Patents
Literature
34results about How to "Ensure safe distribution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
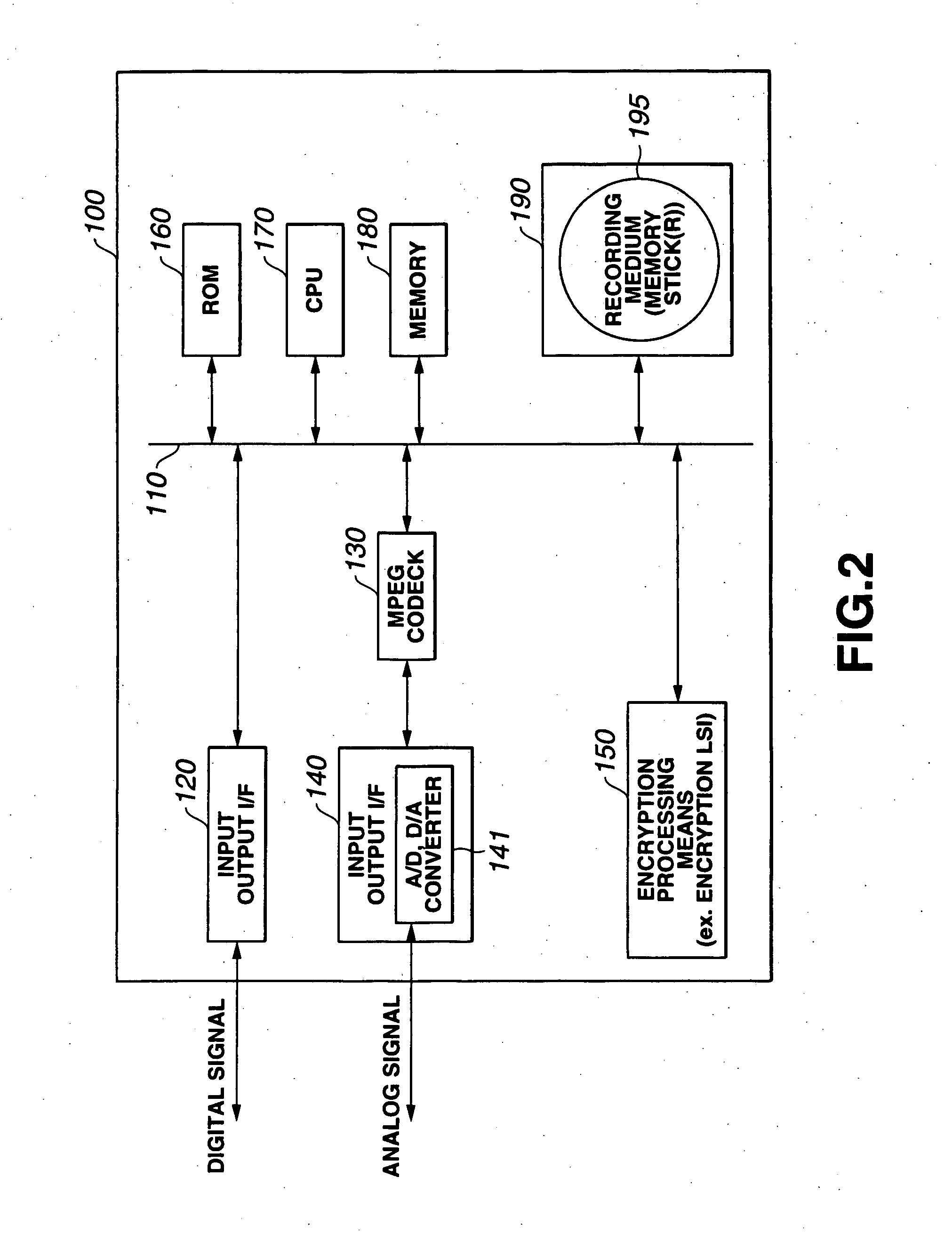
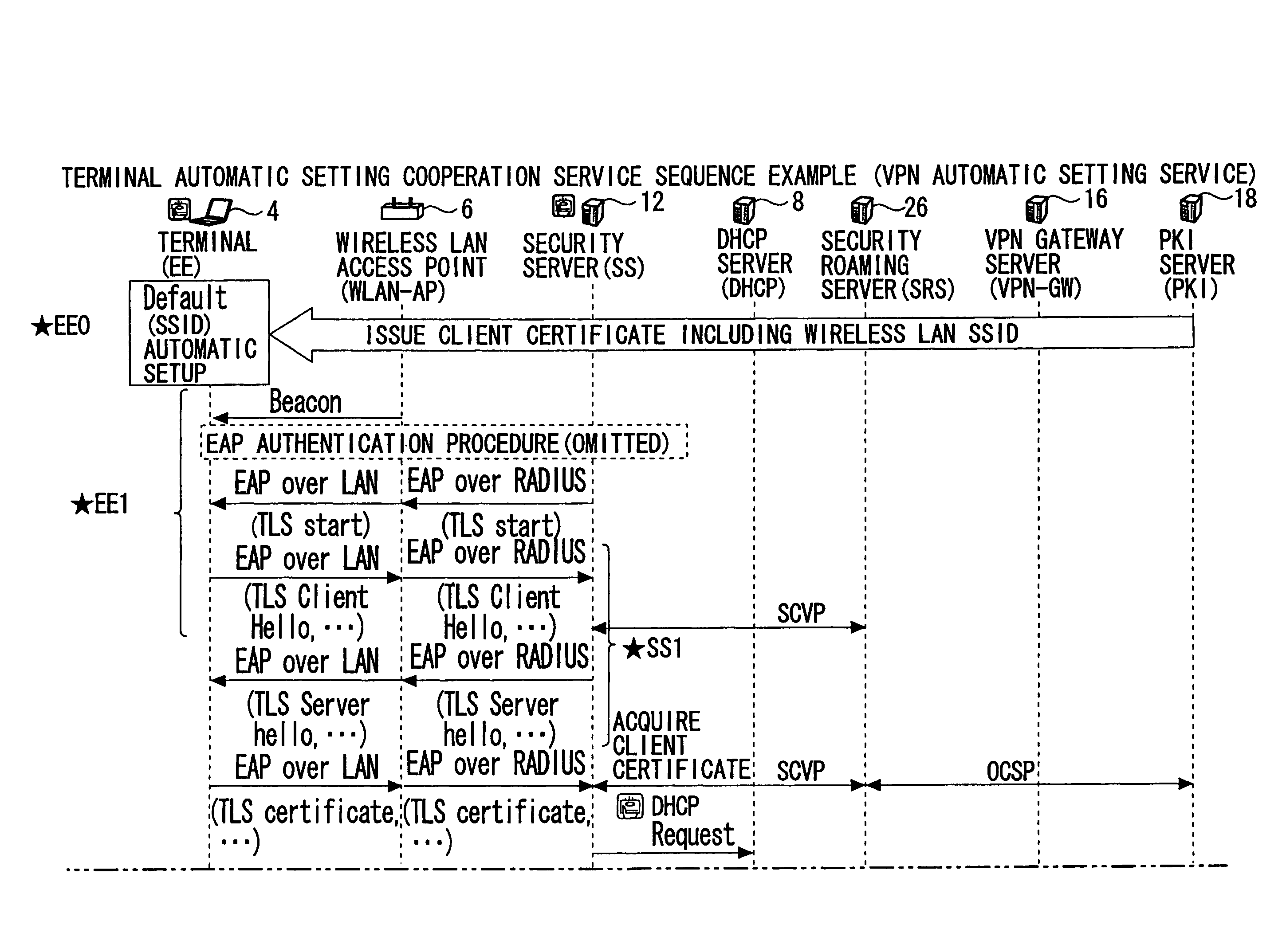
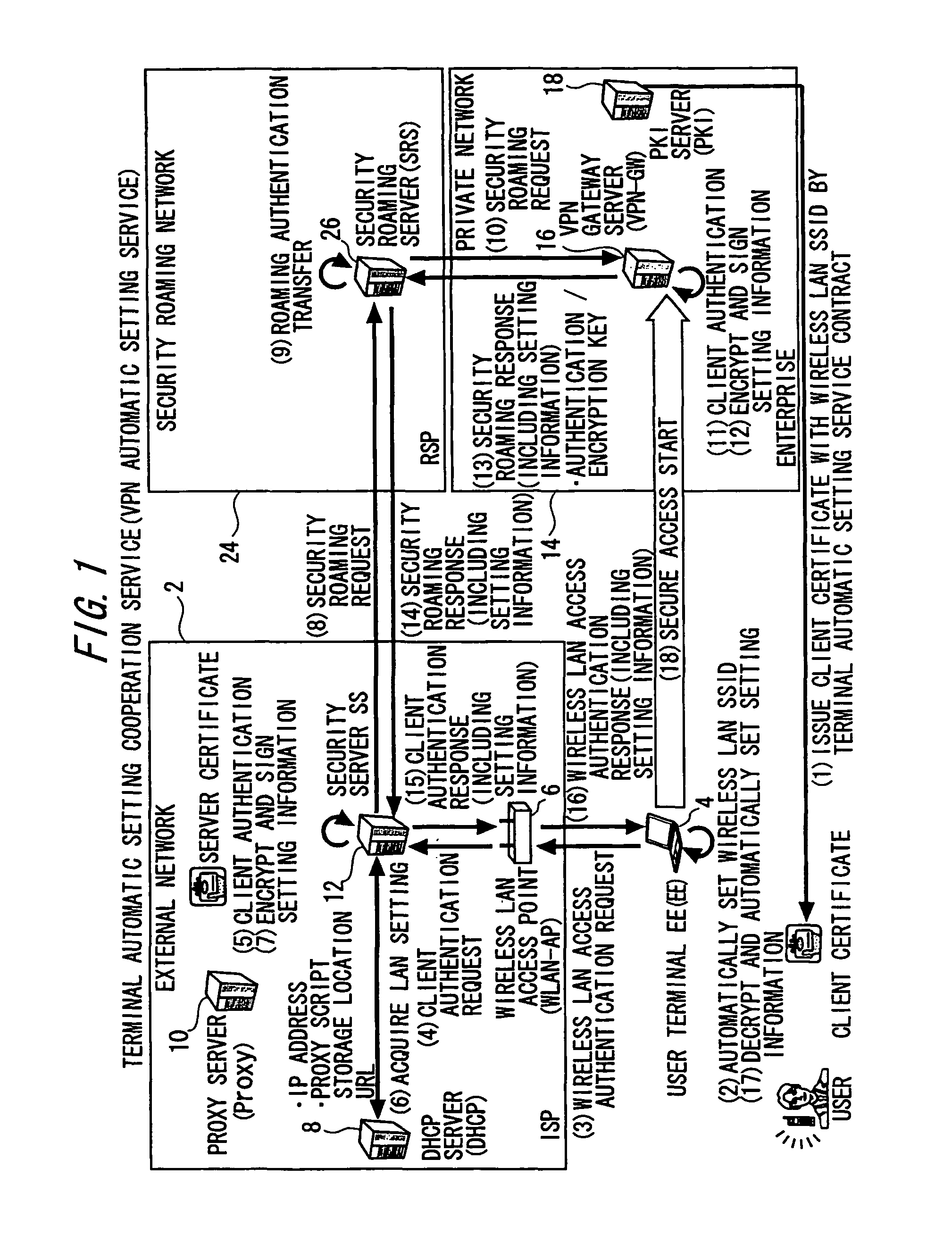
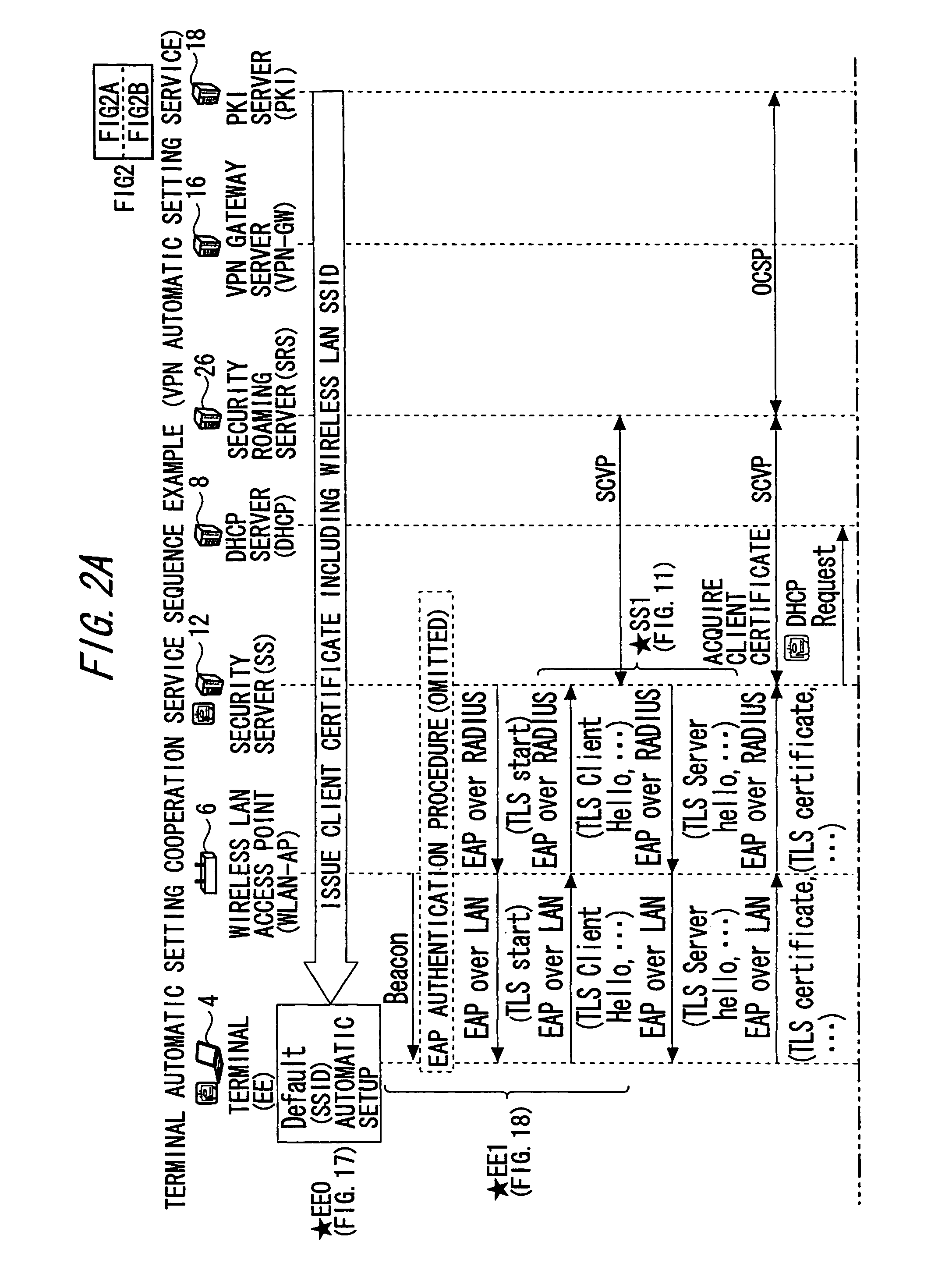
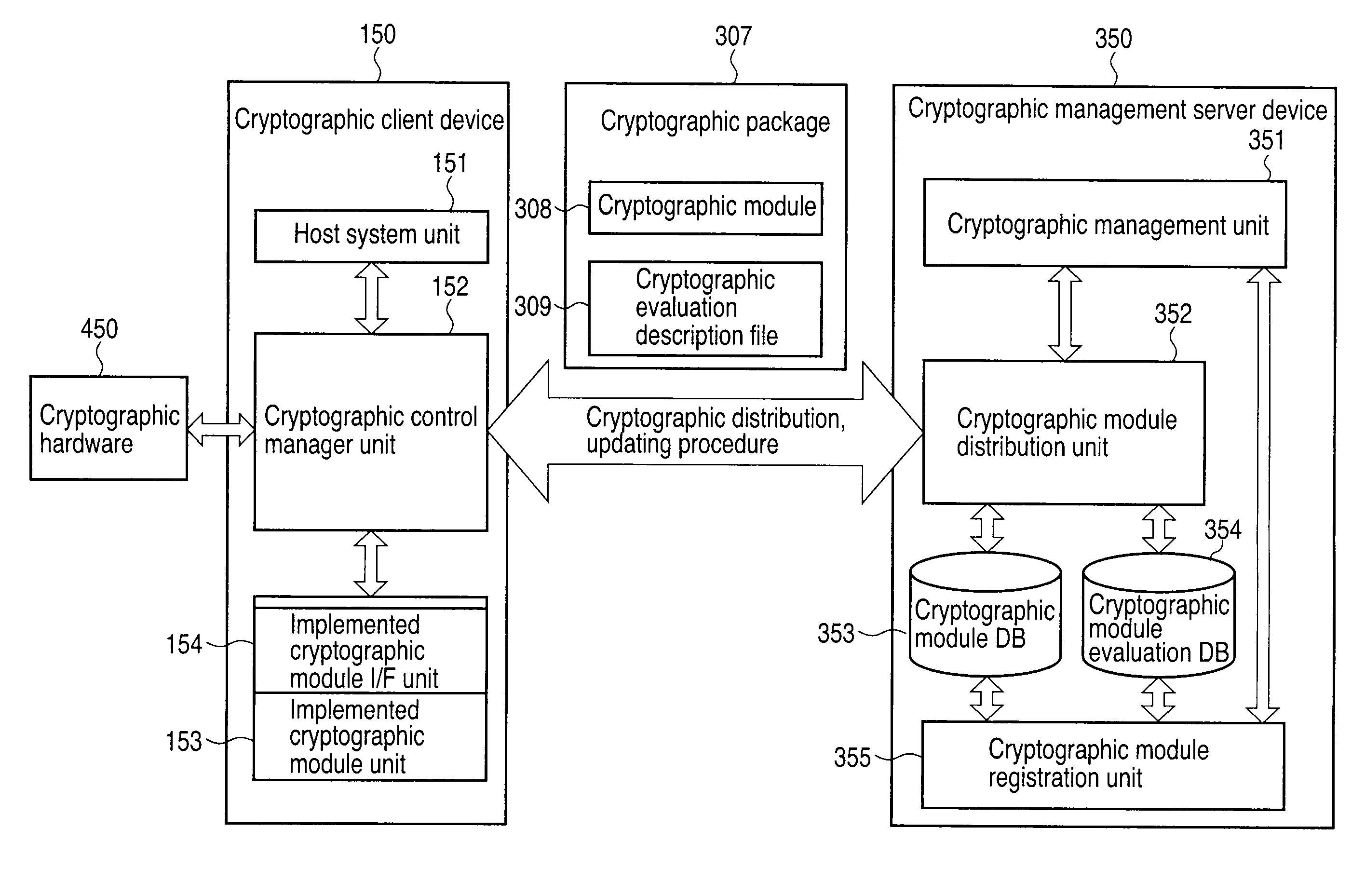
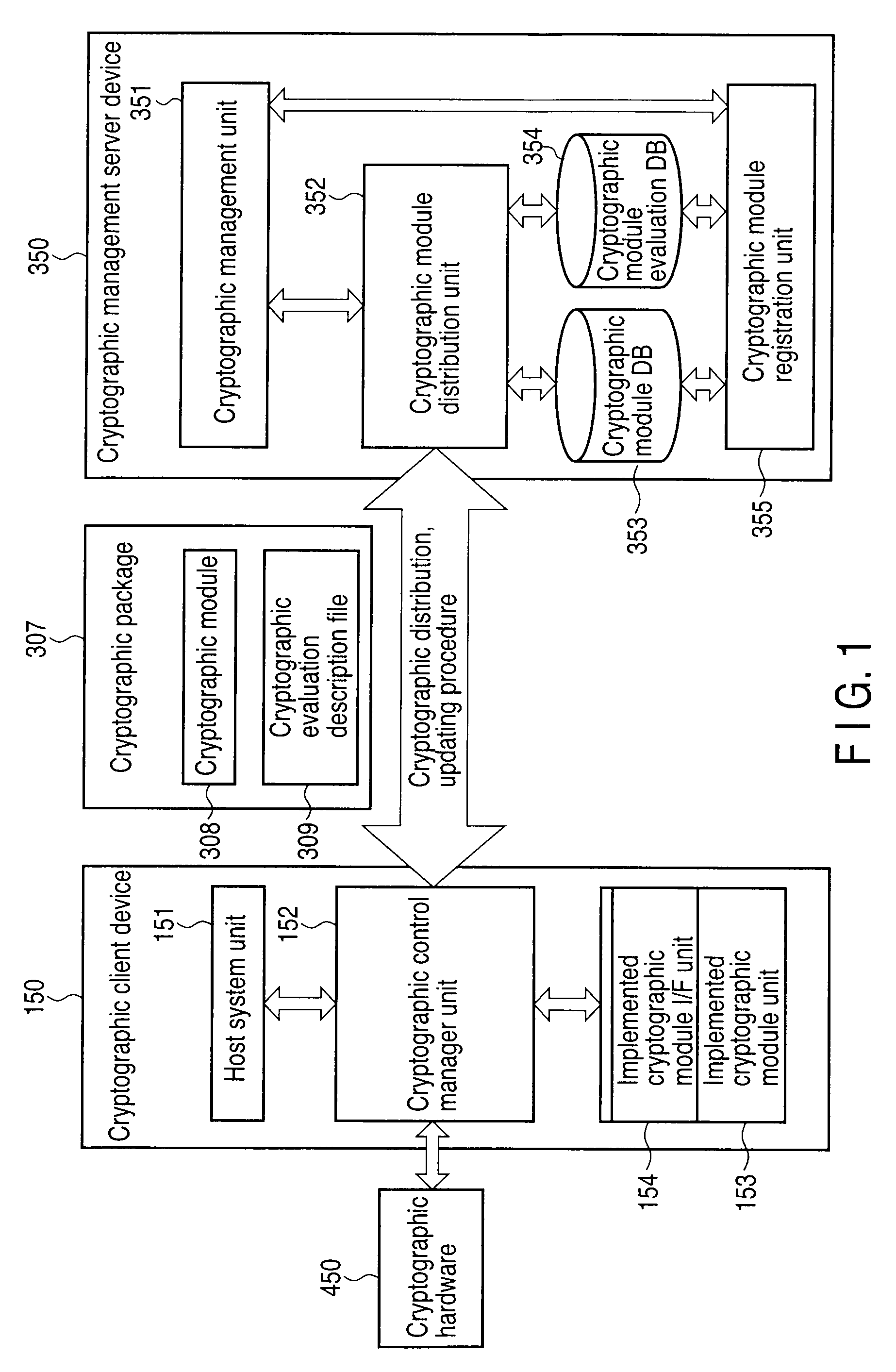
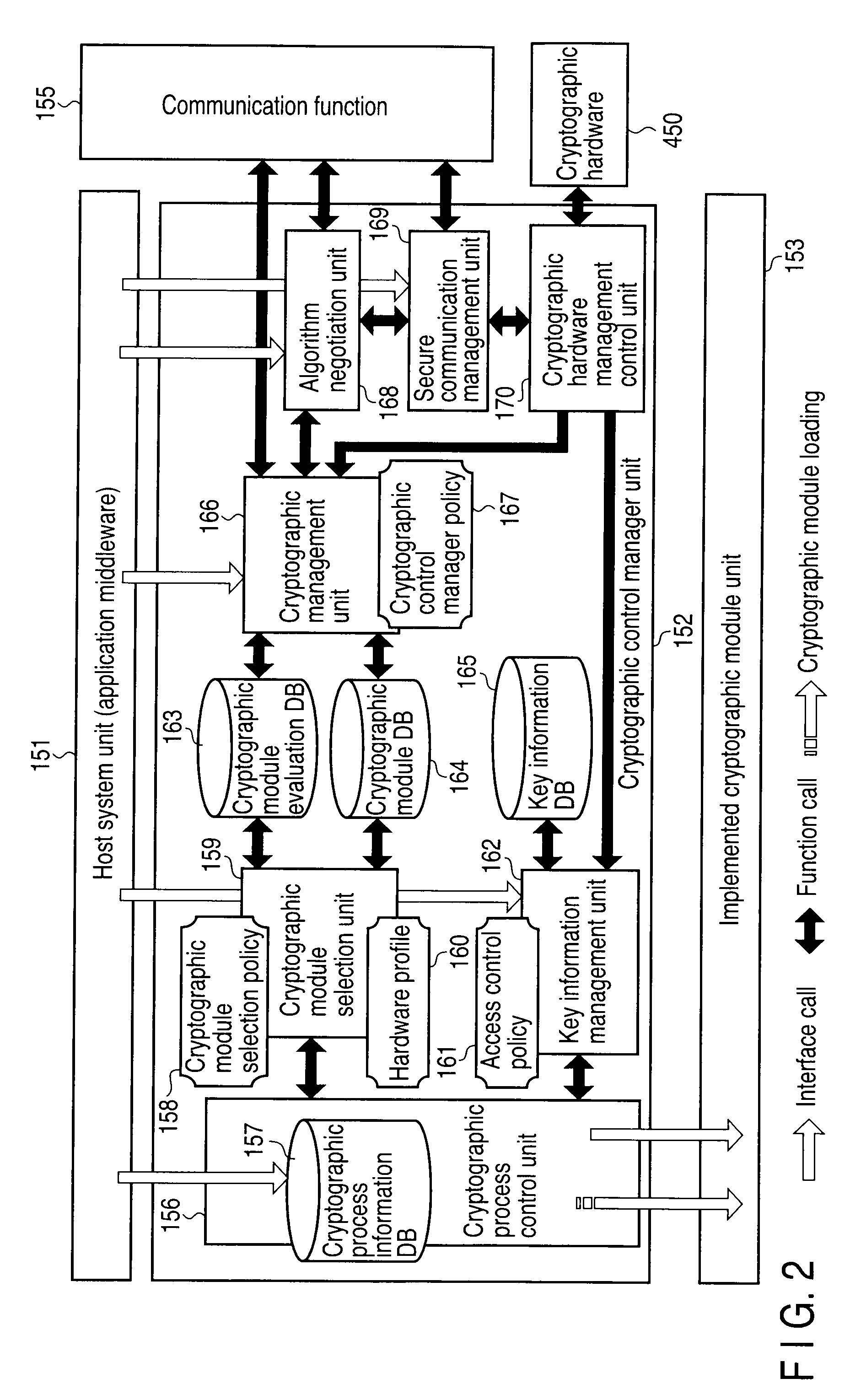
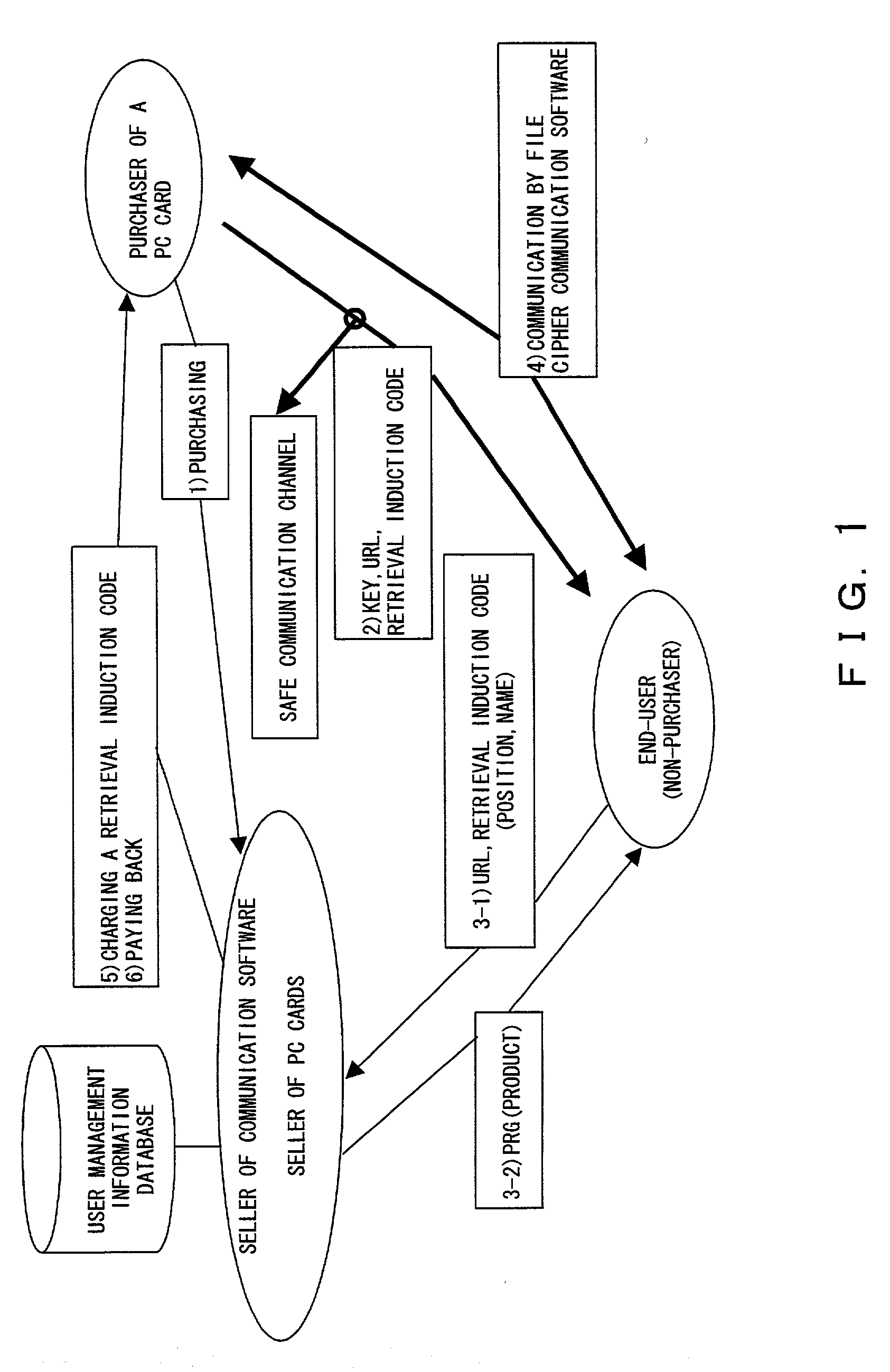
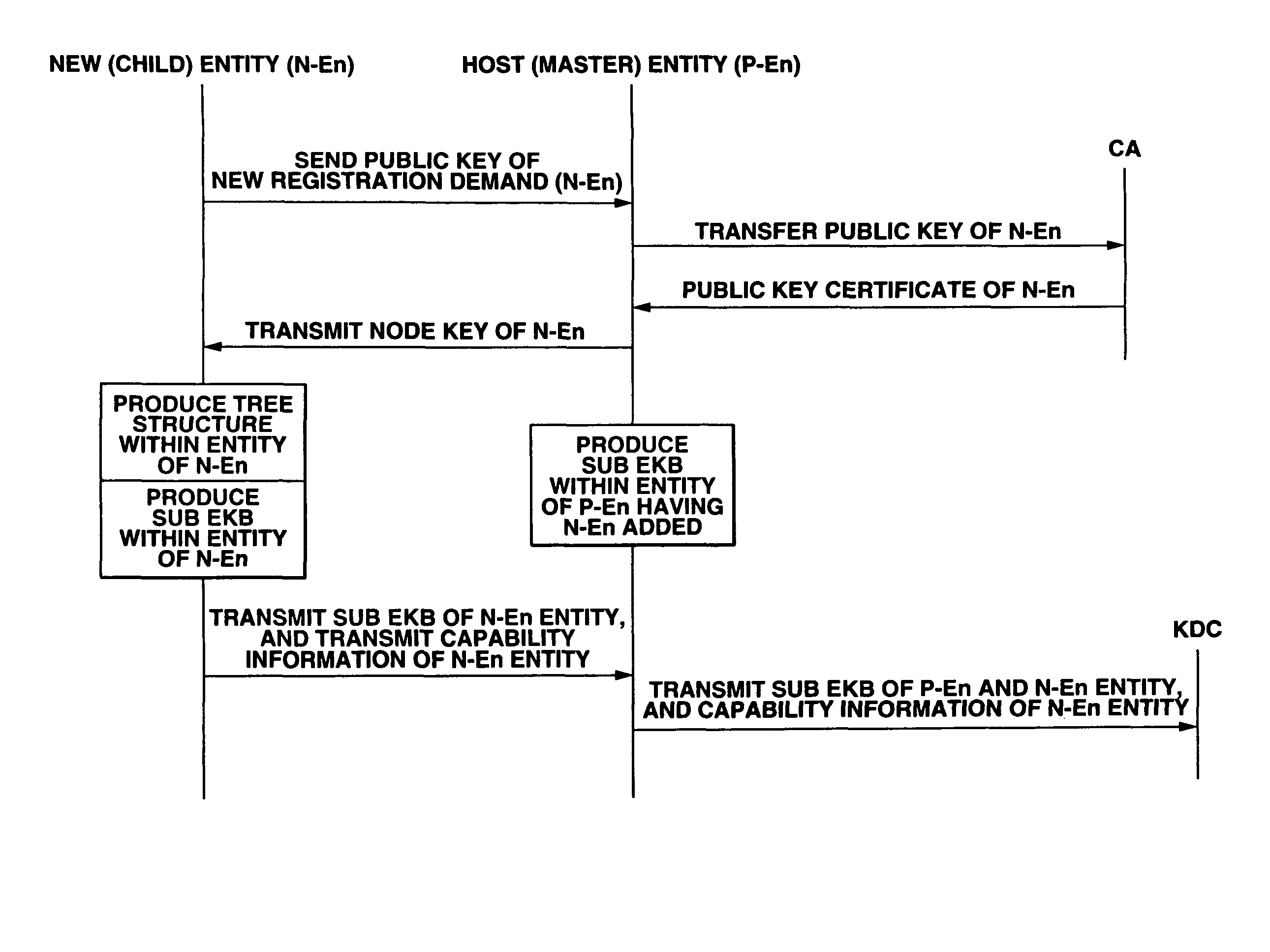
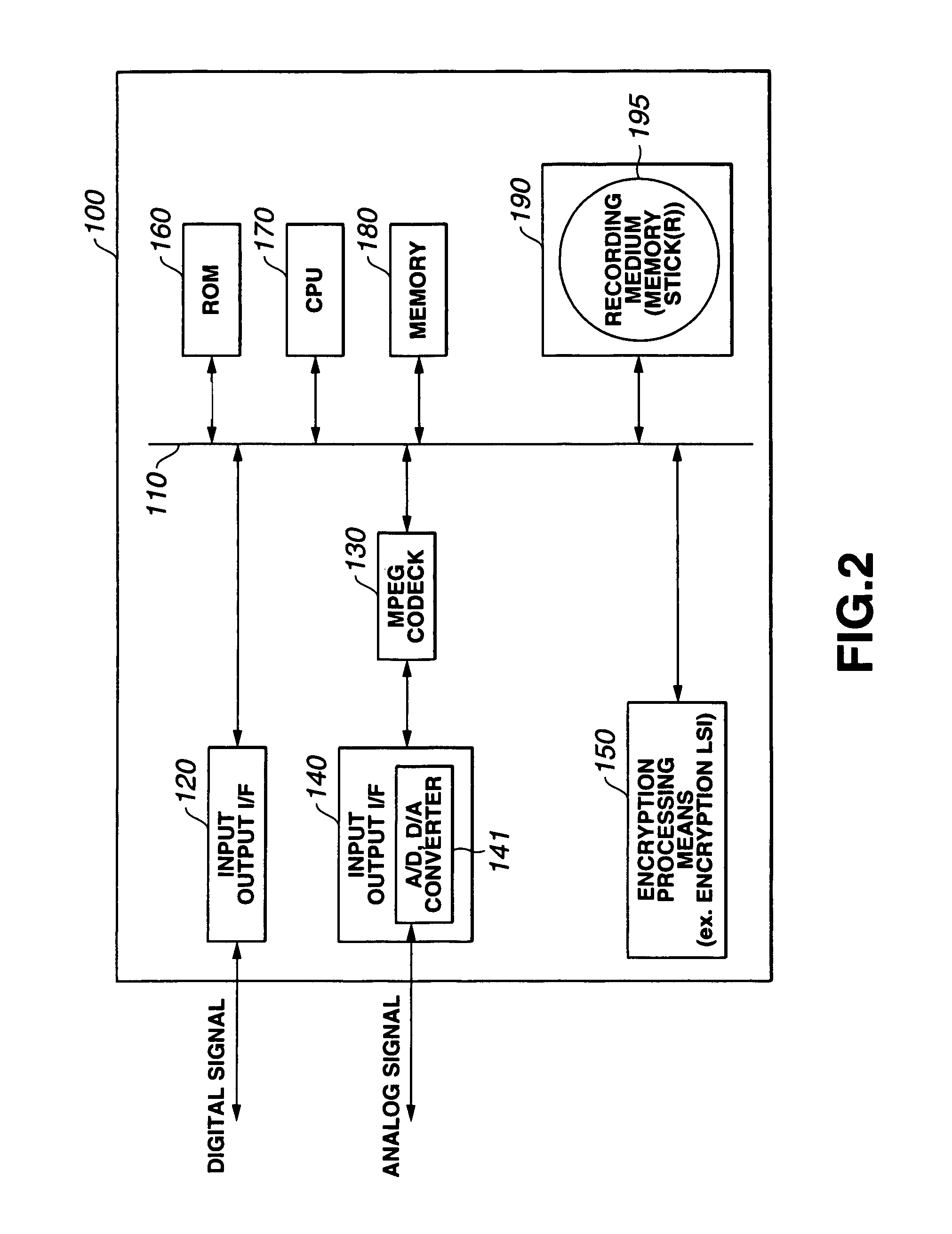
Setting information distribution apparatus, method, program, and medium, authentication setting transfer apparatus, method, program, and medium, and setting information reception program
InactiveUS20060117104A1Improve user 's convenienceGuaranteed correctnessKey distribution for secure communicationUser identity/authority verificationAuthentication
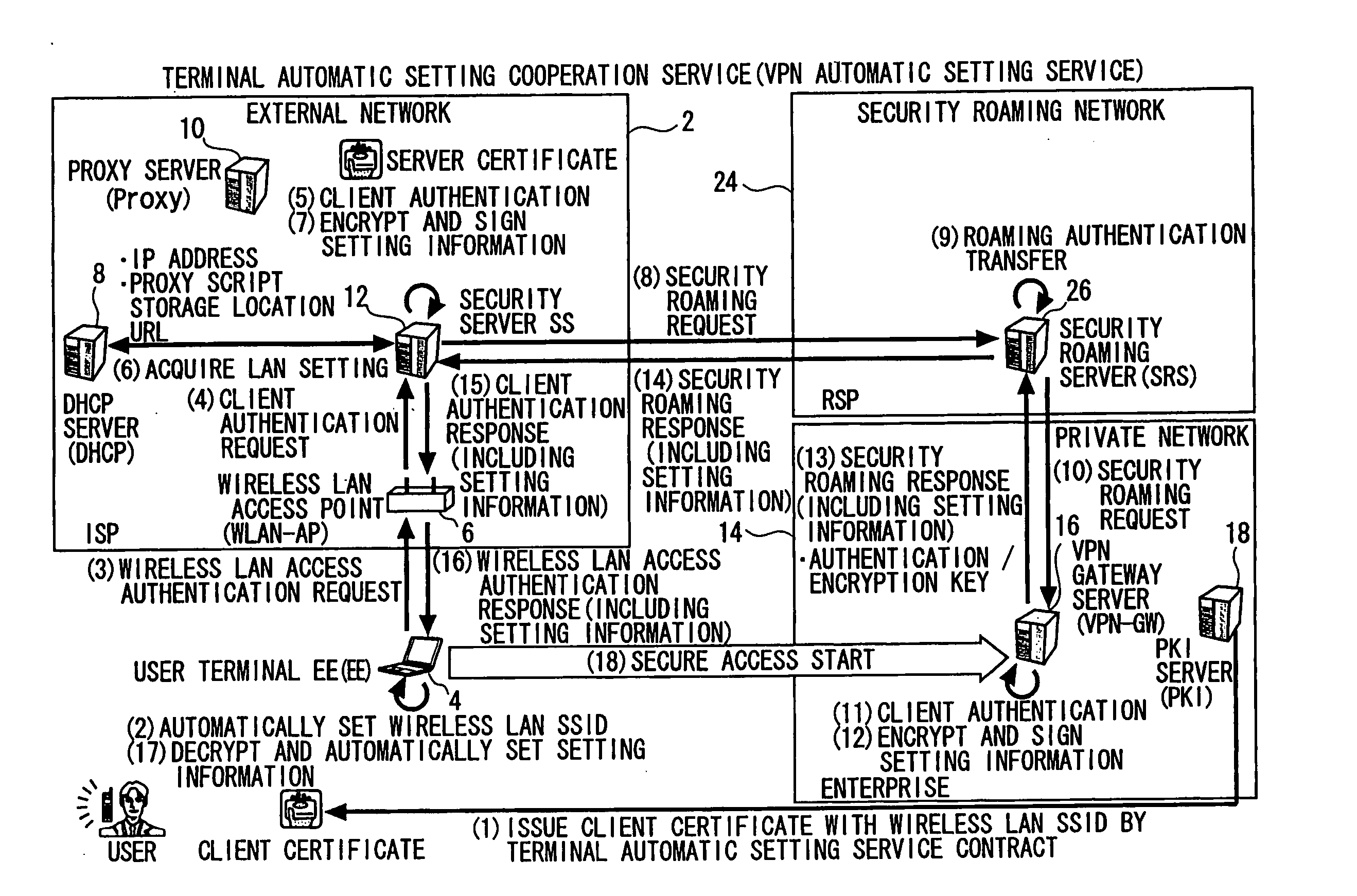
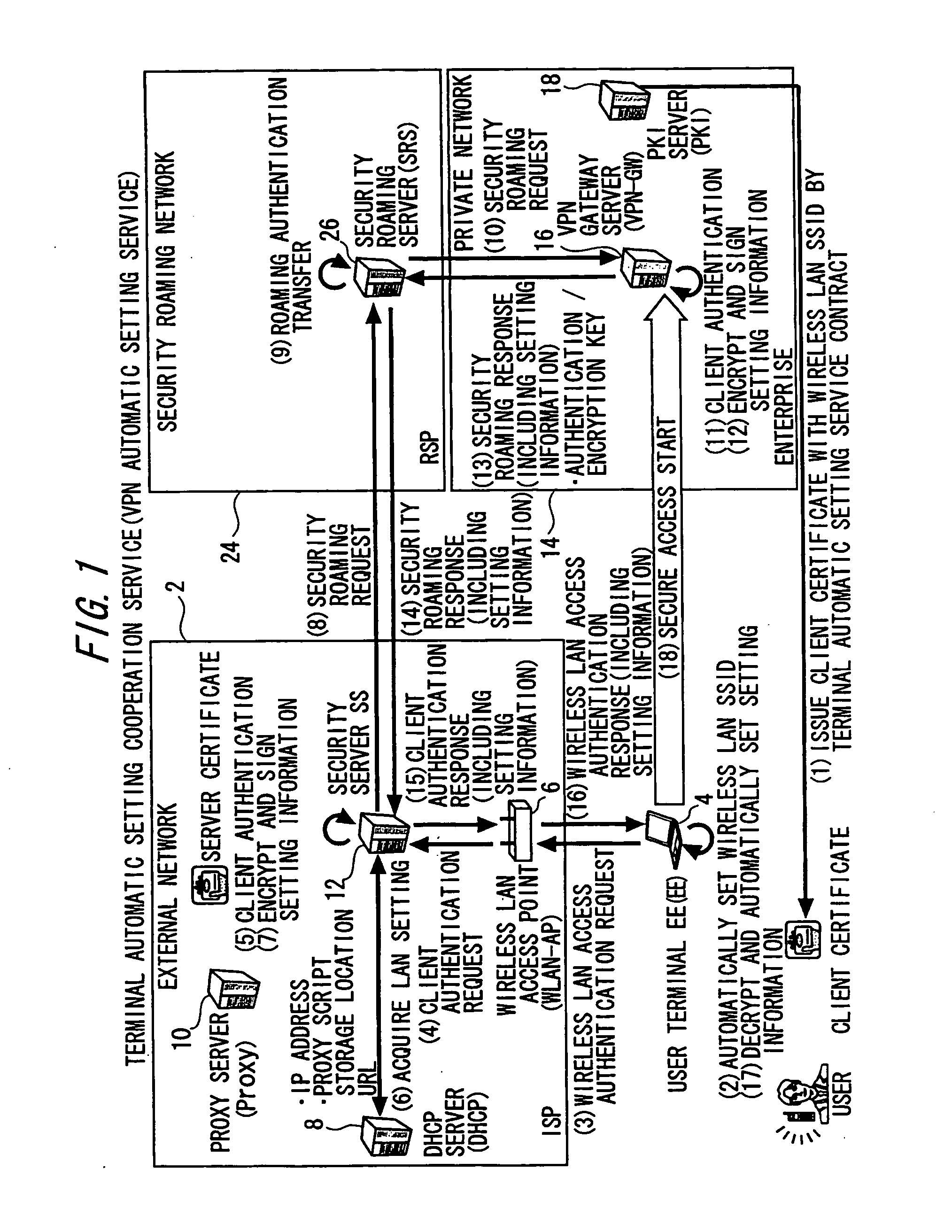
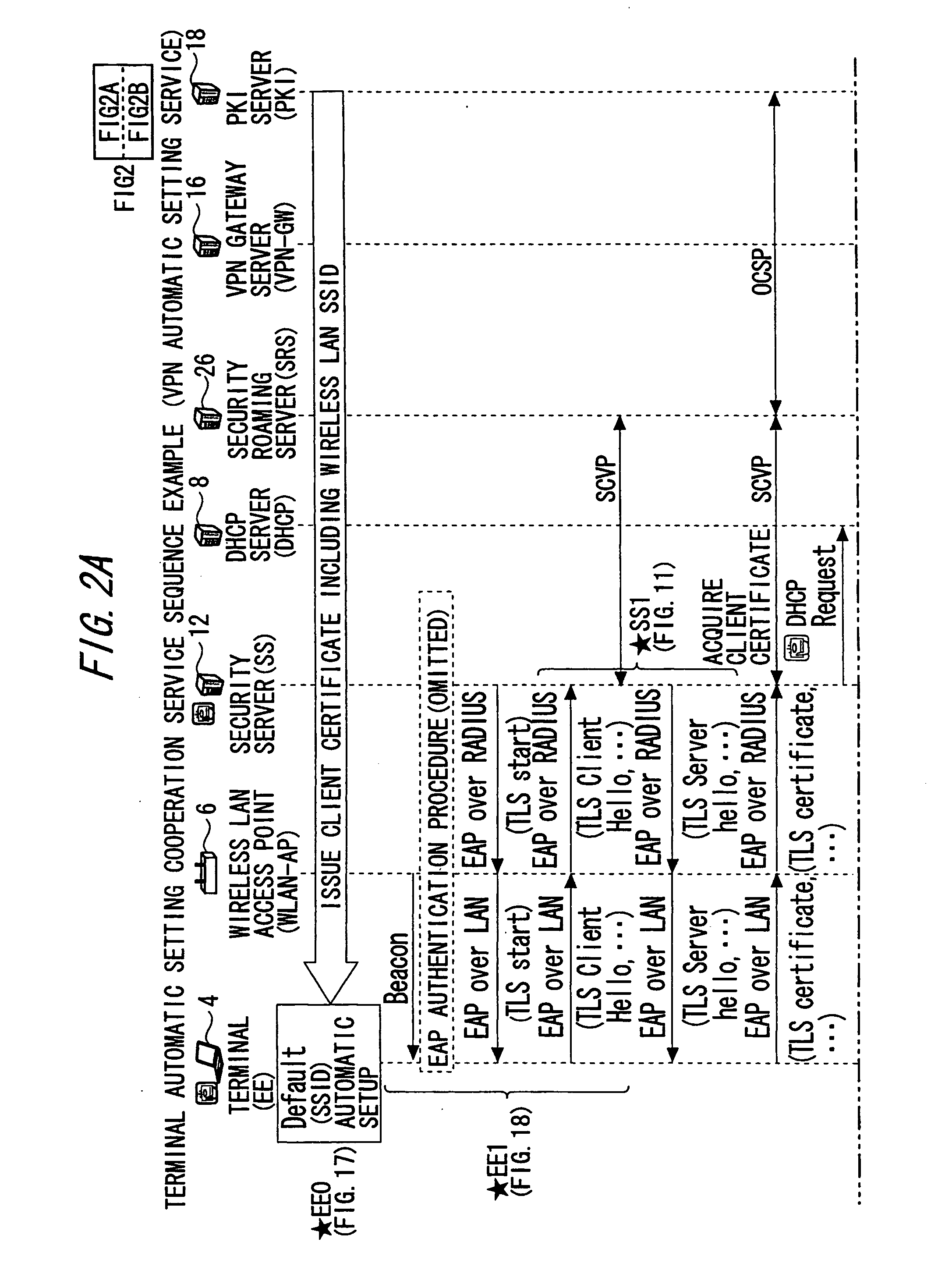
A setting information distribution apparatus belonging to a first network, comprises: authentication unit that receives and authenticates an authentication request from a user terminal which requires an access authentication by using a network access authentication procedure between the user terminal and the first network; transmitting unit that transmits an authentication cooperation request which requires setting data to be set to the user terminal to another, network by using the network access authentication procedure and an authentication cooperation procedure between a plurality of networks; and distribution unit that distributes a first response message added with setting data to the user terminal by producing the first response message corresponding to the authentication request by adding the setting data included in a second response message corresponding to the authentication cooperation request.
Owner:FUJITSU LTD
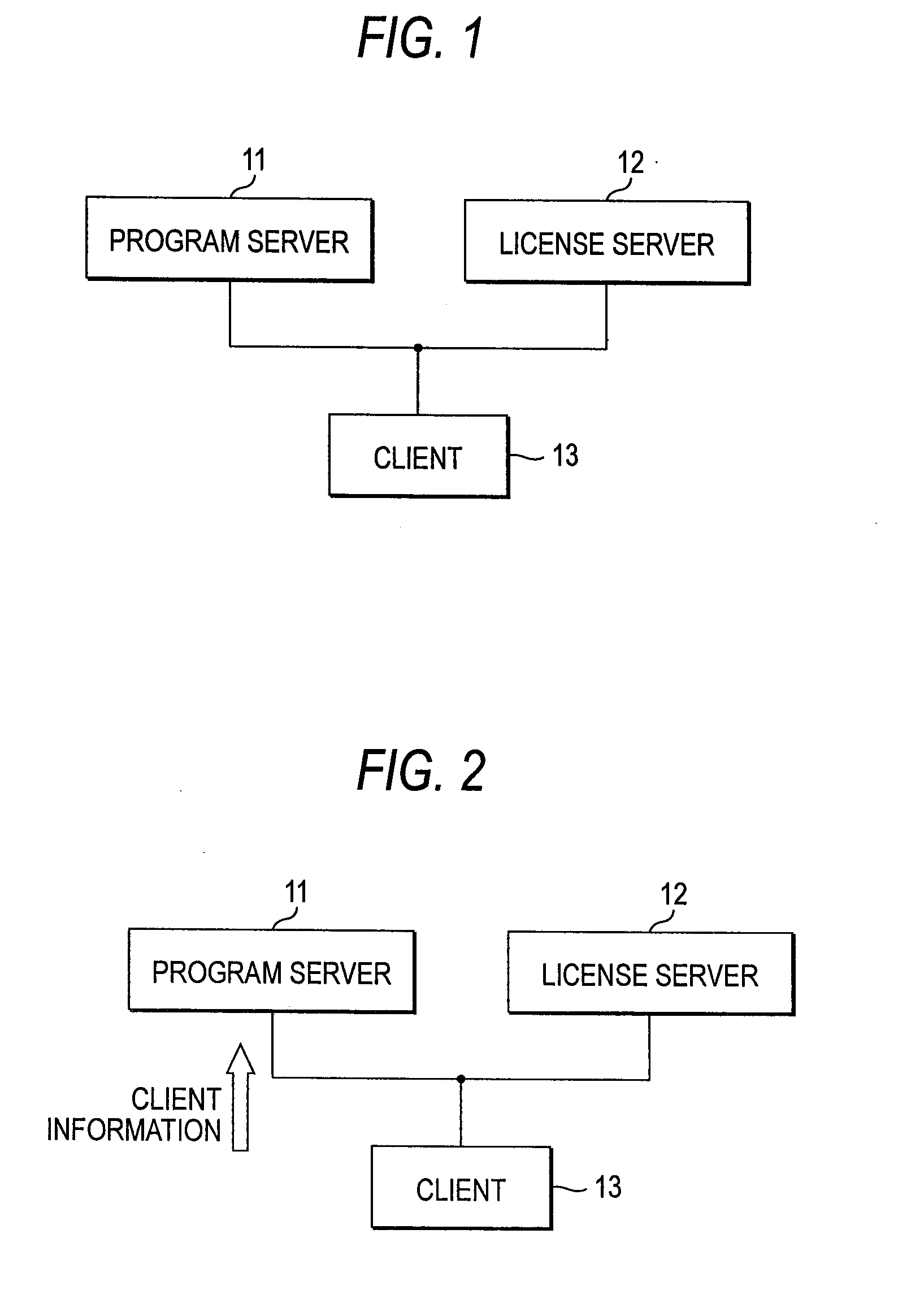
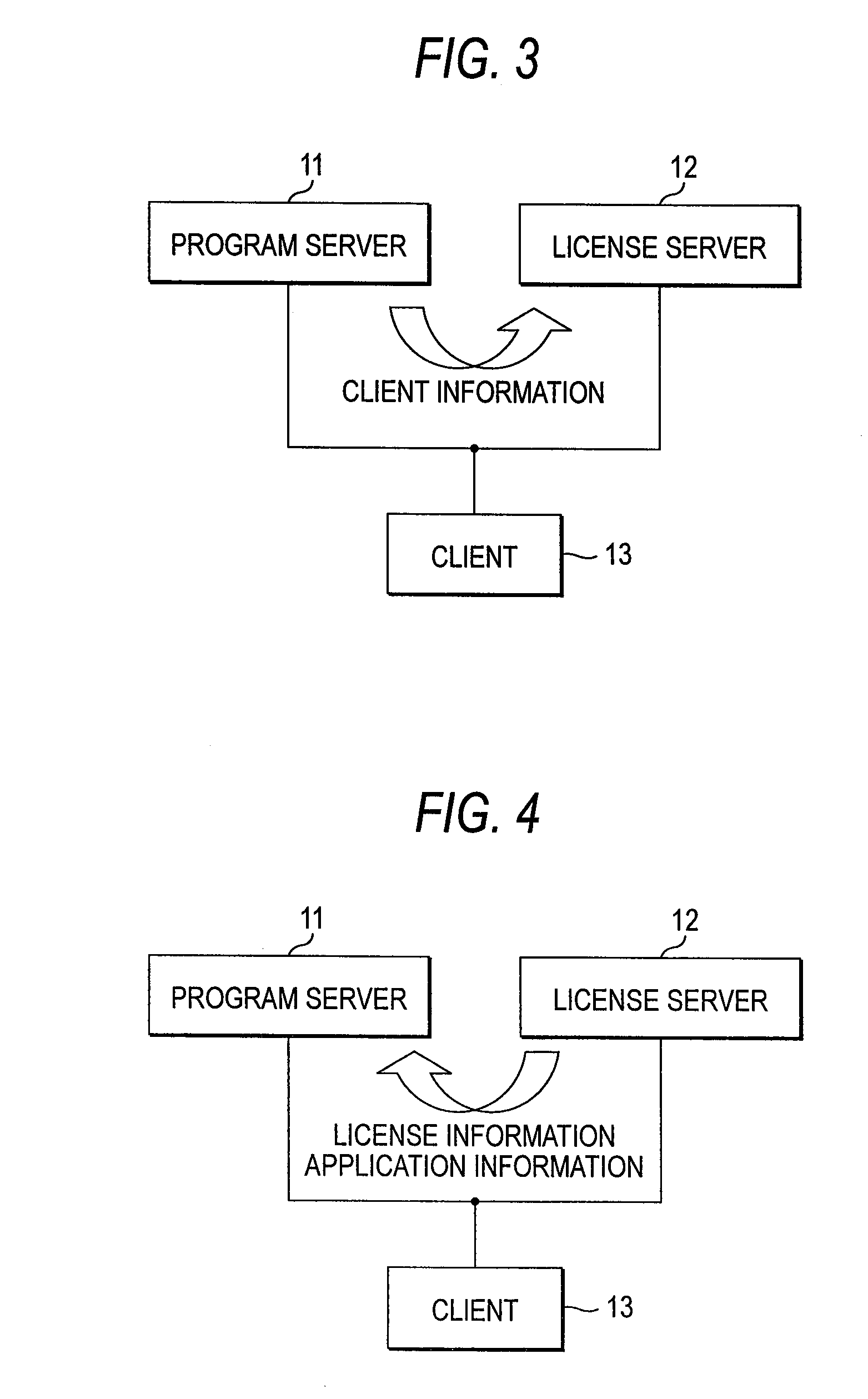
Update method and update system
InactiveUS20080027871A1Effective applicationUpdated safely and efficientlyData processing applicationsProgram loading/initiatingClient-sideLicense
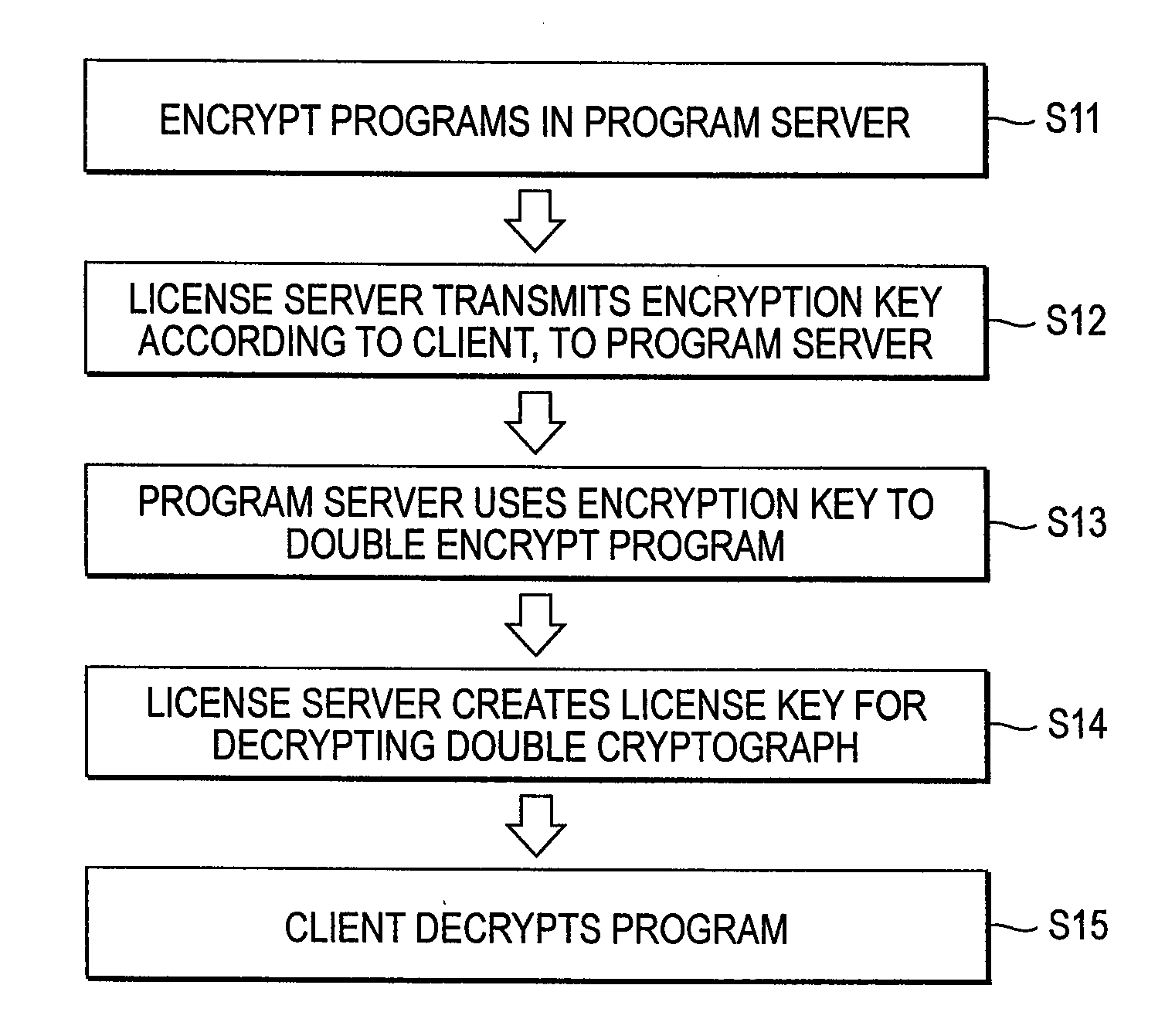
An update system includes: a program server for storing application programs and transmitting the application program corresponding only to an authenticated client; a license server for transmitting information concerning the authenticated client to the program server and transmitting the license key of the application program to the authenticated client; and the client for executing the application program transmitted from the program server based on the license key transmitted from the license server.
Owner:ZIOSOFT
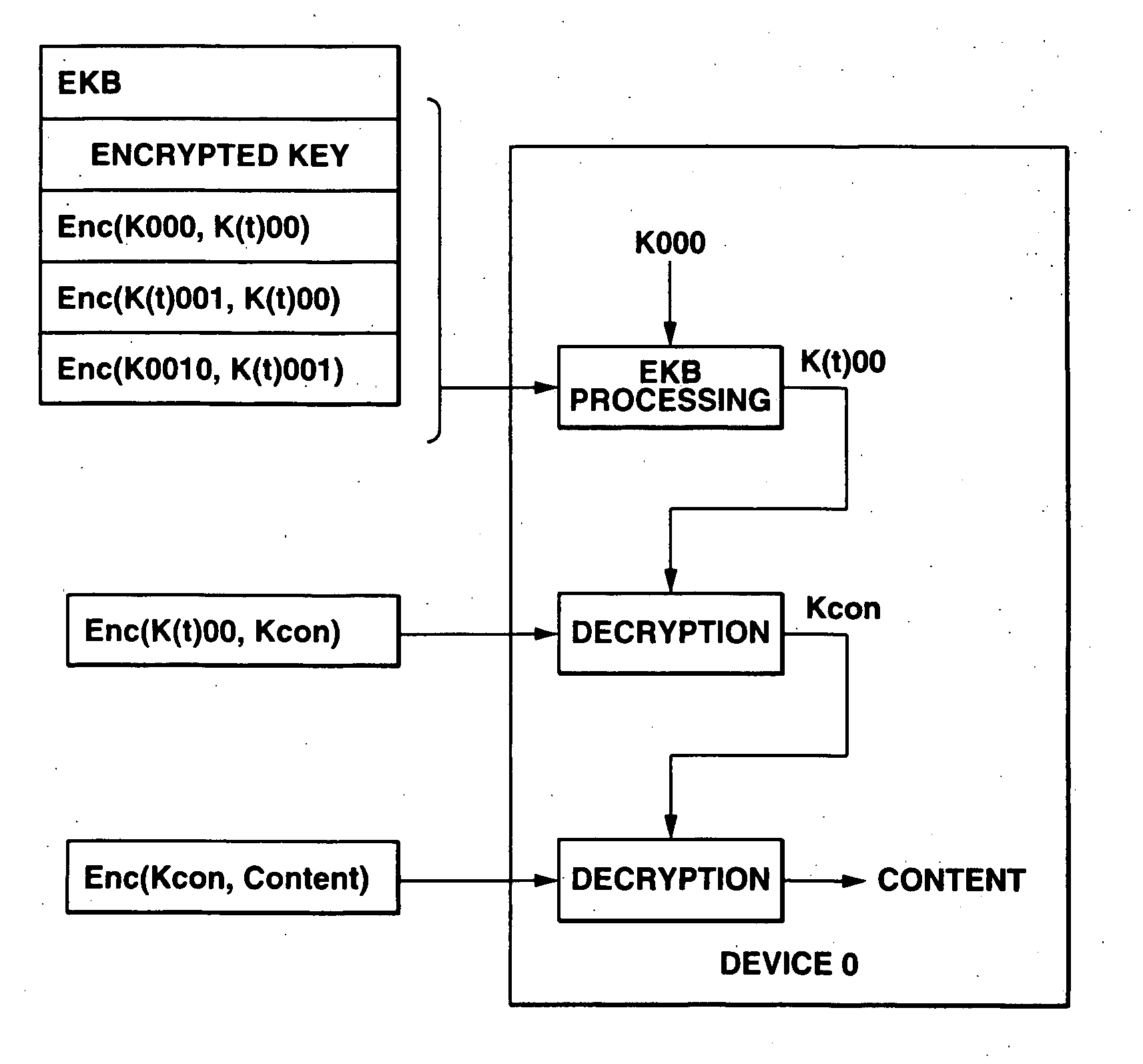
Information processing system and method using encryption key block
InactiveUS20070263875A1Data transmission securitySecure transmissionKey distribution for secure communicationRecord information storageInformation handling systemData processing
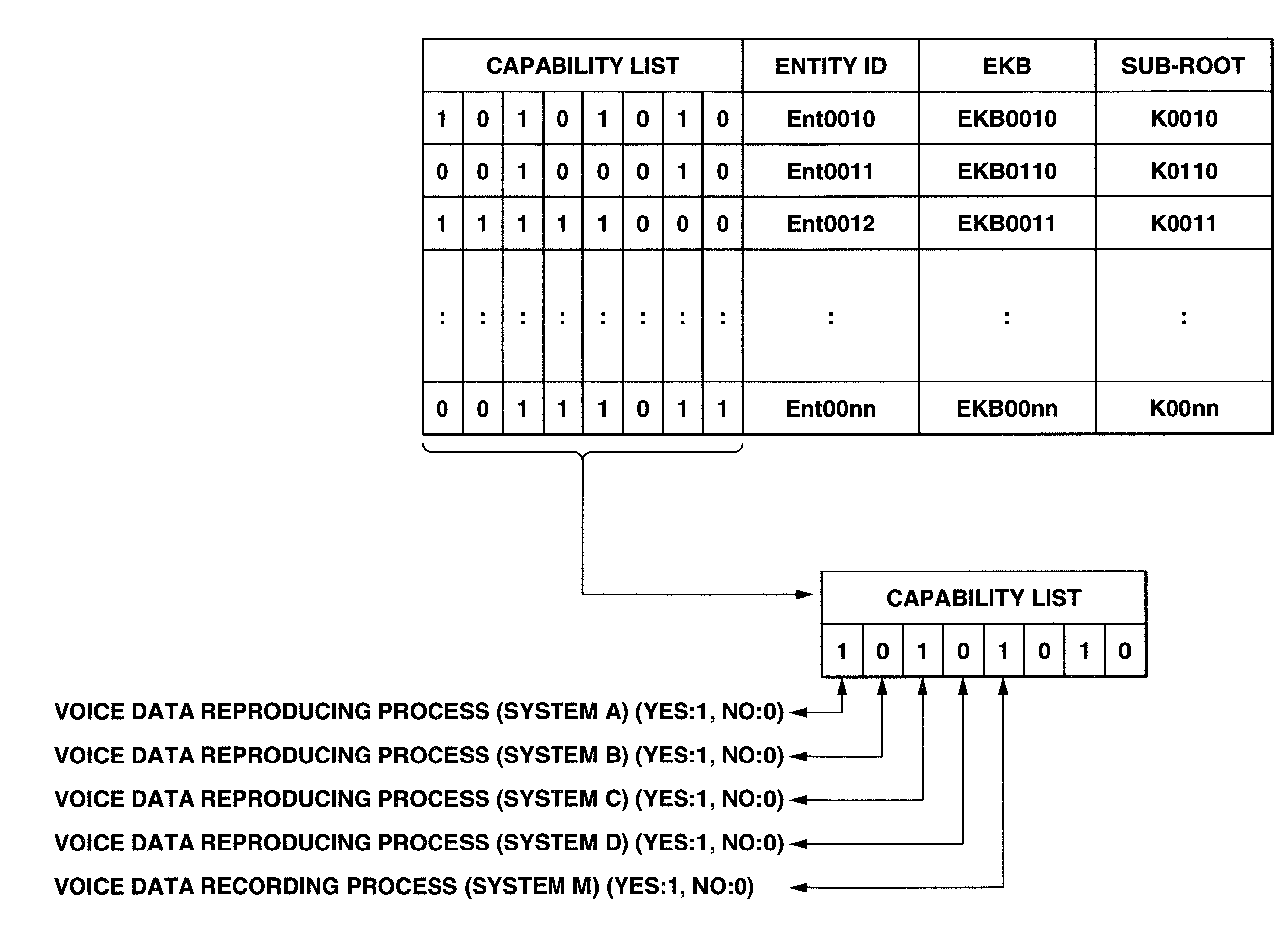
An information processing system and method using an encryption key block sets sub-trees classified based on data processing ability of the devices (capability) in a key tree in which respective keys are corresponded to a root, nodes and leaves of a tree in which a plurality of devices are constituted as the leaves, generates a sub-enabling key block which is effective for an entity in a managing subject of each sub-tree (entity), and generates an enabling key block decodable only by the entities having common capability. Also, an information processing system and method using an encryption key block manages a partial tree of a key tree (sub-tree), generates a sub-enabling key block based only on a key set corresponding to nodes or leaves included in the sub-tree, and generates an enabling key block decodable only by selected entities by using the sub-enabling key block. Thus, it is possible to generate and distribute an enabling key block corresponding to data processing ability of a device and to manage devices by dividing a hierarchical key tree structure.
Owner:SONY CORP
Data processing system, data processing method, and program providing medium
ActiveUS7116785B2Effective method of processingEnsure safe distributionKey distribution for secure communicationPublic key for secure communicationData processing systemData file
The inventive data processing apparatus enables own memory device to store a plurality of key distribution approval data files each containing such a header data comprising a number of “link-count” data units each designating actual number of applicable contents data per decodable contents key based on an enabling key block (EKB) distribution key enciphering key (KEK) enciphered by a corresponding enabling key block (EKB) provided for by a hierarchy key tree structure. When storing a plurality of the enabling key blocks (EKB) in a memory device, such a key enciphering key (KEK) contained in an enabling key block (EKB) having a number of link-count data units is previously decoded and stored in the memory device. By way of applying the stored (KEK) when utilizing contents data, the enabling key block (EKB) processing step is deleted, whereby promoting higher efficiency in the utilization of contents data.
Owner:SONY CORP
Information processing system and method using encryption key block
InactiveUS7269257B2Data transmission securitySecure transmissionKey distribution for secure communicationUnauthorized memory use protectionInformation processingComputer hardware
An information processing system and method using an encryption key block sets sub-trees classified based on data processing ability of the devices (capability) in a key tree in which respective keys are corresponded to a root, nodes and leaves of a tree in which a plurality of devices are constituted as the leaves, generates a sub-enabling key block which is effective for an entity in a managing subject of each sub-tree (entity), and generates an enabling key block decodable only by the entities having common capability. Also, an information processing system and method using an encryption key block manages a partial tree of a key tree (sub-tree), generates a sub-enabling key block based only on a key set corresponding to nodes or leaves included in the sub-tree, and generates an enabling key block decodable only by selected entities by using the sub-enabling key block. Thus, it is possible to generate and distribute an enabling key block corresponding to data processing ability of a device and to manage devices by dividing a hierarchical key tree structure.
Owner:SONY CORP
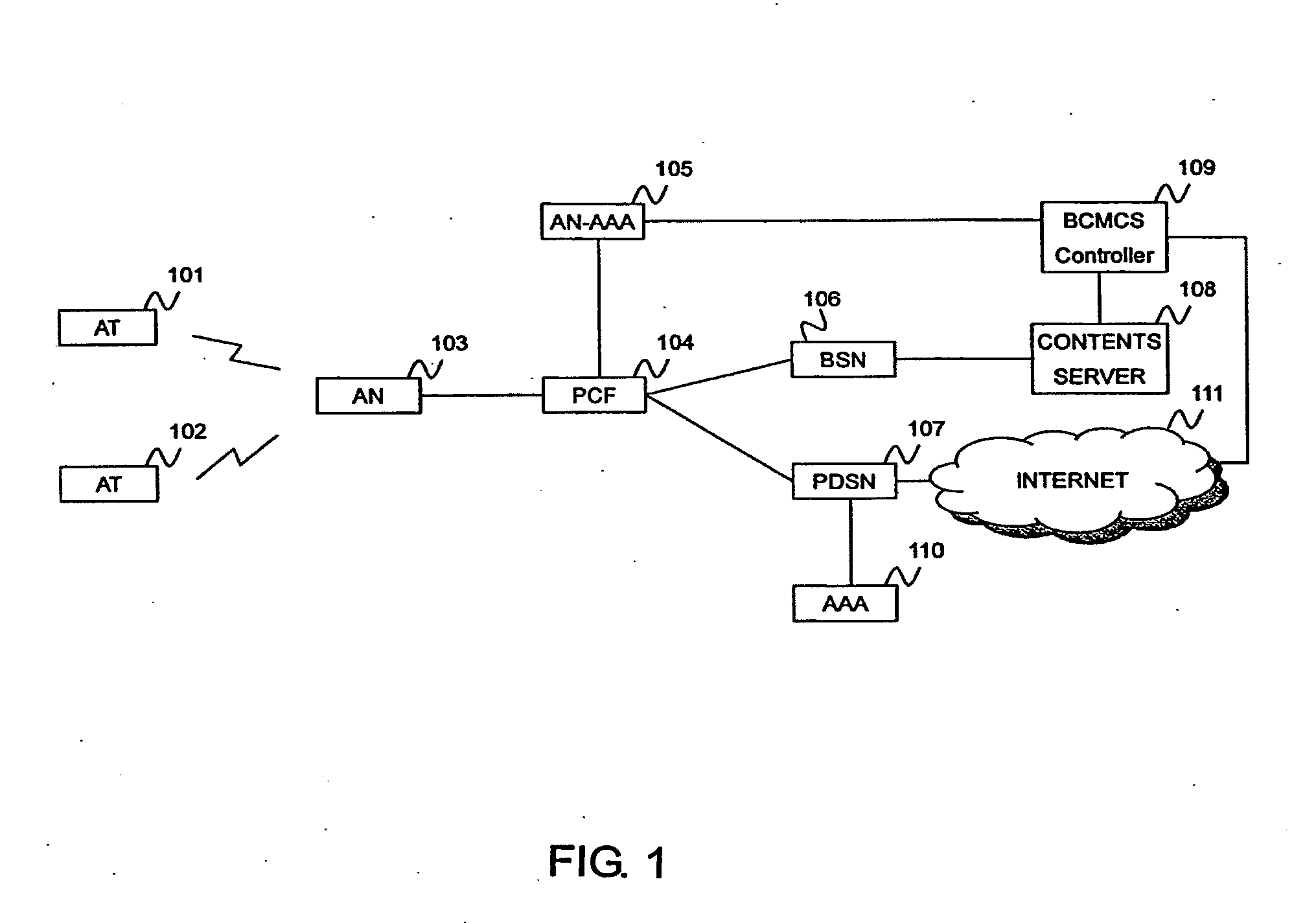
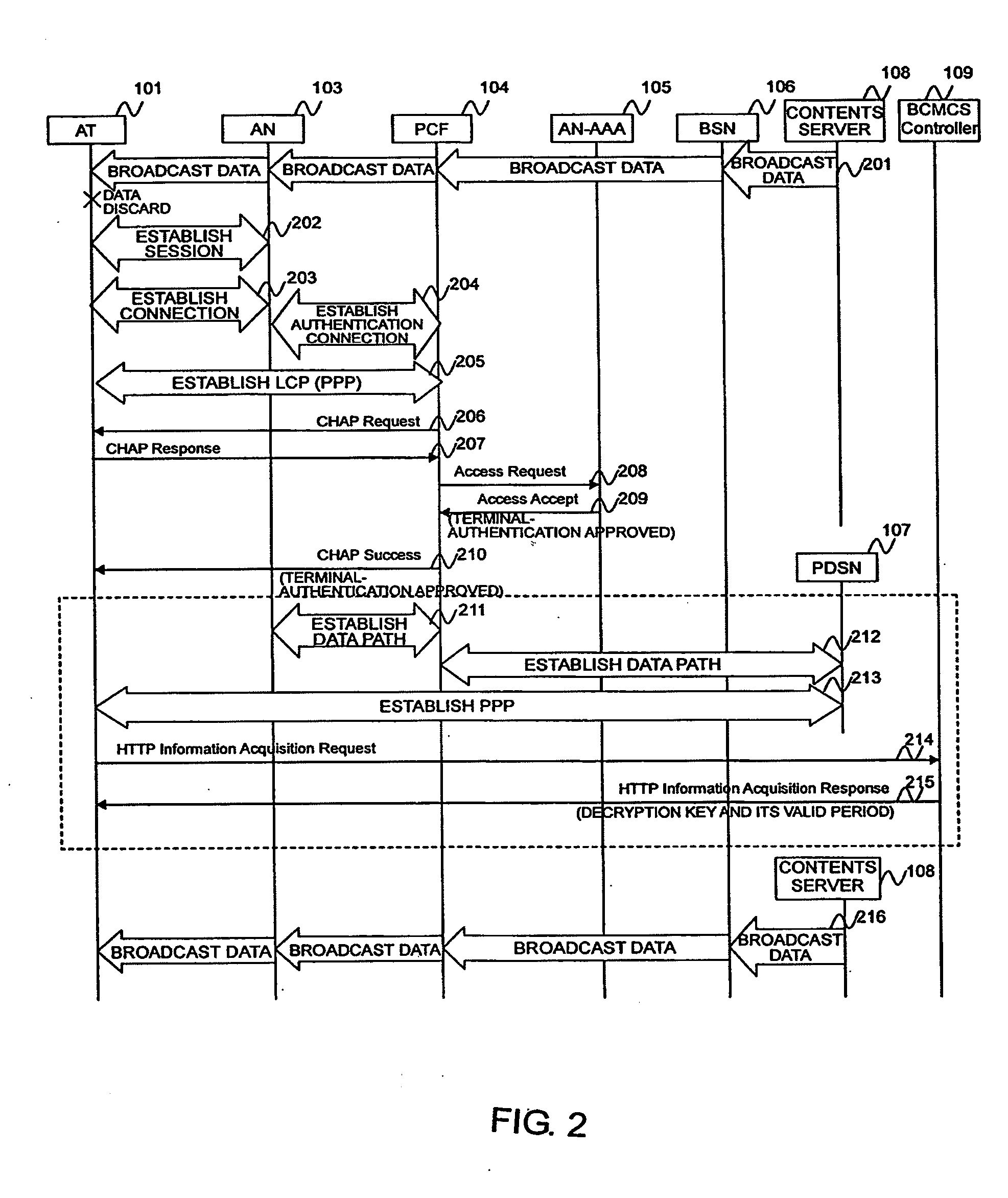
Decryption-key distribution method and authentication apparatus
InactiveUS20110167264A1Reduce the amount of solutionReduce processing timeKey distribution for secure communicationMultiple keys/algorithms usagePacket control unitKey distribution
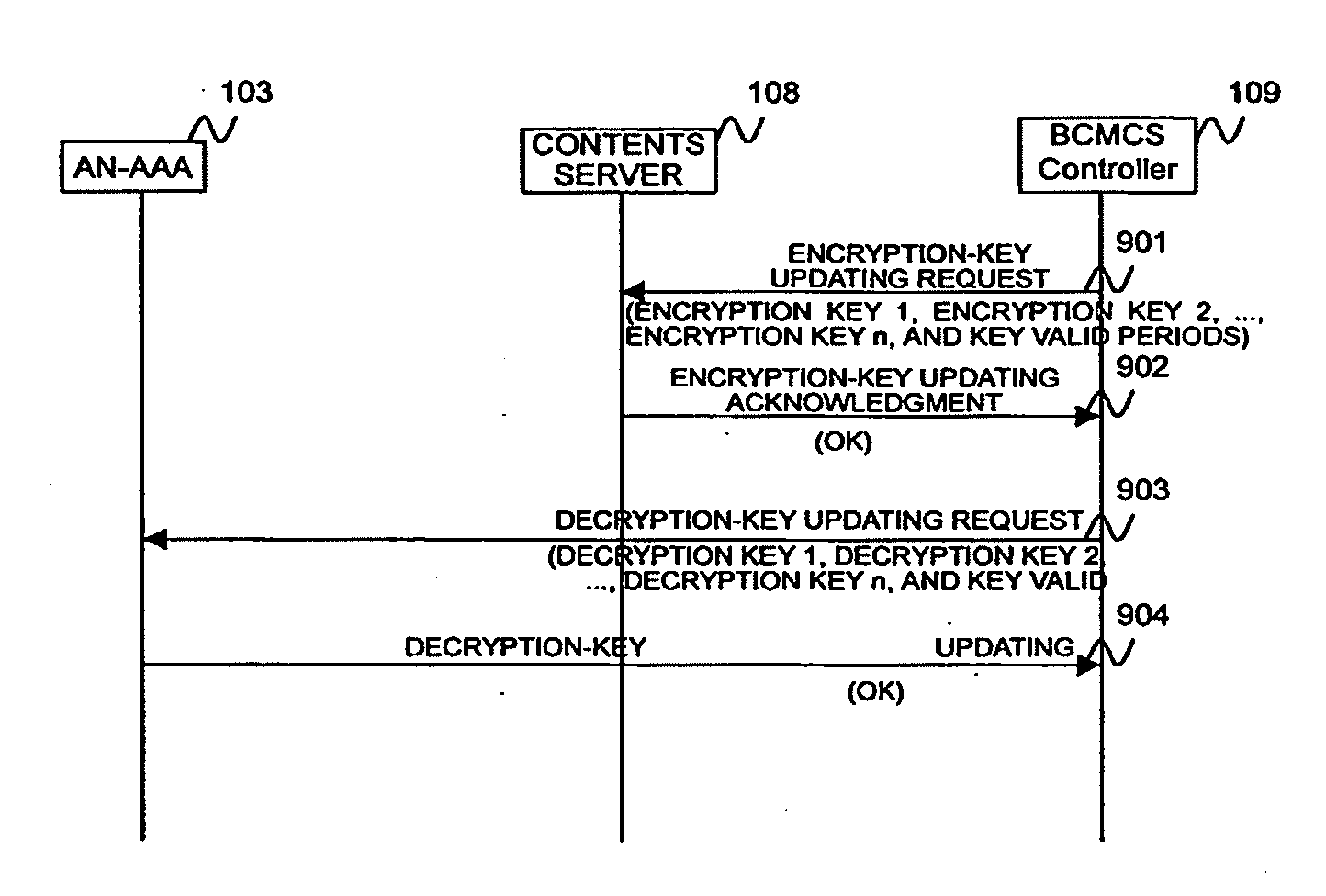
A decryption key for decrypting data from an access node is distributed to an access terminal intending to receive the data. An authentication unit receives a message for terminal authentication including a terminal identifier from the terminal and authenticates the terminal. The authentication unit refers to a content registration table having stored in advance the content type of a content which the terminal can receive, in association with the terminal identifier, according to the received terminal identifier to obtain a corresponding content type. The authentication unit refers to a decryption data base having stored in advance a decryption key and its valid period in association with a content type, according to the obtained content type to obtain a corresponding decryption key and valid period. The authentication unit sends an authentication result and the decryption key and valid period to the terminal or to a packet control unit.
Owner:HITACHI LTD
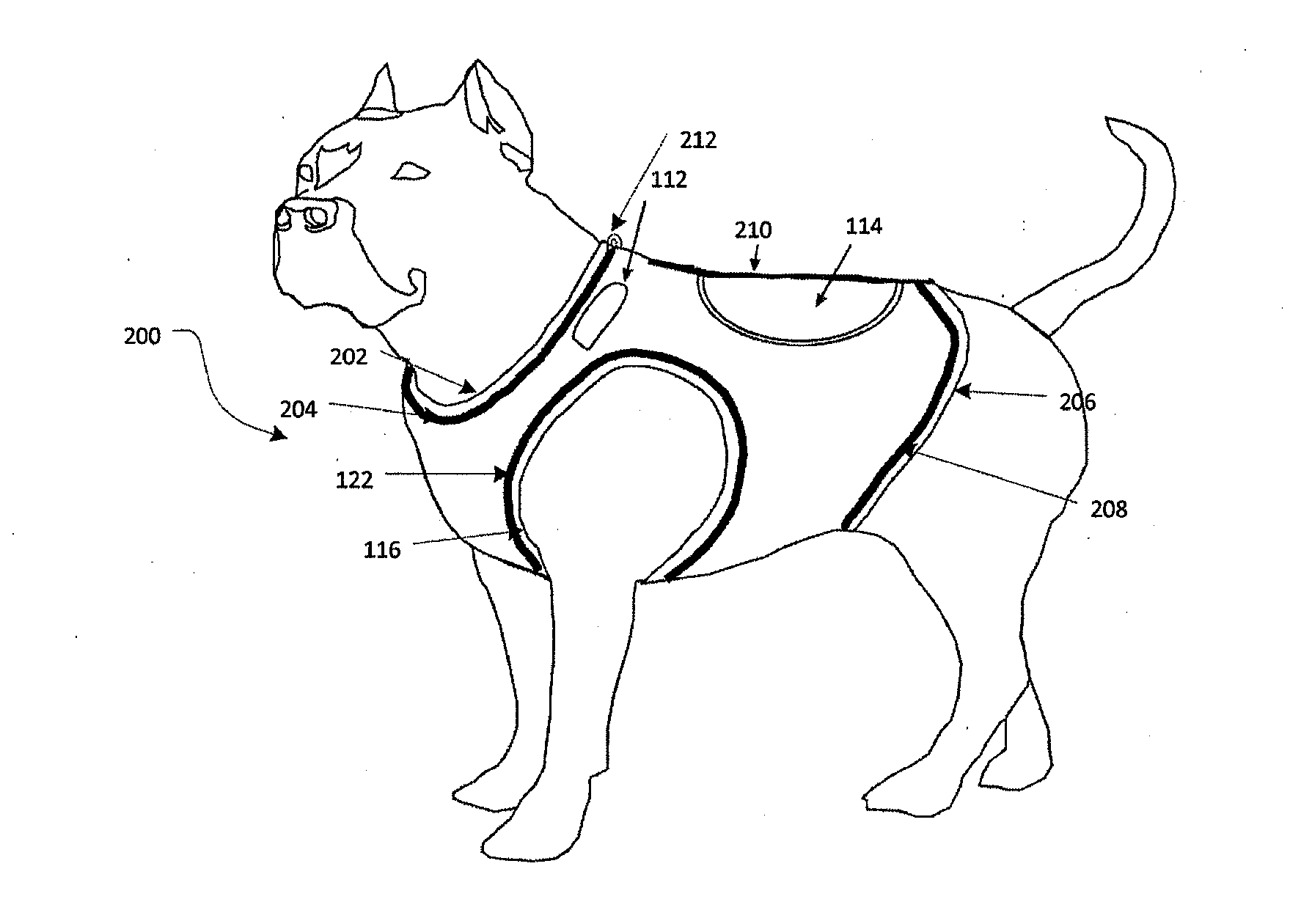
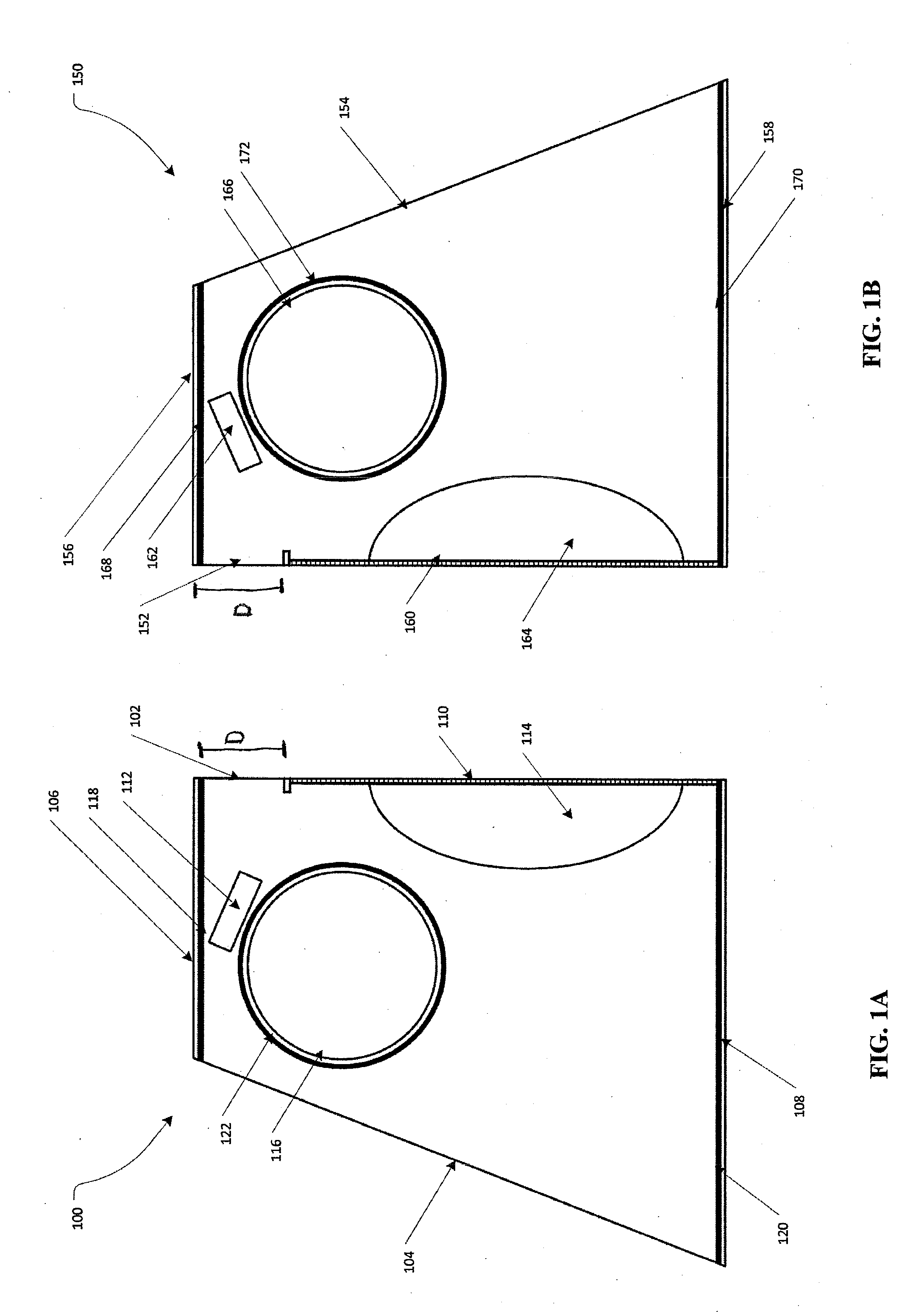
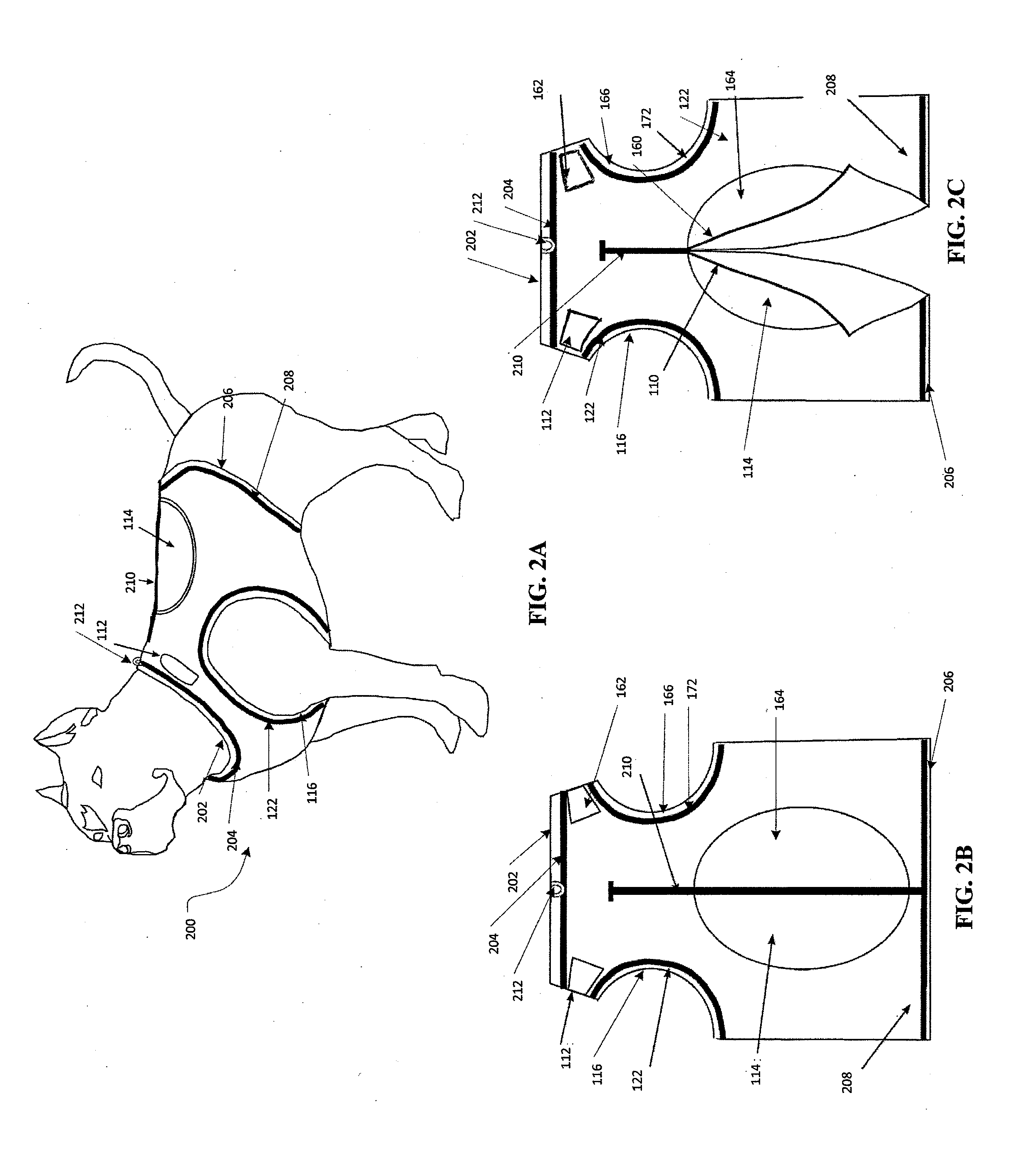
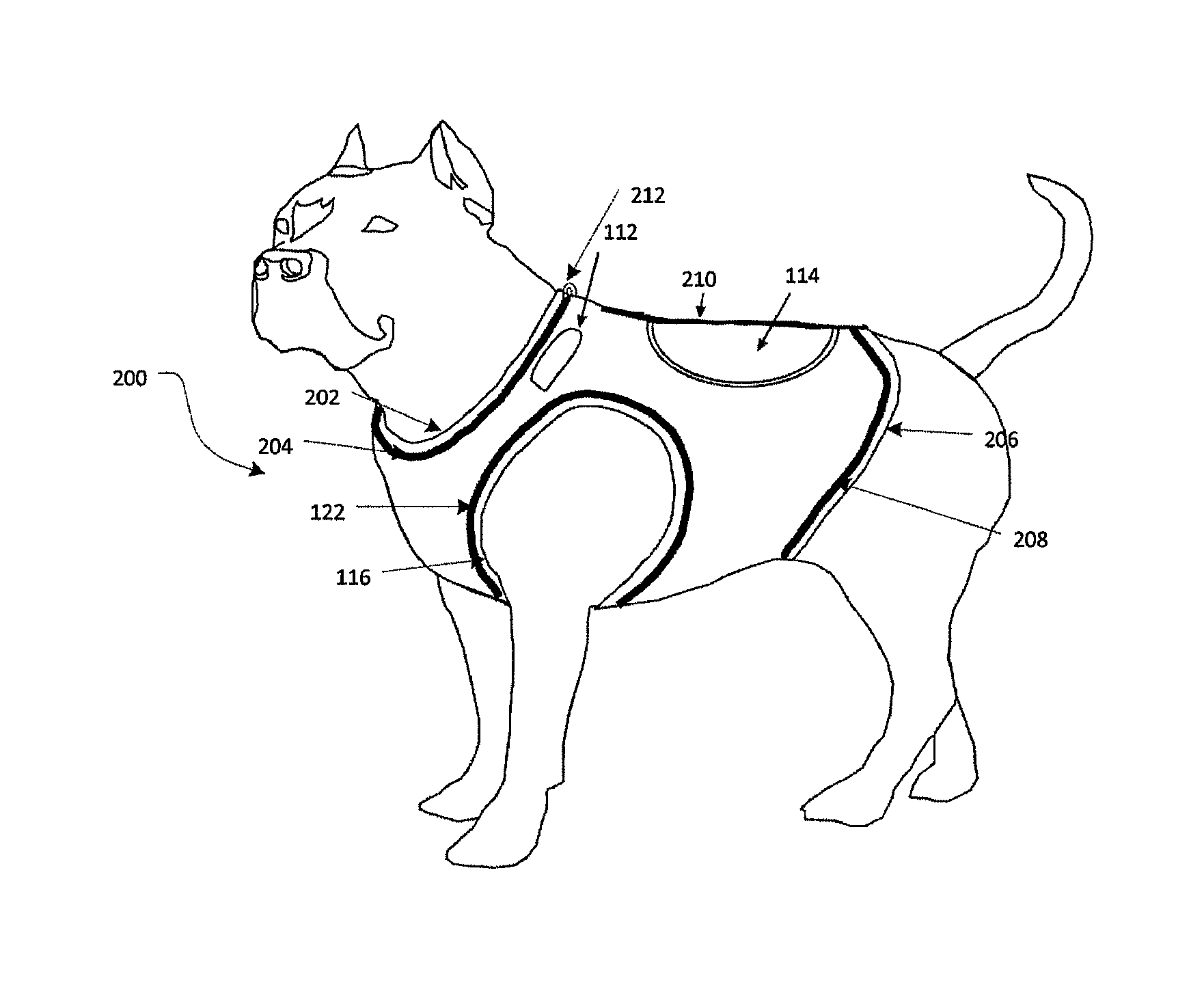
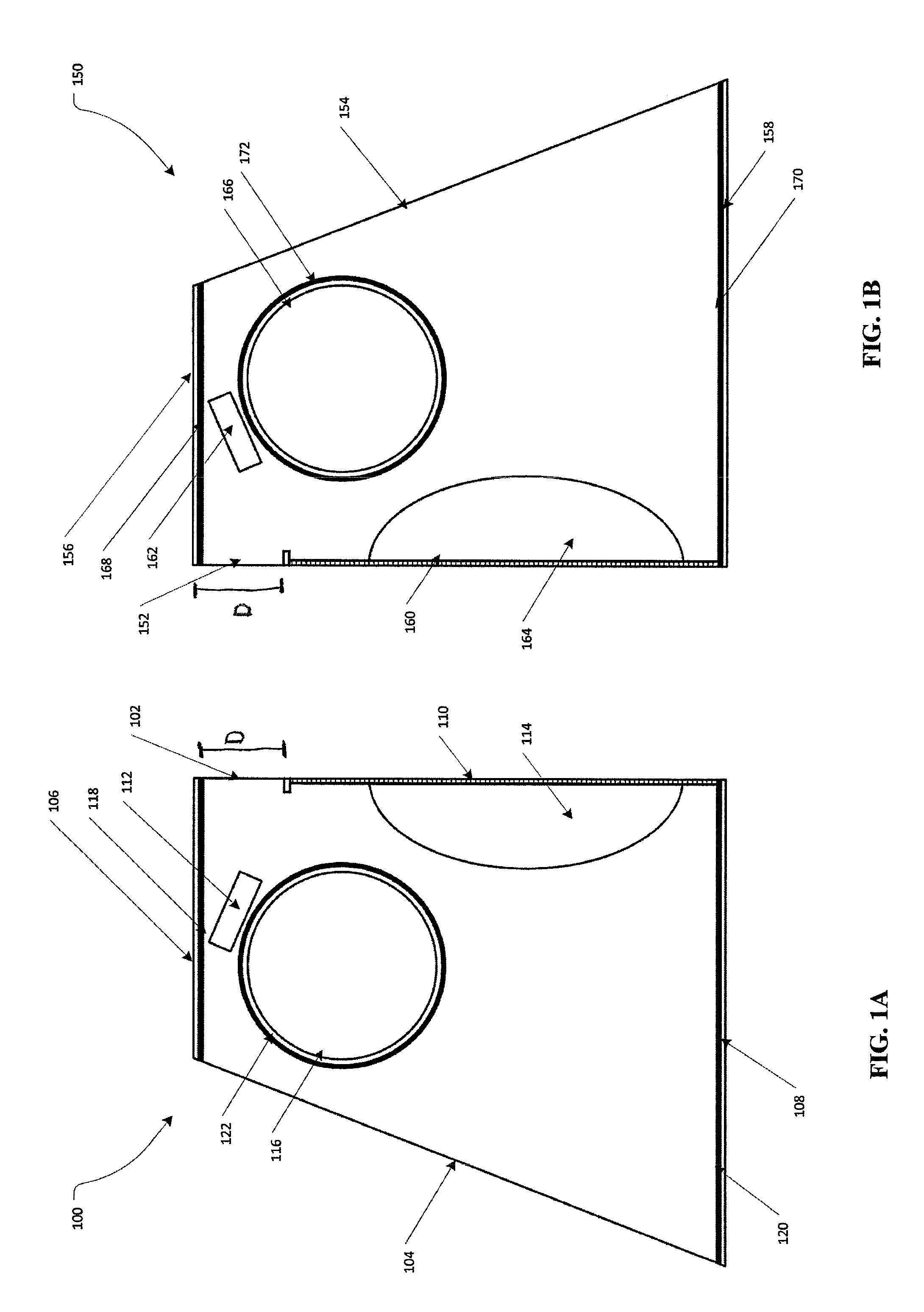
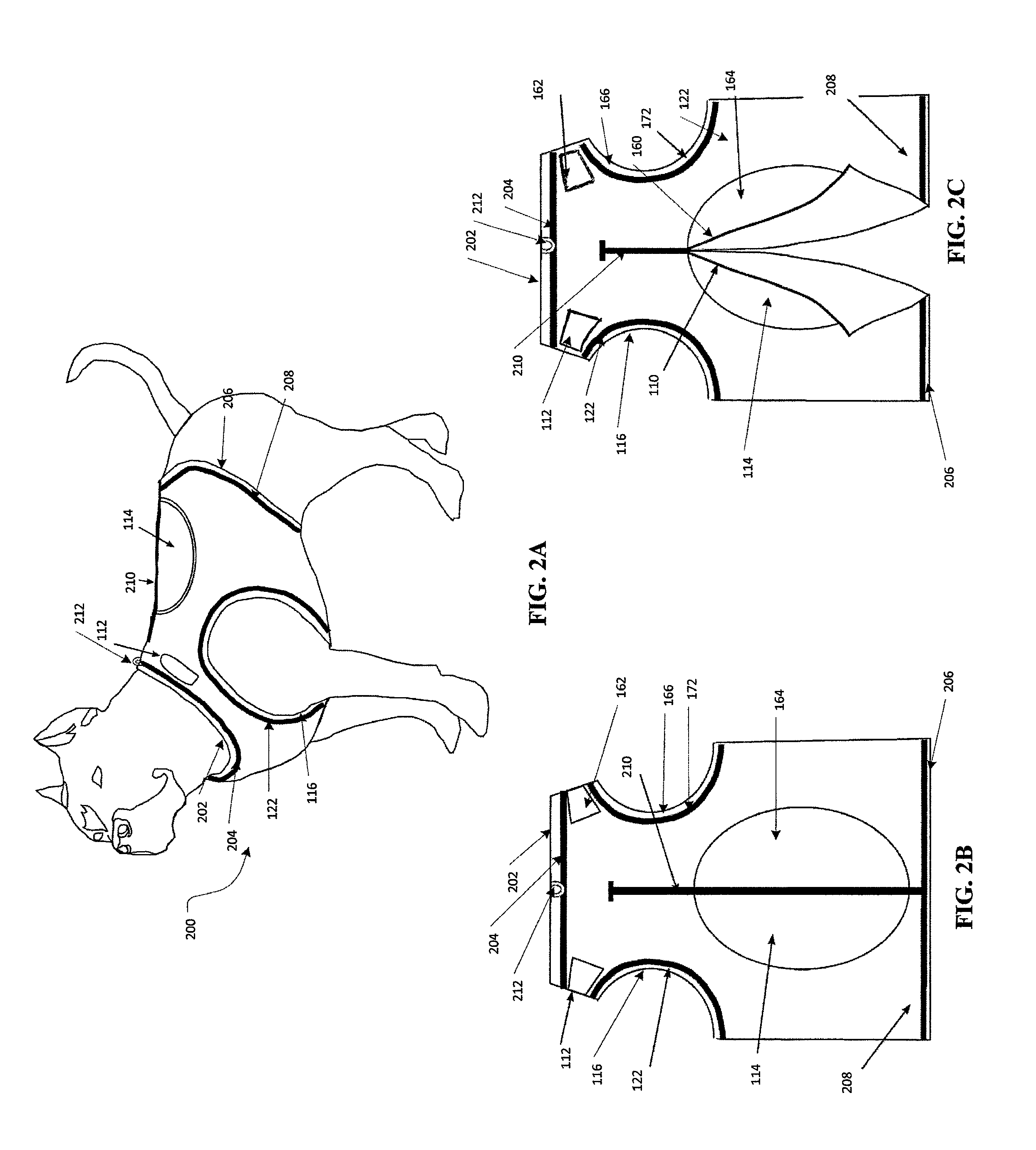
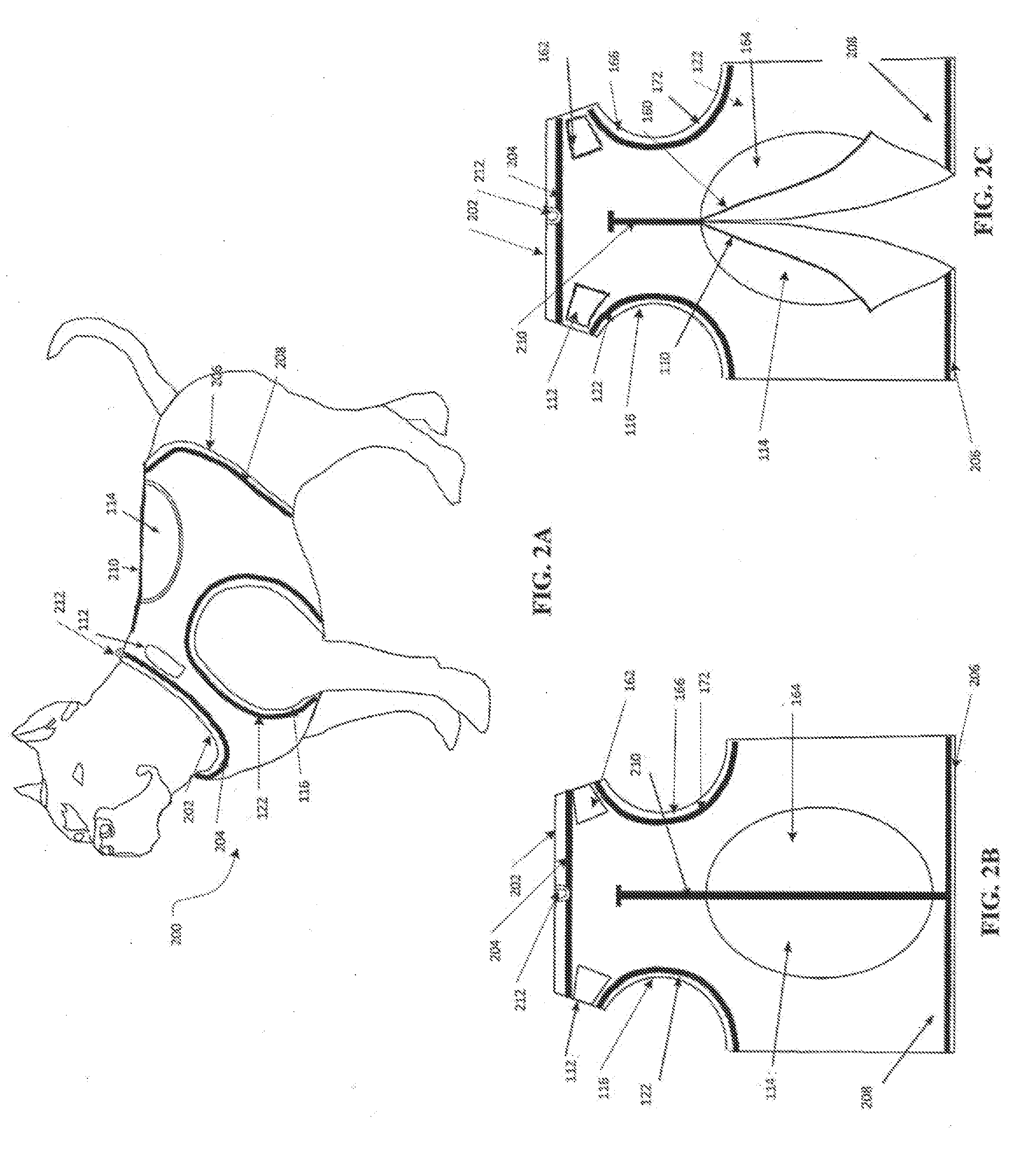
Motion control weighted canine fitness garment
ActiveUS20130333628A1Safely distributeIncrease muscle strengthTaming and training devicesGrooming devicesPhysical exerciseEngineering
A pet vest adapted to safely secure weights to a pet to improve the health benefits of exercise and a method for using same.
Owner:FPW INT LLC
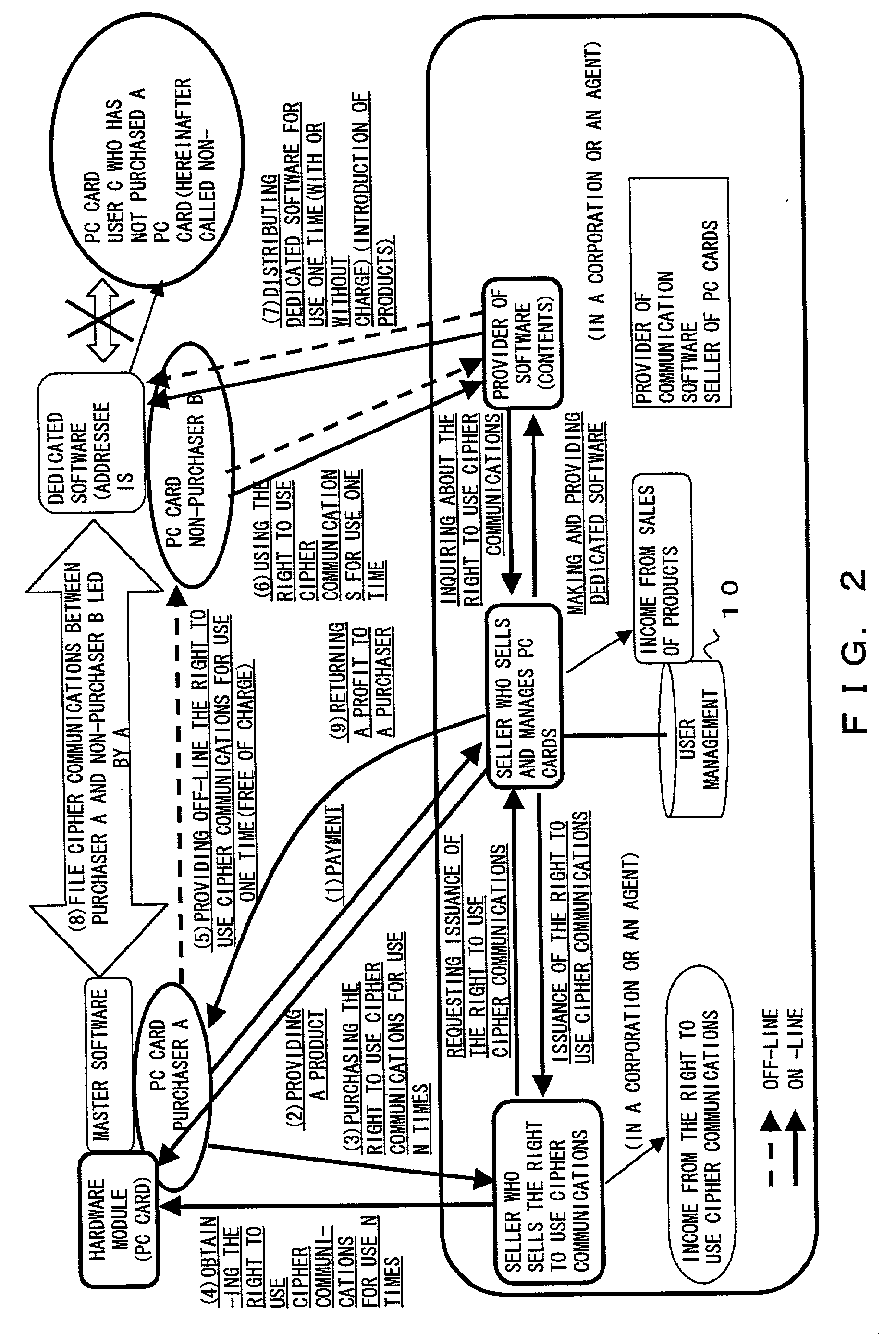
Setting information distribution apparatus, method, program, and medium, authentication setting transfer apparatus, method, program, and medium, and setting information reception program
InactiveUS7913080B2Guaranteed correctnessImprove convenienceKey distribution for secure communicationUser identity/authority verificationComputer terminalAuthentication
A setting information distribution apparatus belonging to a first network, comprises: authentication unit that receives and authenticates an authentication request from a user terminal which requires an access authentication by using a network access authentication procedure between the user terminal and the first network; transmitting unit that transmits an authentication cooperation request which requires setting data to be set to the user terminal to another, network by using the network access authentication procedure and an authentication cooperation procedure between a plurality of networks; and distribution unit that distributes a first response message added with setting data to the user terminal by producing the first response message corresponding to the authentication request by adding the setting data included in a second response message corresponding to the authentication cooperation request.
Owner:FUJITSU LTD
Content Distribution system, Terminal, and Server
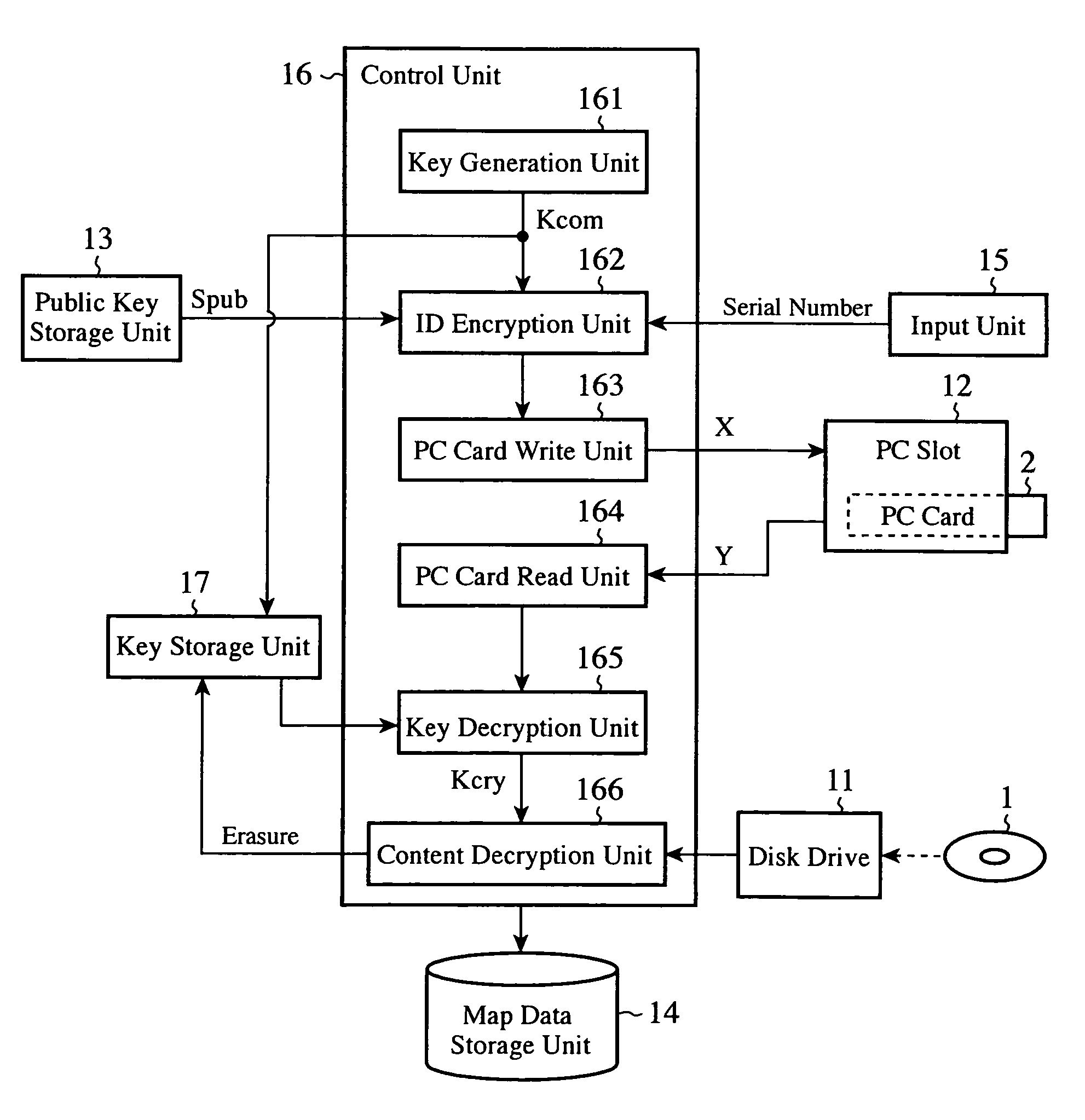
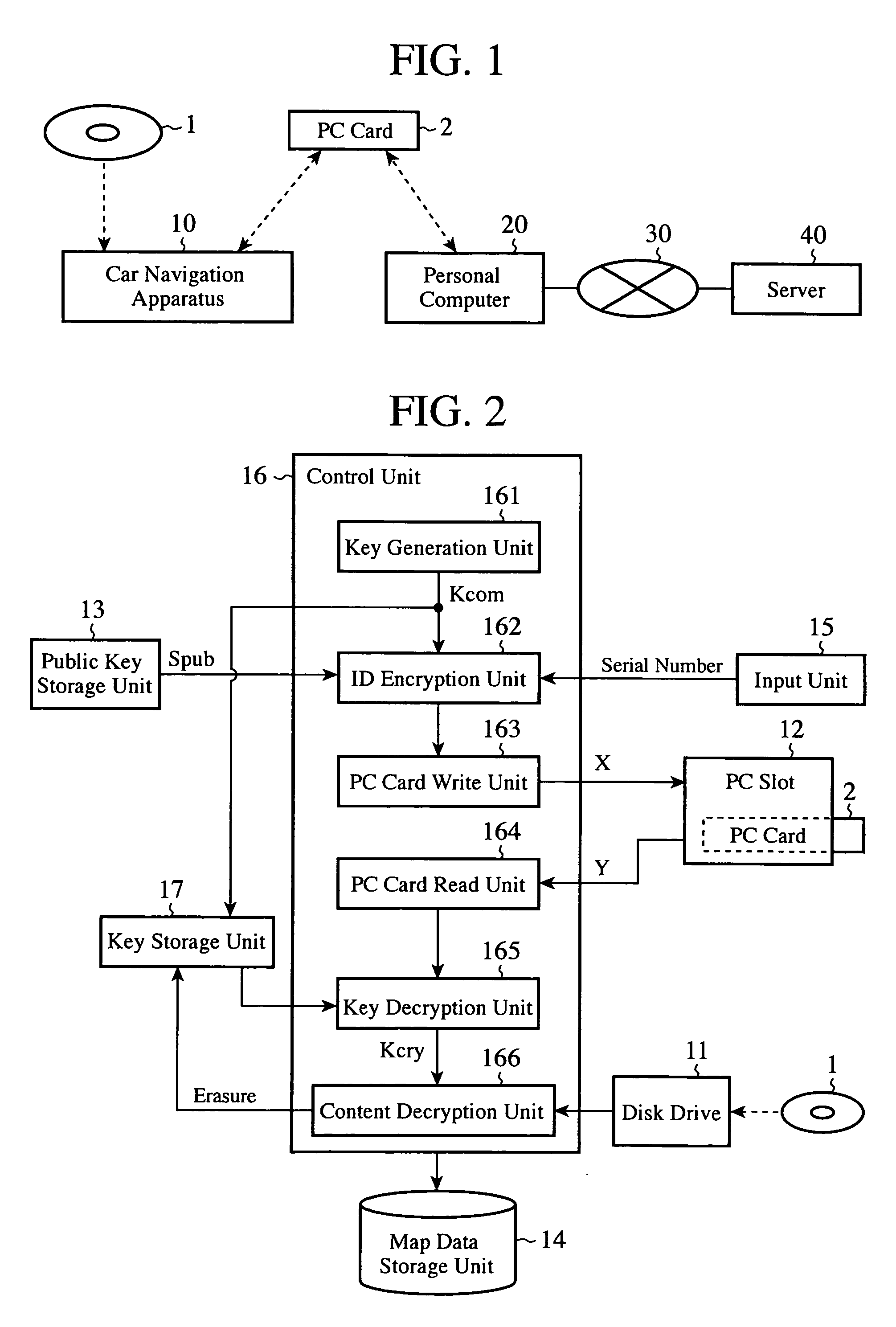
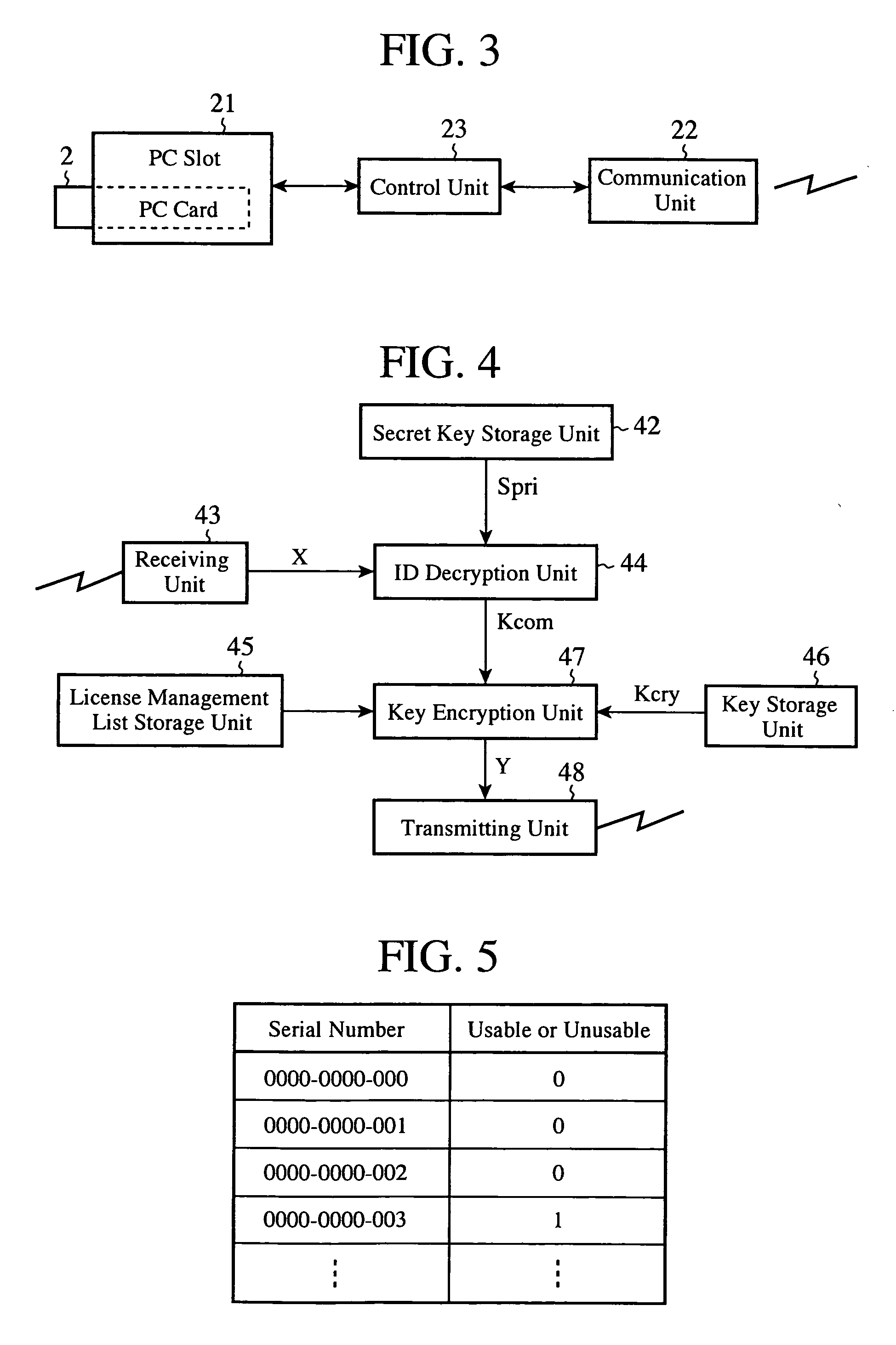
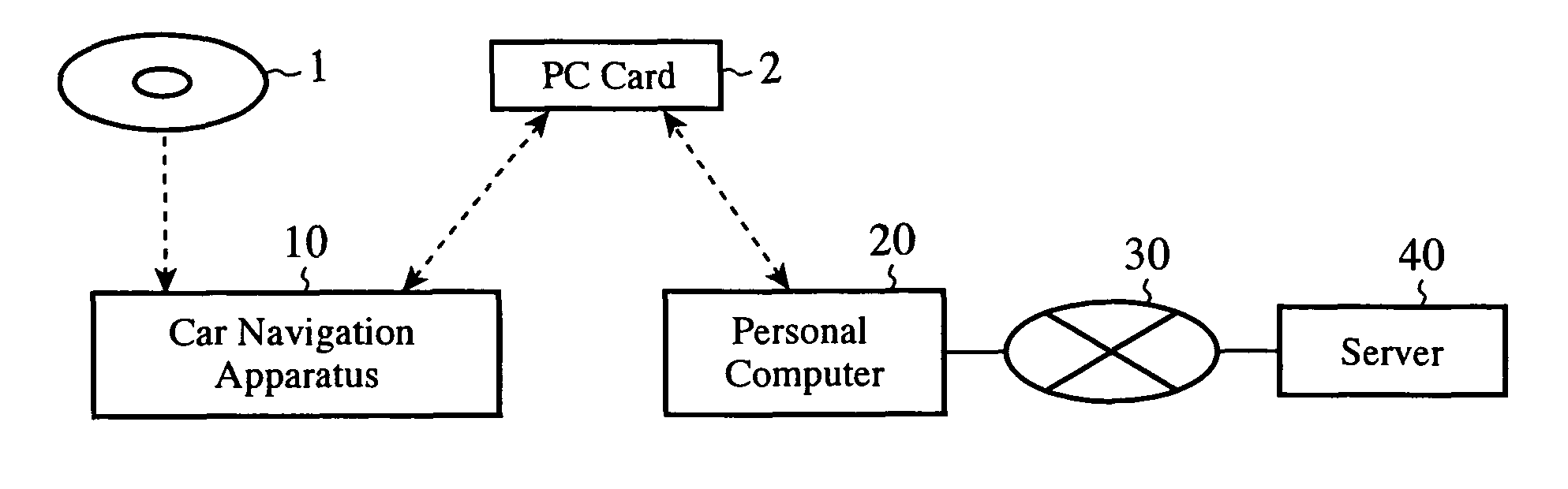
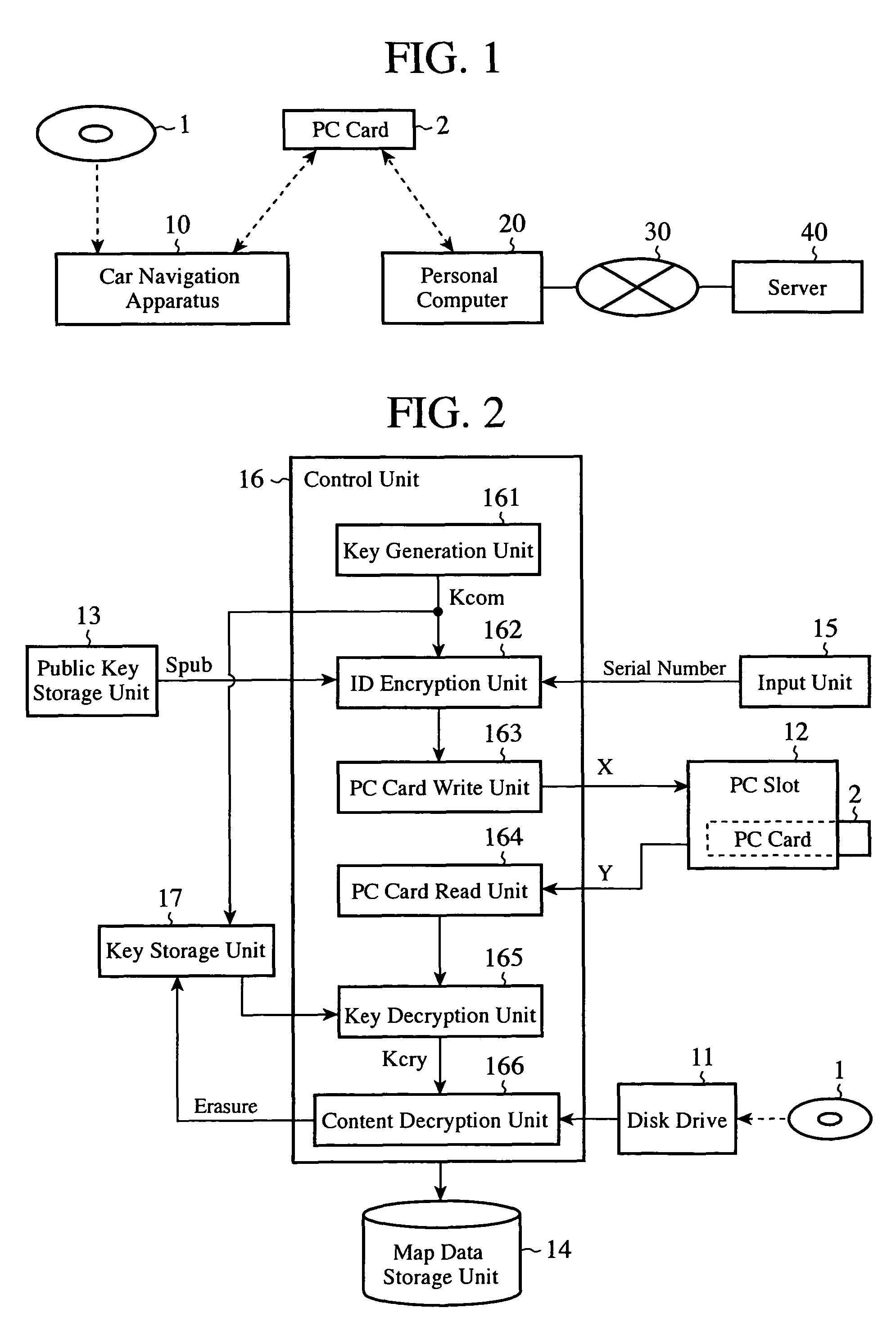
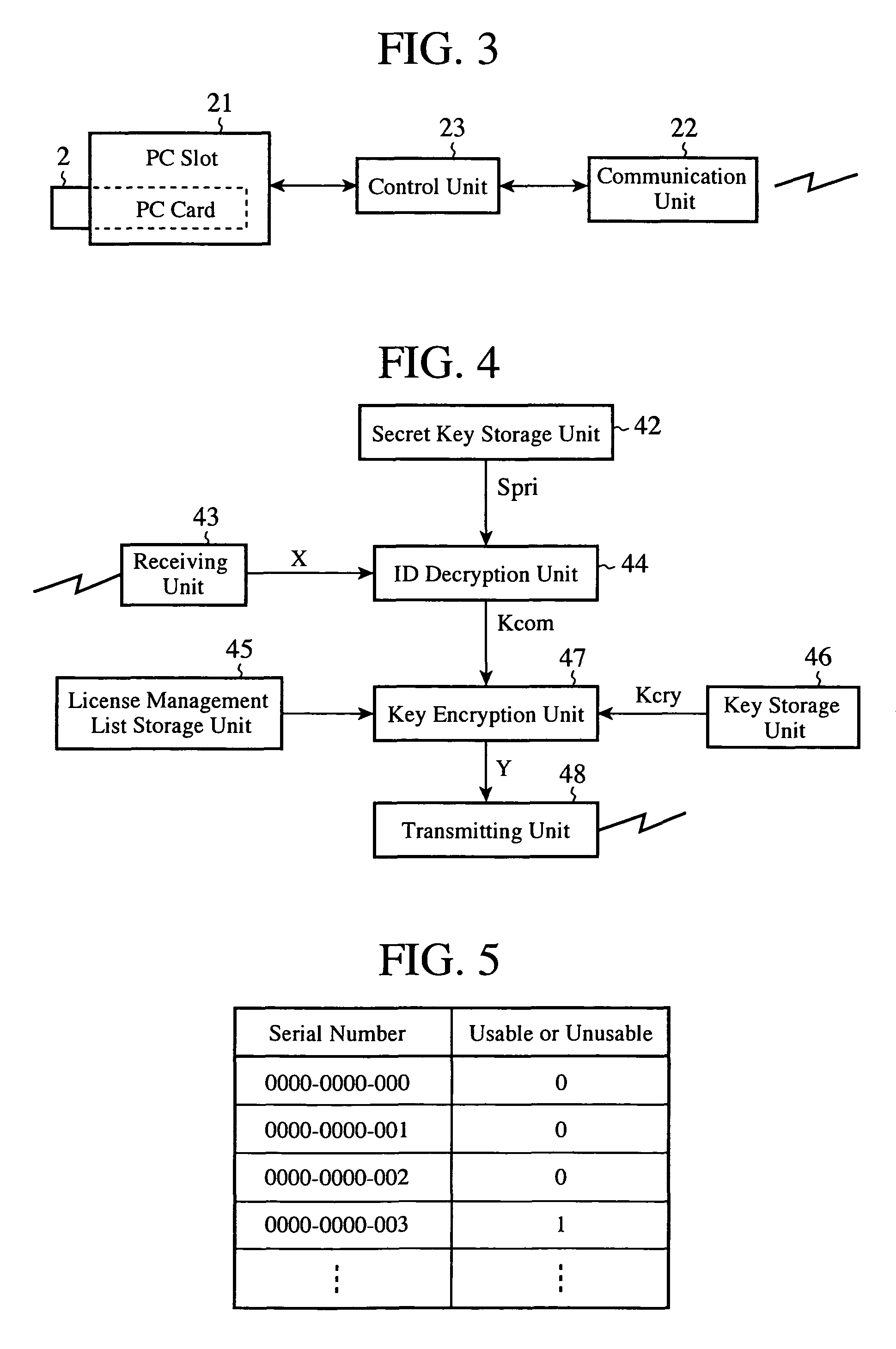
ActiveUS20090265539A1Ensure safe distributionKey distribution for secure communicationDigital data processing detailsContent distributionComputer terminal
A terminal writes first encrypted data in which a communication key and an owner ID are encrypted by using a public key into a second recording medium, and this medium is mounted to a communication apparatus so that the first encrypted data are transmitted to a server. The server sends second encrypted data which it acquires by encrypting a content decryption key by using the communication key which the server acquires by decrypting the received first encrypted data by using a secret key to the communication apparatus, and causes the communication apparatus to record them into the second recording medium. The terminal decrypts a content stored in a first recording medium by using the content decryption key which it acquires by decrypting the second encrypted data read from the second recording medium by using the communication key.
Owner:MITSUBISHI ELECTRIC CORP
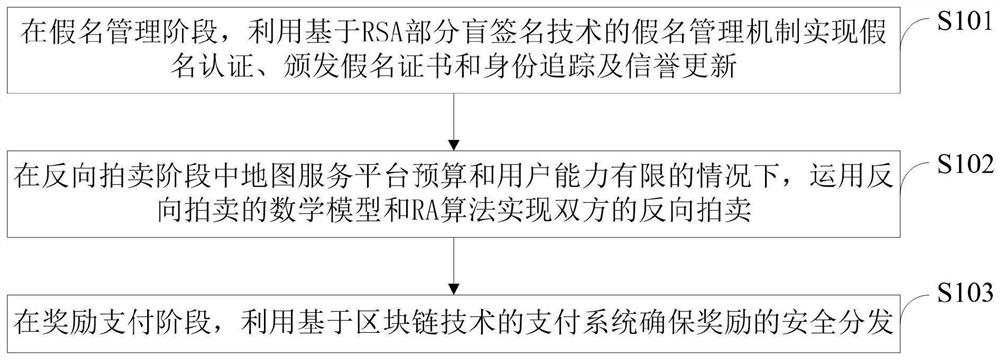
Security-based excitation method with privacy protection and real-time map updating system
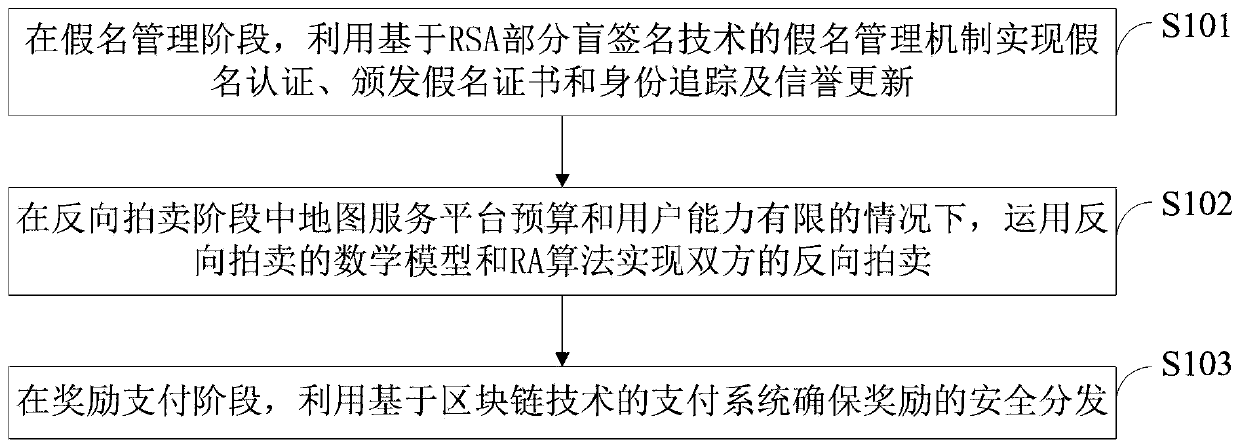
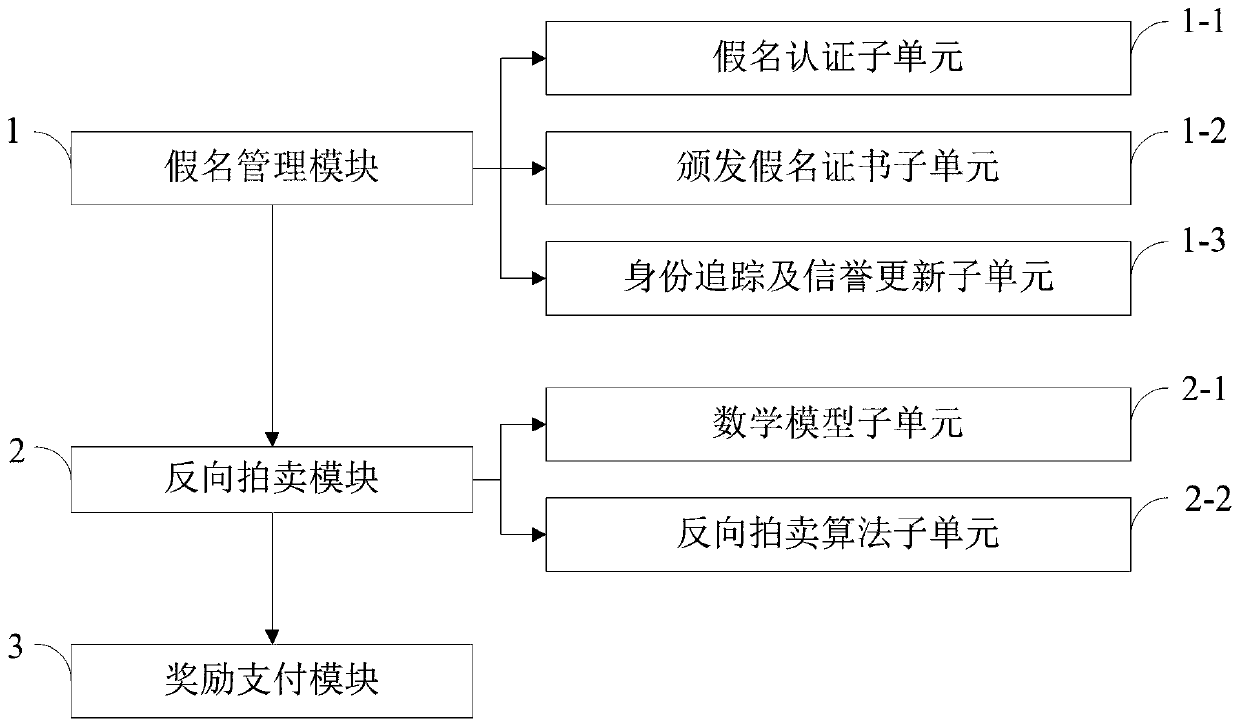
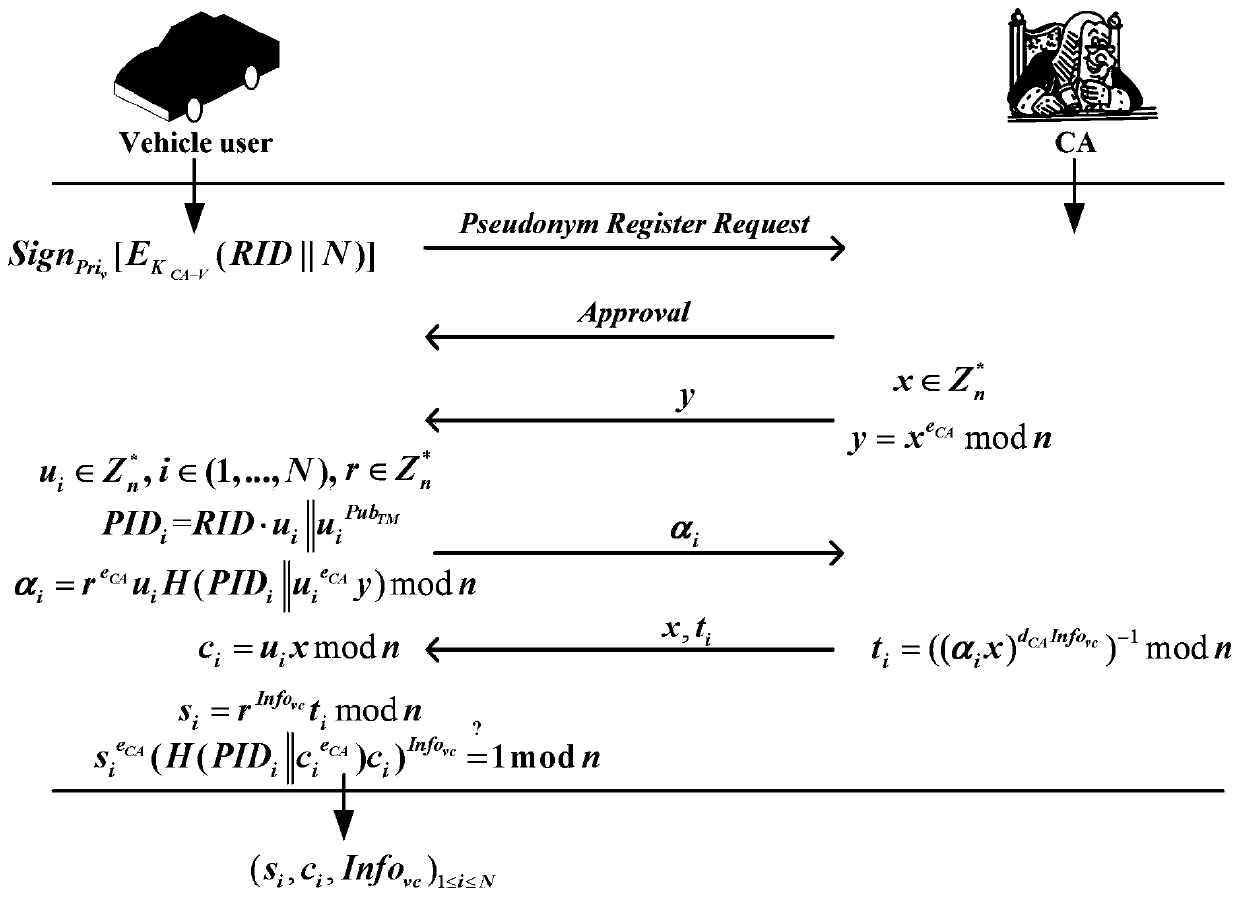
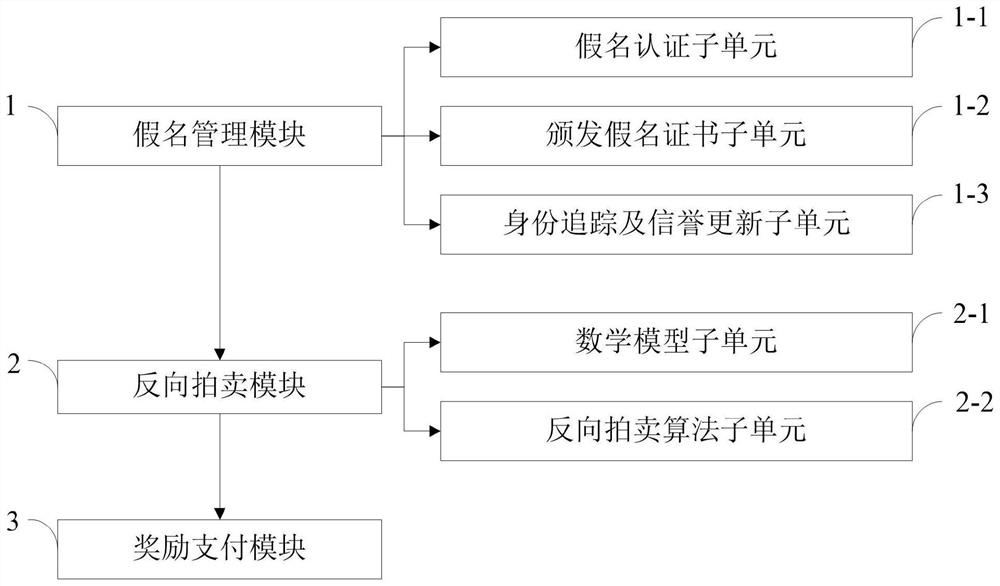
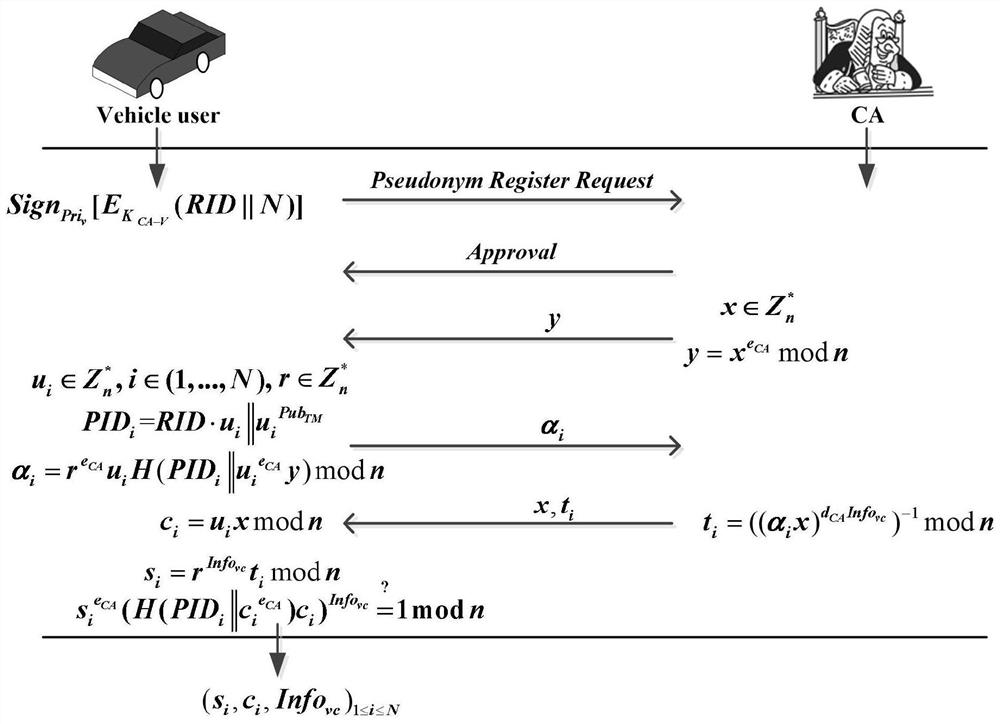
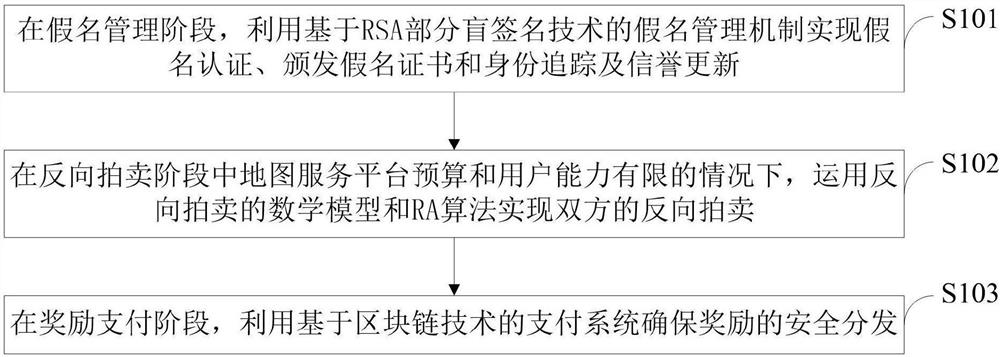
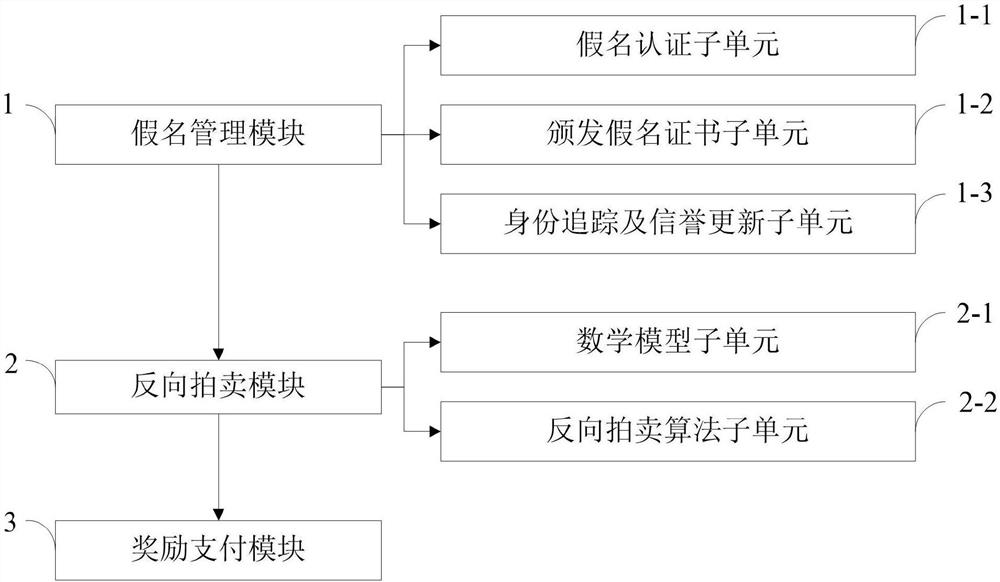
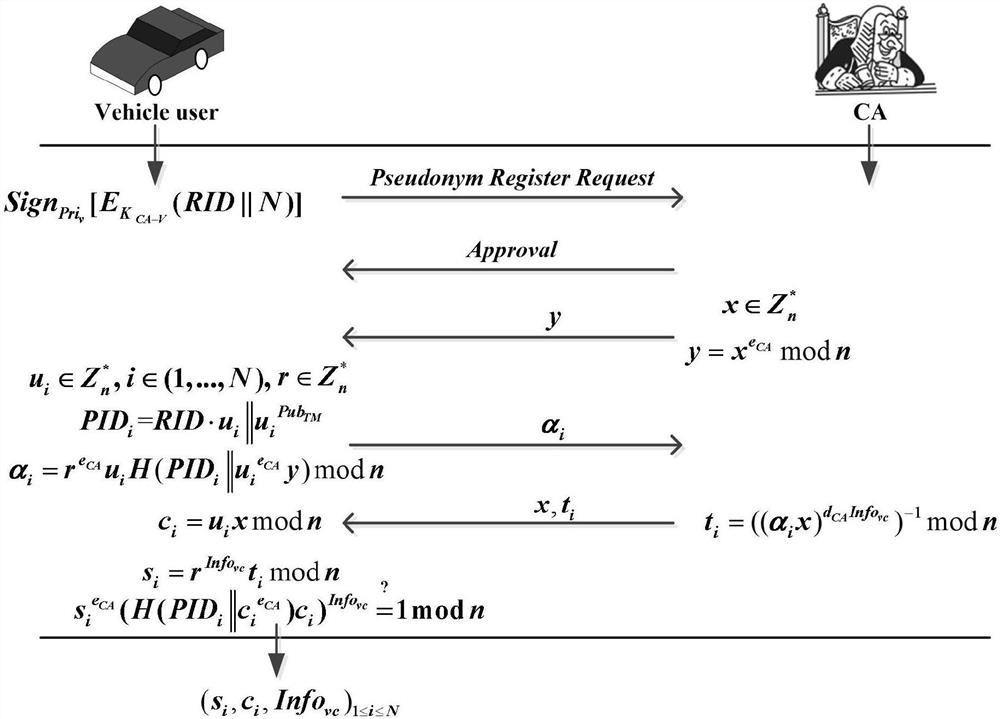
ActiveCN110677395AEnhanced anonymitySolve privacy and security issuesUser identity/authority verificationDigital data protectionMathematical modelPrivacy protection
The invention belongs to the technical field of vehicle map updating in the Internet of Vehicles, and discloses a safe excitation method with privacy protection and a real-time map updating system, which realize pseudonym authentication, pseudonym certificate issuing, identity tracking and reputation updating by utilizing an RSA partial blind signature technology. Reverse auction of the two parties is realized by applying a mathematical model of reverse auction and an RA algorithm; a payment system based on a blockchain technology is used to ensure secure distribution of rewards. The real-timemap updating system comprises a pseudonym management module, a reverse auction module and a reward payment module. According to the invention, the problems of payment control of a map service platform and completion quality of vehicle users are solved by applying a reverse auction algorithm; based on the RSA partial blind signature technology, the security of the excitation method is ensured, andthe privacy security problem of the user is solved; based on the blockchain technology, the problem of updating the reputation account of the user is solved, the safe distribution of rewards is ensured, and the effectiveness of the incentive method is realized.
Owner:XIAN UNIV OF POSTS & TELECOMM
Motion control weighted canine fitness garment
ActiveUS9155286B2Increase muscle strengthImprove stabilityTaming and training devicesGrooming devicesEngineeringCompanion animal
A pet vest adapted to safely secure weights to a pet to improve the health benefits of exercise and a method for using same.
Owner:FPW INT LLC
Software module management device and program
ActiveUS8417964B2Updating the existing software module safelyDistributing more safely the new software moduleUnauthorized memory use protectionHardware monitoringCryptographic protocolComputer module
Owner:TOSHIBA DIGITAL SOLUTIONS CORP +1
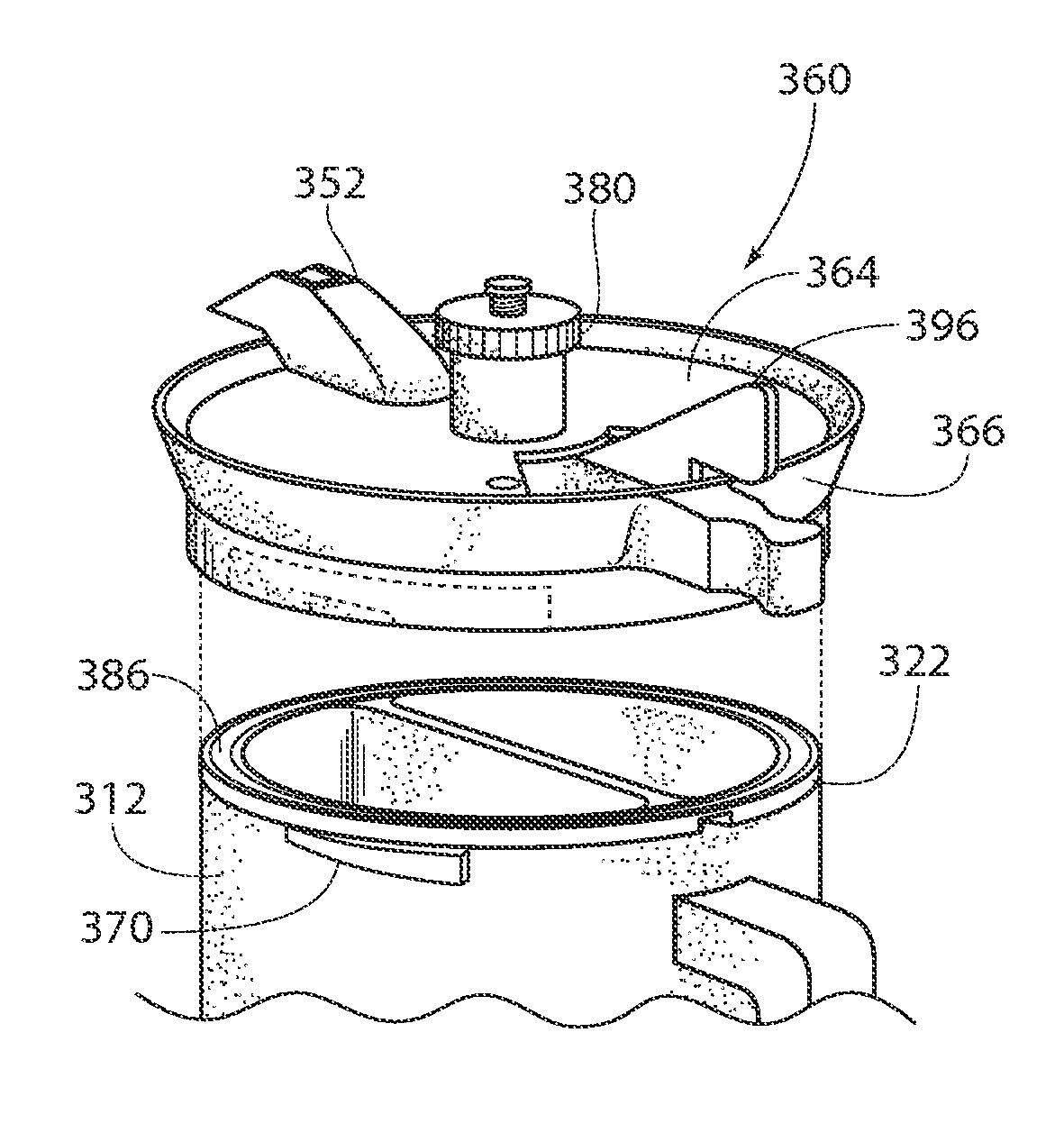
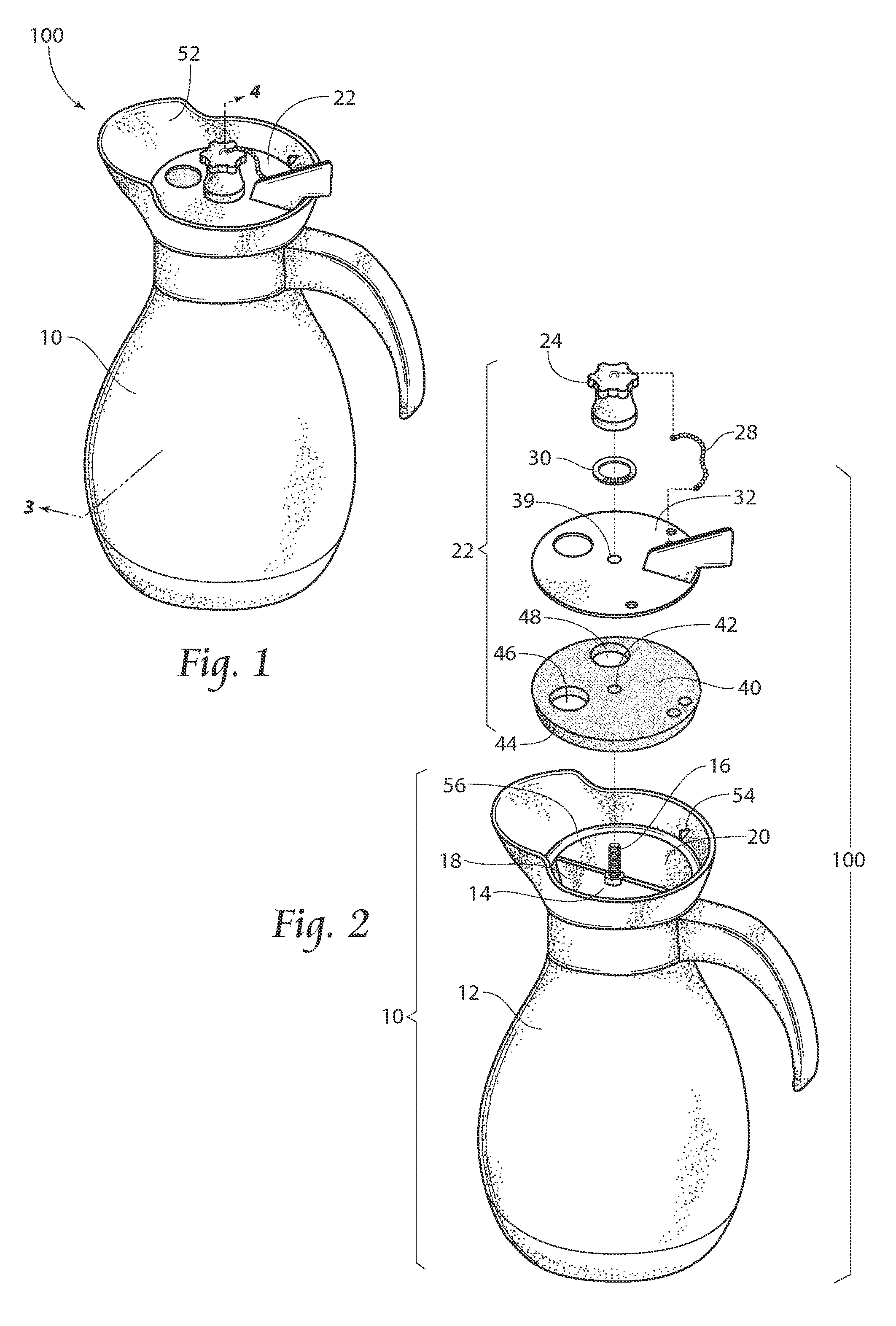
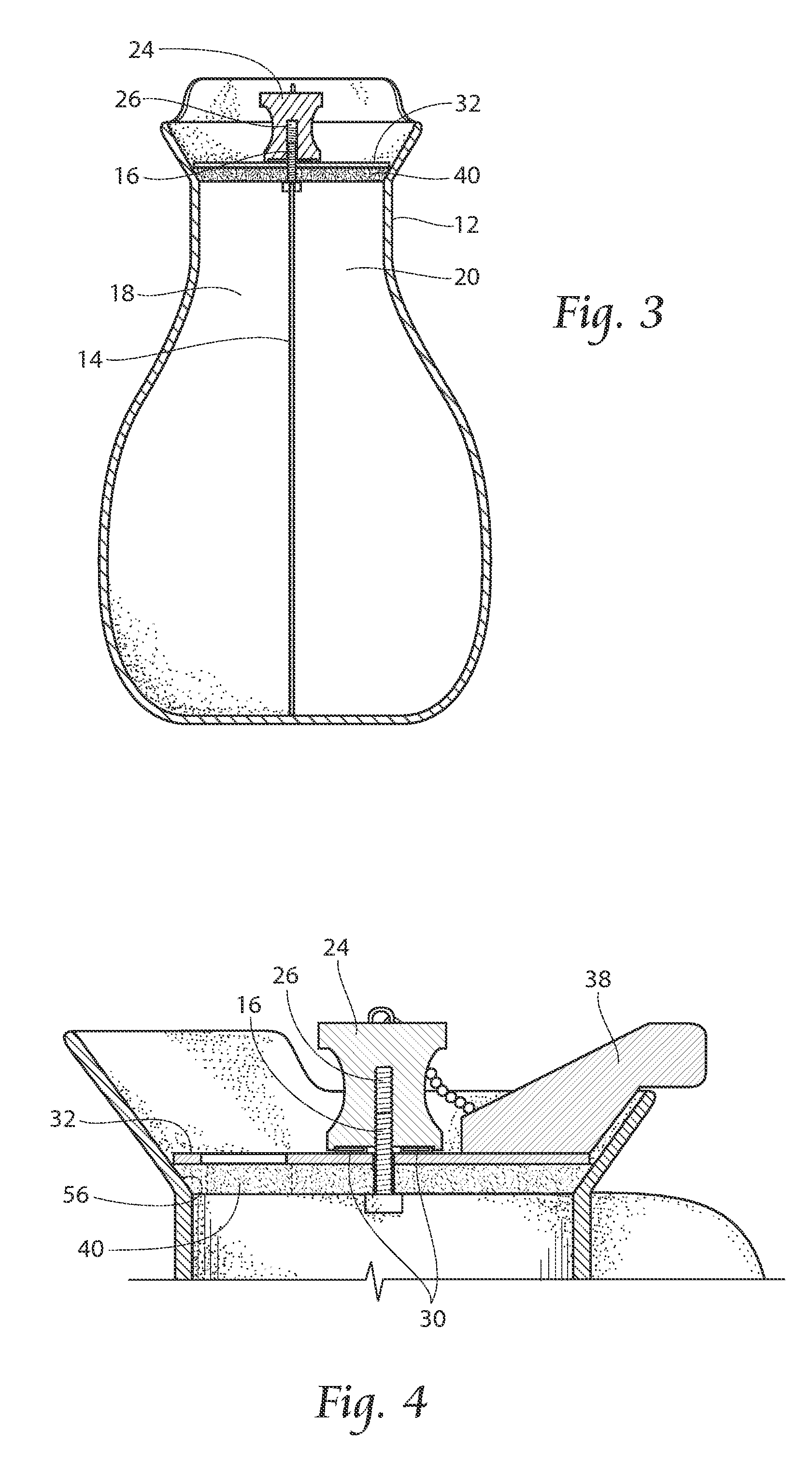
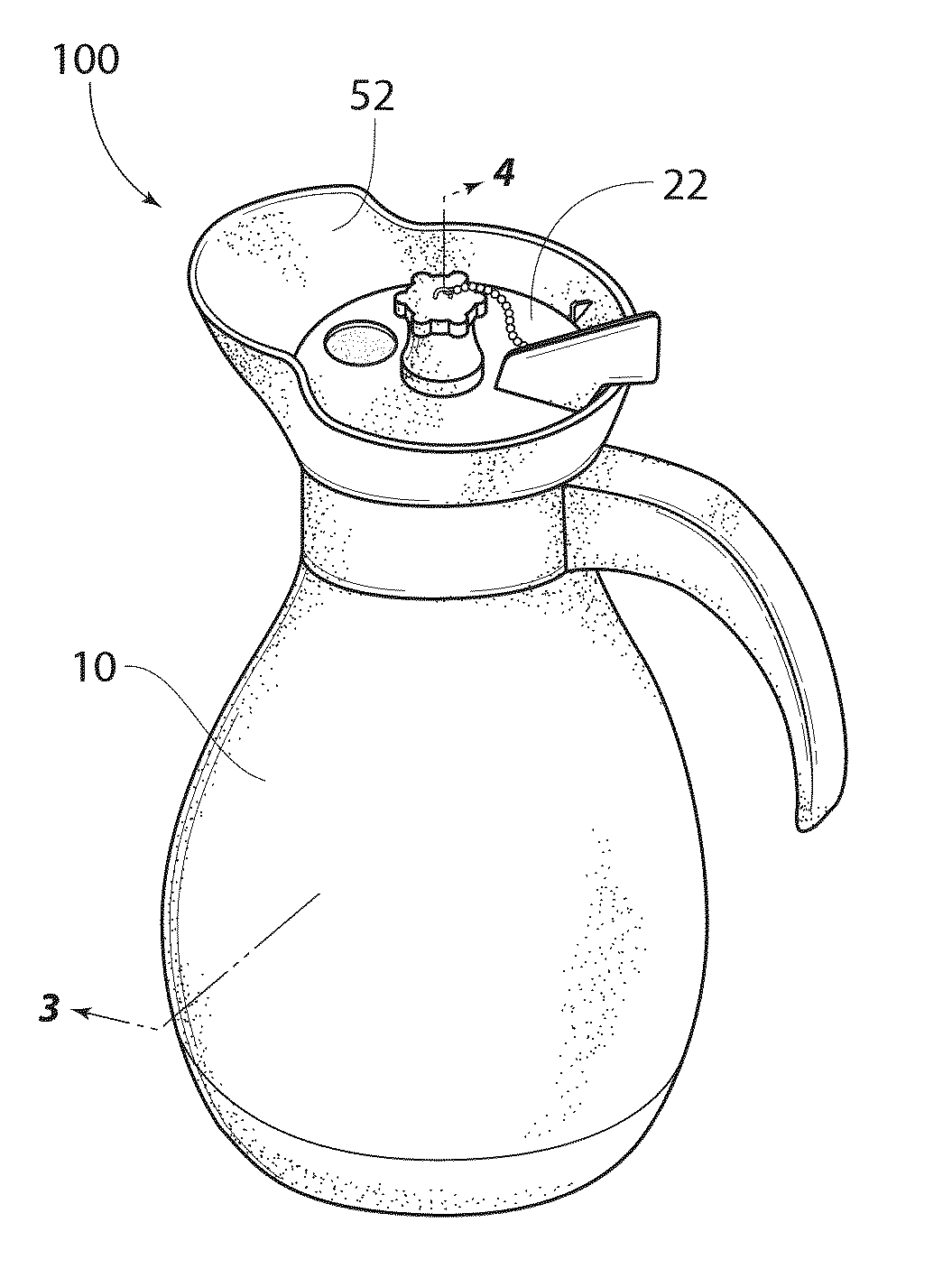
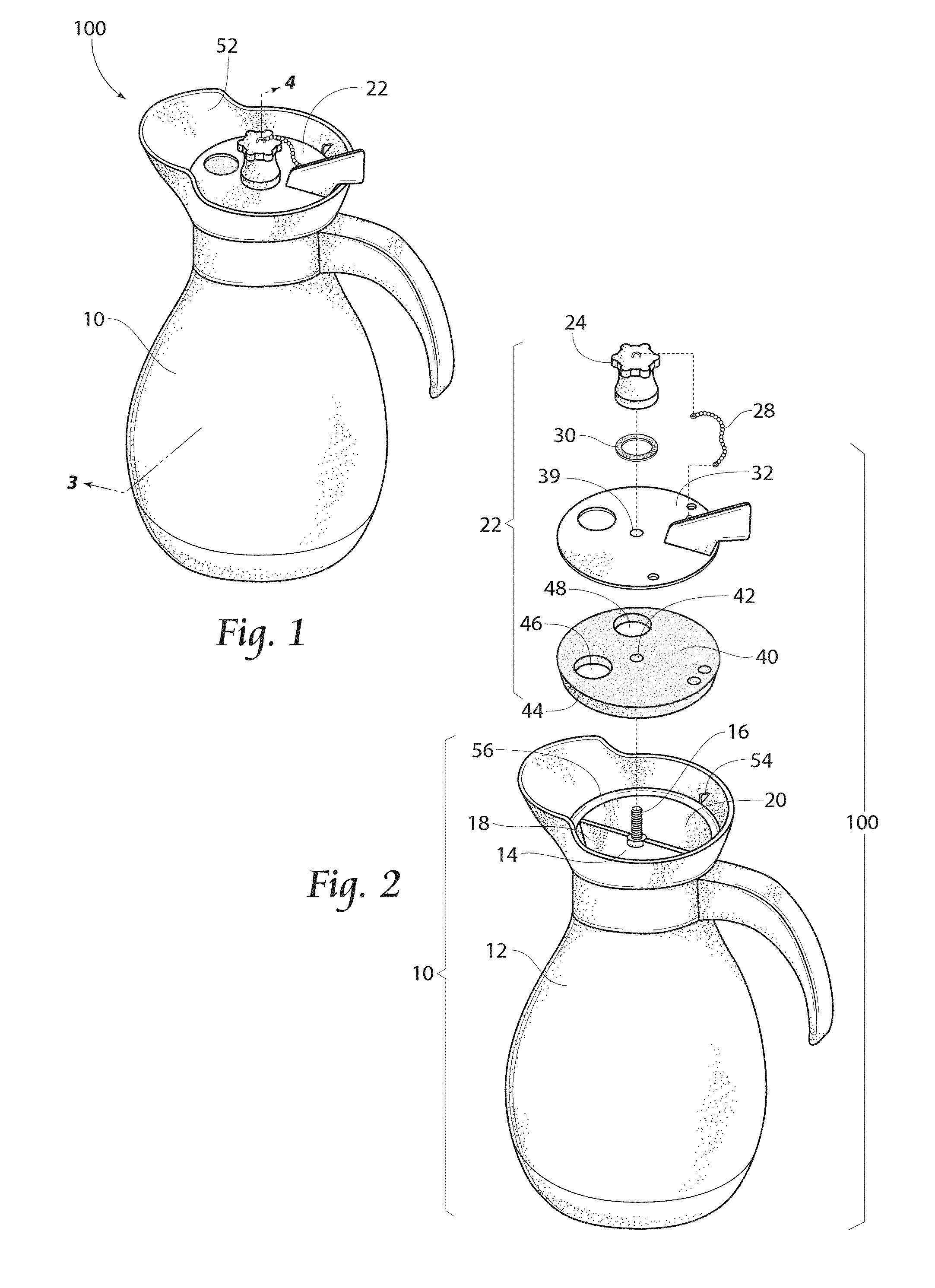
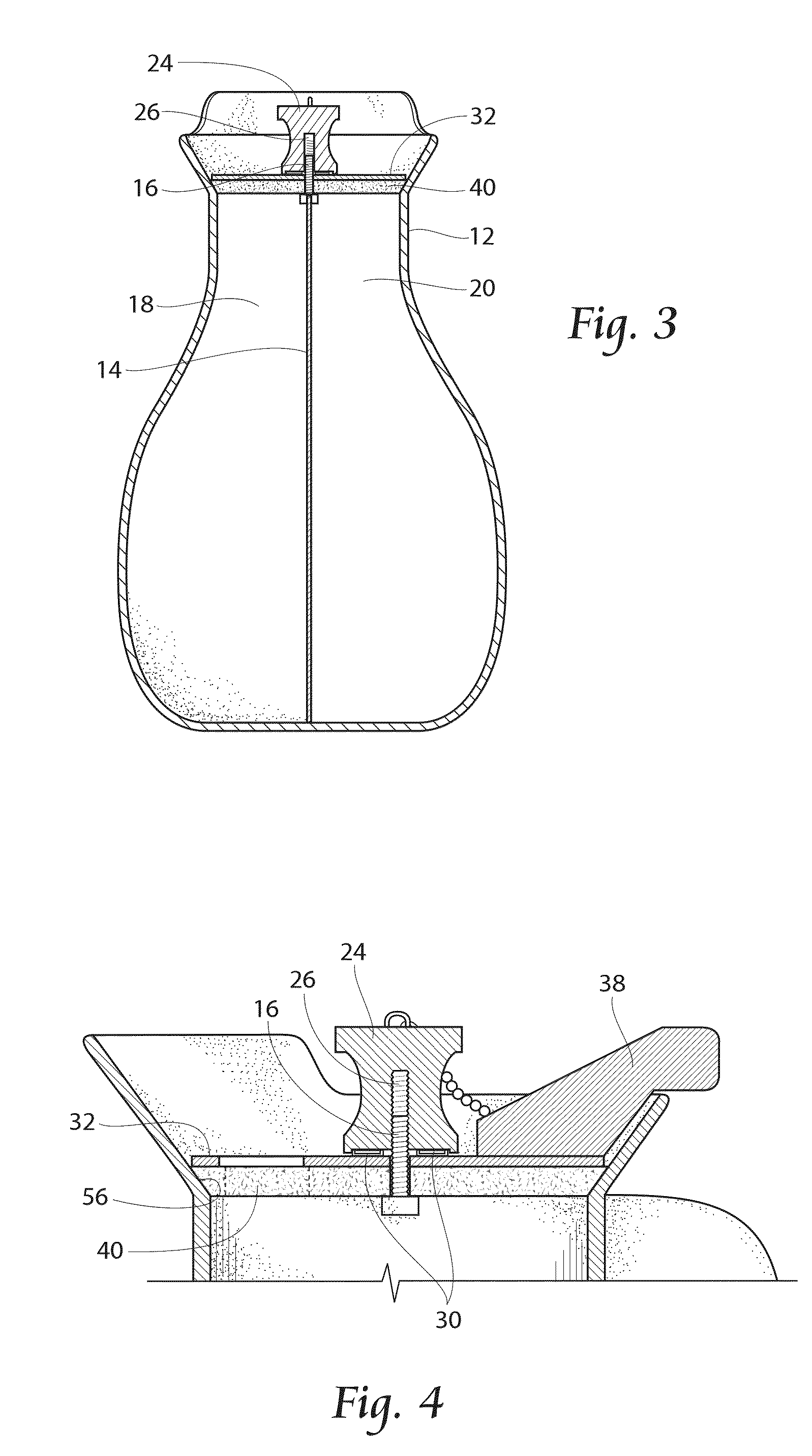
Beverage container
InactiveUS20130026185A1Ensure safe distributionLiquid flow controllersLiquid transferring devicesEngineering
Owner:HORVATH RONALD F +4
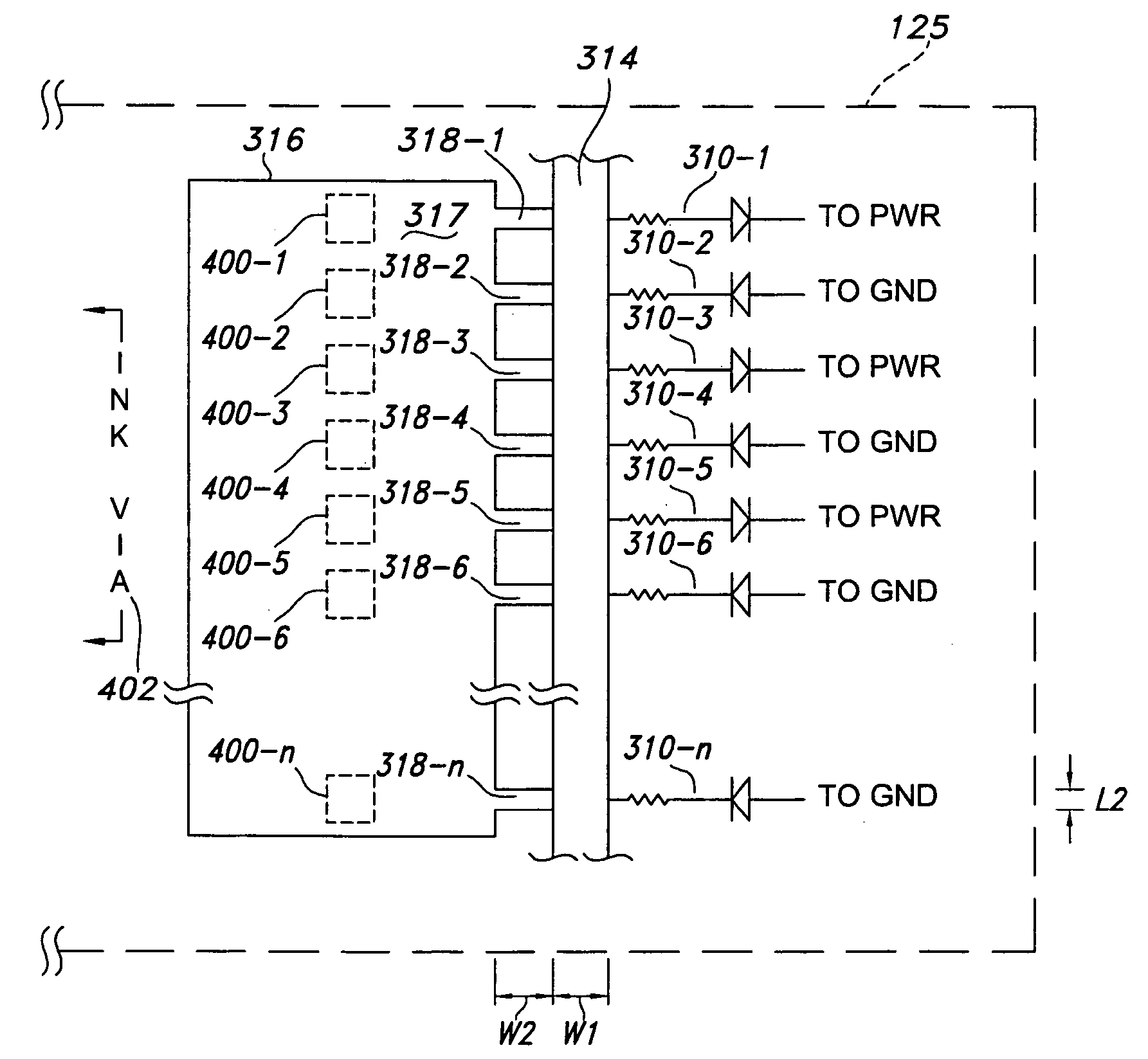
Actuator chip for inkjet printhead with electrostatic discharge protection
InactiveUS7361966B2Discharge safetyEnsure safe distributionSemiconductor/solid-state device manufacturingPrintingBallast resistorCavitation
An inkjet printhead chip includes electrostatic discharge (ESD) circuits to protect the chip during ESD events, including one preventing a thin dielectric layer on a substrate from breakdown. In one embodiment, the chip includes an ESD circuit essentially dedicated per each actuator. In another, ESD circuits alternate connection between power and ground. In still another, actuators are approximately equidistantly spaced regarding respective ESD circuits. Exemplary ESD circuits include a ballast resistor in series with a diode. In turn, diodes are either forward biased toward power or away from ground. In a thermal inkjet embodiment, a cavitation layer above a resistor and dielectric layer have pluralities of fingers connecting the cavitation layer to a metal buss. The metal buss attaches to the ballast resistors. Protection typically embodies the safe distribution of ESD current to ground during both chip manufacture and user printhead installation. Inkjet printheads and printers are also disclosed.
Owner:FUNAI ELECTRIC CO LTD
Motion control weighted canine fitness garment
InactiveUS20150373948A1Increase muscle strengthImprove stabilityTaming and training devicesGrooming devicesEngineeringCompanion animal
A pet vest adapted to safely secure weights to a pet to improve the health benefits of exercise and a method for using same.
Owner:BALL DYNAMICS INT
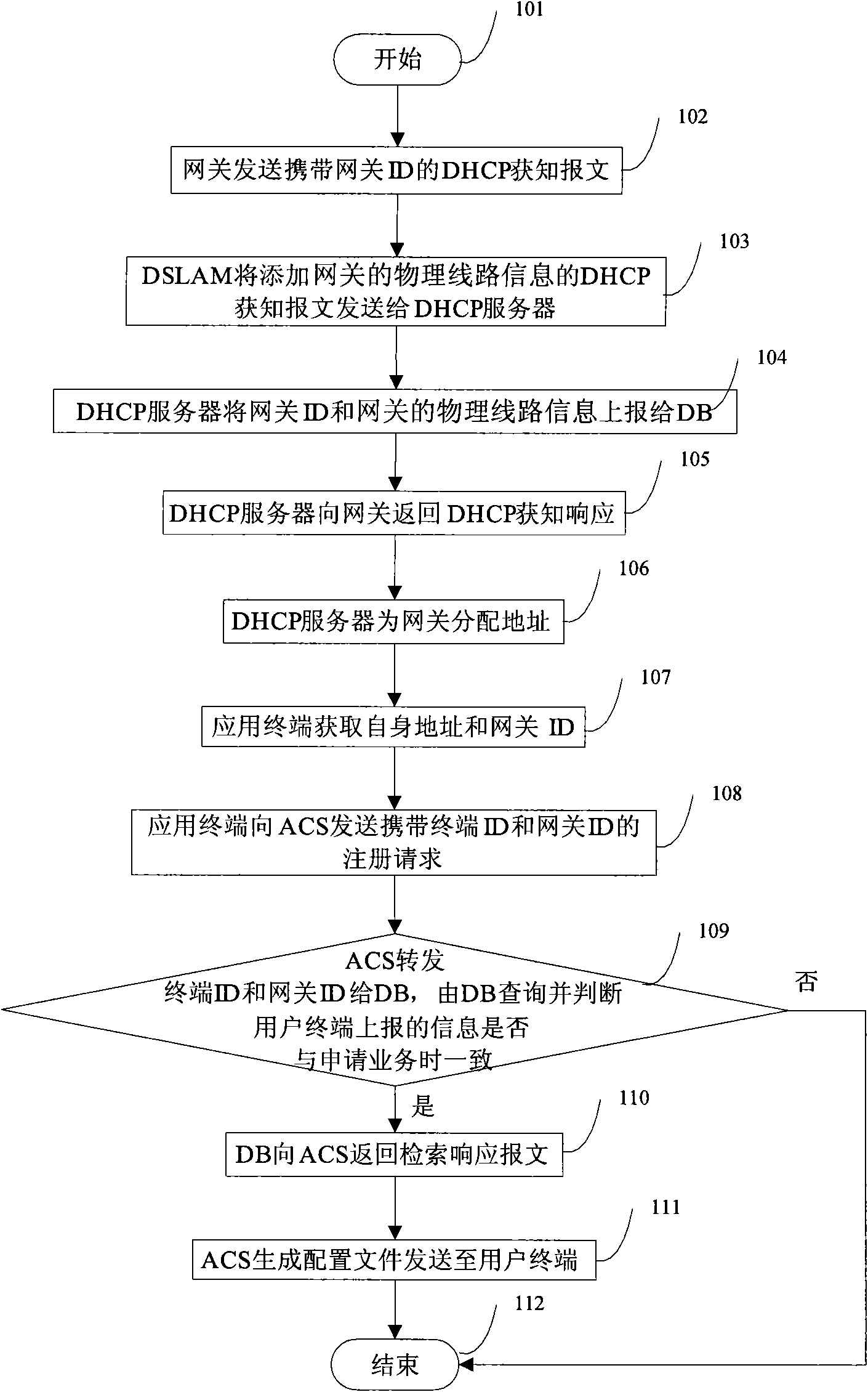
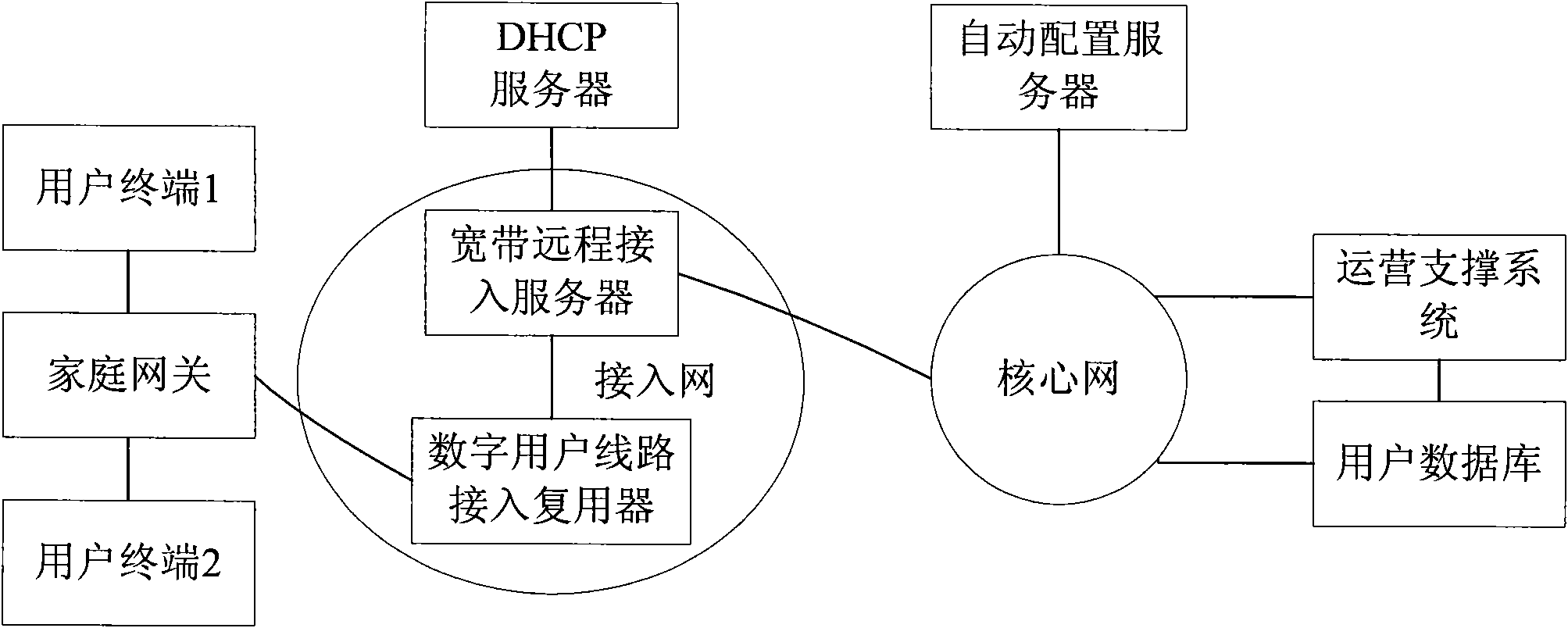
Method and system for sending terminal services
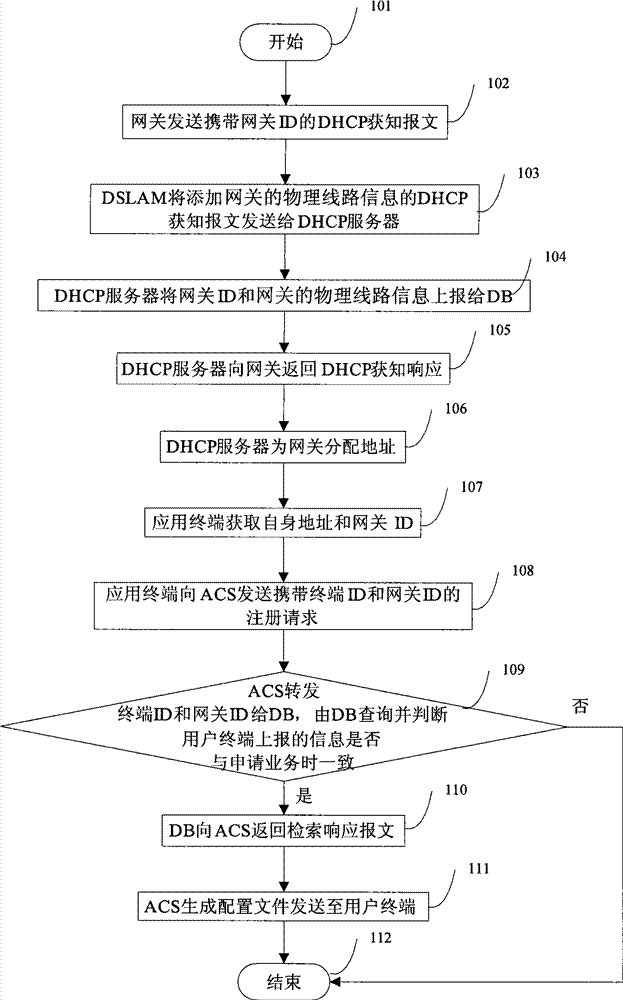
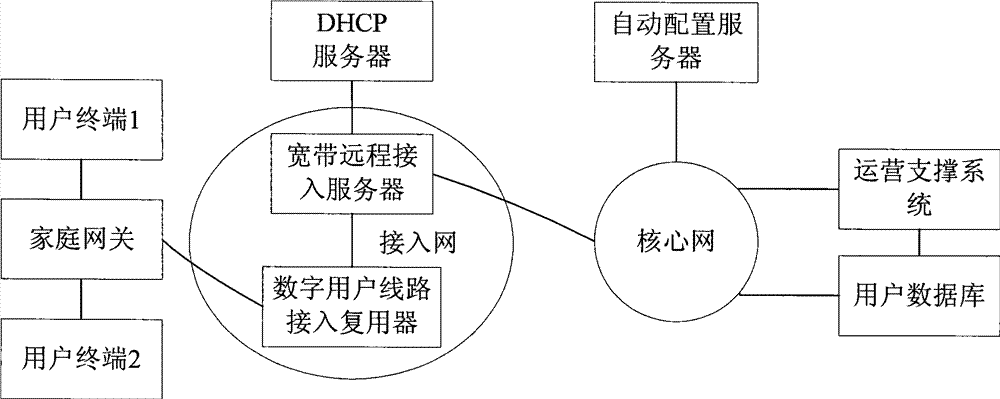
InactiveCN101662456AEnsure safe distributionRealize the bindingData switching by path configurationNetwork connectionsComputer network
The invention discloses a method and a system for sending terminal services. The method comprises the following steps: sending a registration request comprising application terminal identification information and gateway identification information to an automatic configuration server (ACS); and receiving the configuration, corresponding to an application terminal, sent by the ACS, wherein the application terminal identification information and the gateway identification information are sent to a user database (DB) by the ACS; the DB sends user service data to the ACS after determining the userservice data corresponding to the application terminal according to the application terminal identification information, the gateway identification information and physical line information of a gateway; and the ACS sends the configuration to the terminal after generating the configuration according to the user service data. The method and the system for sending the terminal services provided bythe invention can ensure that the services corresponding to the application terminal linked to the gateway are safely sent.
Owner:南通市通州区新志浩实业有限公司
Content distribution system, terminal, and server
ActiveUS8225415B2Ensure safe distributionKey distribution for secure communicationDigital data processing detailsContent distributionComputer terminal
A terminal writes first encrypted data in which a communication key and an owner ID are encrypted by using a public key into a second recording medium, and this medium is mounted to a communication apparatus so that the first encrypted data are transmitted to a server. The server sends second encrypted data which it acquires by encrypting a content decryption key by using the communication key which the server acquires by decrypting the received first encrypted data by using a secret key to the communication apparatus, and causes the communication apparatus to record them into the second recording medium. The terminal decrypts a content stored in a first recording medium by using the content decryption key which it acquires by decrypting the second encrypted data read from the second recording medium by using the communication key.
Owner:MITSUBISHI ELECTRIC CORP
Method for distributing software
InactiveUS20050055313A1Promote disseminationEasy to useDigital data processing detailsUnauthorized memory use protectionComputer hardwareCommunications software
Owner:FUJITSU LTD
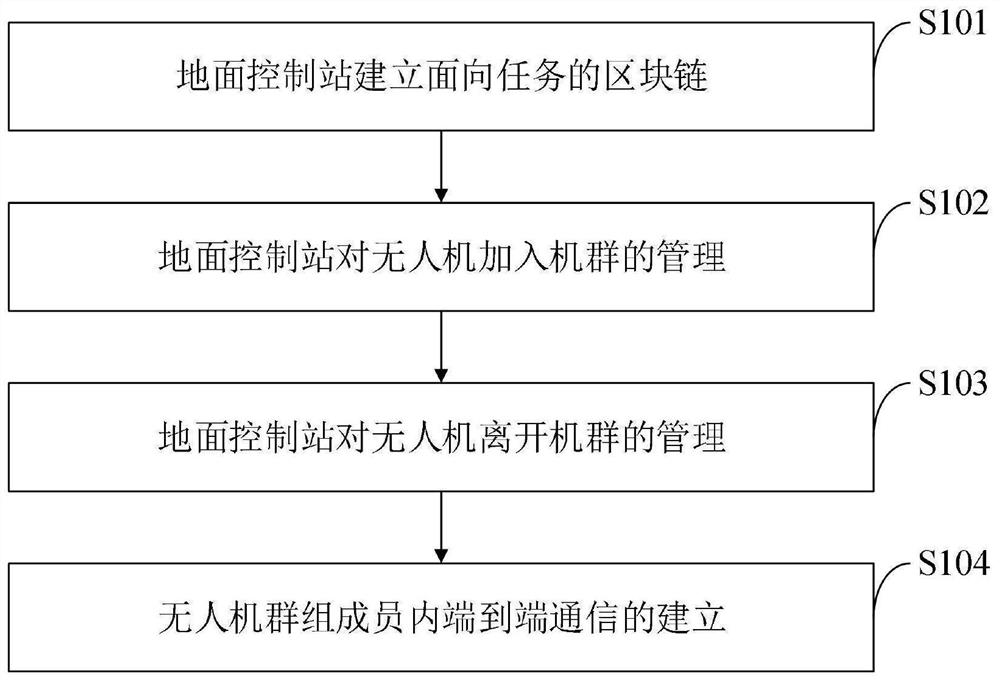
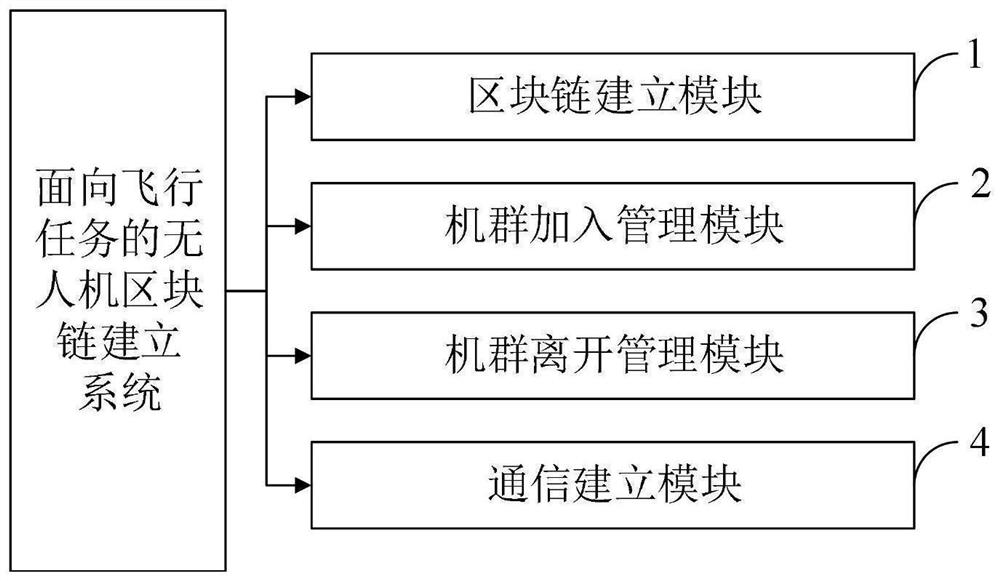
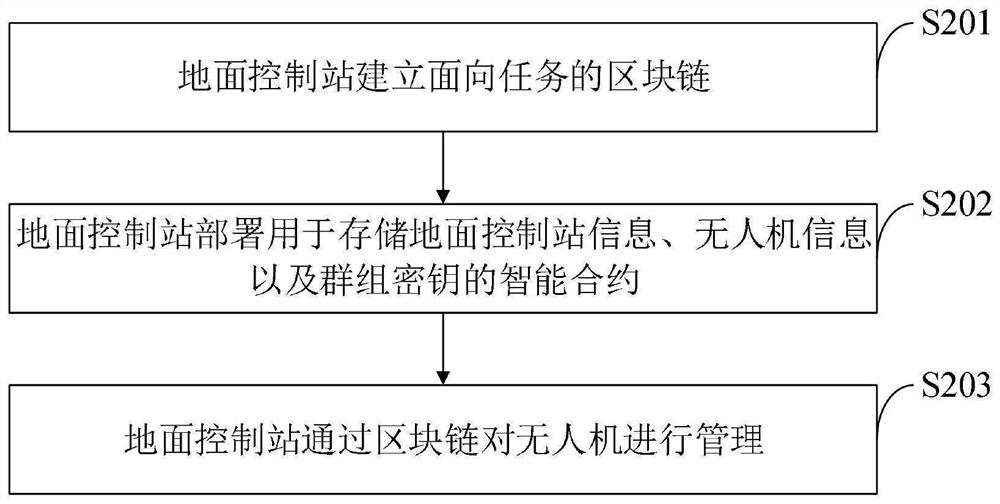
Flight mission-oriented unmanned aerial vehicle block chain establishment method, system, device and terminal
ActiveCN113949432ARealize the establishmentImplement group key managementConnection managementRadio transmissionCommunications securityUncrewed vehicle
The invention belongs to the technical field of unmanned aerial vehicles, and discloses a flight mission-oriented unmanned aerial vehicle block chain establishment method, system, device and terminal, and the flight mission-oriented unmanned aerial vehicle block chain establishment method comprises the steps that a ground control station establishes a task-oriented block chain; the ground control station manages the unmanned aerial vehicles to join the cluster; the ground control station manages the departure of the unmanned aerial vehicles from the cluster; and establishing end-to-end communication in the members of the unmanned aerial vehicle group. According to the invention, the block chain technology is applied to the unmanned aerial vehicle system, and the ground control station establishes a flight task-oriented block chain, so that the ground control station establishes unmanned aerial vehicle group task planning, group key management and end-to-end communication in the unmanned aerial vehicle group; the unmanned aerial vehicle information and the group key recorded in the block chain are difficult to counterfeit or tamper by utilizing the non-tampering characteristic of the block chain, so that the group key is safely distributed when the unmanned aerial vehicle joins or leaves, the trust relationship among unmanned aerial vehicle members is enhanced, and the end-to-end communication safety among the unmanned aerial vehicle group members is realized.
Owner:XIDIAN UNIV +1
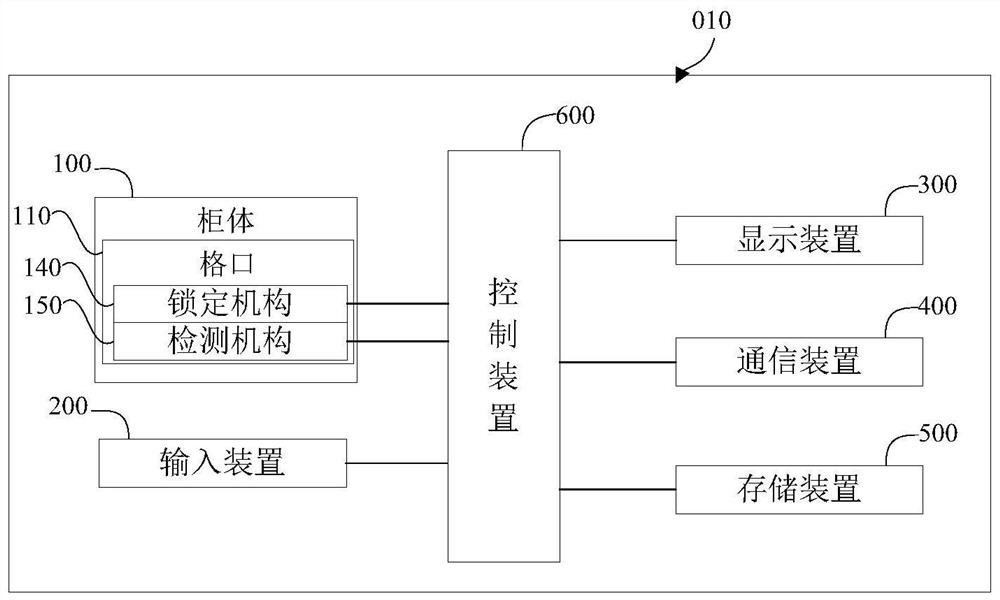
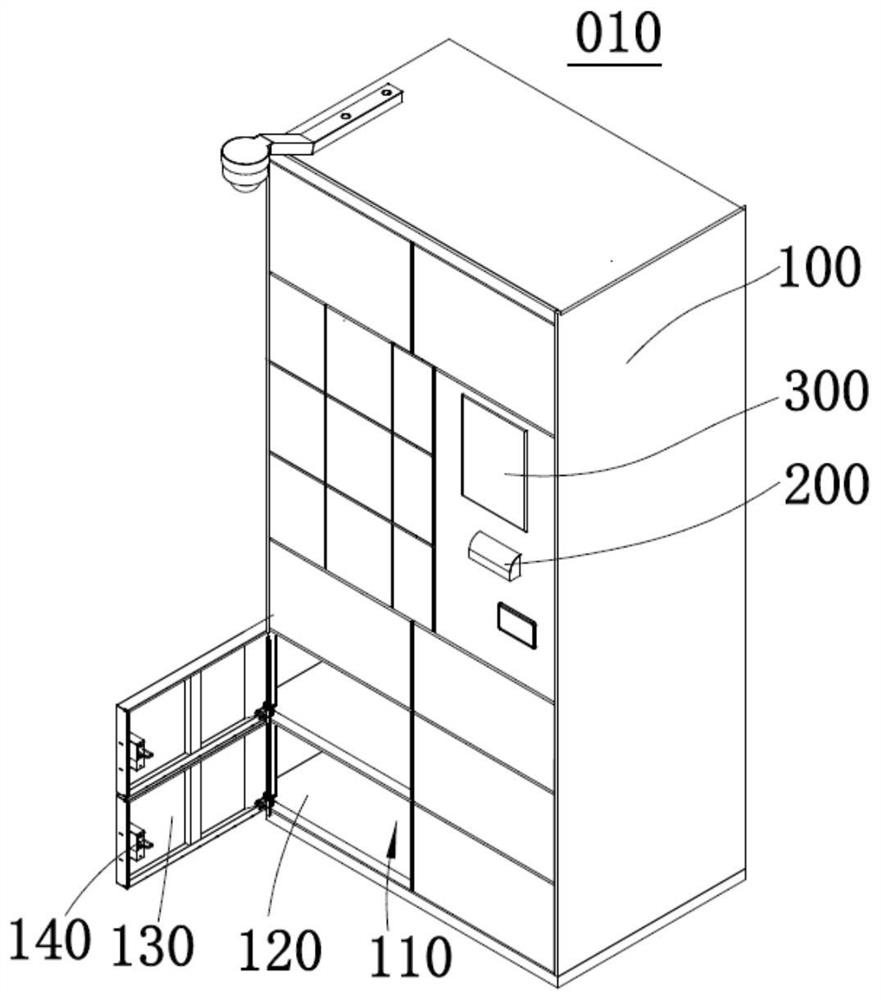
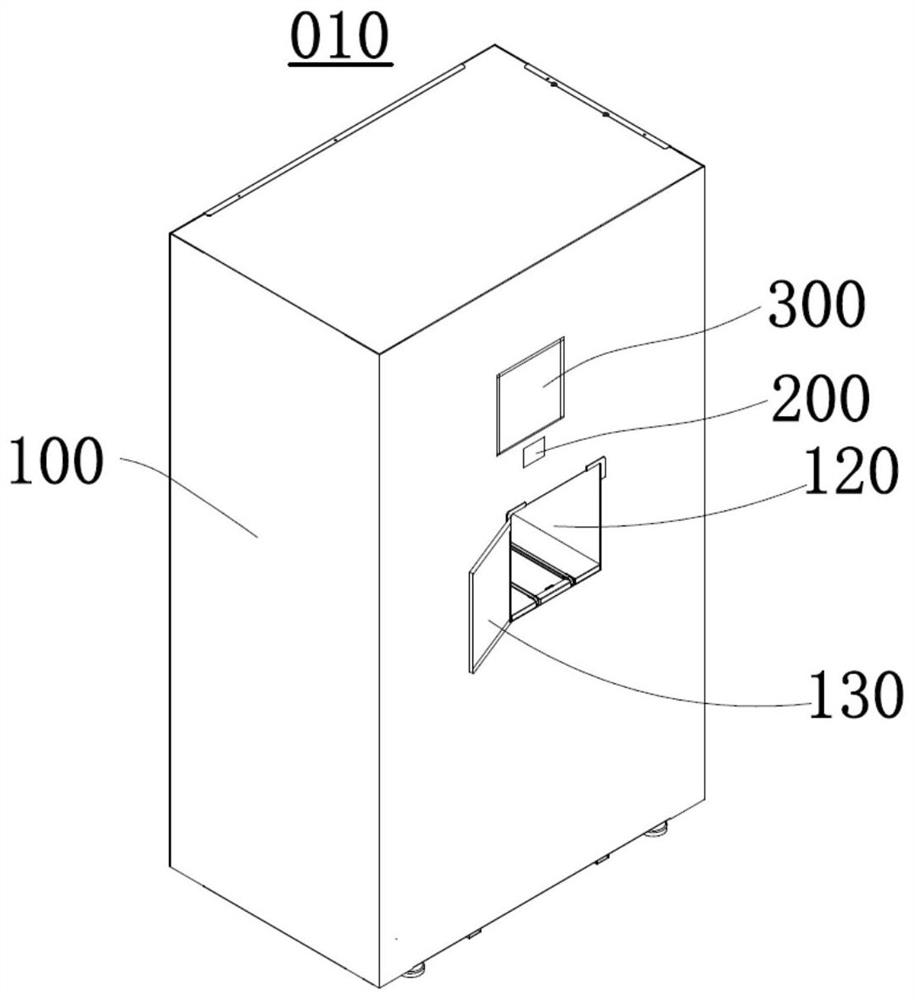
Medicine taking method and device, medicine self-taking cabinet and medicine selling system
PendingCN112017368AFree from the pain of running aroundImprove convenienceApparatus for meter-controlled dispensingIndividual entry/exit registersPatient needPharmacist
The invention belongs to the technical field of self-service medicine taking and discloses a medicine taking method and device, a medicine self-taking cabinet and a medicine selling system. Accordingto the medicine taking method, a locking mechanism of the medicine self-taking cabinet can be controlled to be unlocked through a medicine taking code input by a patient and a box opening instructioninput by a medicine auditor, so that the storing and taking opening of the medicine self-taking cabinet can be opened, and therefore medicine temporarily stored in the medicine self-taking cabinet istaken out. Thus, the patient can take the required medicine when arriving at a community hospital or a pharmacy provided with the medicine self-taking cabinet nearby, the pain of the patient for taking the medicine from a large hospital can be avoided, the convenience for the patient to take the medicine is improved, and the medicine auditor can conveniently guide the patient to take the medicine.According to the method, the medicine taking convenience of the patient is improved, the medicine taking safety of the patient can be guaranteed, and the problems that the patient needs to go to a hospital to take medicine and consumes time and labor in the prior art are solved. The medicine taking device, the medicine self-taking cabinet and the medicine selling system can achieve the medicine taking method, and therefore, have the corresponding advantages.
Owner:WEIHAI NEW BEIYANG DIGITAL TECH +1
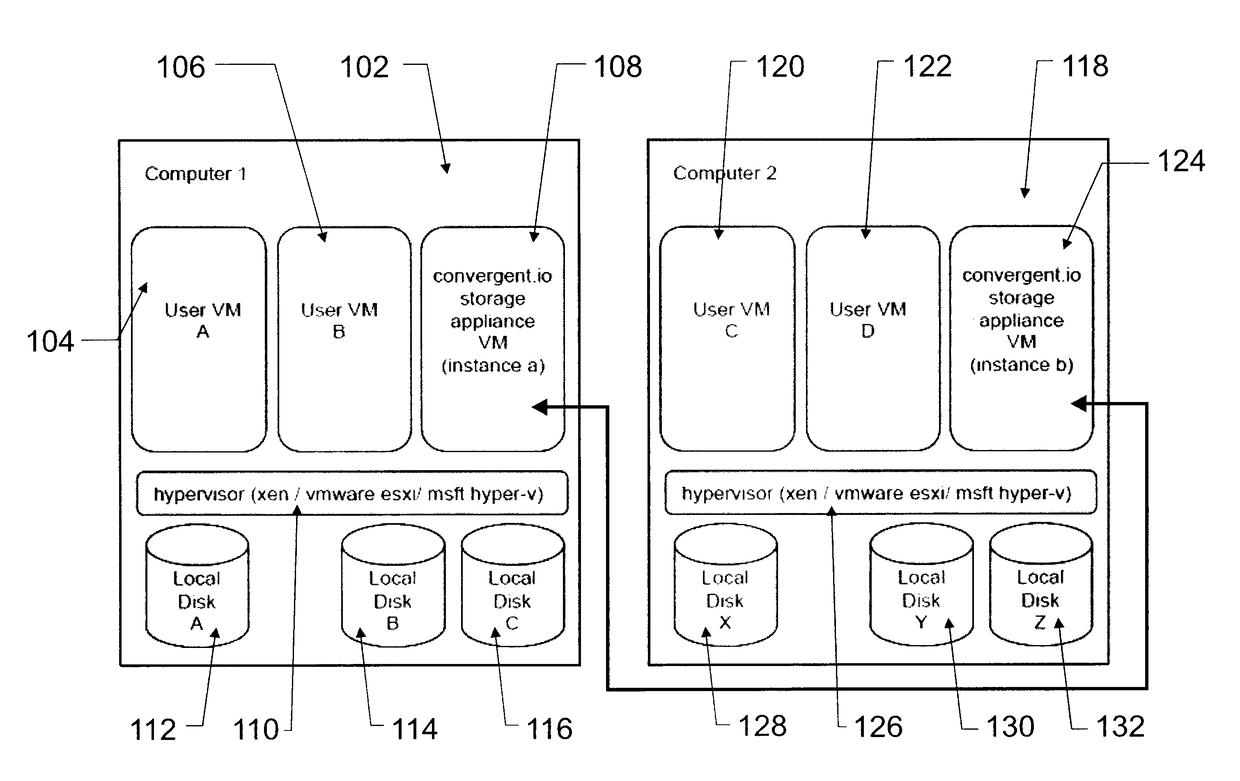
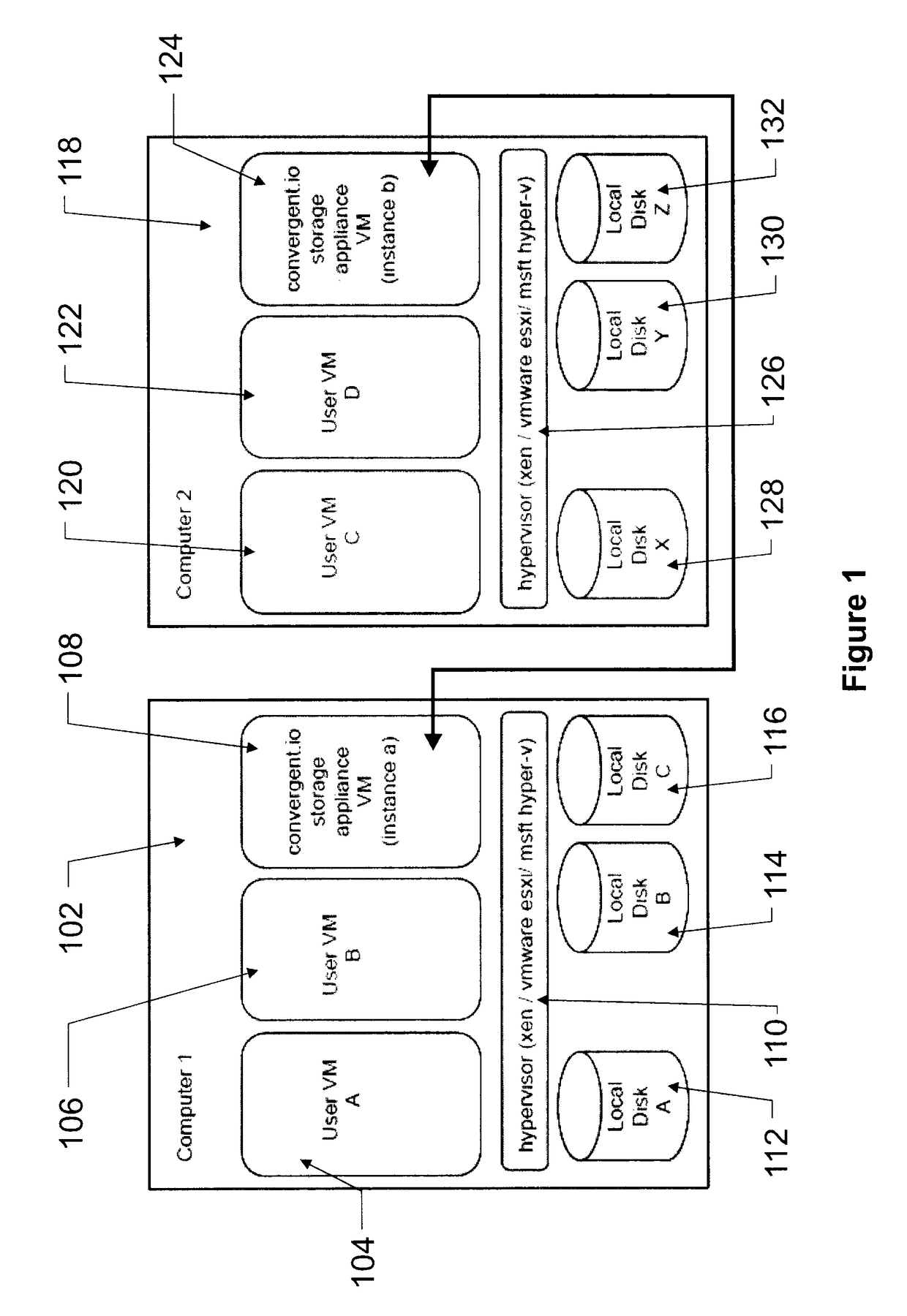
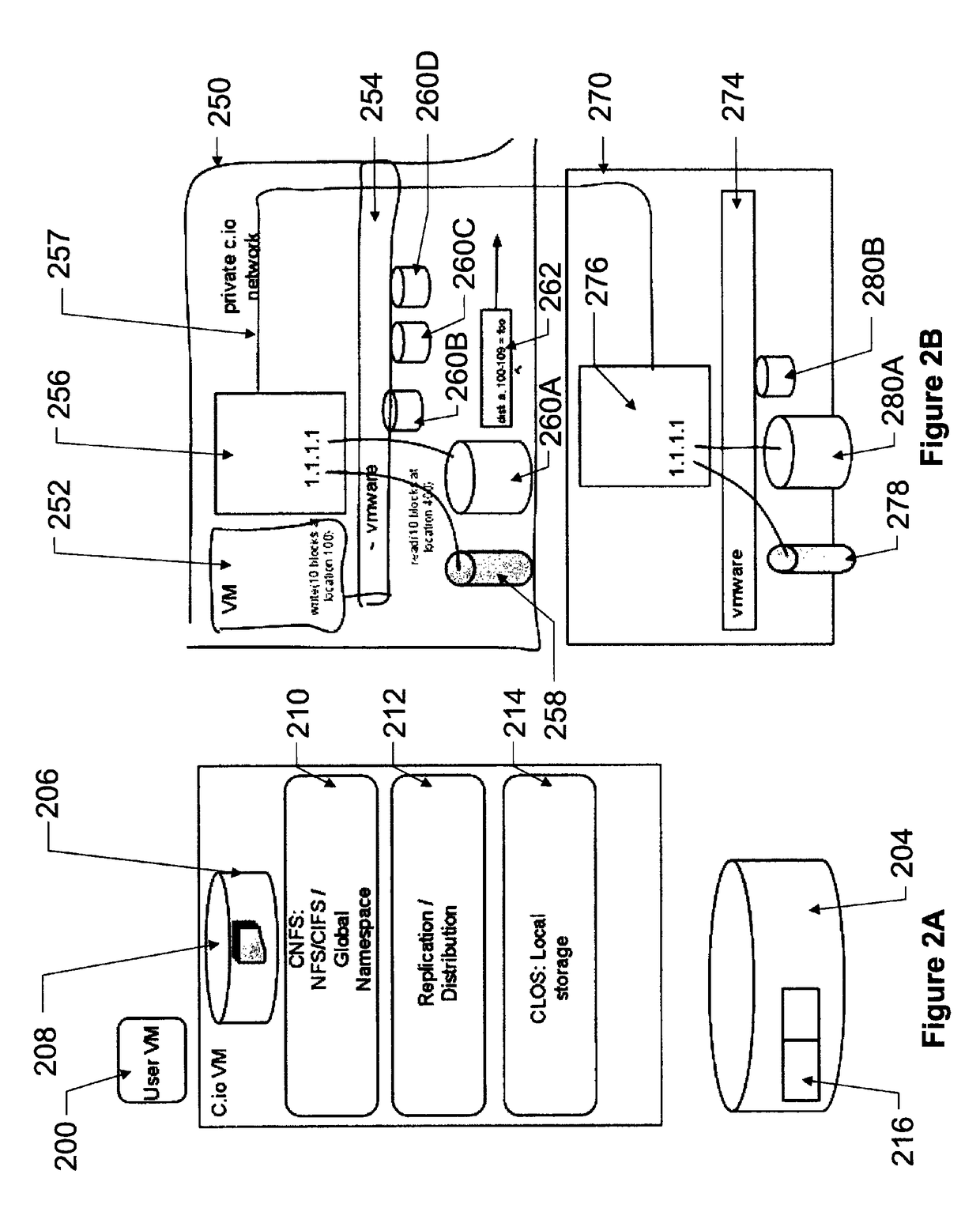
Systems, methods and devices for management of virtual memory systems
ActiveUS10019159B2Maximize the benefitsEnsure safe distributionInput/output to record carriersMultiple digital computer combinationsVirtual memoryParallel computing
Systems, methods and devices for management of instances of virtual memory components for storing computer readable information for use by at least one first computing device, the system comprising at least one physical computing device, each physical computing device being communicatively coupled over a network and comprising: a physical memory component, a computing processor component, an operating system, a virtual machine monitor, and virtual memory storage appliances; at least one of the virtual memory storage appliances being configured to (a) accept memory instructions from the at least one first computing device, (b) instantiate instances of at least one virtual memory component, (c) allocate memory resources from at least one physical memory component for use by any one of the least one virtual memory components, optionally according to a pre-defined policy; and (d) implement memory instructions on the at least one physical memory component.
Owner:IBM CORP
Incentive method and real-time map update system based on security and privacy protection
ActiveCN110677395BEnhanced anonymitySolve privacy and security issuesUser identity/authority verificationDigital data protectionMathematical modelPrivacy protection
The invention belongs to the technical field of vehicle map update in the Internet of Vehicles, discloses a safe and privacy-protected incentive method and a real-time map update system, uses RSA partial blind signature technology to realize pseudonym authentication, pseudonym certificate issuance, identity tracking and credit update; Use the mathematical model of reverse auction and RA algorithm to realize the reverse auction of both parties; use the payment system based on blockchain technology to ensure the safe distribution of rewards. The real-time map update system includes a pseudonym management module, a reverse auction module, and a reward payment module. The invention uses the reverse auction algorithm to solve the payment control of the map service platform and the completion quality of vehicle users; based on the RSA partial blind signature technology, it ensures the security of the incentive method and solves the user's privacy security problem; based on the block chain technology, which solves the problem of updating user reputation accounts, ensures the safe distribution of rewards, and realizes the effectiveness of the incentive method.
Owner:XIAN UNIV OF POSTS & TELECOMM
Beverage Container
Owner:HORVATH RONALD F +4
HMG1 Gene and Uses Thereof in Microsporidium Molecular Detection
ActiveUS20170101689A1Excellent specificity and sensitivityAccurately detectMicrobiological testing/measurementNosema bombycisNucleotide
The present invention disclosed a Nosema bombycis HMG1 gene, a specific primer set used for rapidly detecting Nosema bombycis, a group of microsporidium universal detection primers, and uses thereof. The primer set comprises a primer HMG1-sF and a primer HMG1-sR, and nucleotide sequences of the primers are shown in SEQ ID No. 5-6 respectively. The universal detection primers comprise a primer HMG1F and a primer HMG1R, and nucleotide sequences of the primers are shown in SEQ ID No. 3-4 respectively.
Owner:SOUTH CHINA AGRI UNIV
Method and system for sending terminal services
InactiveCN101662456BEnsure safe distributionRealize the bindingData switching by path configurationNetwork connectionsComputer network
The invention discloses a method and a system for sending terminal services. The method comprises the following steps: sending a registration request comprising application terminal identification information and gateway identification information to an automatic configuration server (ACS); and receiving the configuration, corresponding to an application terminal, sent by the ACS, wherein the application terminal identification information and the gateway identification information are sent to a user database (DB) by the ACS; the DB sends user service data to the ACS after determining the user service data corresponding to the application terminal according to the application terminal identification information, the gateway identification information and physical line information of a gateway; and the ACS sends the configuration to the terminal after generating the configuration according to the user service data. The method and the system for sending the terminal services provided bythe invention can ensure that the services corresponding to the application terminal linked to the gateway are safely sent.
Owner:南通市通州区新志浩实业有限公司
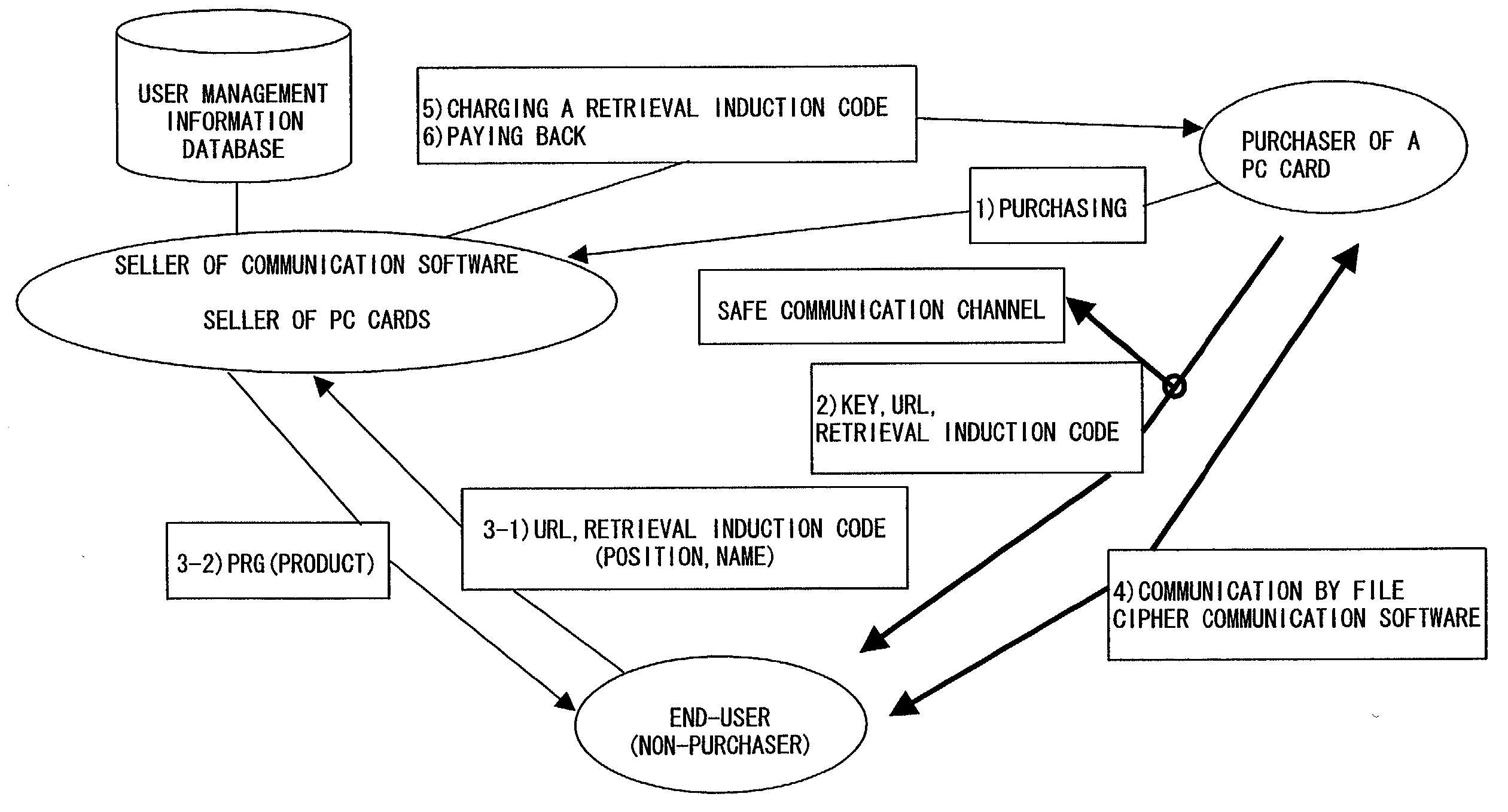
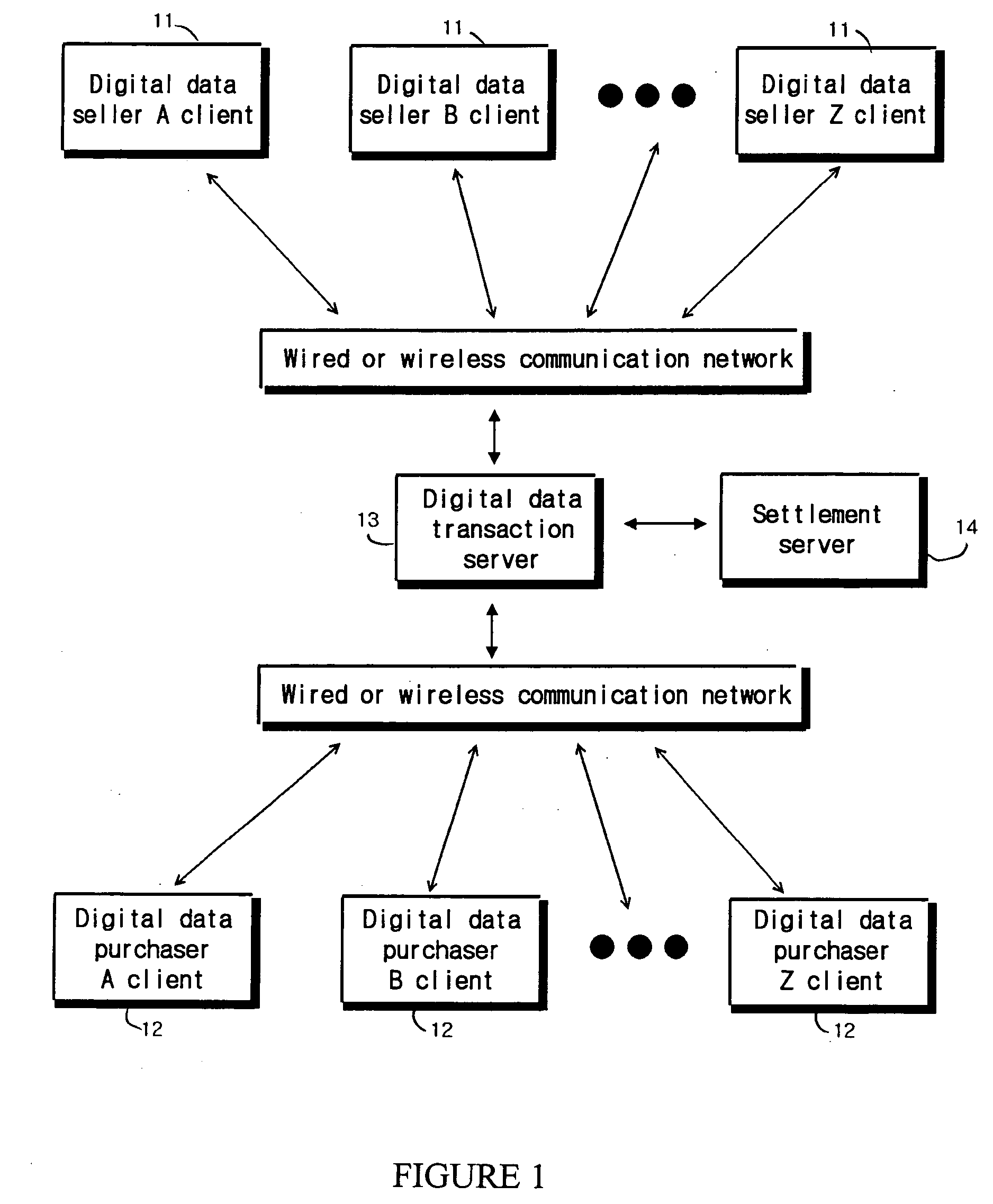
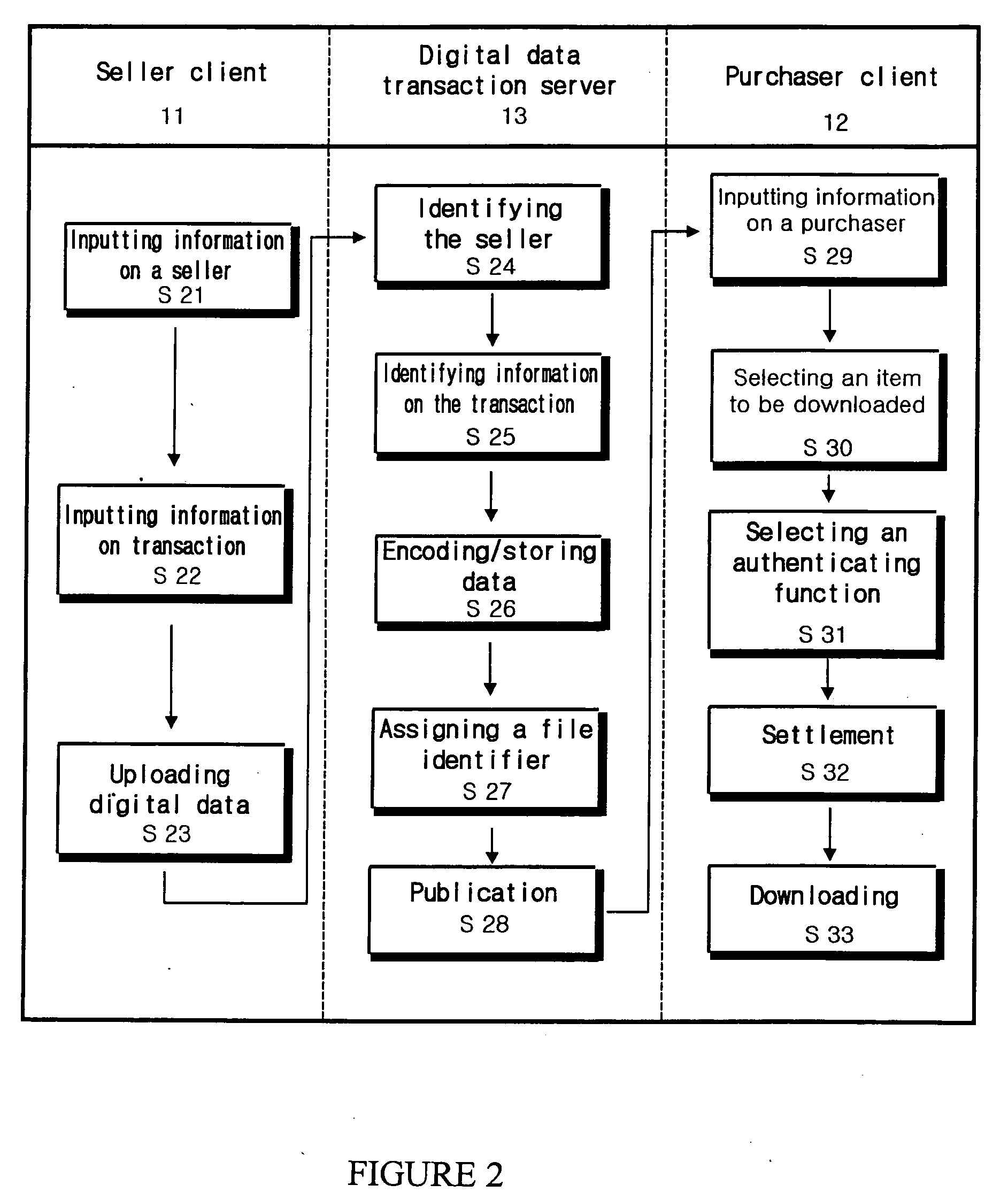
Transaction method of digital data and system thereof
InactiveUS20050251483A1Prevent illegal useSafely distributedUser identity/authority verificationComputer security arrangementsDigital dataTransaction service
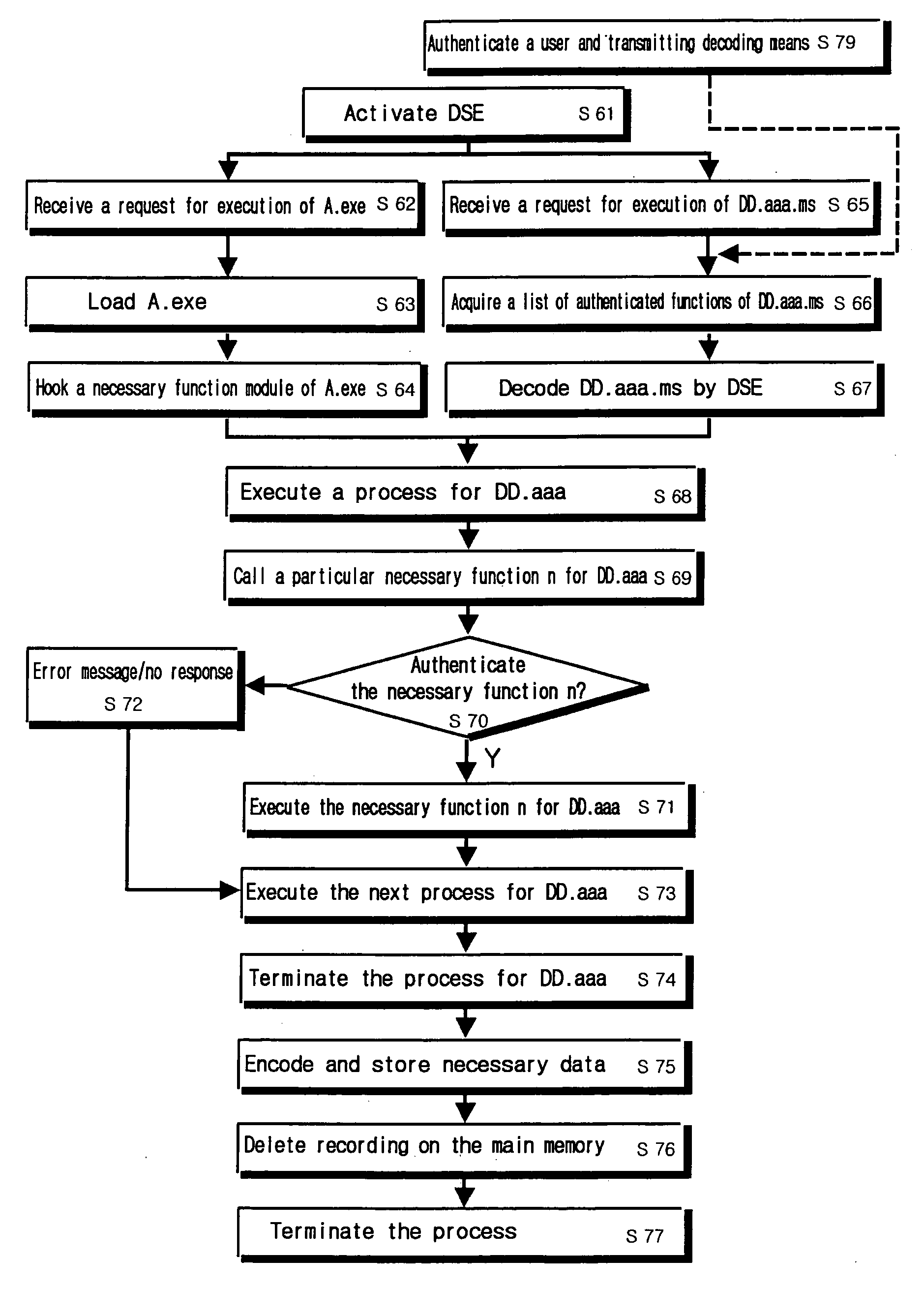
Disclosed is a transaction method including a digital data seller client system, a digital data purchaser client system and a digital data transaction server. The transaction method according to the invention includes the steps of: inputting digital data including information on a seller, information on digital data, information on transactional functions, and digital data in the digital data transaction server by the digital data seller client system; publicizing the information on digital data and the information on transactional functions of the digital data on-line by the digital data transaction server; selecting an authenticated function from the information on transactional functions to use the digital data from the digital data transaction server by the digital data purchaser client system; encoding the digital data and a list of authenticated functions and transmitting the same to the digital data purchaser client by the digital data transaction server; and transmitting decoding means for decoding the encoded data to the digital data purchaser client system by the digital data transaction server.
Owner:TERUTEN
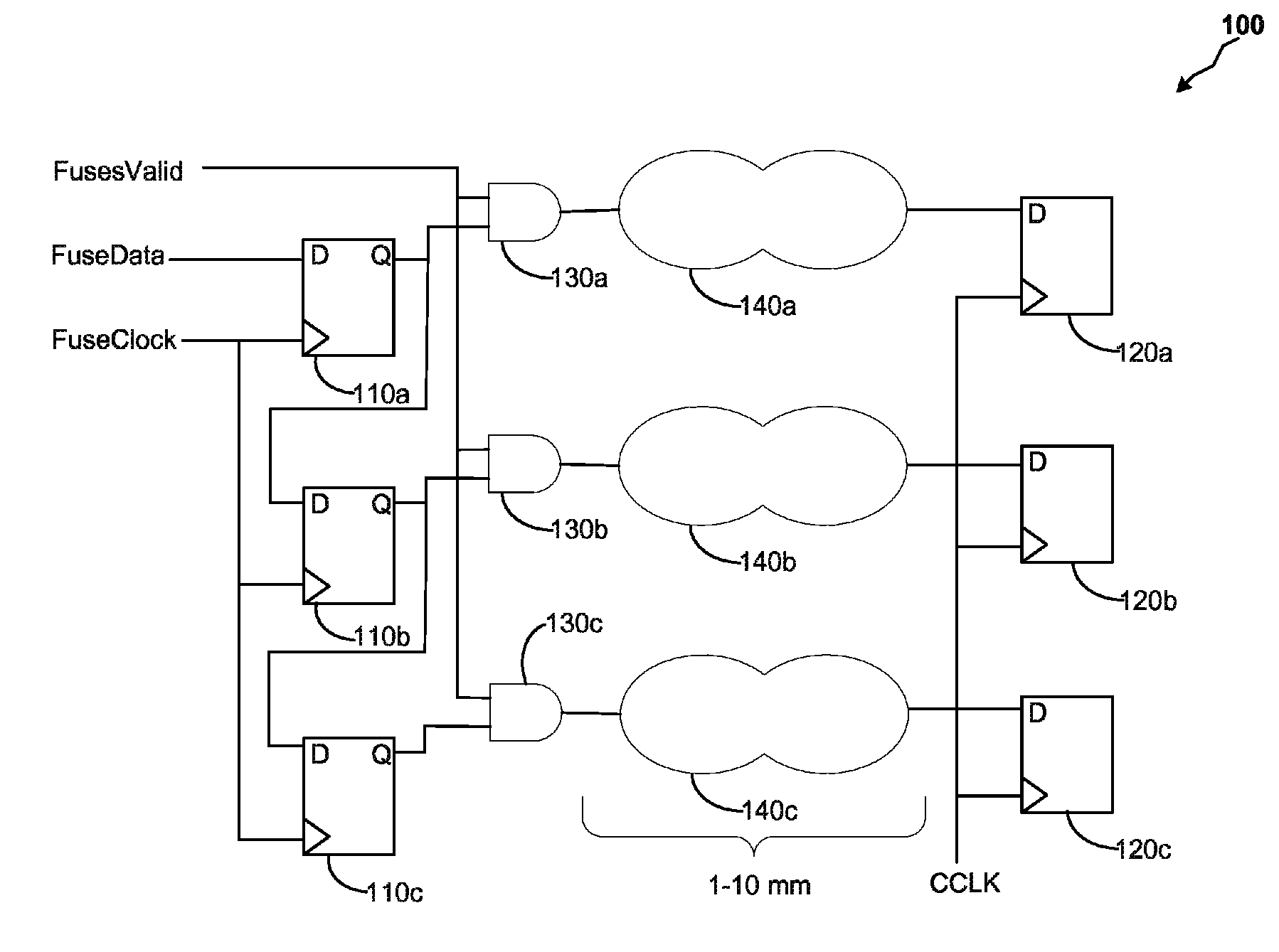
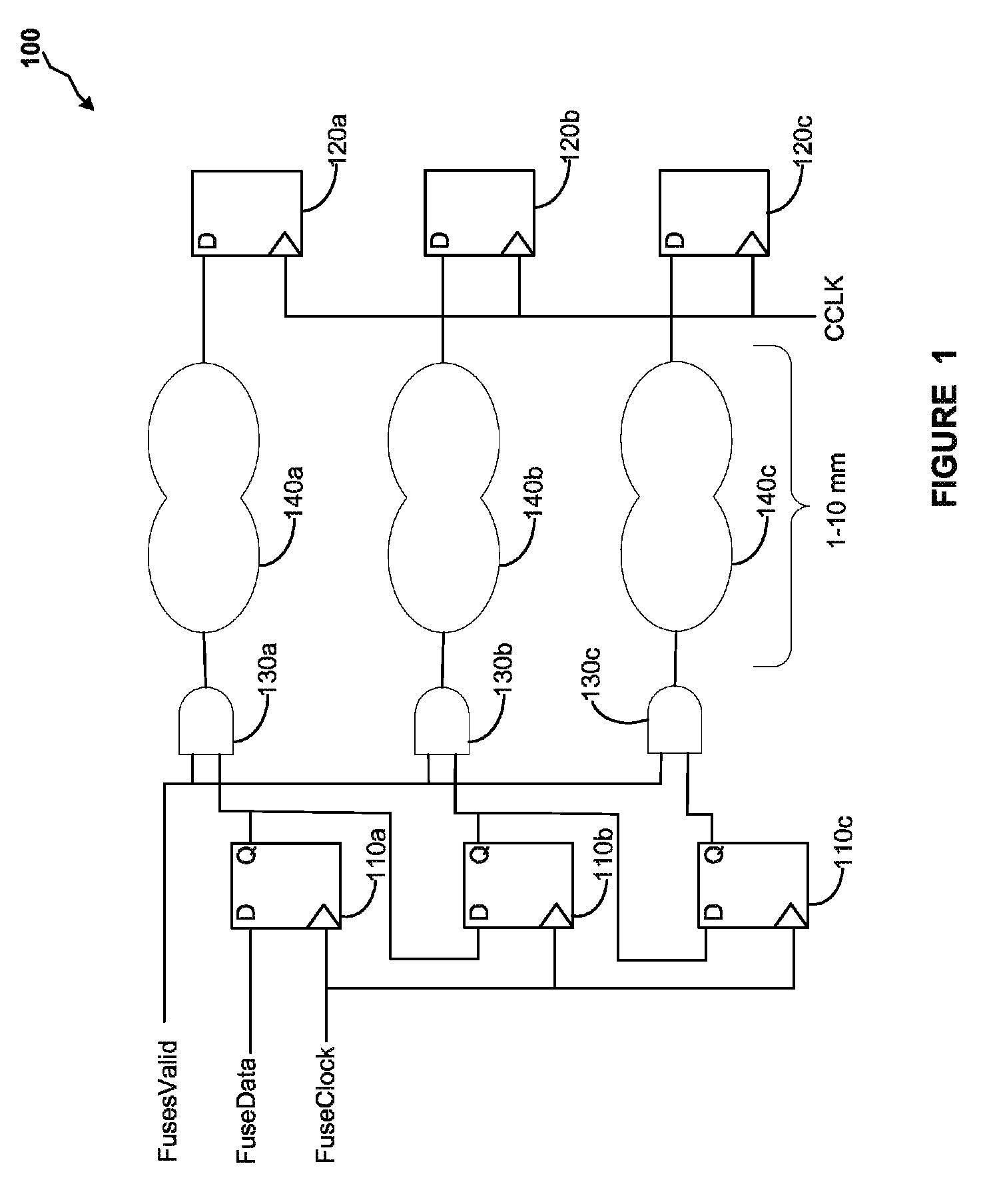
Safe reset configuration of fuses and flops
ActiveUS8884668B2Save complexitySave power consumptionPulse automatic controlElectric pulse generator circuitsIntegrated circuitFLOPS
Owner:ADVANCED MICRO DEVICES INC
HMG1 gene and uses thereof in microsporidium molecular detection
ActiveUS10435759B2Reliable test resultsEasy to operateMicrobiological testing/measurementNosema bombycisNucleotide
The present invention disclosed a Nosema bombycis HMG1 gene, a specific primer set used for rapidly detecting Nosema bombycis, a group of microsporidium universal detection primers, and uses thereof. The primer set comprises a primer HMG1-sF and a primer HMG1-sR, and nucleotide sequences of the primers are shown in SEQ ID No. 5-6 respectively. The universal detection primers comprise a primer HMG1F and a primer HMG1R, and nucleotide sequences of the primers are shown in SEQ ID No. 3-4 respectively.
Owner:SOUTH CHINA AGRI UNIV
Information processing system and method using encryption key block
InactiveUS7957537B2Data transmission securitySecure transmissionKey distribution for secure communicationRecord information storageInformation processingStructure of Management Information
An information processing system and method using an encryption key block sets sub-trees classified based on data processing ability of the devices (capability) in a key tree in which respective keys are corresponded to a root, nodes and leaves of a tree in which a plurality of devices are constituted as the leaves, generates a sub-enabling key block which is effective for an entity in a managing subject of each sub-tree (entity), and generates an enabling key block decodable only by the entities having common capability. Also, an information processing system and method using an encryption key block manages a partial tree of a key tree (sub-tree), generates a sub-enabling key block based only on a key set corresponding to nodes or leaves included in the sub-tree, and generates an enabling key block decodable only by selected entities by using the sub-enabling key block. Thus, it is possible to generate and distribute an enabling key block corresponding to data processing ability of a device and to manage devices by dividing a hierarchical key tree structure.
Owner:SONY CORP
Incentive method and real-time map update system based on security and privacy protection
ActiveCN110677395B9Enhanced anonymitySolve privacy and security issuesUser identity/authority verificationDigital data protectionMathematical modelPrivacy protection
Owner:XIAN UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com