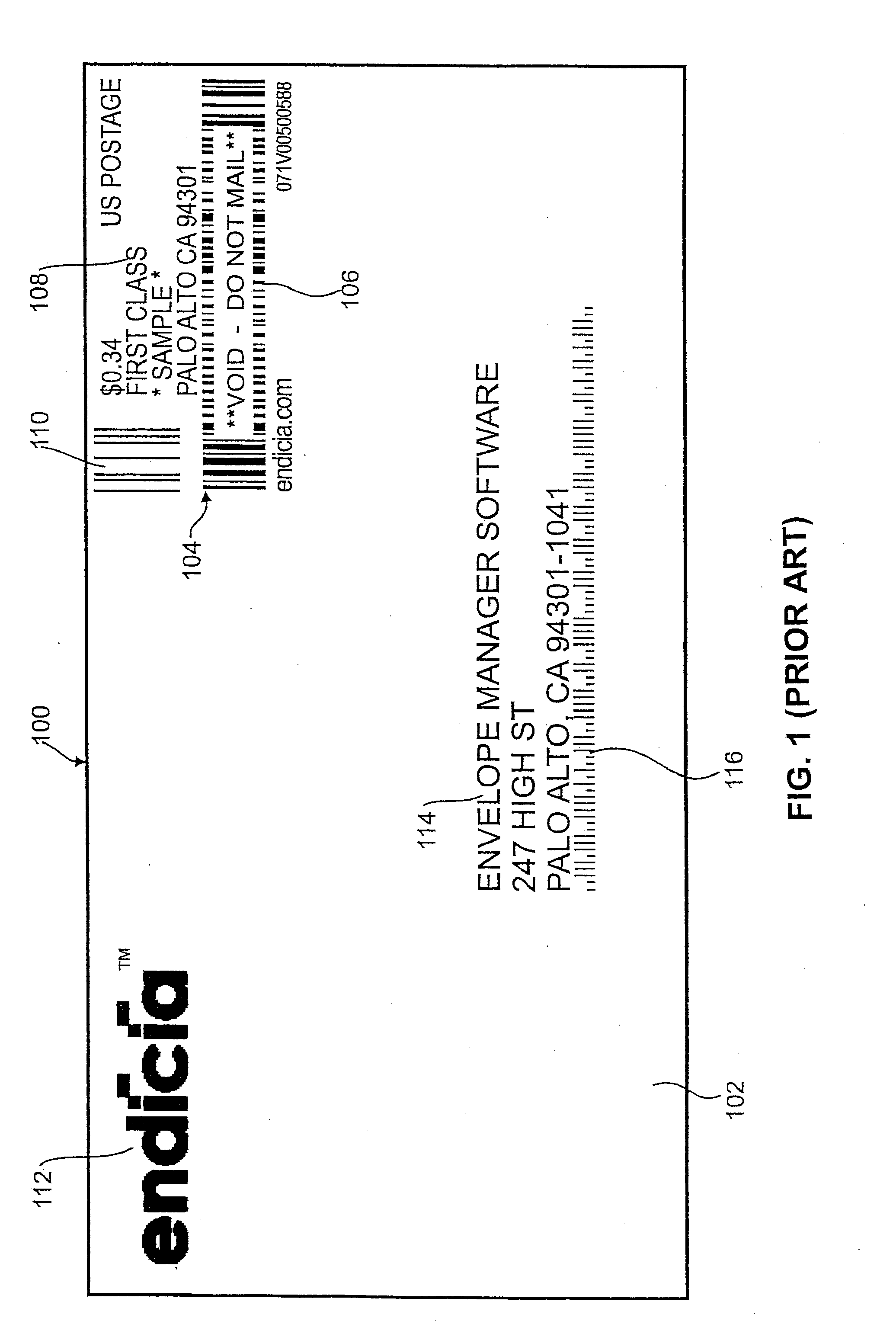
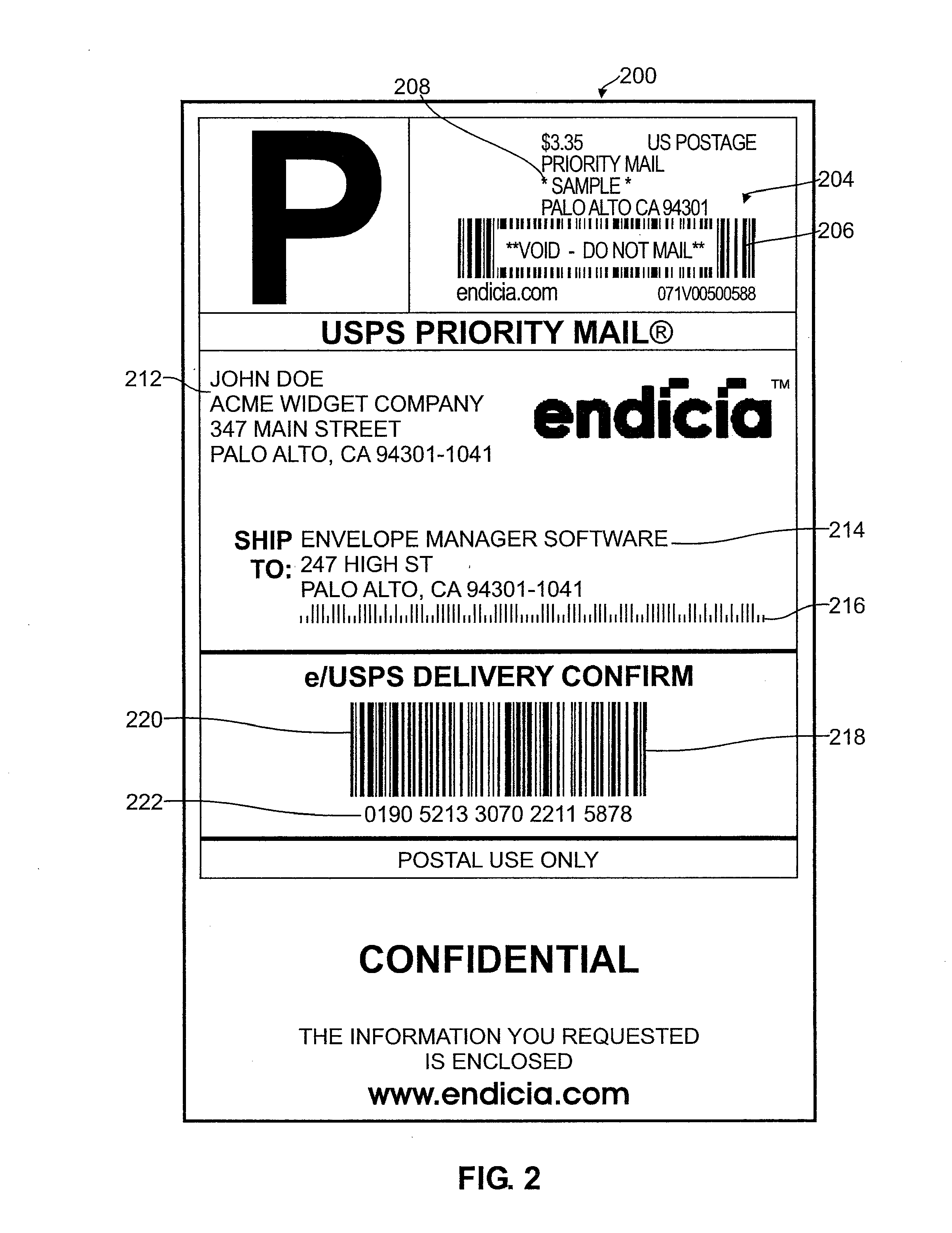
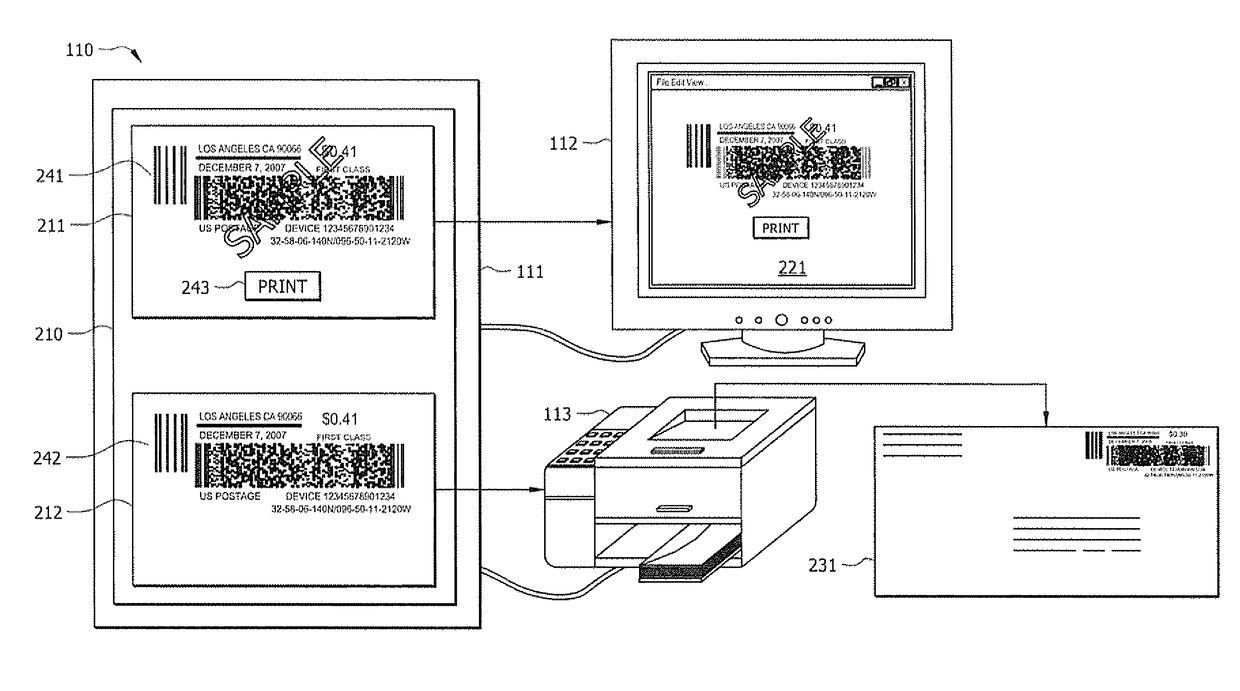
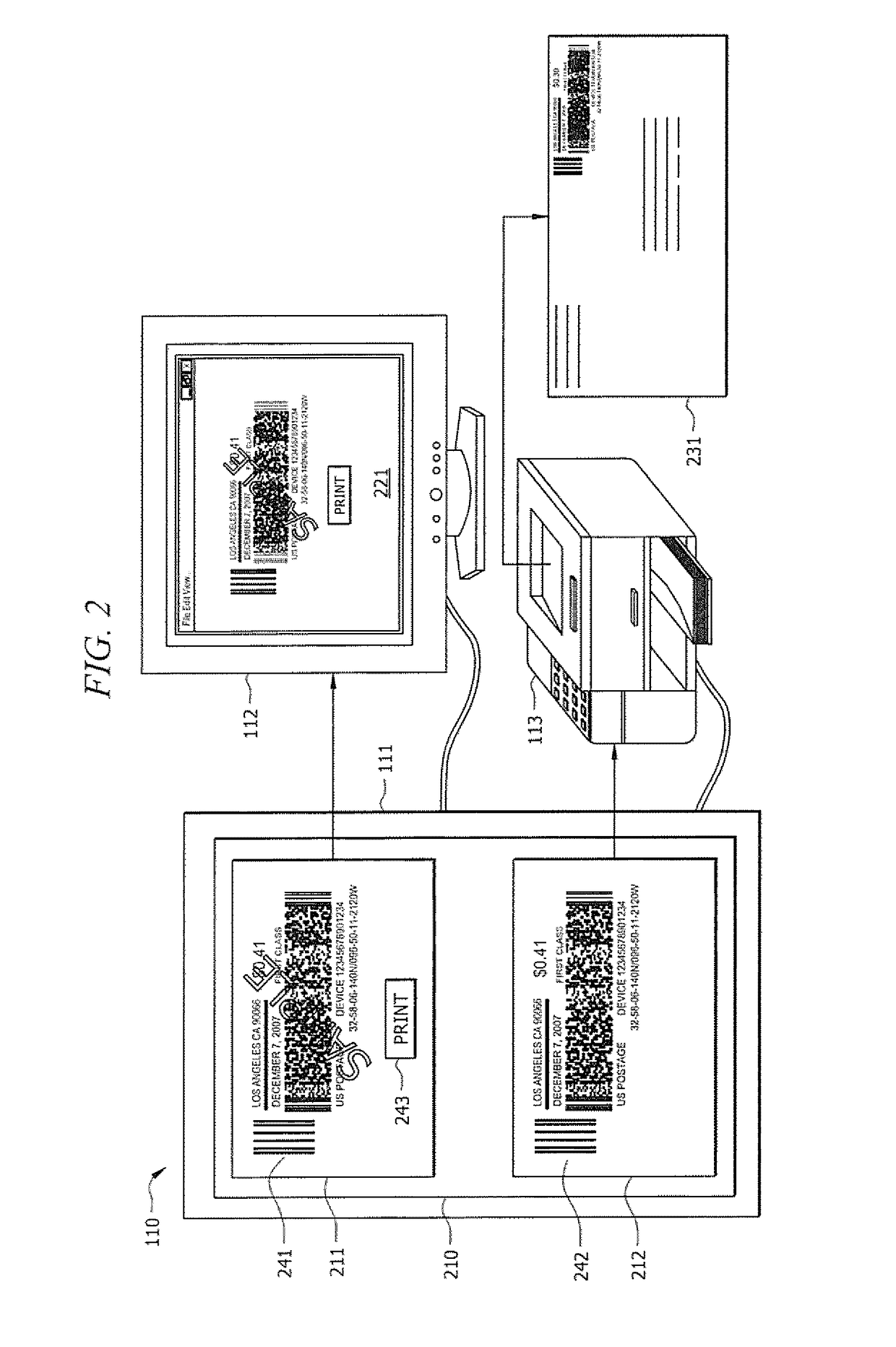
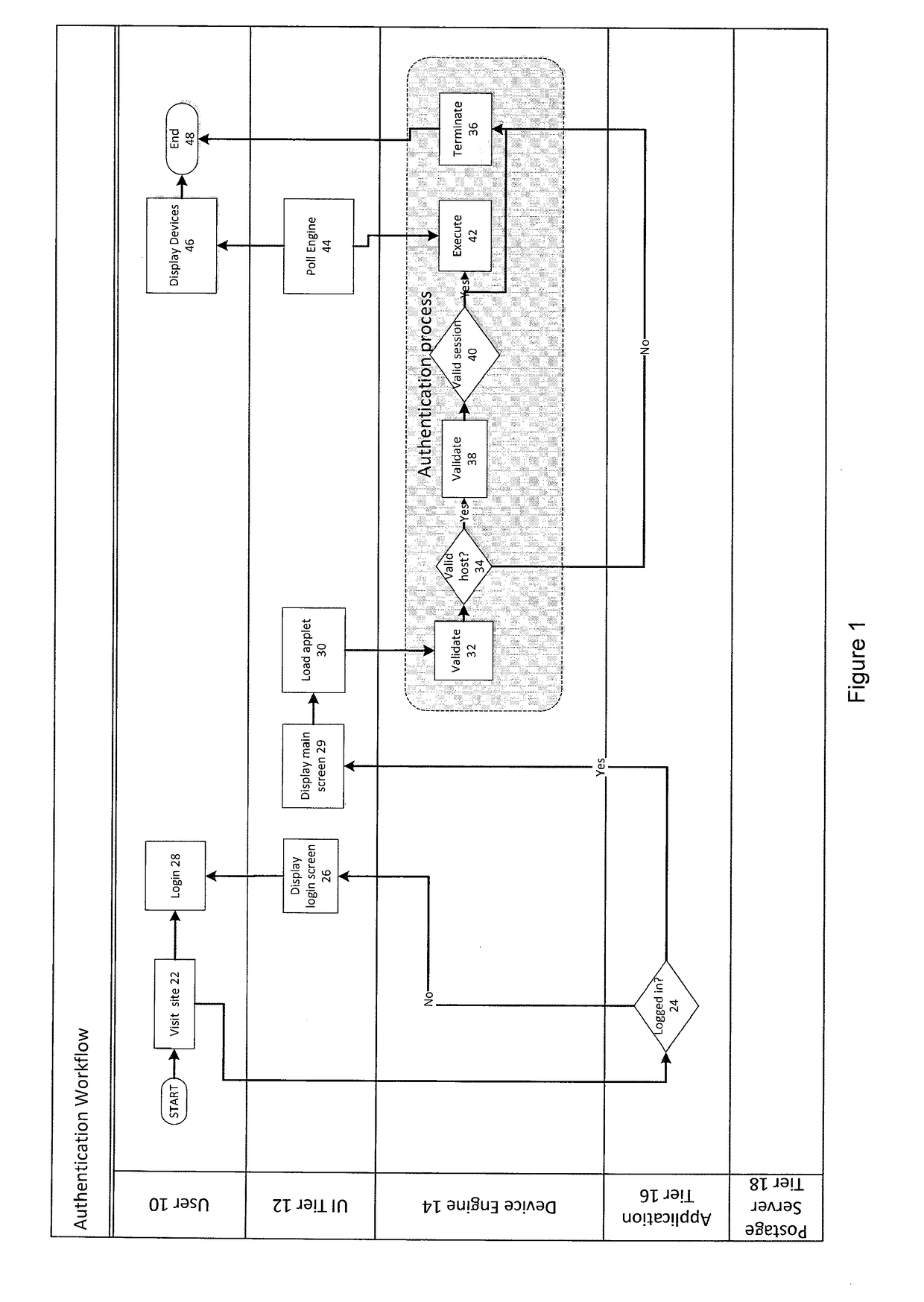
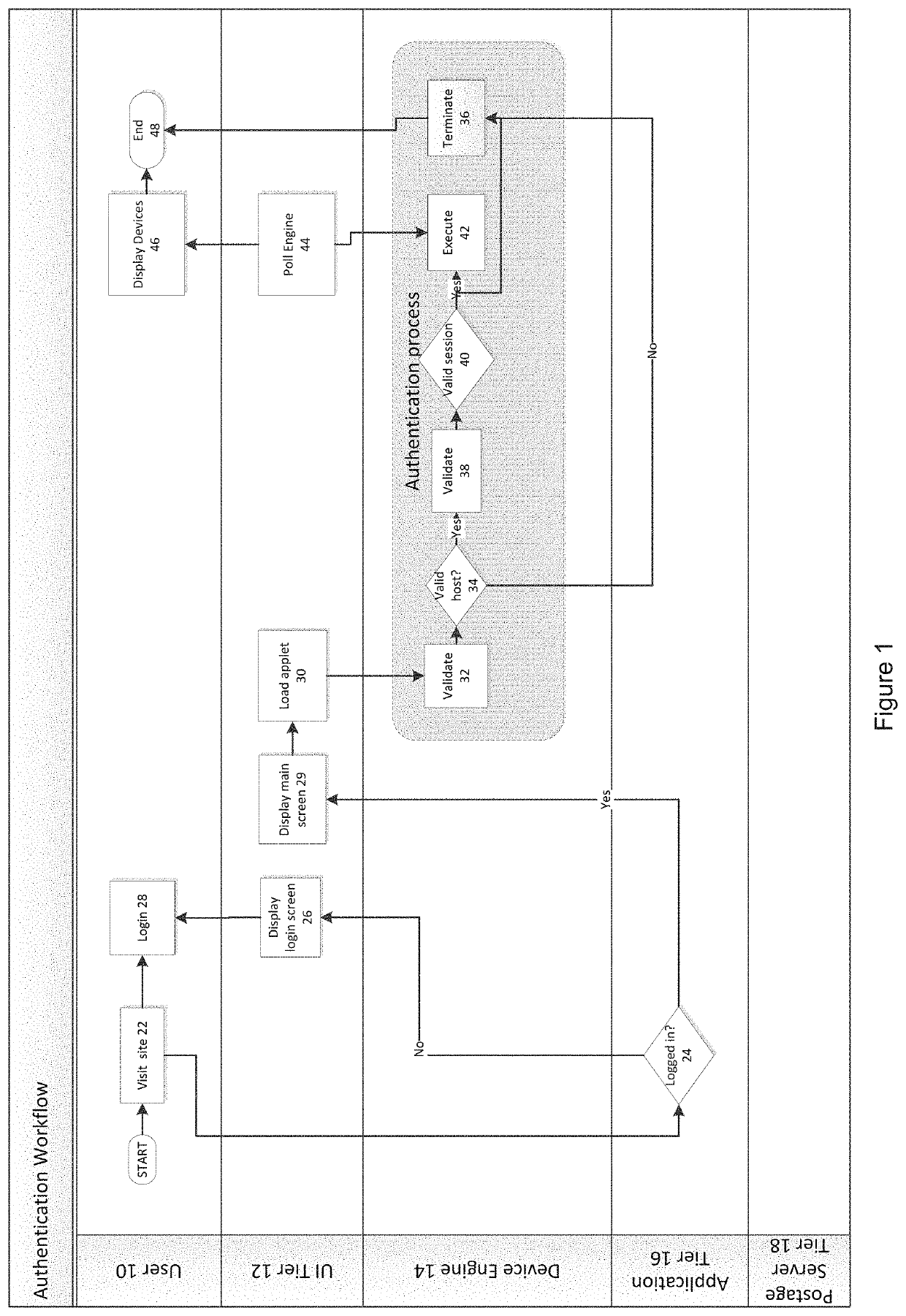
Systems and methods for detecting postage fraud using an indexed lookup procedure
ActiveUS7831518B2Small sizeEliminate transmissionPostage metering systemPayment architectureInternet privacyEnd user
A method and system for using an indexing identifier (such as, e.g., a tracking ID or the combination of a postage vendor ID, user account, and piece count) to decrease the size of the postage indicium transmitted to an end user computer, or eliminate transmission of the postage indicium altogether, is provided. When the postage indicium for the end user computer is generated, it is stored, and the indexing identifier, rather than the postage indicium, is transmitted to the end user computer. The indexing identifier is applied to a mail piece, which is then scanned by the postal authority. The postal authority can obtain the stored postage indicium by reference to the indexing identifier. In this manner, the postal authority has access to the postage indicium without having to apply it to the mail piece. The indexing identifiers can optionally be used to index sender identification information for verifying that the sender of a mail piece is a trusted individual or entity.
Owner:PSI SYST
Systems and methods for detecting postage fraud using an indexed lookup procedure
ActiveUS20110015935A1Small sizeEliminate transmissionPostage metering systemFranking apparatusInternet privacyComputer terminal
A method and system for using an indexing identifier (such as, e.g., a tracking identifier or the combination of a postage vendor ID, user account, and piece count) to decrease the size of the postage indicium transmitted to an end user computer, or eliminate transmission of the postage indicium altogether, is provided. When the postage indicium for the end user computer is generated, it is stored, and the indexing identifier, rather than the postage indicium, is transmitted to the end user computer. The indexing identifier is applied to a mail piece, which is then scanned by the postal authority. The postal authority can obtain the stored postage indicium by reference to the indexing identifier. In this manner, the postal authority has access to the postage indicium without having to apply it to the mail piece. The indexing identifiers can optionally be used to index sender identification information for verifying that the sender of a mail piece is a trusted individual or entity.
Owner:PSI SYST
Pain tracking and management device
InactiveUS20120190936A1Pointing accuratelyPhysical therapies and activitiesElectrotherapyDiabetes mellitusDisease
A system, method and apparatus for real time measurement and monitoring of various personal health parameters including controlled delivery of drugs / medications by intelligent pump appliances, intelligent inhalation appliances and intelligent skin patch appliances used in a standalone manner or in a wired or wireless networked configuration, in conjunction with various peripheral devices, other intelligent appliances, servers, RF ID Tags and stationary / mobile devices. The intelligent appliances relate to the measurement, monitoring and delivery of insulin / other drugs for the treatment of diabetes and other diseases. The method also additionally includes the application of intelligent appliances for pain management including visualization of organs and body locations exhibiting pain.
Owner:IP HLDG LLC
Method and system for delivering items
ActiveUS20180349834A1Convenient timeExtension of timePostage metering systemLogisticsTransport engineeringDelivery location
A method for delivering a plurality of items to a plurality of delivery locations uses a mobile transport vehicle to transport a plurality of delivery robots to a first robot drop location. The robots are released at the first robot drop location and travel to assigned, respective delivery locations, which are in the vicinity of the first robot drop location. After completing delivery, each of the robots may proceed to a first robot pick-up location which may be different from the first drop off location. The robots are collected by a mobile transport vehicle and are transported to a second robot drop off location. While being transported, the robots can be reloaded with items for delivery in the vicinity of the second drop off location. A system may include one or more such mobile transport vehicles and a plurality of such robots, under the control of a server.
Owner:STARSHIP TECH OU
Method and system for providing technology change using of technology life cycle graph
Owner:KOREA INST OF SCI & TECH INFORMATION
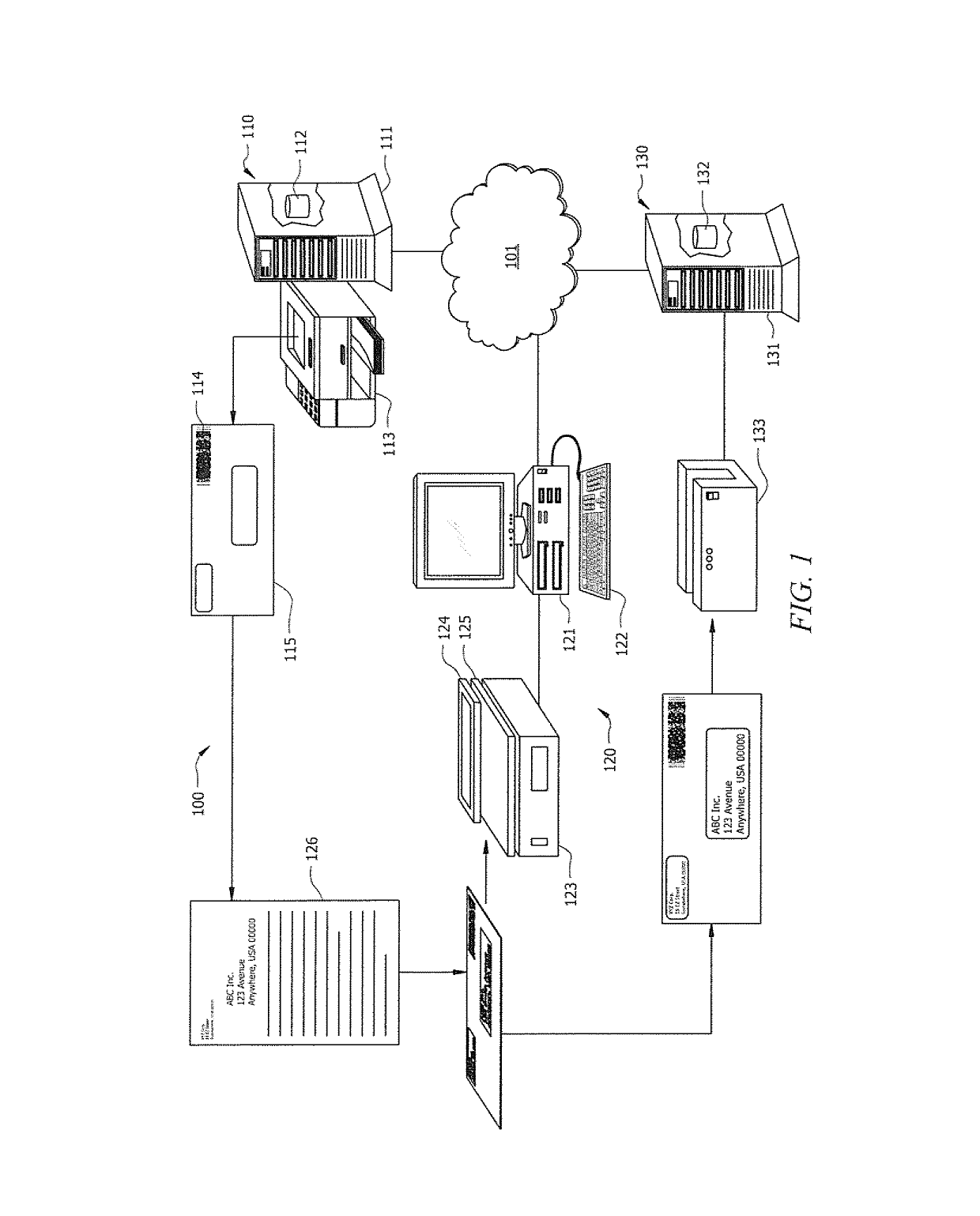
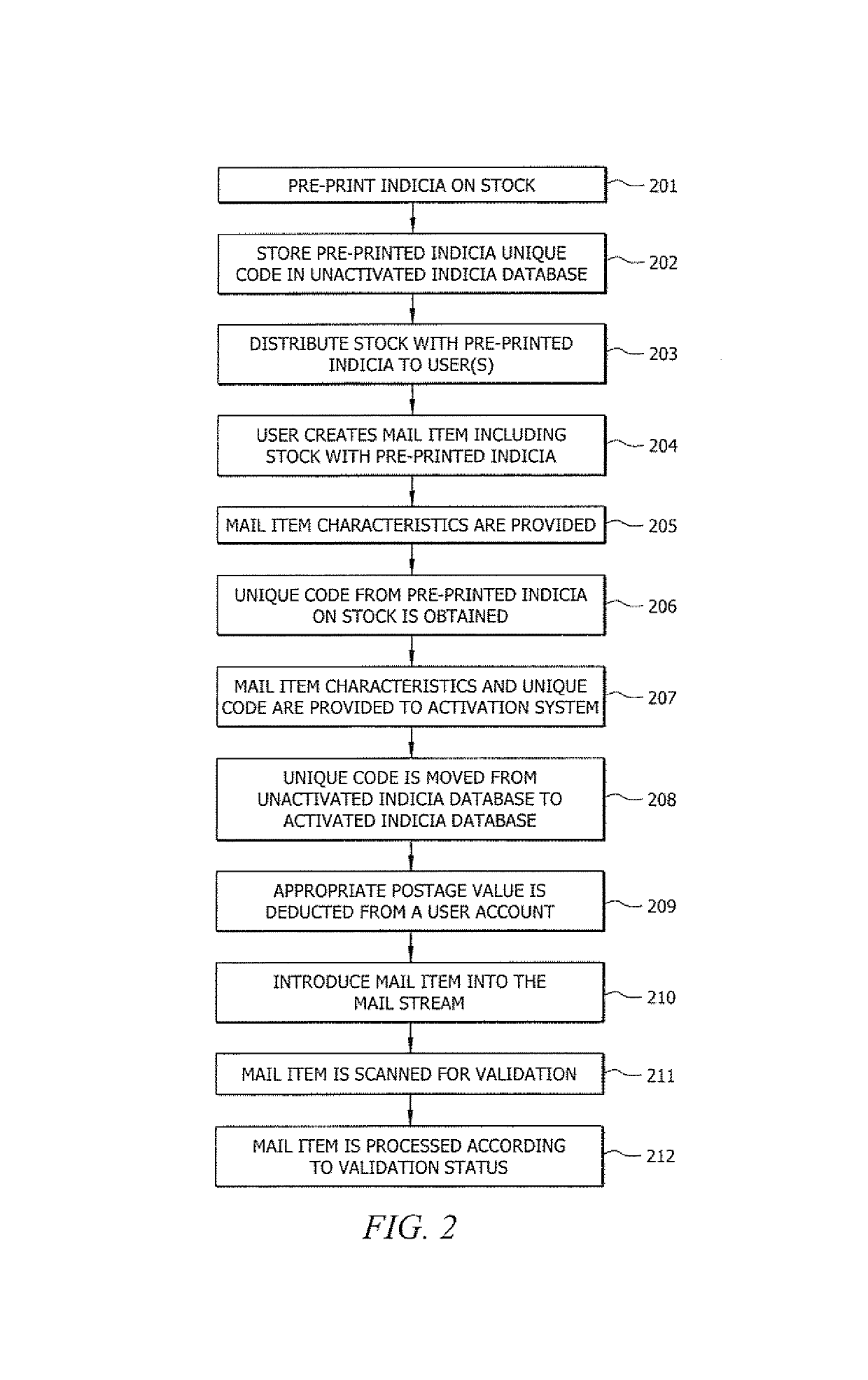
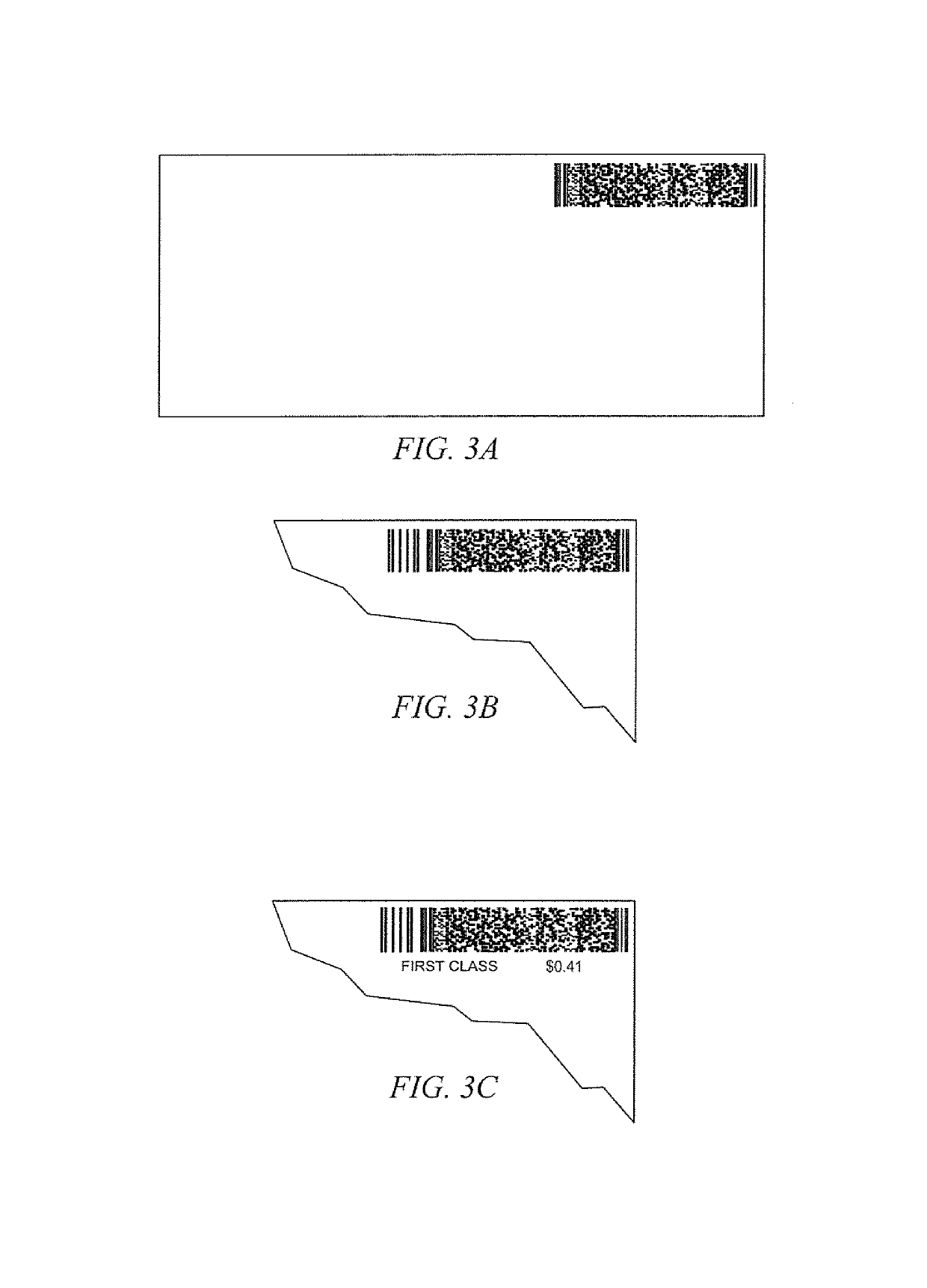
Systems and methods for distributed activation of postage
ActiveUS10373398B1Improve trustPromote activationPostage metering systemFranking apparatusBiological activationComputer science
Systems and methods which provide for distributed activation of pre-printed, or otherwise pre-produced, indicia to thereby provide value bearing indicia, such as postage indicia, are shown. Embodiments apply indicia to fungible items, such as envelopes, paper stock, labels, etc., at a central location. When one of the items bearing the pre-produced indicia is incorporated into a mail item by a user, the pre-produced indicia may be activated and thus becomes valid postage indicia for use in posting the mail item. Various images, information, characters, symbols, and / or marks may be provided in association with pre-produced indicia. Such marks may be printed using a same or different media than an accompanying pre-produced indicia. Embodiments implement a system for scanning pre-produced indicia for activation as postage indicia.
Owner:AUCTANE INC
High volume serialized postage at an automated teller machine or other kiosk
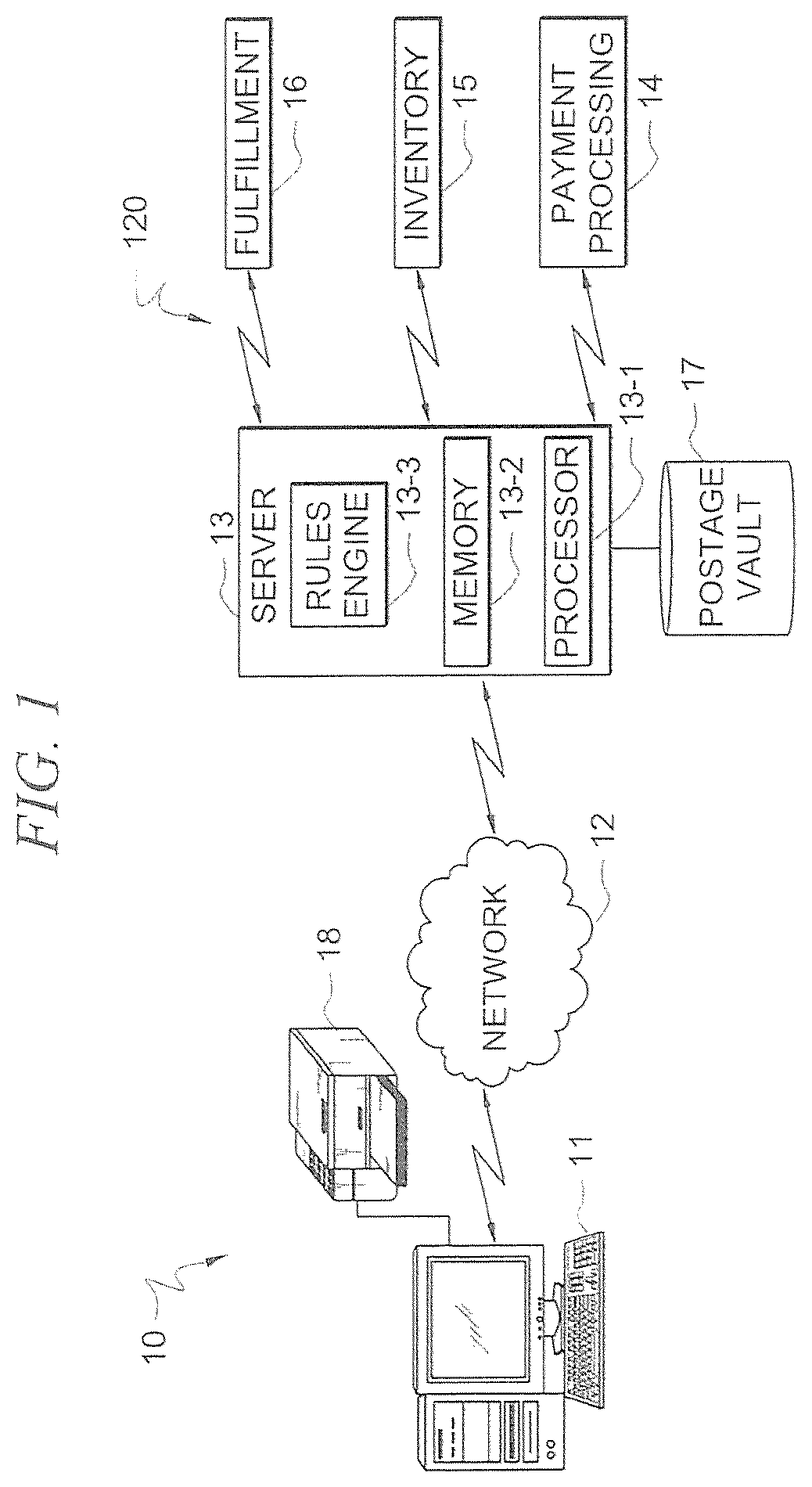
A system and method for retrieving a plurality of indicia are described. The method includes receiving, by a computer system associated with a postage provider a request from a user, the request including a number of the plurality of indicia, and a monetary value of each of the plurality of indicia; and authenticating the request. The method further includes verifying whether sufficient funds exist in an account of the user for the number and monetary value of the plurality of requested indicia. If the request is found authentic and the computer system determines that sufficient funds exist in the account of the user for the number and monetary value of the requested indicia, extracting the plurality of indicia. The method further includes assembling in a return message the plurality of indicia as at least one binary data message; and transmitting the message to a computer associated with the user.
Owner:PSI SYST
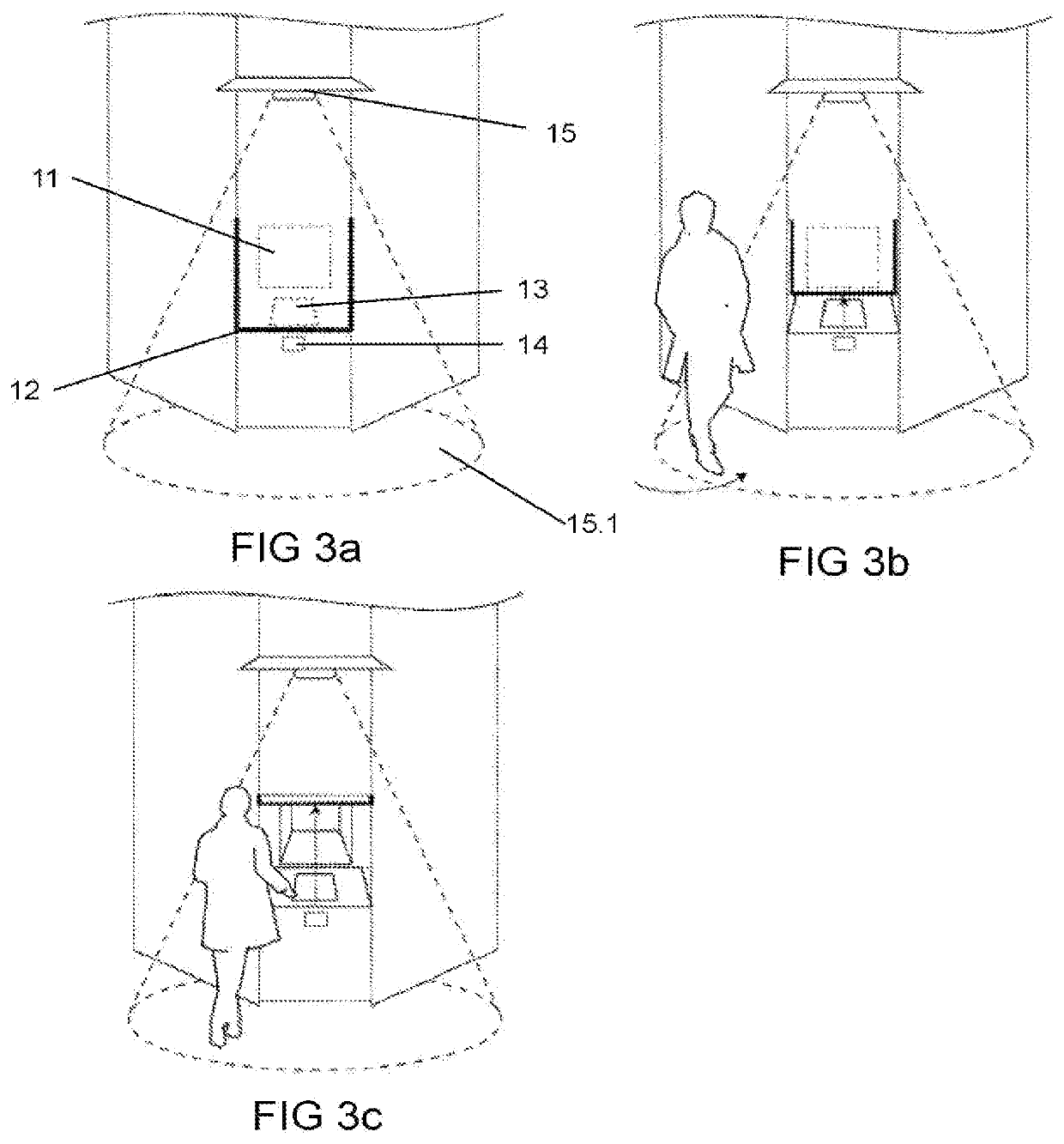
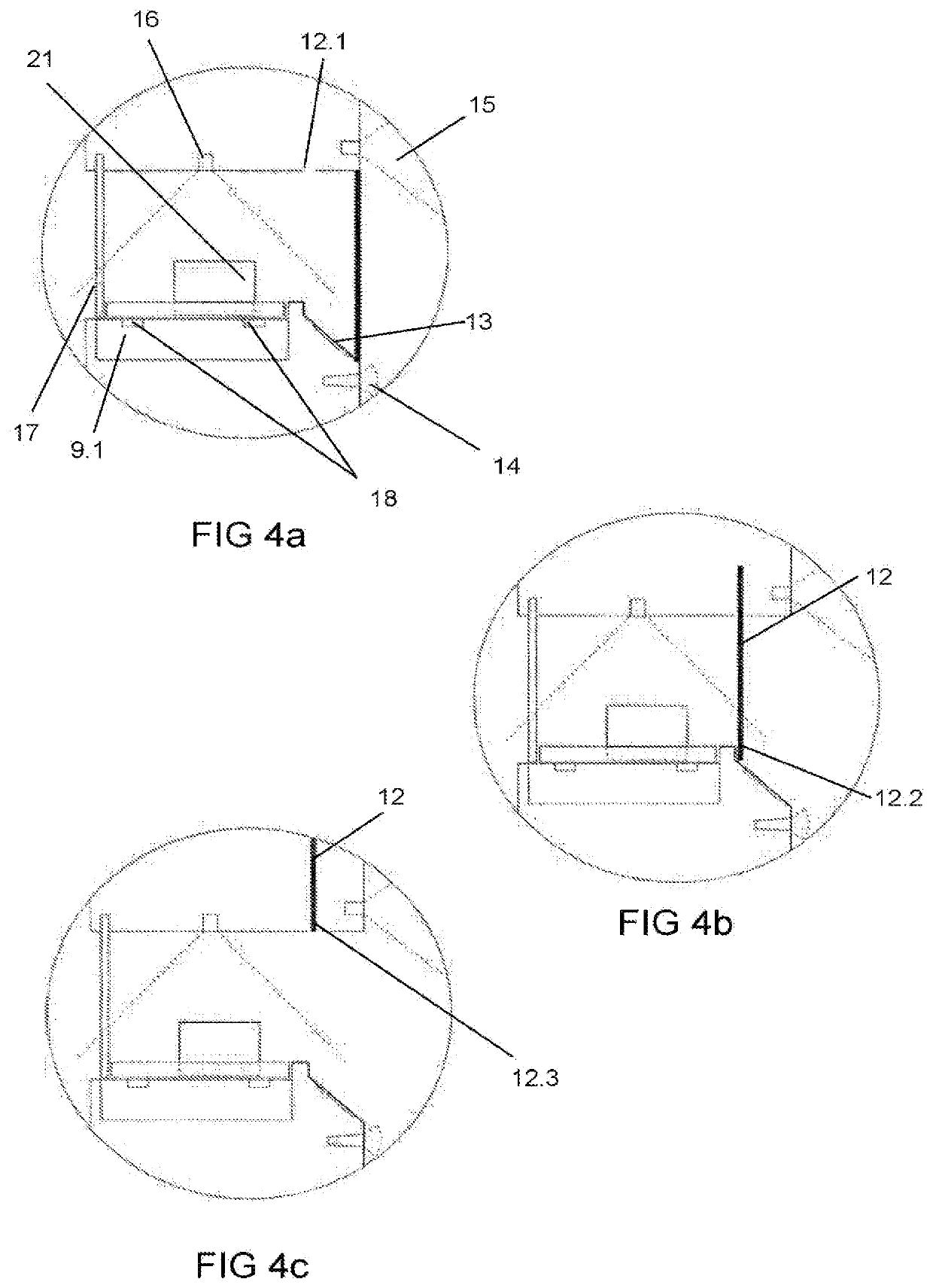
Self-Service Parcel Terminal with Optimized Shelving Arrangement
PendingUS20220245373A1ConveyorsCoin-freed apparatus detailsElectronic controllerElectronic communication
This disclosure includes a parcel terminal that may include a shelving unit comprising a plurality of shelves that are separated by respective predetermined distances along a dimension of the unit. In an embodiment, the plurality of shelves may be evenly spaced. The parcel terminal may further include a receptable for receiving a parcel from a user, a loader configured to transfer the parcel from the receptacle to a shelf on the shelving unit, and an electronic controller in electronic communication with the loader. The electronic controller may be configured to determine a number of open shelves required to accommodate the parcel based on a size of the parcel and on the respective predetermined distances, to select a set of shelves having at least the required number of open shelves, and to initiate a movement of the loader so as to place the parcel within the selected set of shelves.
Owner:CLEVON AS
Systems and methods for protecting content when using a general purpose user interface application
Systems and methods which prevent or limit access to protected content (e.g., value bearing indicia (VBI)) by a general purpose user interface application (e.g., web browser) are shown. Embodiments implement techniques to avoid displaying protected content by a general purpose user interface application, or displaying protected content during a time in which a user does not have access to particular functions of the general purpose user interface application, to protect the content from various operations, such as repeated printing, electronic copying, etc. Data presentation formatting control in the form of style sheets may be utilized to control access to content. Additionally or alternatively, executable code or an executable object may be implemented within a page or other content to control access to content. Similarly, separate areas, such as windows or pages, may be utilized to control access to content.
Owner:AUCTANE INC
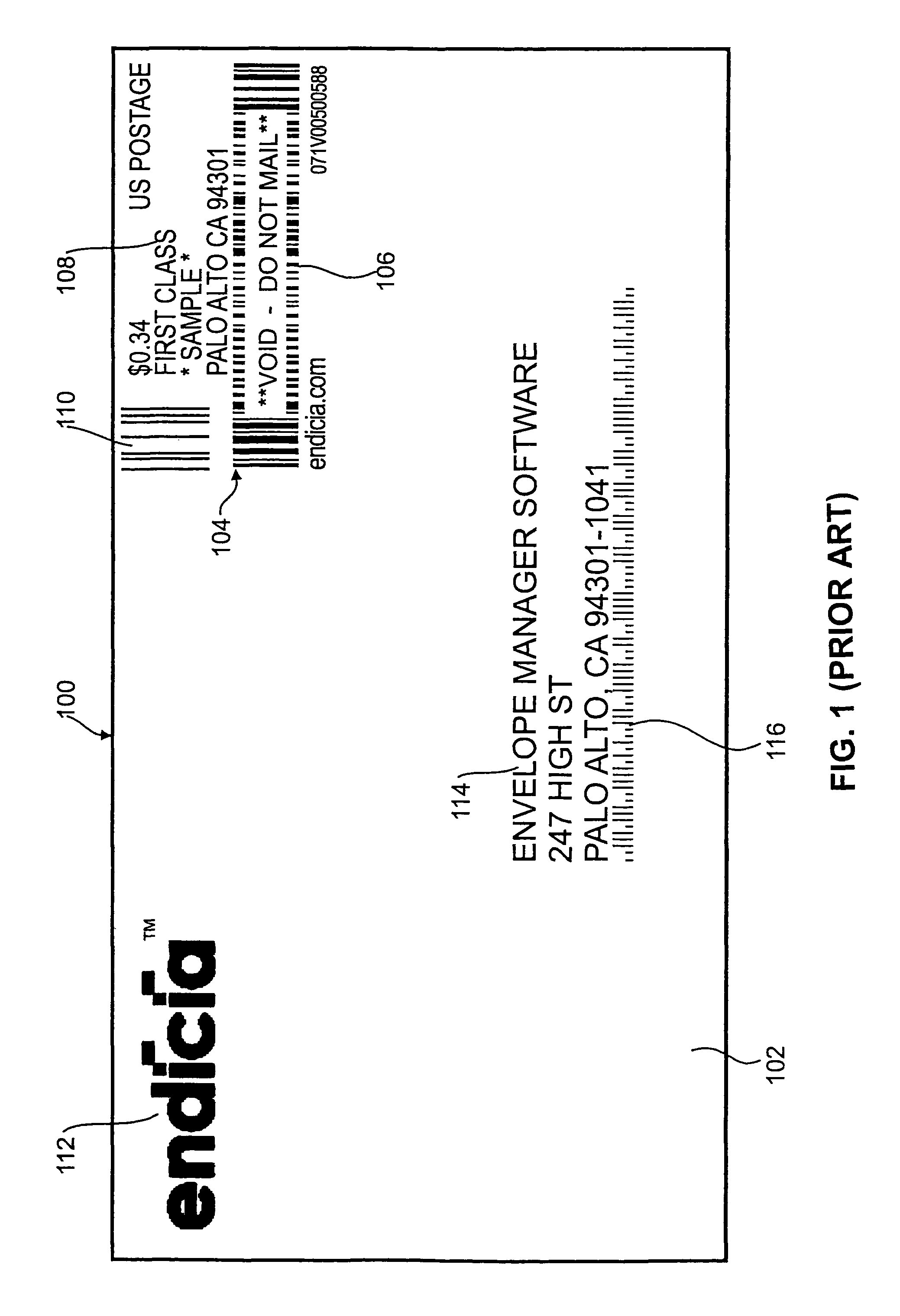
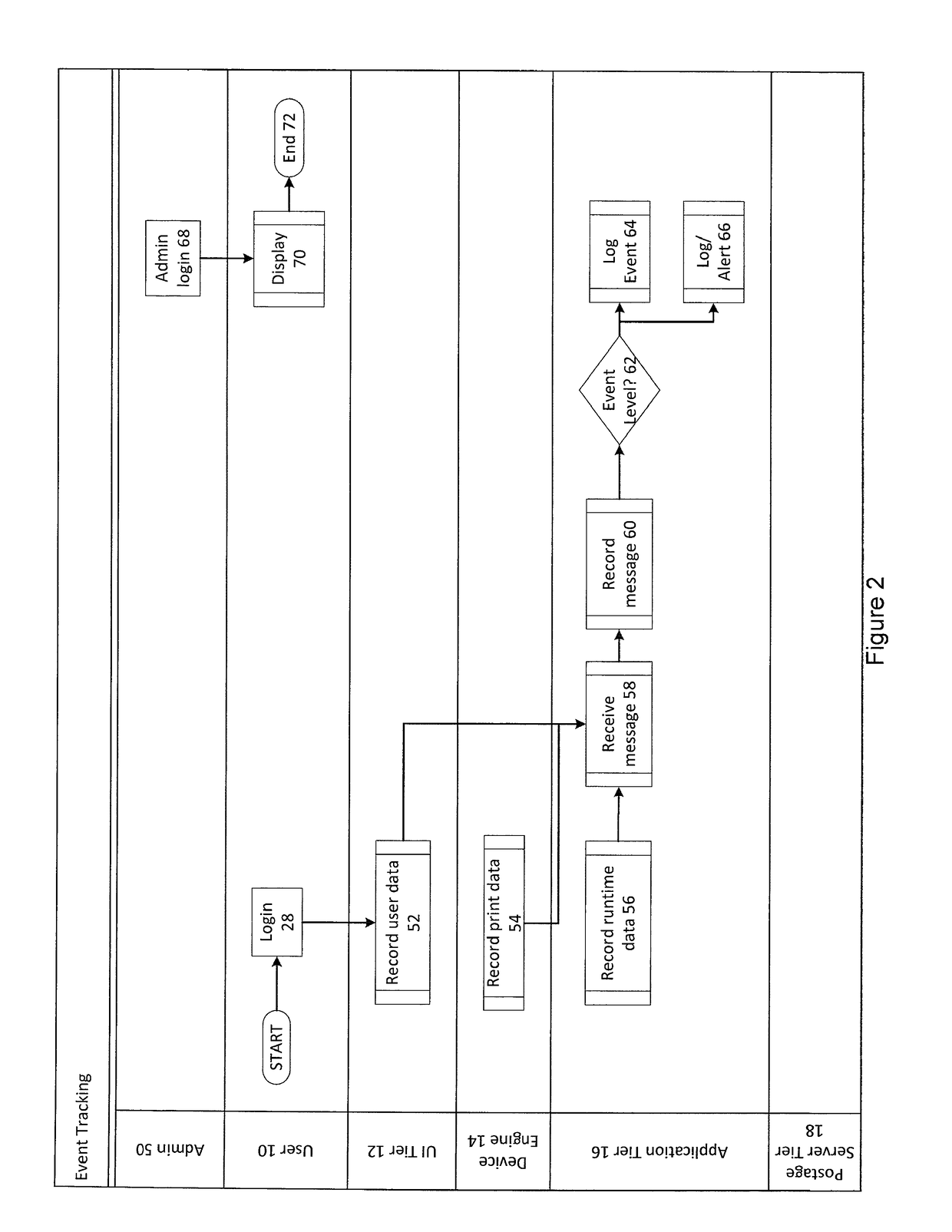
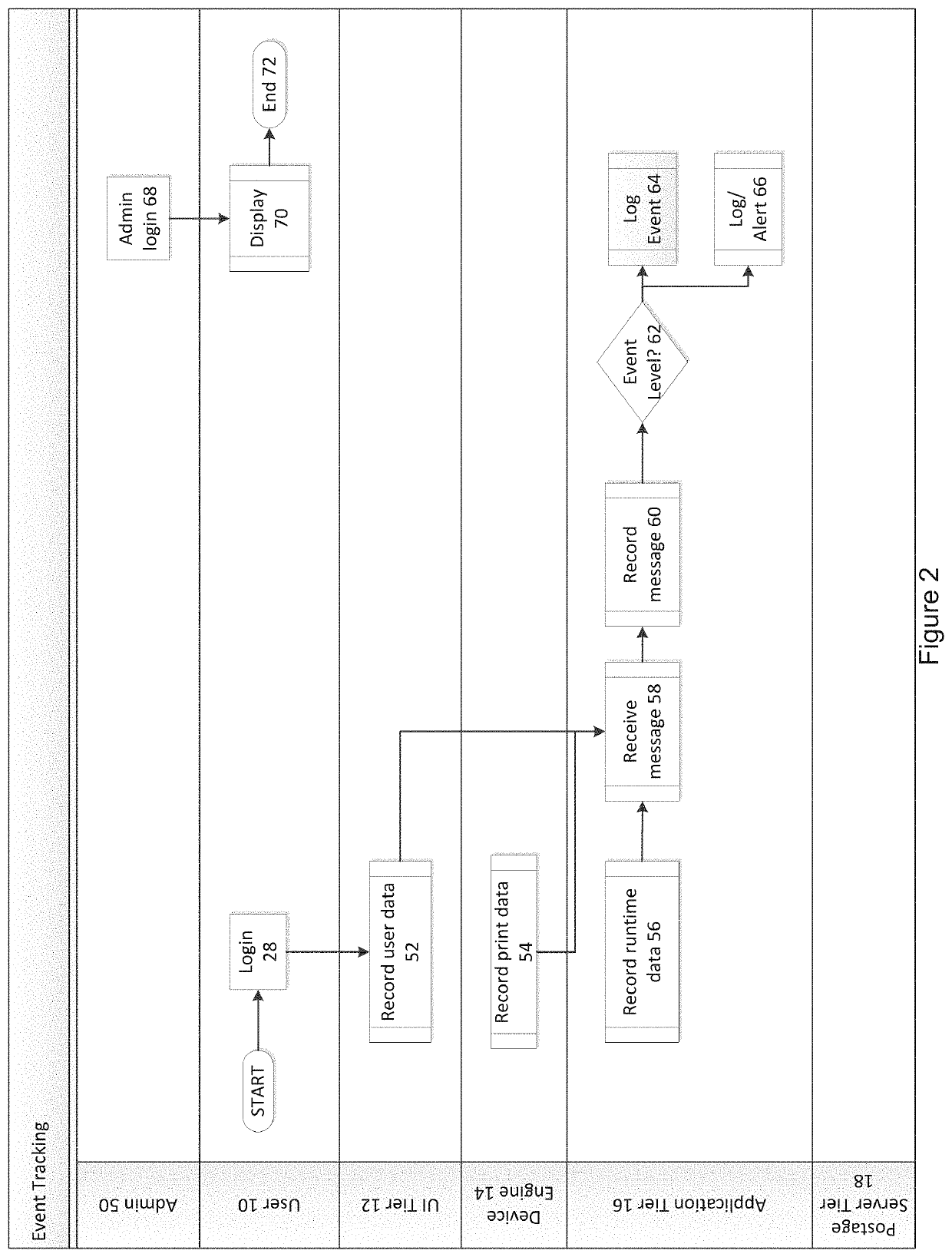
System and method for creating managing and verifying postal correspondences
A system for creating, managing and verifying postal correspondences is disclosed. The system includes a plurality of non-transitory storage media information that includes a home page screenshot, a features page screenshot, a CASEMAIL™ screenshot and a pricing screenshot. The method for managing postal correspondences includes postage type selected from the group consisting of standard mail, first-class mail or express mail, choosing to send an e-mail invite to a third party for additional editing and approving one or more letters before submitting for processing, choosing to have e-mail notifications via e-mail or other suitable communication and choosing to log-in into the user's account to track delivery status step that further includes utilizing tracking numbers and other suitable tracking information.
Owner:RUIZ JOE
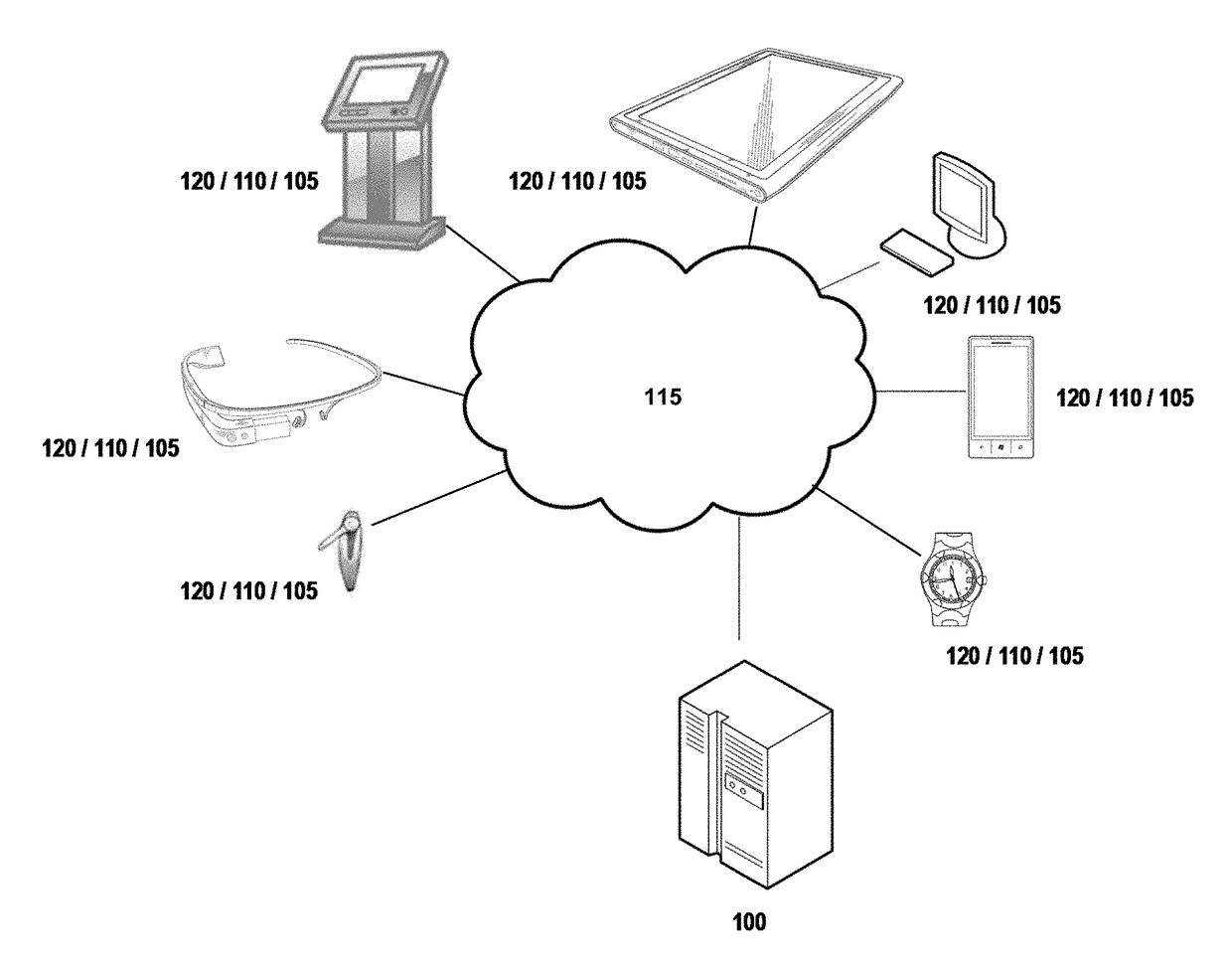
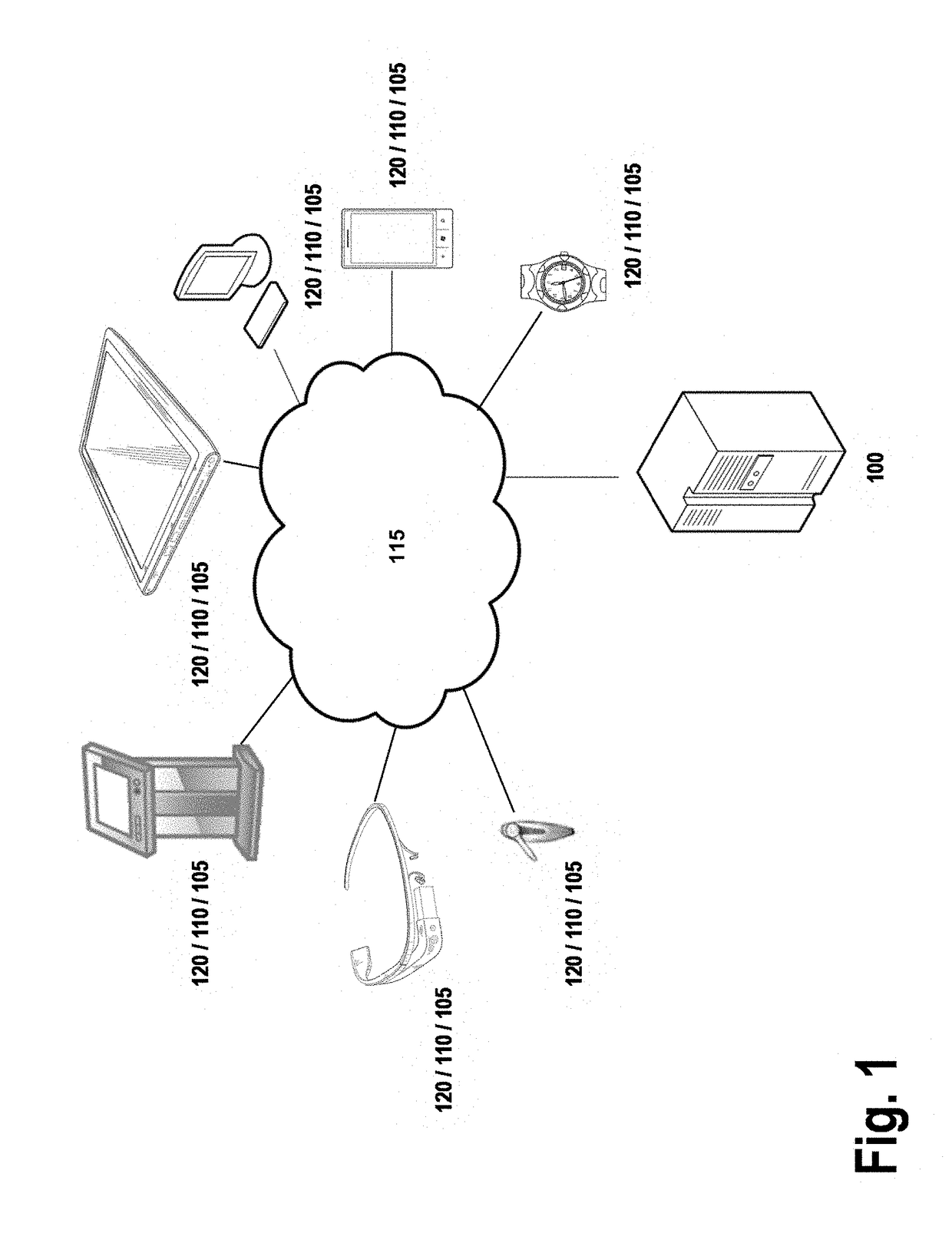
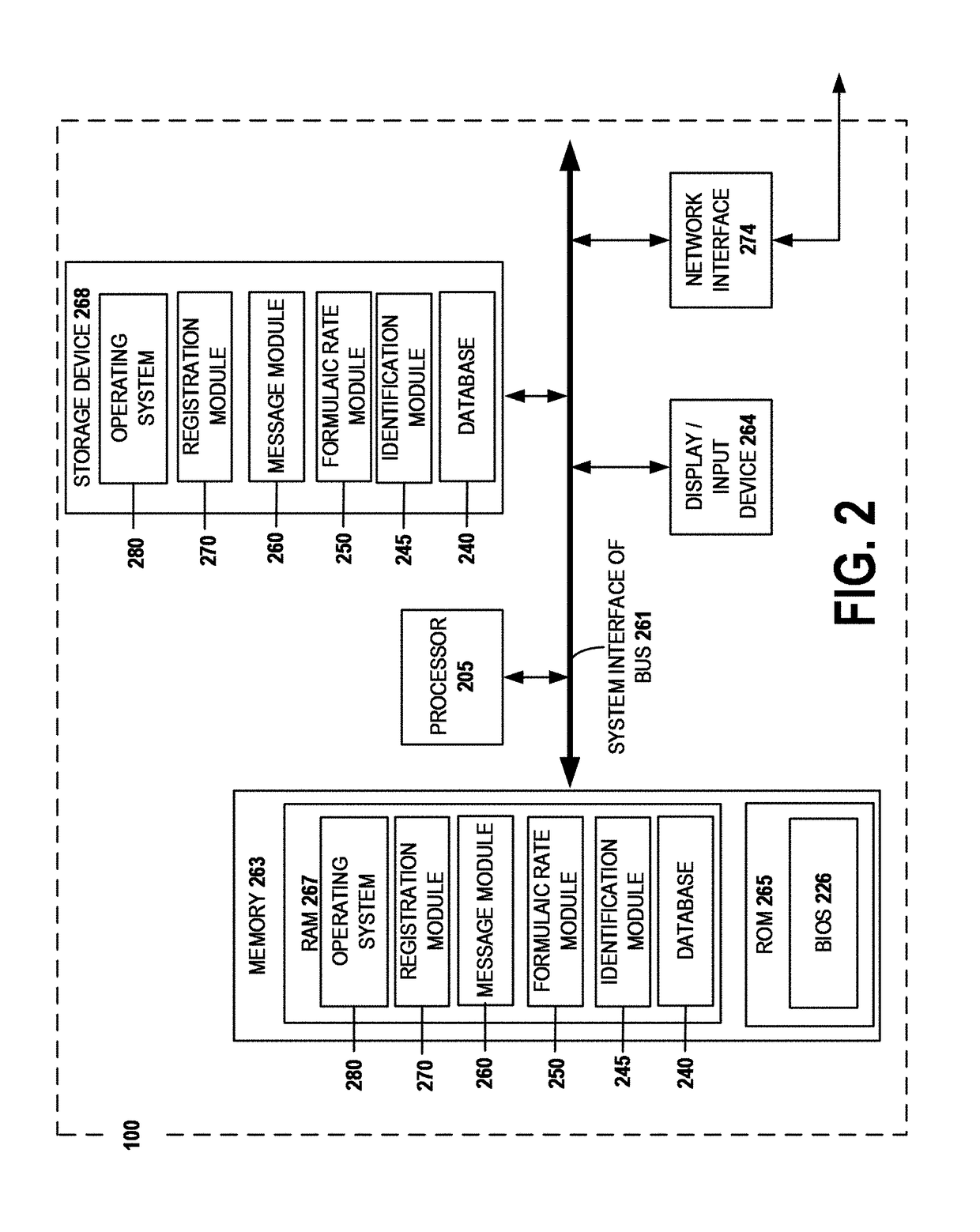
Systems, methods, apparatuses, and computer program products for managing and providing formulaic rates
InactiveUS20170286894A1Generate efficientlyMaintain rateDigital data information retrievalDiscounts/incentivesComputer scienceComputer program
An apparatus is provided for generating formulaic rates. The apparatus may include at least one memory and a processor(s) configured to define a first formula(s) in a row(s) of a database to calculate a first shipping rate value for a first type of shipping rate, among plural types of shipping rates, associated with a first rate identifier. The processor is further configured to define content in the row to analyze a predecessor rate identifier(s) of a previously generated source. The processor is also configured to detect a second shipping rate value corresponding to the predecessor rate identifier. The second shipping rate value is associated with a second type of shipping rate. The processor is further configured to determine the first shipping rate value for the first type of shipping rate based on calculating the formula using the second shipping rate value. Corresponding computer program products and methods are also provided.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
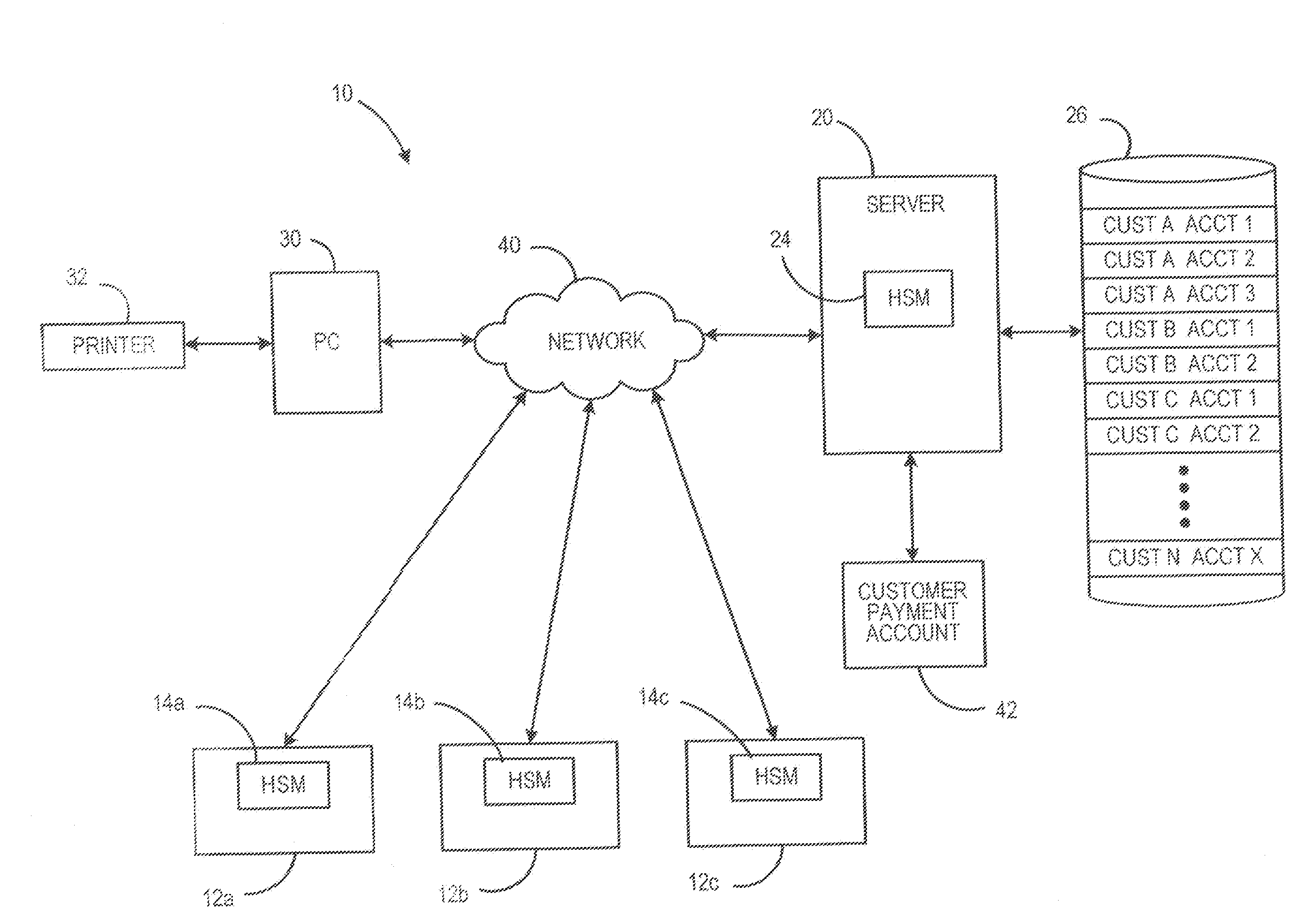
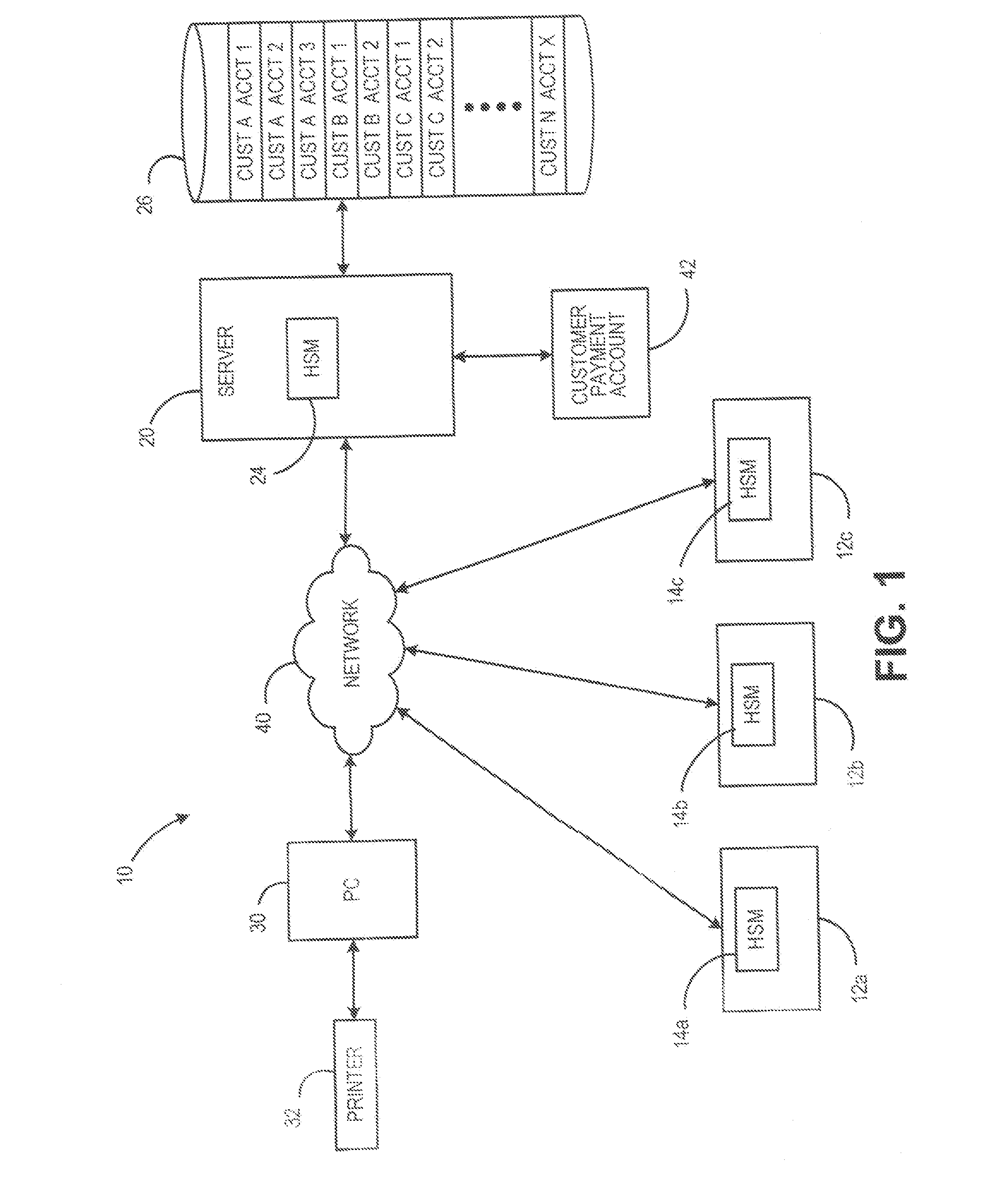
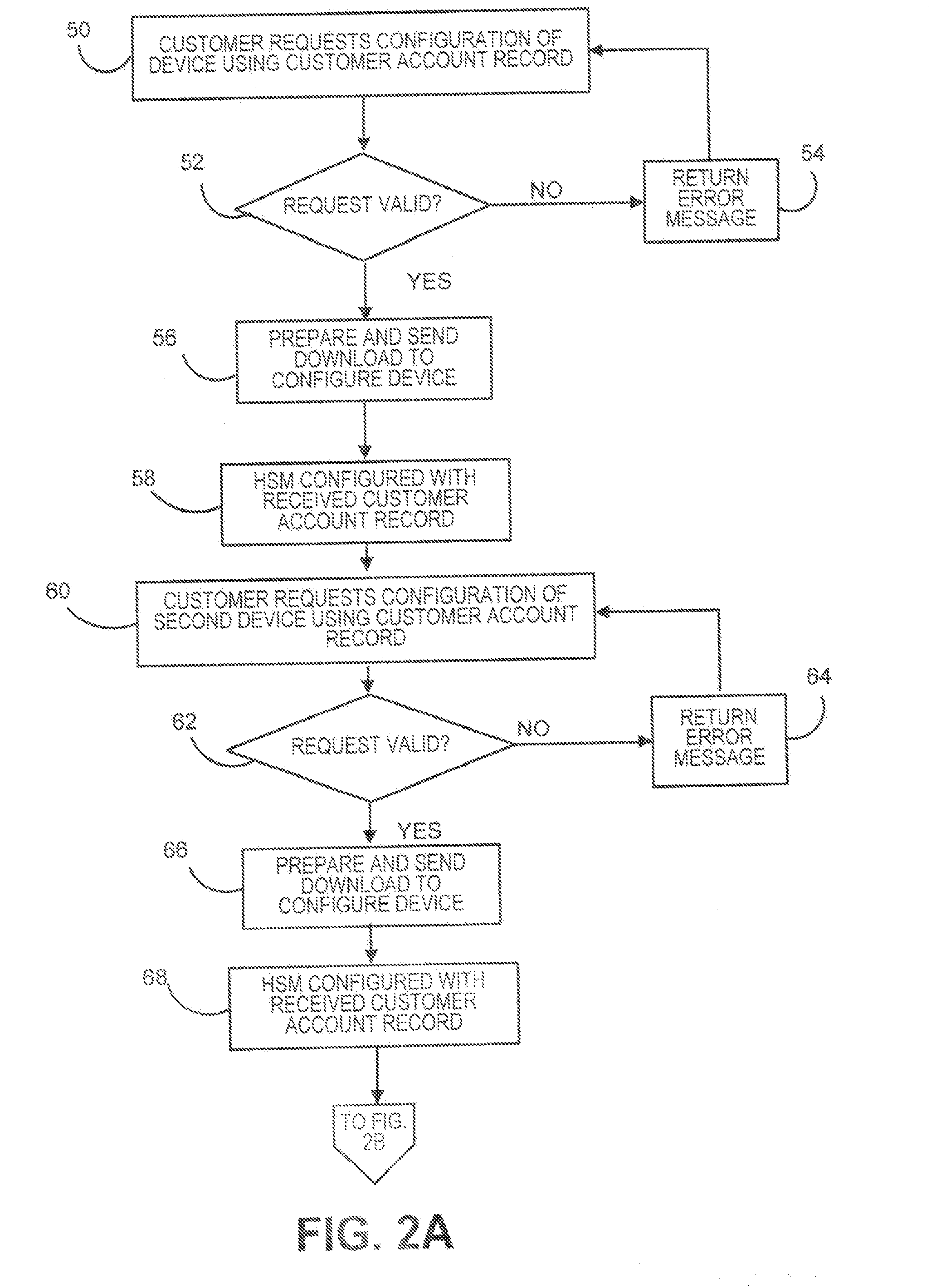
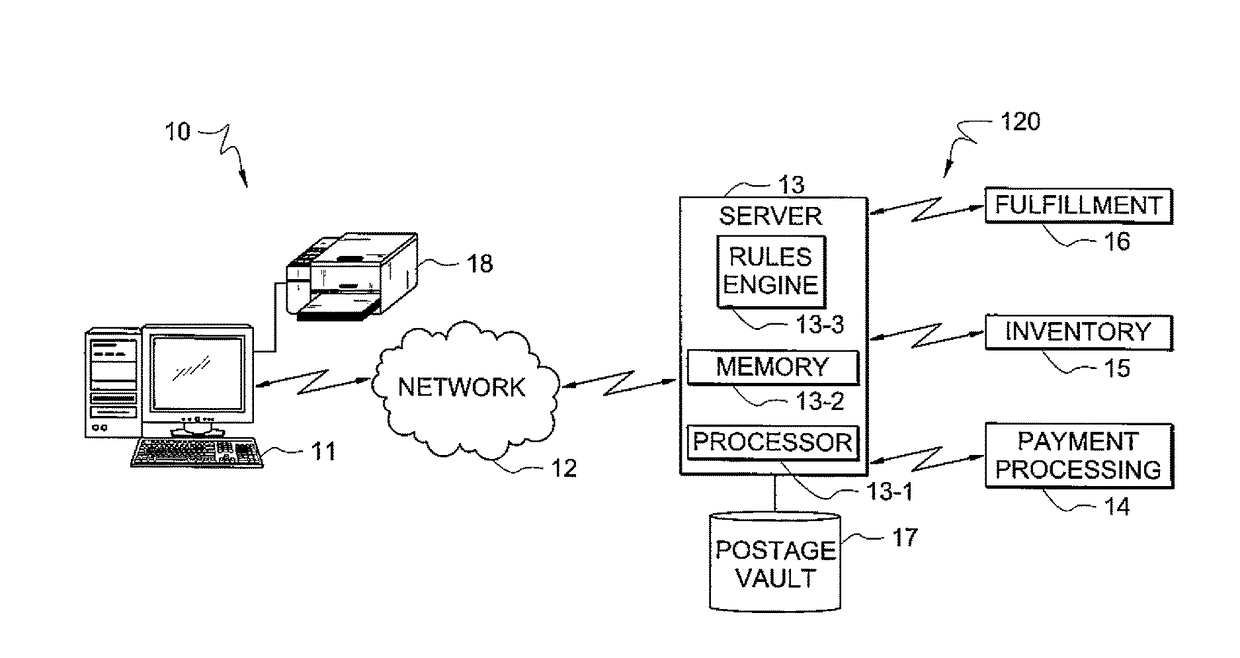
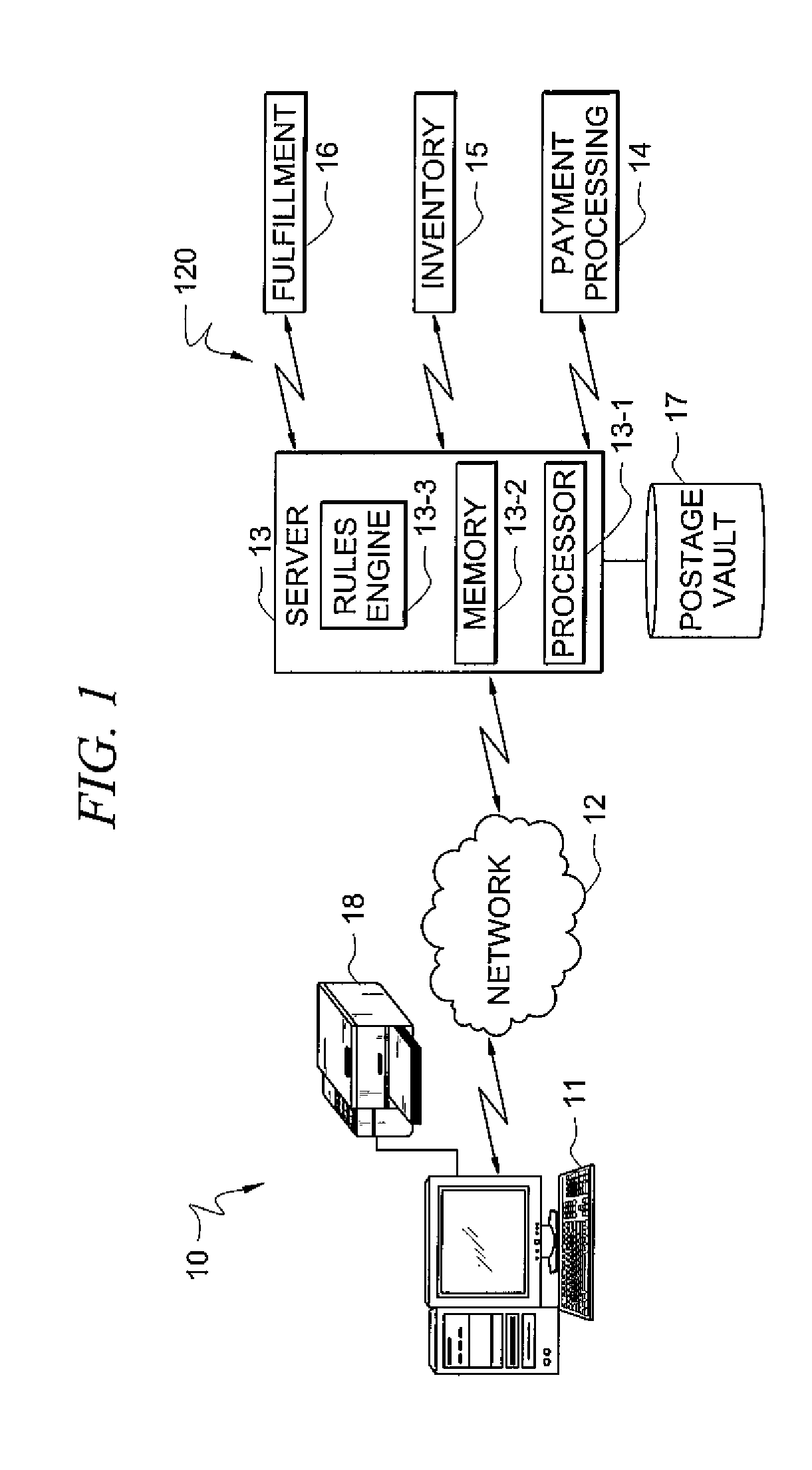
Method and system for supporting multiple postage printing devices using multiple customer accounts without having to maintain funds in each customer account
A system and method for allowing a customer to maintain multiple customer accounts used for generating and printing postage without having to maintain a minimum amount of funds in each account. When multiple accounts are maintained for a customer, only one the of the multiple accounts maintains pre-paid funds in the registers. The other accounts do not have any pre-paid funds, i.e., maintain zero funds, in the registers. When a customer account that does not have any pre-paid funds stored therein is utilized to generate postage, the register in that account is refilled for the exact amount of postage to be generated from a customer payment account. By performing on-demand postage refills for the exact amount needed to generate an indicium, the customer is no longer required to have funds committed to each customer account while still being able to utilize multiple accounts for multiple postage printing devices.
Owner:PITNEY BOWES INC
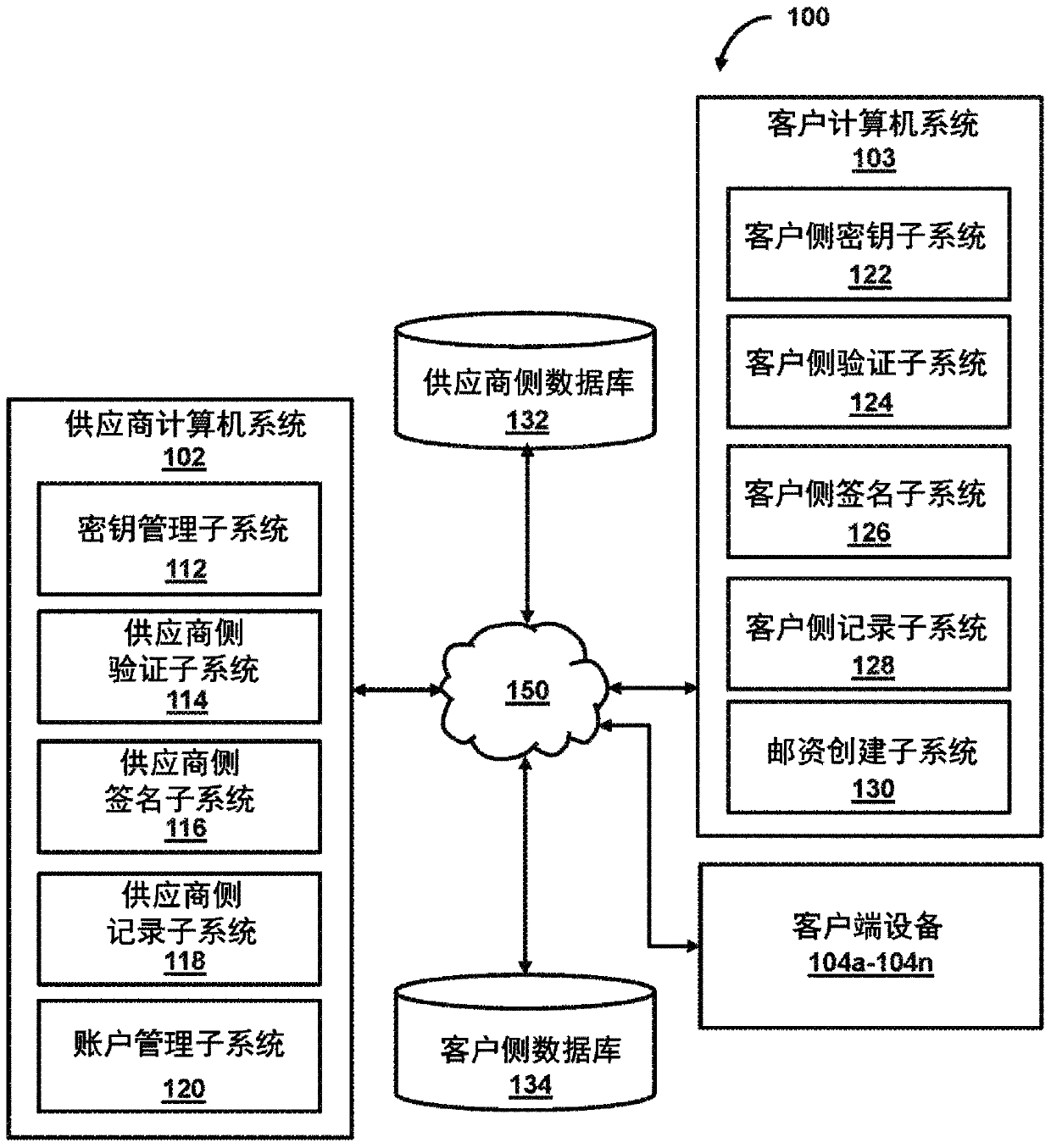
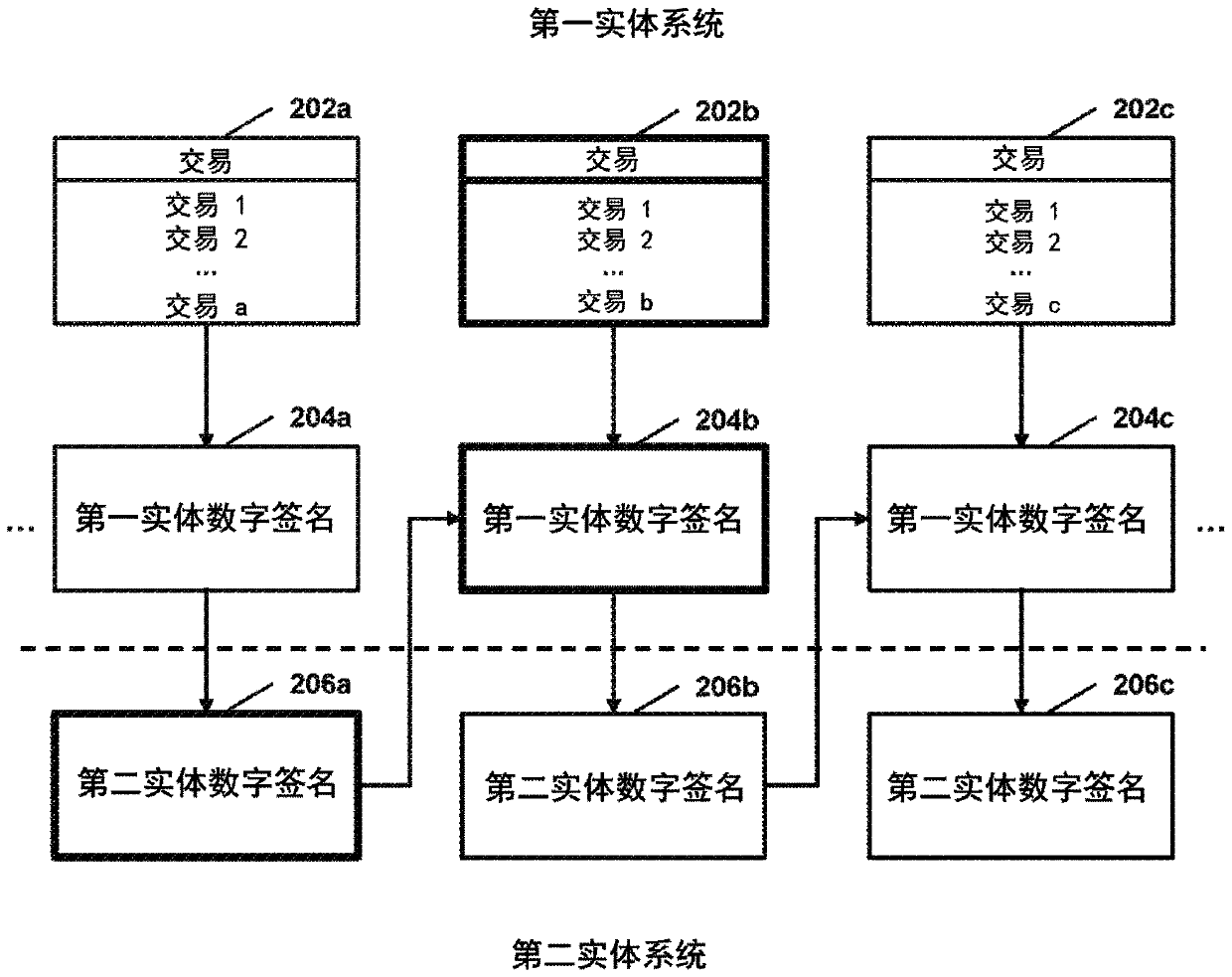
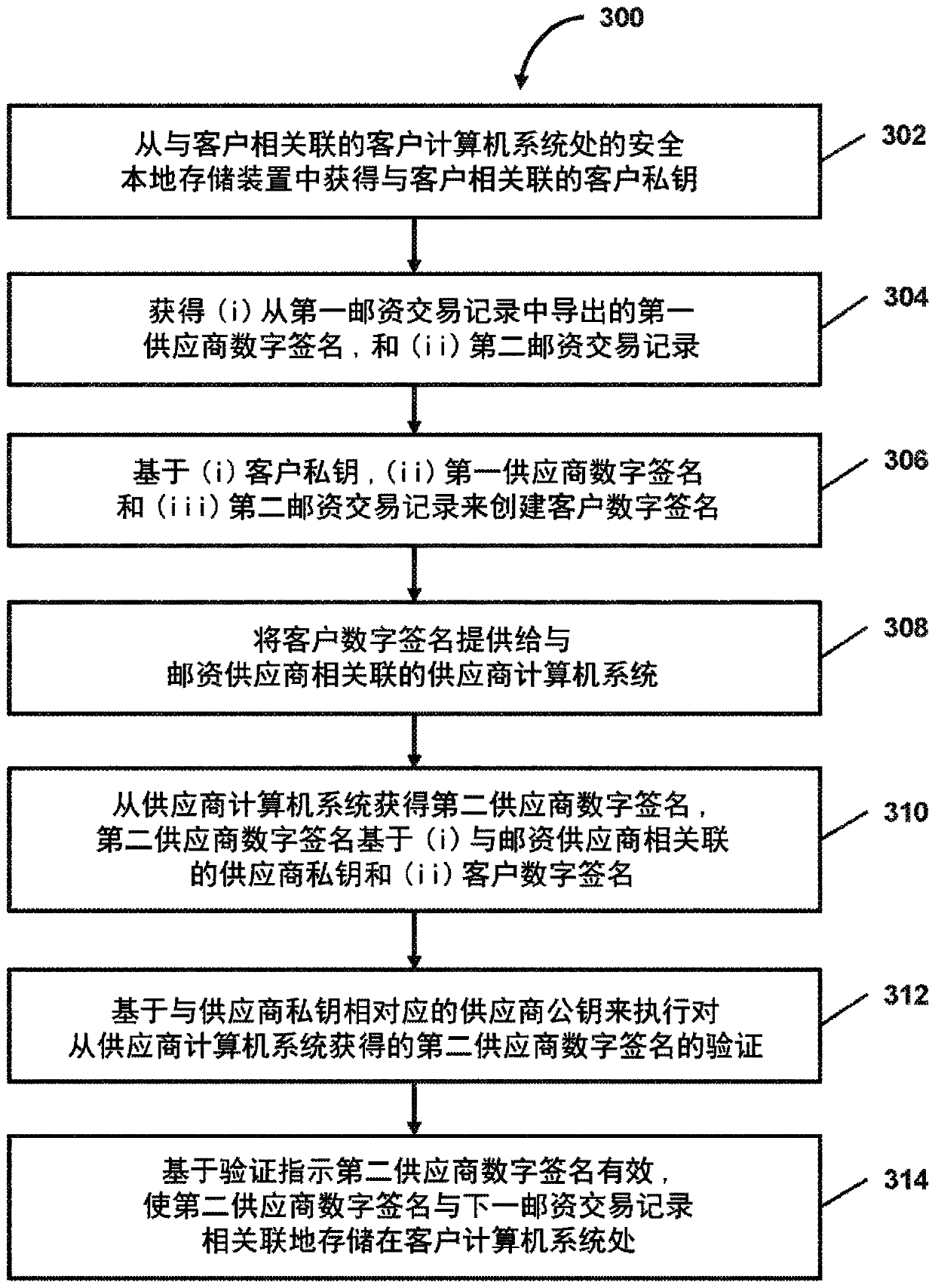
System and method for cryptographic-chain-based verification of postage transaction records
PendingCN110753940AMultiple keys/algorithms usagePostage metering systemDigital signatureEngineering
In certain embodiments, cryptographic-chain-based verification of postage transaction records may be facilitated. In some embodiments, a customer computer system may obtain a customer private key associated with a customer from a secure local storage at the customer computer system. The customer computer system may obtain (i) a first vendor digital signature derived from a first postage transaction record and (ii) a second postage transaction record. The customer computer system may create a customer digital signature based on (i) the customer private key, (ii) the first vendor digital signature, and (iii) the second postage transaction record. The customer computer system may provide the customer digital signature to a vendor computer system associated with the postage vendor, and, in response, obtain a second vendor digital signature from the vendor computer system, wherein the second vendor digital signature is based on (i) a vendor private key associated with the postage vendor and(ii) the customer digital signature.
Owner:斯坦普斯网站公司
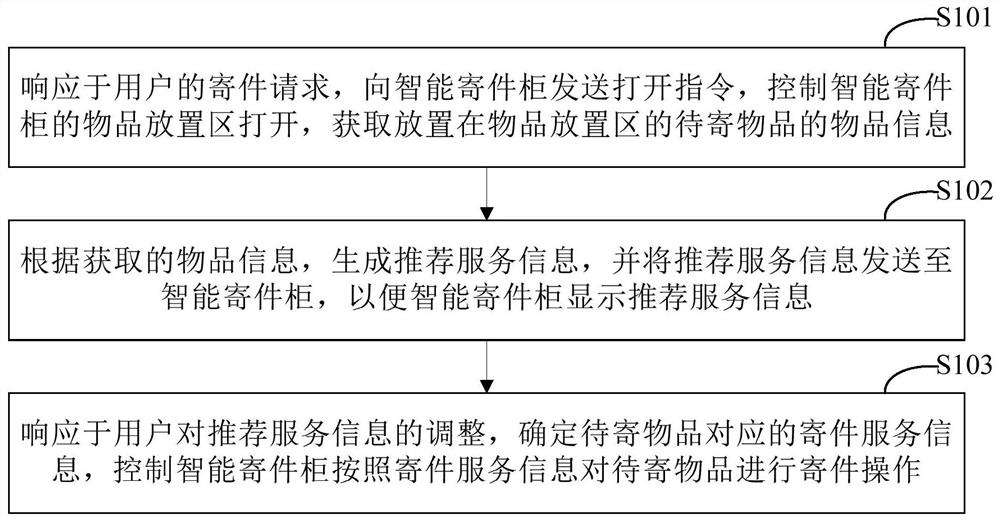
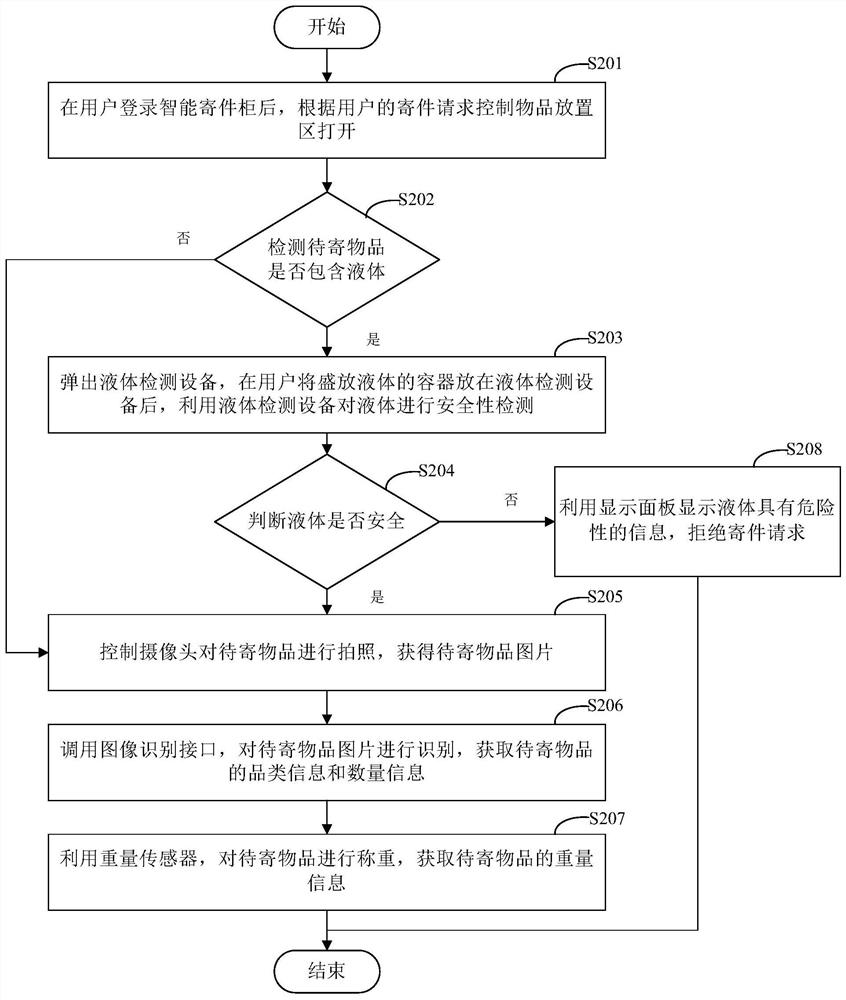
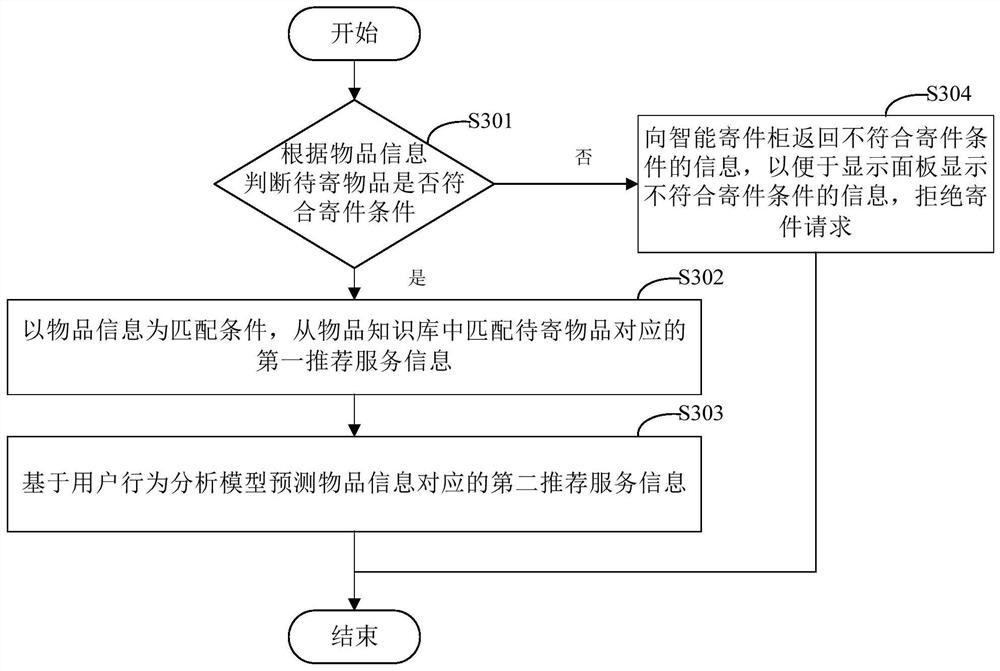
Mailing method and mailing device
ActiveCN113763645AGood experienceImprove user experienceDigital data information retrievalApparatus for meter-controlled dispensingRecommendation serviceService information
The invention discloses a mailing method and a mailing device, and relates to the technical field of computers. A specific embodiment of the method comprises the steps of sending an opening instruction to an intelligent mailing cabinet in response to a mailing request of a user, controlling an article placement area of the intelligent mailing cabinet to be opened, and obtaining article information of a to-be-mailed article placed in the article placement area; according to the obtained article information, generating recommendation service information, and sending the recommendation service information to the intelligent mailing cabinet, so that the intelligent mailing cabinet displays the recommendation service information; and in response to adjustment of the recommended service information by the user, determining mailing service information corresponding to the to-be-mailed article, and controlling the intelligent mailing cabinet to perform mailing operation on the to-be-mailed article according to the mailing service information. According to the embodiment, the problem that in the prior art, information of online operation is not matched with information of actual mailing can be solved, mailing operation is carried out through different mailing services, more actual application scenes are met, and good use experience is brought to a user.
Owner:BEIJING JINGDONG ZHENSHI INFORMATION TECH CO LTD
Convenient payment method and payment device thereof
InactiveCN106327181AEnsure safetyGuarantee payment securityPostage metering systemPayment protocolsPaymentPassword
The invention relates to a convenient payment method and a payment device for realizing the method. When shopping payment is performed through the device according to the method, a mobile phone is used as a verification key for payment by utilizing the characteristic that the moderns basically carry the mobile phone. Passwords and other identity verification information do not need to be instantly inputted in payment and the payment security can be guaranteed so that the method has the effects of being convenient and rapid. All the steps of the method are completed by the payment device at the instant of payment. When payment is legal, the payer performs the action of "swiping" and does not need to perform additional input operation at the macro level so that the payment efficiency and the payment experience can be enhanced.
Owner:屈卫兵
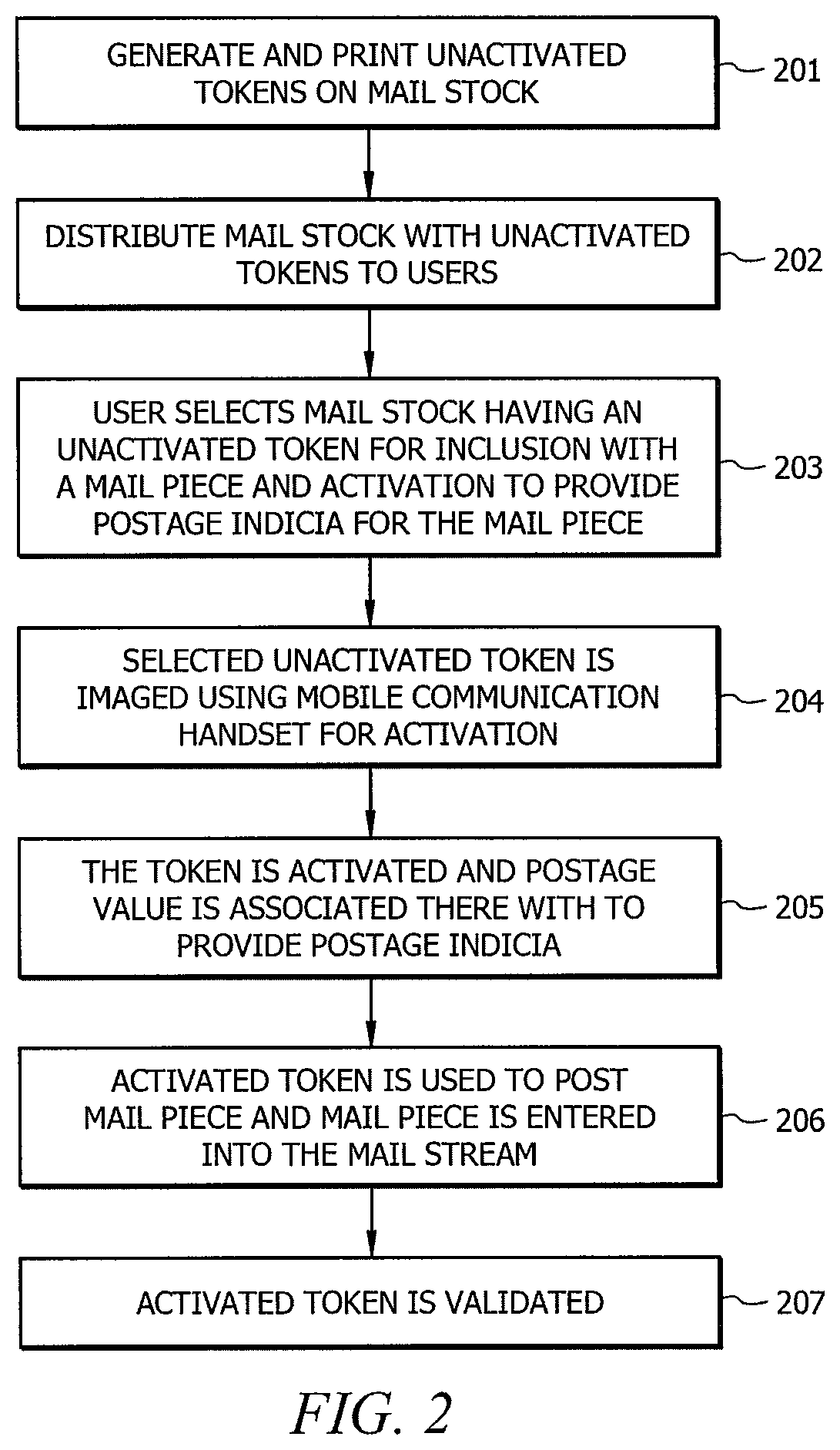
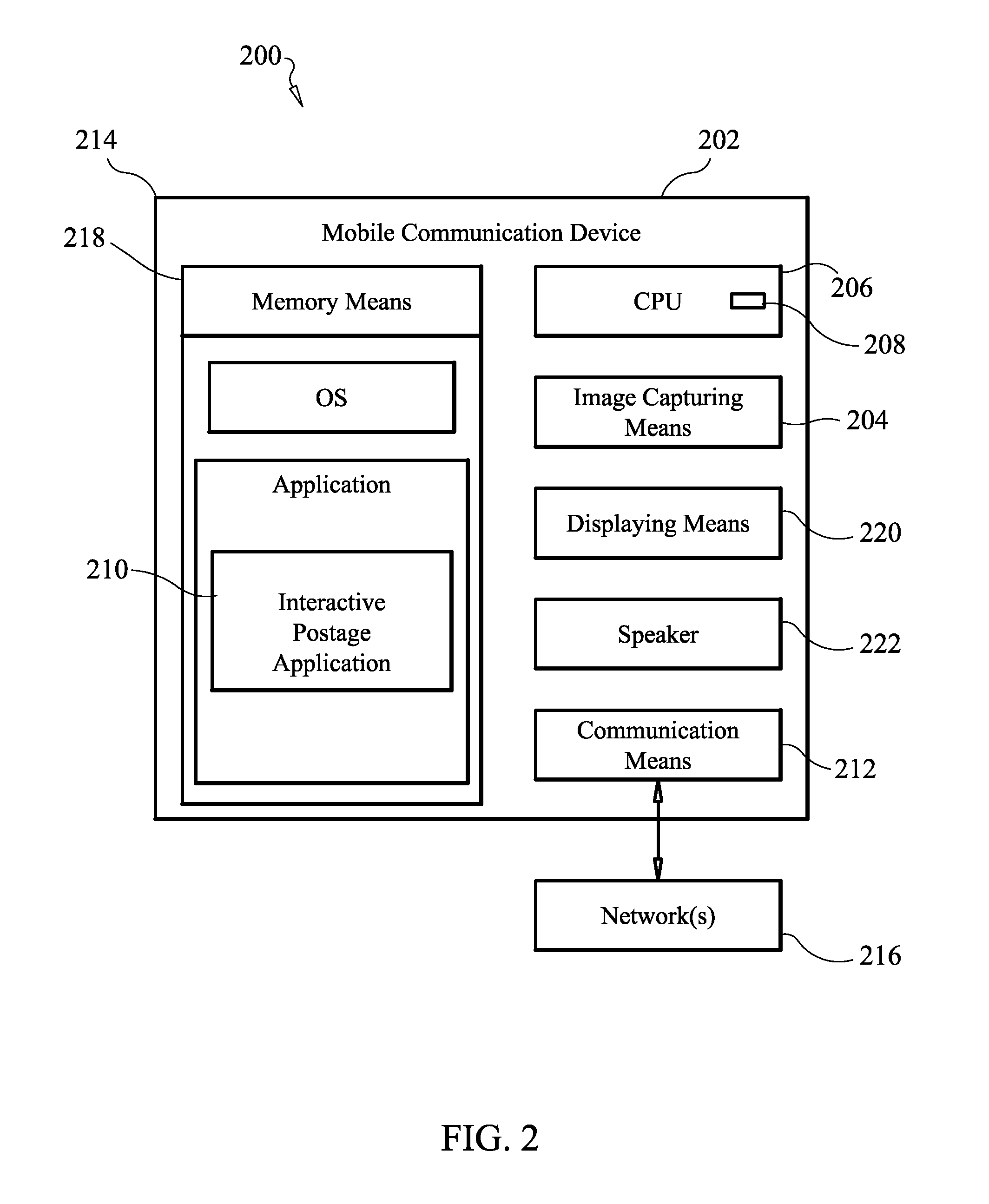
Systems and methods using mobile communication handsets for providing postage
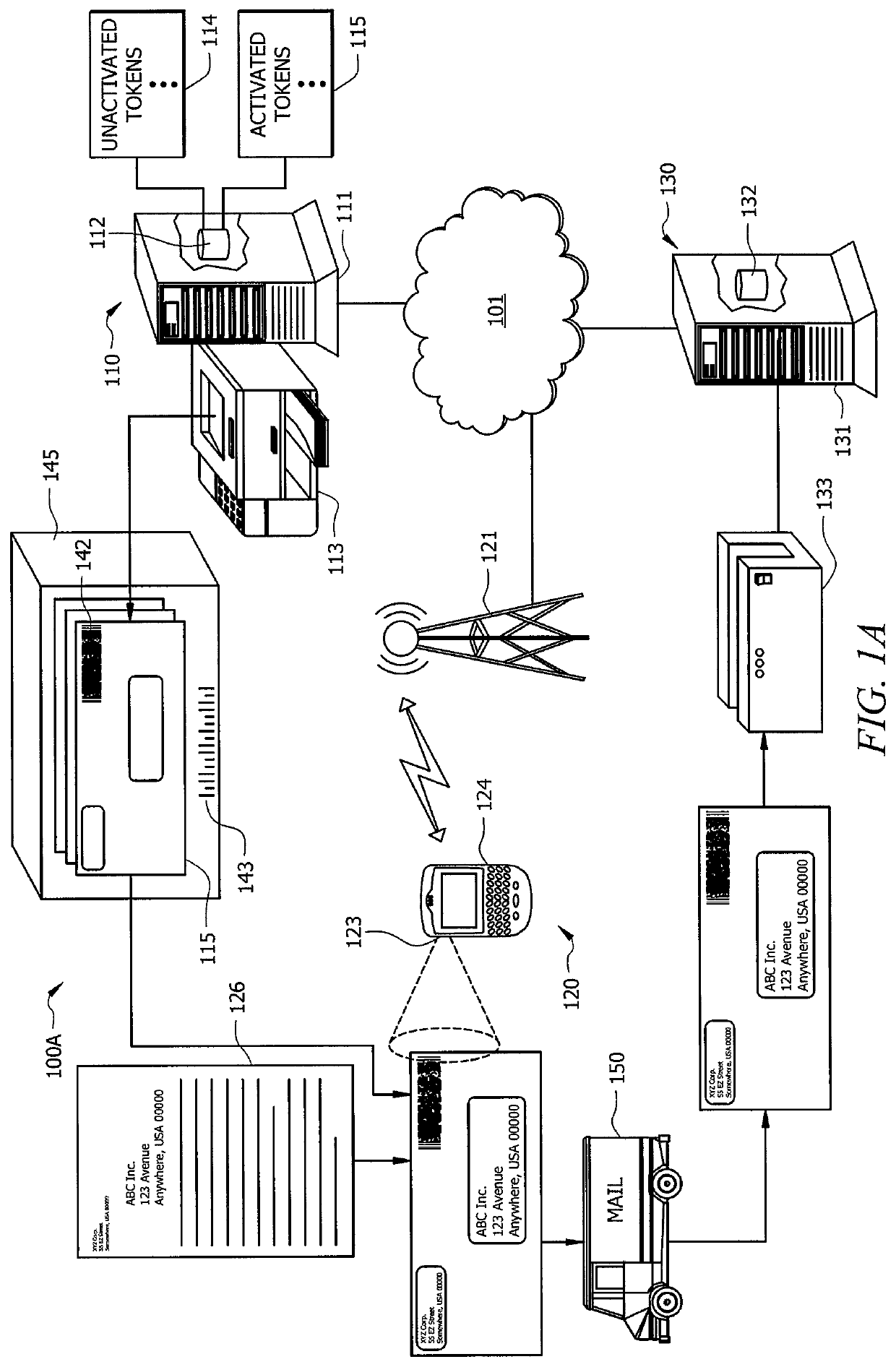
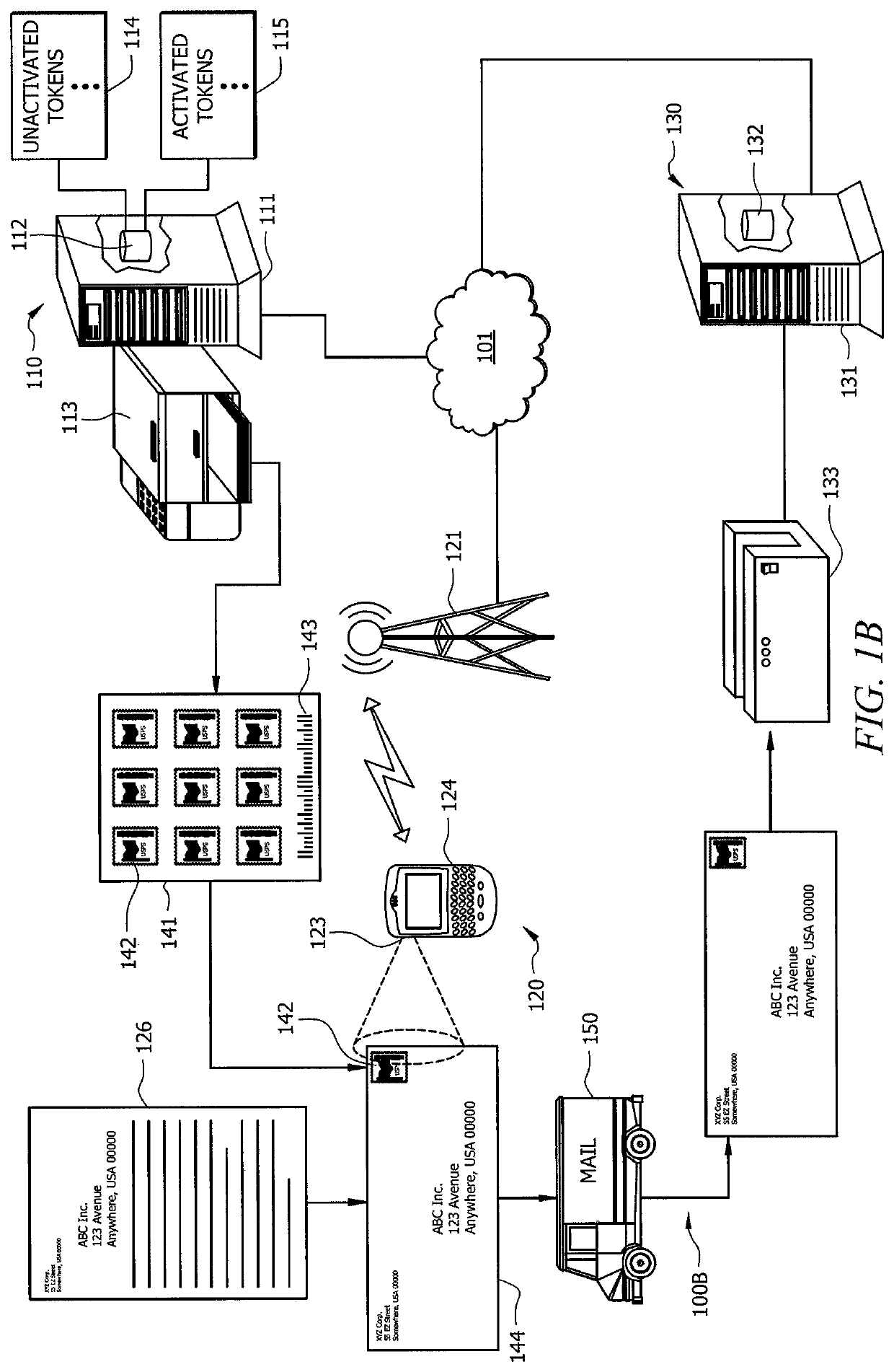
Systems and methods which provide postage indicia using mobile communication handsets are shown. According to embodiments, users are enabled to introduce mail pieces into a mail delivery stream which are accepted as having activated, value comprising postage indicia associated therewith without the use of traditional metering systems, processor-based postage generation and printing systems, or even printers. Instead, a token comprising substantially unique identification information identifying a mail piece is activated as an activated token having postage value associated therewith using mobile communication handsets, such as a smart phone, network enabled personal digital assistant, etc. according to embodiments of the invention.
Owner:AUCTANE INC
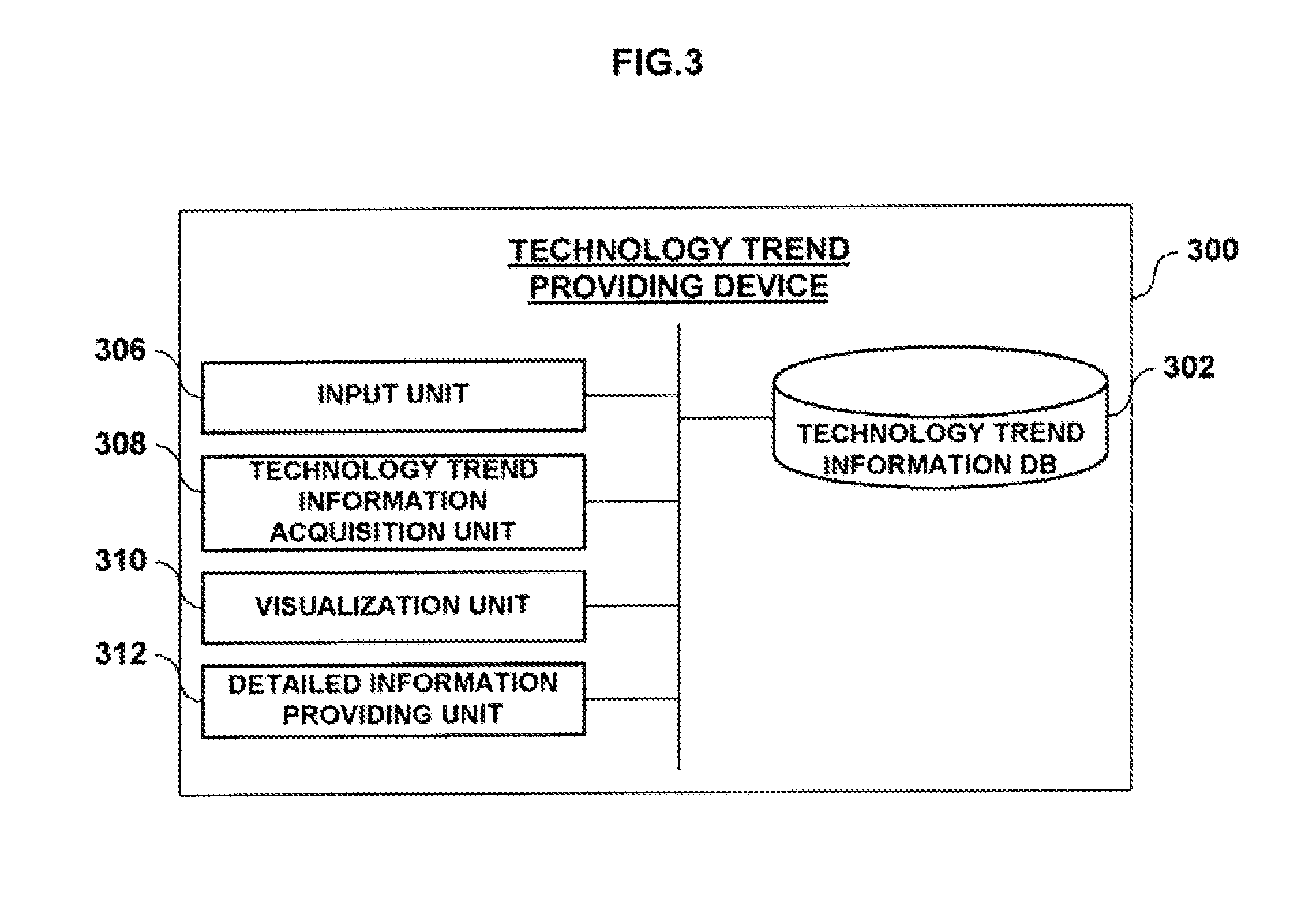
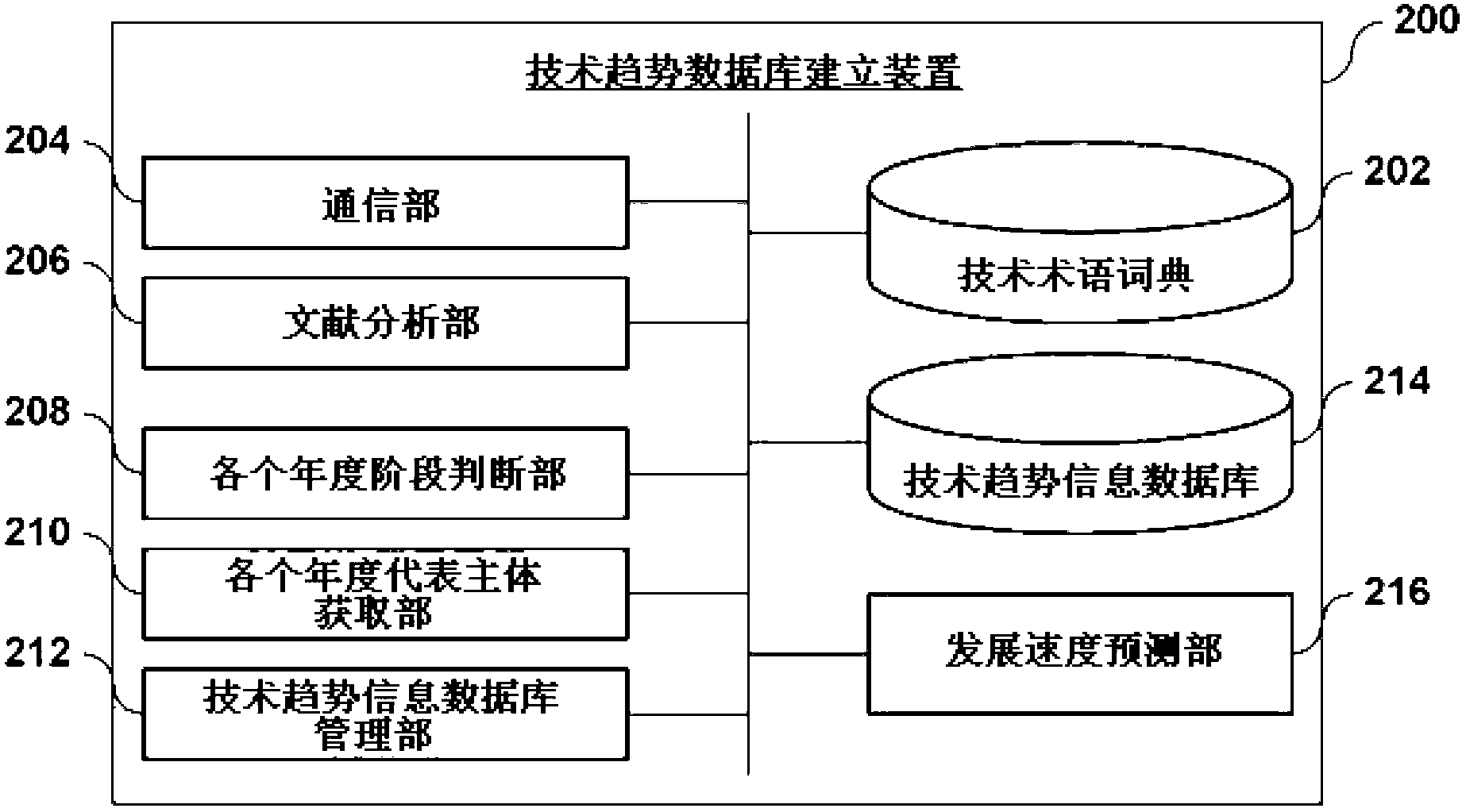
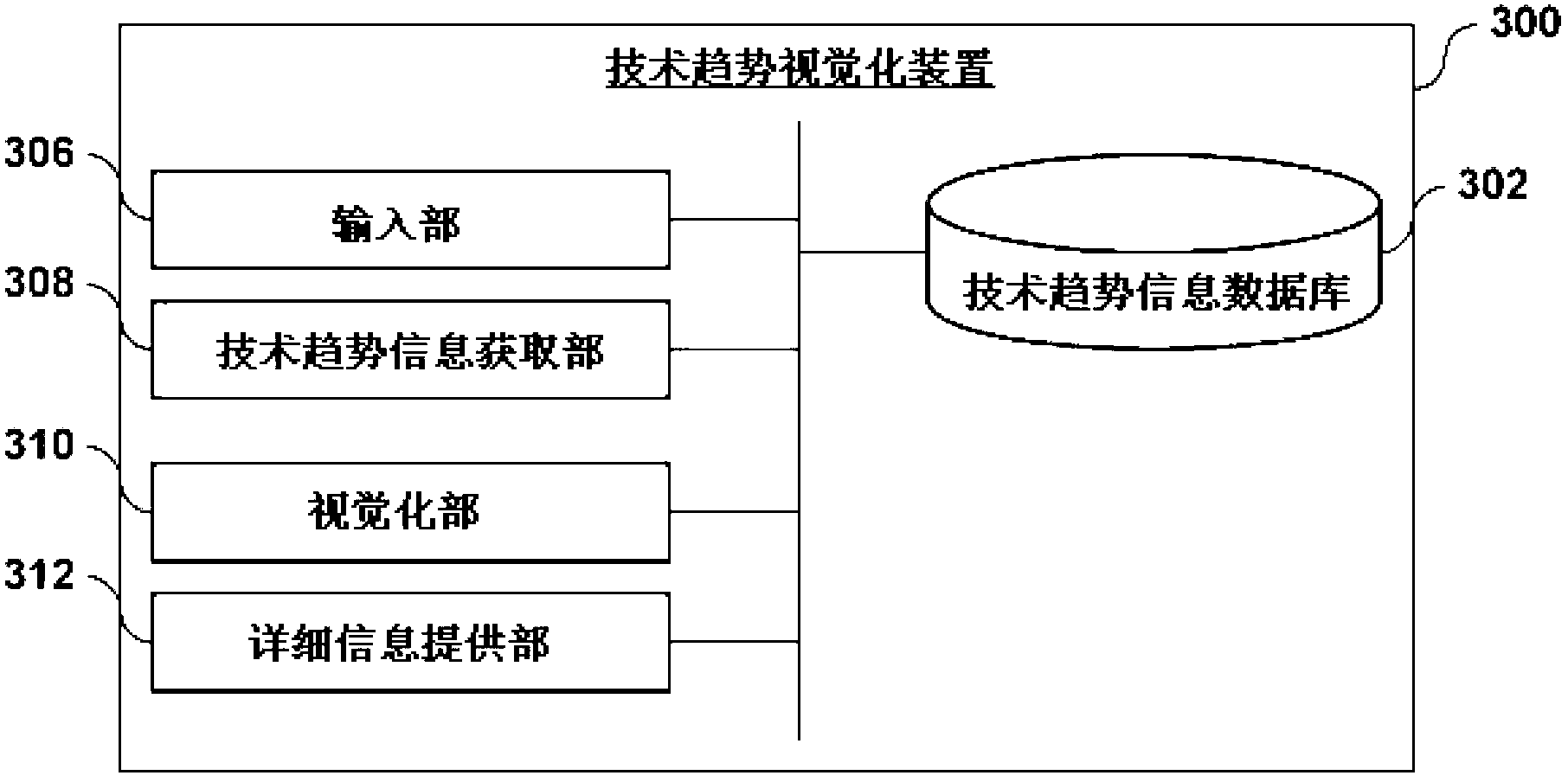
Method and system for porviding technology change using of technology life cycle graph
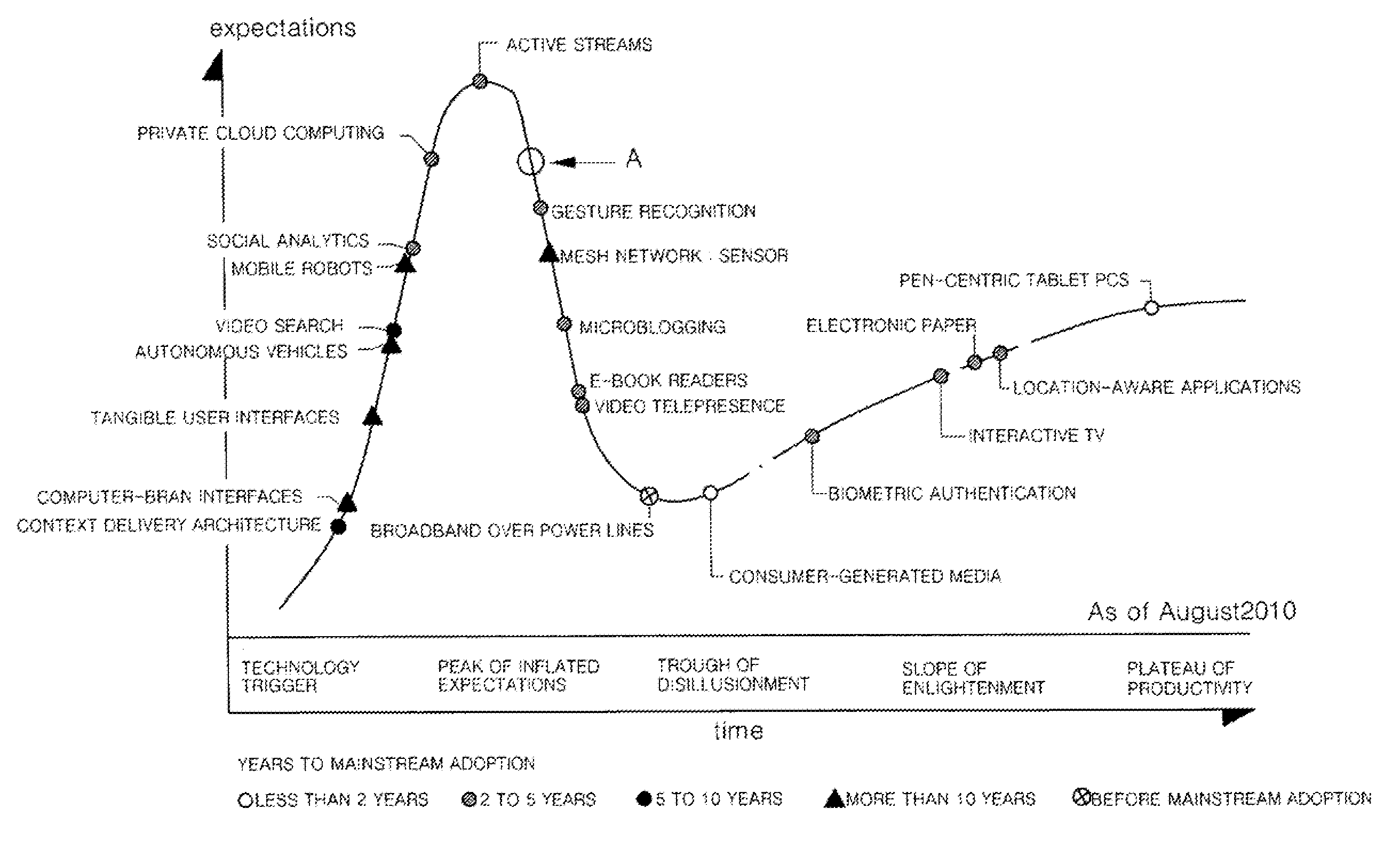
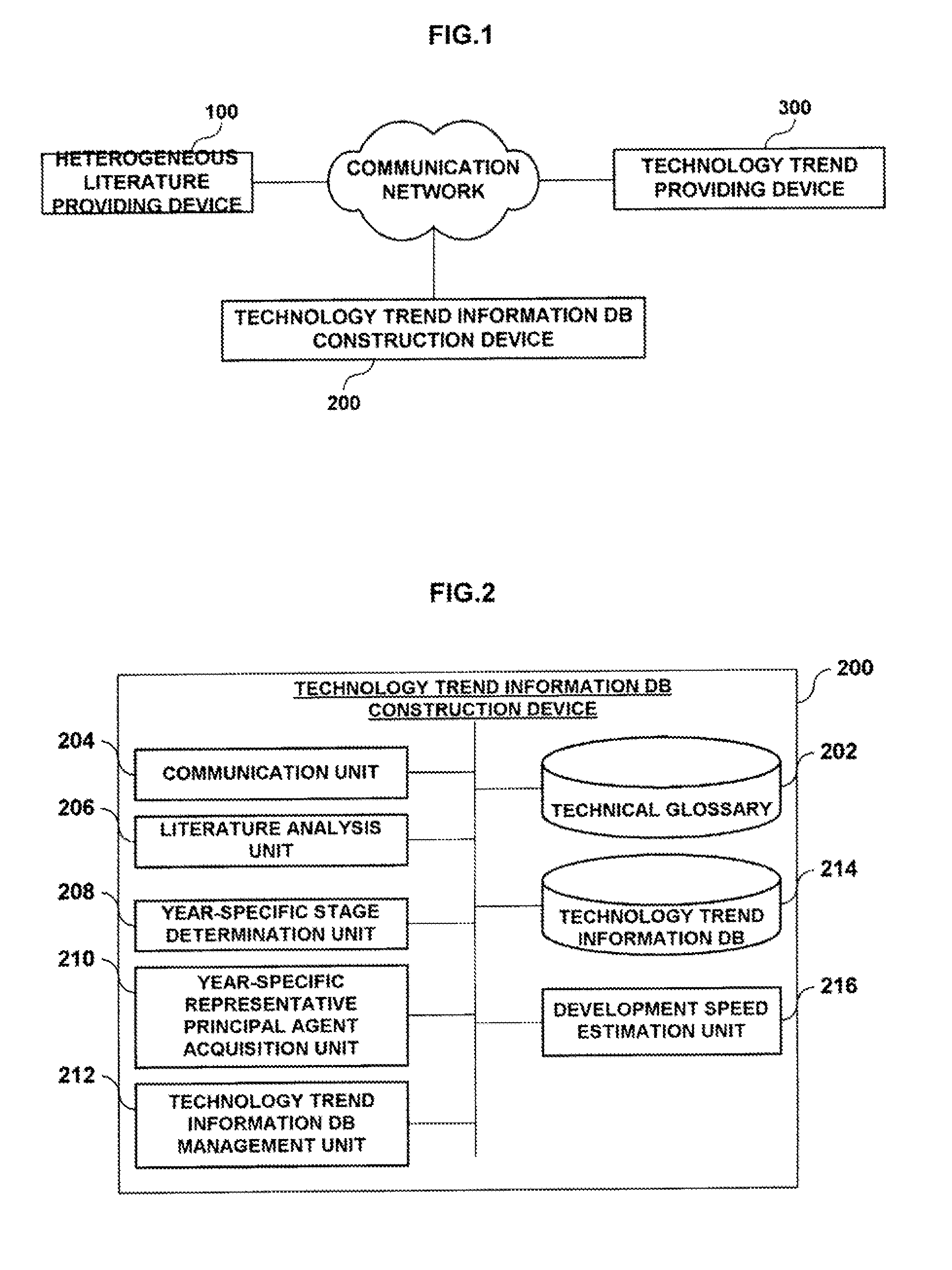
A technology development providing method using a technology life cycle graph and a system thereof are provided to obtain stages by year and representative items by year to display on the technology life cycle graph. A technology development information DB(Database) building device(200) builds a technology development information DB in which stages by year and representative items by year for each technology are stored to be displayed on a technology development life cycle graph. A technology development providing device(300) acquires stages by year and representative items by year for a specific technology displayed on the technology development life cycle graph. The technology development providing device displays acquired contents on the technology development life cycle graph.
Owner:KOREA INST OF SCI & TECH INFORMATION
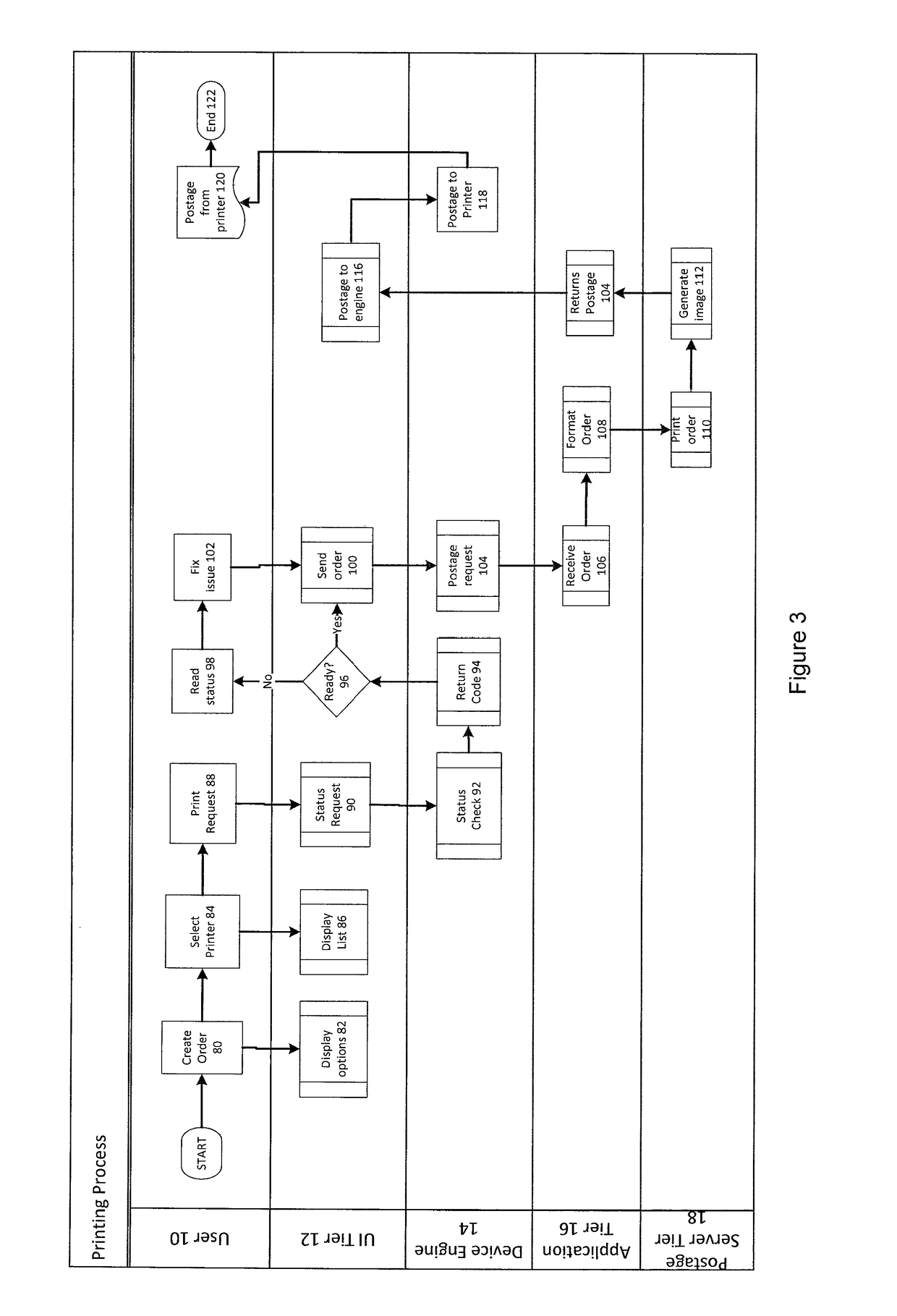
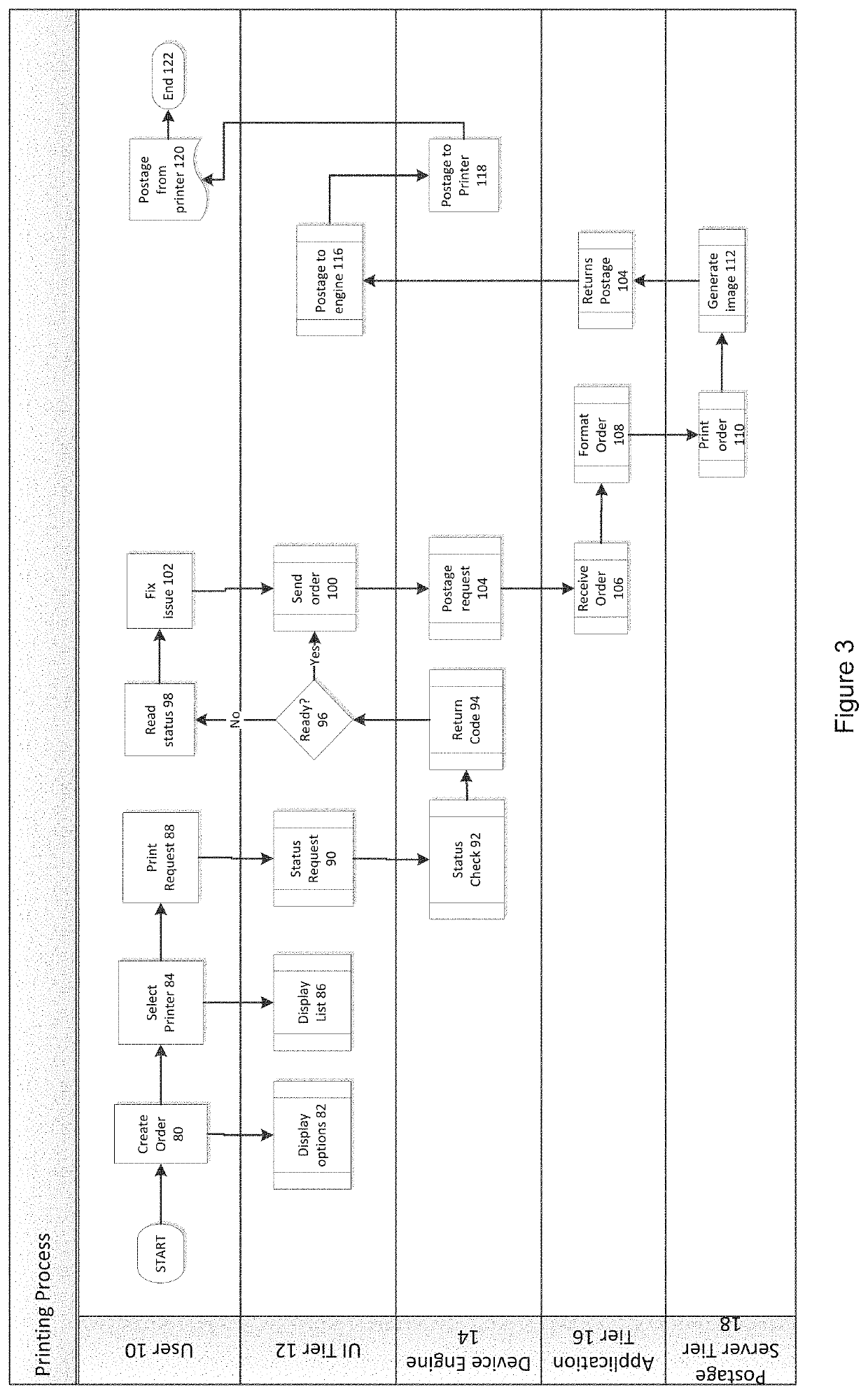
System and method for printing postage
ActiveUS10223736B1Postage metering systemBuying/selling/leasing transactionsSoftware engineeringFinancial transaction
A system and method for conducting a web-based postage transaction, includes receiving user credentials at a web server, validating the user credentials, and in response to valid credentials, providing access to a remote client to at least one module of a postage software application. The module is configured to execute requests to perform the web-based postage transaction and to, for each revenue generating request, perform a validation check. The validation check includes a requirement that the module have access to the web server for the request to be fulfilled. In an embodiment, the postage software application includes a module configured and arranged to determine the availability of a client-side device configured to execute the request to perform the web-based postage transaction and, when the client-side device is unavailable, to prevent execution of the request, and when the client-side device is available, to allow execution of the request.
Owner:PSI SYST
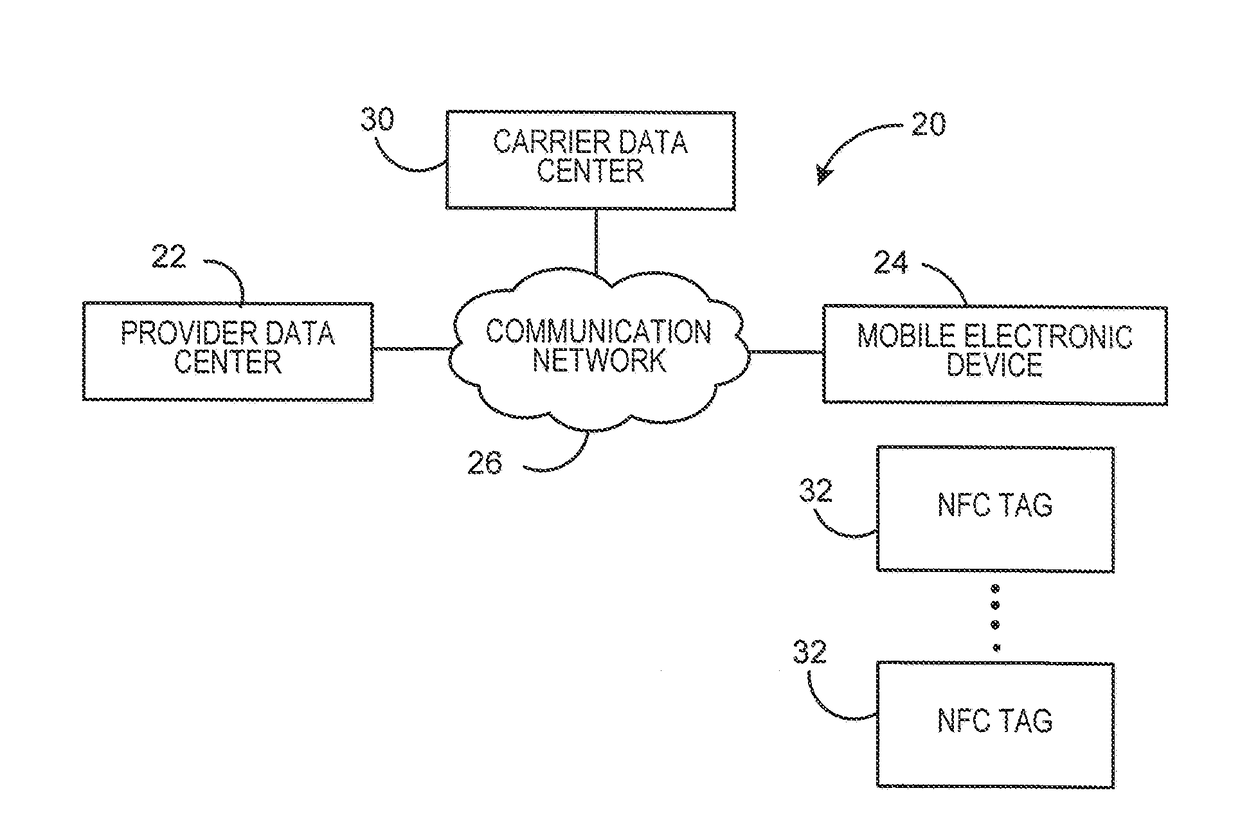
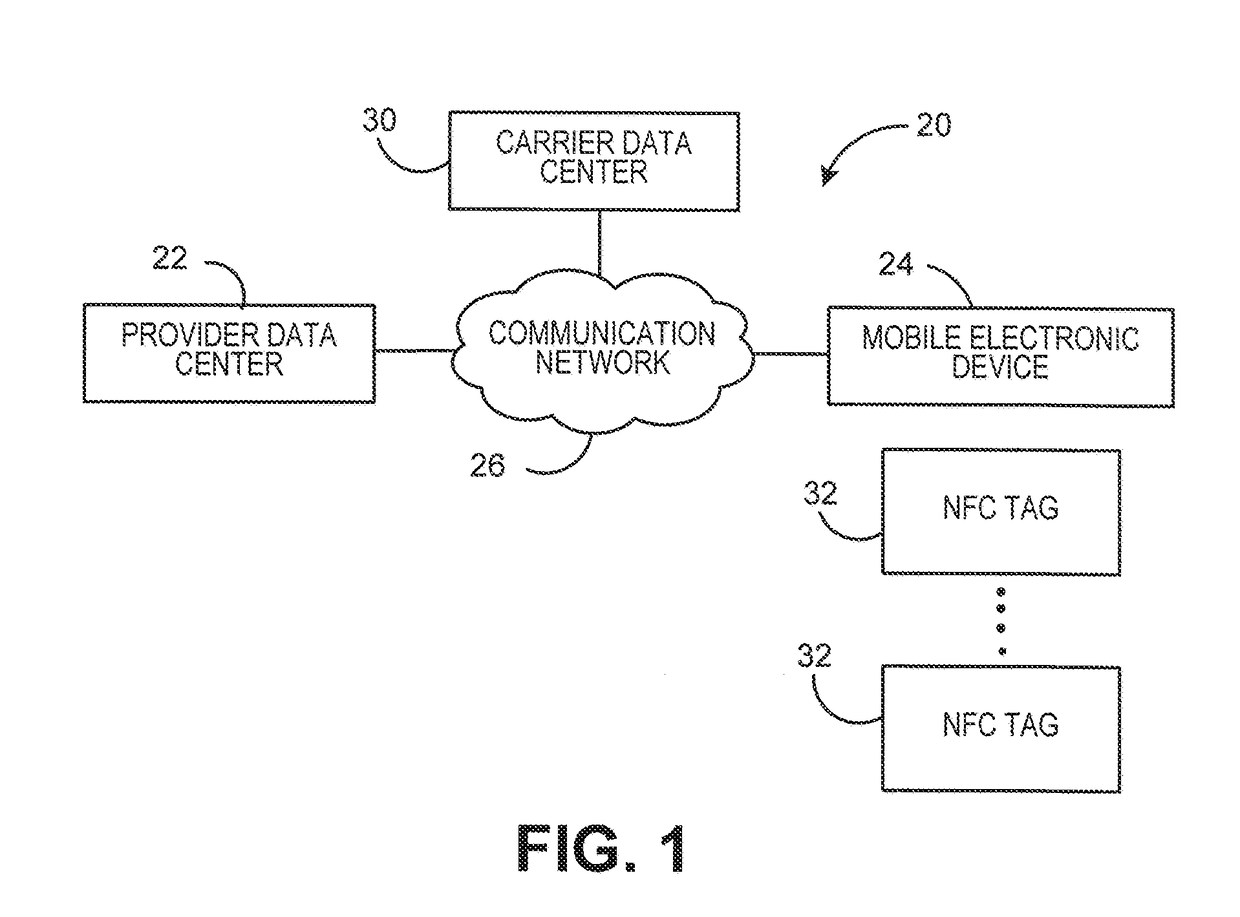
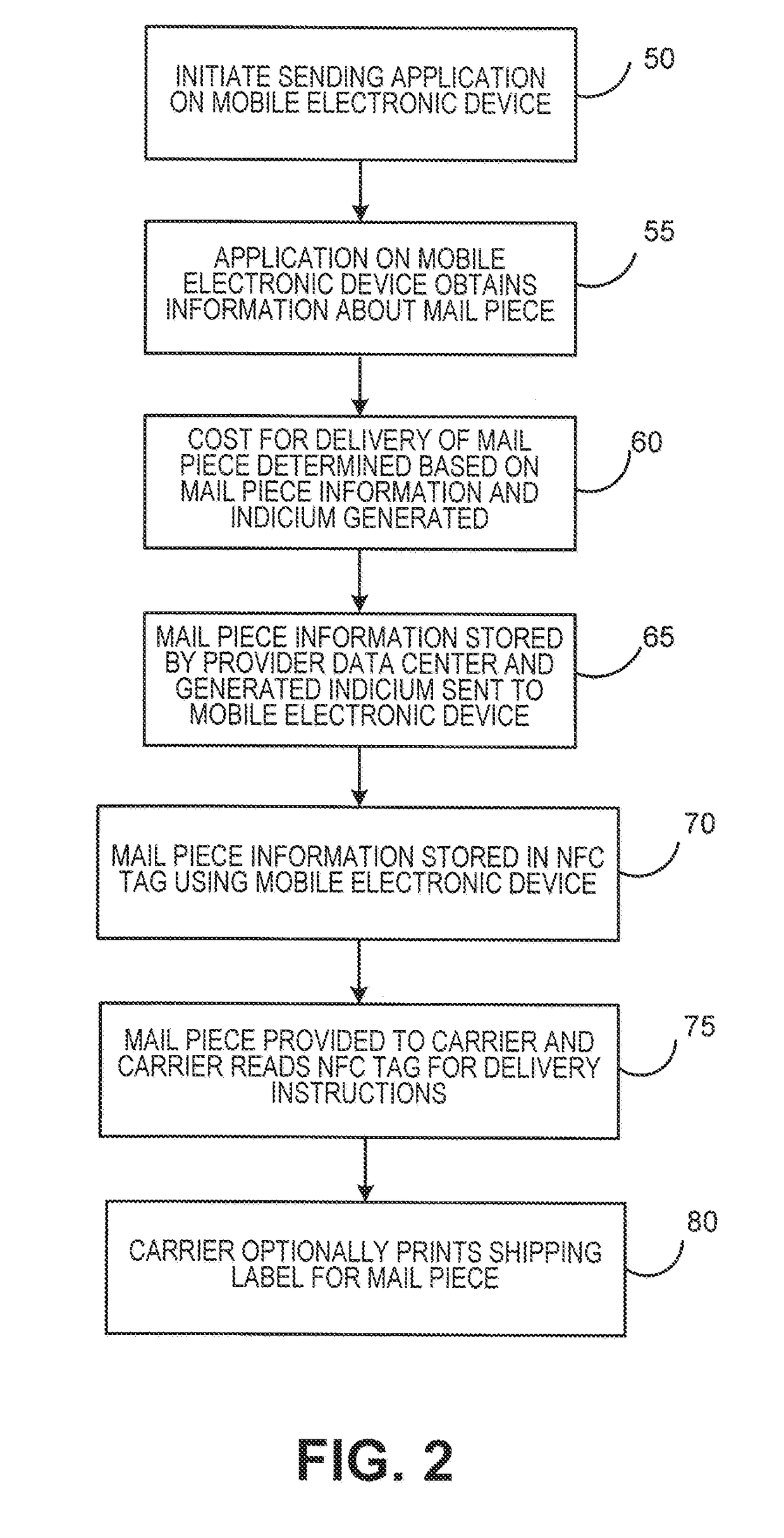
Generating and dispensing evidence of payment for delivery of a mail piece using a mobile device and NFC tag
A system and method for dispensing evidence of payment for delivery of a mail piece that does not require the user to have a printer readily available to print a label that includes the evidence of payment for delivery is provided. The mail piece sender utilizes a software application operating on a mobile electronic device to determine the cost for delivery of a mail piece. An indicium that evidences payment for the delivery of the mail piece is generated, and the mobile electronic device is utilized to program a Near Field Communication (NFC) tag that is adhered to the mail piece. When the mail piece is received by a carrier, the carrier can read the information stored in the NFC tag to process and deliver the mail piece. Optionally, the carrier can print a label based on the information obtained from the NFC tag for adhering to the mail piece.
Owner:PITNEY BOWES INC
System and method for identifying and preventing on-line fraud
The present invention is directed to systems and methods which identify fraudulent situations during the transaction phase. In one embodiment, such detection is accomplished by monitoring for situations either outside the range of normal for the general population or outside the range of normal for this particular user. The normal range could be rule driven and, for example, could include size of a given purchase, frequency of purchases, identity of use equipment being utilized for the current transaction, etc. The rule could be relaxed or tightened, at least in part, based on the length of time that the user has been a customer and the user's past payment history. In one embodiment, device ids are used to detect fraudulent users. These device (or software) ids could, for example, be a “fingerprint” of the user's equipment, or a “cookie” previously downloaded to the user that identifies the user to the fulfillment system. In situations where fraud is detected downloading the value to the user is interrupted.
Owner:AUCTANE INC
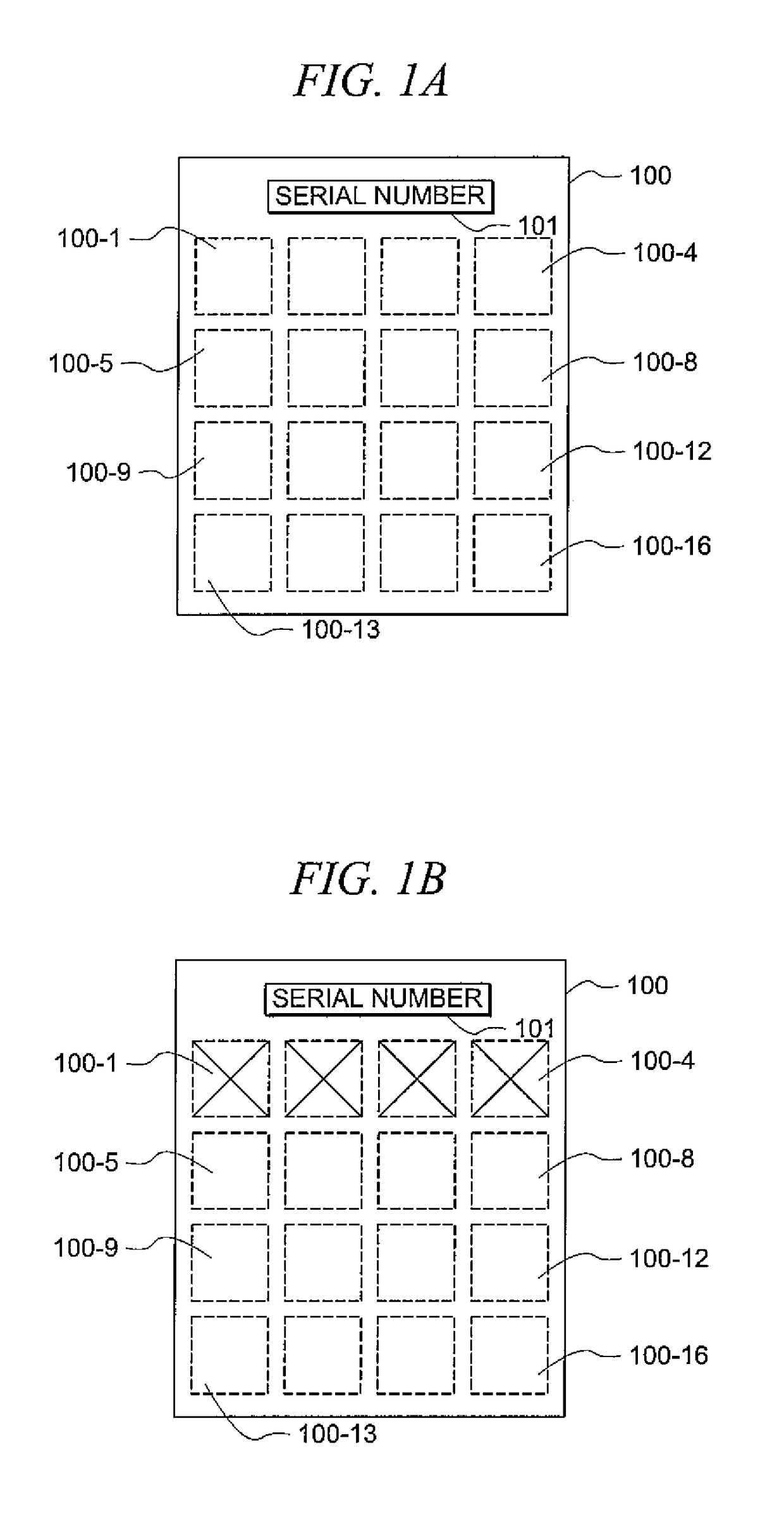
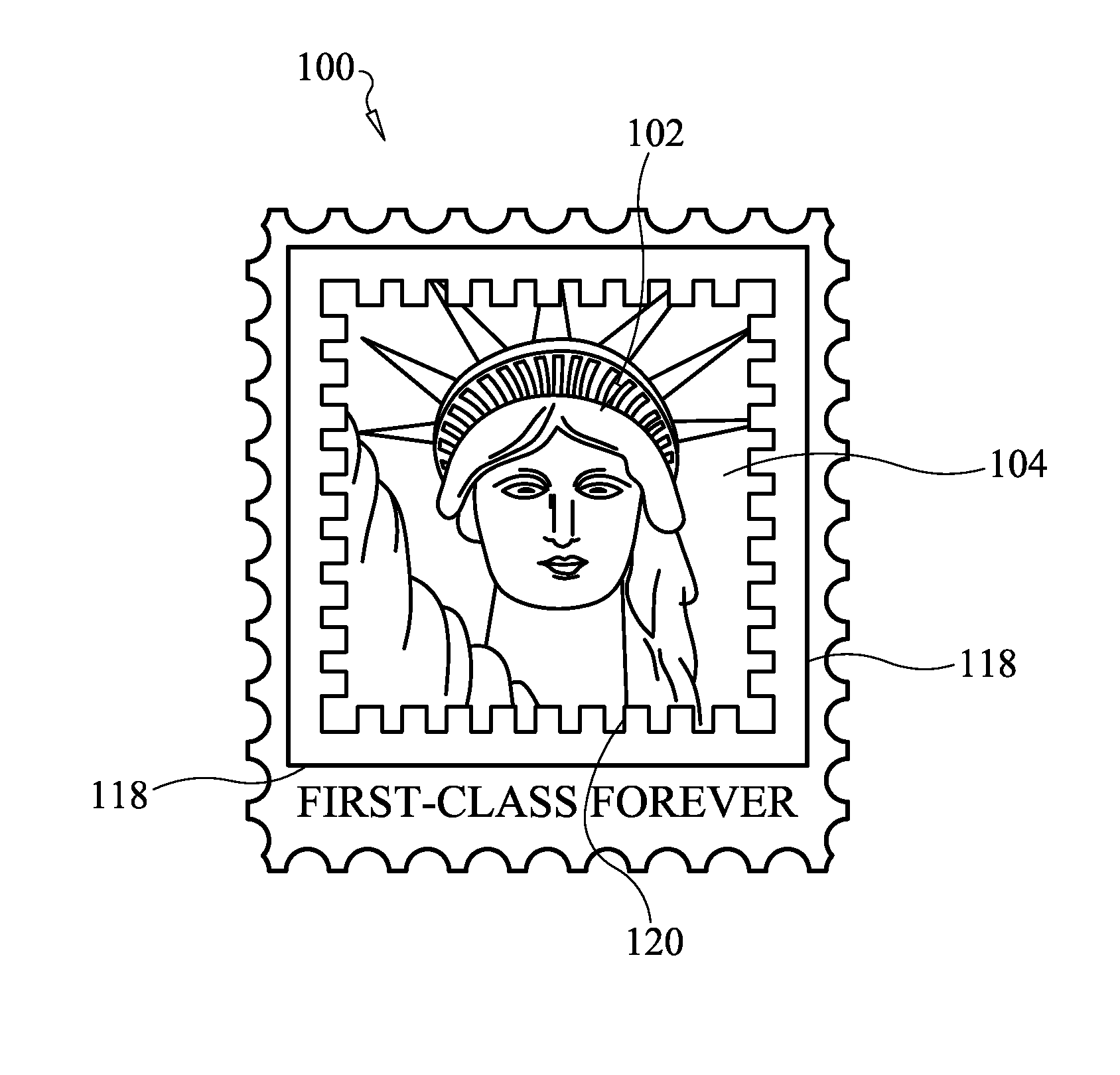
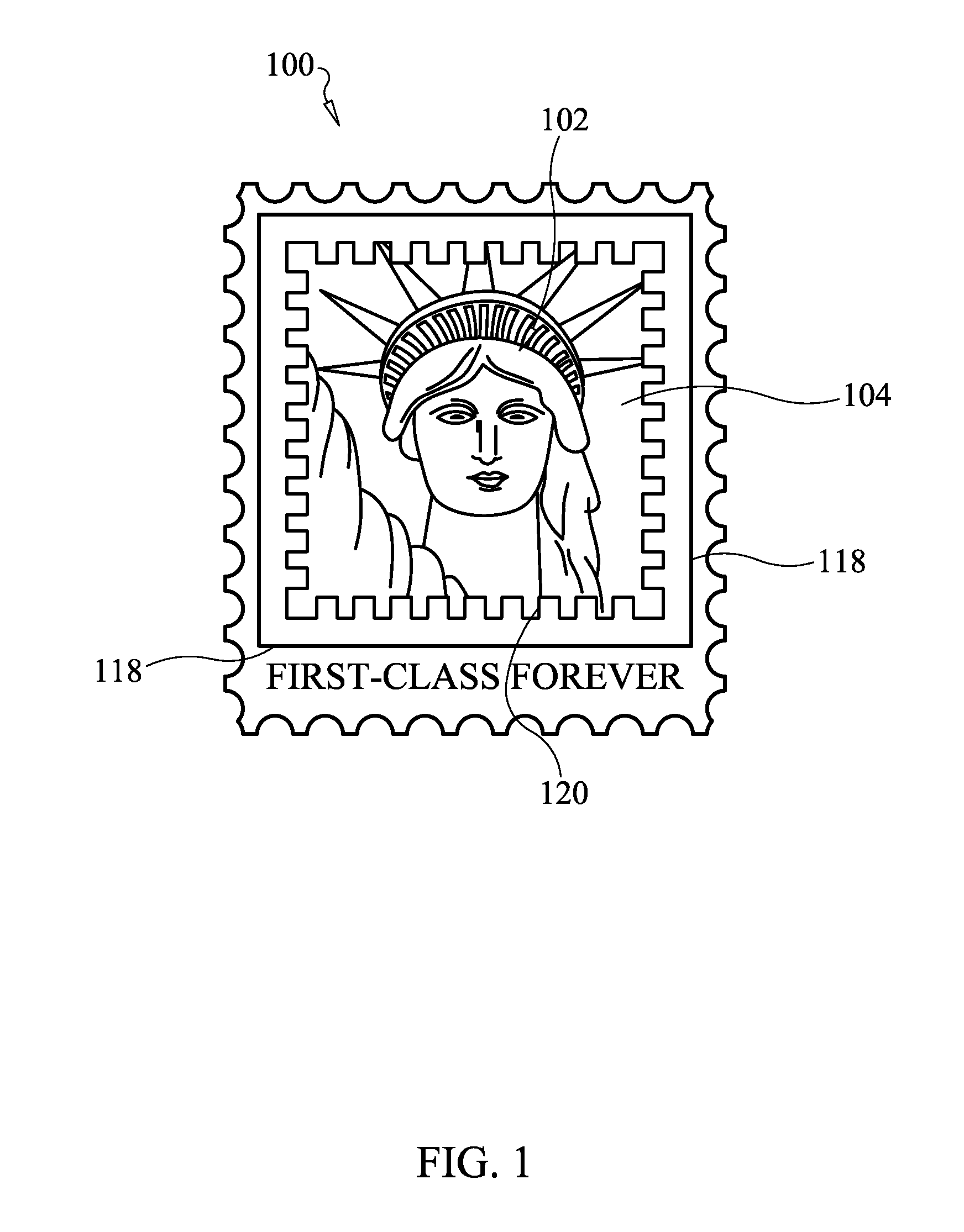
Apparatus, system and method of transmitting multimedia communications using printed stamps
An interactive postage stamp displayable on a mail item 102 evidencing payment of postage, and represented by an encoded image framed by an interactive frame that includes at least one embedded icon activated by scanning the interactive frame causing the activation of the at least one embedded icon, where upon activation the at least one embedded icon may be engaged for accessing the multimedia content linked to the interactive postage stamp, and for controlling the review of the multimedia content using control commands represented by the activated at least one embedded icon or at least one hyperlink within the activated interactive frame.
Owner:ISAAC DANIEL INVENTORSHIP GRP LLC
High volume serialized postage at an automated teller machine or other kiosk
A system and method for retrieving a plurality of indicia are described. The method includes receiving, by a computer system associated with a postage provider a request from a user, the request including a number of the plurality of indicia, and a monetary value of each of the plurality of indicia; and authenticating the request. The method further includes verifying whether sufficient funds exist in an account of the user for the number and monetary value of the plurality of requested indicia. If the request is found authentic and the computer system determines that sufficient funds exist in the account of the user for the number and monetary value of the requested indicia, extracting the plurality of indicia. The method further includes assembling in a return message the plurality of indicia as at least one binary data message; and transmitting the message to a computer associated with the user.
Owner:PSI SYST
System and method for identifying and preventing on-line fraud
The present invention is directed to systems and methods which identify fraudulent situations during the transaction phase. In one embodiment, such detection is accomplished by monitoring for situations either outside the range of normal for the general population or outside the range of normal for this particular user. The normal range could be rule driven and, for example, could include size of a given purchase, frequency of purchases, identity the equipment being utilized for the current transaction, etc. The rule could be relaxed or tightened, at least in part, based on the length of time that the user has been a customer and the user's past payment history. In one embodiment, device ids are used to detect fraudulent users. These device (or software) ids could, for example, be a “fingerprint” of the user's equipment, or a “cookie” previously downloaded to the user that identifies the user to the fulfillment system. In situations where fraud is detected downloading the value to the user is interrupted.
Owner:AUCTANE INC
Preventing the fill of ineffective or under-effective medications through integration of genetic efficacy testing results with legacy electronic patient records
ActiveUS11398312B2Improve usabilityPrevent cost and complexityDrug and medicationsOffice automationMedical recordDispensary
Owner:XACT LAB LLC
Systems and methods facilitating shipping services rate resale
Owner:AUCTANE INC
System and method for printing postage
ActiveUS11037223B1Postage metering systemBuying/selling/leasing transactionsSoftware engineeringComputer access
In some embodiments, a web-based postage transaction may be facilitated. In some embodiments, an applet embedded on a web page may be provided to a client computer in response to the client computer accessing the web page. A request related to a postage transaction may be received from the client computer. In response to the request, a validation check may be performed by providing a validation token to the embedded applet at the client computer to be validated by the embedded applet. Based on a determination by the embedded applet at the client computer that the validation token is valid, the embedded applet at the client computer is configured to execute at least a part of the request.
Owner:PSI SYST
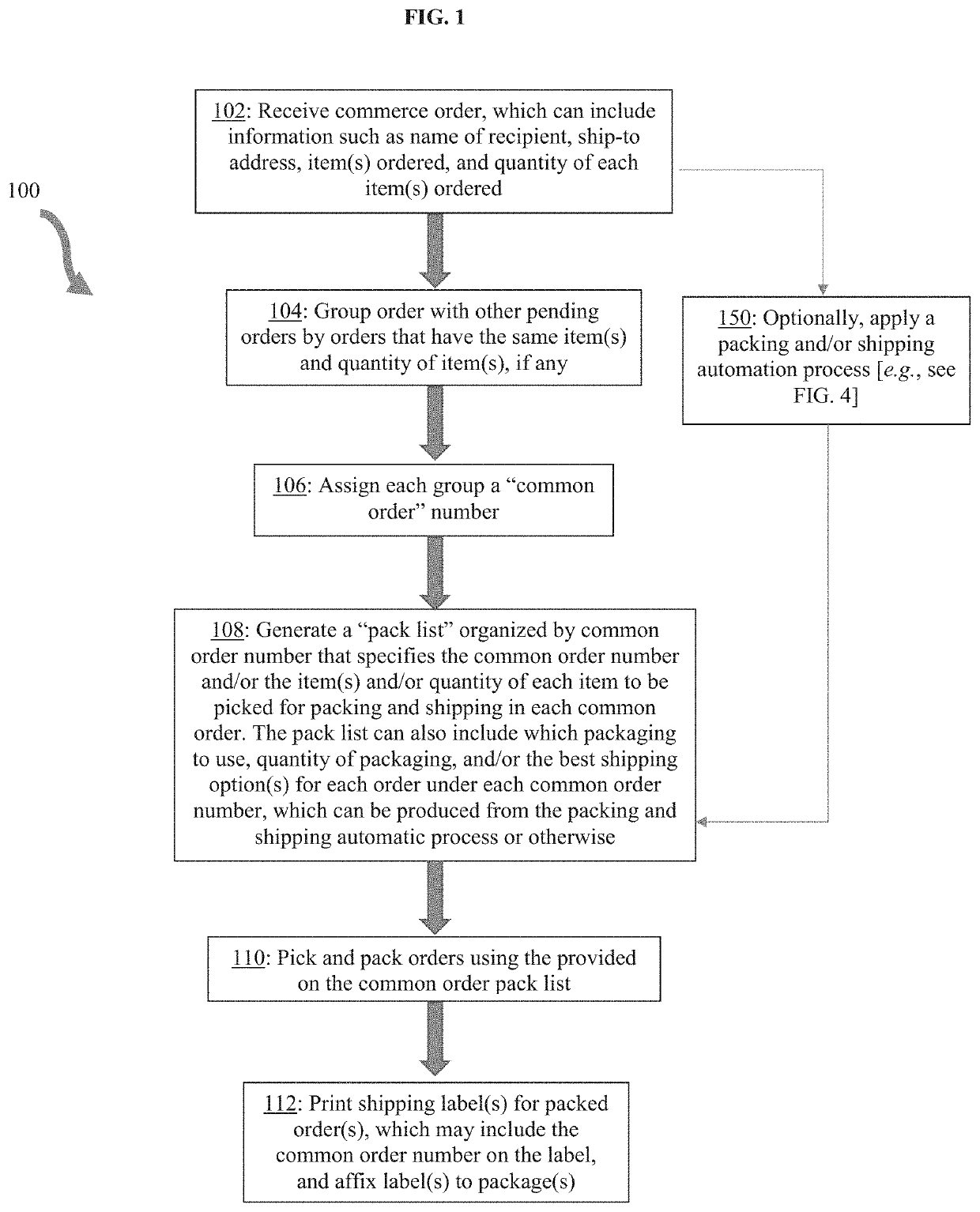
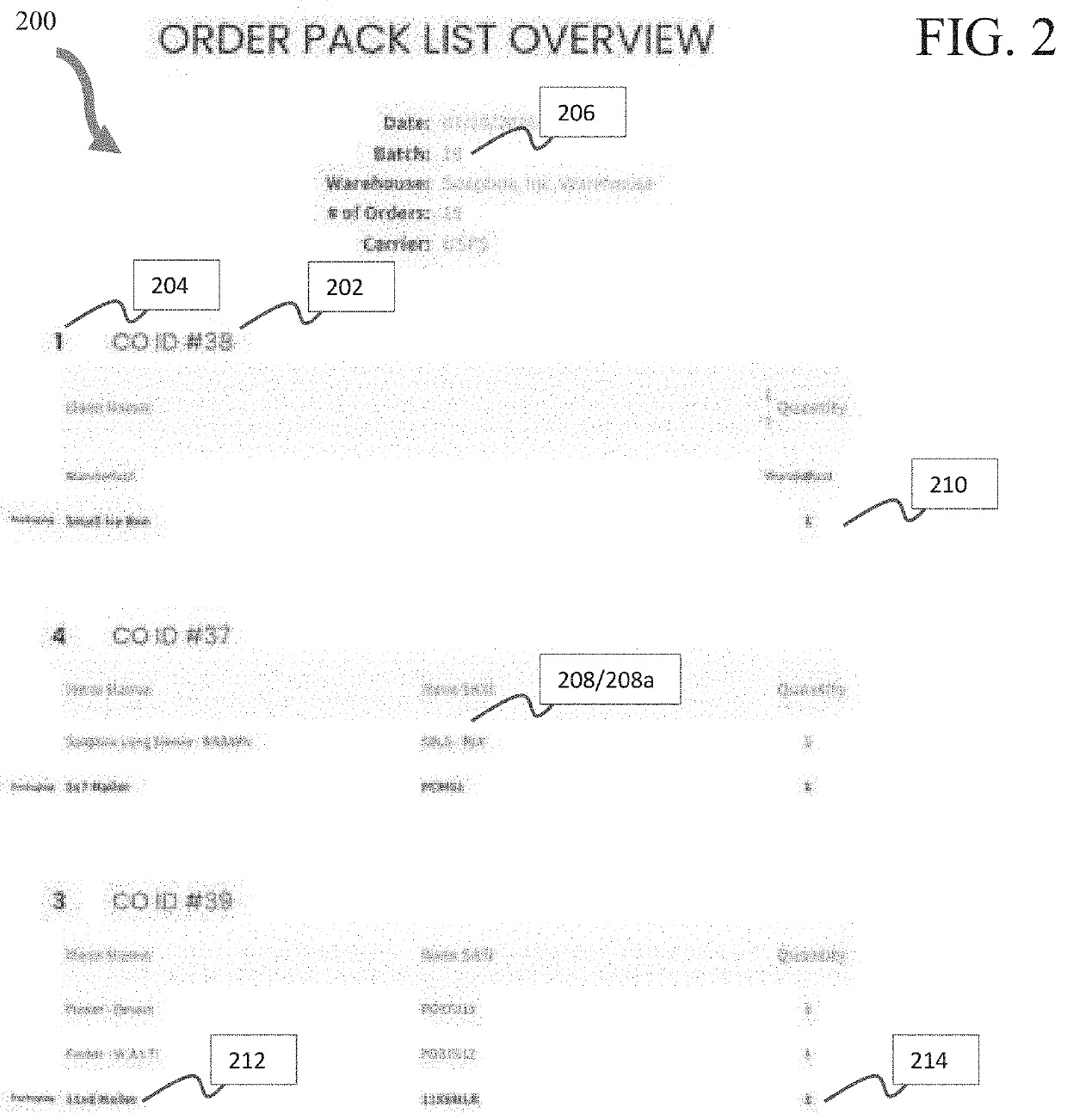
Systems and methods for order fulfillment, common order pack lists, multi-item order packing, and shipping rate automation
PendingUS20220083943A1Visual presentation using printersPostage metering systemOrder fulfillmentE-commerce
Owner:SOAPBOX SAAS INC
Method and system for delivering items
ActiveUS11416804B2Easy to optimizeReduce needPostage metering systemLogisticsSimulationDelivery location
A method for delivering a plurality of items to a plurality of delivery locations uses a mobile transport vehicle to transport a plurality of delivery robots to a first robot drop location. The robots are released at the first robot drop location and travel to assigned, respective delivery locations, which are in the vicinity of the first robot drop location. After completing delivery, each of the robots may proceed to a first robot pick-up location which may be different from the first drop off location. The robots are collected by a mobile transport vehicle and are transported to a second robot drop off location. While being transported, the robots can be reloaded with items for delivery in the vicinity of the second drop off location. A system may include one or more such mobile transport vehicles and a plurality of such robots, under the control of a server.
Owner:STARSHIP TECH OU
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com