Patents
Literature
145results about "Existing connections interruption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
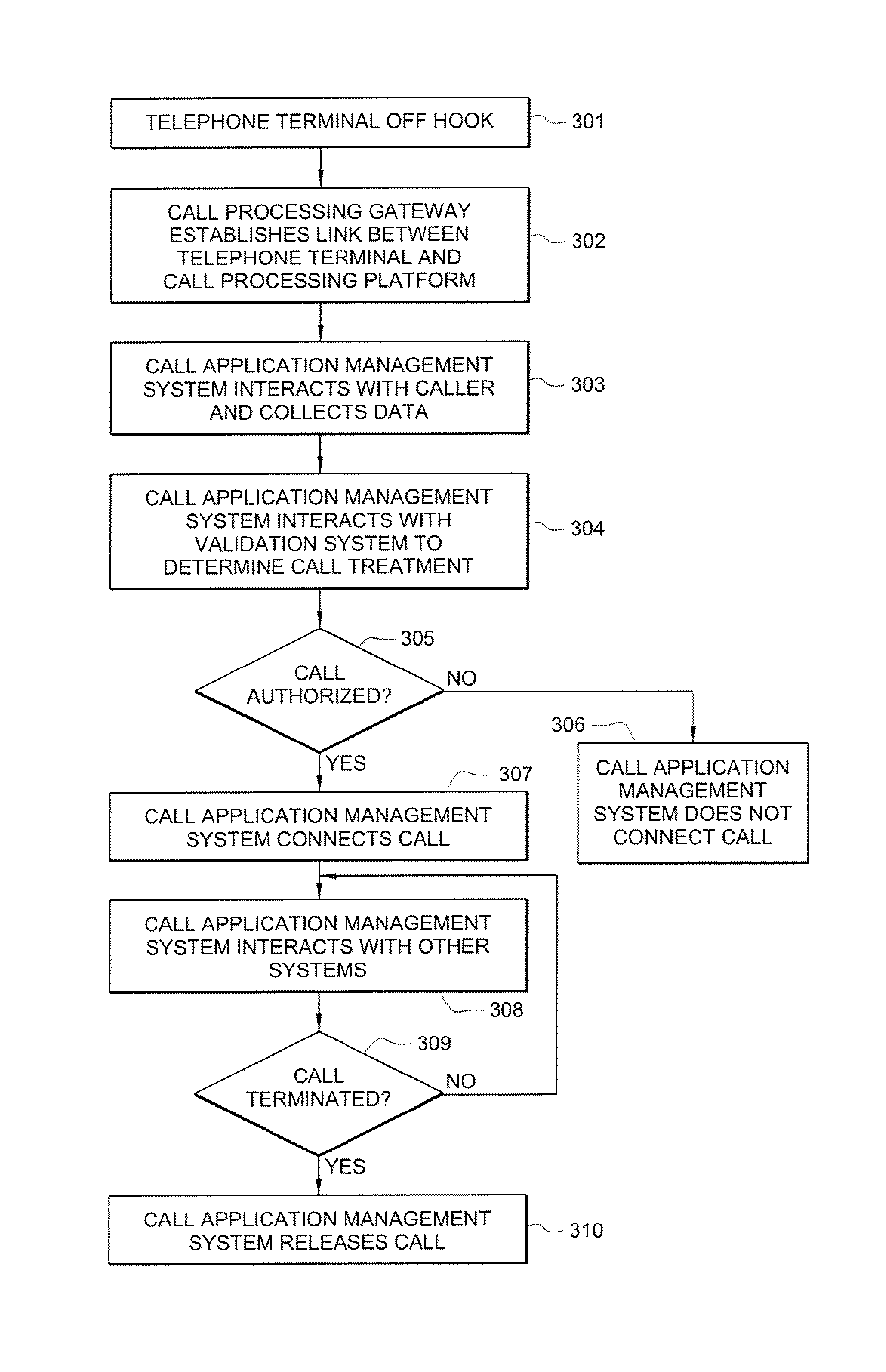
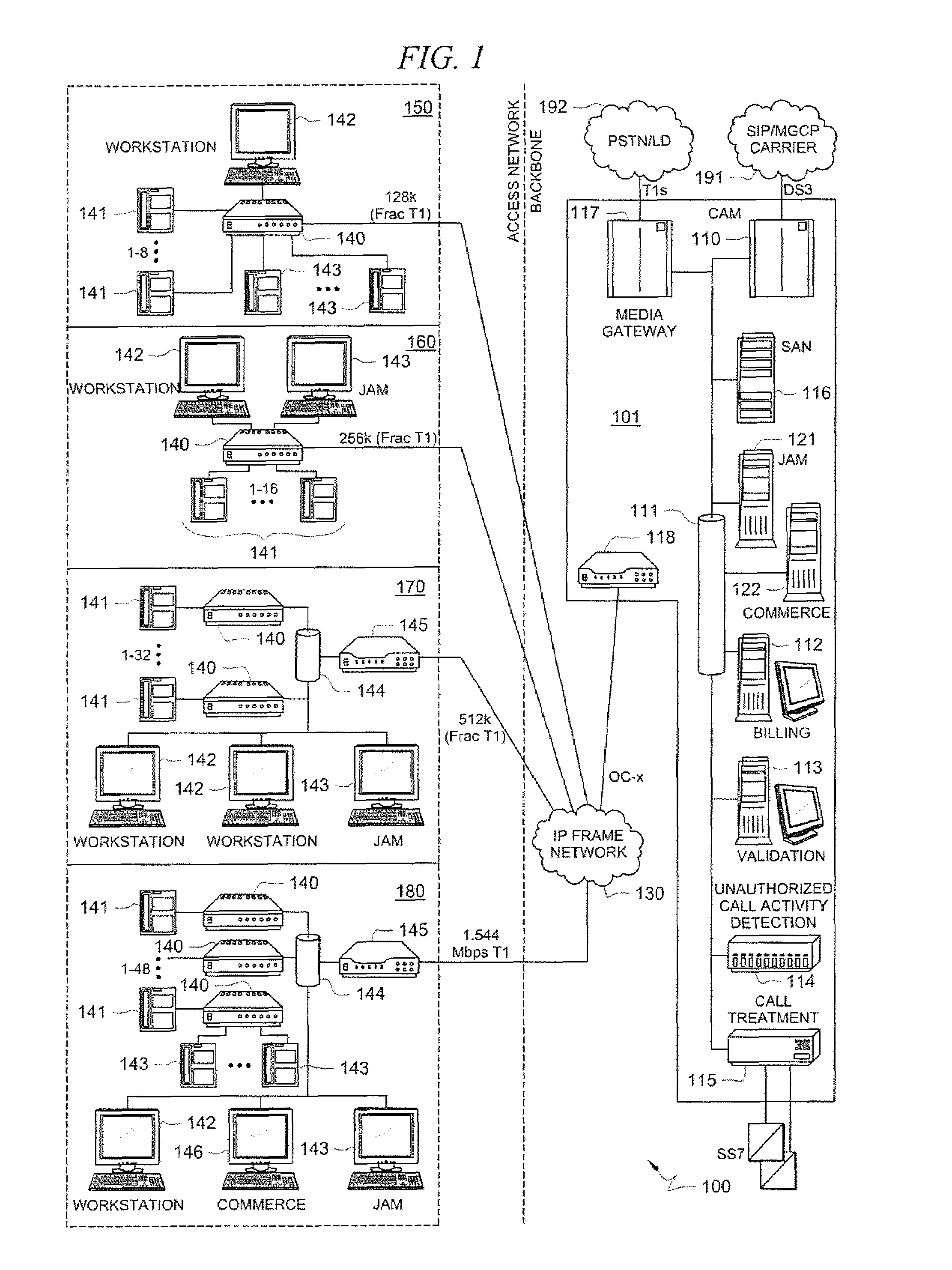
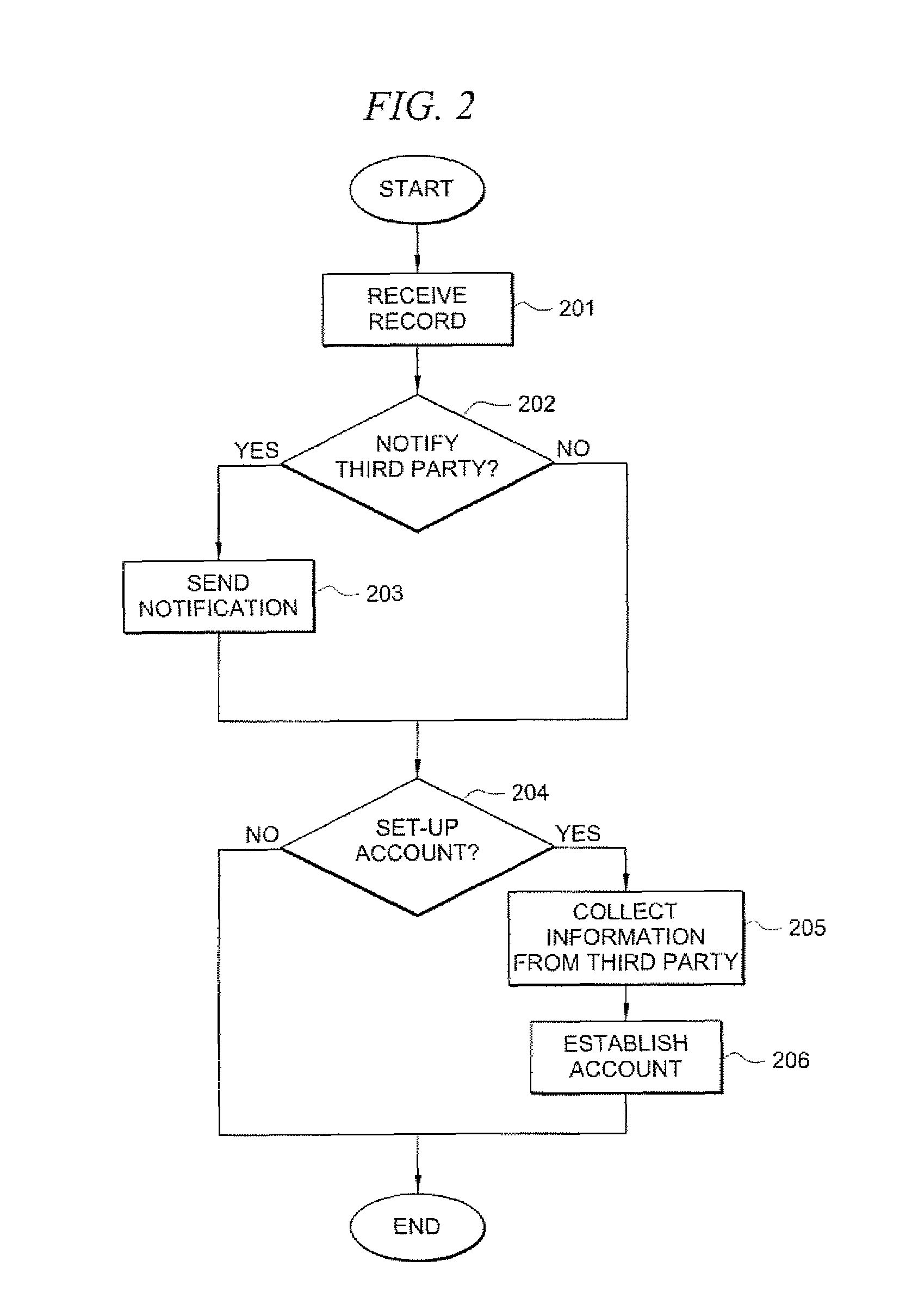
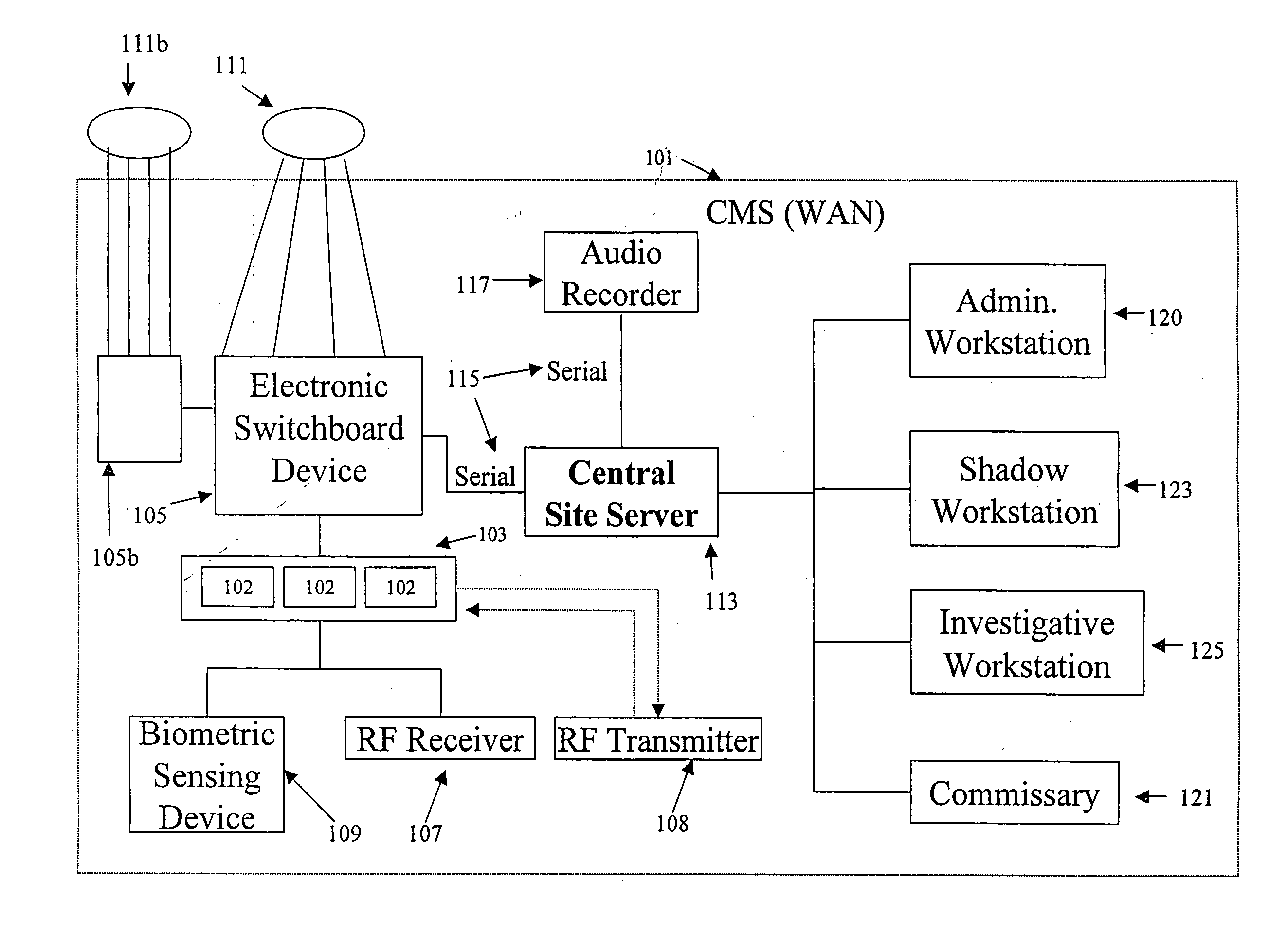
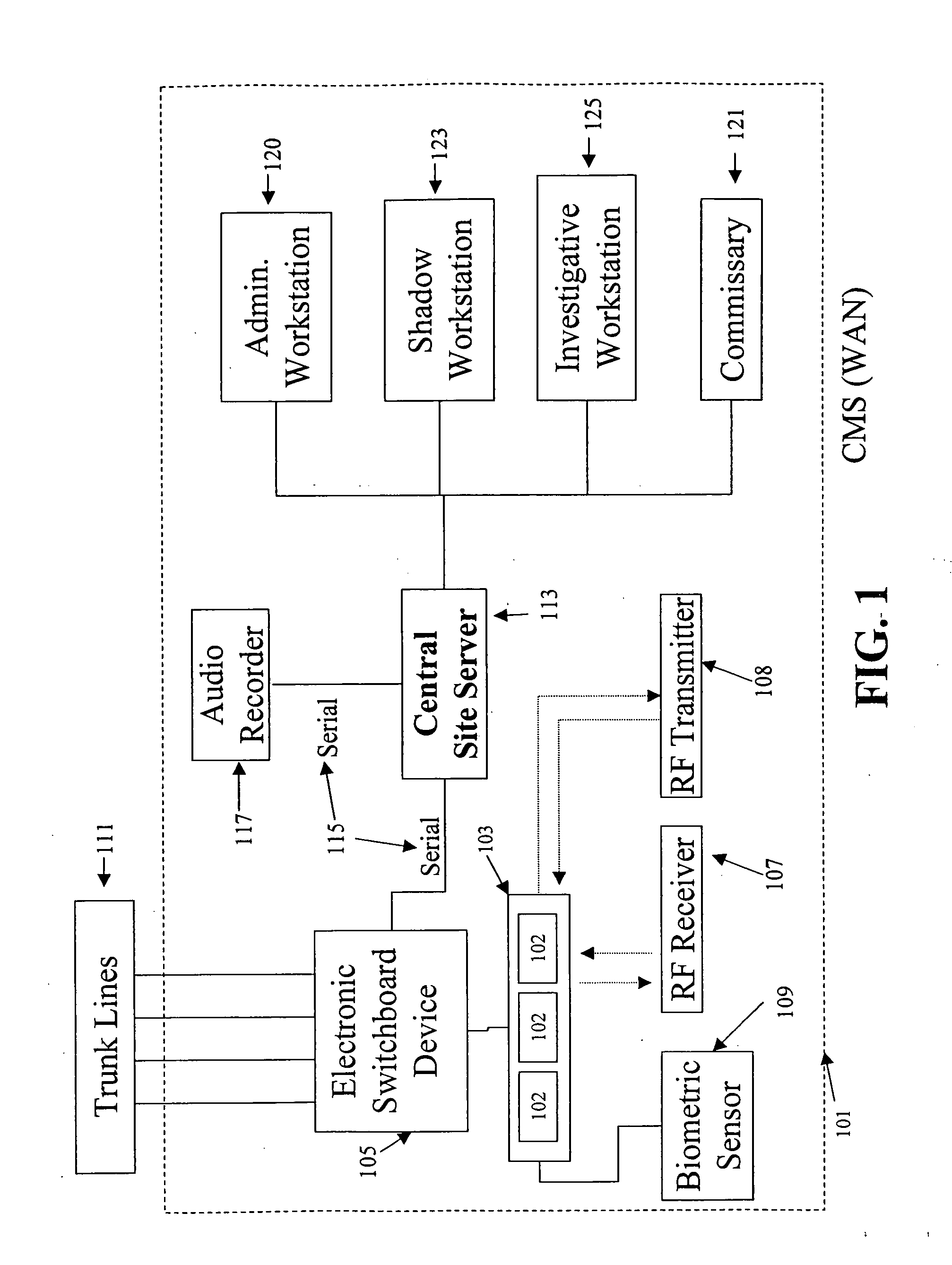
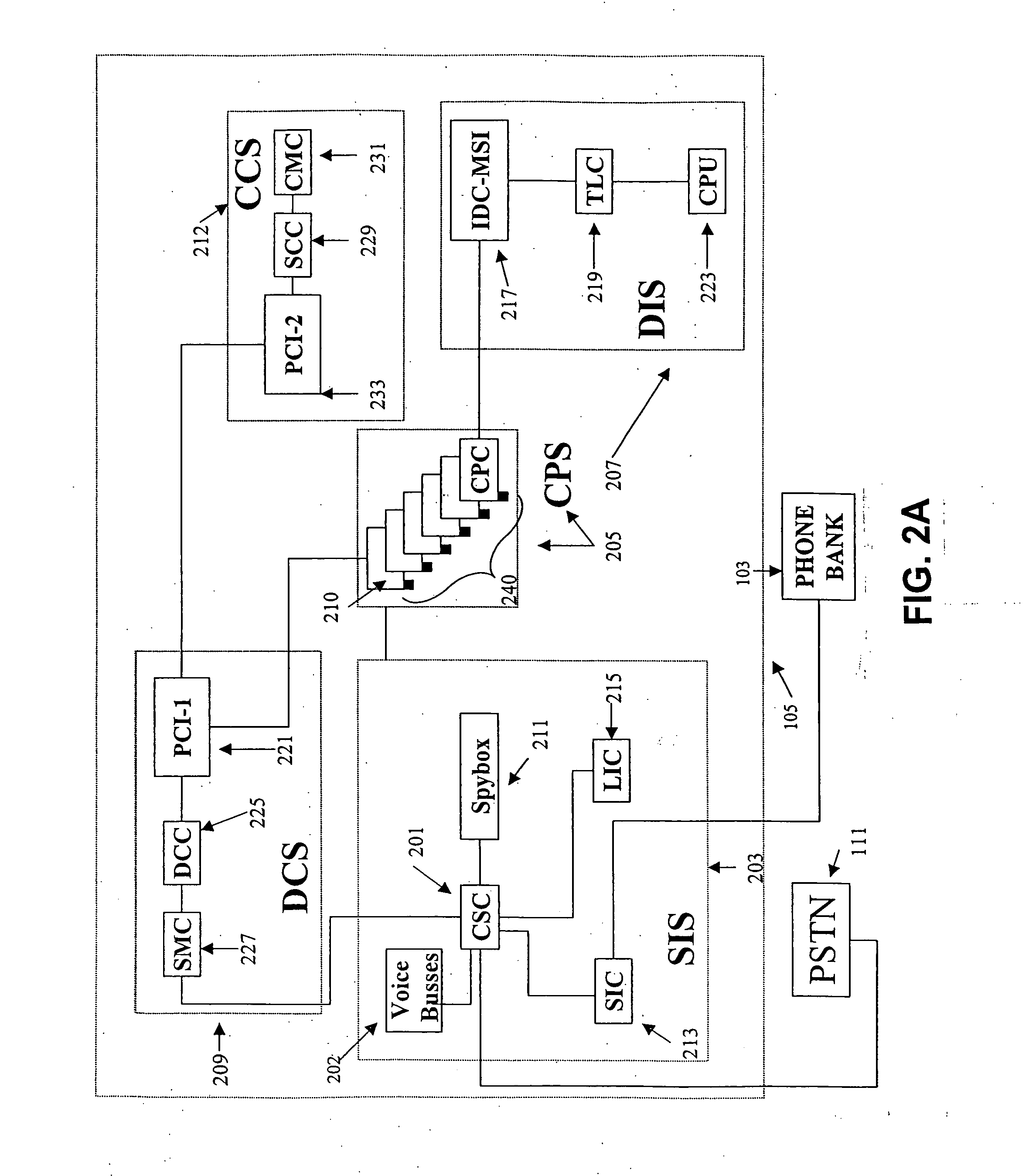
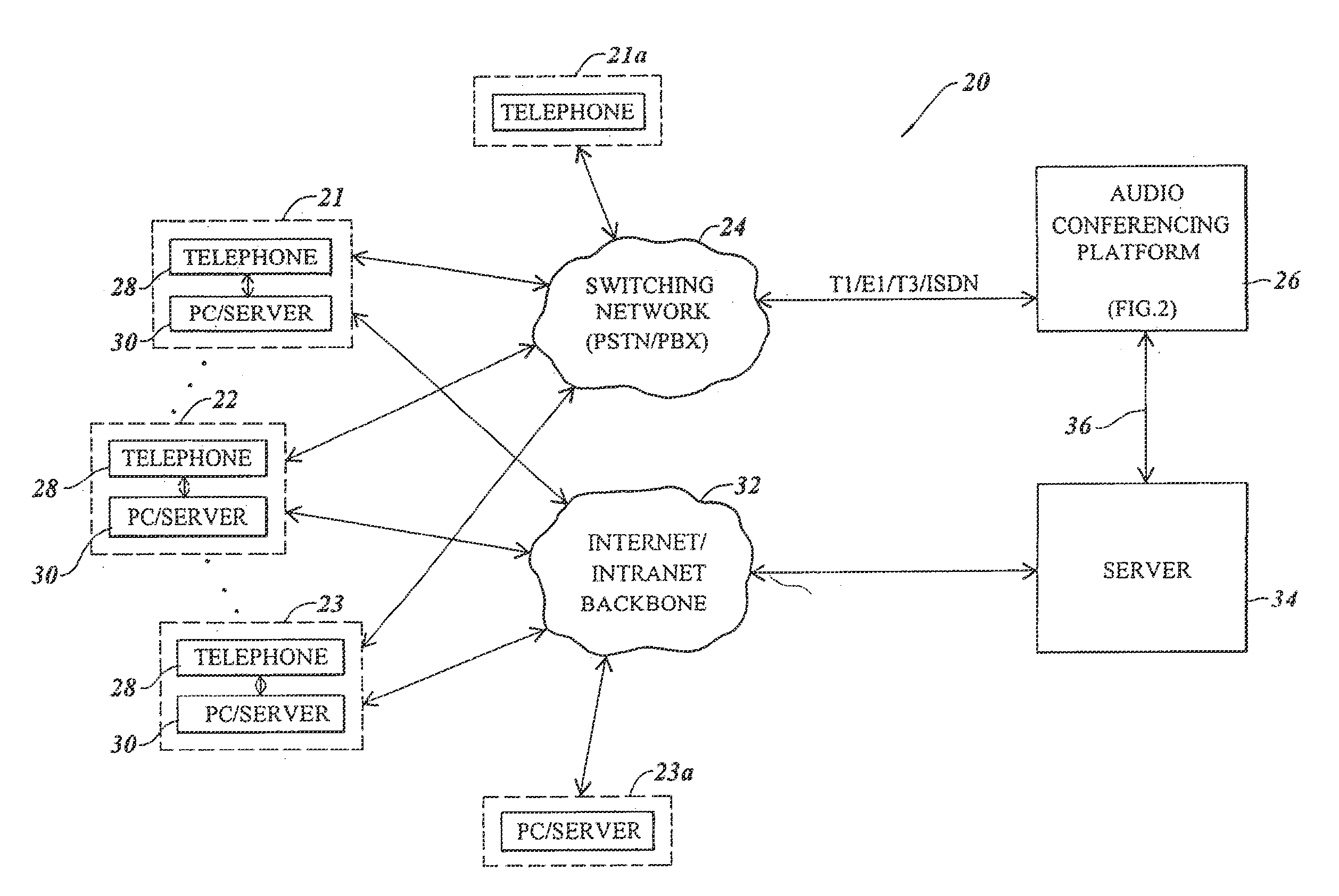
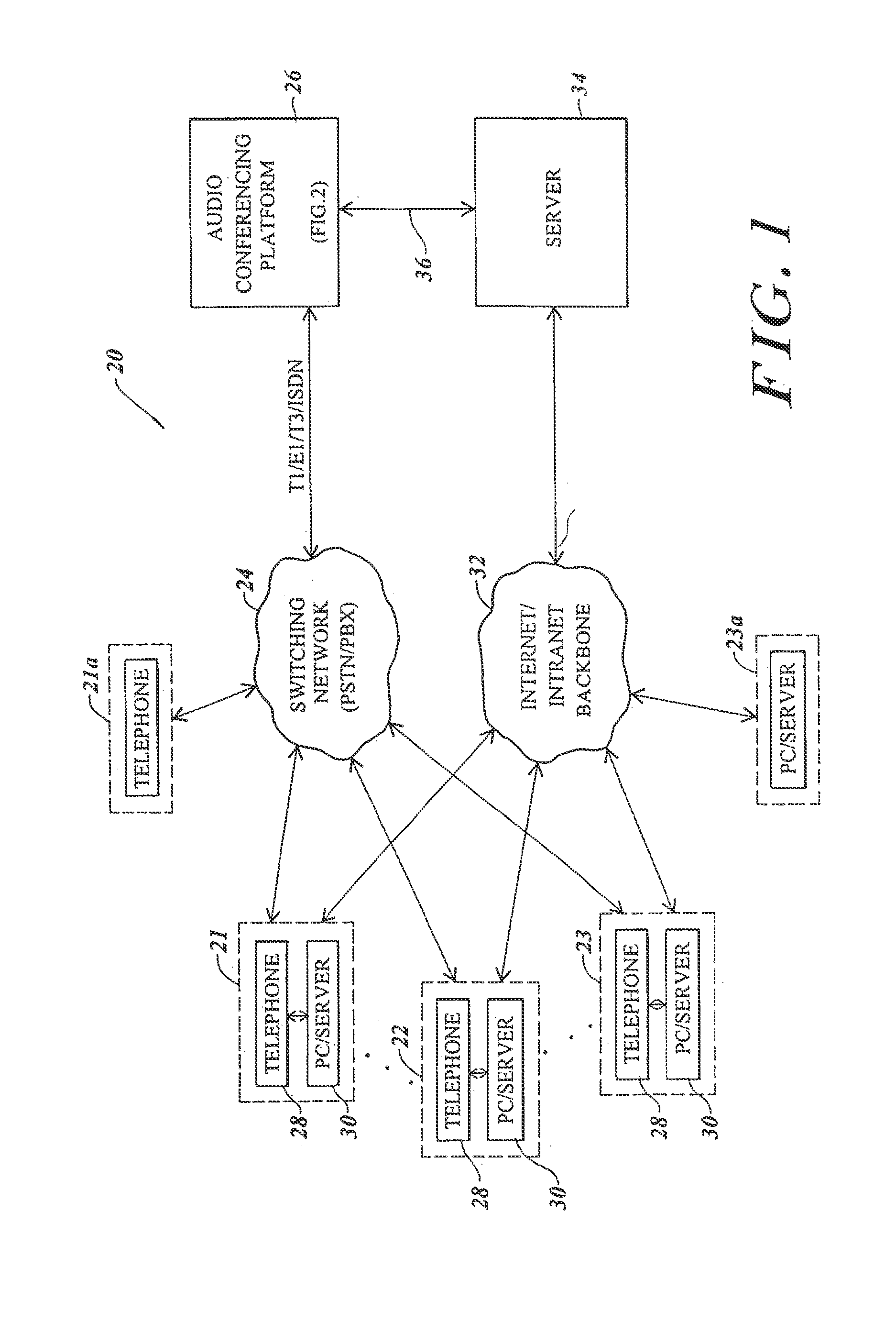
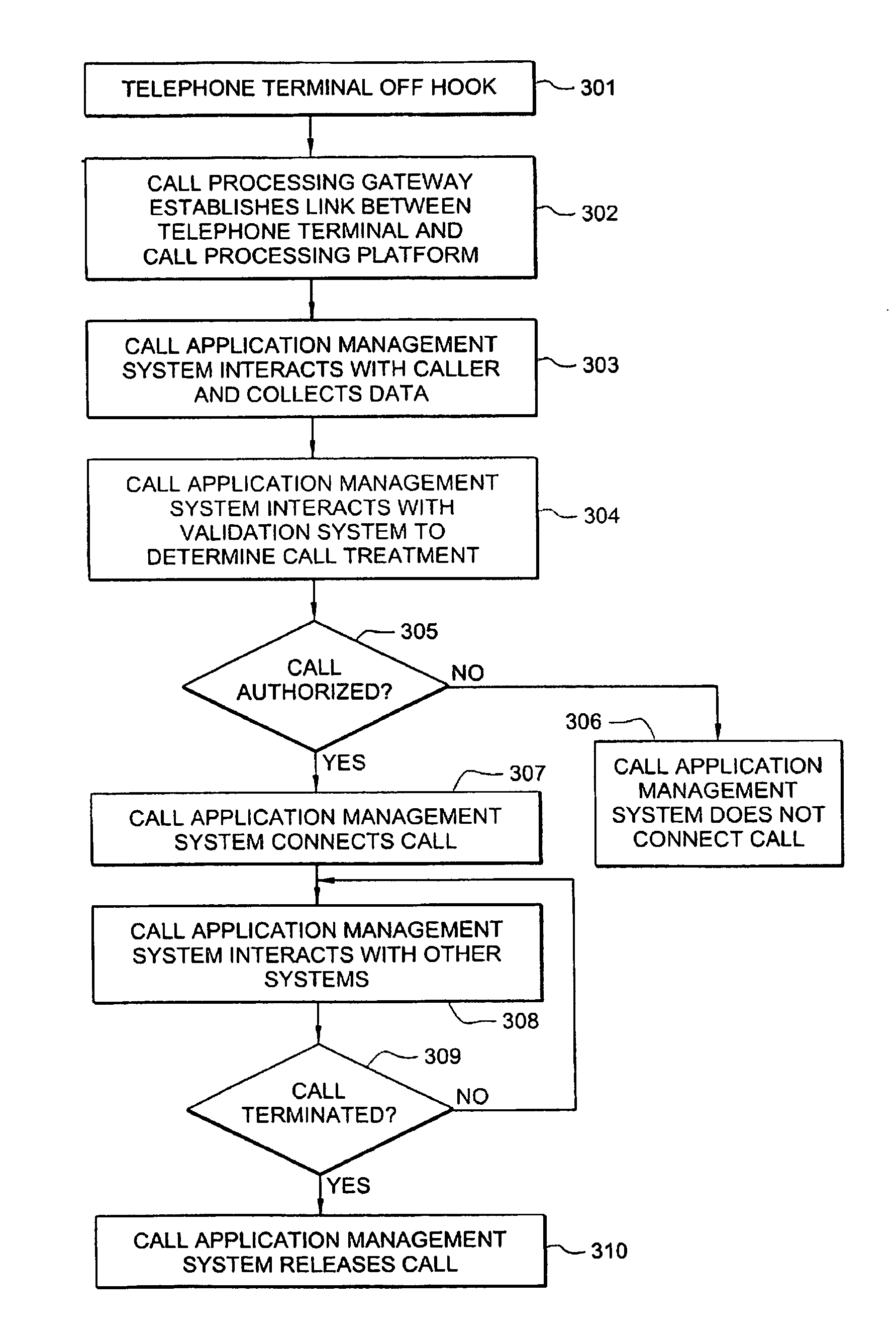
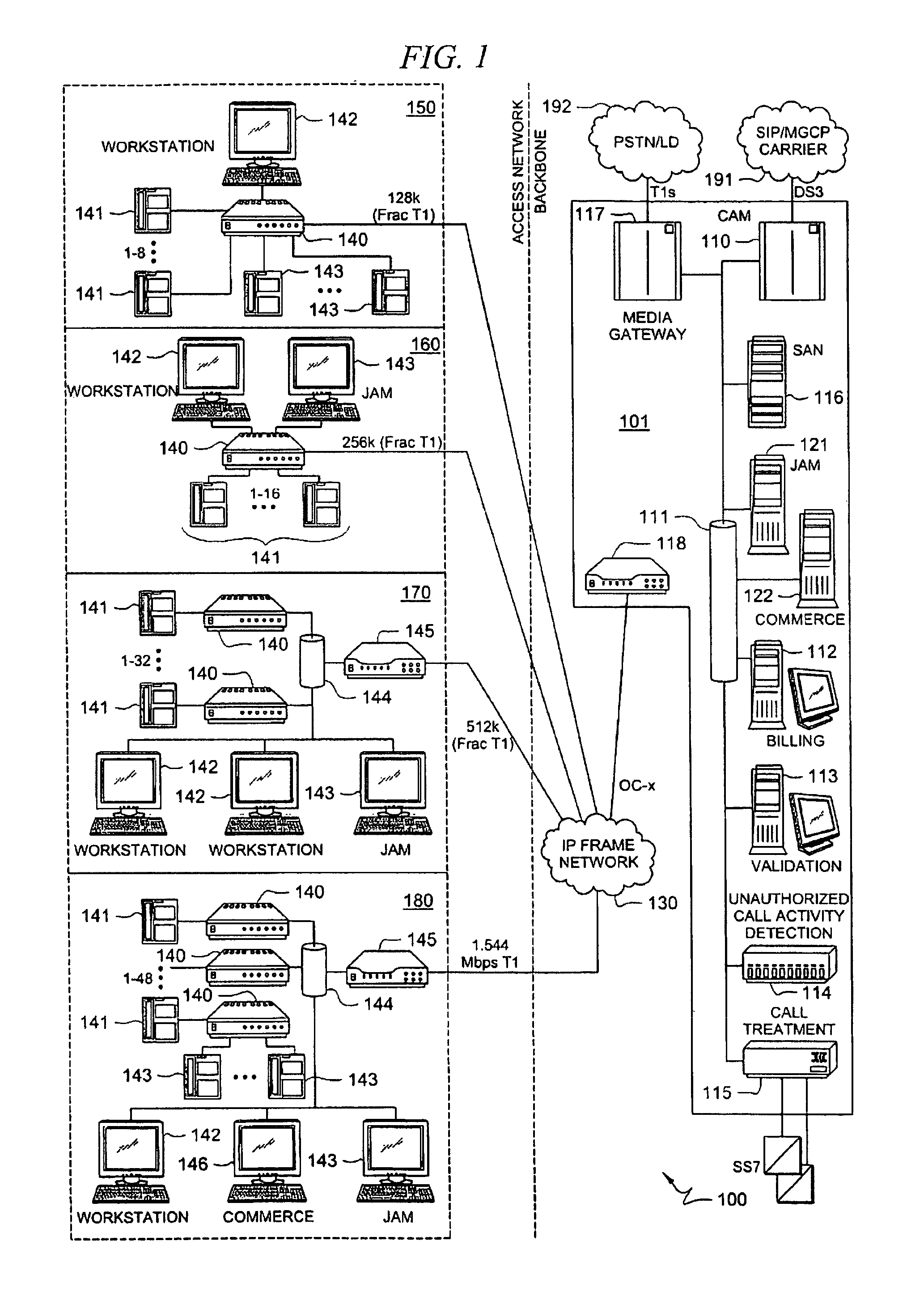
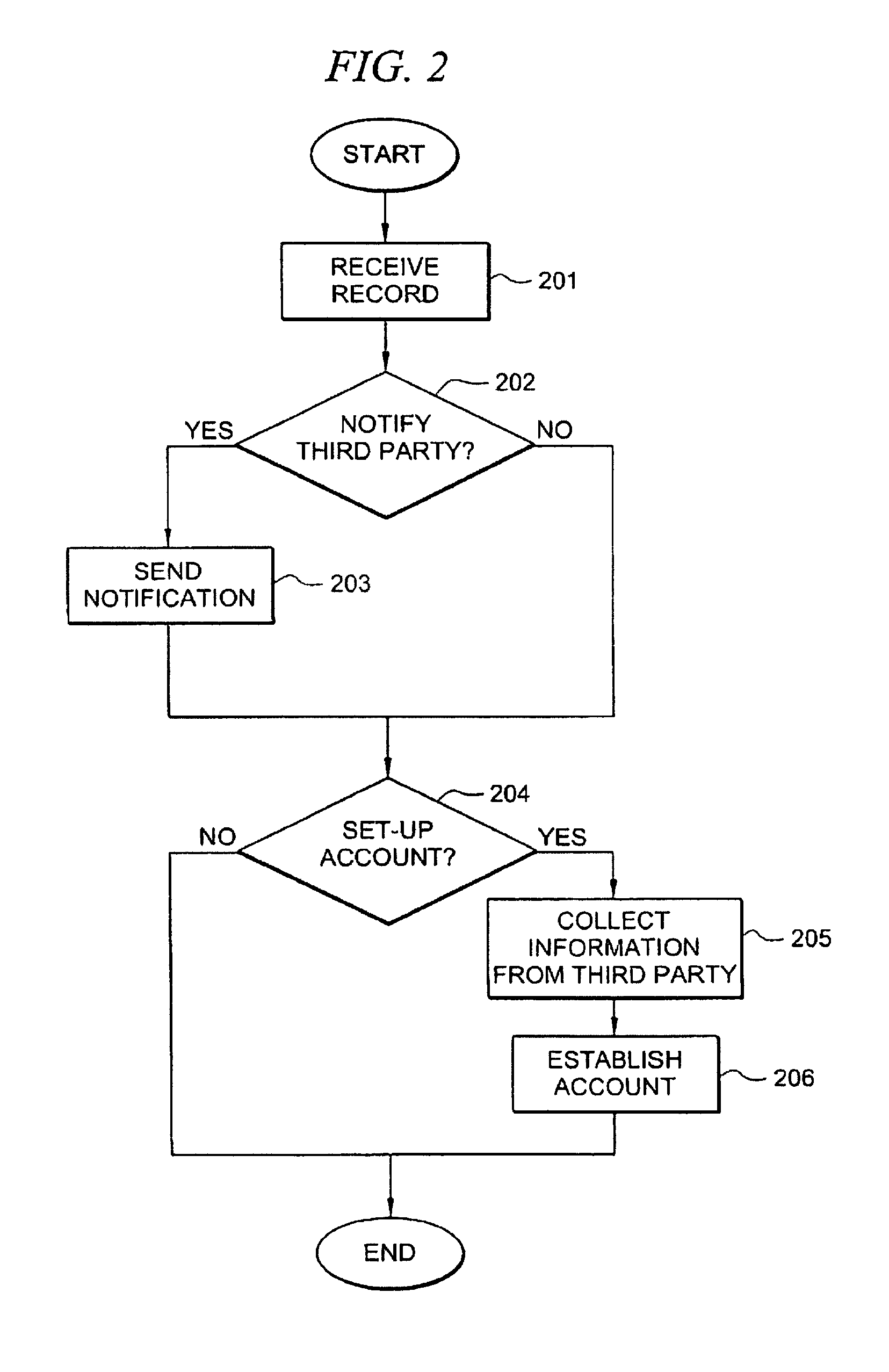
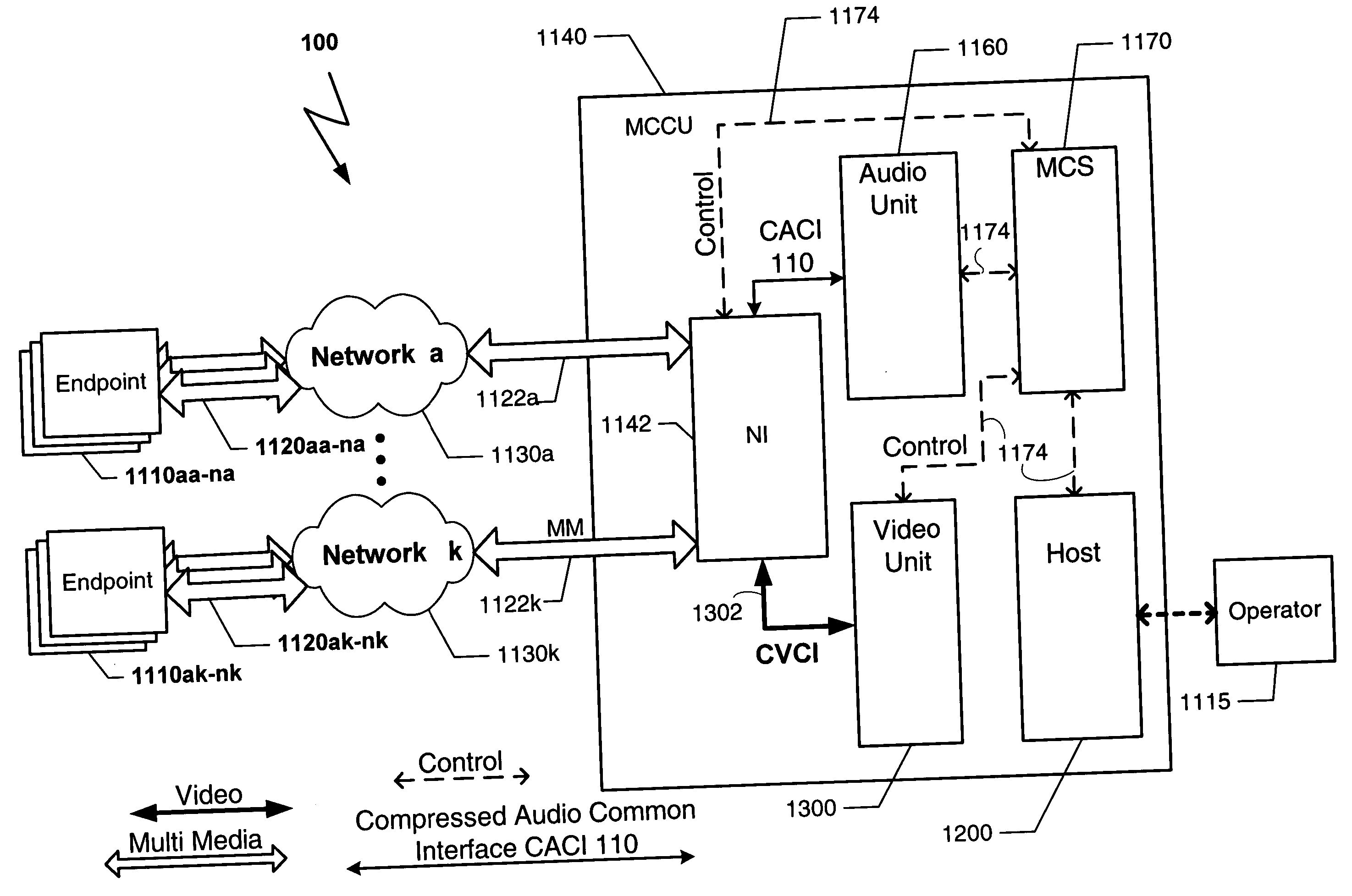
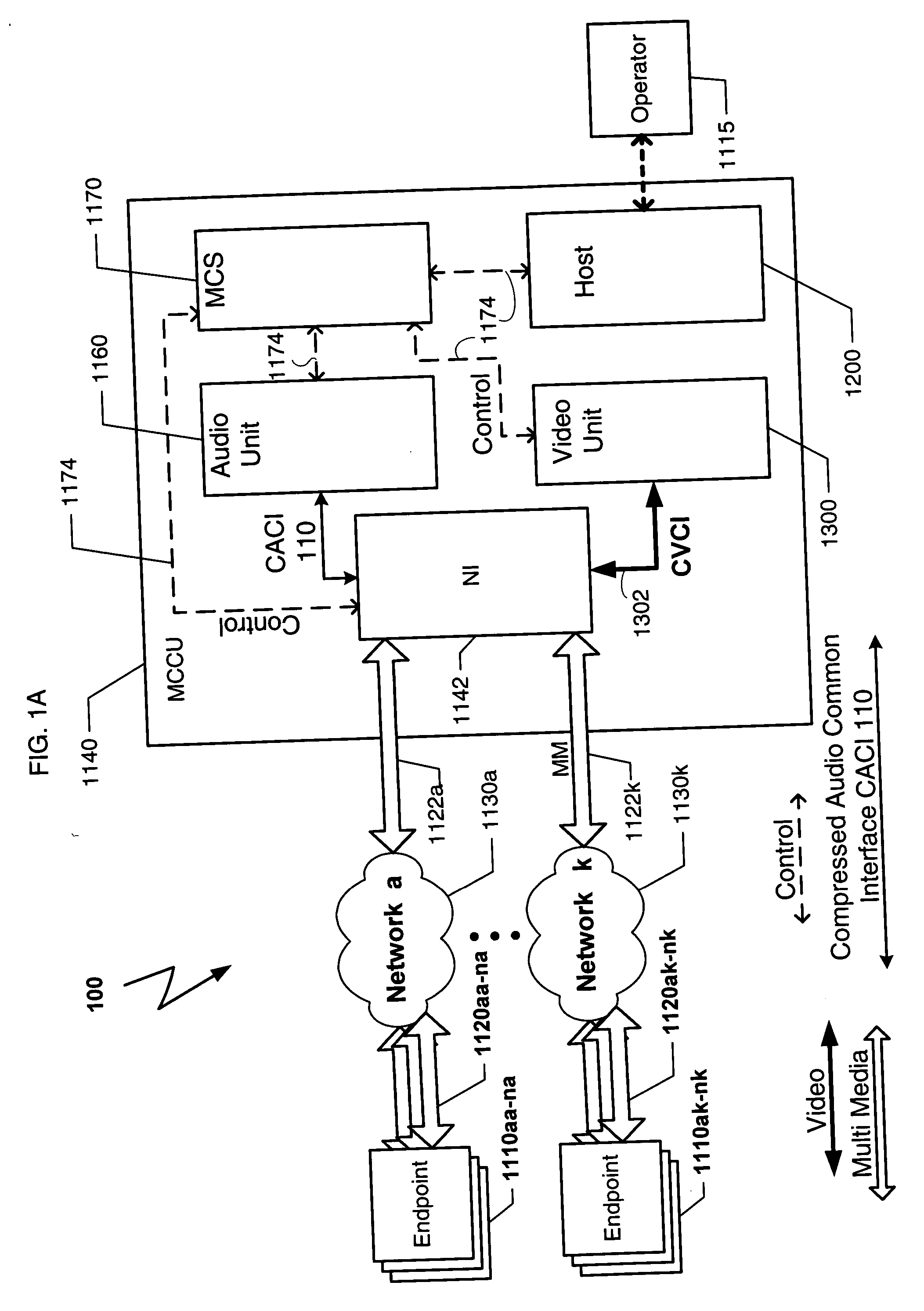
Inmate management and call processing systems and methods
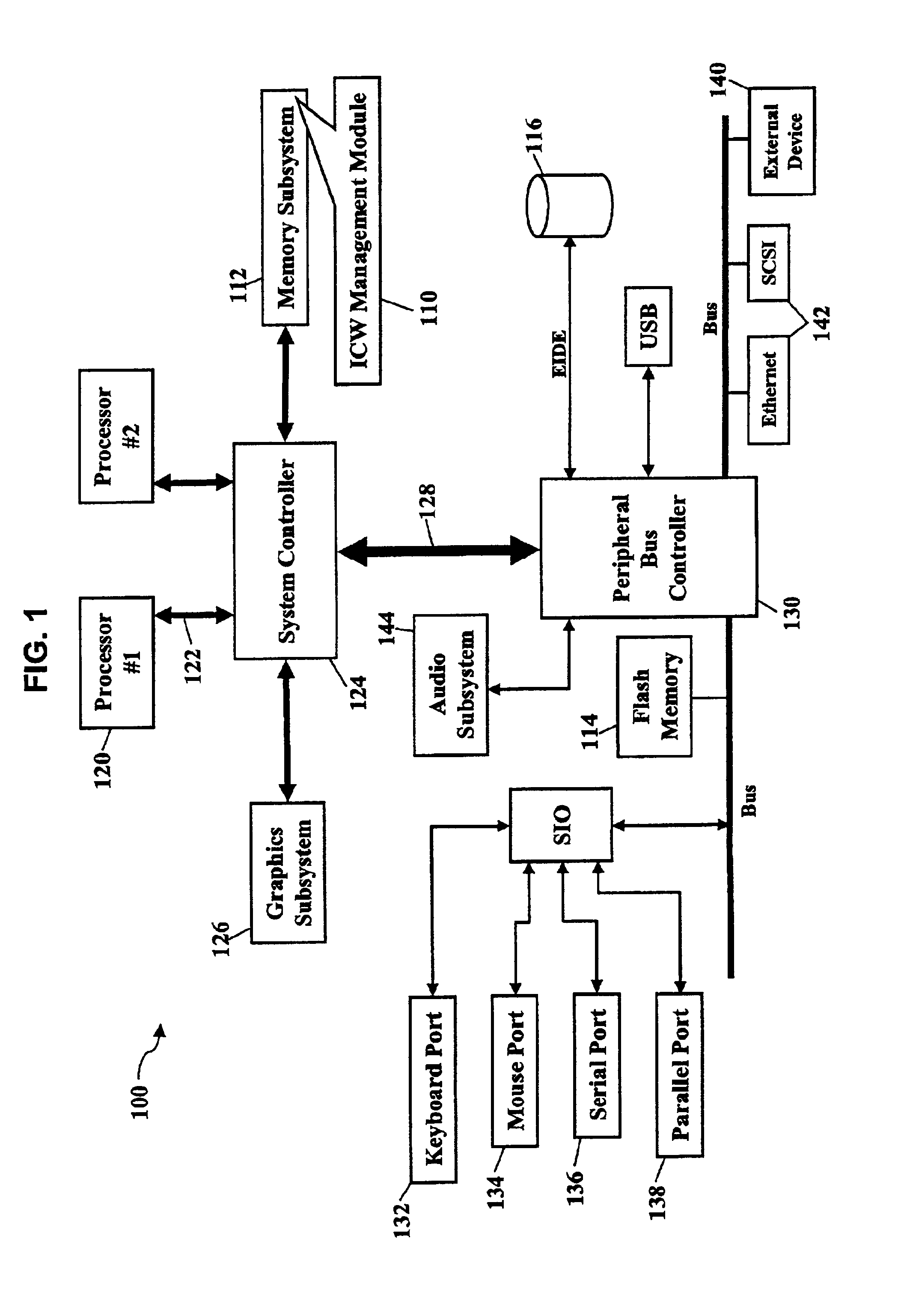
InactiveUS7529357B1Reduce data communicationLower connection costsMultiplex system selection arrangementsSpecial service provision for substationThird partyHandling system
Disclosed are systems and methods that provide centralized or nodal inmate management and telephone call processing capabilities to controlled environment facilities. An inmate management and call processing system serves a plurality of facilities and includes an inmate information database. The database is shared across the facilities and contains inmate records that may be accessed and modified by each facility as the inmate is transferred among those facilities. Each inmate record may include, among other information, contact information of third parties whom may be notified of the inmate's arrest and / or subsequent transfers of the inmate to different facilities. The inmate management and telephone call processing system may use third party contact information to establish accounts used to charge calls or transactions made by an inmate while residing at the facility. Some systems may also provide call processing, video conferencing, e-mail, voicemail, and / or videomail applications, and the like to the facilities.
Owner:SECURUS TECH LLC
Telecommunication call management and monitoring system with voiceprint verification
InactiveUS20050043014A1Accurate verificationEliminating system overloadTelevision system detailsUnauthorised/fraudulent call preventionPersonal identification numberMonitoring system
Disclosed is a secure telephone call management system for authenticating users of a telephone system in an institutional facility. Authentication of the users is accomplished by using a personal identification number, preferably in conjunction with speaker independent voice recognition and speaker dependent voice identification. When a user first enters the system, the user speaks his or her name which is used as a sample voice print. During each subsequent use of the system, the user is required to speak his or her name. Voice identification software is used to verify that the provided speech matches the sample voice print. The secure system includes accounting software to limit access based on funds in a user's account or other related limitations. Management software implements widespread or local changes to the system and can modify or set any number of user account parameters.
Owner:GLOBAL TELLINK
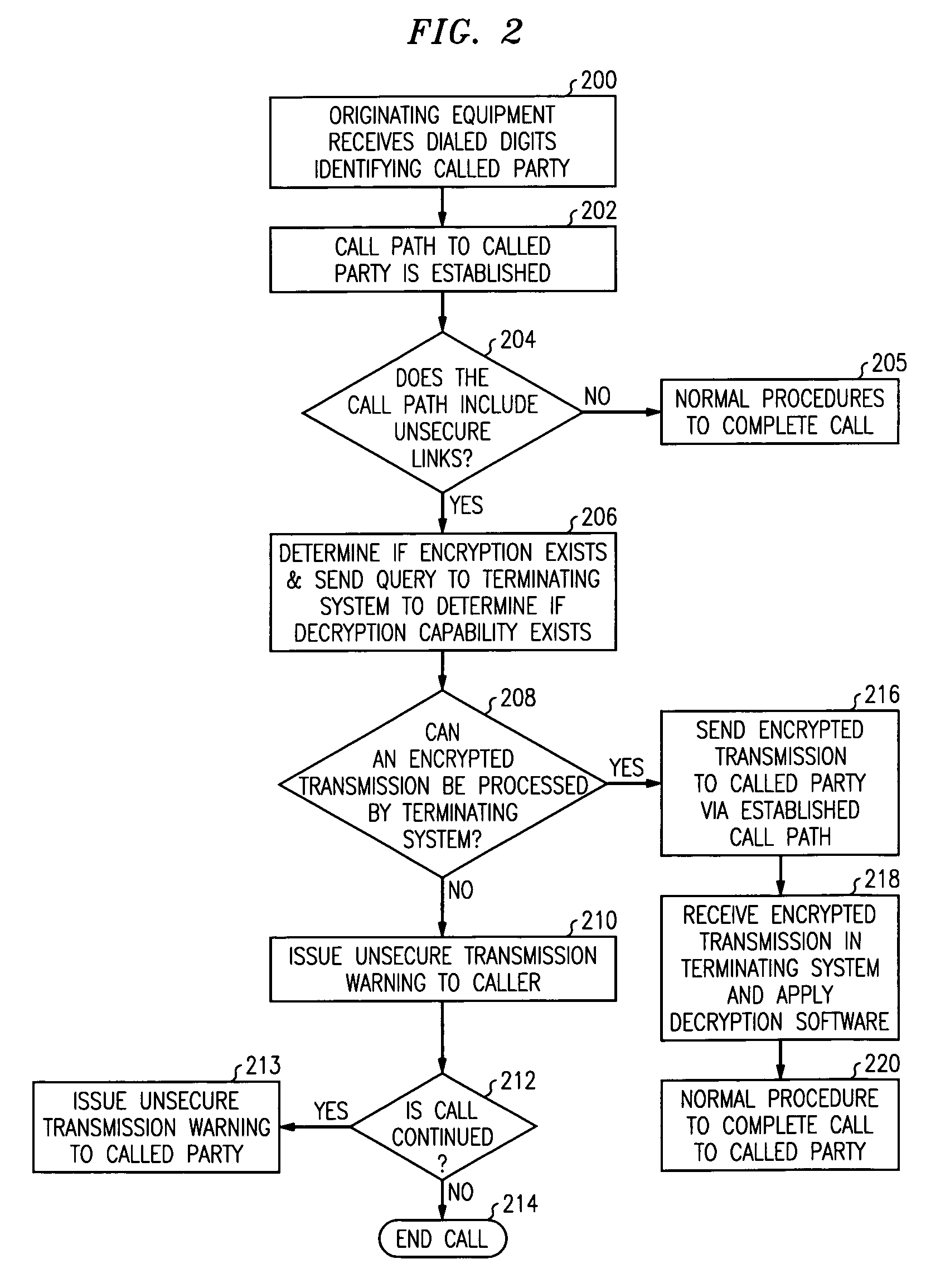
Method for determining the security status of transmissions in a telecommunications network
InactiveUS6959184B1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsTelecommunications linkTelecommunications network
A method for determining the security level associated with transmissions in a telecommunications network includes means for alerting parties of the security status of the transmission. When a route interconnecting the parties includes an insecure link, an alert is provided so that the parties are aware of the insecure nature of the call before communications begin. Alternatively, the parties may elect to decline or alter content of the communications to preserve integrity.
Owner:LUCENT TECH INC
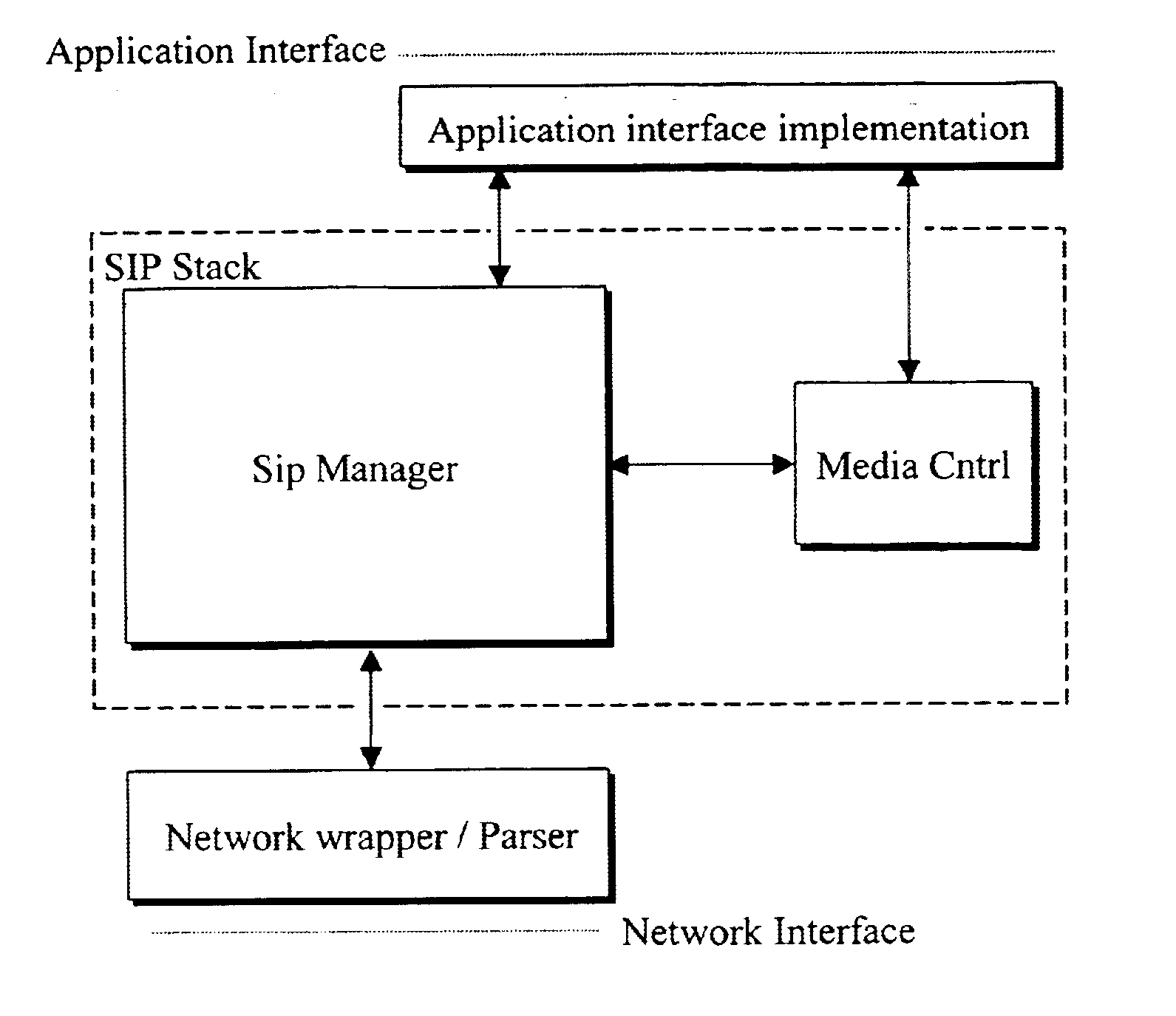
VoIP terminal security module, SIP stack with security manager, system and security methods
InactiveUS6865681B2Interconnection arrangementsUser identity/authority verificationModularitySecure voice
A secure voice over internet protocol (VoIP) terminal includes a modular security manager for use in conjunction with a protocol stack thereof, wherein the security manager includes a plurality of interfaces to the stack. In an SIP embodiment, these may include a security stack interface (SSA) between an SIP manager of an SIP stack and the security manager, a security terminal interface (SST) between a telephony application and the security manager, a security media interface (SSM) between the security manager and a media controller, and a security manager application interface (SMA) between the security manager and a security application (PGP) outside the stack.
Owner:NOKIA TECHNOLOGLES OY
Method and apparatus for providing media-independent self-help modules within a multimedia communication-center customer interface
InactiveUS6910072B2Highly-selective helpMultimedia data browsing/visualisationDc level restoring means or bias distort correctionOperational systemMedia type
In a multimedia call center (MMCC) operating through an operating system, a client-specific self-help wizard is provided for active clients and updated periodically with information related to client transaction history with the MMCC. A connected client is presented by the wizard with a selective media function through which the client may a select a media type for interaction and help, and the MMCC will then re-contact the client through the selected media. The client, for example, may select IP or COST telephony, and the MMCC will place a call to the client to a number or IP address listed for the client, and interactivity will then be through an interactive voice response unit. Help information specific to a client is updated in the client's wizard periodically according to ongoing transaction history with the MMCC. The wizard may also monitor client activity with the wizard and make reports available to various persons.
Owner:GENESYS TELECOMMUNICATIONS LABORATORIES INC +1
Method and apparatus for delivering secured telephony service in a hybrid coaxial cable network
InactiveUS20050034168A1Low costEliminate useInterconnection involving common lineBroadcast transmission systemsCoaxial cableInteractive video
A hybrid coaxial cable network employing interdiction to ensure privacy in telephony communications. The video and telephony signals are secured such that telephony and interactive video signals to and from a subscriber do not appear on the network at any other undesired subscriber location.
Owner:COMCAST MO GROUP
System and method for call management
ActiveUS20100220849A1Interconnection arrangementsSpecial service for subscribersCall managementTelephony
A method and system for call management is provided. In a system embodiment a call manager server is provided that can managing incoming call requests from certain telephony devices and effect connections to other telephony devices based on those incoming call requests. The call manager server can also maintain a policy that defines permissions as to whether certain telephony devices can request interruption of an ongoing phone call at a destination telephony device.
Owner:MALIKIE INNOVATIONS LTD
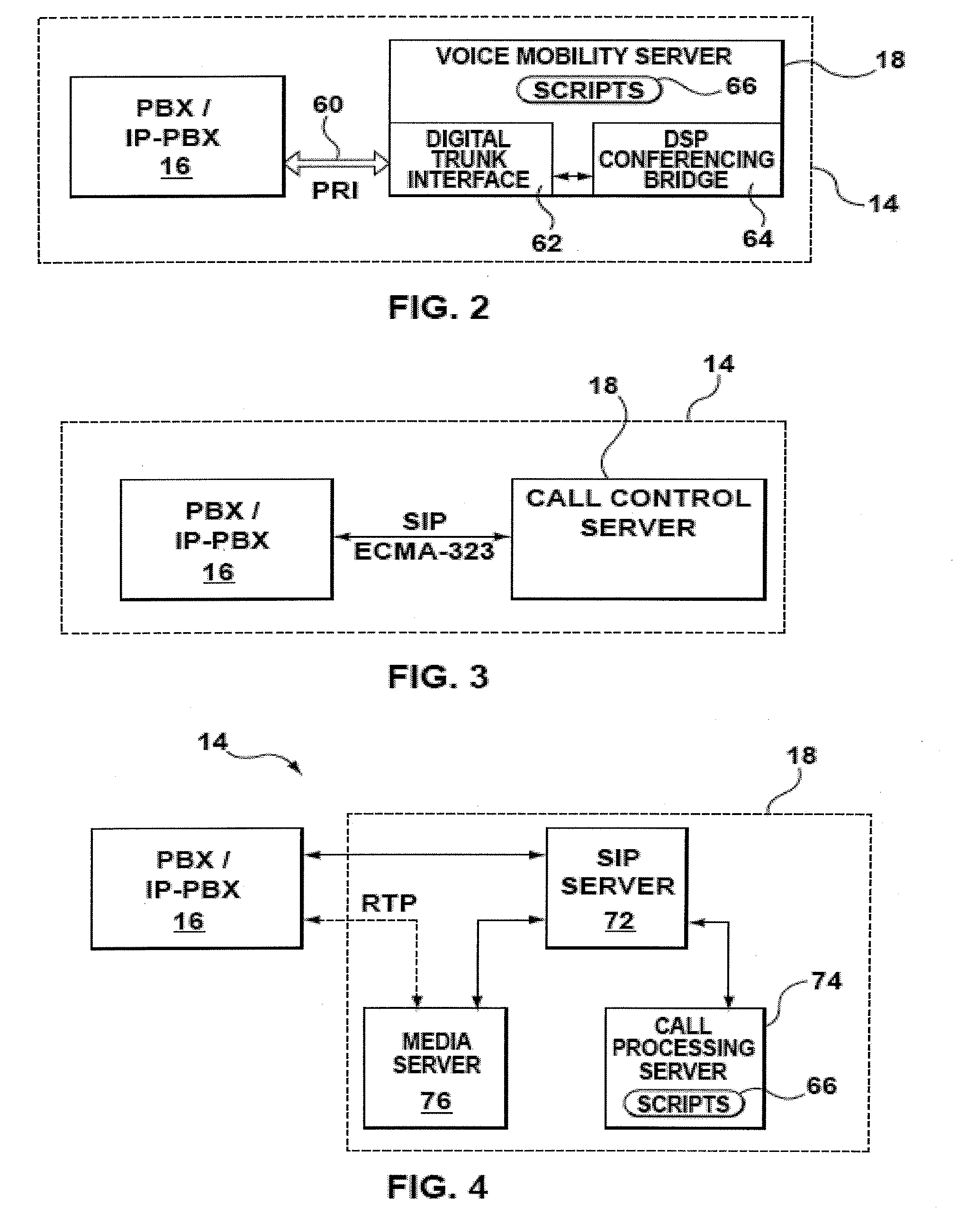
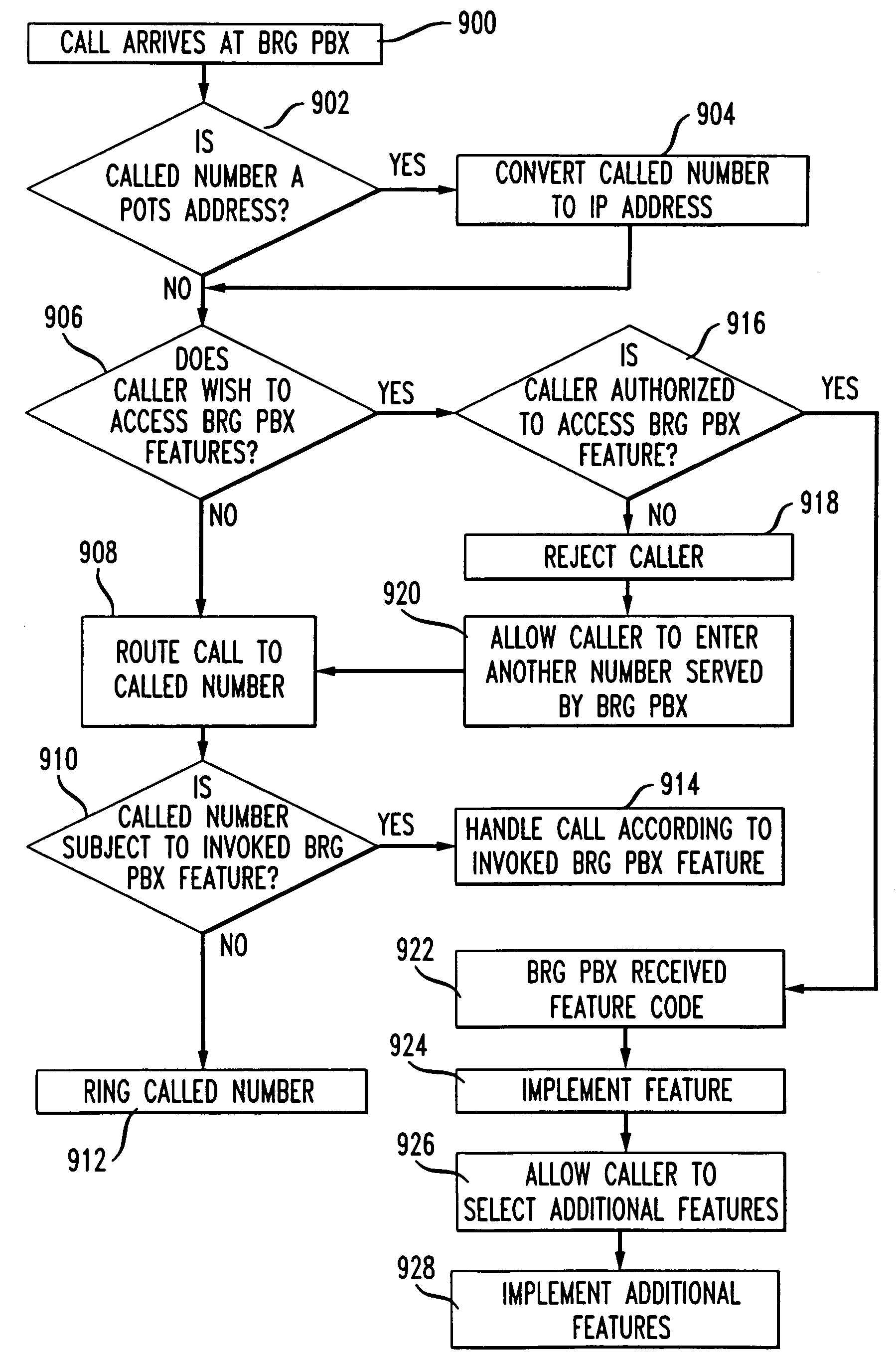
BRG with PBX capabilities
InactiveUS7075918B1Minimizing problems during installationMinimizes problemInterconnection arrangementsSpecial service for subscribersGeographic regionsResidence
A residential private branch exchange (PBX) allowing IP telephones, analog telephones and computers to connect to an IP communication network. A broadband residential gateway (BRG) PBX provides residences with multiple phone lines capability and the implementation of complex calling features traditionally associated with complex and expensive business PBX systems. The BRG PBX provides an open architecture interface minimizing problems during installation and operation, minimizes interoperability problems across multi-vendor equipment platforms and may provide customers with an option to bypass the local telephone company's high cost infrastructure. The BRG PBX may also provide a range of services from basic calling with few features to highly sophisticated calling features servicing multiple phone lines to the residence. The BRG PBX may be configured to connect multiple BRG PBX systems together in a Local Area Network (LAN) or Wide Area Network (WAN) configuration. These network configurations may be implemented to connect neighborhoods or families across multiple geographic regions. In addition to having the capability of connecting to each other, the BRG PBXs may be connected to IP Central Stations forming an IP communication network.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
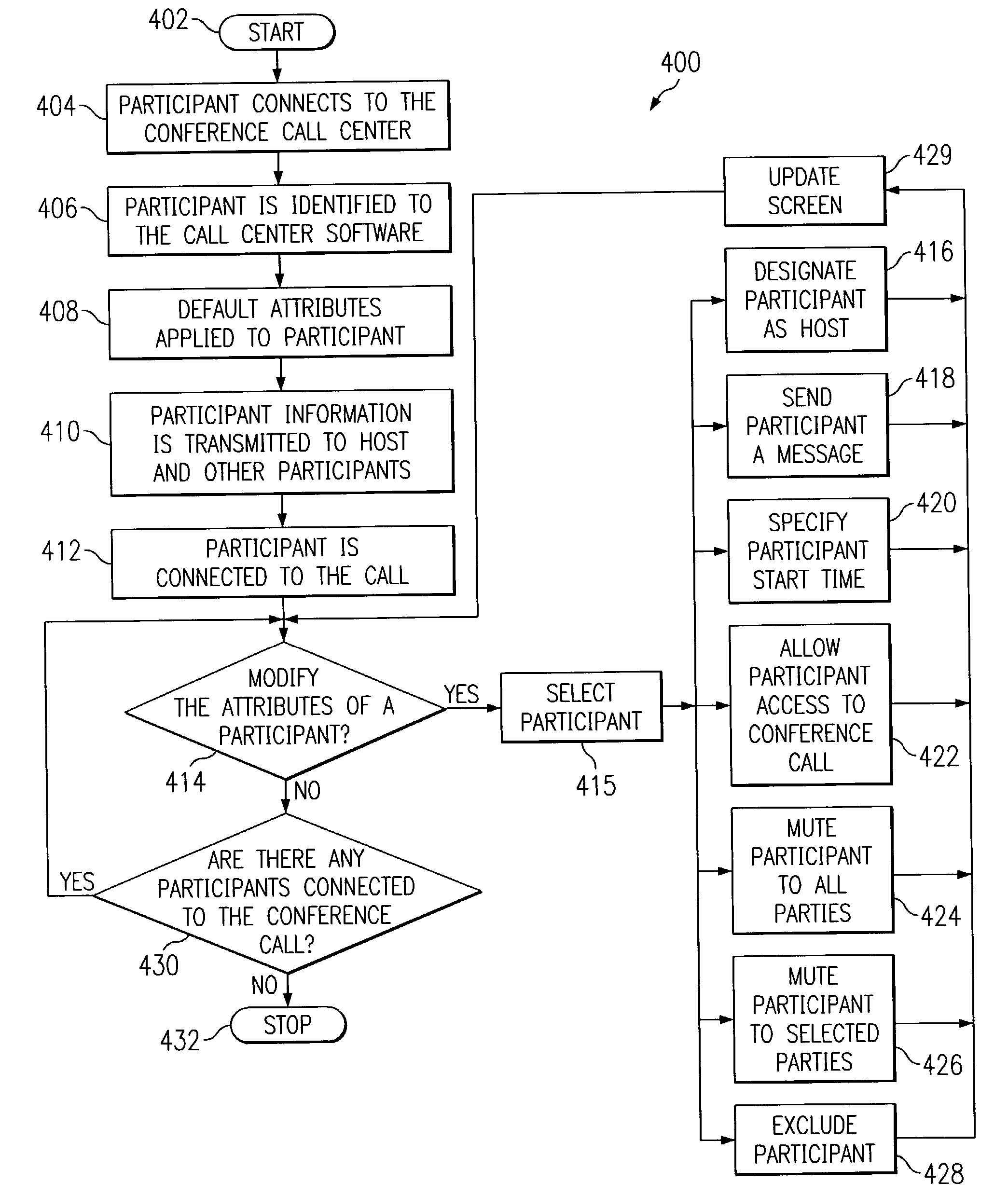
Apparatus and method for controlling conference call participants
InactiveUS7317791B2Interconnection arrangementsSpecial service for subscribersComputer softwareTeleconference
The present invention, which meets the needs identified above, is an apparatus and method of controlling a conference call using an improvement on the conference calling center's computer software. The control program allows the host of a conference call to selectively control the dissemination of information between conference call participants. The control program allows the host to designate other hosts, create private meetings among conference call participants, mute any number of participants in relation to each other, or completely exclude participants. The participants may also send messages to other participants or the host using the present invention. A control screen is disclosed that allows the user to direct the flow of information among participants. A connection screen is also disclosed to further assist the host in determining the appropriate flow of information between participants.
Owner:GOOGLE LLC
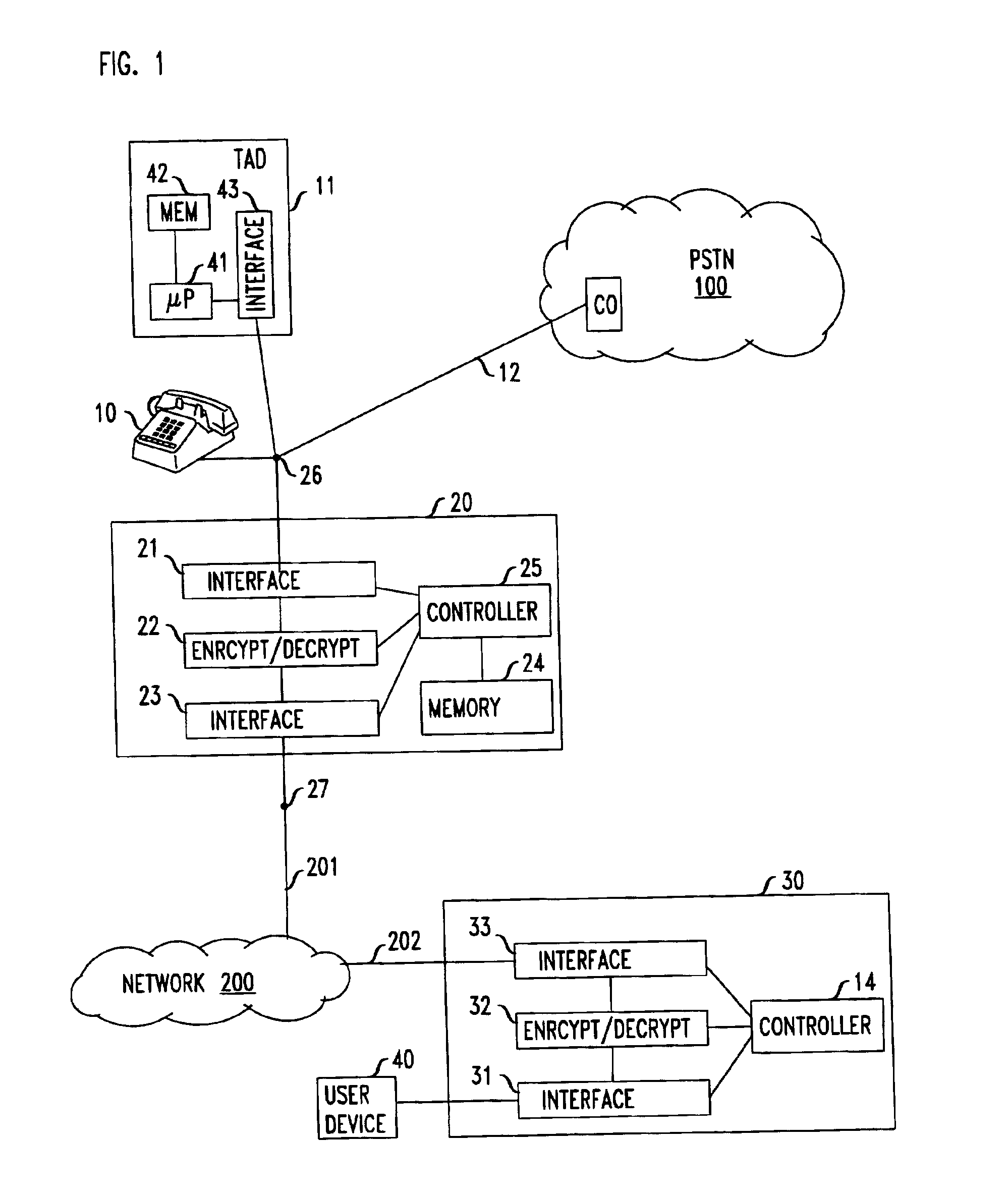
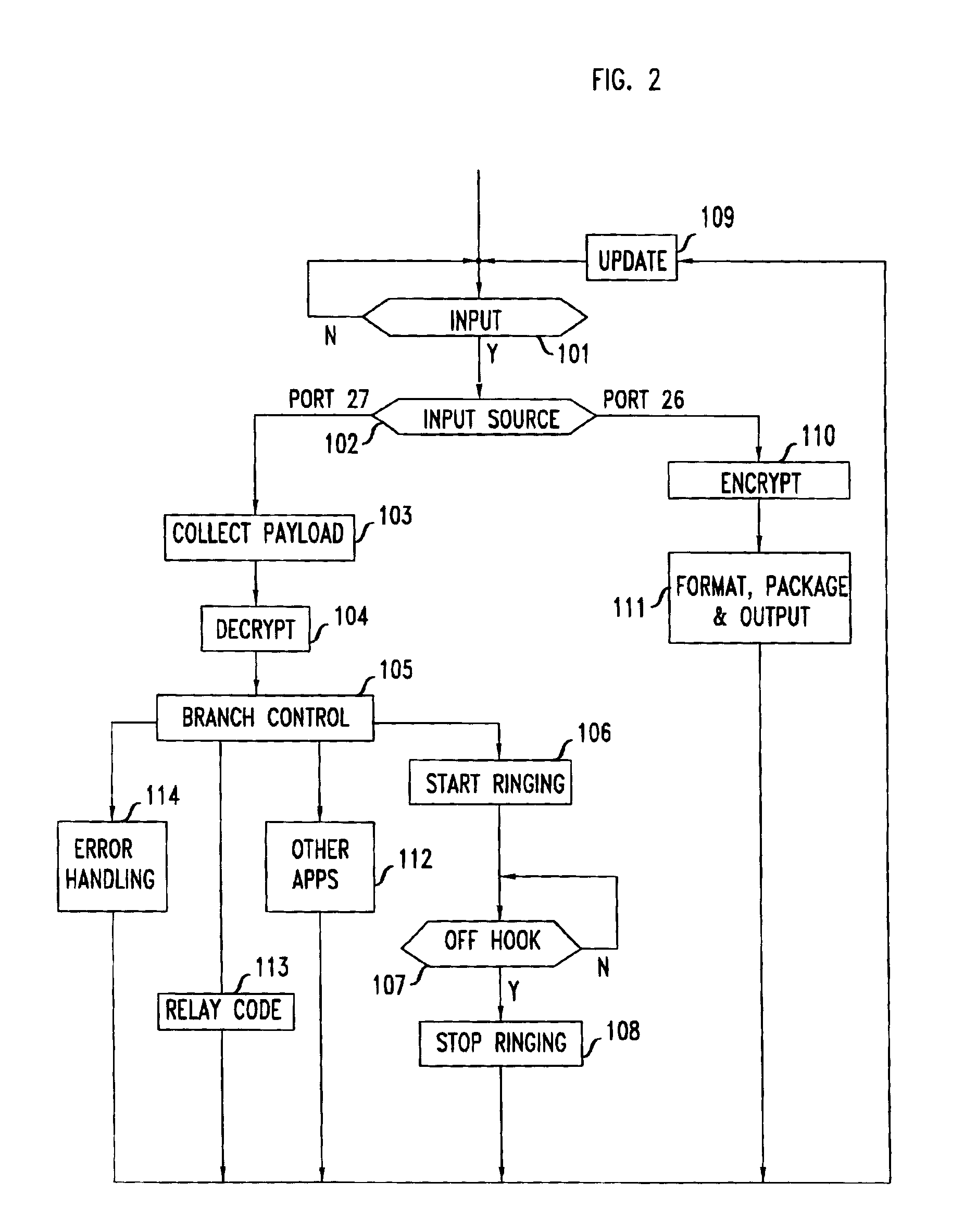
Secure remote access to voice mail
InactiveUS6912275B1Overcome problemsEavesdropping prevention circuitsAutomatic call-answering/message-recording/conversation-recordingTelephone networkEavesdropping
A coupler includes an analog port for interfacing with a telephone answering system a network port that is adapted for connection to an insecure network. The security problem associated with eavesdropping over insecure network is overcome by encrypting the messages that exit through the coupler's network port. In one embodiment, the coupler and the telephone answering system are distinct hardware elements and the coupler is connected to the TAD. In another embodiment, a single processor and associated memory perform the functions of the coupler's controller and of the telephone answering system, thus forming a single device that has an analog port for connecting to the public switched telephone network, as well as a port for connection to the insecure network. In yet another embodiment, the coupler / TAD combination includes a control port to allow connection to the control port of an ISDN telephone.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
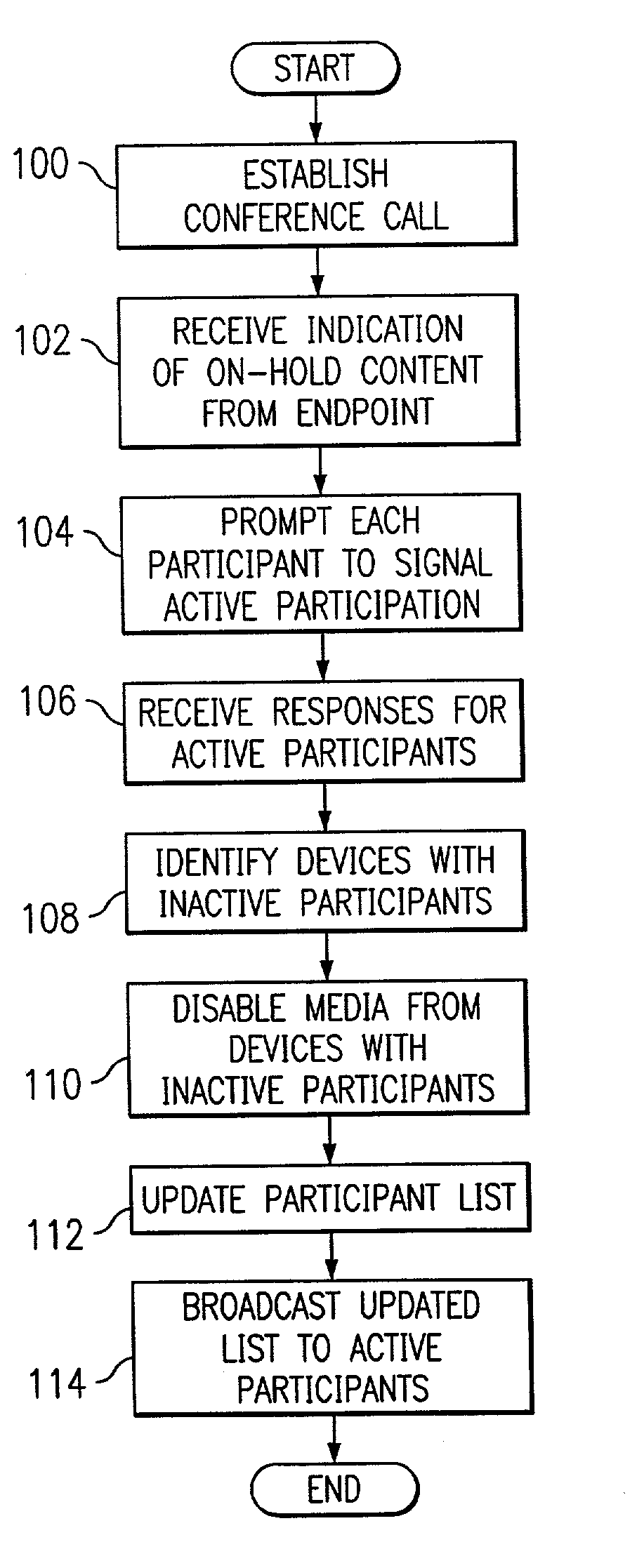
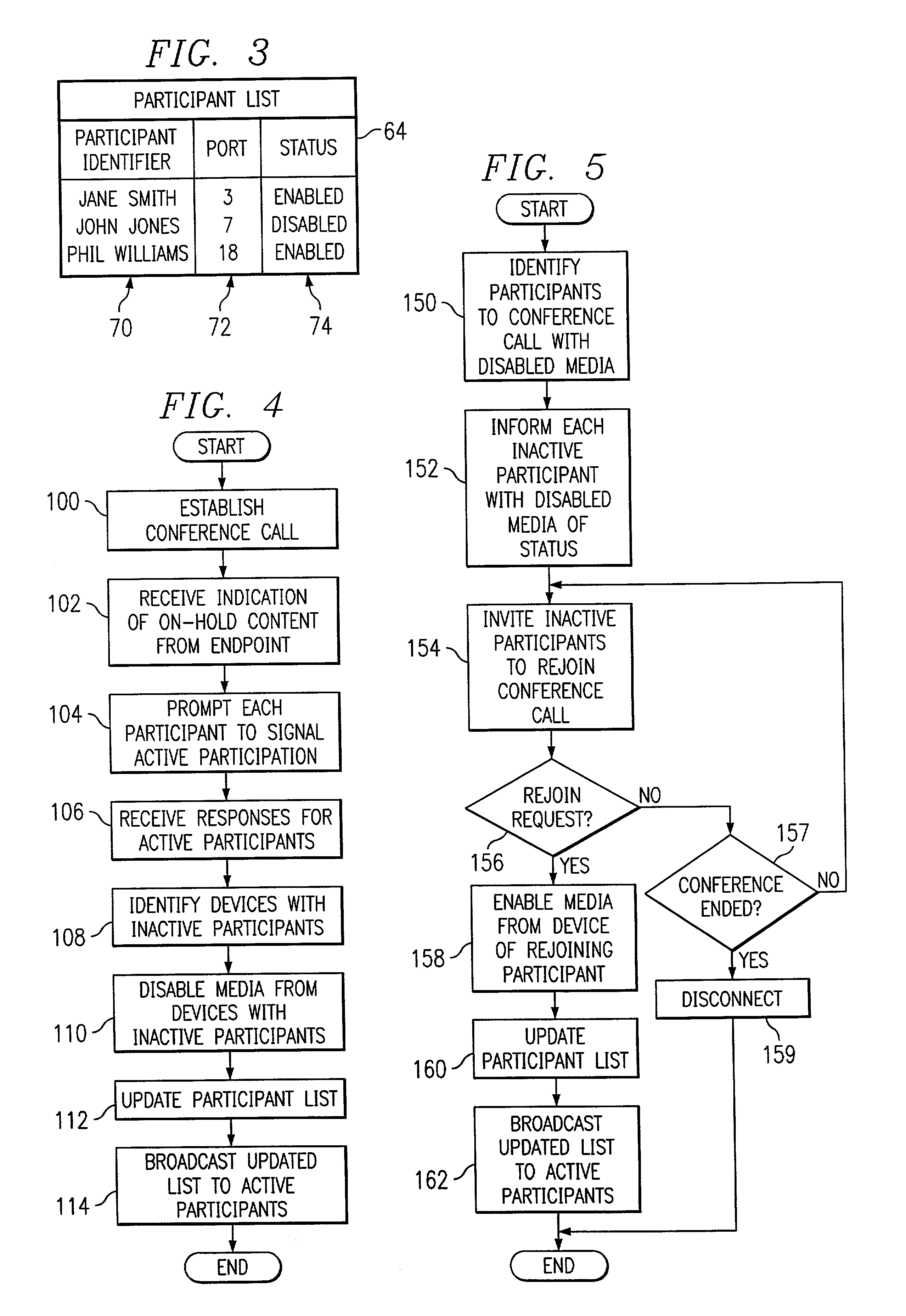
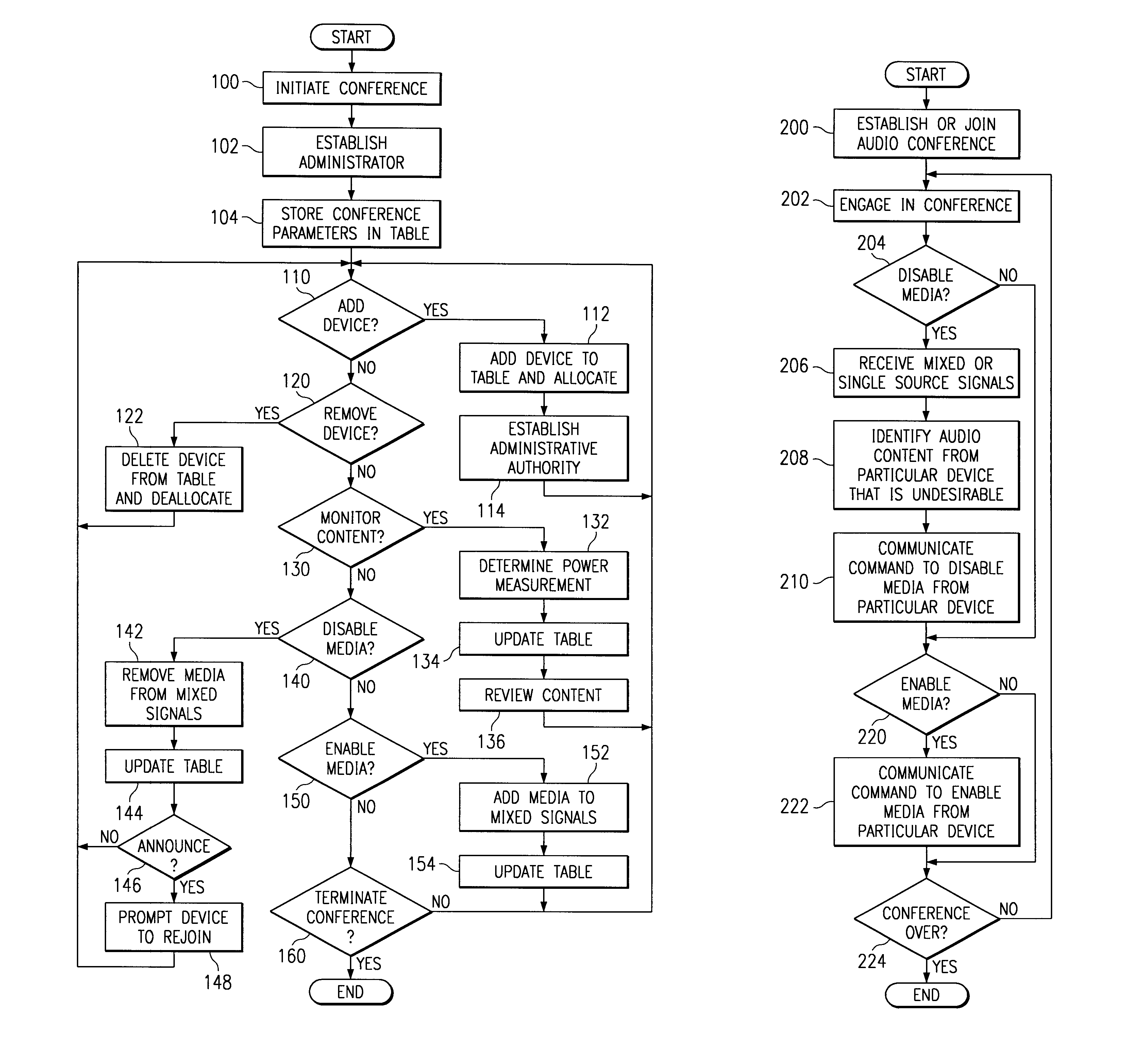
Method and system for controlling audio content during multiparty communication sessions
InactiveUS6978001B1Readily apparentSpecial service provision for substationMultiplex system selection arrangementsComputer networkMultiparty communication
A method and system for controlling audio content during a multiparty communication session includes prompting active participants to the multiparty communication session to identify themselves. Media from a particular device from which no active participant is identified is disabled to terminate communication of the media from the particular device to other devices in the multiparty communication session.
Owner:CISCO TECH INC
Virtual PBX based on feature server modules
ActiveUS20070047534A1Special service for subscribersData switching by path configurationOperating systemBranch exchange
A virtual private branch exchange is formed by a plurality of interconnected feature server modules, each having an integral feature server that is configured and operates independently of the other feature server modules. Within a virtual private branch exchange, the feature server modules may be logically arranged in a hierarchy having at least a main feature server module and one or more subordinate feature server modules. A particular feature server module may operate in multiple virtual private branch exchanges, and may have a distinct set of rules for handling calls originating in different virtual private branch exchanges.
Owner:RESOURCE CONSORTIUM LTD LLC
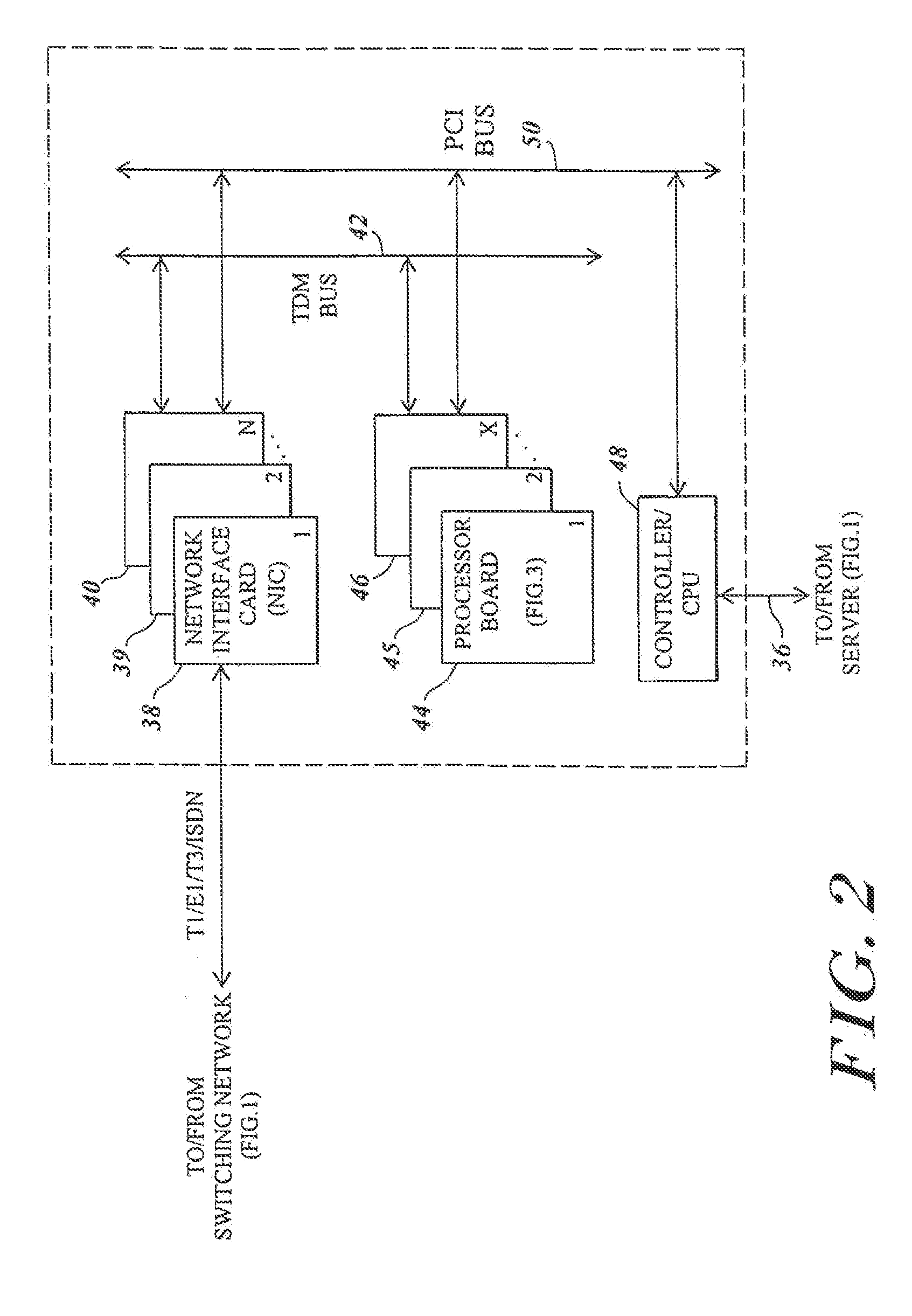
Audio conference platform with dynamic speech detection threshold
InactiveUS20130028404A1Improve conferencingReduce echoSpecial service provision for substationTwo-way loud-speaking telephone systemsEngineeringSpeech sound
The present invention comprises a method for audio / video conferencing. In a preferred embodiment, the method comprises using a dynamic threshold value to determine whether there is speech on a line. One aspect, the method comprises determining a dynamic threshold value based on one or more characteristics of signals received on a port, associating that dynamic threshold value with the port; and comparing one or more characteristics of signals subsequently received on the port to the dynamic threshold value. Signals received over a plurality of ports are summed, but for ports whose signal characteristics have a specified relationship to the dynamic threshold value associated with that port, signals are not contained in the sum.
Owner:HEWLETT PACKARD DEV CO LP
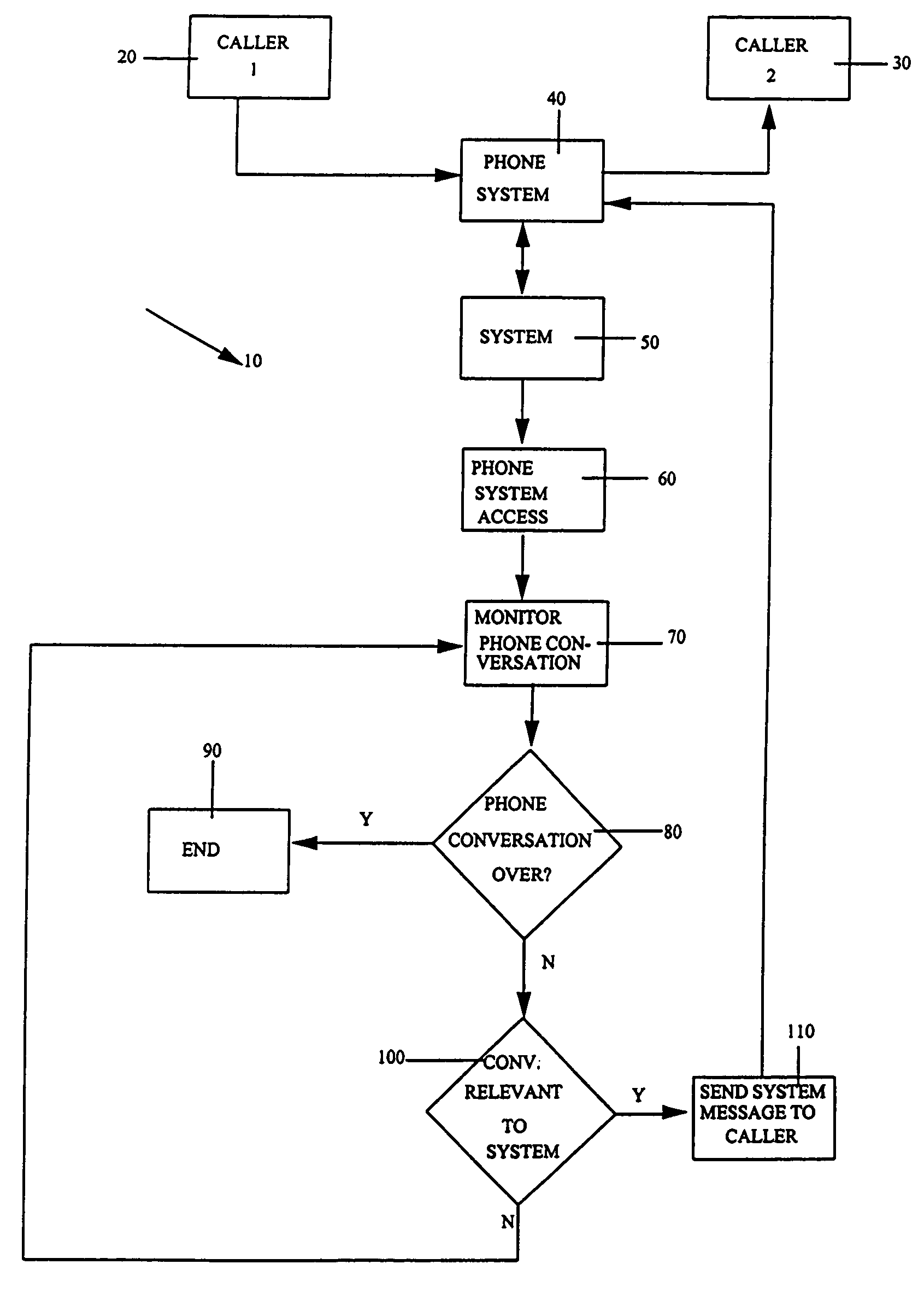
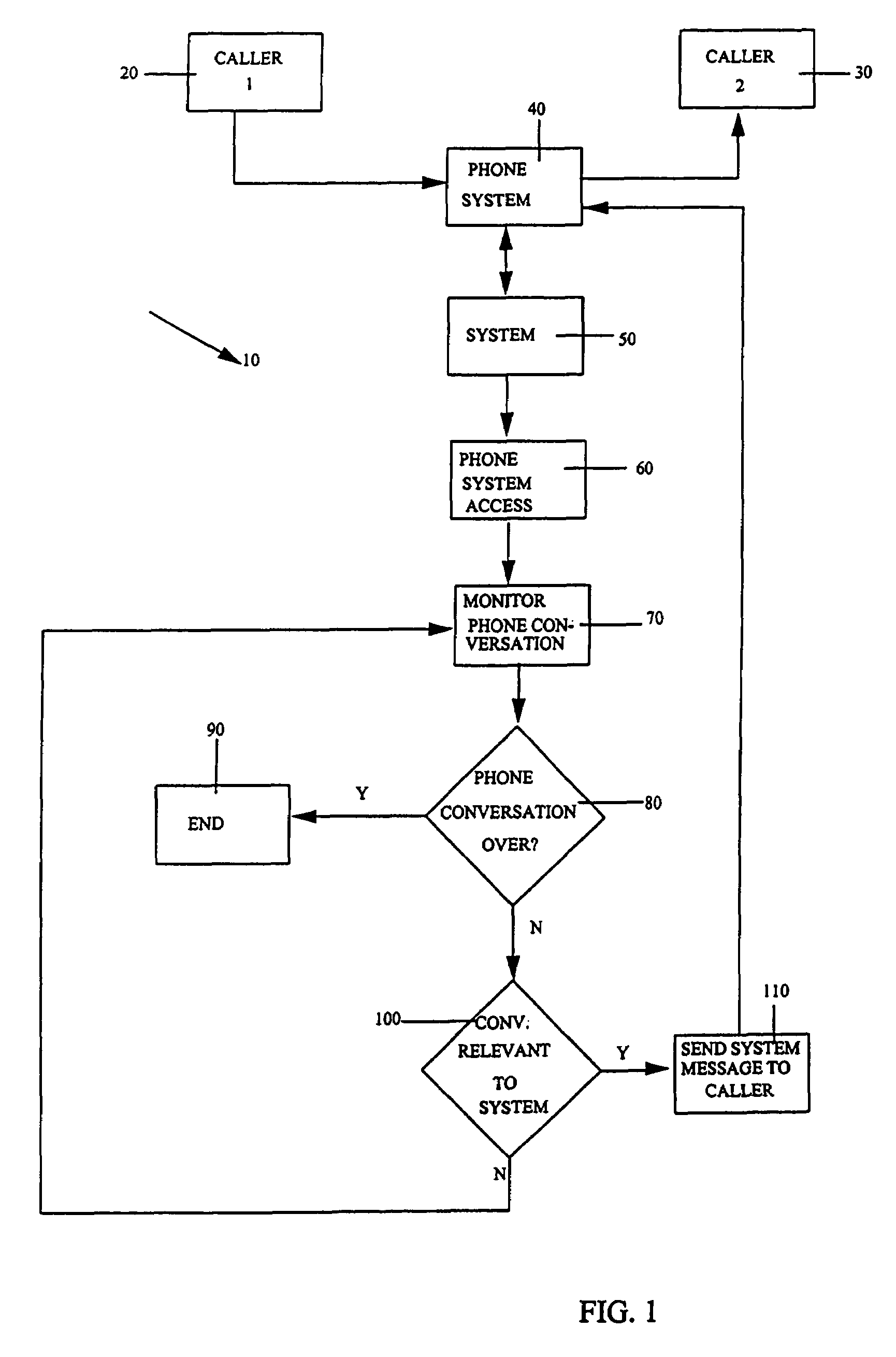
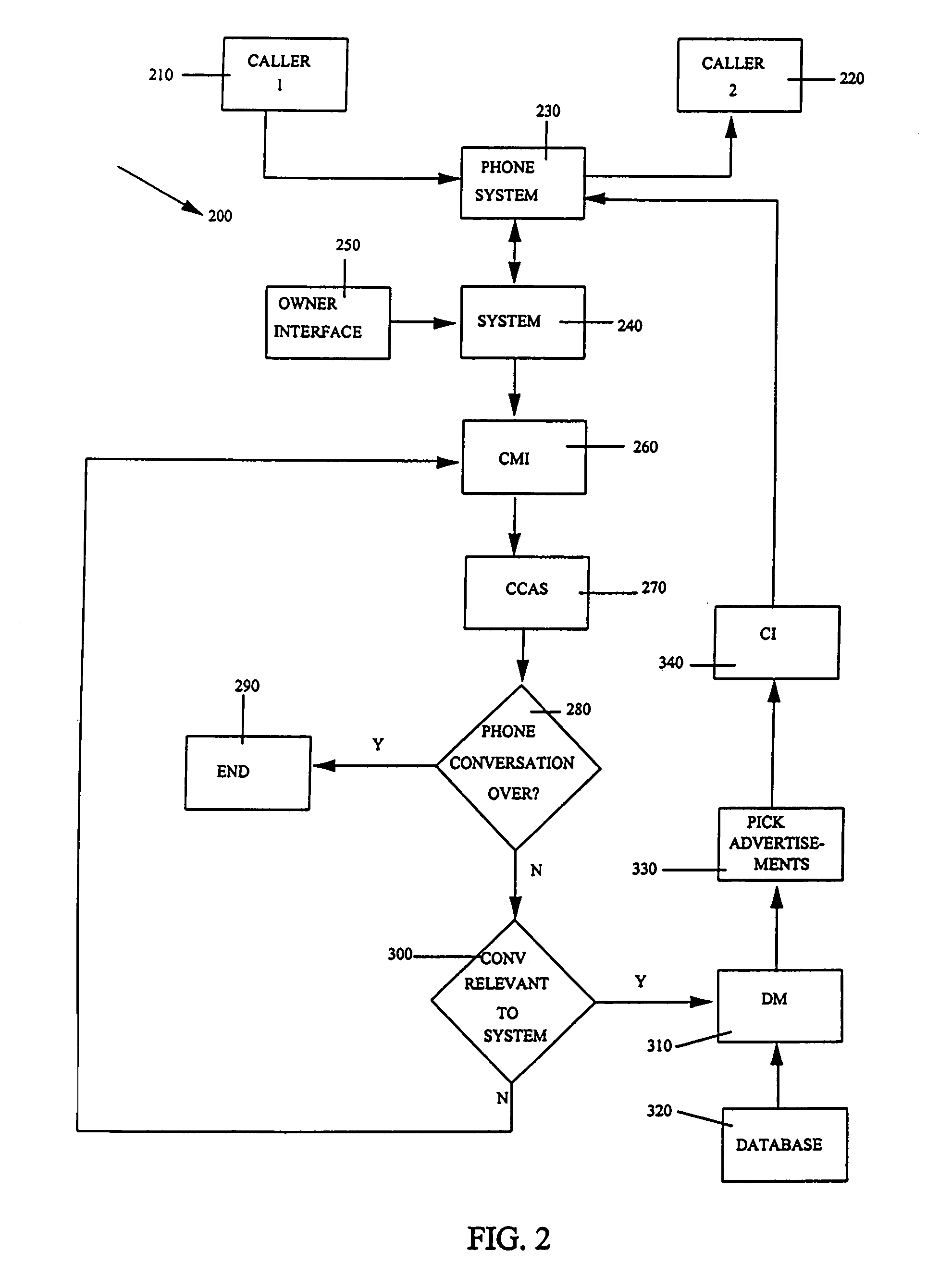
System and technique for dynamically interjecting live advertisements in the context of real-time isochronous (telephone-model) discourse
ActiveUS7400711B1Automatic call-answering/message-recording/conversation-recordingSpecial service for subscribersSelection systemHuman language
A method, system and program storage device are provided for interjecting messages into a real-time isochronous discourse (such as a telephone call) between a plurality of callers wherein the method, system and device accesses the call between the callers, monitors the discourse to determine if the discourse relates to a system message desired to be communicated to the caller, chooses and communicates the system message to the callers when the discourse is determined to be relevant to the system message and continues the above accessing, monitoring and communicating steps until the call being accessed between the callers is terminated. The interjected messages are primarily related to advertising and can be introduced to one or more callers, or, separate messages in different languages can be introduced to one or more callers depending on the caller's accessing the telephone. Caller subscribers of the system will typically have the cost of the call partly or totally subsidized by the method and system.
Owner:GOOGLE LLC
Method of and Apparatus for Communicating User Related Information Using a Wireless Information Device
InactiveUS20080045184A1Special service for subscribersSubstation equipmentTime scheduleRelevant information
A mobile telephone which can supply or post 'pre-answer' information which the device owner considers of relevance to a potential call recipient. This information enables a potential call recipient to be given useful information about a potential call before actually answering that call. The information is dynamic, unlike Caller ID information. Examples include: information about the subject of an intended voice call, a mood, a current activity, part or whole of a schedule of meetings or events, information about the urgency of an intended voice call, personal information, expected call duration, commercial inducements to a consumer to answer a call (special offers, loyalty points etc.), location information.
Owner:NOKIA TECHNOLOGLES OY
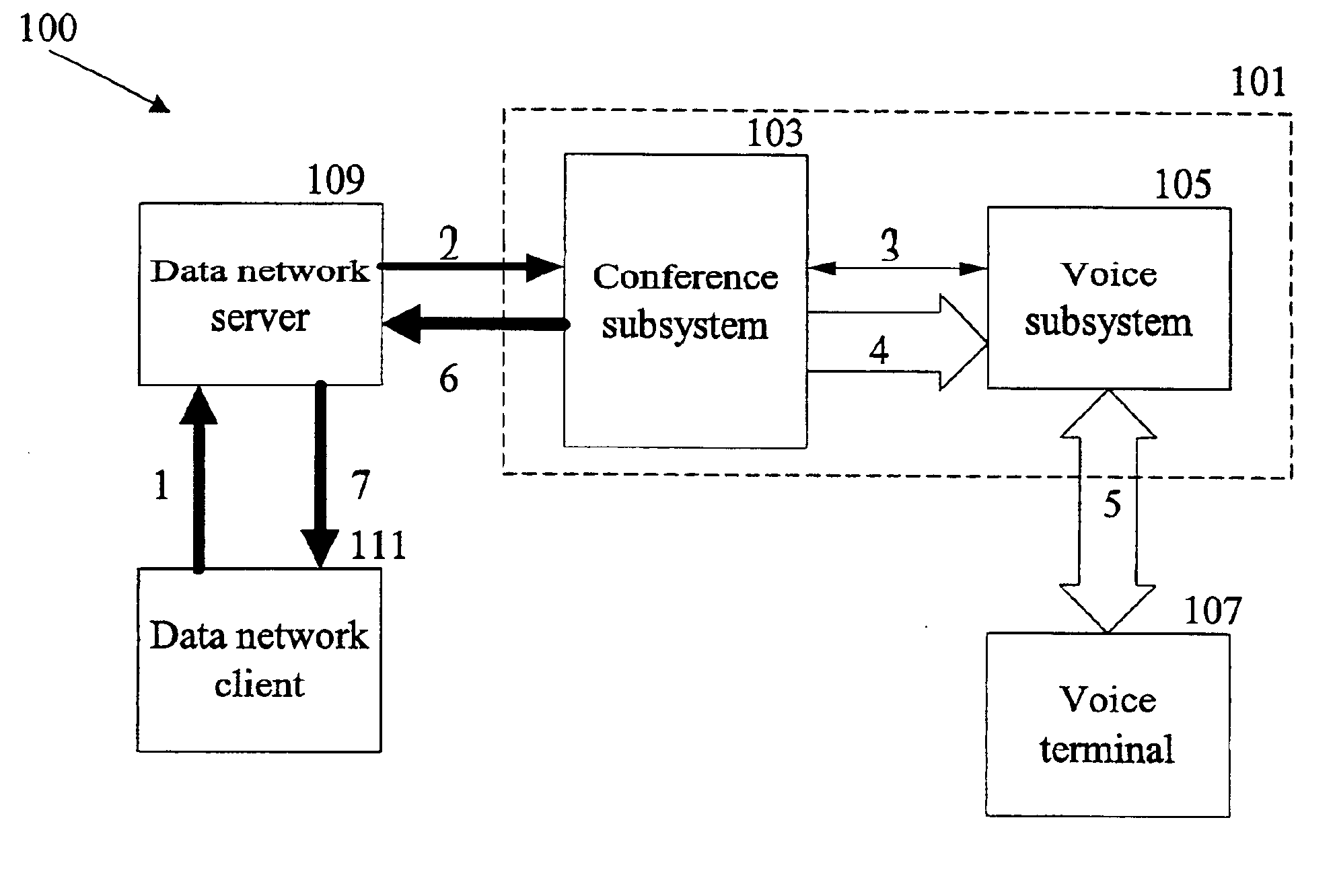
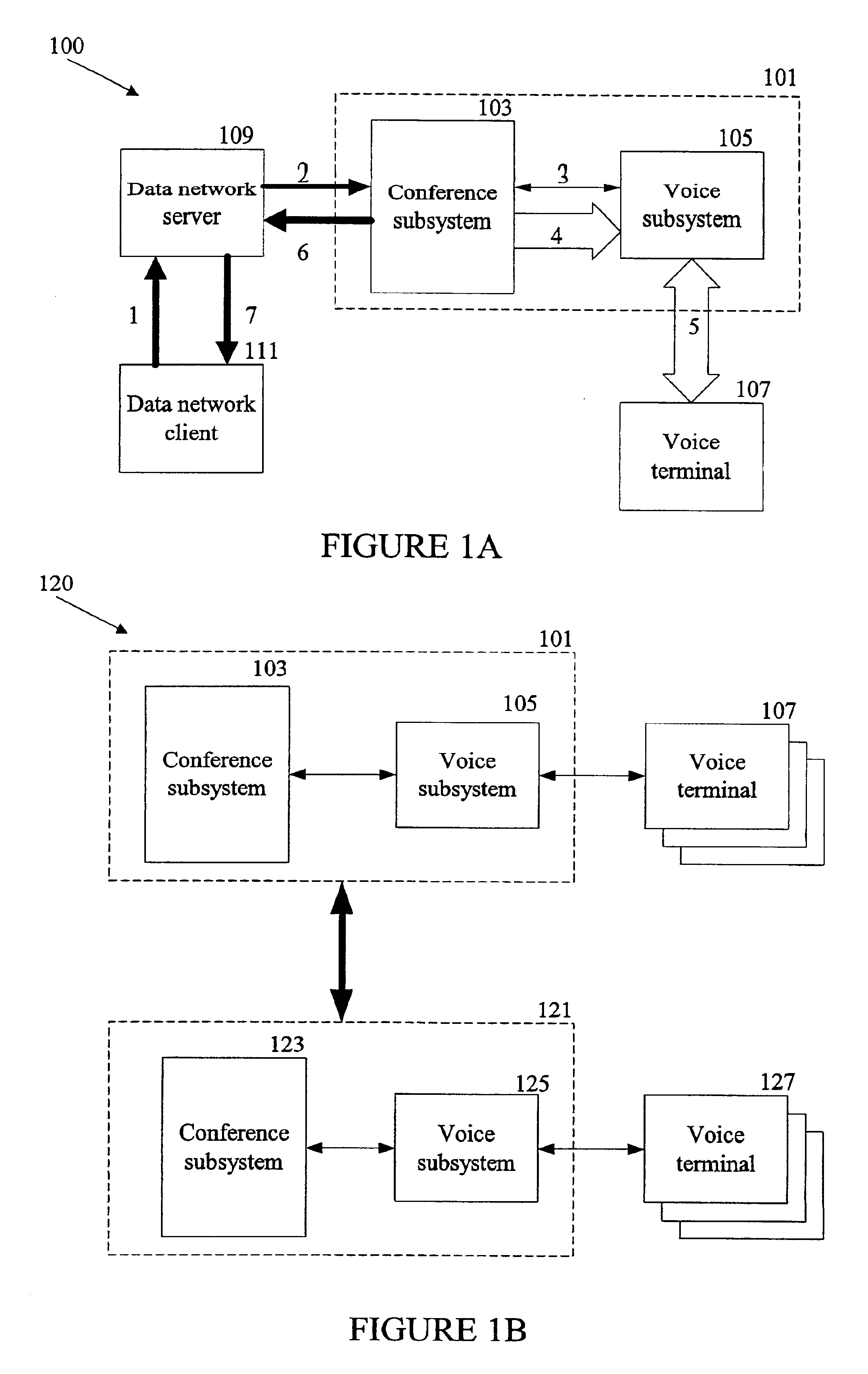
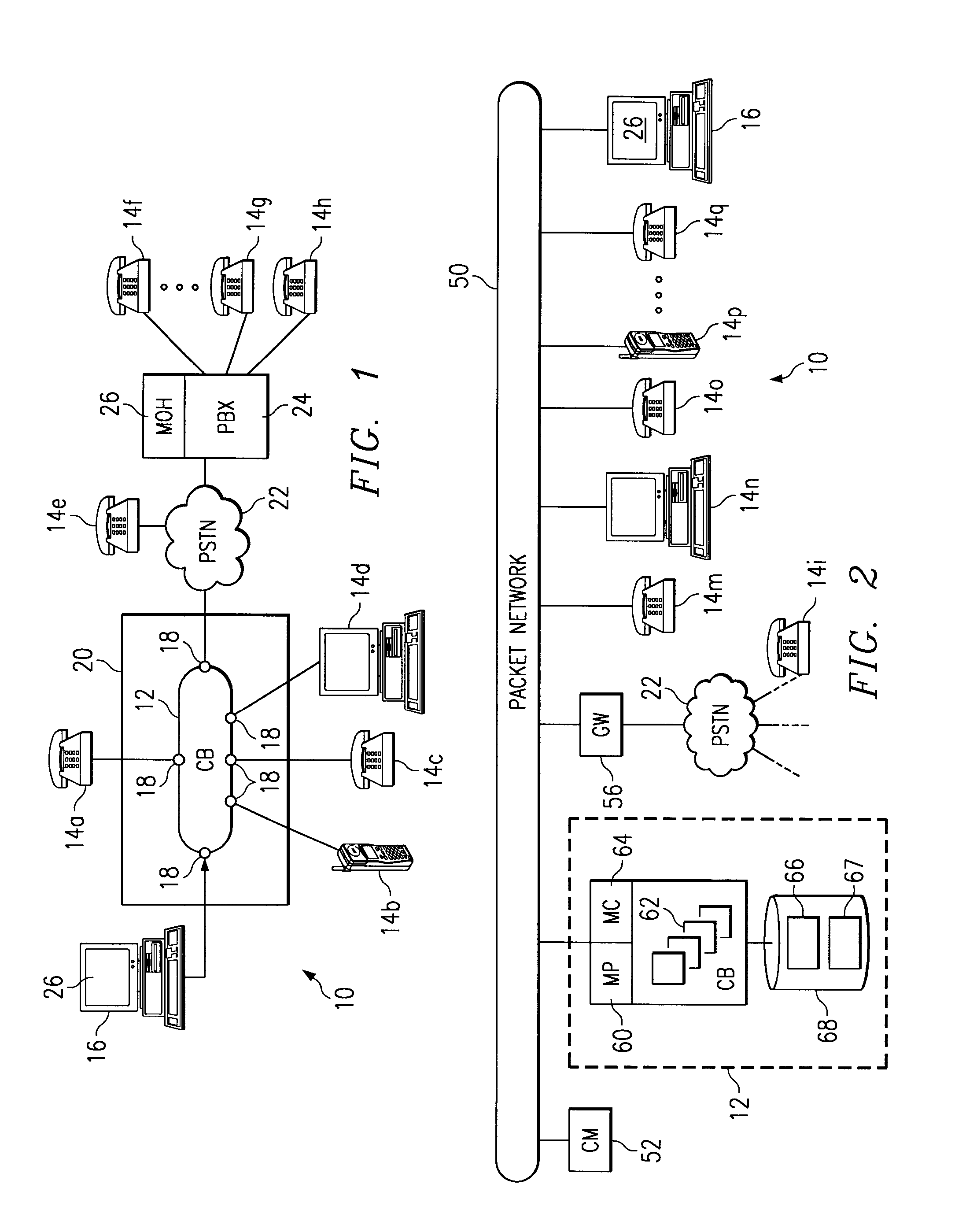
End user control of a teleconferencing network through a data network
InactiveUS6915331B2Telephone data network interconnectionsSpecial service for subscribersGraphicsGraphical user interface
A user connected to a data network controls a parallel teleconference network by sending requests through the data network. The requests are validated against permissions granted to the user and an action associated with a request is performed at the teleconferencing network if the request is validated. A status for a teleconference hosted by the teleconferencing network may be sent when the action is performed or when other changes occur during the teleconference. A voice message also may be sent to a user that is affected by the action. In one aspect, the allowed actions are presented to the user through the data network. In another aspect, a graphical user interface for controlling the teleconferencing network is presented to the user through the data network.
Owner:CISCO TECH INC
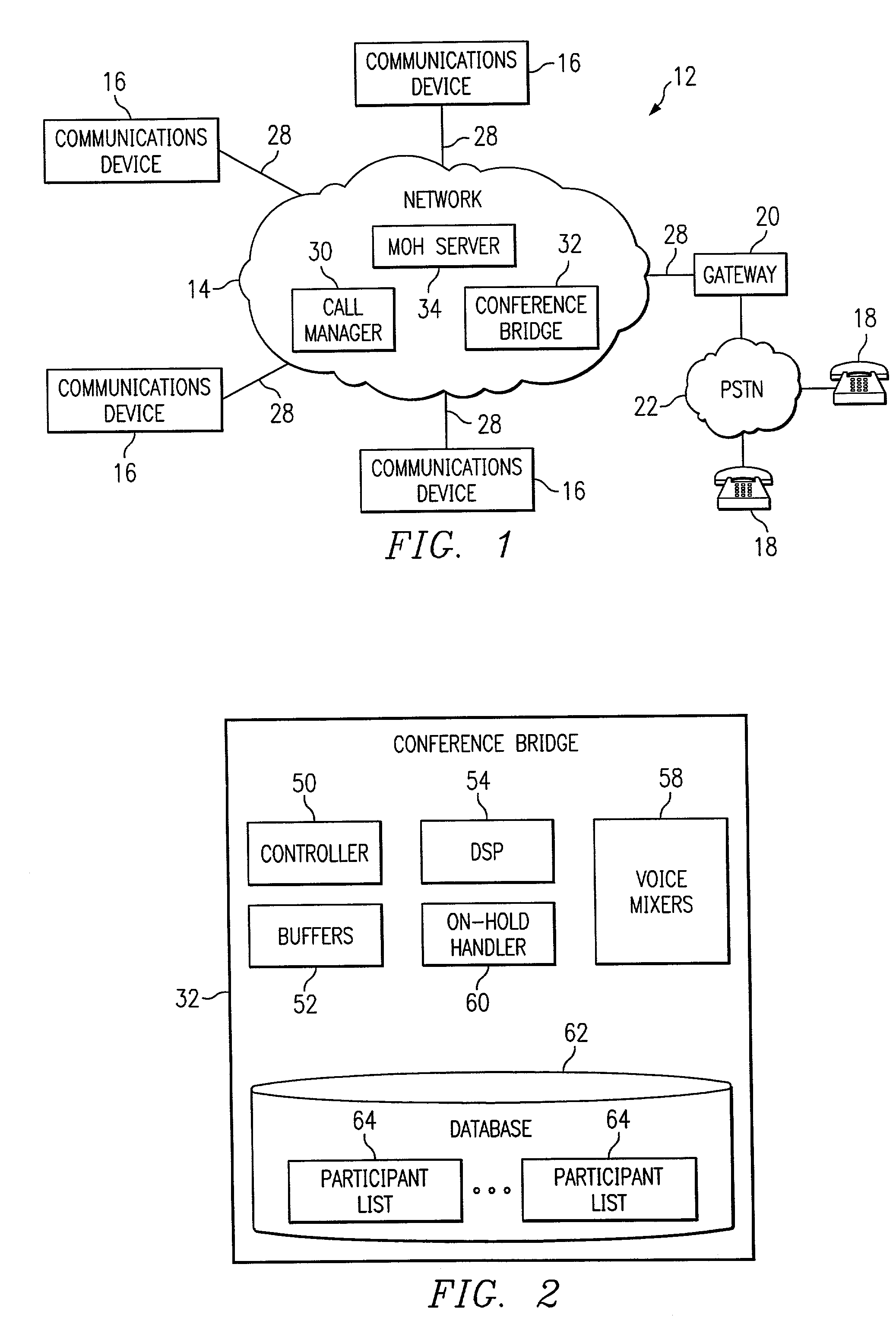
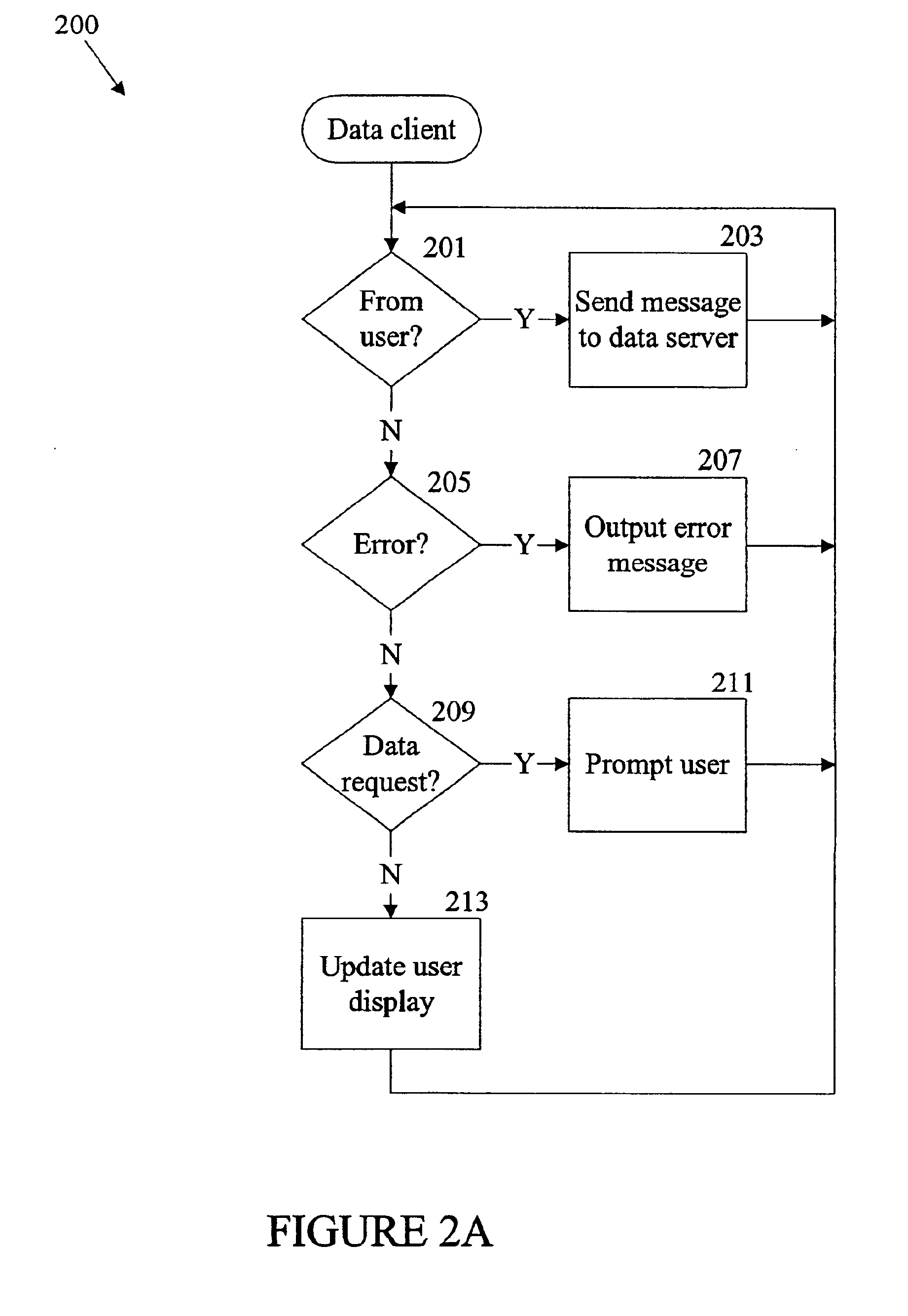
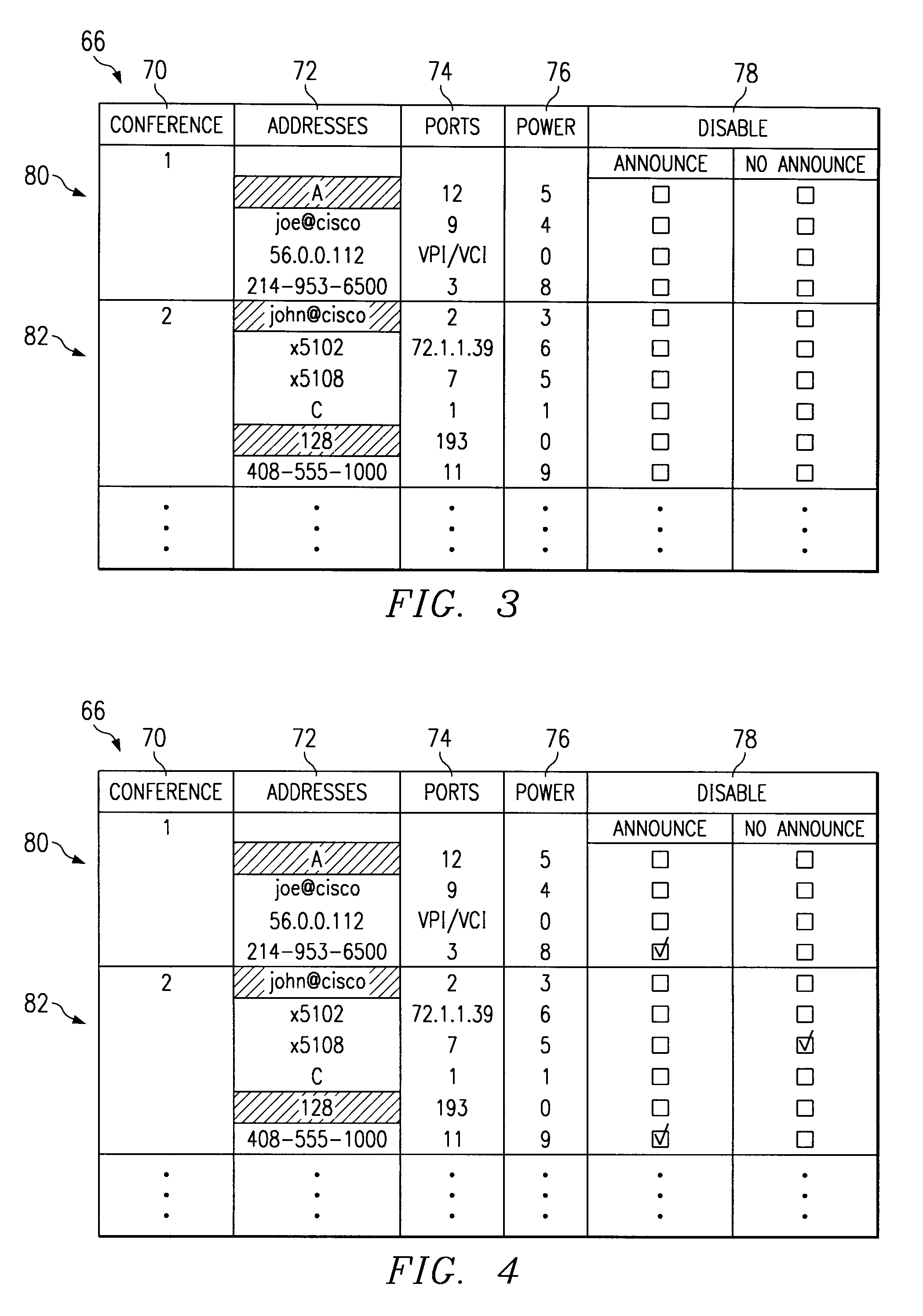
Apparatus and method for controlling an audio conference
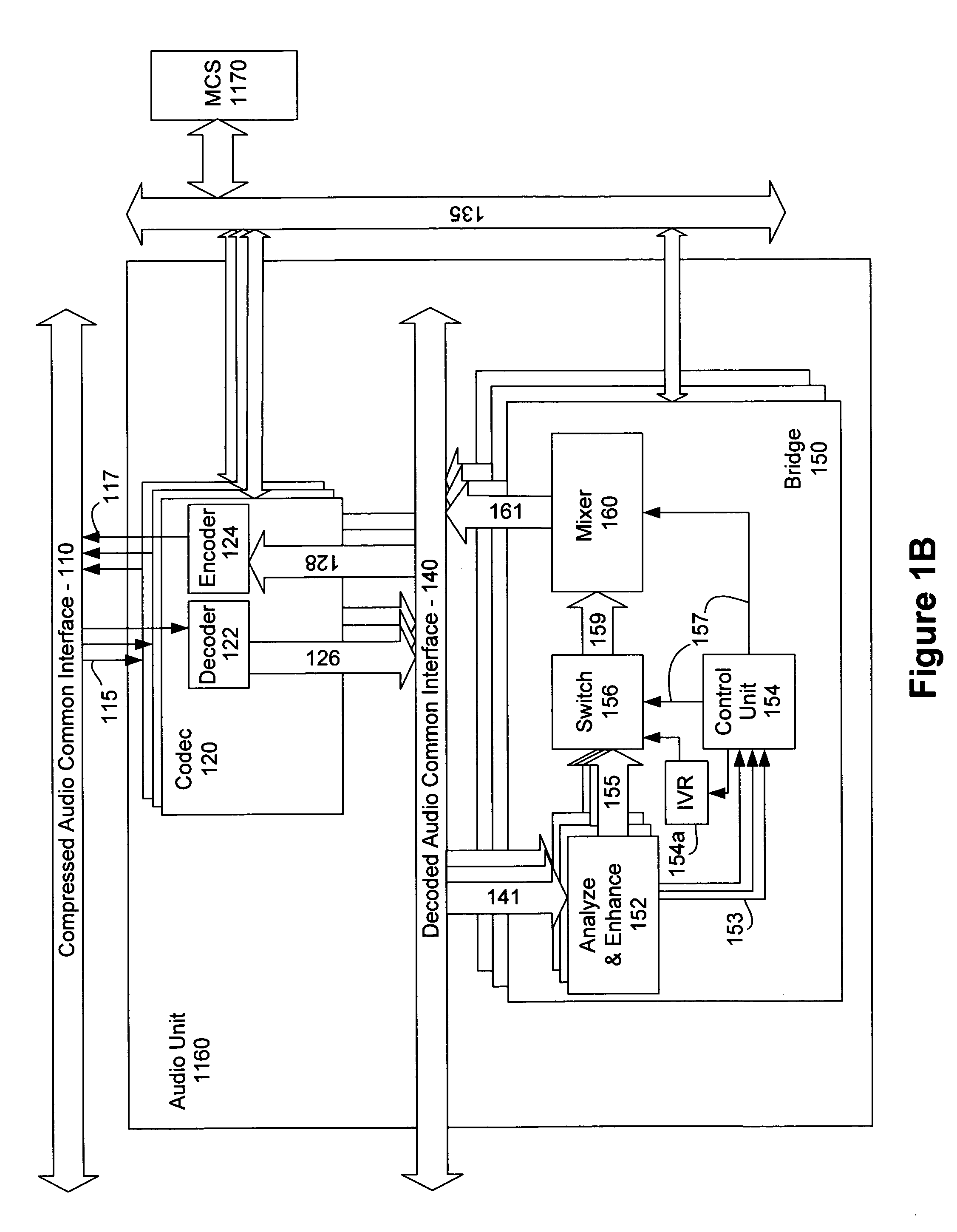
InactiveUS6839416B1Improve quality and efficiencySpecial service for subscribersExisting connections interruptionConference managementHuman–computer interaction
A conferencing system includes a number of devices that can participate in an audio conference using a conference bridge. Responding to a human or automated conference administrator, the bridge determines that audio content of media from a particular device is undesirable, and disables media from the particular device. If appropriate, the device receives prompts to rejoin the conference at a later time.
Owner:CISCO TECH INC
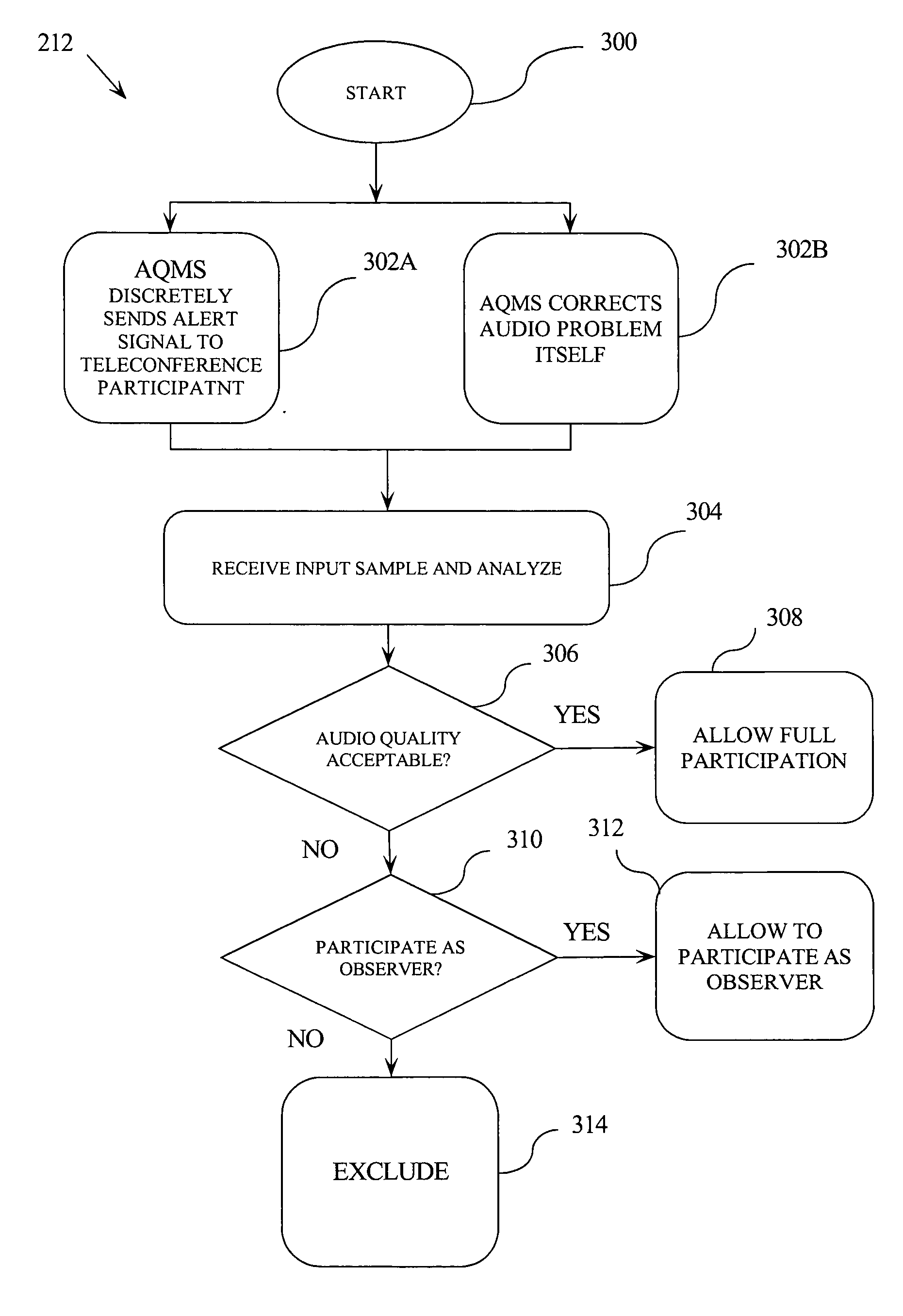
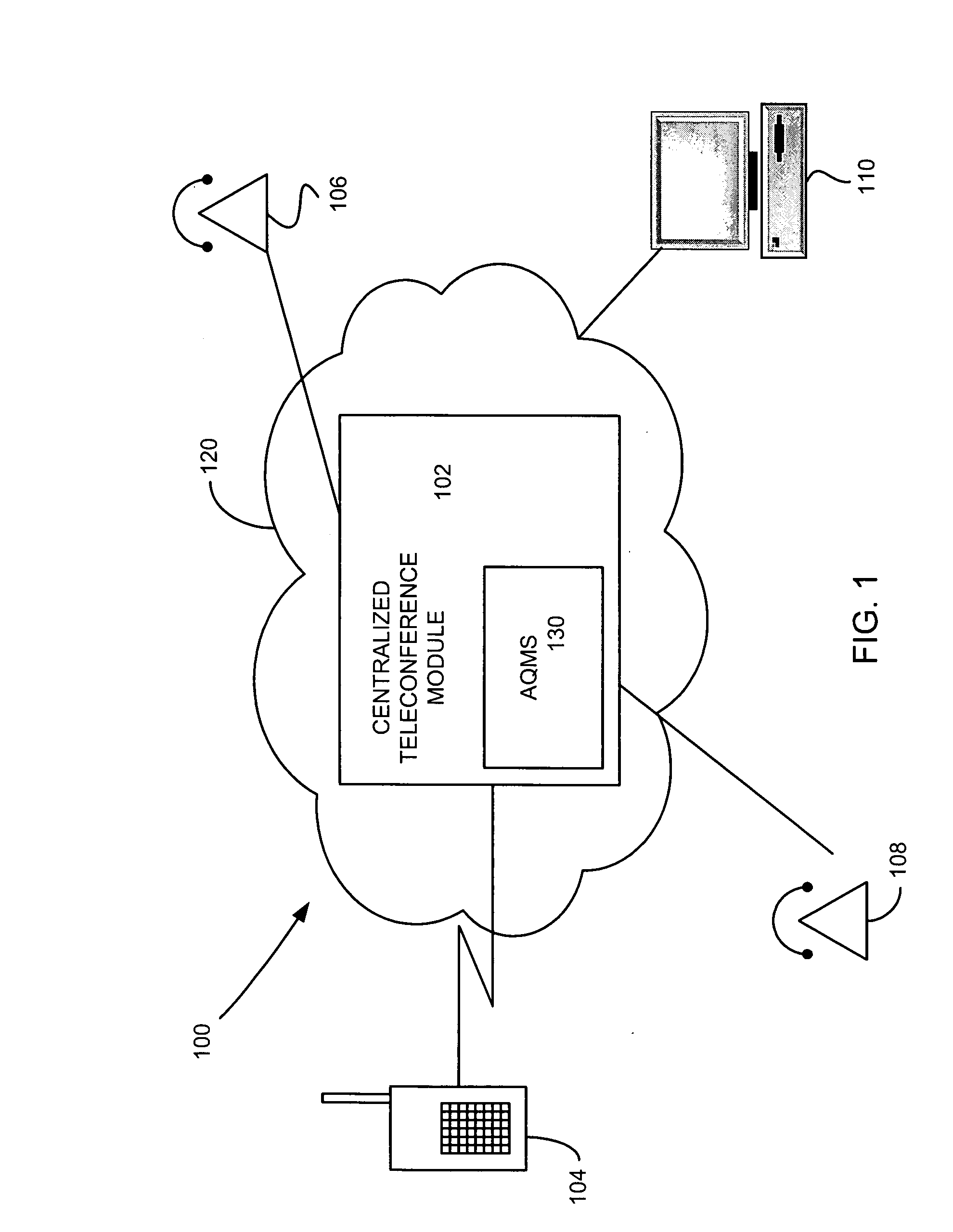
Teleconference audio quality monitoring
InactiveUS20060023061A1Two-way loud-speaking telephone systemsGain controlTeleconferenceSpeech sound
A method for adjusting voice levels of participants in a teleconference that involves a plurality of teleconference stations is disclosed. The method includes receiving a first audio input from one of the teleconference stations. The method further includes electronically ascertaining whether a volume of the first audio input is acceptable. If the volume of the first audio input is unacceptable, the method includes indicating to one of the participants via the one of the teleconference stations that the volume of the first audio input is unacceptable. Such indicating is performed in a manner that is substantially transparent to at least another of the participants.
Owner:HEWLETT PACKARD DEV CO LP
Adapter for secure VoIP communications
ActiveUS20050144445A1Interconnection arrangementsUnauthorised/fraudulent call preventionSecure communicationEngineering
Method and adapter apparatus for securing information exchanged between a calling party and a called party. A first signal is generated, which is representative of an analog probe signal. The first signal is released towards the called party. Responsive to receipt from the called party of a second signal responsive to the analog probe signal and indicative of an ability of the called party to participate in a secure information exchange, negotiations are performed with the called party to securely exchange subsequent information with the called party. In this way, the adapter apparatus can securely exchange information without prior knowledge of whether the called party is secure-capable or secure-incapable and without prior knowledge of whether the called party is a POTS phone or a packet-switched device.
Owner:BCE
Inmate management and call processing systems and methods
InactiveUS8340260B1Large capacityIncrease speedSpecial service provision for substationMultiplex system selection arrangementsThird partyHandling system
Disclosed are systems and methods that provide centralized or nodal inmate management and telephone call processing capabilities to controlled environment facilities. An inmate management and call processing system serves a plurality of facilities and includes an inmate information database. The database is shared across the facilities and contains inmate records that may be accessed and modified by each facility as the inmate is transferred among those facilities. Each inmate record may include, among other information, contact information of third parties whom may be notified of the inmate's arrest and / or subsequent transfers of the inmate to different facilities. The inmate management and telephone call processing system may use third party contact information to establish accounts used to charge calls or transactions made by an inmate while residing at the facility. Some systems may also provide call processing, video conferencing, e-mail, voicemail, and / or videomail applications, and the like to the facilities.
Owner:SECURUS TECH LLC
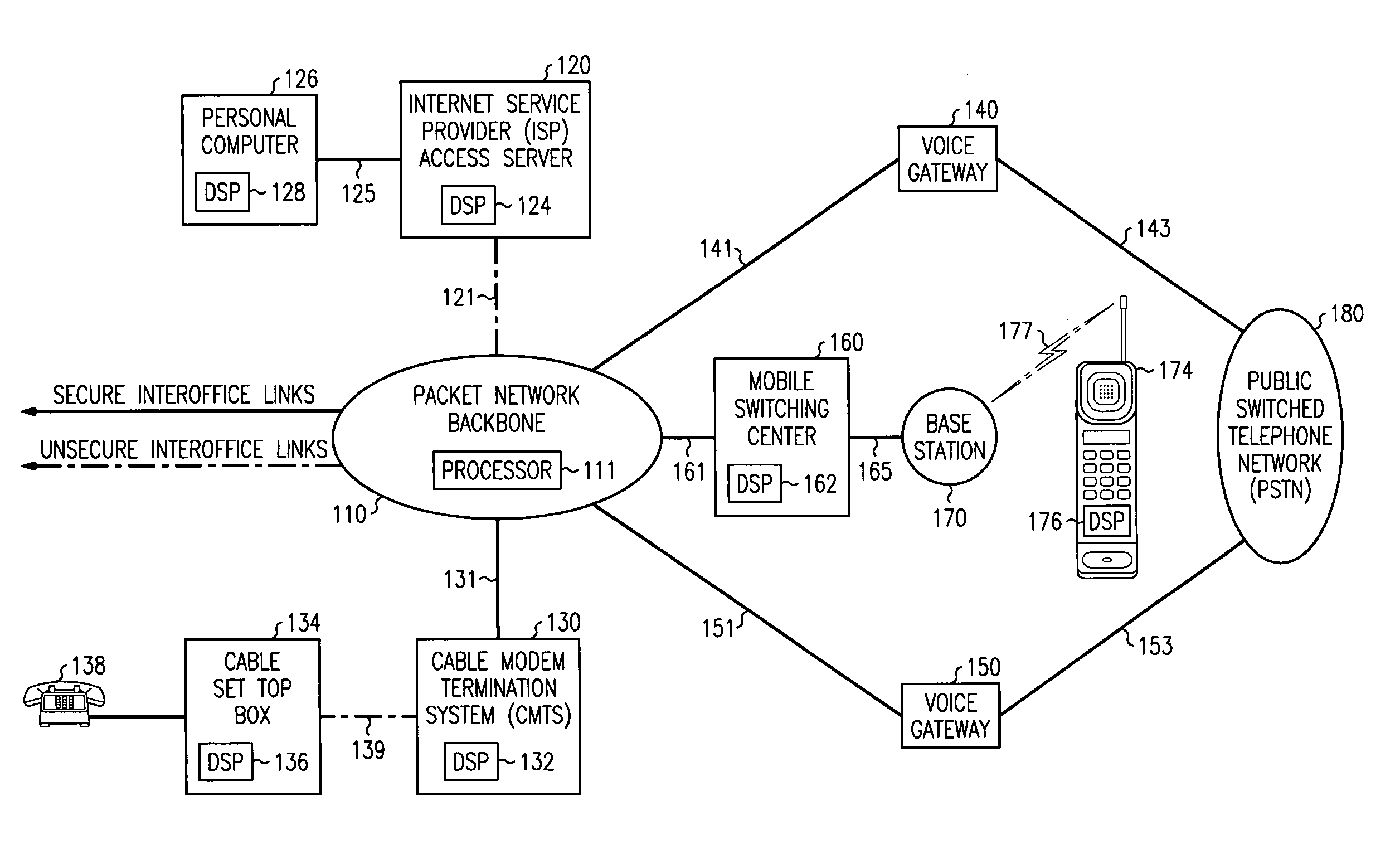
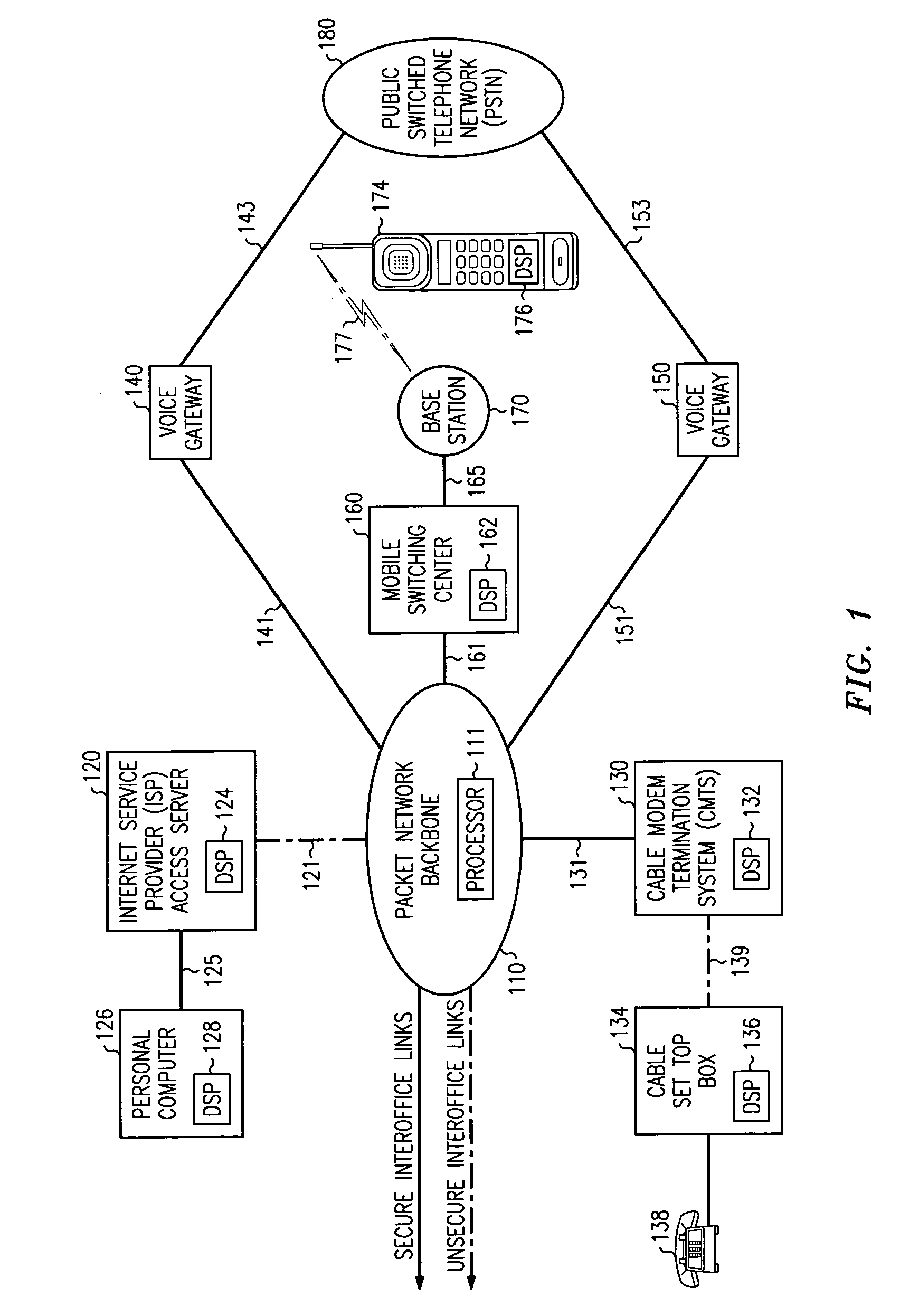
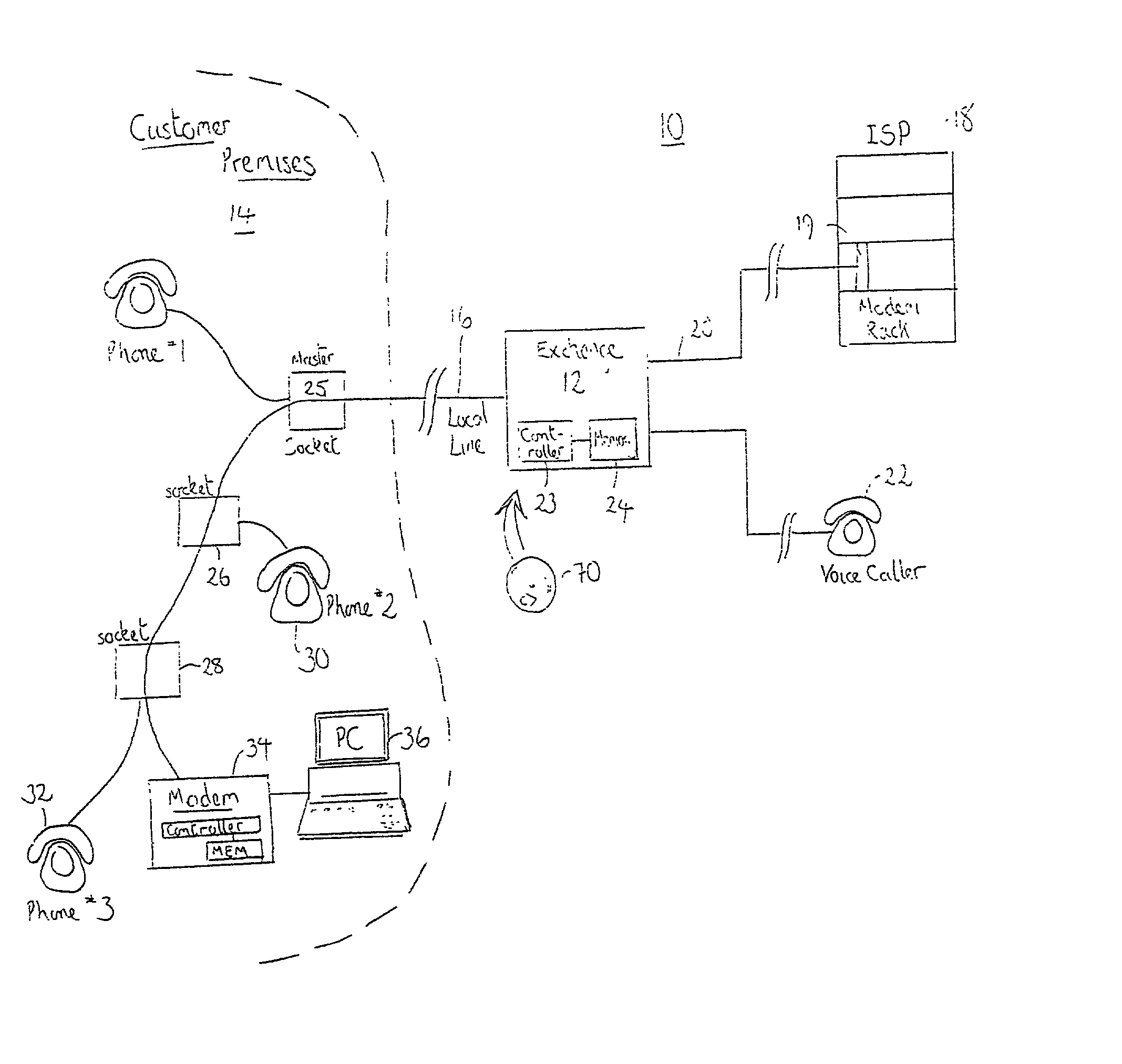
Modem and system with call waiting switching facilities and method of supporting customer access to a service provider
InactiveUS20020176558A1Avoid spreadingRaise the possibilityTelephone data network interconnectionsSpecial service for subscribersData connectionModem device
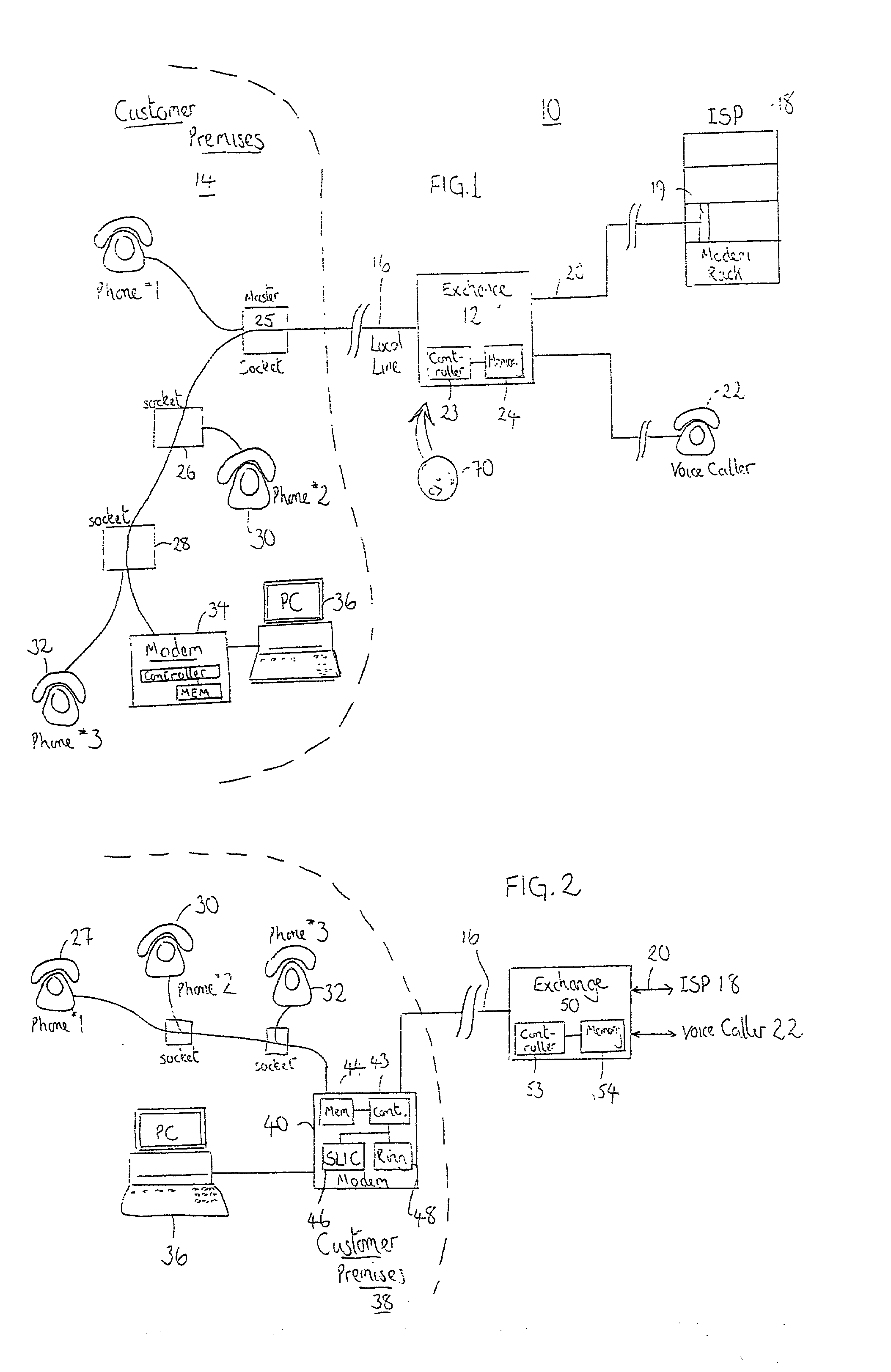
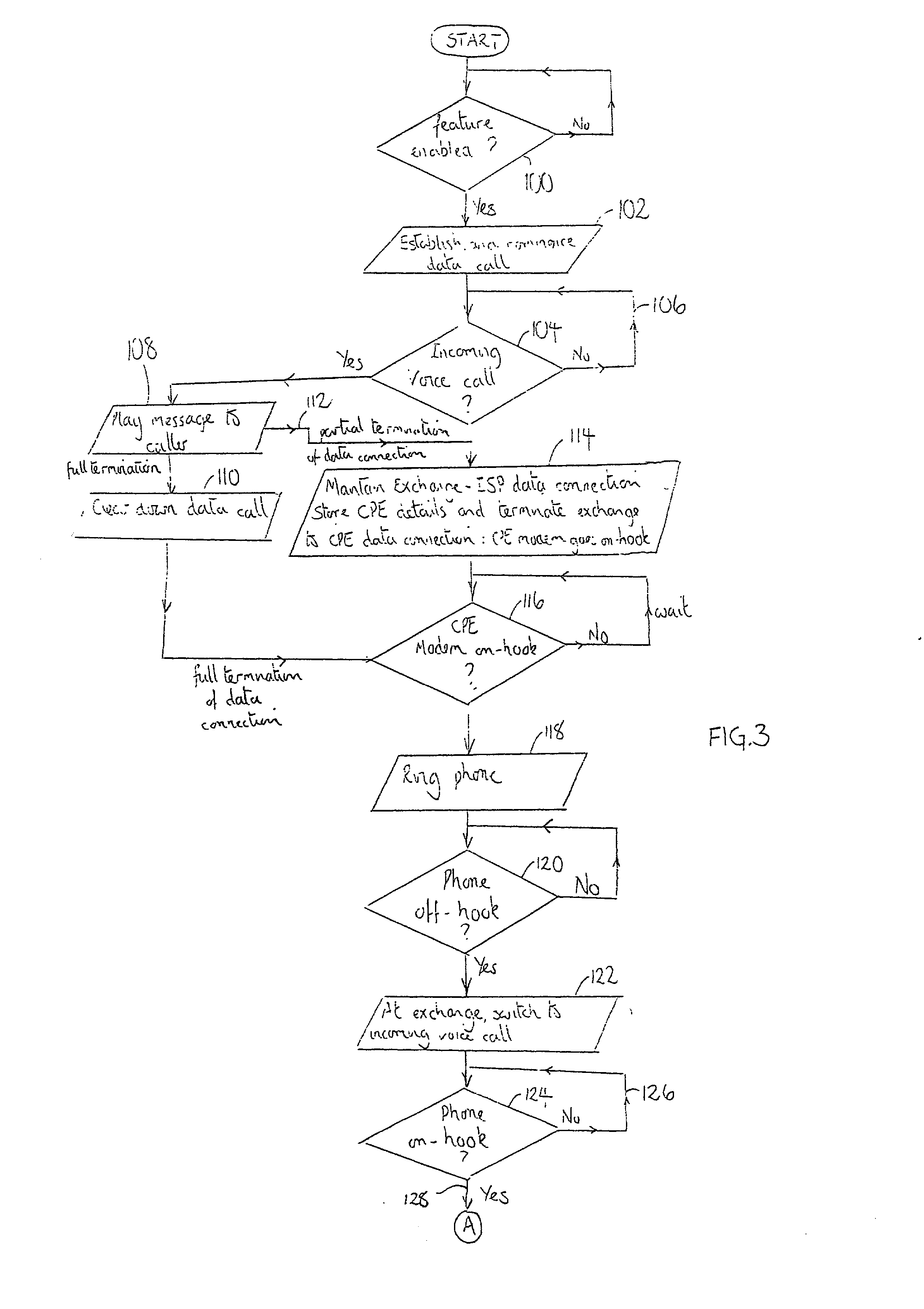
A modem (34, 40) at a customer premises (14, 38) and a switch at an exchange (12, 50) are modified to allow a data session (102, 202) supported on a dedicated wireline communication resource (16) to be optionally terminated (110), but preferably suspended (114, 218), upon detection of a subsequently placed voice call (104, 204) on the dedicated wireline communication resource (16). Before termination of a data session, a user either selects a termination option or is provided with an in-call option to terminate the data session, with the voice call then switched (122) to the dedicated wireline communication resource (16). The data session is therefore cleared down rather than lost through connection corruption. Alternatively, the modem (34, 40) and the exchange (50) interact to silence modem transmissions therebetween, whilst retaining a data connection (20) between the exchange (12, 50) and an end-point data service provider (ISP, 18). Assuming acceptance (128, 228) of the voice call and its subsequent termination, the modem (34, 40) and the exchange (12, 50) again interact (134, 236) to re-establish (136, 238) the data session across the dedicated wireline communication resource (16). Re-training (138, 238) of modems involved in the data session is required, but suspension of a sector in an end-to-end physical link avoids re-dialing and any associated connection costs.
Owner:NORTEL NETWORKS LTD
Method and apparatus for managing subscription-type messages
ActiveUS7224778B2Automatic call-answering/message-recording/conversation-recordingSupervisory/monitoring/testing arrangementsThird partyComputer network
Owner:META PLATFORMS INC
System and method for call routing and enabling interaction between callers with calls positioned in a queue
InactiveUS7426268B2Interconnection arrangementsSpecial service for subscribersTelecommunicationsCall routing
According to at least one embodiment of the present invention, a method and apparatus are provided for enabling a caller on hold to listen to one or more ongoing calls. The method includes receiving an incoming call, determining a subject category and at least one keyword associated with the incoming call, and determining an ongoing call based on the subject category and the at least one keyword. In one embodiment, keywords associated with calls may be stored in a database.
Owner:WALKER DIGITAL
Enhanced call feature service
InactiveUS7164762B2Telephone data network interconnectionsSpecial service for subscribersCall forwarding
The present invention provides a system and method for managing calls for a subscriber, including accessing a calling plan while the subscriber is in an existing active call with at least one other party. The call is placed or received by the subscriber at a first device. At least one service feature of the calling plan is invoked during the active call. This service feature includes an add callers feature for adding at least one additional party to the existing active call between the subscriber and the other party. The service feature additionally includes a transfer devices feature for transferring the existing active call to at least one additional device of the subscriber and hanging up on the first device by the subscriber to confirm the transfer of the call to the additional device.
Owner:INTELLECTUAL DISCOVERY CO LTD
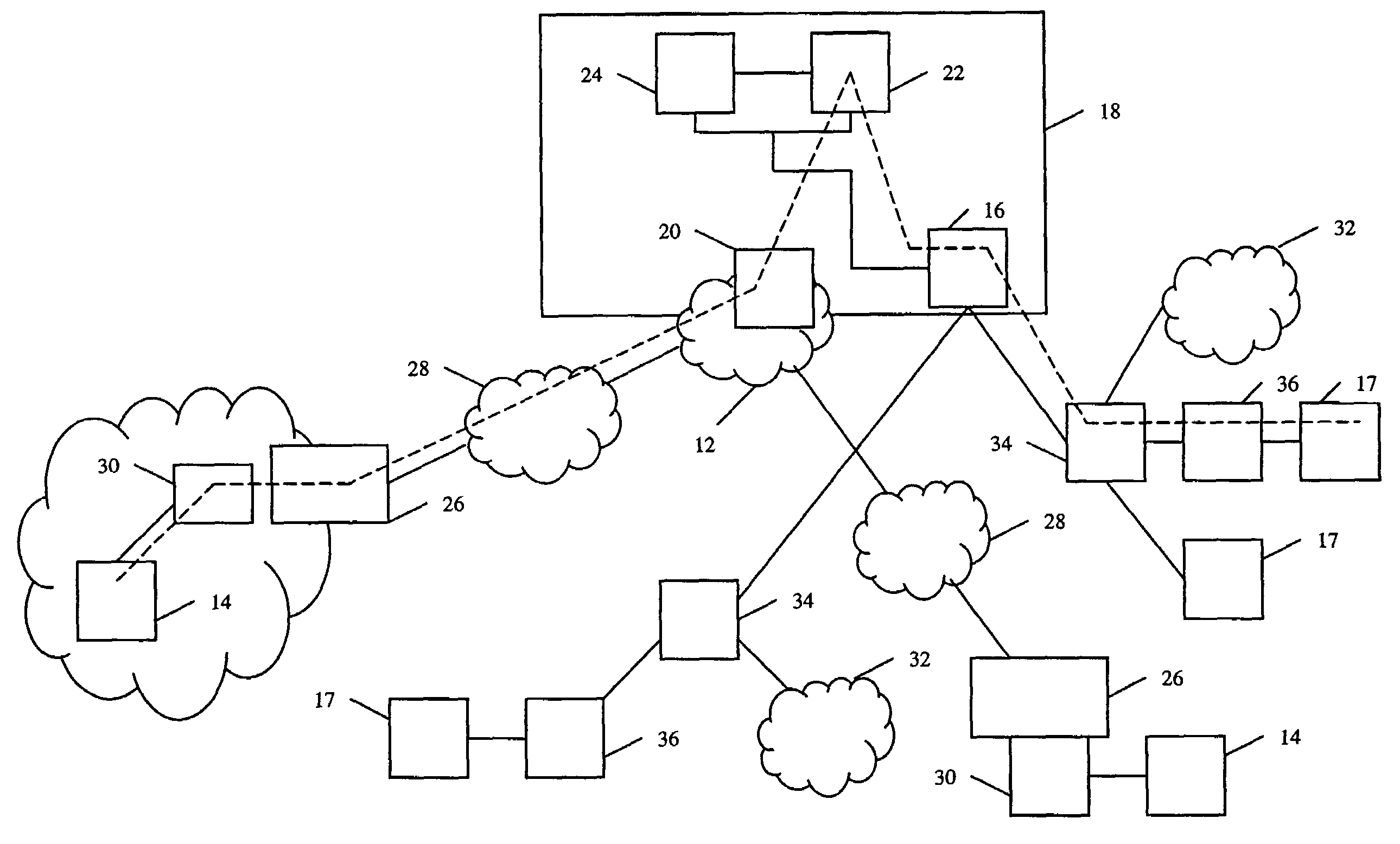
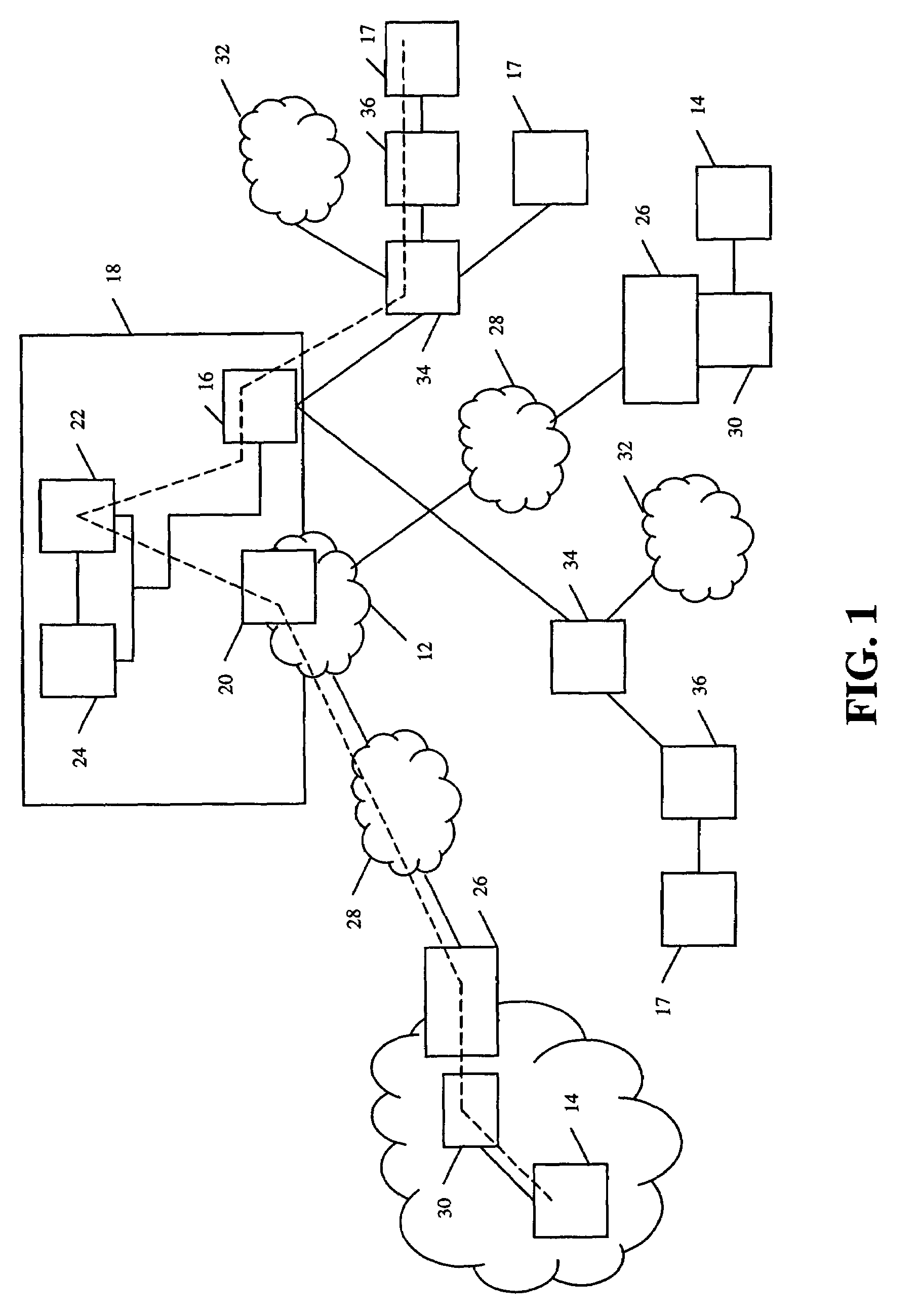
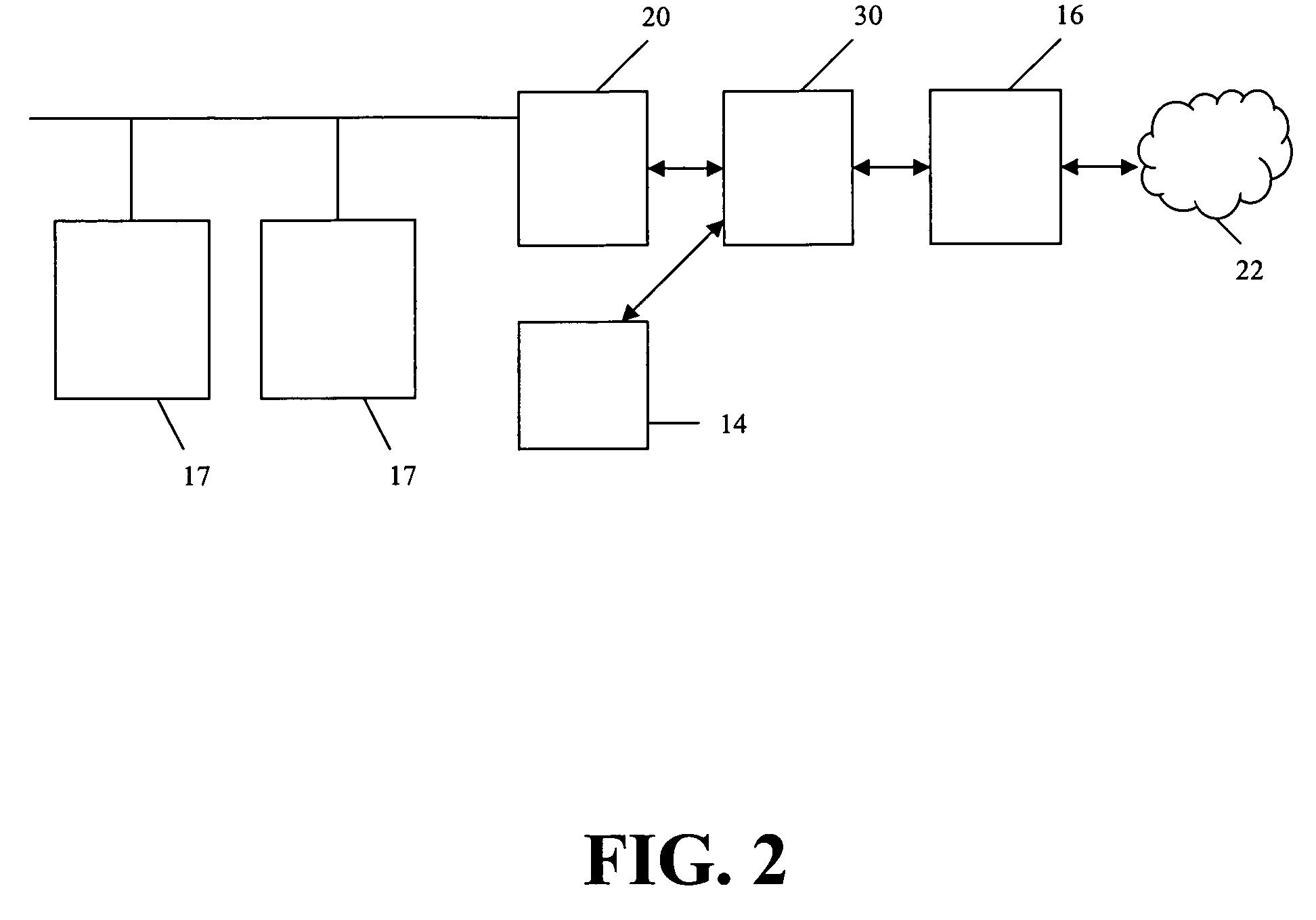
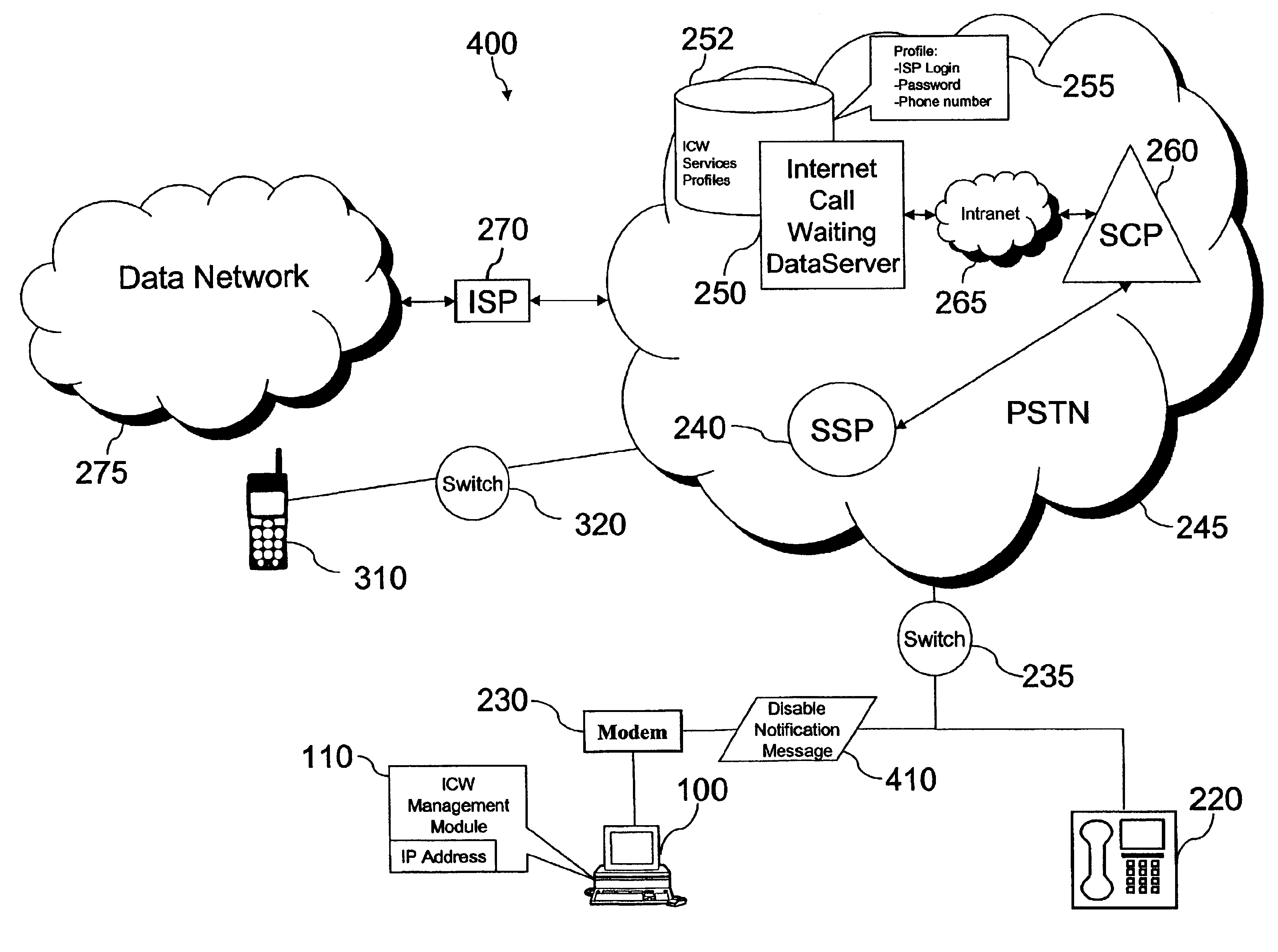
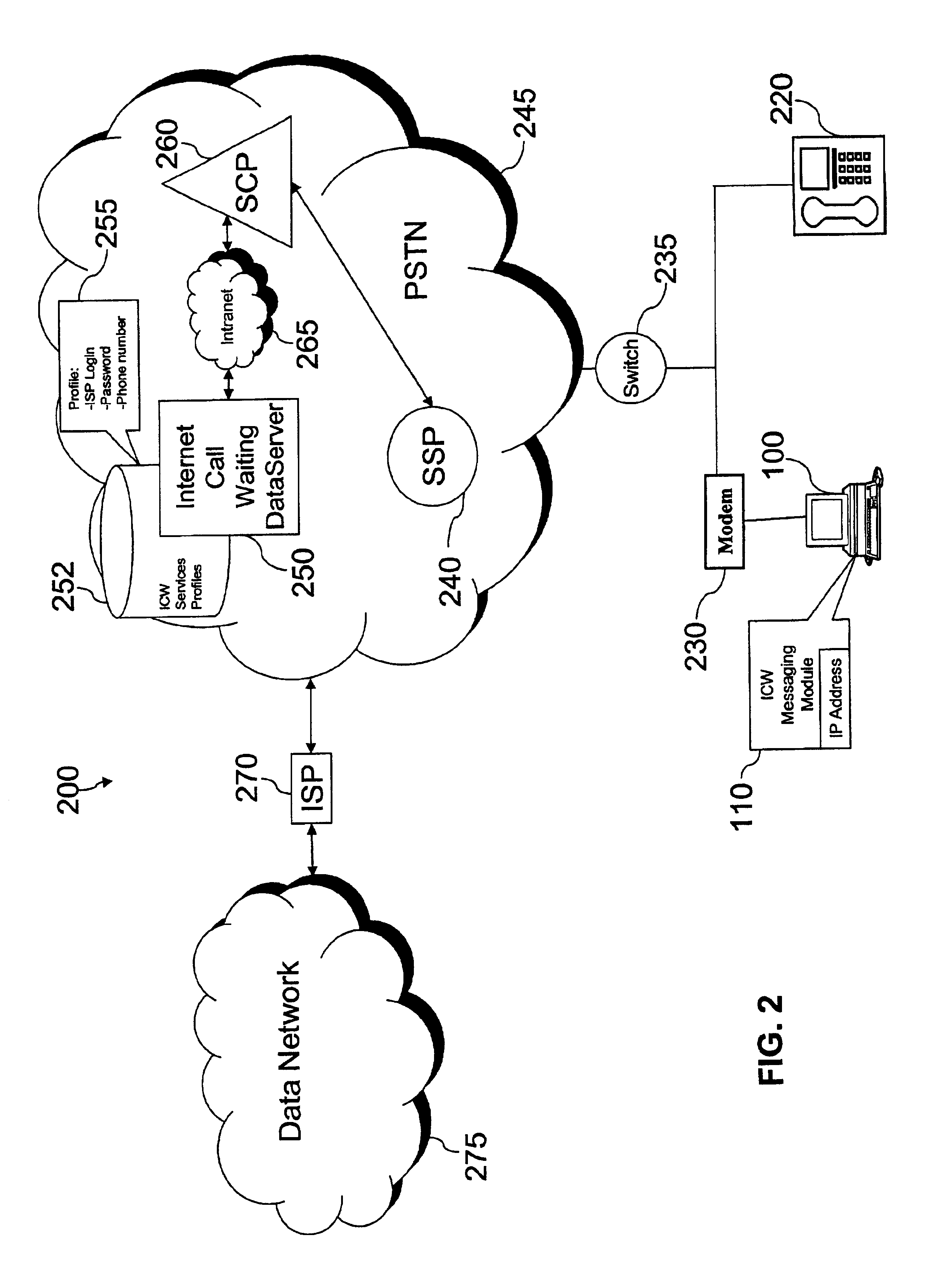
Caller control of internet call waiting
InactiveUS6931117B2Special service for subscribersExisting connections interruptionData connectionTelecommunications network
Systems, methods, and apparatuses are disclosed for providing Caller Control of Internet Call Waiting (ICW) Services. In an embodiment, a calling party places an incoming call to a called telephone number having an active ICW session and data connection. The calling party may enter an authorized code that authorizes interruption or disabling of ICW and the data connection. The interrupt code entered by the calling party is received in a telecommunications network, such as, for example the Public Switched Telephone Network (PSTN) or a mobile switching network. The telecommunications network verifies that the interrupt code to enable caller control, and, thereafter, disables or interrupts the ICW session and data connection to connect the incoming call.
Owner:AT&T INTPROP I L P +1
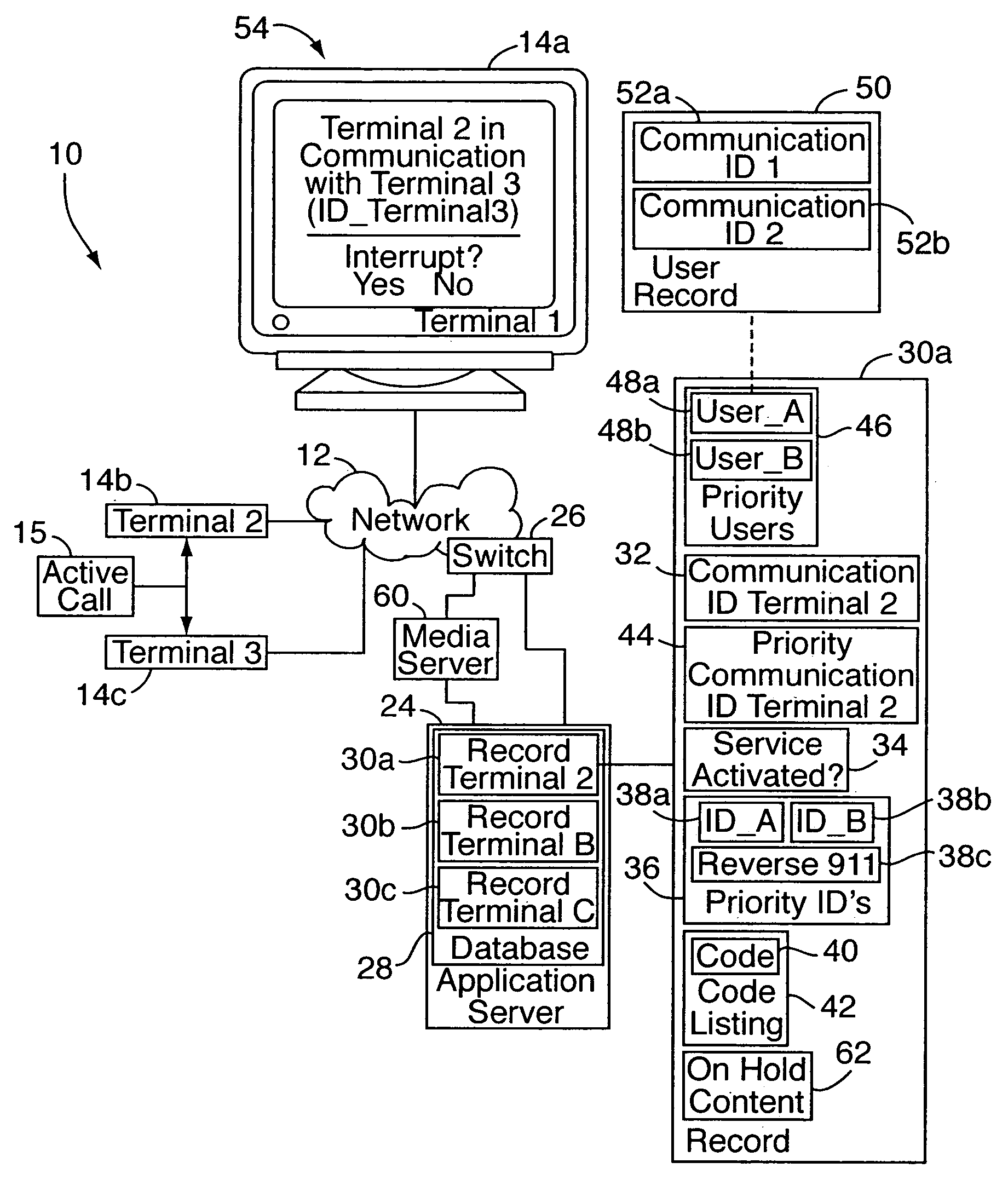
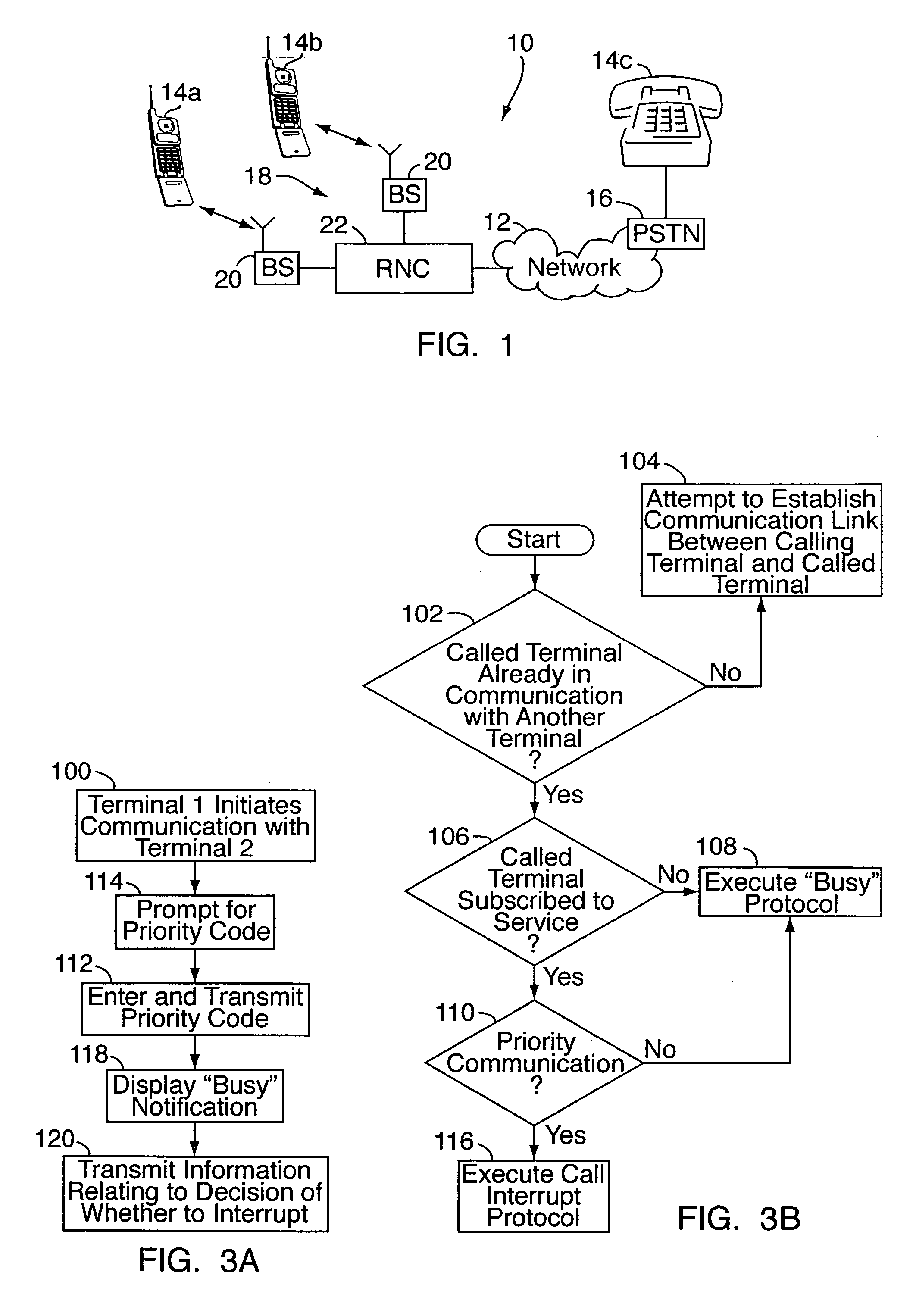
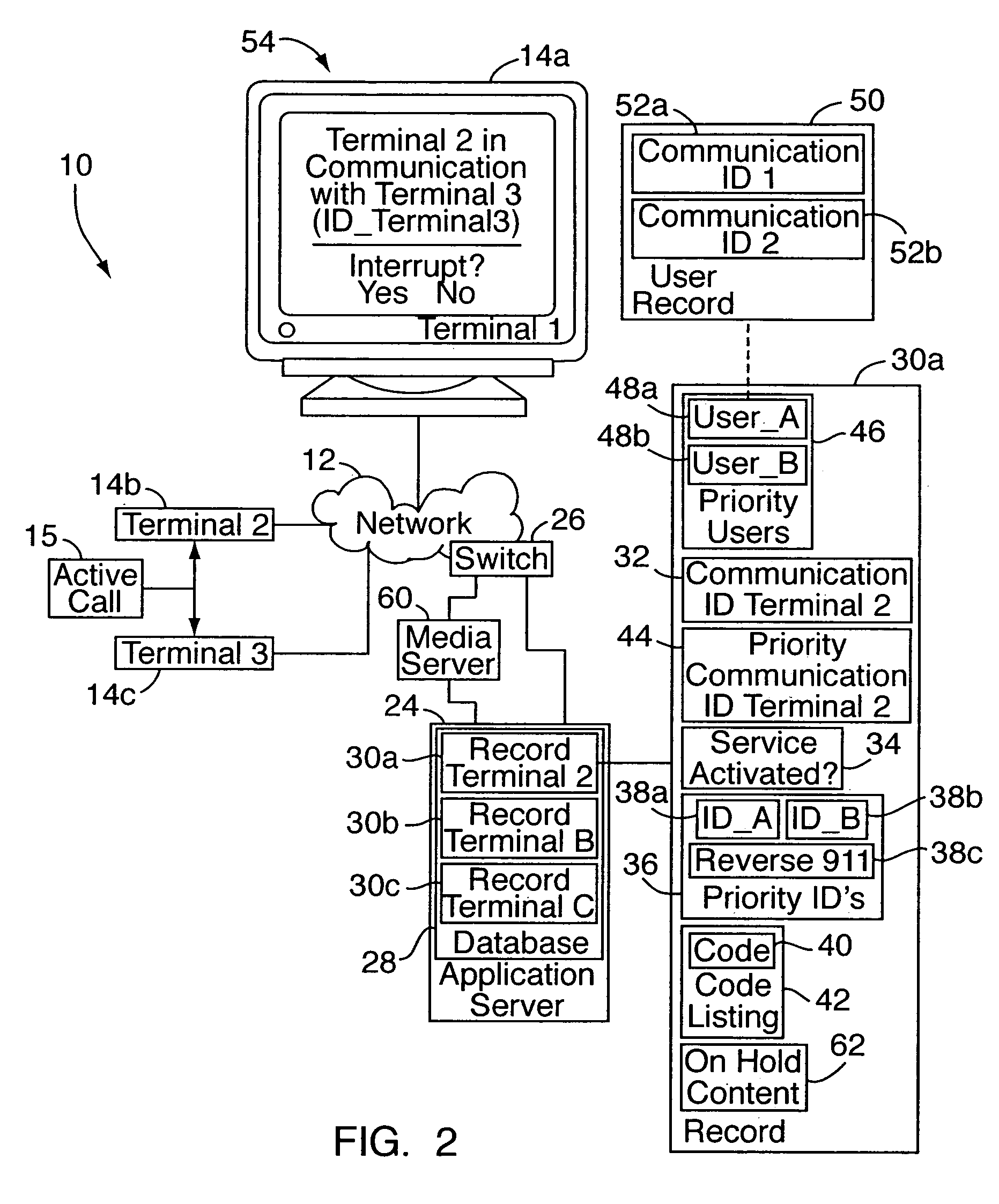
Call priority management system for communication network
InactiveUS20080037753A1Special service for subscribersCommmunication supplementary servicesTelecommunications linkTelecommunications
A call priority management system is implemented on or as part of one or more communication networks, for allowing authorized calling parties to control call disposition when the party being called is already on another call. In operation, when a first terminal initiates communication with a second terminal that is already in communication with a third terminal, the system determines if the newly initiated communication is a priority communication. By “priority” communication, it is meant a communication associated with a user and / or terminal having a designated or assigned privilege to interrupt ongoing communications at the second terminal. If so, the ongoing communication between the second and third terminals is interrupted, and a communication link is established between the first and second terminals. Prior to interruption, the calling party may be informed that the second / called terminal is already engaged in another call, for optionally interrupting the ongoing call.
Owner:LUCENT TECH INC
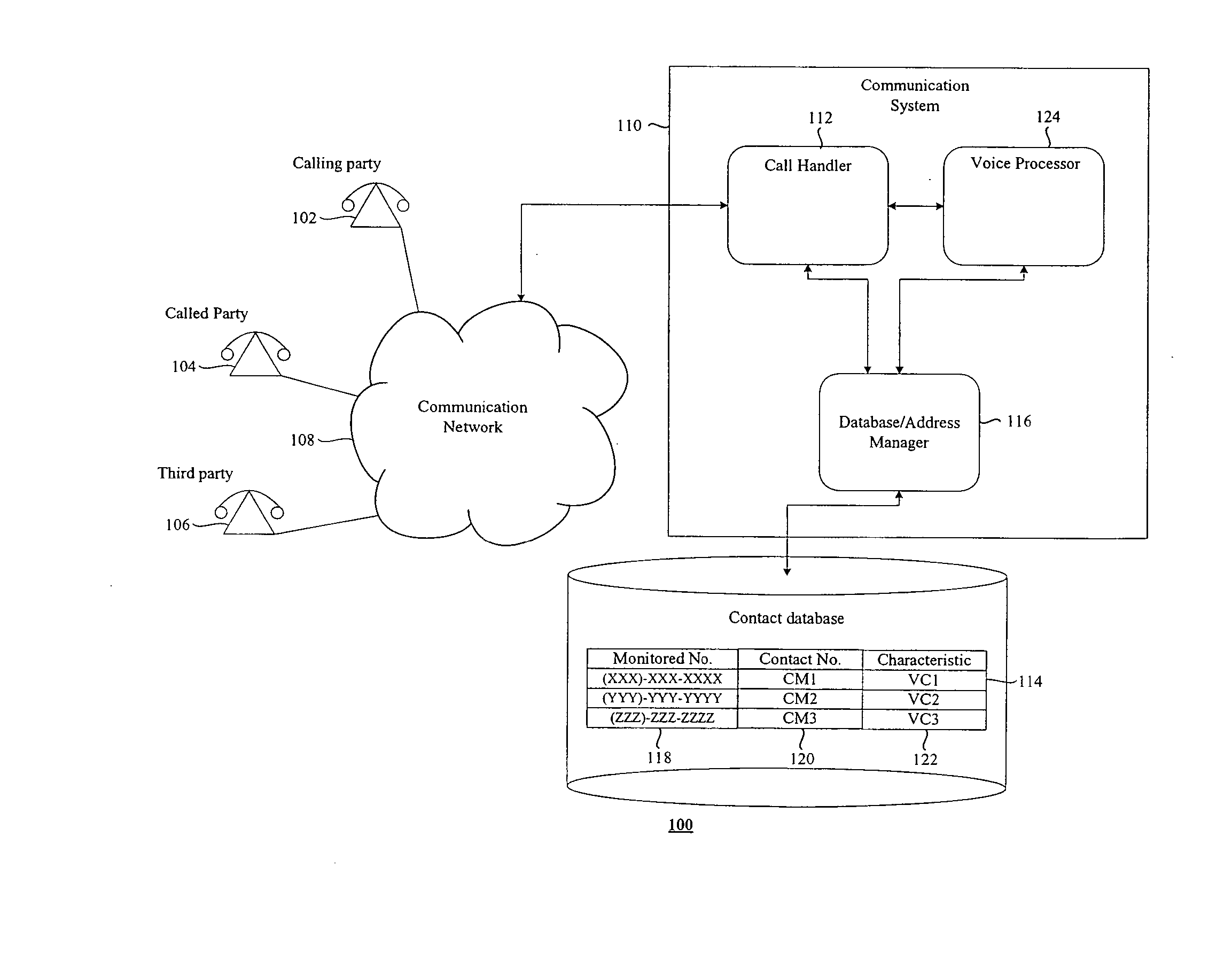
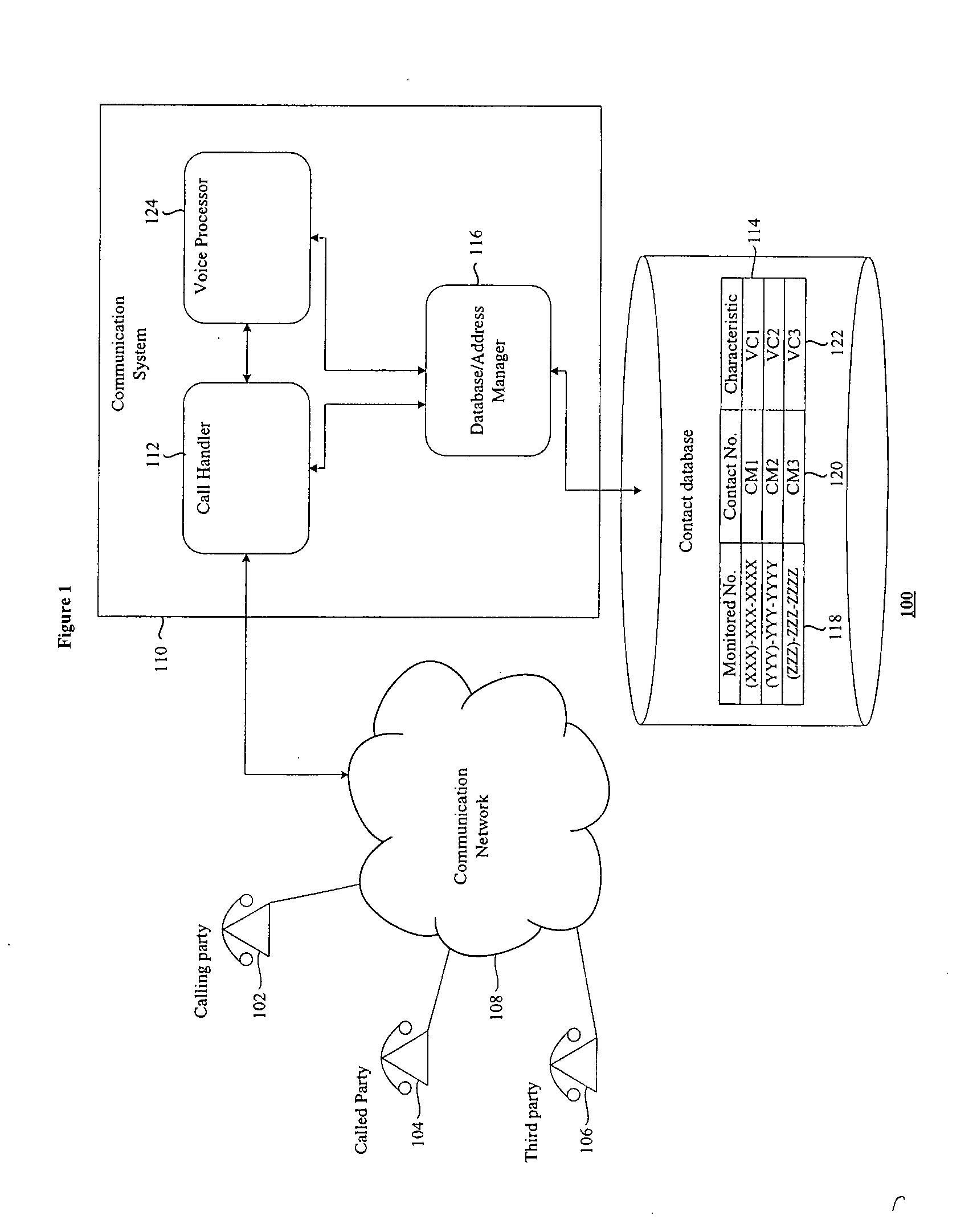
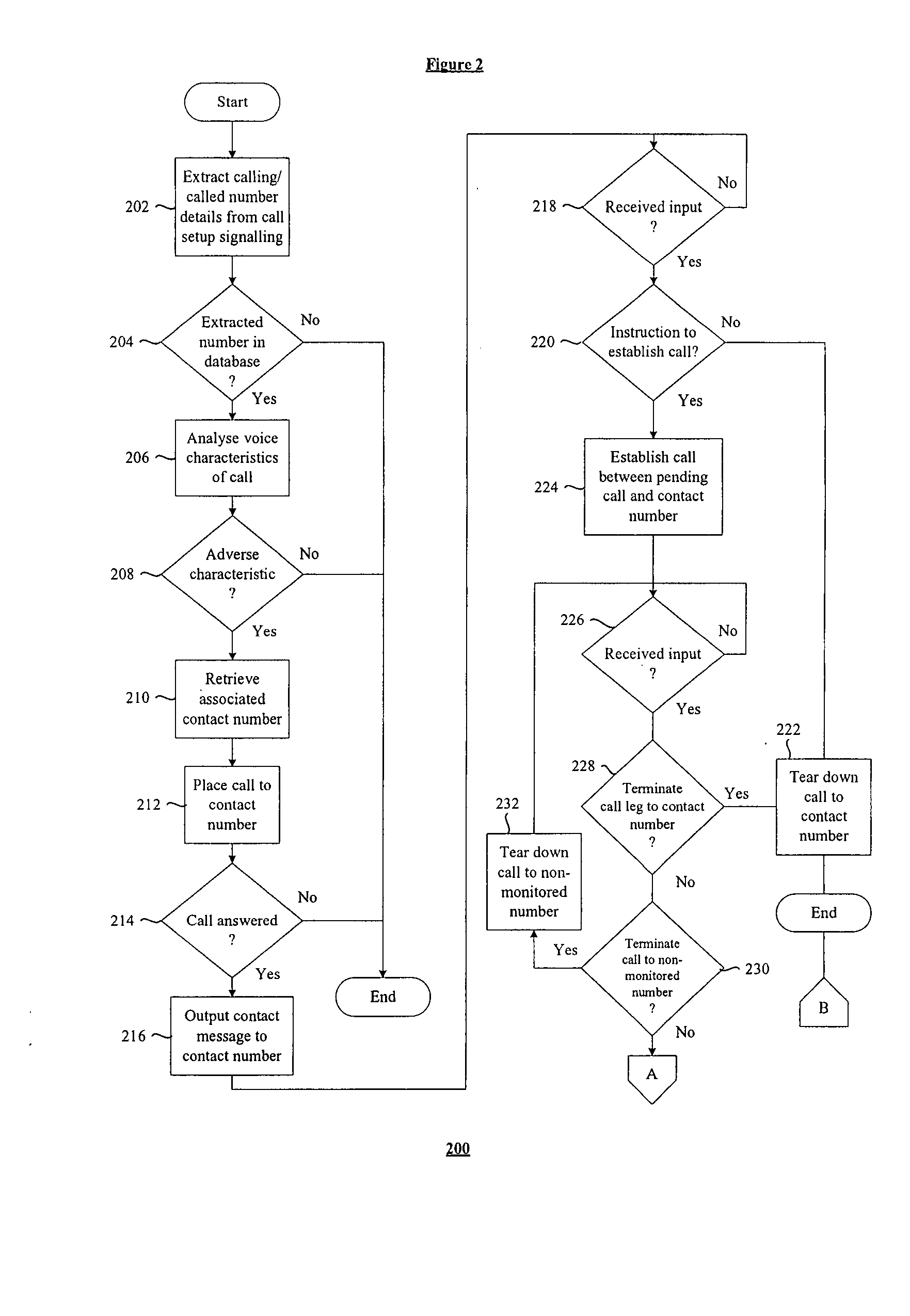
Communication system and method
ActiveUS20070286389A1Automatic call-answering/message-recording/conversation-recordingSpecial service for subscribersThird partyCommunications system
According to one embodiment of the present invention there is provided a communication method comprising the steps of making a determination in respect of at least initiating a first call between first and second communication devices having first and second contact numbers respectively; said making the determination comprising identifying at least one of the first and second contact numbers associated with said initiating, accessing a database comprising at least a first monitored contact number and at least one associated third party number corresponding to a third communication device, determining whether or not at least one of a first contact number and the second contact number match the first monitored contact number; and establishing, in response to the determination, a third party call to the third communication device.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
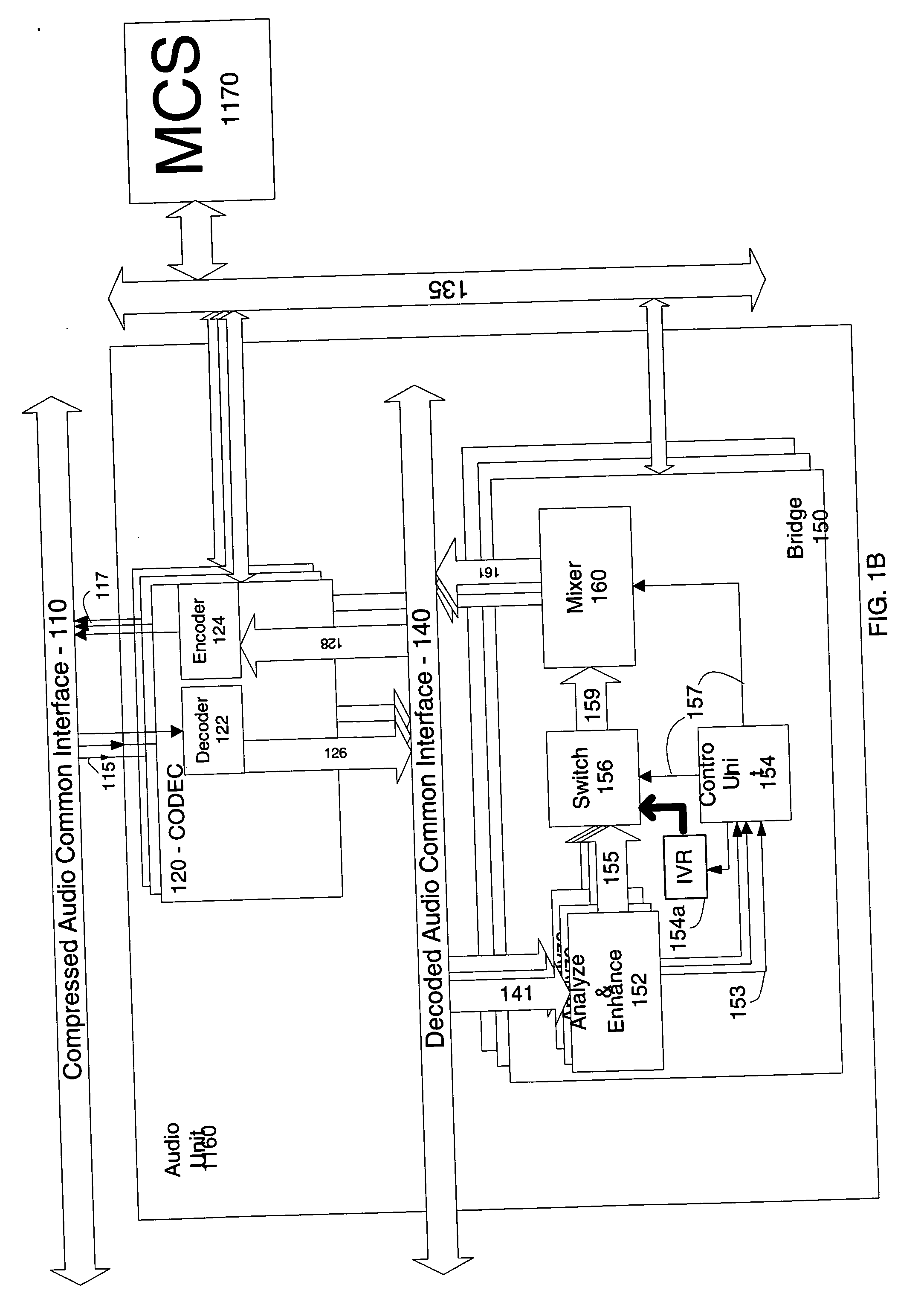
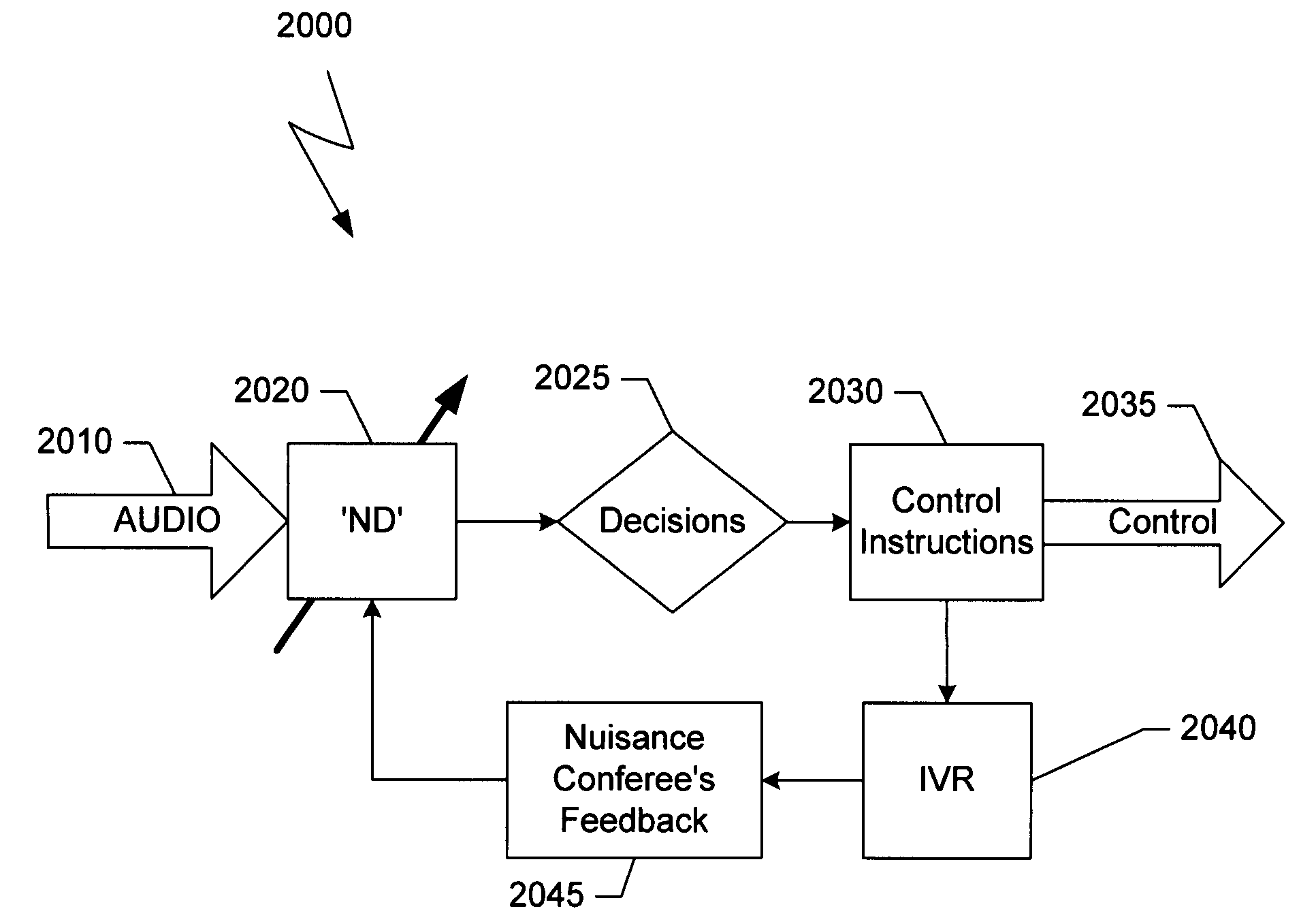
Method and apparatus for improving nuisance signals in audio/video conference
InactiveUS20050069114A1Quality improvementOptimizationSpeech amplifier applicationsSpecial service for subscribersPush-to-talkSpeech sound
System to allow a conferee that has been defined as a source of nuisance to respond to an automatic decision of an MCU. If the conferee places the conference on ‘HOLD’ with hold music, the ND may identify this as a nuisance connection and send this indication to a control unit in the MCU. The control unit may mute the signal coming from this conferee and may place an Interactive Voice Response (IVR) message to the conferee. A message may inform the conferee that he has been muted and request to press a touch tone key, for instance ‘1’, if he returned from ‘HOLD,’ to press ‘3’ if using a noisy line / environment, or press ‘5’ to disable the ND algorithm. If a response is not received, the message may continue for a certain period or for the rest of the conference. If one of those keys has been pushed the system may act as follows. If the key is ‘1’ an embodiment cancels the mute situation and enables the conferee to be heard. If the key is ‘3’ the embodiment may reduce the sensitivity of the ND algorithm. If the new level is above a defined tolerance the embodiment may instruct the conferee that he is too noisy and not add the conferee's audio to the conference. If the key is ‘5’ the embodiment may disable the ND algorithm and connect the nuisance conferee without condition. Other embodiments may place a noisy conferee in push to talk (PTT) operation.
Owner:POLYCOM INC
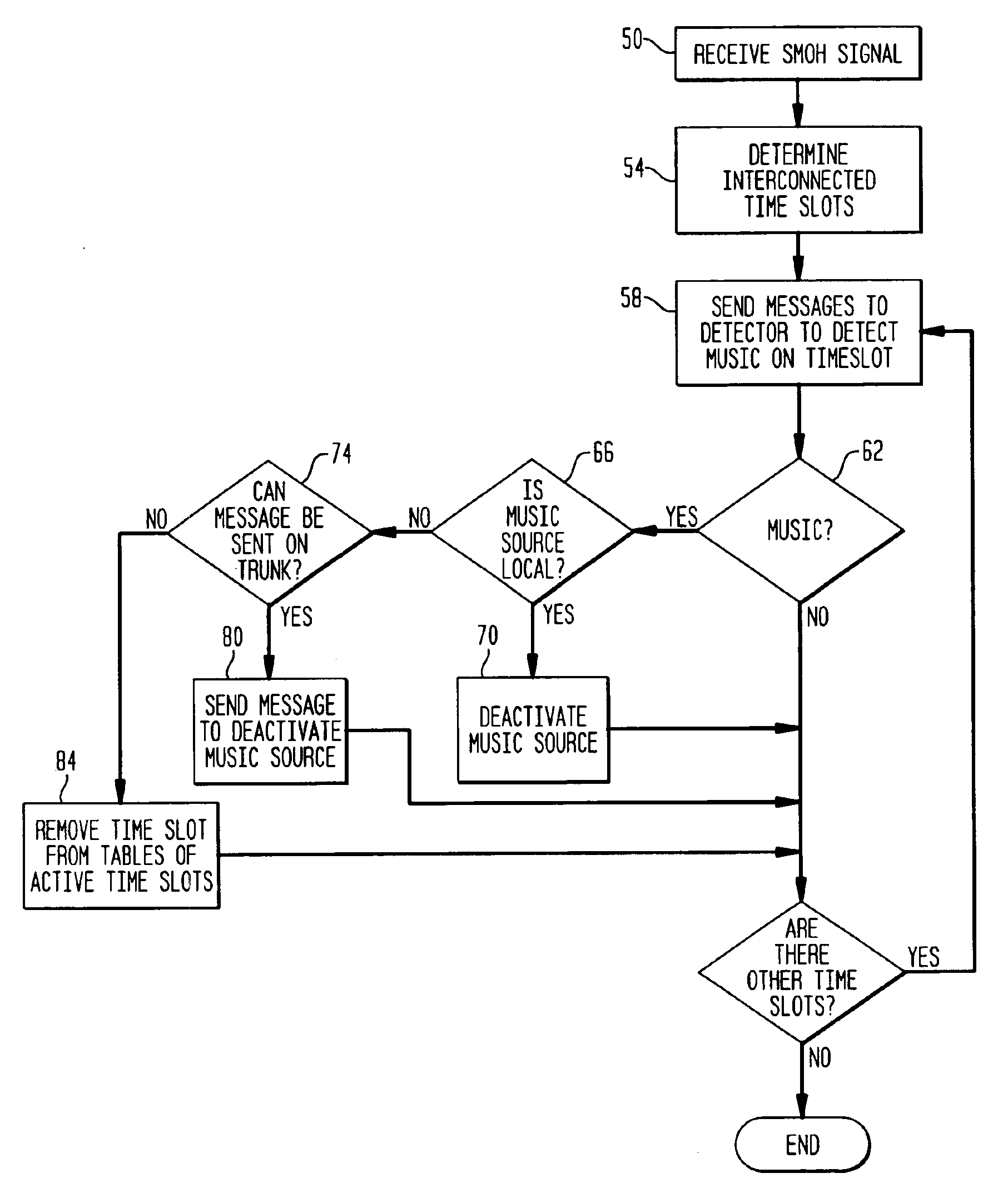
Method and apparatus for suppressing music on hold
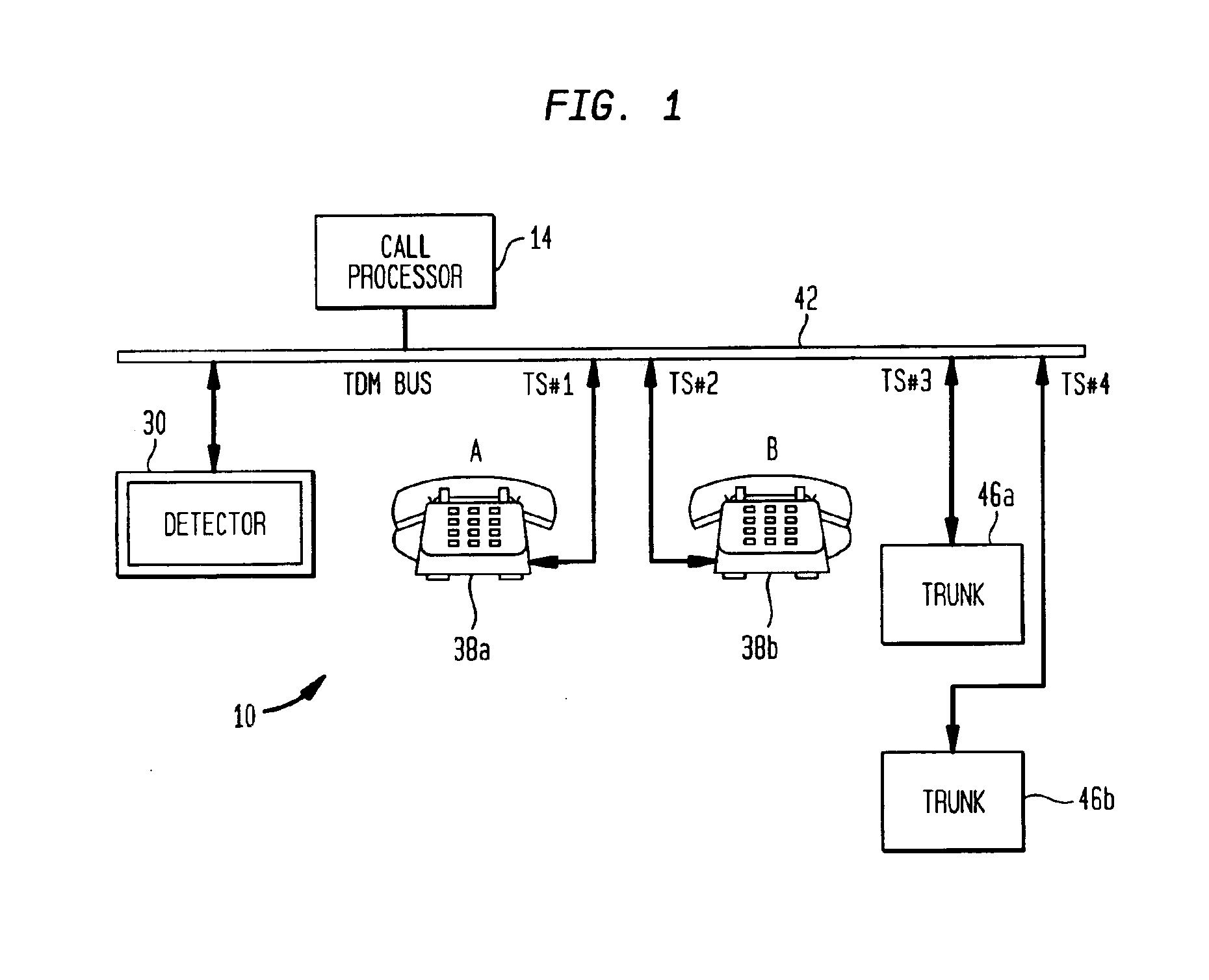
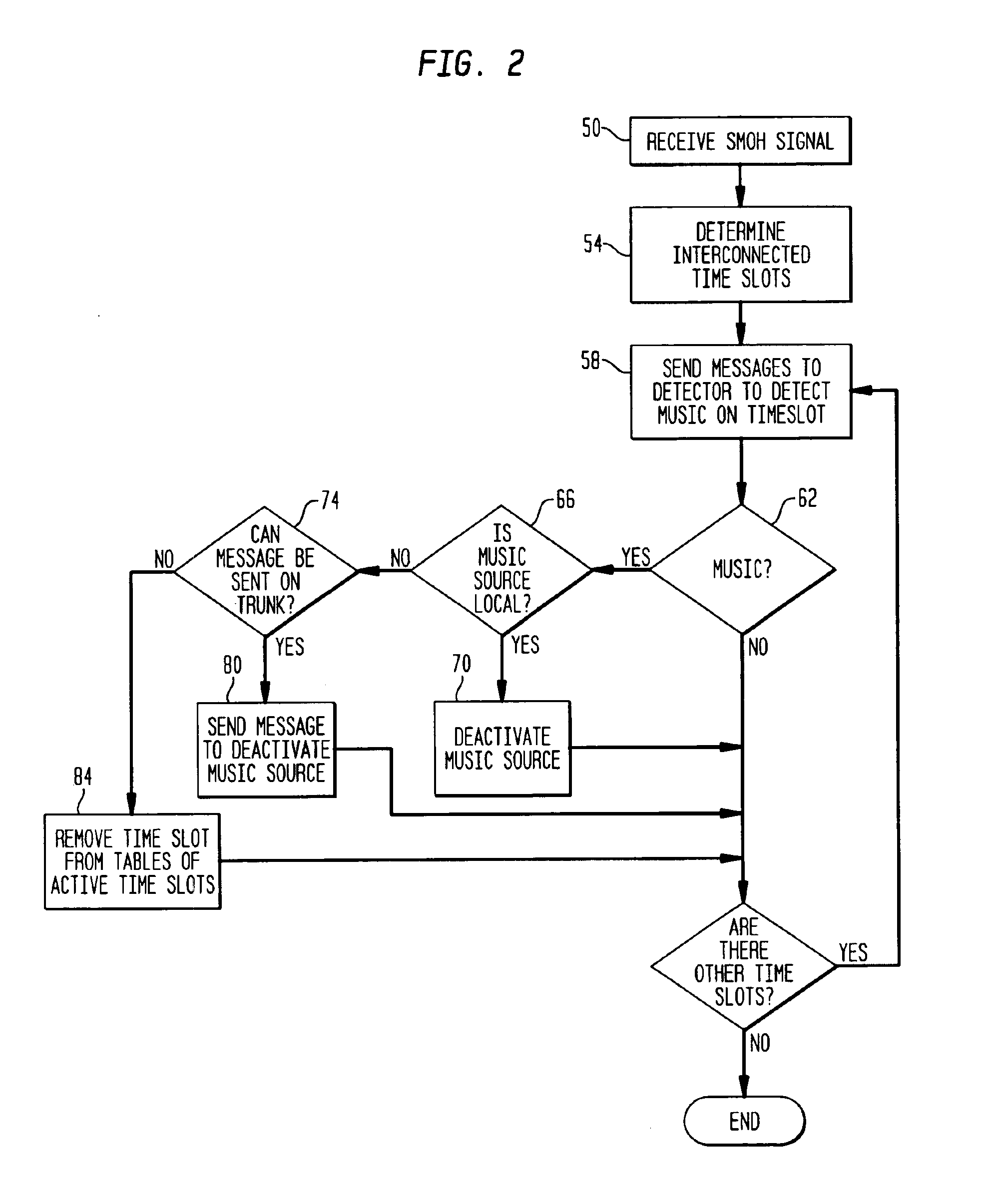
InactiveUS6870807B1Reduce the amplitudeAdvancement over the artMultiplex system selection arrangementsSpecial service provision for substationSound sourcesEngineering
The subject invention is directed to a method and system for removing music or other unwanted noise from a conference call particularly when the music or other unwanted noise is not directly under the control of the telecommunication equipment the user is attached to and using. The method and system detects the unwanted sound, deactivates the sound source or disconnects from the line carrying the sound, monitors the disconnected line for voice energy, and reconnects the line when voice energy is detected. This capability provides the telecommunications equipment user with control over unwanted music sources being provided by equipment located either in the private or public networks.
Owner:AVAYA INC
Method and apparatus for improving nuisance signals in audio/video conference
InactiveUS7269252B2Quality improvementOptimizationSpeech amplifier applicationsSpecial service for subscribersMultipoint control unitAudio frequency
A system to allow a conferee defined as a nuisance source to respond to an automatic nuisance decision of a Multipoint Control Unit is disclosed. For example, a conferee placing a conference on hold may generate on hold music, which may be identified by a nuisance detector. The nuisance detector sends an indication of the nuisance condition to a control unit in the MCU. The control unit mutes the signal coming from this conferee and sends an Interactive Voice Response (IVR) message to the conferee. The message may inform the conferee that he has been muted and requests the conferee for example to press one of a plurality of touch tone keys depending on his situation. For instance, the conferee can select particular keys if he is returning from the hold condition, if he is experiencing a noisy line / environment and needs to reduce the sensitivity of the nuisance detector algorithm, or if he wishes to disable the nuisance detector algorithm.
Owner:POLYCOM INC
Popular searches
Graded-service arrangements Manual exchanges Character and pattern recognition Sensing record carriers Special data processing applications Web data retrieval using information identifiers Co-operative working arrangements Lock-out/secrecy provision Record carriers used with machines Heterocyclic compound active ingredients
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com