Patents
Literature
34 results about "Named parameter" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer programming, named parameters, pass-by-name, or keyword arguments refer to a computer language's support for function calls that clearly state the name of each parameter within the function call.
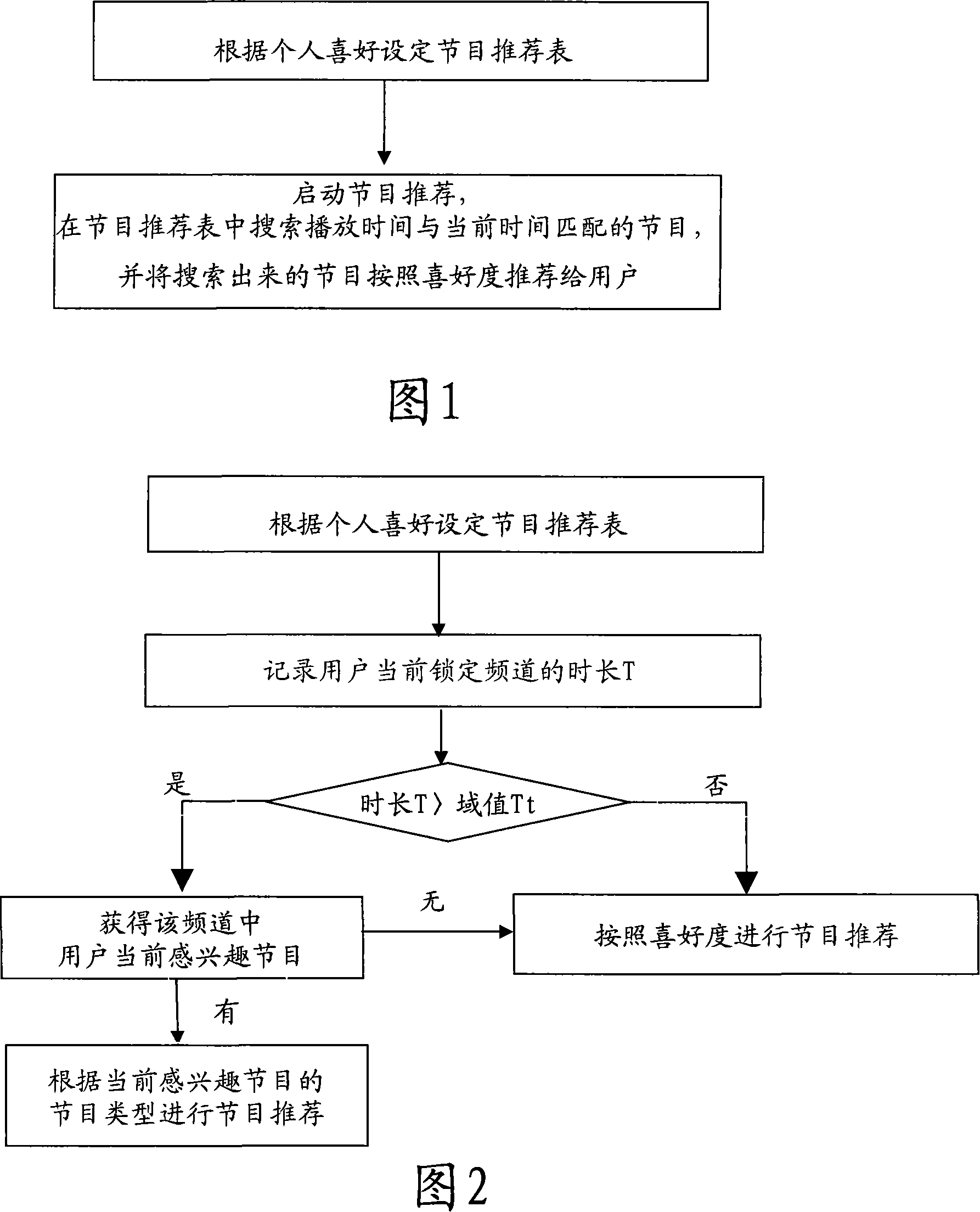
Device and method for recommending TV programs
InactiveCN101094372ARapid positioningPositioning directlyTelevision system detailsColor television detailsChannel parameterStart up
The method comprises: setting up a program recommendation list comprising the program name parameter, channel parameter, play time parameter and loving grade parameter. Said program name parameter is used for saving the program name; the channel parameter is used for saving the play channel corresponding to the relevant program; the play time parameter is used for saving the play time of relevant program; the loving grade parameter is used for saving the loving grade of user for the relevant program; starting up the program recommendation to search the program whose play time matches the current moment program; recommending the matched program to users according to a sequence of loving grade.
Owner:VIMICRO CORP
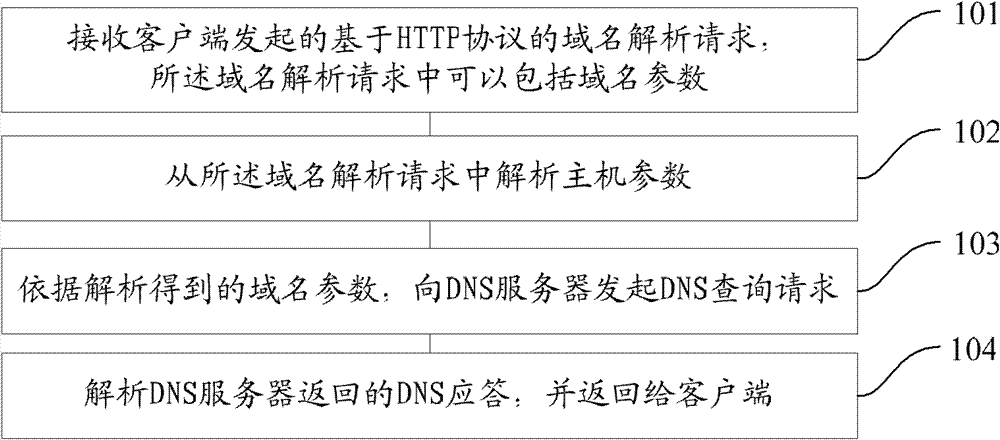
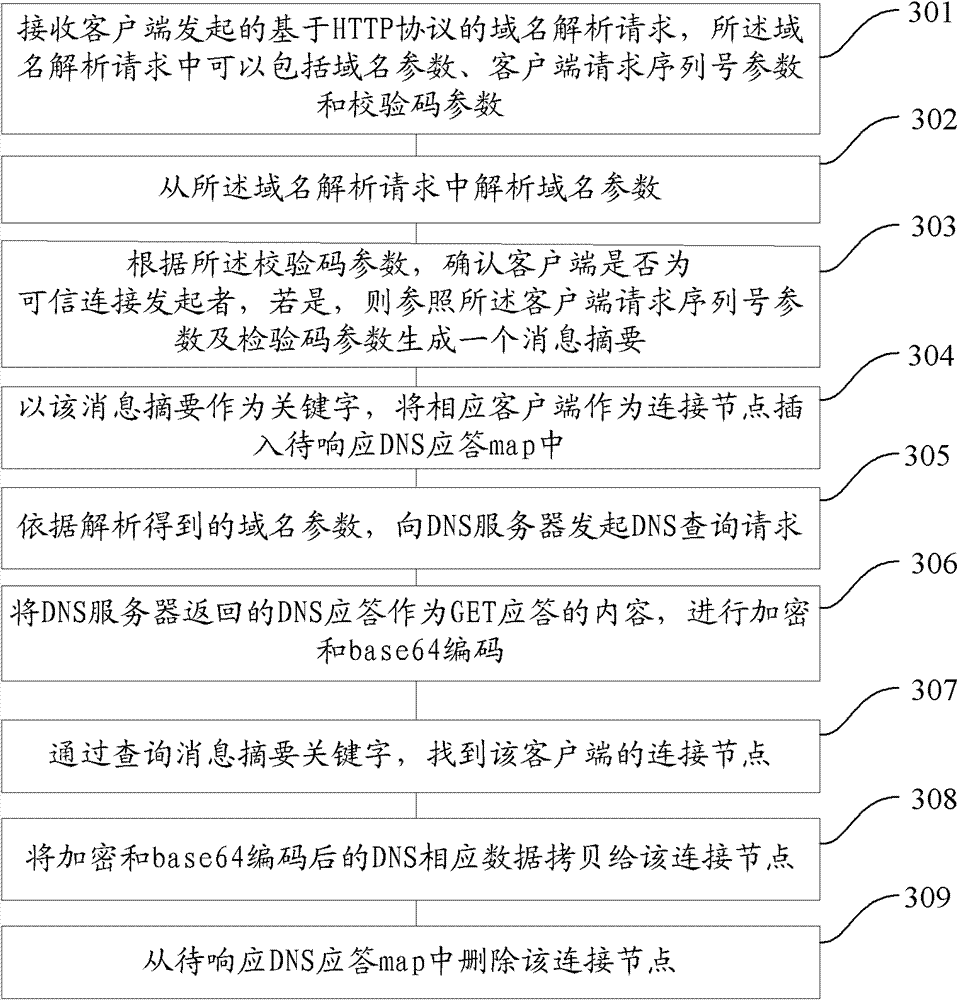
Domain name resolution agent method and system, and domain name resolution agent server
The invention provides a domain name resolution agent method and system, and a domain name resolution agent server, wherein the domain name resolution agent method specifically comprises the following steps: a client starts a domain name resolution request based on a hypertext transport protocol (HTTP), wherein the domain name resolution request comprises a domain name parameter; the domain name resolution request is received; the domain name parameter is resolved from the domain name resolution request; according to the resolved domain name parameter is obtained, a domain name server (DNS) query request is sent to the DNS; the DNS response returned by the DNS is resolved and then returned to the client. According to the invention, the domain name resolution can be conducted through the DNS agent resolution technology based on the HTTP, so that the safety of the domain name resolution is improved.
Owner:三六零数字安全科技集团有限公司
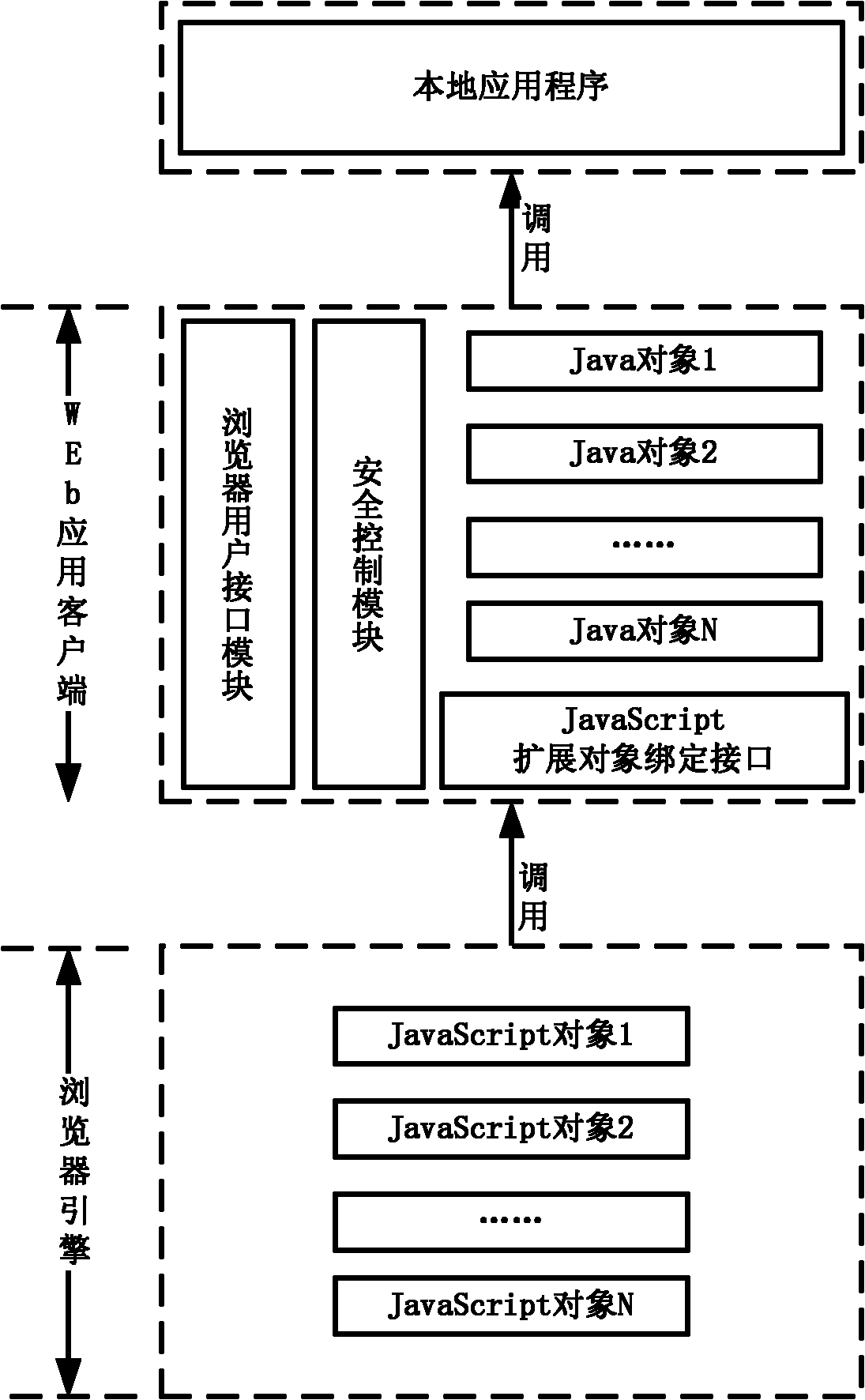
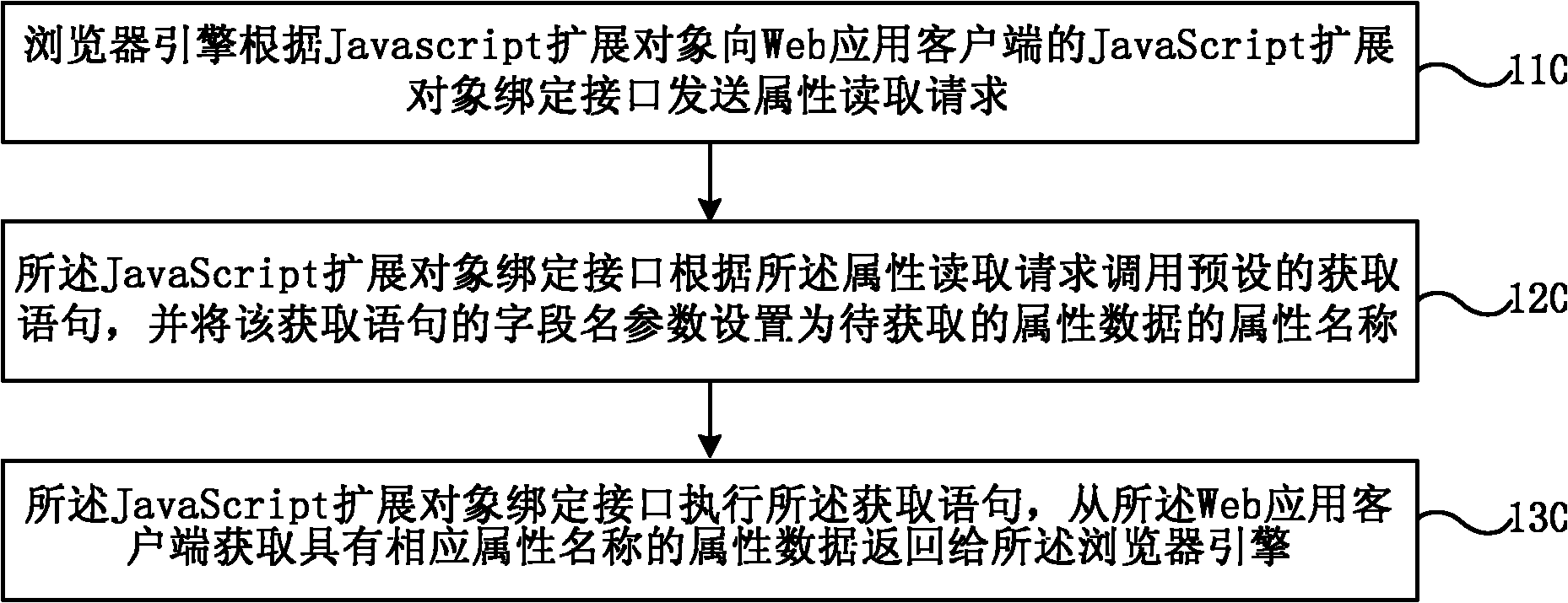
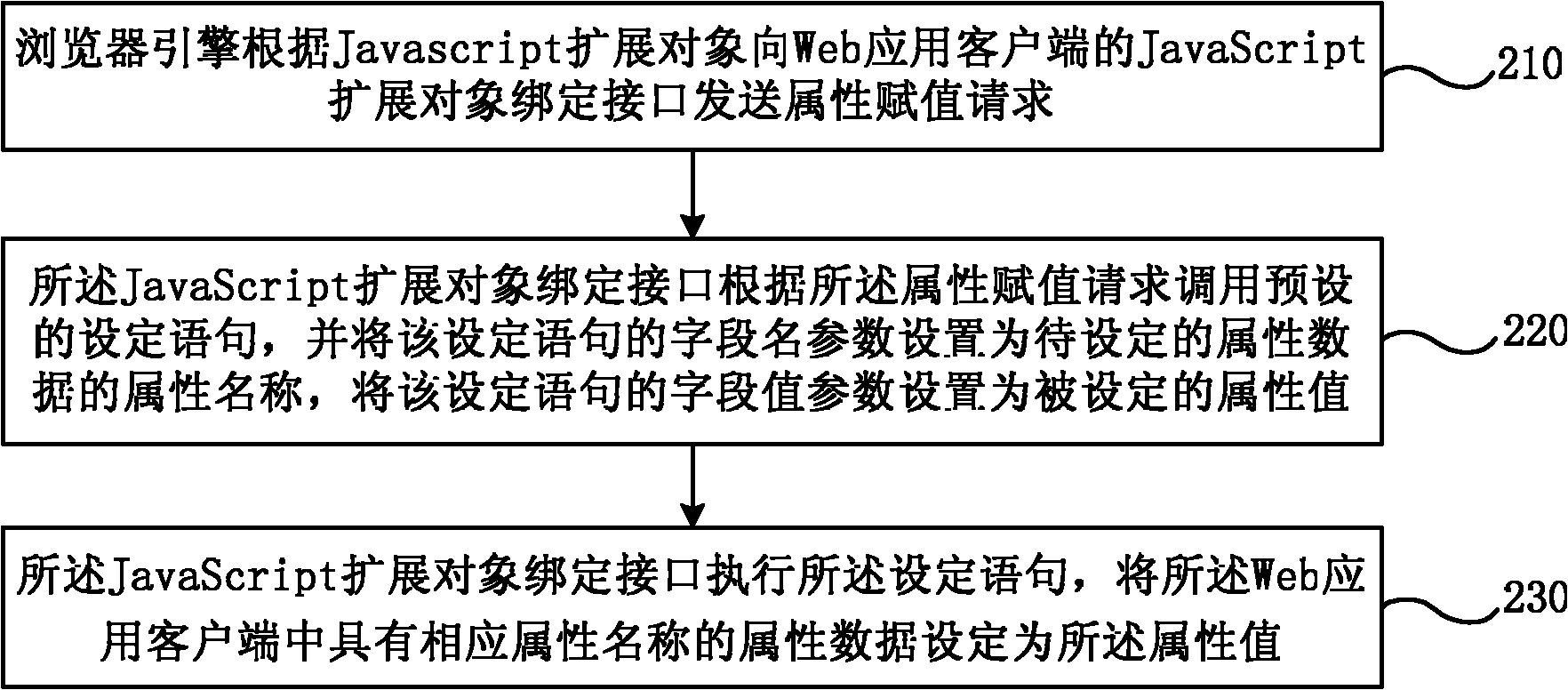
Realizing method of JavaScript extended object based on Android platform, and binding interface structure
ActiveCN102207873ADirect readRealize assignmentSpecific program execution arrangementsWeb applicationValue assignment
The invention provides a realizing method of a JavaScript extended object based on an Android platform, and a binding interface structure. The realizing method of the JavaScript extended object based on the Android platform comprises the following steps of: sending an attribute reading request to the binding interface of the JavaScript extended object of a Web application client by a browser engine according to the JavaScript extended object; calling a pre-set acquisition statement by the binding interface of the JavaScript extended object according to the attribute reading request and setting field name parameters of the acquisition statement to be an attribute name of attribute data to be acquired; and executing the acquisition statement and returning the attribute data which has the corresponding attribute name and is acquired from the Web application client back to the browser engine. According to the realizing method and the binding interface structure, the direct reading and value assignment of the attribute date of the Java object are realized so that the conditions for realizing more abundant extending function are created.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
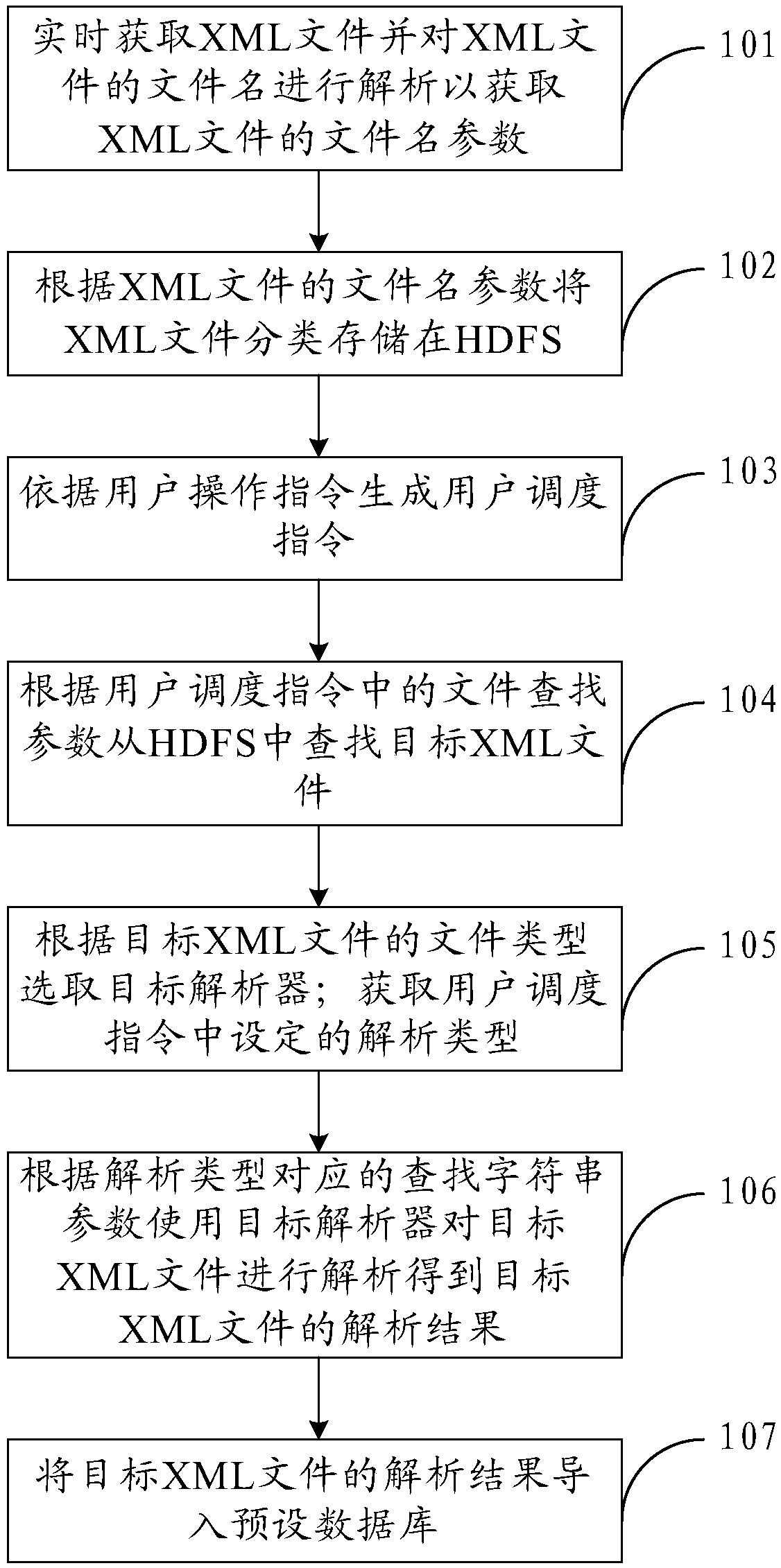
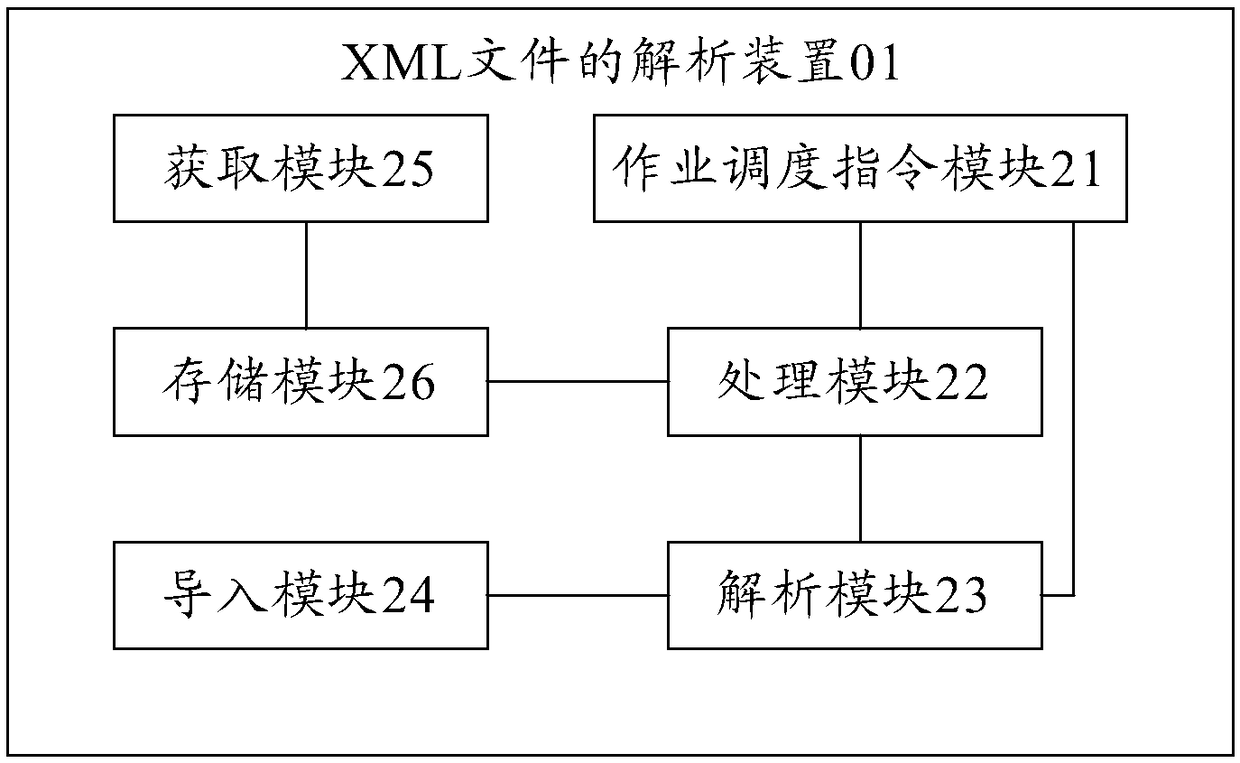
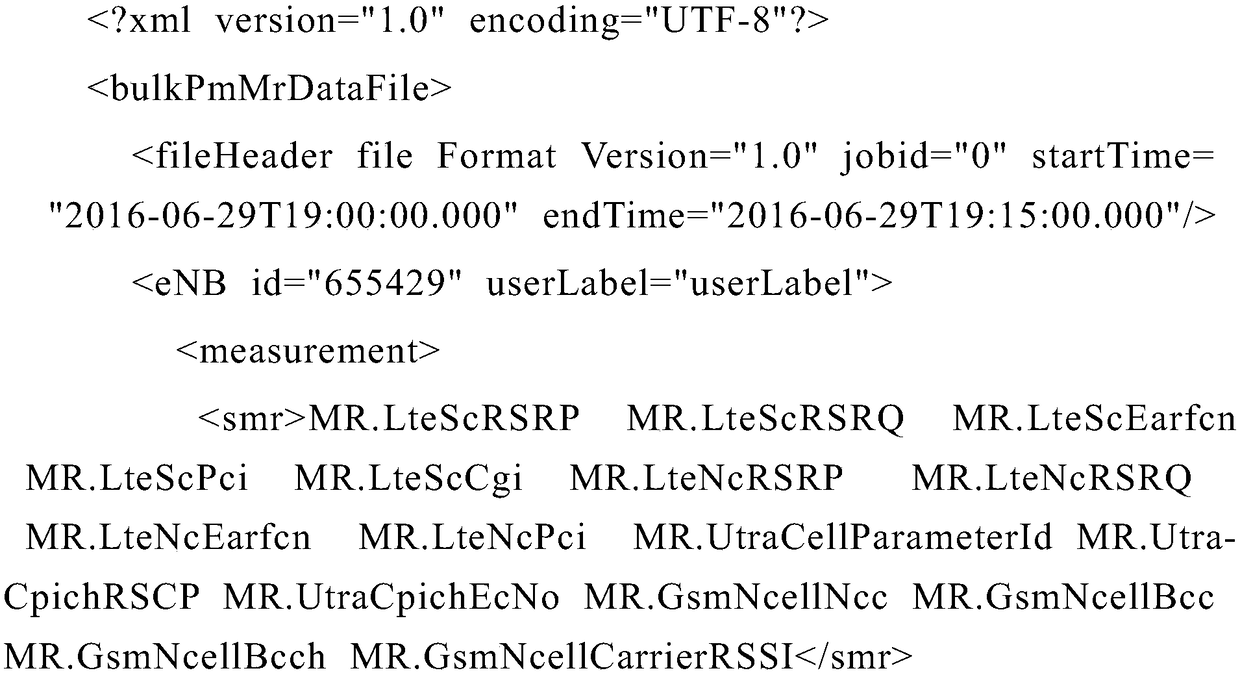
Analysis method and device for XML (Extensible Markup Language) files
ActiveCN108509658AImprove analysis efficiencyEasy to handleSpecial data processing applicationsCode compilationDistributed File SystemScheduling instructions
The embodiment of the invention provides an analysis method and device for XML (Extensible Markup Language) files and relates to the field of file analysis. The analysis efficiency of the XML files can be improved. The method comprises the steps of generating a user scheduling instruction according to a user operation instruction; searching target XML files from an HDFS (Hadoop Distributed File System) according to file searching parameters in the user operation instruction, wherein the XML files are classified and stored in the HDFS according to file name parameters of the XML files; selecting target analyzers according to file types of the target XML files; obtaining analysis types set in the user scheduling instruction, and analyzing the target XML files through utilization of the target analyzers according to searching character string parameters corresponding to the analysis types, thereby obtaining analysis results of the target XML files, wherein the analysis types comprise rapid searching and total analysis; and importing the analysis results of the target XML files to a preset database.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
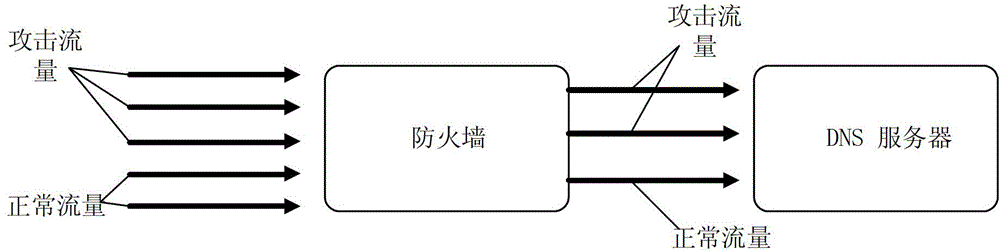
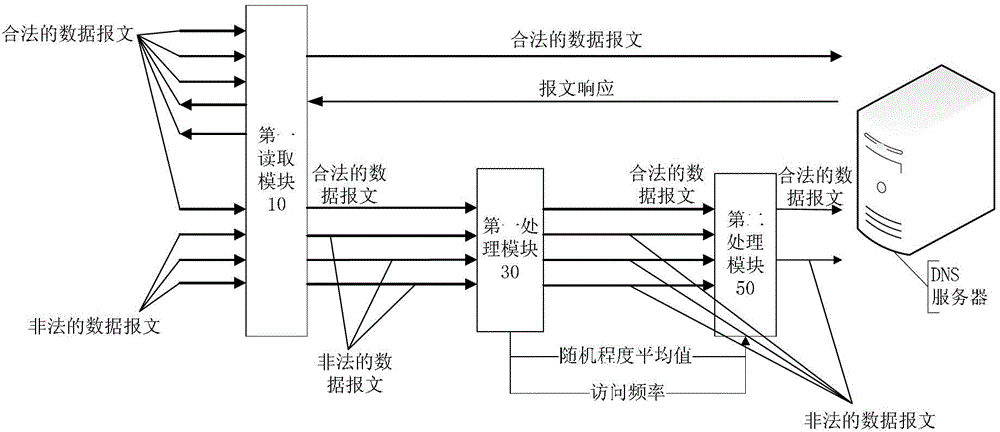
Detection method and device for data message
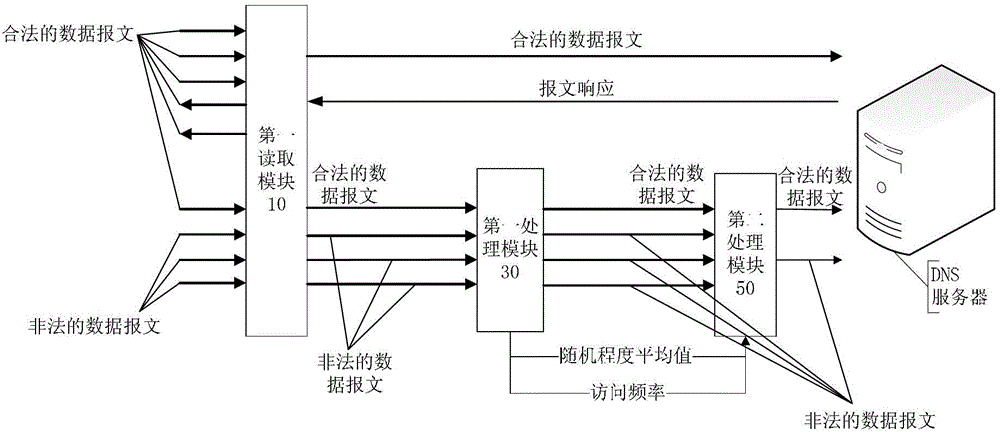
ActiveCN102984178AEffective and efficient cleaningAccurate identificationData switching networksDomain nameTraffic capacity
The invention discloses a detection method and a device for a data message. The method comprises a detection method of the data message. The method comprises the following steps: reading the domain name parameter of a received first data message; performing a random degree calculation to the domain name parameter of the first data message and a preset domain name parameter to obtain a random degree score of the domain name parameter of the first data message, wherein the preset domain name parameter is a domain name parameter of a preset valid data message; judging if the random degree score is more than a blocking threshold; and determining the first data message to be an invalid data message when the random degree score is more than the blocking threshold. According to the detection method, accurately identifying the invalid data message is achieved, so that the invalid data message can be processed from a flow of all DNS (Domain Name Server) random requests, the invalid data message of the DNS random requests can be effectively and efficiently cleaned, and a DNS random request attack loses a DDOS (Distributed Denial of Service) effect.
Owner:HILLSTONE NETWORKS CO LTD +1
WAP-based method and WAP-based system for controlling accesses to SP
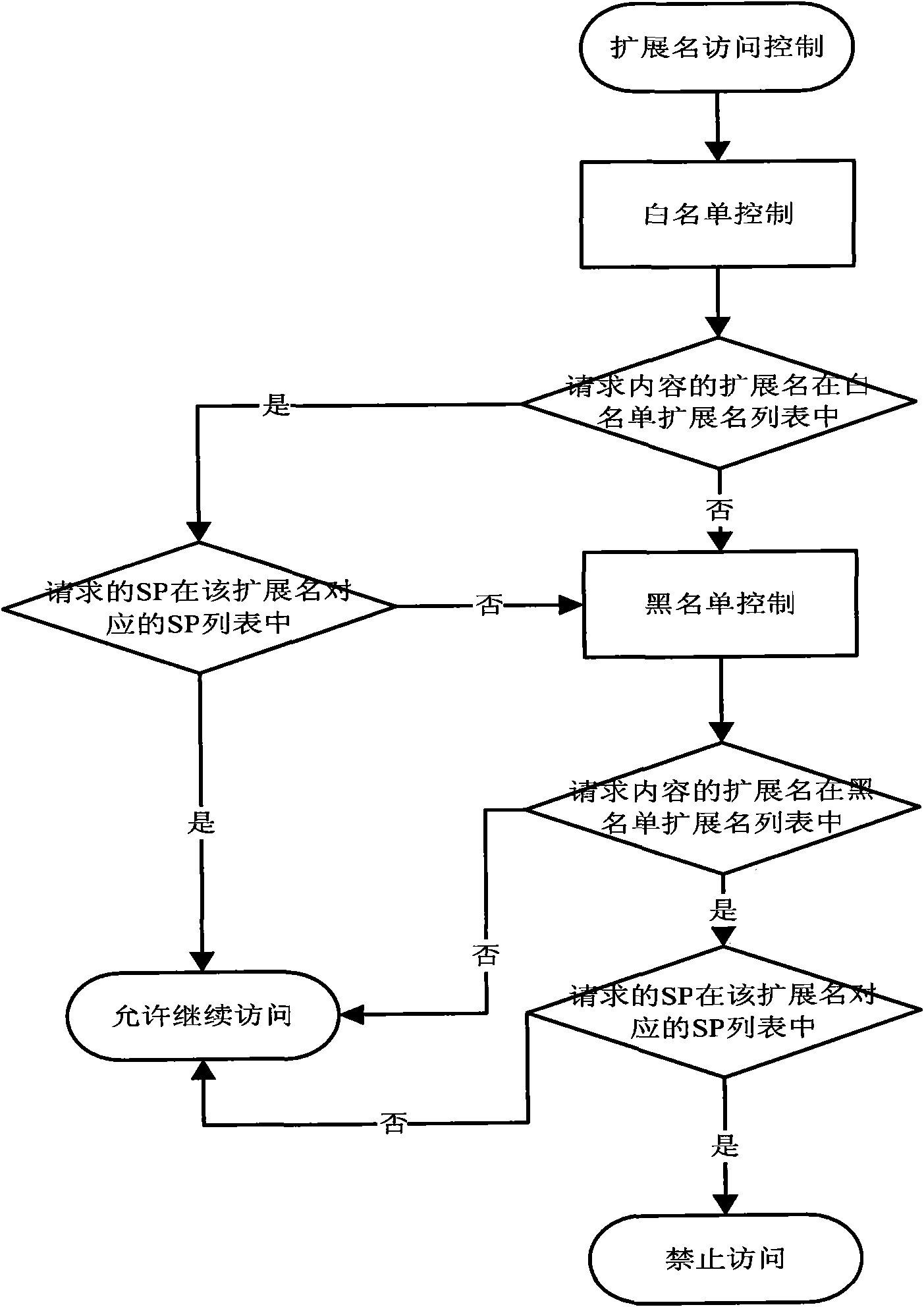
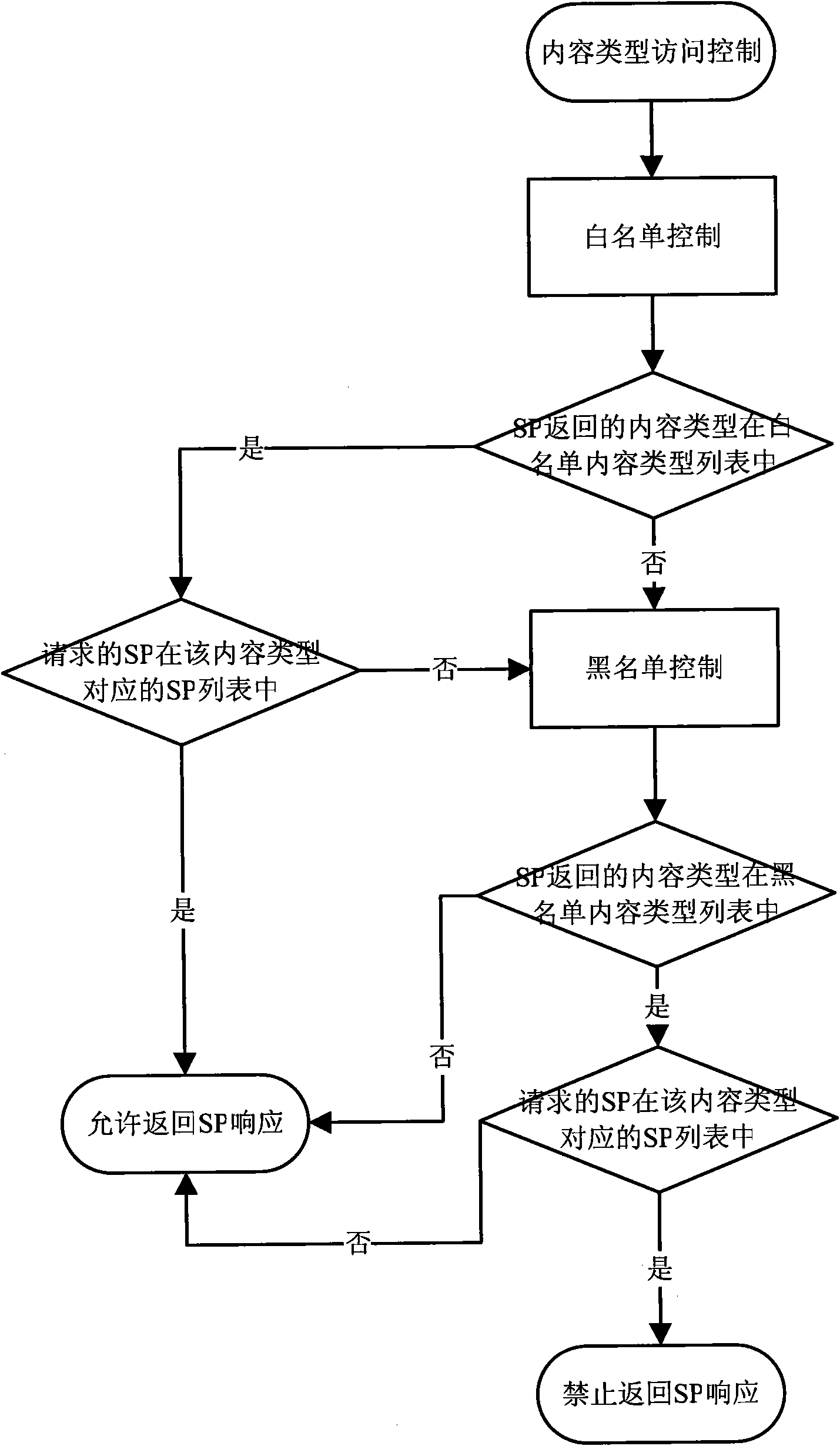
InactiveCN101600207AImprove securityPrevent fraudAssess restrictionWireless network protocolsFiltrationBlack list
The invention discloses a WAP-based method and a WAP-based system for controlling accesses to SP, which set black lists and white lists for the SP access parameters to allow eligible user requests passing through the filtration of the black lists and the white lists to be processed on a WAP gateway after the SP gives a response, thereby improving the safety of a WAP application system. In addition, flexible configuration of access control policies can be realized through a multi-step access control of setting the black and white lists and priority for a plurality of SP access parameters. The invention also provides a processing mechanism for controlling the accesses to an accessed content expanded-name parameter and an SP feedback content type parameter respectively, which avoids fraudulent conducts in accesses to the SP.
Owner:ZTE CORP
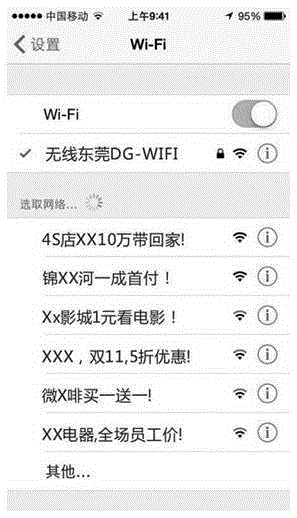
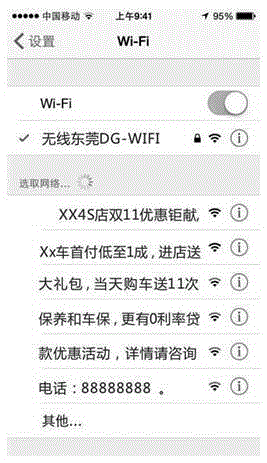
Method and system for publishing advertisement through WLAN service set identifier
InactiveCN105357741ARealize the dissemination of publicityLow costAssess restrictionComputer terminalUser identifier
The invention discloses a method for publishing advertisements through a WLAN service set identifier. The method comprises the steps: configuring an SSID (service set identifier) name parameter which is advertisement content; in a WLAN (wireless local area network), configuring the SSID name parameter to be displayed in the form of a list, and therefore, when a user of a WIFI connection terminal performs WIFI connection, opening a WIFI list and making the SSID with the preconfigured name parameter displayed in the WIFI list, so that a purpose of propagating the advertisement content is achieved. According to the method for publishing the advertisement through a WLAN service set identifier, parameters of the SSID are preconfigured, so that the user can see the relative advertisement content as long as the user opens the WIFI list, convenient propagation and publishing of the advertisement can be realized.
Owner:东莞市松山湖信息网络有限公司
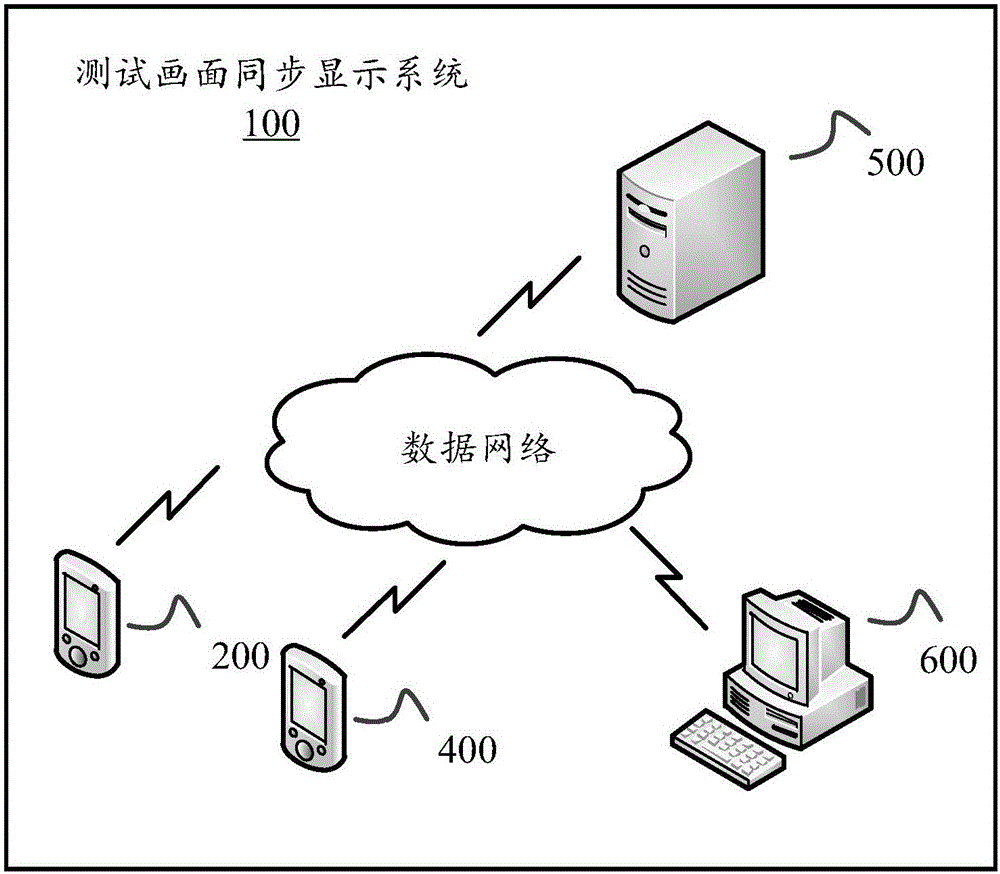
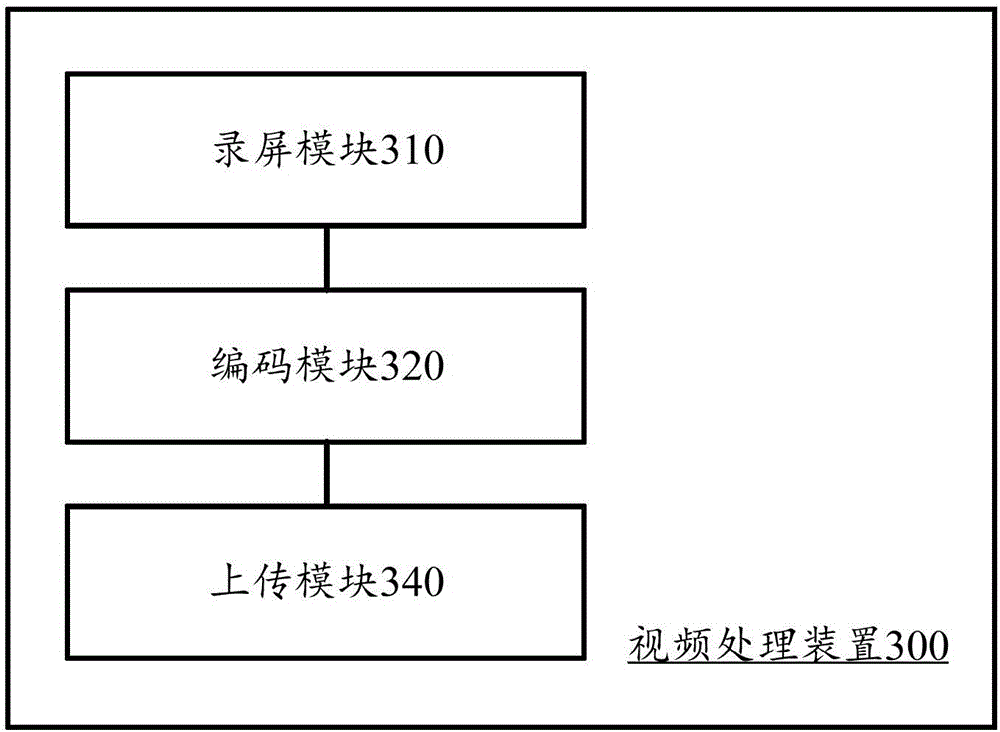
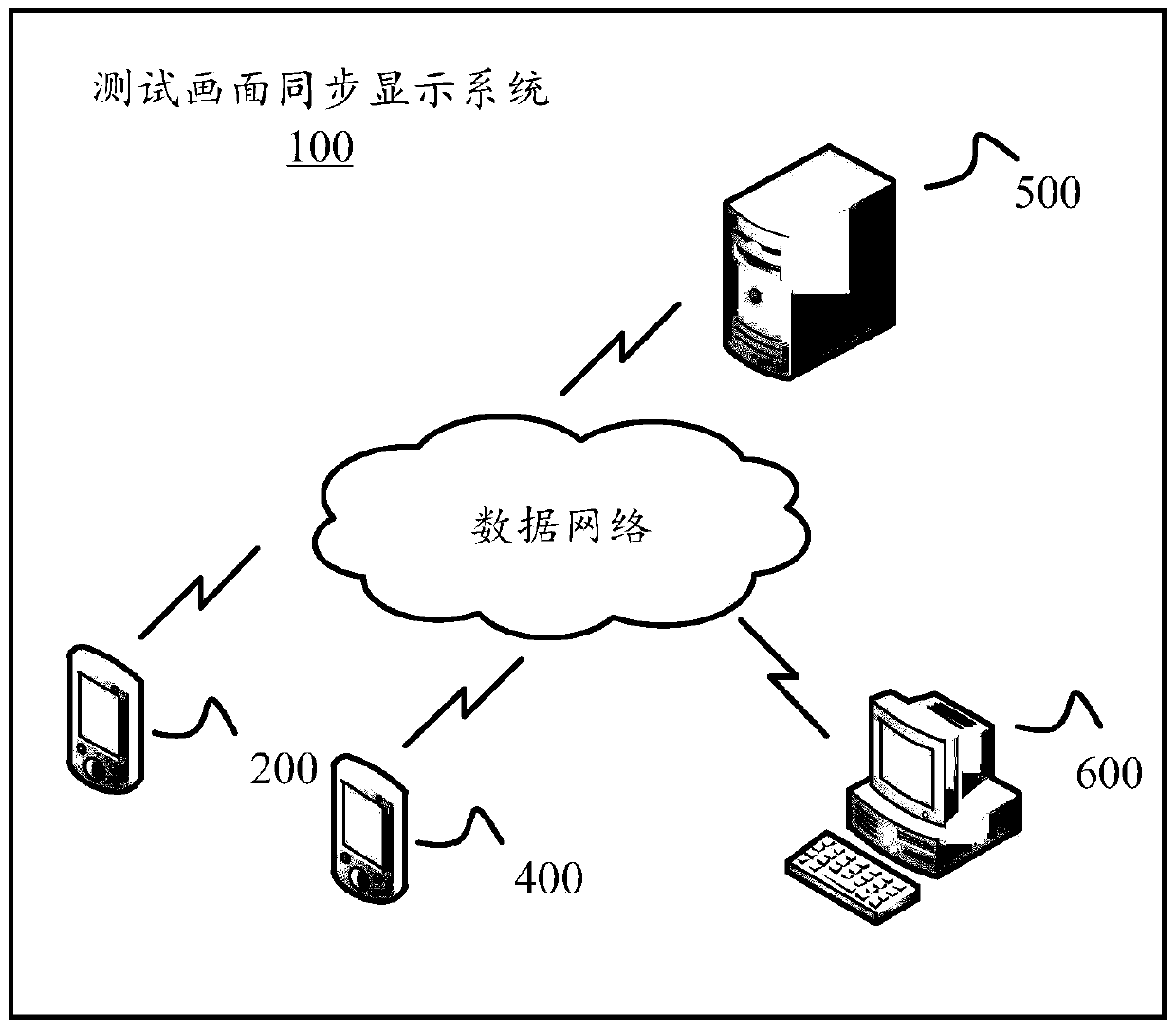
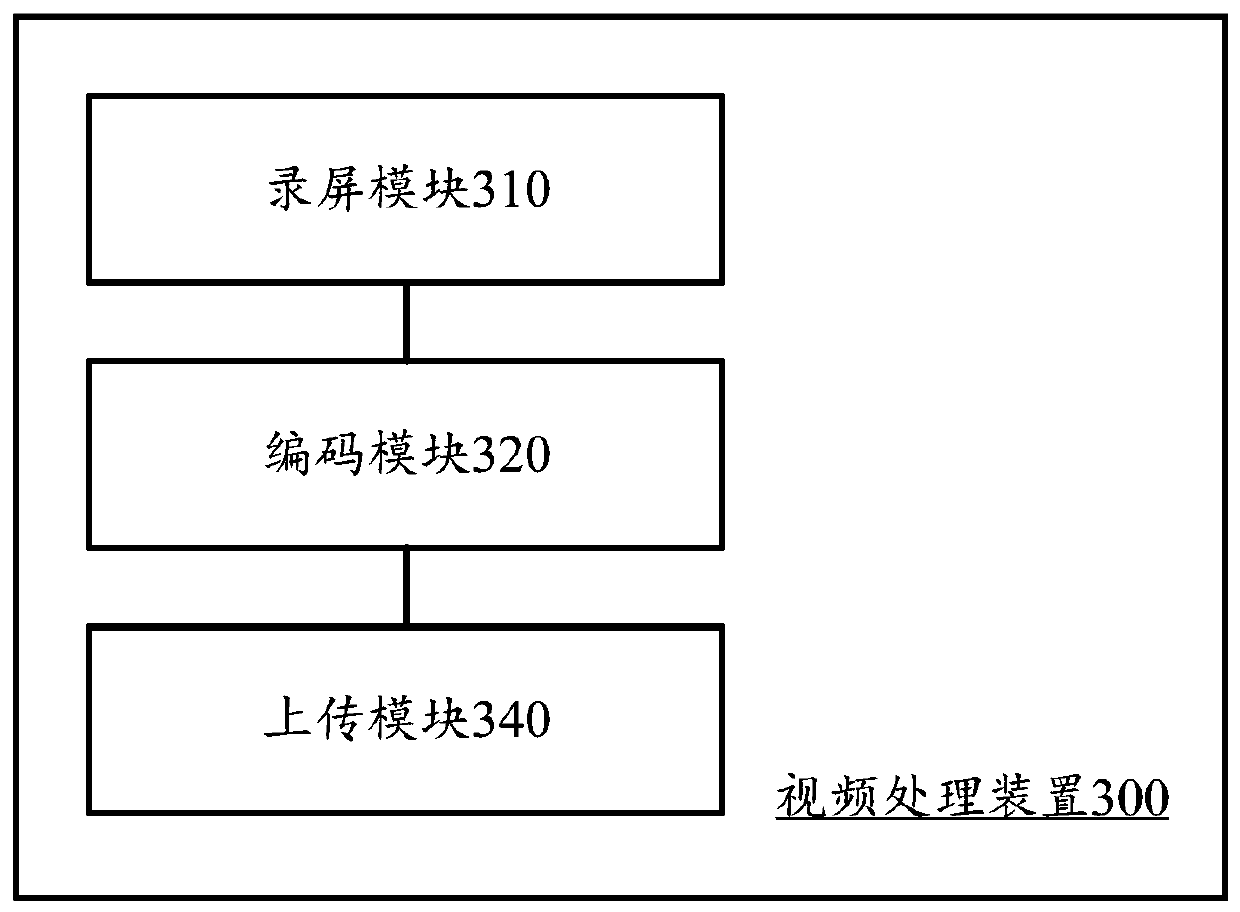
Synchronous test image display method and system
The invention discloses a synchronous test image display method and system, wherein the synchronous test image display method is applicable to execution in the synchronous test image display system. The synchronous test image display system comprises multiple mobile terminals, a server and a computing device. The method comprises that mobile terminals record images in a current test process, thus obtaining first video data; the first video data is coded, thus forming second video data; the second video is packaged, thus obtaining third video data; the third video data is uploaded to the server; the server obtains the name parameters of the mobile terminals from the uploaded third video data; the server generates multiple corresponding URL addresses according to the name parameters, wherein the URL addresses correspond to the third video data of the mobile terminals; the computing device accesses the URL addresses in multiple web pages; and the corresponding third video data is decoded and played, thus synchronously displaying the test images of the mobile terminals.
Owner:XIAMEN MEITU MOBILE TECH CO LTD
Method for copying phone directories of mobile phones based on network
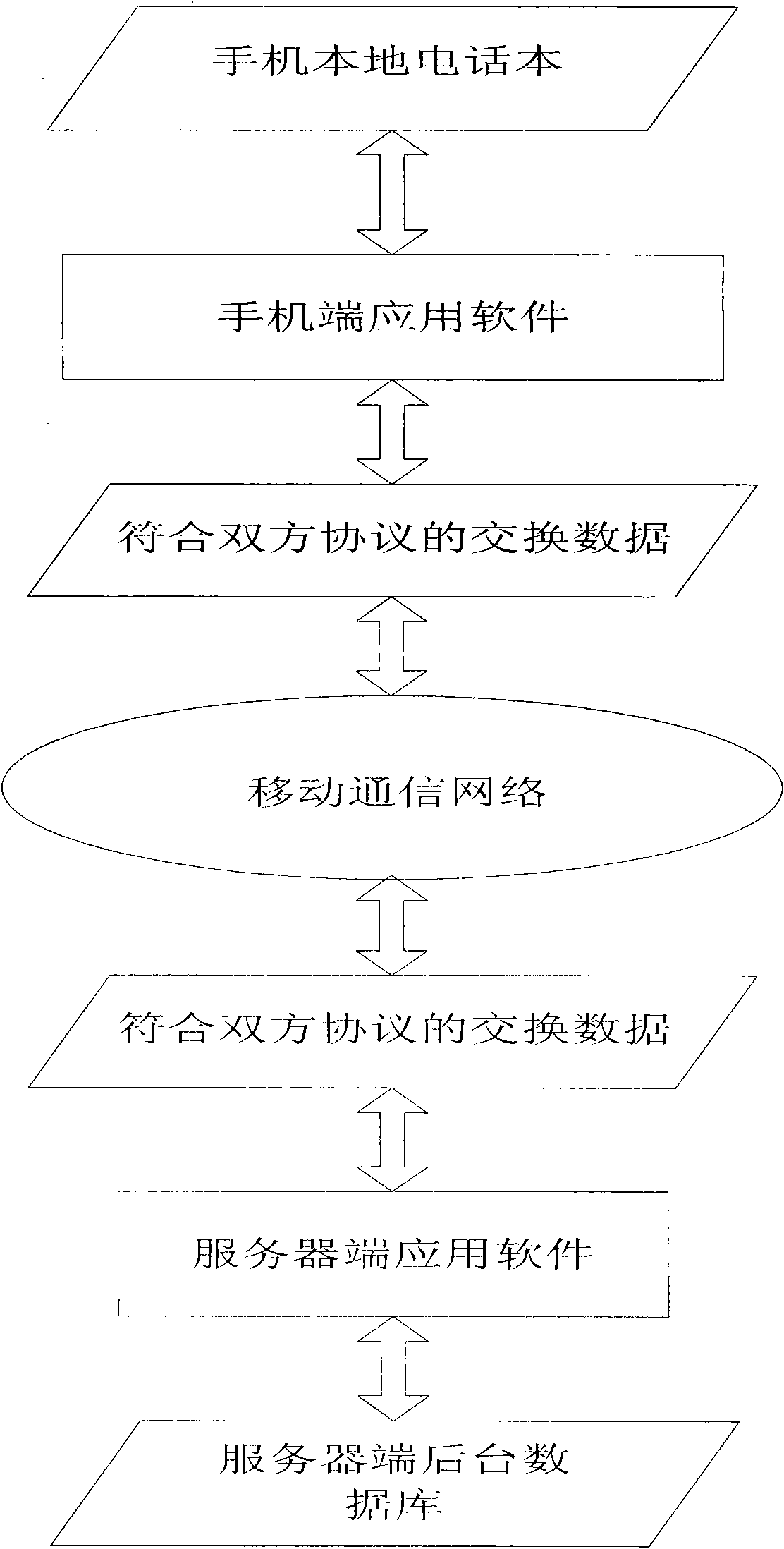
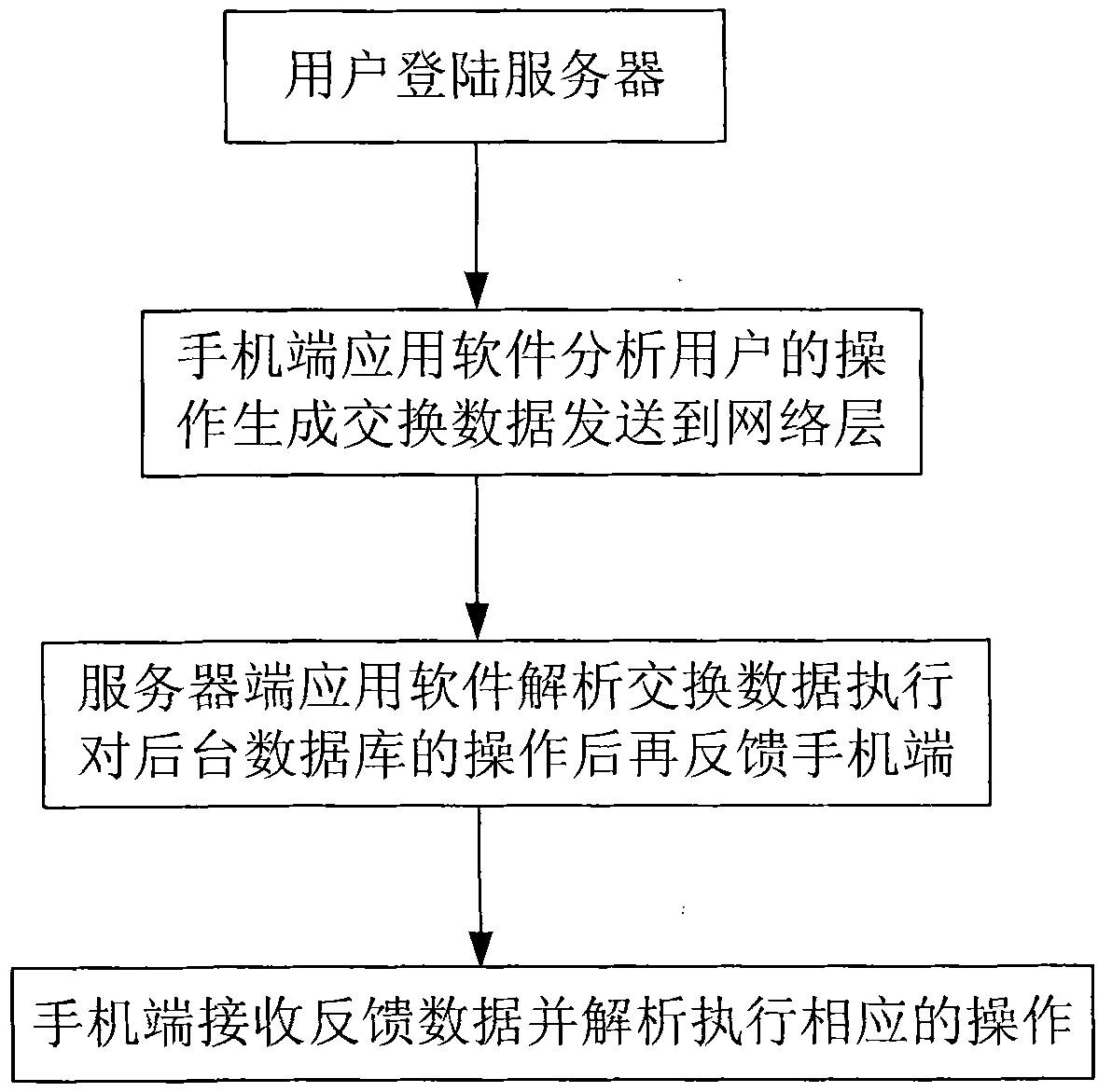
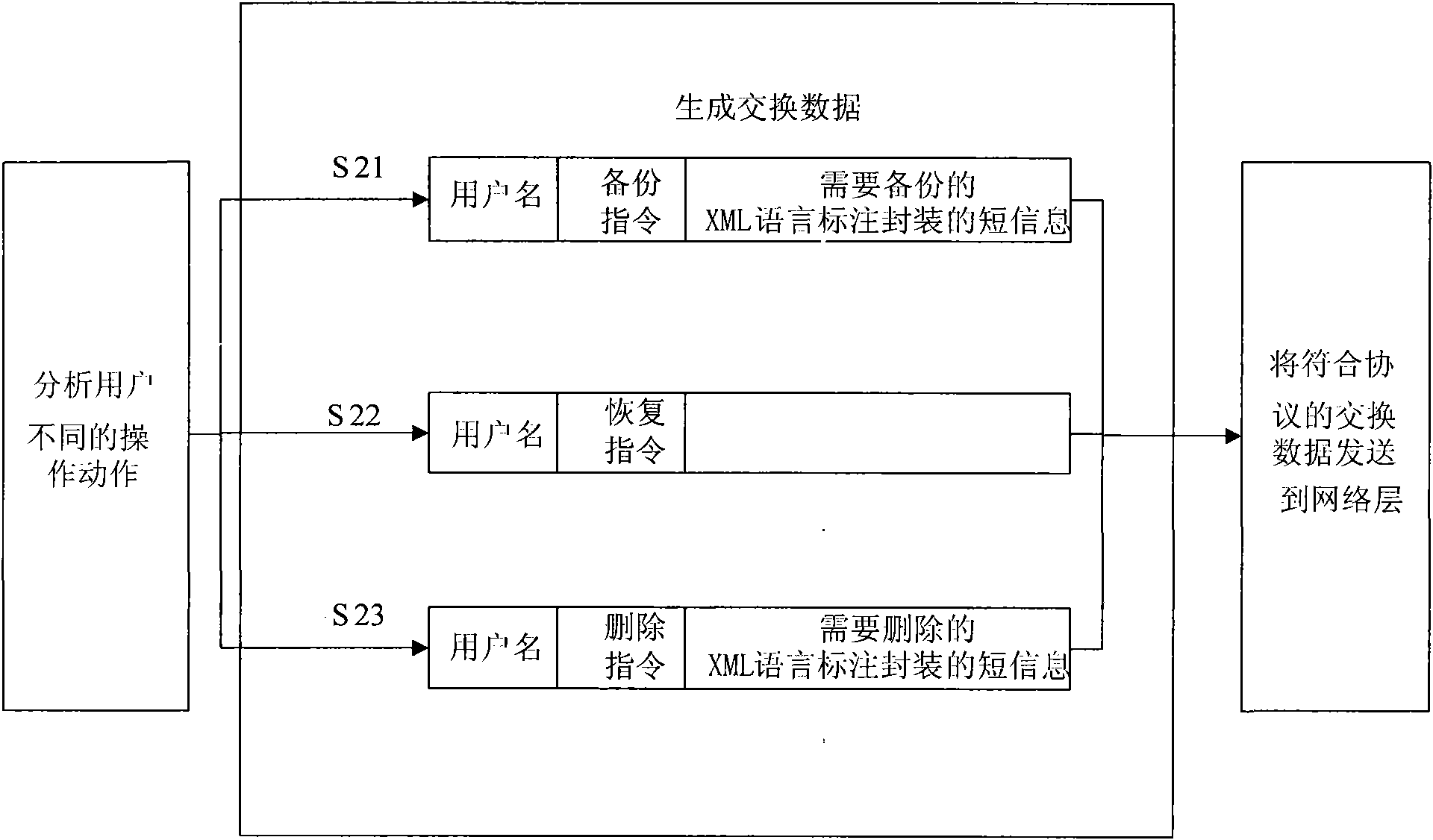
InactiveCN101577900AImplement backupAchieve recoveryNetwork data managementSecret codeService condition
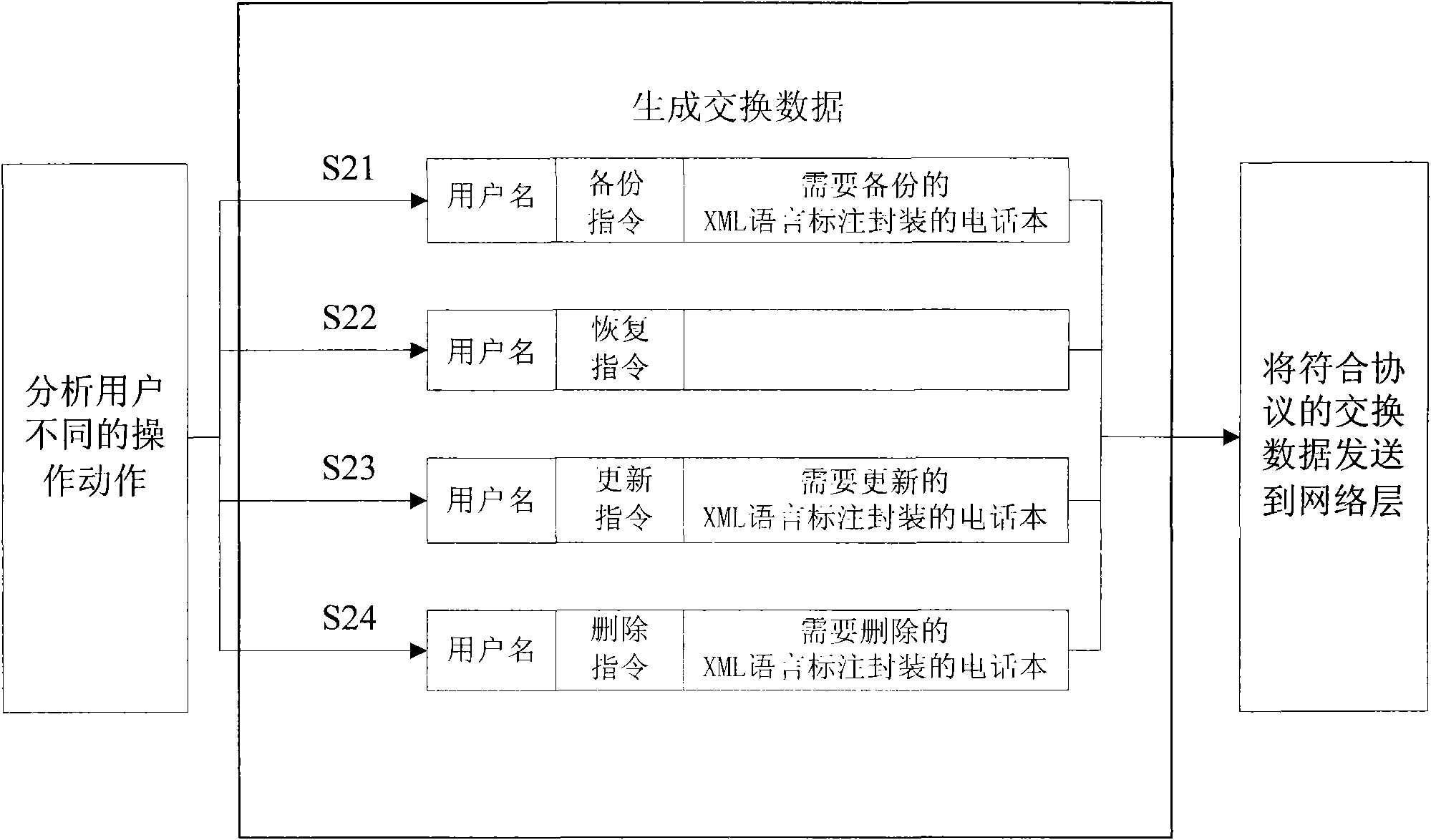
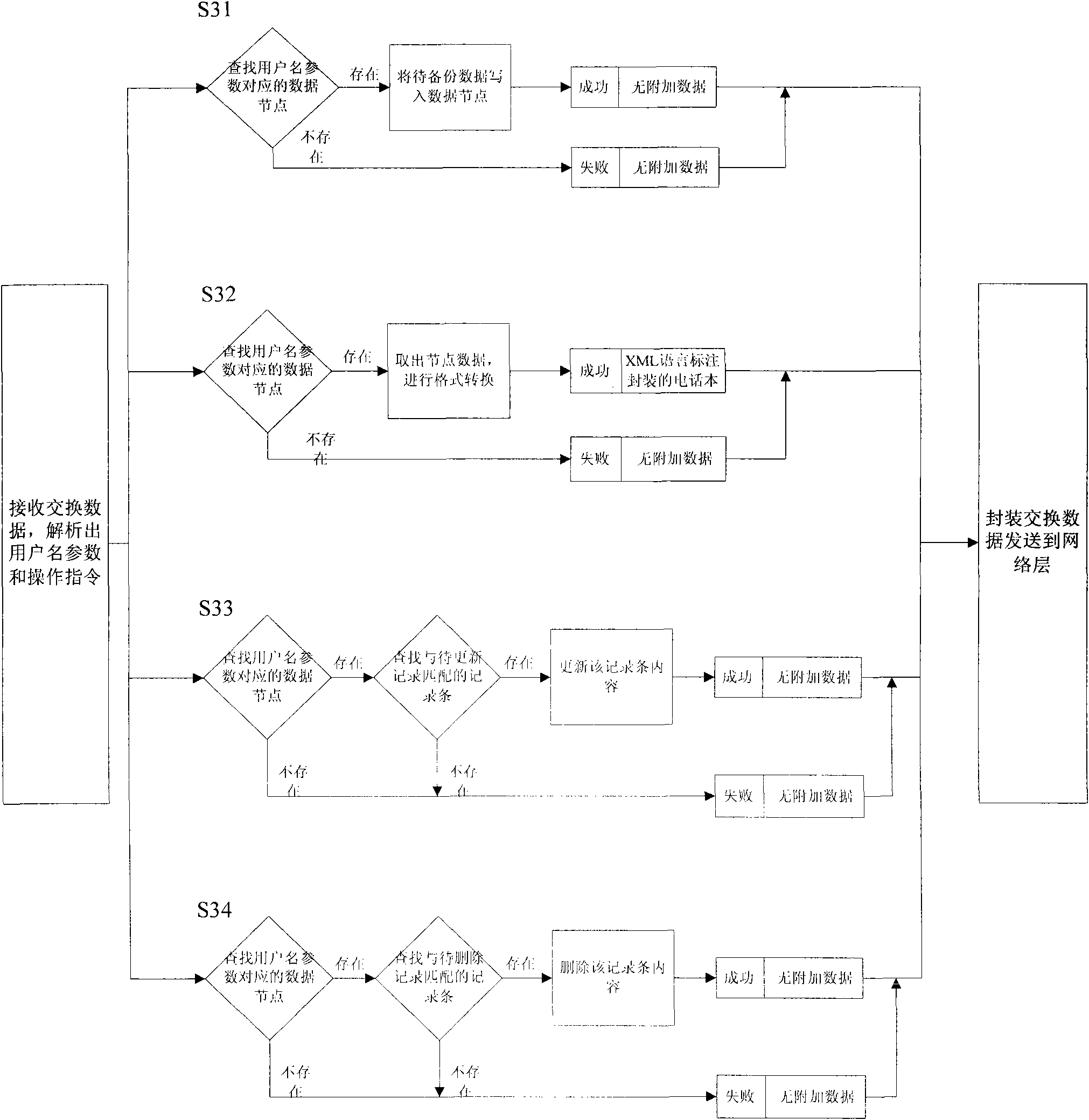
The invention discloses a method for copying a phone directory of a mobile phone based on network, which comprises the following steps that: a server is logged on, the user name, code and server state are verified, and usable service condition is fed back; a mobile phone end processes local phone directory data according to an operation action of a user, generates additional data and an operational instruction required by operation, encapsulates corresponding operational instruction, additional data and user name parameter as required, and transmits the encapsulated operational instruction, the encapsulated additional data and the encapsulated user name parameter to a server end through a network layer; the server end receives and analyzes data from the network layer, executes corresponding operation according to the operational instruction of the user and the additional data, encapsulates execution result feedback and the additional data as required according to executed operation results, and transmits the encapsulated execution result feedback and the encapsulated additional data to the mobile phone end through the network layer; and the mobile phone end receives and analyzes feedback data of the server end and executes corresponding local processing according to the execution result feedback and the additional data. The method realizes operations such as copying of the phone directory on the server, and has strong practicality.
Owner:SHANGHAI WINGTECH ELECTRONICS TECH
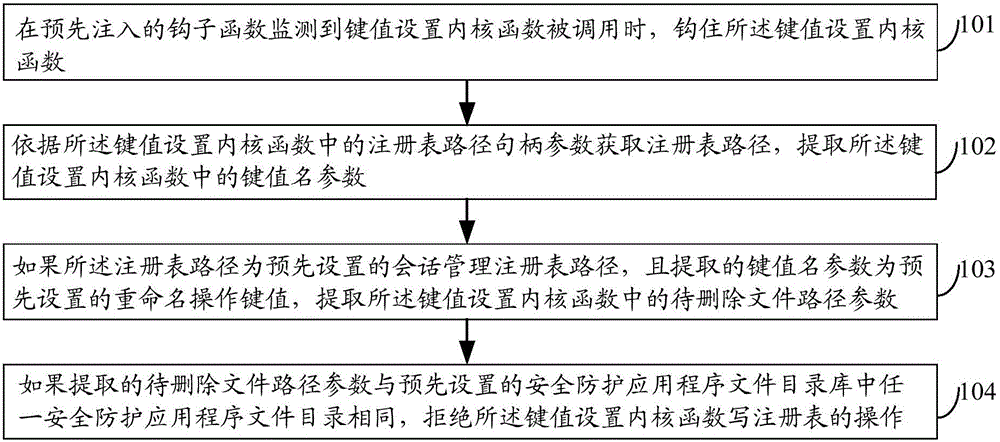
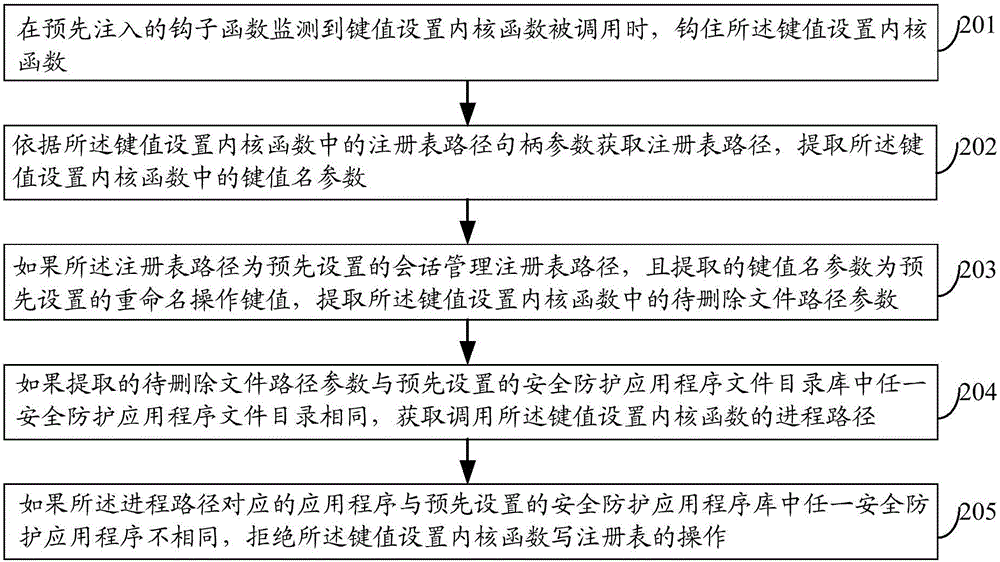
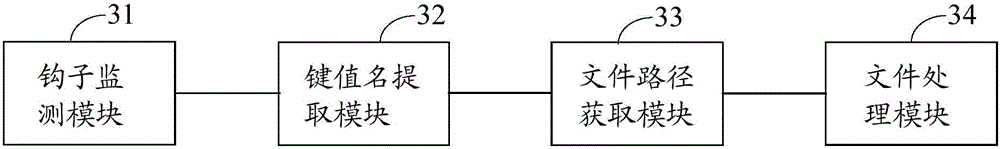
Method and device for protecting safety protection application program files and electronic equipment
The embodiment of the invention discloses a method and device for protecting safety protection application program files and electronic equipment and relates to an information safety technology. The method comprises the following steps: when monitoring that a key value setting kernel function is called by a pre-injected hook function, hooking the function; acquiring a registry path according to registry path handle parameters in the key value setting kernel function, and extracting key value name parameters in the key value setting kernel function; if the registry path is a conversation management registry path and the extracted key value name parameters are renaming operation key values, extracting parameters of file paths to be deleted in the key value setting kernel function; and if the extracted parameters of file paths to be deleted in the key value setting kernel function are the same as any safety protection application program file catalogue in a pre-set safety protection application program file catalogue library, rejecting the operation of writing a registry of the key value setting kernel function. The method is applicable to protection of the safety protection application program files.
Owner:ZHUHAI BAOQU TECH CO LTD
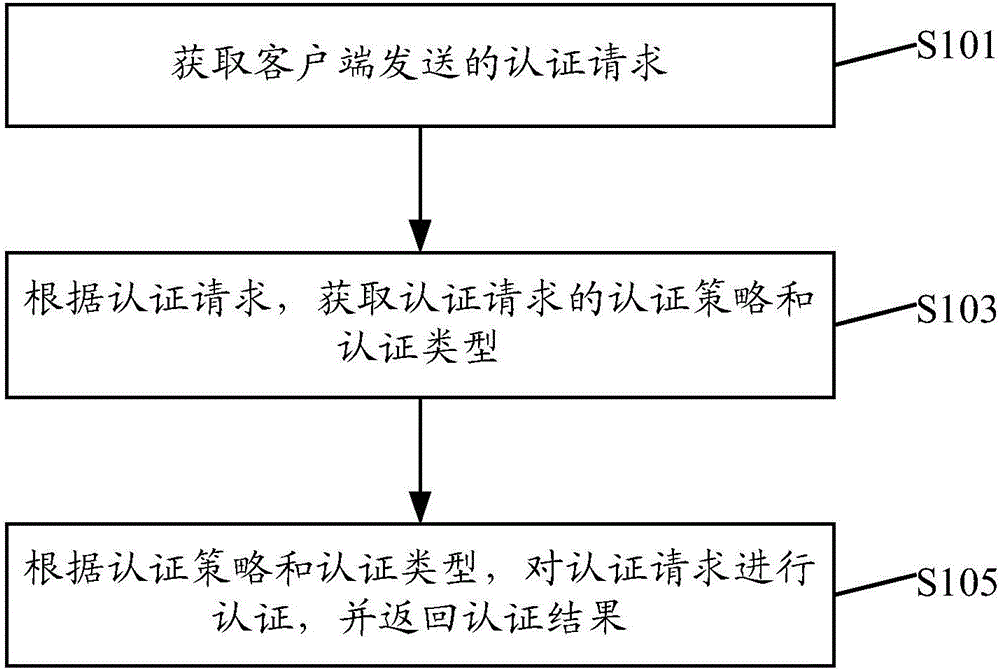
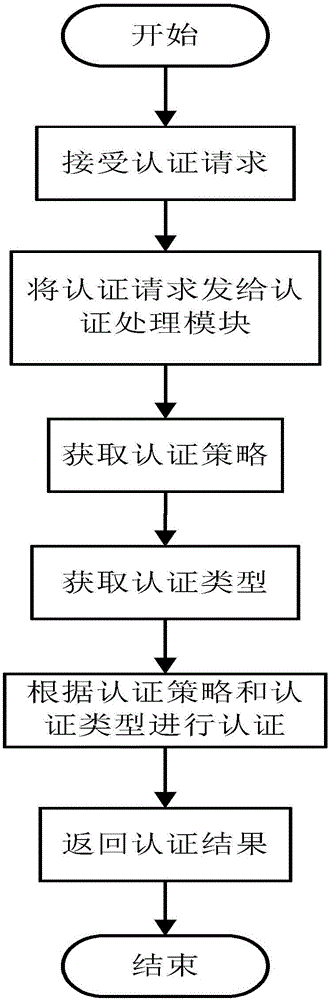
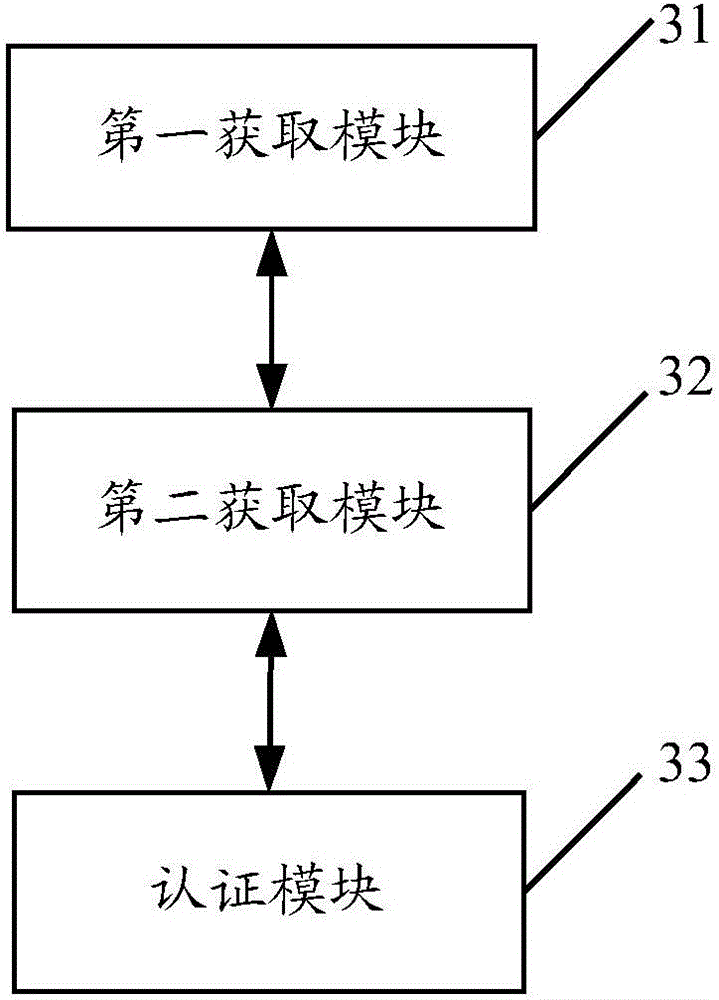
Authentication method and apparatus
InactiveCN106657112AImprove good performanceConvenient custom authenticationTransmissionPersonalizationClient-side
The invention provides an authentication method and apparatus. The authentication method comprises the following steps: obtaining an authentication request sent by a client; obtaining an authentication strategy and an authentication type of the authentication request according to the authentication request; and authenticating the authentication request according to the authentication strategy and the authentication type, and returning an authentication result. According to the authentication method and apparatus provided by the invention, as a unified authentication interface is adopted, the expansion and customization of authentication of an application system by a developer are greatly facilitated, different user demands are satisfied, meanwhile the authentication type is individually selected in a configuration file for the actual demands of each user to serve as the authentication of the user, in addition, different authentication modes can also be customized according to different users, and the name parameters and authentication strategies of all kinds of authentication are stored in the form of the configuration file, so that the expansion and customization of the authentication are more convenient and flexible.
Owner:DAWNING INFORMATION IND BEIJING
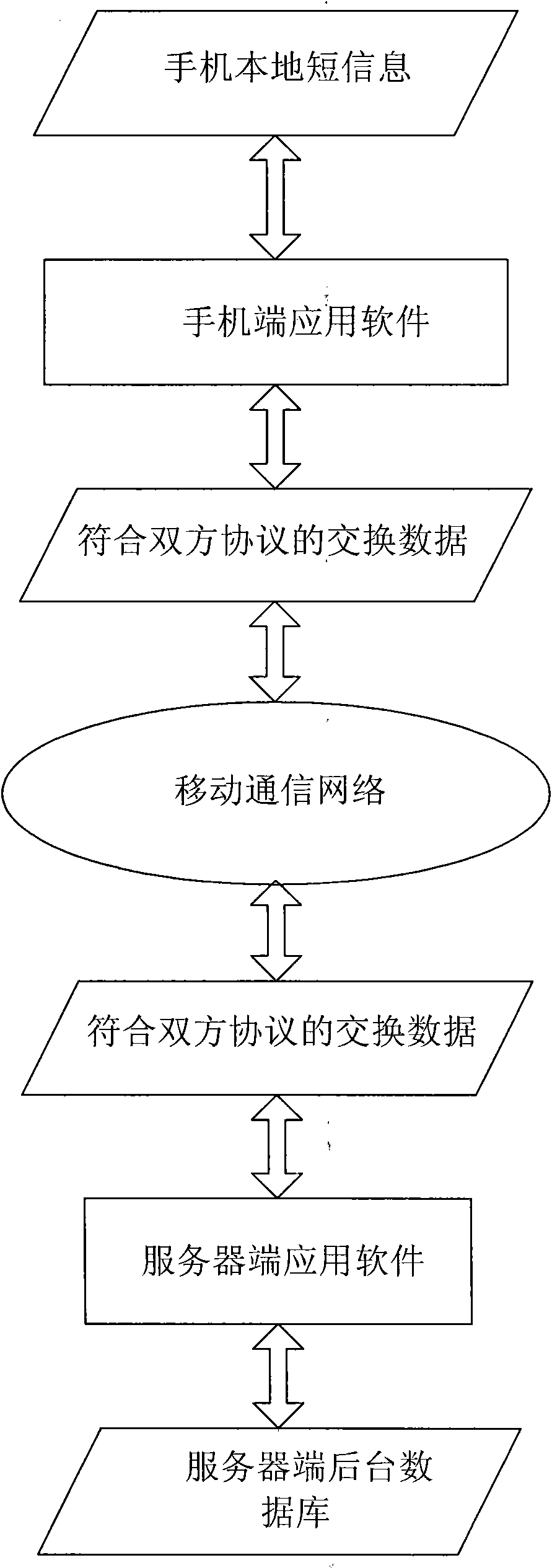
Method for backing up mobile phone short messages based on network
InactiveCN102014350AImplement backupAchieve recoveryMessaging/mailboxes/announcementsNetwork data managementApplication softwareMobile phone
The invention discloses a method for backing up mobile phone short messages based on network, comprising the following steps that: a user logins a server, checks the identity of the user and the state of the server and feeds back the available service state; mobile terminal application software processes local short message data according to the operational action of the user, generates additional data and an operational instruction required by the operation, necessarily packages the corresponding operational instruction, the additional data and user name parameters and transmits the corresponding operational instruction, the additional data and the user name parameters to a server end through a network layer; server end application software receives data from the network layer and analyzes, executes corresponding operation according to the operation instruction of the user and the additional data, feeds back the execution result according to the result of the execution operation, necessarily packages the additional data and transmits the additional data to the mobile phone terminal through the network layer; and the mobile phone terminal receives feedback data of an analyzing server end and locally processes according to the execution result feedback and the additional data. The invention can realize the backup, restoration and other operations of the short messages on the server.
Owner:SHANGHAI WINGTECH ELECTRONICS TECH
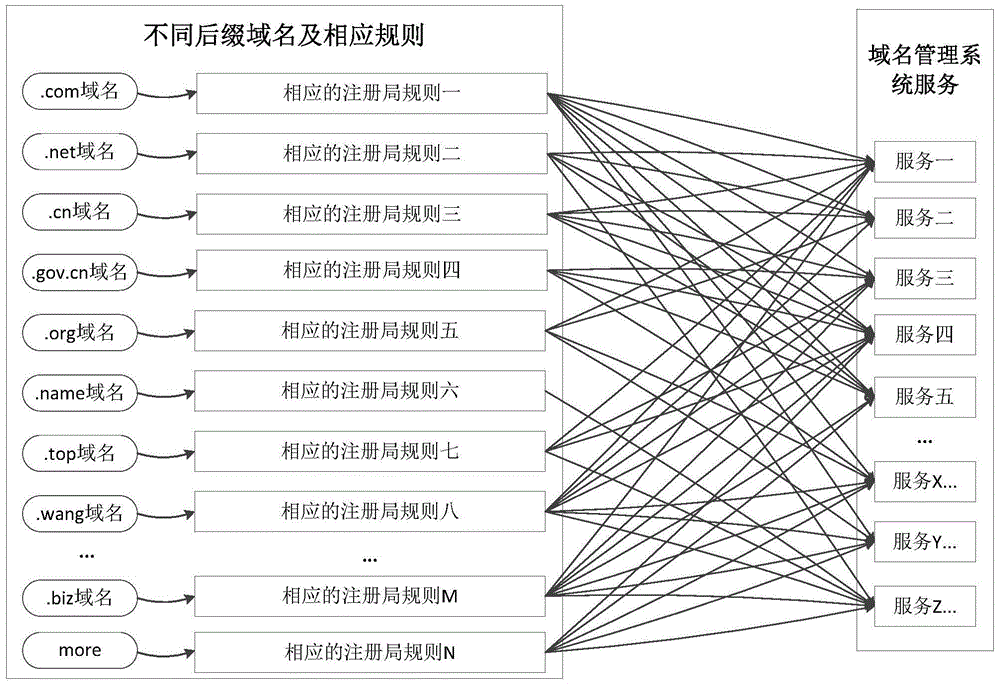
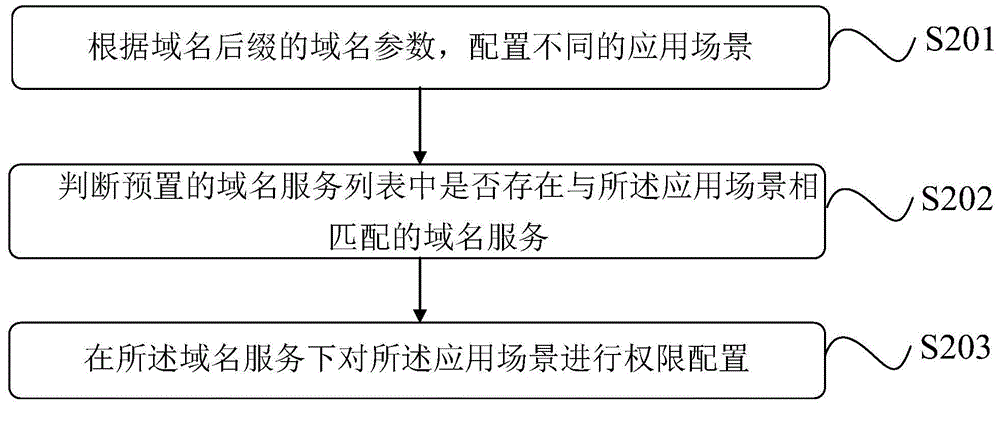
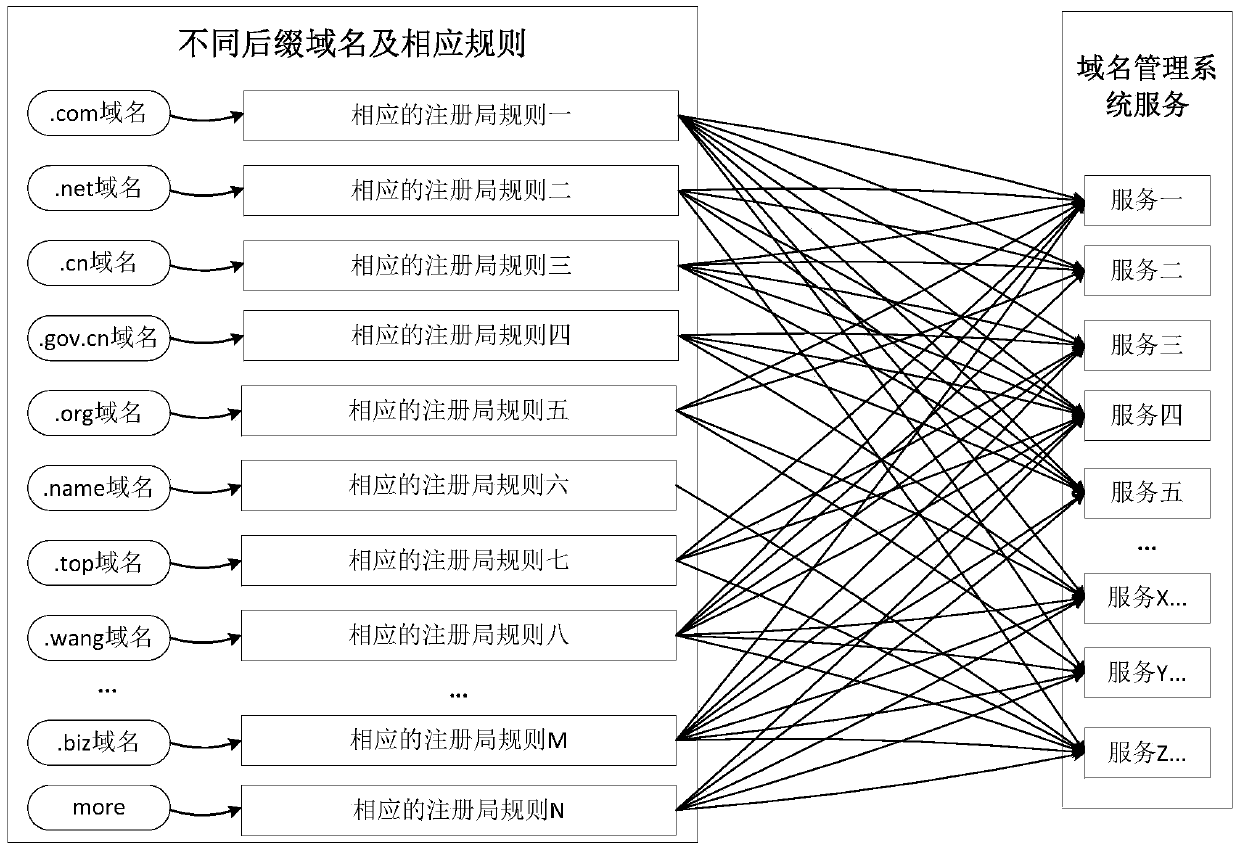
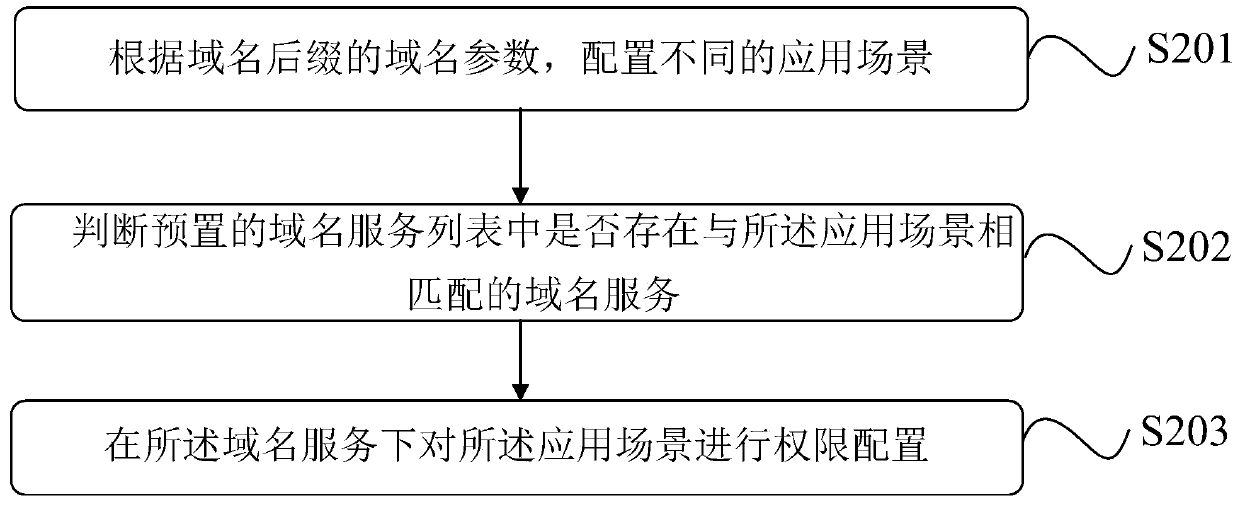
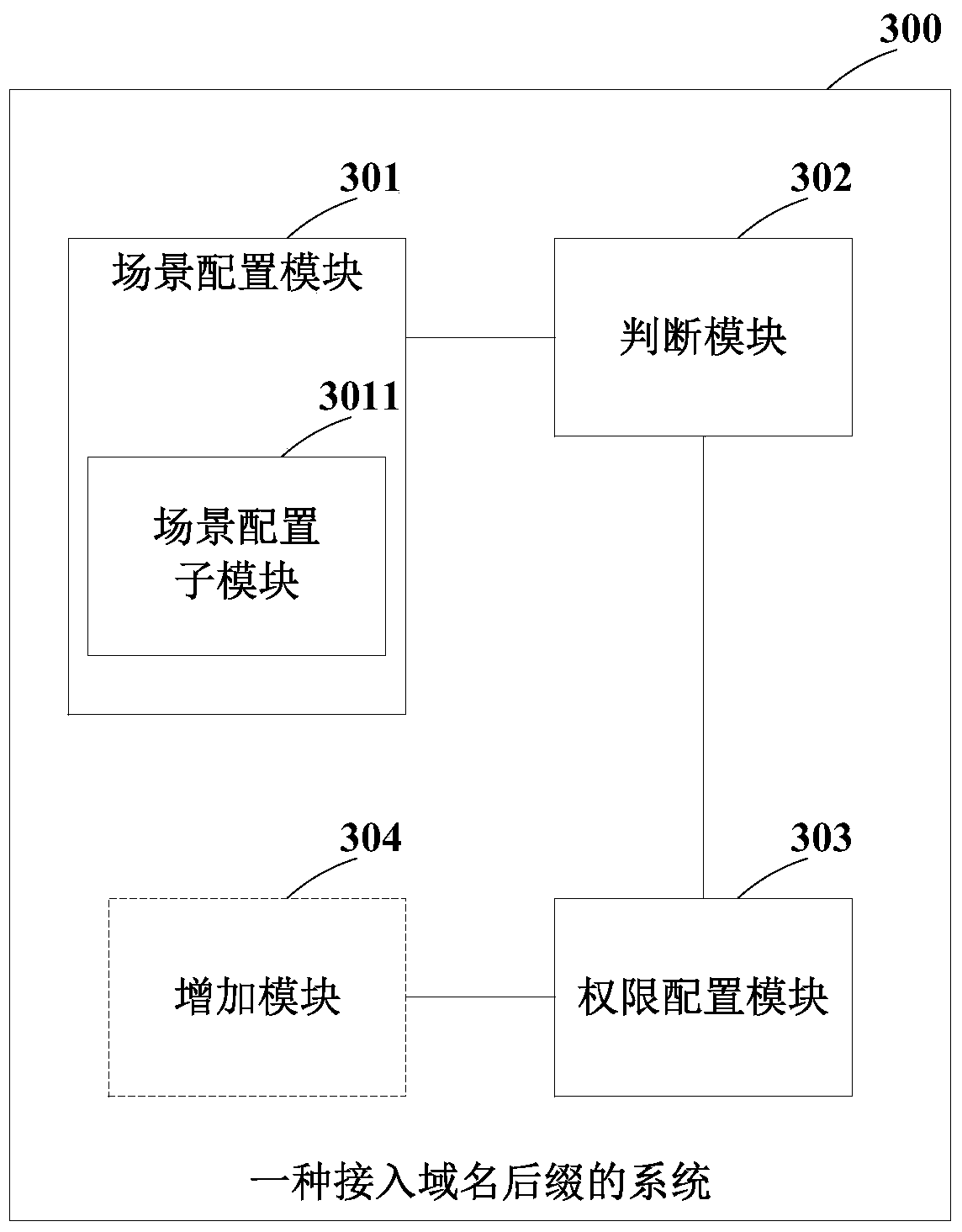
Domain name suffix inputting method and system
The invention discloses a domain name suffix inputting method and system. The method comprises that according to a domain name parameter of a domain name suffix, different application scenes are configured; whether a domain name service that matches the application scene exists in a preset domain name service list is determined; and if YES, the authority of the application scene in the domain name service is configured. According to the method, the process of inputting the new domain name suffix can be simplified, and the efficiency of inputting the new domain name suffix is improved.
Owner:ALIBABA GRP HLDG LTD
Mapping method for data collected by automatic safety device and EMS system primary equipment model
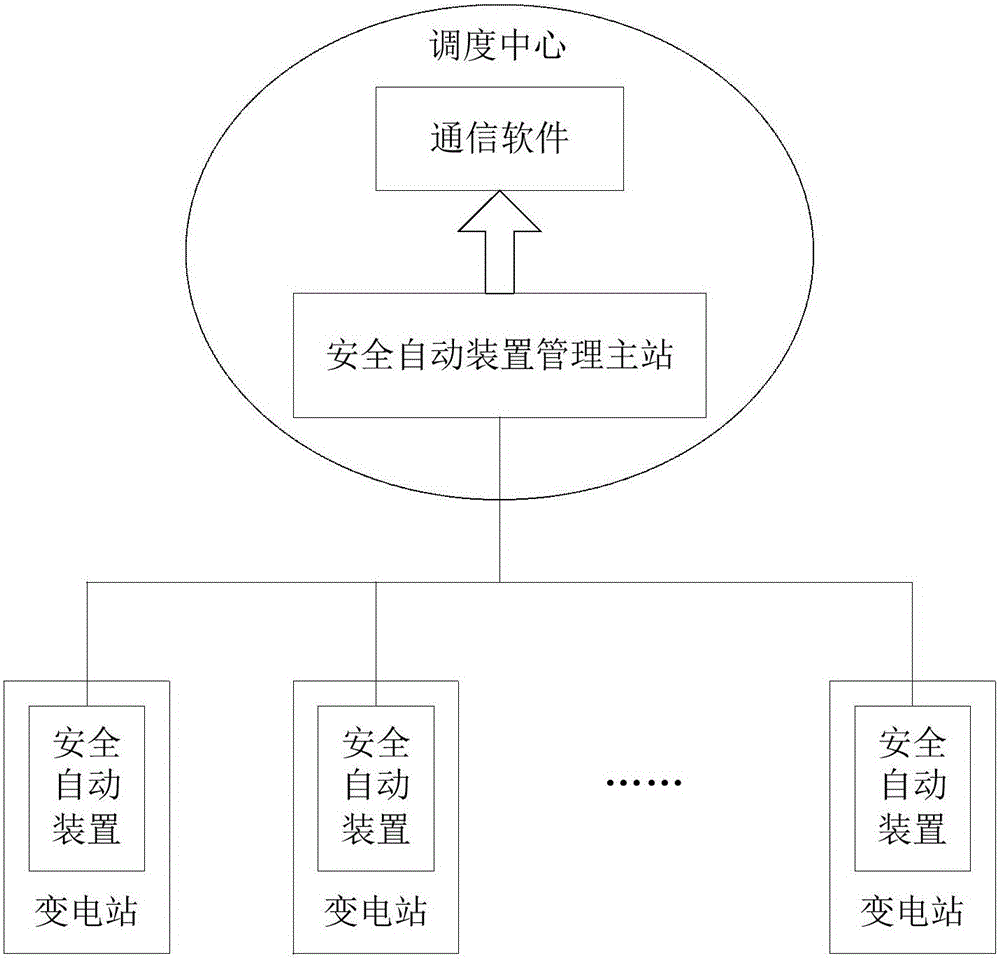
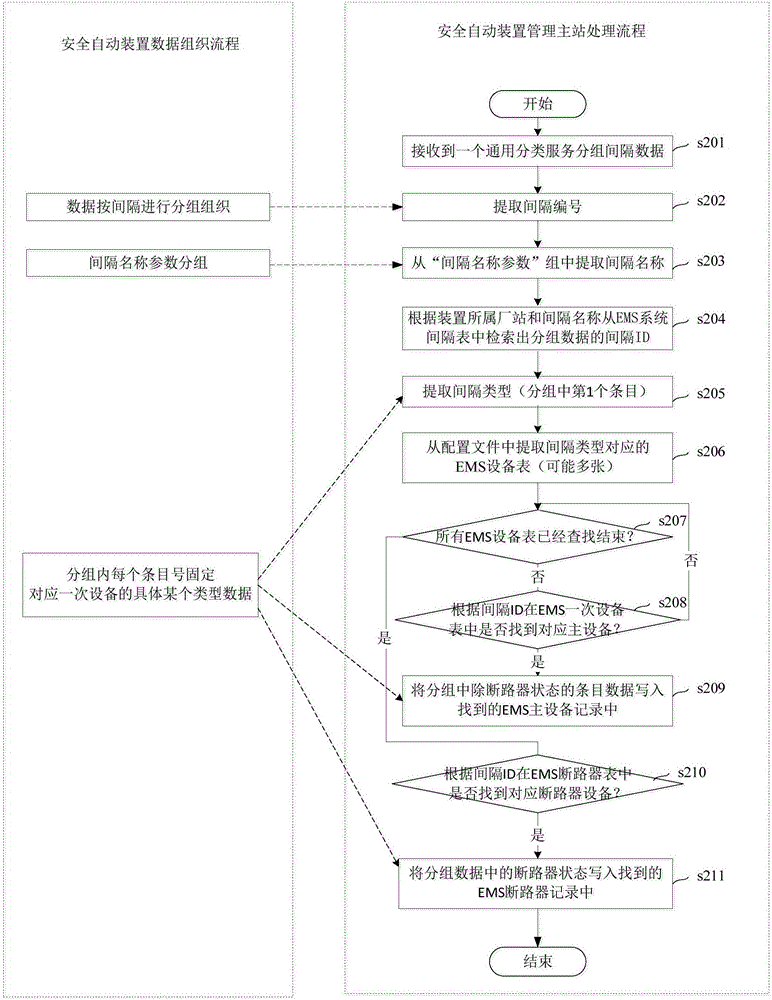
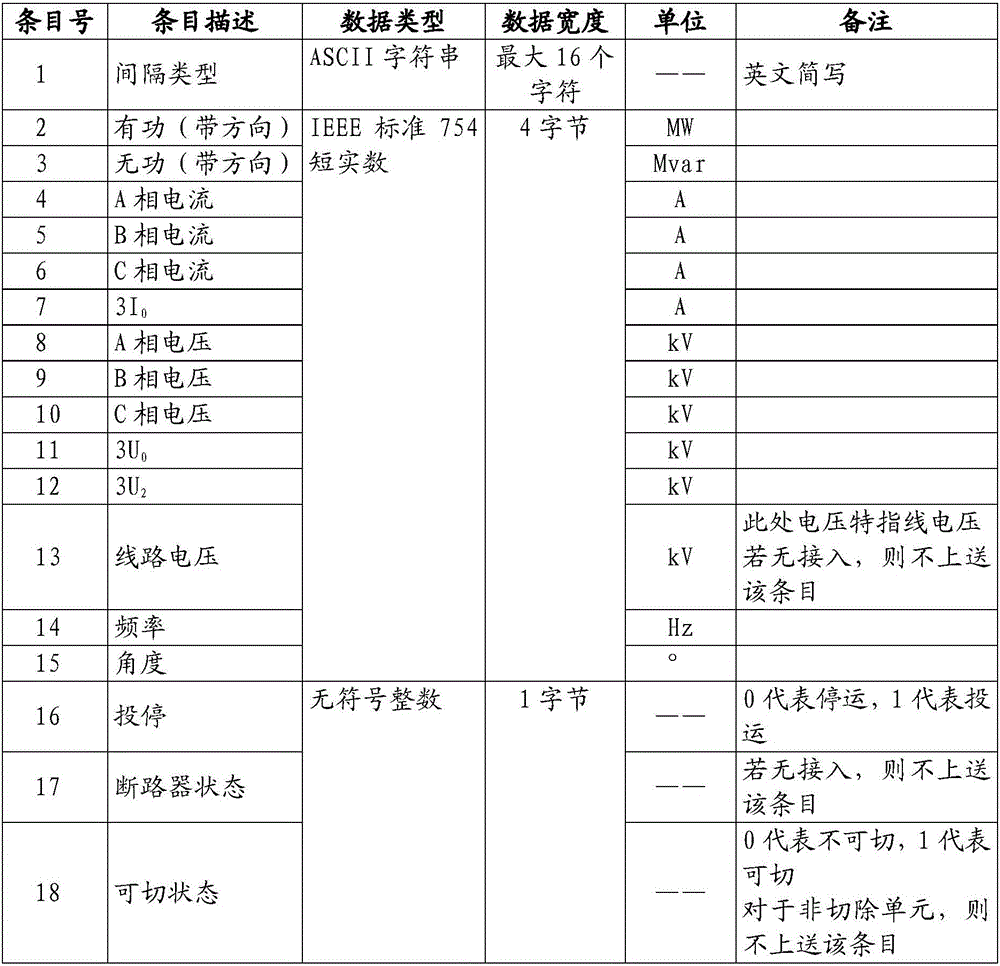
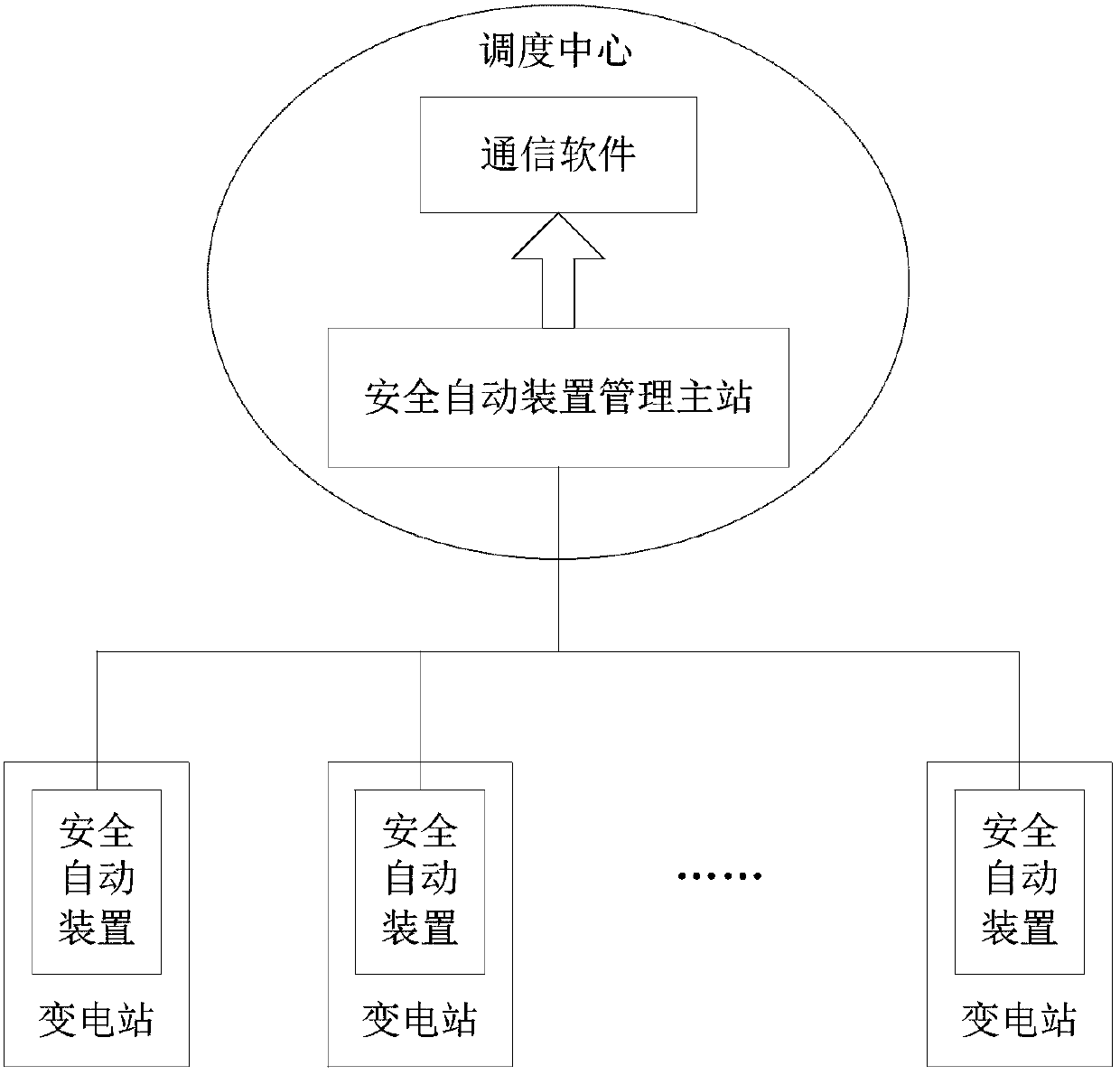
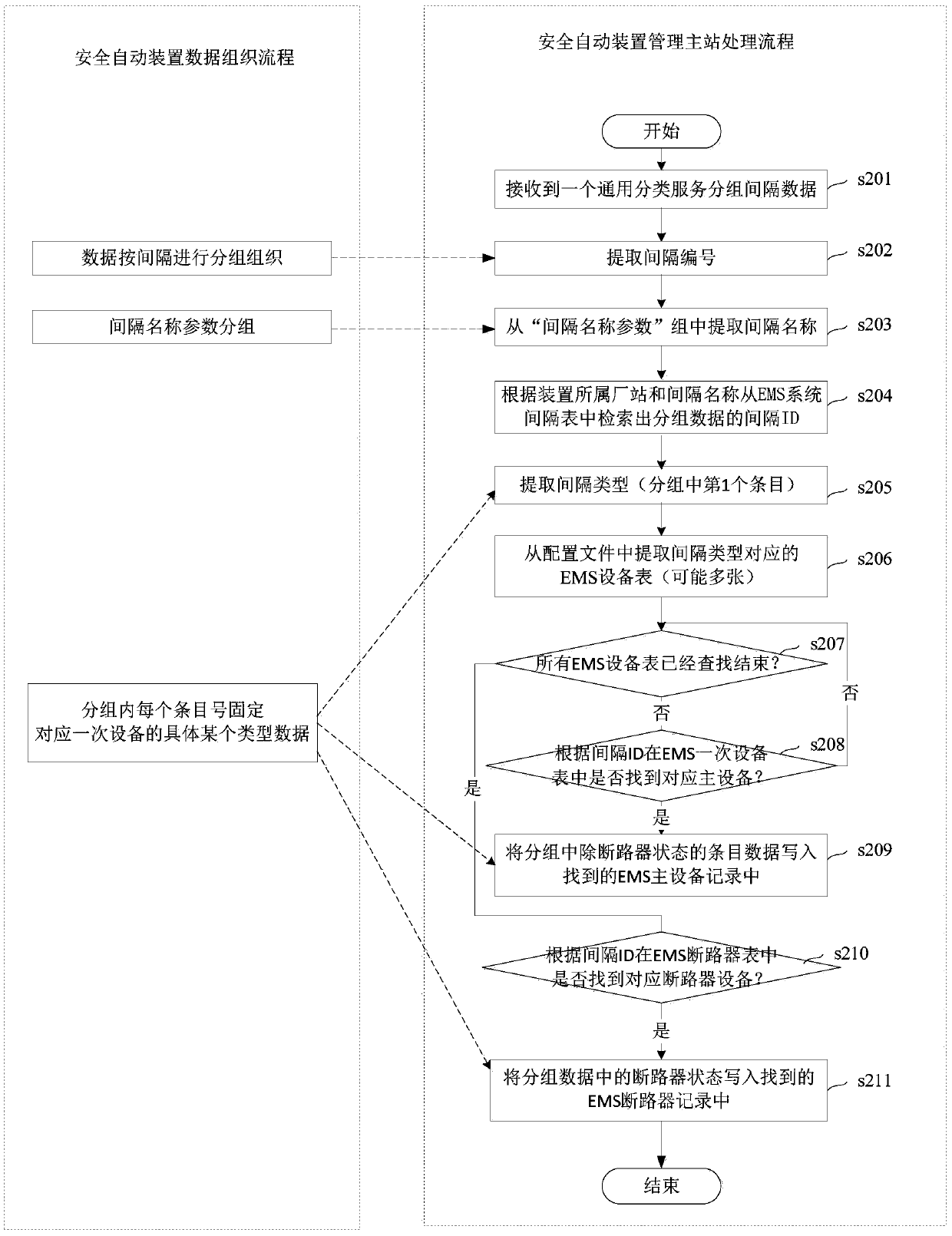
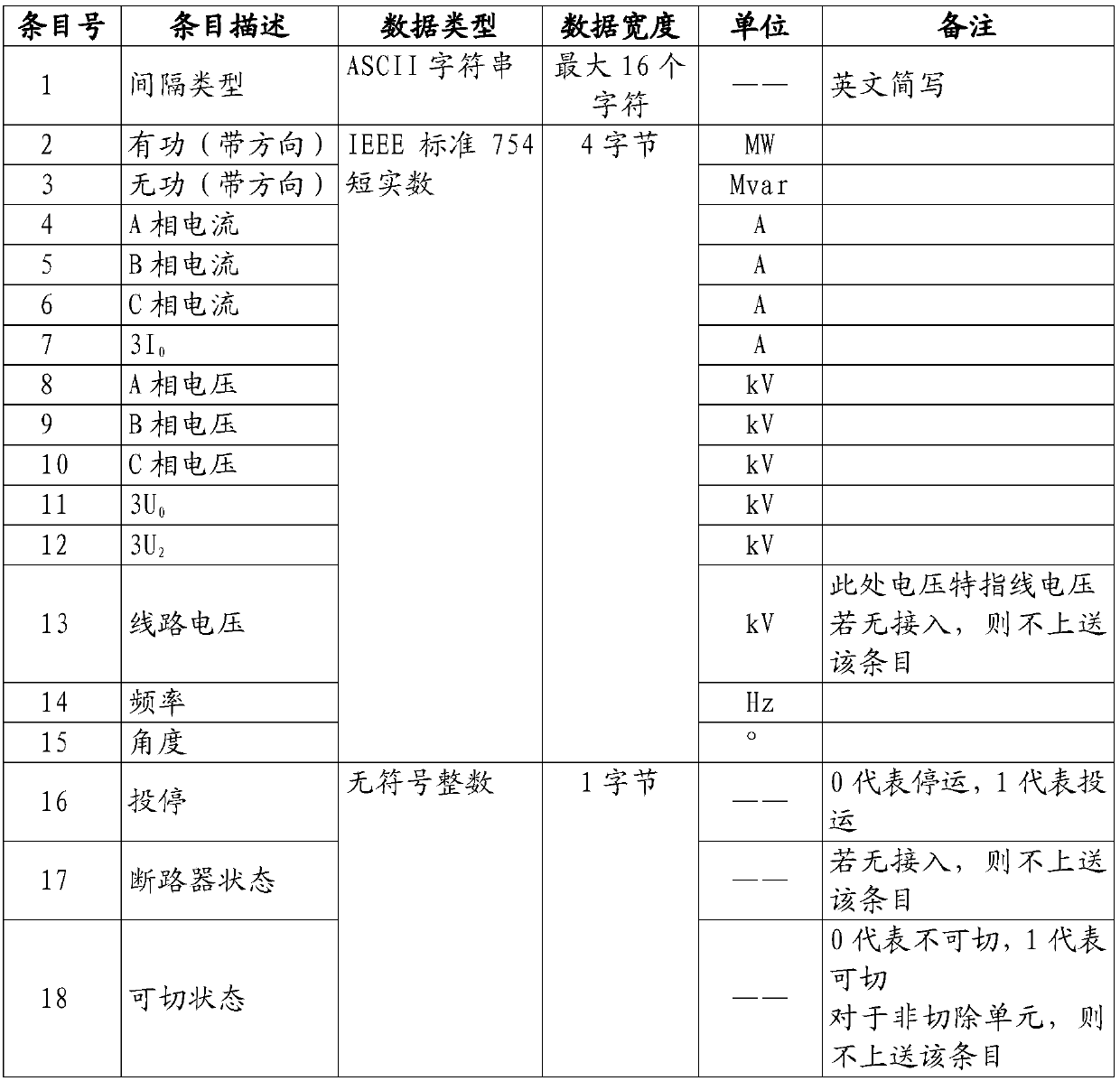
ActiveCN106202814AImprove maintenance efficiencyImprove accuracyDesign optimisation/simulationSpecial data processing applicationsElectric power systemCommunications software
The invention relates to a mapping method for data collected by an automatic safety device and an EMS system primary equipment model. The mapping method comprises the steps that the automatic safety device collects real-time operating data of primary equipment, and grouping organization is carried out in an electrical power system interval mode; the data is placed in a universal classification service group structure to be uploaded to a management master station of the automatic safety device; the management master station receives interval data of universal classification service groups through communication software, and interval serial numbers are extracted from group names; the interval name parameter groups are searched for interval dispatching names corresponding to the interval serial numbers, the EMS module is searched for corresponding interval IDs according to the interval dispatching names in a matching mode, the primary equipment in the EMS model is positioned according to the interval types included in the interval data groups and the interval IDs, and the values of fixed items in the real-time operating data are written in an attribute domain corresponding to the primary equipment in the EMS model. The accuracy of the data corresponding relationship is improved on the premise of improving data maintenance efficiency.
Owner:POWER DISPATCHING CONTROL CENT OF GUANGDONG POWER GRID CO LTD
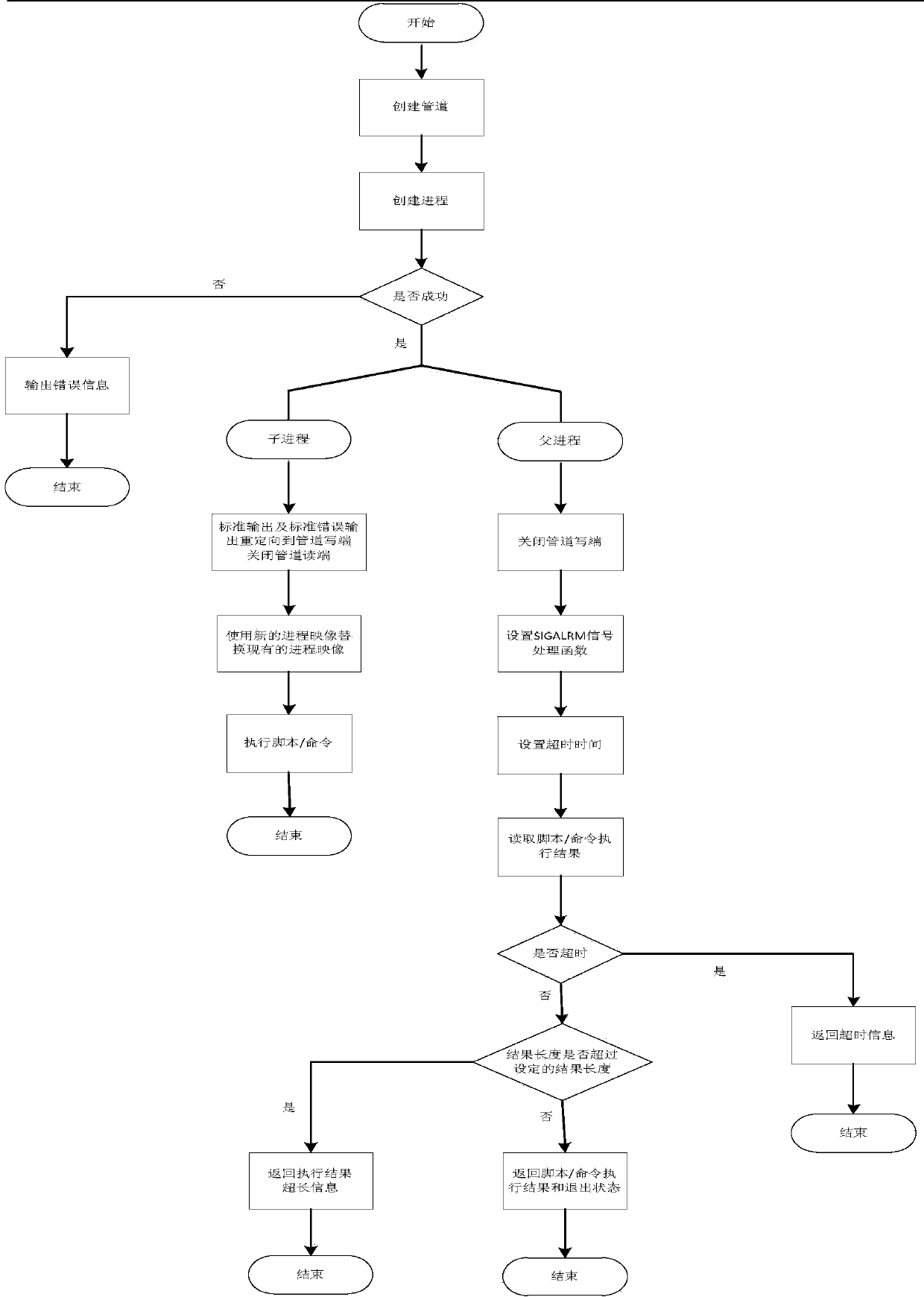
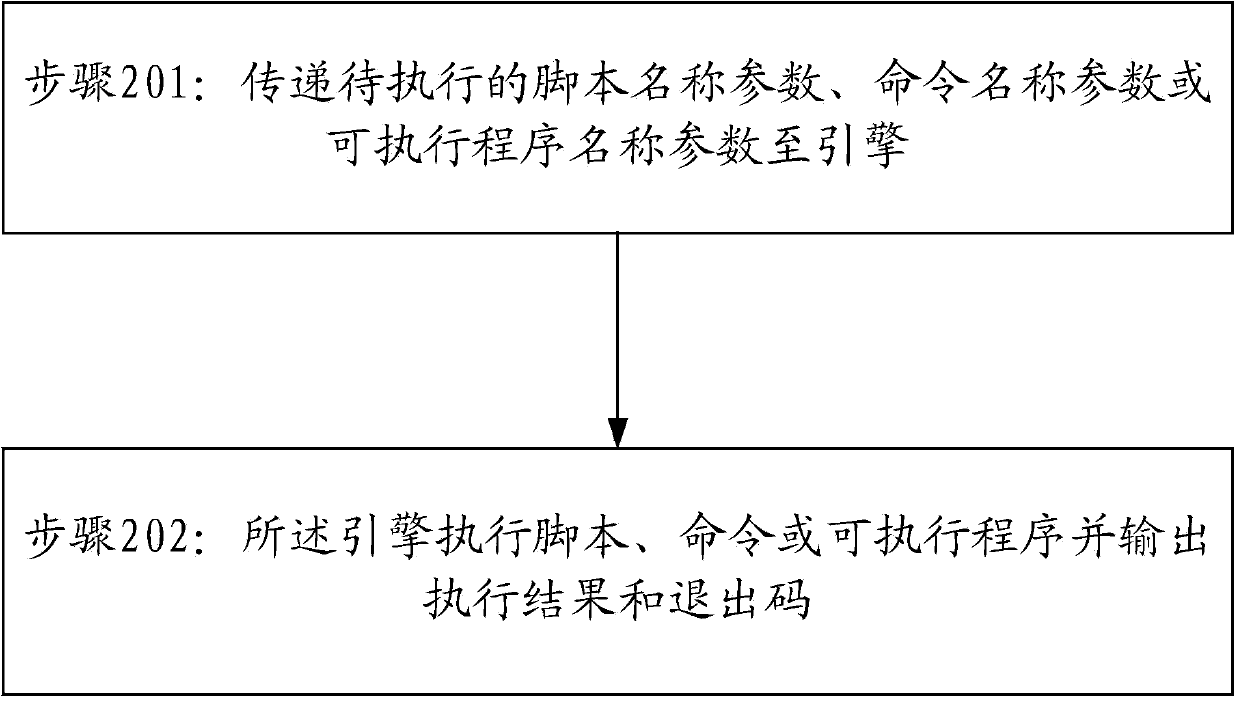
Engine and method for executing scripts and commands based on Linux pipeline technology
InactiveCN103744675AExecutive controlInterprogram communicationSpecific program execution arrangementsGNU/LinuxComputer software
The invention provides an engine and a method for executing scripts and commands based on a Linux pipeline technology. The engine and the method are applied to the field of computer software. The method comprises the following steps: transmitting name parameters of scripts and commands to be executed or name parameters of executable programs to the engine; executing the scripts, commands or the executable programs by the engine and outputting execution results and exit codes. Due to the implementation of the engine and the method, more accurate control of the execution of the scripts, commands or the executable programs can be realized.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
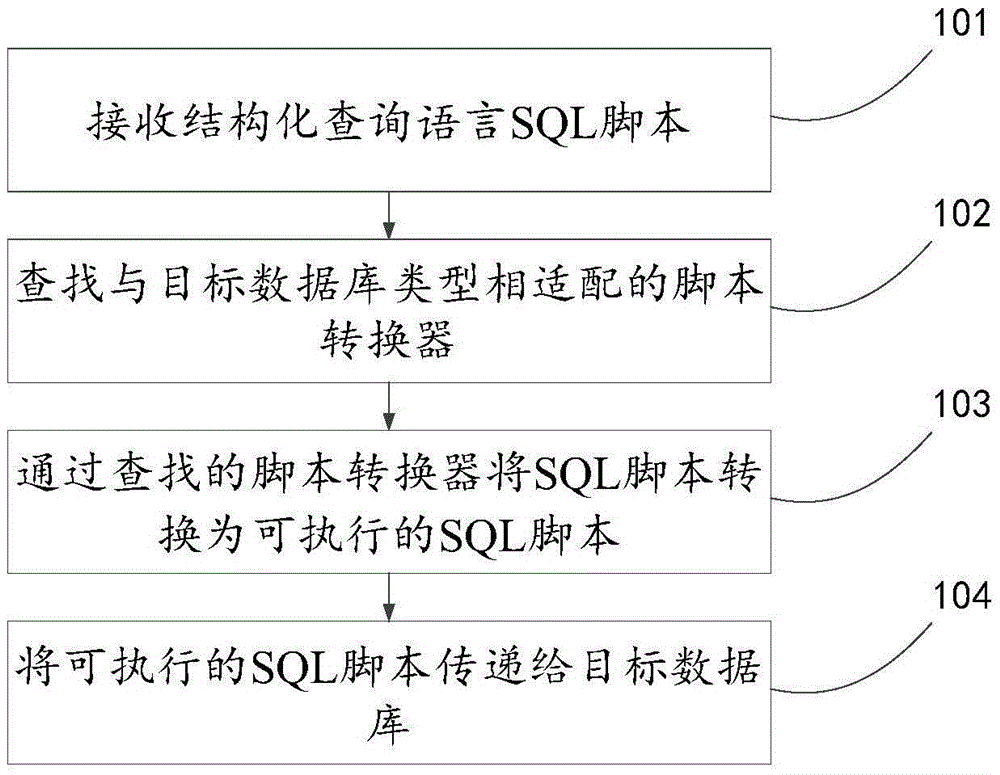
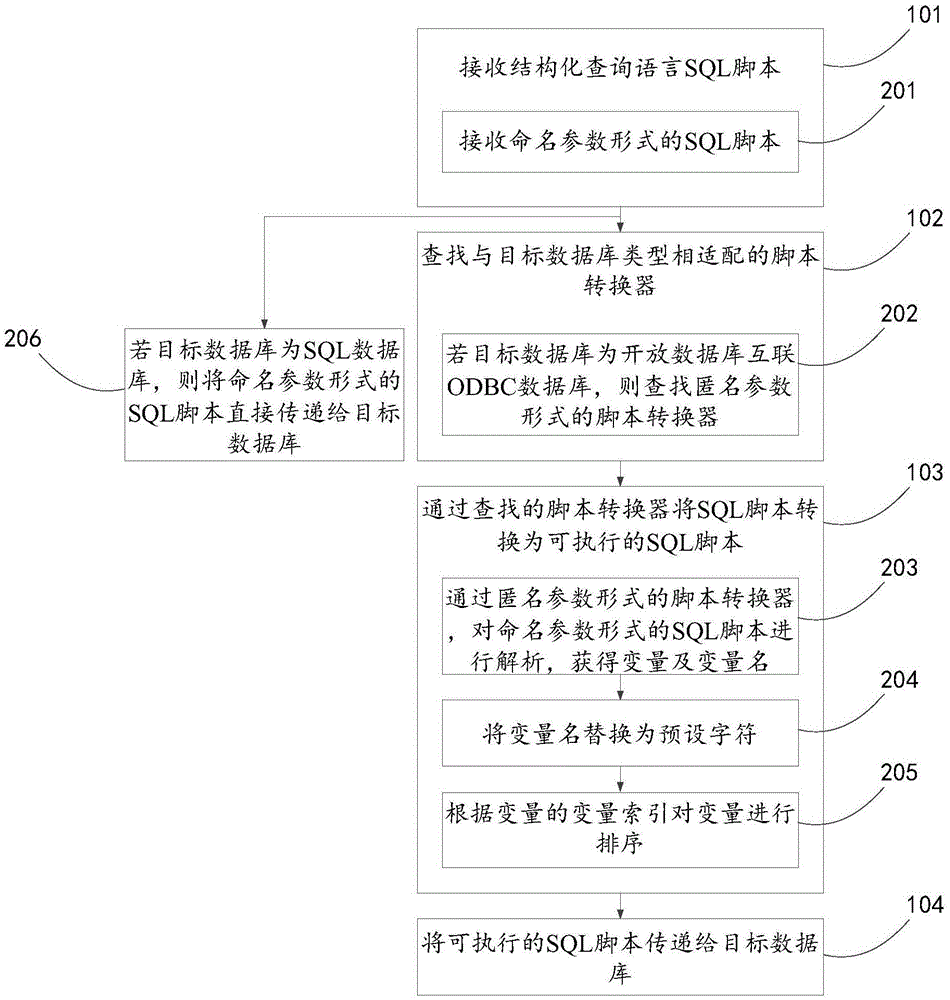
Database query method and device
InactiveCN106802901AReduce development costsSpecial data processing applicationsThe InternetData query
The invention discloses a database query and a device, which relates to the network field, the invention is provided to solve the problem of the higher compatible cost between the SQL database and ODBC database. The method comprises the following steps receiving structured query language SQL script, the SQL script carries change quantity for data query; querying script convertor matching with object database type; converting the SQL script into the executable SQL scrip through the script convertor queried, the executable SQL script is that transfer parameter is consistent with target data type; transferring the executable SQL script to the target database to make the target database carry out data query according to the change quantity carried by the executable SQL script. The invention is applied in the process that the SQL script of named reference form is converted into the SQL script of anonymity reference form.
Owner:BEIJING GRIDSUM TECH CO LTD
An interface operation and maintenance method and device
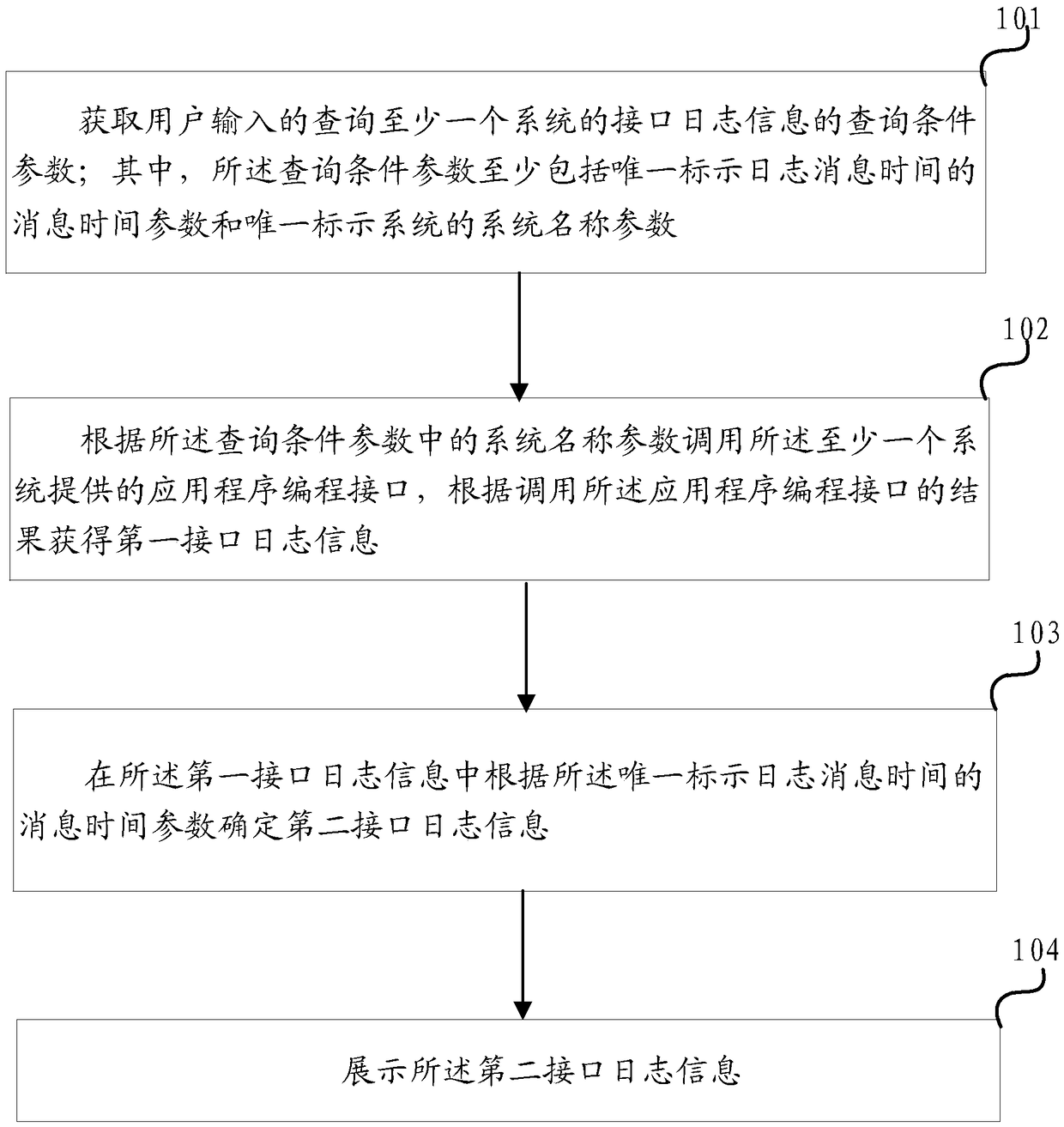
ActiveCN109408337AImprove efficiencyShorten the timeHardware monitoringProgram controlUser inputApplication programming interface
The invention discloses an interface operation and maintenance method and device. The method comprises the steps that query condition parameters input by a user and used for querying interface log information of at least one system are acquired, wherein the query condition parameters at least comprise a message time parameter uniquely indicating log message time and a system name parameter uniquely indicating a system; calling an application programming interface provided by the at least one system according to a system name parameter in the query condition parameters, and obtaining first interface log information according to a result of calling the application programming interface; determining second interface log information in the first interface log information according to the message time parameter uniquely indicating the log message time; and displaying the second interface log information. By applying the method and the device provided by the invention, the operation and maintenance efficiency of the system interface can be improved.
Owner:BOE TECH GRP CO LTD
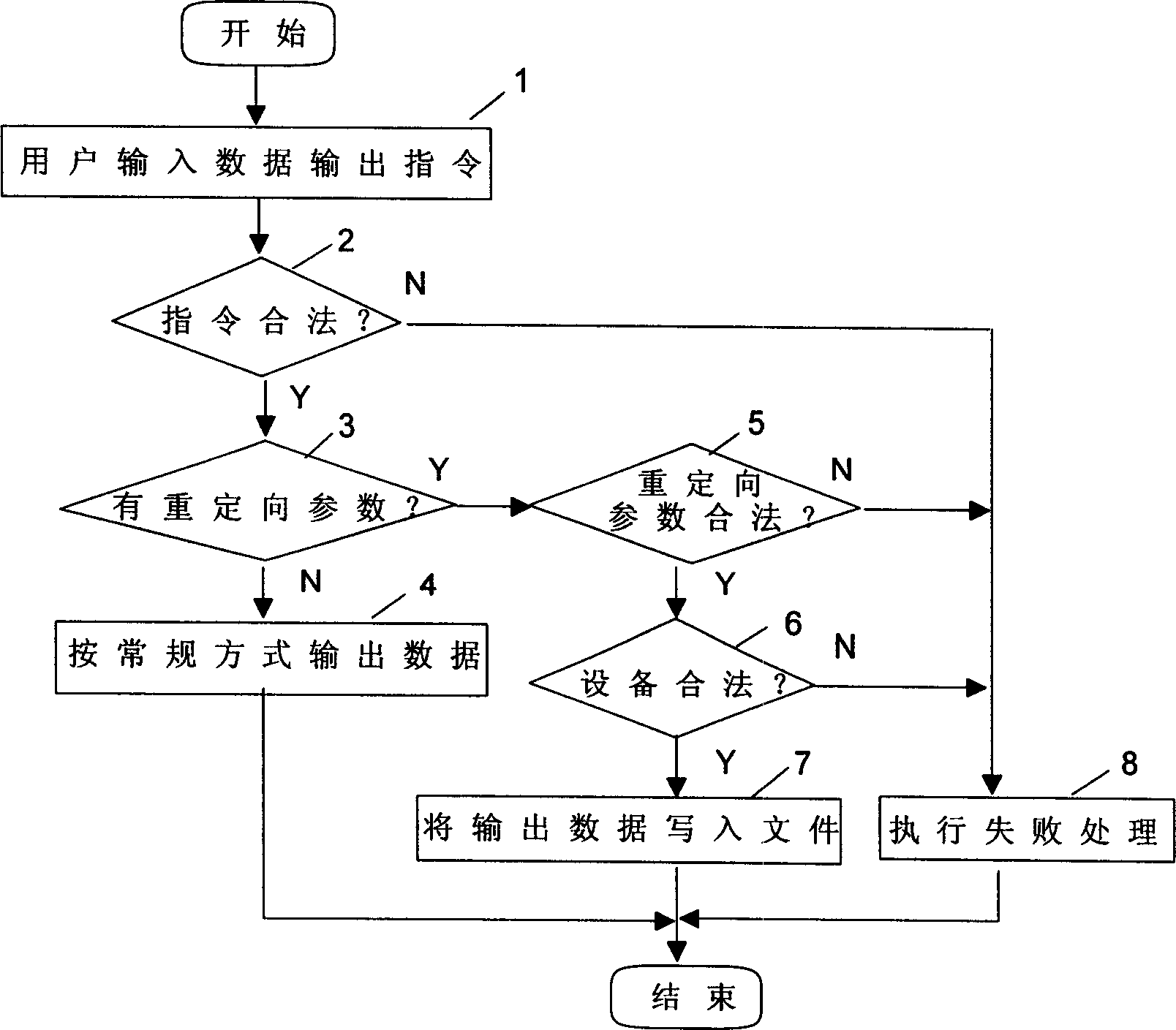
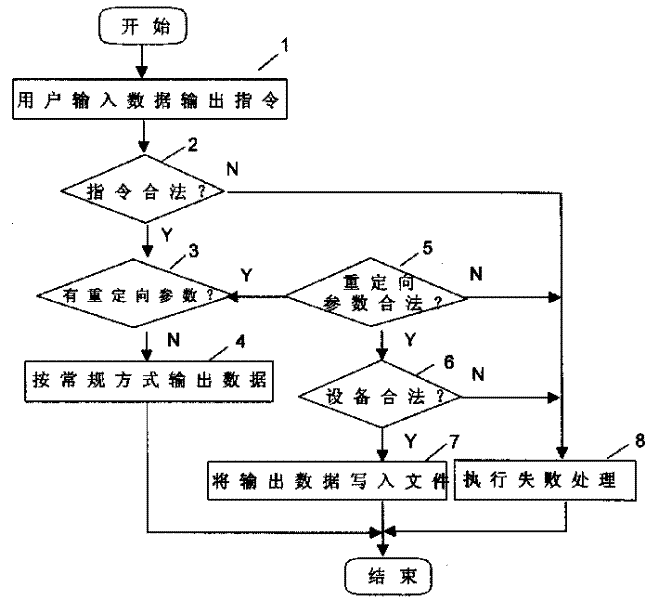
Method of realizing communication equipment output reorientation
This invention discloses a method for realizing redirecting to communication equipment output. The method is to add key words and paper name parameter of redirection in data output order of communication equipment and when data output orders forwarding to communication equipment by users have legal output redirectional parameters, the communication equipment order process modulewill store the output data into the redirectional labeled papers provided in the order while can guarantee the completion of real time and flexibility of communication equipment output data to resolve the problem of real time data storage.
Owner:HUAWEI TECH CO LTD
Method of advertisement placement in process of APP downloading
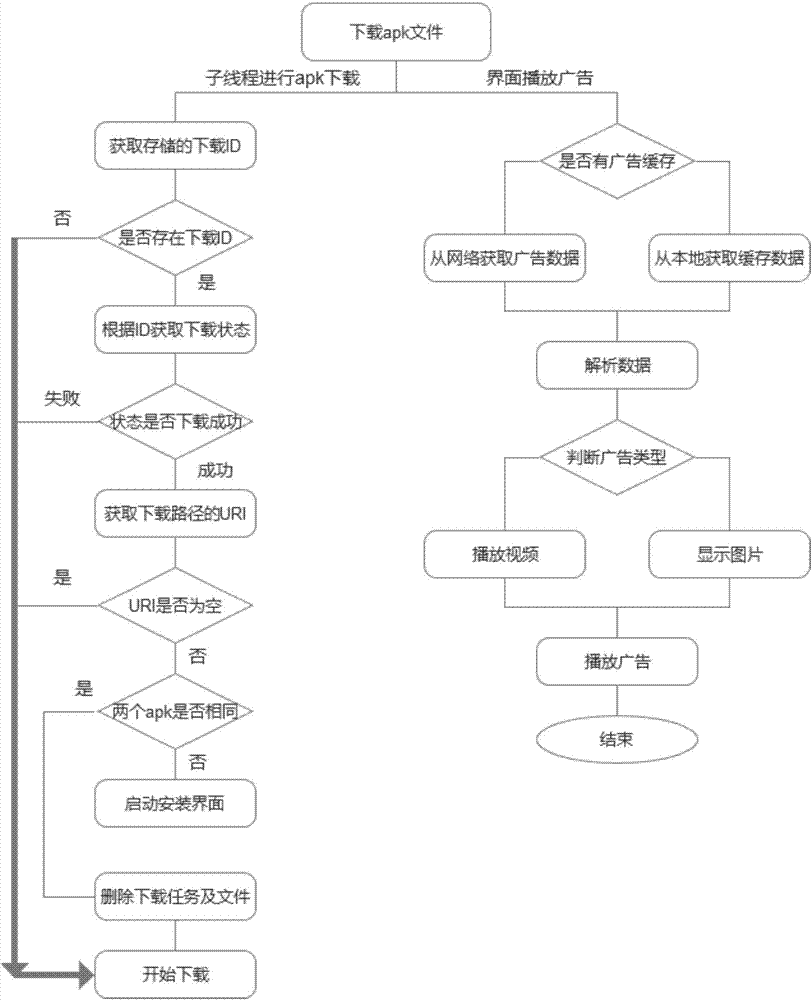
InactiveCN107172491ASignificant rise in temperatureIncrease reachAdvertisementsSelective content distributionApp storeComputer terminal
Provided is a method of advertisement placement in the process of APP downloading. When a user clicks an APK of a television terminal to upload an APP from a downloading manager of the television terminal or upgrade the version of an APP, an SDK at the user side receives an URL for upgrade, the title of an APK needing to be uploaded or upgraded, and APP name parameters, and the television terminal calls the SDK at the user side to download an APP. According to the method of advertisement placement in the process of application downloading, in the process of APP downloading by users in a television APP store, high-quality advertising content is pushed to users waiting for the completion of downloading to make users feel less anxious and irritable, and advertising stops automatically at the end of APP downloading. Therefore, advertisements are pushed to users without forcibly occupying the time of users. Advertising is more moderate. The reach rate of advertisements is increased.
Owner:FUTURE TV CO LTD
Diameter flooding attack detection device and method
ActiveCN109040127AImprove securityData switching networksCommunications securityMobile communication network
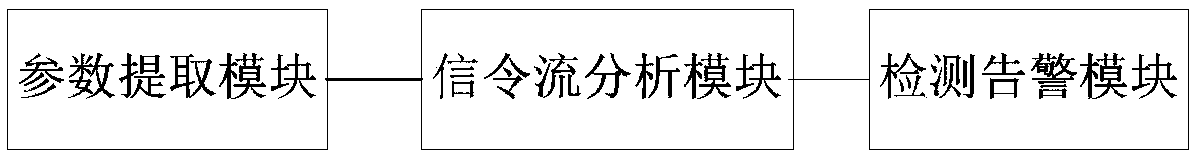
The invention belongs to the technical field of communication security, in particular to a Diameter flooding attack detection device and method, The device comprises a parameter extracting module, which is used for extracting the signaling message parameters flowing through the signaling, and matching the state machine according to the parameters, wherein the signaling message parameters include the session identification parameters, the source host parameters and the user name parameters, and setting and initializing each signaling message parameter counter, a signaling flow analysis module which is used for early warning analysis of the signaling message parameters in the signaling according to the state machine matching condition and using the counter count value, a detection alarm module which is used for flooding attack alarm according to the warning analysis result of the signaling message parameters. The invention is applicable to an IMS network in a mobile communication network, security detection and early warning of Diameter flooding attacks are implemented, Automatic identification and detection of Diameter flooding attacks are performed based on IMS signaling flows, detection and early warning of Diameter flooding attacks are detected and early warned from signaling flows, thus improving IMS network security and having important guiding significance for the securityof communication networks.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
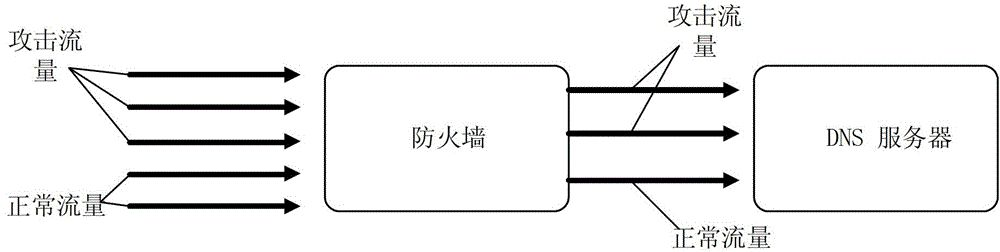
Game plug-in behavior monitoring method based on DNS flow characteristics
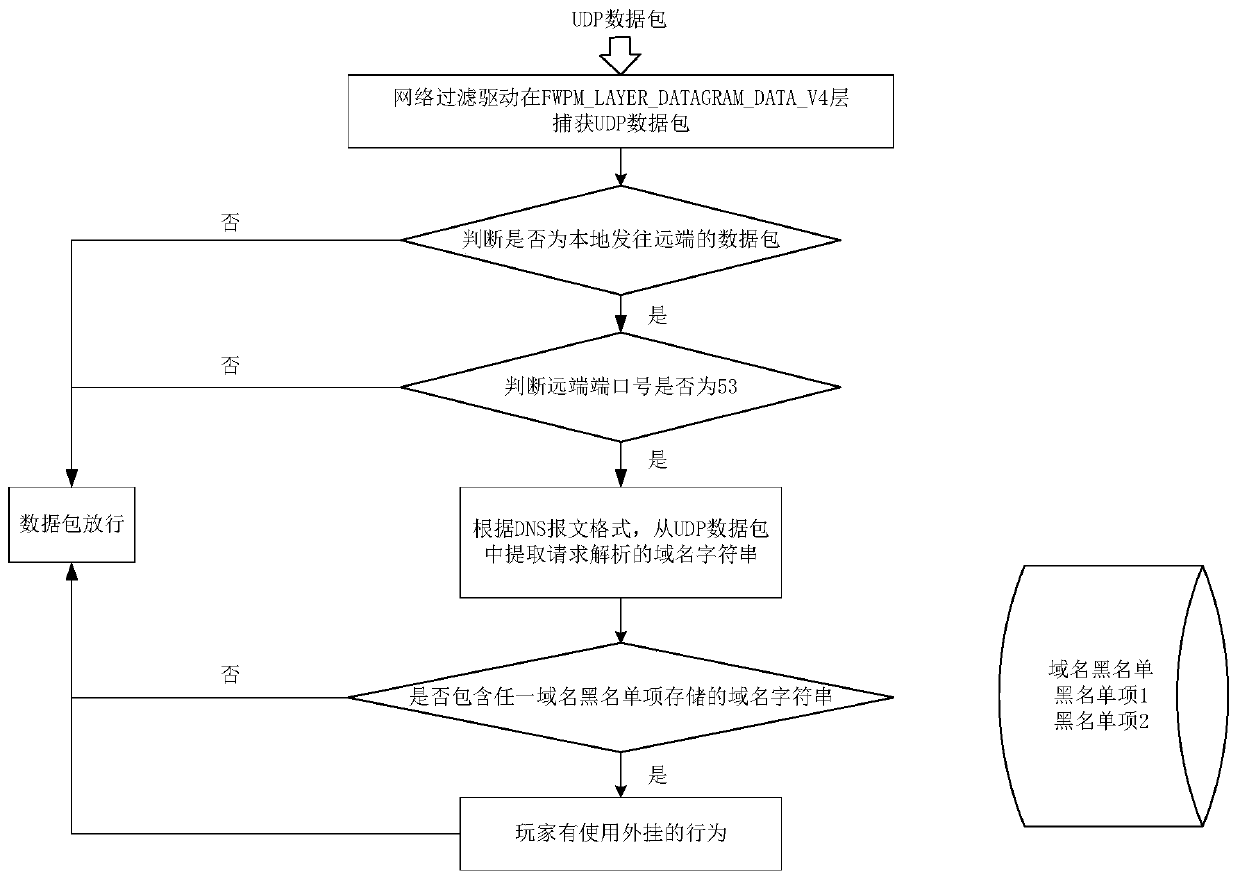
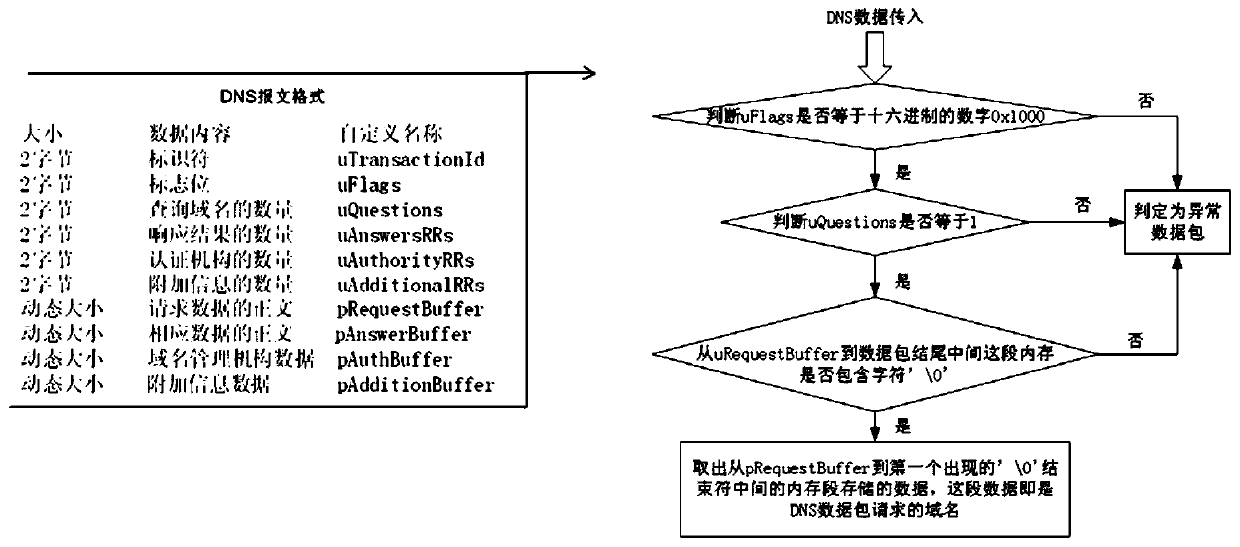
ActiveCN110535719AMonitor usage behaviorEasy to detectData switching networksTraffic capacityDomain name
The invention provides a game plug-in behavior monitoring method based on DNS flow characteristics. The method comprises the following steps that S1, enabling a client of a Windows system applicationlayer to create a network filtering drive on a drive layer; S2, establishing a domain name blacklist; S3, capturing all UDP data packets in a data packet layer by the network filtering driver, comparing a domain name parameter requested to be analyzed by the UDP data packet with the domain name blacklist for judgment, if the domain name parameter is any domain name character string contained in the domain name blacklist, judging that the game player has a plug-in use behavior, and enabling the domain name blacklist to store the domain name character string requested to be analyzed by the plug-in. According to the invention, the plug-in use behavior of the known DNS flow characteristics can be efficiently monitored.
Owner:福建天晴在线互动科技有限公司
Method and system for data migration
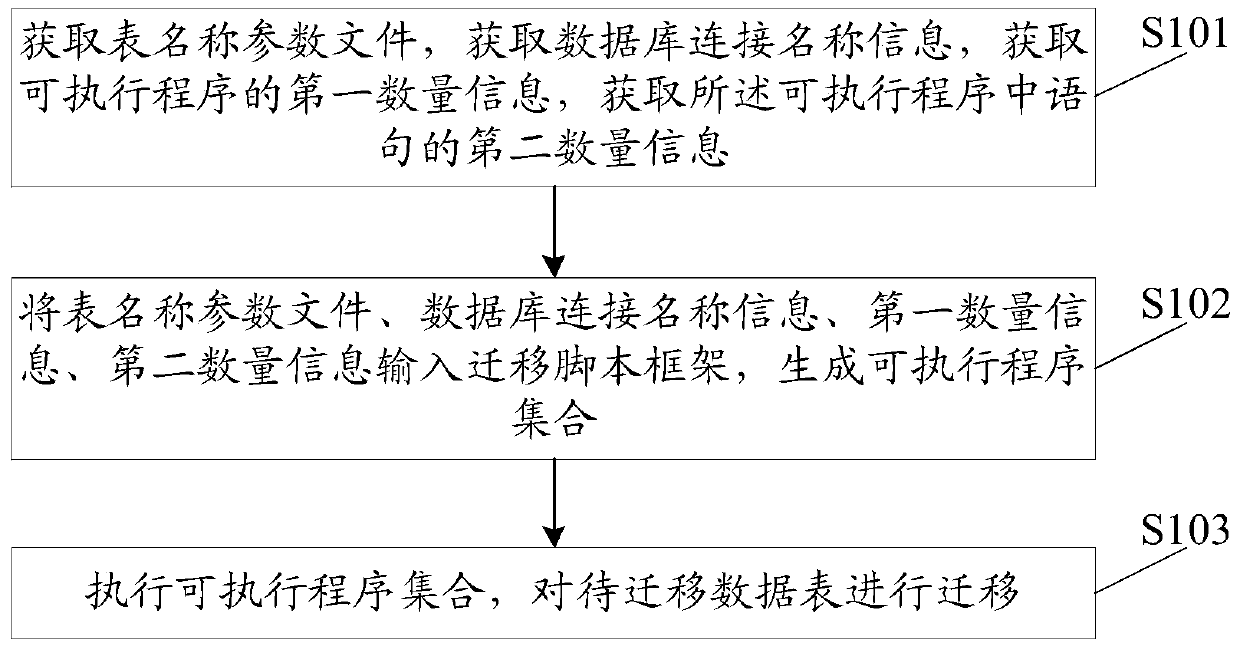
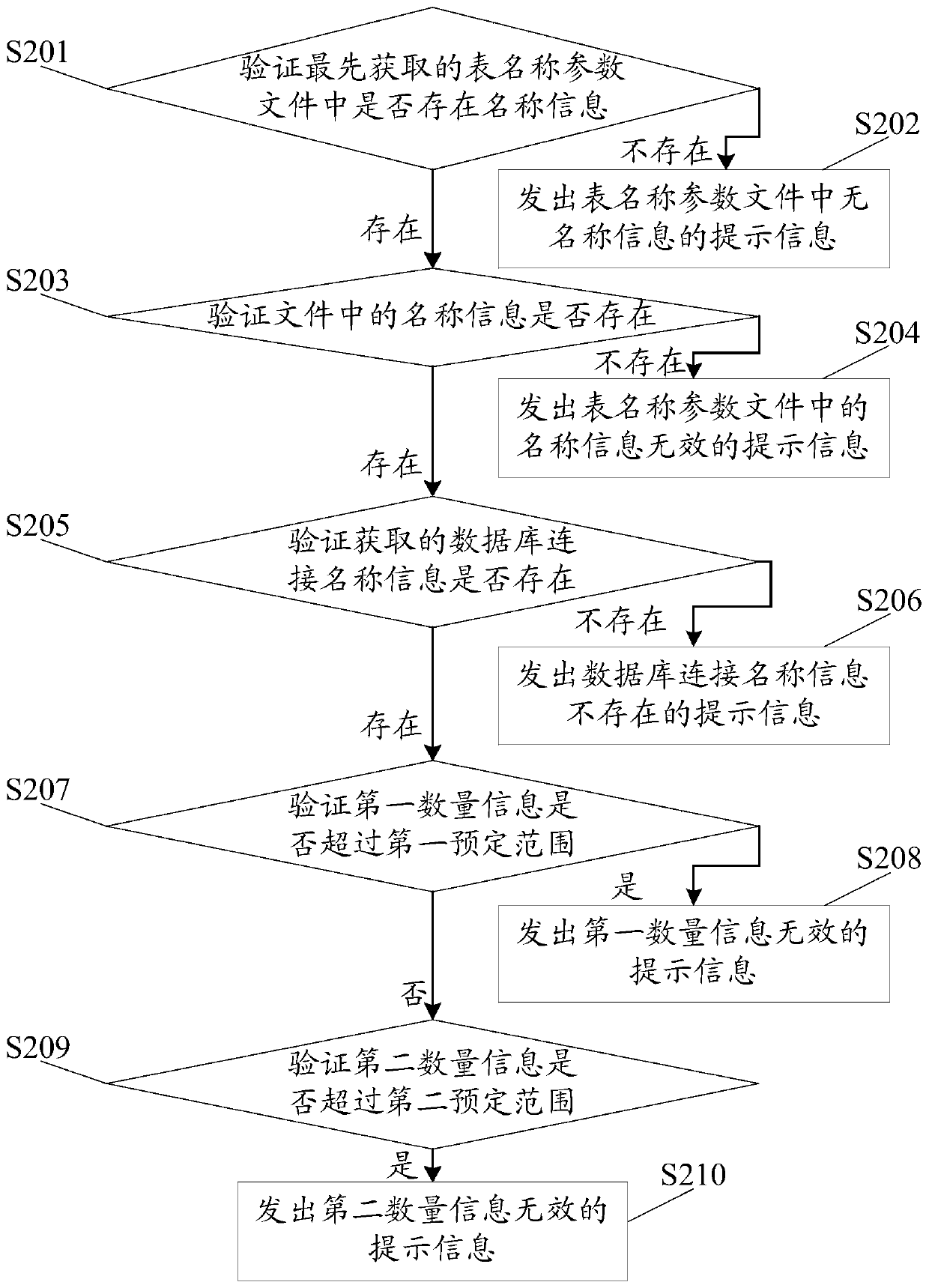
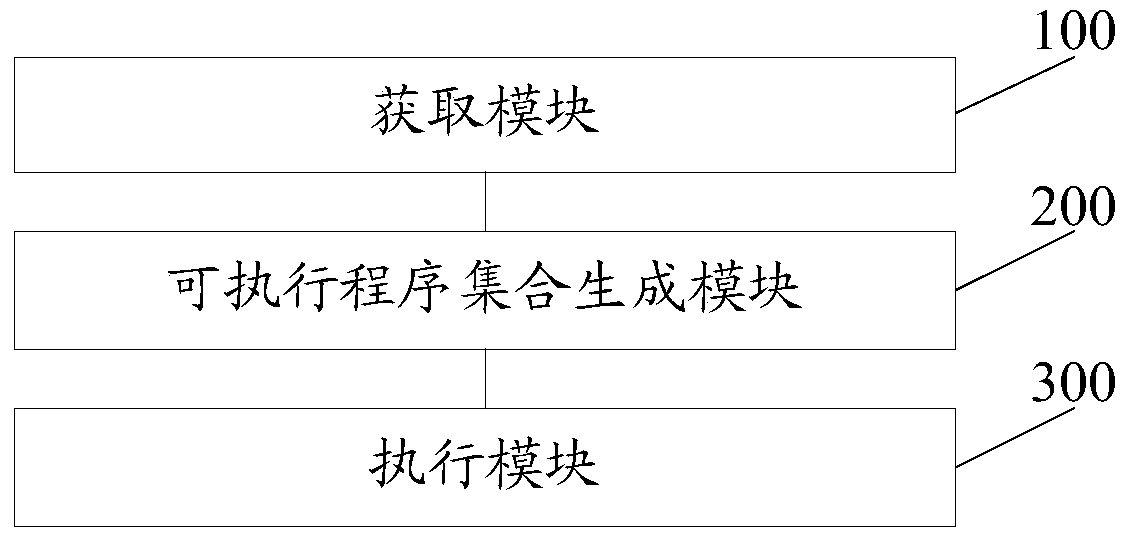
ActiveCN105956191BImprove integrityImprove accuracyRelational databasesSpecial data processing applicationsDatabase connectionNamed parameter
The invention discloses a data migration method. The method comprises the steps of when data in a database is migrated, inputting migration parameters required for data migration into a programmed migration script framework; automatically generating a corresponding number of executable program sets according to the migration parameters; and migrating the data by running the executable program set, so that the problem of repetition, omission, errors or the like caused by manual execution of a migration process is reduced, the efforts of engineers are released, the migration process and a result are concerned, and the working efficiency and the data migration integrity and accuracy are improved, wherein the migration parameters are a table name parameter file, database connection name information, first quantity information of executable programs and second quantity information of statements in the executable programs. The invention furthermore discloses a data migration system, which can achieve the technical effect as well.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
Method and device for detecting data message
ActiveCN102984178BAccurate identificationEffective and efficient cleaningData switching networksTraffic capacityDomain name
The invention discloses a detection method and a device for a data message. The method comprises a detection method of the data message. The method comprises the following steps: reading the domain name parameter of a received first data message; performing a random degree calculation to the domain name parameter of the first data message and a preset domain name parameter to obtain a random degree score of the domain name parameter of the first data message, wherein the preset domain name parameter is a domain name parameter of a preset valid data message; judging if the random degree score is more than a blocking threshold; and determining the first data message to be an invalid data message when the random degree score is more than the blocking threshold. According to the detection method, accurately identifying the invalid data message is achieved, so that the invalid data message can be processed from a flow of all DNS (Domain Name Server) random requests, the invalid data message of the DNS random requests can be effectively and efficiently cleaned, and a DNS random request attack loses a DDOS (Distributed Denial of Service) effect.
Owner:HILLSTONE NETWORKS CO LTD +1
Method for rapidly executing previous command and replacing named parameters
InactiveCN107562441AGet the specified parametersGet replacement valueMachine execution arrangementsUser inputComputer science
The invention provides a method for executing a previous command and replacing named parameters and relates to the technical field of running and maintenance. By adopting the method, the previous executed command can be automatically acquired, and meanwhile two parameters of a named parameter and a replaced parameter input by a user can be acquired; through traversal of the previous executed command, the named parameter is replaced by the replaced parameter, and then the whole command is executed. When contextual management operation maintenance work is conducted, the method can remarkably improve the working efficiency.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
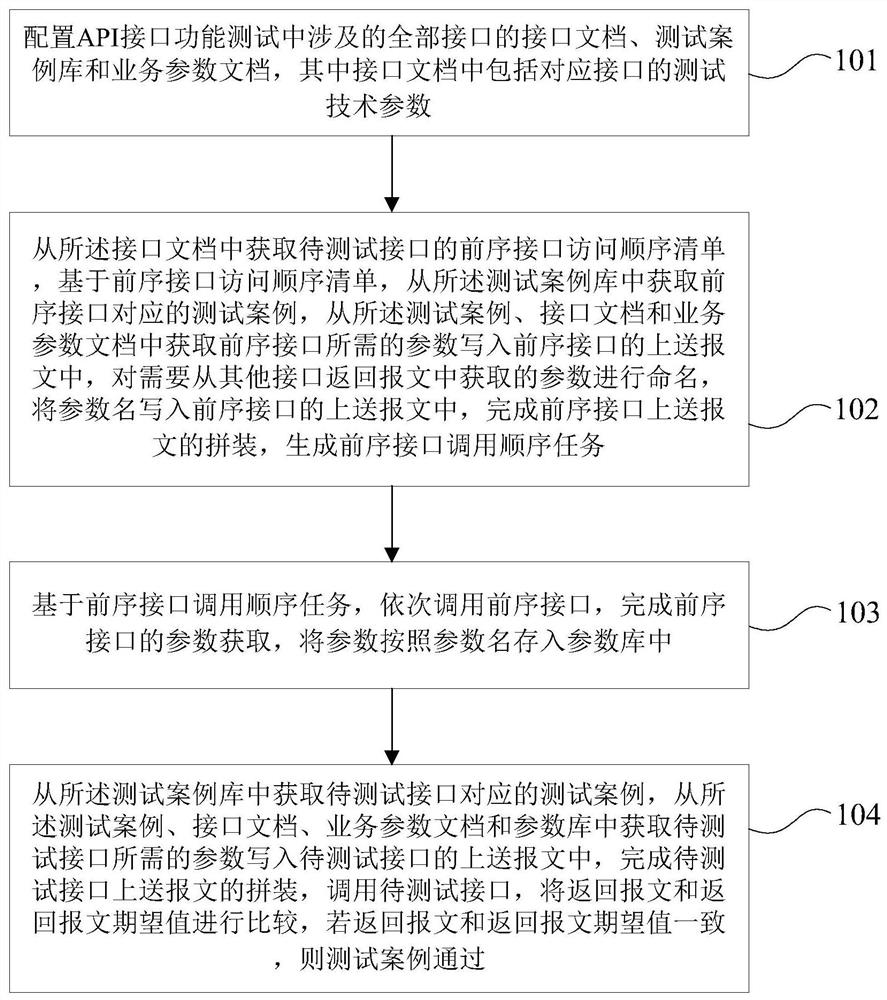
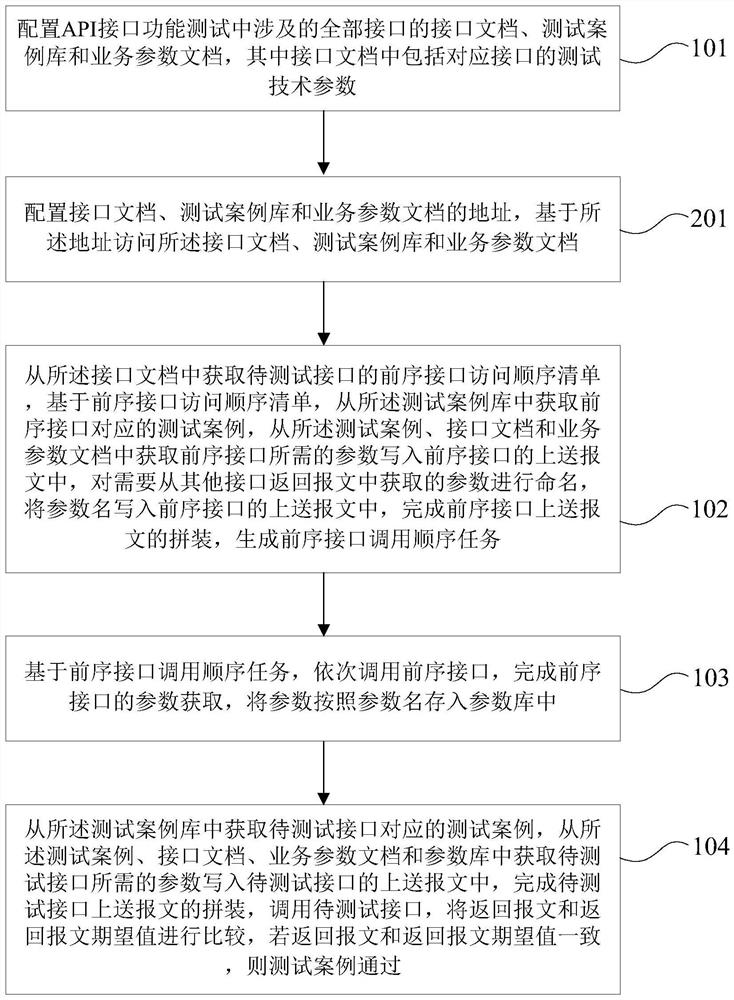
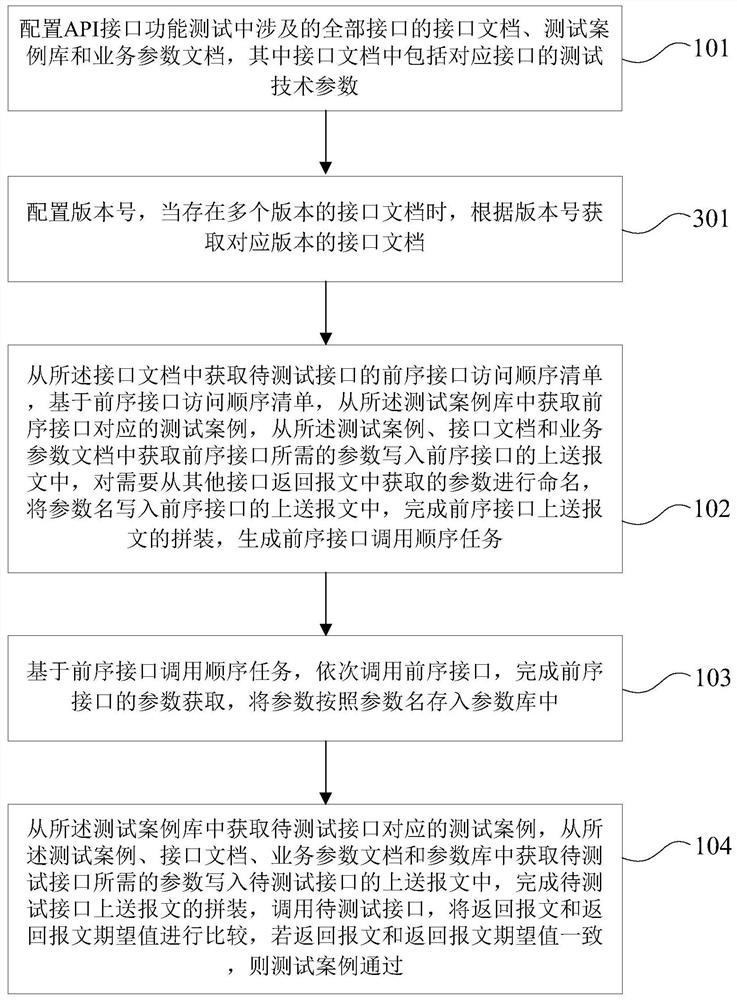
Method and device for automatically testing full-process scene of interface
PendingCN113360415ASolve the problem of interface full-process test automationSoftware testing/debuggingEngineeringHuman–computer interaction
The invention discloses a method and device for automatically testing full-process scene of an interface, and belongs to the technical field of artificial intelligence. The method comprises the steps of: configuring an interface document, a test case library and a business parameter document; obtaining a preorder interface access sequence list of a to-be-tested interface from the interface document, obtaining test cases corresponding to preorder interfaces from the test case library, obtaining parameters required by the preorder interfaces from the test cases, the interface document and the business parameter document, and writing the parameters into a reporting message, naming parameters which need to be acquired from messages returned from other interfaces, and writing parameter names into the reporting message; calling the preorder interfaces in sequence, completing parameter acquisition of the preorder interfaces, and storing the parameters in a parameter library according to parameter names; and acquiring the parameters from the test cases, the interface document, the business parameter document and the parameter library, writing the parameters into the reporting message of the to-be-tested interface, calling the to-be-tested interface, and completing the automatic interface test. According to the method and device of the invention, full-process interface scenarized automatic testing can be realized.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
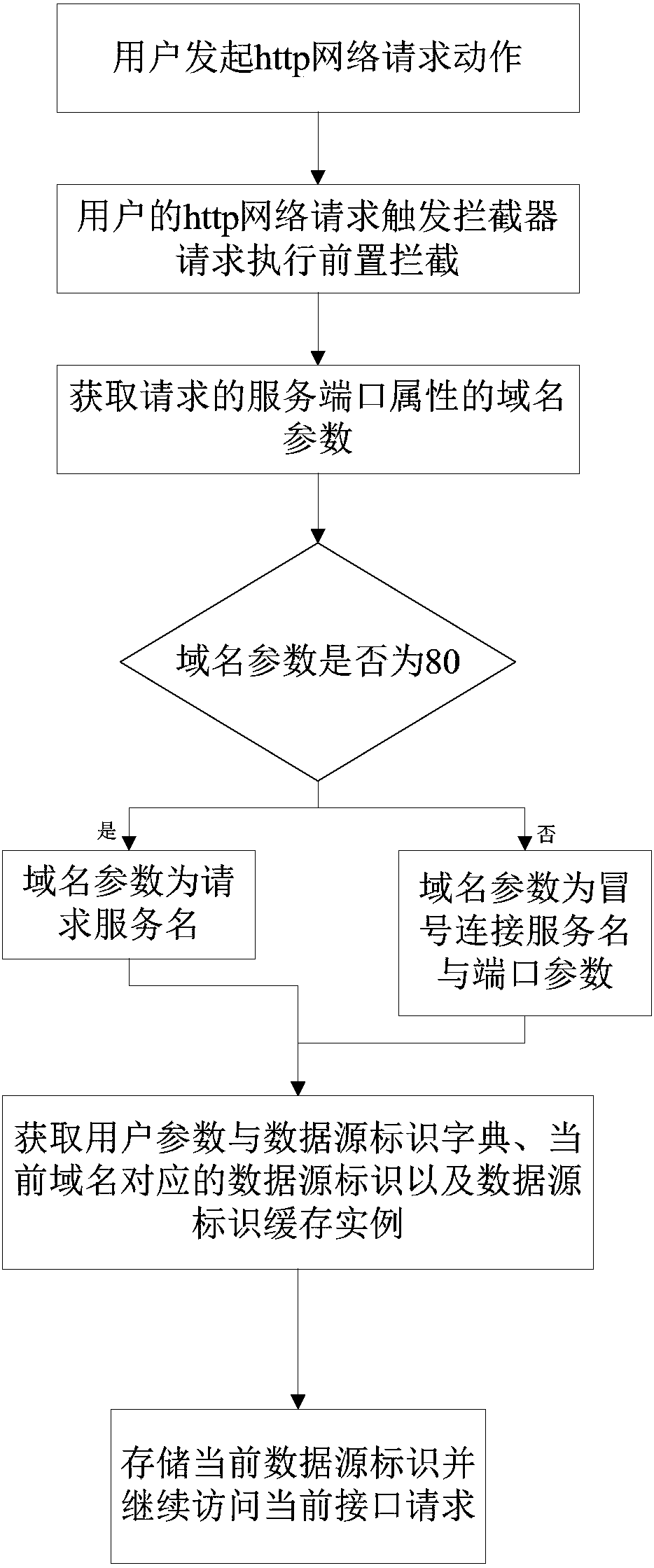
Data source identification selection method
InactiveCN108600265ASolve the usage scenario, the use of the data source switching module is safeSolve the use of securityTransmissionDomain nameRequest - action
The invention discloses a data source identification selection method. The method is characterized by comprising the following steps: S1, initiating http network request action by a user; S2, requesting to execute front interception by an http network request trigger interceptor of the user; S3, acquiring a domain name parameter about the attribute of a requested service port; S4, acquiring user parameter and a data source identification dictionary, data source identification corresponding to the user parameter, and a data source identification package caching instance; and S5, storing the current data source identification and continuously accessing the current access request. Through the method disclosed by the invention, the dynamic data configuration and switch are automatically performed through an underlying framework so as to avoid the data operation error caused by concurrence abnormality; the centralized management on the configuration parameter is performed more flexibly, sothat the configuration parameter can be more quickly transmitted to all load-end system service in a unified way, the abnormality caused by manual repeated operation and possible omission or misoperation is avoided, and a dynamic database connection management mechanism is provided for the network system.
Owner:JULONG
Method and system for synchronously displaying test images
The invention discloses a method and system for synchronously displaying a test picture, wherein the method for synchronously displaying a test picture is suitable for execution in a system for synchronously displaying a test picture, and the system for synchronously displaying a test picture includes a plurality of mobile terminals, servers and computing devices. The method includes: each mobile terminal records the screen of the current test process to obtain first video data; encodes the first video data to form second video data; and encapsulates the second video data to obtain The third video data is uploaded to the server; the server obtains the name parameters of each mobile terminal uploading the third video data; according to the name parameters, the server generates a plurality of corresponding URL addresses, and the URL addresses correspond to the mobile terminals respectively The third video data: the computing device decodes and plays the corresponding third video data to synchronously display the test images of each mobile terminal by accessing each URL address in multiple web pages.
Owner:XIAMEN MEITU MOBILE TECH CO LTD
A method and system for generating a player's game name
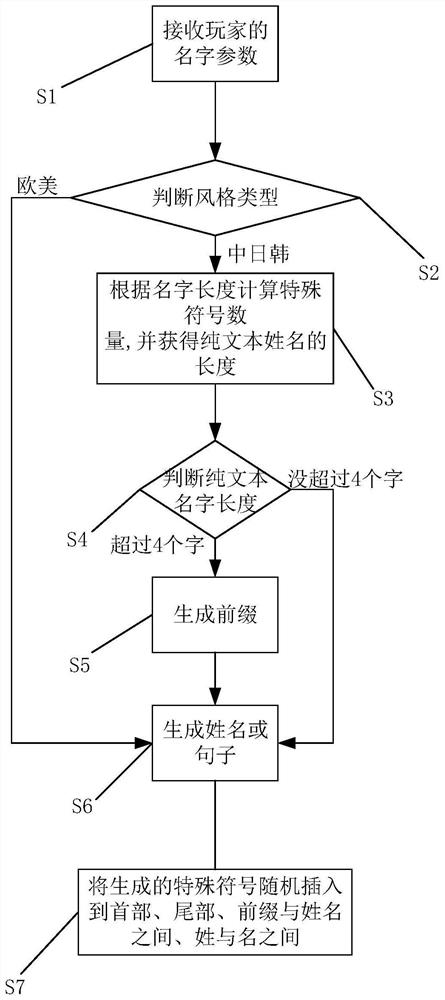
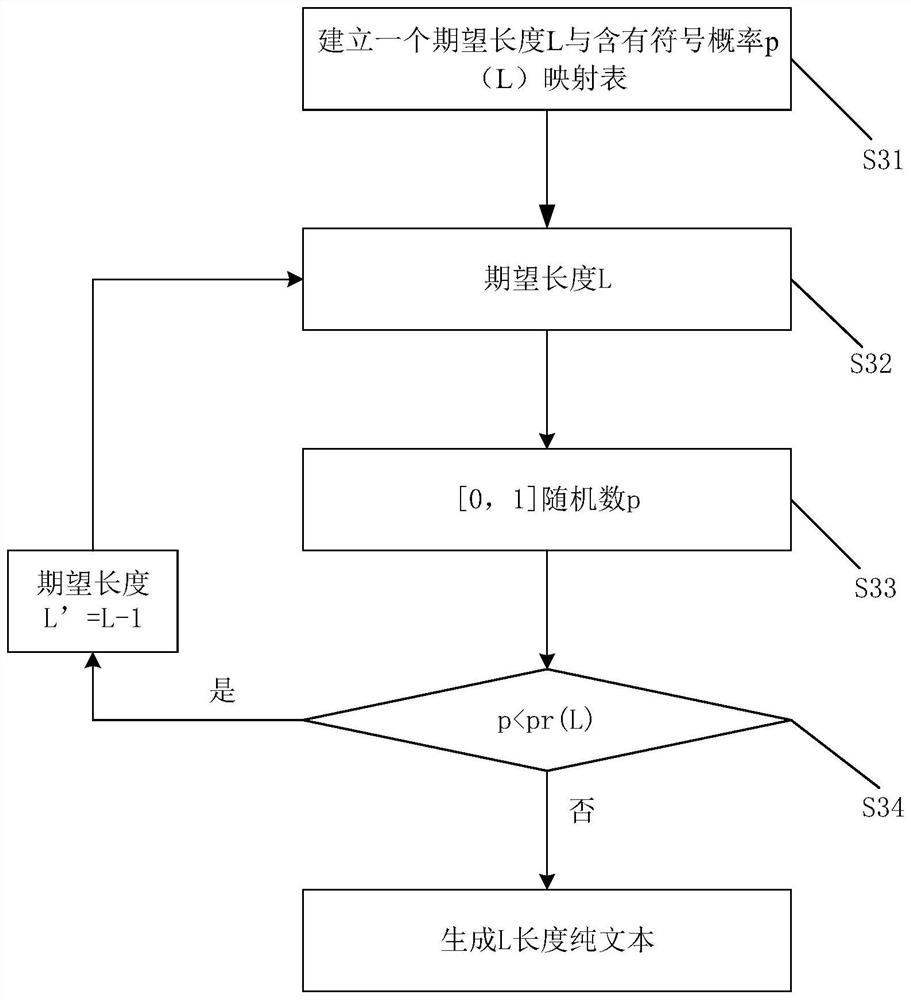
ActiveCN107729301BMeets requirementsGuaranteed sizeNatural language data processingOther databases queryingGame playerTheoretical computer science
The invention provides a game player game name generating method and a game player game name generating system for implementation of the game player game name generating method. The method includes: S1, receiving name parameters set by a game player, wherein the parameters include expected length, gender and style types, and the style types include a western style and a China, Japan and South Korea style; S2, judging style types, executing a step S3 if the China, Japan and South Korea style is determined, and executing a step S6 if the western style is determined; S3, calculating special symbol quantity according to the expected length, and acquiring length of a plain text name; S4, judging the length of the plain test name, executing a step S5 if the length of the plain text name is larger than 4, and otherwise, executing a step S6; S5, generating a prefix; S6, generating a name or sentence; S7, when existence of special symbols is determined, generating special symbols in corresponding quantity, randomly inserting among a start portion, an end portion, a family name and a first name and between the prefix and the name.
Owner:GUANGZHOU DUOYI NETWORK TECH +2
Method and system for accessing domain name suffix
The invention discloses a domain name suffix inputting method and system. The method comprises that according to a domain name parameter of a domain name suffix, different application scenes are configured; whether a domain name service that matches the application scene exists in a preset domain name service list is determined; and if YES, the authority of the application scene in the domain name service is configured. According to the method, the process of inputting the new domain name suffix can be simplified, and the efficiency of inputting the new domain name suffix is improved.
Owner:ALIBABA GRP HLDG LTD
Mapping method of data collected by safety automatic device and primary equipment model of ems system
ActiveCN106202814BImprove maintenance efficiencyImprove accuracyDesign optimisation/simulationSpecial data processing applicationsElectric power systemCommunications software
The invention relates to a mapping method for data collected by an automatic safety device and an EMS system primary equipment model. The mapping method comprises the steps that the automatic safety device collects real-time operating data of primary equipment, and grouping organization is carried out in an electrical power system interval mode; the data is placed in a universal classification service group structure to be uploaded to a management master station of the automatic safety device; the management master station receives interval data of universal classification service groups through communication software, and interval serial numbers are extracted from group names; the interval name parameter groups are searched for interval dispatching names corresponding to the interval serial numbers, the EMS module is searched for corresponding interval IDs according to the interval dispatching names in a matching mode, the primary equipment in the EMS model is positioned according to the interval types included in the interval data groups and the interval IDs, and the values of fixed items in the real-time operating data are written in an attribute domain corresponding to the primary equipment in the EMS model. The accuracy of the data corresponding relationship is improved on the premise of improving data maintenance efficiency.
Owner:POWER DISPATCHING CONTROL CENT OF GUANGDONG POWER GRID CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com