Patents
Literature
37 results about "Procedure context" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
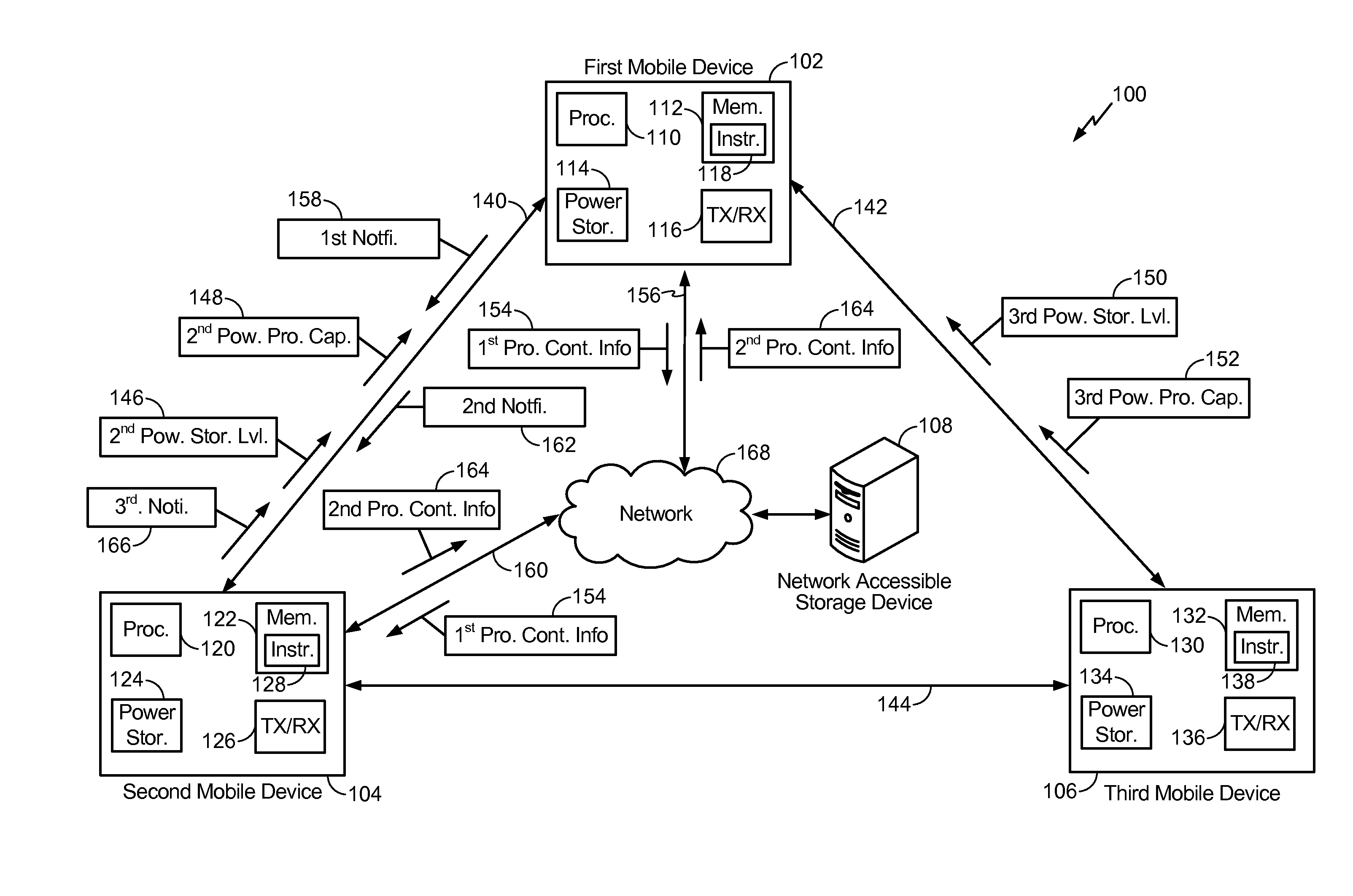
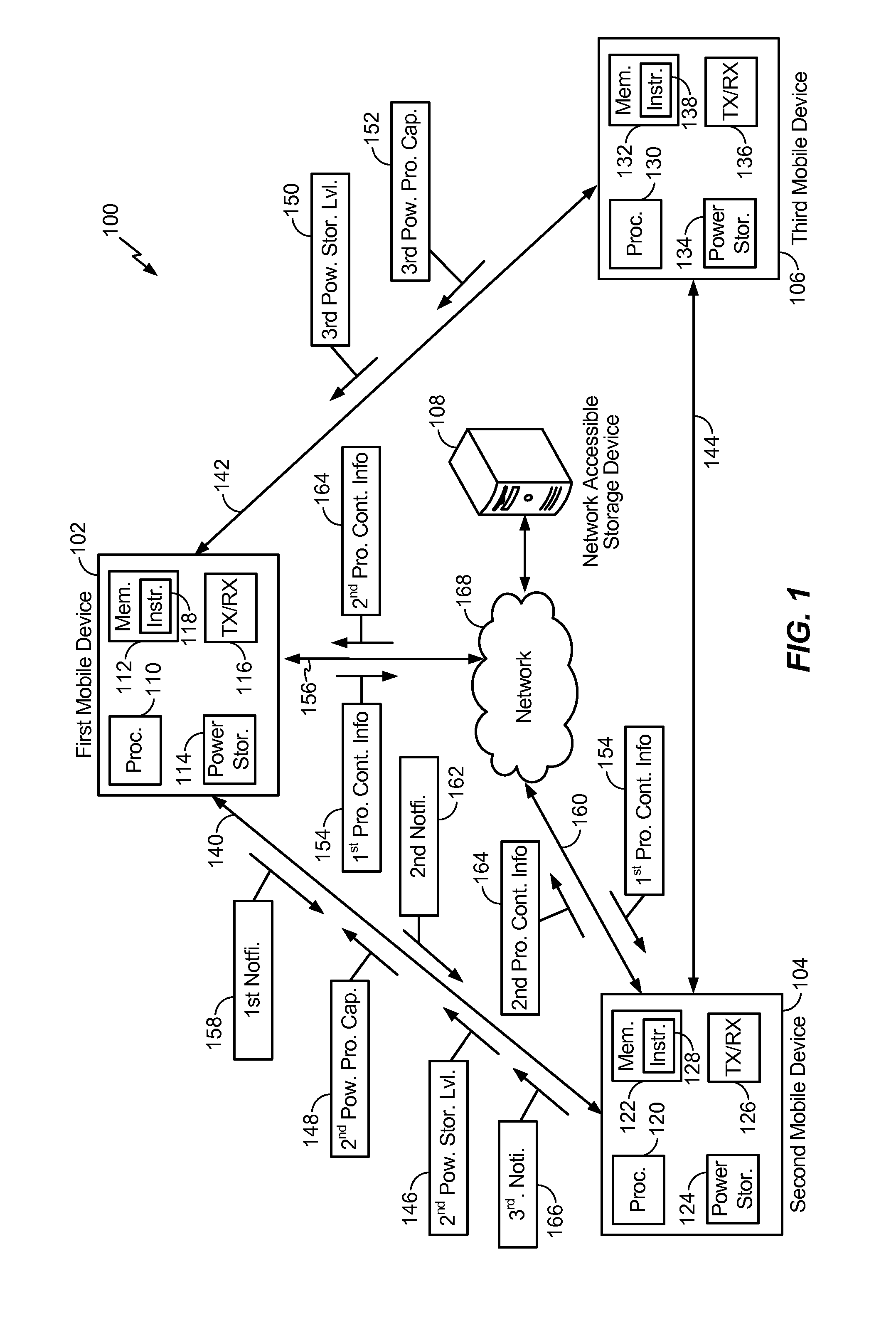
System and methods of transferring tasks from a first mobile device to a second mobile device
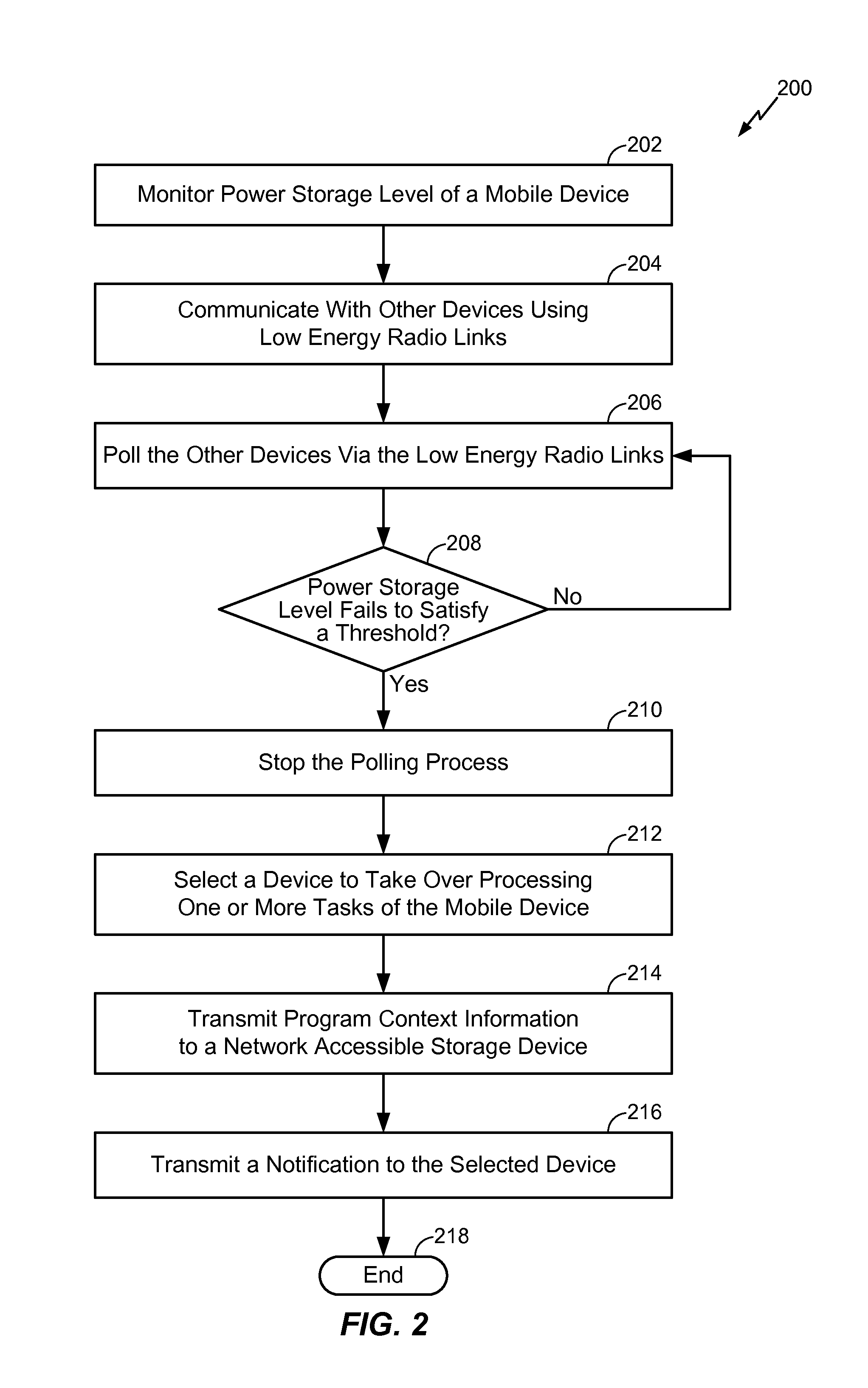
A method includes selecting a target mobile device based on information regarding a power storage level of the particular mobile device. The method further includes transmitting program context information associated with a task of the first mobile device to a network accessible storage device. The method further includes transmitting a notification regarding the program context information to the target mobile device. The present disclosure describes a power and task (data and / or voice) handover system that enables a user to transfer task(s) from one mobile device to another mobile device using a network (wired or wireless) based handover scheme.
Owner:QUALCOMM INC
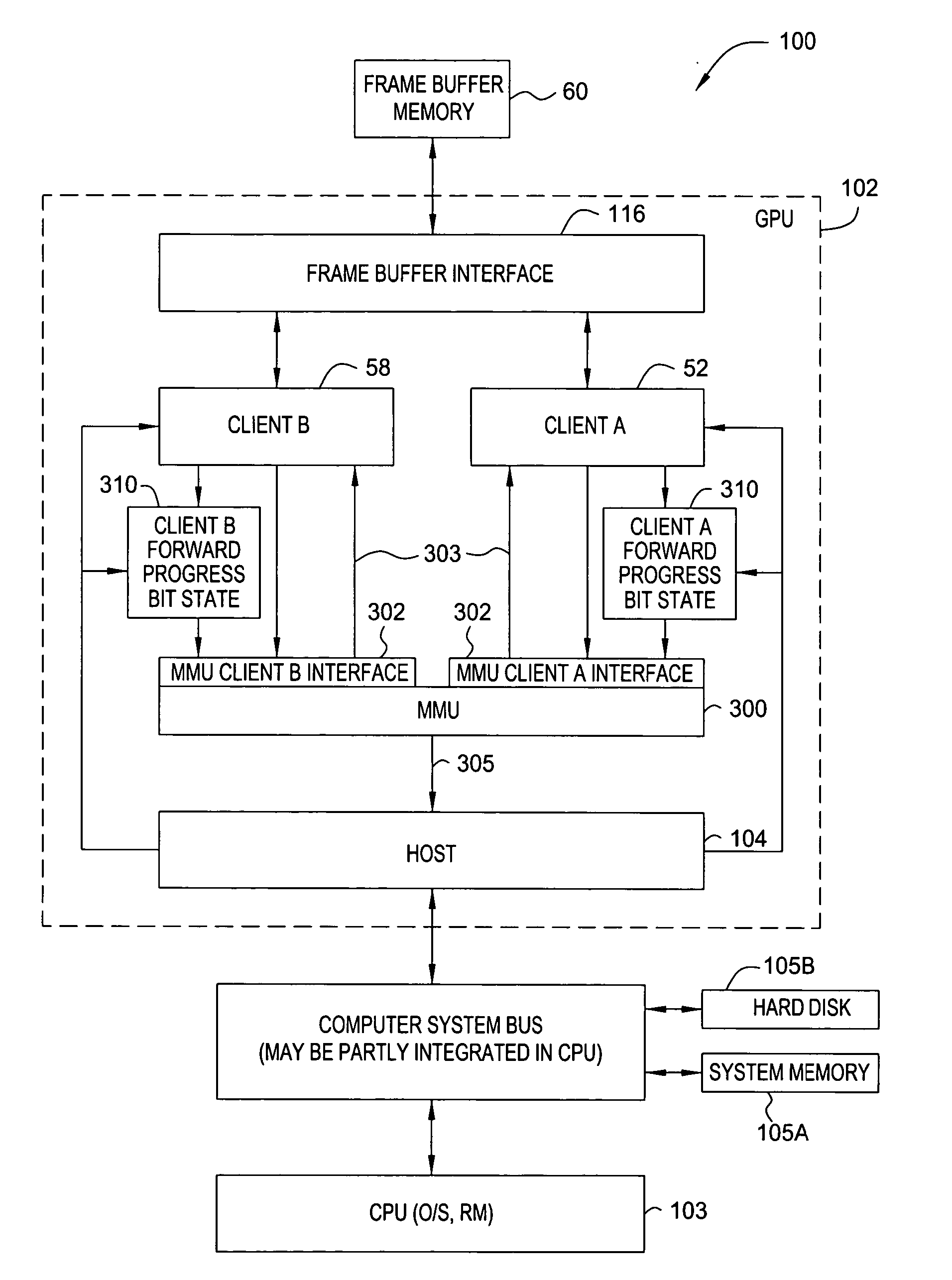
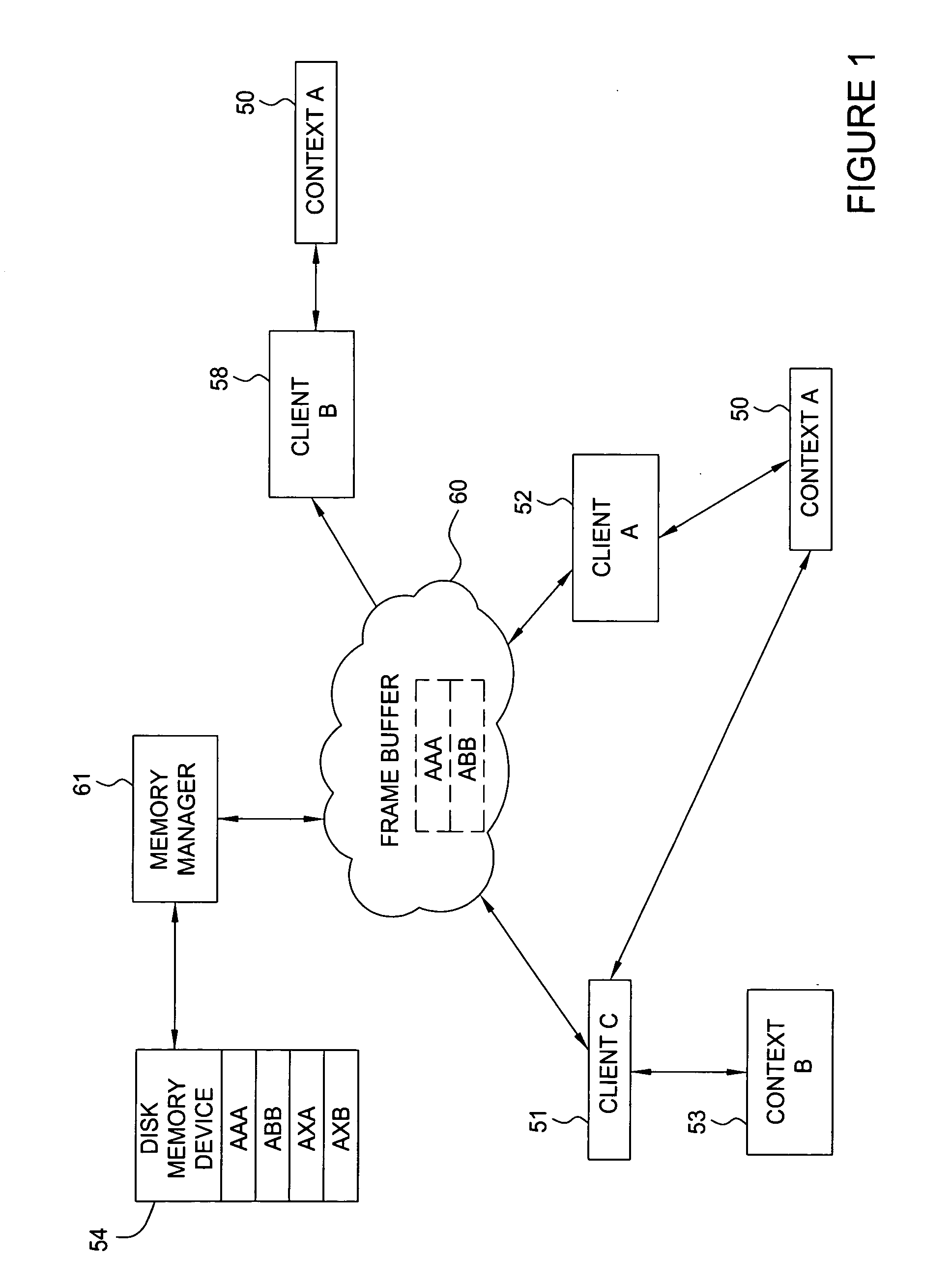
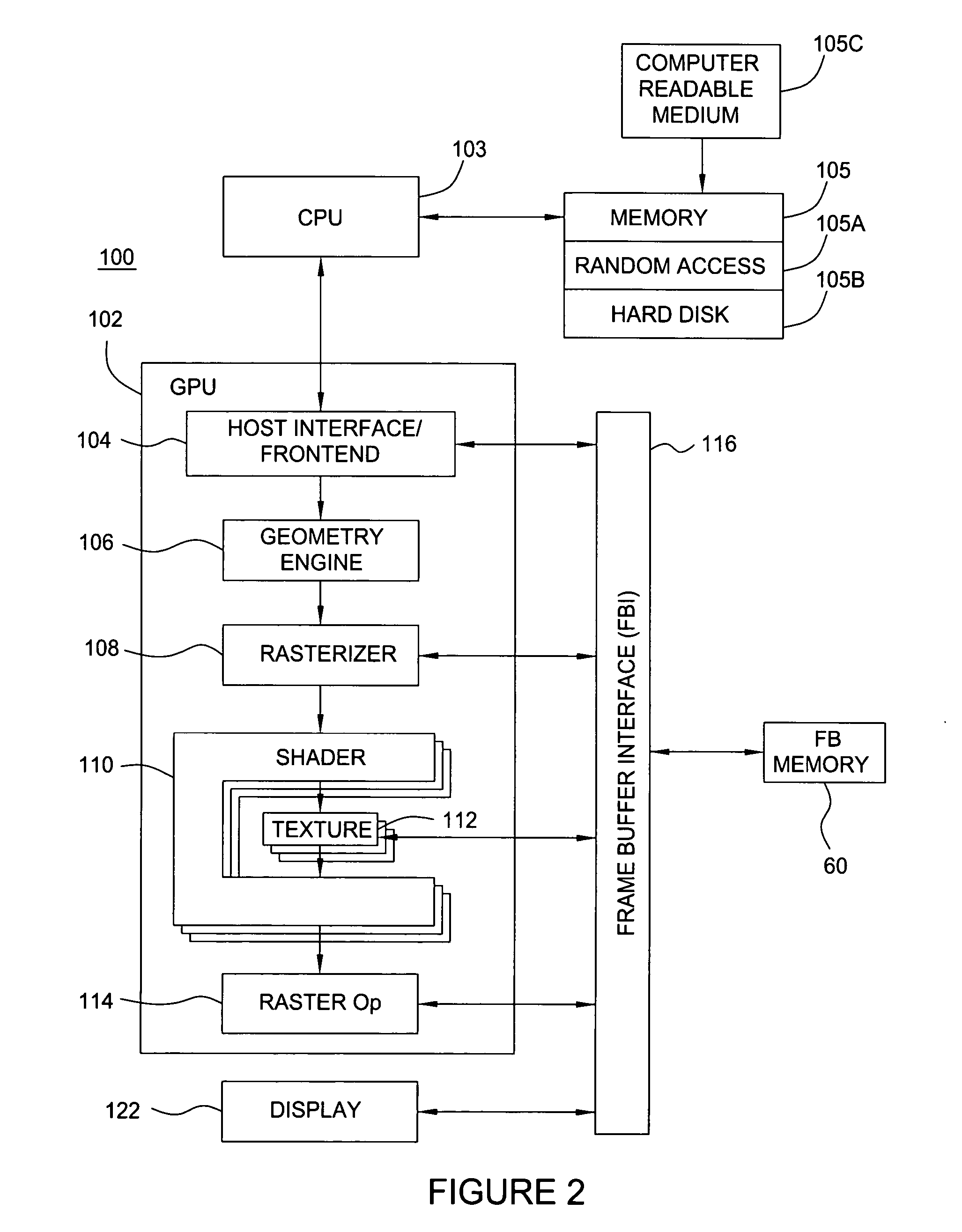
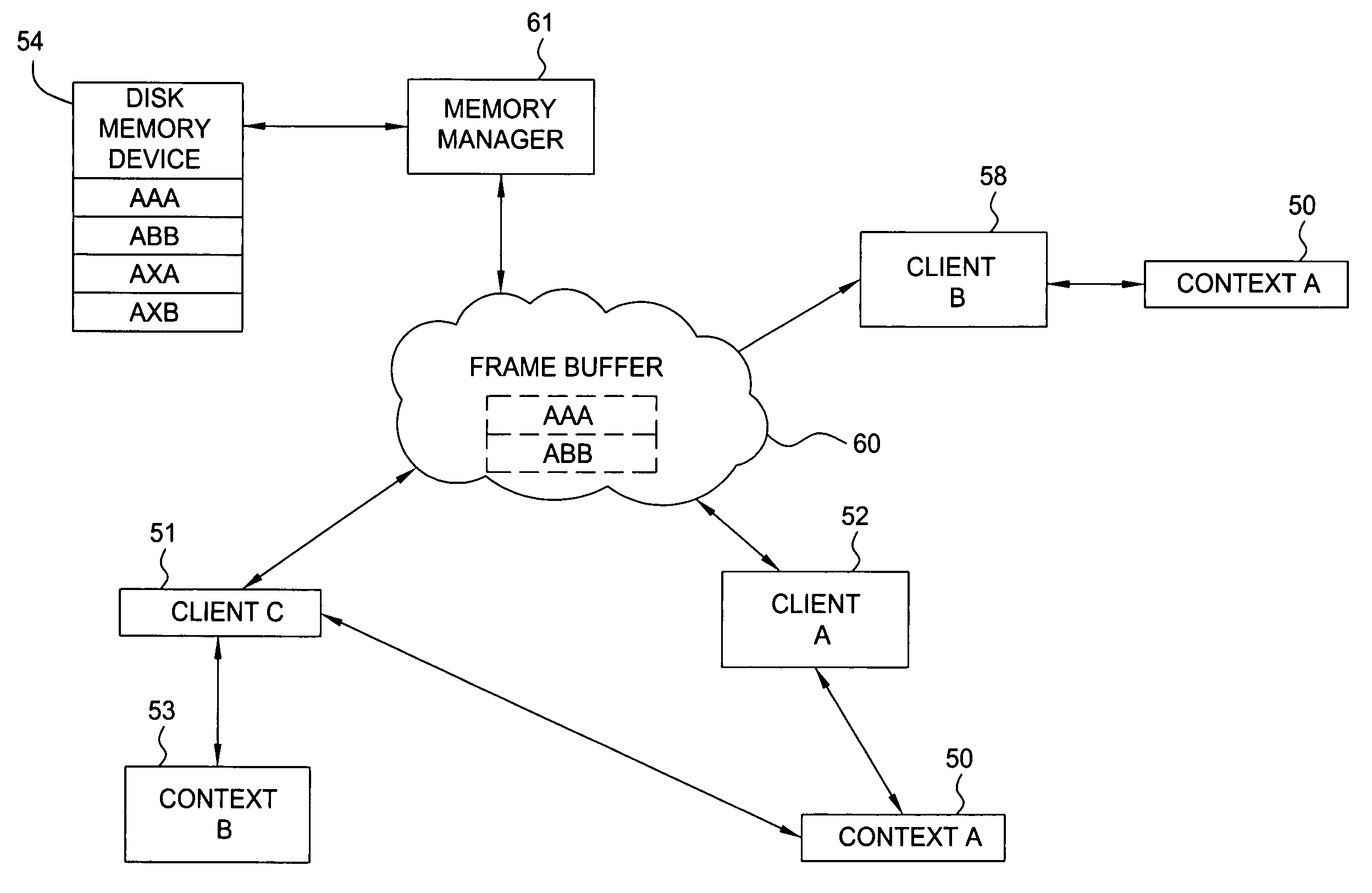
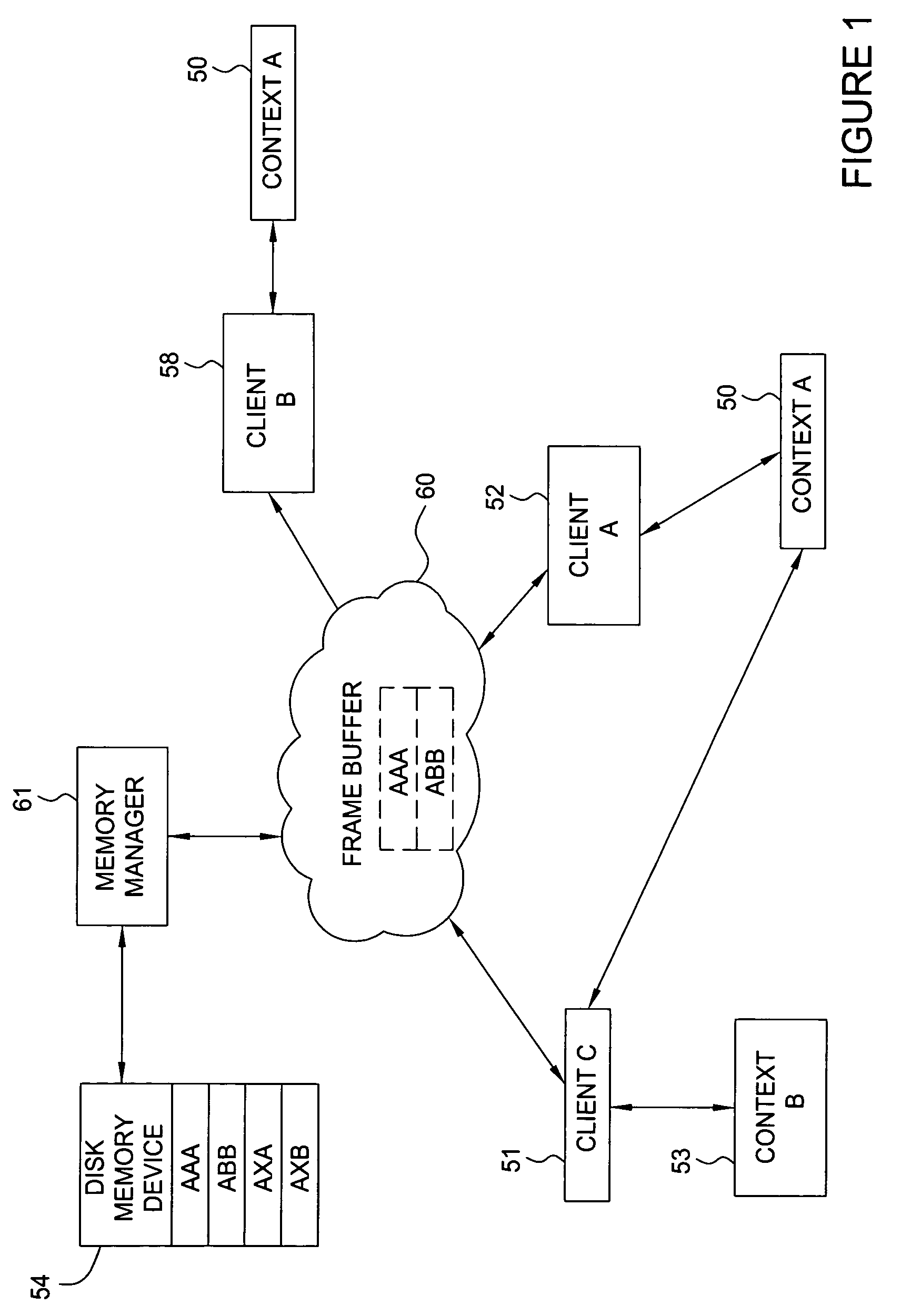
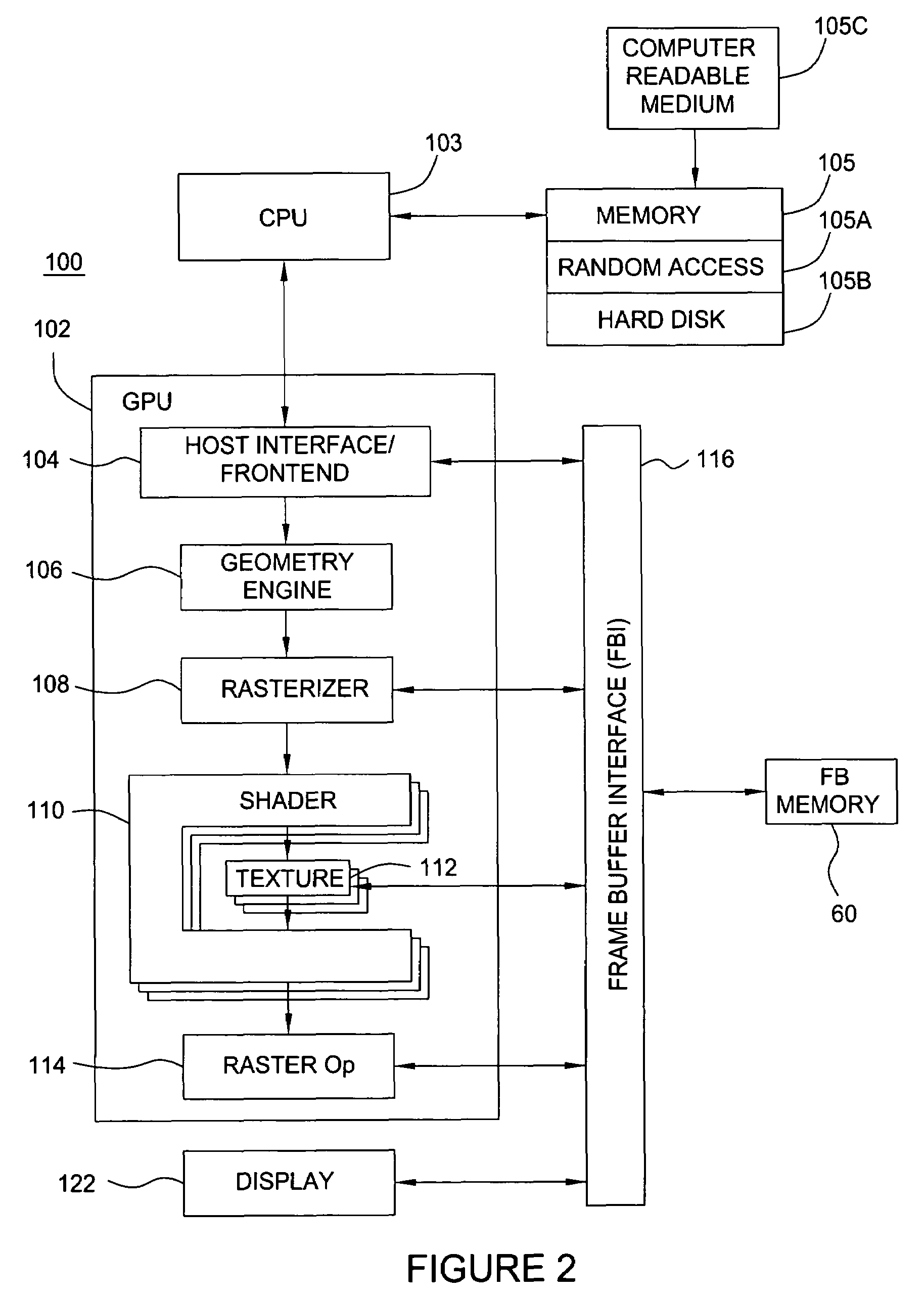
Memory management system having a forward progress bit
A virtual memory system that maintains a list of pages that are required to be resident in a frame buffer to guarantee the eventual forward progress of a graphics application context running on a graphics system composed of multiple clients. Pages that are required to be in the frame buffer memory are never swapped out of that memory. The required page list can be dynamically sized or fixed sized. A tag file is used to prevent page swapping of a page from the frame buffer that is required to make forward progress. A forward progress indicator signifies that a page faulting client has made forward progress on behalf of a context. The presence of a forward progress indicator is used to clear the tag file, thus enabling page swapping of the previously tagged pages from the frame buffer memory.
Owner:NVIDIA CORP
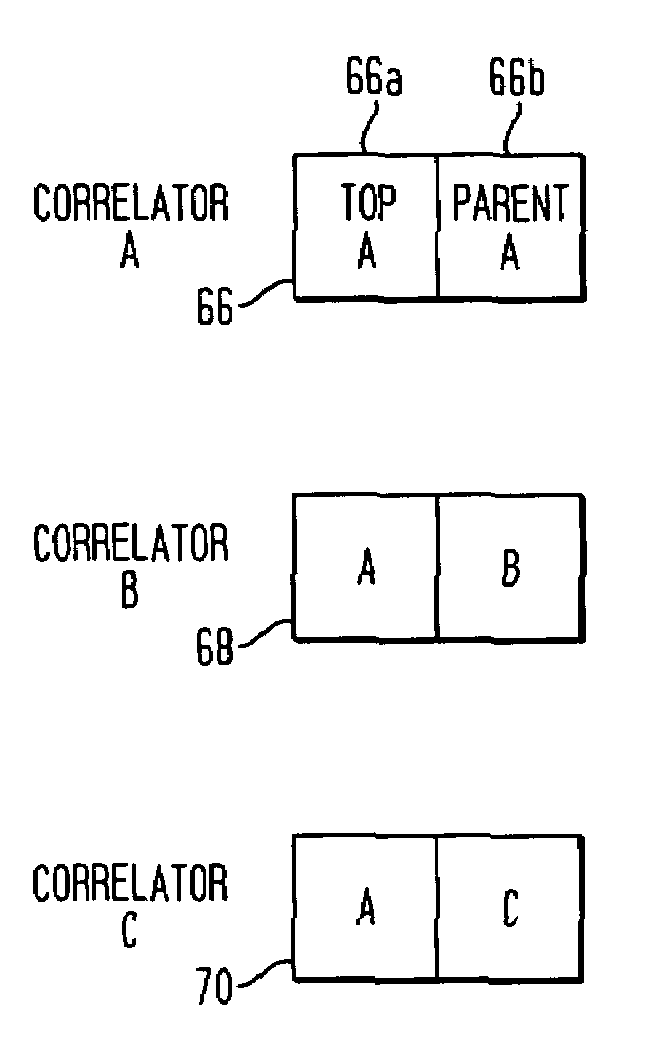
Use of thread-local storage to propagate application context in Java 2 enterprise editon (J2EE) applications
InactiveUS20050039186A1Error detection/correctionMultiprogramming arrangementsApplication serverProcedure context
In a J2EE application server, a method of passing context information among transactions in a hierarchical parent-child transaction chain executing in a single thread of execution. The method comprises generating a correlator corresponding to a top level transaction spawning a plurality of child transactions in the parent-child transaction chain. The correlator is stored in a Java thread local (JTL) stack associated with the thread of execution. For each child transaction, the JTL stack is referenced to access a correlator associated with a parent of the child transaction. The method further comprises utilizing context information provided by said parent correlator to generate a correlator for said child transaction.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
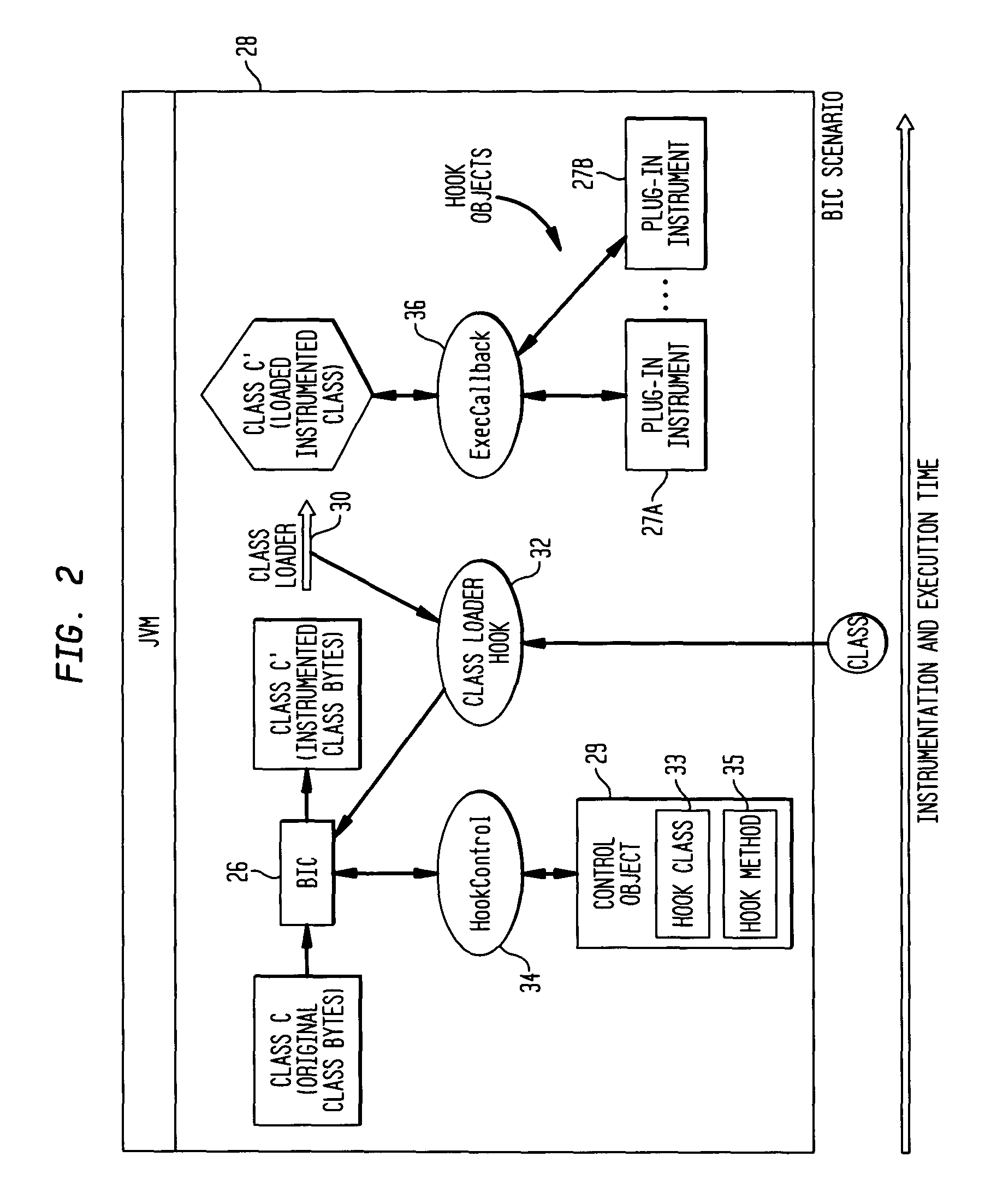
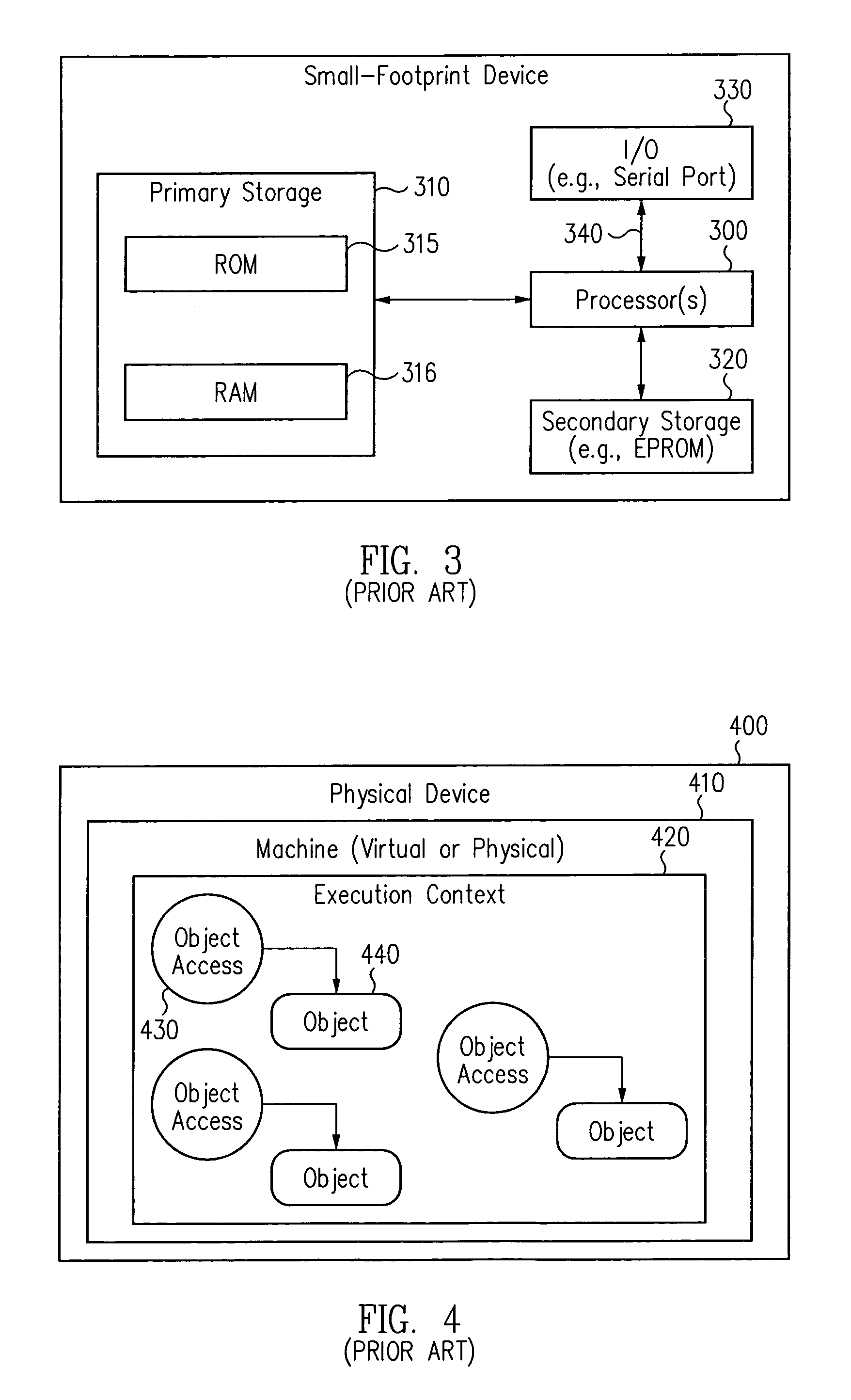
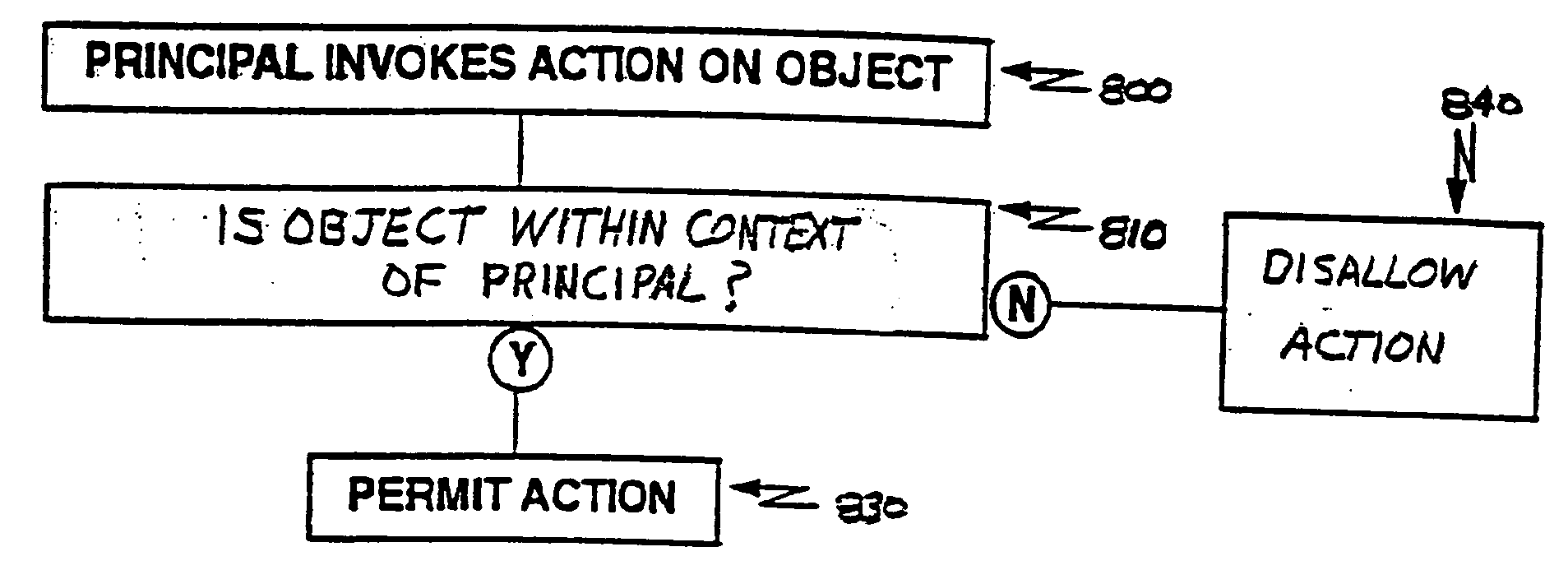
Techniques for permitting access across a context barrier on a small footprint device using an entry point object
InactiveUS20050193218A1Specific access rightsDigital data processing detailsSmall footprintSecurity check
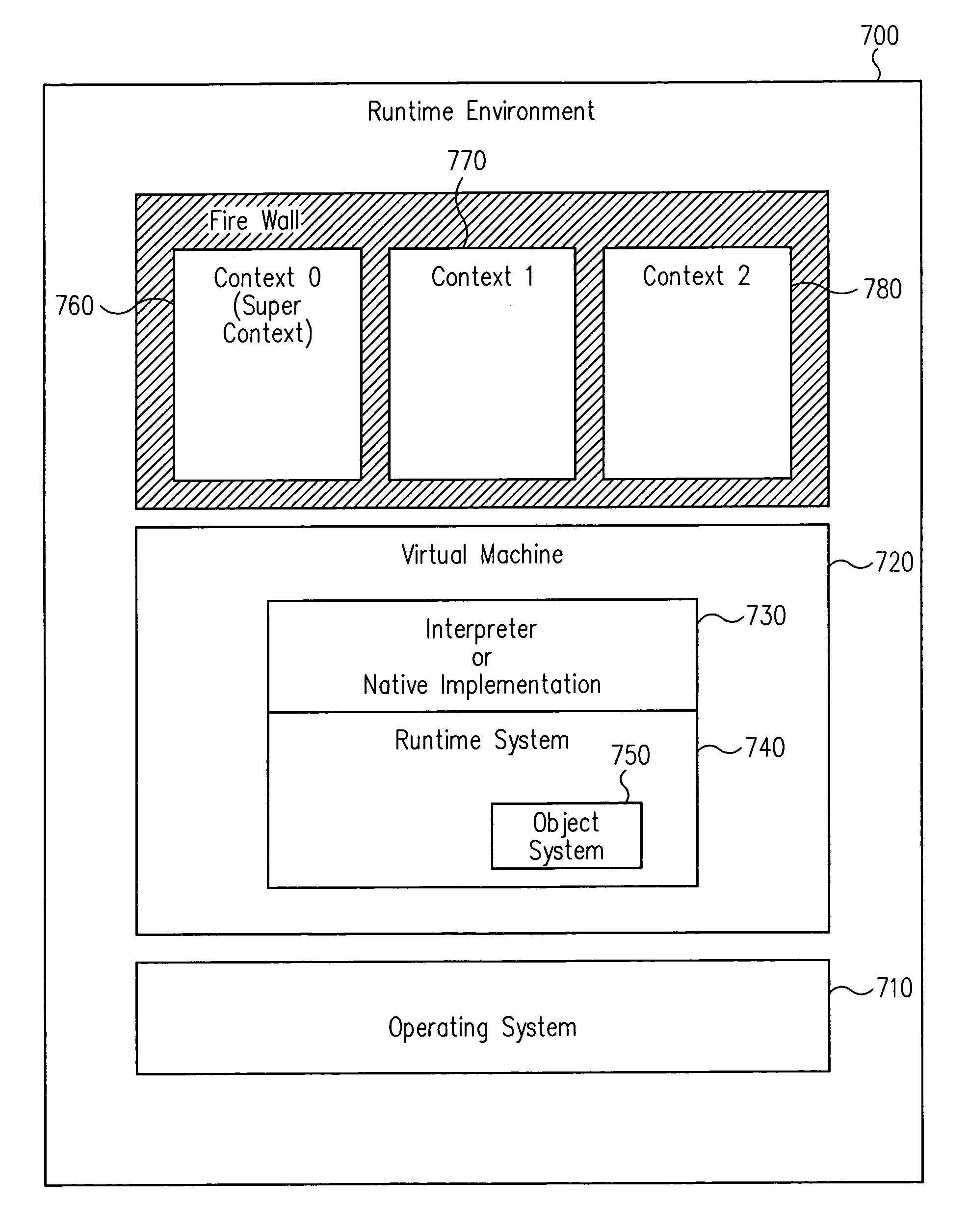
A small footprint device can securely run multiple programs from unrelated vendors by the inclusion of a context barrier isolating the execution of the programs. The context barrier performs security checks to see that principal and object are within the same namespace or memory space and to see that a requested action is appropriate for an object to be operated upon. Each program or set of programs runs in a separate context. Access from one program to another program across the context barrier can be achieved under controlled circumstances by using an entry point object. The entry point object can either perform accesses across the context barrier on behalf of a requesting program or can pass the request to the program to be accessed and switch contexts to the program to be accessed.
Owner:ORACLE INT CORP
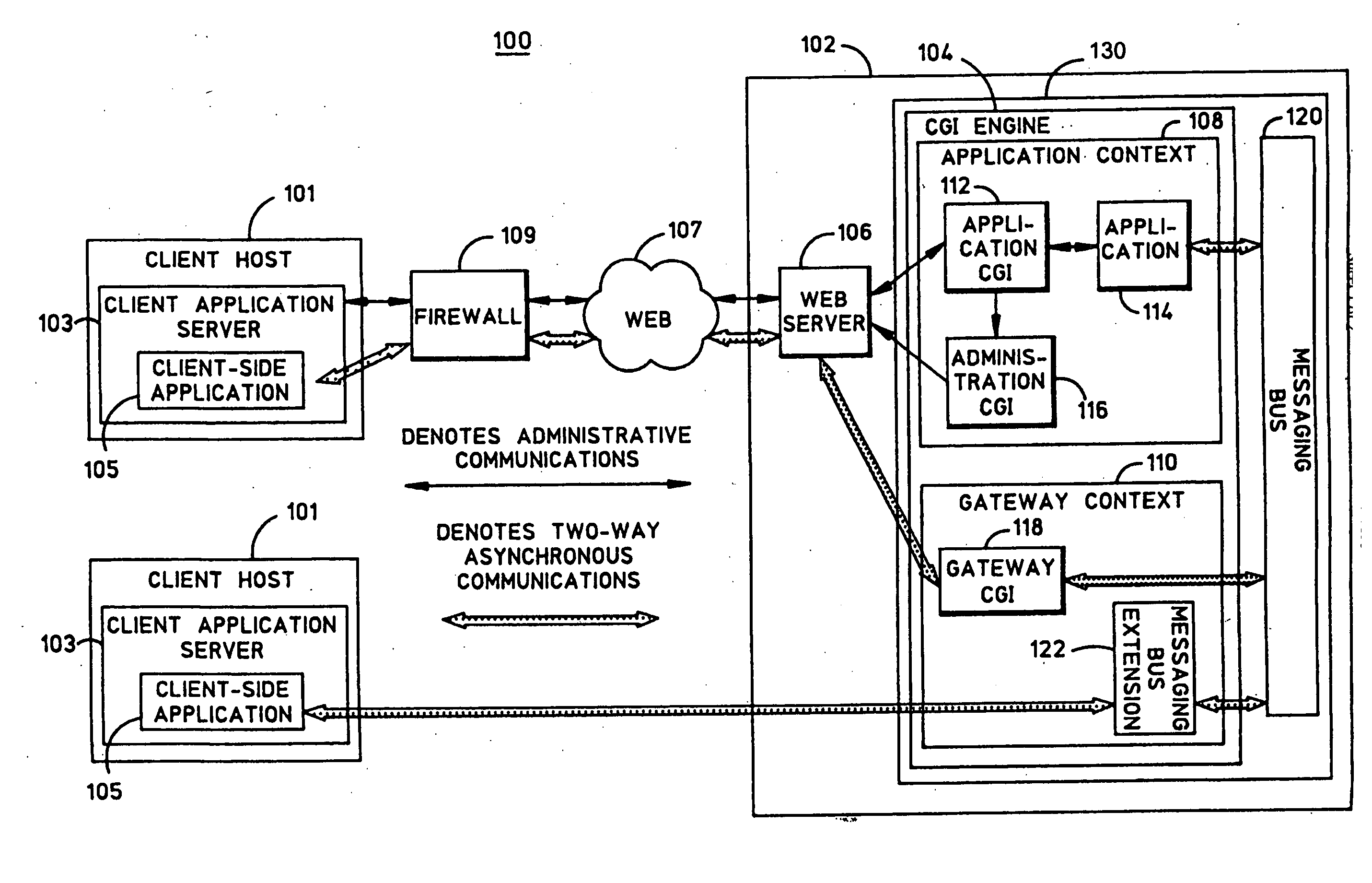
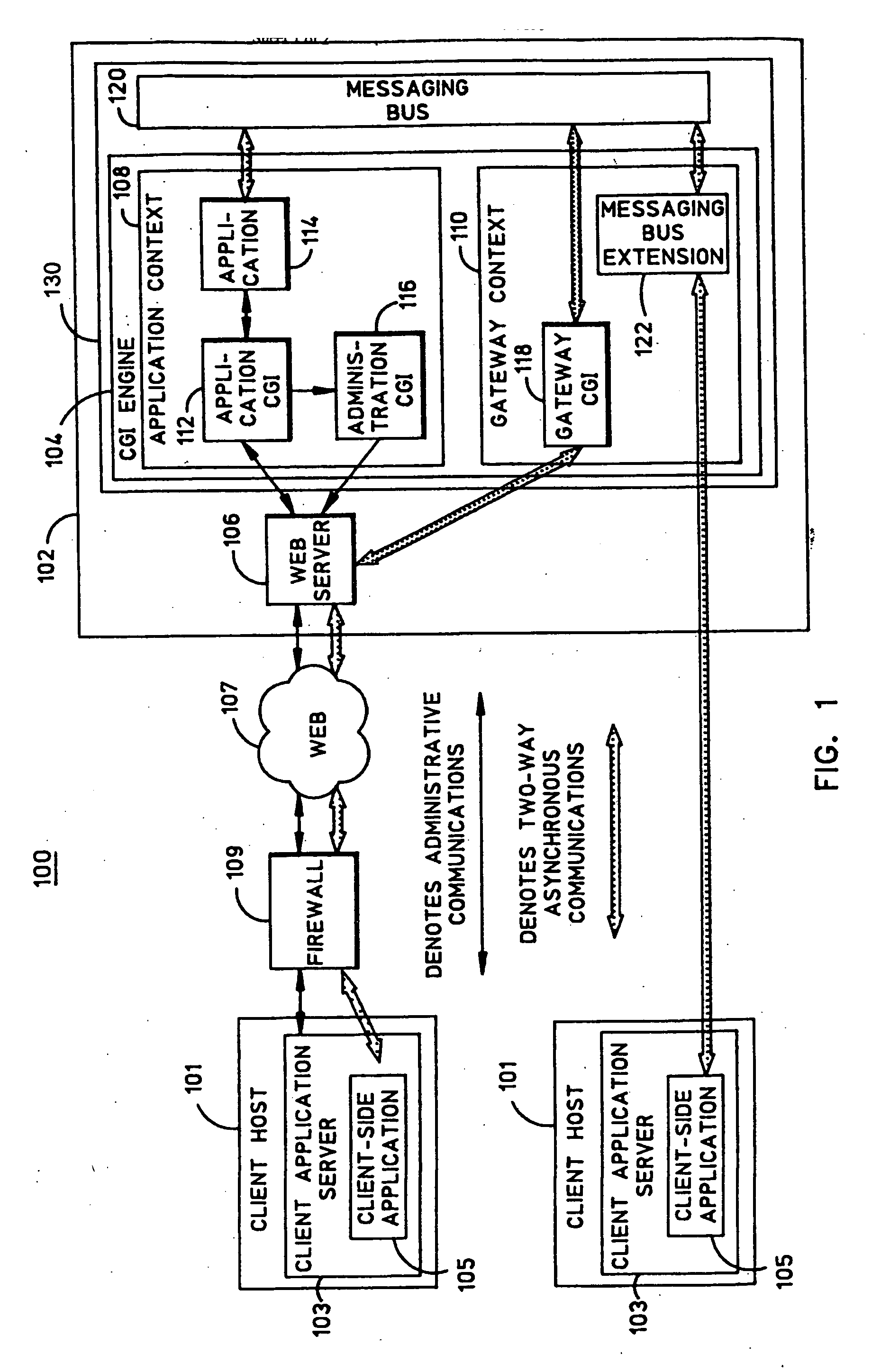
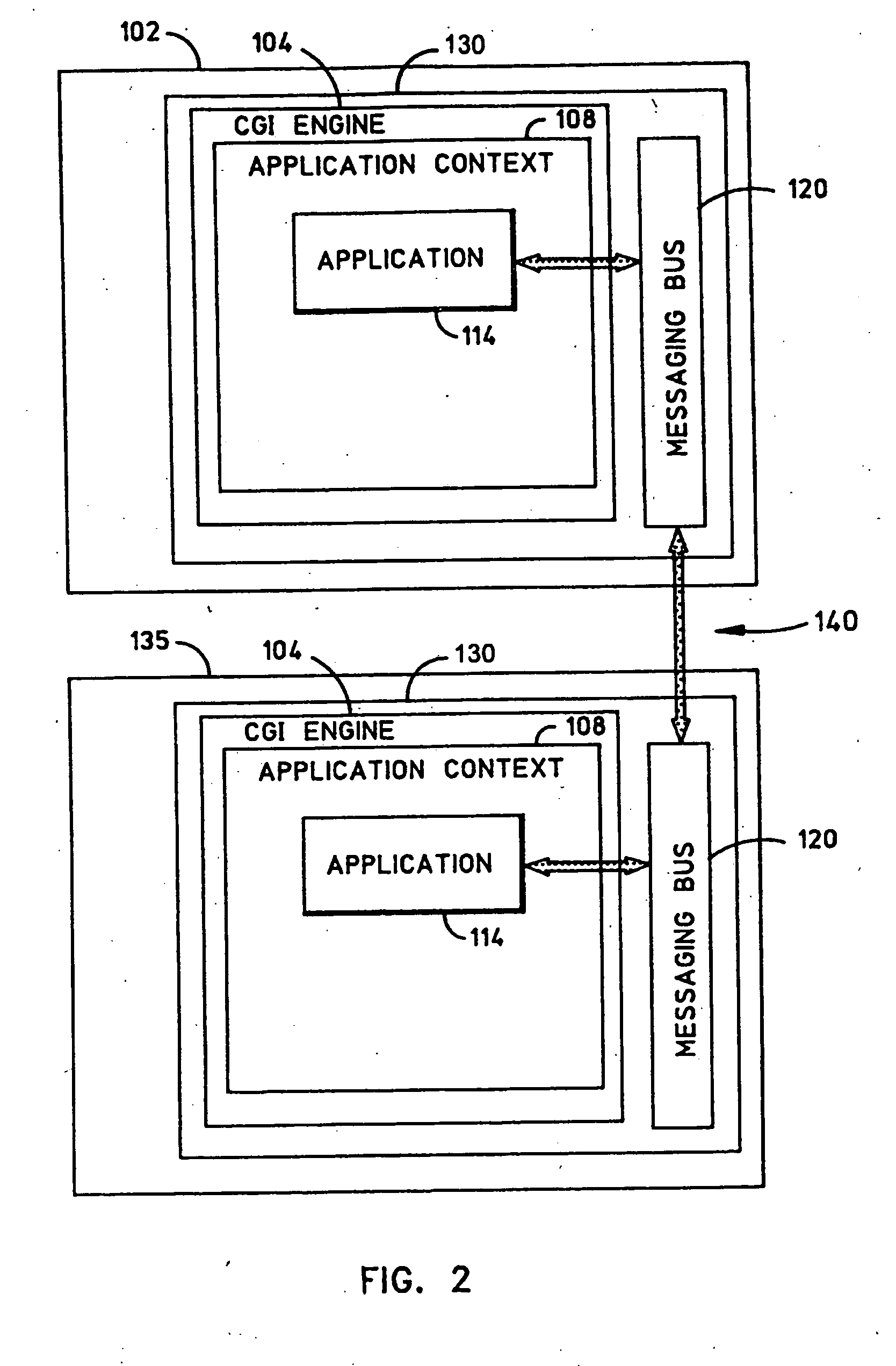
System and method for collaborative processing of distributed applications
InactiveUS20060253535A1Program initiation/switchingMultiple digital computer combinationsCommunication interfaceCollaborative processing
A system and operation is disclosed for collaborative processing of distributed applications. In a collaborative processing system, at least one application context is provided in which an application is executed. The context includes an application CGI for managing the application, and a communication interface on which application data is communicated as messages. A messaging bus is provided that is configured to communicate the messages for processing by the application.
Owner:SORTEO GAMES
Method and system for implementing thread sleep in computer system
InactiveCN1801096AReduce stepsImprove performanceProgram initiation/switchingSingle processWorking environment
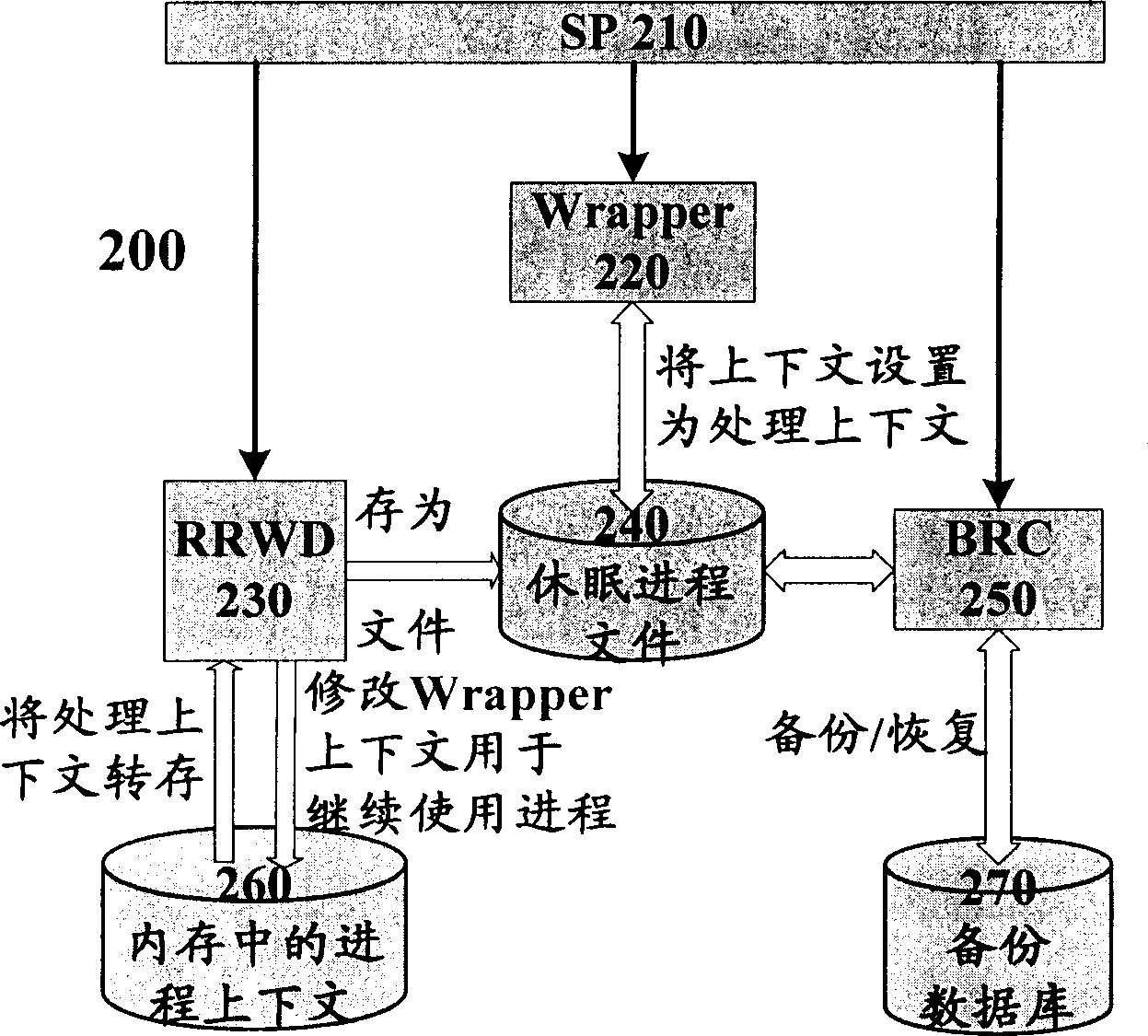
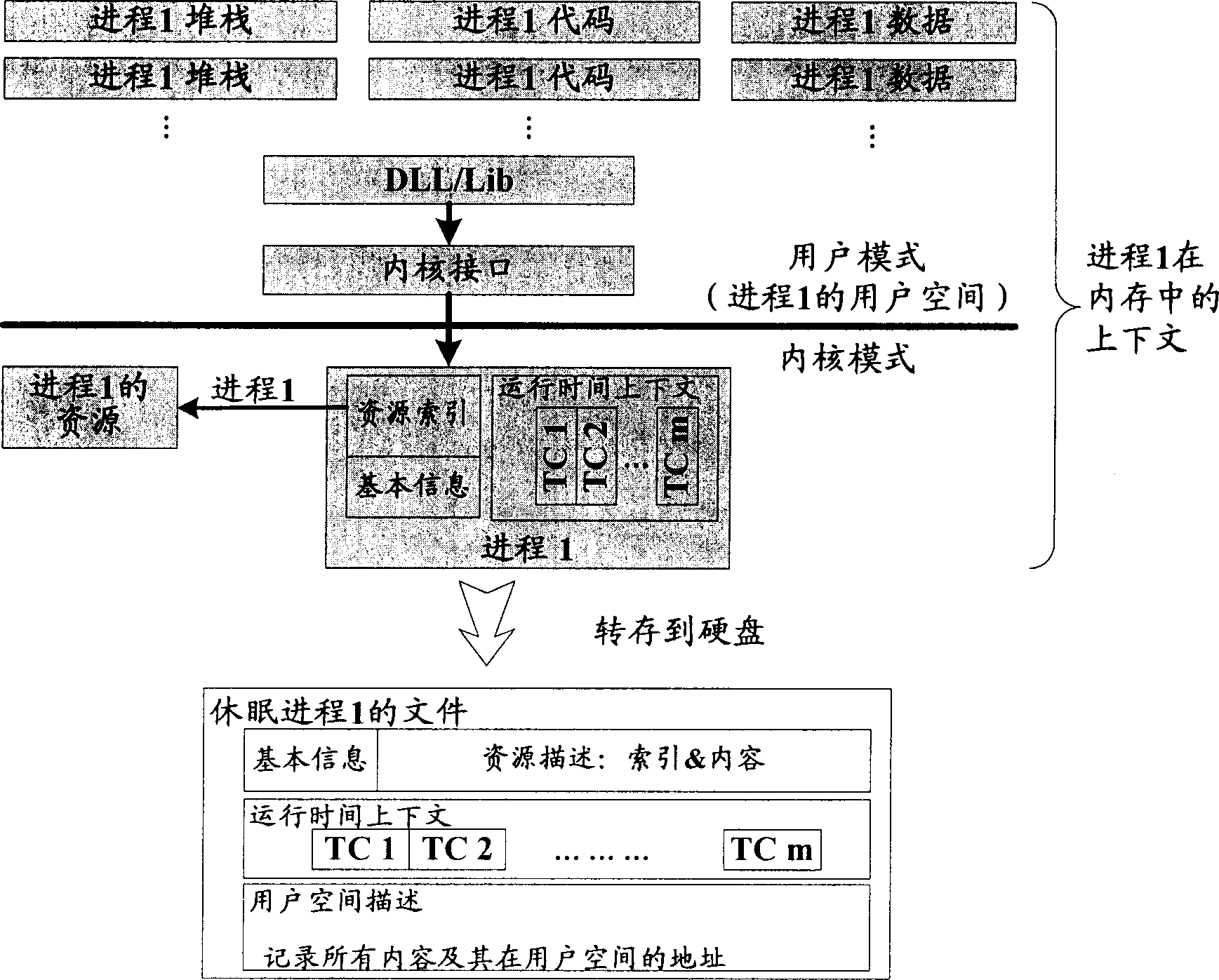
The invention discloses a single process dormant-and-arousing method and system in the computer system, wherein the dormant process comprises the following steps: concealing all process windows; suspending all process line-courses; recording all contexts; loading the dormant process file of context; terminating all process dormant; the arousing process comprises the following steps: structuring a packer similar to the context structure in the dormant process; restoring the dormant context; arousing all line-courses in the dormant process; displaying all windows to use the relative process continually. The invention reduces the operation of switch the applying program and optimizes the system resource, which stores the present working environment automatically and restores the entire environment when the accident occurs in the computer.
Owner:LENOVO (SINGAPORE) PTE LTD
Techniques for permitting access across a context barrier in a small footprint device using shared object interfaces
InactiveUS7093122B1Provide protectionSpecific access rightsError detection/correctionSmall footprintSecurity check
A small footprint device can securely run multiple programs from unrelated vendors by the inclusion of a context barrier isolating the execution of the programs. The context barrier performs security checks to see that principal and object are within the same namespace or memory space or to see that a requested action is authorized for an object to be operated upon. Each program or set of programs runs in a separate context. Access from one program to another program across the context barrier can be achieved under controlled circumstances by using shared interface objects. Shared interface objects have a property that permits them to be accessed across the context barrier regardless of security restrictions that would otherwise apply. Shared interface objects, however, may enforce their own security rules independently of the context barrier.
Owner:ORACLE INT CORP
Use of thread-local storage to propagate application context in Java 2 enterprise edition (J2EE) applications
InactiveUS7493622B2Error detection/correctionMultiprogramming arrangementsApplication serverProcedure context
In a J2EE application server, a method of passing context information among transactions in a hierarchical parent-child transaction chain executing in a single thread of execution. The method comprises generating a correlator corresponding to a top level transaction spawning a plurality of child transactions in the parent-child transaction chain. The correlator is stored in a Java thread local (JTL) stack associated with the thread of execution. For each child transaction, the JTL stack is referenced to access a correlator associated with a parent of the child transaction. The method further comprises utilizing context information provided by said parent correlator to generate a correlator for said child transaction.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Proactive seamless service provisioning in mobile networks through transferring of application context
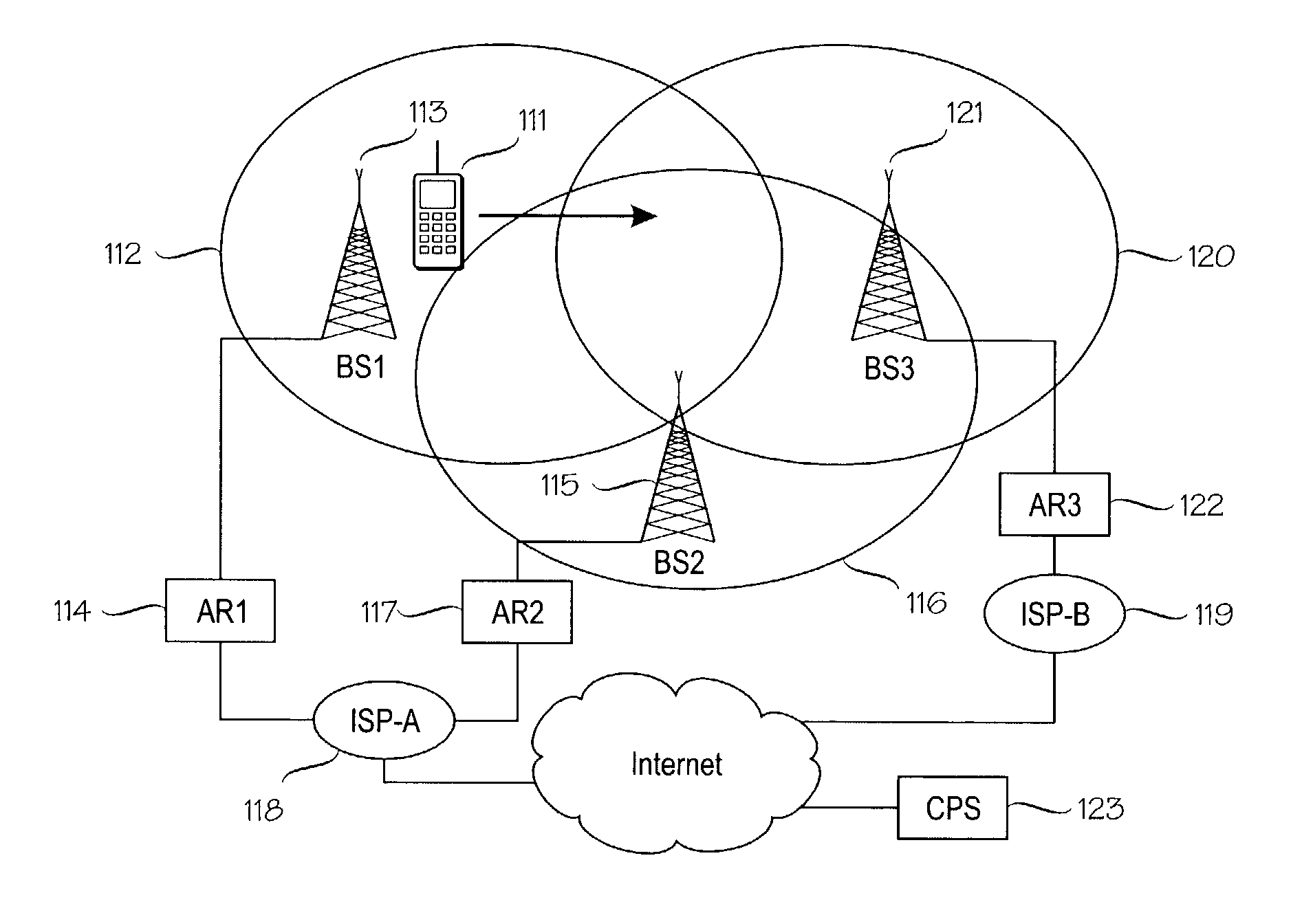
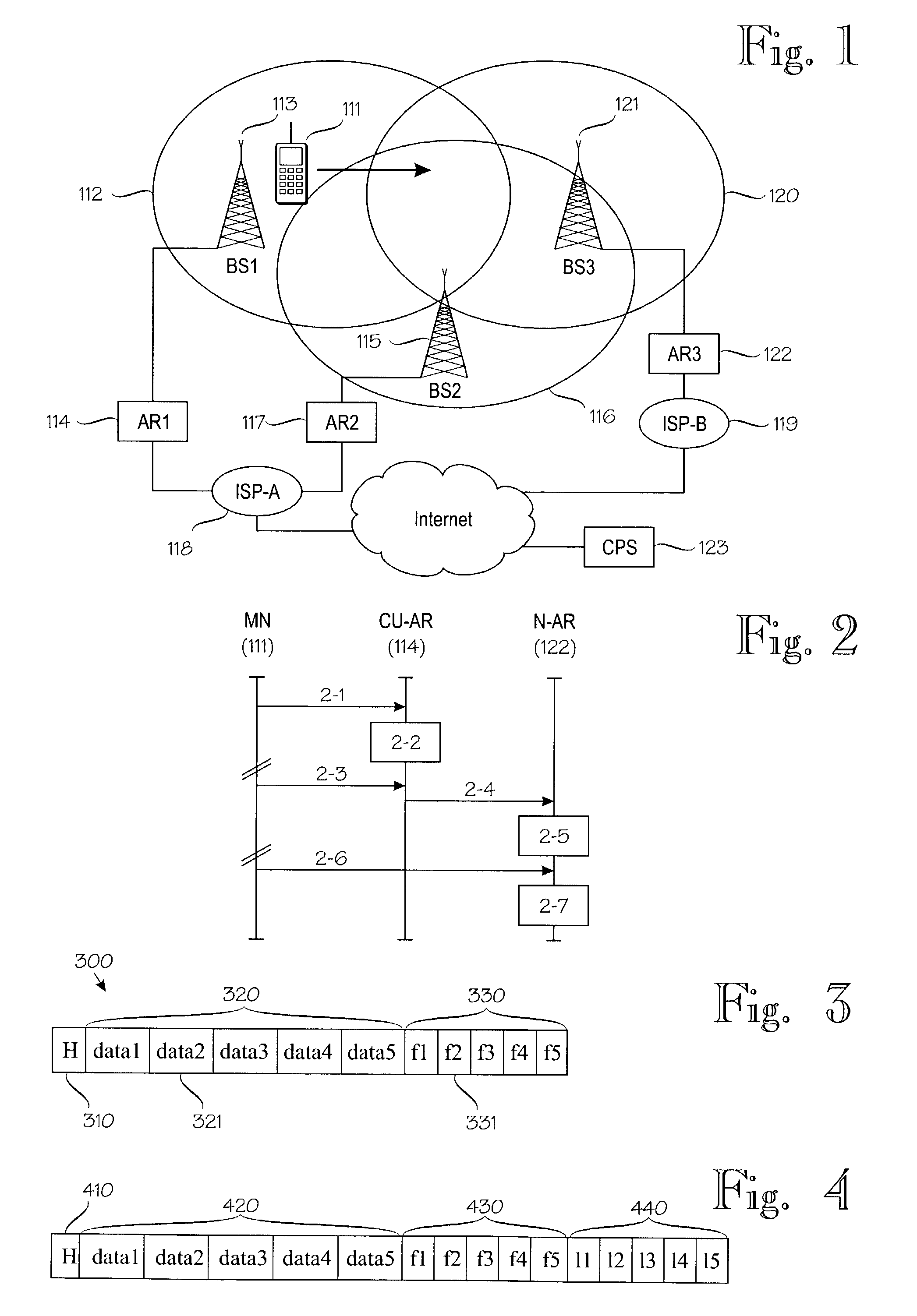
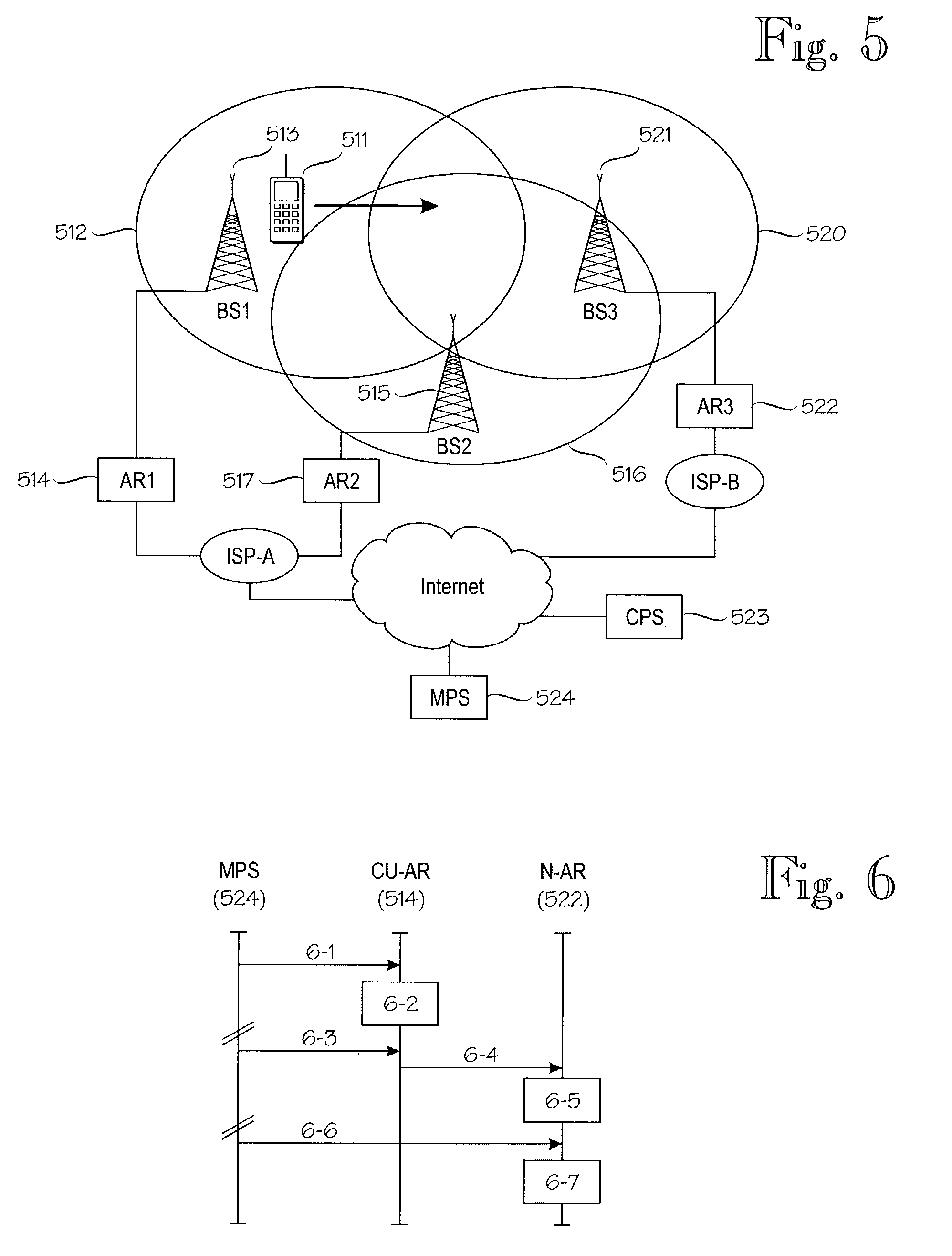
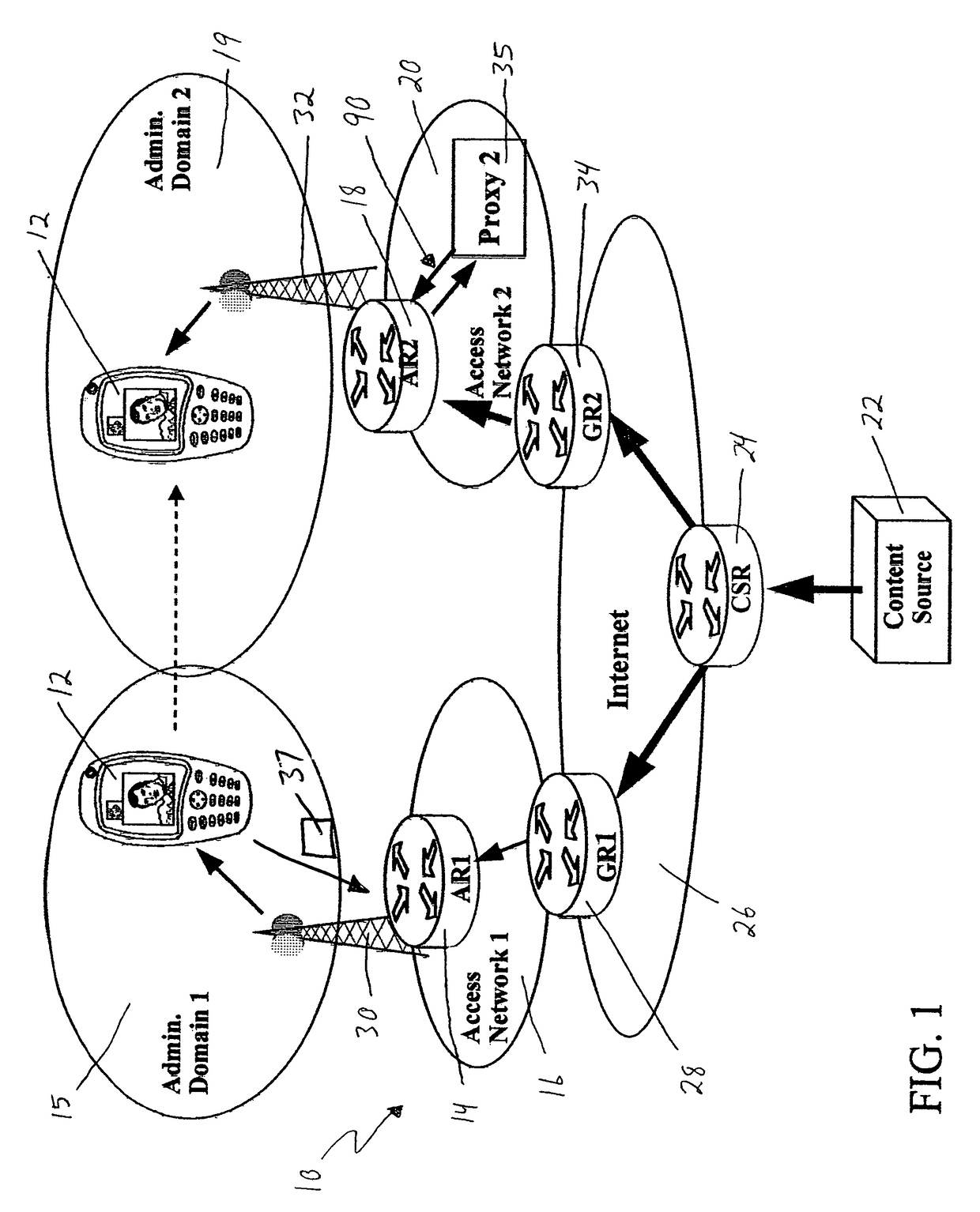
ActiveUS7388851B2Data switching by path configurationWireless network protocolsMobile communication systemsHandover
A method for supporting relocation of an IP session during a network layer handover in a mobile communication system. In the method, application context information indicating activities that are advantageously executed pro-actively before the network layer handover is sent. The indicated activities are then pro-actively executed in a receiving network node. An advantage of the method and arrangement of the invention is that the pro-active actions, including pre-allocation of some critical resources for seamless handover of an ongoing IP session, facilitate timely implementation of the activities required for handing over an IP session, and / or selection of a target access router.
Owner:INTELLECTUAL VENTURES I LLC
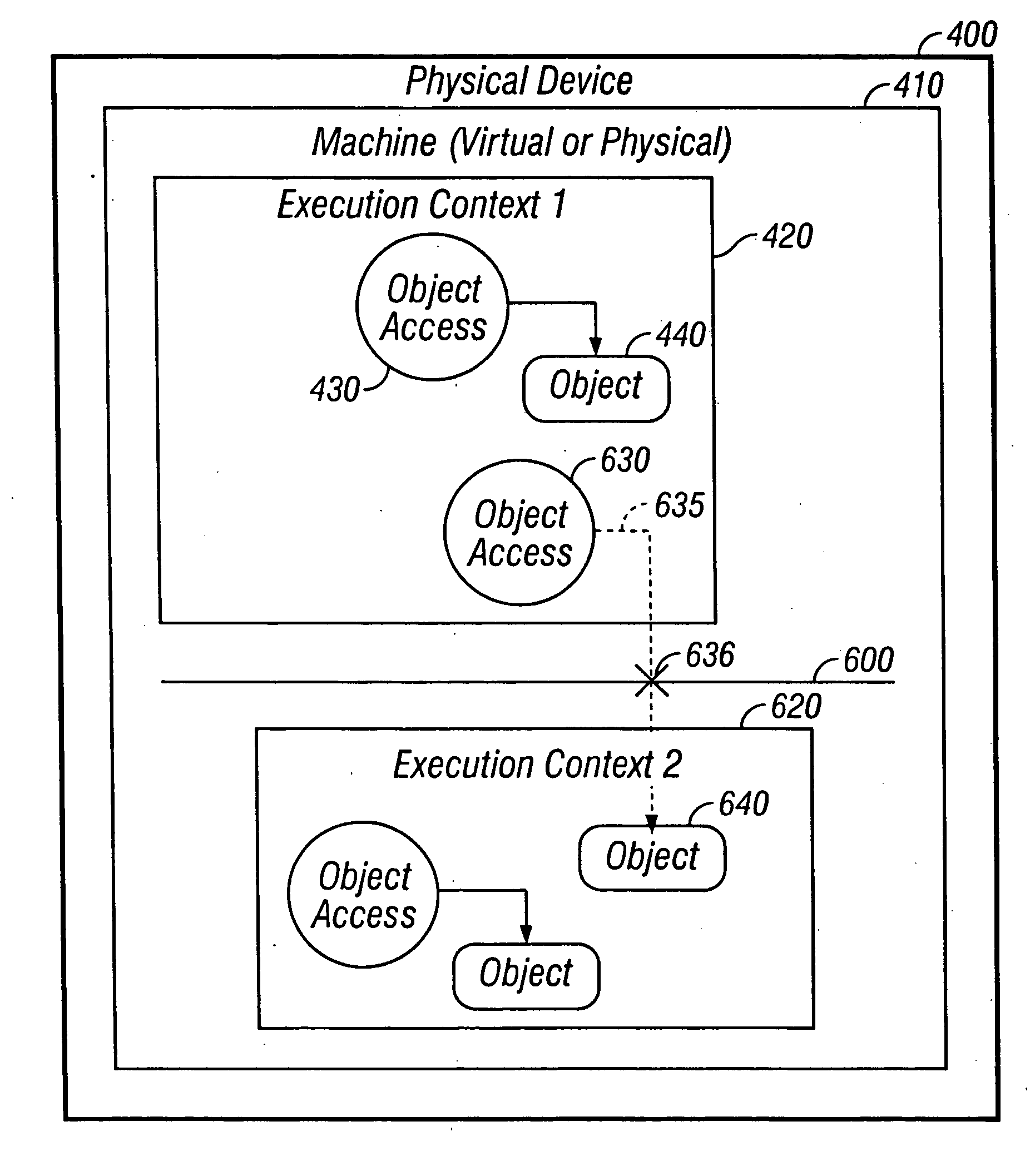
Techniques for permitting access across a context barrier in a small footprint device using global data structures
InactiveUS20050102679A1Provide protectionSpecific access rightsDigital data processing detailsSmall footprintTerm memory
A small footprint device can securely run multiple programs from unrelated vendors by the inclusion of a context barrier isolating the execution of the programs. The context barrier performs security checks to see that principal and object are within the same namespace or memory space and to see that a requested action is appropriate for an object to be operated upon. Each program or set of programs runs in a separate context. Access from one program to another program across the context barrier can be achieved under controlled circumstances by using a global data structure.
Owner:ORACLE INT CORP
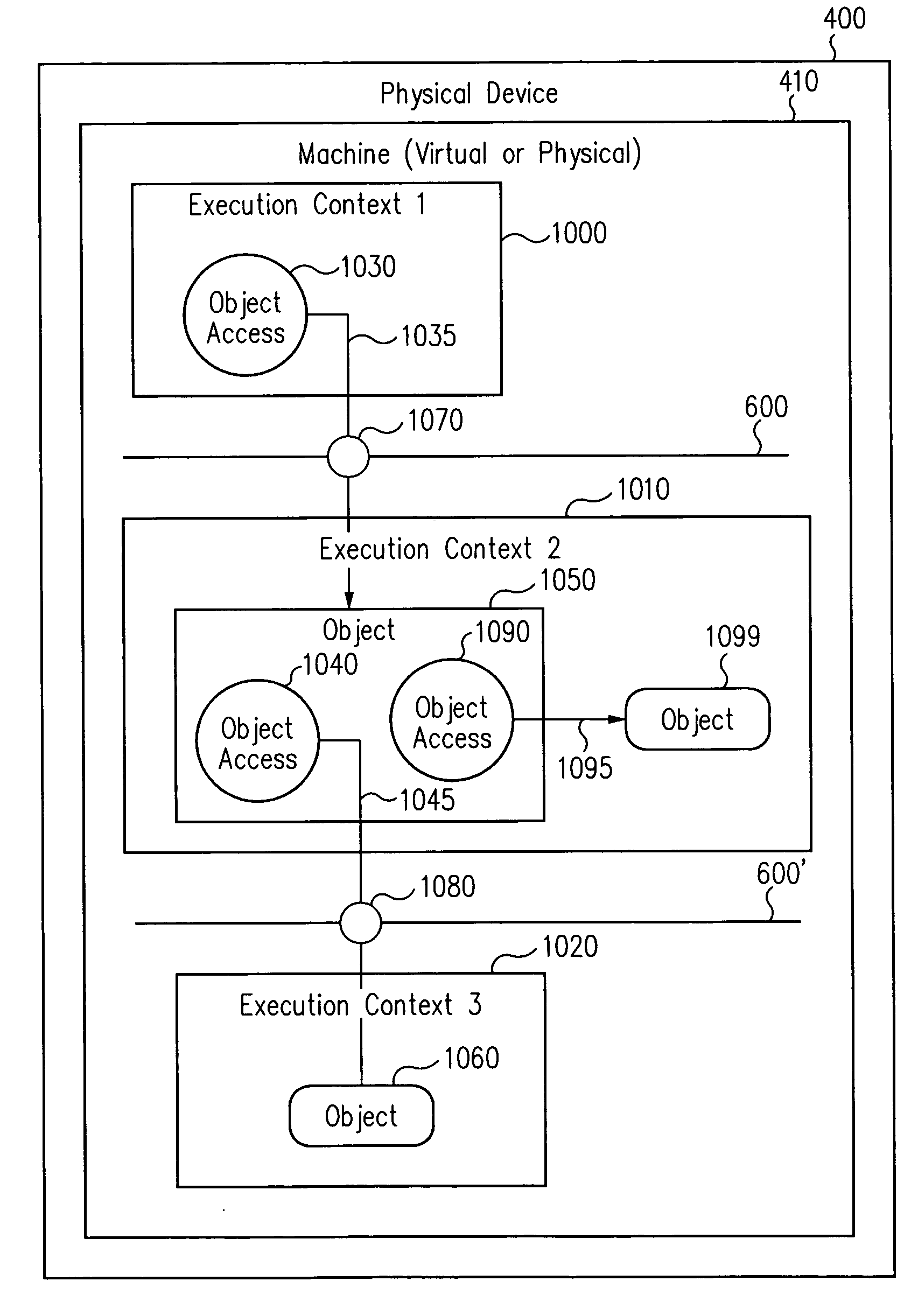
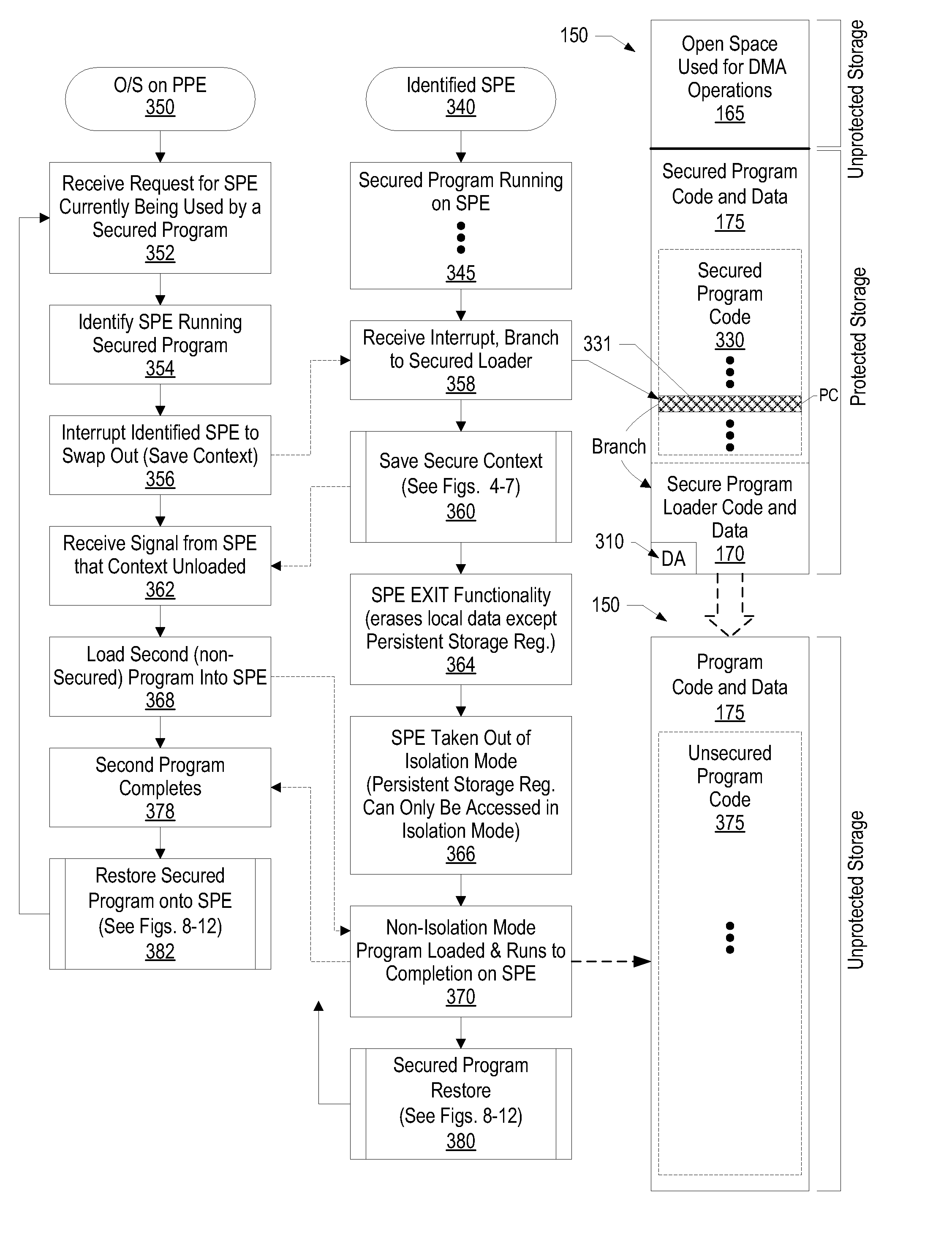
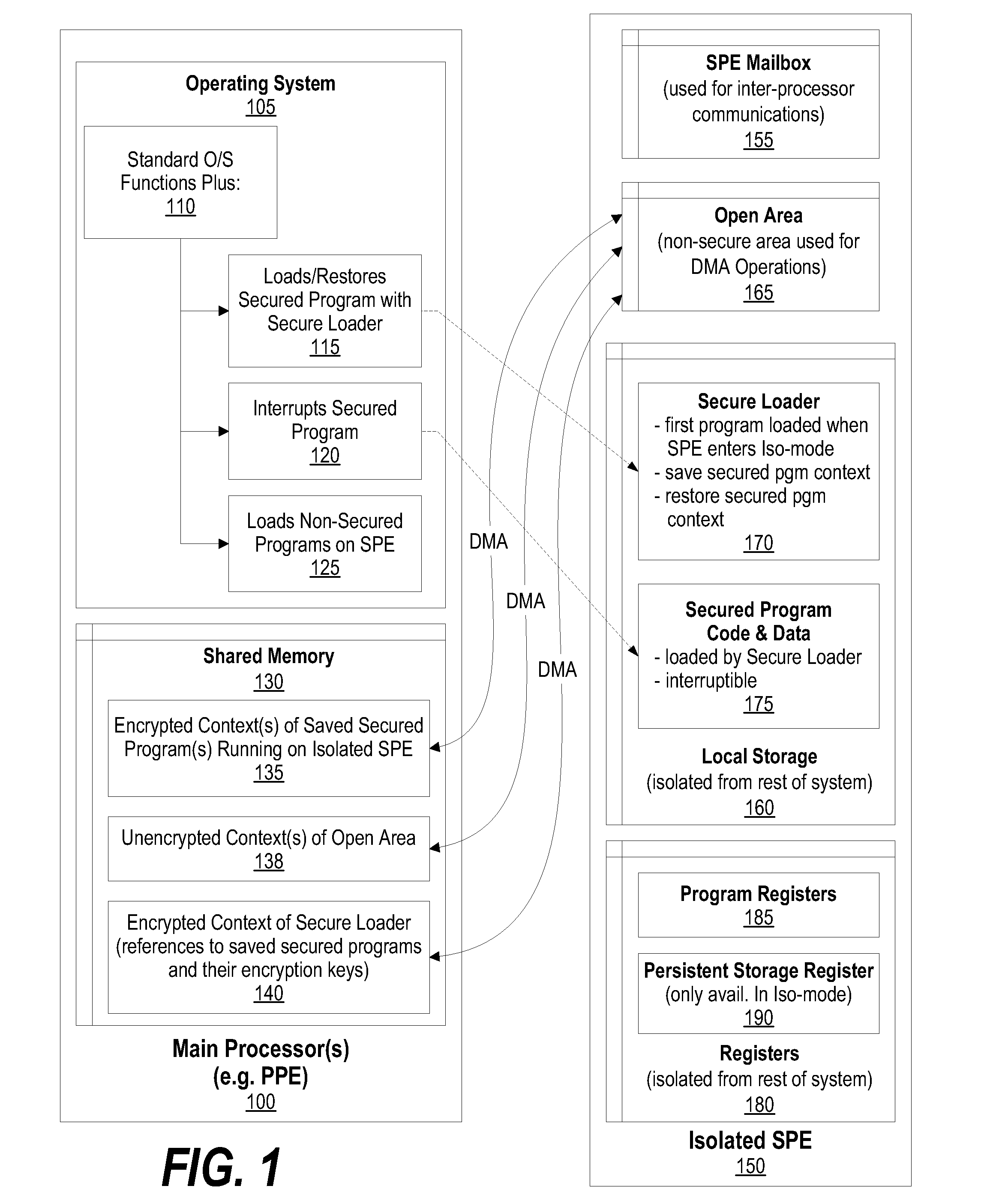
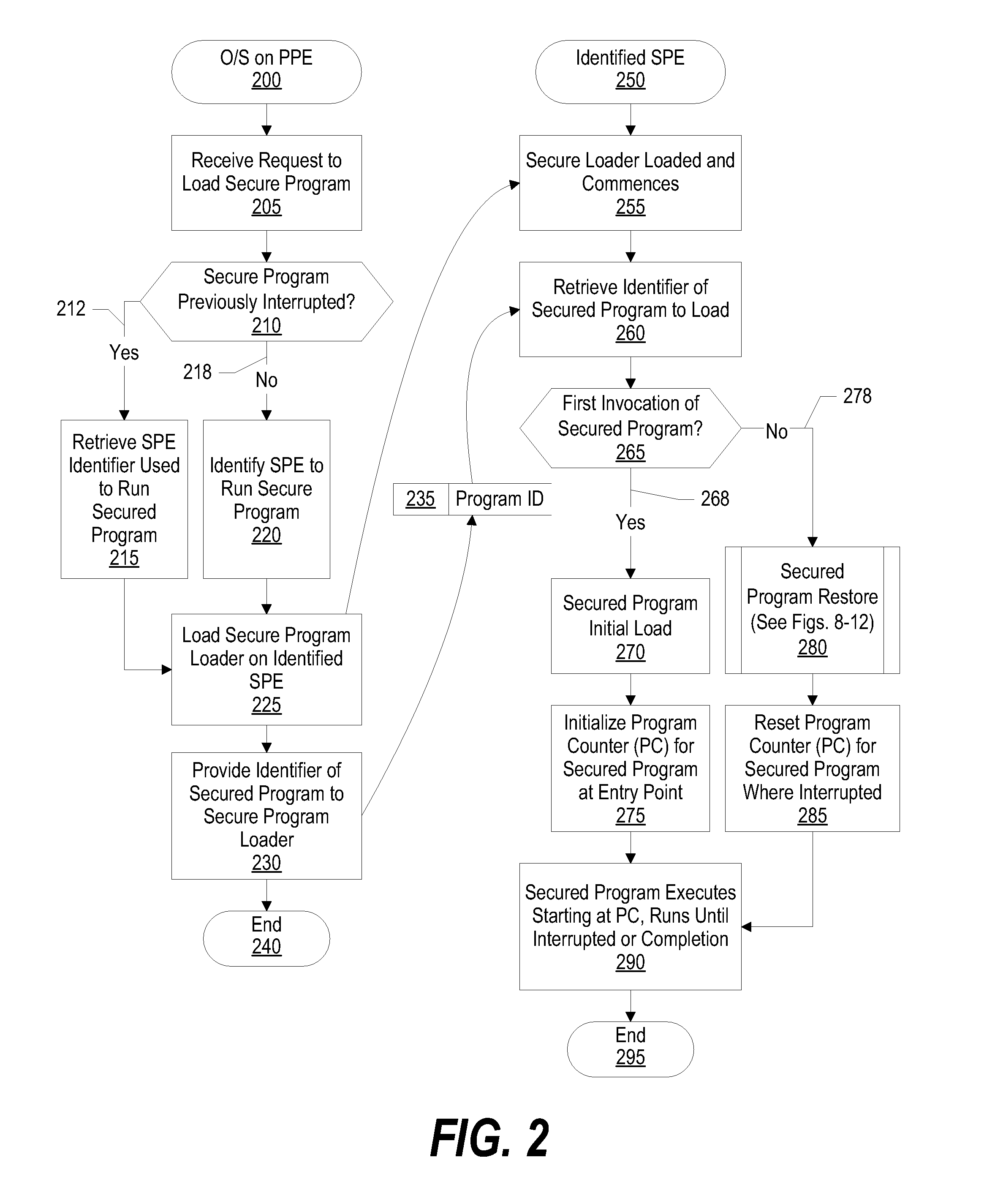
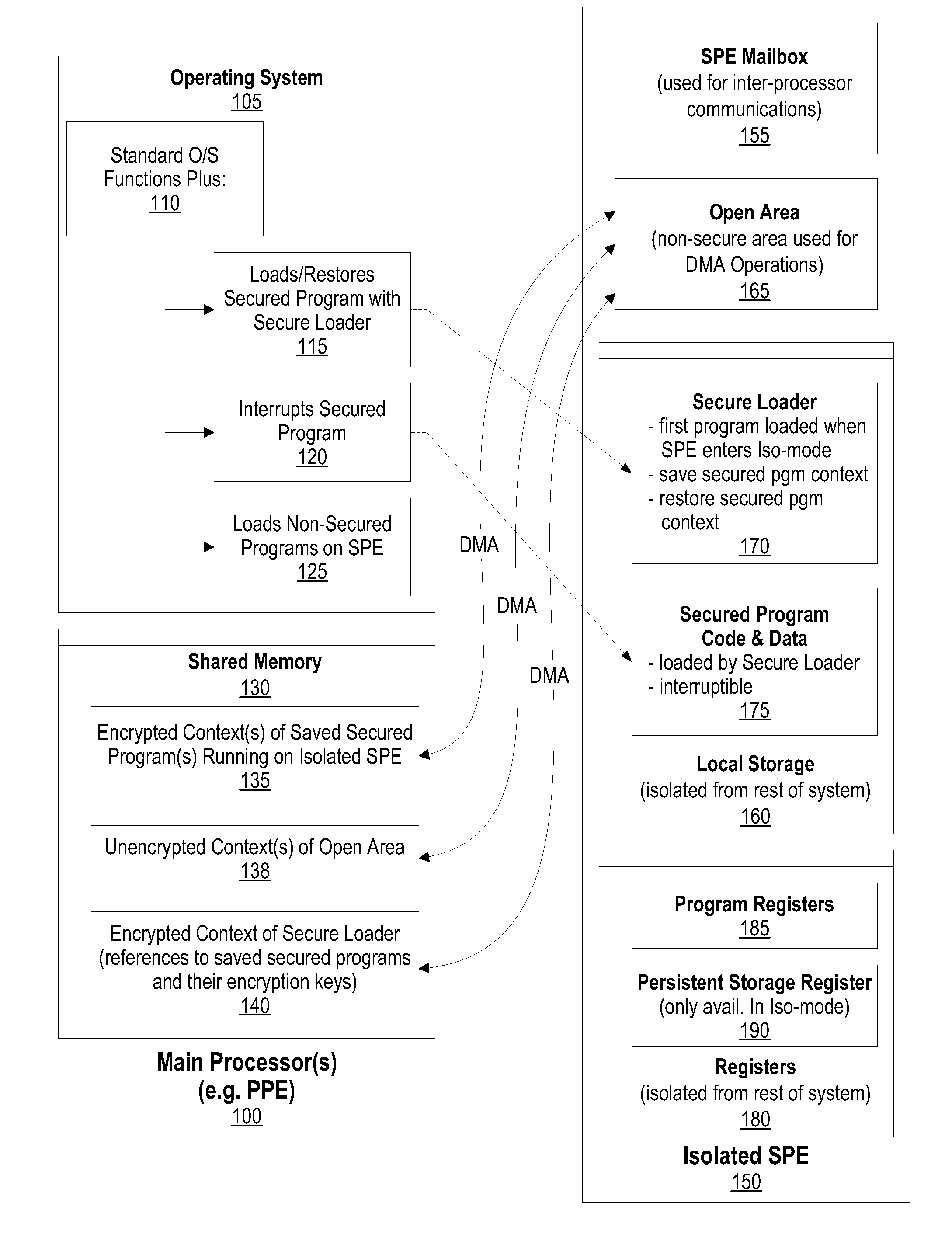
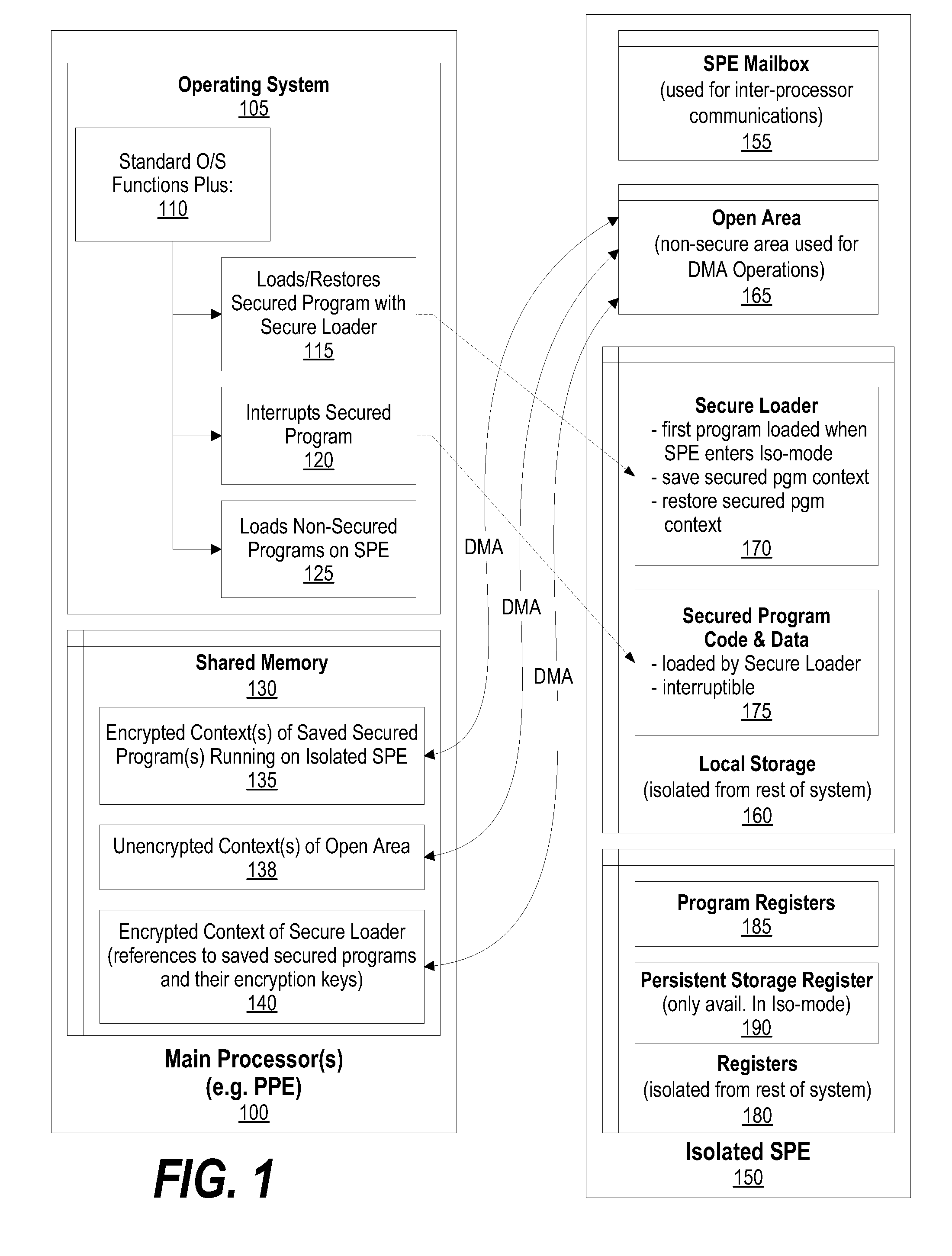
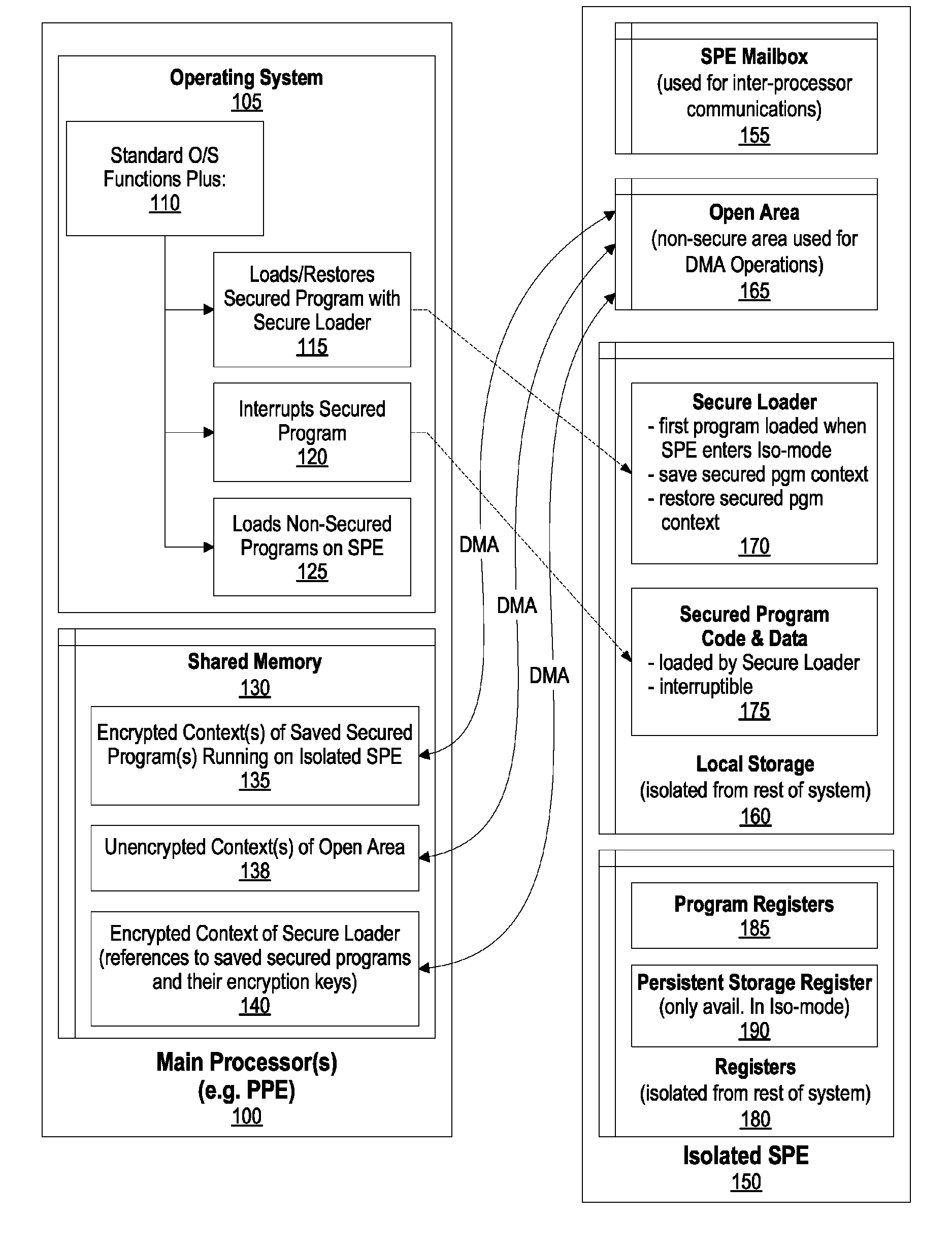
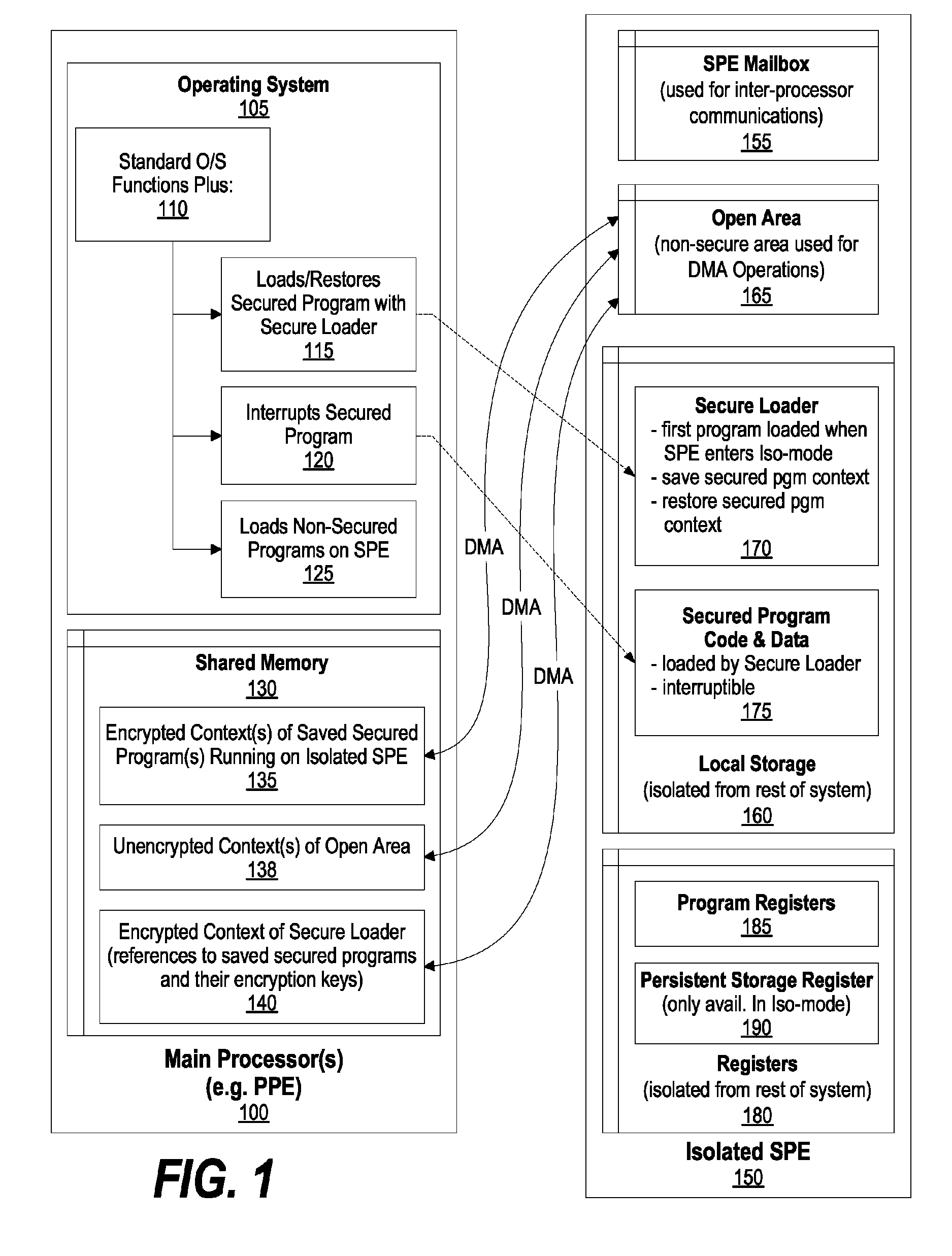
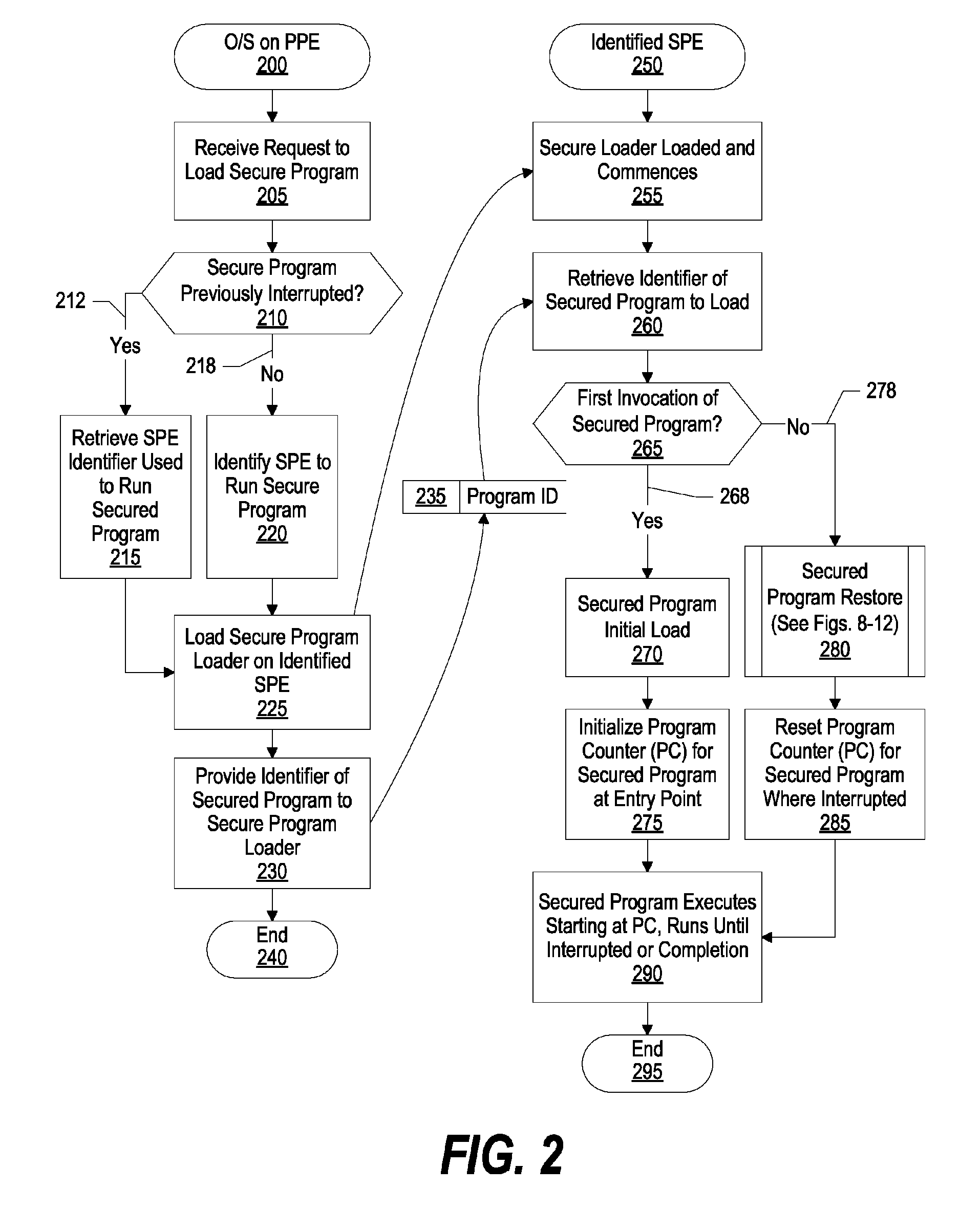
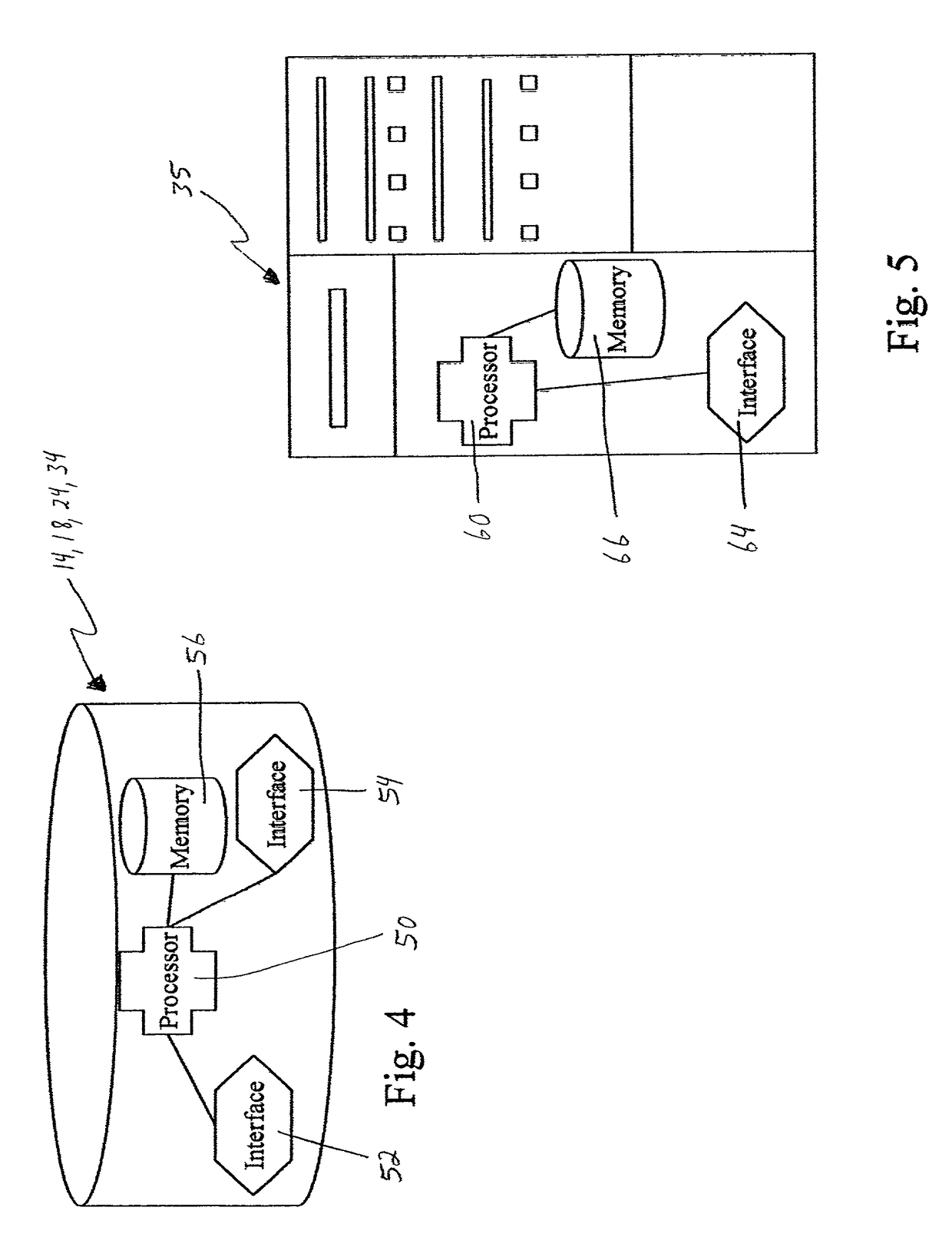
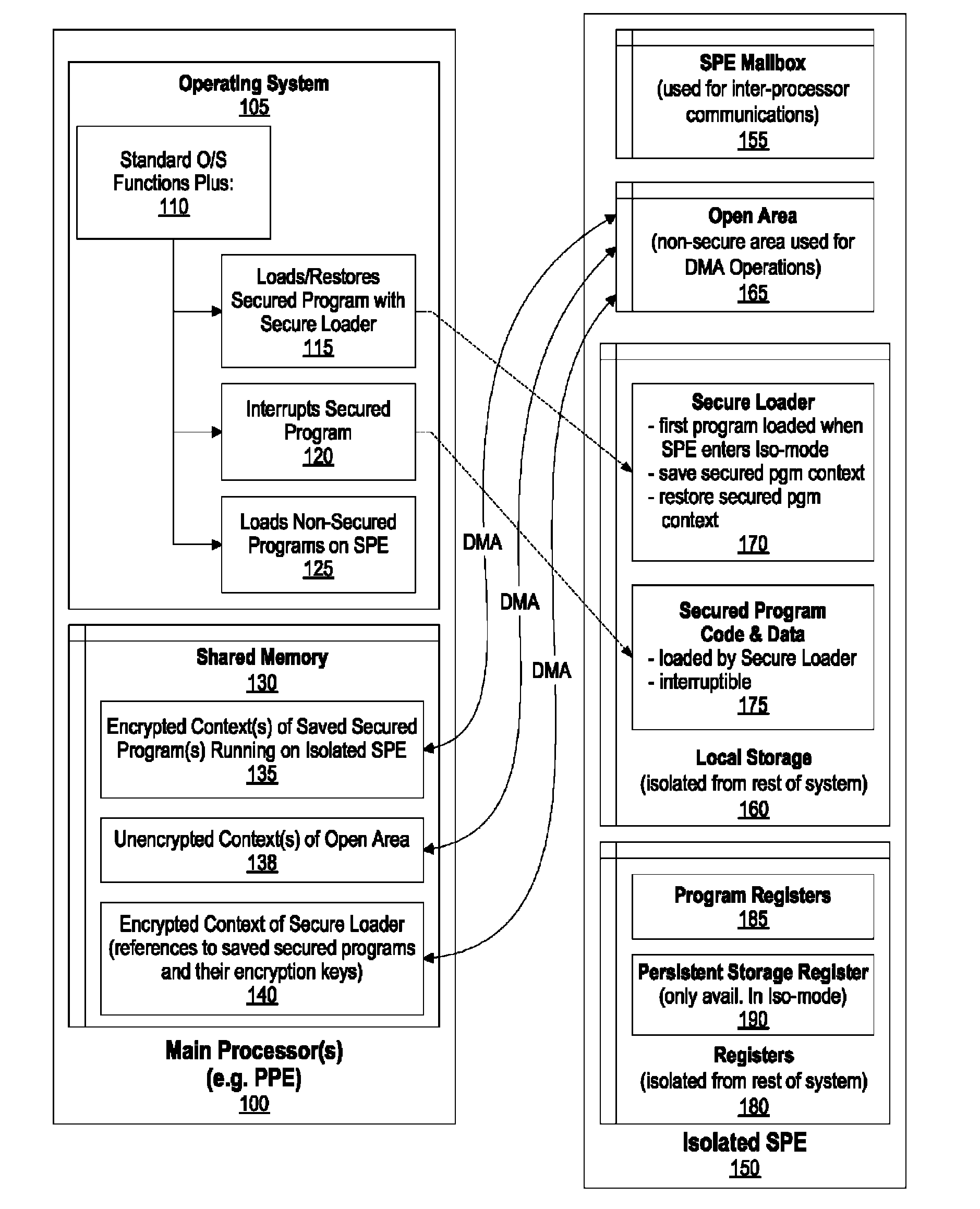
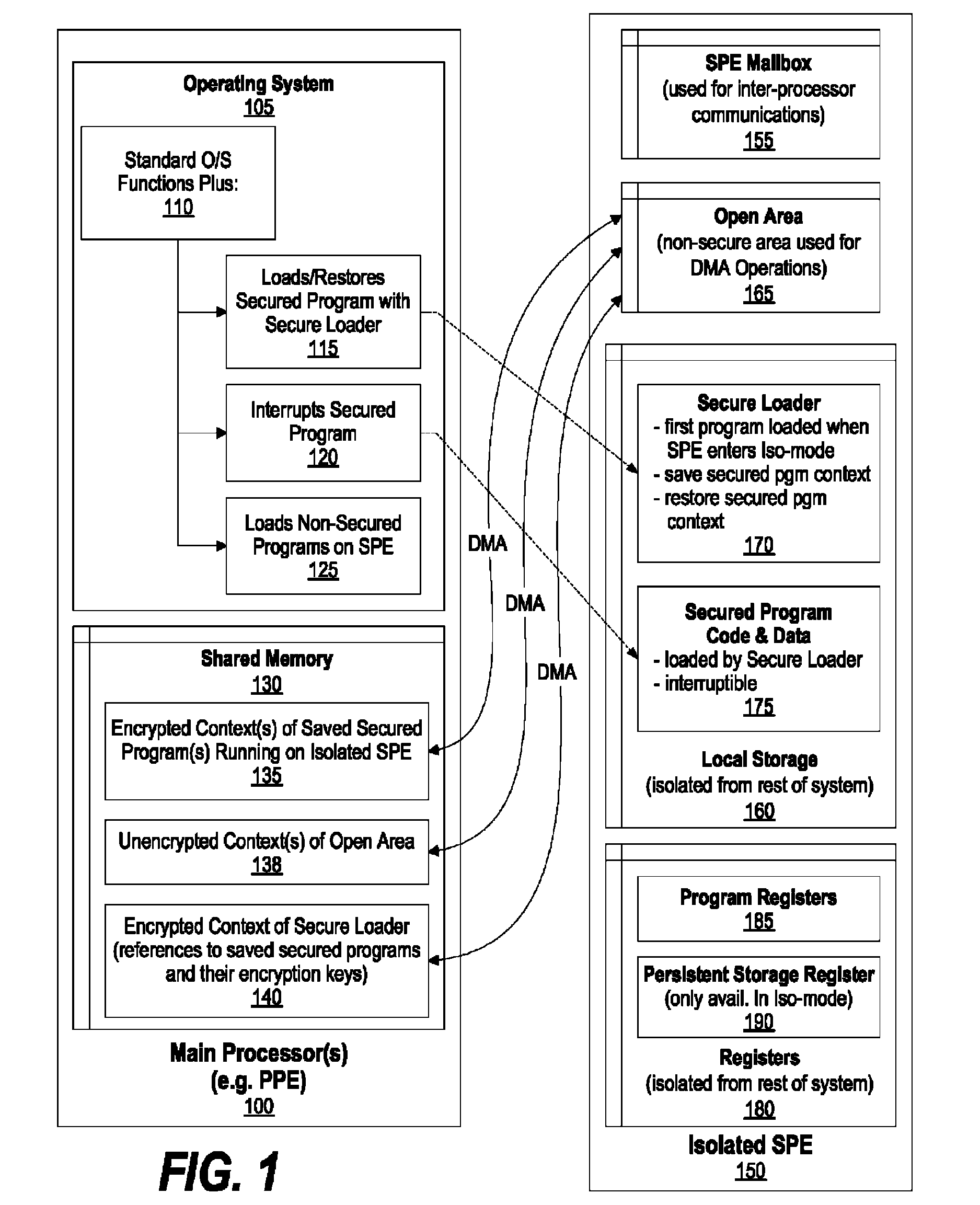
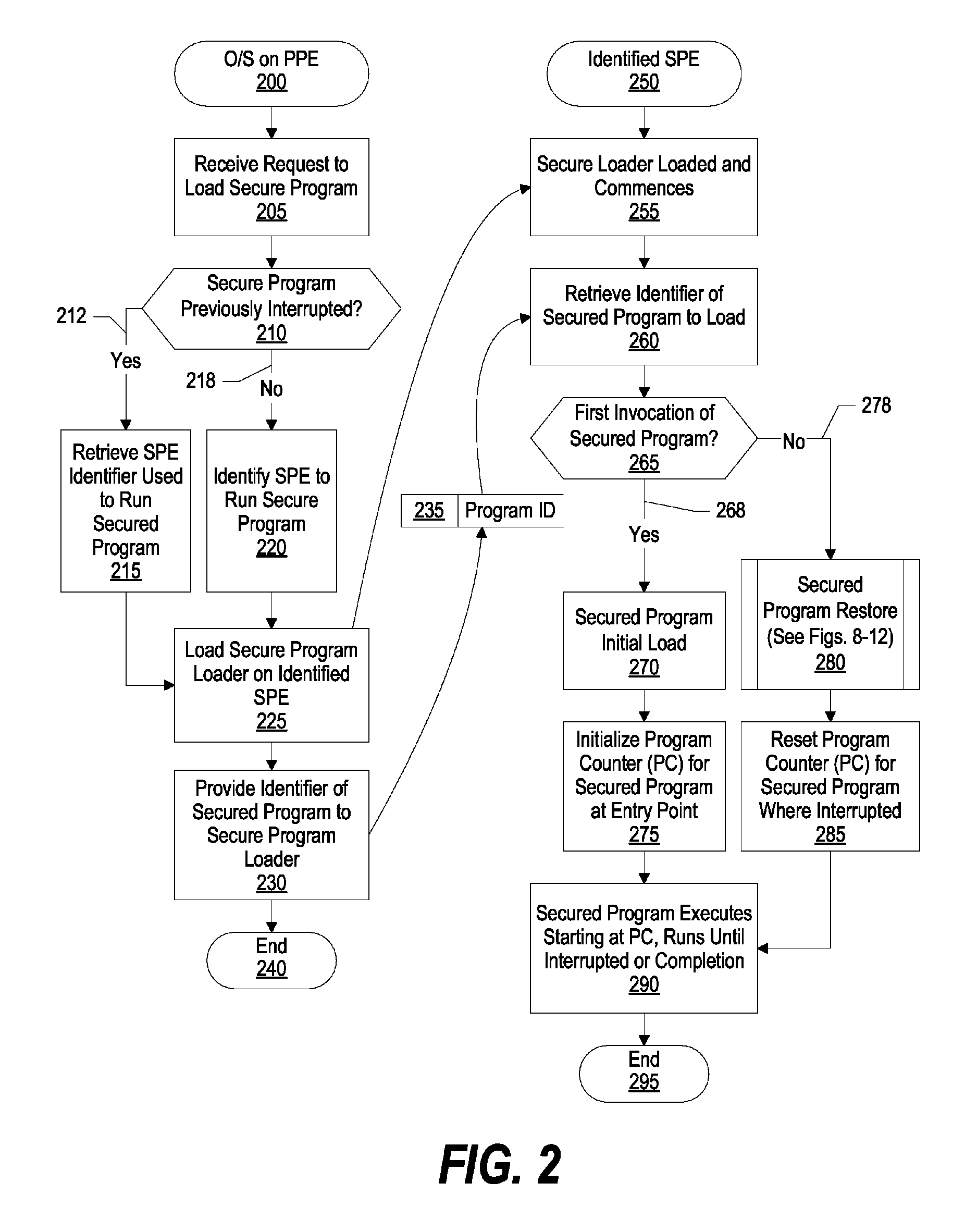
System and Method for Securely Saving a Program Context to a Shared Memory
ActiveUS20080066074A1Program control using stored programsUnauthorized memory use protectionGeneral purposeData value
A system, method and program product for securely saving a program context to a shared memory is presented. A secured program running on an special purpose processor core running in isolation mode is interrupted. The isolated special purpose processor core is included in a heterogeneous processing environment, that includes purpose processors and general purpose processor cores that each access a shared memory. In isolation mode, the special purpose processor core's local memory is inaccessible from the other heterogeneous processors. The secured program's context is securely saved to the shared memory using a random persistent security data. The lines of code stored in the isolated special purpose processor core's local memory are read along with data values, such as register settings, set by the secured program. The lines of code and data values are encrypted using the persistent security data, and the encrypted code lines and data values are stored in the shared memory.
Owner:IBM CORP
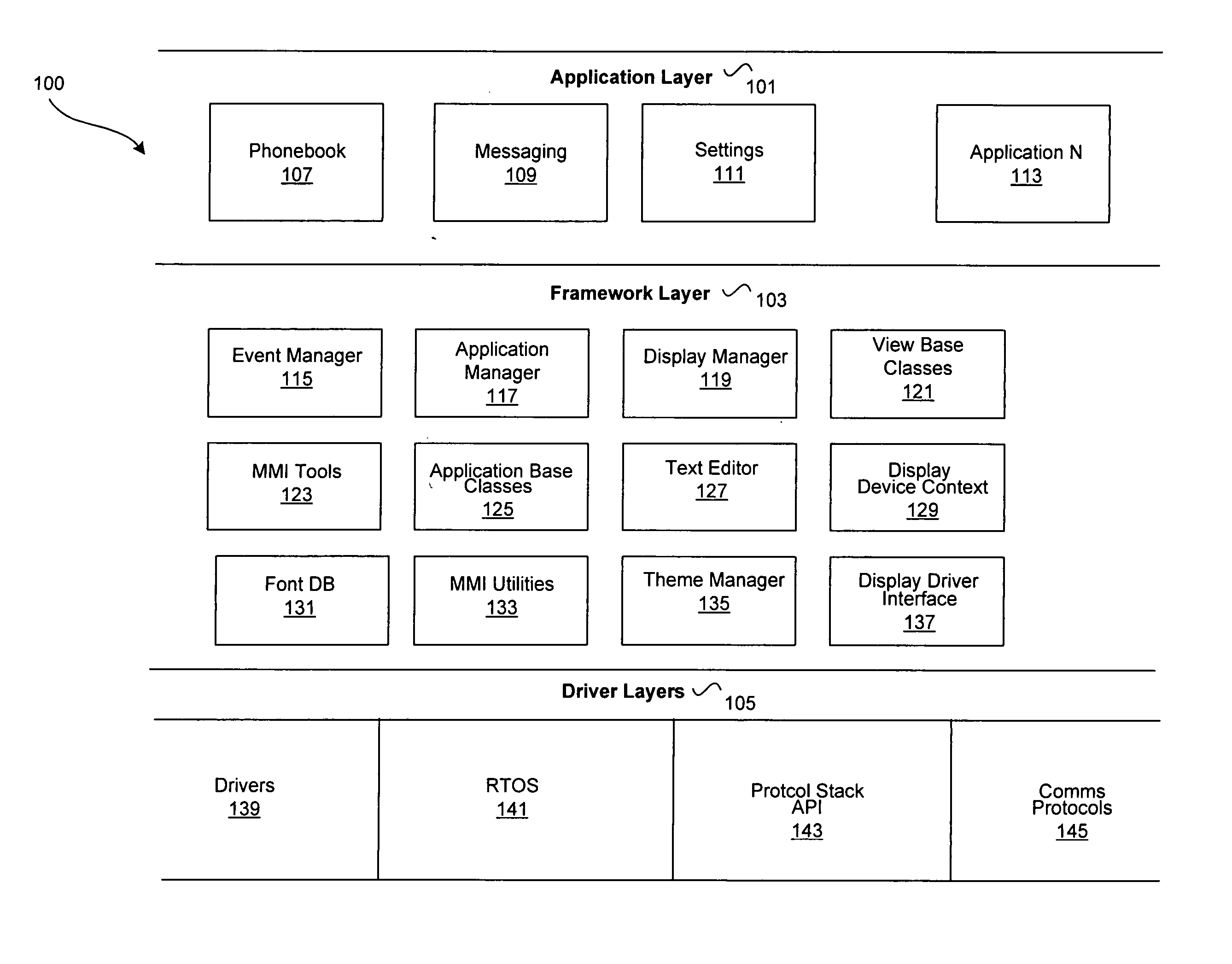
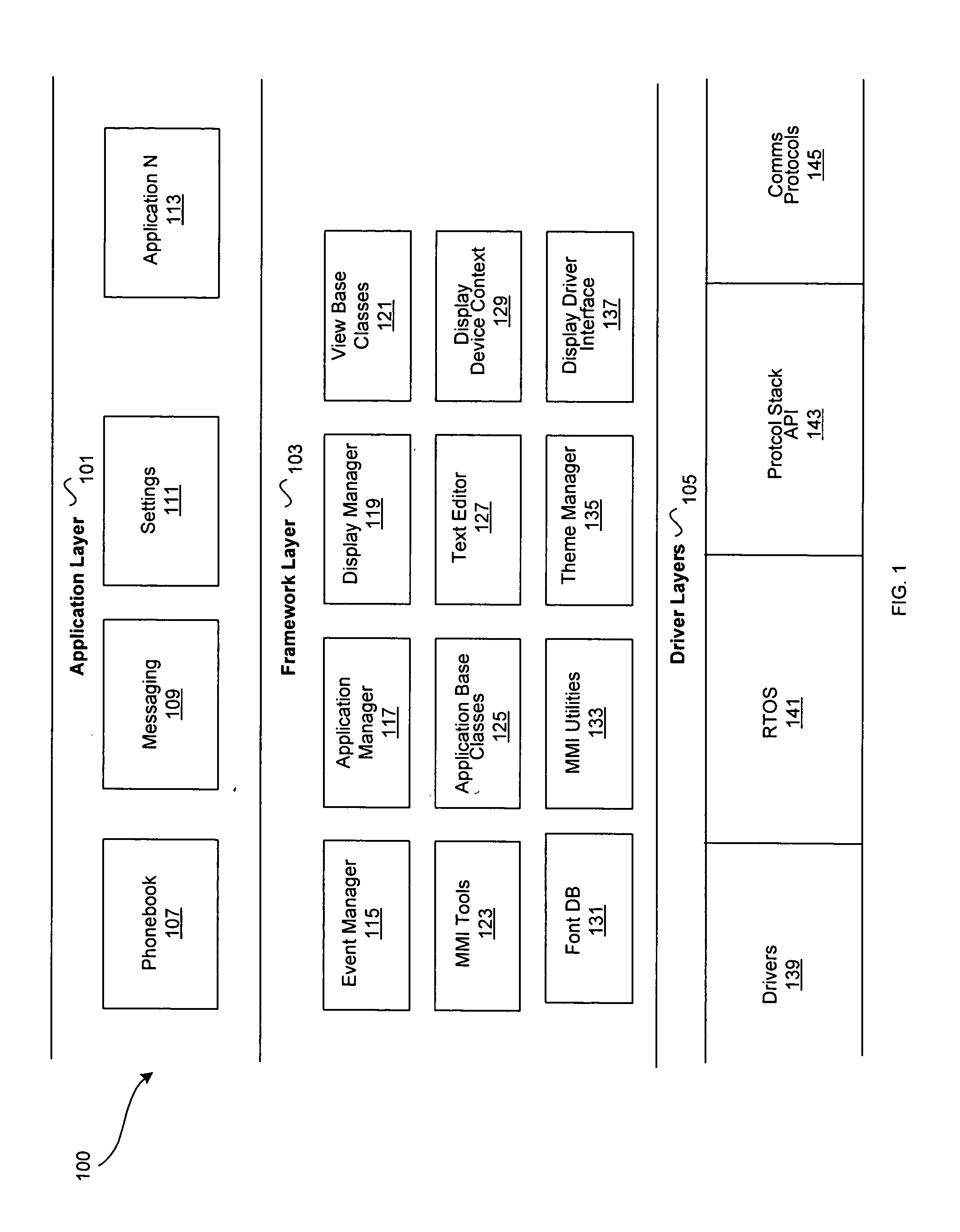
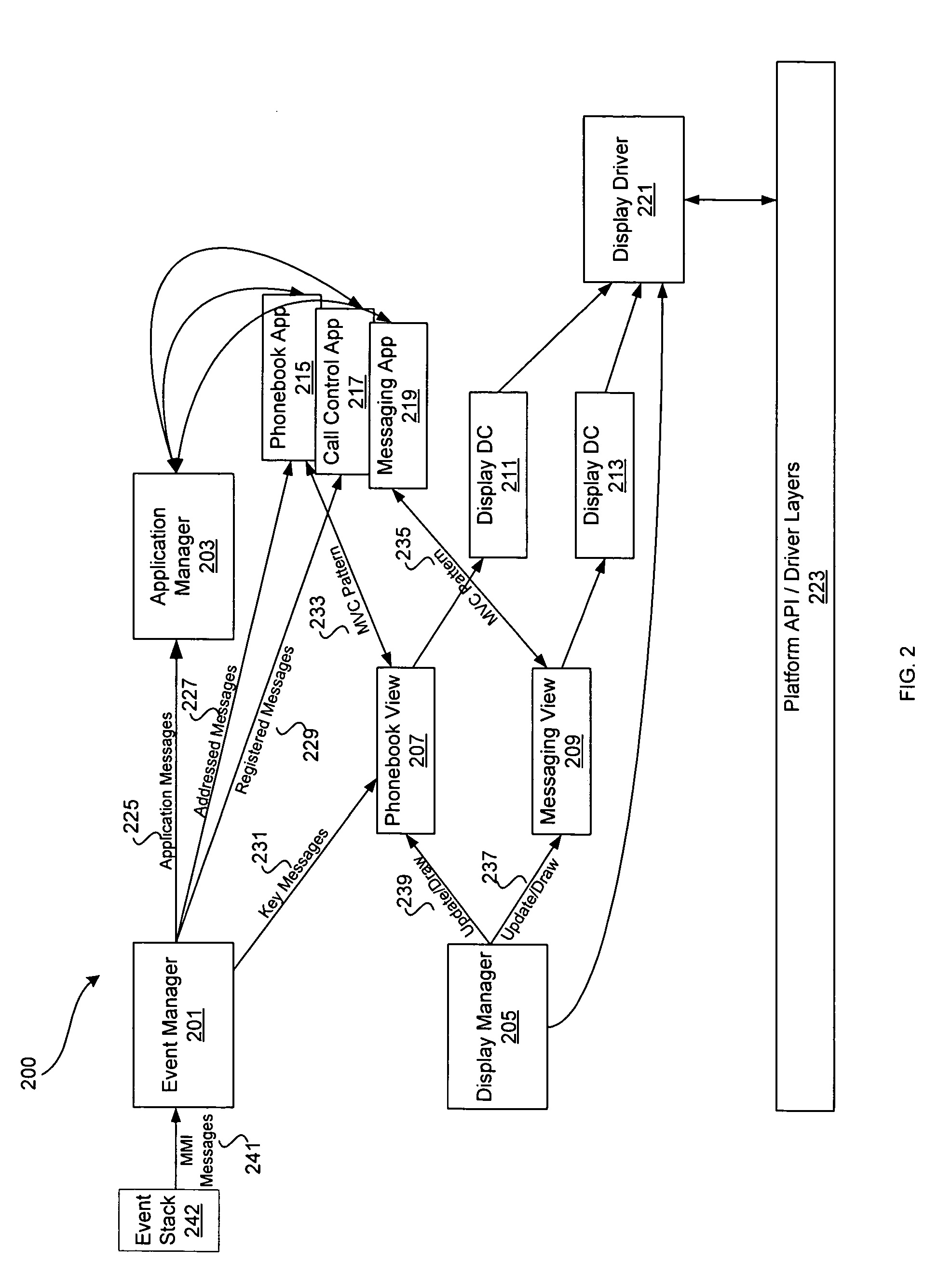
Method and system for an application framework for a wireless device
InactiveUS20050288001A1Interprogram communicationWireless network protocolsMan machineOperating system
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Method and system for implementing mobile device data tracking through software development toolkit
InactiveCN105630512AImprove efficiencyReduce development riskSoftware maintainance/managementSoftware designTraffic capacityInstability
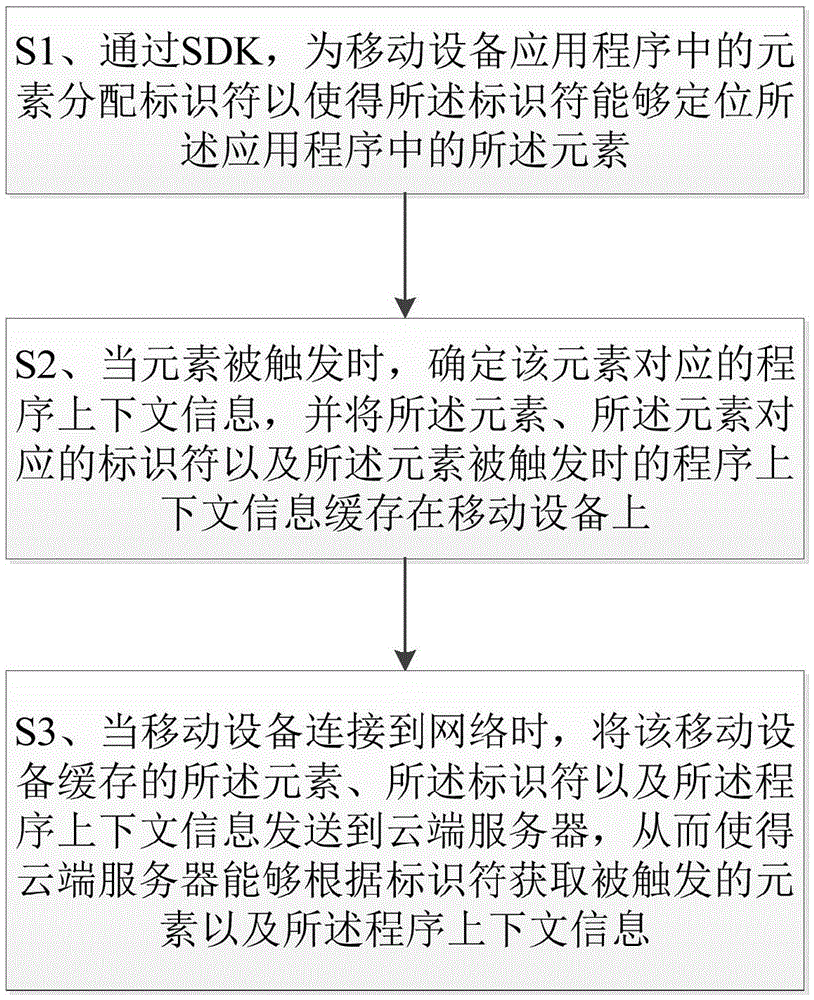
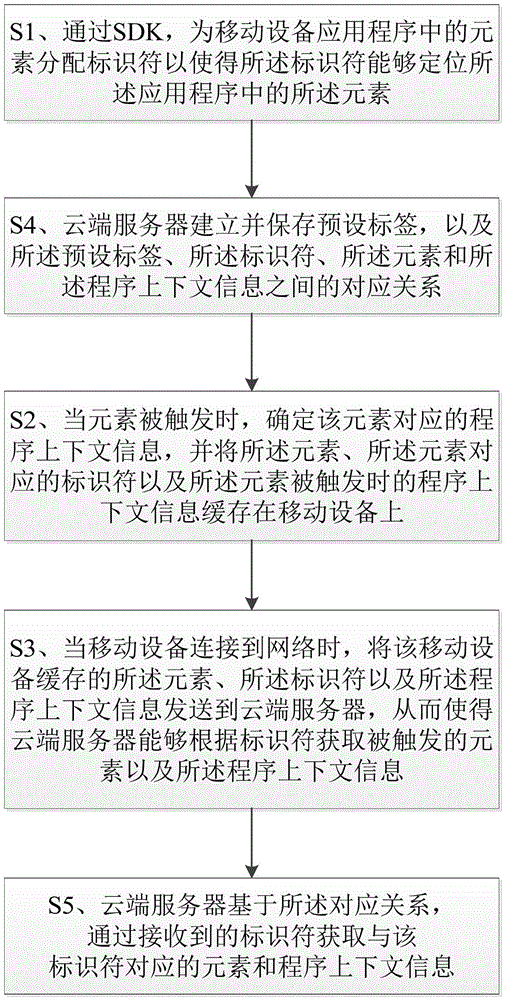
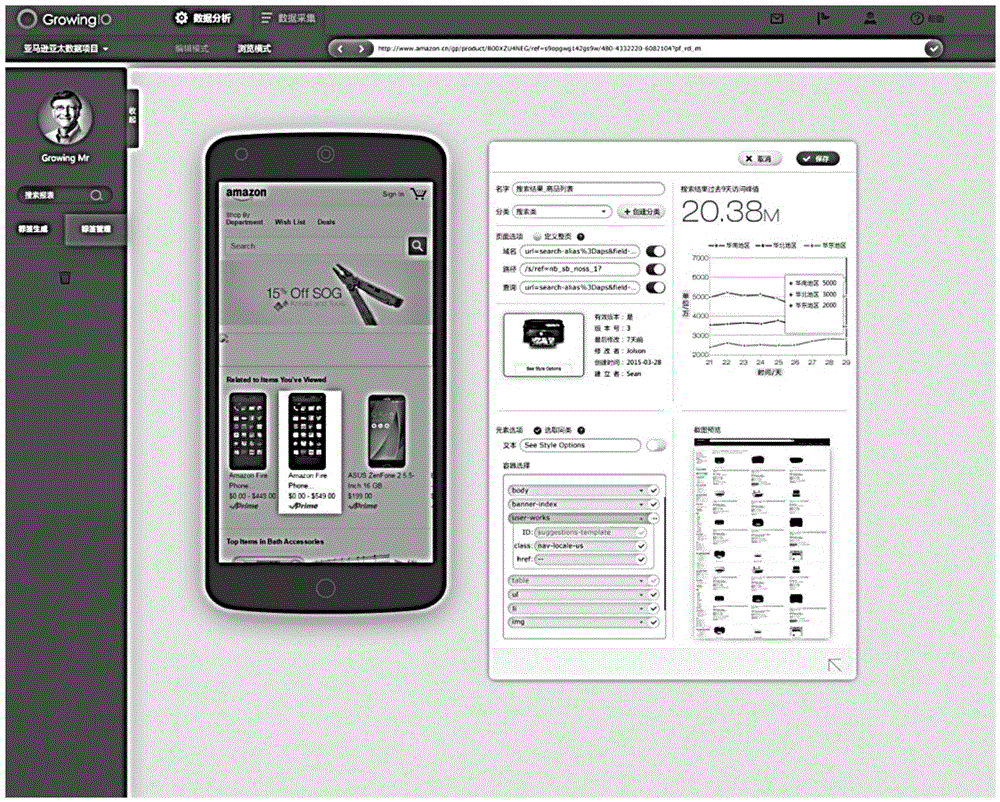
The invention relates to a method and system for implementing mobile device data tracking through a software development toolkit SDK.The method comprises: distributing identifiers for elements in a mobile device application so that the identifiers can position the elements in the application; when the elements are triggered, determining application context information corresponding to the elements, and caching in a mobile device the elements, the identifiers and the application context information obtained when the elements are triggered; when a connection to a network is made, transmitting the elements, the identifiers and the application context information cached in the mobile device to a cloud server so that the cloud server can acquire the elements and the application context information according to the received identifiers; the application context information contains trigger time, displayed time of a page of the elements, means of trigger and the like, and therefore, data tracking efficiency can be improved and labor resource cost can be saved.In addition, data caching prevents repeated retry in case of network instability and also prevents unnecessary traffic loss.
Owner:BEIJING GAOYI INFORMATION TECH CO LTD
Techniques for implementing security on a small footprint device using a context barrier
InactiveUS20050091659A1Specific access rightsDigital data processing detailsProgramming languageSmart card
A small footprint device, such as a smart card, can securely run multiple programs from unrelated vendors by the inclusion of a context barrier isolating the execution of the programs. The context barrier performs security checks to see that principal and object are within the same namespace or memory space and to see that a requested action is appropriate for an object to be operated upon.
Owner:ORACLE INT CORP
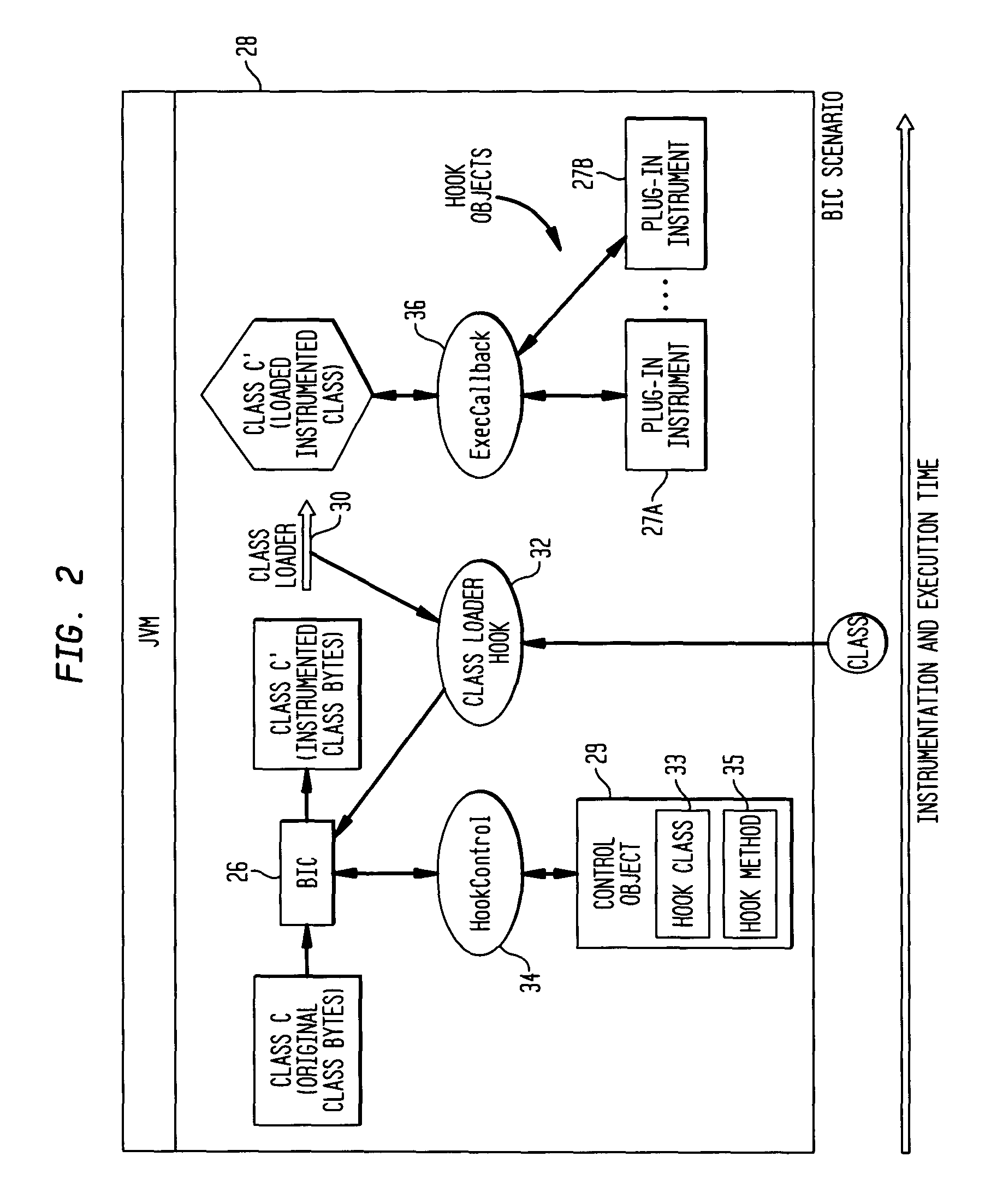
Method and apparatus for context oriented computer program tracing and visualization
InactiveUS20070150870A1Error detection/correctionSpecific program execution arrangementsProgram codeInstrumentation
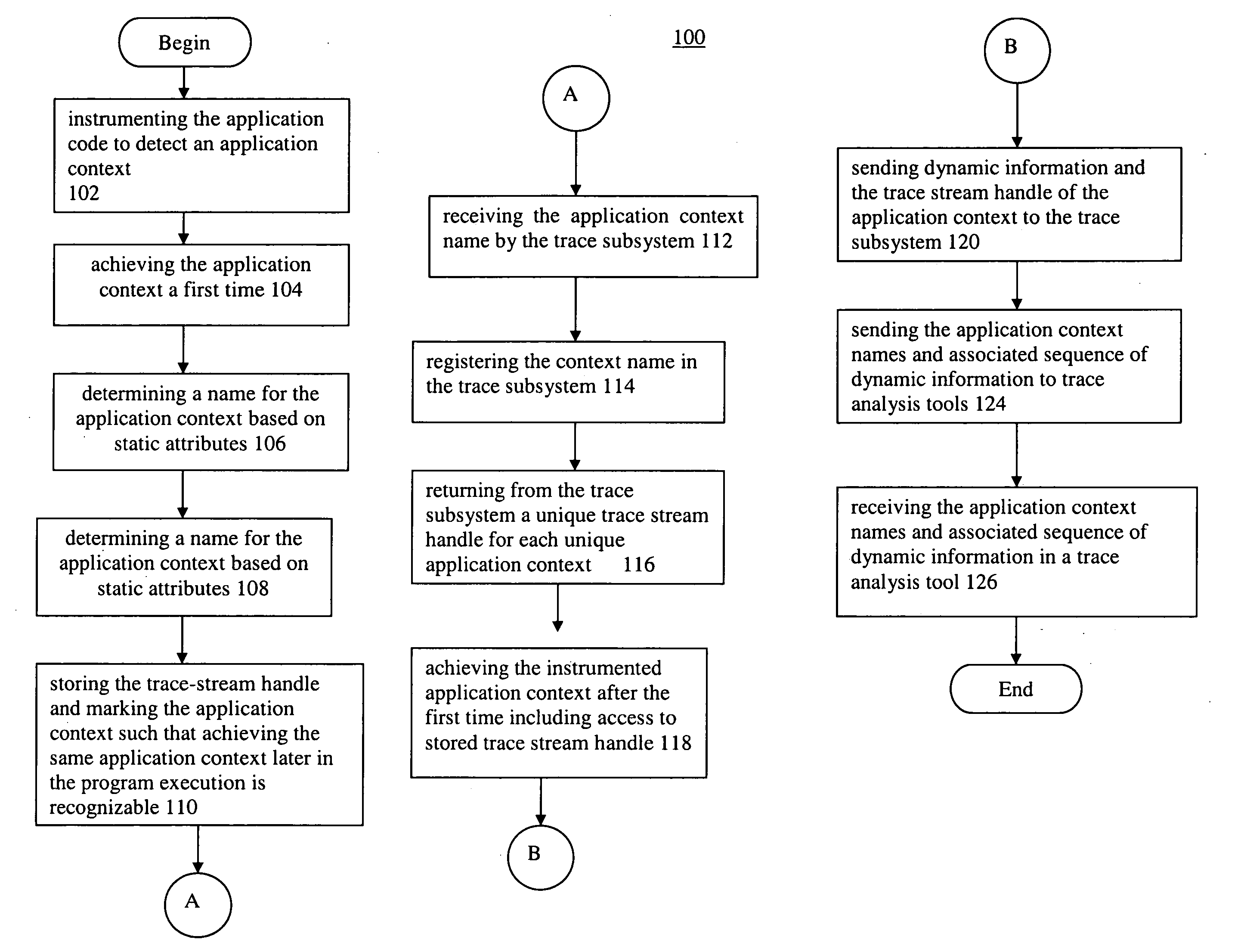
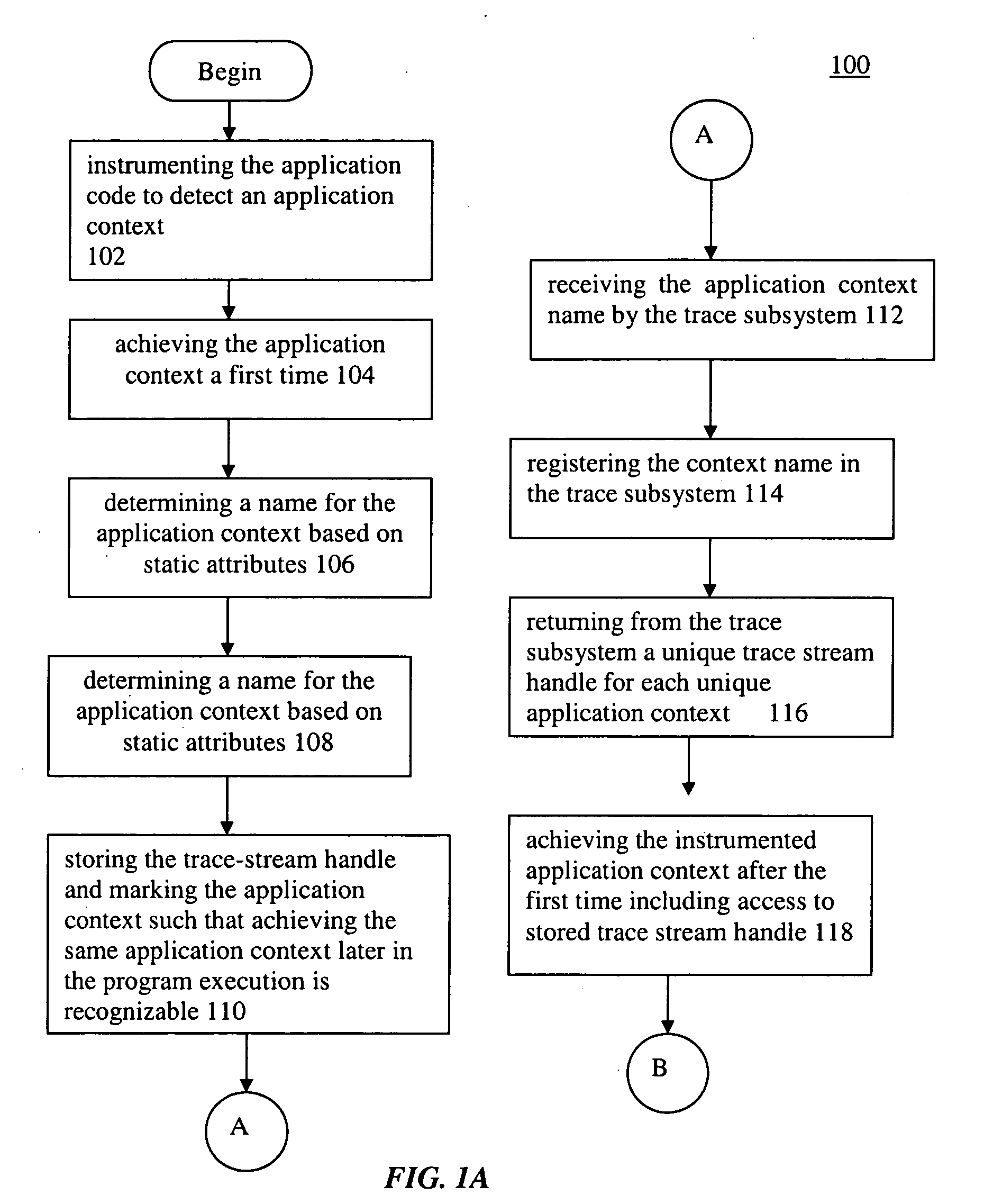
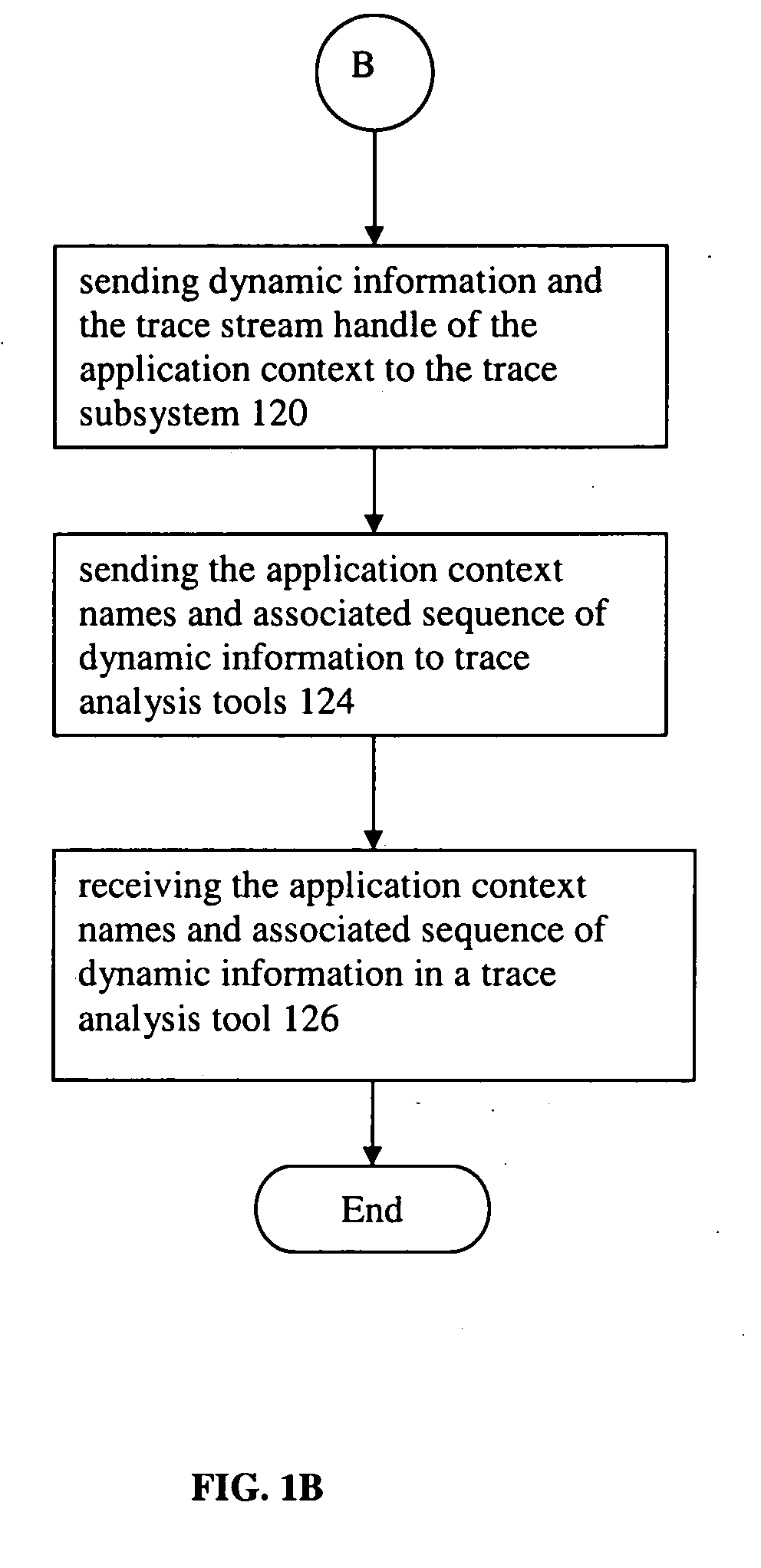
A computer-implemented method for collecting trace streams in application code, instruments the application code to detect an application context. The application context includes static and dynamic attributes. The method also includes steps of: achieving the application context a first time, collecting static attributes of the application context, determining a name for the application context based on static attributes, sending the application context name to the trace subsystem and receiving a trace stream handle in return, storing the trace-stream handle and marking the application context such that achieving the same application context later in the program execution is recognizable, receiving the application context name by the trace subsystem, registering the context name in the trace subsystem, returning from the trace subsystem a unique trace stream handle for each unique application context, achieving the instrumented application context after the first time including access to stored trace stream handle, sending dynamic information and the trace stream handle of the application context to the trace subsystem, sending the application context names and associated sequence of dynamic information to trace analysis tools, and receiving the application context names and associated sequence of dynamic information in a trace analysis tool.
Owner:IBM CORP
Gaming machine having game play suspension and resumption features using biometrically-based authentication and method of operating same
InactiveUS7979740B2Electric signal transmission systemsDigital data processing detailsData matchingBiometric data
Owner:MUDALLA TECH
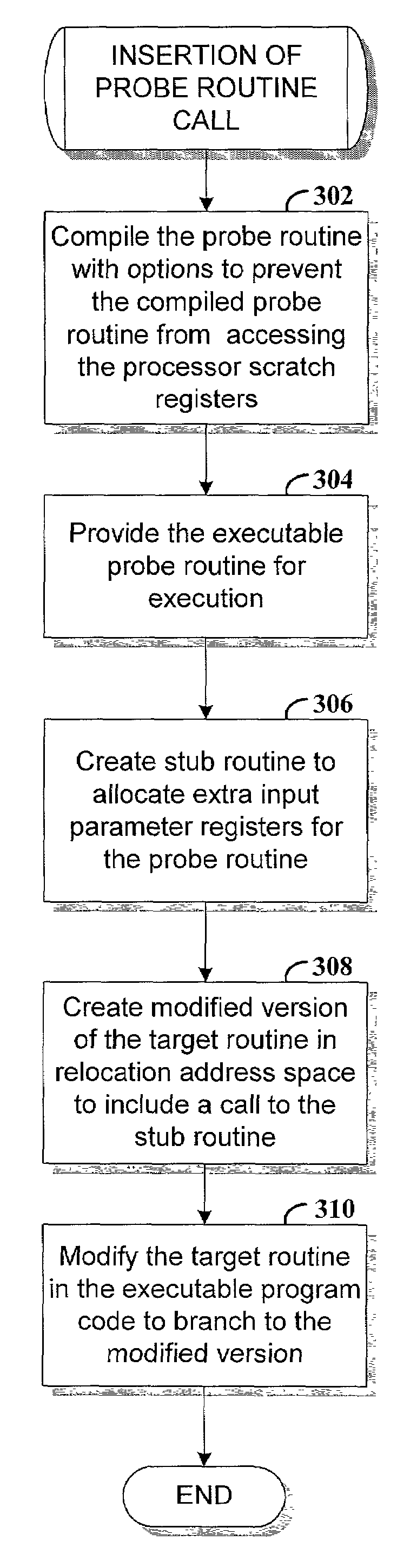
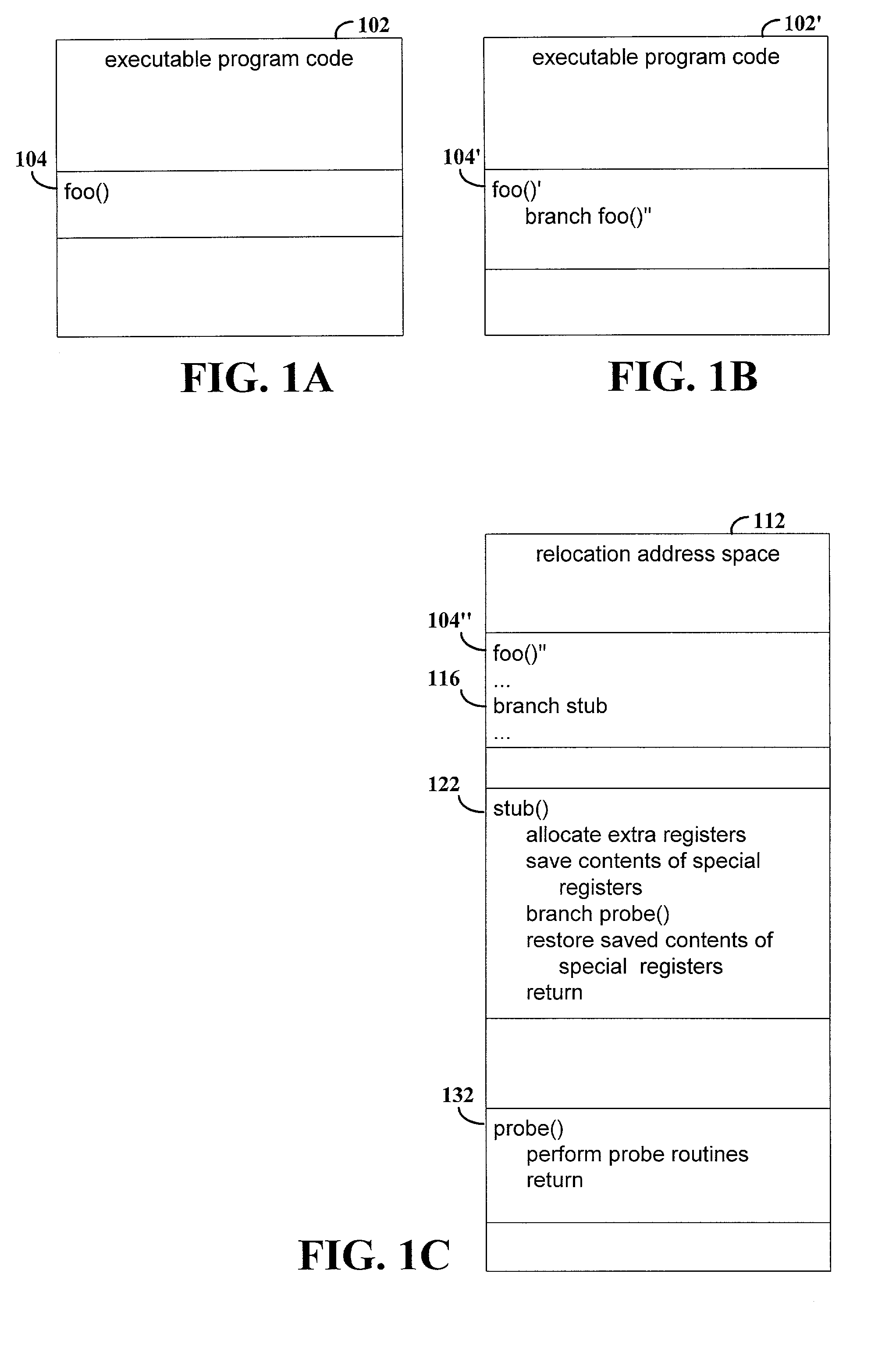
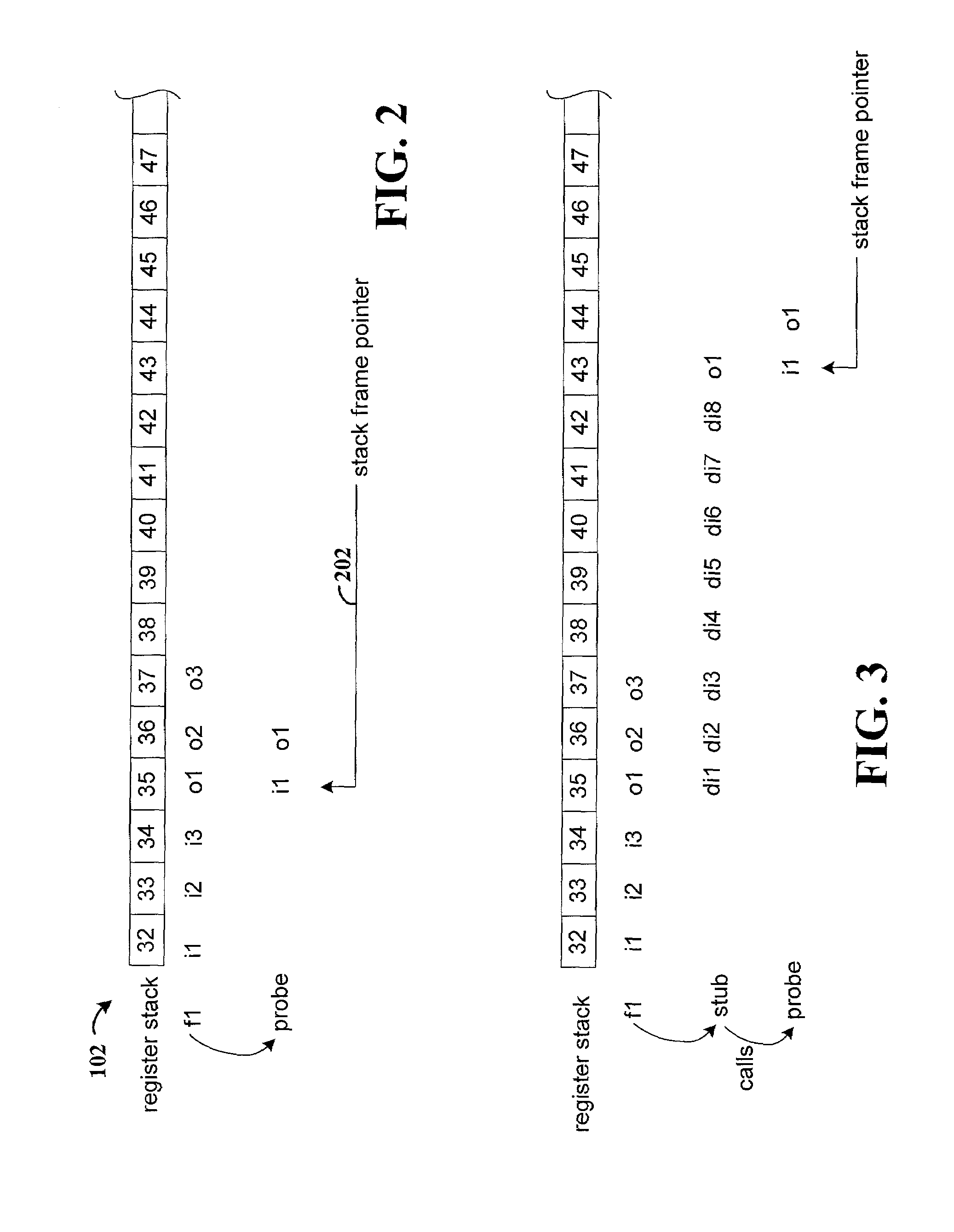
Preserving program context when adding probe routine calls for program instrumentation
ActiveUS7107579B2Content of may changeSpecific program execution arrangementsMemory systemsProcessor registerParallel computing
Method and apparatus for preserving program context when causing execution of a probe routine from a target routine of an executable computer program code. Executable code for the probe routine is created such that the probe routine does not reference a first set of registers that are usable by the target routine. A modified version of the target routine is created to cause execution of the probe routine. The modified version of the target routine is performed instead of the original version when the target routine is called during program execution. A second set of registers on the processor register stack is allocated when the probe routine is invoked. The second set of registers is not manipulated by the probe routine so as to avoid changing contents of registers of the register stack that are used by the target routine.
Owner:HTC CORP
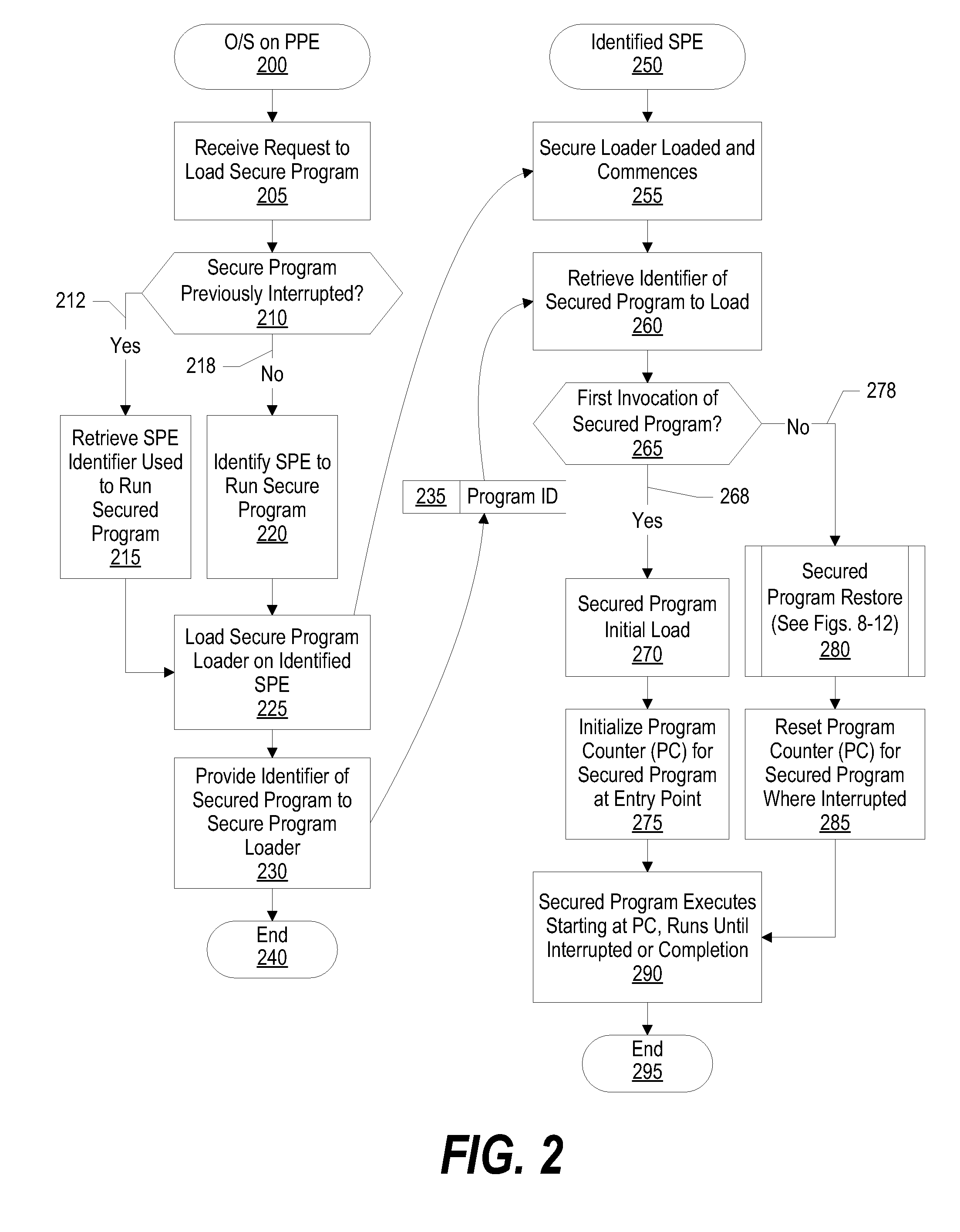
System and Method for Securely Restoring a Program Context from a Shared Memory
InactiveUS20080065907A1User identity/authority verificationUnauthorized memory use protectionContextual integrityLocal memories
A system and method for securely restoring software program context is presented. A special purpose processor core is included in a heterogeneous processing environment where each processor can access a shared memory. The isolated special purpose processor core includes an isolated local memory. The isolated special purpose processor core receives an identifier corresponding to the secured program. The identifier is used to read an encrypted context of the secured program from the shared memory. The encrypted context is decrypted using an encryption key. The decrypted context is stored in the isolated special purpose processor core's local memory. The secured program's context integrity is verified by using a persistent security data that is retrieved from a secure location, such as a persistent storage register that can only be accessed when the special purpose processor core is running in isolation mode. If the context is verified, the secured program is executed.
Owner:IBM CORP
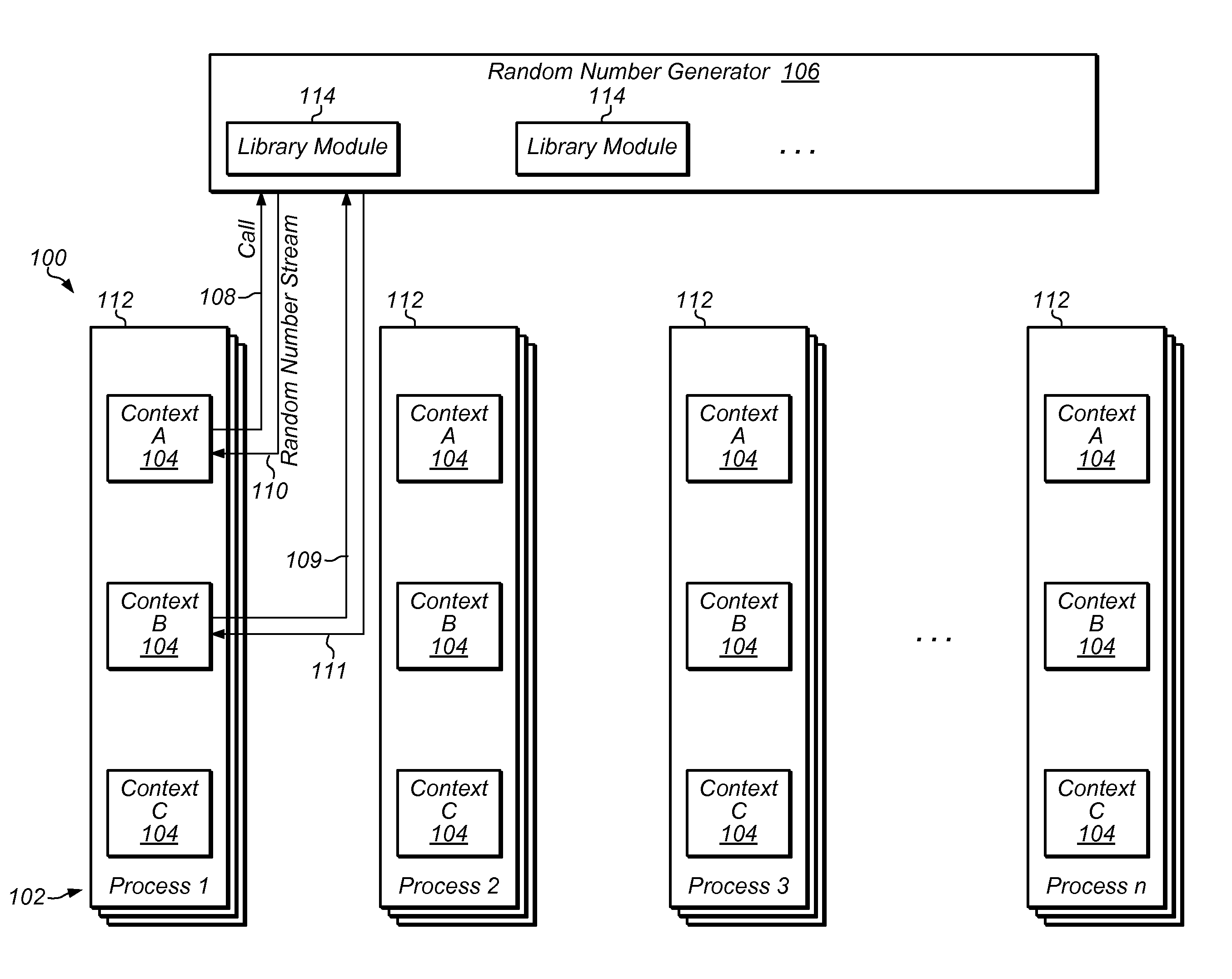
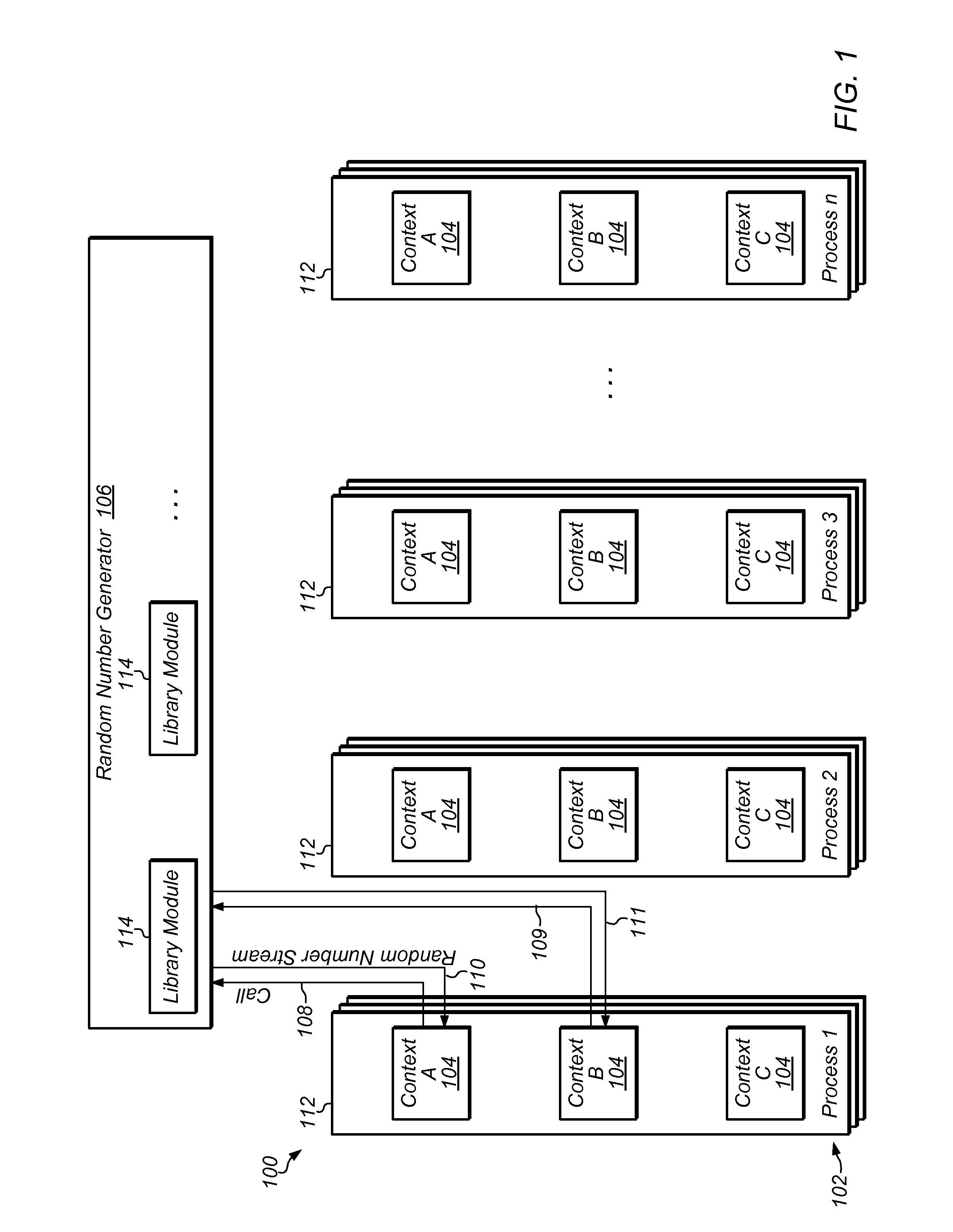
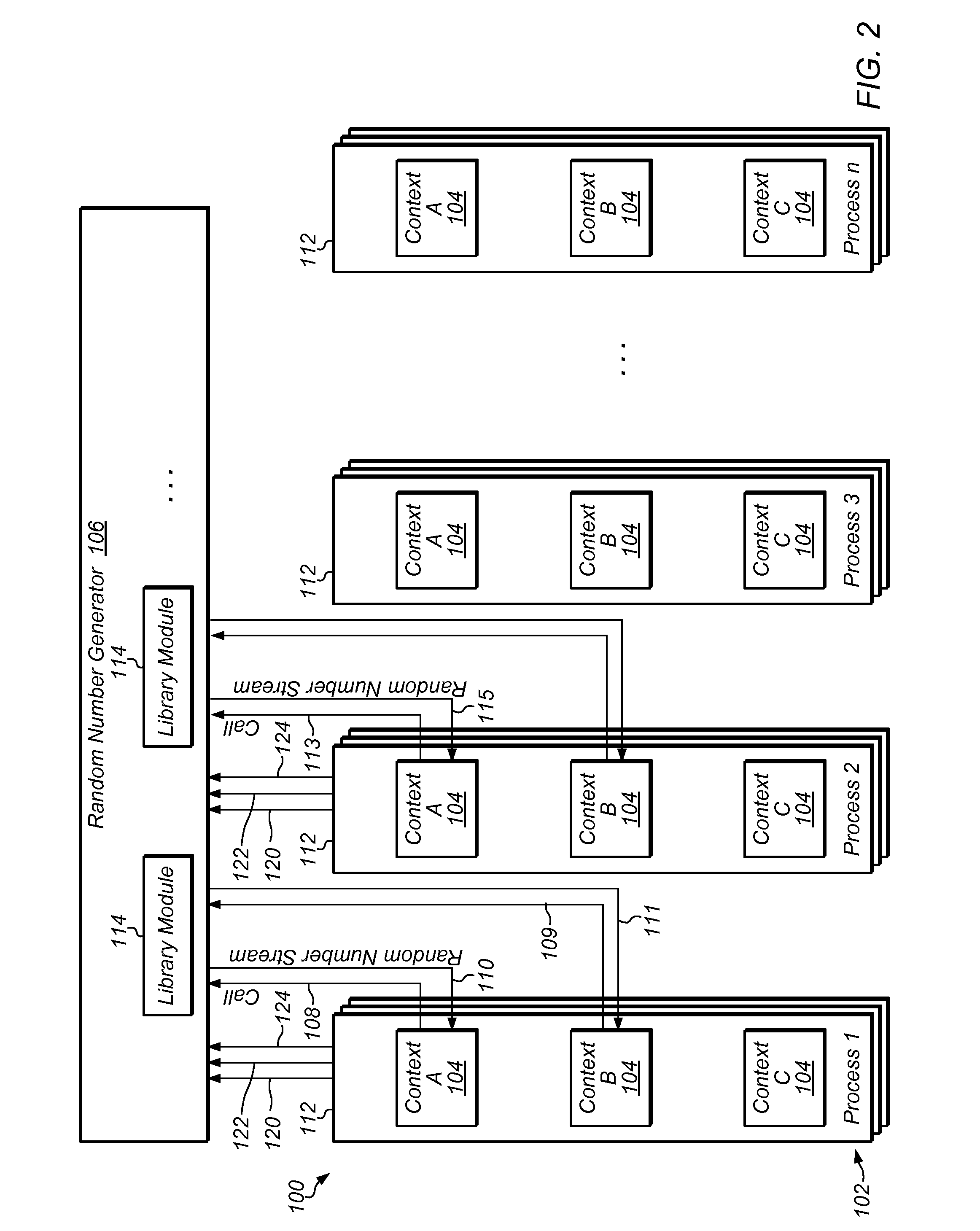
Generation of distinct pseudorandom number streams based on program context
A method of providing random number streams to a process includes determining two or more program contexts within a process. Each of the program contexts may include code that calls for one or more random numbers. For each of at least two of the program contexts, a random number stream is provided to the process. The random number stream for each program context is based on the determined program context and is distinct from the random number stream for the other program contexts in the process.
Owner:BOARD OF RGT THE UNIV OF TEXAS SYST
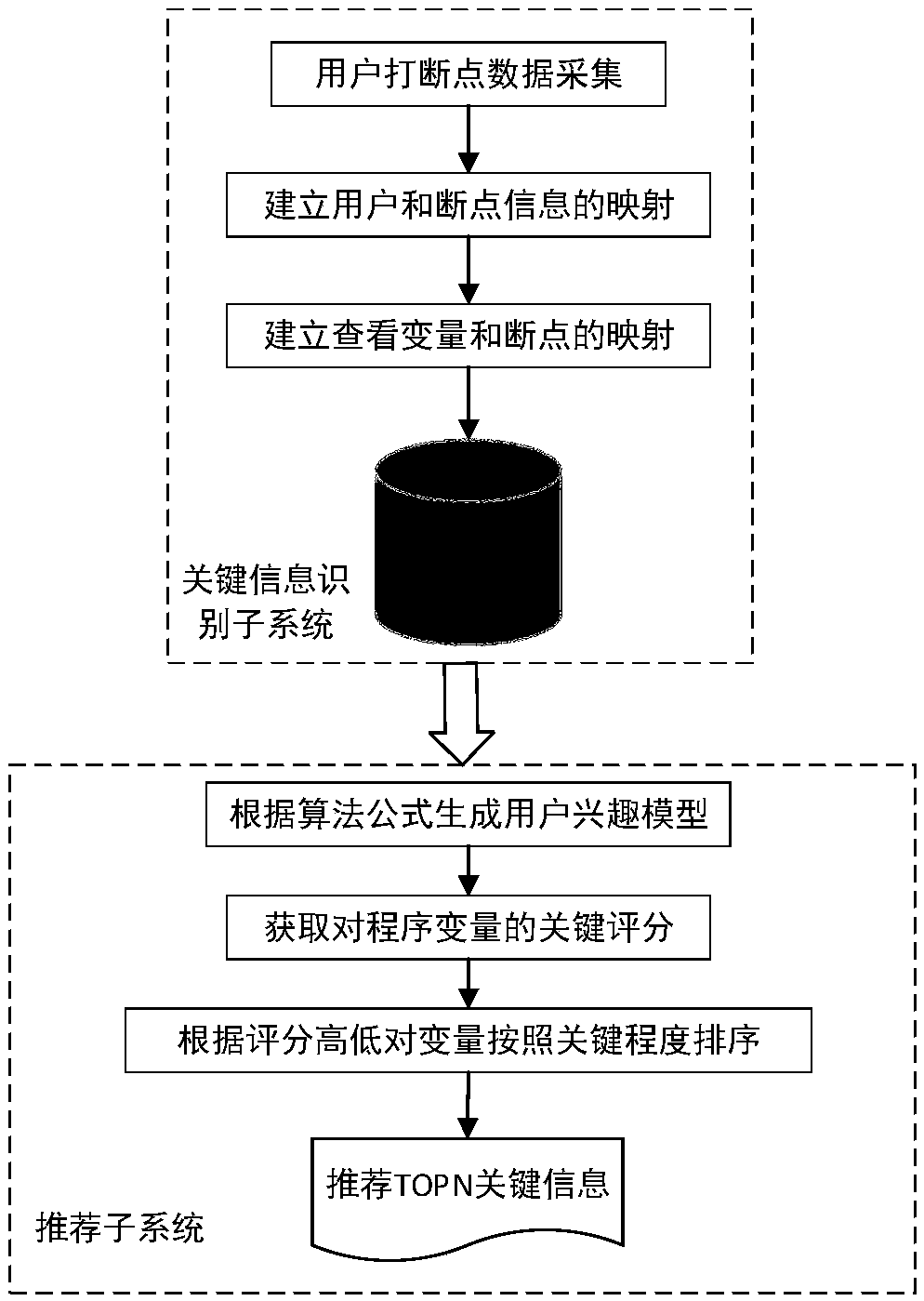
Interpreter language debugging method and device
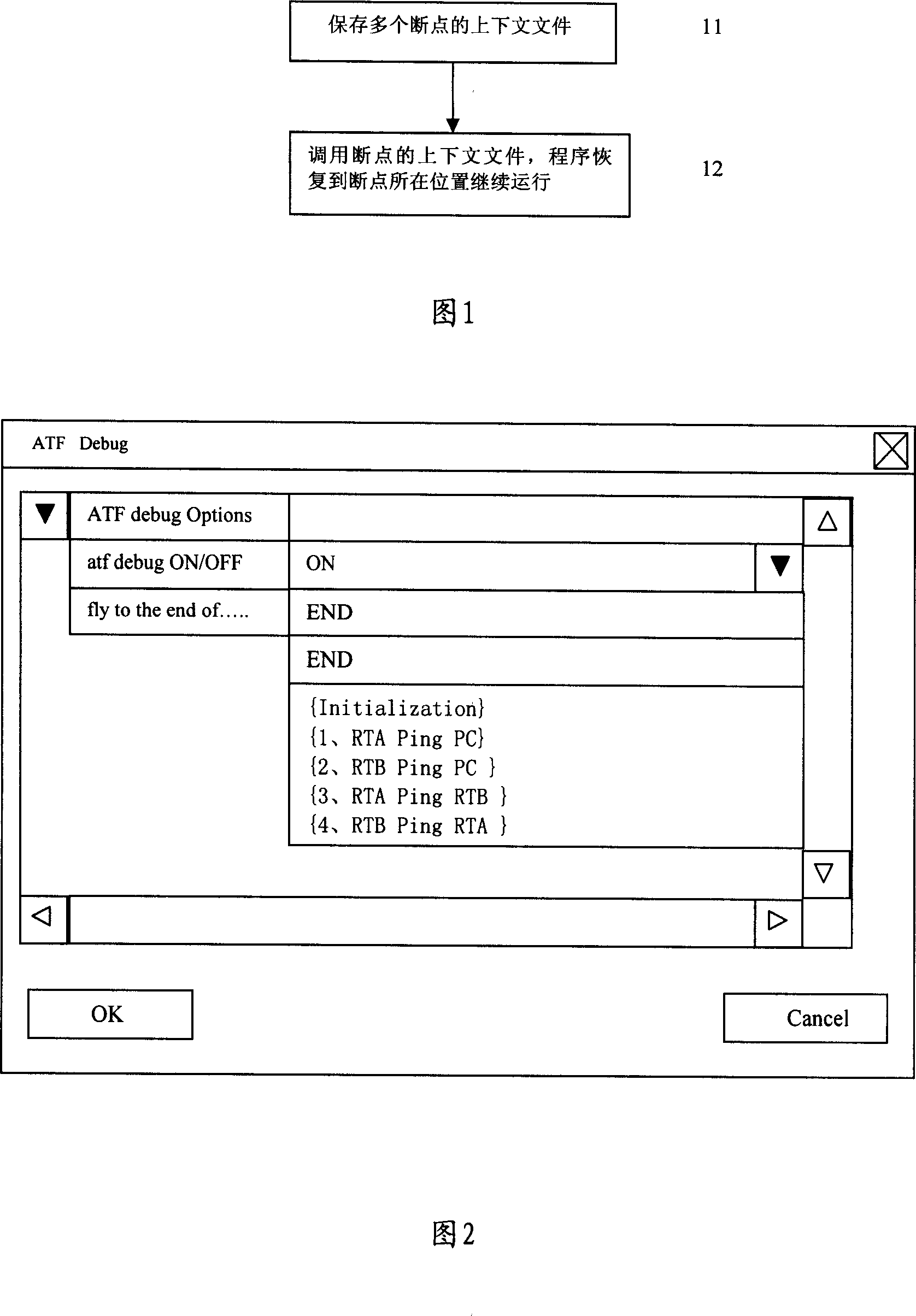
InactiveCN101021812AFast and efficient commissioningSoftware testing/debuggingInterpreters languageHuman language
The invention relates to a method and device for debugging interpretations. The method includes: It saves a number of breakpoints in the context of files. It chooses breakpoint for jump and calls the context of relate to the breakpoint in the document to restore the interpretation program to the location of breakpoint and operates the program continually. The described device includes: a preservation module is used for preserving the context related to the breakpoints during the process of interpretation, and a recovery module is used for calling the context of relate to the breakpoint to restore interpretation program to the location of breakpoint.
Owner:HUAWEI TECH CO LTD
System and method for securely restoring a program context from a shared memory
InactiveUS7945789B2Unauthorized memory use protectionHardware monitoringContextual integrityComputer science
A system and method for securely restoring software program context is presented. A special purpose processor core is included in a heterogeneous processing environment where each processor can access a shared memory. The isolated special purpose processor core includes an isolated local memory. The isolated special purpose processor core receives an identifier corresponding to the secured program. The identifier is used to read an encrypted context of the secured program from the shared memory. The encrypted context is decrypted using an encryption key. The decrypted context is stored in the isolated special purpose processor core's local memory. The secured program's context integrity is verified by using a persistent security data that is retrieved from a secure location, such as a persistent storage register that can only be accessed when the special purpose processor core is running in isolation mode. If the context is verified, the secured program is executed.
Owner:INT BUSINESS MASCH CORP
Provisioning seamless applications in mobile terminals through registering and transferring of application context
ActiveUS7908378B2Data switching by path configurationMultiple digital computer combinationsAccess networkService domain
Service provisioning in mobile terminals is provided through registering and transferring of application context, which permits substantially seamless transfer of application functionality across administrative service domains. An architecture for providing application context transfer may include access routers, transcoder proxy servers, and gateway routers. A mobile terminal served by a current access router creates an application context for a session and registers it with the current access router. Around the time of handoff, the current access router transfers the application context to a new access router associated with a new administrative domain and a new access network. The new access router evaluates the application context and takes steps to provide application functionality for the mobile terminal and current sessions. These steps may include the use of a network entity, such as a transcoder proxy server, to modify data for a session and thereby provide application functionality in the new administrative domain.
Owner:WSOU INVESTMENTS LLC
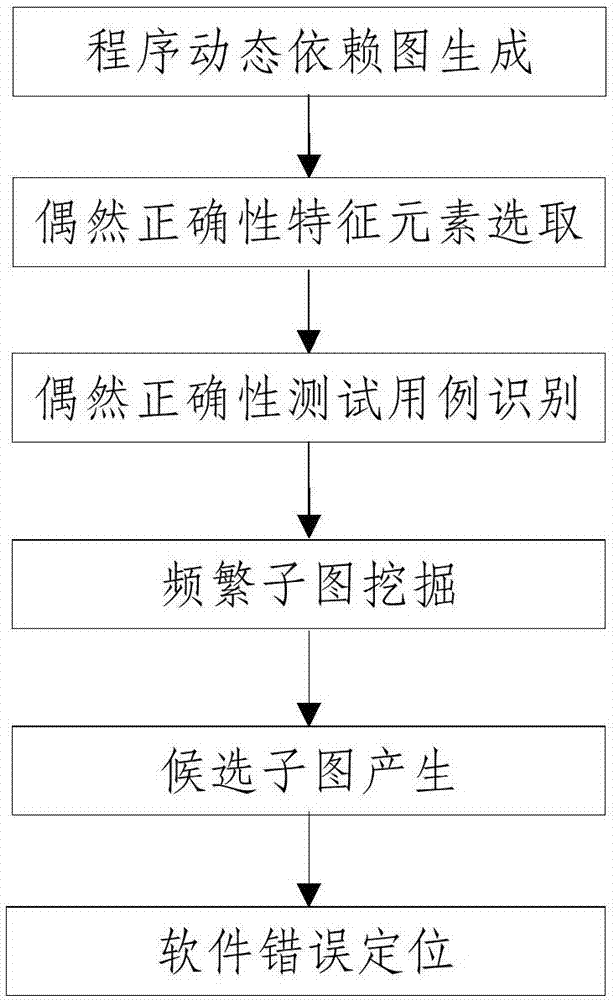
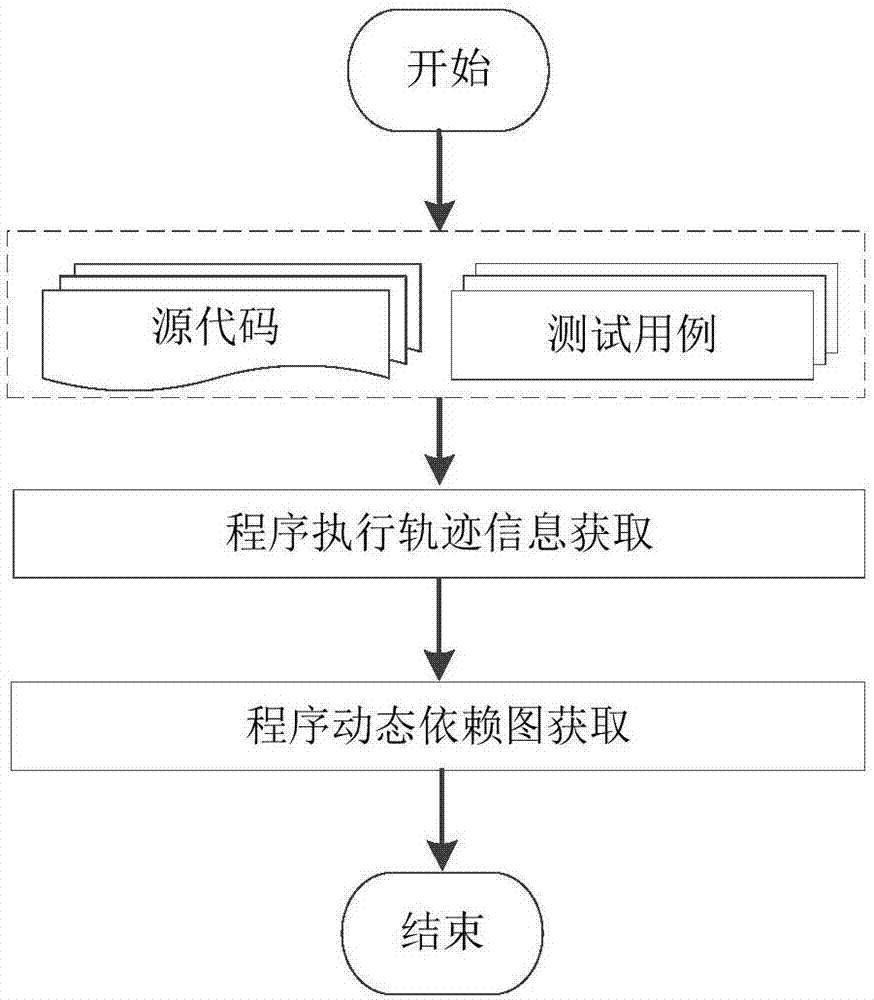
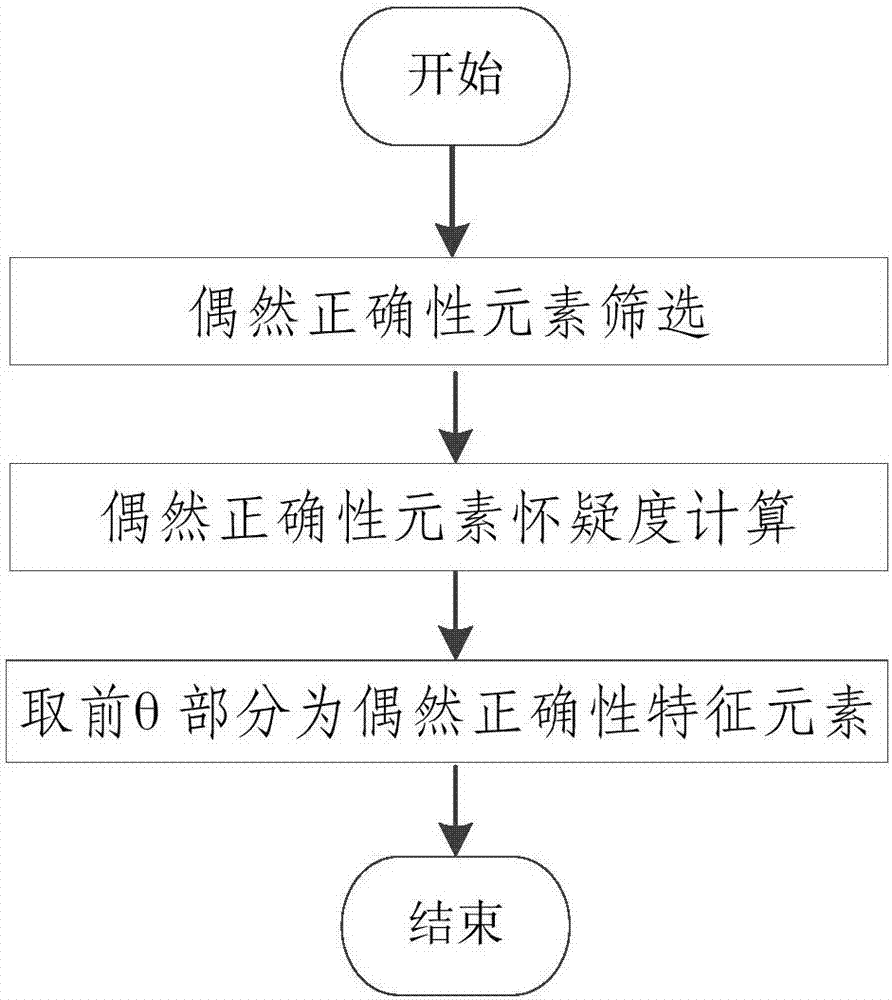
Software error locating method based on frequent subgraph mining and processing device
The invention relates to the technical field of software testing, in particular to a software error locating method based on frequent subgraph mining and a processing device. According to the method,an accidental correctness program dynamic dependence graph in a program dynamic dependence graph generated by a program dynamic dependence relationship in test case acquiring software is removed at first, then the program dynamic dependence graph without accidental correctness is mined by using a frequent subgraph algorithm, thus, error locating is carried out, error associated program contextualinformation is obtained, debugging information which contains context is provided for developers, the developers can understand error locating results favorably, the error locating precision is improved favorably, and the problem that the error locating efficiency in an existing software error positioning process is low is solved.
Owner:HENAN UNIVERSITY OF TECHNOLOGY
System and method for securely saving a program context to a shared memory
ActiveUS8095802B2Program control using stored programsUnauthorized memory use protectionGeneral purposeData value
A system, method and program product for securely saving a program context to a shared memory is presented. A secured program running on an special purpose processor core running in isolation mode is interrupted. The isolated special purpose processor core is included in a heterogeneous processing environment, that includes purpose processors and general purpose processor cores that each access a shared memory. In isolation mode, the special purpose processor core's local memory is inaccessible from the other heterogeneous processors. The secured program's context is securely saved to the shared memory using a random persistent security data. The lines of code stored in the isolated special purpose processor core's local memory are read along with data values, such as register settings, set by the secured program. The lines of code and data values are encrypted using the persistent security data, and the encrypted code lines and data values are stored in the shared memory.
Owner:INT BUSINESS MASCH CORP
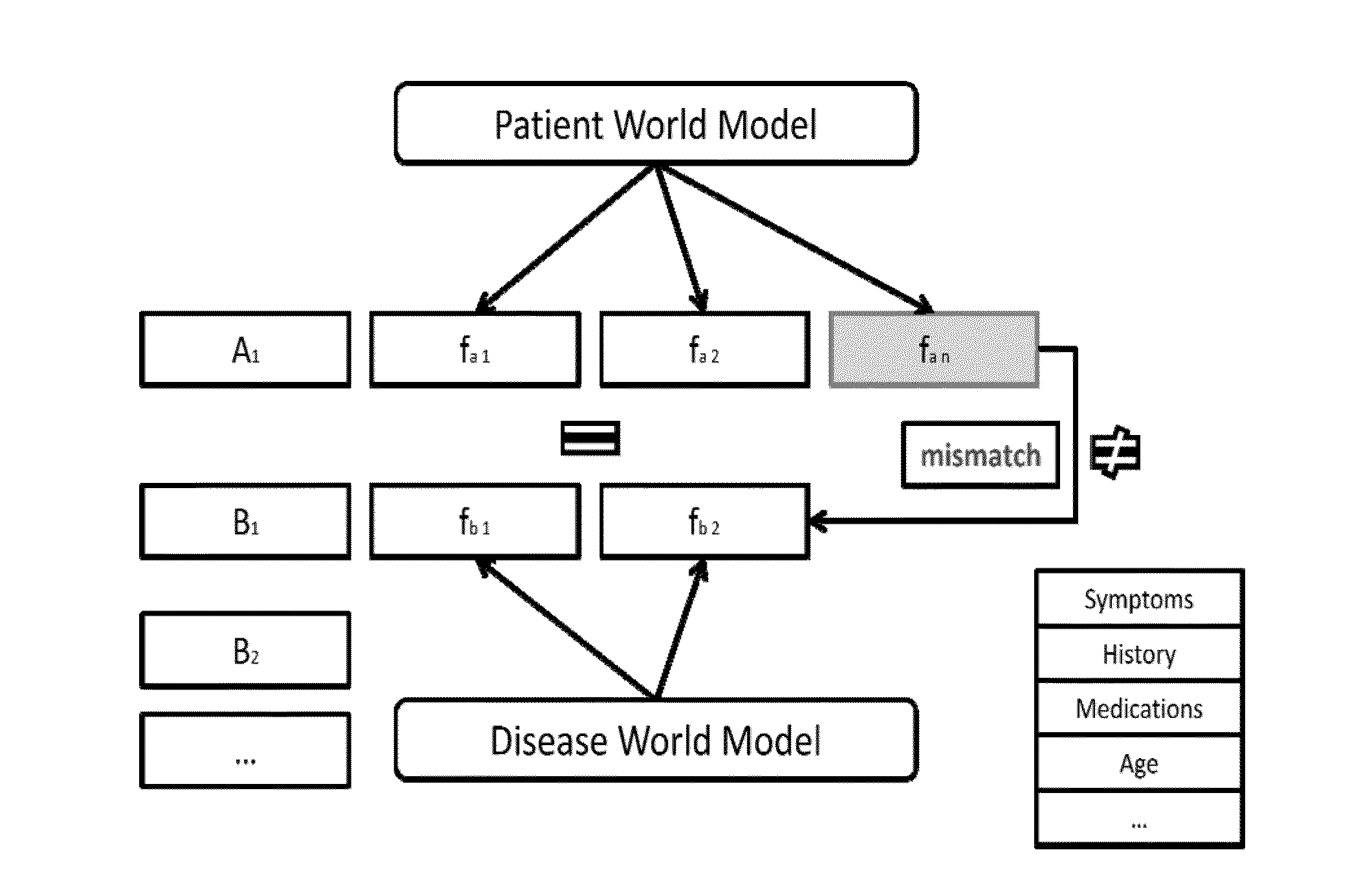
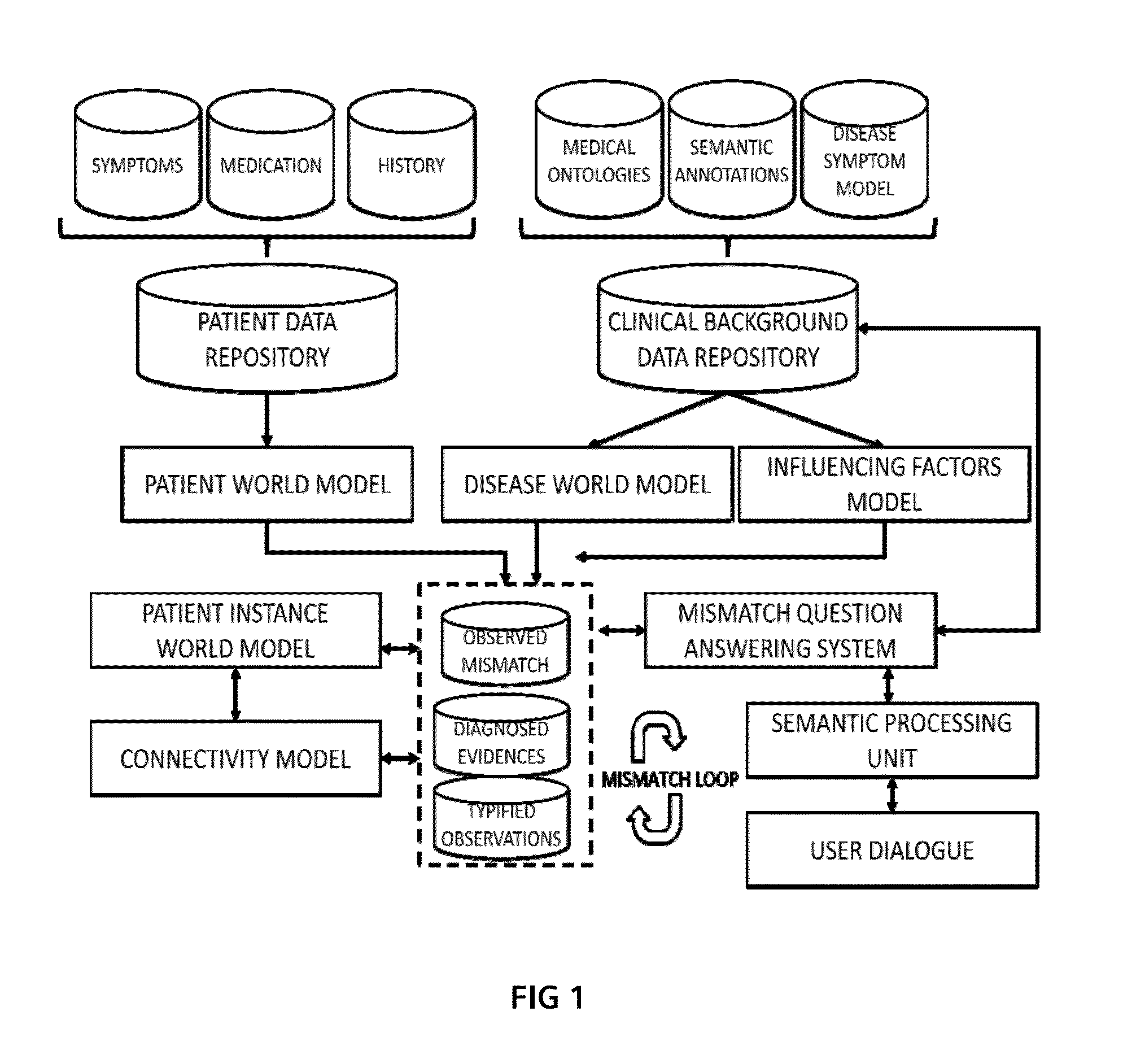
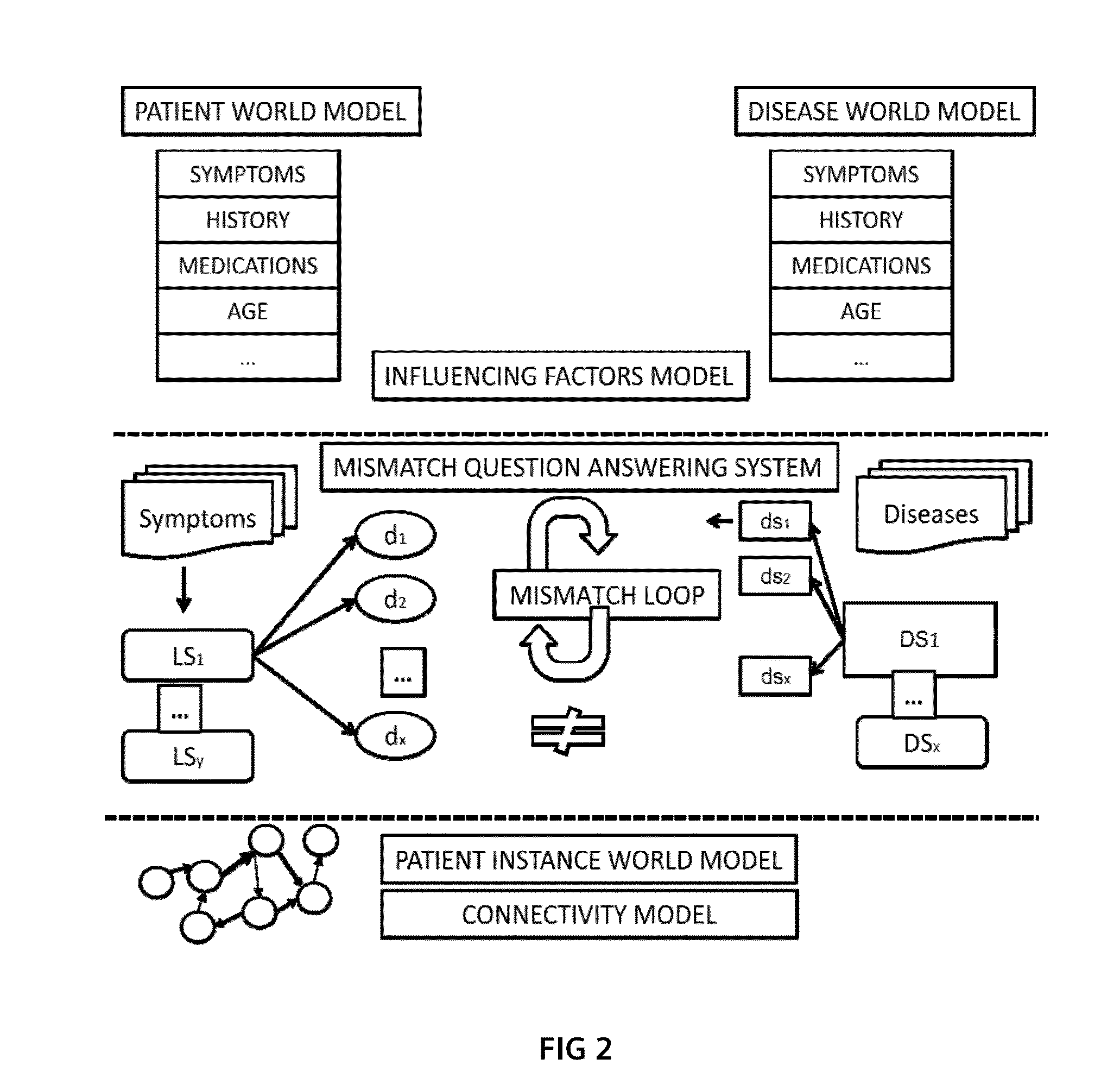
Method and System for Supporting a Clinical Diagnosis
InactiveUS20150169833A1Reducing and even eliminating need for consultingMedical simulationData processing applicationsInformation accessEntry point
Medical experts are supported in the process of specifying and fine-tuning initial search requests by aggregating additional information about a patient context (e.g., patient, assumption, internal diagnose, external diagnose and procedure context). Mismatching information units are subsequently used as an entry point for improved and tailored information access by question answering systems. Different to traditional similarity-driven evidence ranking, an approach that does not disregard the mismatching information but emphasizes such silent signals is established.
Owner:SIEMENS AG
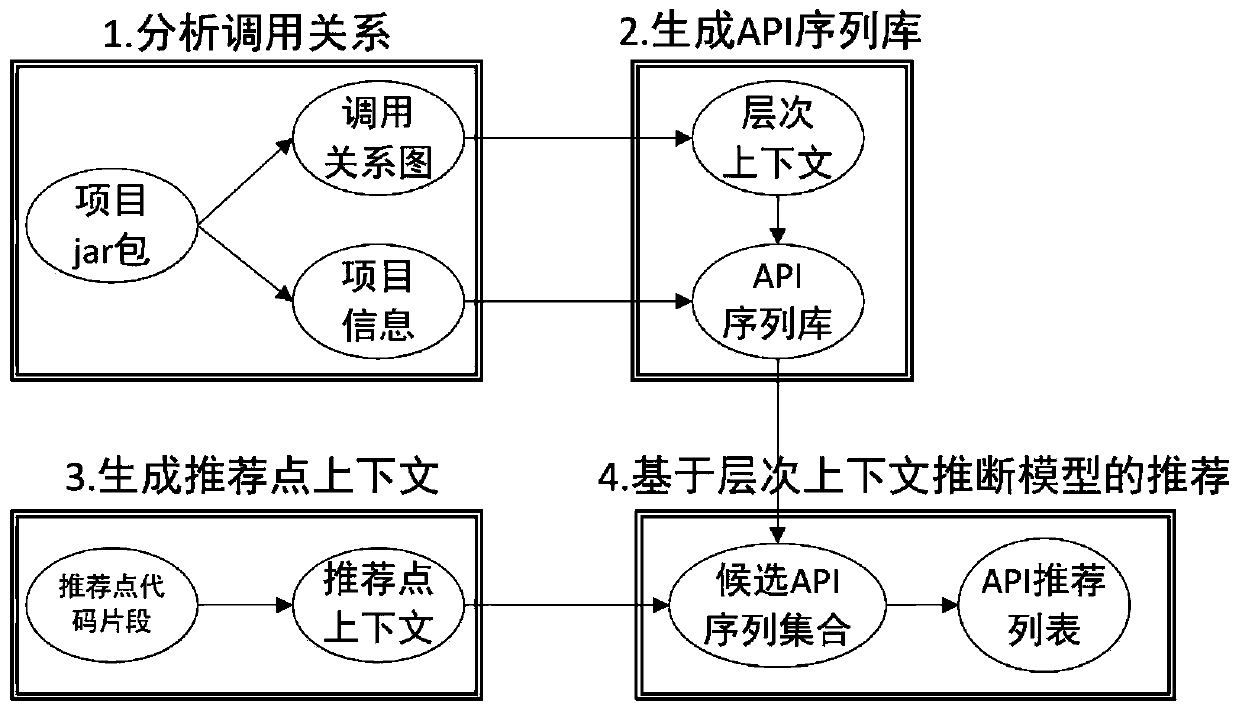
API recommendation method based on hierarchical context
ActiveCN110297657AImprove accuracyImprove effectivenessSoftware maintainance/managementApplication programming interfaceSoftware engineering
The invention discloses an API (Application Programming Interface) recommendation method based on a hierarchical context. The API recommendation method comprises the following steps: recommending an application program interface (API) according to the hierarchical context; automatically generating an API sequence library through an API calling relation in a static analysis method, and then using amethod based on a hierarchical context inference model to recommend an appropriate API. According to the method, the API association relationships of different calling levels in the program context are fully mined, the effectiveness of the API sequence library is improved, and the accuracy of the recommendation result is improved.
Owner:SOUTHEAST UNIV
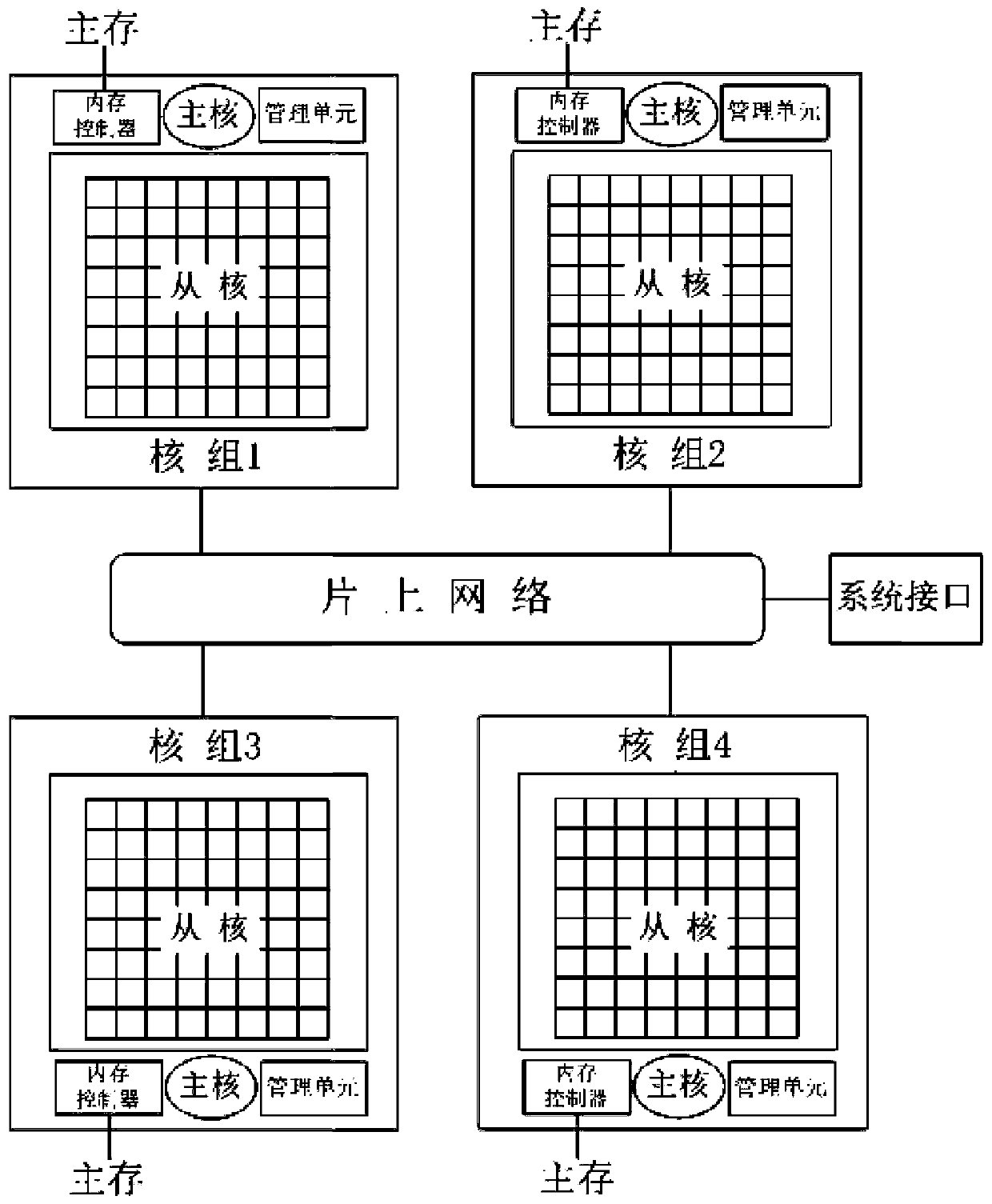
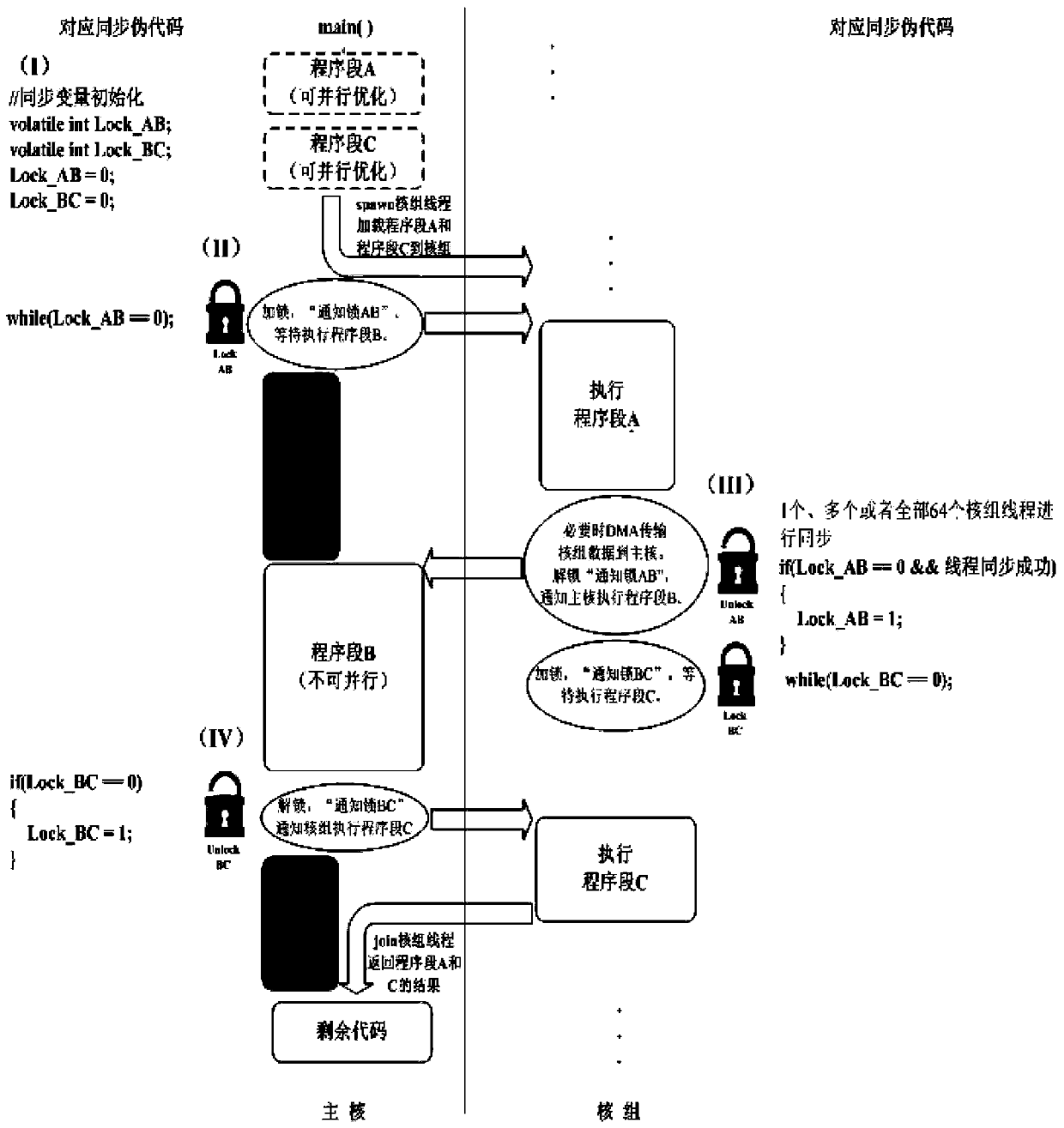
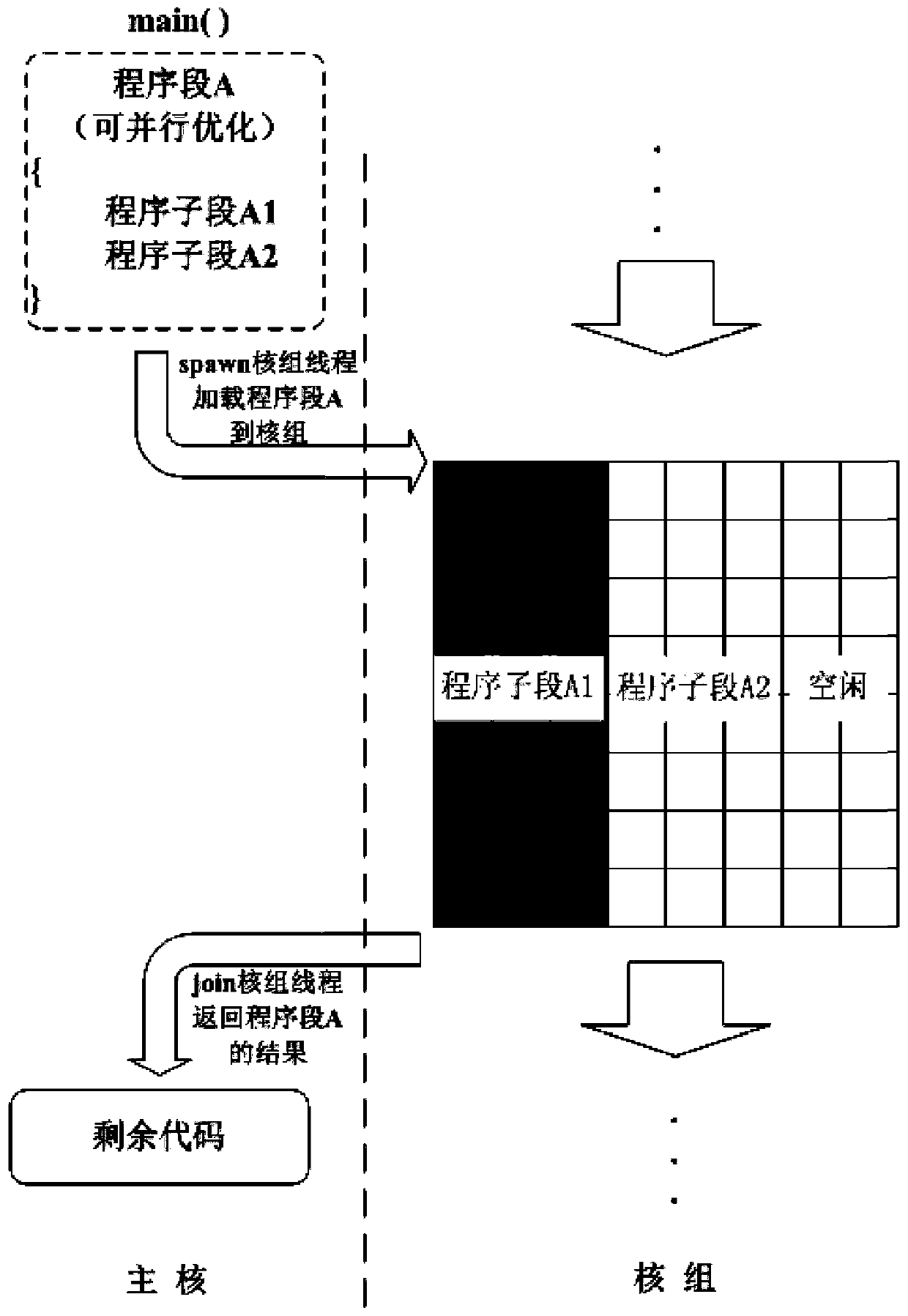
Accelerated running method based on Sunway many-core processor
PendingCN110222007AImprove execution efficiencyReduce waiting timeProgram initiation/switchingProgram synchronisationParallel processingWaiting time
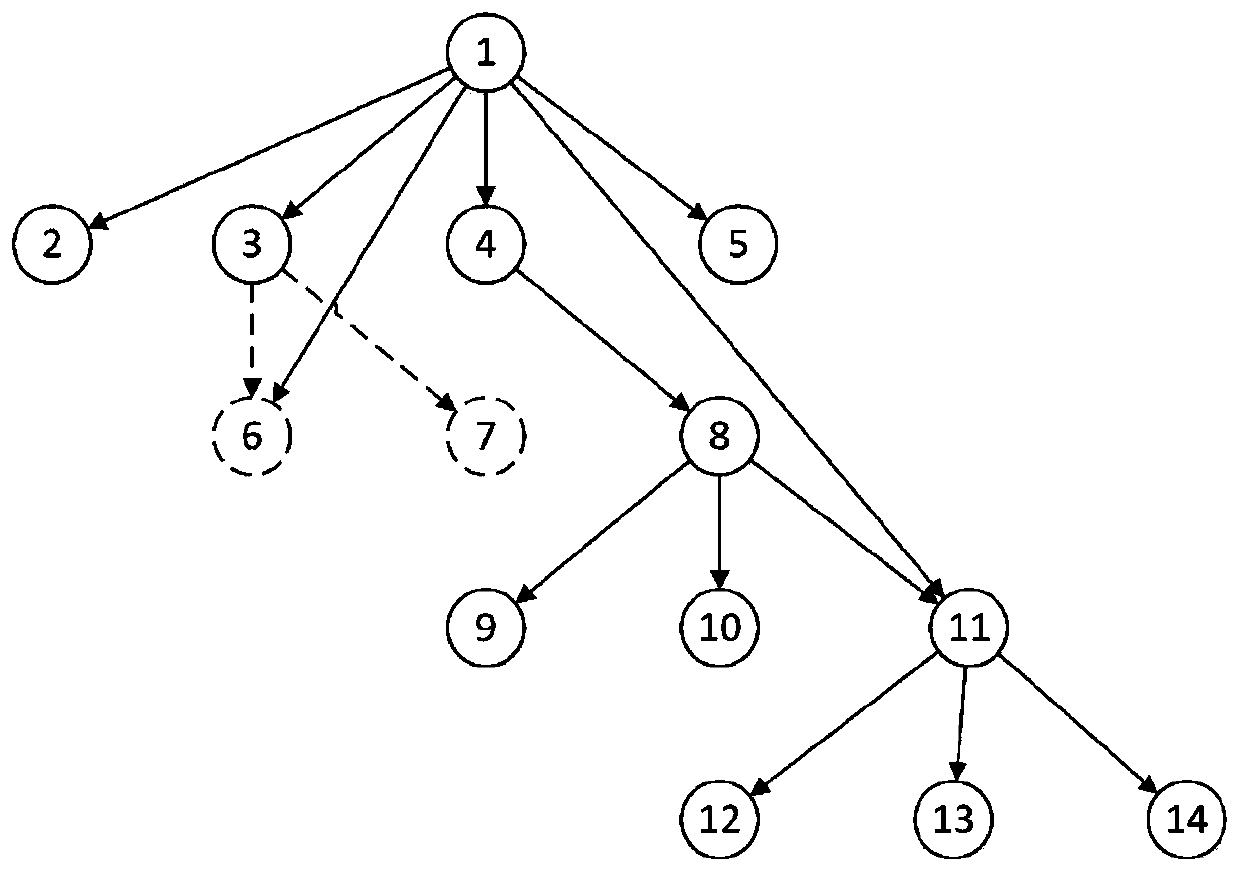
The invention relates to an accelerated running method based on a Sunway many-core processor. The accelerated running method comprises the following steps: A, judging a program context dependency relationship among a program segment A, a program segment B and a program segment C; if program context dependency relationships exist among the program segment A, the program segment B and the program segment C, executing the program segments in sequence; otherwise, adjusting the execution sequence among the program segment A, the program segment B and the program segment C, and executing the programsegments; and B, executing the step A on the three continuous program segments until all the programs are executed. The program context dependency relationship between a program segment and a programsub-segment is judged; the method is flexible in processing according to conditions, a communication lock synchronization mechanism is introduced, the waiting time of a main core is saved, parallel processing of the main core and a core group is realized, the required times of threads of a spawn and a join core group are reduced in the program execution process, and the program execution efficiency is improved.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
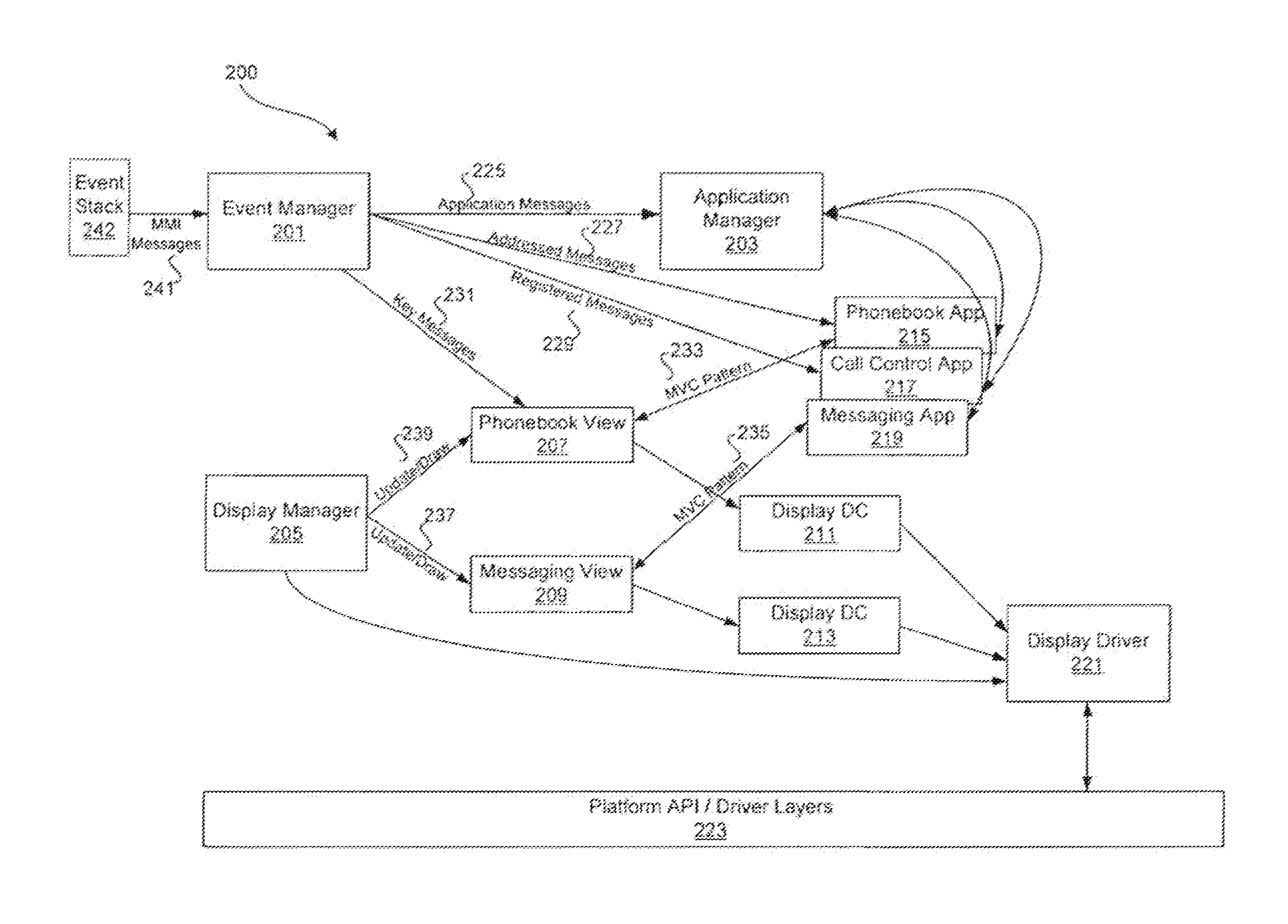
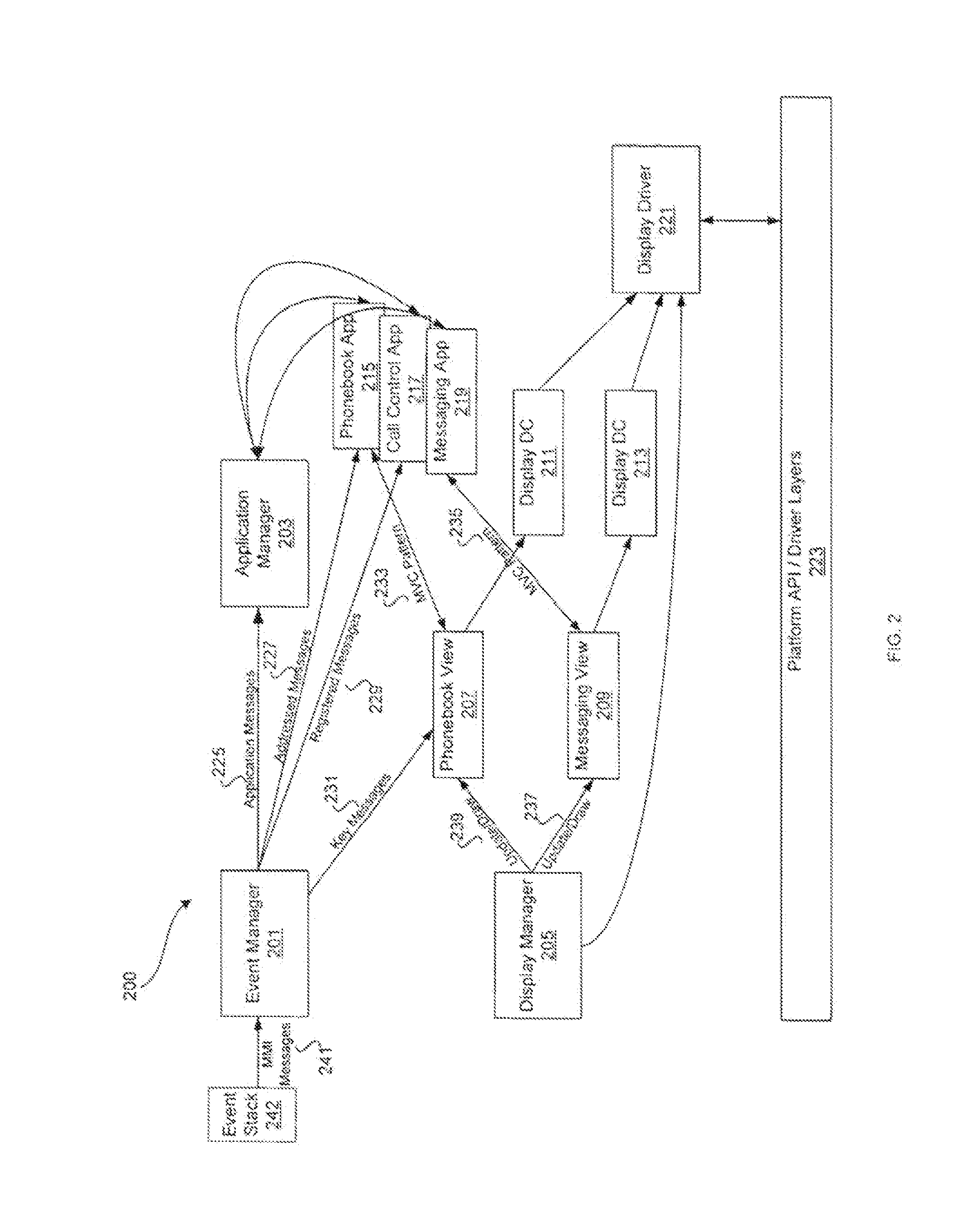
Method and System for an Application Framework for a Wireless Device
InactiveUS20140033235A1Interprogram communicationWireless network protocolsApplication procedureMan machine
Methods and systems for managing applications by an application manager within a man machine interface (MMI) application framework are disclosed. Aspects of the method may include creating an active application context upon launching a first application by the application manager. The active application context may be transitioned into a suspended application context upon suspending the first application by the application manager. The suspended application context may be stored in an application manager context stack. The stored suspended application context may be acquired from the application manager context stack upon receipt of an exit message by the application manager. The application manager context stack may comprise a last-in-first-out (LIFO) context stack. The first application associated with said suspended application context may be reactivated upon removal of the suspended application context from the application manager context stack.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
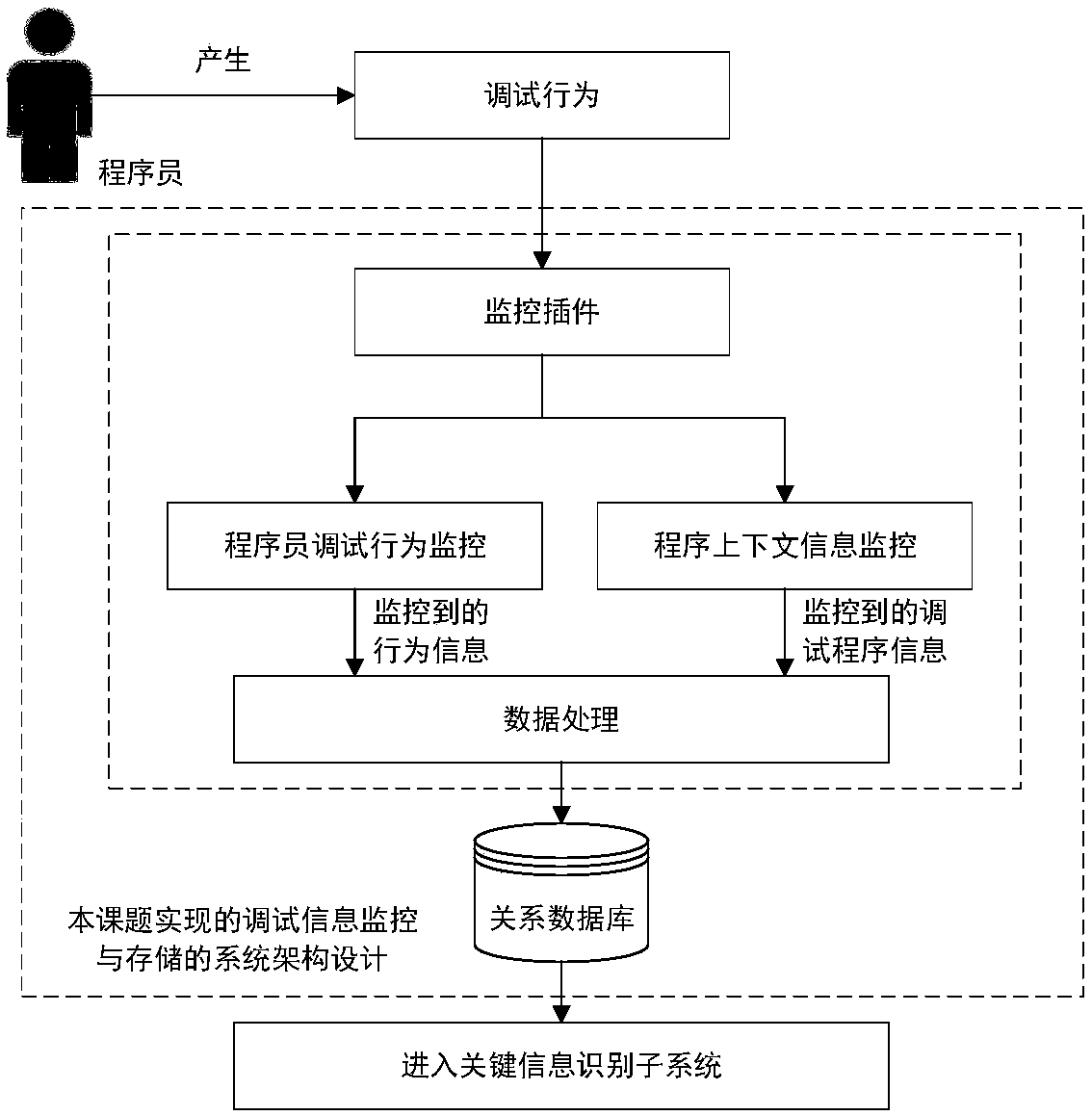
A software fault location system removing the perfect understanding hypothesis
ActiveCN108984402AImprove debugging efficiencyImprove fault location speedHardware monitoringSoftware testing/debuggingHypothesisSoftware fault
The invention discloses a software fault location method for removing the perfect understanding hypothesis. The method realizes the Eclipse monitoring plug-in and saves the debugging information of auser in a MYSQL database, and the information includes the debugging behavior information of the user and the program context scenario information. Through analysis of this information, it is found that the debugging trajectory of the same fault debugger is related to each other, the key information in debugging is given by referring to the key class, the key information identification method based on label is adopted as a general recommendation rule, and the key information is directly fed back to the user's integrated development environment as the recommendation content, so the debugger isassisted to locate the fault.
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY
Memory management system having a forward progress bit
A virtual memory system that maintains a list of pages that are required to be resident in a frame buffer to guarantee the eventual forward progress of a graphics application context running on a graphics system composed of multiple clients. Pages that are required to be in the frame buffer memory are never swapped out of that memory. The required page list can be dynamically sized or fixed sized. A tag file is used to prevent page swapping of a page from the frame buffer that is required to make forward progress. A forward progress indicator signifies that a page faulting client has made forward progress on behalf of a context. The presence of a forward progress indicator is used to clear the tag file, thus enabling page swapping of the previously tagged pages from the frame buffer memory.
Owner:NVIDIA CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com