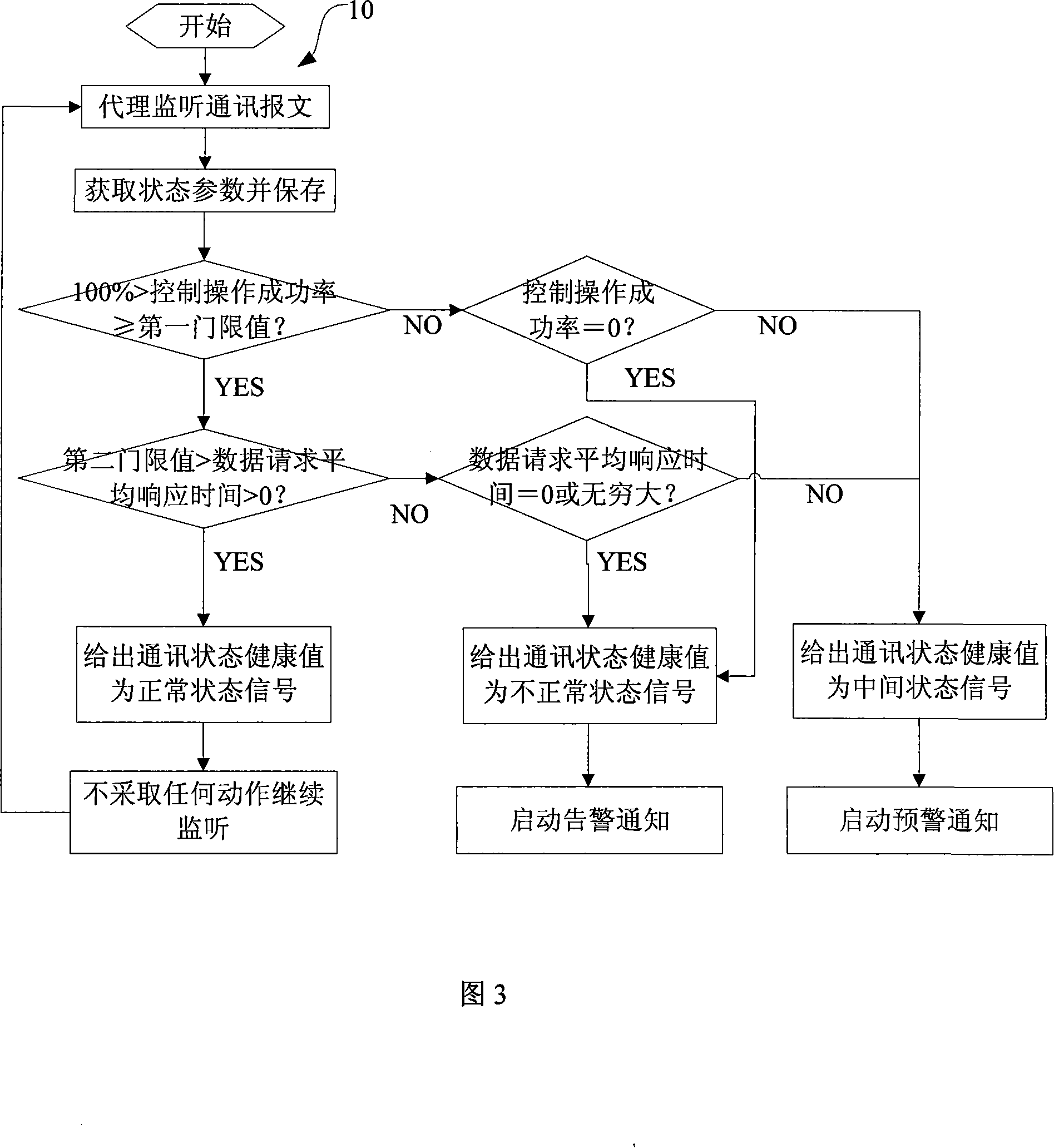
Patents
Literature
129 results about "Connection broker" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
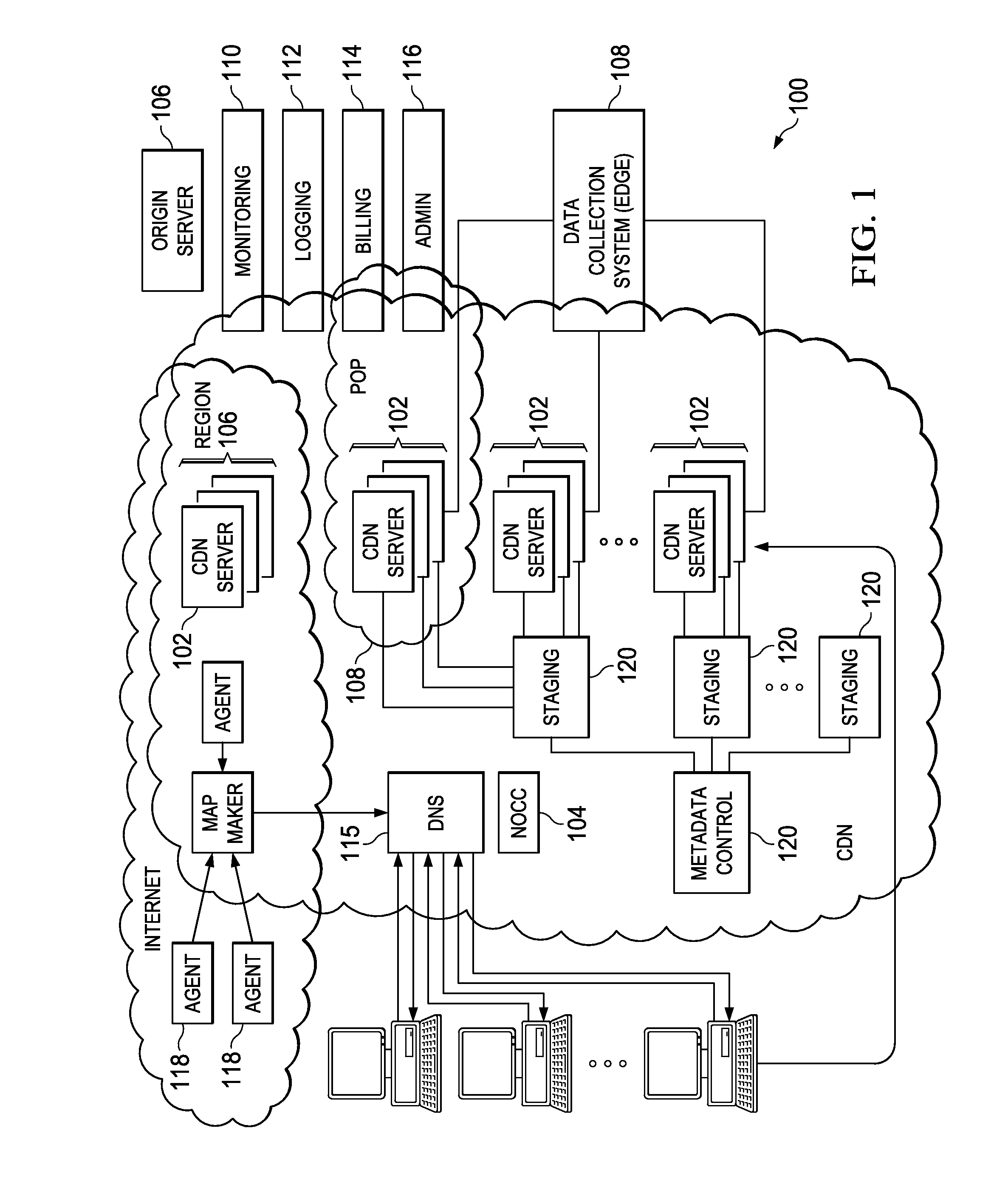
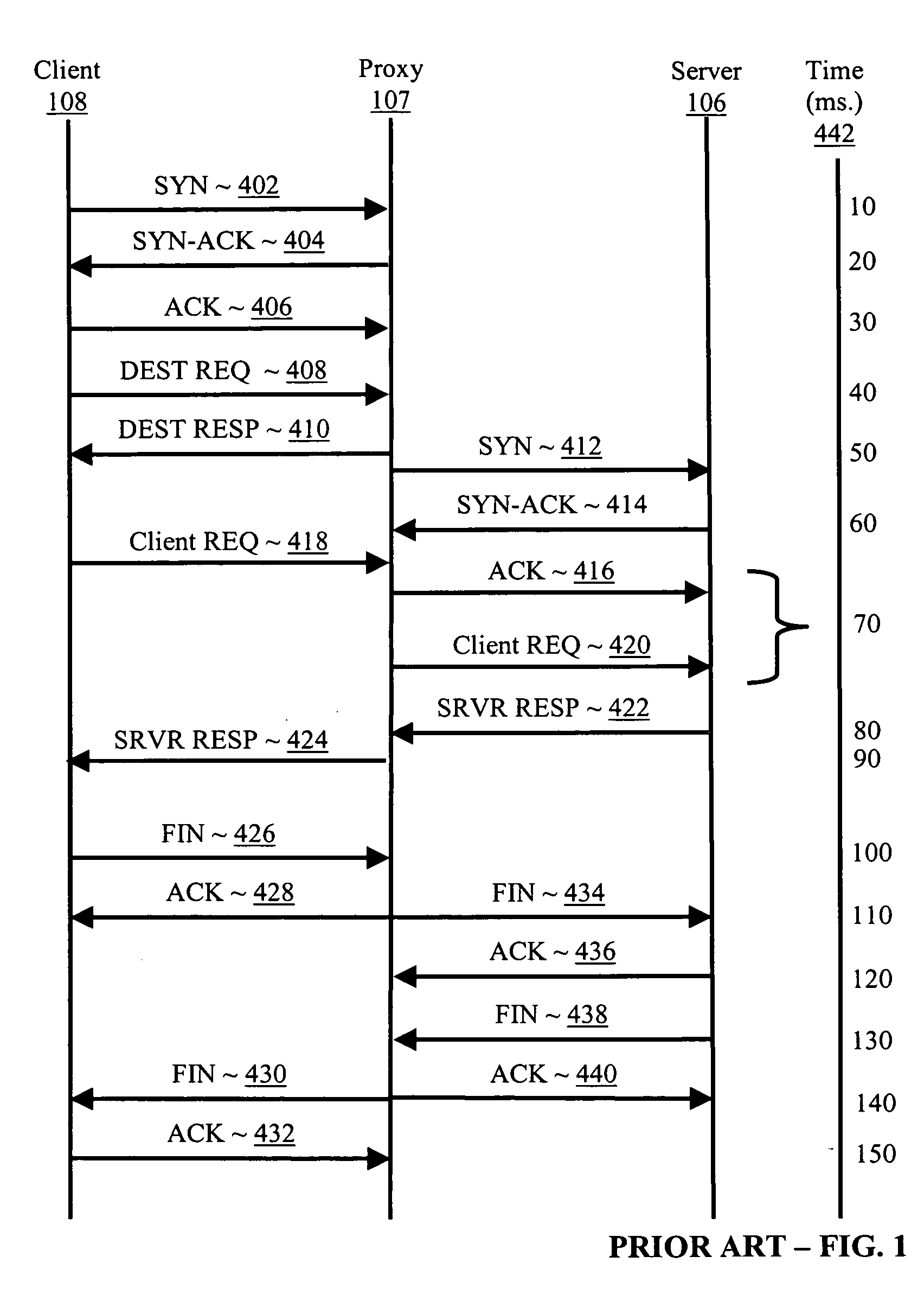
In software engineering, a connection broker is a resource manager that manages a pool of connections to connection-based resources such as databases or remote desktops, enabling rapid reuse of these connections by short-lived processes without the overhead of setting up a new connection each time.
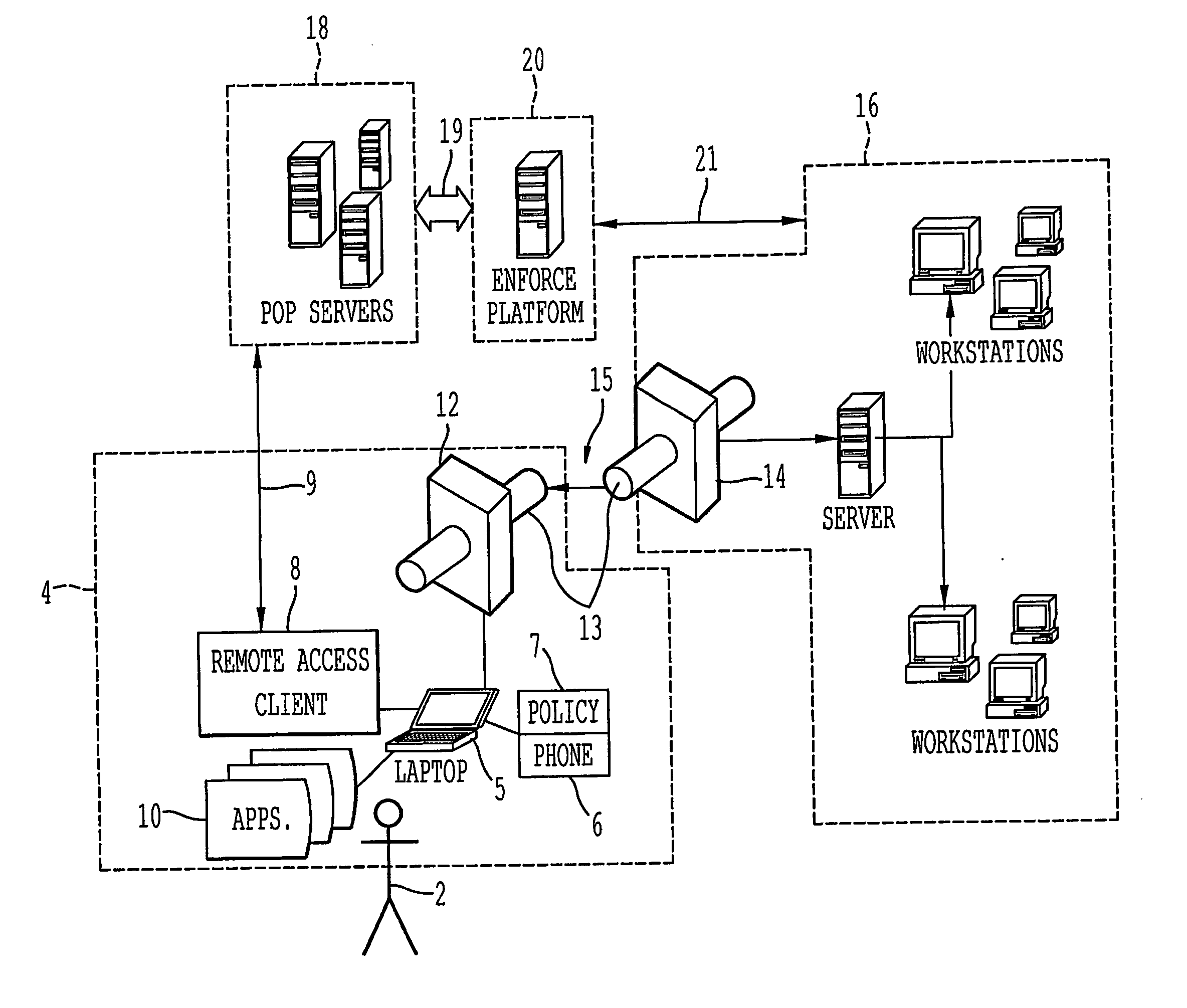
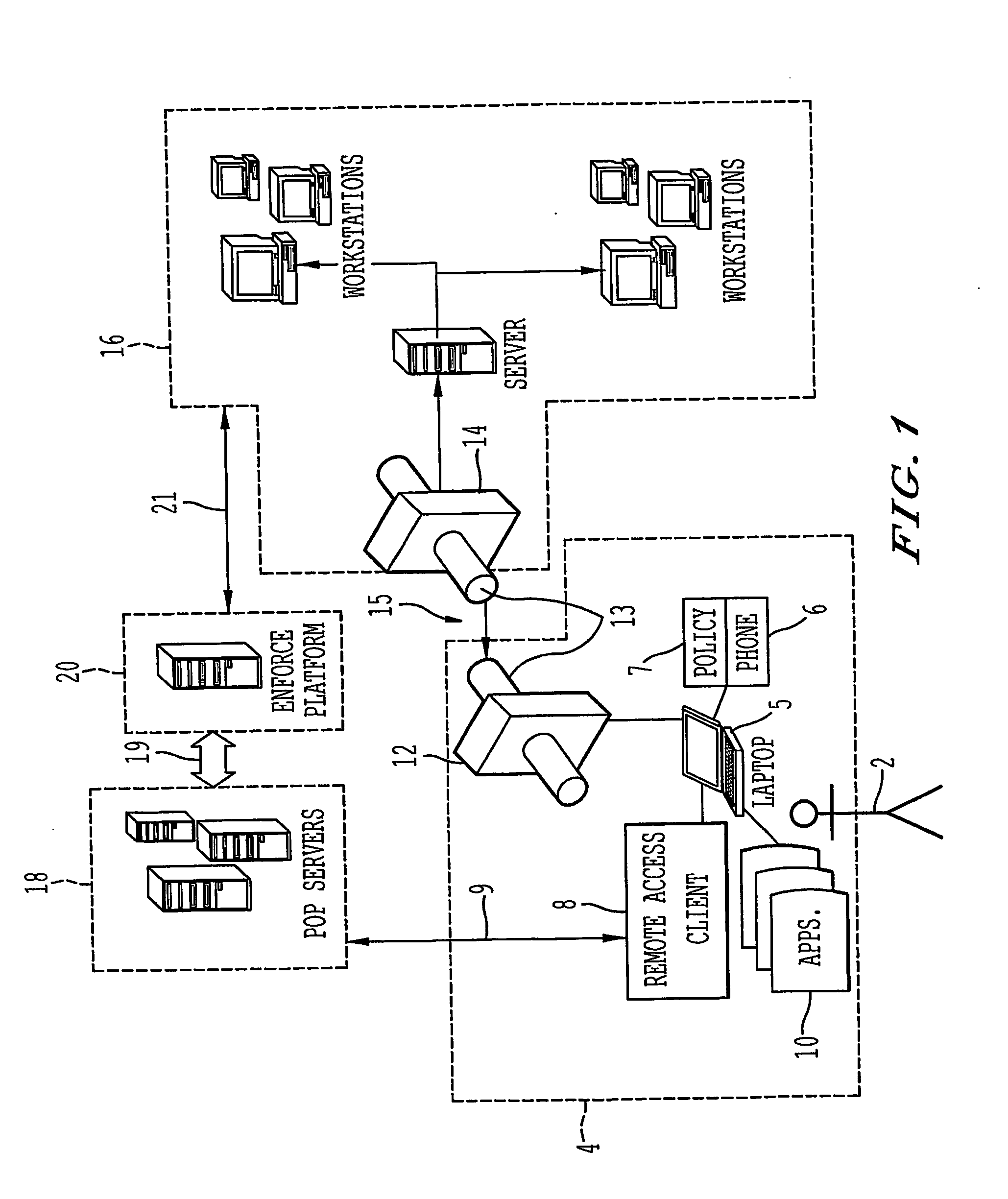
Client-side network access polices and management applications
ActiveUS20050022012A1Digital data processing detailsMultiple digital computer combinationsData terminalPoint of presence
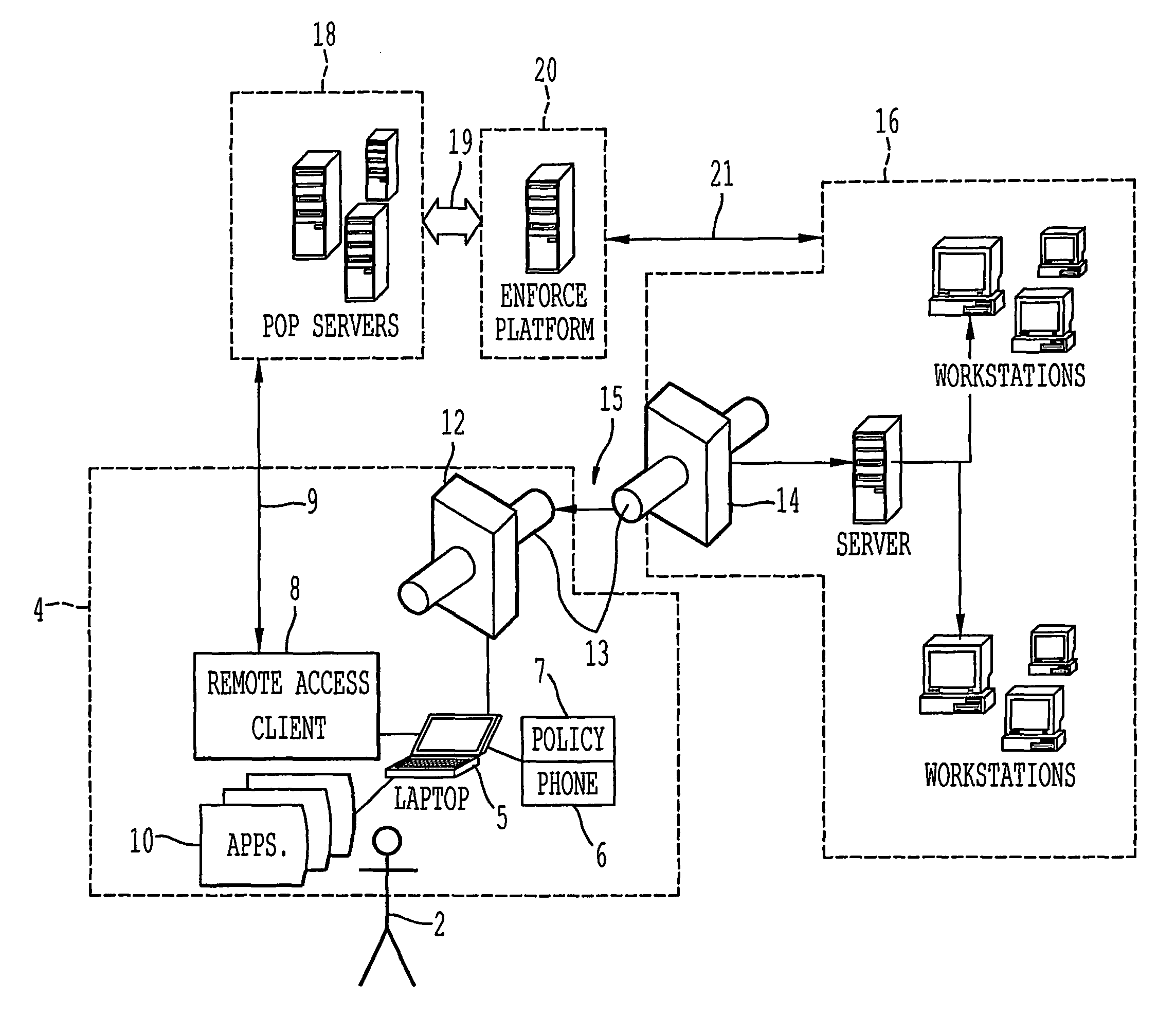
A remote access client is provided for enabling communication between a remote data terminal configured to access a public network, and an enterprise network by way of a VPN tunnel through the public network. The remote access client includes at least one application program interface (API) to receive a first verification of the operating state of a predetermined application of the remote data terminal to enable a connection agent for establishing a point of presence on the public network. Upon connection to the point of presence, the API exchanges data between the remote access client and the predetermined application of the remote data terminal. The remote access client receives a second periodic verification of the operating state of the predetermined application via the API for terminating the connection to the point of presence upon the absence of the second verification. The point of presence enables the VPN tunnel for transporting data from the remote data terminal to the enterprise network across the public network.
Owner:GINEGAR LLC
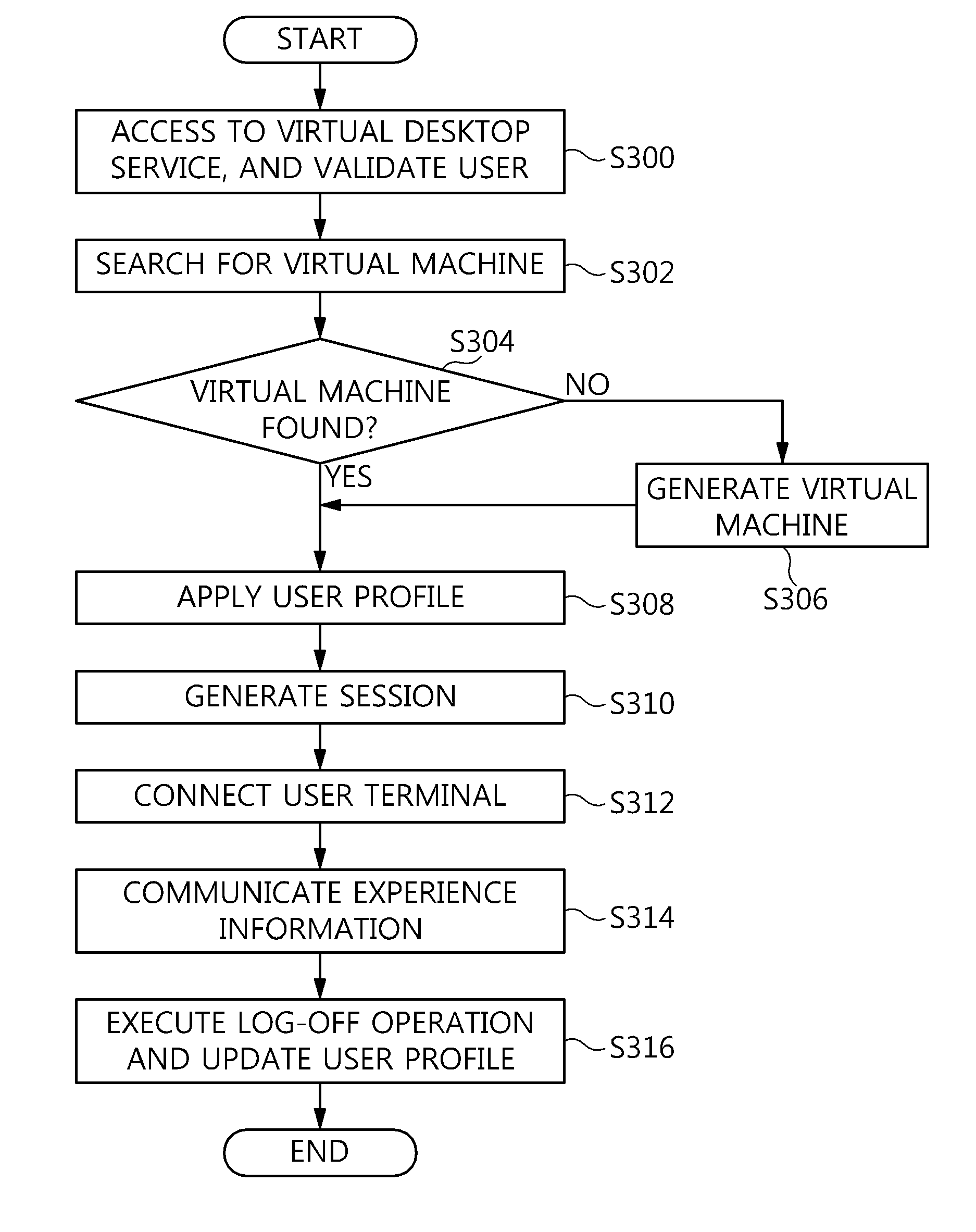
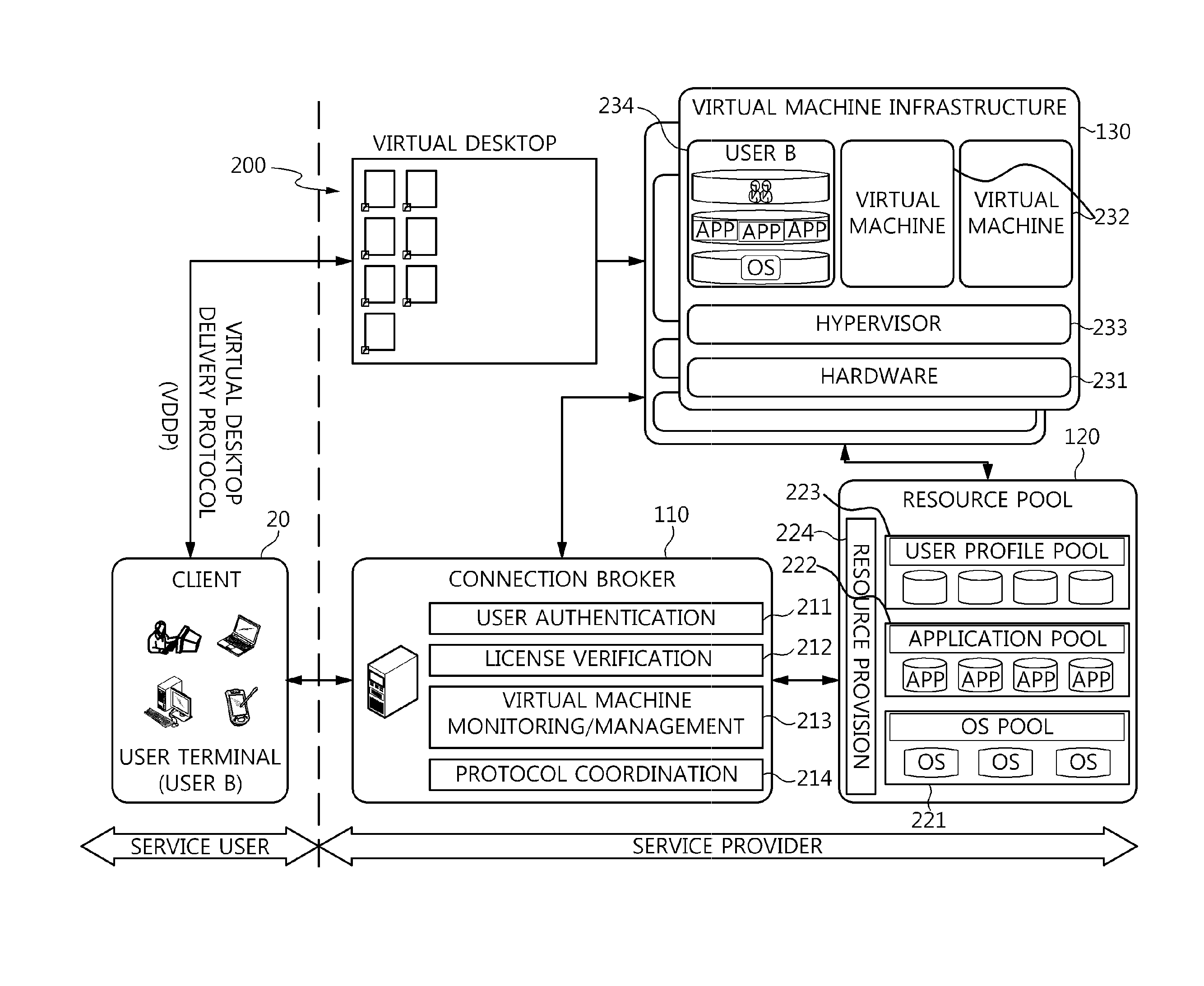
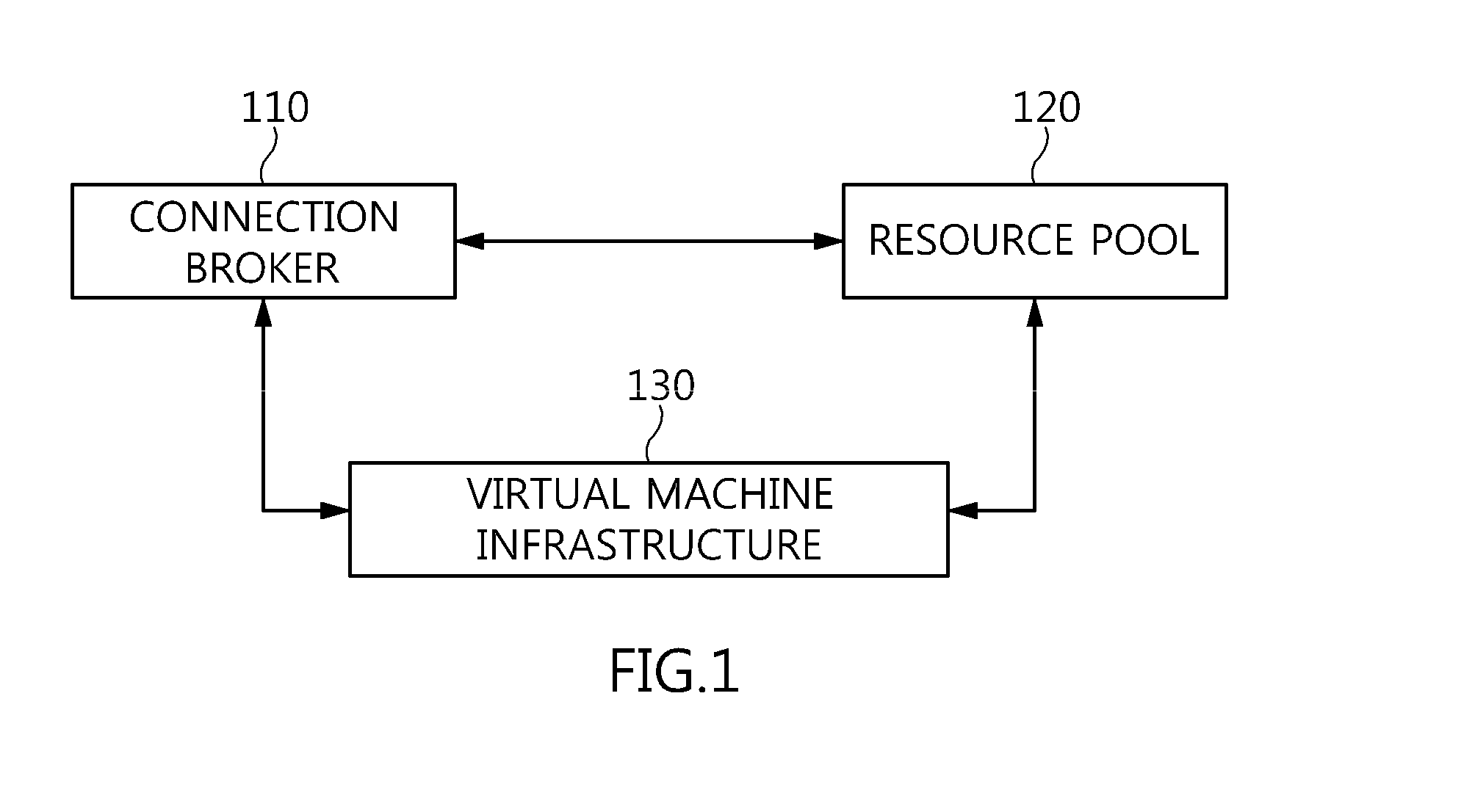
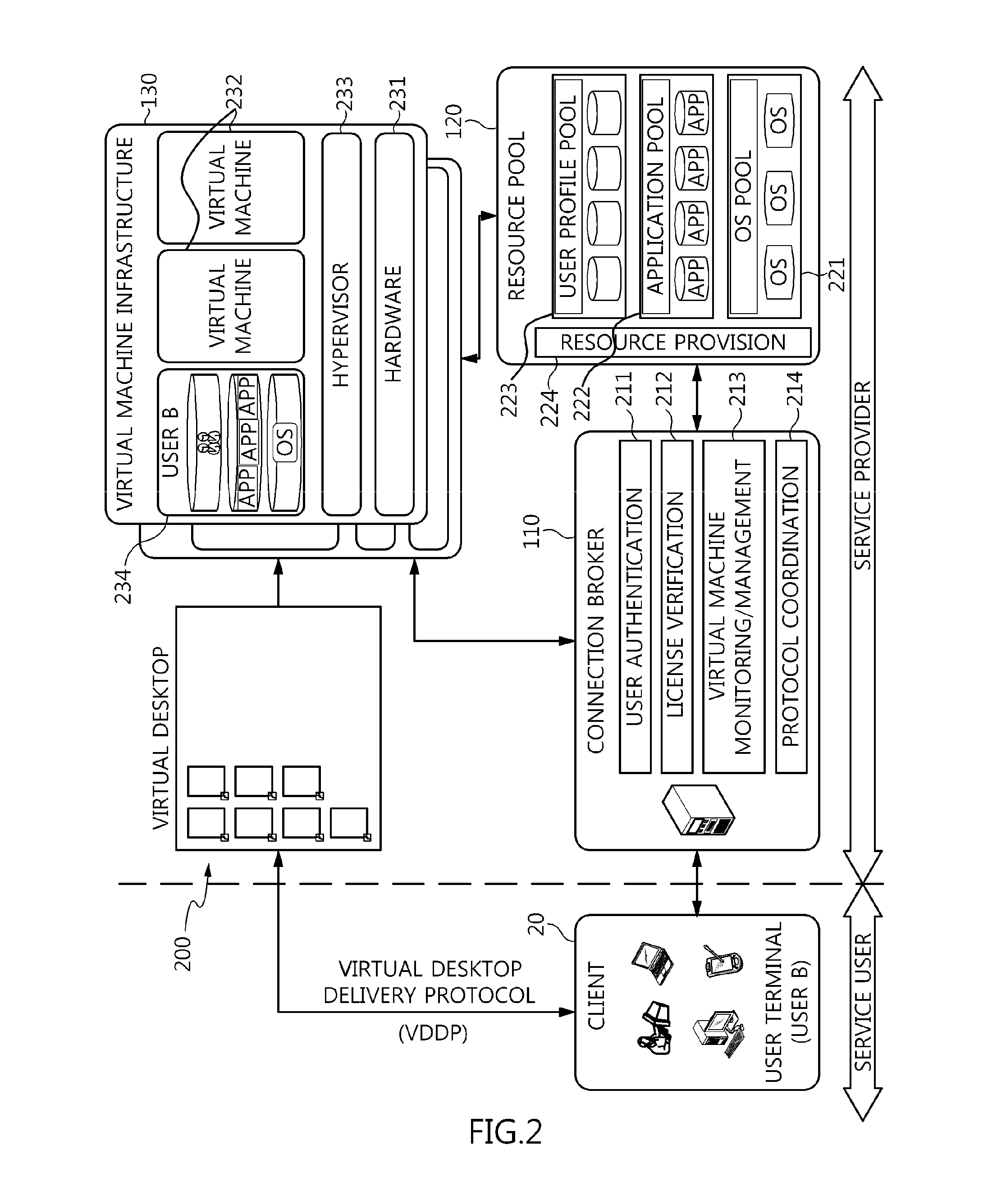
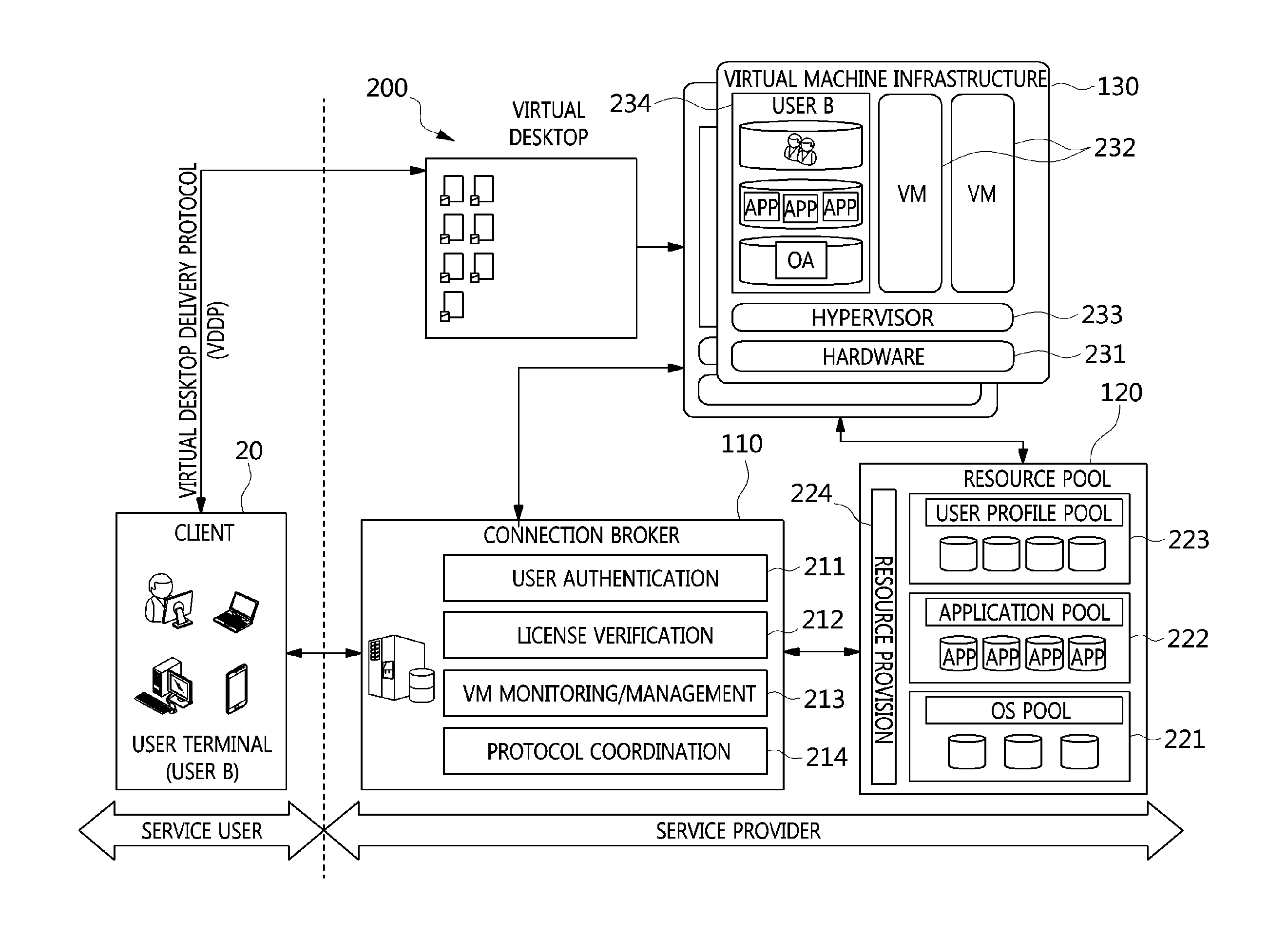
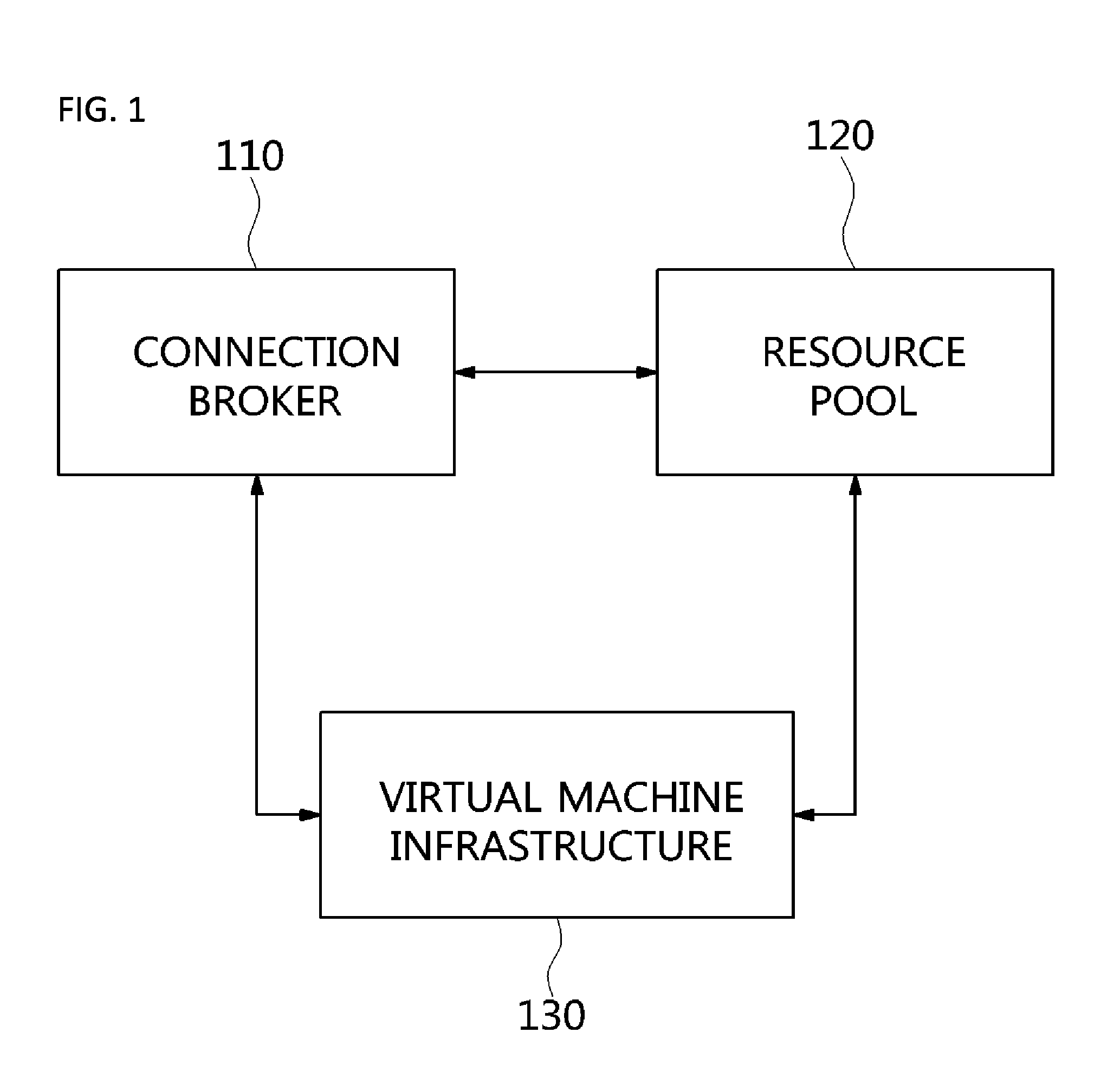
Method and architecture for virtual desktop service
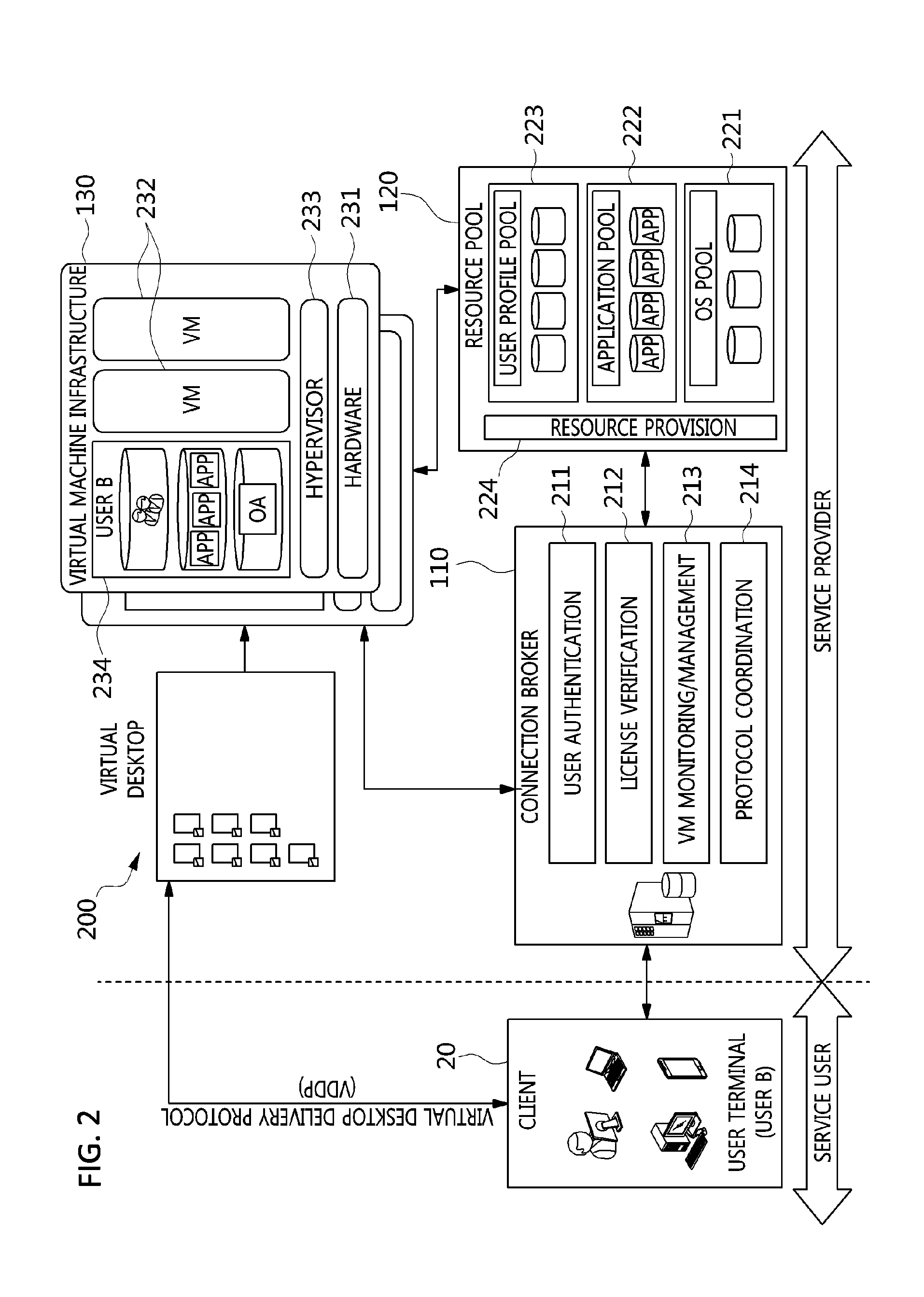
ActiveUS9086897B2Efficiently provideAvoid lossMultiple digital computer combinationsDigital data authenticationResource poolOn demand
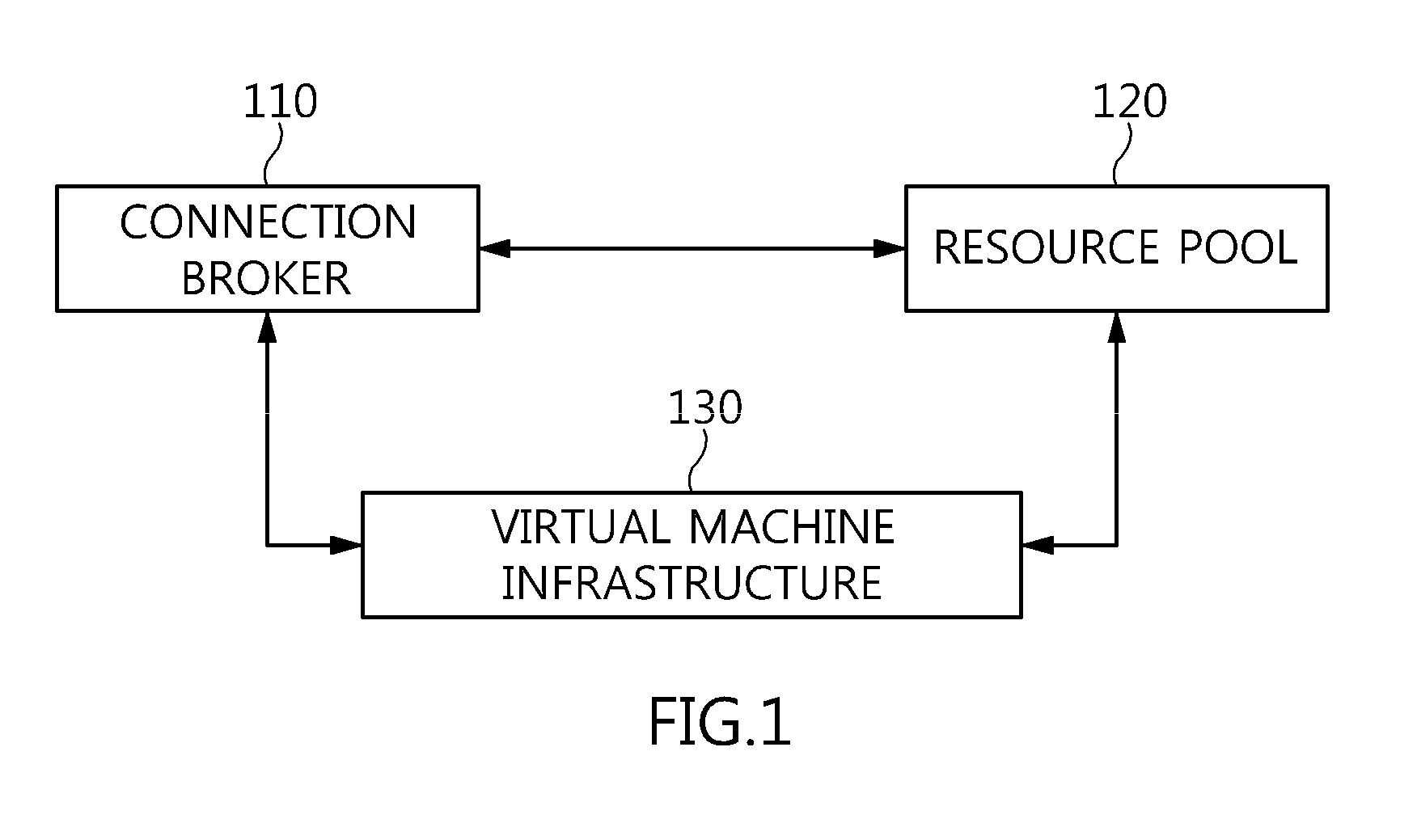
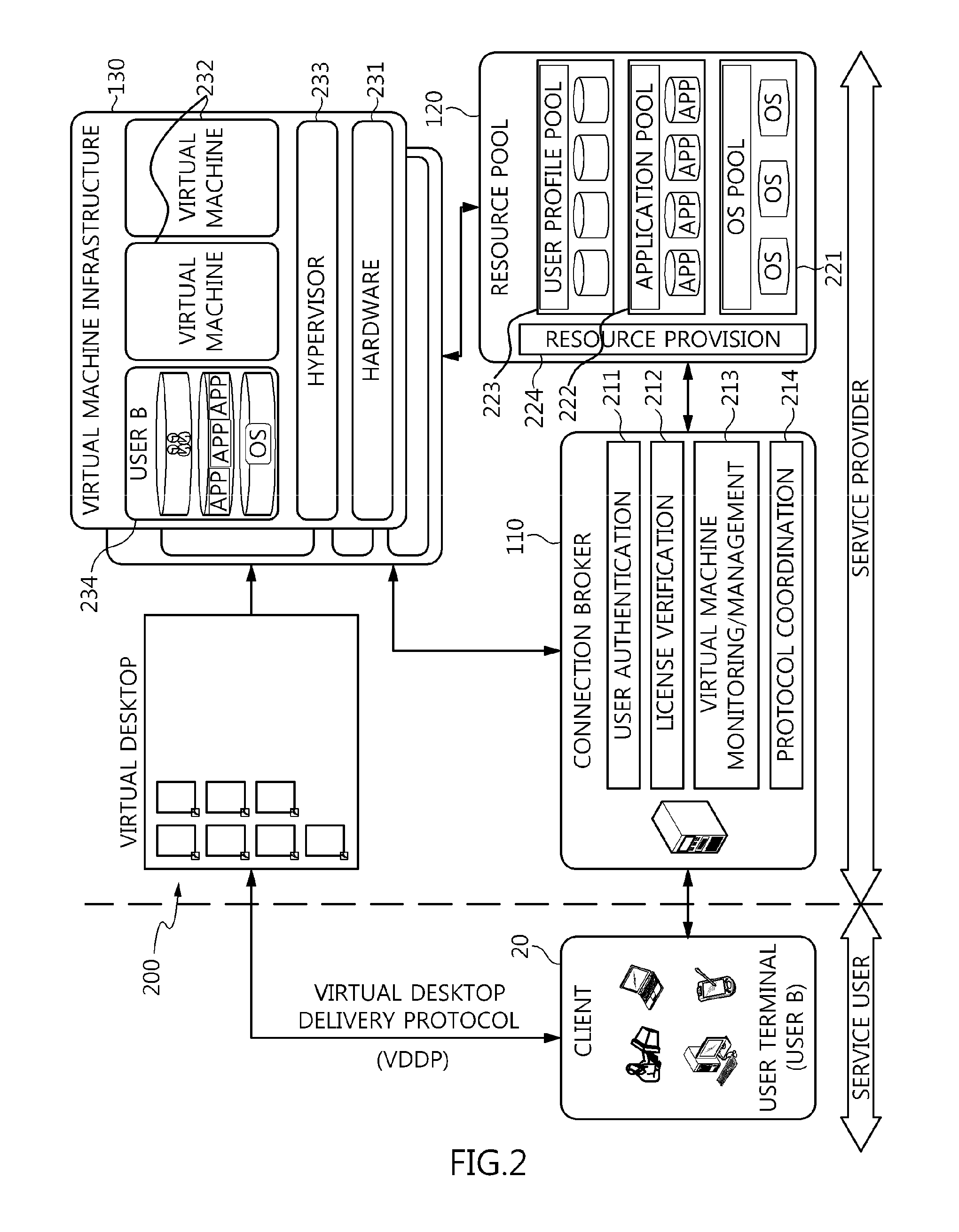
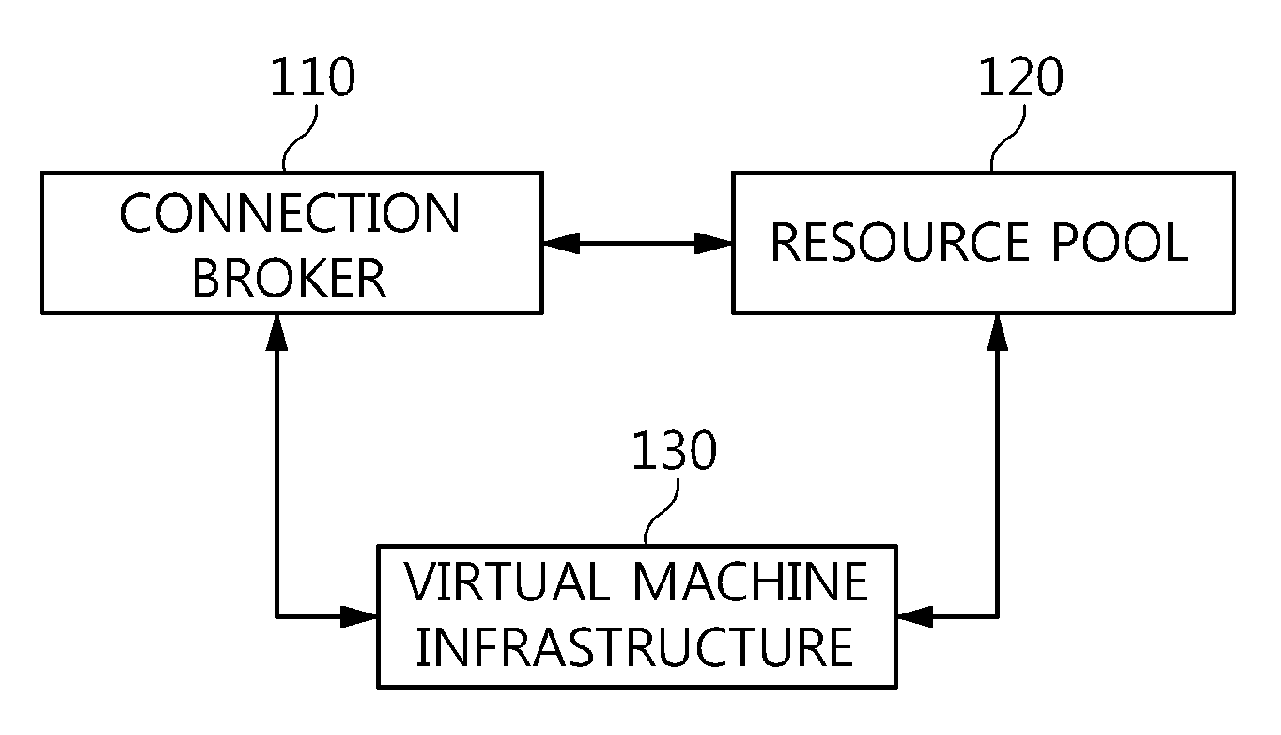
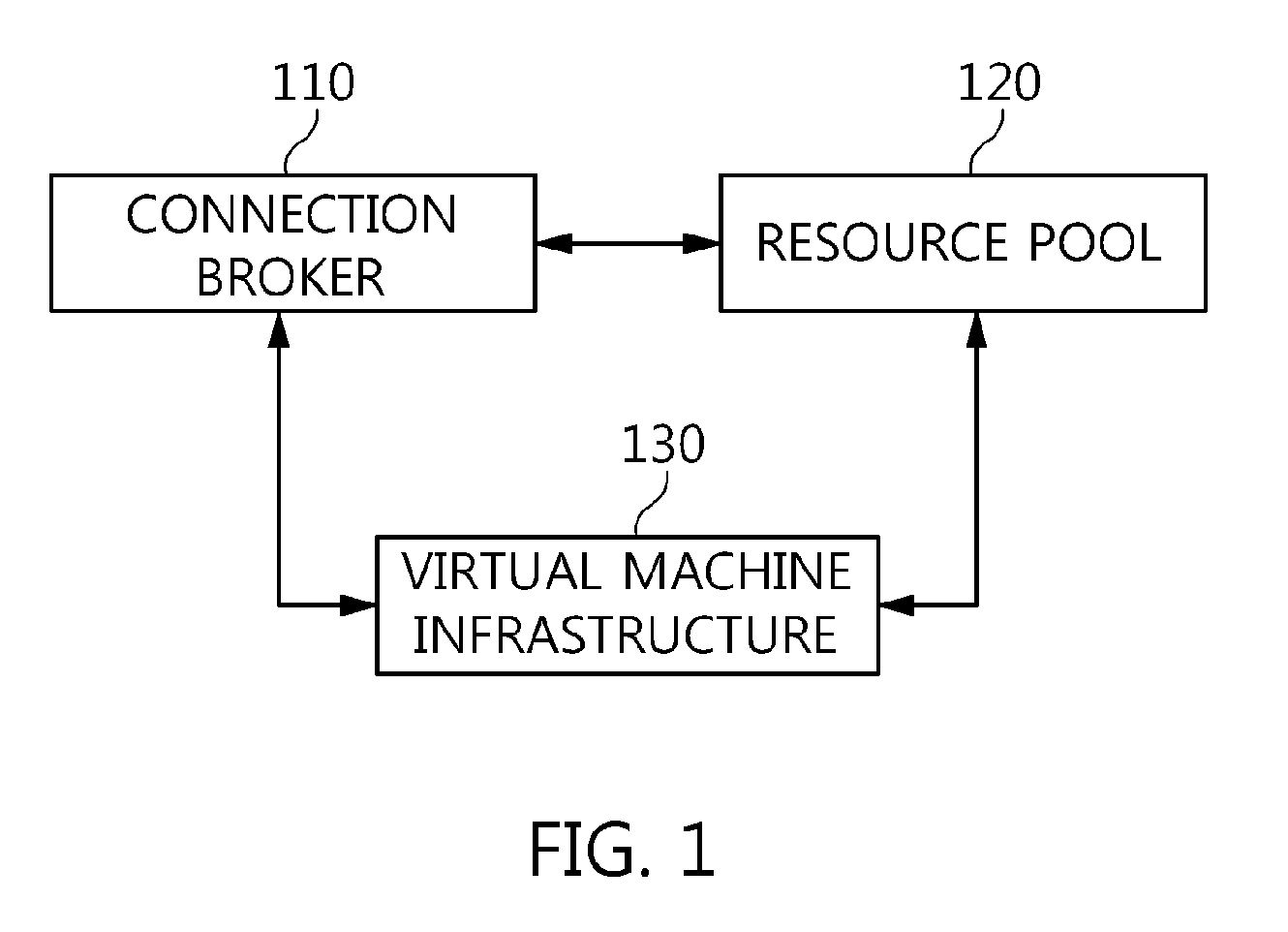
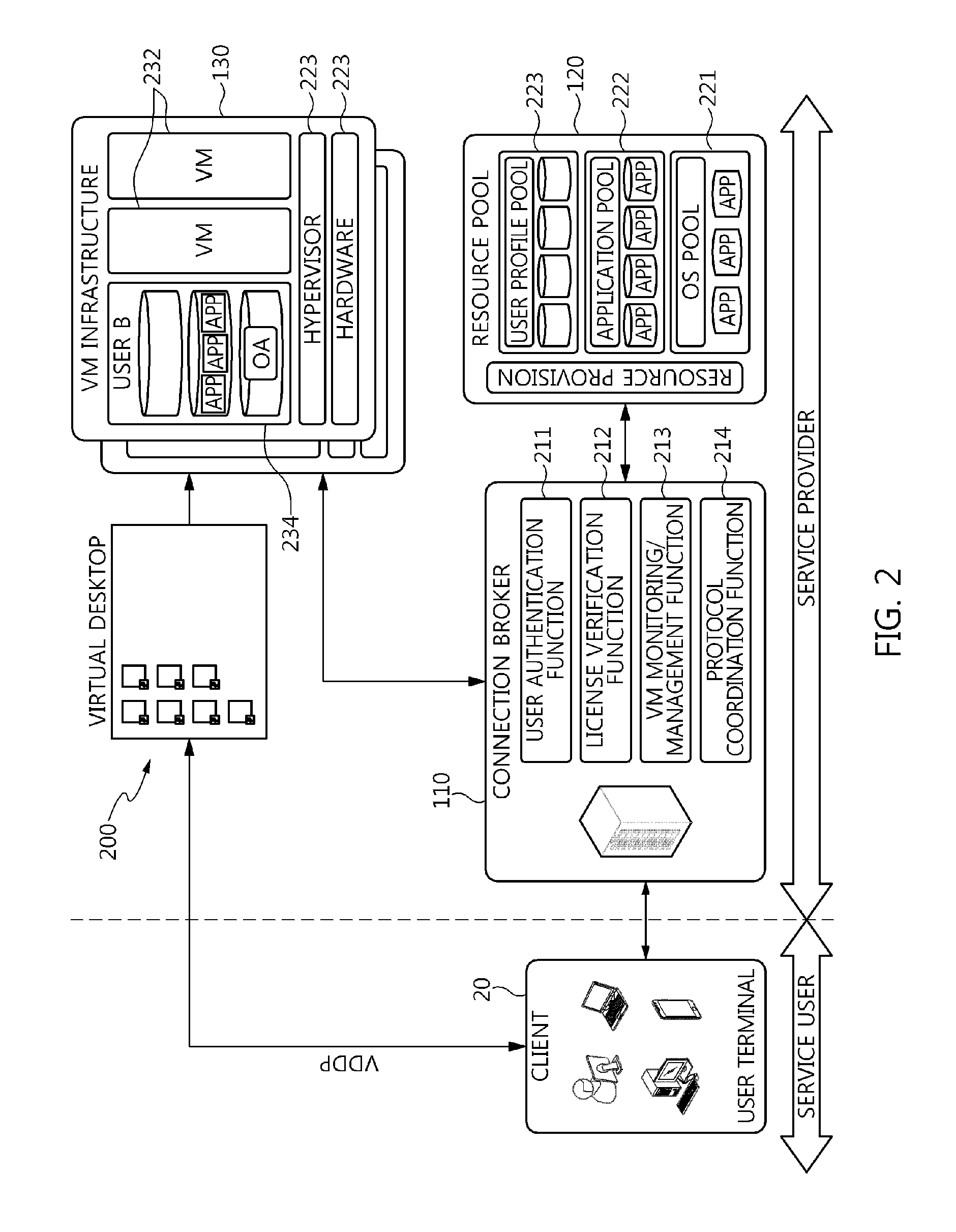
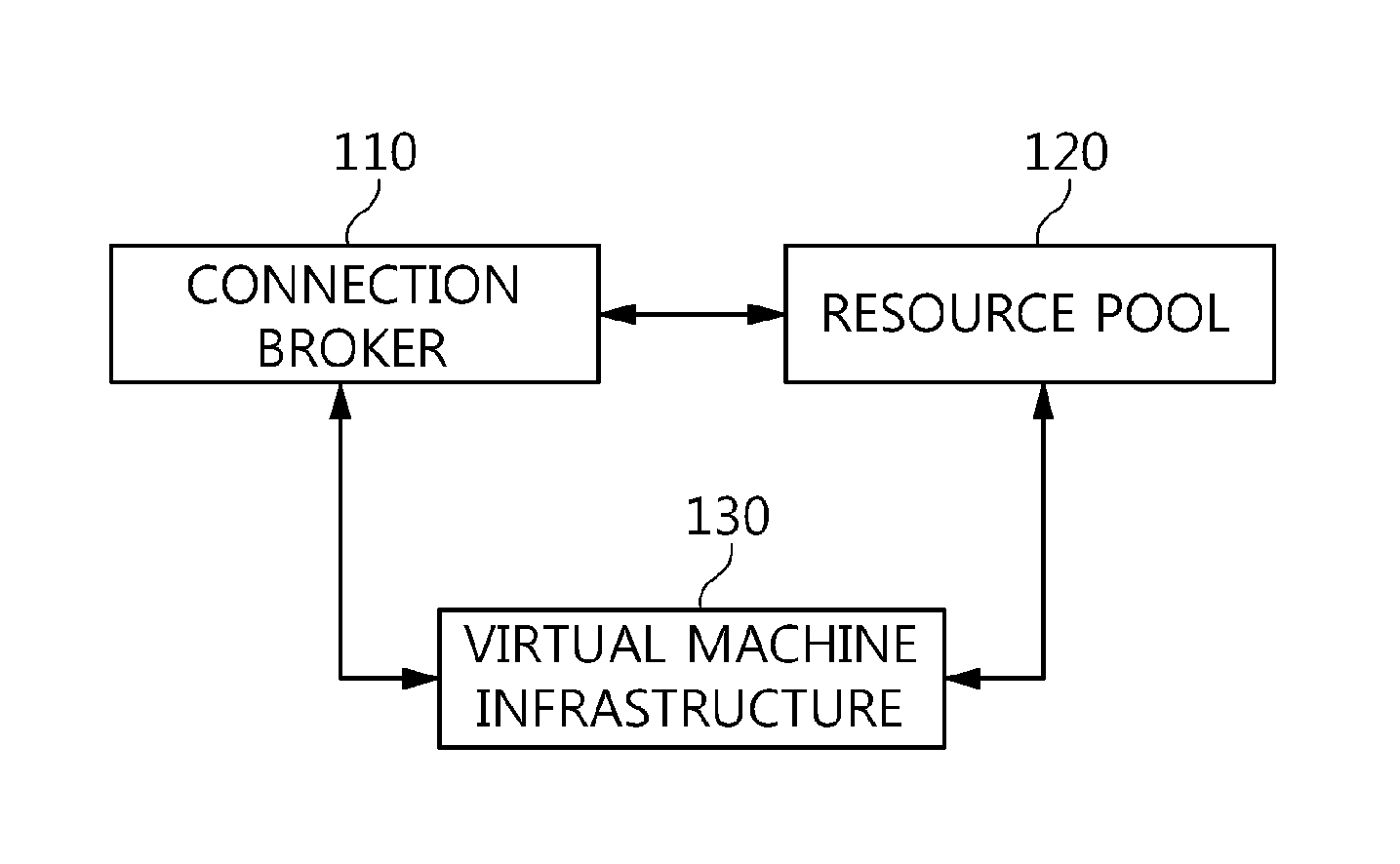
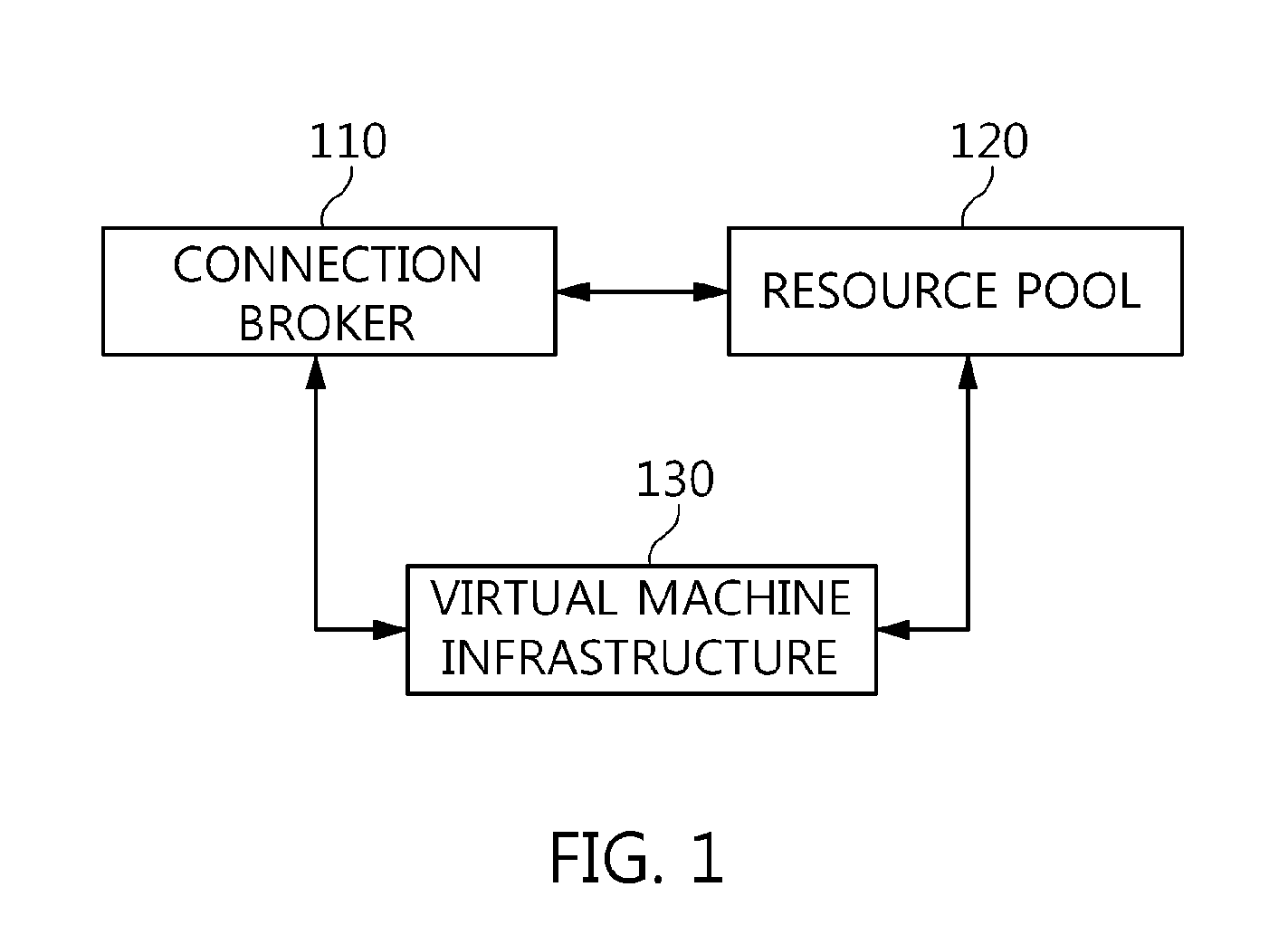
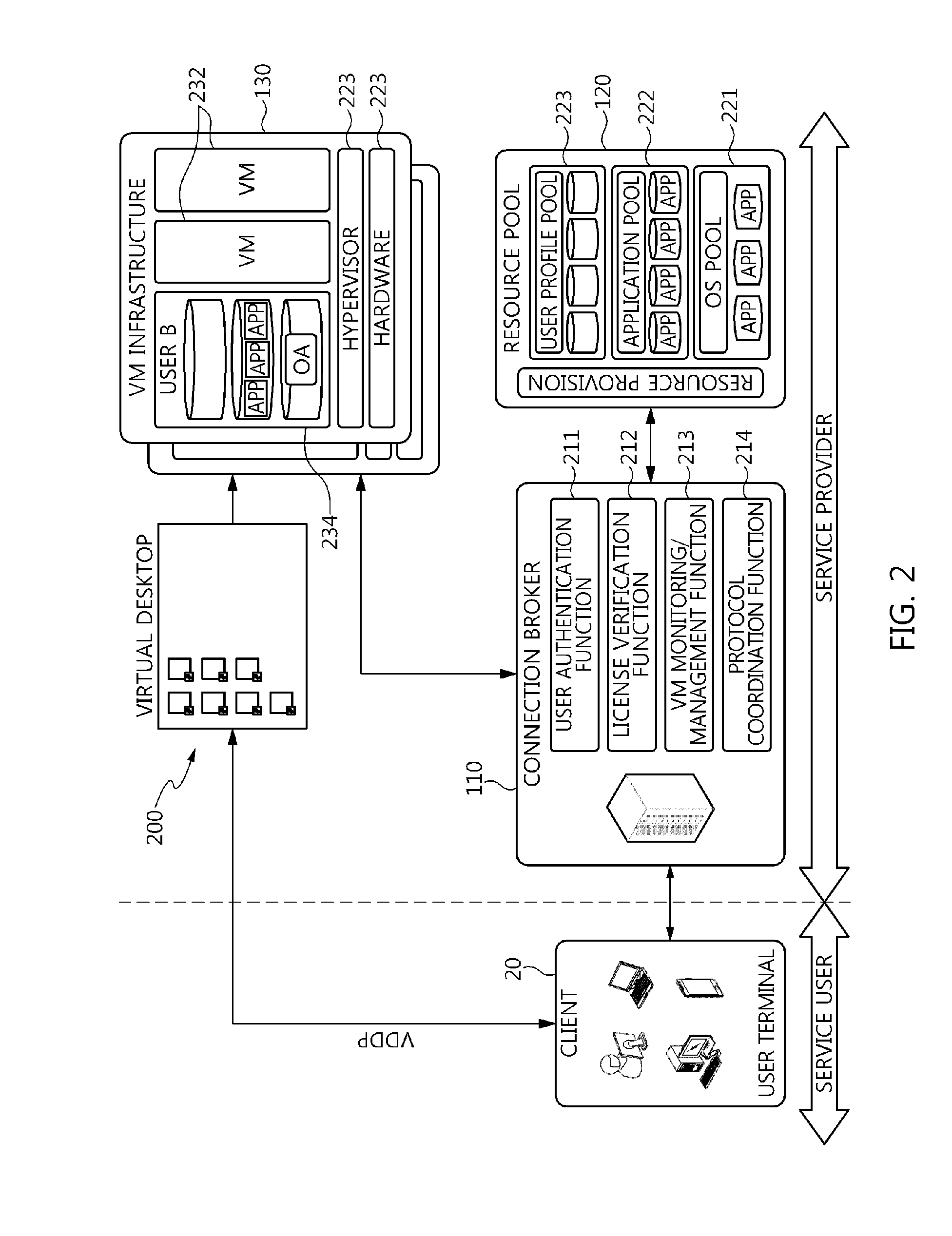
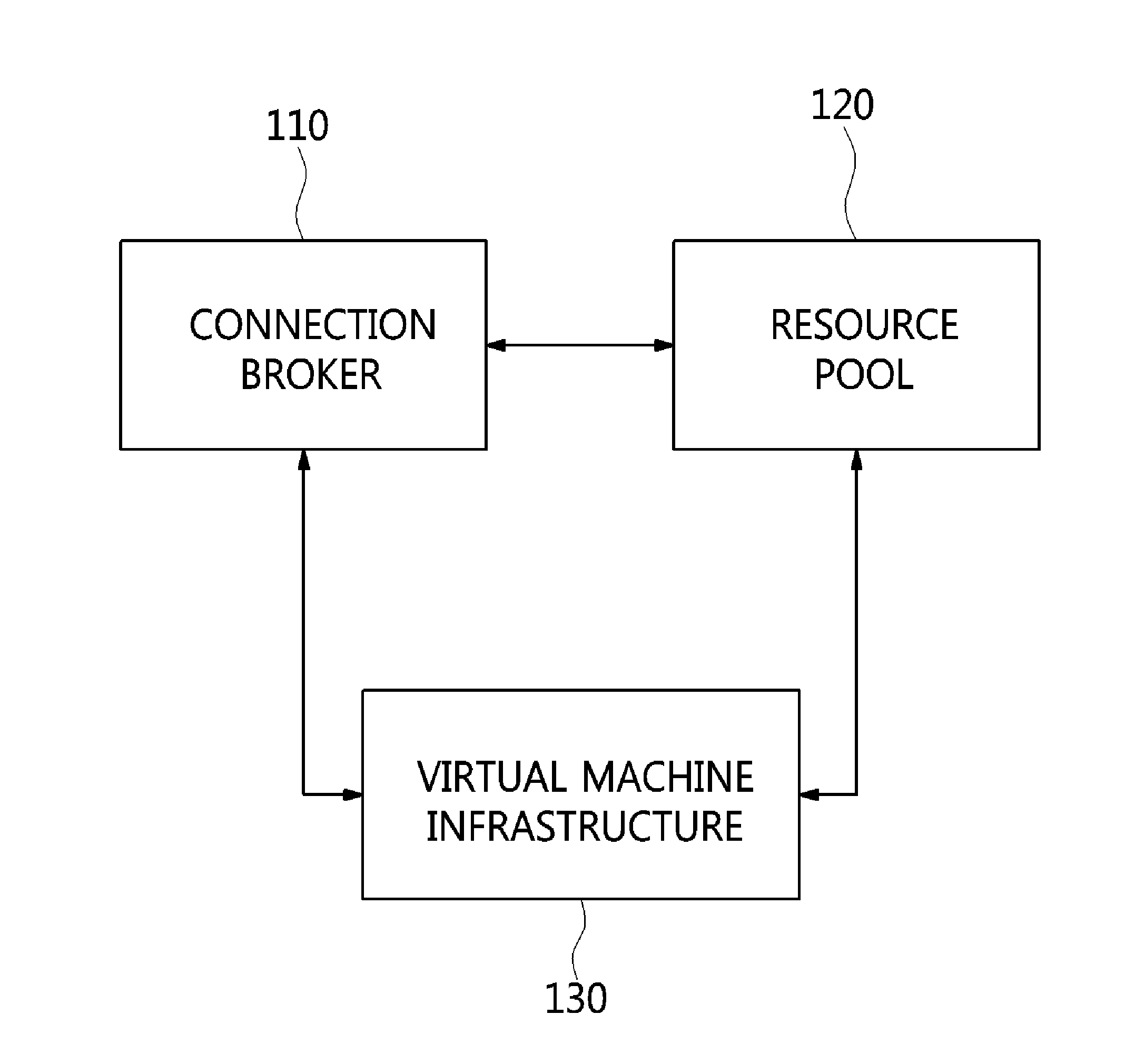
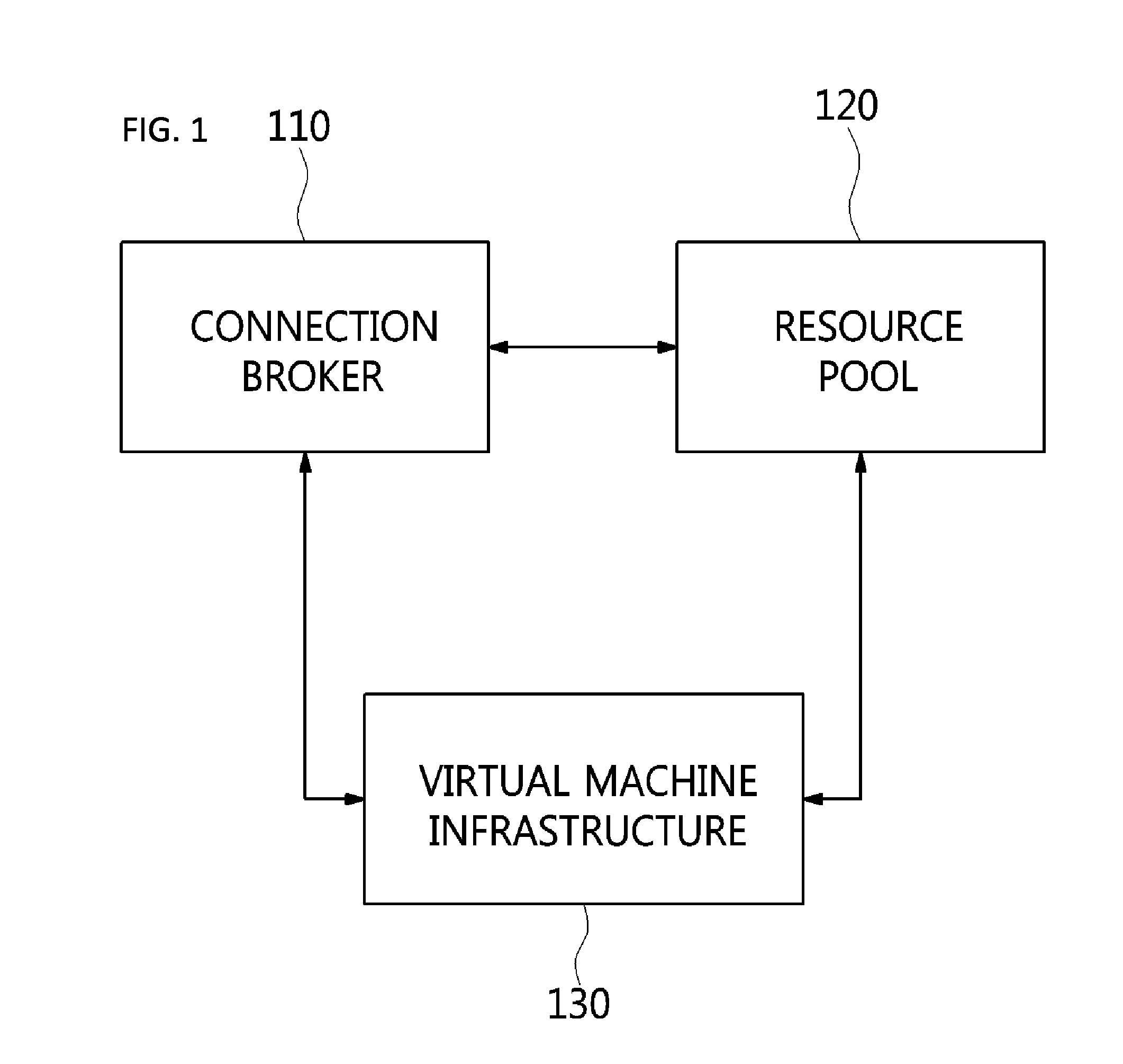
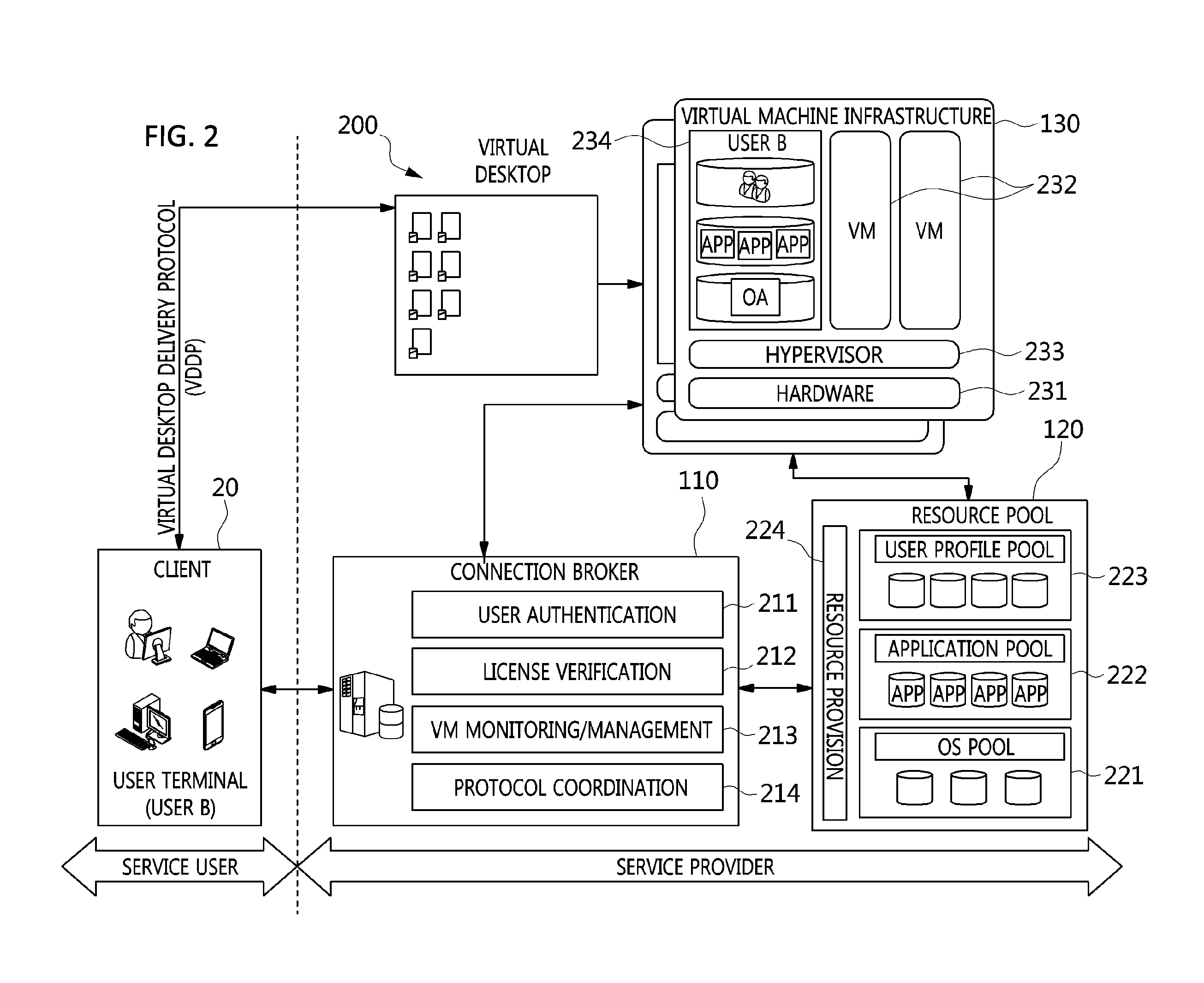
The present invention relates to a method and an architecture capable of efficiently providing a virtual desktop service. The service architecture for the virtual desktop service includes a connection broker for performing the management of virtual machines, a server monitoring function, and a protocol coordination function. A resource pool is configured to manage software resources that are transferred to a specific virtual machine in a streaming form at a predetermined time and that are executed on the specific virtual machine and to provide provision information about the managed software resources at the request of the connection broker, in order to provide an on-demand virtual desktop service. A virtual machine infrastructure is configured to support hardware resources, generate virtual machines in which the software of the user terminal is operated, and provide the virtual machines as virtual desktops.
Owner:ELECTRONICS & TELECOMM RES INST
Apparatus and method for virtual desktop service
ActiveUS9489227B2Efficiently providedResource allocationPlatform integrity maintainanceResource poolSpecific time
Disclosed herein are a method and architecture capable of efficiently providing virtual desktop service. A service architecture for virtual desktop service according to the present invention includes a connection broker configured to perform authentication, manage virtual machines, and perform a server monitoring and protocol coordination function, a resource pool configured to manage software resources that are delivered to a specific virtual machine in a streaming form on a specific time in order to provide on-demand virtual desktop service and are executed on the specific virtual machine and to provide provision information about the managed software resources in response to a request from the connection broker, and a virtual machine infrastructure configured to support hardware resources, generate virtual machines in which the software of a user terminal is executed, and provide the generated virtual machine as virtual desktops.
Owner:ELECTRONICS & TELECOMM RES INST
Virtualized desktop allocation system using virtual infrastructure
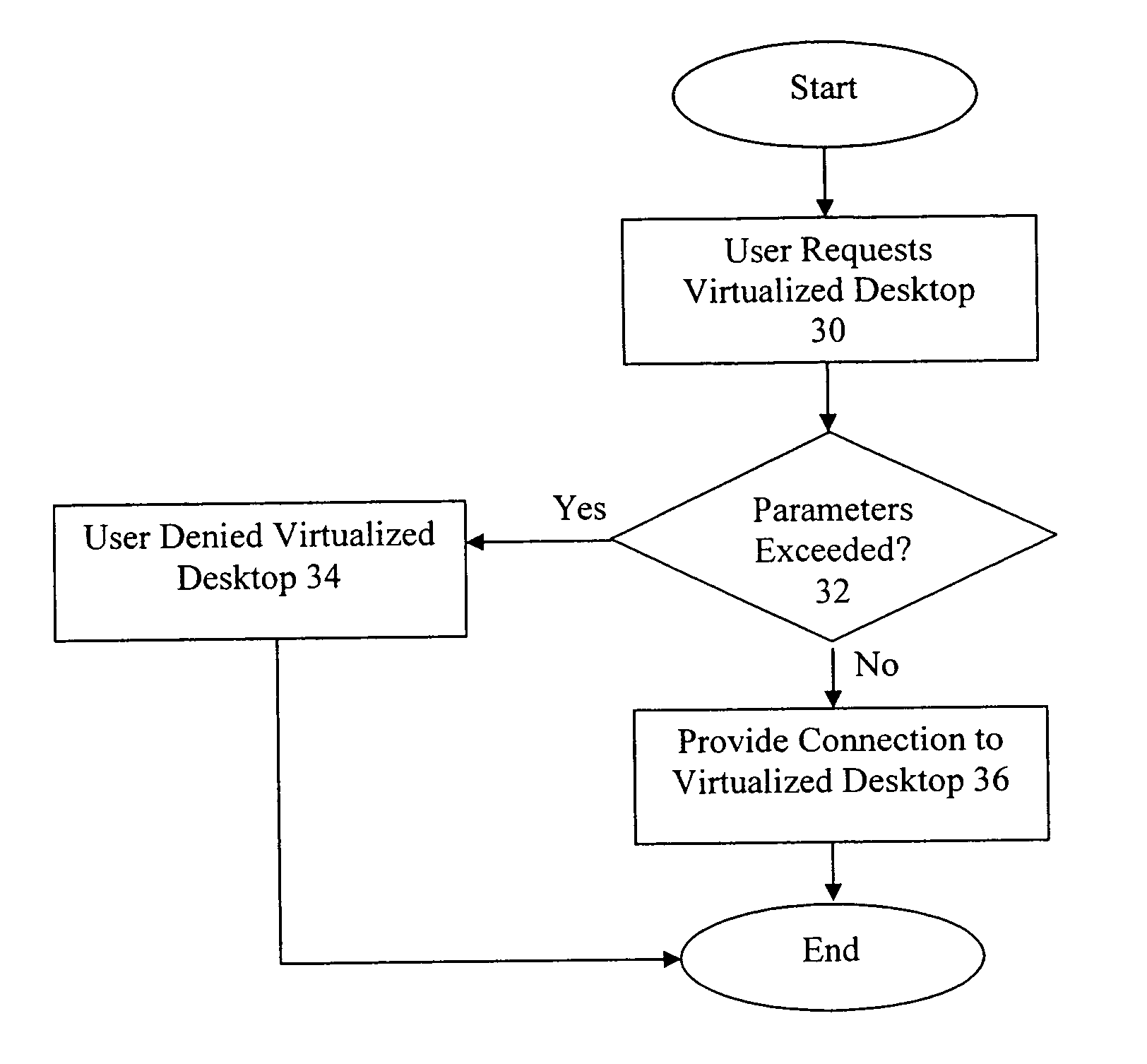
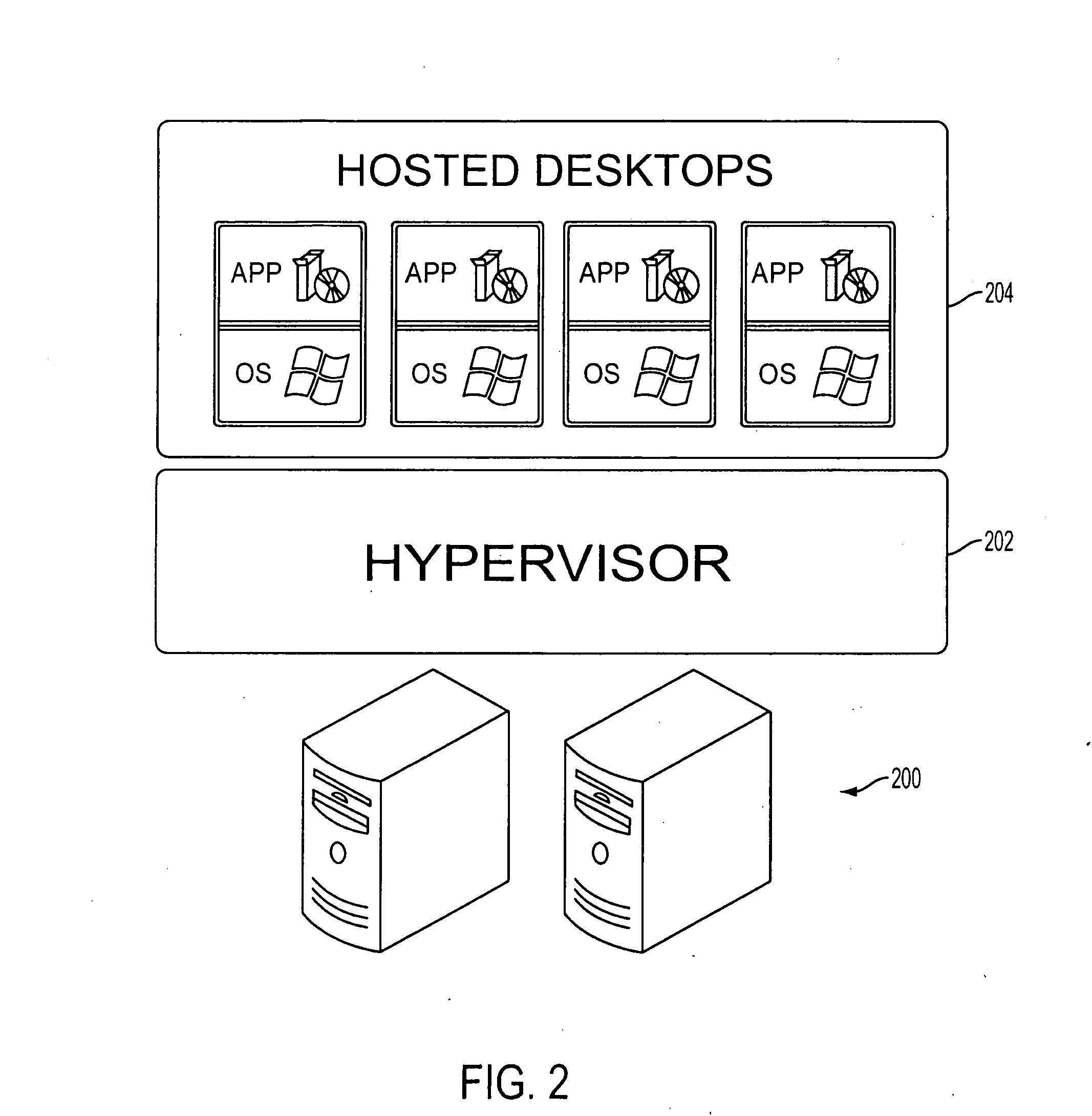
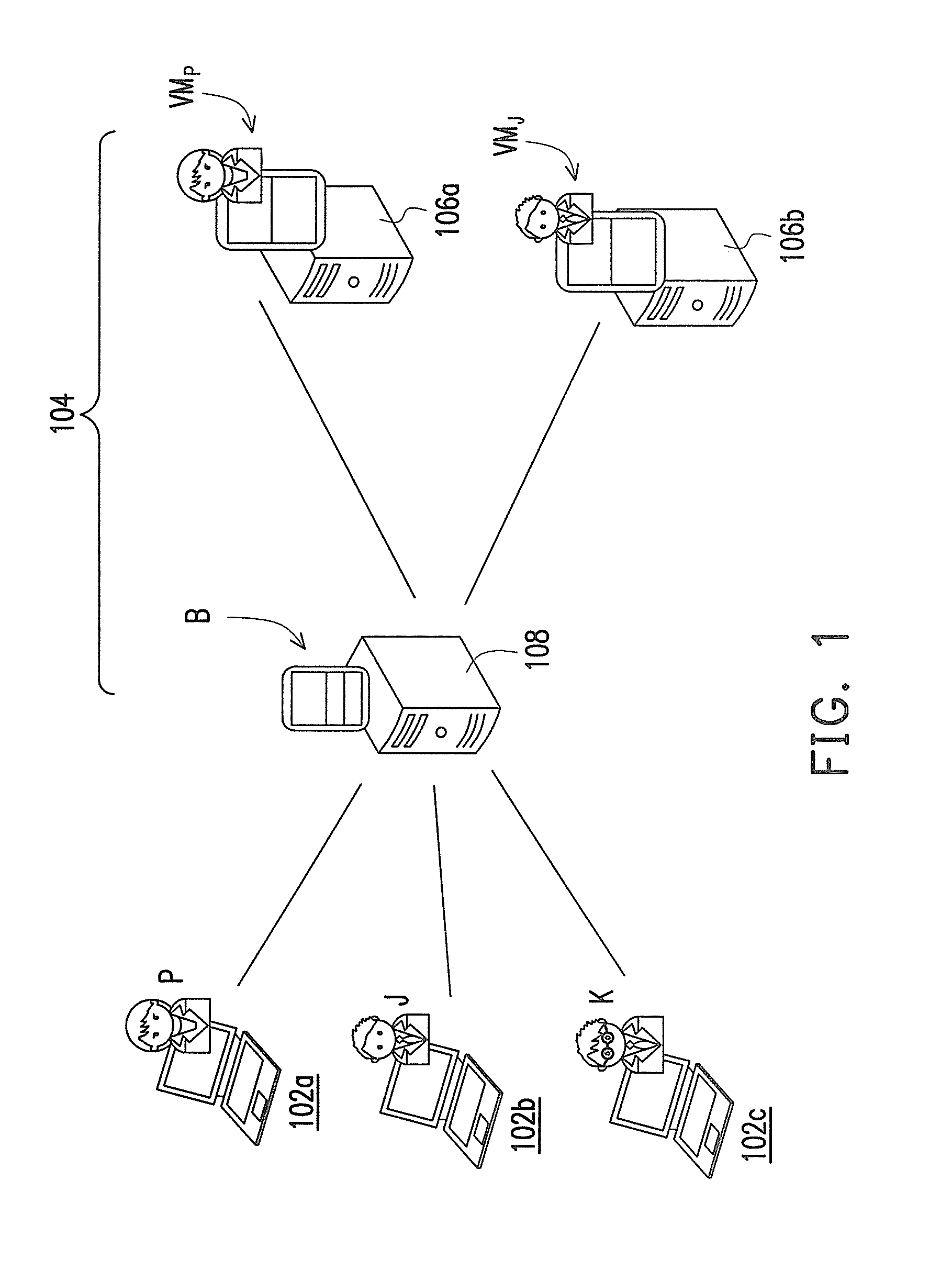
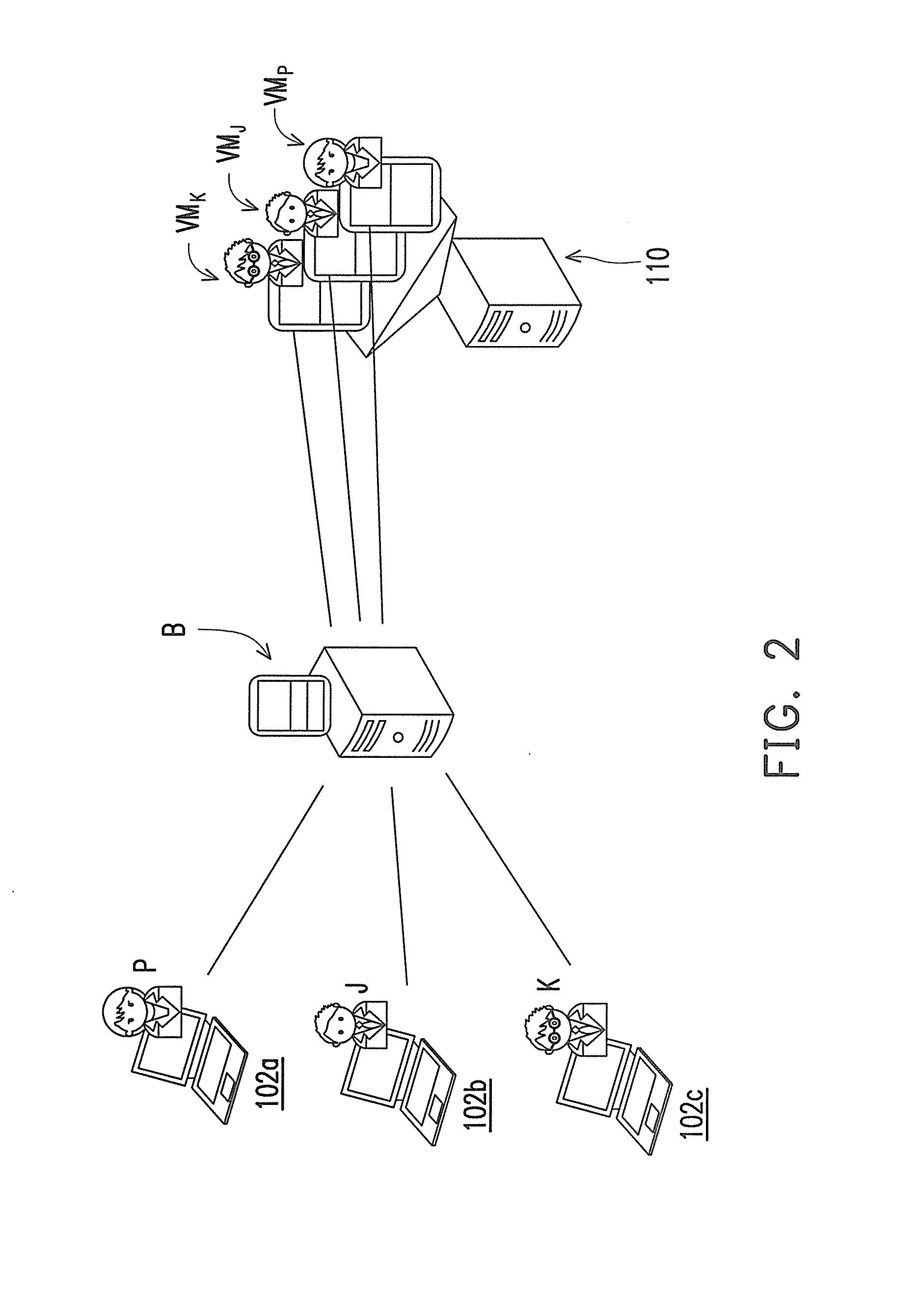
A plurality of virtual machines (VMs) is established and maintained by virtualization software on one or more physical servers. Desktop management software operates to provide the VMs to remote users as virtualized desktops. The desktop management software includes a connection broker, that allows a remote user to select a type of virtualized desktop and initiate a desktop session. The desktop management software further includes lease management functionality, that ensures users are provided access to a particular virtualized desktop for only a fixed period of time. In addition, the desktop management software provides an administrative console, which allows an administrator to set various parameters, including QoS parameters, and parameters specifying the resources allocated to each user. The desktop management software interacts with lower level software to provide load-balancing functionality, that adjusts the resources provided to each VM based on the needs of the VM. The load-balancing functionality also ensures that QoS parameters are met, and that the parameters specifying the maximum resources allocated to each user are not exceeded.
Owner:VMWARE INC
Method and architecture for virtual desktop service
ActiveUS20130007737A1Avoid lossEfficiently provideMultiple digital computer combinationsDigital data authenticationResource poolOn demand
The present invention relates to a method and an architecture capable of efficiently providing a virtual desktop service. The service architecture for the virtual desktop service includes a connection broker for performing the management of virtual machines, a server monitoring function, and a protocol coordination function. A resource pool is configured to manage software resources that are transferred to a specific virtual machine in a streaming form at a predetermined time and that are executed on the specific virtual machine and to provide provision information about the managed software resources at the request of the connection broker, in order to provide an on-demand virtual desktop service. A virtual machine infrastructure is configured to support hardware resources, generate virtual machines in which the software of the user terminal is operated, and provide the virtual machines as virtual desktops.
Owner:ELECTRONICS & TELECOMM RES INST
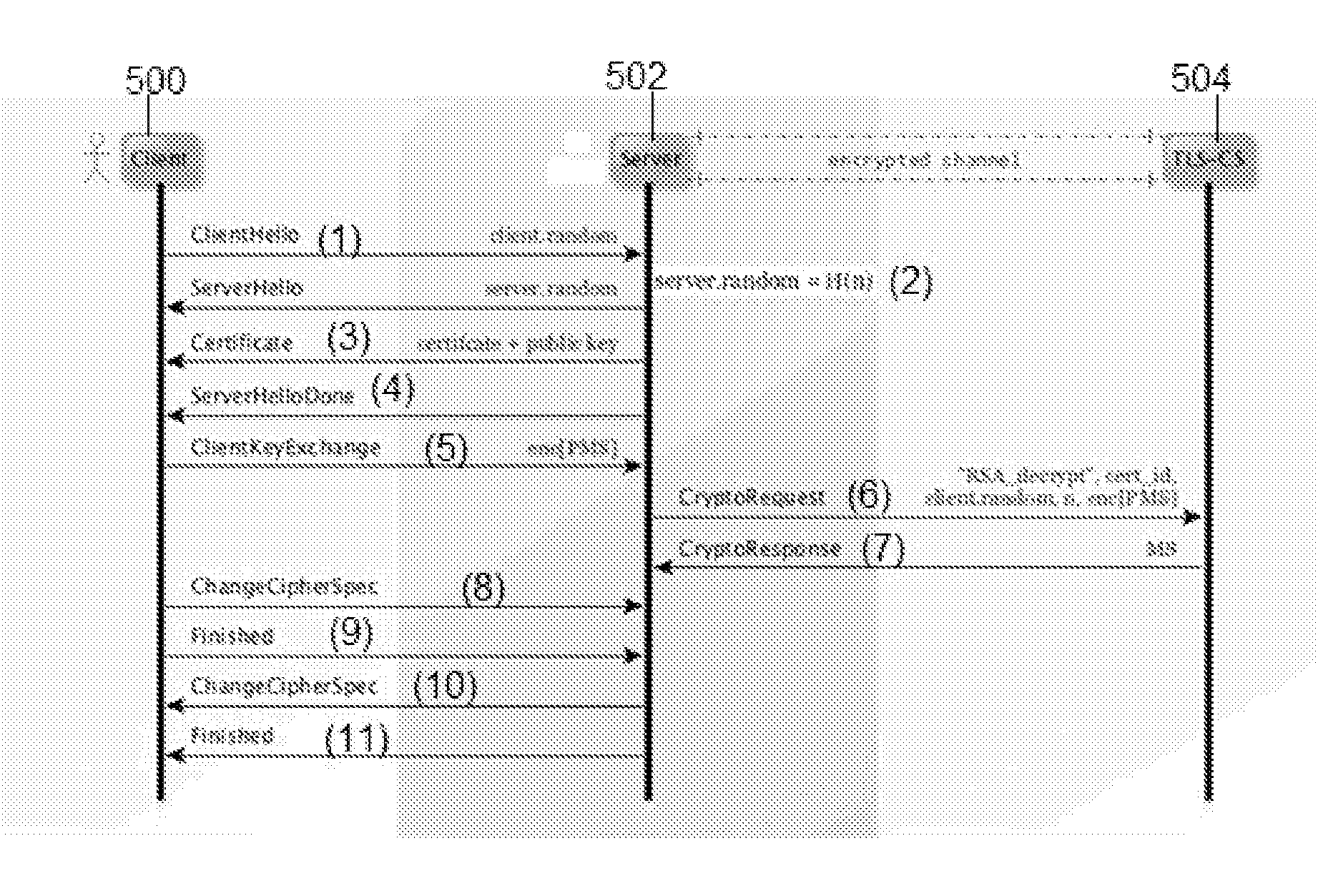
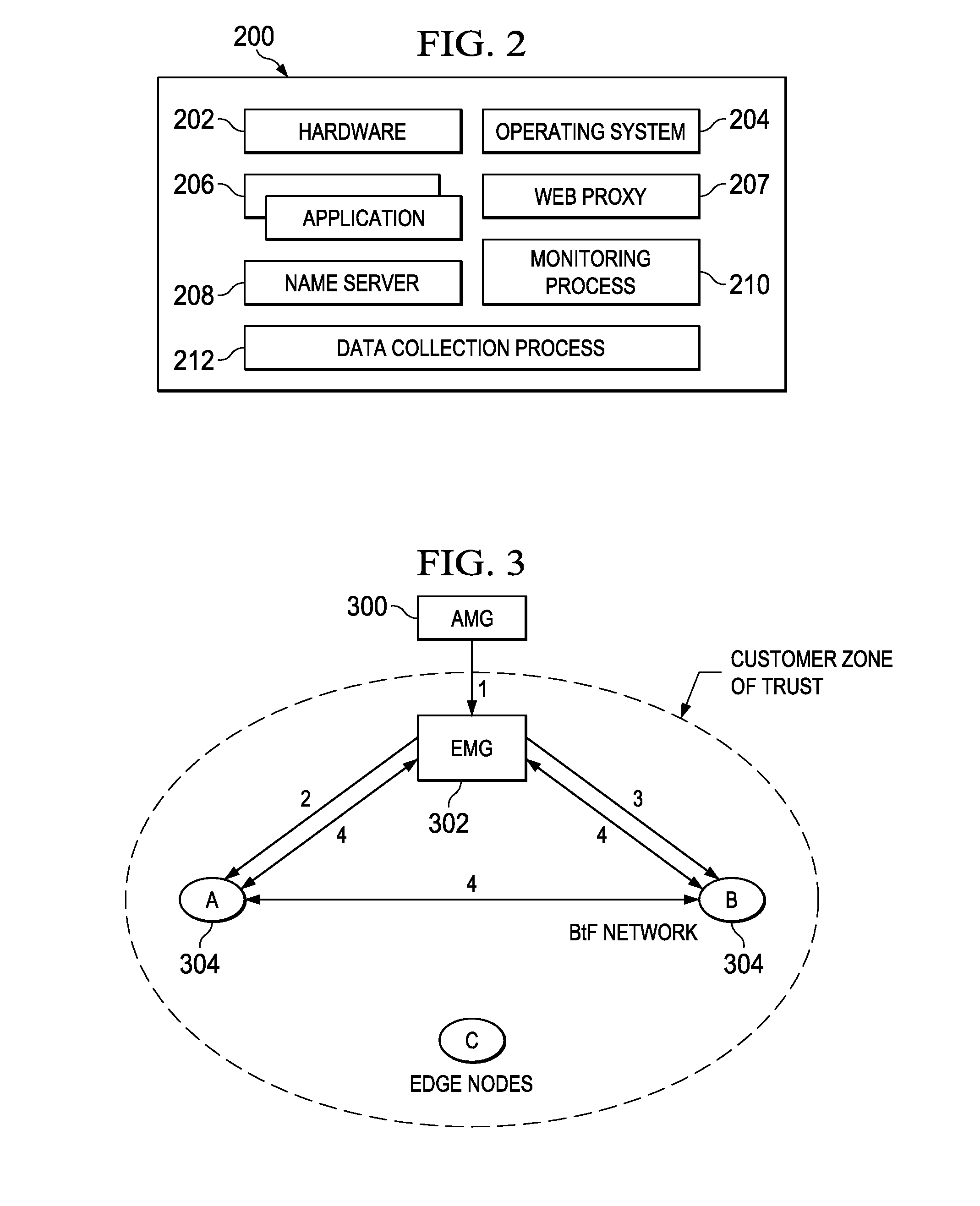
Providing forward secrecy in a terminating TLS connection proxy
ActiveUS20150106624A1User identity/authority verificationElectrical componentsProtocol for Carrying Authentication for Network AccessForward secrecy
An infrastructure delivery platform provides a RSA proxy service as an enhancement to the TLS / SSL protocol to off-load, from an edge server to an external cryptographic server, the decryption of an encrypted pre-master secret. The technique provides forward secrecy in the event that the edge server is compromised, preferably through the use of a cryptographically strong hash function that is implemented separately at both the edge server and the cryptographic server. To provide the forward secrecy for this particular leg, the edge server selects an ephemeral value, and applies a cryptographic hash the value to compute a server random value, which is then transmitted back to the requesting client. That server random value is later re-generated at the cryptographic server to enable the cryptographic server to compute a master secret. The forward secrecy is enabled by ensuring that the ephemeral value does not travel on the wire.
Owner:AKAMAI TECH INC
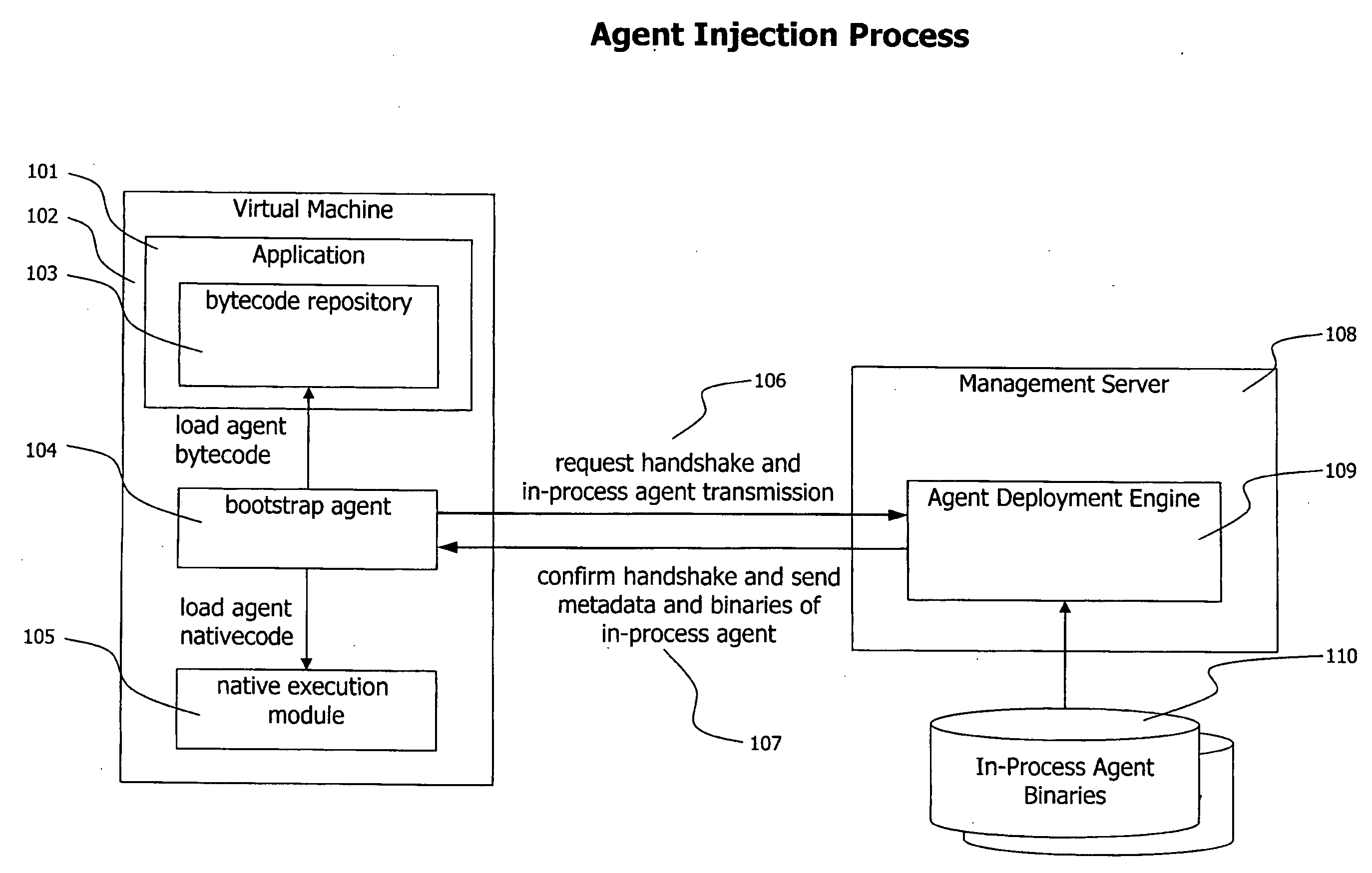
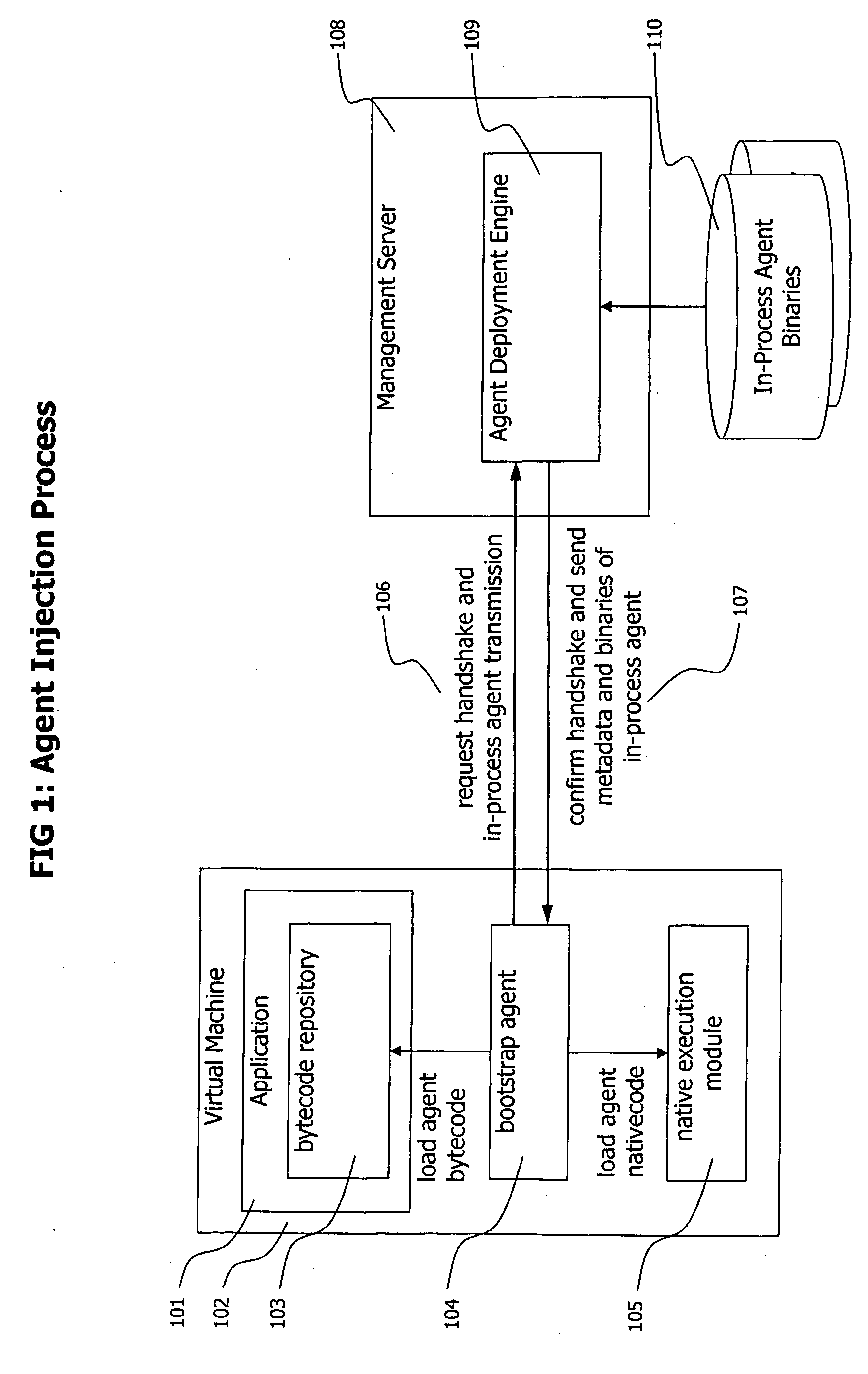
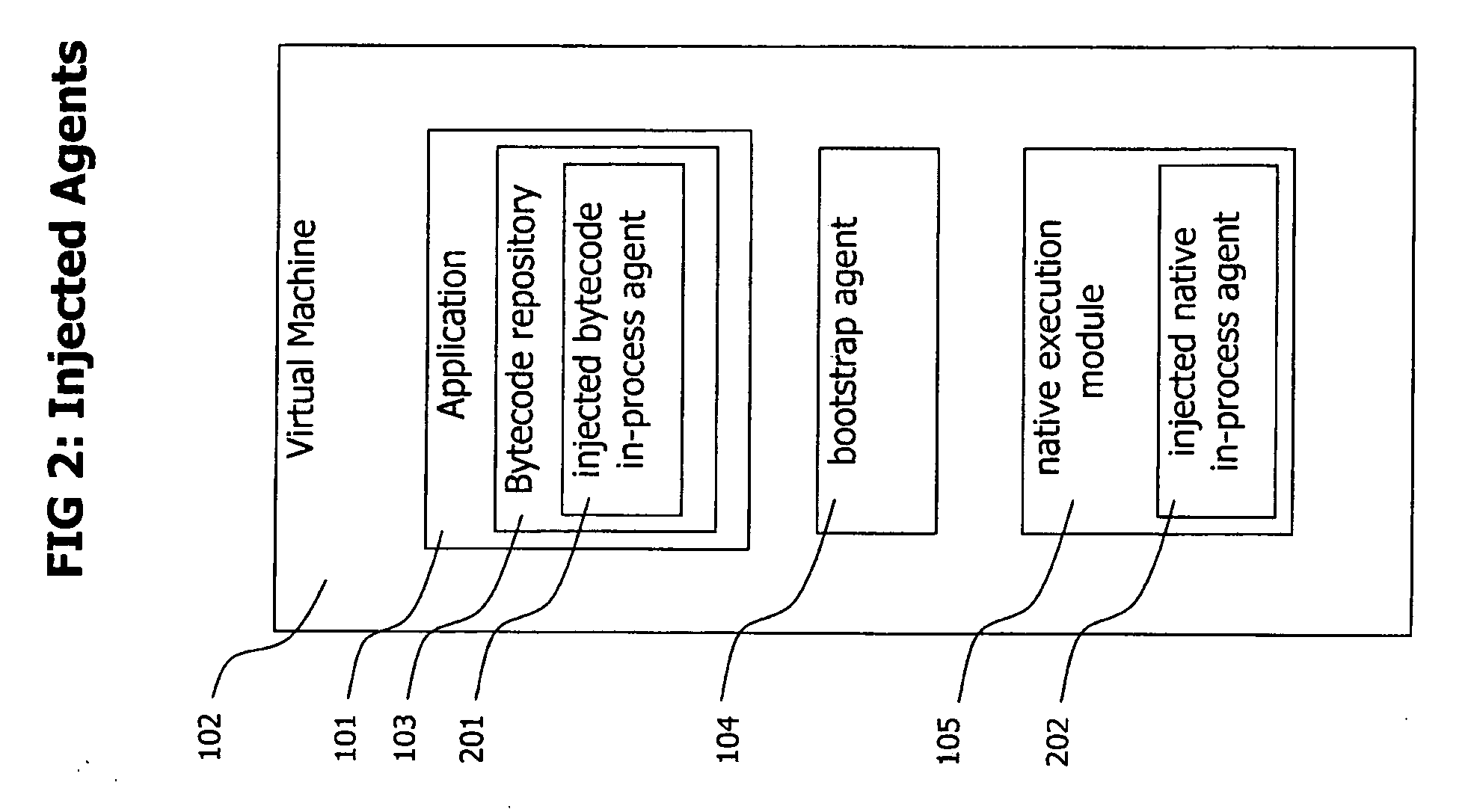
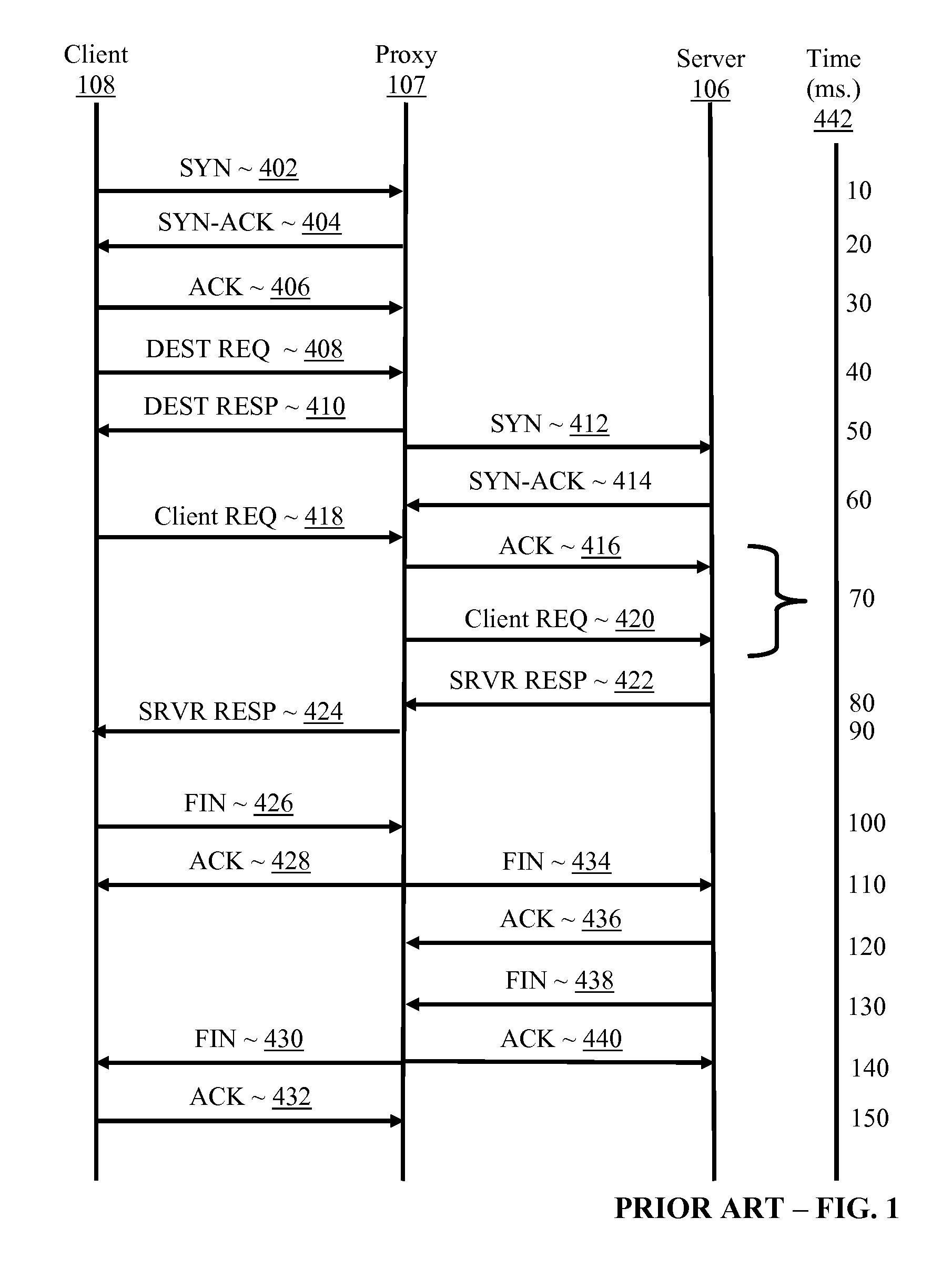
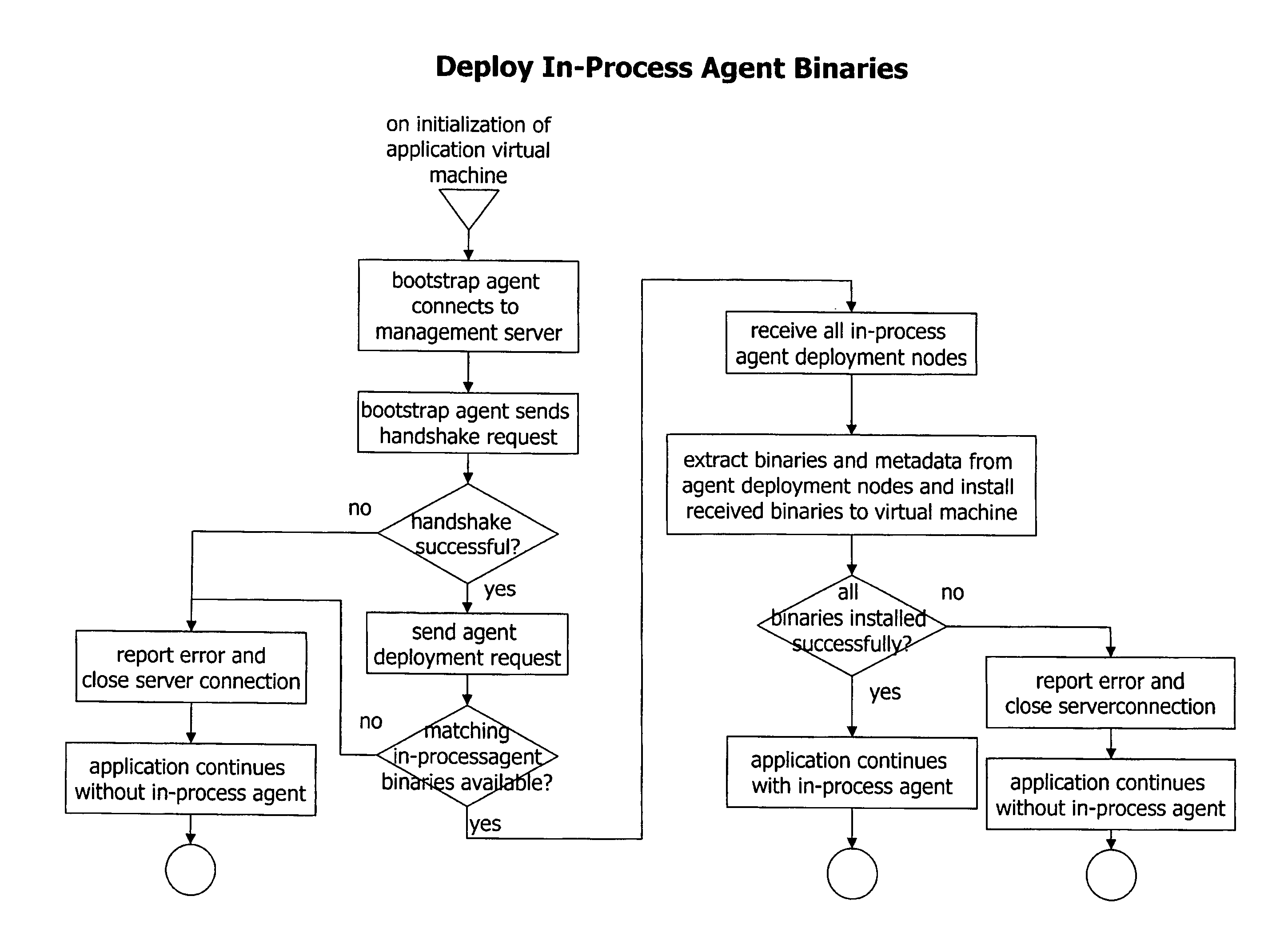
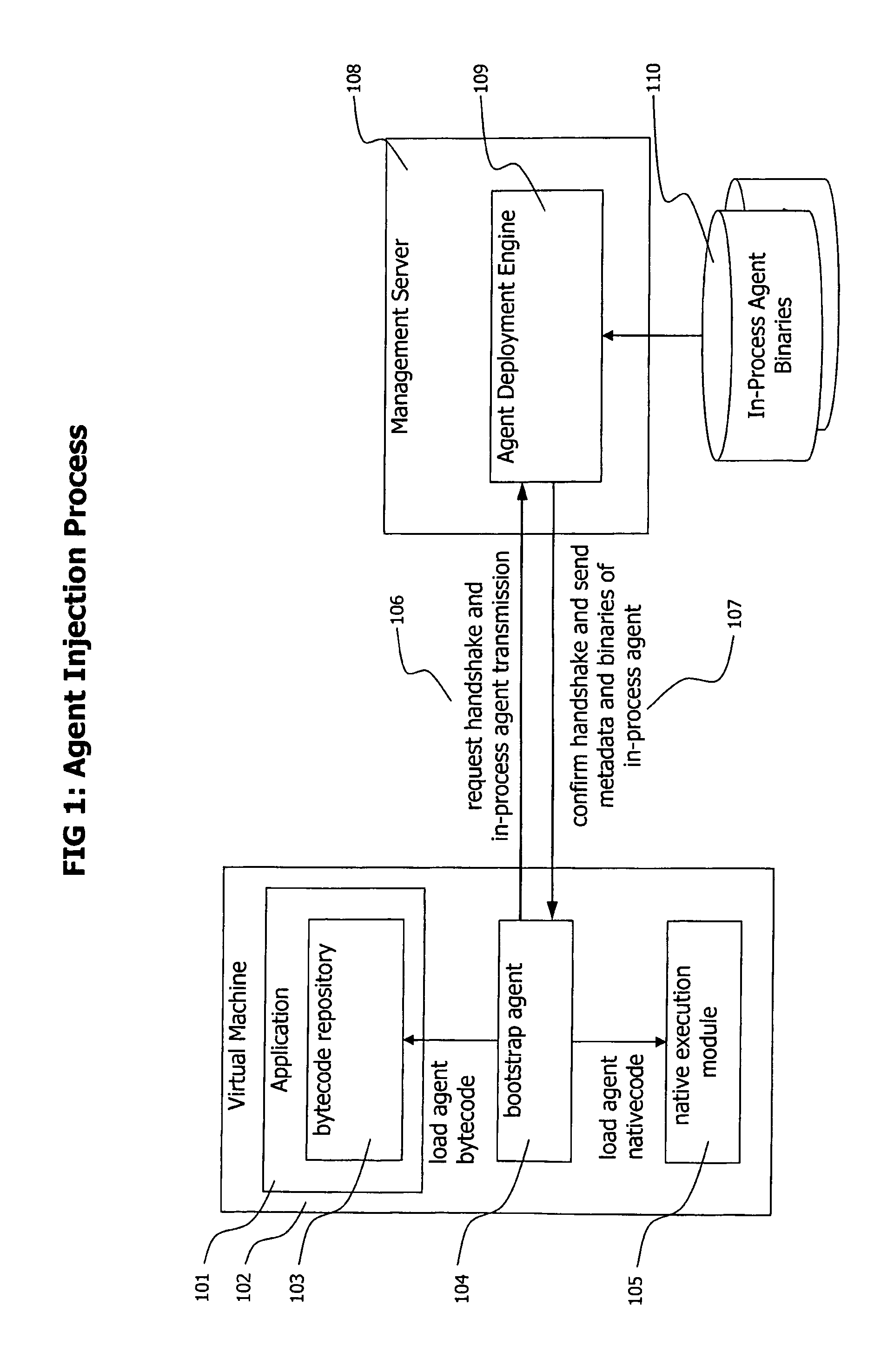
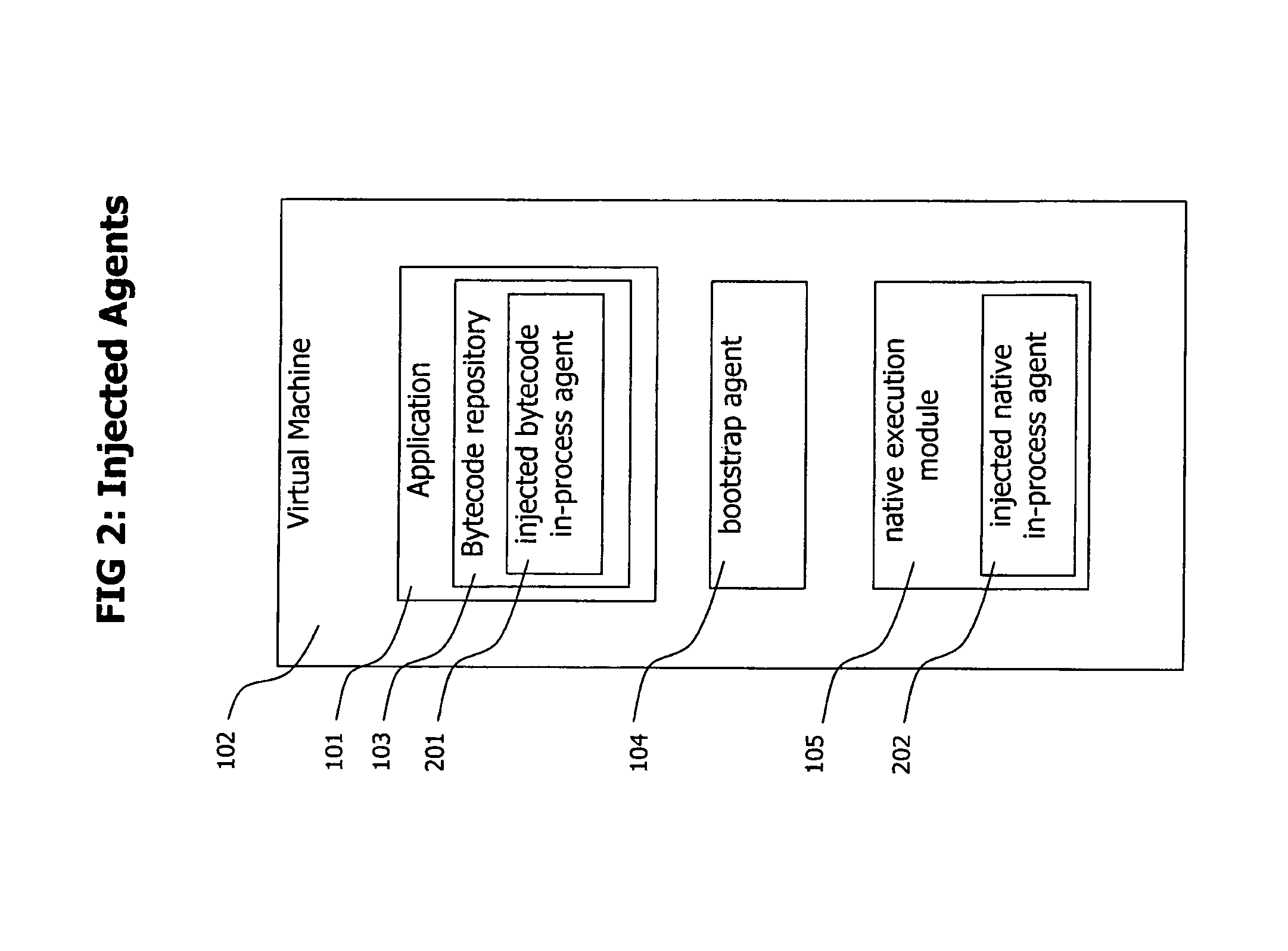
Method and System for Dynamic Remote injection of In-process Agents into Virtual Machine based Applications
A method and system for dynamic and adaptive deployment of in-process agents to virtual machine based applications which may run on remote hosts is provided. A bootstrap agent is injected into the application, using standardized interfaces provided by virtual machine based systems like Sun Microsystems' Java or Microsoft's .NET. Said bootstrap agent establishes a network connection to a management server which provides binaries representing in-process agents in bytecode or native code format. The bootstrap agent sends data identifying its runtime environment to the management server, which determines the matching in-process agent binaries for the runtime environment of the connected agent and sends the selected binaries to the bootstrap agent. The bootstrap agent receives the binaries and installs them to its hosting virtual machine, according to their format (bytecode or native code).
Owner:DYNATRACE
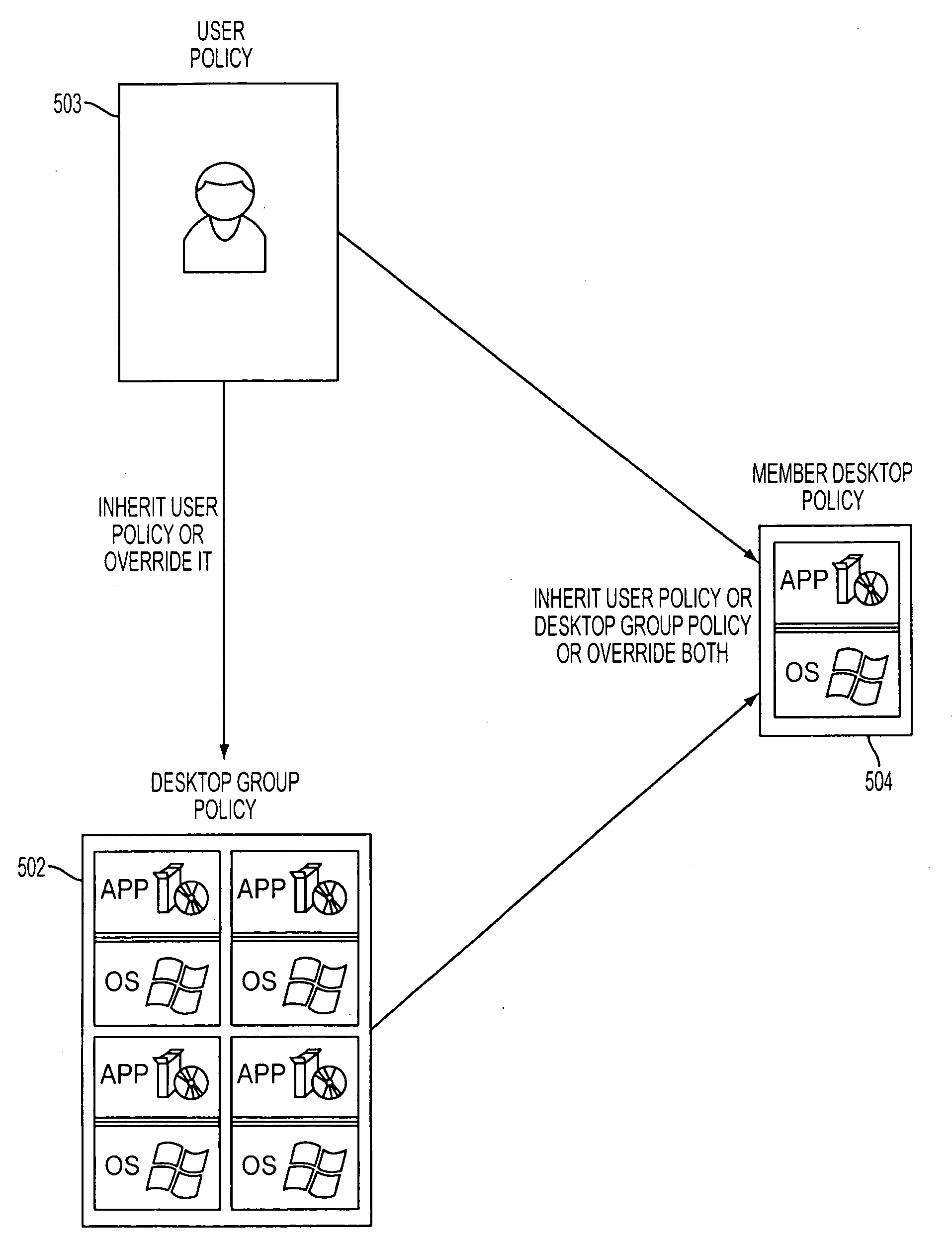
System for provisioning, allocating, and managing virtual and physical desktop computers in a network computing environment
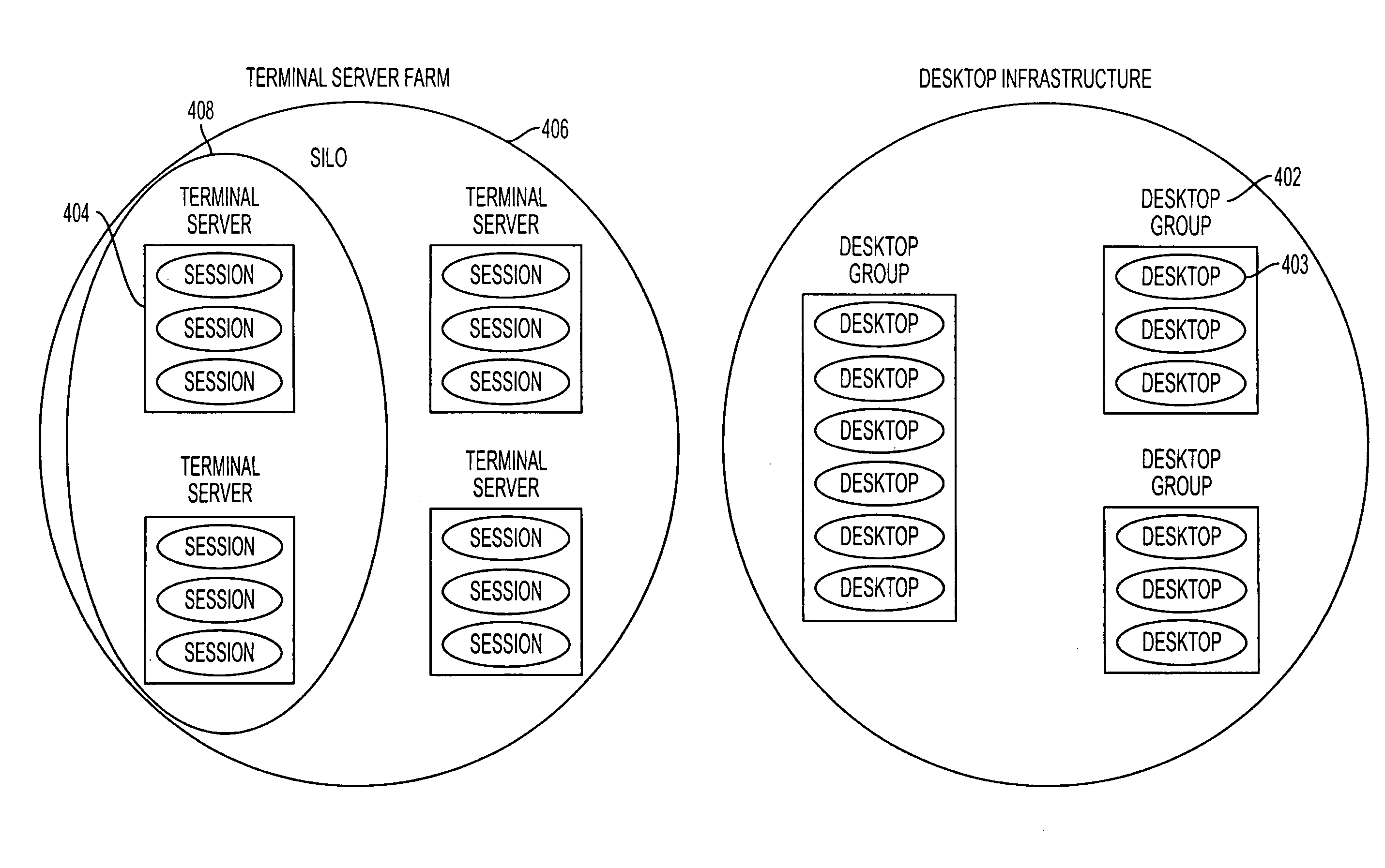
A system for provisioning, allocating, and managing virtual and physical desktop computers in an enterprise network computing environment allows for these physical and desktop computers to be grouped logically based on personnel, organizational, or networking efficiencies without regard to the hardware or server that will ultimately run the virtual machine terminal once it is accessed. A connection broker connects incoming connections to one desktop in a desktop group, based on information relating to that incoming connection.
Owner:DELL PROD LP
Client-side network access policies and management applications
ActiveUS8200773B2Digital data processing detailsMultiple digital computer combinationsData terminalNetwork management application
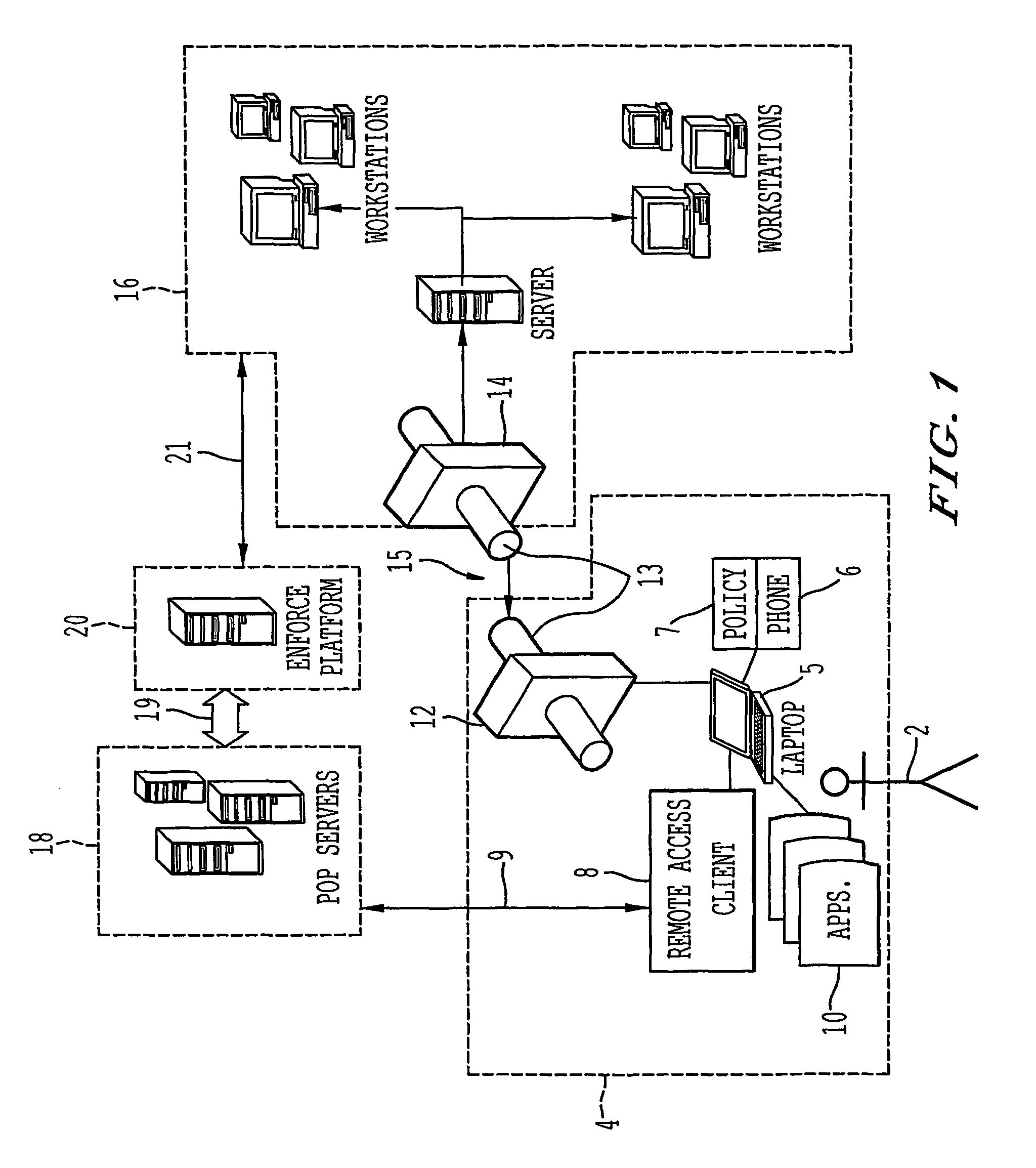
A remote access client is provided for enabling communication between a remote data terminal configured to access a public network, and an enterprise network by way of a VPN tunnel through the public network. The remote access client includes at least one application program interface (API) to receive a first verification of the operating state of a predetermined application of the remote data terminal to enable a connection agent for establishing a point of presence on the public network. Upon connection to the point of presence, the API exchanges data between the remote access client and the predetermined application of the remote data terminal. The remote access client receives a second periodic verification of the operating state of the predetermined application via the API for terminating the connection to the point of presence upon the absence of the second verification. The point of presence enables the VPN tunnel for transporting data from the remote data terminal to the enterprise network across the public network.
Owner:GINEGAR LLC
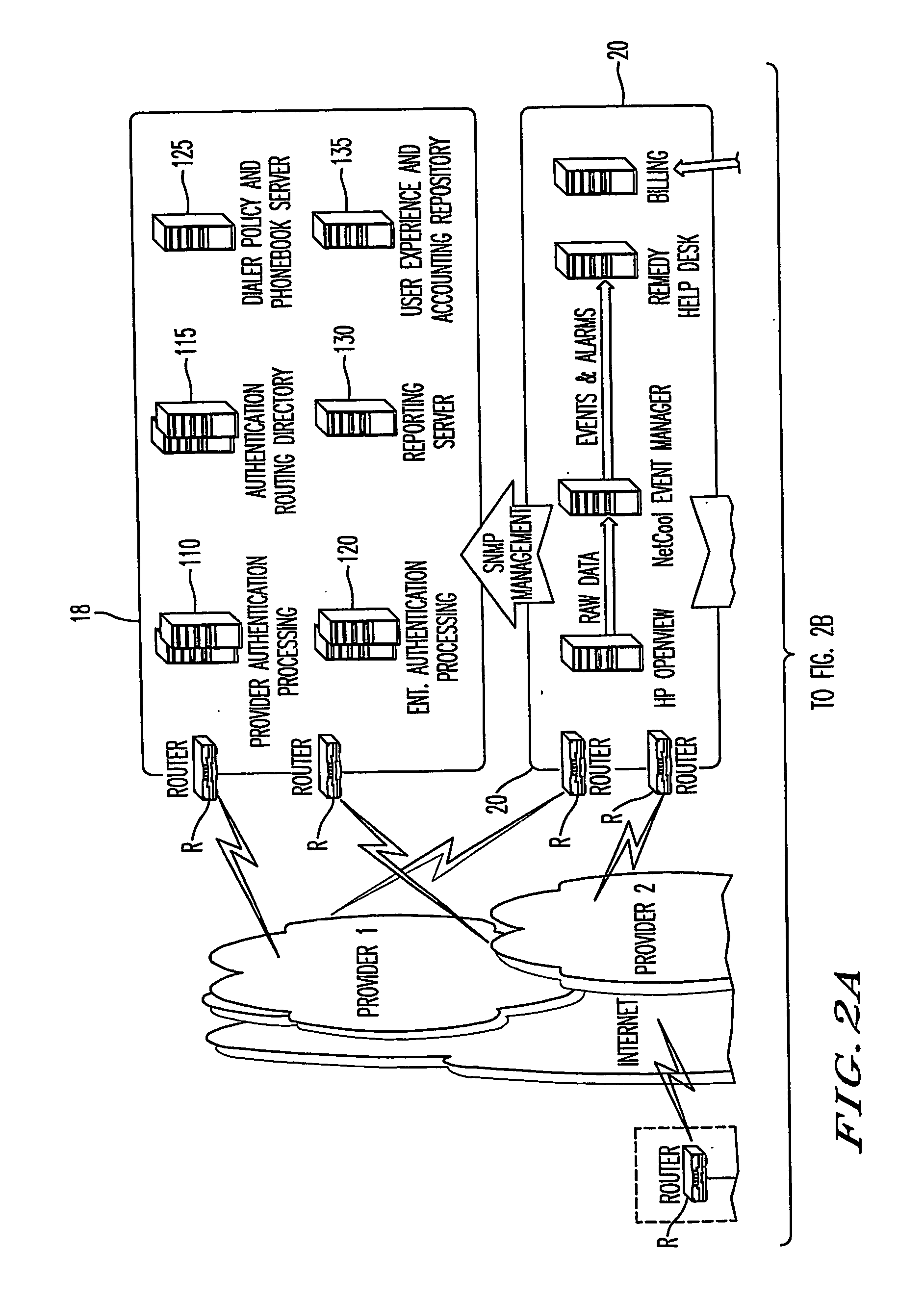
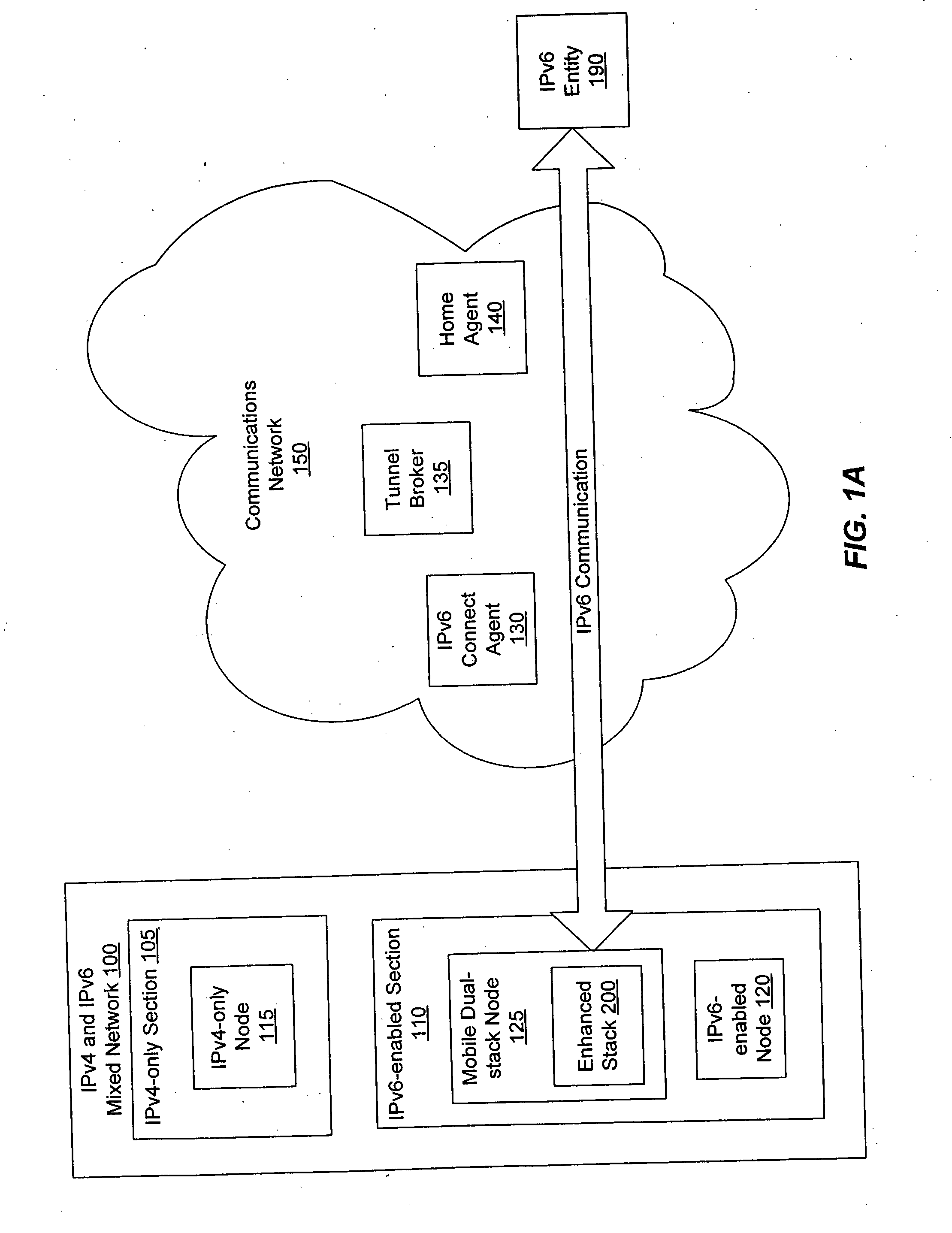
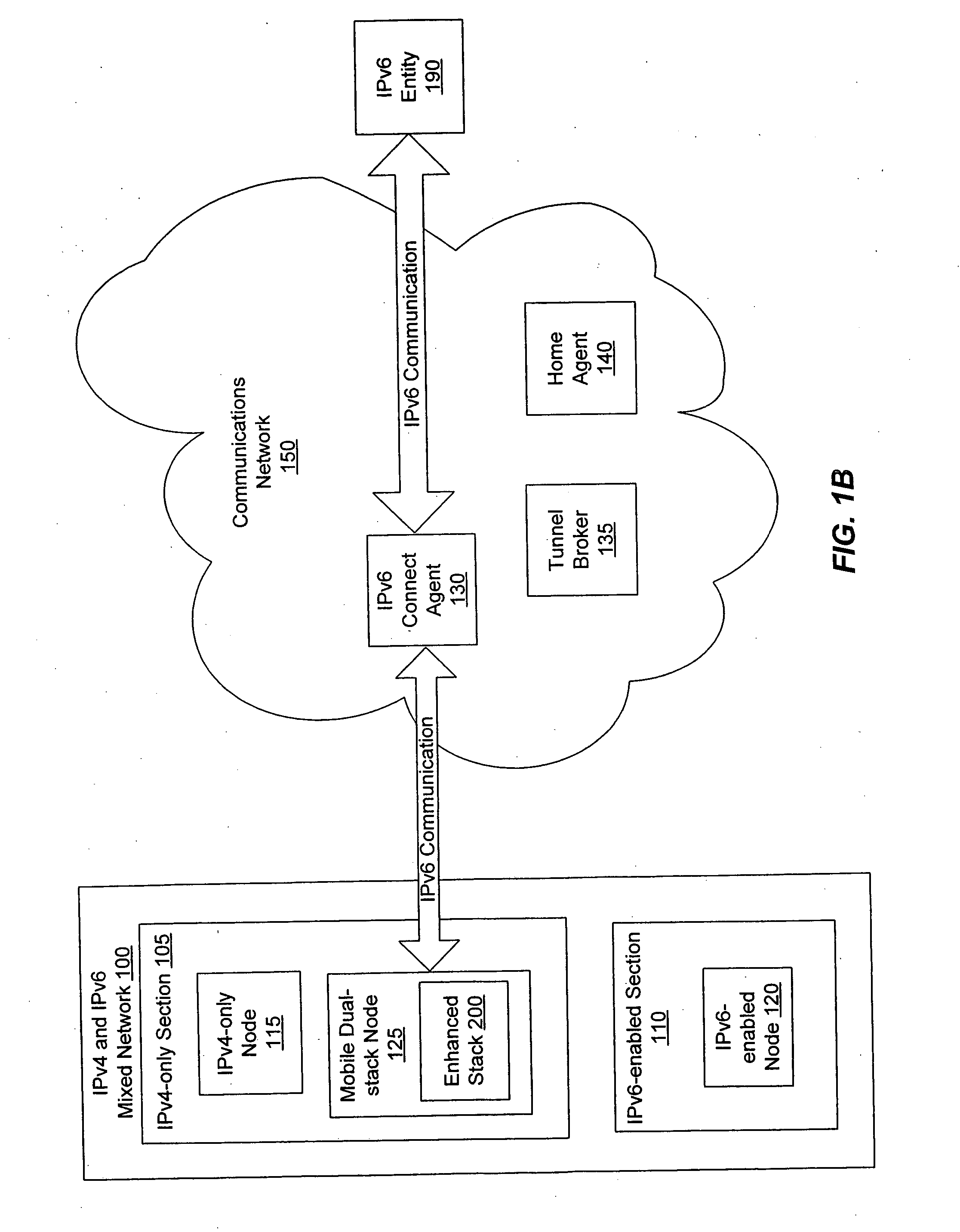
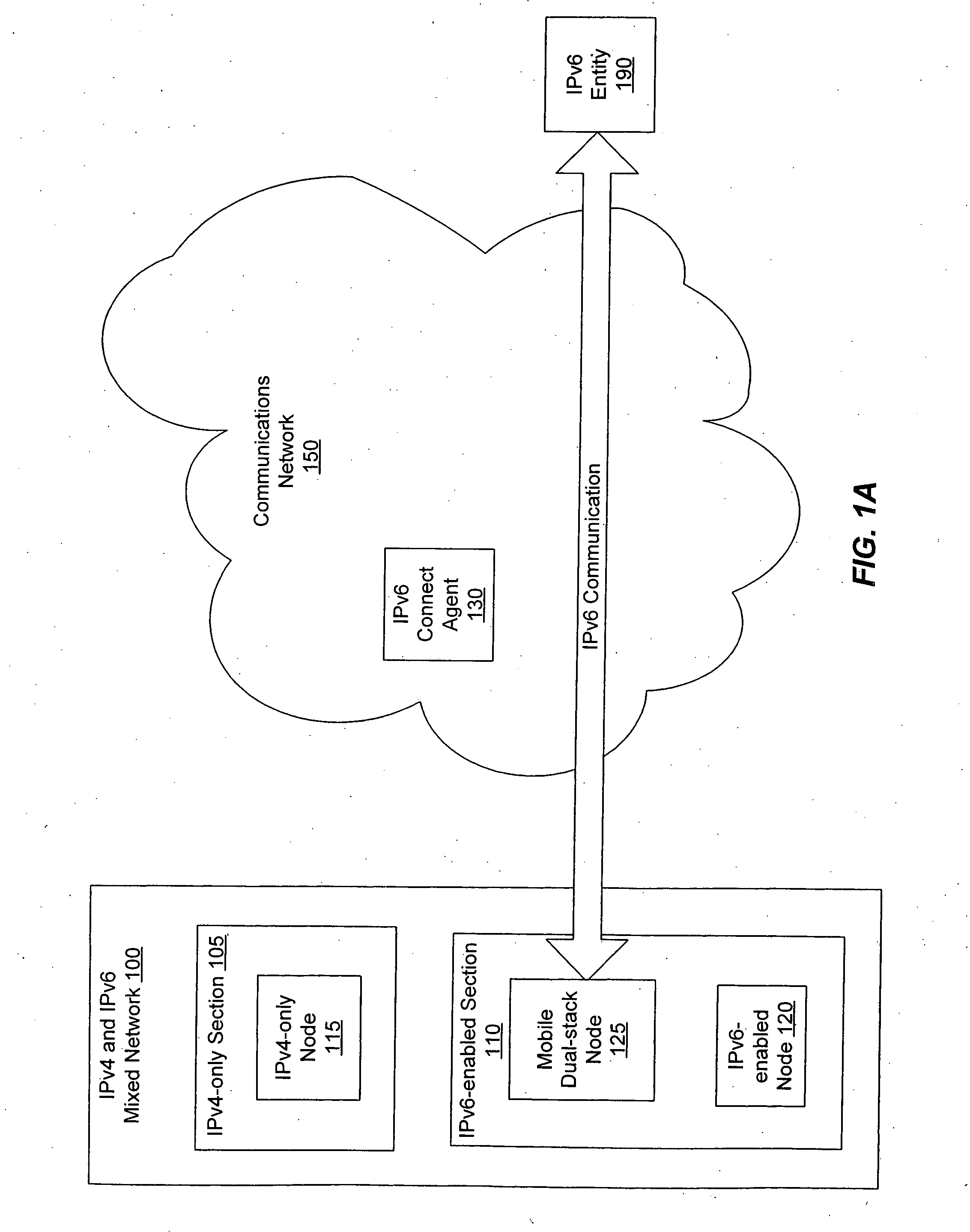
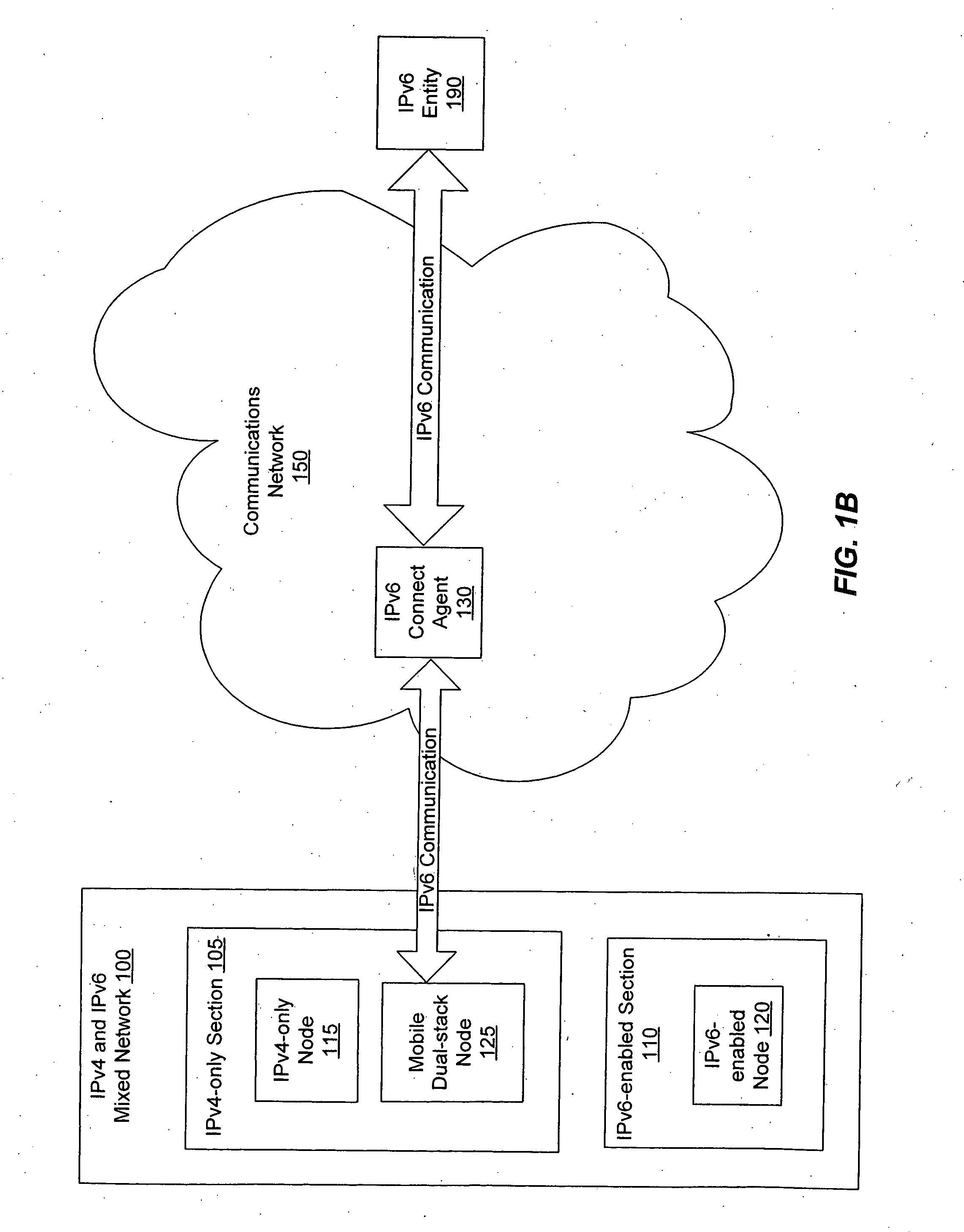
Enabling mobile IPv6 communication over a network containing IPv4 components using a tunnel broker model
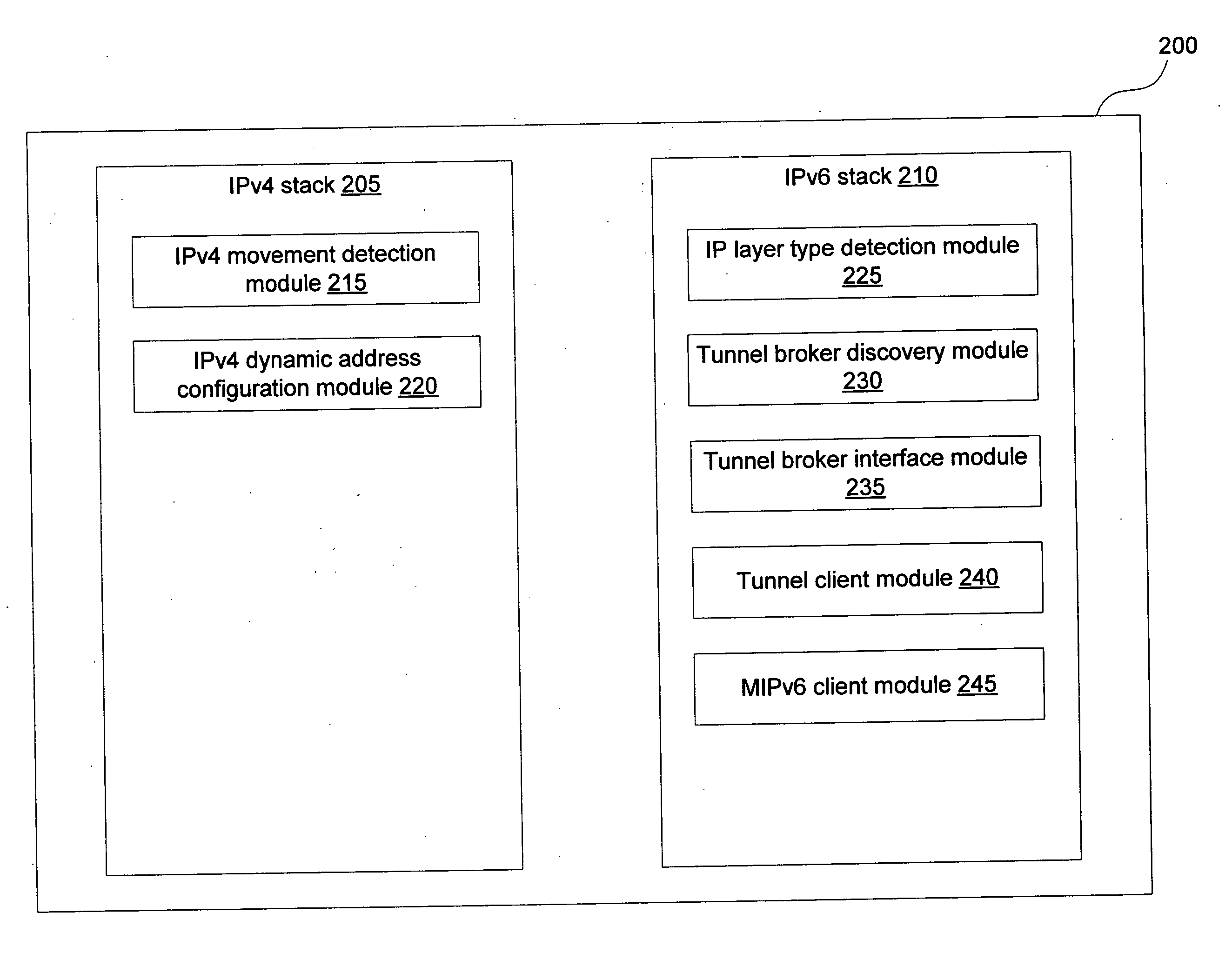
InactiveUS20050099976A1Reducing packet lossTime-division multiplexWireless network protocolsData packTunnel broker
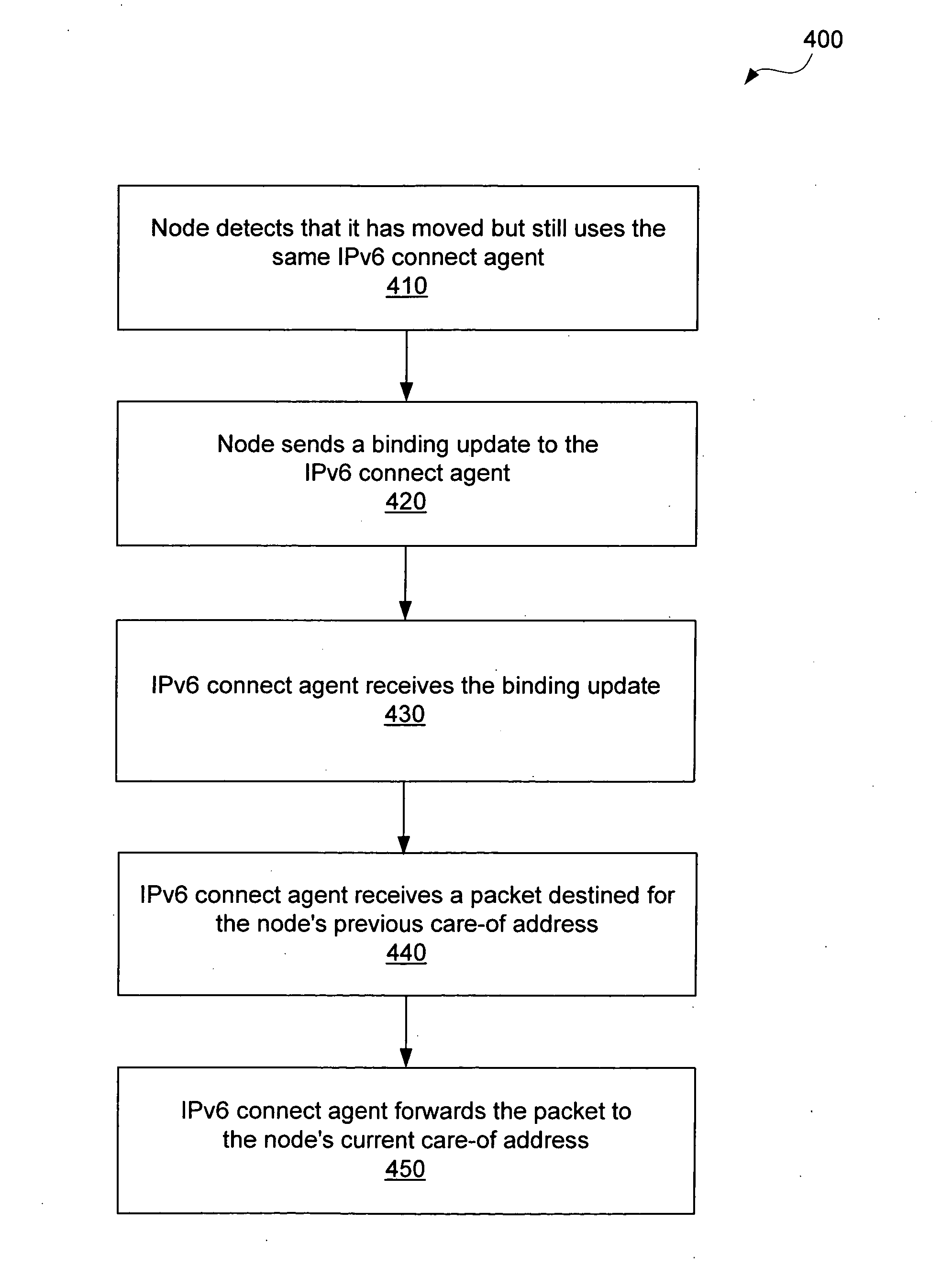
A mobile dual-stack node engages in IPv6 communication while roaming within an IPv4-only network. The node determines that it has moved and obtains a new IPv4 address. After determining that the visited network contains no IPv6-enabled components, the node communicates with a tunnel broker to obtain a care-of address and a tunnel to an IPv6 connect agent (e.g., a tunnel server). If the obtained care-of address differs from the care-of address that the node had been using prior to the move, the node sends MIPv6 binding updates to its home agent and corresponding peers. The node can optimize the handoff when it has obtained a different care-of address by sending a binding update to the connect agent comprising the previous care-of address and the current care-of address. When the connect agent receives a packet destined for the previous care-of address, it forwards the packet to the current care-of address.
Owner:KDDI CORP
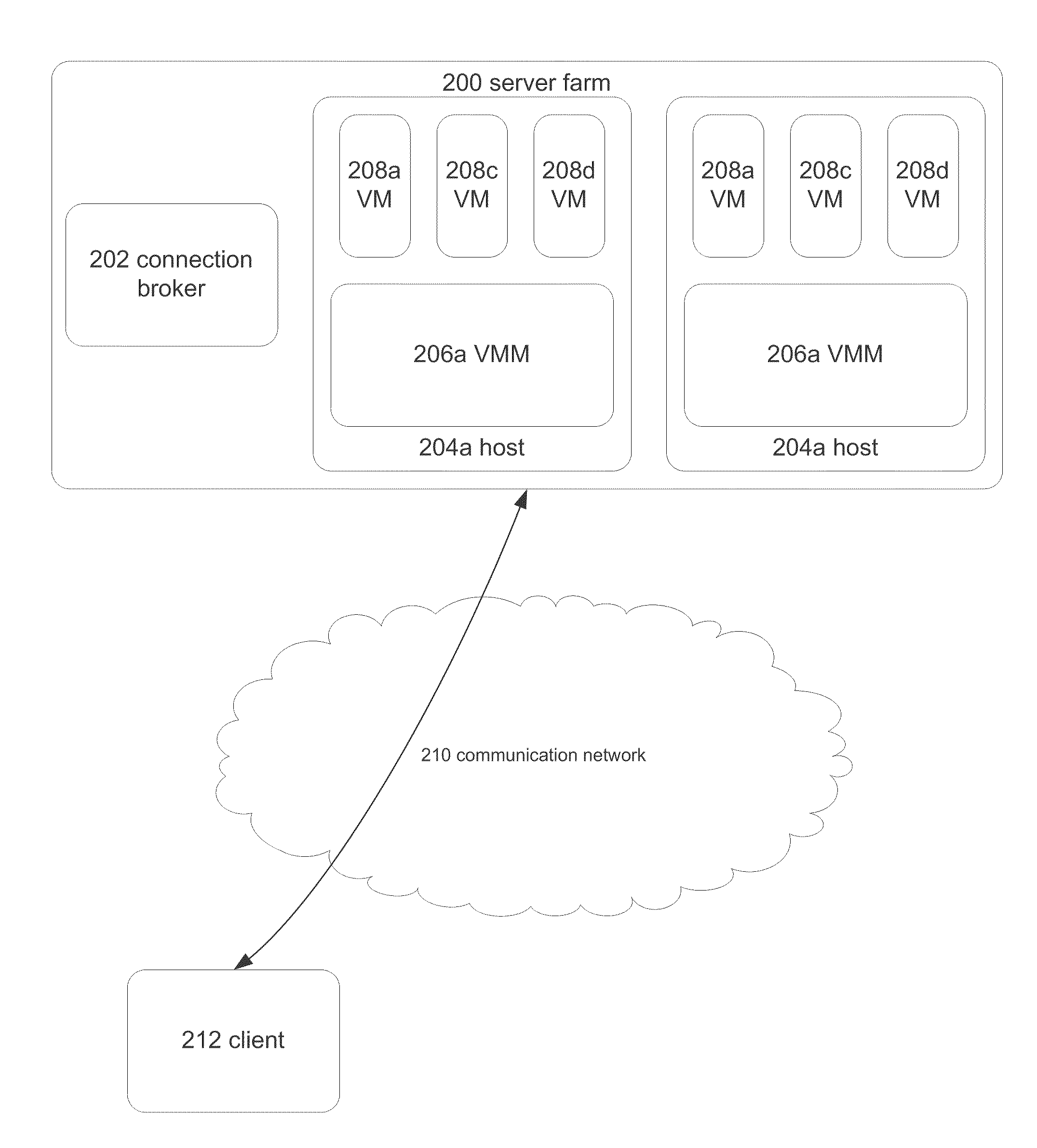
Virtualized Eco-Friendly Remote Presentation Session Role
ActiveUS20110161957A1Minimize the numberReduce electricity consumptionEnergy efficient ICTMultiple digital computer combinationsVirtualizationOperating system
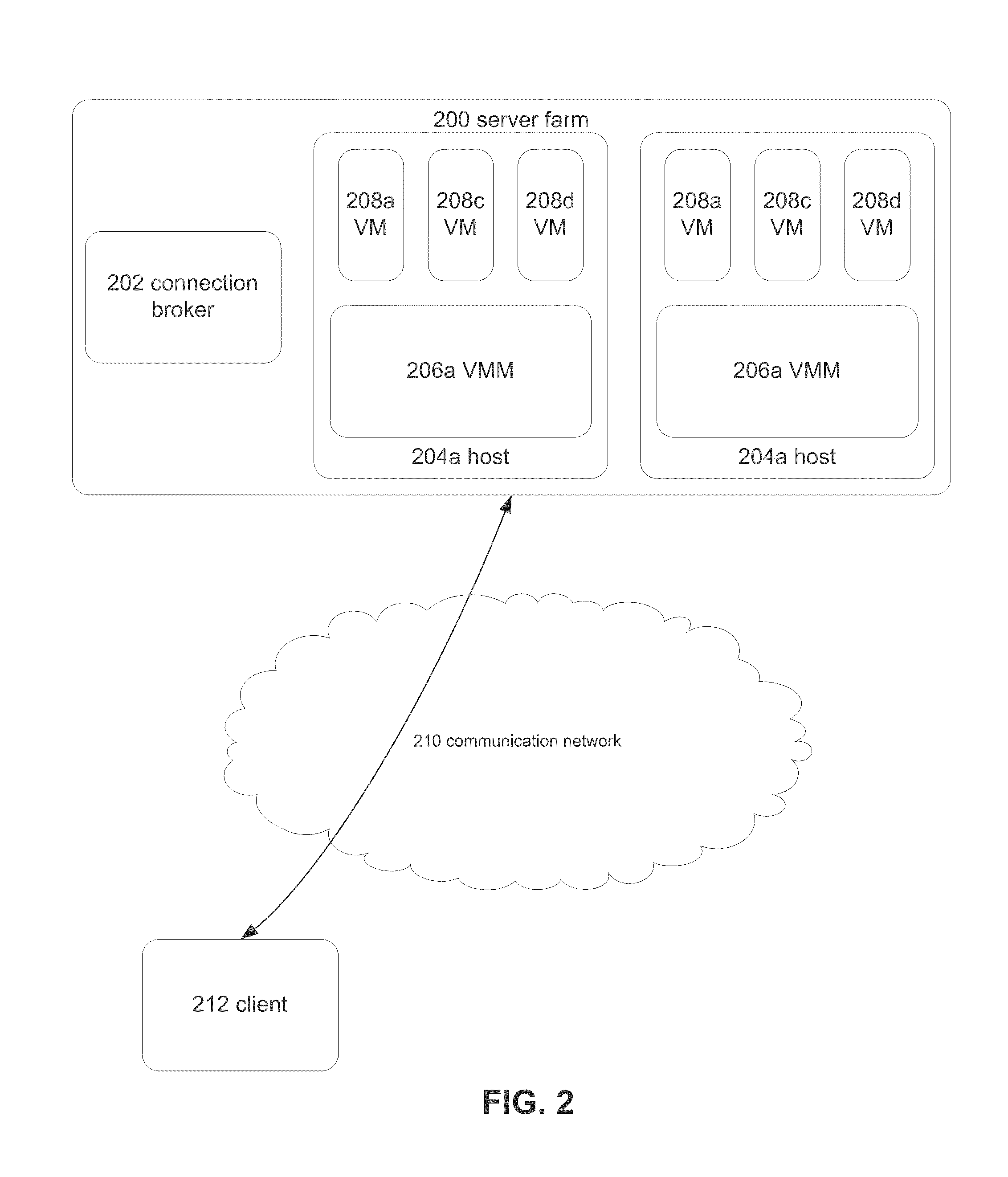
Systems, methods, and computer-readable storage media are disclosed for virtualized eco-friendly remote presentation session roles. In an embodiment, a connection broker monitors the servers of a server farm, and, based upon characteristics of remote presentation sessions served by VMs executing on those servers, directs VMs on those servers to be migrated between servers, changed from sleeping to running or vice versa, or other operations that may improve the performance of the server farm as a whole.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for providing a conditional single sign on
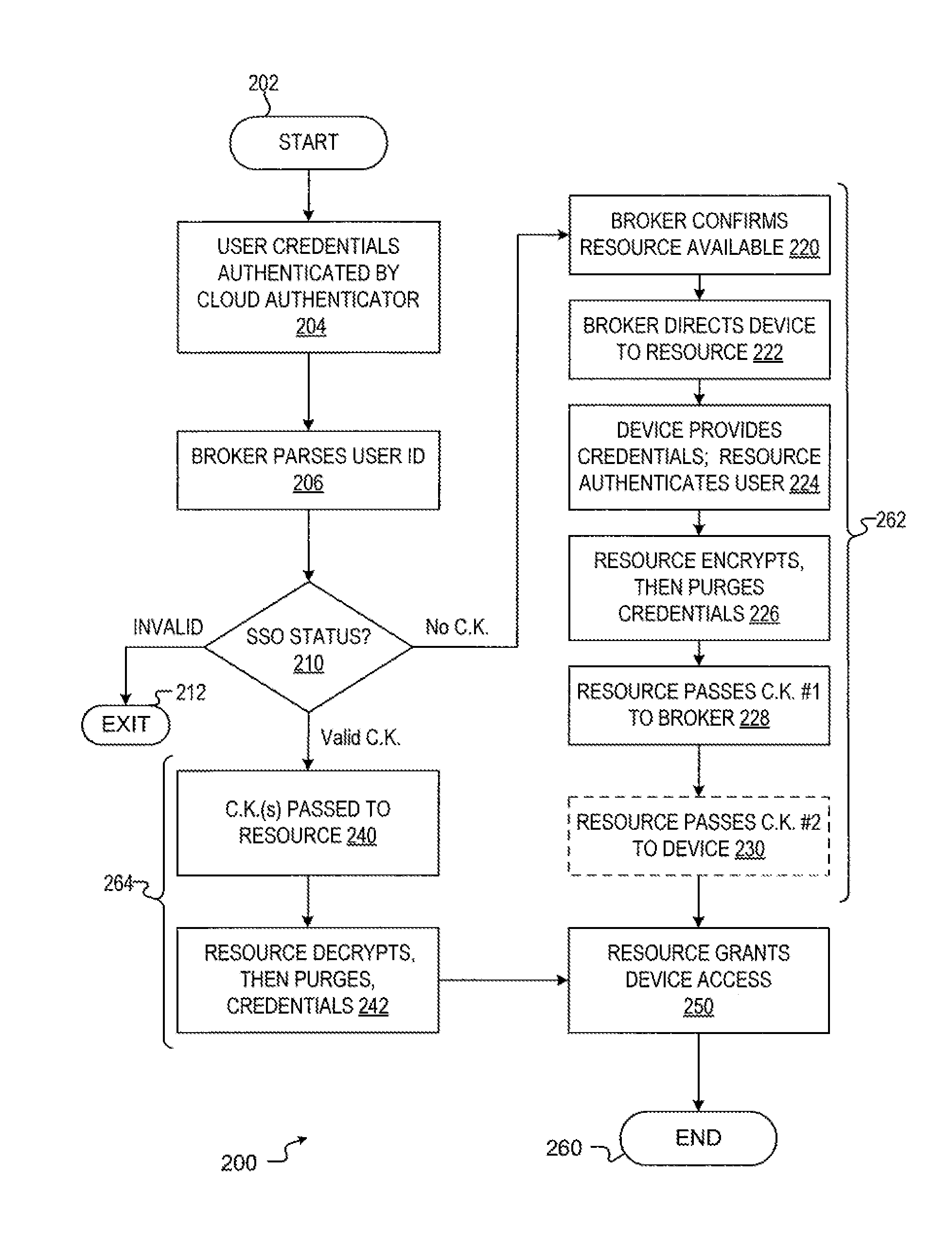
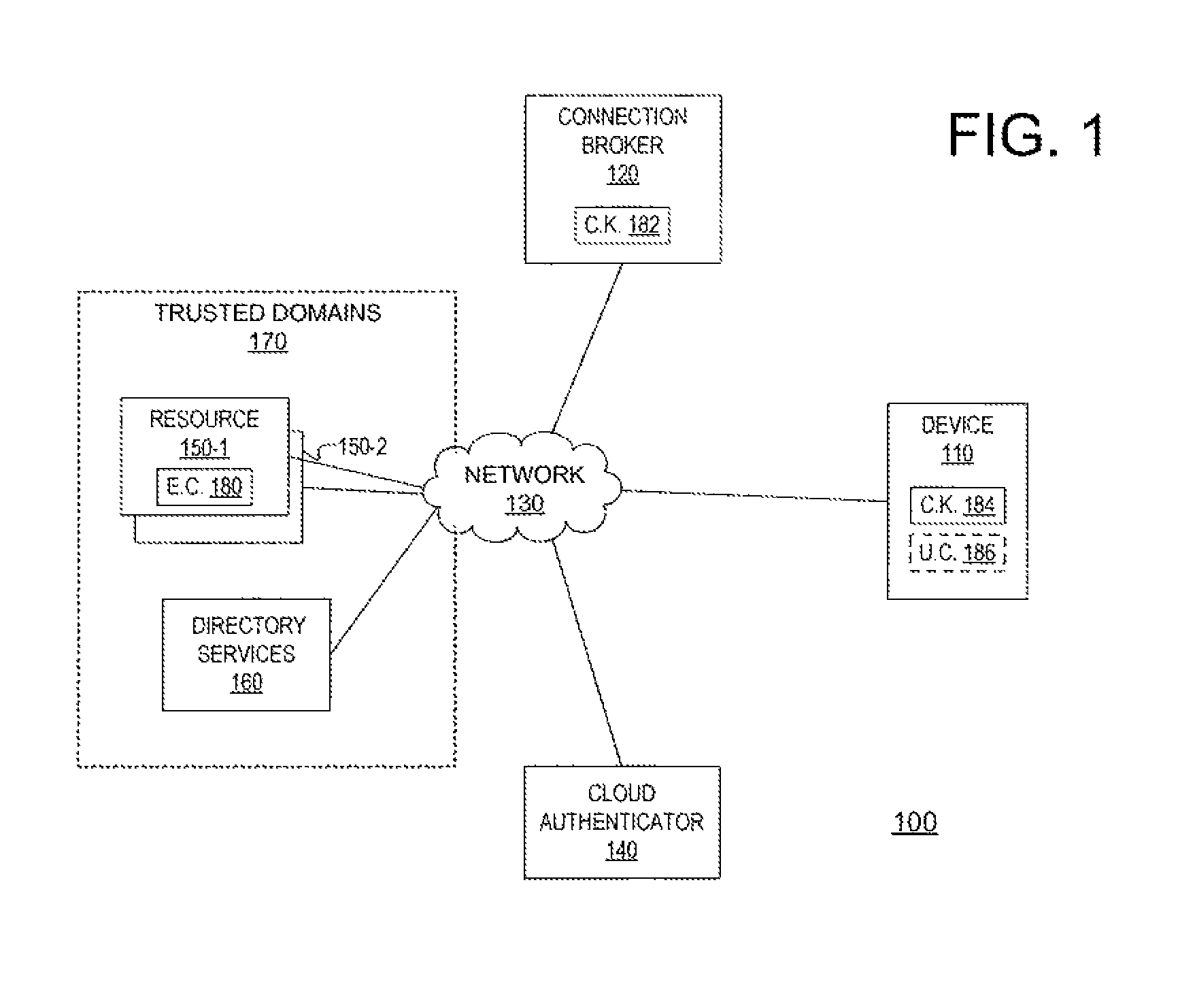
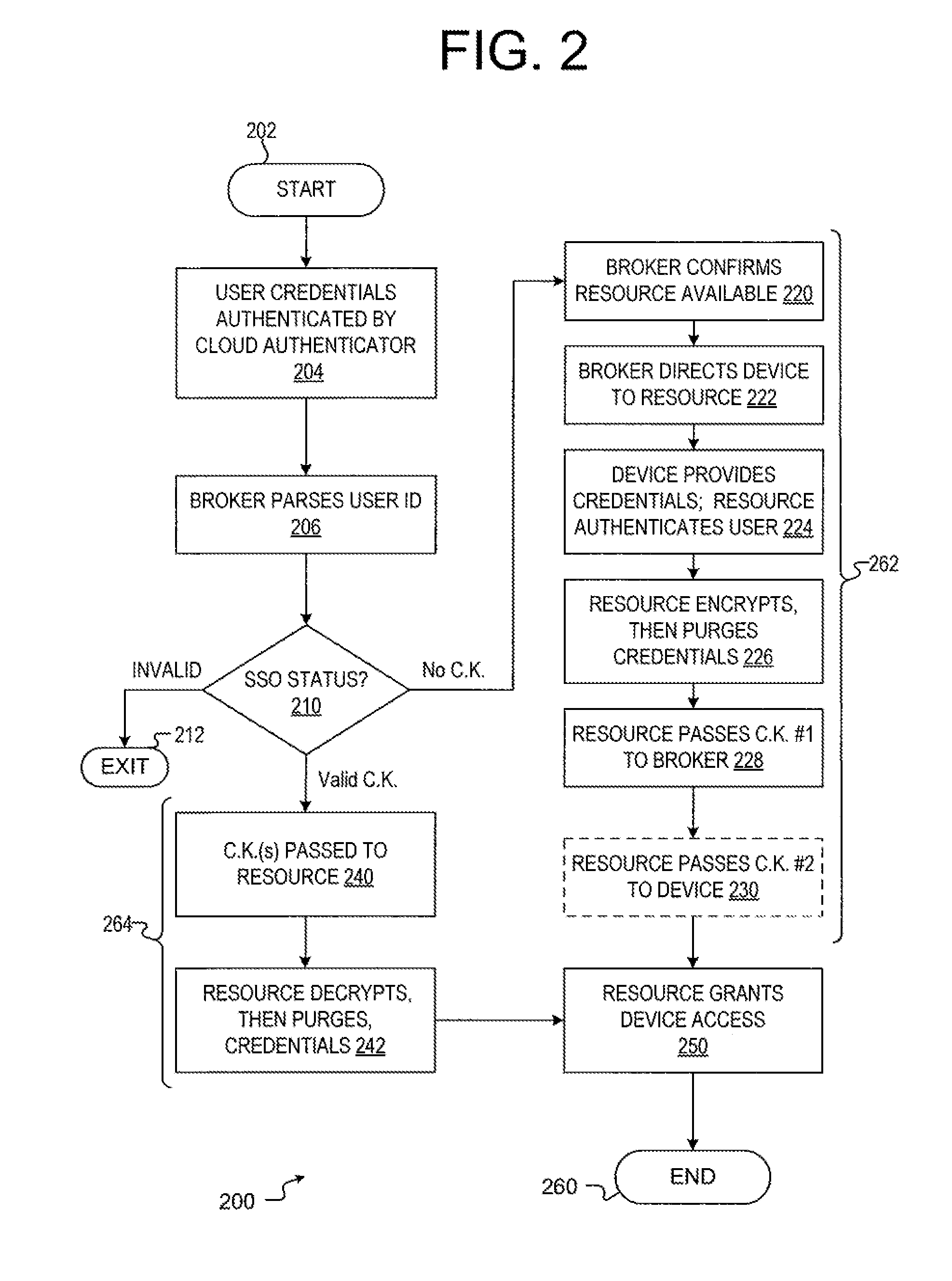
ActiveUS9461820B1Key distribution for secure communicationMultiple keys/algorithms usageComputer resourcesSingle point
A method and apparatus for accessing a computer resource, wherein, during a first access sequence, the computer resource receives credentials of a user from a device the user is using to access the computer resource, encrypts the credentials using at least a first credentials key stores the encrypted credentials, communicates the first credentials key to a connection broker or to the device, and purges the first credentials key. The computer resource, during a subsequent access sequence, receives the first credentials key, decrypts the encrypted credentials using the first credentials key, and purges the first credentials key. The computer resource authenticates the user using the credentials and purges the credentials after the user is authenticated and enables the device to access the computer resource following the authentication of the user.
Owner:TERADICI CORP
Multi-thread network crawler processing method based on connection proxy optimal management
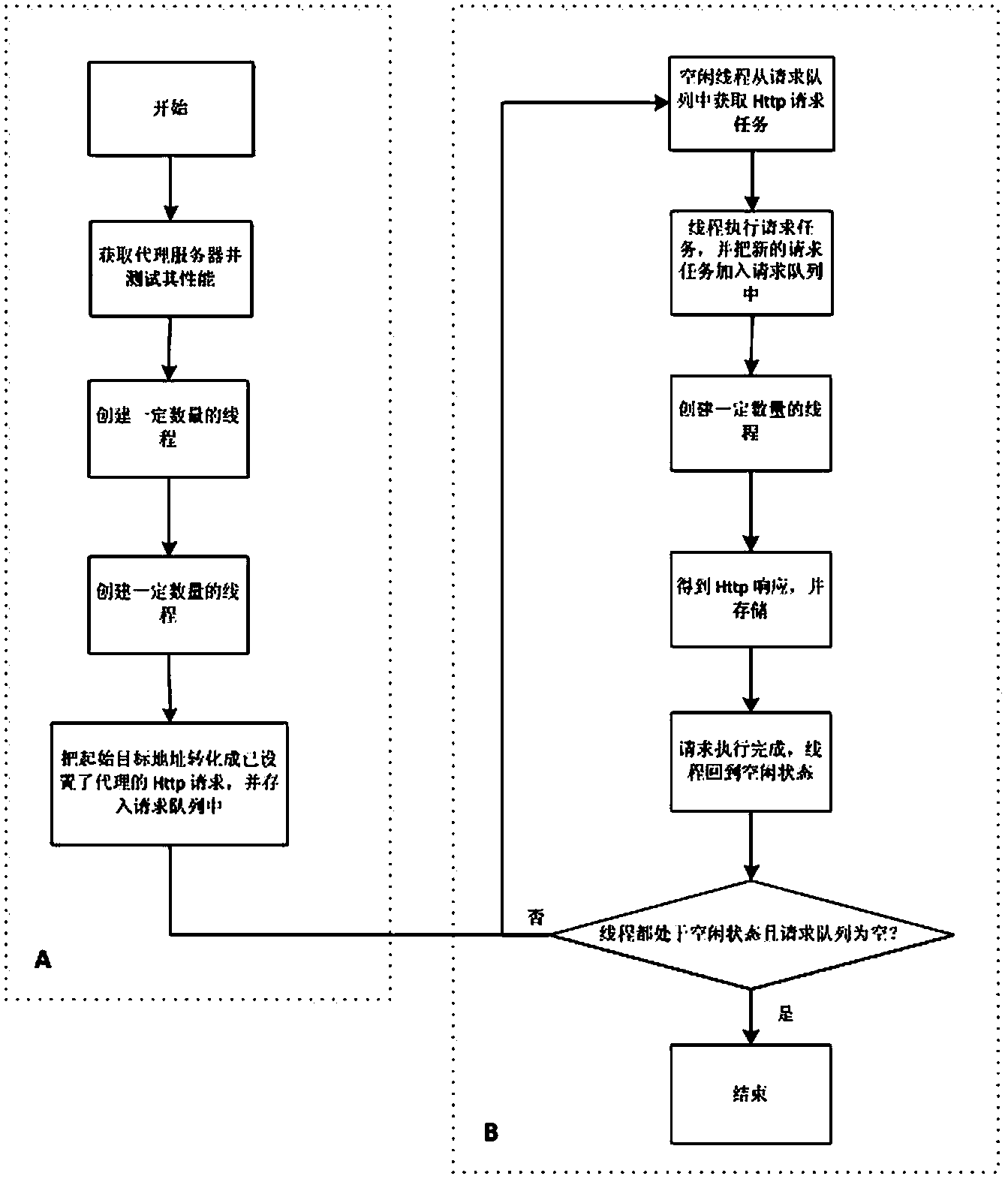
InactiveCN103902386ABalanced usageAffect normal useResource allocationTransmissionEngineeringServer-side
The invention belongs to the technical field of information processing, and particularly relates to a multi-thread network crawler processing method based on connection proxy optimal management. The multi-thread network crawler processing method comprises the steps of firstly, obtaining a public proxy server on a network, testing the network connection performance of the proxy server, obtaining the optimal number of threads according to the performance of the proxy server, then managing a proxy server pool, setting a valid proxy server for each Http request, and finally executing an access request for a Web page. The multi-thread network crawler processing method has the advantages that the number of the threads is obtained through calculation, resources can be effectively utilized to the maximum extent, resource waste cannot be caused, the number of use of each usable proxy server is balanced, and the phenomenon that frequent access is detected by a server terminal is effectively avoided.
Owner:FUDAN UNIV
Resource sharing system and method thereof
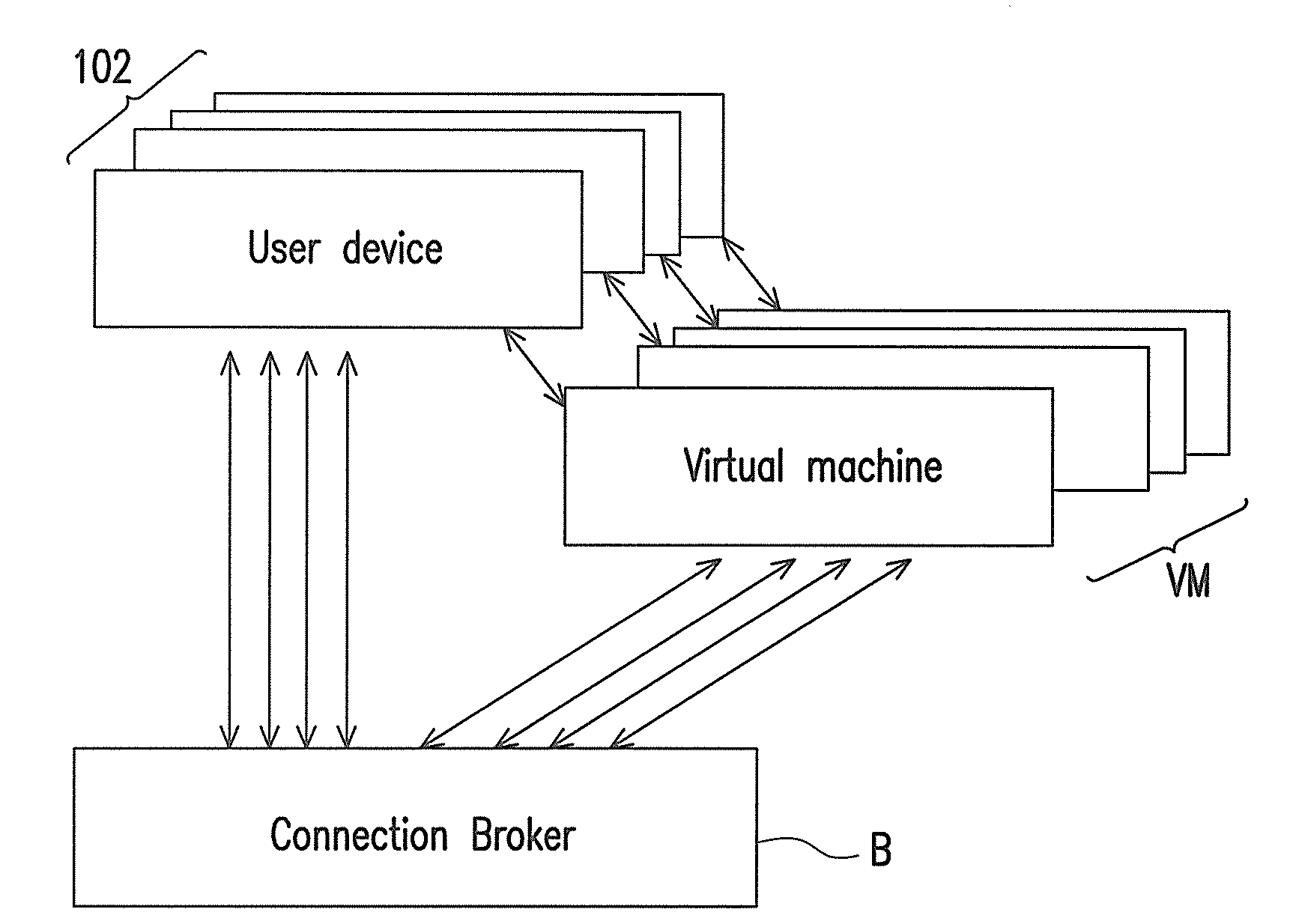
ActiveUS20120110576A1Easy to operateImprove ease of useResource allocationTransmissionUser deviceResources of a Resource
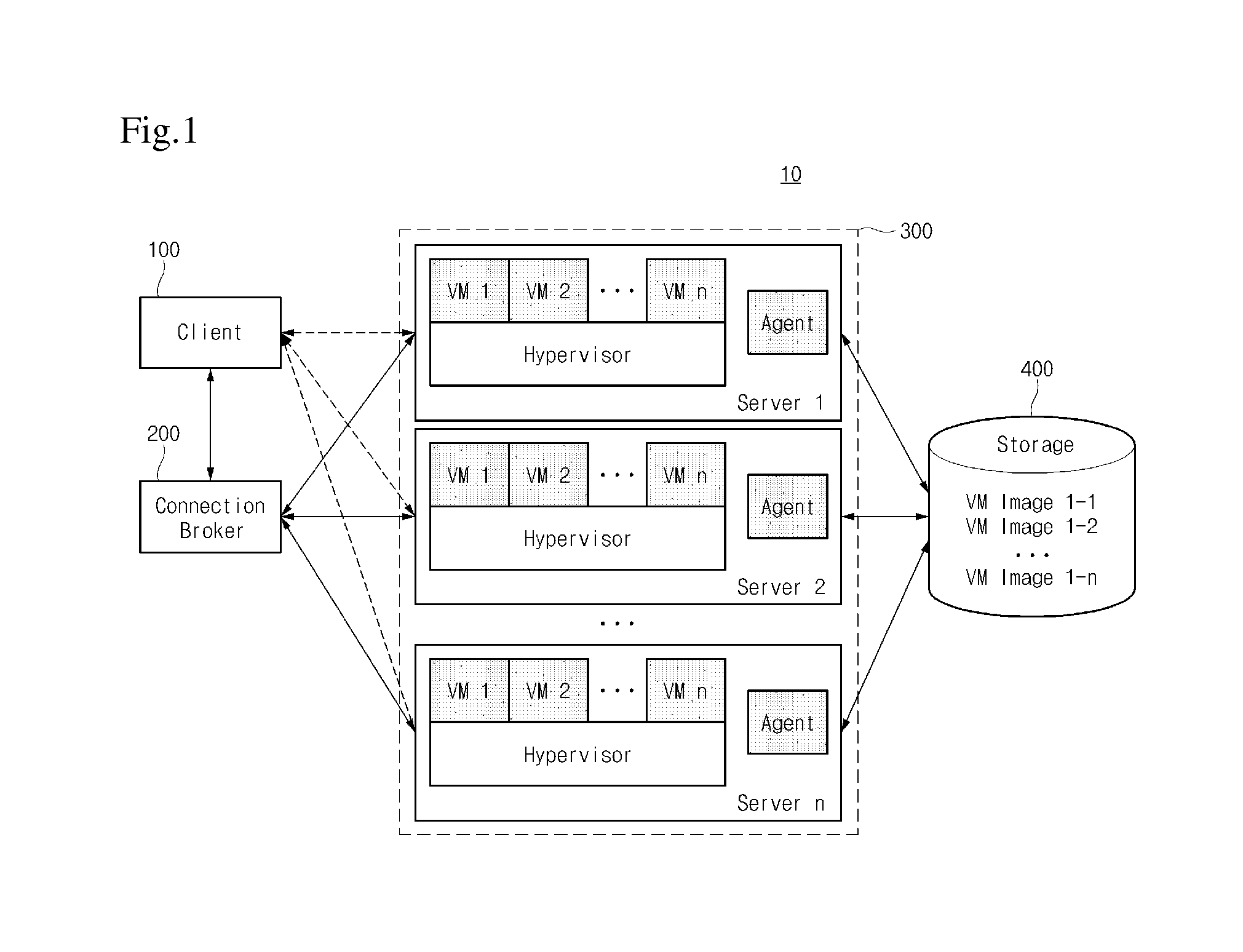
A resource sharing system for a plurality of user devices accessing at least one resource at the same time is provided. The system comprises a plurality of virtual machines and a connection broker. The virtual machines are established on at least one computer, wherein each user device corresponds to at least one of the virtual machines and each of the at least one resource corresponds to one of the virtual machines. The connection broker connects to the virtual machines and receives login information from each of the virtual machines and joins the virtual machines sending the login information into a group. Through the connection broker, the user devices share and access the resources corresponding to the virtual machines in the group.
Owner:INSTITUTE FOR INFORMATION INDUSTRY
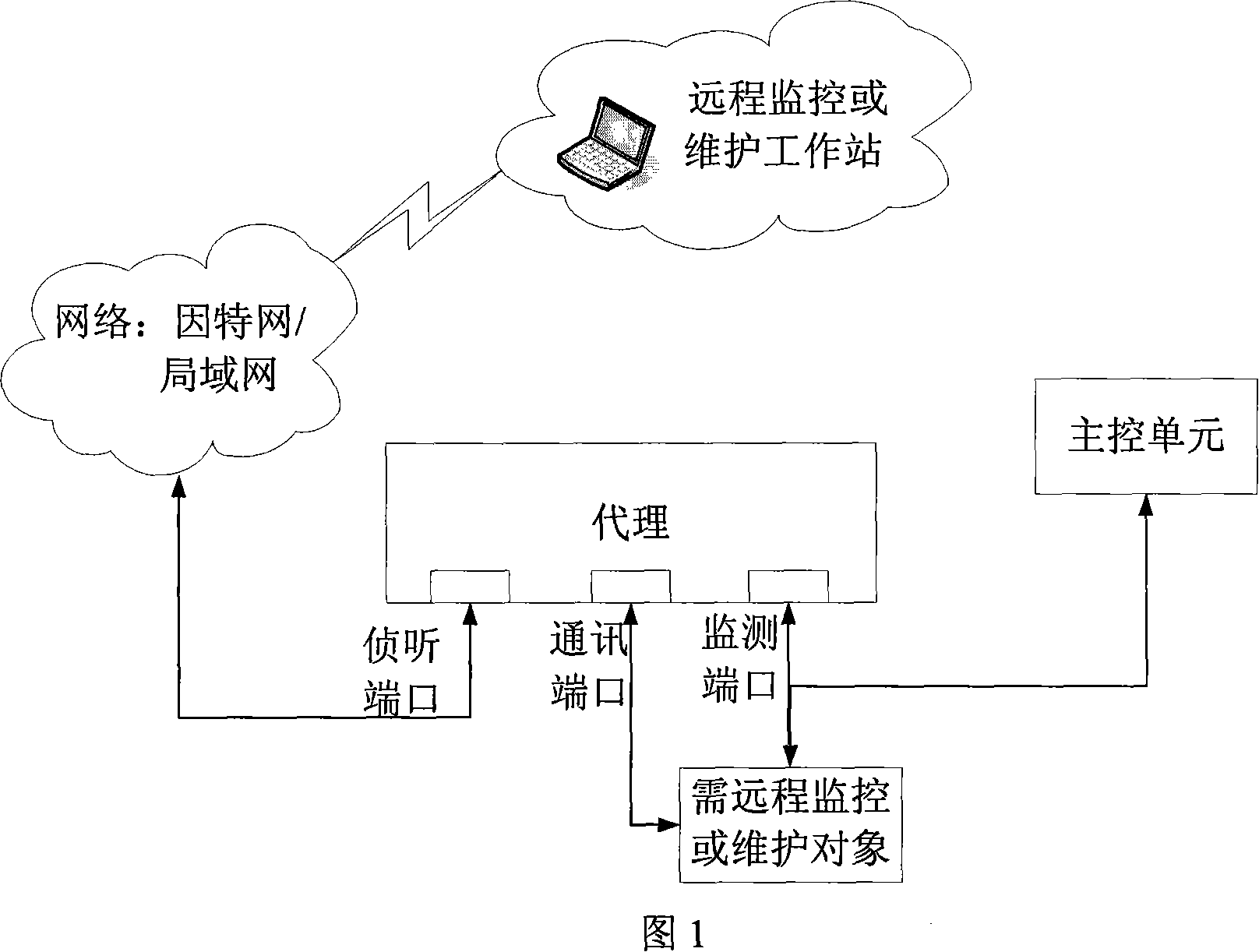
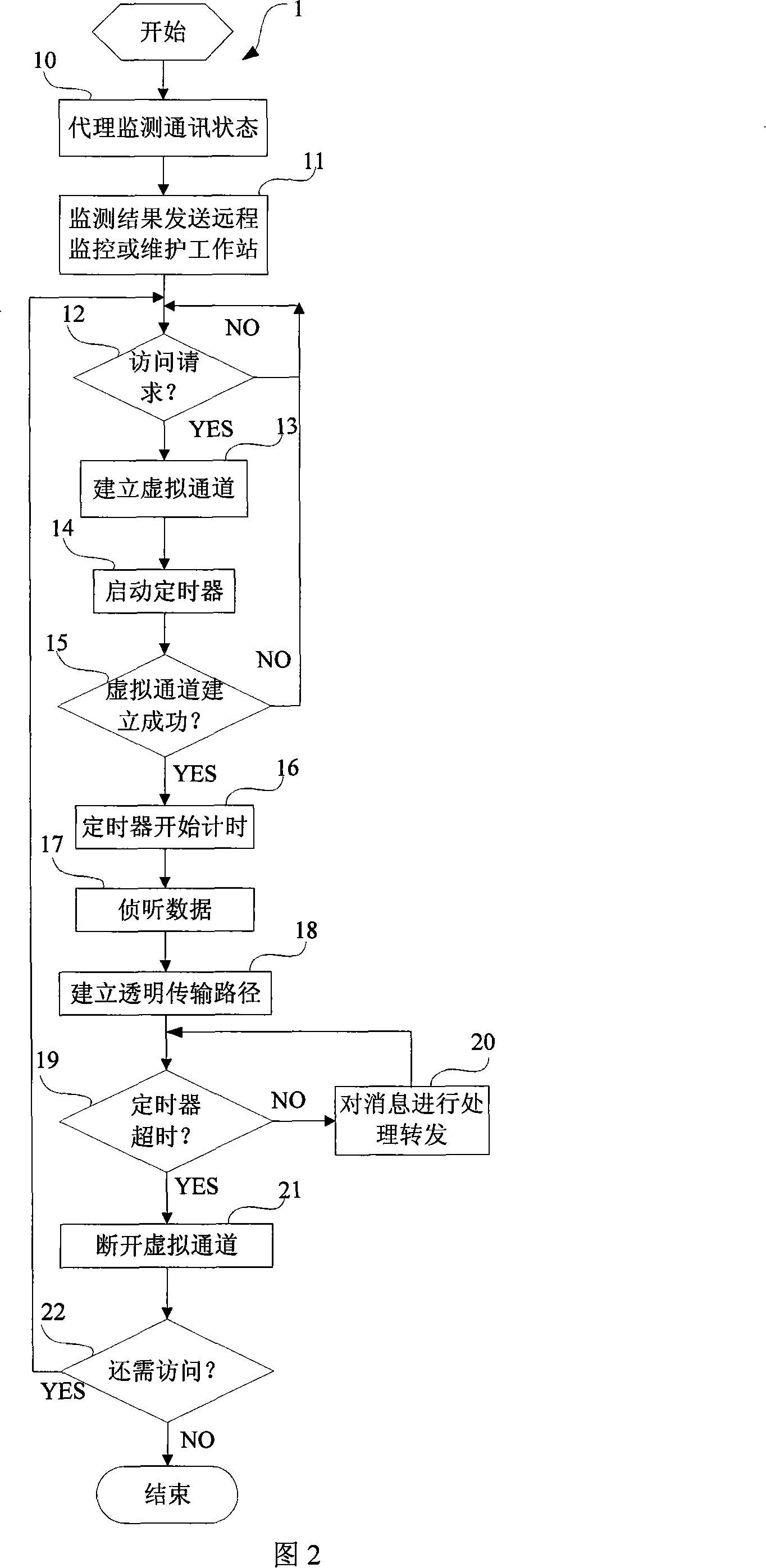
A remote monitoring or maintenance method and device
This invention relates to a method for remote monitor or maintenance and a device for realizing it, in which, a remote monitor or maintenance working station is connected with an agent connected with an object needing remote monitor or maintenance via network, and the agent first of all monitors the communication state of the object and then transmits the monitor result to the working station to decide if it needs to access the object, after the agent sets up a virtual channel for the connection requirement of the station, it manages the channel safely by setting a timer with fixed time interval and sets up a transparent transmission path between the station and the object.
Owner:ASAT CHINA TECH
Enabling mobile IPv6 communication over a network containing IPv4 components using ISATAP
InactiveUS20050008032A1Reducing packet lossTime-division multiplexData switching by path configurationComputer networkTelecommunications
A mobile IPv6 dual-stack node engages in IPv6 communication while roaming within an IPv4-only network, for example using ISATAP. First, the node determines that it has moved and obtains a new IPv4 address. After determining that the visited network contains no IPv6-enabled components, the node uses in IPv6 connect agent to engage in IPv6 communication. The node configures its care-of address using the IPv6 connect agent's routing information and the node's newly-obtained IPv4 address. In one embodiment, the node and the connect agent optimize the handoff when the node has moved but still uses the same connect agent. The node sends a binding update to the connect agent comprising the node's old care-of address and the node's new care-of address. When the connect agent receives a packet destined for the node's previous care-of address, it forwards the packet to the node's current care-of address, thereby reducing packet loss.
Owner:KDDI CORP
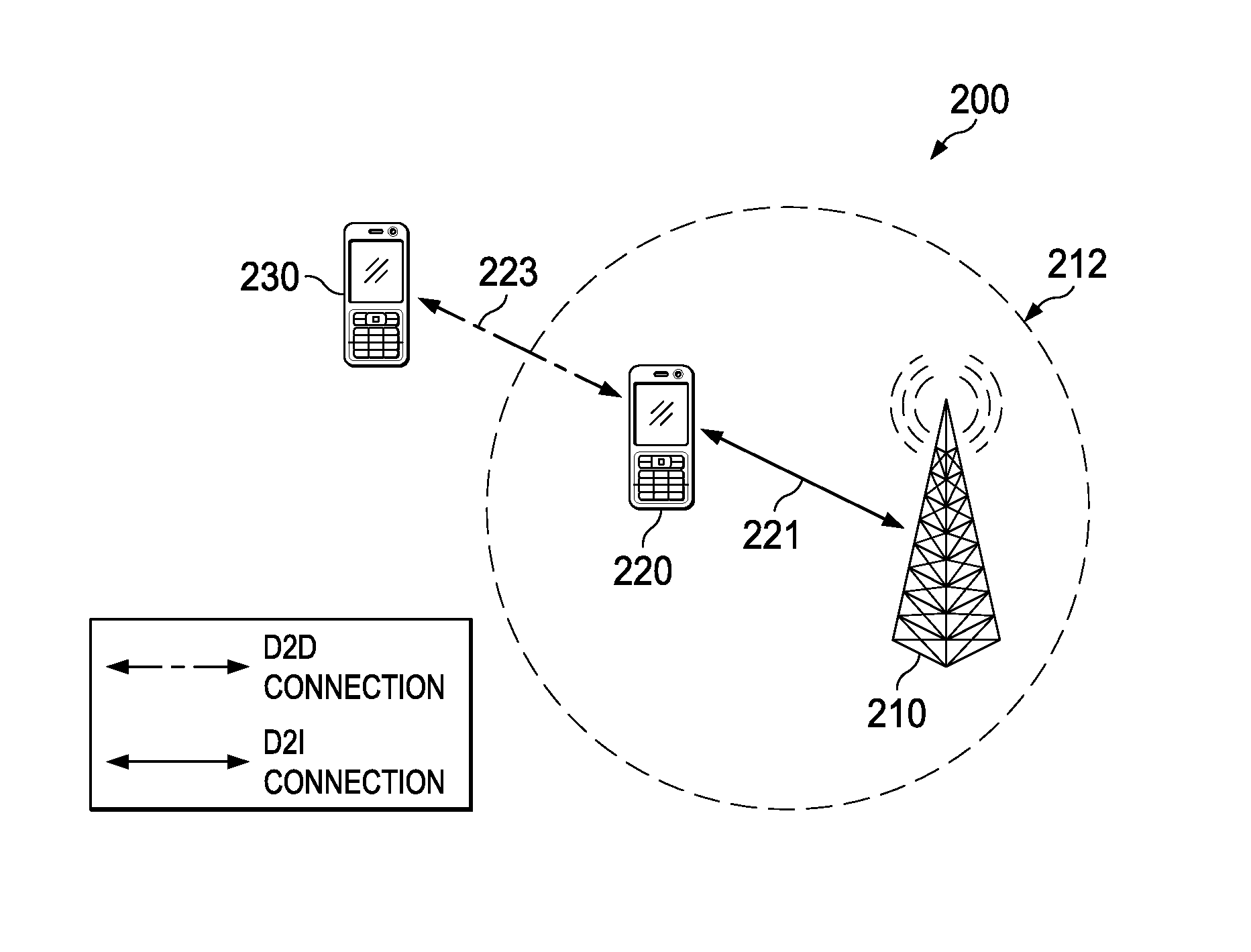
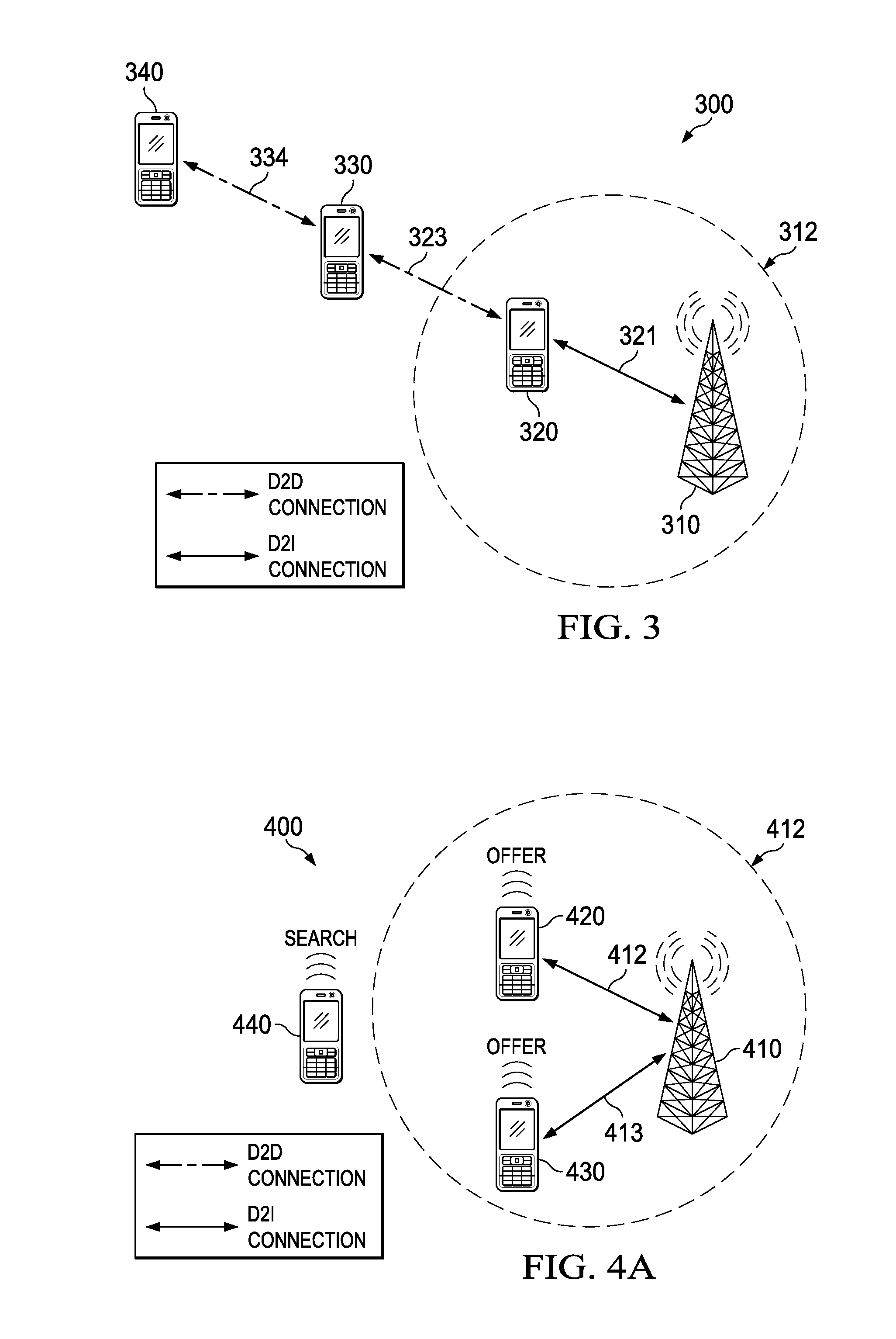
Contention-based Integration of Device to Device (D2D) Networks with Wireless Infrastructure
ActiveUS20150056987A1Facilitate indirect connectionIncrease contactConnection managementWireless commuication servicesDevice to deviceConnection broker
Efficient D2D link integration can be achieved by allowing mobile devices to independently initiate D2D / connection-proxy discovery without re-broadcasting beacons originating from the wireless access point. A mobile station wanting to establish a D2D link may broadcast a search message to neighboring mobile stations, which may return offer messages specifying a connection quality and / or parameters of the candidate indirect connection. The requesting mobile station may then select one of the responding neighboring mobile stations through which to establish the indirect connection. Responding mobile stations may delay offer message transmission by a period that is proportional to a connection quality to reduce offer message redundancy.
Owner:HUAWEI TECH CO LTD
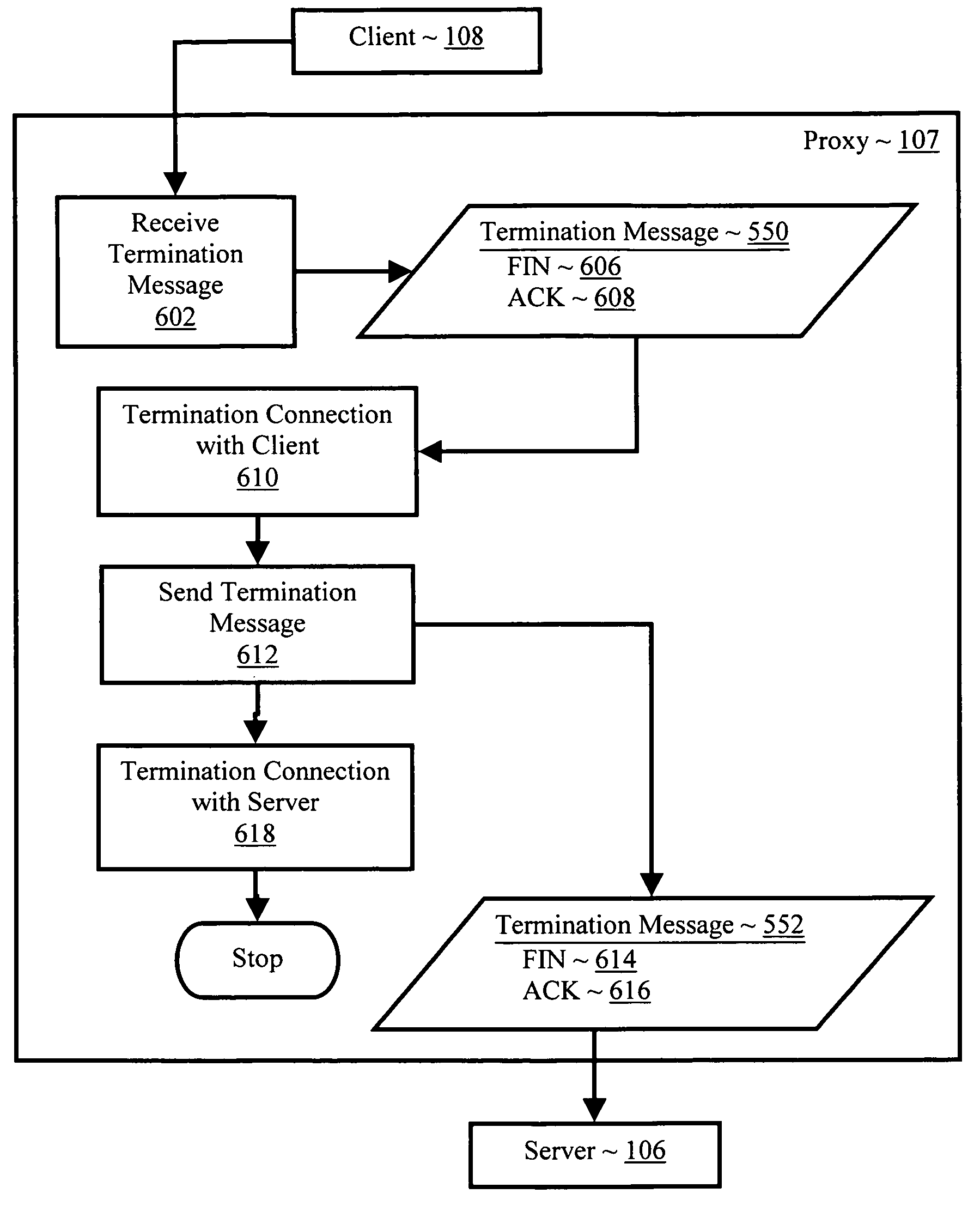
Data communications through a split connection proxy
InactiveUS20060031571A1Digital computer detailsTransmissionNetwork Communication ProtocolsClient-side
Data communications through a split connection proxy in a data communications protocol, including receiving in a proxy from a client, asynchronously with respect to any other messages between the client and the proxy, one or more client messages including client message data items including a connection request for a connection between the client and the proxy, destination connection data identifying a destination server, and a message from the client to the destination server; and sending from the proxy to the server, asynchronously with respect to any messages between the client and the proxy and asynchronously with respect to any other messages between the proxy and the server, one or more proxy messages including proxy message data items including a connection request for a connection between the proxy and the destination server and the message from the client to the destination server.
Owner:IBM CORP
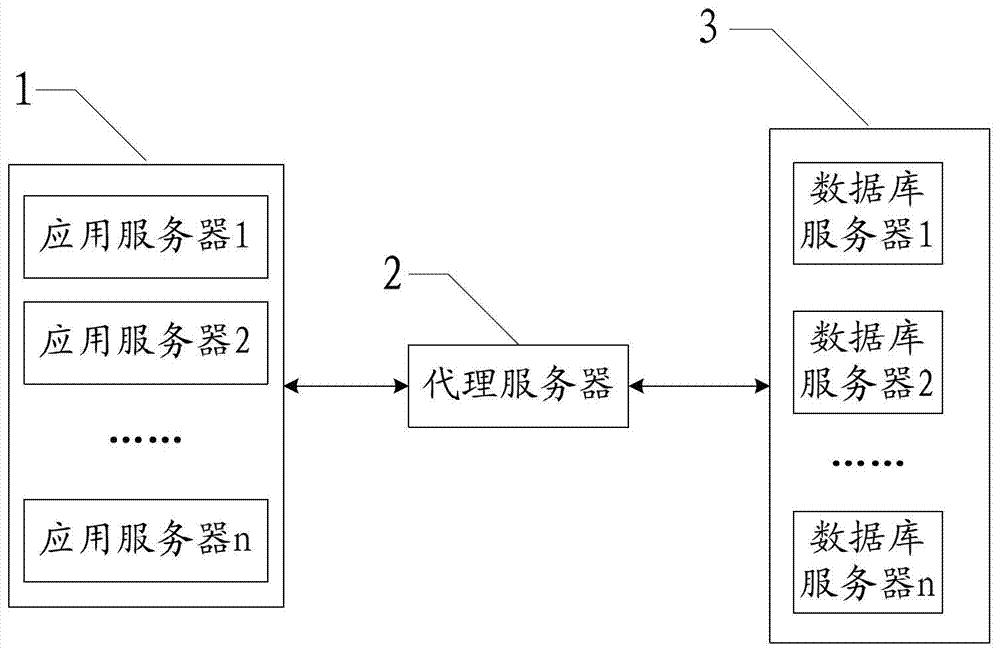
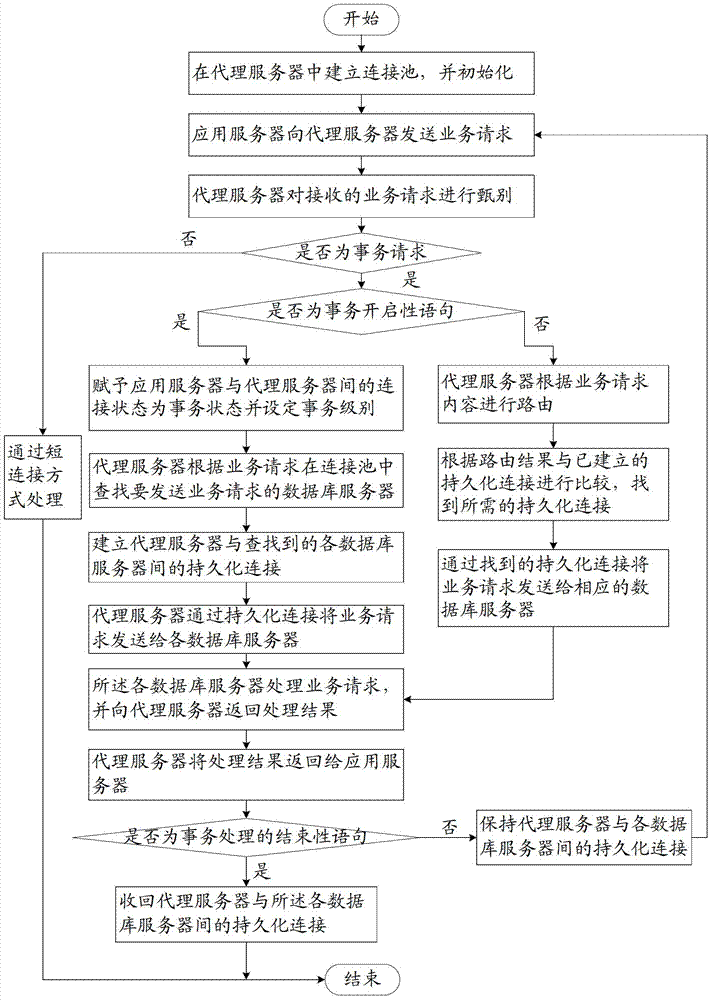
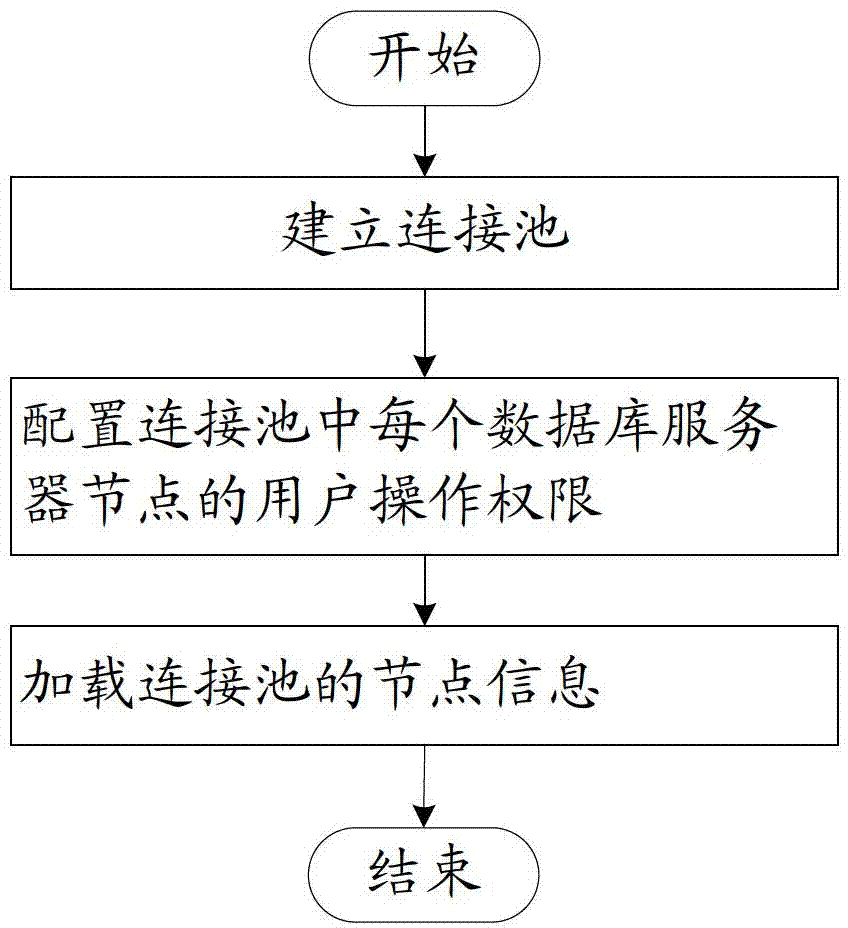
Distributed transaction processing method based on connection pool management
InactiveCN103500180AImprove securityEnsure consistencyTransmissionSpecial data processing applicationsApplication serverDatabase server
The invention relates to a distributed transaction processing method based on connection pool management. The distributed transaction processing method based on connection pool management comprises the steps that a connection pool is established on a proxy server; when the proxy server receives a first service request, sent by an application server, for transaction processing, persistent connection is established between the proxy server and a relevant database server, the service request is sent by the proxy server to each database server to be processed through the persistent connection, and all following service requests belonging to the transaction processing are sent to each database server to be processed through the established persistent connection; when the service request sent by the application server is the request for ending of the transaction processing or is not a transaction request, the proxy server withdraws the persistent connection established between the application server and each database server. By the adoption of the distributed transaction processing method based on connection pool management, the consistency and the integrity of transaction processing data are guaranteed, the isolation level of transactions is guaranteed, the promotion function on a high-concurrency data service is achieved, and the data consistency of high-concurrency access is guaranteed.
Owner:北京思特奇信息技术股份有限公司
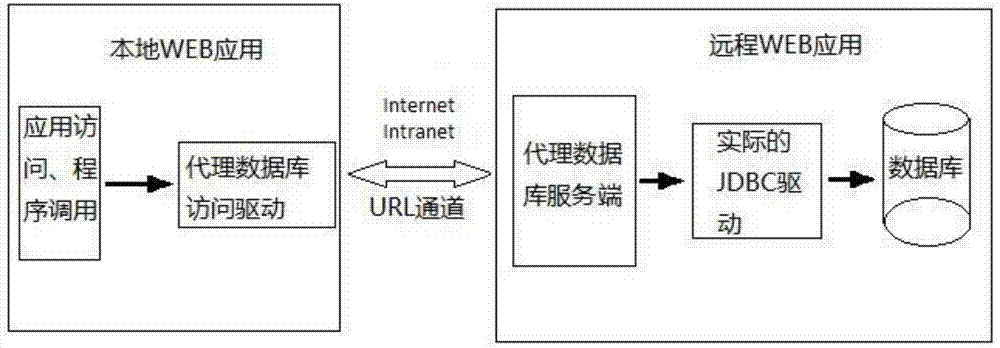
Access drive and data access method of proxy database
InactiveCN103488765AEasy accessEasy to integrateSpecial data processing applicationsWeb serviceInformation access
The invention belongs to the technical field of software development, and particular discloses an access drive and a data access method of a proxy database. The data access method includes that a web application with a proxy component is deployed in a web service which can be directly connected with a database service, wherein the web application includes an actual JDBC (java database connectivity) database drive capable of accessing a connected database; safety authorization information accessed by the proxy database is configured in a configuration file corresponding to the web application, and a server side accessed by the proxy database is formed after releasing; only parameters of a corresponding proxy database access drive need to be configured in a local web application to access an actual database data through connection to the server side accessed by the proxy database in case of incapability of directly connecting to the actual database, all database operations such as adding, deleting and correcting can be performed, and complete proxy of an actual database JDBC drive can be realized. The access drive can access data safely and rapidly in a B / S (browser / server) mode, and convenience is brought to completion of cross-service data integration and remote debugging and maintaining.
Owner:雷虹
Apparatus and method for in-memory-based virtual desktop service
ActiveUS20160378535A1Efficiently provideEfficiently providedExecution for user interfacesSoftware simulation/interpretation/emulationResource poolComputer terminal
Disclosed herein are an apparatus and method for in-memory-based virtual desktop service. The apparatus for in-memory-based virtual desktop service includes a connection broker for performing a task for coordinating a delivery protocol that is used between at least one user terminal that uses virtual desktop service and multiple servers that provide the virtual desktop service, a resource pool for providing software resources including an Operating System (OS) for the virtual desktop service; and virtual machine infrastructure for supporting hardware resources, and dynamically allocating software stored in the software resources to the hardware resources.
Owner:ELECTRONICS & TELECOMM RES INST
Access proxy platform
An access proxy system is disclosed. A proxy server receives, from a client device, a request to access a protected resource. The protected resource represents a mapping between a user-facing domain and an internal domain that is only accessible from behind a set of one or more proxies that includes the proxy server. In response to receiving a grant of permission by an access policy engine, the proxy server proxies access to the protected resource using a mutual-TLS connection with the client device.
Owner:BARRACUDA NETWORKS
Apparatus and method for virtual desktop service
ActiveUS20140366093A1Efficiently provideEfficiently providedDigital data processing detailsMultiple digital computer combinationsResource poolSpecific time
Disclosed herein are a method and architecture capable of efficiently providing virtual desktop service. A service architecture for virtual desktop service according to the present invention includes a connection broker configured to perform authentication, manage virtual machines, and perform a server monitoring and protocol coordination function, a resource pool configured to manage software resources that are delivered to a specific virtual machine in a streaming form on a specific time in order to provide on-demand virtual desktop service and are executed on the specific virtual machine and to provide provision information about the managed software resources in response to a request from the connection broker, and a virtual machine infrastructure configured to support hardware resources, generate virtual machines in which the software of a user terminal is executed, and provide the generated virtual machine as virtual desktops.
Owner:ELECTRONICS & TELECOMM RES INST
Data Communications Through A Split Connection Proxy
InactiveUS20080177829A1Multiple digital computer combinationsTransmissionNetwork Communication ProtocolsClient-side
Data communications through a split connection proxy in a data communications protocol, including receiving in a proxy from a client, asynchronously with respect to any other messages between the client and the proxy, one or more client messages including client message data items including a connection request for a connection between the client and the proxy, destination connection data identifying a destination server, and a message from the client to the destination server; and sending from the proxy to the server, asynchronously with respect to any messages between the client and the proxy and asynchronously with respect to any other messages between the proxy and the server, one or more proxy messages including proxy message data items including a connection request for a connection between the proxy and the destination server and the message from the client to the destination server.
Owner:INT BUSINESS MASCH CORP
Method and system for dynamic remote injection of in-process agents into virtual machine based applications
A method and system for dynamic and adaptive deployment of in-process agents to virtual machine based applications which may run on remote hosts is provided. A bootstrap agent is injected into the application, using standardized interfaces provided by virtual machine based systems like SUN MICROSYSTEMS' JAVA system or MICROSOFT's .NET system. The bootstrap agent establishes a network connection to a management server which provides binaries representing in-process agents in bytecode or native code format. The bootstrap agent sends data identifying its runtime environment to the management server, which determines the matching in-process agent binaries for the runtime environment of the connected agent and sends the selected binaries to the bootstrap agent. The bootstrap agent receives the binaries and installs them to its hosting virtual machine, according to their format (bytecode or native code).
Owner:DYNATRACE
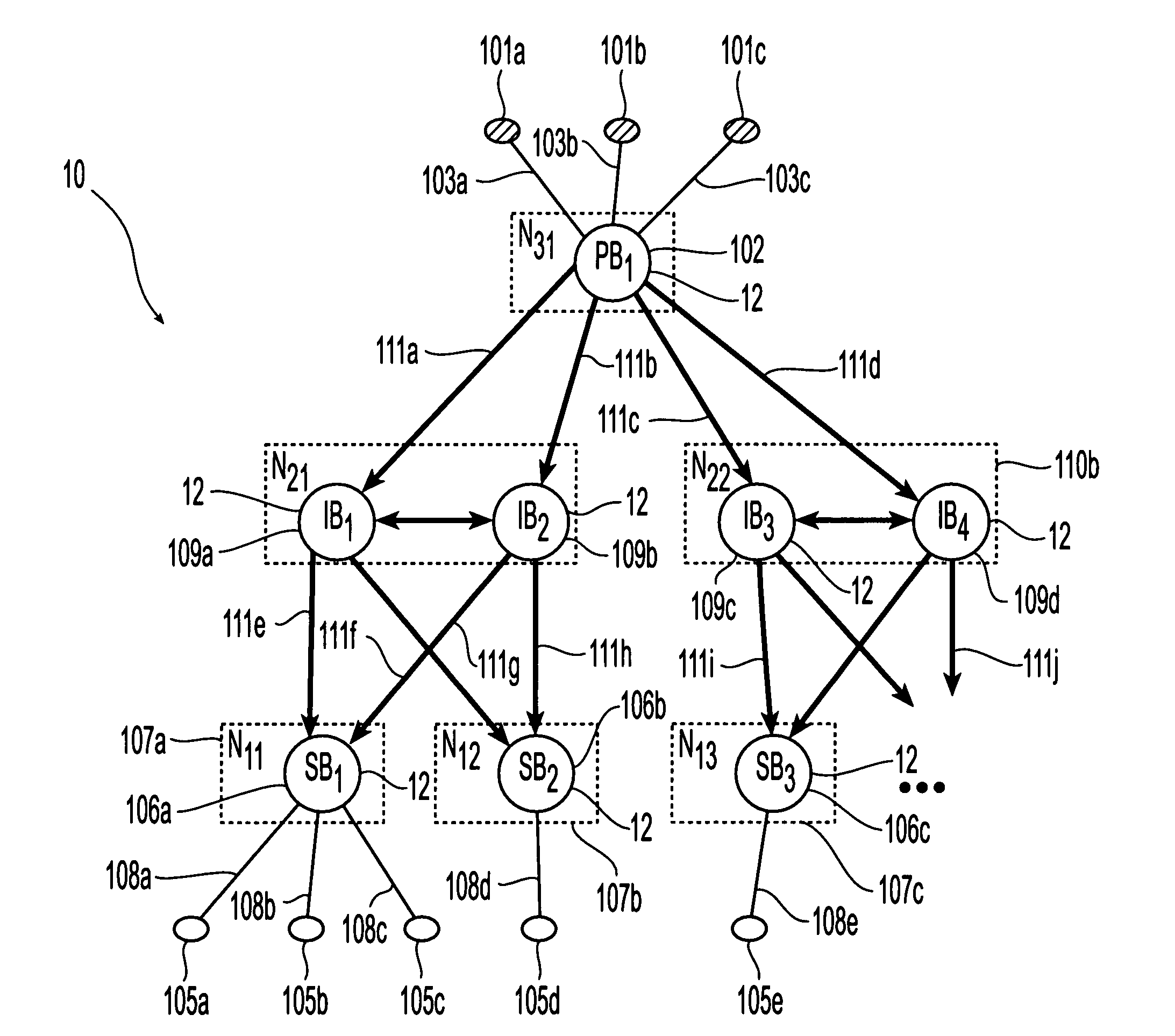
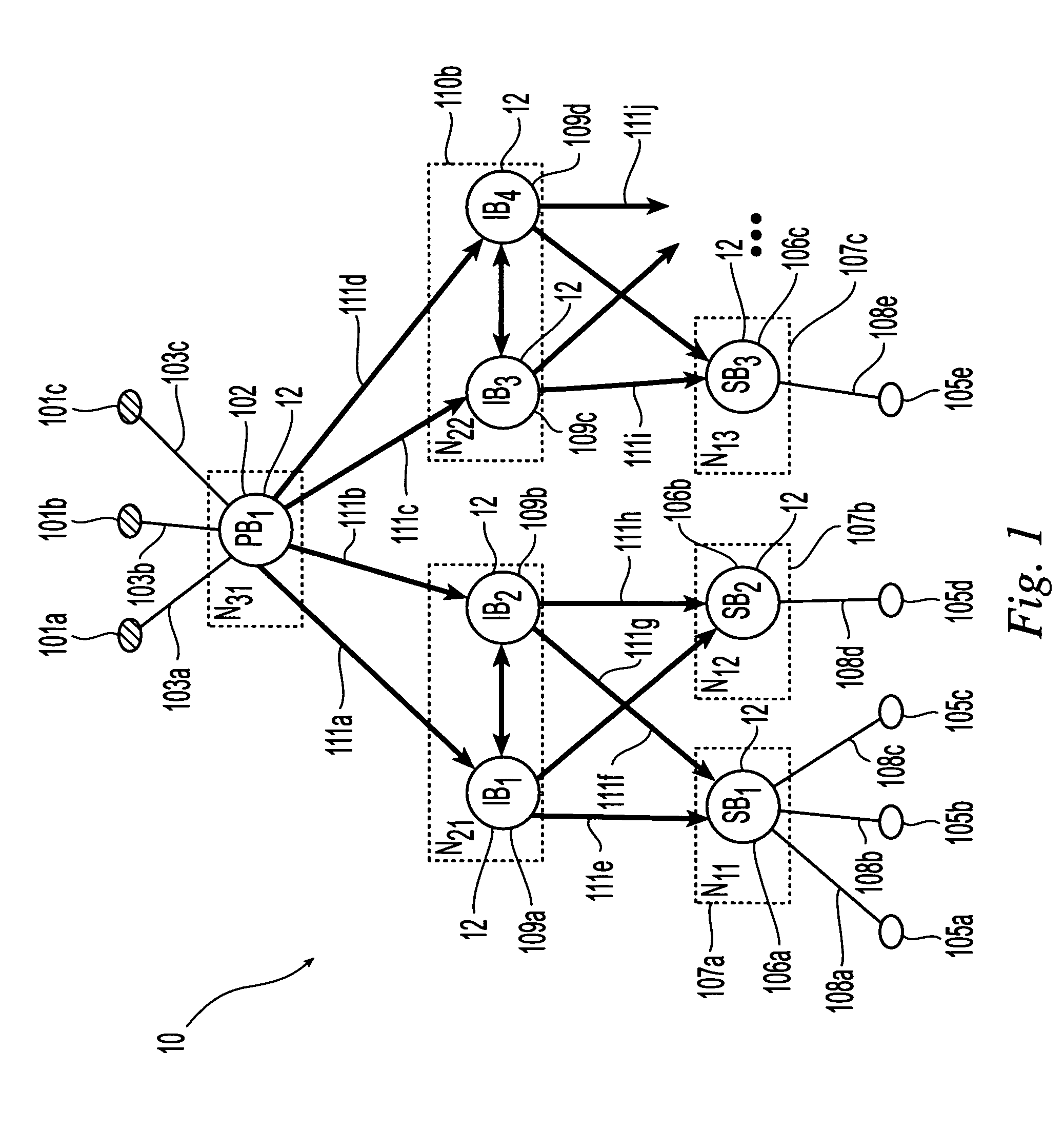
Subscription propagation in a high performance highly available content-based publish/subscribe system
ActiveUS7822801B2Improve performanceEliminate needMultiple digital computer combinationsOffice automationStart timeHigh availability
The present invention is directed to a publish / subscribe system containing a plurality of brokers, a plurality of subscribers and plurality of brokers including publisher connecting brokers, intermediate brokers and subscriber connecting brokers. Subscriptions are introduced into the system by the subscribers through associated subscription brokers. New subscriptions are aggregated, assigned a virtual start time and propagated through the system toward the publishers. Each broker maintains subscription information in the form of a directed acyclic graph and a broker vector. Messages are published through the system by the publishers through their associated publisher connecting brokers. Each message is assigned a message vector associating subscriptions to that message. The published messages are routed through the brokers toward the subscribers in accordance with comparisons of message brokers and vector brokers conducted at each broker.
Owner:DROPBOX
Apparatus and method for virtual desktop service
ActiveUS20160378534A1Efficiently provideEfficiently providedExecution for user interfacesSoftware simulation/interpretation/emulationResource poolOperational system
Disclosed herein are an apparatus and method for virtual desktop service. The apparatus for virtual desktop service includes a connection broker for performing a task for coordinating a delivery protocol that is used between at least one user terminal that uses virtual desktop service and multiple servers that provides the virtual desktop service, a resource pool for providing software resources including an Operating System (OS) for the virtual desktop service, and virtual machine infrastructure for supporting hardware resources.
Owner:ELECTRONICS & TELECOMM RES INST
System for provisioning, allocating, and managing virtual and physical desktop computers in a network computing environment
A system for provisioning, allocating, and managing virtual and physical desktop computers in an enterprise network computing environment allows for these physical and desktop computers to be grouped logically based on personnel, organizational, or networking efficiencies without regard to the hardware or server that will ultimately run the virtual machine terminal once it is accessed. A connection broker connects incoming connections to one desktop in a desktop group, based on information relating to that incoming connection.
Owner:DELL PROD LP
Method and system for providing server virtual machine for real-time virtual desktop service, and server device supporting the same
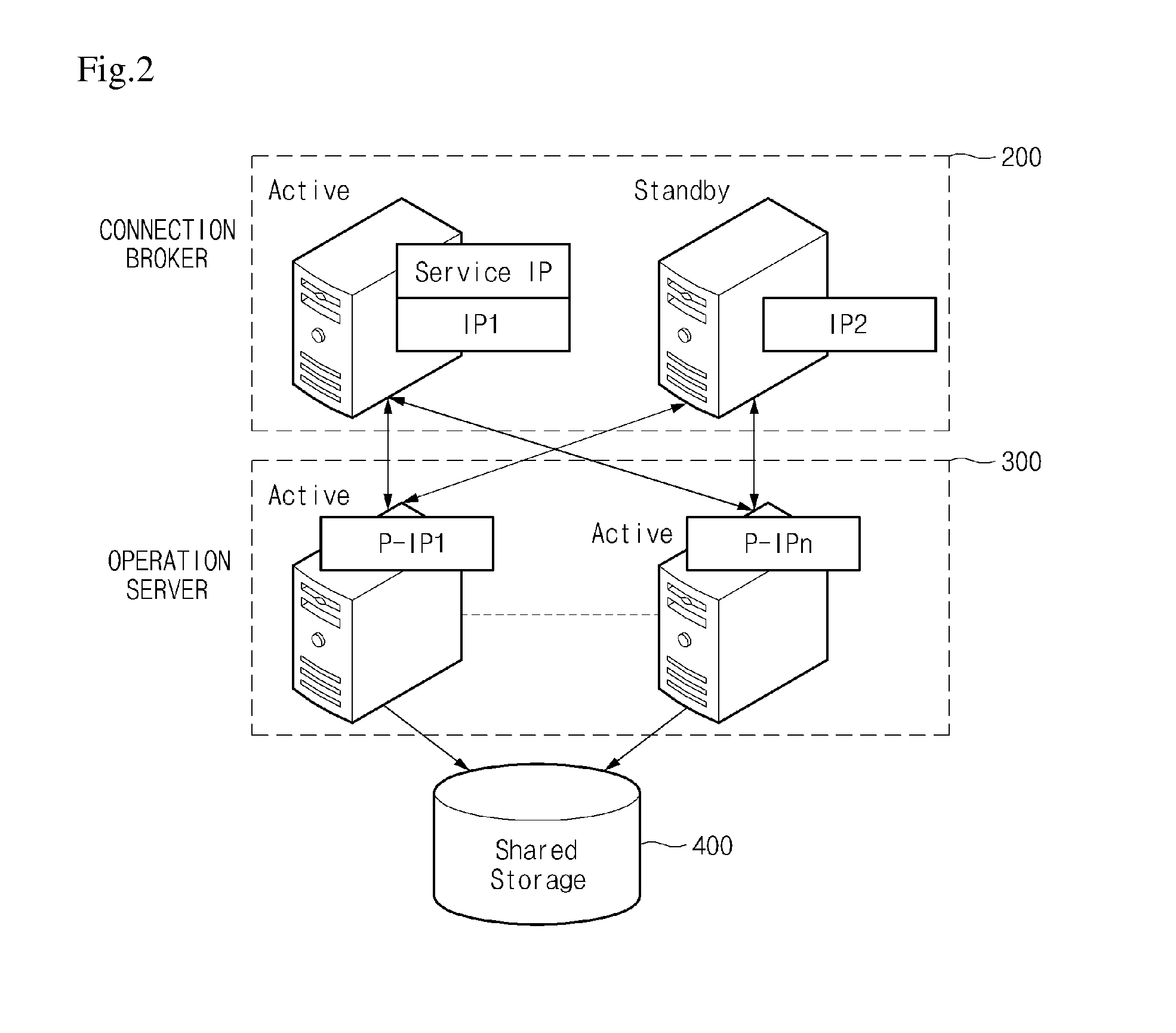
ActiveUS20150201004A1Short-time imagingReduce stepsTransmissionExecution for user interfacesClient-sideServer appliance
Provided is a virtual desktop service, and disclosed is a system for providing a server virtual machine, including: a client configured to receive allocation of a virtual machine for using a virtual desktop service; a connection broker configured to control a type of virtual machine to be allocated to be classified according to user terminal registration information of the client, any one operation server to be selected among a plurality of operation servers, and the virtual machine to be allocated; the plurality of operation servers configured to provide the client with a virtual machine under a control of the connection broker; and a shared storage configured to store data related to the client for providing the virtual machine, and provide the stored data to the operation servers, a method of providing a server virtual machine, and a server device supporting the same.
Owner:ELECTRONICS & TELECOMM RES INST
Apparatus and method for remote processing while securing classified data
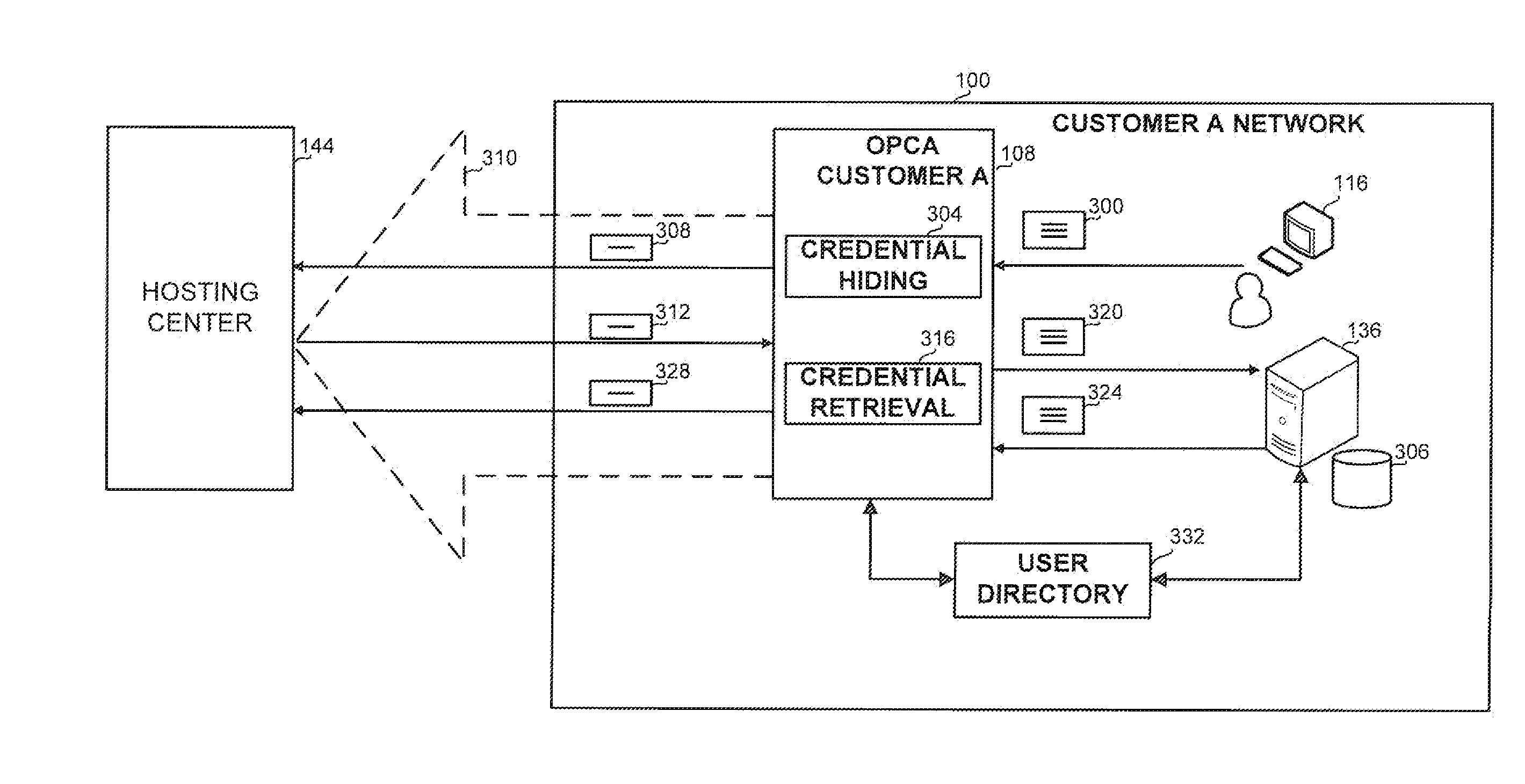
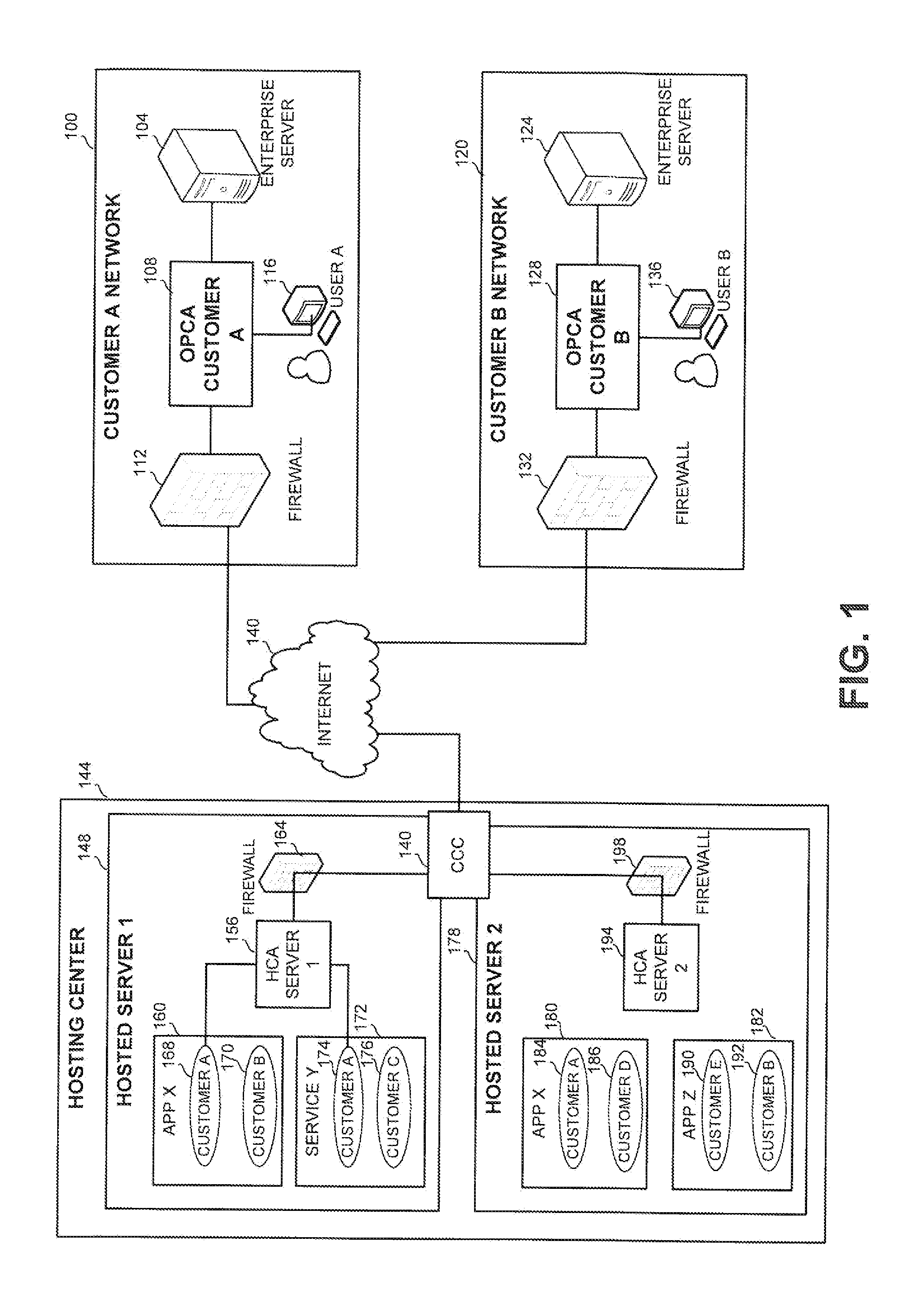
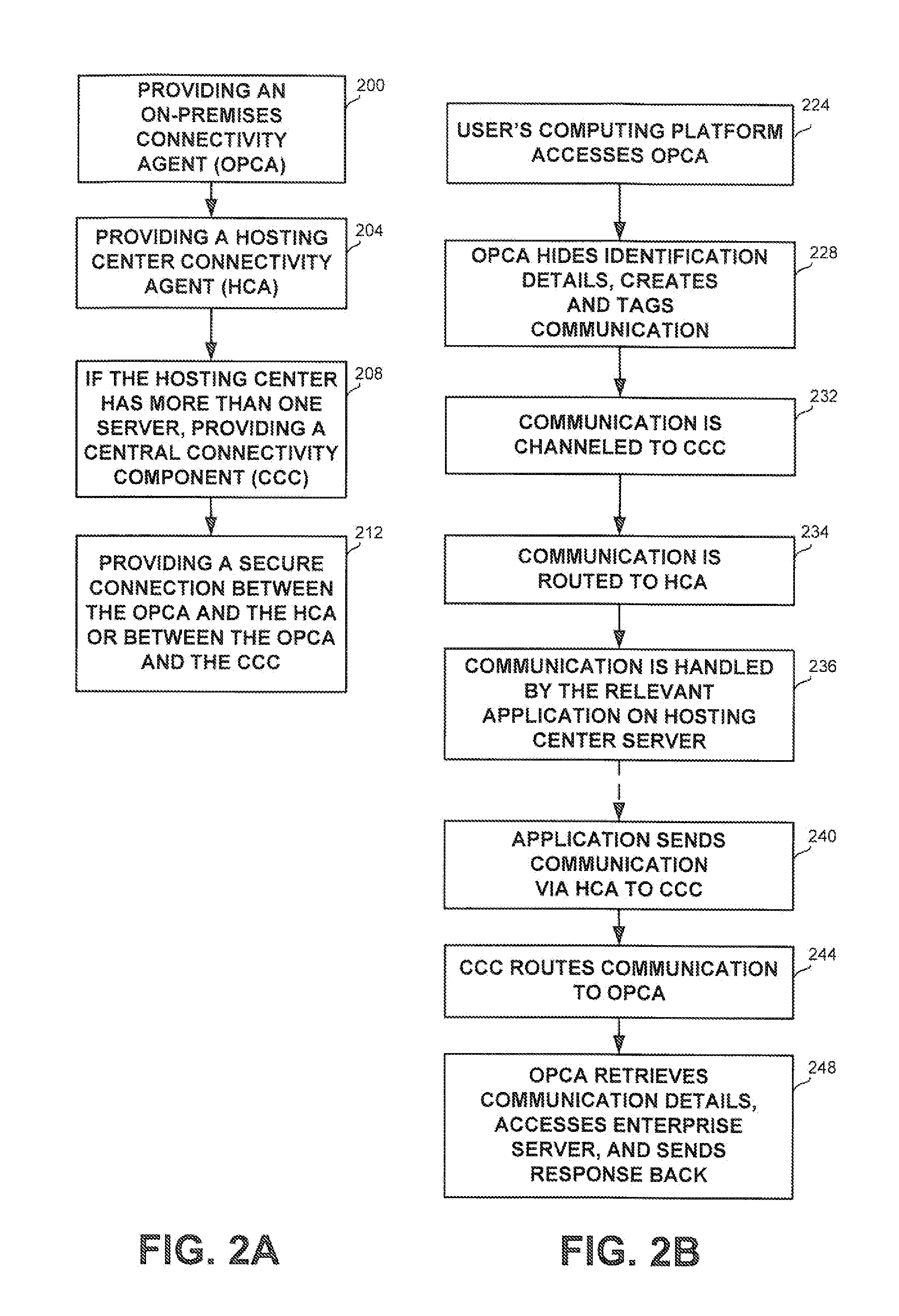
InactiveUS20110162074A1Digital data processing detailsAnalogue secracy/subscription systemsWorld Wide WebOn demand
A method and apparatus for providing an on-demand service to an organization by a hosting center, without having classified data leave the organization network, comprising: receiving a message sent from a first computing platform of the organization to an on-premise connectivity agent, the message comprising classified data; generating a code in accordance with the classified data, by a credential hiding component associated with the on-premise connectivity agent; sending the code to the hosting center; receiving a second message from the hosting center, the second message comprising the code; retrieving the classified data using the code by a credential retrieval component associated with the on-premise connectivity agent; and sending a third message to a second computing platform, the third message comprising the classified data.
Owner:SAP PORTALS ISRAEL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com