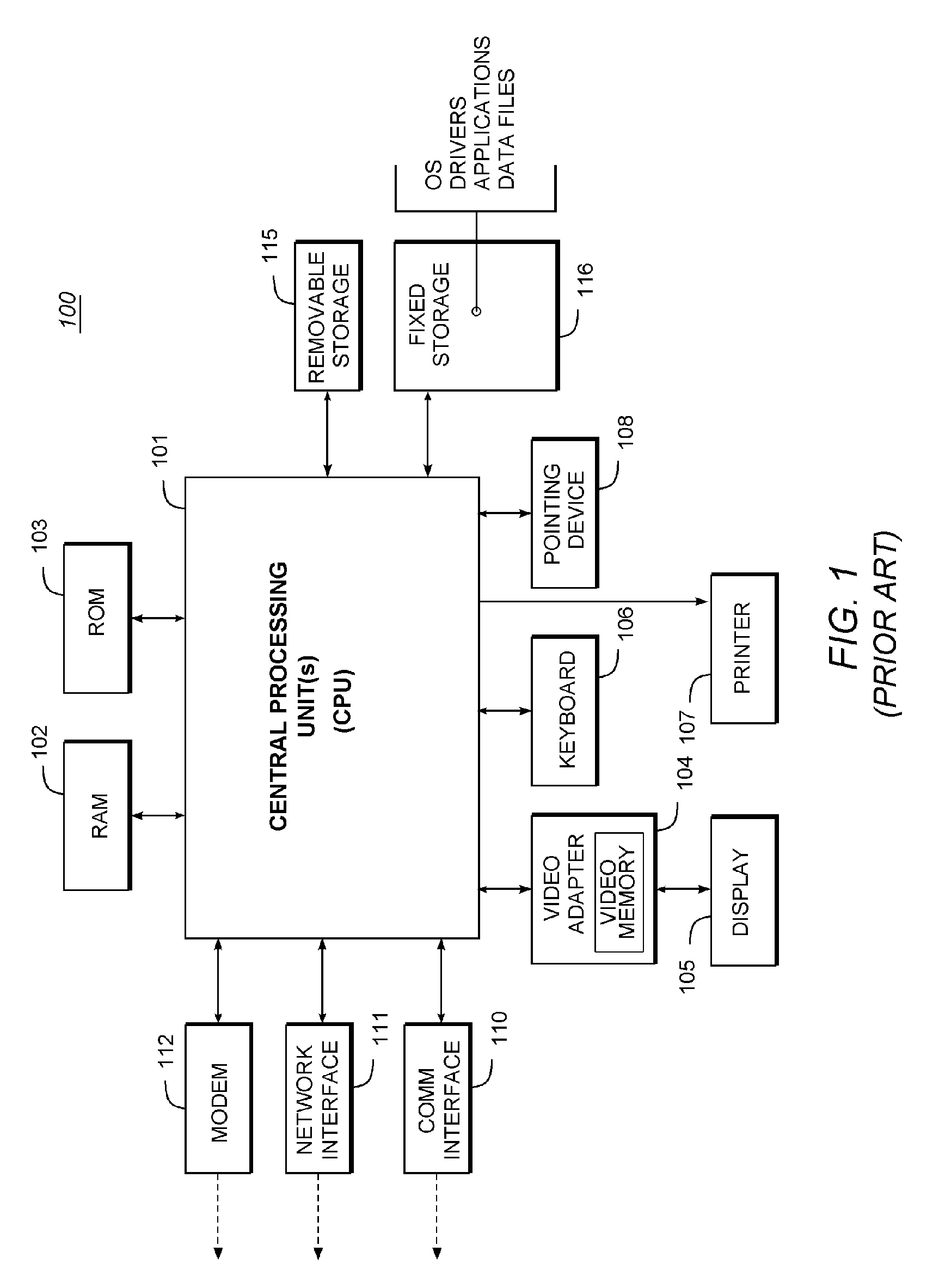
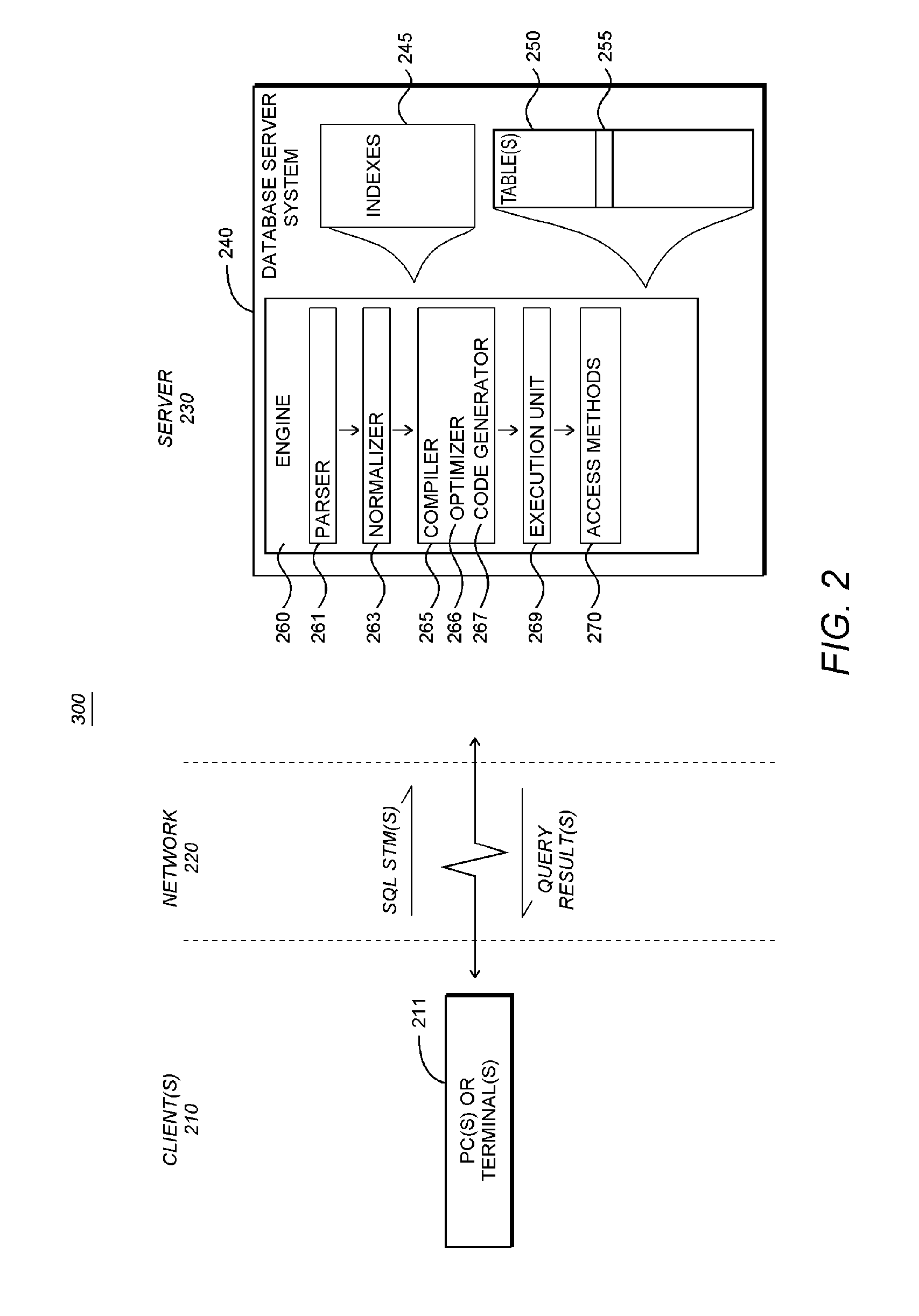
Patents
Literature
128 results about "Database connectivity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
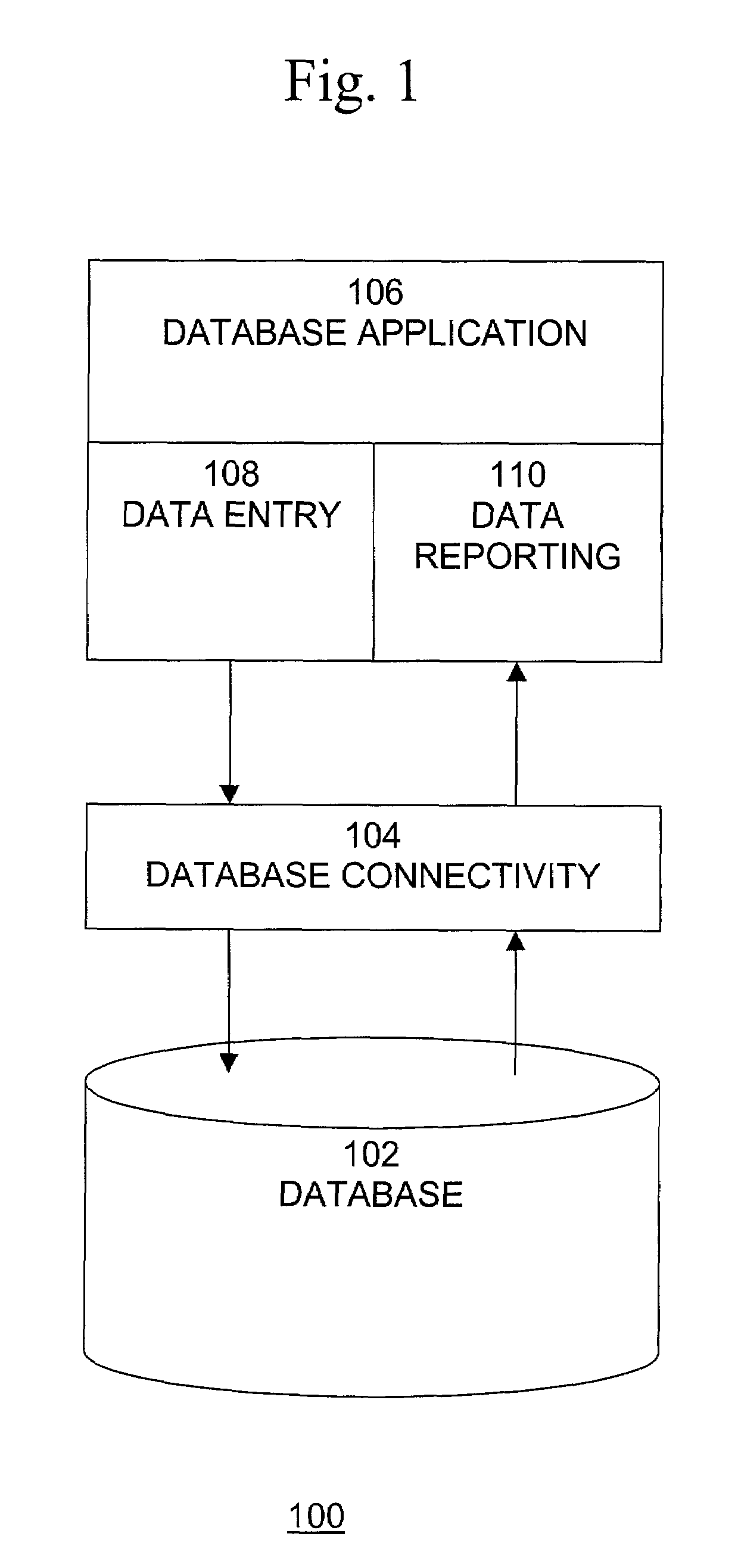
Database Connectivity. Database connectivity means when we have a database which is of some other source even on the same project first we have to create a connection with if so that we perform any CRUD operation in the database so for connecting SQL database with c# window application we use using System.Data.SqlClient; namespace library.
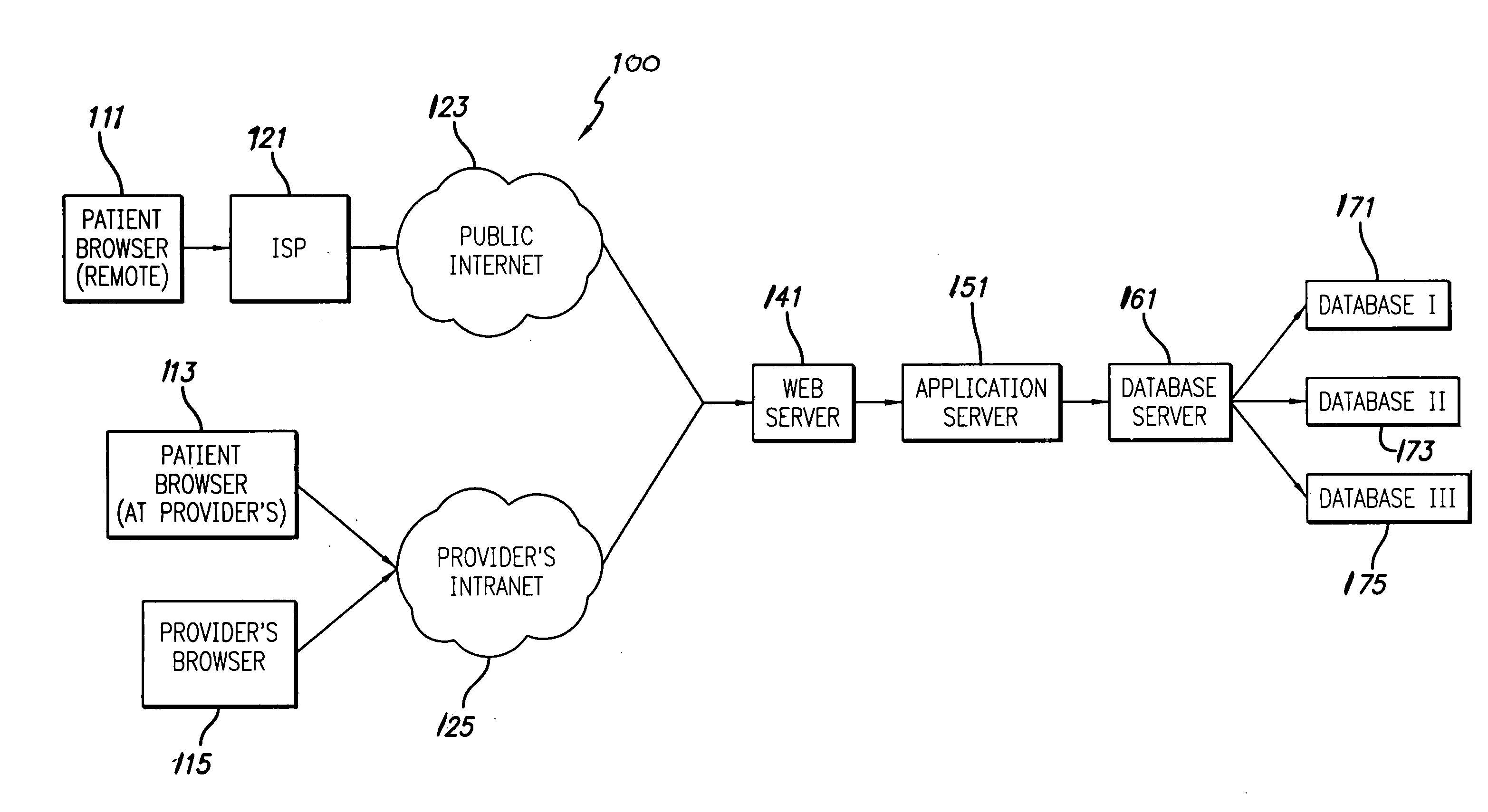
Digital image collection and library system
InactiveUS20050027570A1Minimization requirementsData processing applicationsDigital data processing detailsSystems managementDigital image data
Collection, access and management of controlled-access digital image data across disparate image data protocols from different sources, for example, clinical-quality and communicative-quality images of all types used in the practice of medicine, is achieved using a digital image collection and library system over a wide area network. The system includes a database connectivity module configured for automatic uploading of image data from image repositories employing data protocols of various types for image data, in association with subject data. A central library system manages distribution and control of collected images to qualified requesters.
Owner:PT INTERACTIVE INC
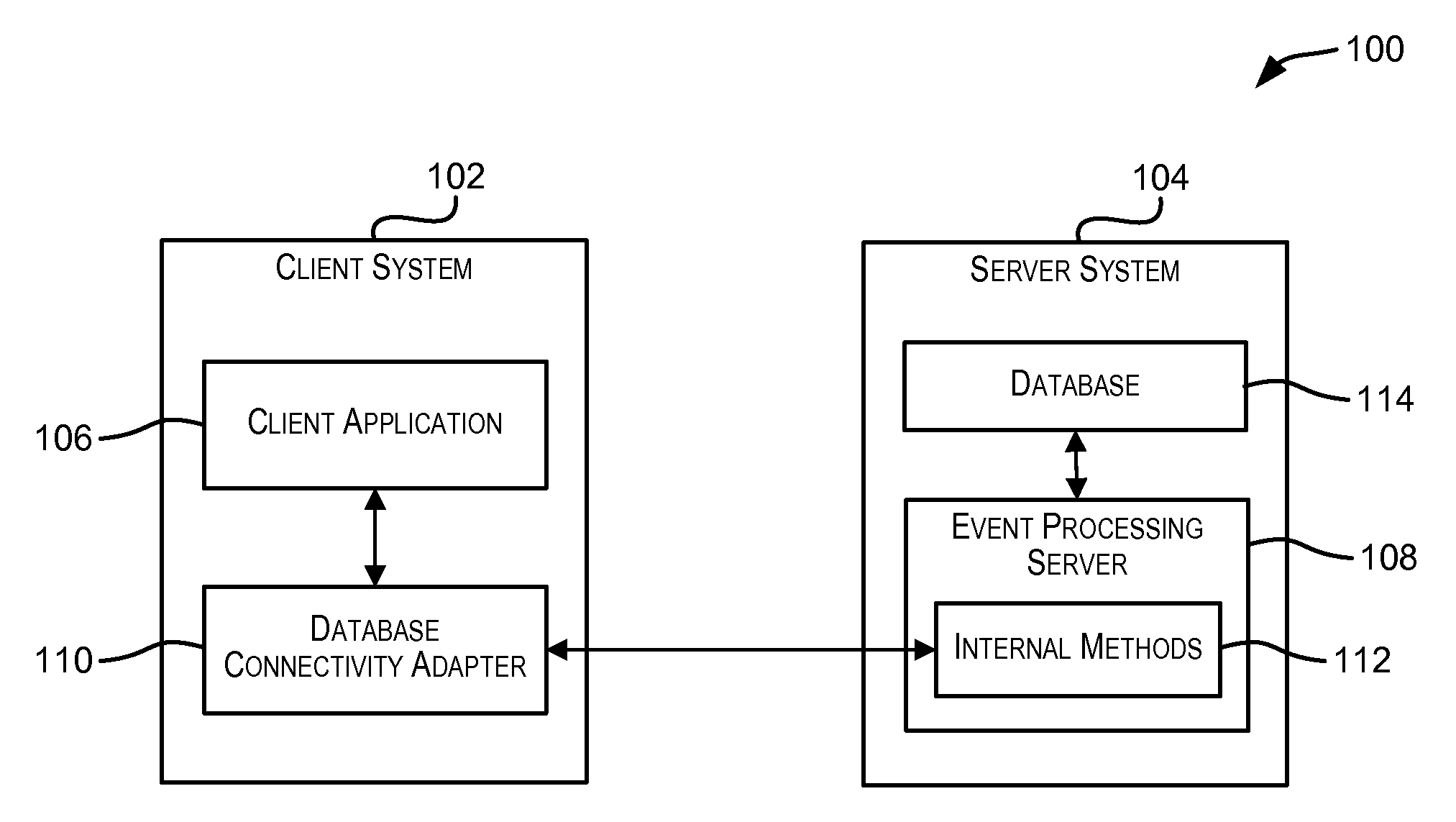
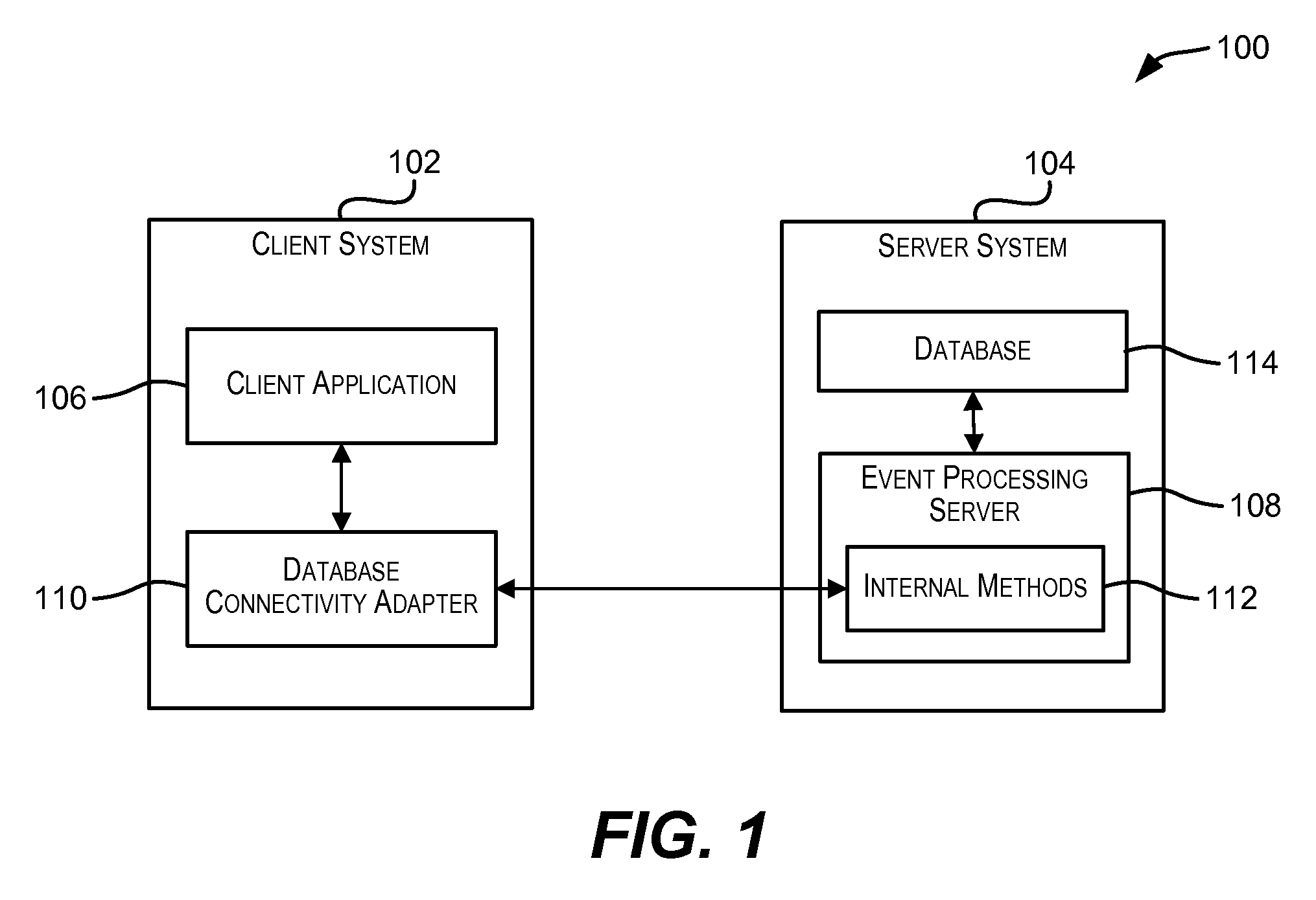
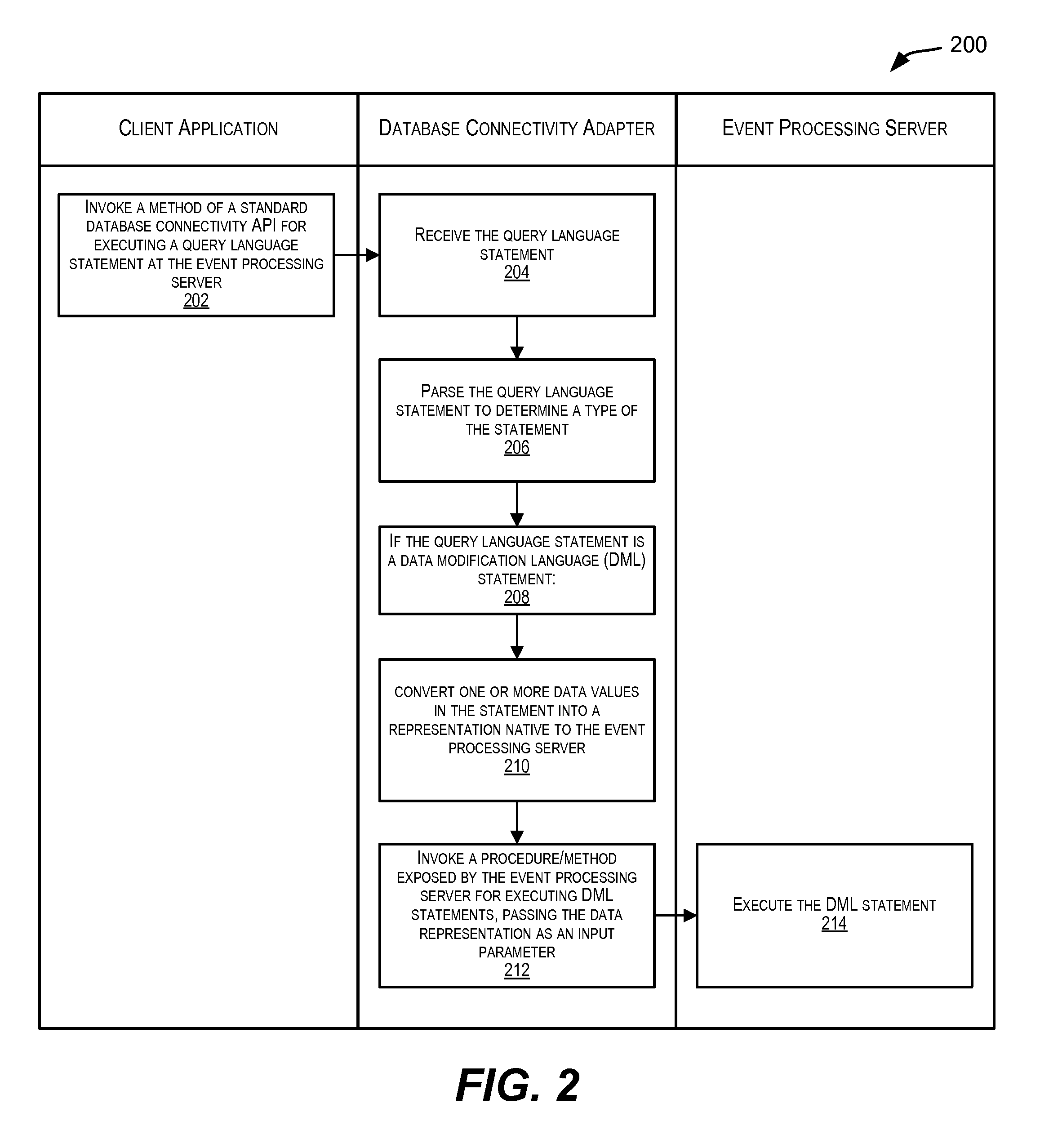
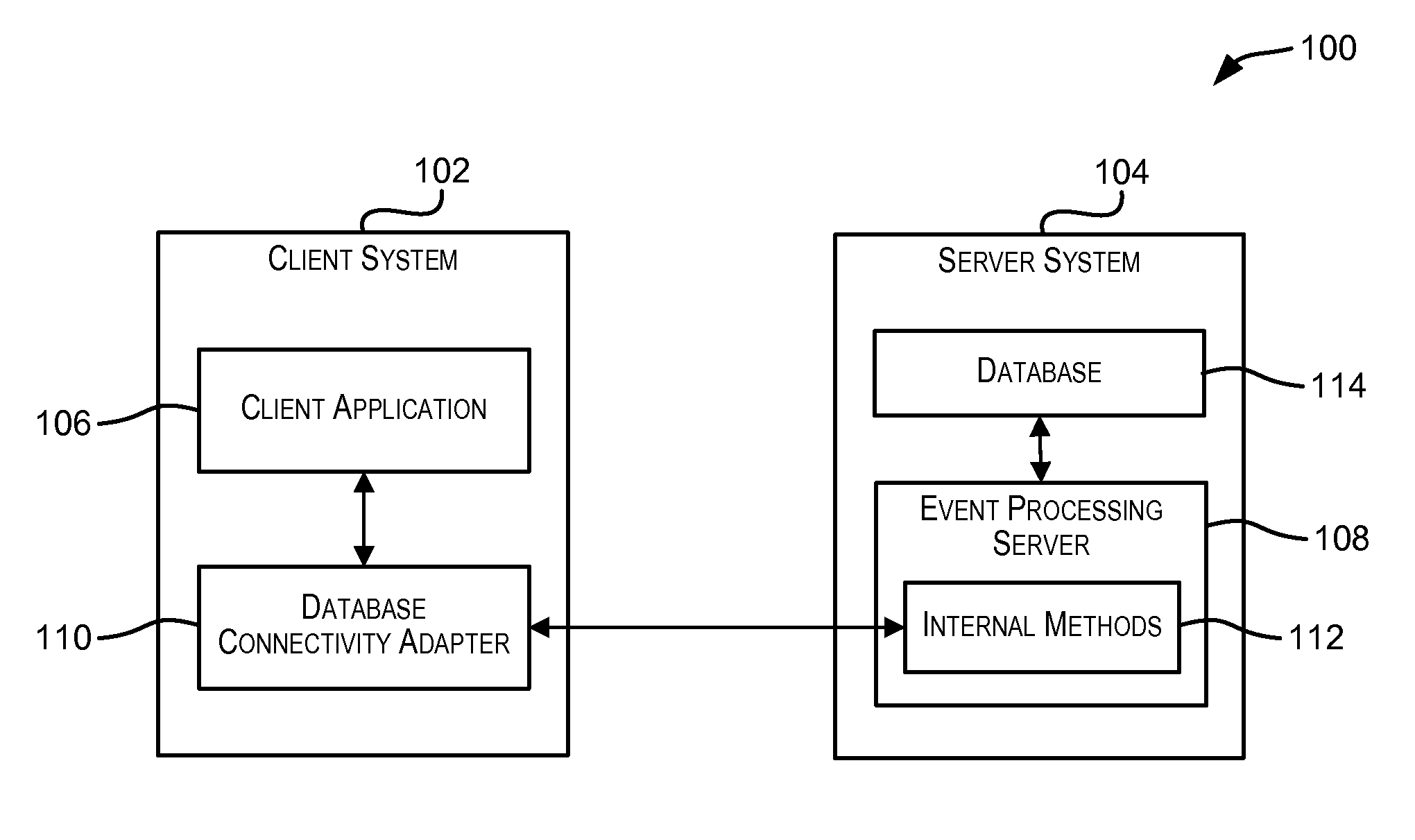
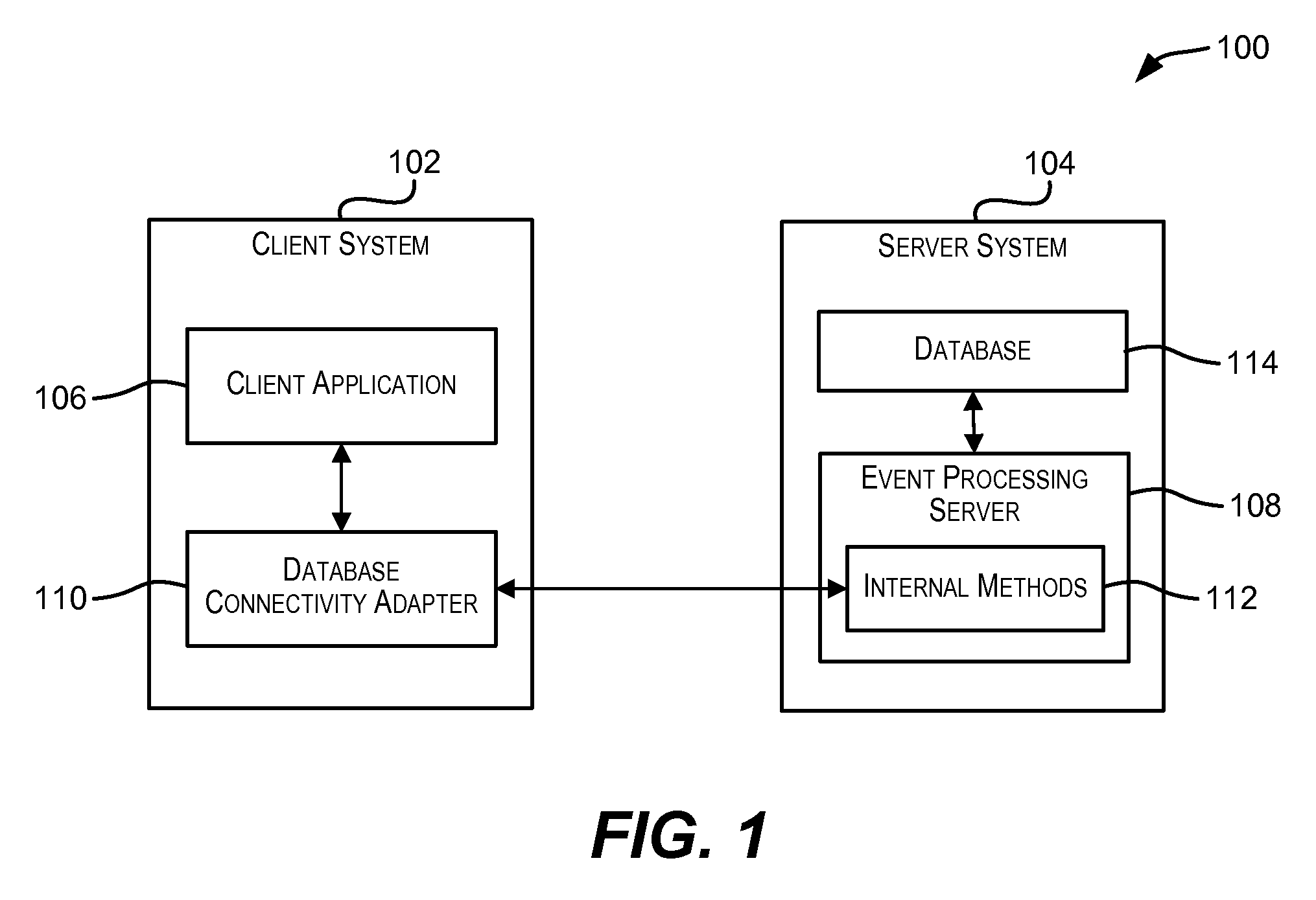
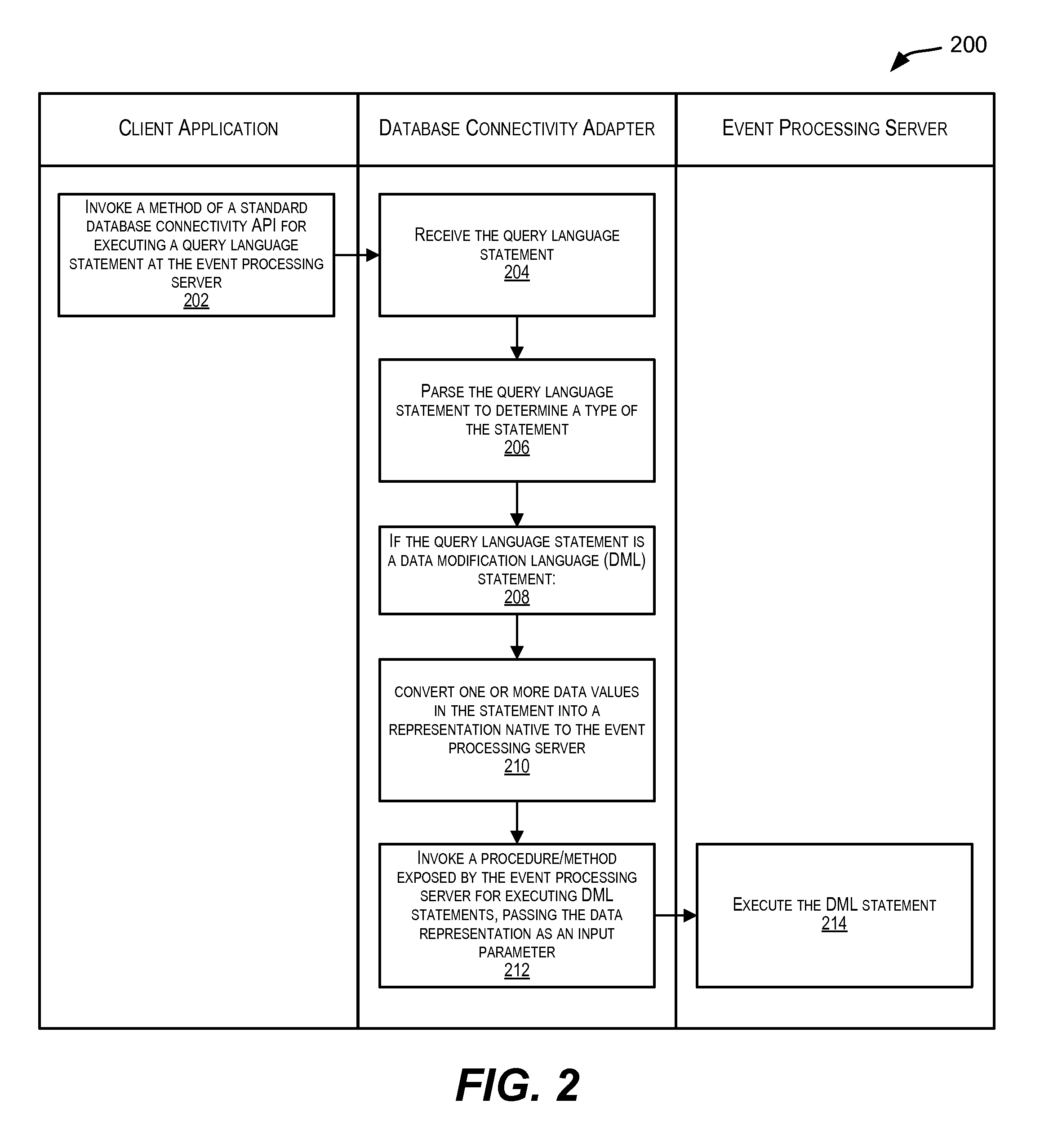
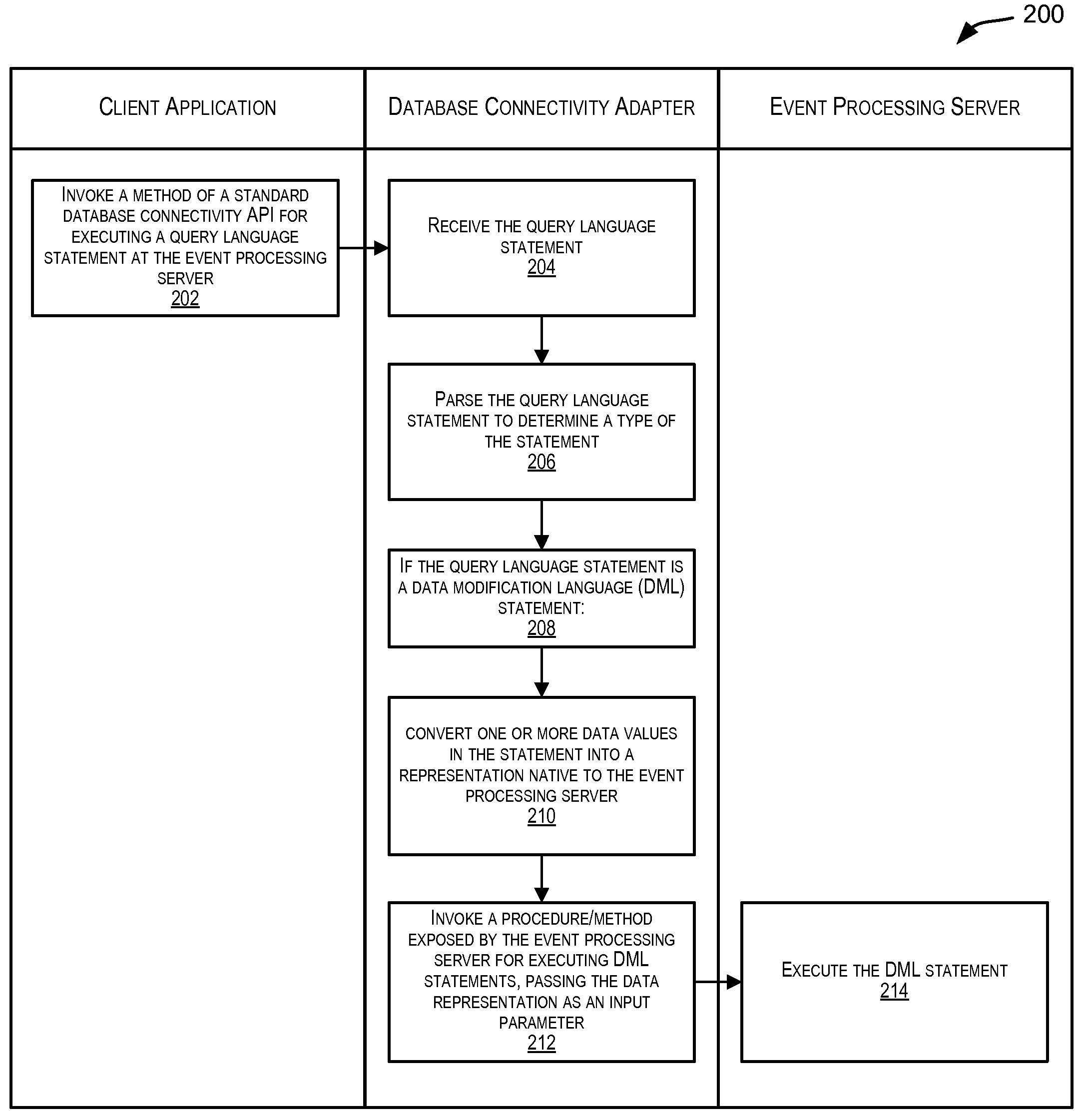
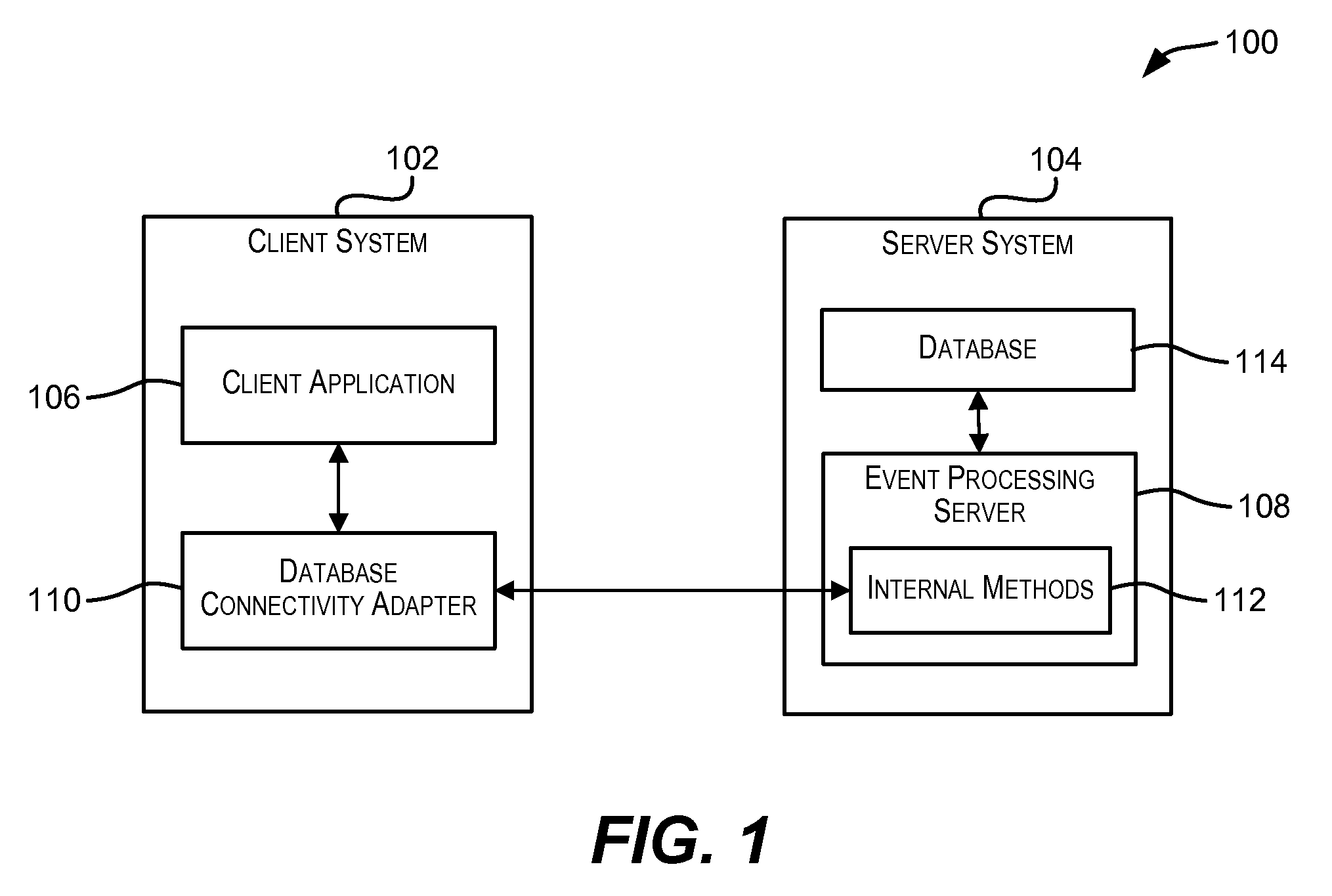
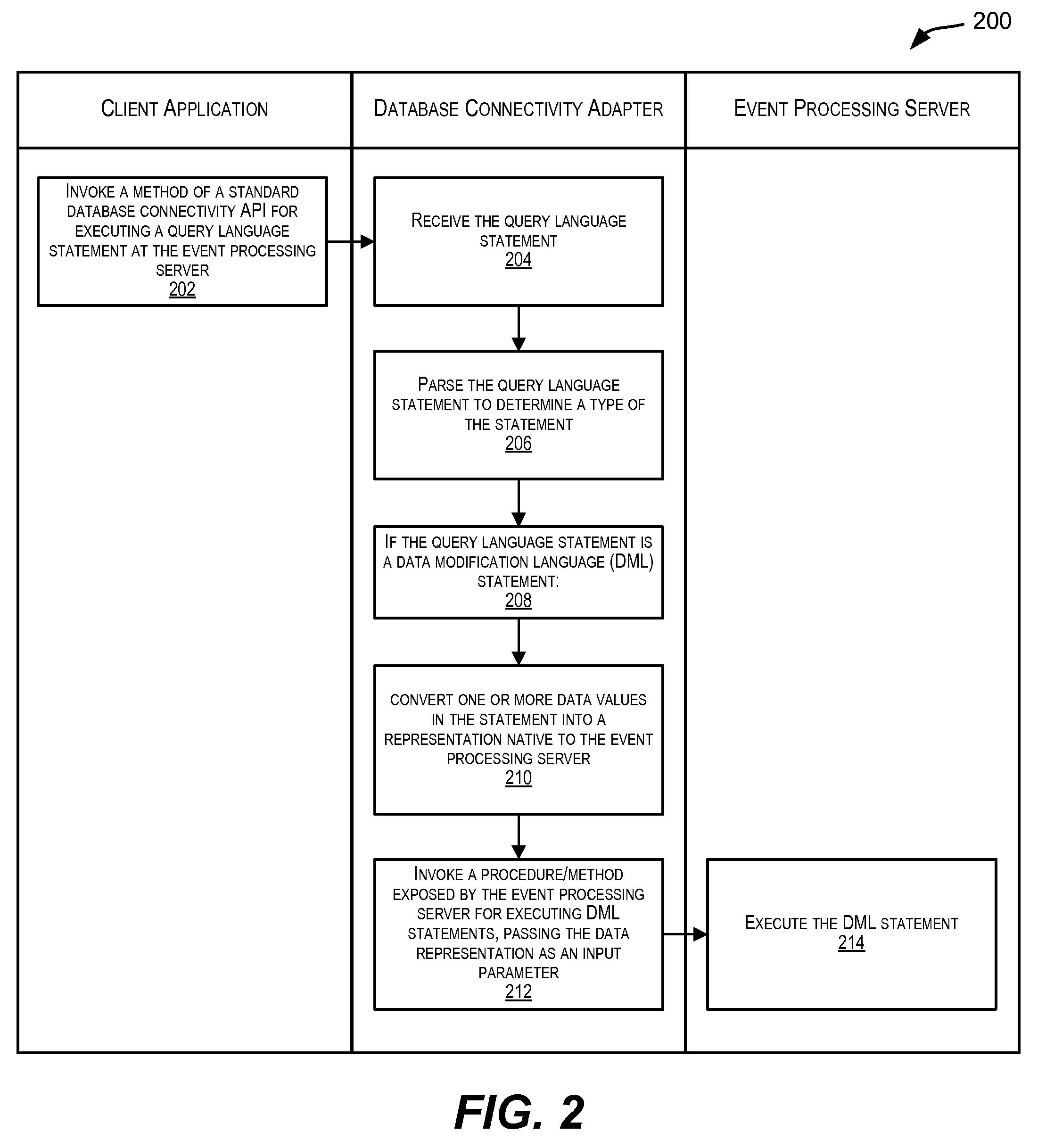
Standardized database connectivity support for an event processing server
ActiveUS20110023055A1Facilitate communicationDigital data information retrievalDigital data processing detailsApplication softwareClient-side
Techniques for facilitating communication between one or more client applications and an event processing server. In one set of embodiments, a framework is provided that enables a client application to communicate with an event processing server via a standard database connectivity API, such as Java Database Connectivity (JDBC).
Owner:ORACLE INT CORP
Standardized database connectivity support for an event processing server
ActiveUS8387076B2Facilitate communicationDigital data information retrievalDigital data processing detailsClient-sideApplication software
Techniques for facilitating communication between one or more client applications and an event processing server. In one set of embodiments, a framework is provided that enables a client application to communicate with an event processing server via a standard database connectivity API, such as Java Database Connectivity (JDBC).
Owner:ORACLE INT CORP
Standardized database connectivity support for an event processing server in an embedded context
ActiveUS8321450B2Facilitate intra-process communicationFacilitate communicationDigital data information retrievalDigital data processing detailsApplication softwareClient-side
Techniques for facilitating communication between one or more client applications and an event processing server. In one set of embodiments, a framework is provided that enables a client application to communicate with an event processing server via a standard database connectivity API, such as Java Database Connectivity (JDBC).
Owner:ORACLE INT CORP
Method for accessing object linking-embedding database data via JAVA database connectivity
ActiveUS7089566B1Multiprogramming arrangementsSpecific program execution arrangementsClient-sideApplication software
Owner:UNISYS CORP
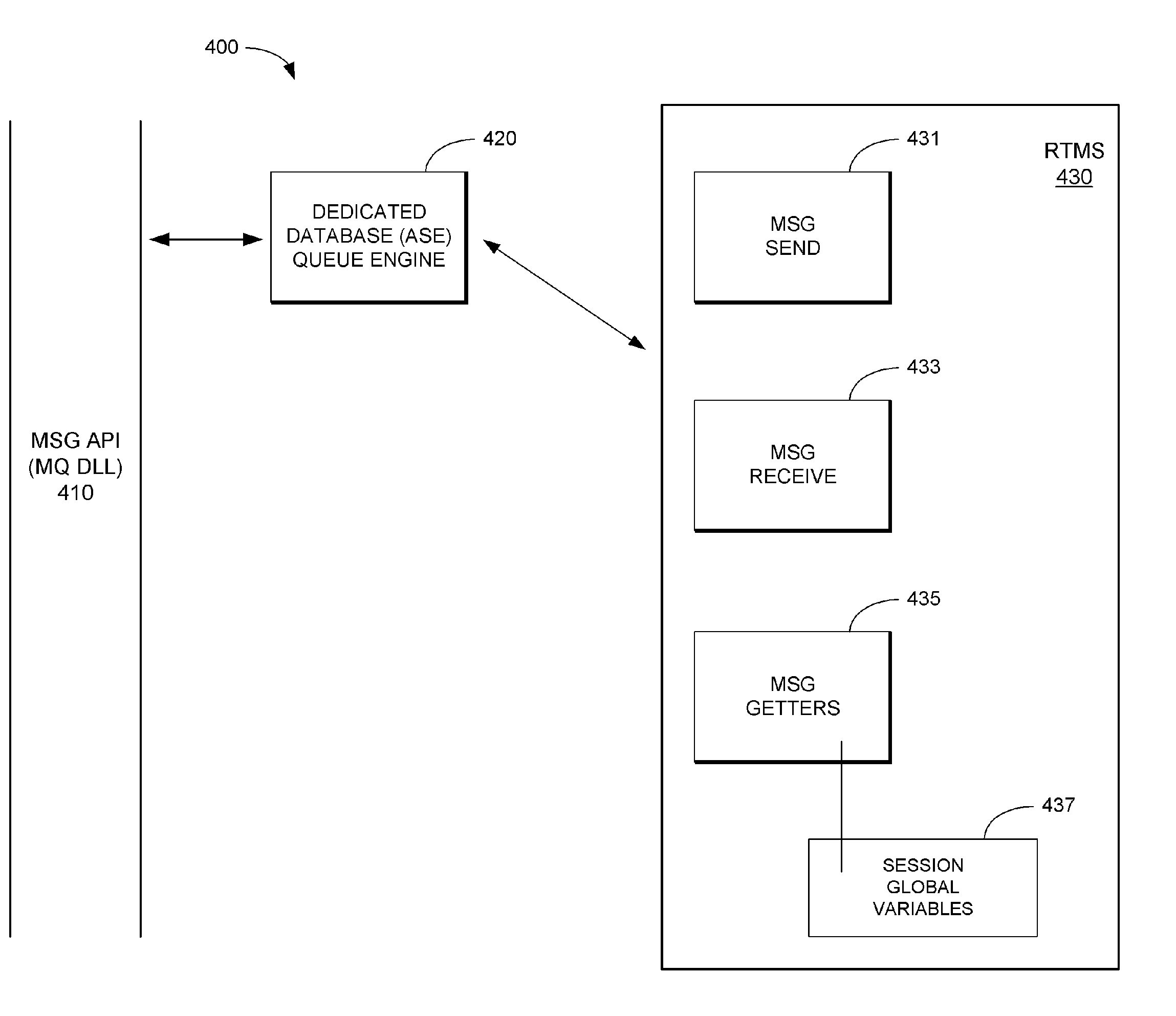
Real-Time Messaging System for Bridging RDBMSs and Message Buses
InactiveUS20070162421A1Digital data information retrievalSpecial data processing applicationsQuery languageHuman language
Owner:SYBASE INC
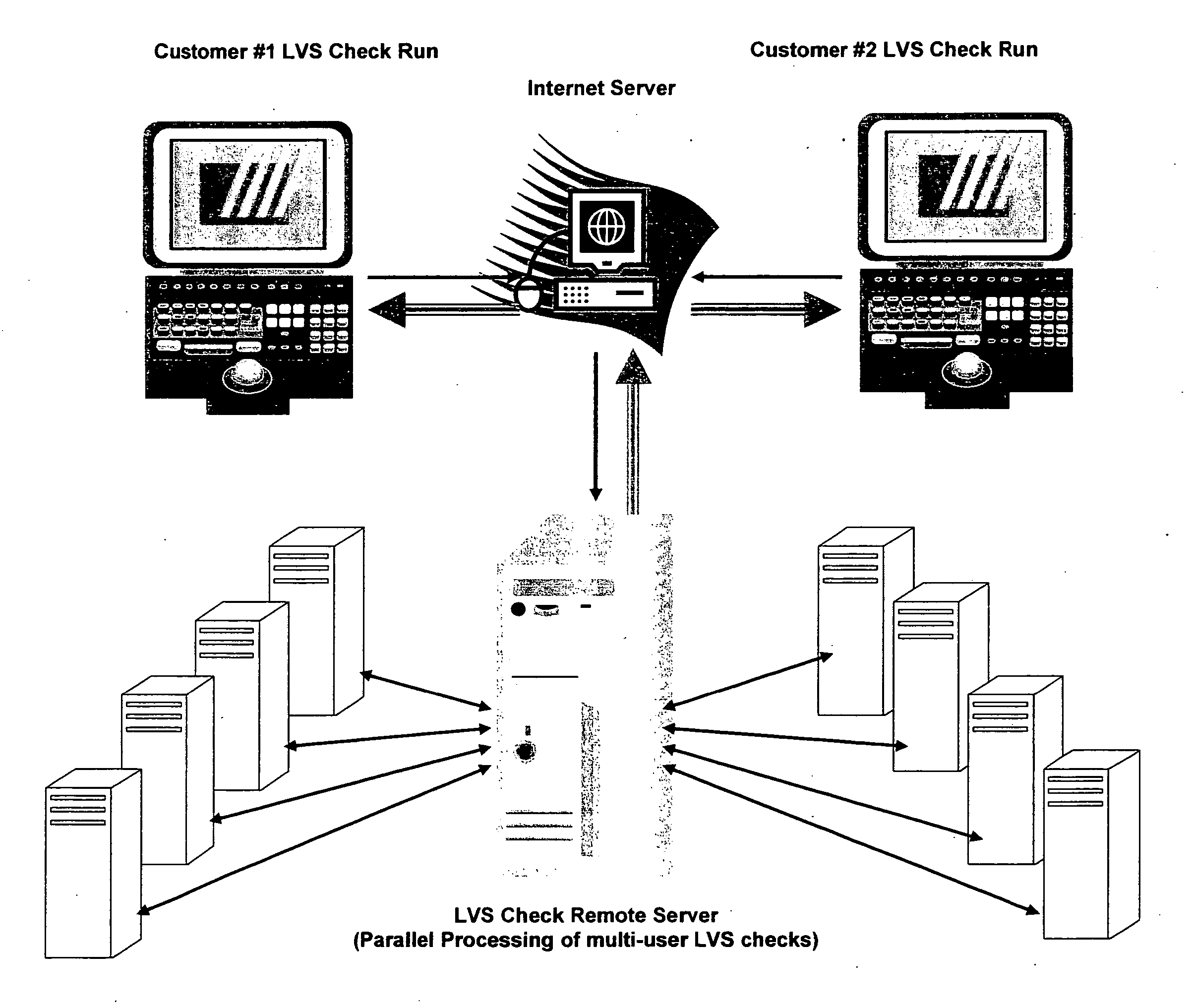
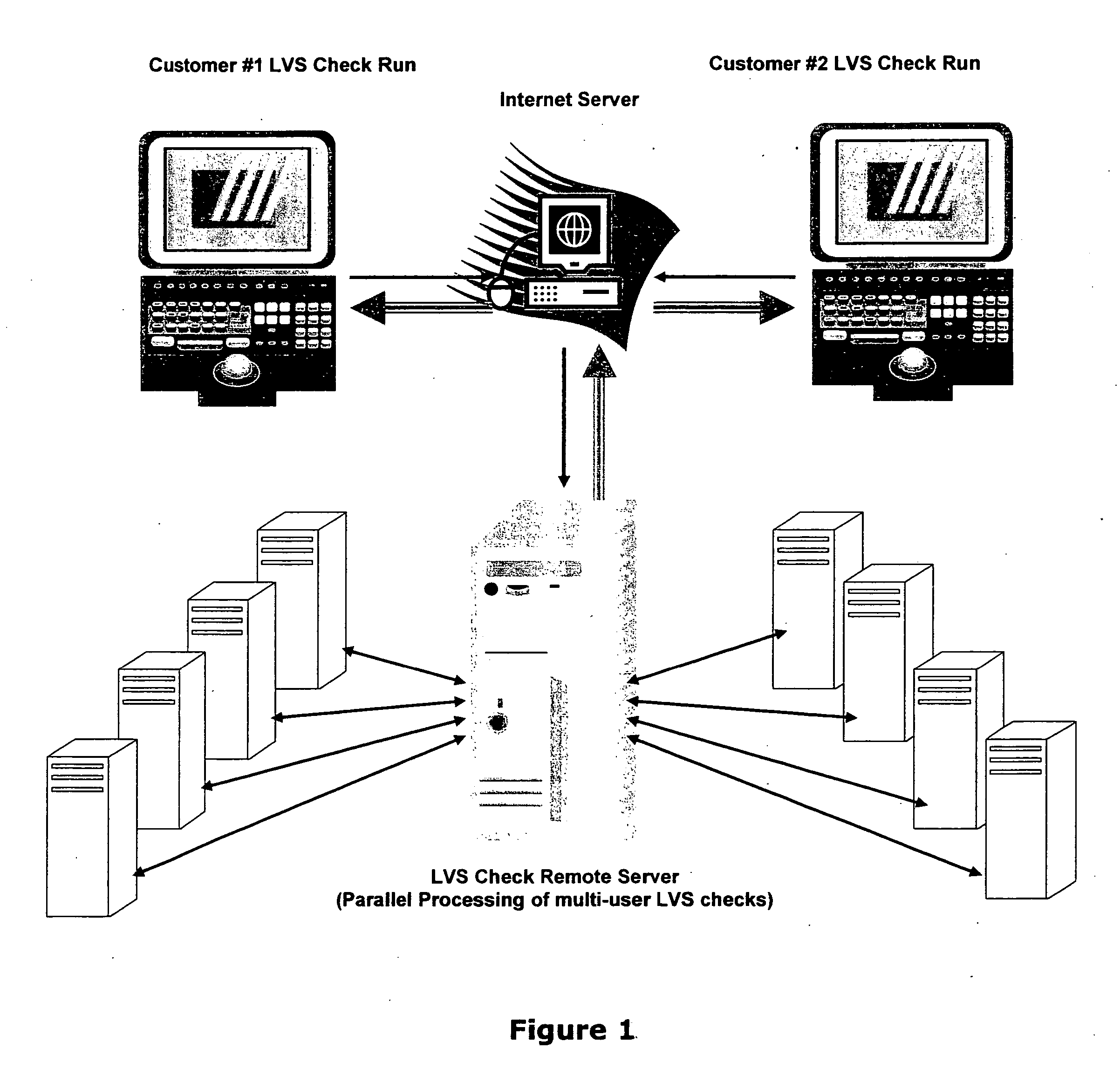
Connectivity verification of IC (integrated circuit) mask layout database versus IC schematic; LVS check, (LVS: IC layout versus IC schematic) via the internet method and computer software
InactiveUS20060200789A1Avoid repetitive drawingShorten the timeCAD network environmentCAD circuit designThe InternetLayout Versus Schematic
This paper describes an EDA (Electronic Data Automation) method and computer software invention for connectivity verification of IC mask Layout database versus IC Schematic; LVS Check (LVS: IC Layout versus IC Schematic) over the internet. The technique takes advantage of a unique algorithm to check the mask layout database connectivity, compare it with its corresponding schematic diagram for any mismatches in the mask layout polygons connections. The input of the tool is a mask layout database blocks (i.e.: IC layout) that were made manually and / or automatically using synthesized tools. These blocks may have some connectivity mismatches that need to be fixed in order to match the corresponding integrated circuit (IC) schematic diagrams. The output of the software tool is a text based descriptive log file and errors markers pointers that may be read into the mask layout database in order to point any connectivity mismatches of the mask layout database, comparing it to its corresponding schematic diagram. The end result is a mask layout set of markers and a text format log file that describes any mismatched connections in the mask layout database, comparing it to its corresponded schematic diagram. The software performs on individual mask layout blocks and / or on hierarchical structure of mask layout blocks. The system works hierarchically and / or flat. System also checks mask layout database incrementally, means only blocks that have been changed are checked. The system can be run via the internet using our secured protocol. The system offer a web based control panel to execute all necessary setups for submitting LVS check over the internet. The system offers the option to run on a local machine (user's computer) or on the main server over the internet. (Inventor's computer) The system also offers a PDA (Personal Digital Assistant) interface to launch LVS runs via industry's standard PDA's. The procedure is fully secured by 128 bit security protocol. All necessary file including mask layout GDSII (or GDSIII) file, netlist and technology file are securely encrypted using 128 bit protocol and send to the remote server. These files are decrypted and submitted for LVS check on the remote servers. The main remote server is distributing the task among other computer system for advanced parallel processing to achieve fast results. All results log files are encrypted using 128 bit security protocol and available for download by the user. In case of local LVS check the results files are available on the user's local machine.
Owner:RITTMAN DAN
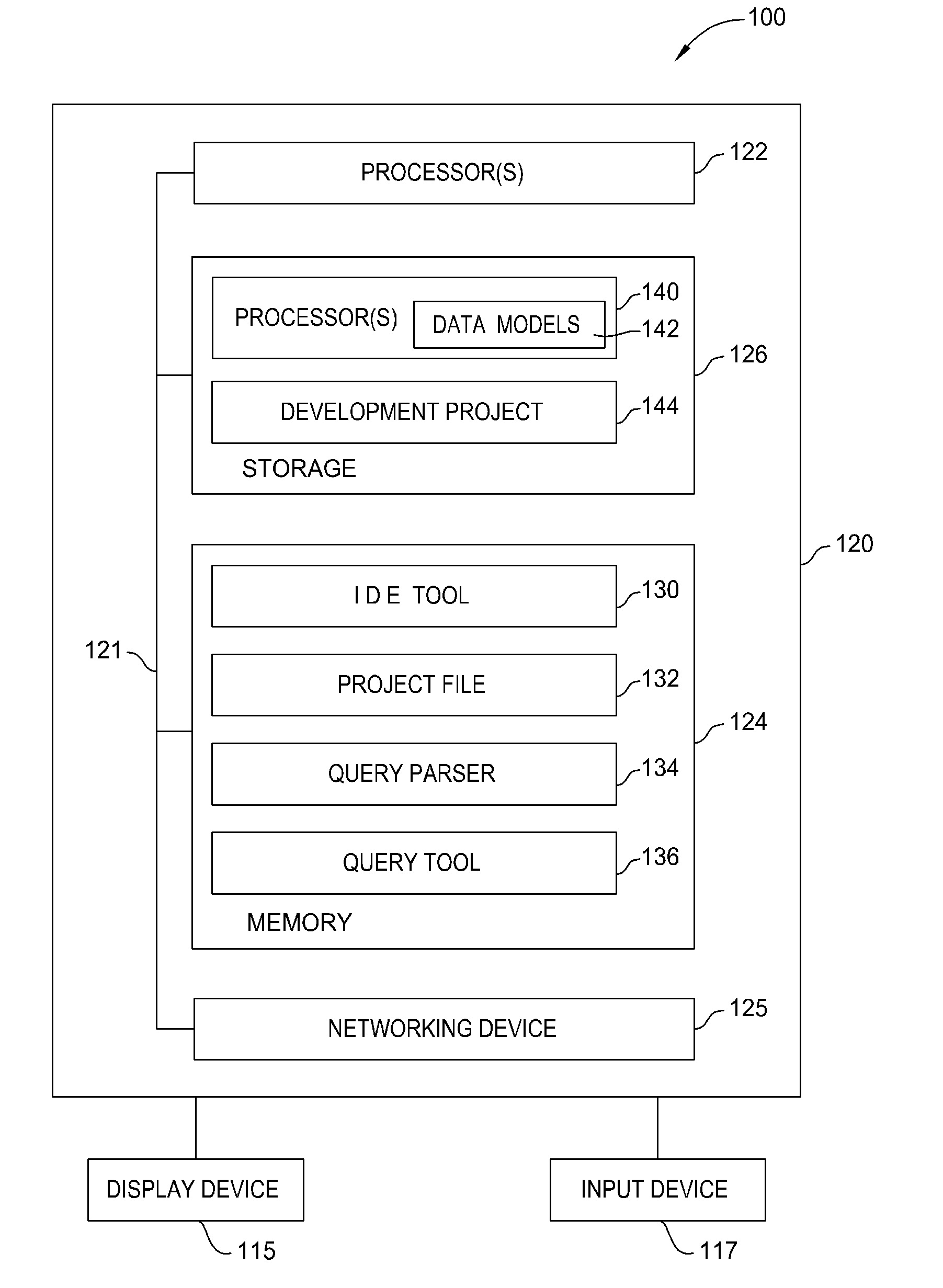
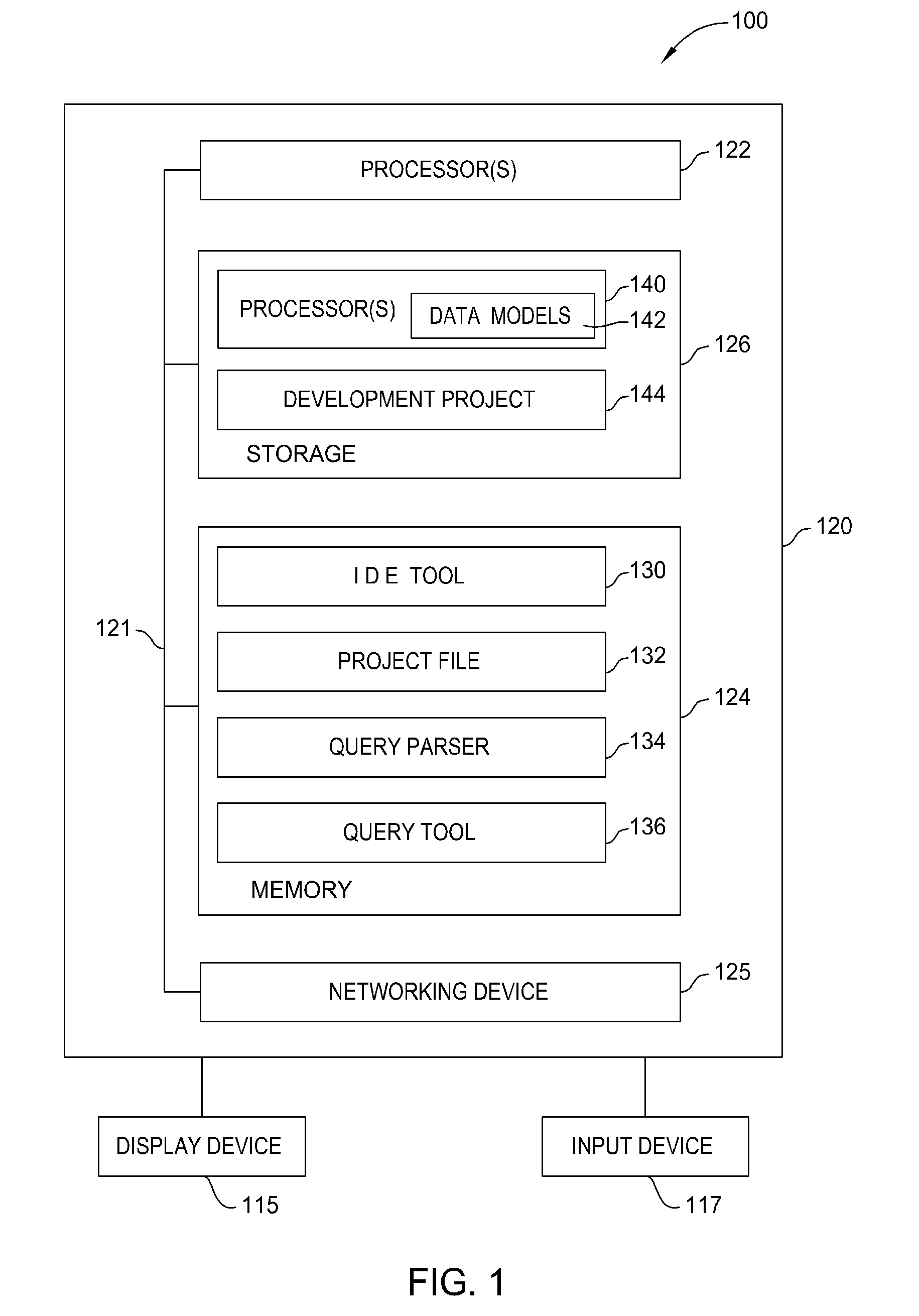
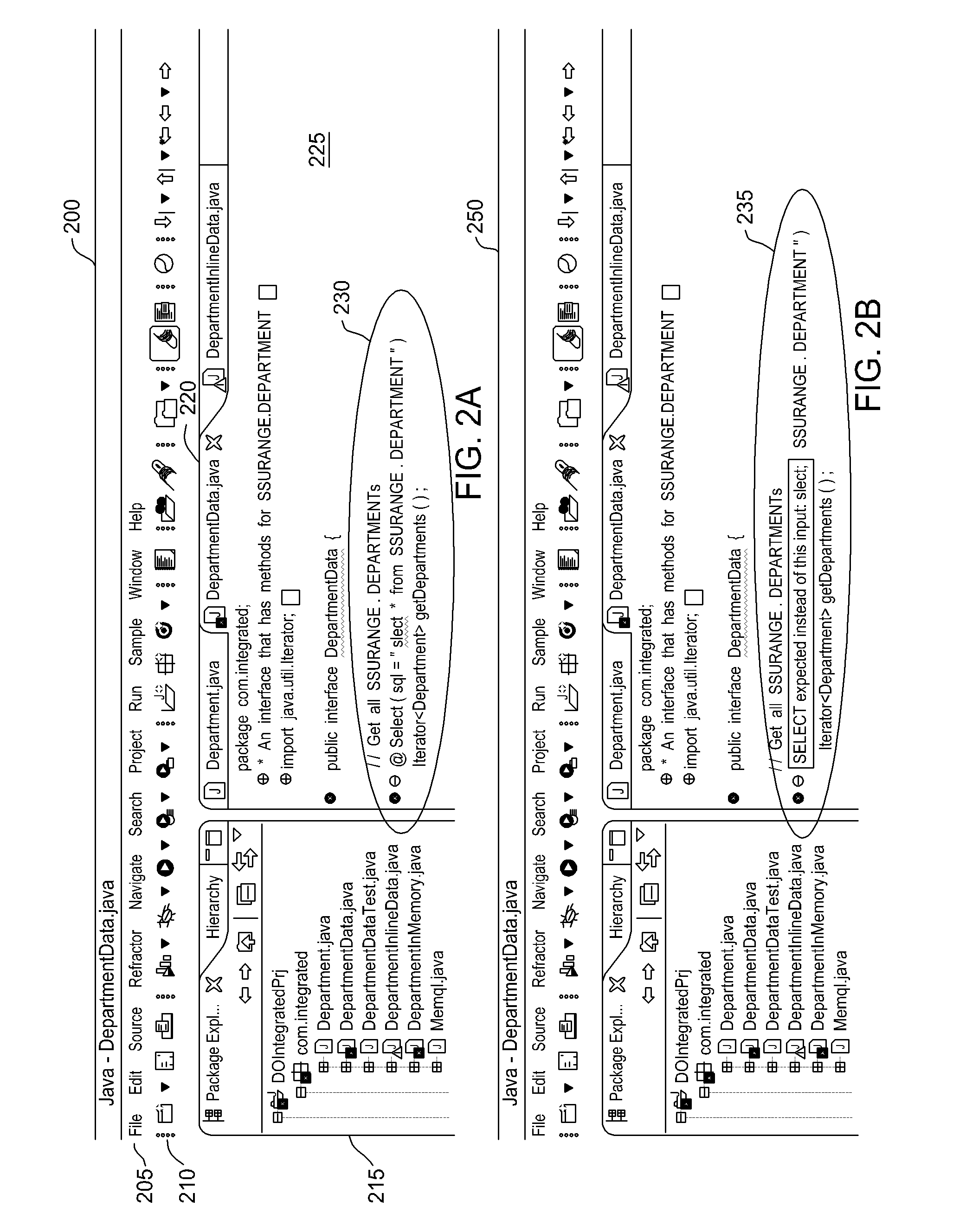
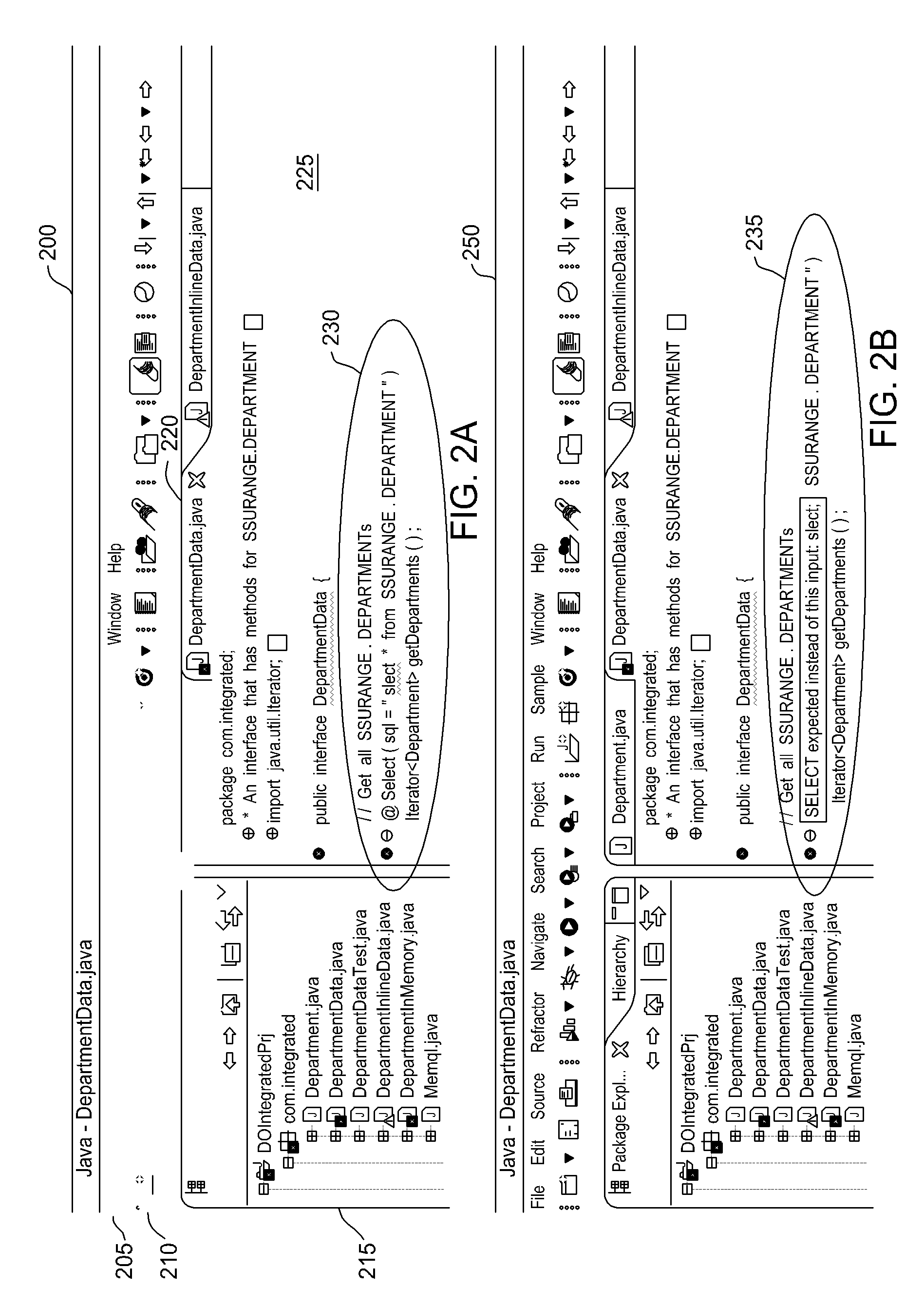
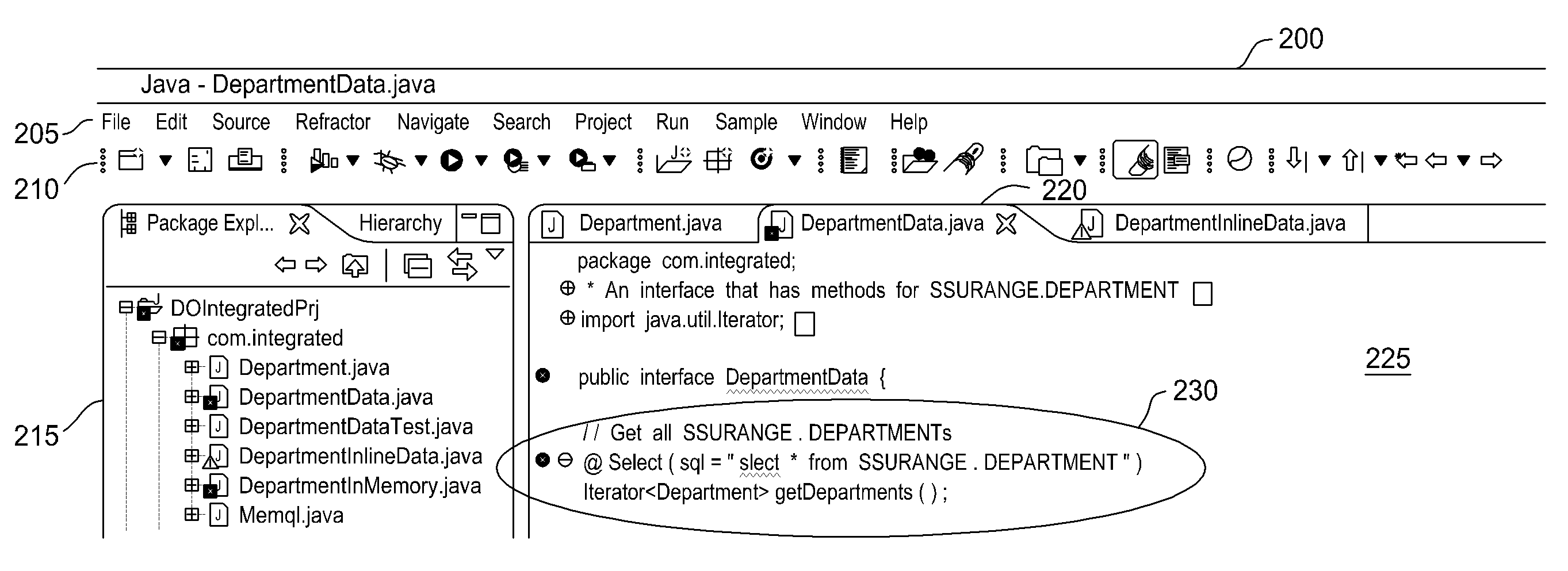
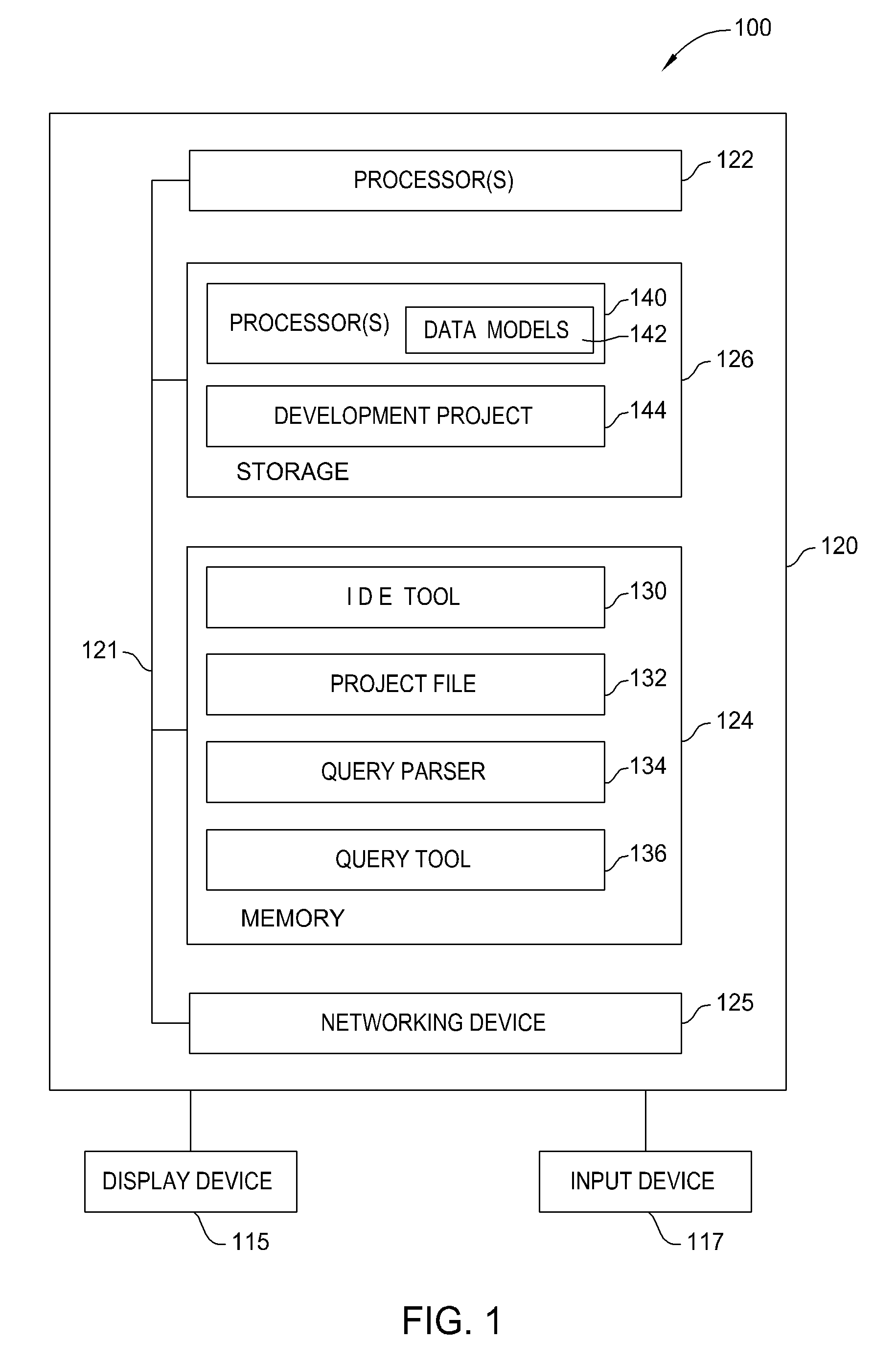
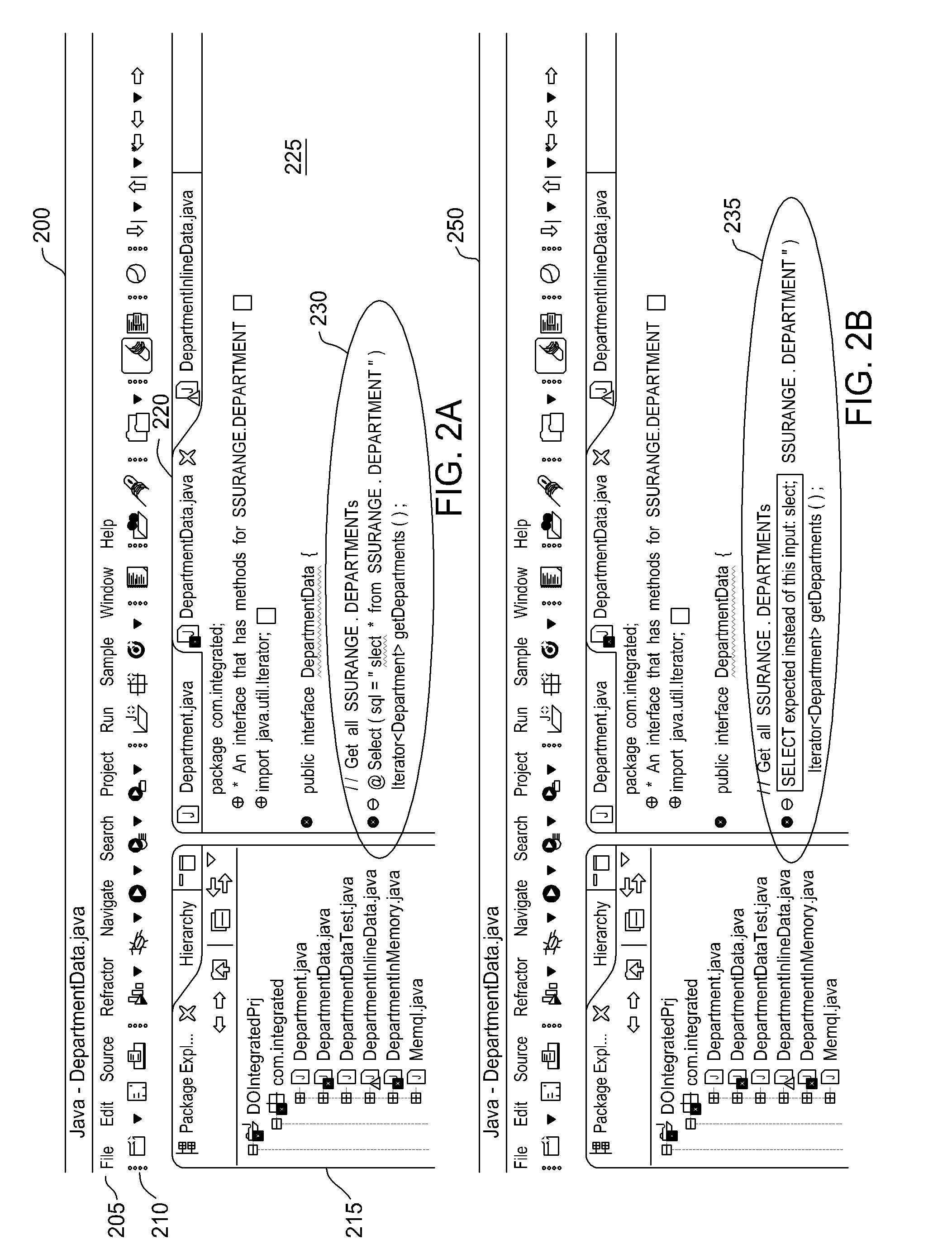
Database connectivity and database model integration within integrated development environment tool
InactiveUS20080270983A1Digital data information retrievalError detection/correctionApplication softwareSource code
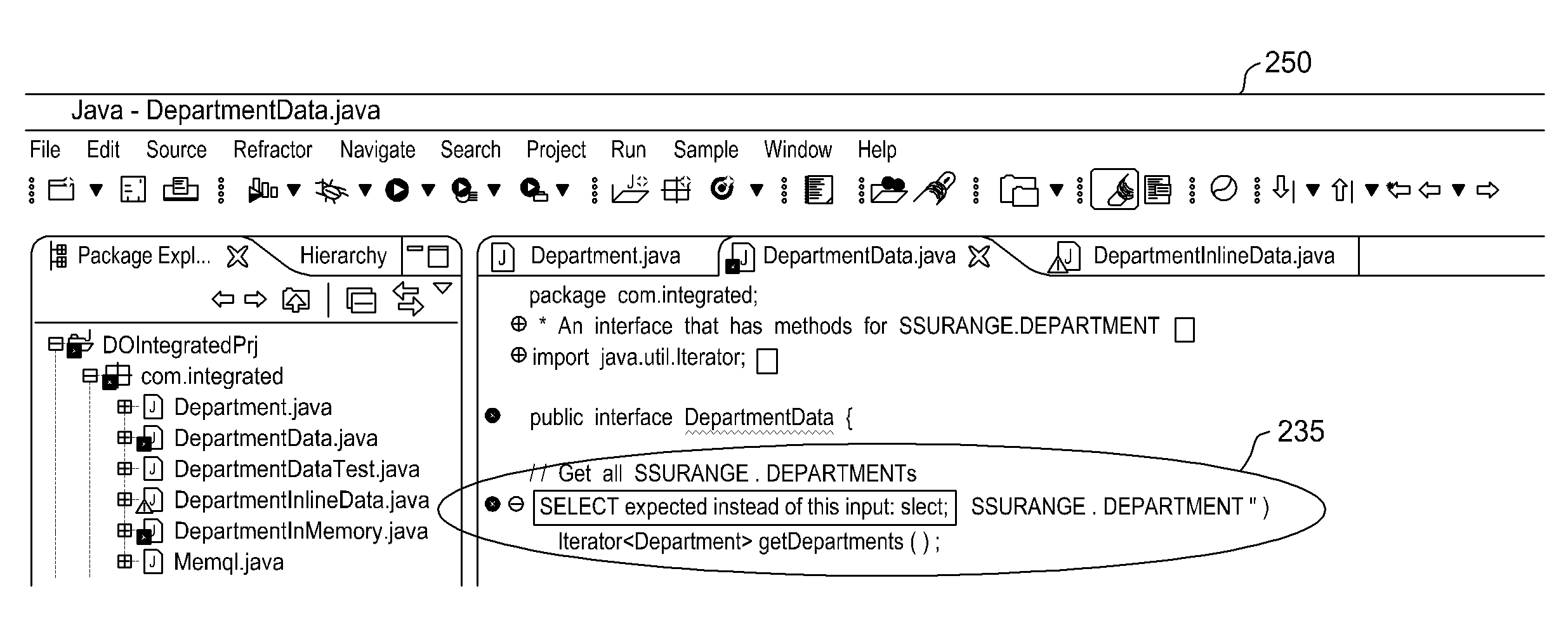
Embodiments of the invention provide database integration within an integrated development environment (IDE) tool for displaying database structure and other database information, query editing and execution, and error detection for database statements embedded in program source code. Embodiments of the invention integrate database connectivity and error detection into the IDE tool, thereby potentially reducing the time required for database-aware application development.
Owner:IBM CORP
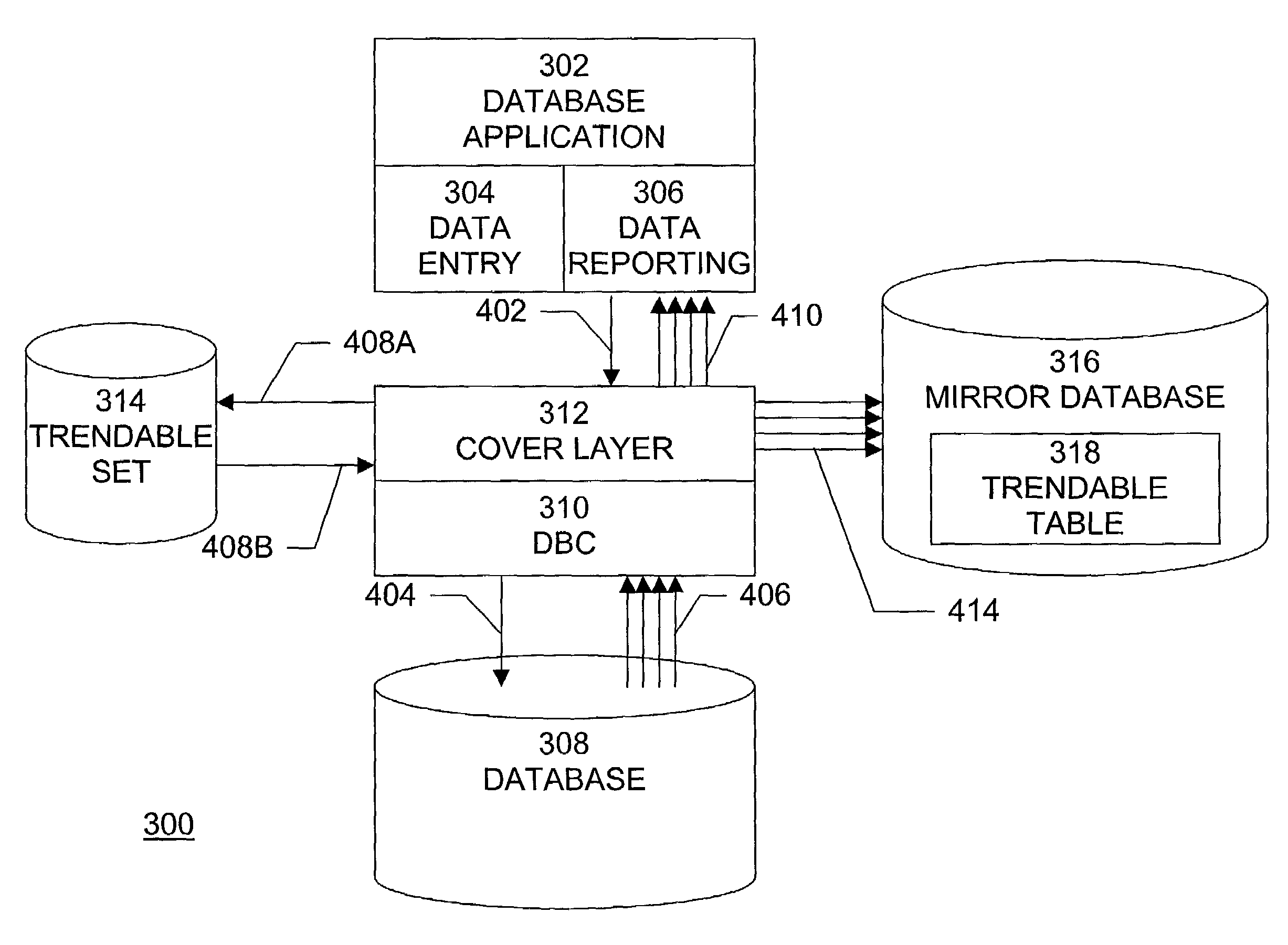
Automatic trend analysis data capture
InactiveUS7069263B1Data processing applicationsDigital data information retrievalData setDatabase application
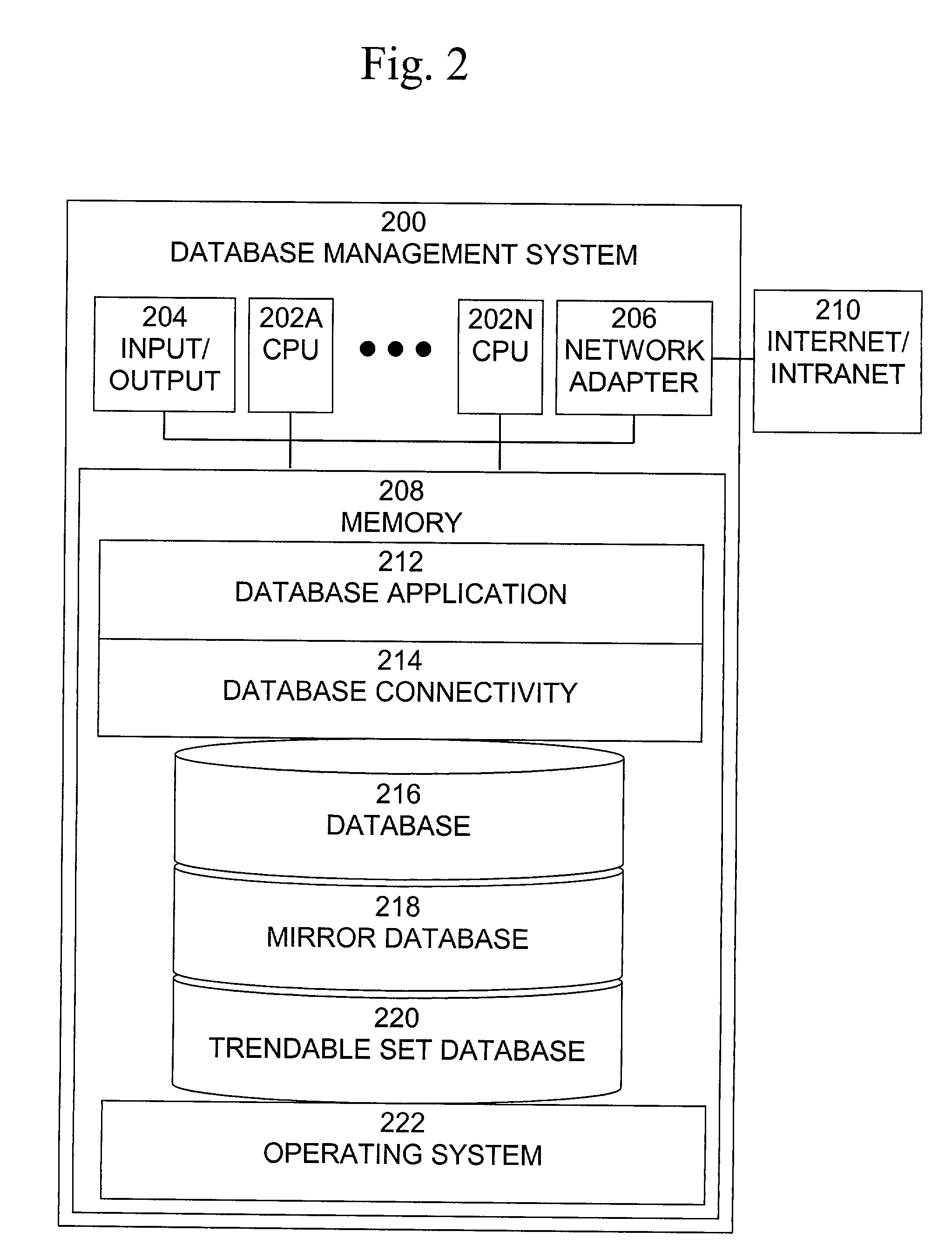
A method, system, computer program product, and database connectivity layer provides the capability to capture data over time so that trend analysis may be performed that does not require modifications to the data model and the data processing applications. A method of automatically capturing data for trend analysis comprises the steps of: receiving a query for data from a database application, issuing the received query to a database management system, receiving a response to the query from the database management system, the response indicating a result dataset, creating or updating a database table that is suitable for trend analysis, and populating or updating the database table with data from the result dataset.
Owner:ORACLE INT CORP
Detecting and displaying errors in database statements within integrated development environment tool
ActiveUS20080270989A1Digital data processing detailsIntelligent editorsDatabase connectivityApplication software
Embodiments of the invention provide database integration within an integrated development environment (IDE) tool for displaying database structure and other database information, query editing and execution, and error detection for database statements embedded in program source code. Embodiments of the invention integrate database connectivity and error detection into the IDE tool, thereby potentially reducing the time required for database-aware application development.
Owner:IBM CORP
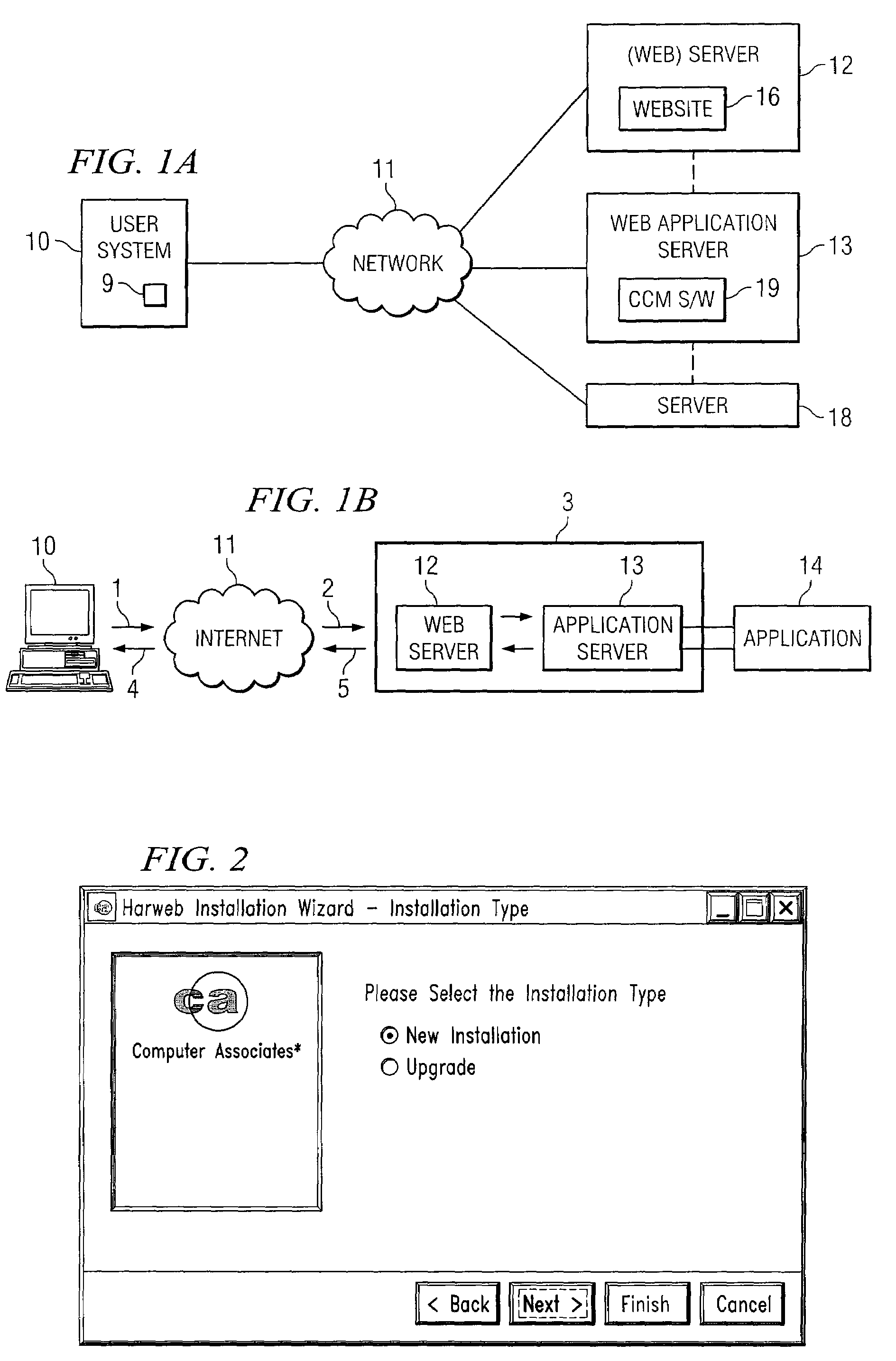
Automated Deployment of Change and Configuration Management Software Tools
ActiveUS20080016186A1Simplified expedited seamless deploymentLower potentialDigital data processing detailsMultiple digital computer combinationsWeb applicationApplication software
A system and method for automatically deploying a change and configuration management software tool to a web application server includes launching a configurable wizard application programmed to solicit data from a user. The user is queried regarding a desired web application server and database connectivity authentication parameters. A location on the user's system of the desired web application server's installation package is identified. The user's input is integrated with the selected web application server. The change and configuration management software tool is automatically deployed to the desired web application server.
Owner:CA TECH INC
Processing database queries embedded in application source code from within integrated development environment tool
InactiveUS20080270343A1Digital data information retrievalIntelligent editorsDatabase connectivityDatabase query
Embodiments of the invention provide database integration within an integrated development environment (IDE) tool for displaying database structure and other database information, query editing and execution, and error detection for database statements embedded in program source code. Embodiments of the invention integrate database connectivity and error detection into the IDE tool, thereby potentially reducing the time required for database-aware application development.
Owner:IBM CORP
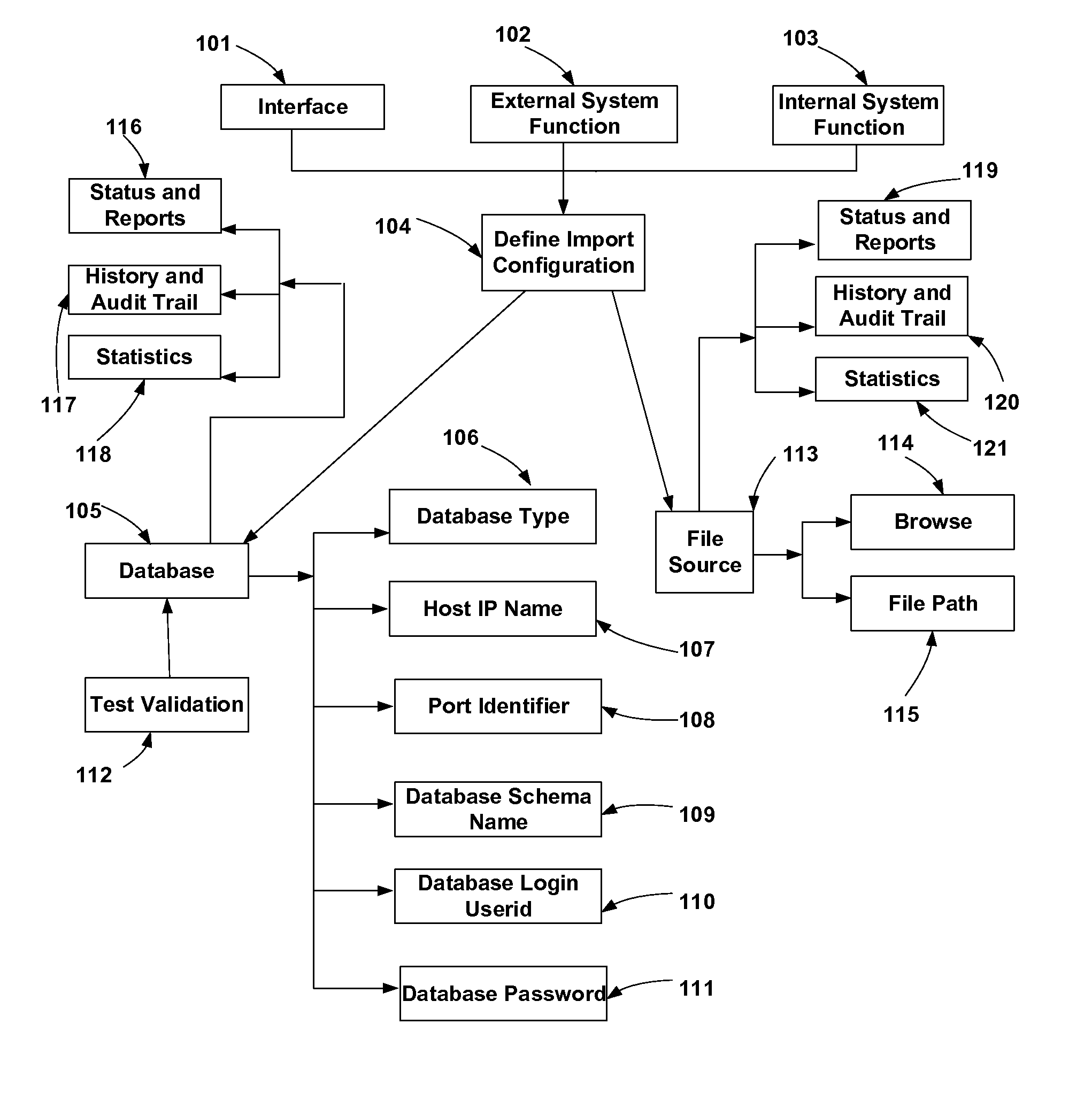
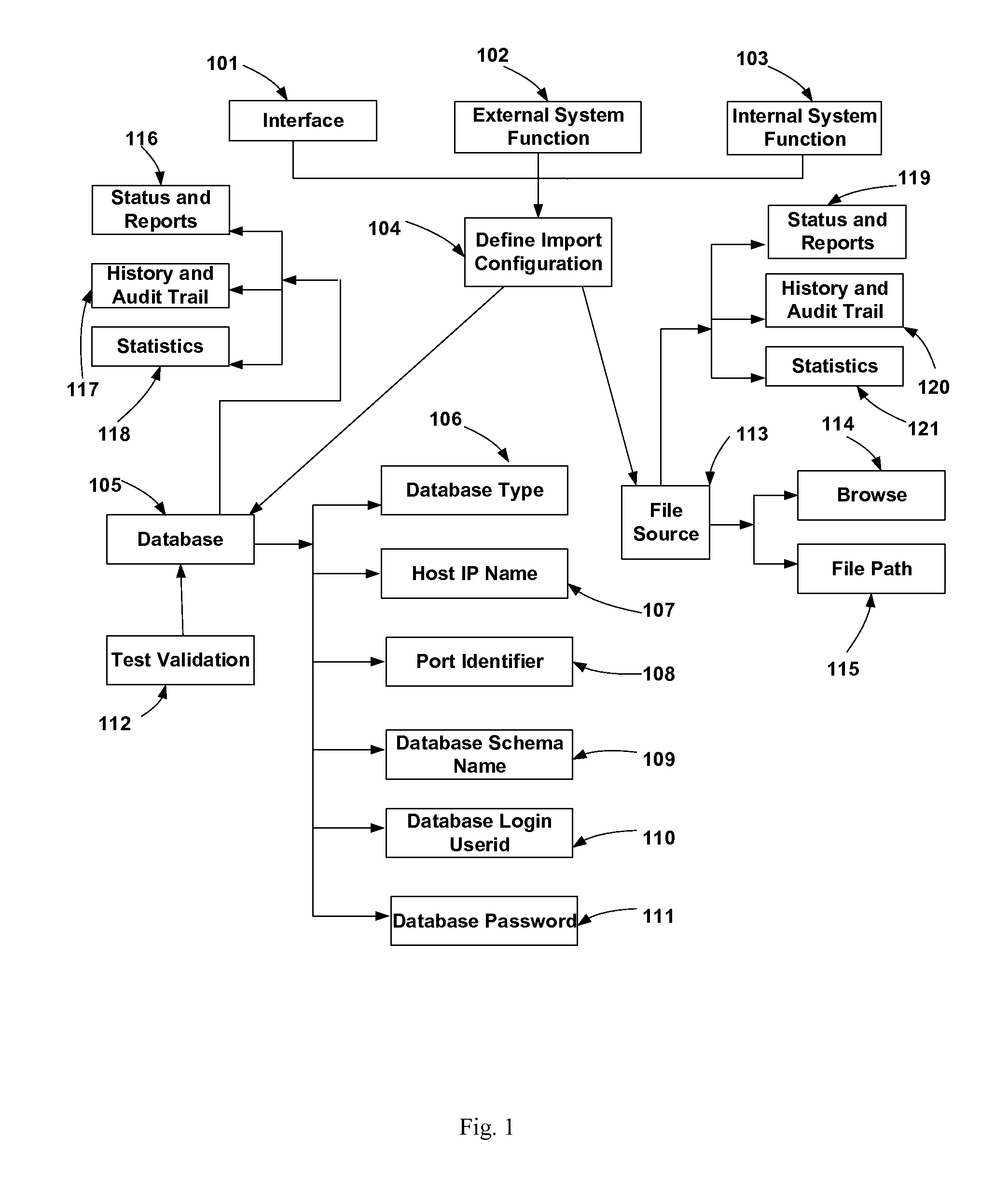
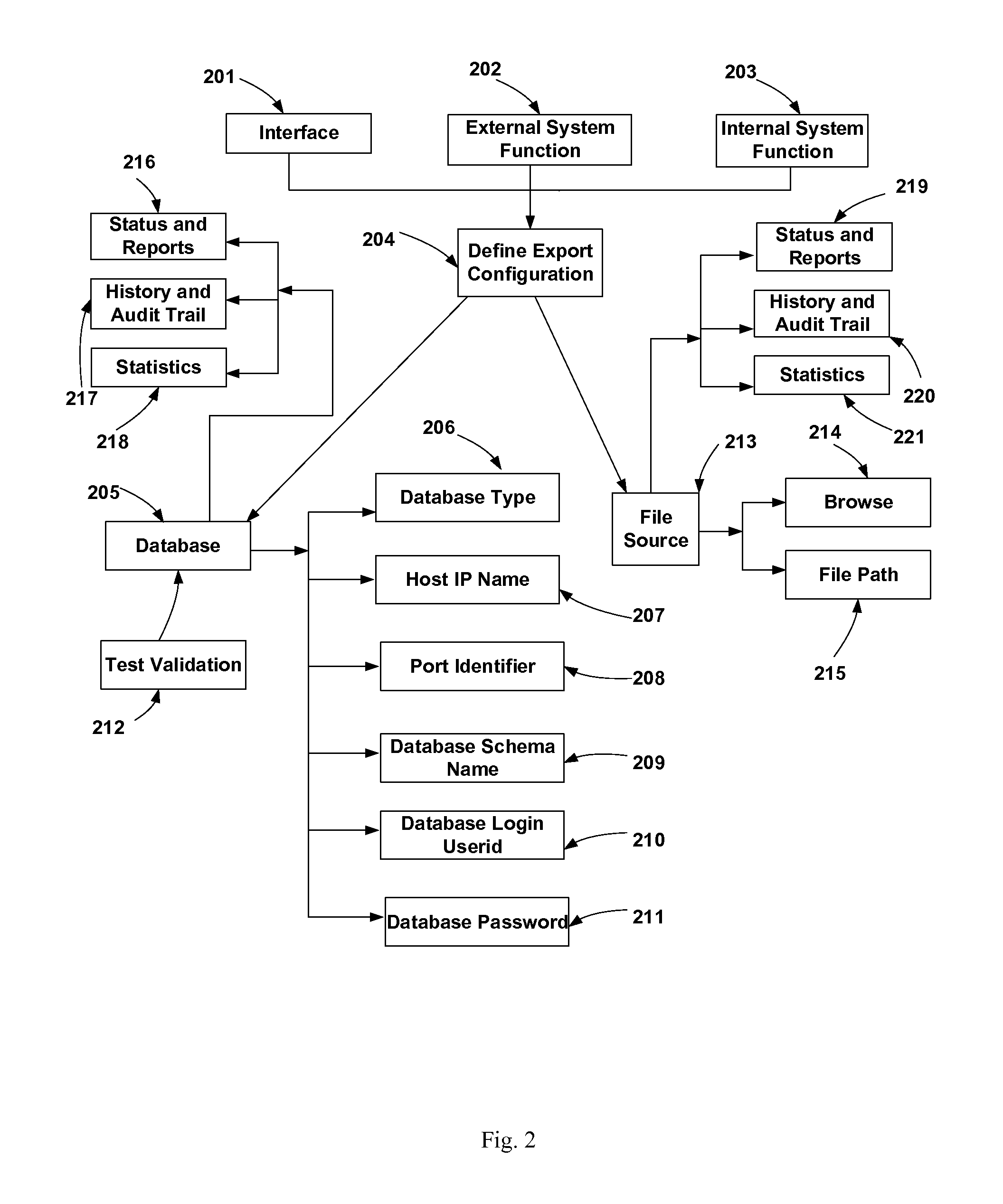
Method and system for handling program, project and asset scheduling management with reserves management and application integration
The invention comprises management of integration with interfacing applications, with emphasis on configurable database connectivity, logic manipulation of data, error checking with correction capability, with or without conditional criteria through a Graphical User Interface. The data can further be configured to be transported directly or through user-controlled means that allows manual modifications. The system mines the original and modified data with timestamp, history and audit trail that can generate audit-related information any time in the future. It further provides a hierarchical roll up and breakdown capability of managing reserves assets. Approval, Action Item, document attaching, notification and instant messaging functions can be linked to the integral functions. Status, history, audit trail, reports and statistics are tracked, maintained and linked to each element of the data and its related function, and this information is producible in any statistical, graphical or textual format.
Owner:NAGAR AJAY R +1
Access drive and data access method of proxy database
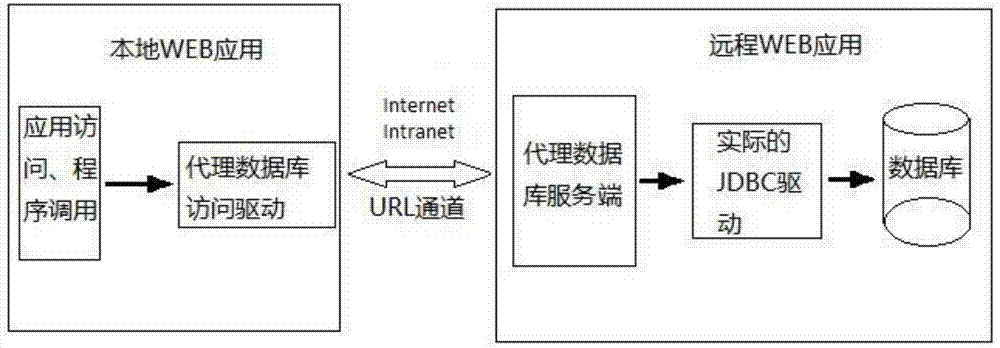
InactiveCN103488765AEasy accessEasy to integrateSpecial data processing applicationsWeb serviceInformation access
The invention belongs to the technical field of software development, and particular discloses an access drive and a data access method of a proxy database. The data access method includes that a web application with a proxy component is deployed in a web service which can be directly connected with a database service, wherein the web application includes an actual JDBC (java database connectivity) database drive capable of accessing a connected database; safety authorization information accessed by the proxy database is configured in a configuration file corresponding to the web application, and a server side accessed by the proxy database is formed after releasing; only parameters of a corresponding proxy database access drive need to be configured in a local web application to access an actual database data through connection to the server side accessed by the proxy database in case of incapability of directly connecting to the actual database, all database operations such as adding, deleting and correcting can be performed, and complete proxy of an actual database JDBC drive can be realized. The access drive can access data safely and rapidly in a B / S (browser / server) mode, and convenience is brought to completion of cross-service data integration and remote debugging and maintaining.
Owner:雷虹
Method used for quickly constructing forms in enterprise information system development process
InactiveCN103853543AReduce the amount of codeSpecific program execution arrangementsData displaySoftware engineering
The invention discloses a method used for quickly constructing dynamic business forms in a J2EE (java 2 platform enterprise edition) enterprise information system development process, and belongs to the technology of the software middleware software in the technical field of electronic information. In form field UI (user interface) design, the HTML (hypertext markup language) dynamic template technology is adopted, and a form customization page and a form field customization page in a B / S (browser / server) mode are provided; form data is directly operated in a JDBC (java database connectivity) mode; after form customization is finished, a background automatic generation module generates table definition data to the whole form and the design requirement of the form field according to customization information, and the table definition data is stored in a background foundation database; when a foreground page displays data, a background uniform page template is used for dynamically taking truthful data from a corresponding entity table; the truthful data is displayed according to the table definition data. The method used for quickly constructing the form in the enterprise information system development process, which is disclosed by the invention, has the advantages of small code quantity and simple and efficient system; the system does not need to be restarted, practical effect can be immediately seen by the revision operation to the form field definition, the form customization efficiency can be improved, the development cost is lowered, a user can customize the form according to the self requirement, and the form can become effective in real time and can be applied.
Owner:BEIJING YUNTIAN TIME & SPACE TECH CO LTD
Automated deployment of change and configuration management software tools
ActiveUS8219649B2Simplified expedited seamless deploymentLower potentialDigital data processing detailsMultiple digital computer combinationsWeb applicationDatabase
A system and method for automatically deploying a change and configuration management software tool to a web application server includes launching a configurable wizard application programmed to solicit data from a user. The user is queried regarding a desired web application server and database connectivity authentication parameters. A location on the user's system of the desired web application server's installation package is identified. The user's input is integrated with the selected web application server. The change and configuration management software tool is automatically deployed to the desired web application server.
Owner:CA TECH INC
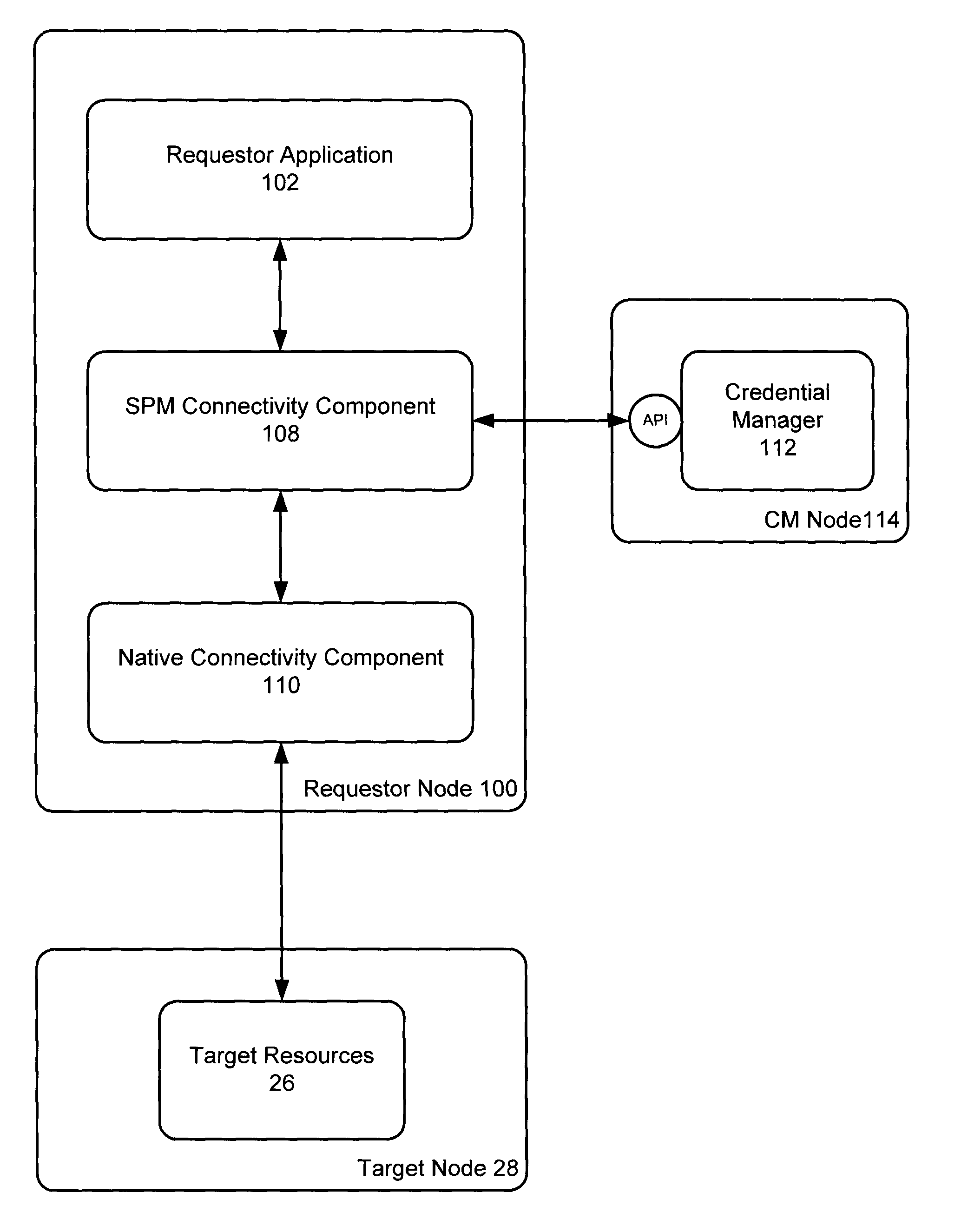
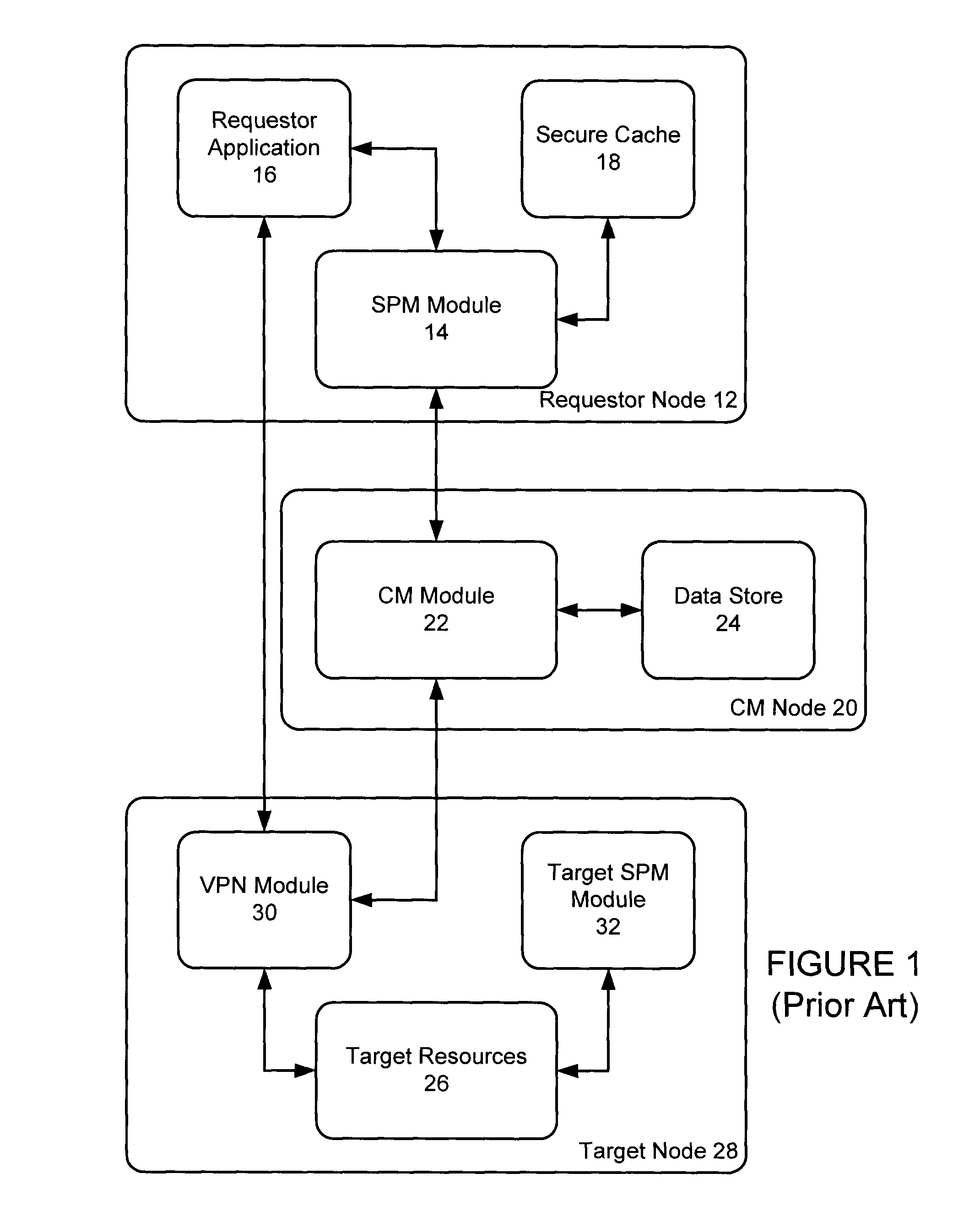
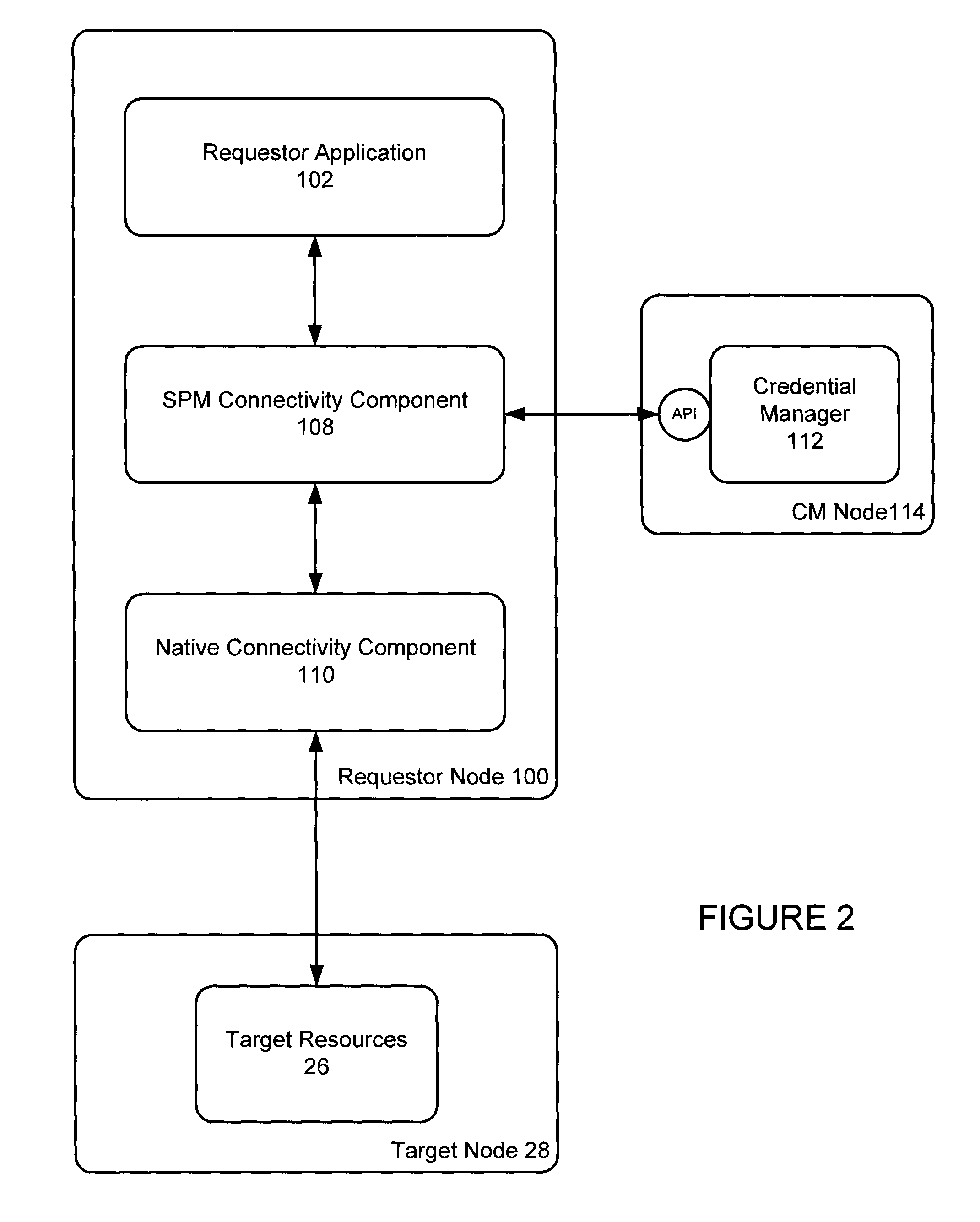
Authenticated database connectivity for unattended applications
A custom database connectivity component is deployed in conjunction with a native database connectivity component and a credential manager. The custom connectivity component has a requestor interface for communicating with a requestor application, a credential service interface for communicating with the credential manager, a native database connectivity interface for communicating with native connectivity components, and a decision engine for determining how to convert a request from a requestor to an appropriate API call to the credential manager. The custom connectivity component provides an authenticated and authorized database connection for a requestor application. The component transparently serves retrieves database, or other target resource, credentials on a real time basis, without requiring code changes to the requestor application.
Owner:IRDETO ACCESS
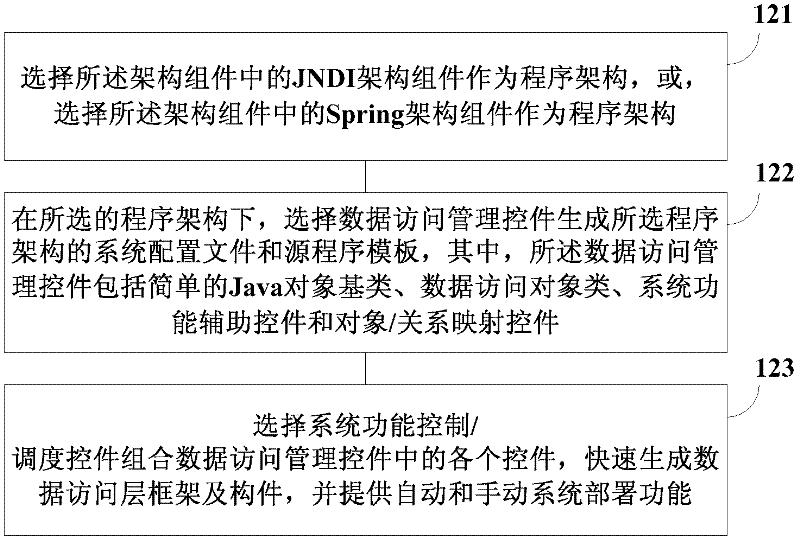
JDBC (java database connectivity) based data access layer building method and device utilizing same
ActiveCN102541996AImprove unityAchieve standardSpecial data processing applicationsSystem configurationSystem development
The invention provides a JDBC (java database connectivity) based data access layer building method and a device utilizing the same, which solve the problem that the system is complicated in configuration due to difference between the architecture of programs and the programming mode during development of the data access layer. The JDBC based data access layer building method includes: generating a JDBC based data access layer frame generating component which comprises an architecture component and function controls by integrating with a source opening component and packaging user-defined function members; selecting a program architecture according to the architecture component, selecting the corresponding function control according to the selected program architecture to generate system configuration files and source program templates applicable to the program architecture, and building a data access layer through relevant program configurations by the selected program architecture and the system configuration files and the source program templates thereof. By the generating component capable of generating the framework and members of the data access layer, complexity of system development is reduced and time thereof is shortened, and uniformity and standardization of development of the data access layer are realized.
Owner:DATANG SOFTWARE TECH
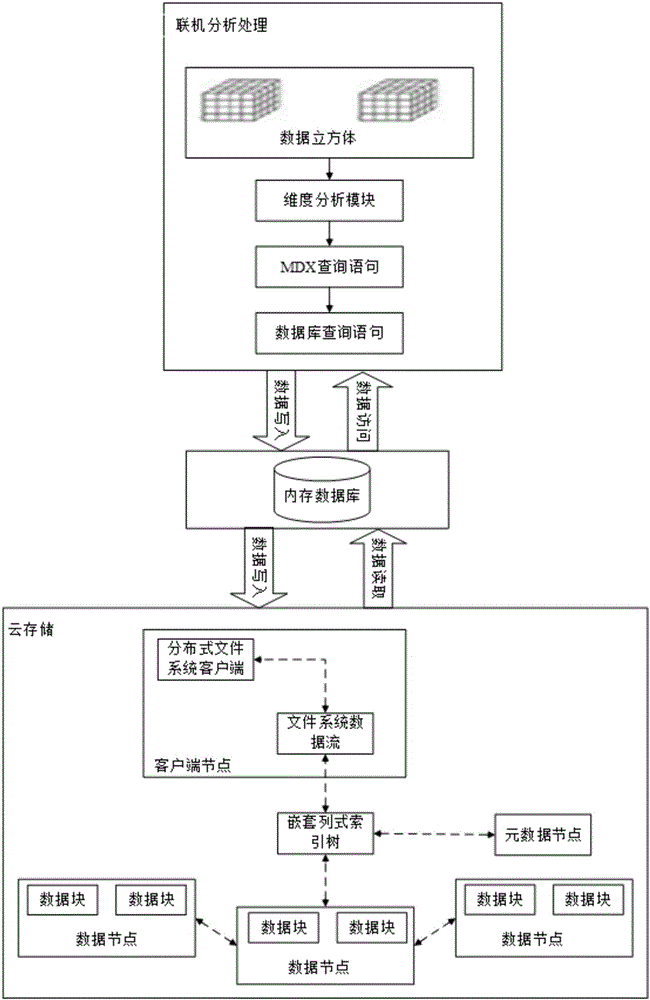
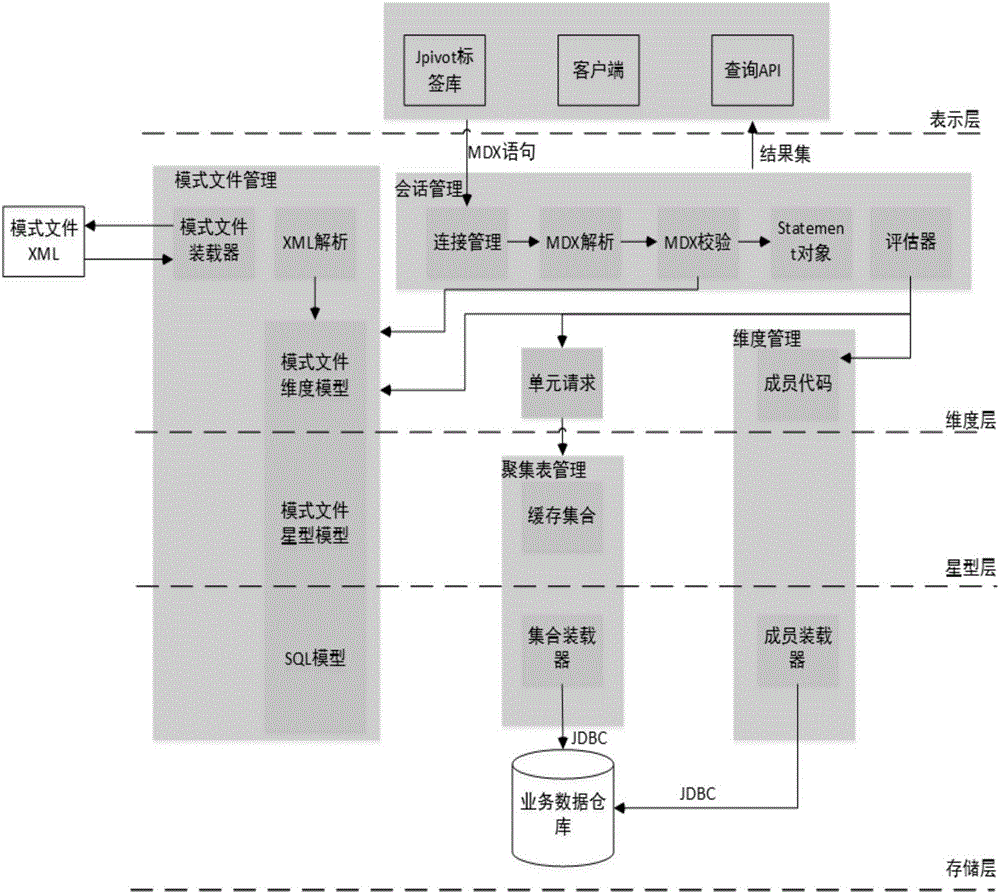
On-line analyzing and processing system of social security data on the basis of distributed data warehouse
InactiveCN106126604AImplementing the Unified Query InterfaceLoad balancingData processing applicationsSpecial data processing applicationsDistributed File SystemQuery language
The invention discloses an on-line analyzing and processing system of social security data on the basis of a distributed data warehouse. The on-line analyzing and processing system comprises a display layer, a dimensional layer, a star-shaped layer and a storage layer, wherein the display layers interacts with a multidimensional analysis server; the dimensional layer analyzes a MDX (Multidimensional Expressions) statement and executes query computation by the analyzed statement; the star-shaped layer manages the cache of an aggregation result; and the storage layer is in charge of receiving a SQL (Structured Query Language) statement emitted from the start-shaped layer, executing the SQL statement in the data warehouse and returning a result. The data warehouse of the system is realized through a distributed file system, and a distributed file system cluster is uniformly managed via a cloud computation platform to realize the load balancing of resources. By use of the system, through functional multilayer distribution, a uniform query interface for the distributed data warehouse which stores mass data is realized, and a multidimensional operation for a data cube is finished by a query way similar to JDBC (Java DataBase Connectivity).
Owner:SOUTH CHINA UNIV OF TECH
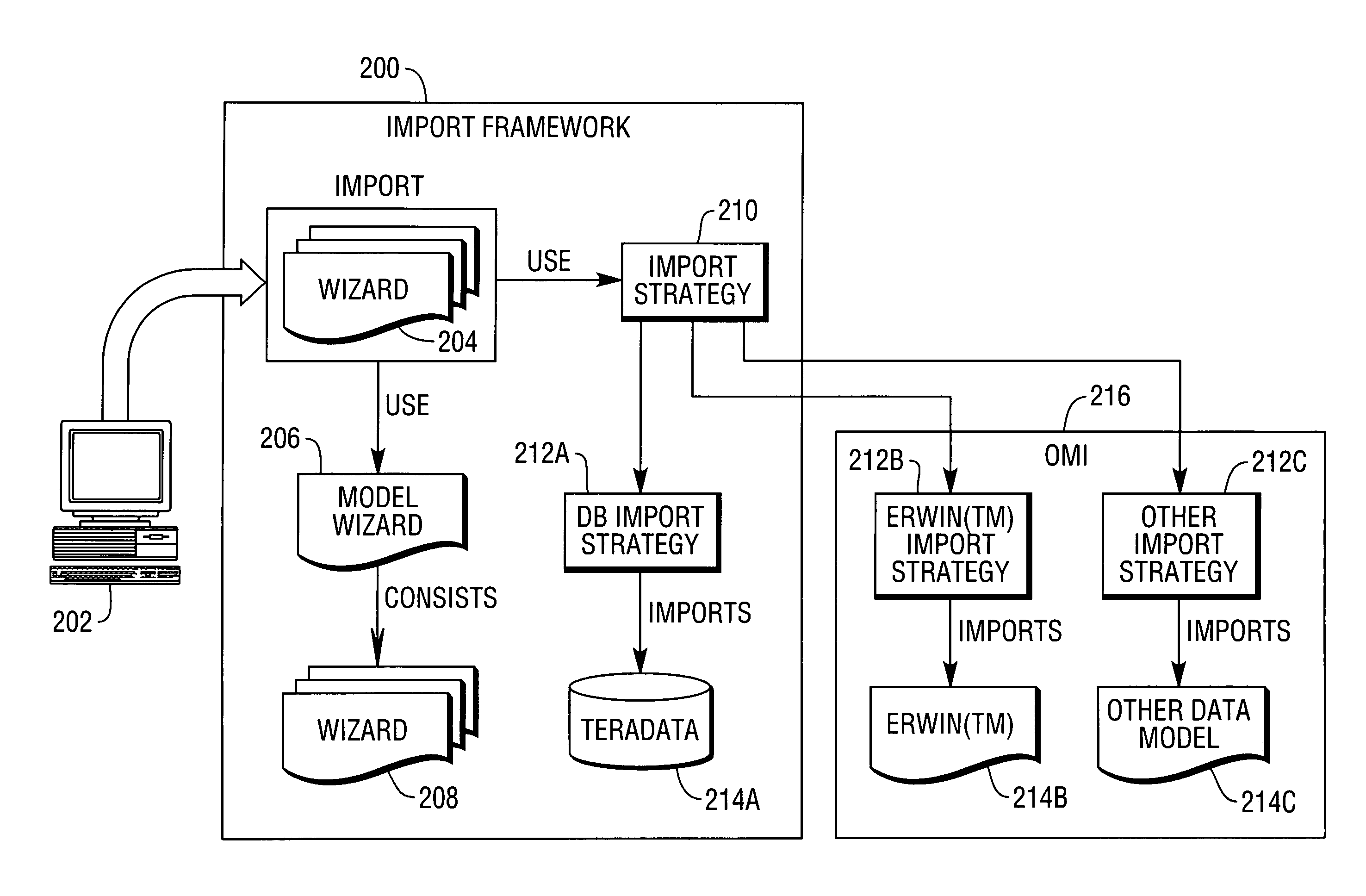
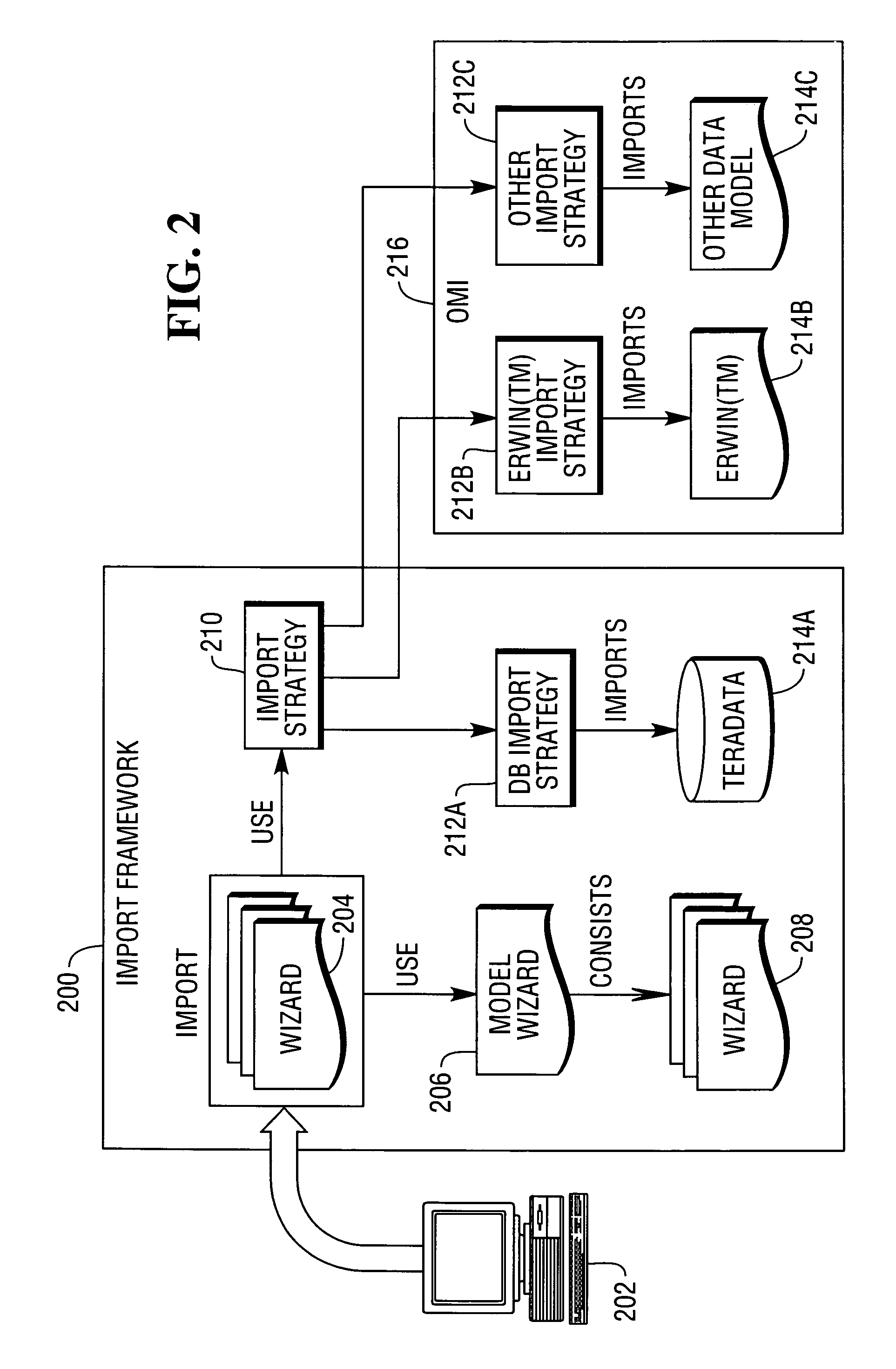
Open model ingestion for Master Data Management
ActiveUS20090164943A1Structured data retrievalSpecial data processing applicationsGraphicsGraphical user interface
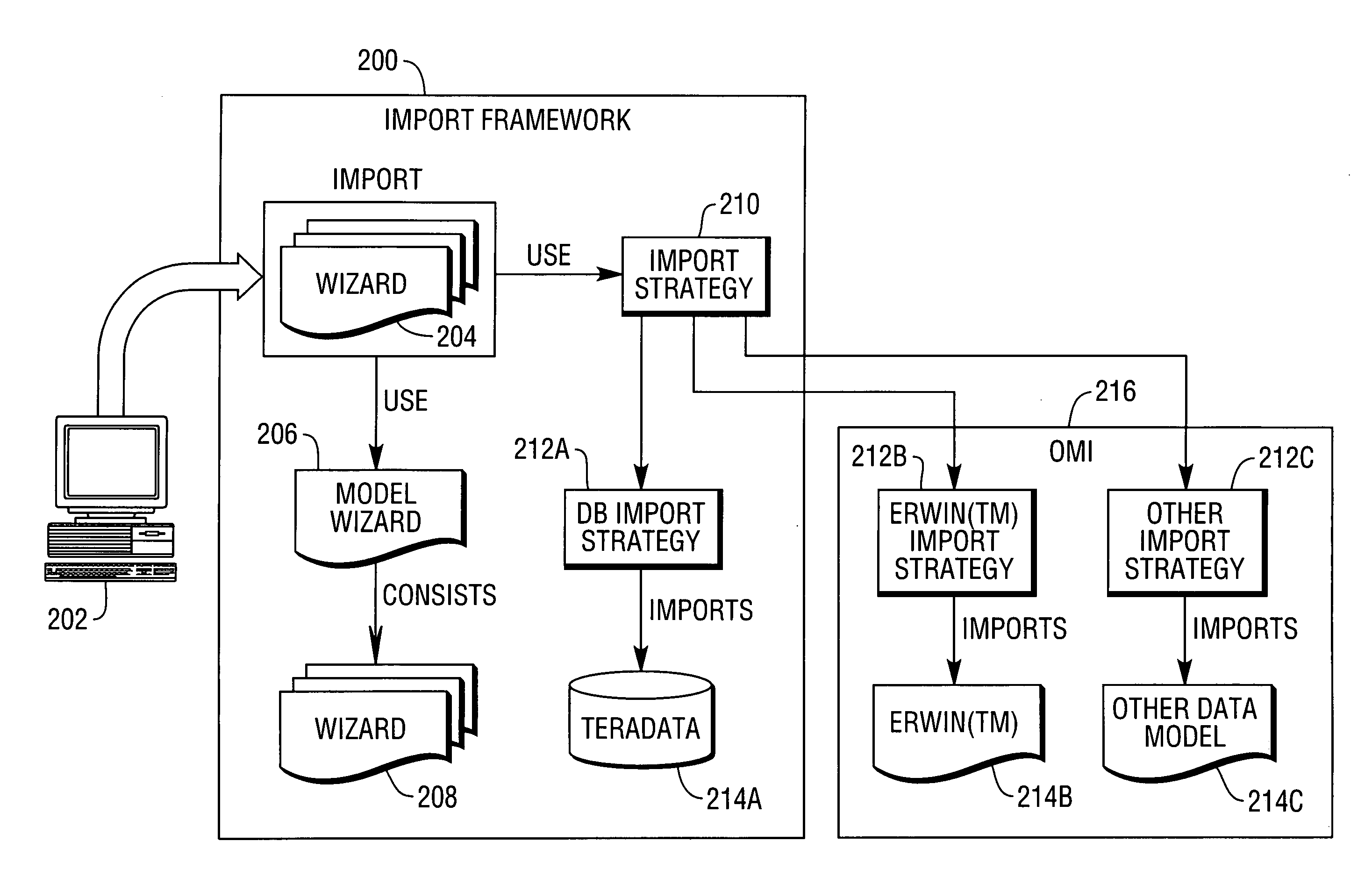
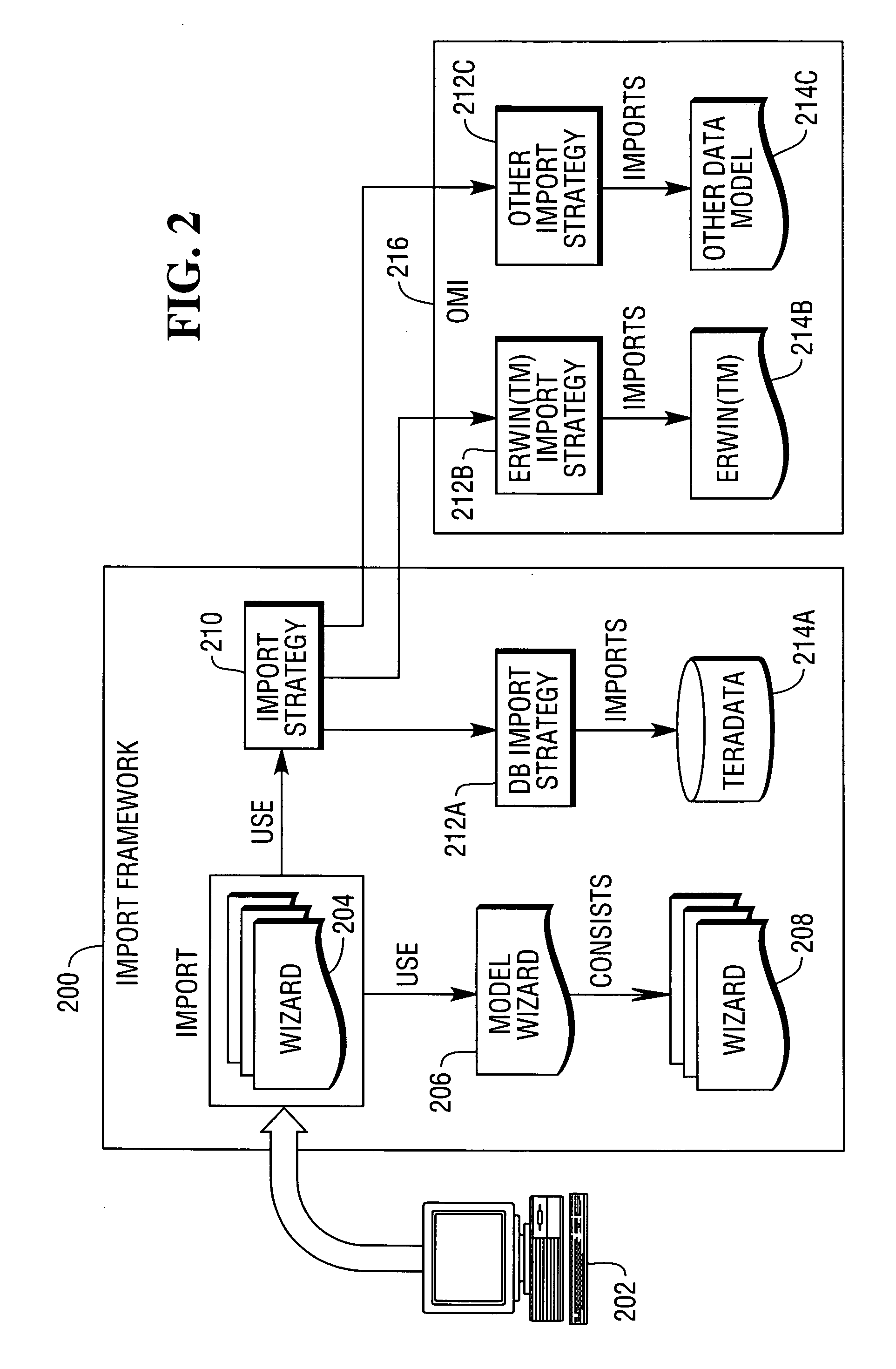
A method, apparatus, and article of manufacture provide the ability to import a first data model into a meta-data representation in one or more computers. An import wizard or graphical user interface is invoked and guides a user through a process of importing the first data model into the meta-data representation. A source is selected that specifies database connectivity information of a source database containing the first data model. A schema is selected from the selected source, from which tables will be imported into the meta-data representation. A list of all table names within the selected schema is retrieved and displayed. Tables are selected from the list of all table names to import into the meta-data representation. Table information, for all of the selected tables, is populated into the meta-data representation.
Owner:TERADATA
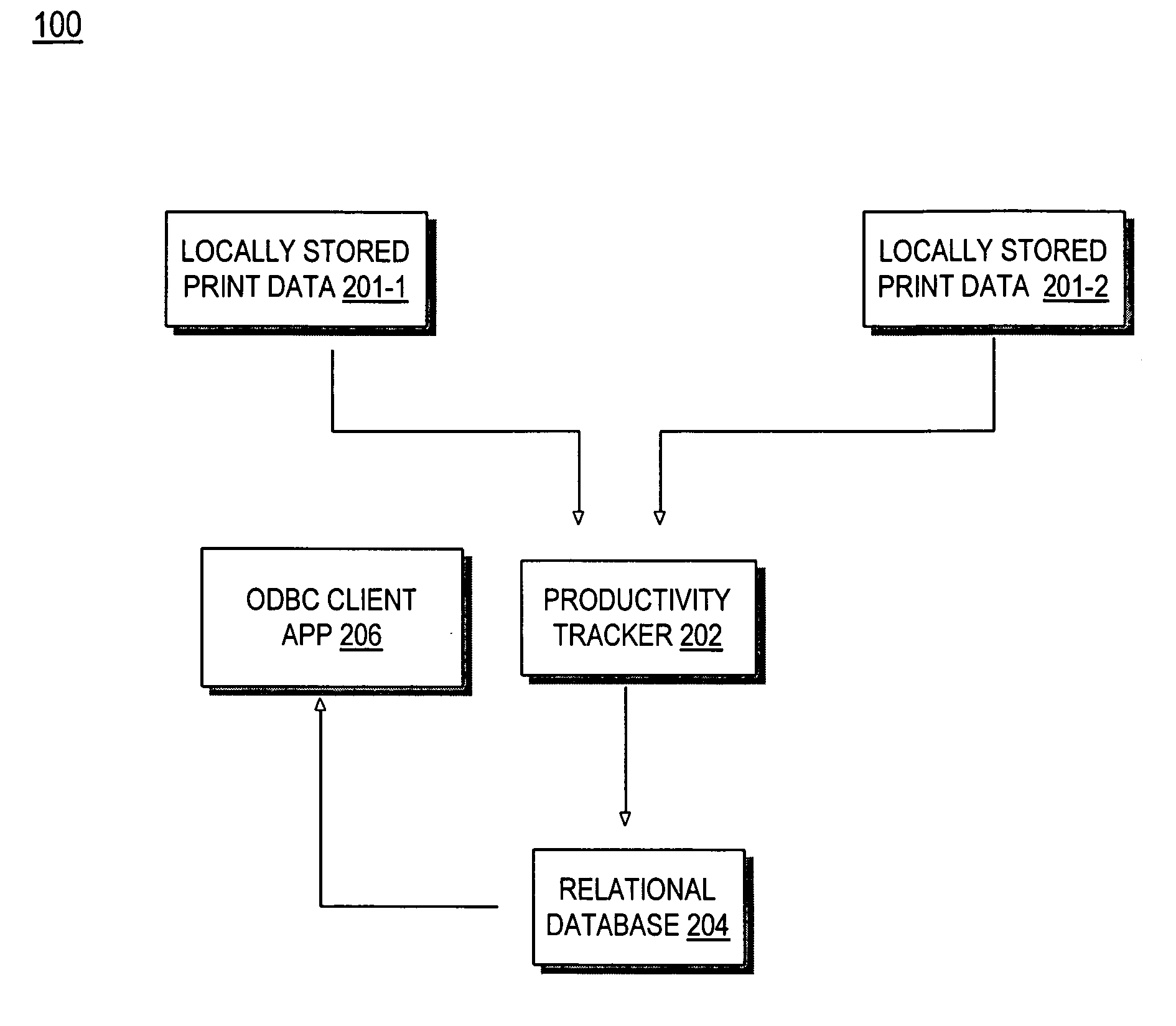
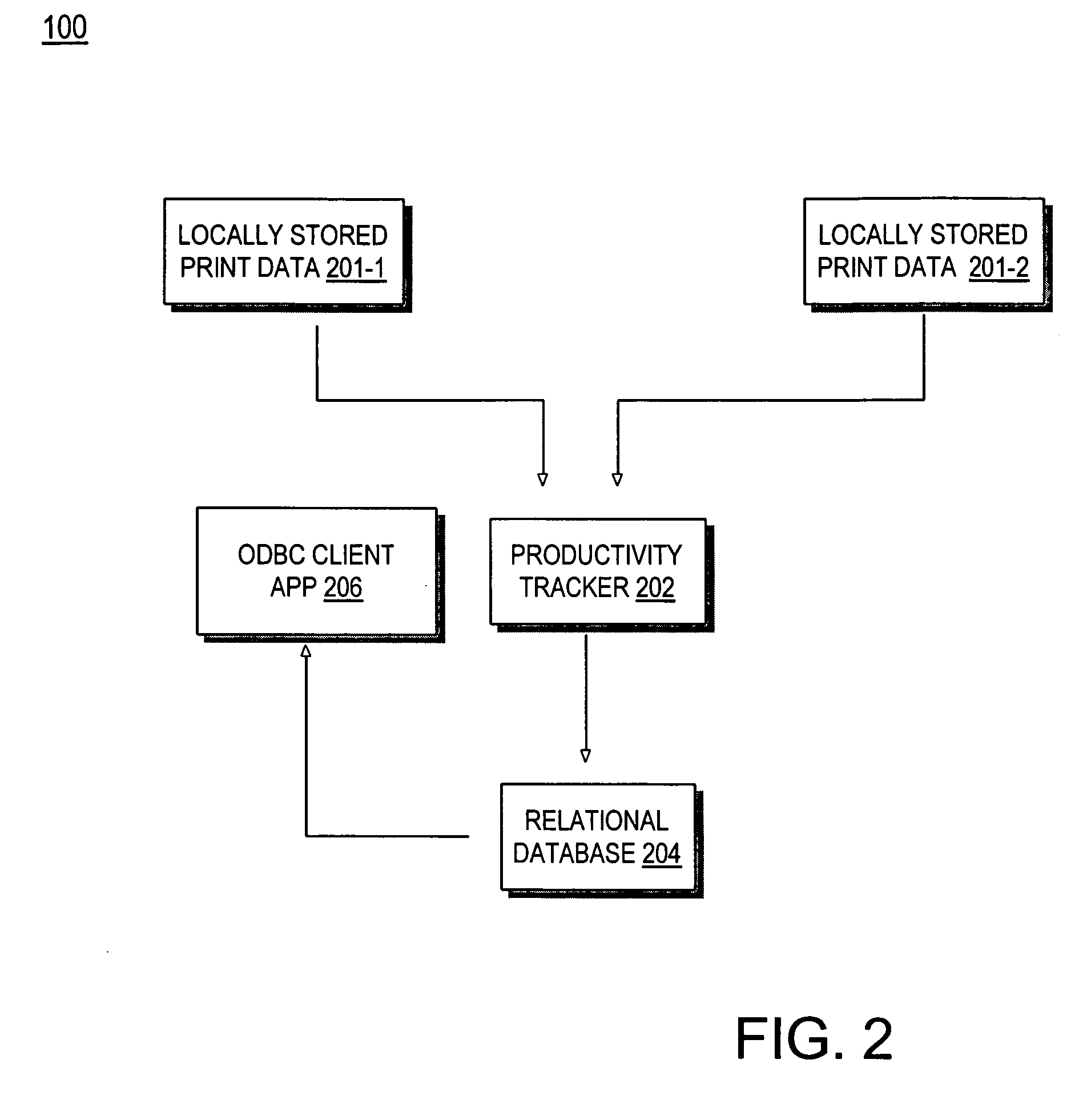
Productivity tracking for printer systems
A method for tracking printer productivity includes retrieving archived data stored on a remote printer that is connected to a network. The data is parsed and stored in a relational database. The data is retrieved from the database and used to generate a graphical representation of the data. The data may be represented as XML data and retrieving the data may include establishing a simple object access protocol (SOAP) connection between the printer system data and sending XML commands to the printer system. Storing the parsed data in a relational database may include establishing a Java database connectivity (JDBC) connection with a database server. The data is a log of events occurring on the printer system. The logged events may include status events indicating an operational status of the printer, job events indicating the beginning and ending of jobs, and intervention events indicating error status changes of the printer system.
Owner:INFOPRINT SOLUTIONS COMPANY LLC
Integrated task management systems and methods for executing rule-based operations
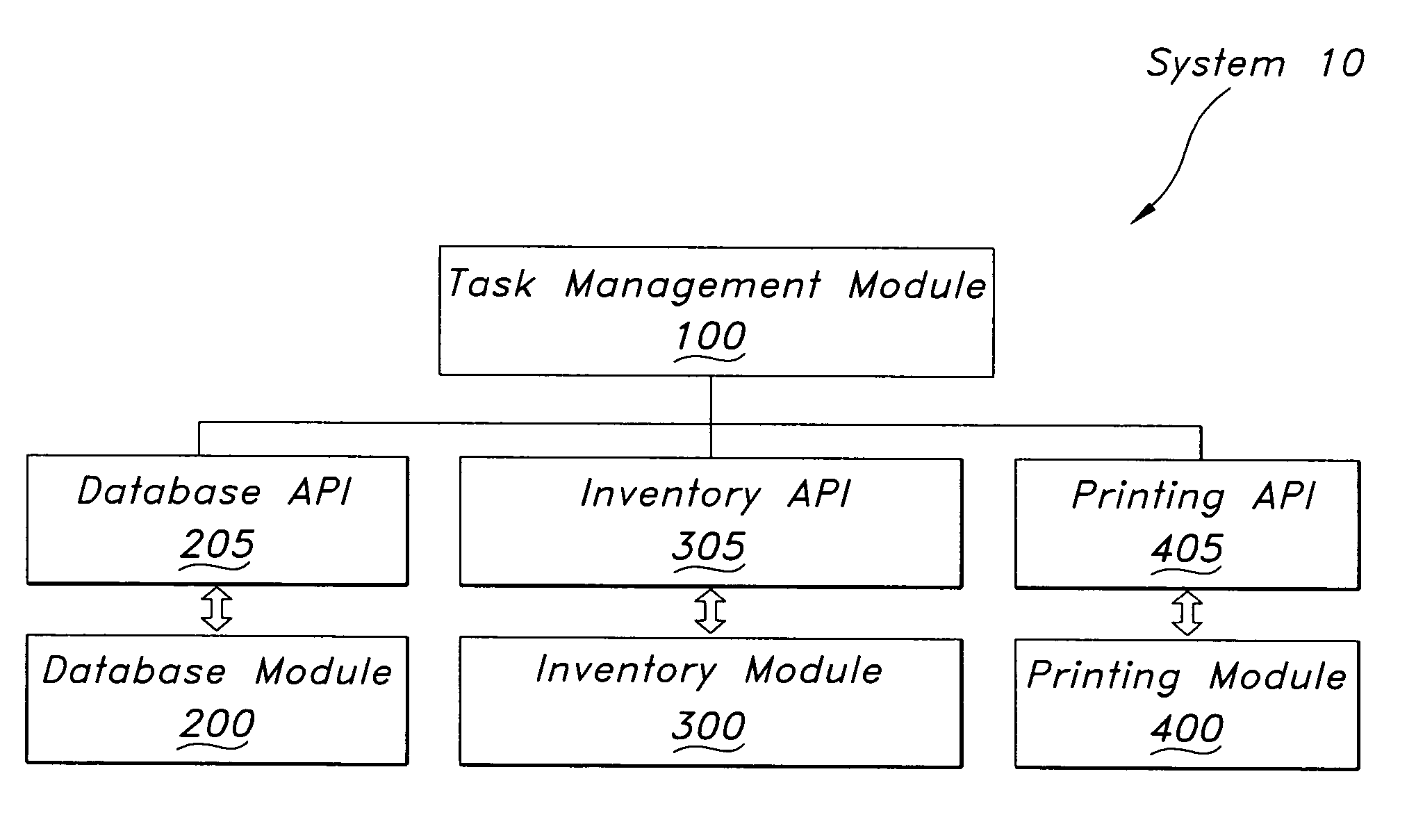
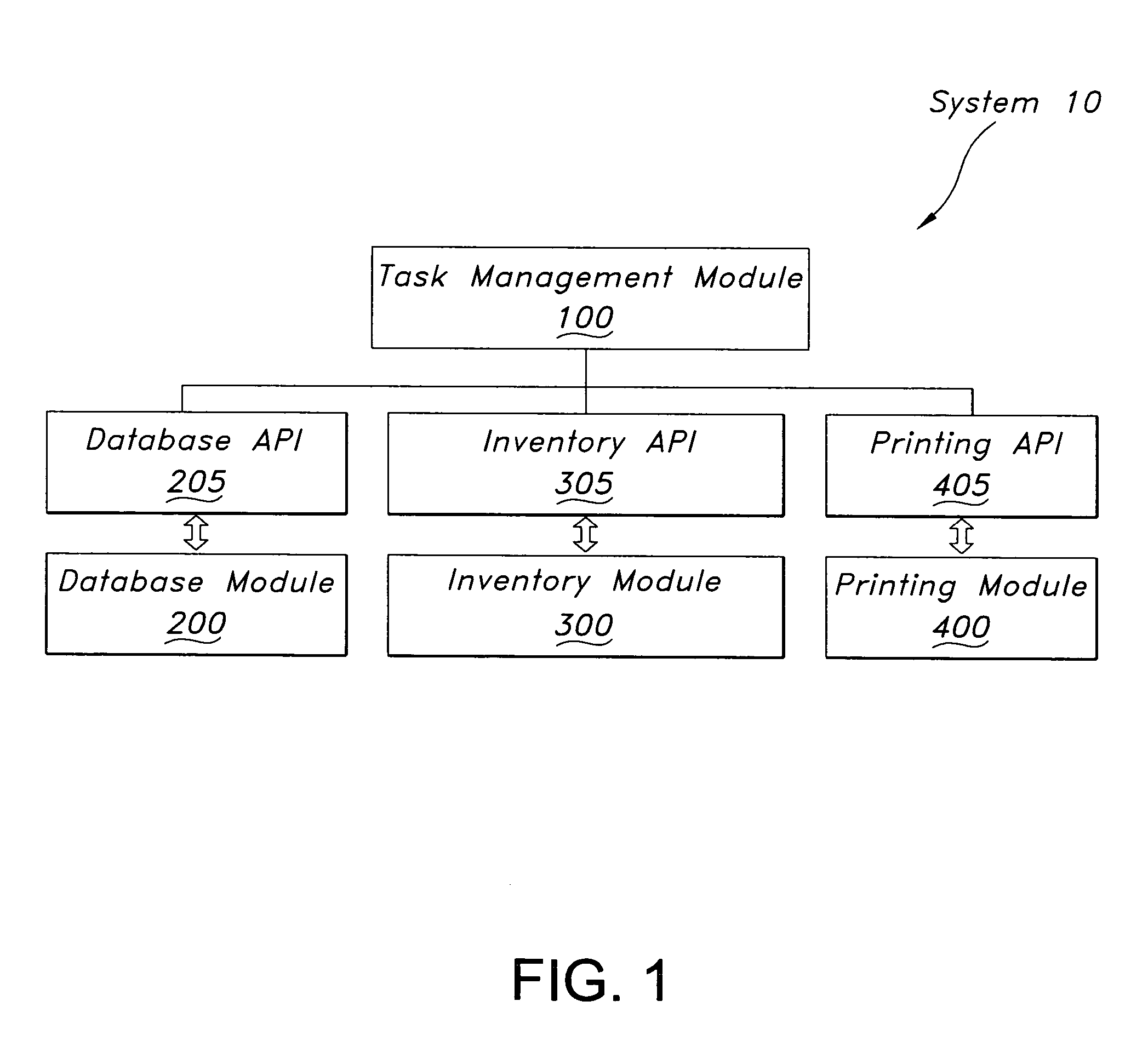
ActiveUS20050248806A1Digitally marking record carriersHand manipulated computer devicesSubject matterRemote computer
A system for integrating multiple software modules configured to produce output according to established business rules is provided. The system in one embodiment coordinates the printing of a variety of labels and reports according to a set of complex business rules. Complex output tasks may be distributed to remote computers in a network for optimum efficiency. The system may be configured to comply with one or more standard database connectivity standards in order to provide a generic interface with foreign systems. The method in one embodiment includes acquiring an input, sending a query to a database, retrieving business rules and associated tasks, and building scripts or commands for each task. This Abstract is provided to comply with the rules, which require an abstract to quickly inform a searcher or other reader about the subject matter of the application. This Abstract is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
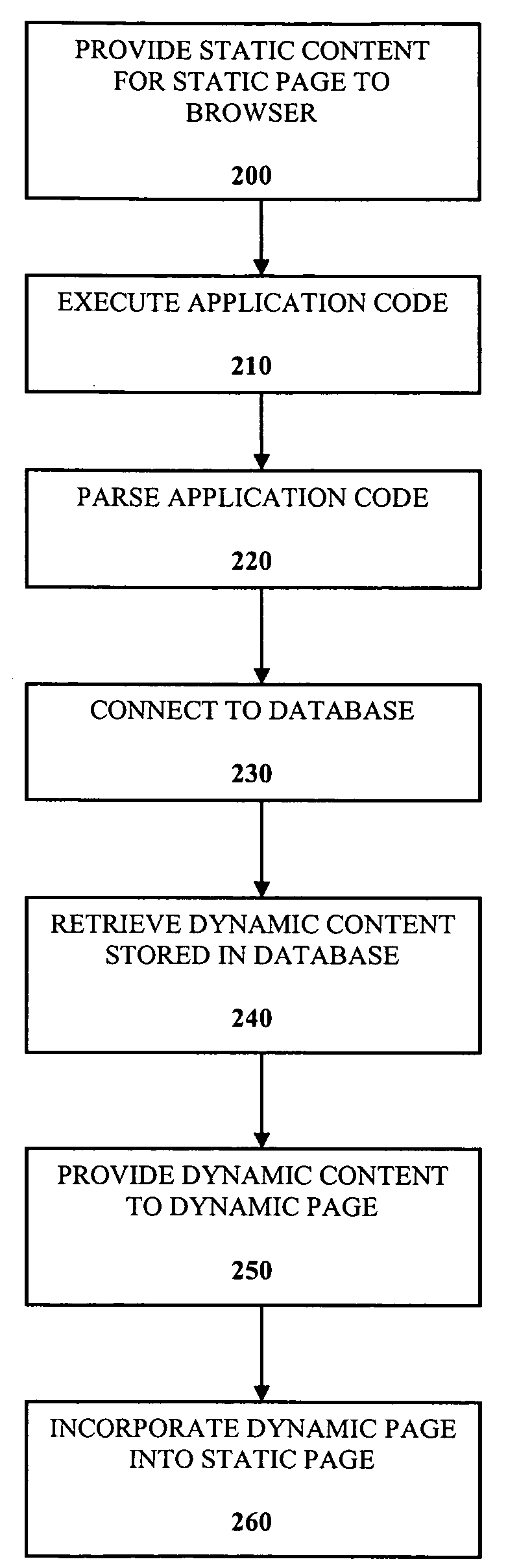
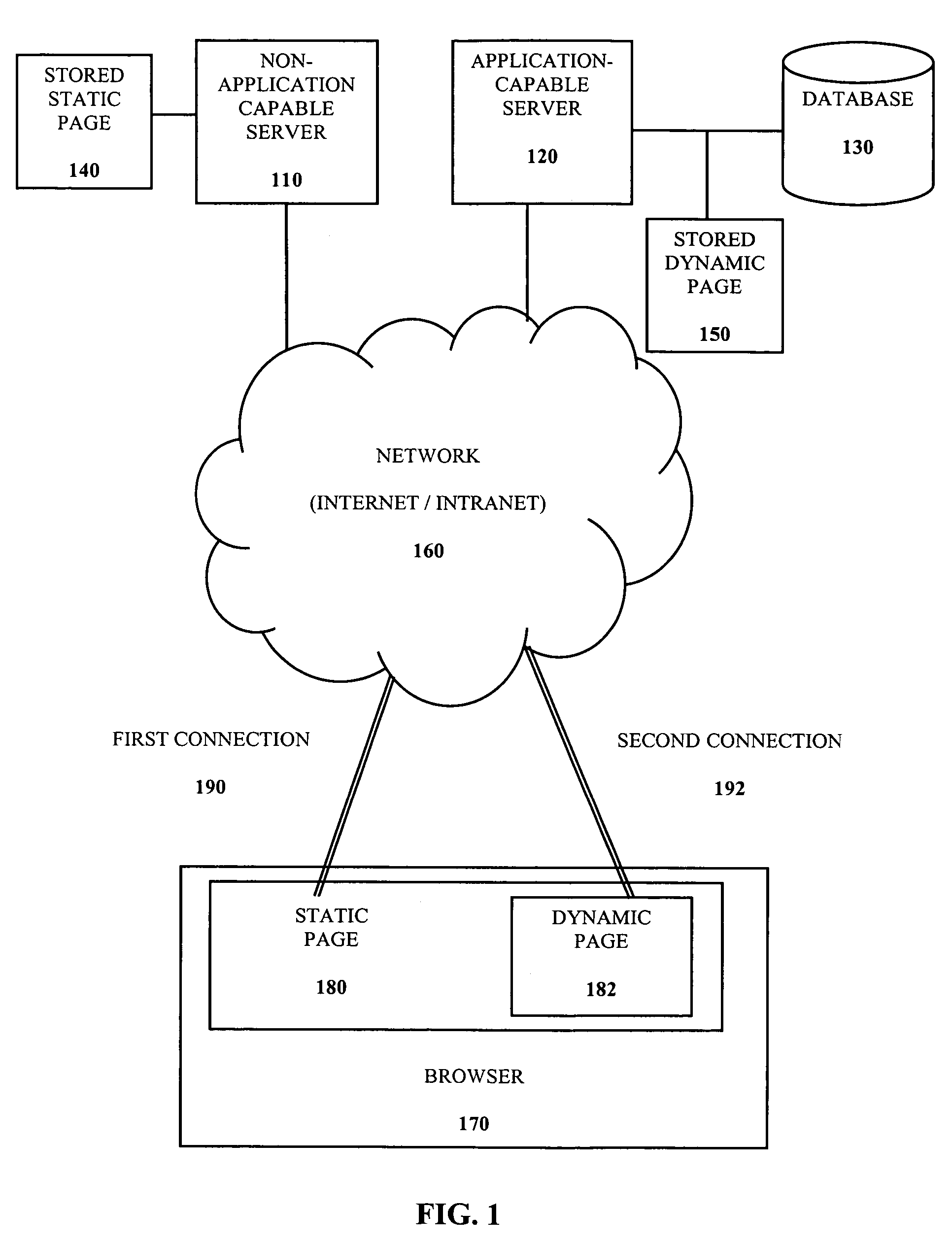
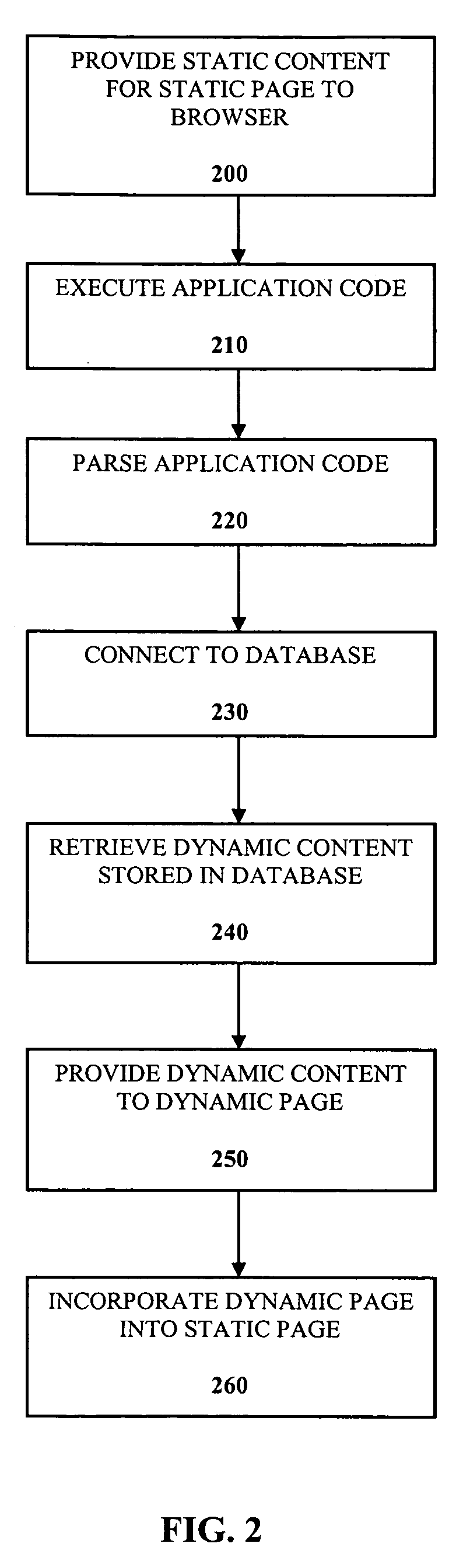
Dynamic content delivery to static page in non-application capable environment
InactiveUS7320028B2Multiple digital computer combinationsWebsite content managementApplication softwareDatabase
A system to provide dynamic content to a static page includes a database to store the dynamic content to be incorporated into the static page. A non-application capable server is provided to store the static page. The non-application capable server has no database connectivity and no ability to execute applications. A dynamic page is adapted to make a connection to the database and execute an application code. An application capable server is provided to store the dynamic page, to parse the application code and to connect to the database. The static page incorporates the dynamic page to provide the dynamic content to the static page.
Owner:INTEL CORP
Open model ingestion for master data management
A method, apparatus, and article of manufacture provide the ability to import a first data model into a meta-data representation in one or more computers. An import wizard or graphical user interface is invoked and guides a user through a process of importing the first data model into the meta-data representation. A source is selected that specifies database connectivity information of a source database containing the first data model. A schema is selected from the selected source, from which tables will be imported into the meta-data representation. A list of all table names within the selected schema is retrieved and displayed. Tables are selected from the list of all table names to import into the meta-data representation. Table information, for all of the selected tables, is populated into the meta-data representation.
Owner:TERADATA
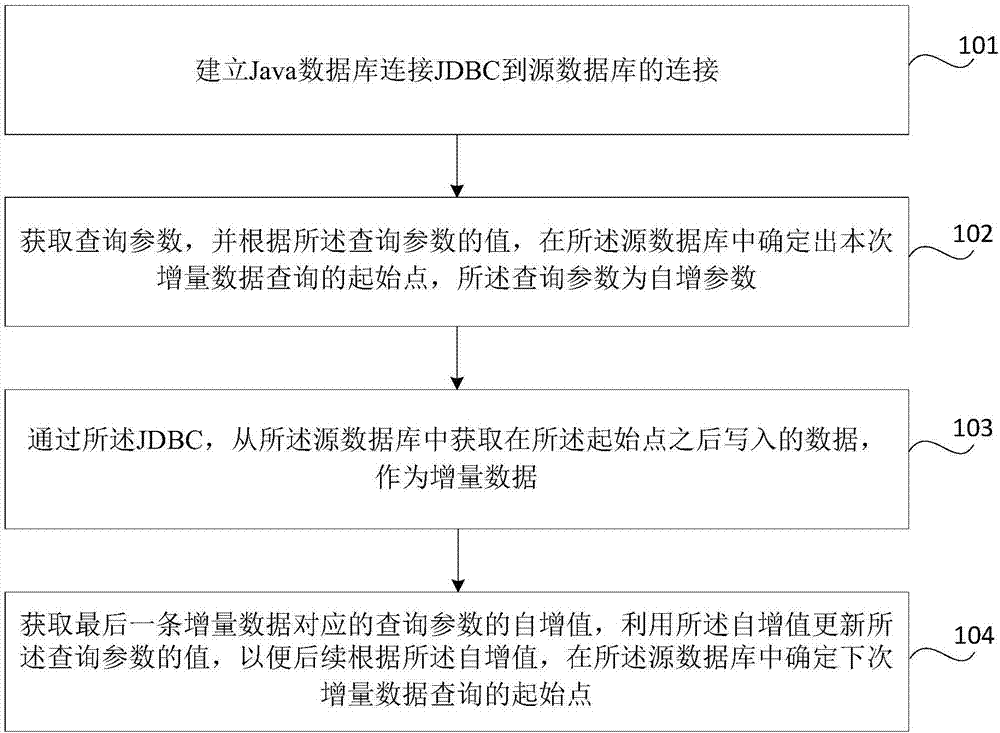
Incremental data query method and device, storage medium and electronic equipment
InactiveCN108009207AEnsuring Extraction PerformanceImprove compatibilityDatabase management systemsSpecial data processing applicationsComputer compatibilityData query
The invention relates to an incremental data query method and device, a storage medium and electronic equipment. The method includes the steps: establishing connection from JDBC (Java database connectivity) to a source database; acquiring query parameters and determining an incremental data query starting point in the source database according to values of the query parameters; acquiring data written after the starting point as incremental data from the source database through the JDBC; acquiring the auto-increment value of the query parameter corresponding to the last incremental datum, updating the values of the query parameters by the auto-increment value, and subsequently determining the starting point of next incremental data query in the source database according to the auto-increment value. The query parameters are auto-increment parameters. Therefore, compatibility of an incremental data query scheme and data extraction performance can be improved.
Owner:NEUSOFT CORP
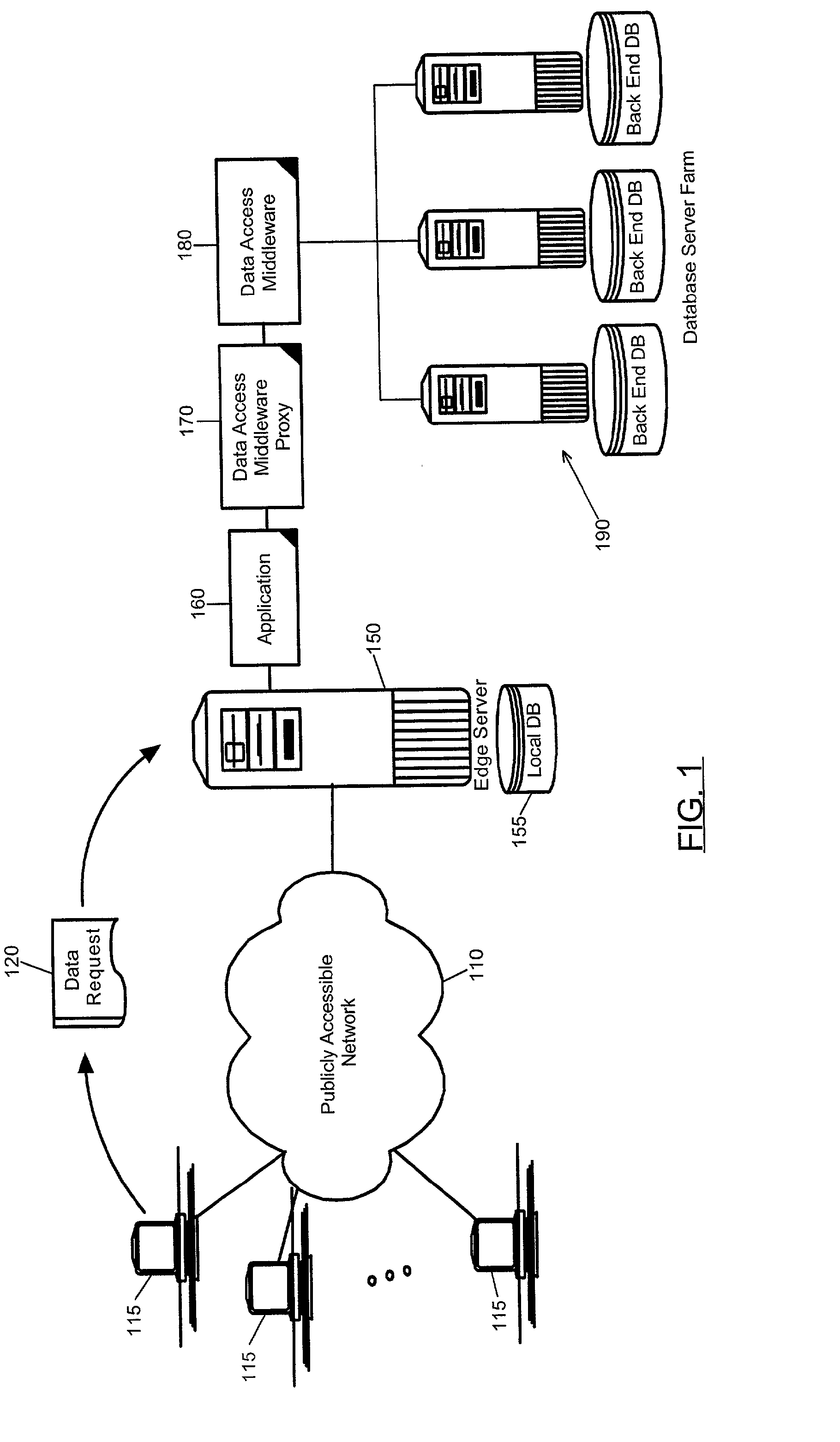
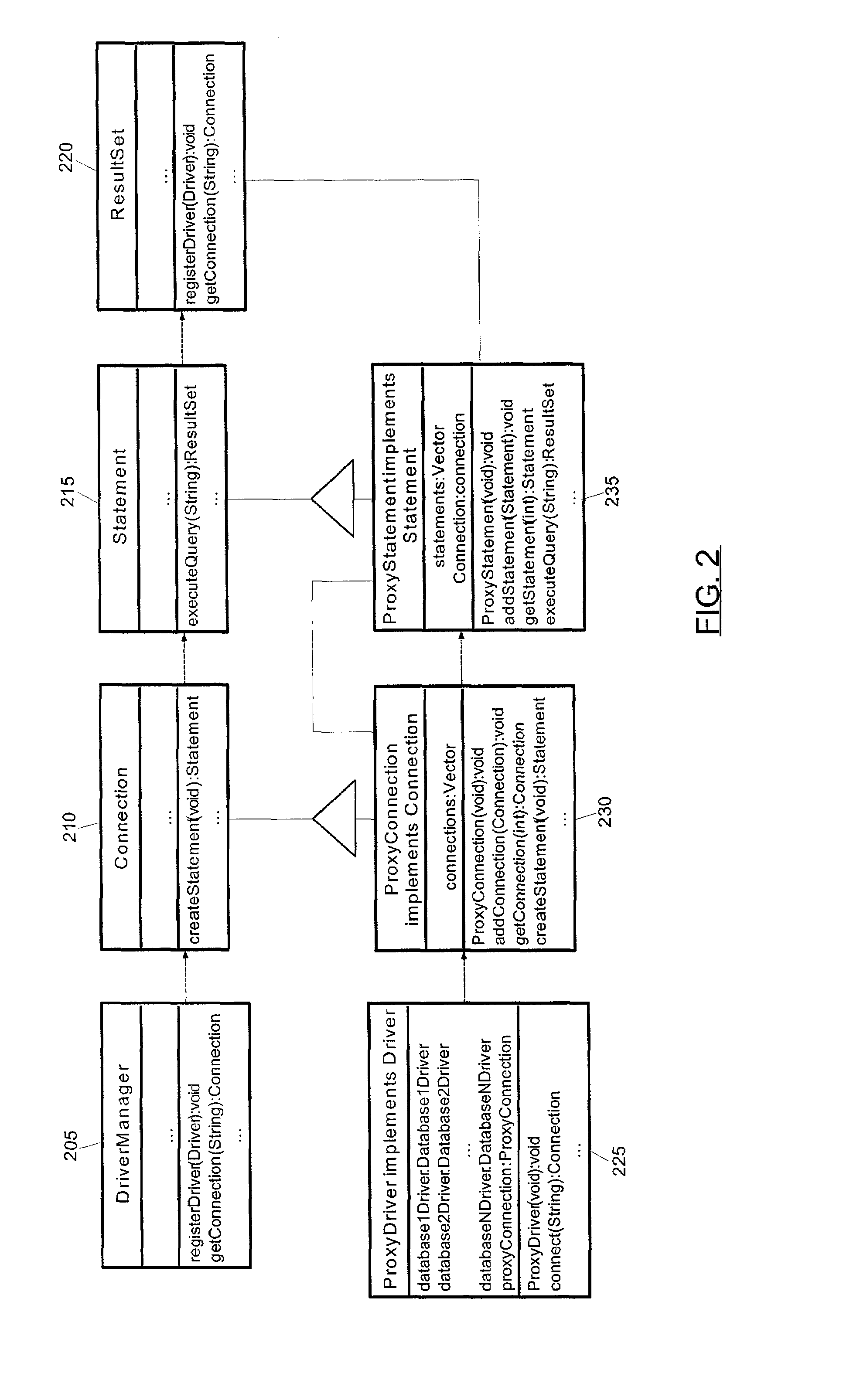
Edge deployed database proxy driver
An edge-deployed database proxy. A database access system which has been configured with the database proxy can include a universal database connectivity driver having a first exposed interface through which access to a database server can be provided; a database proxy driver registered with the universal database connectivity driver; and, a database driven application programmatically linked to the database proxy driver. Significantly, the database proxy driver can have a second exposed interface which conforms with the first exposed interface of the universal database connectivity driver. The database proxy driver further can have a configuration for invoking at least one auxiliary task in addition to providing access to the database server through the first exposed interface of the universal database connectivity driver.
Owner:IBM CORP
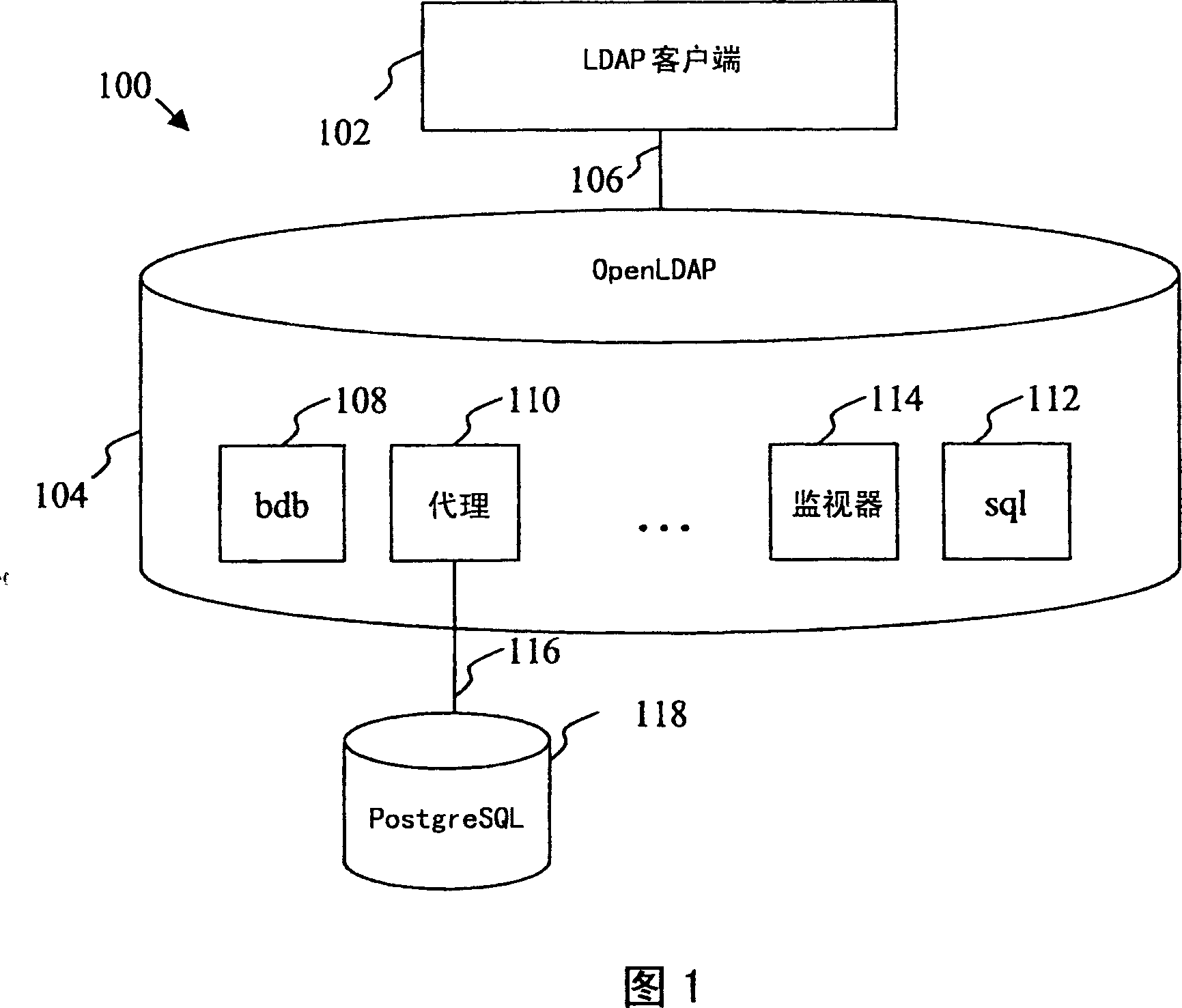
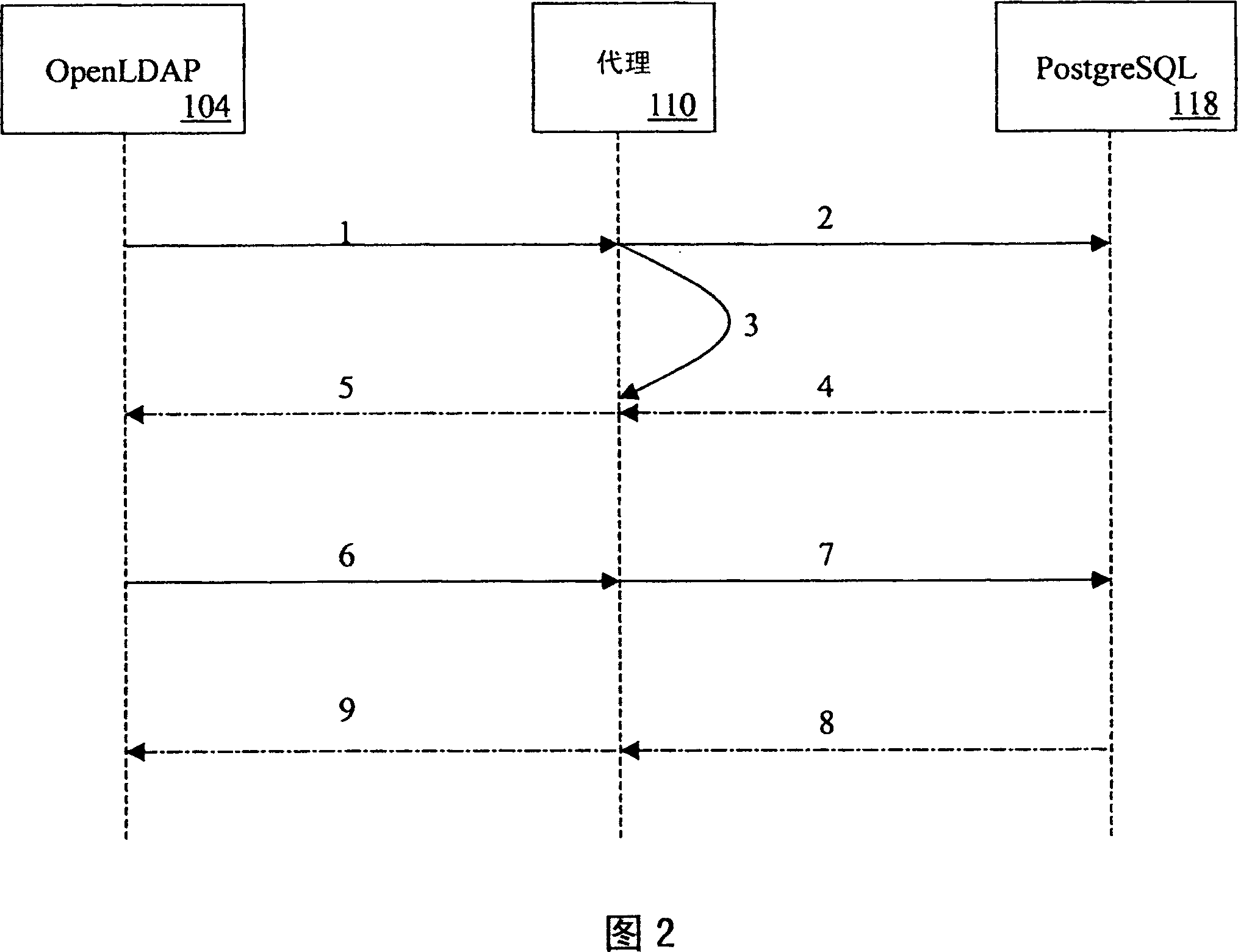
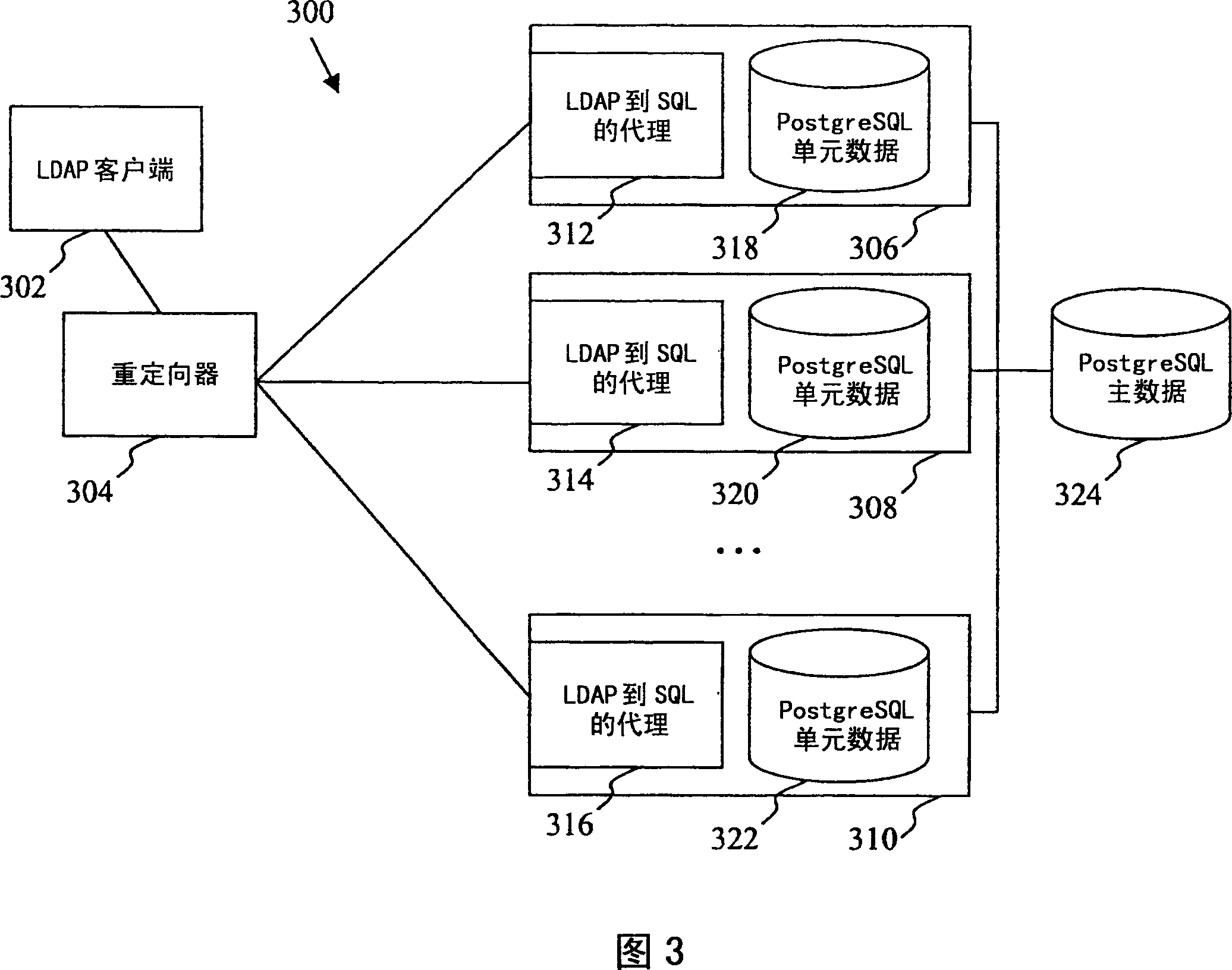
LDAP to SQL database proxy system and method
An LDAP to SQL proxy to adapt a relational database as a directory service for an LDAP client is provided. The database may be defined in accordance with a database schema which is external to an LDAP server serving the LDAP client. The proxy comprises LDAP to SQL query and response mappings preferably for a reduced set of LDAP operations. The proxy may comprise a mechanism to maintain a plurality of persistent database connections to reduce query processing overhead. The proxy may further be adapted to maintain a plurality of persistent connections to each of at least two alternative databases for executing queries to provide enhanced failsafe operations. A plurality of LDAP to SQL proxied databases may be configured for sharing query loads to enhance scalability and performance.
Owner:RES IN MOTION LTD
Method and device for achieving uniform control management of computing resource and object authority
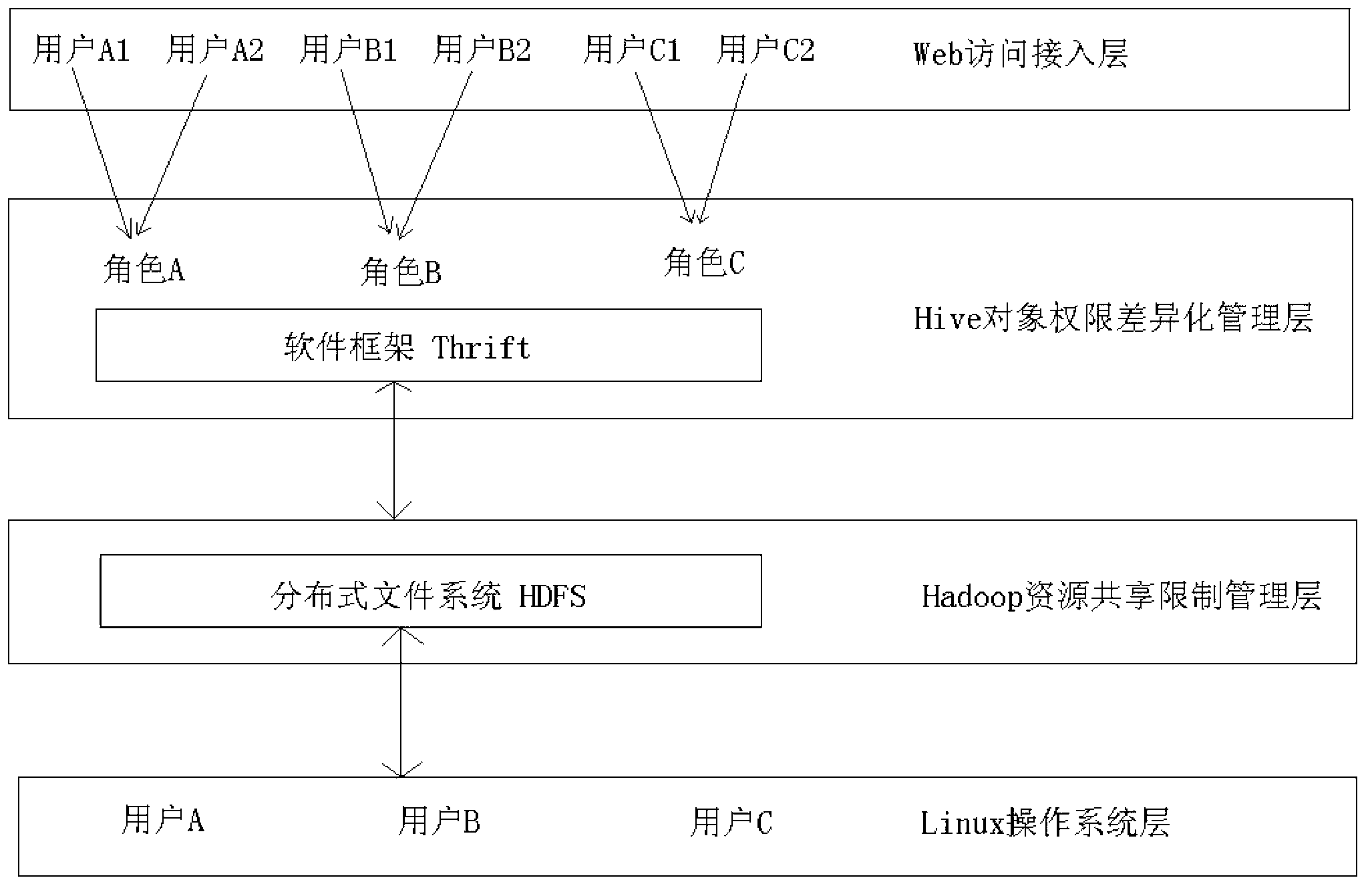
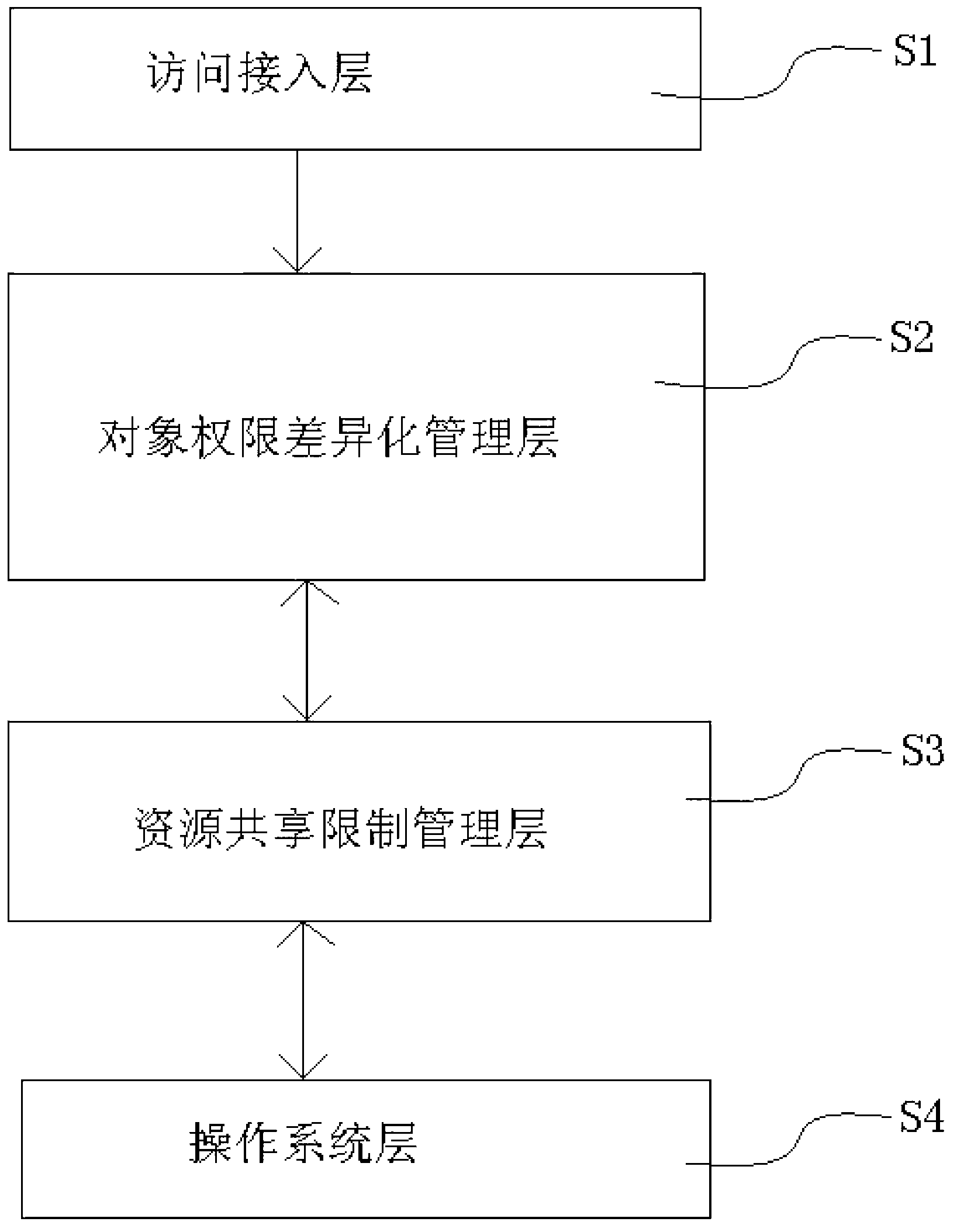
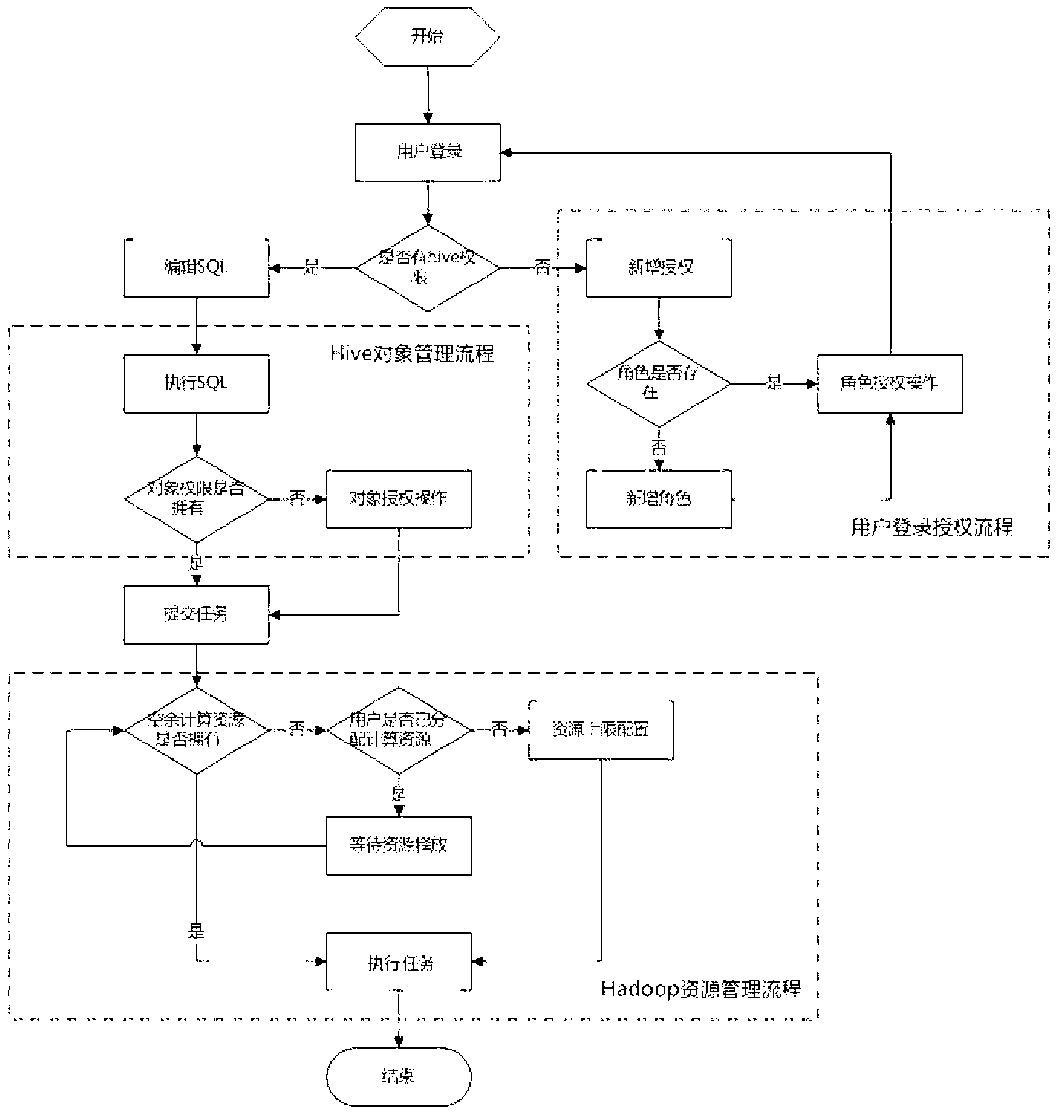
InactiveCN102917006AEasy to handleRealize unified control and managementTransmissionSpecial data processing applicationsDatabase connectivityRights management
The invention discloses a method and a device for achieving uniform control management of a computing resource and an object authority, and aims at providing application program which is capable of effectively and rapidly processing a huge data set of a data cluster, and a method and a device for achieving uniform control management of the computing resource and the object authority of the data set. The method comprises the following steps: the step of differentiated management of the object authority: authorizing an object to a Hive role, providing a sole Hive role port for each Hive role, starting a hive server interception by a linux system user through the Hive role port corresponding to the linux system user; configuring an external access user by a JDBC (java database connectivity) or a Thrift mode, appointing the Hive role port to be connected with a Hive object, and then carrying out a data retrieval request sentence. The device comprises a differentiated management layer of the object authority, a resource sharing restrict management layer, an operation system layer and an access layer. The method and the device disclosed by the invention are mainly applied to a resource and authority management technology.
Owner:杭州斯凯网络科技有限公司
Knowledge archival and recollection systems and methods
ActiveUS20080059531A1Digital data processing detailsDigital computer detailsDatabase serverData acquisition
A knowledge archival and recollection system accessible by a user, comprising: a data acquisition module in communication with a database server, a file archive and a database connectivity module; a data presentation module in communication with a report module and a search module; a timing module in communication with the database server; an automatic billing module in communication with a report module and database server; a messenger monitor module in communication with the database server, and the file archive; a database connectivity module in communication with the data acquisition module, the file archive, the database server, the report module, the search module, the automatic billing module, the timing module and the messenger monitor module; the system gathers user activity data and files accessed by user through the data acquisition module and archives the data and files on the database server and file archive for retrieval by each user.
Owner:APPLIEDE
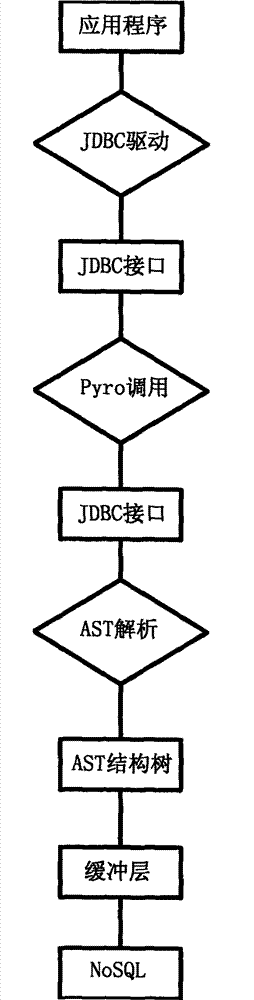
NoSQL (not only SOL) based medical information system database implementation method
InactiveCN103761265AImprove performanceImprove scalabilitySpecial data processing applicationsExtensibilityRapid access
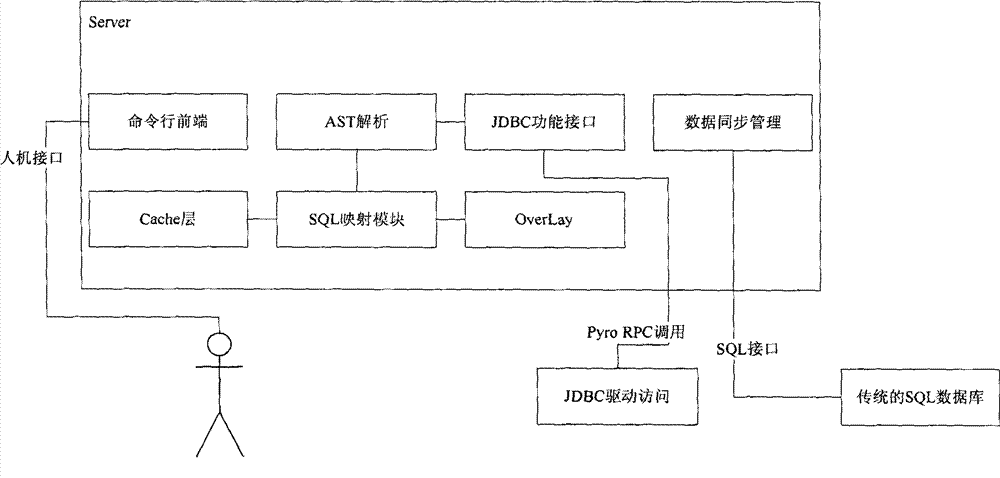
The invention discloses a NoSQL (not only SQL) based medical information system database implementation method. The implementation method includes the steps that A, an application program is driven to be connected to a JDBC (java database connectivity) interface through JDBC; B, the JDBC interface is called and connected to a Server module through Pyro; C, the Server module performs AST (glutamic oxalacetic transaminase) analysis upon SQL (structured query language) to obtain an AST structure tree; D, the AST structure tree is analyzed, if an association list is obtained, an Overlay operation is performed, and if an independent list is obtained, a Cache operation is performed; E, the AST structure tree is converted to form an executing script; F, the executing script is mapped to an NoSQL database through an API (application program interface). By the application of the implementation method, shortcomings in the prior art can be overcome, and rapid access with high performance, high expandability and a high-redundancy database can be realized.
Owner:上海起维信息科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com