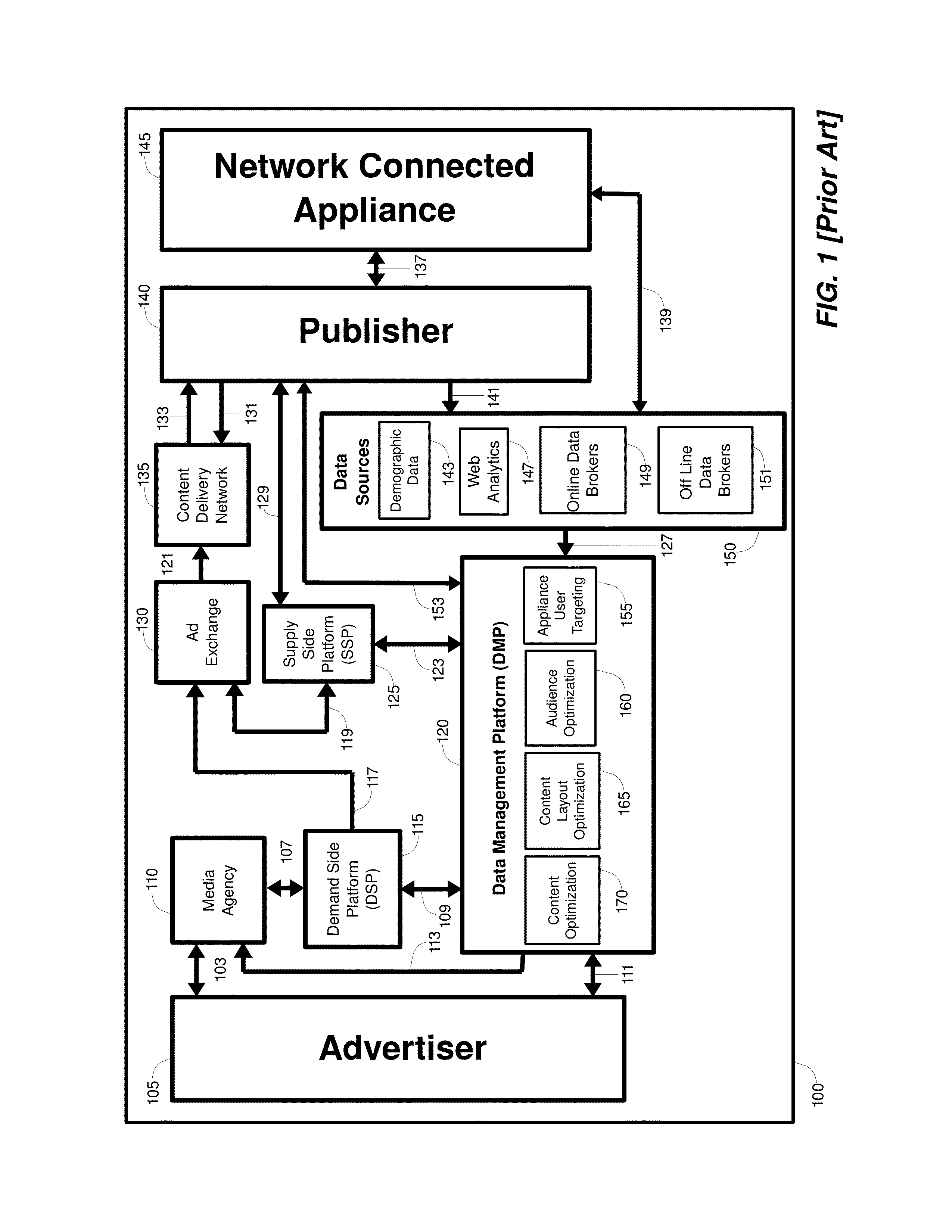
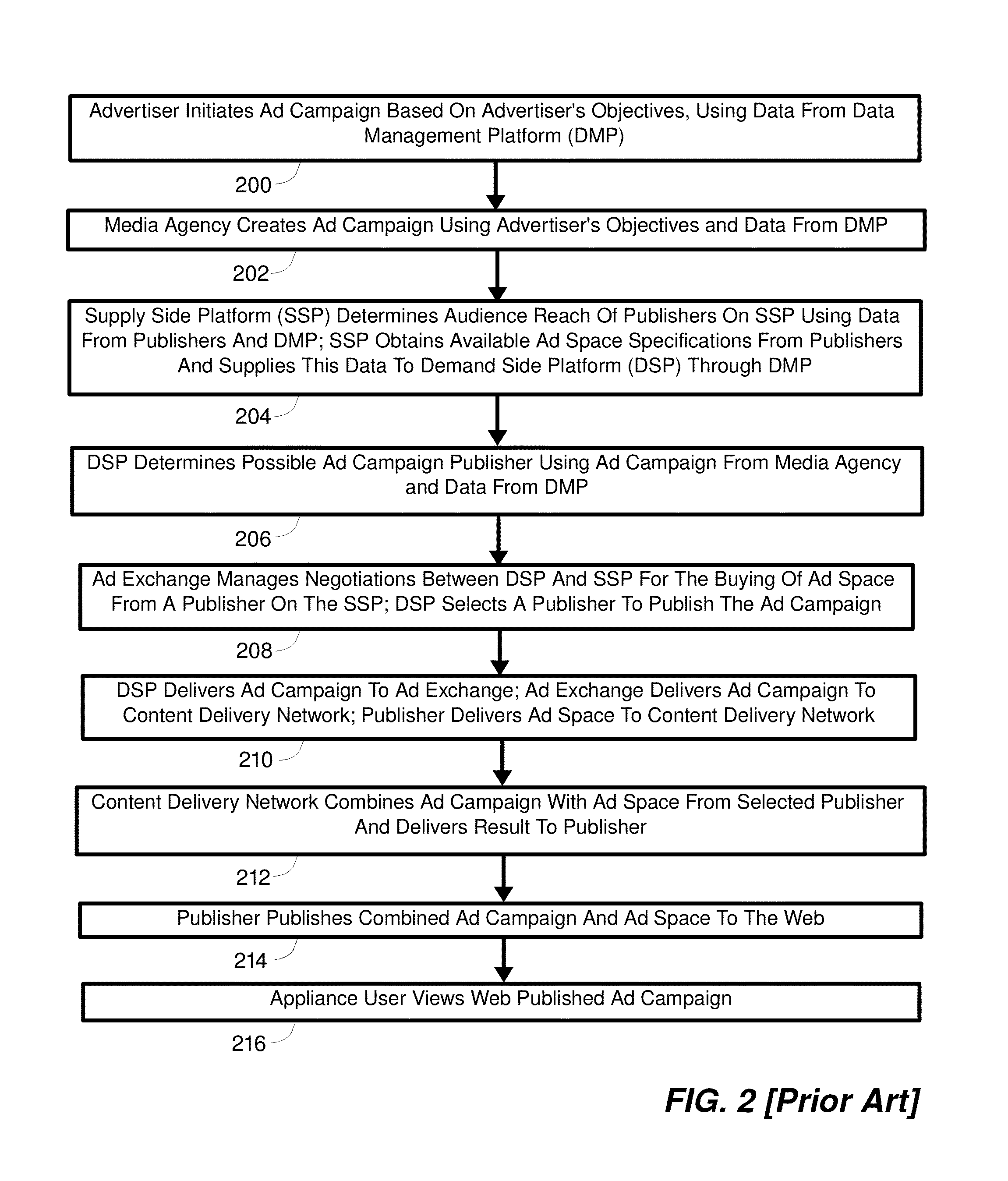
Patents
Literature
40 results about "Consumer privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Consumer privacy is information privacy as it relates to the consumers of products and services. A variety of social, legal and political issues arise from the interaction of the public's potential expectation of privacy and the collection and dissemination of data by businesses or merchants. Consumer privacy concerns date back to the first commercial couriers and bankers who enforced strong measures to protect customer privacy. In modern times, the ethical codes of various professions specify measures to protect customer privacy, including medical privacy and client confidentiality. State interests include matters of national security. Many organizations have a competitive incentive to collect, retain, and use customer data for various purposes, and many companies adopt security engineering measures to control this data and manage customer expectations and legal requirements for consumer privacy.
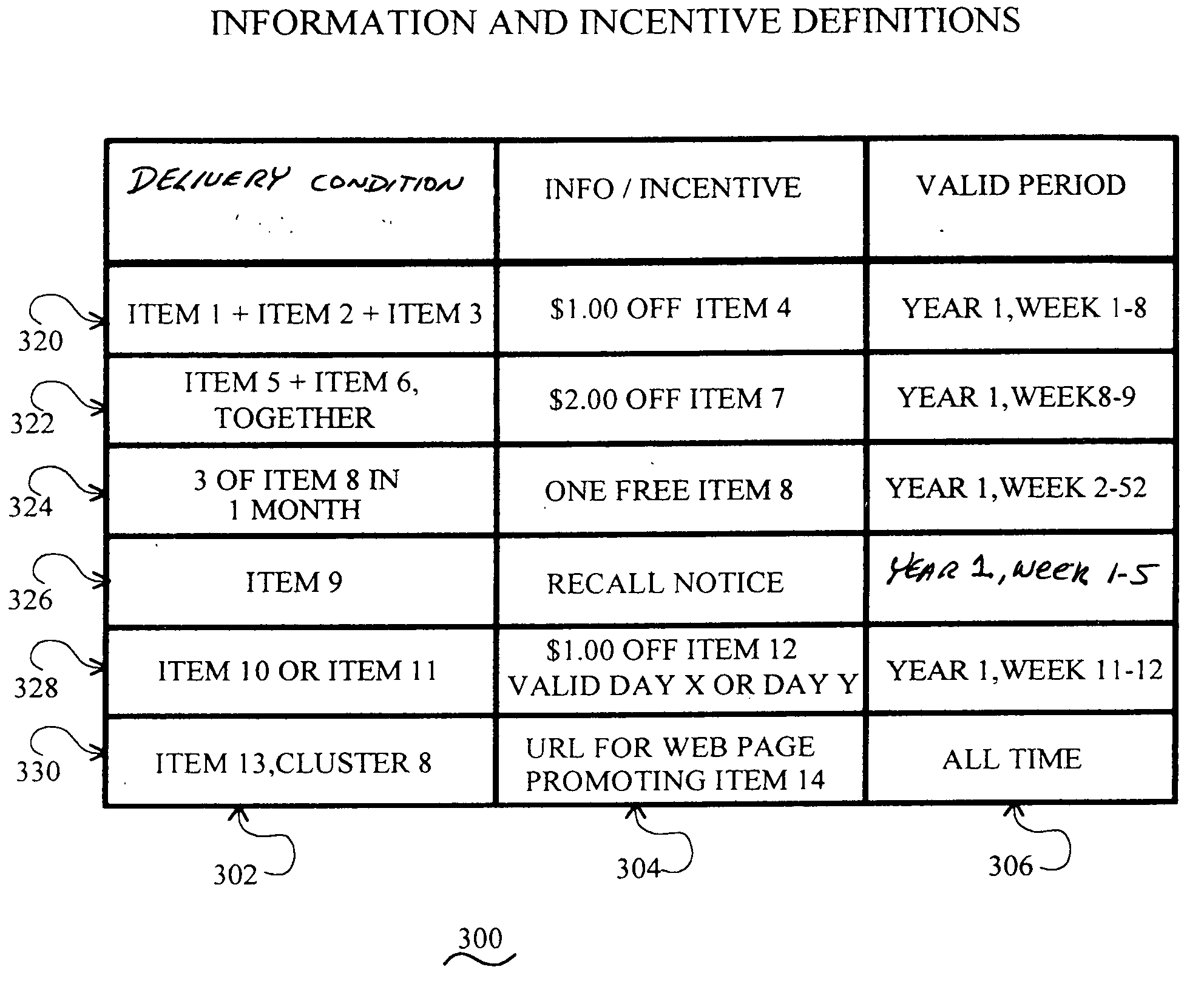
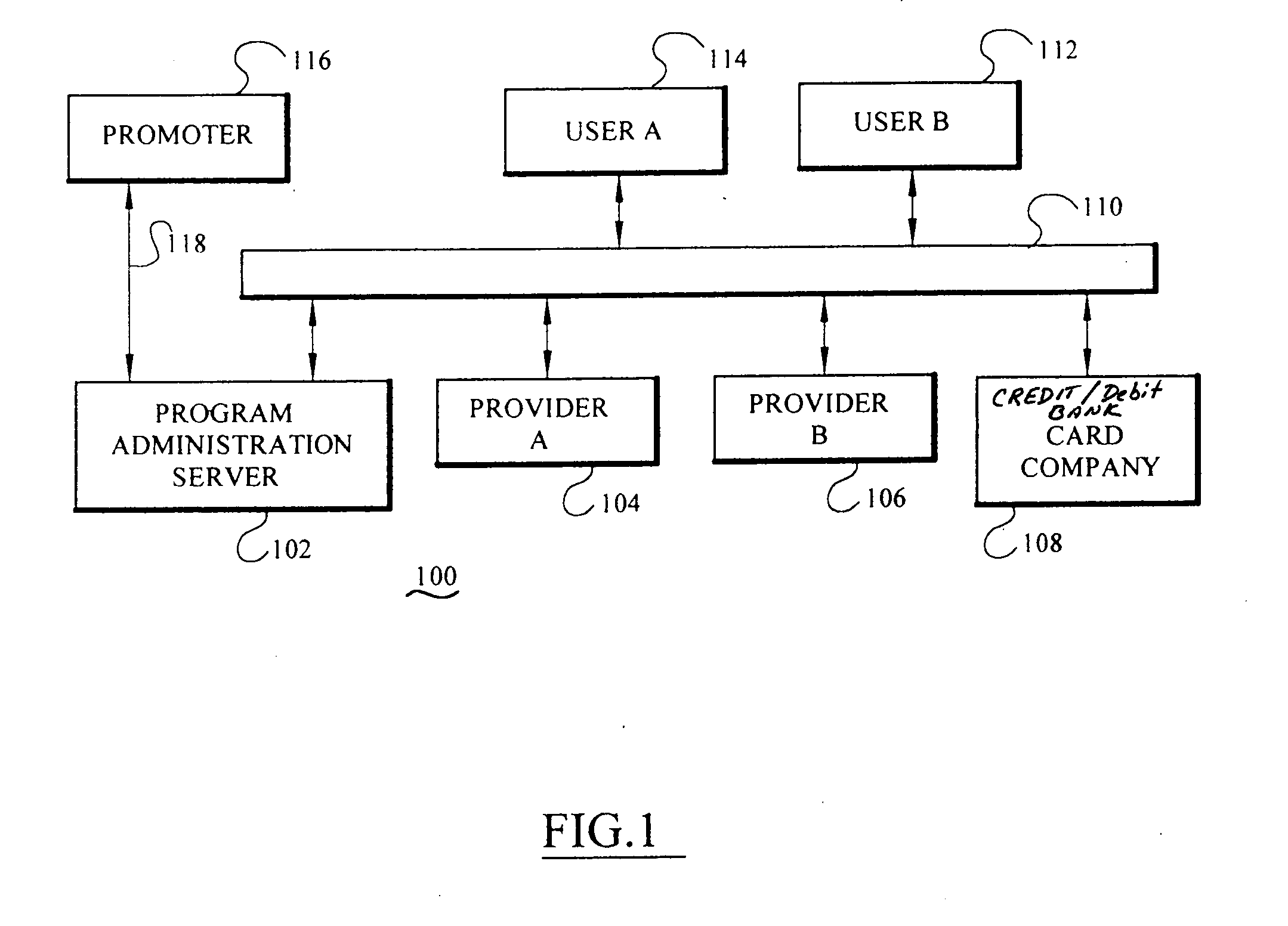
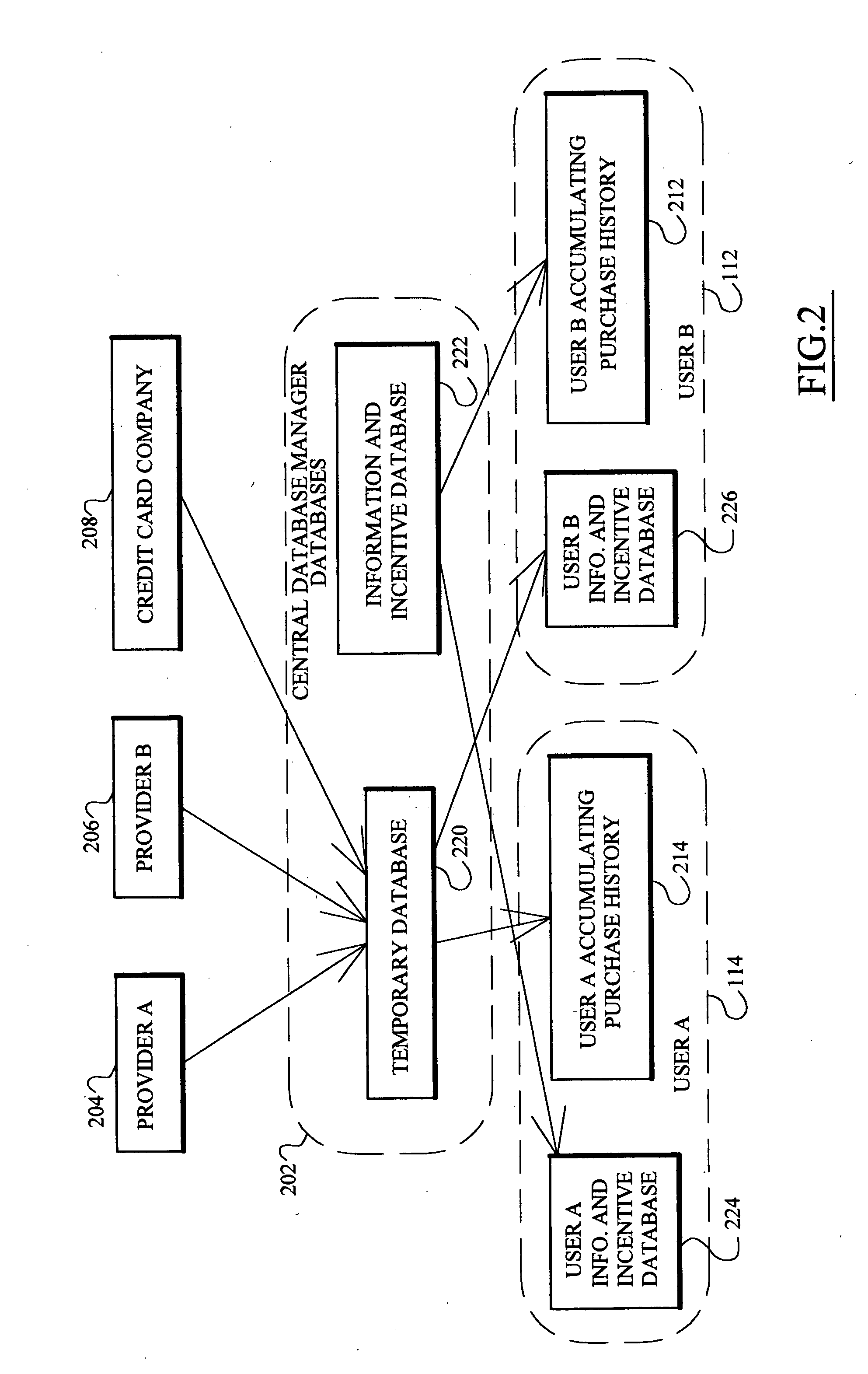
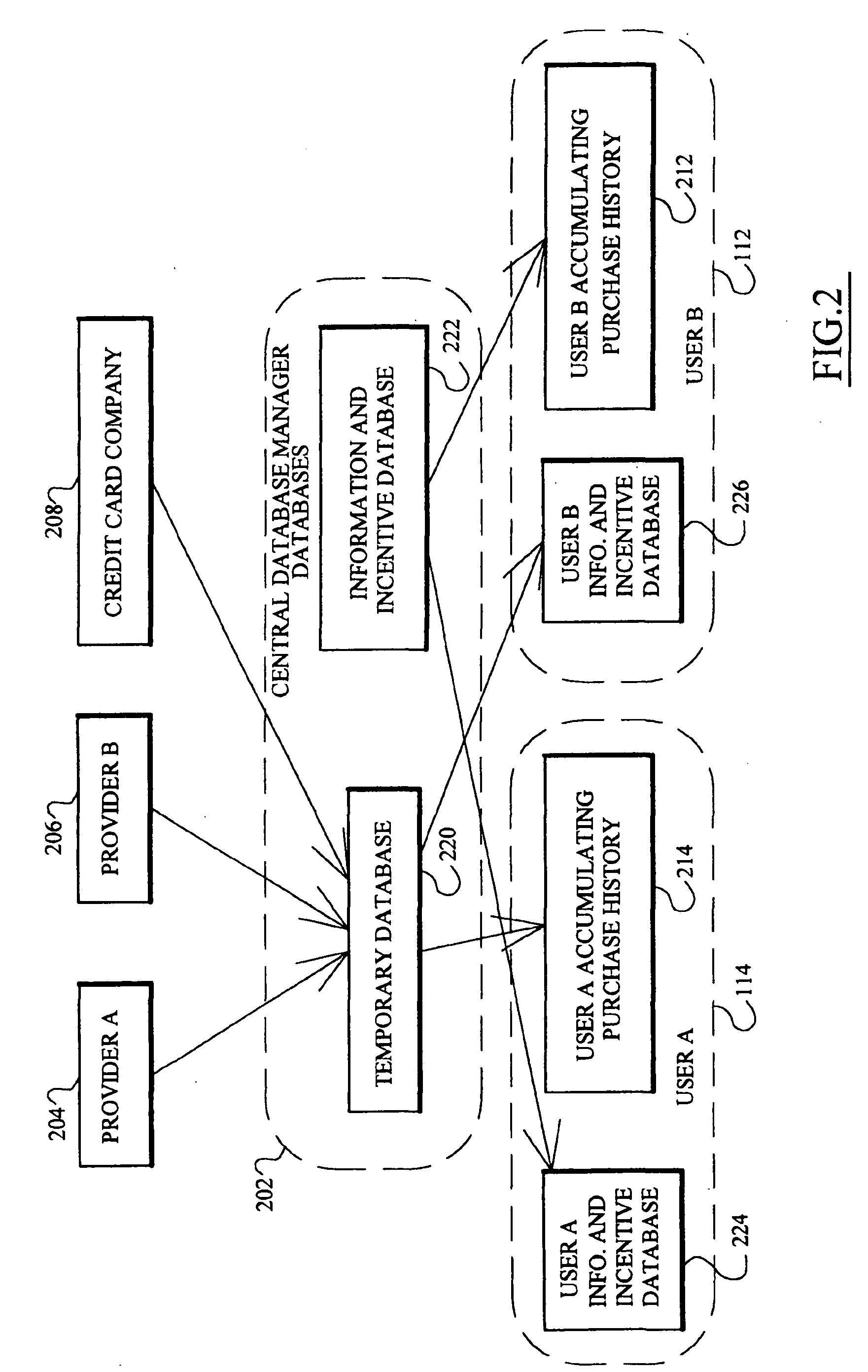
Individually controlled and protected targeted incentive distribution system
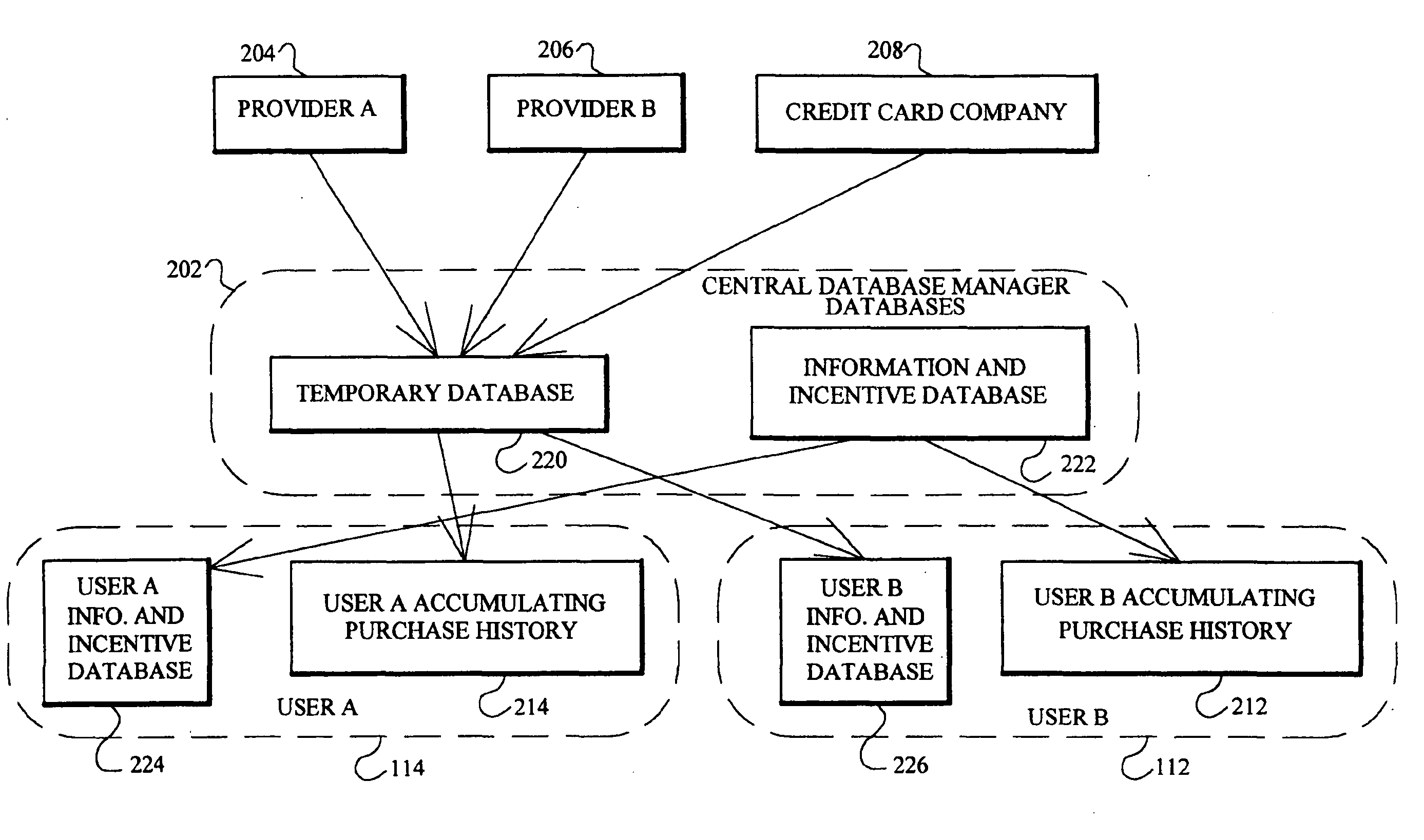
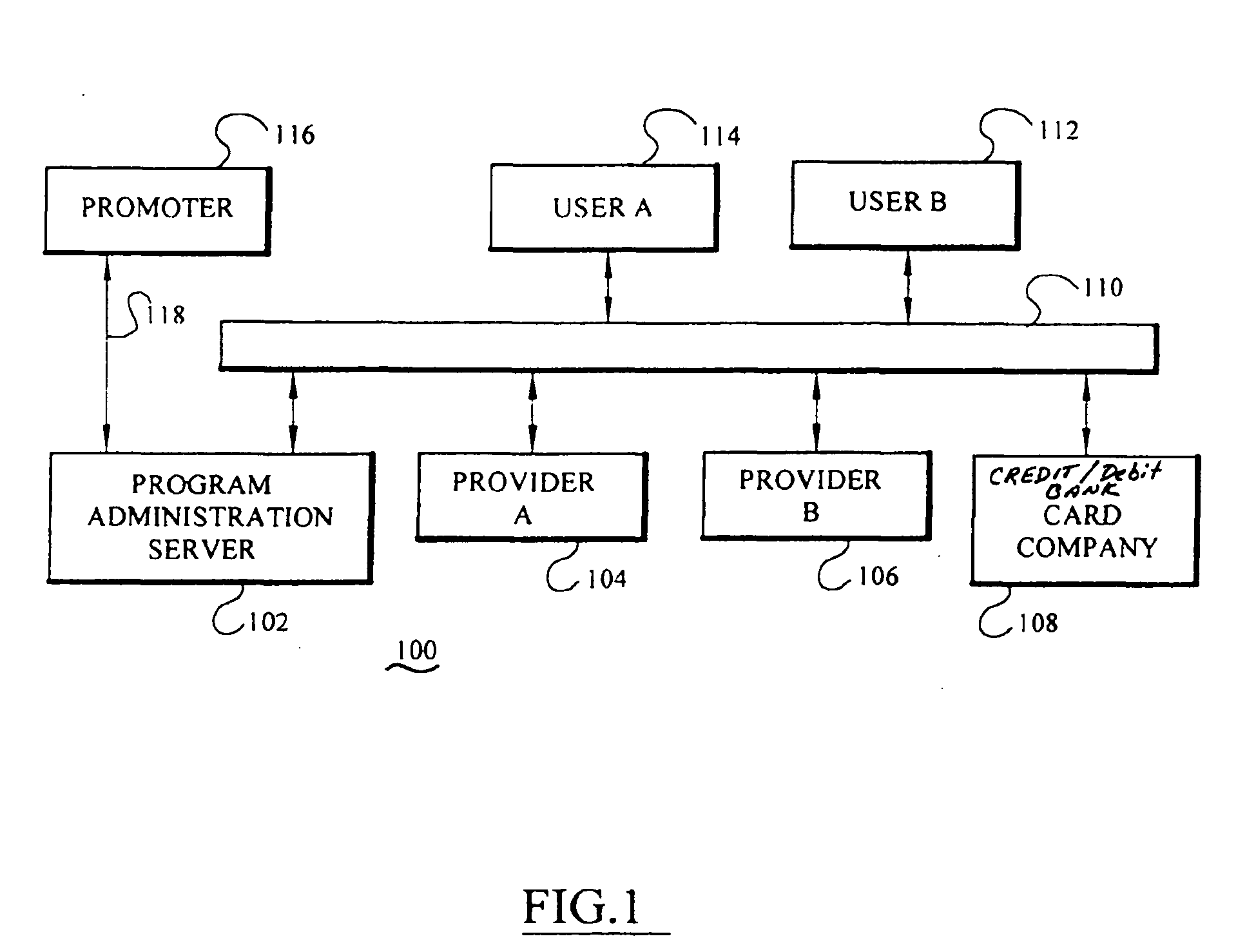
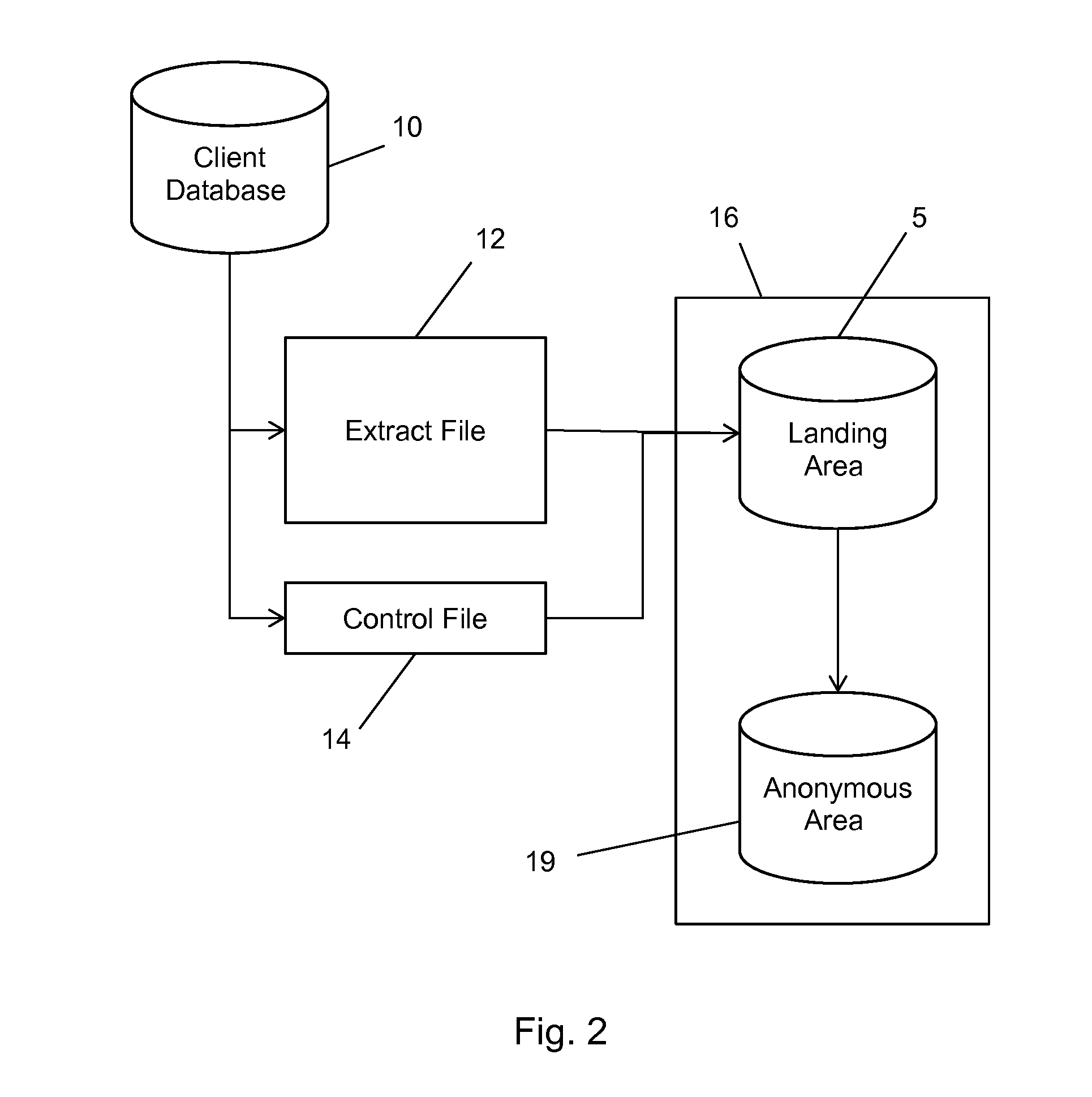
A targeted information and incentive distribution system that protects consumer privacy and analyzes individuals', including individual households' or individual groups, purchase histories obtained from several retailers and other providers of goods and / or services to determine targeted information and / or incentives to deliver to individuals. Purchase history and other relevant data for each individual user are accumulated at a computer that is under the control of that user and analyzed to determine which targeted information items and / or incentives to deliver to that individual user. Purchase history data in the exemplary embodiment is only maintained at the user's computer so as to increase the privacy for the user of this extensive purchase history data that was derived from multiple sources. Abridged purchase history data that does not contain information to identify the individual to which it pertains is uploaded for comprehensive analysis to develop future purchase incentive programs.
Owner:ICOOD
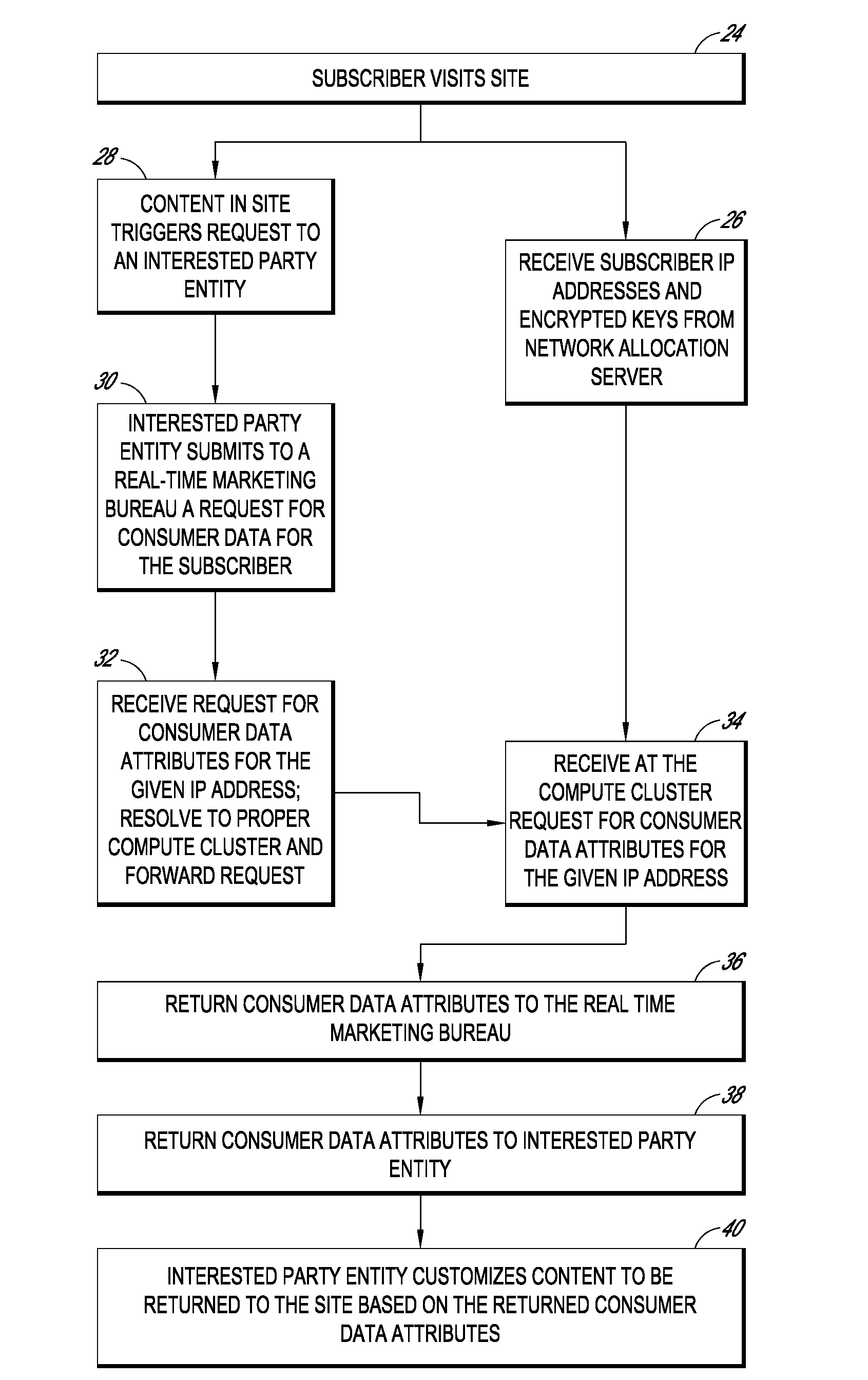
Systems and methods for providing real time anonymized marketing information
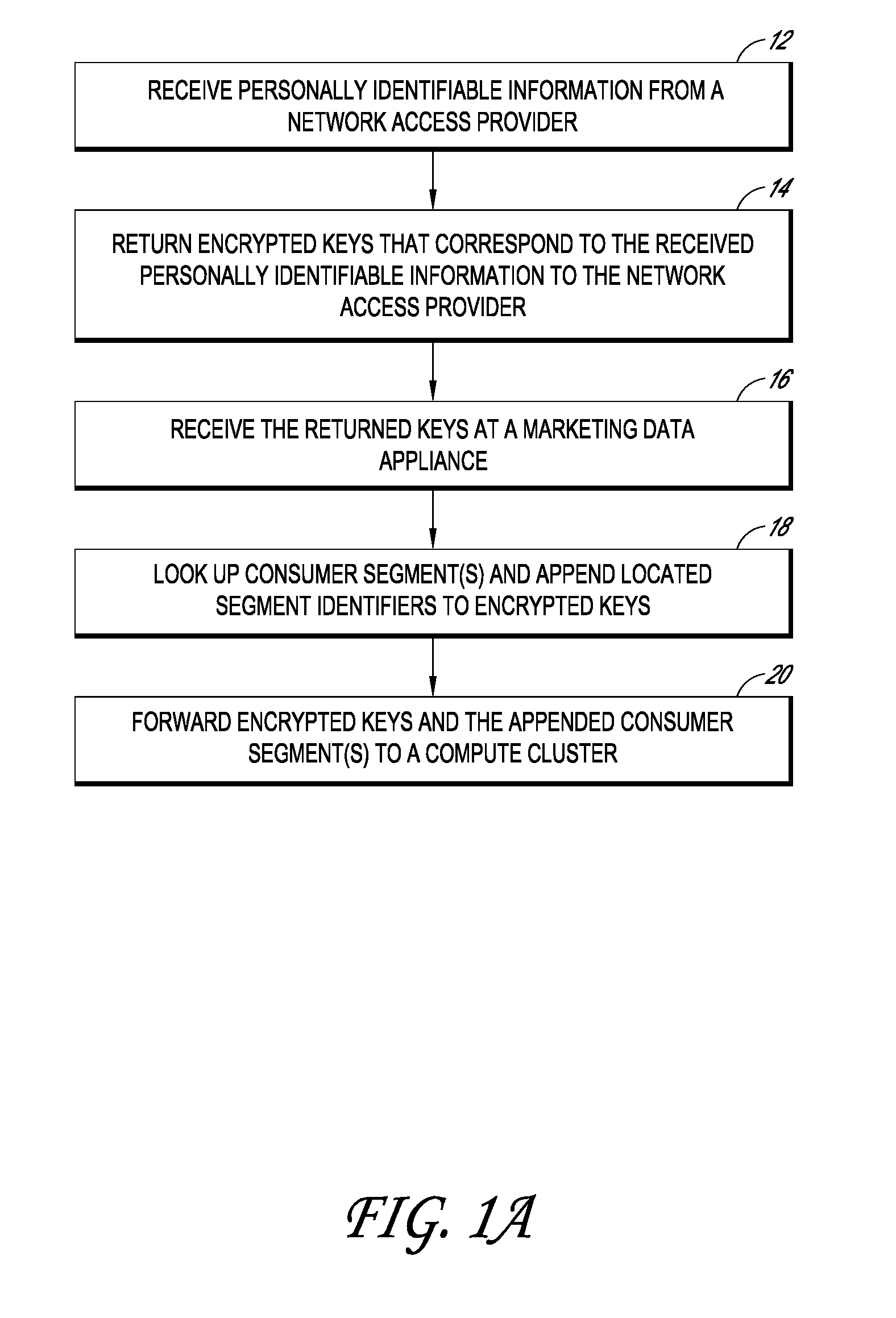
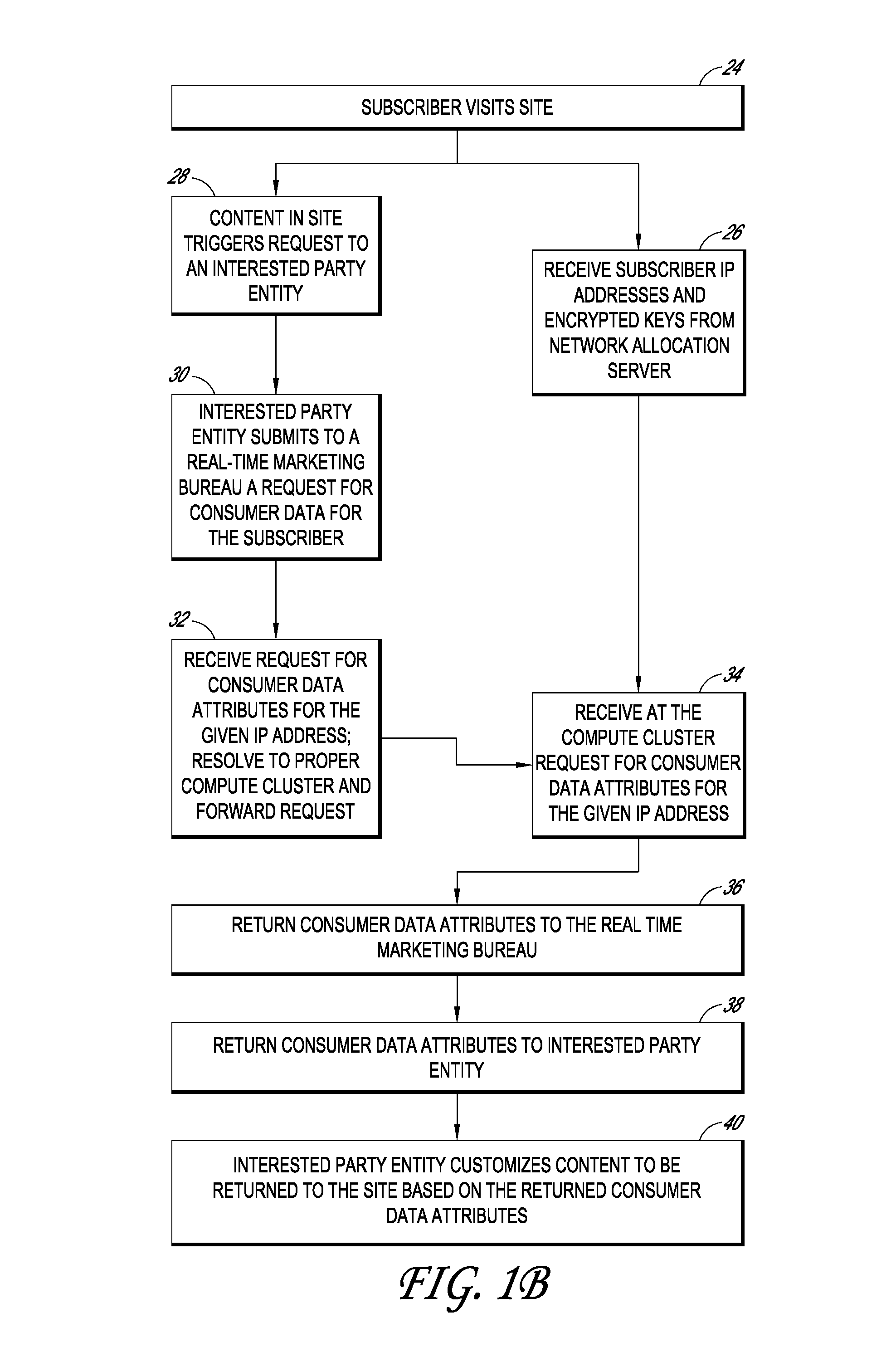
InactiveUS20100094758A1Protects consumer privacyPrivacy protectionMultiple keys/algorithms usageComputer security arrangementsReal-time marketingThird party
Embodiments disclosed herein are directed to systems and methods for enabling the matching of third party data with access providers' subscriber data in a privacy compliant manner, and then connecting an internet user to that third party data for use by marketers, content providers, or other interested parties in a manner that protects consumer privacy at all times. In one embodiment, an access provider such as an ISP sends its subscriber data to a double blind processor that generates an encrypted key for each subscriber. The key is then used to find matching consumer data, for example, consumer segments that represent previously collected or modeled consumer attitudinal, habit, or financial data. The key may be forwarded to a real time marketing bureau, which may use the matched data in subsequent real-time or substantially real-time operations to provide consumer or business data to advertisers, content providers, and other interested parties.
Owner:EXPERIAN MARKETING SOLUTIONS
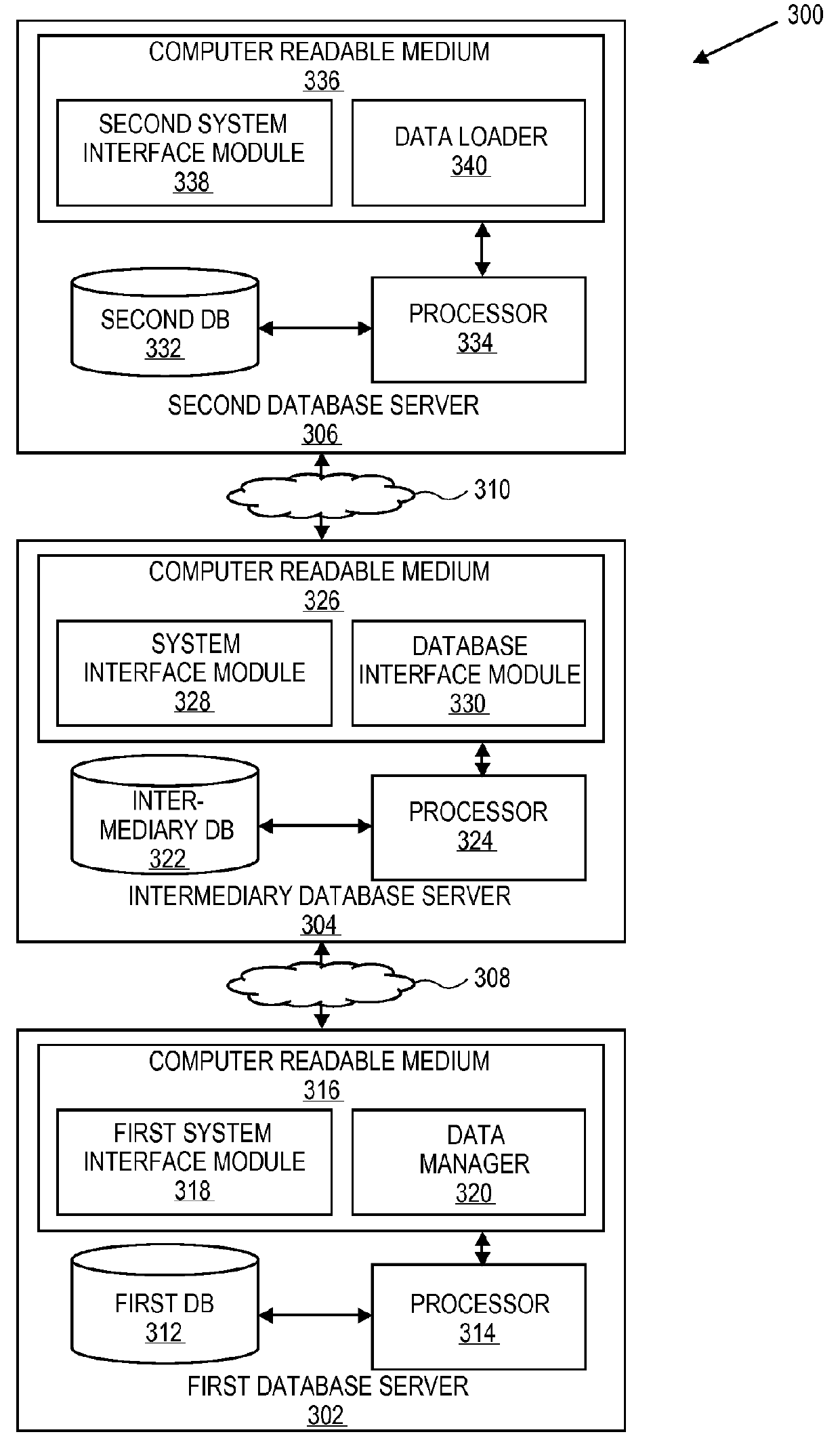
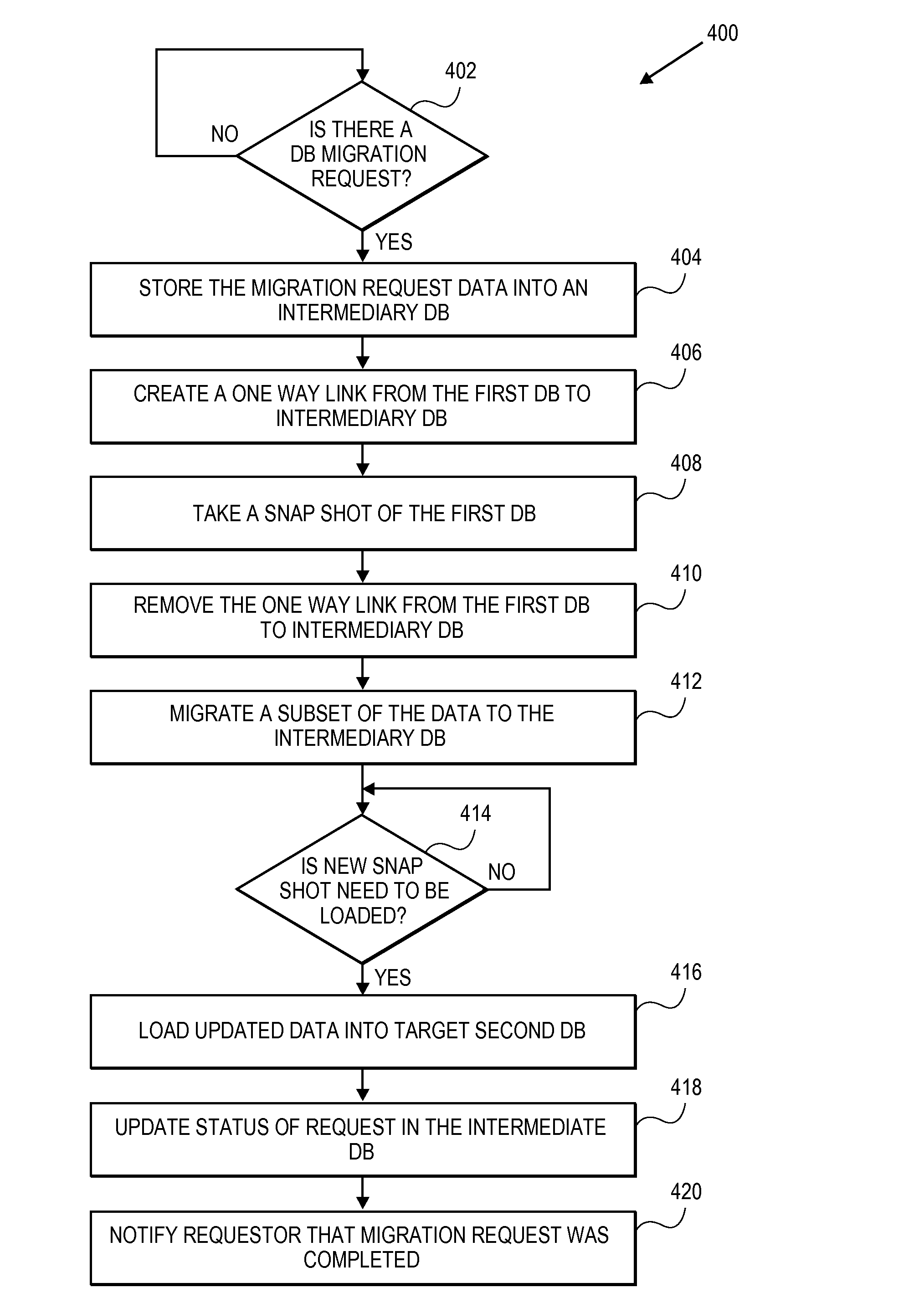
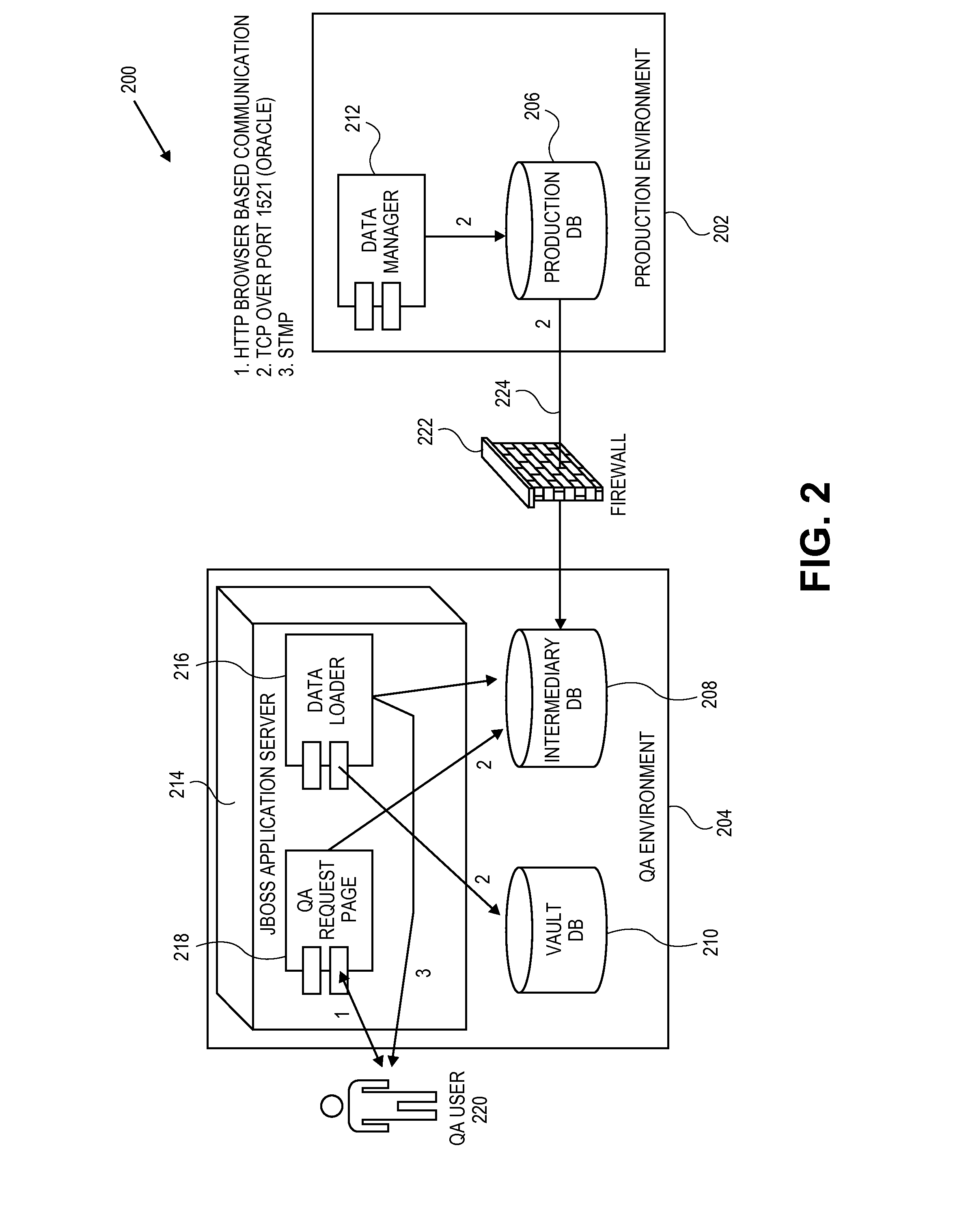
Database cloning and migration for quality assurance
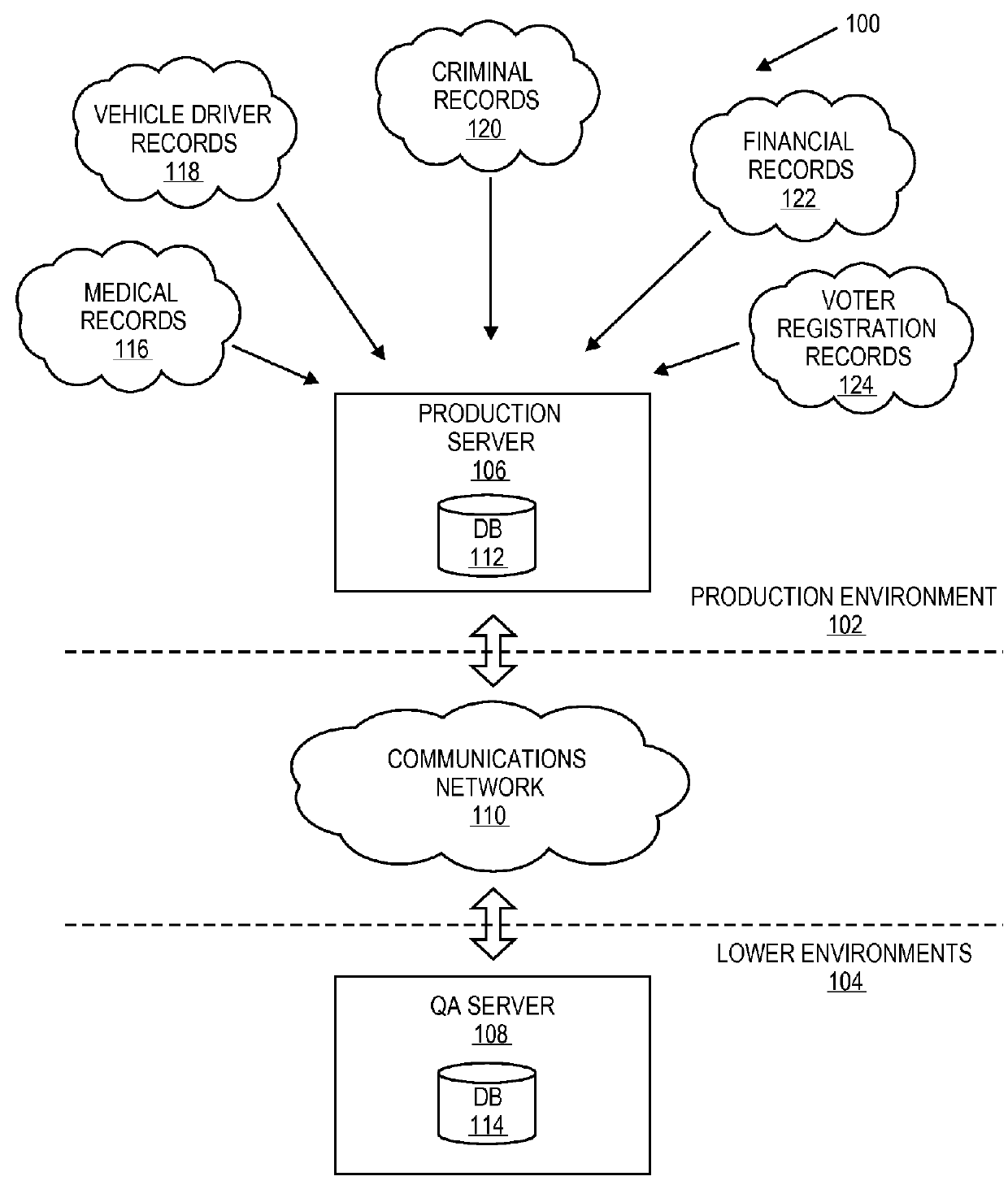
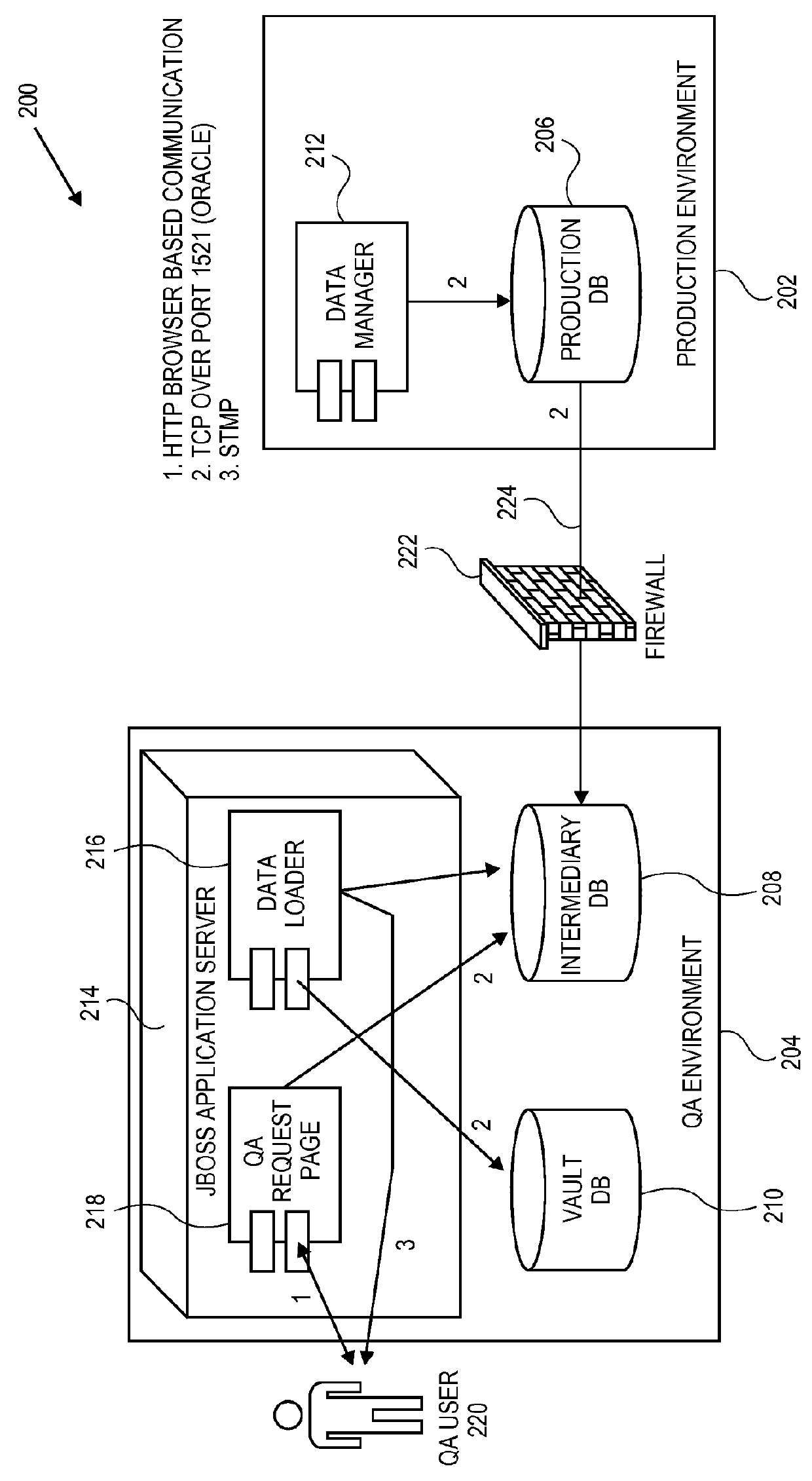
ActiveUS9229964B2Data processing applicationsDigital data information retrievalPaymentQuality assurance
Embodiments of the invention relate to systems and methods for cloning a production database for quality assurance (QA) by the merchant users. A QA user may request tokens, card types and other data associated with a payment device for quality assurance purposes. The payment network redirects the QA request to a go-between database that is present between the QA user and the production environment of the payment network rather than pull the information directly from the production environment. As a result, the merchant is able to use tokens for testing, without violating consumer privacy and security rules and regulations (e.g., PCI rules). The QA user does not have to create a customized testing solution.
Owner:VISA INT SERVICE ASSOC
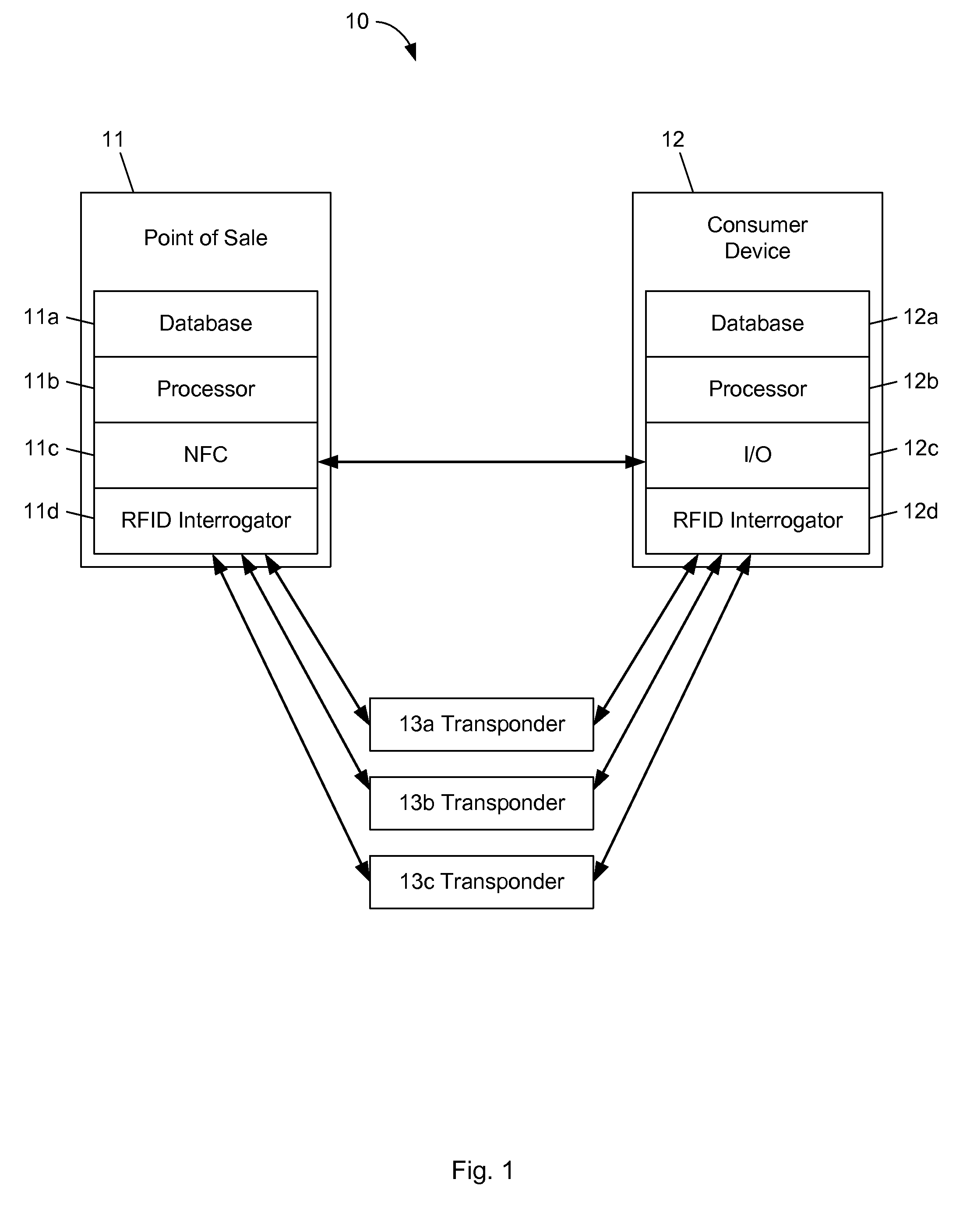
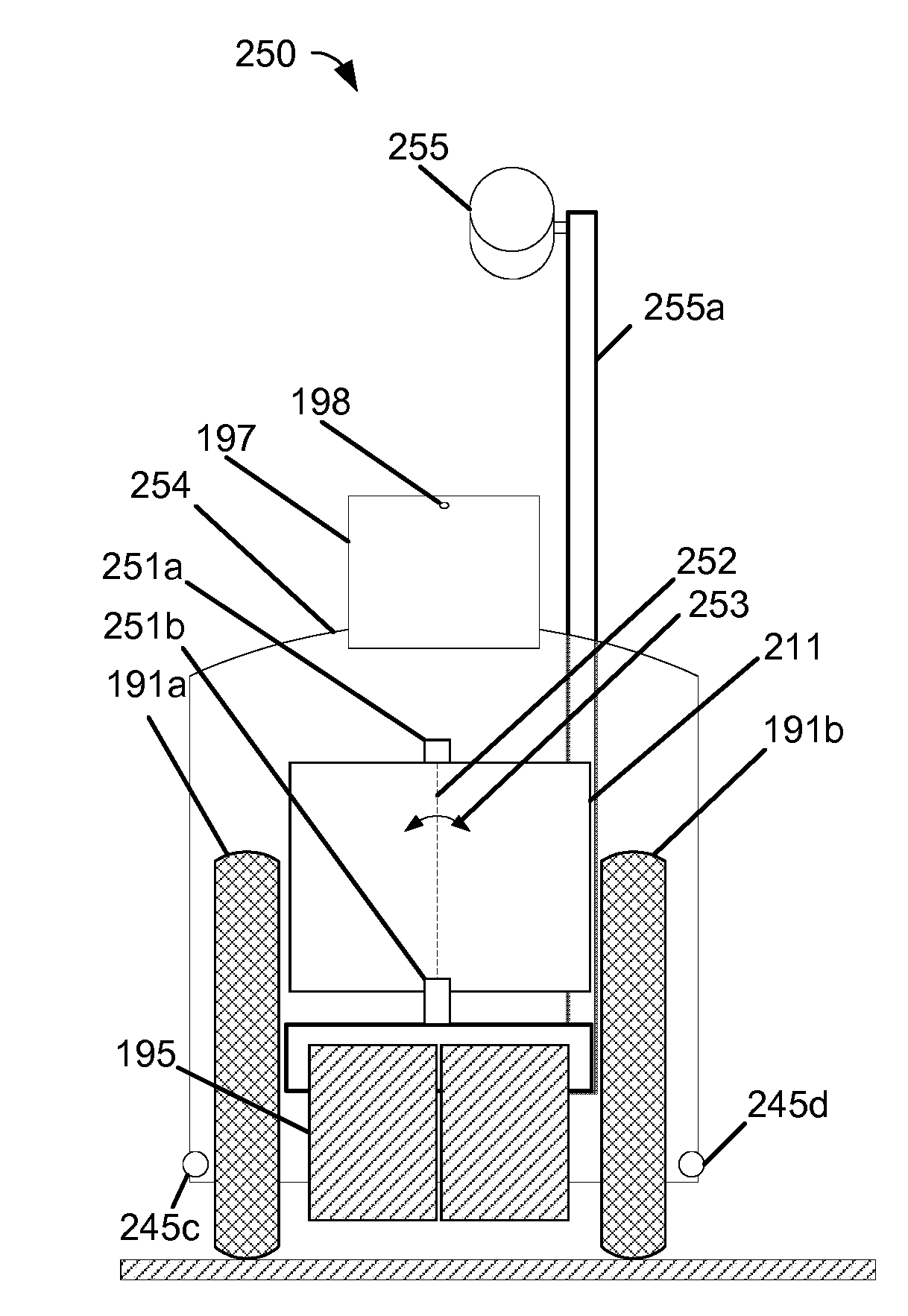
RFID and robots for multichannel shopping
InactiveUS20140152507A1Prevent promiscuous transmissionConvenient timeDirection finders using radio wavesHelical antennasComputer scienceConsumer privacy
The present invention relates to systems, methods, and devices for consumers using RFID-tagged items for multichannel shopping using smartphones, tablets, and indoor navigation, preservation of consumer's privacy related to RFID-tagged items that they leave a retail store with, and automatically reading and locating retail inventory without directly using store labor. Robots and aerial mobile automated RFID reading devices are disclosed.
Owner:ADASA
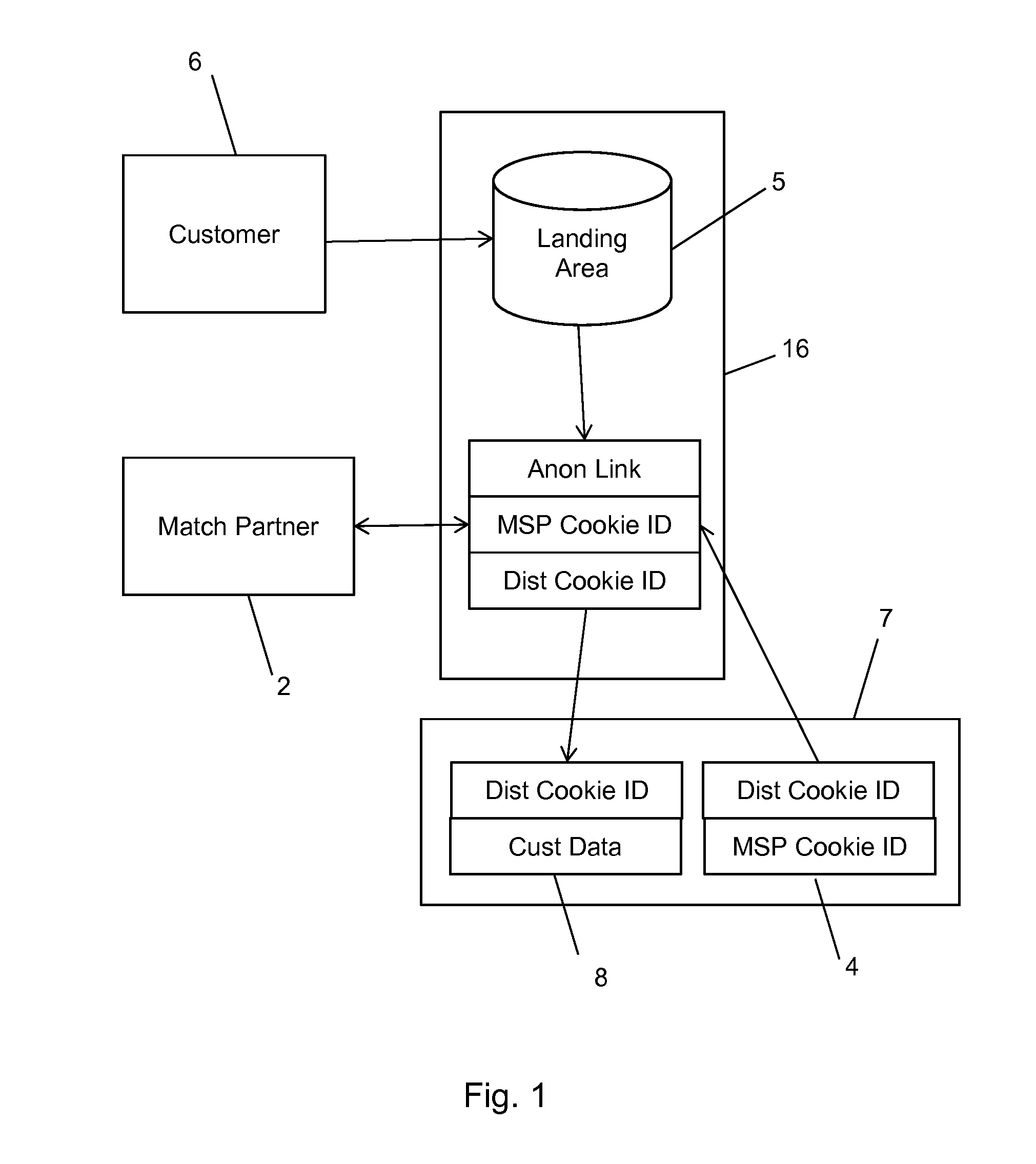
Apparatus and method for bringing offline data online while protecting consumer privacy
ActiveUS9665883B2Precise positioningIncreased marketingAdvertisementsComputer security arrangementsInternet privacyOnline and offline
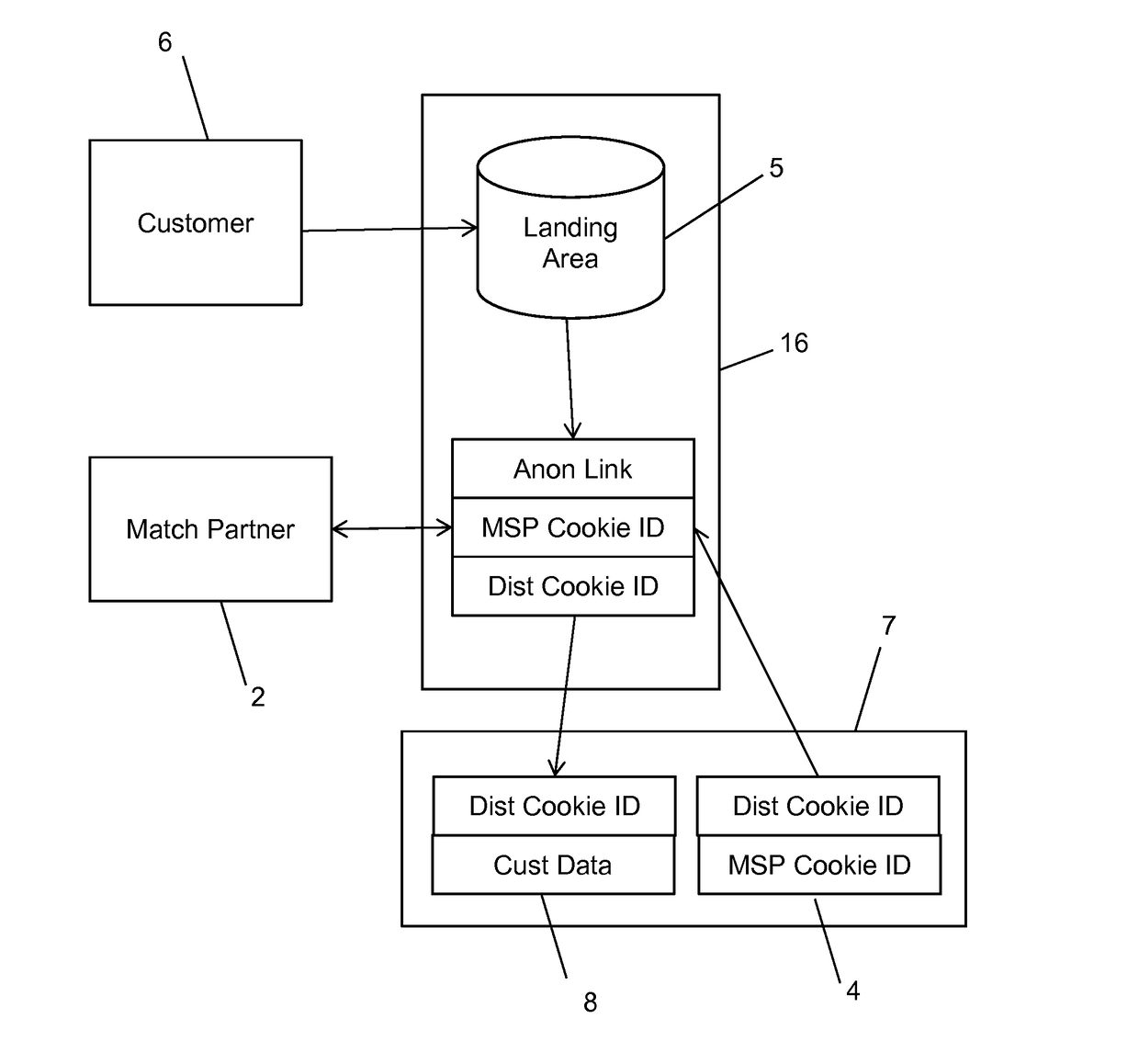
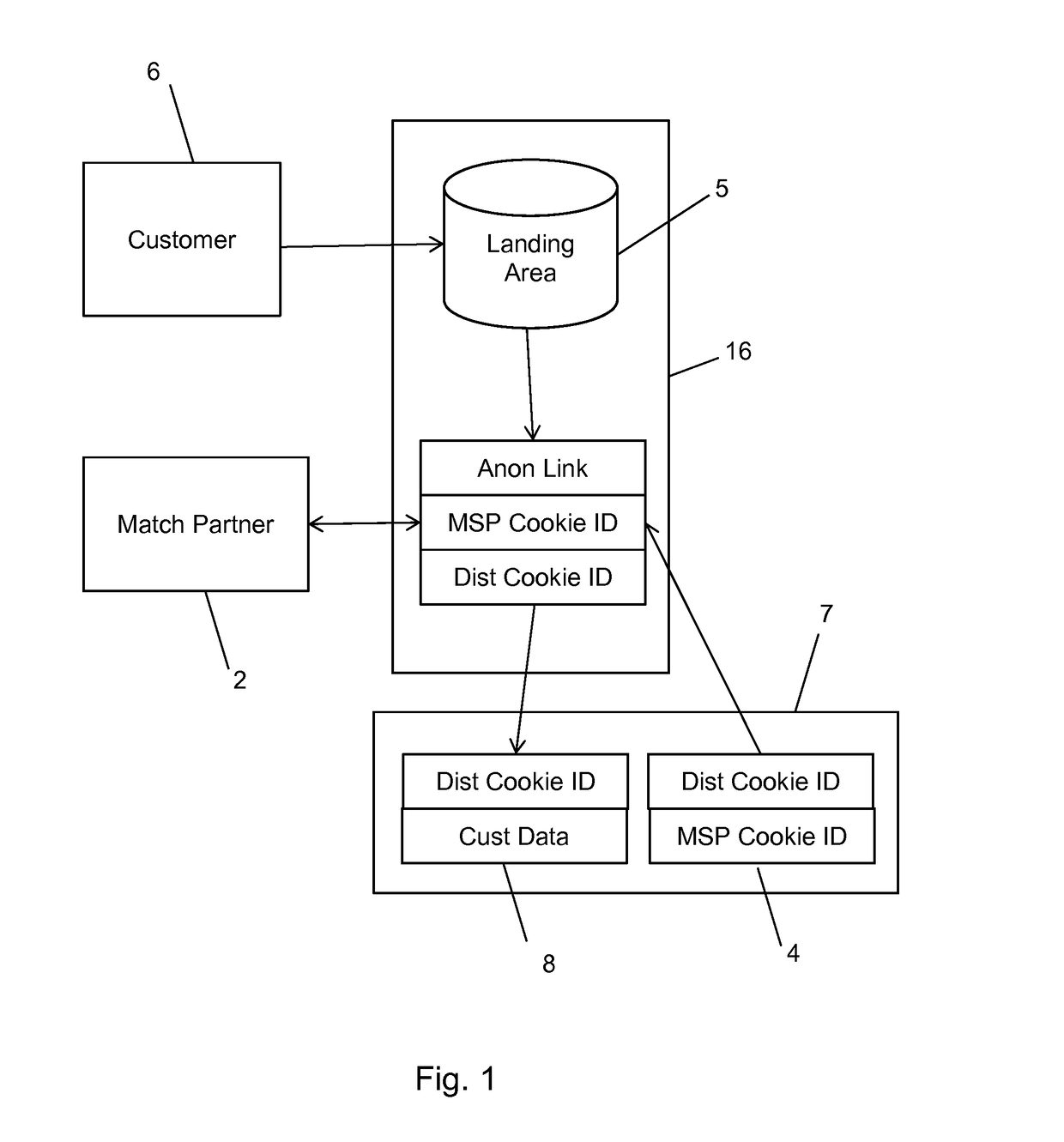
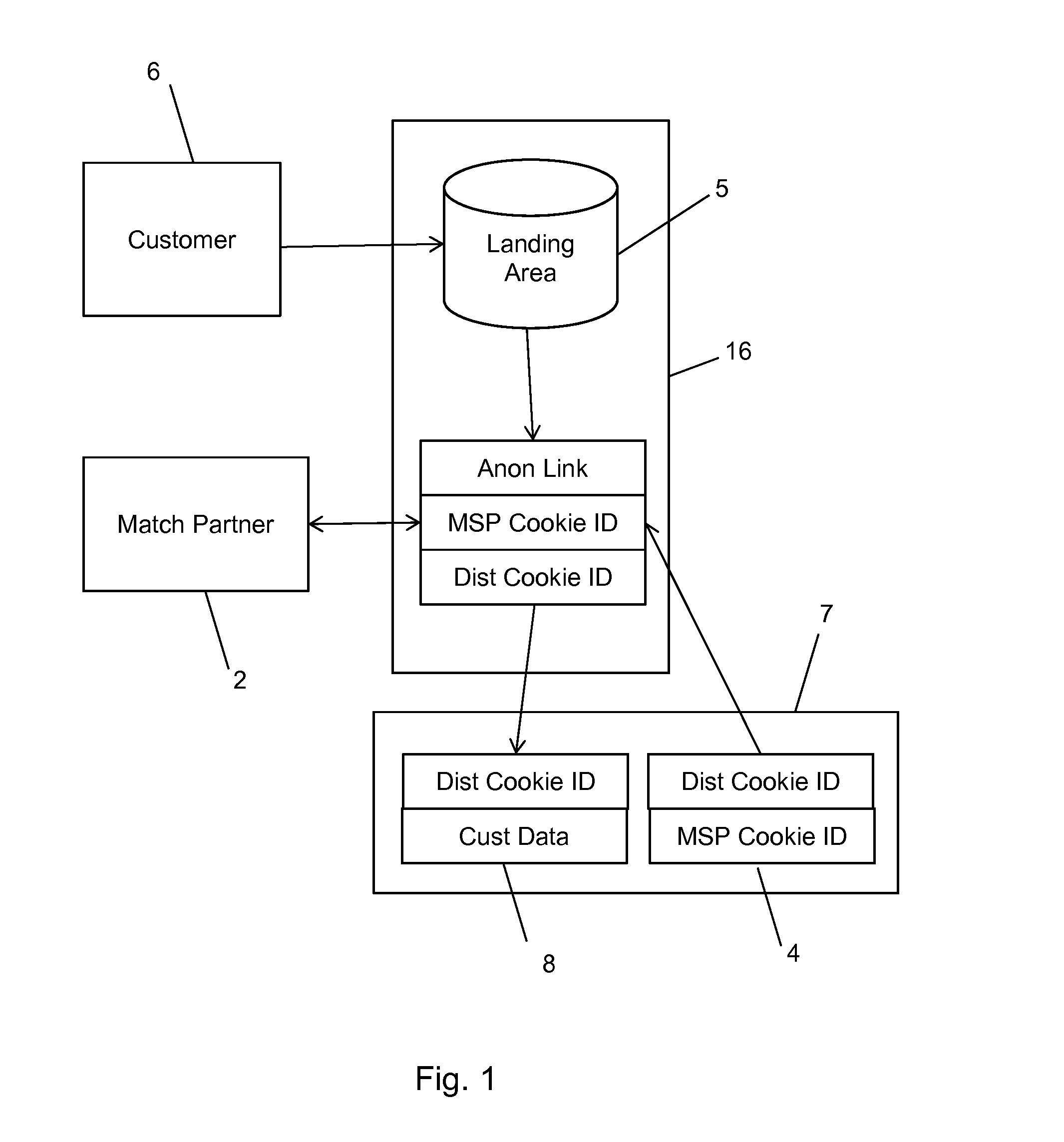
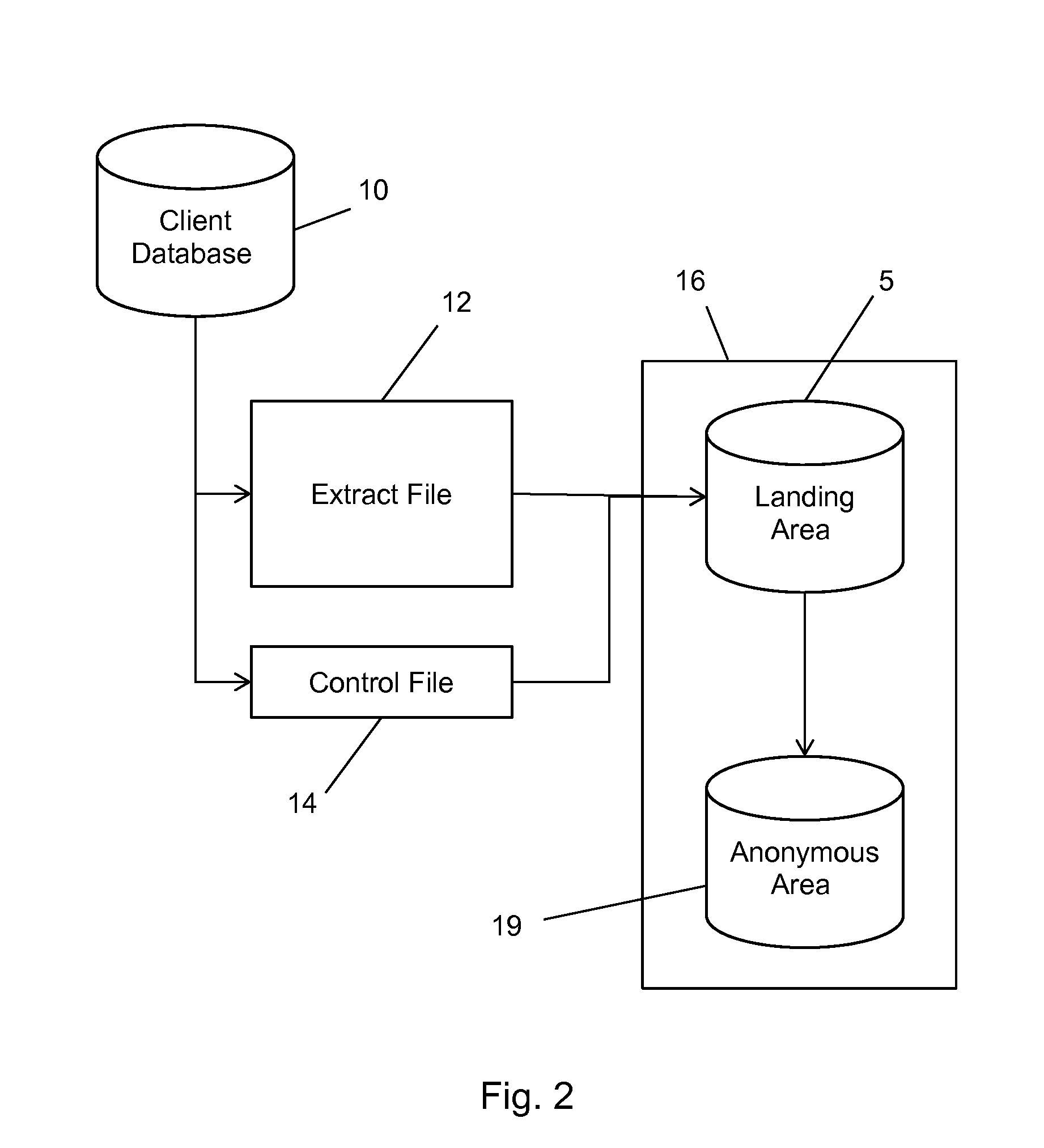
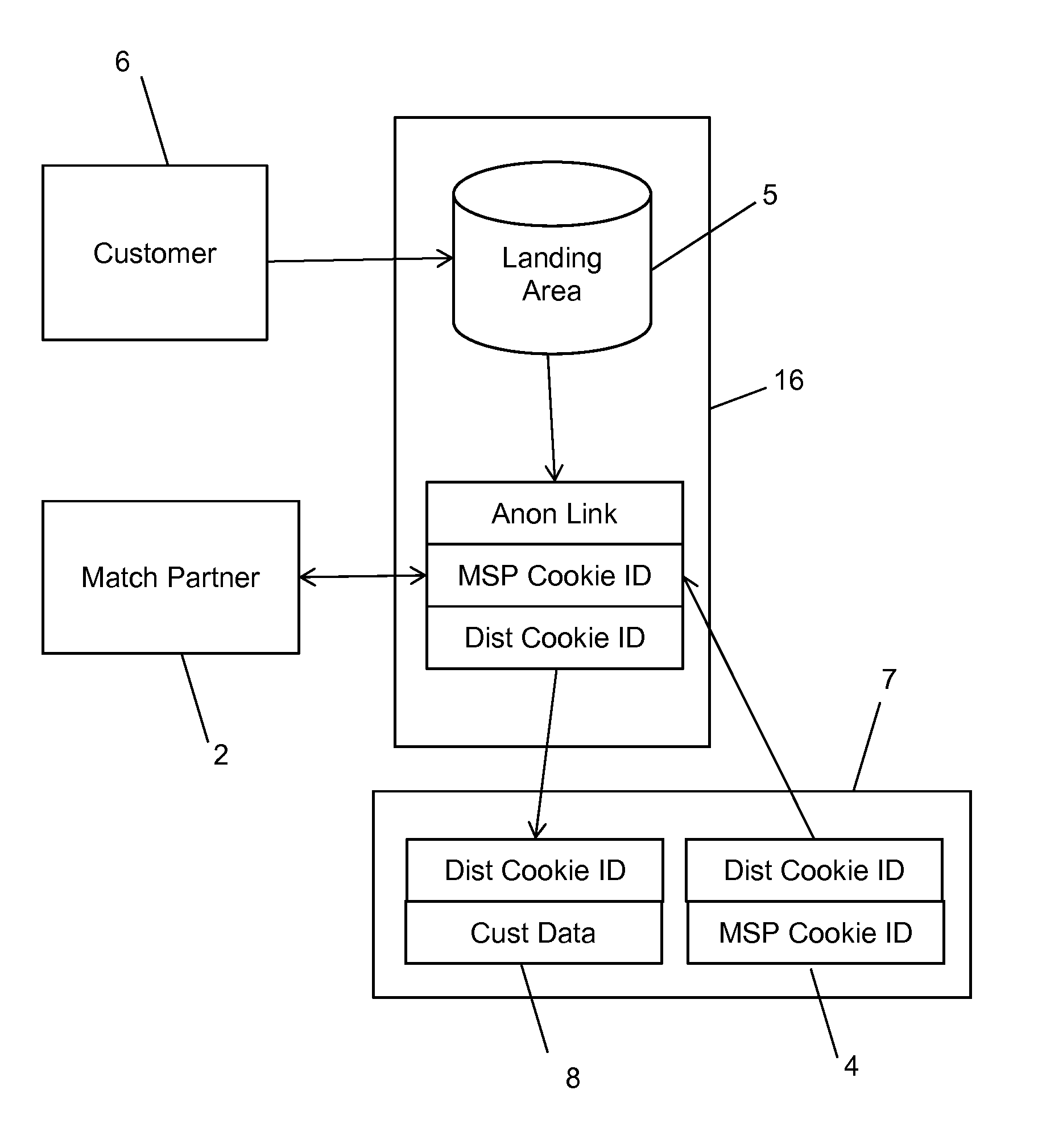
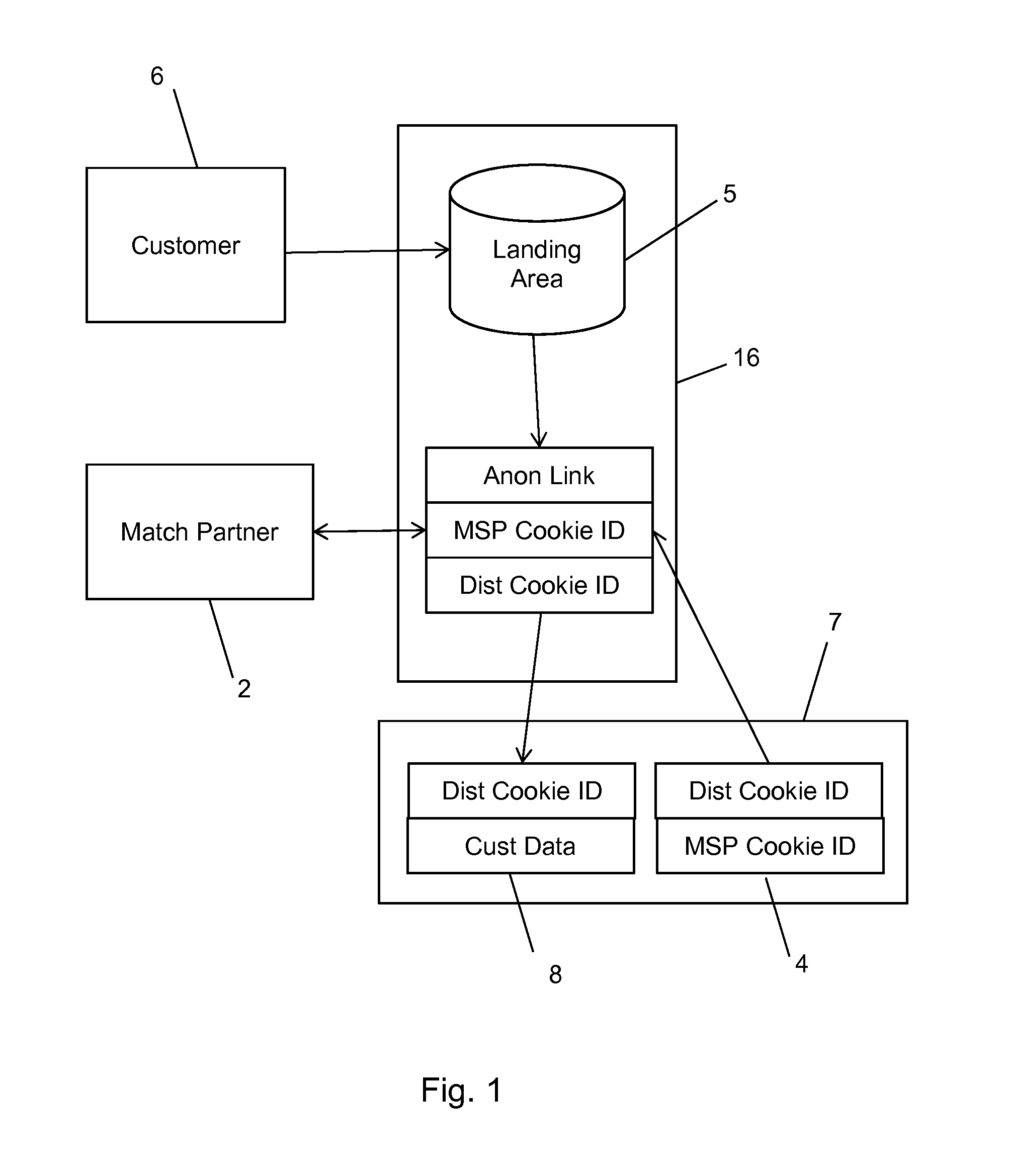
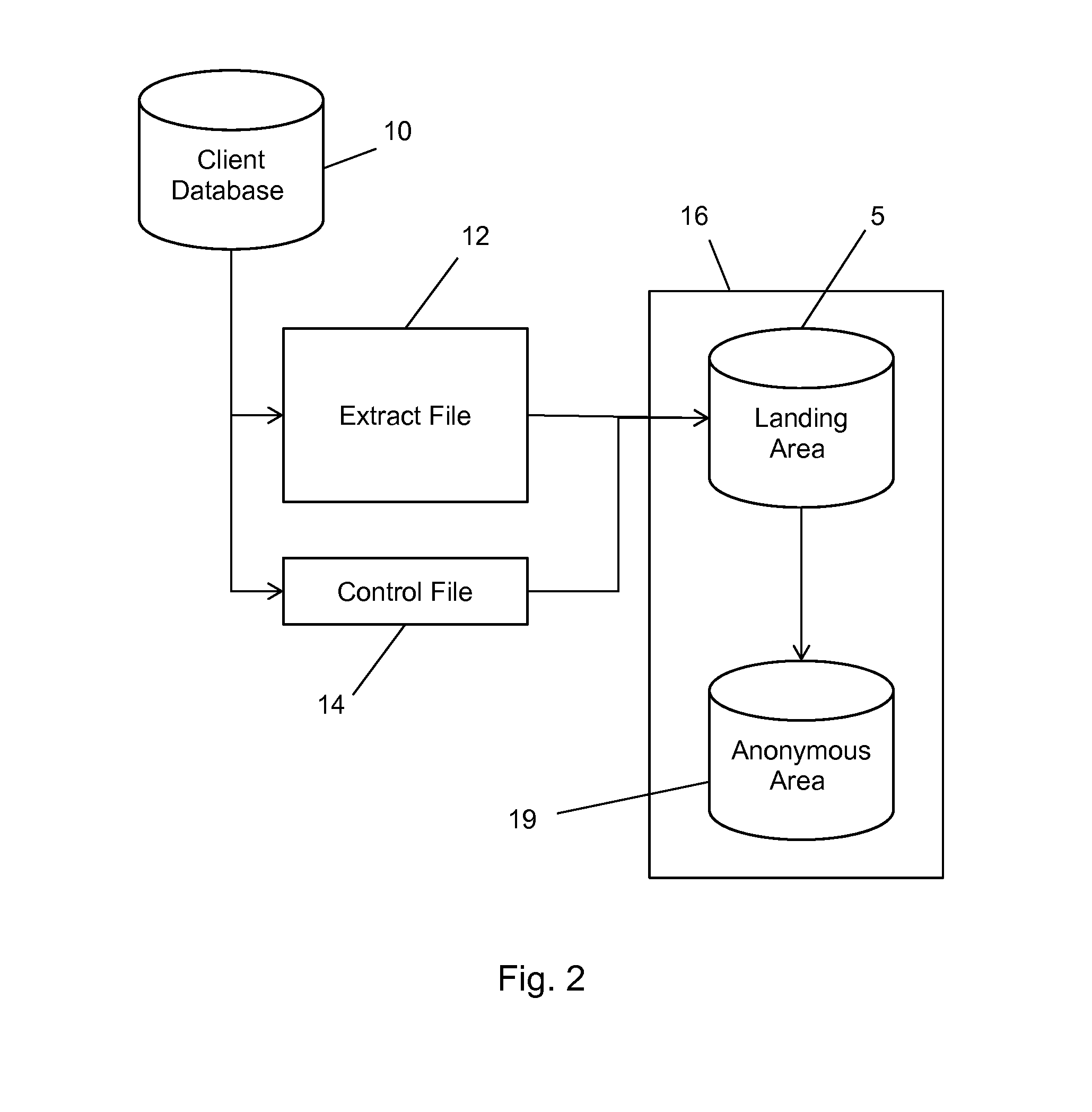
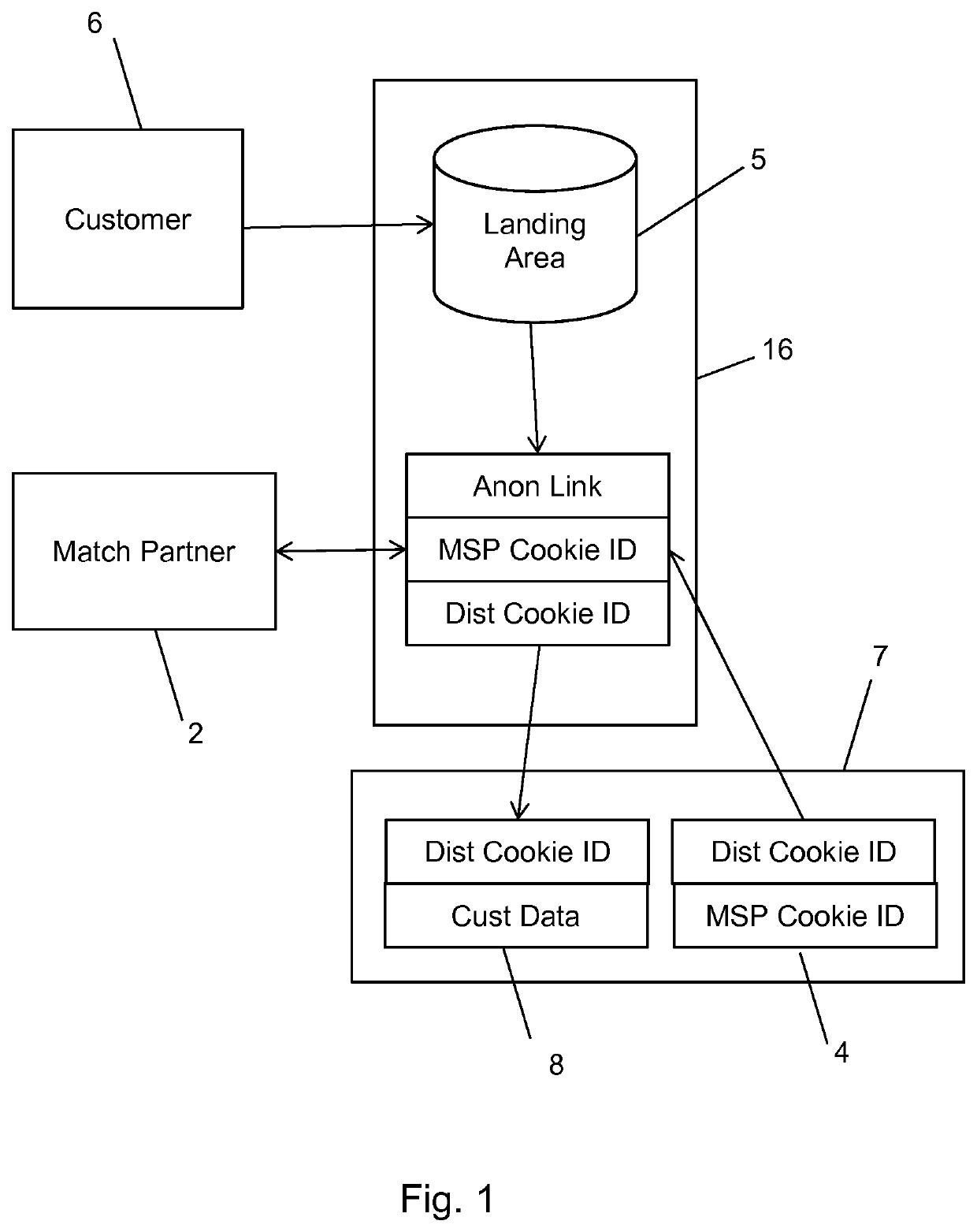
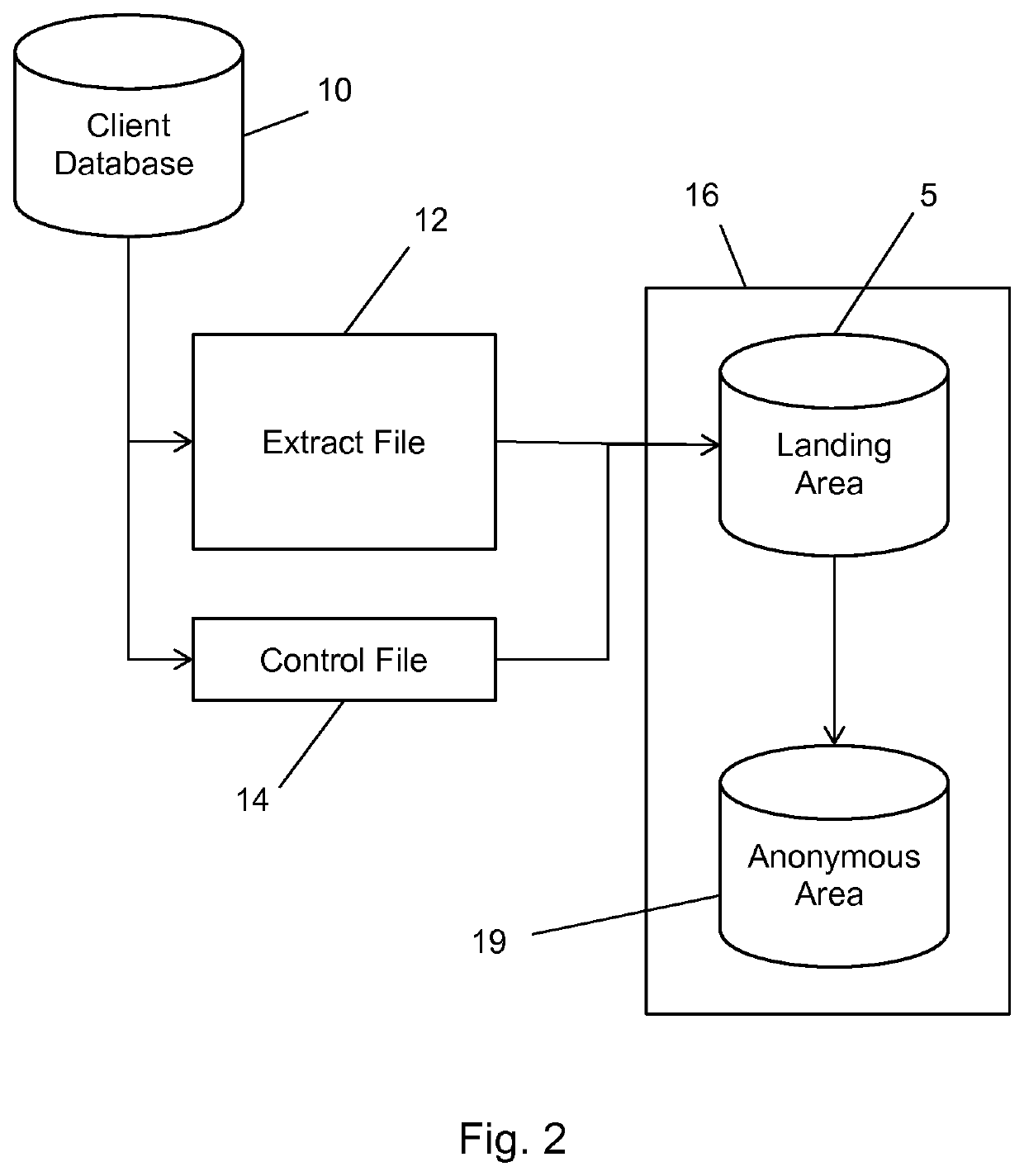
A method and system for bringing together online and offline advertising uses anonymous links that are associated with consumer data. The anonymous links allow processing without personally identifiable information (PII) in a secure environment. Data is matched using the anonymous links, and further using identifiers that are encrypted for use in connection with individual match distribution partners. The method and system allows a marketer to utilize offline data to precisely target advertisements without the use of PII, and to perform analytics concerning the use of the online advertisements to more precisely determine the effectiveness of multichannel marketing efforts.
Owner:LIVERAMP
Method to provide a product to a consumer to protect consumer privacy
InactiveUS20050137940A1Buying/selling/leasing transactionsSpecial data processing applicationsConsumer privacyIndustrial engineering
A method of providing a product to a consumer in which an identity of the product is concealed is disclosed. The method can be useful when a consumer wishes to prevent others from knowing the identity of a product being purchased or otherwise obtained. In particular embodiments of the method, a request is received from the consumer to purchase a product. A disguising packaging material in which to package the requested product is selected. The requested product is packaged with the disguising packaging material to create a custom packaged product. The custom packaged product is provided to the consumer. The customer is billed for the custom packaged product. In certain embodiments, the custom packaged product includes one or more signalers which are scanned to determine information pertaining to the requested product.
Owner:BINFORMA GROUP LIABILITY
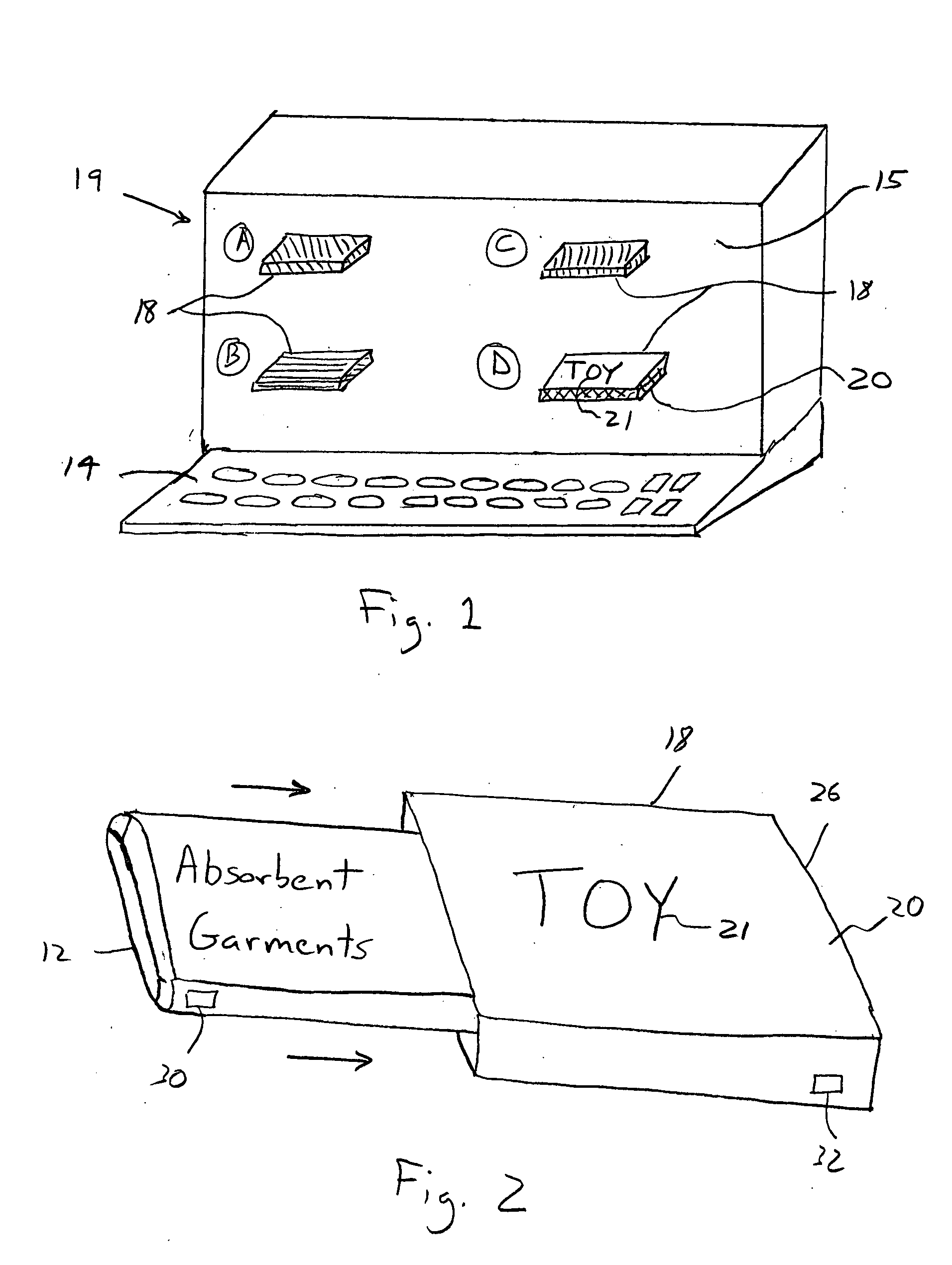
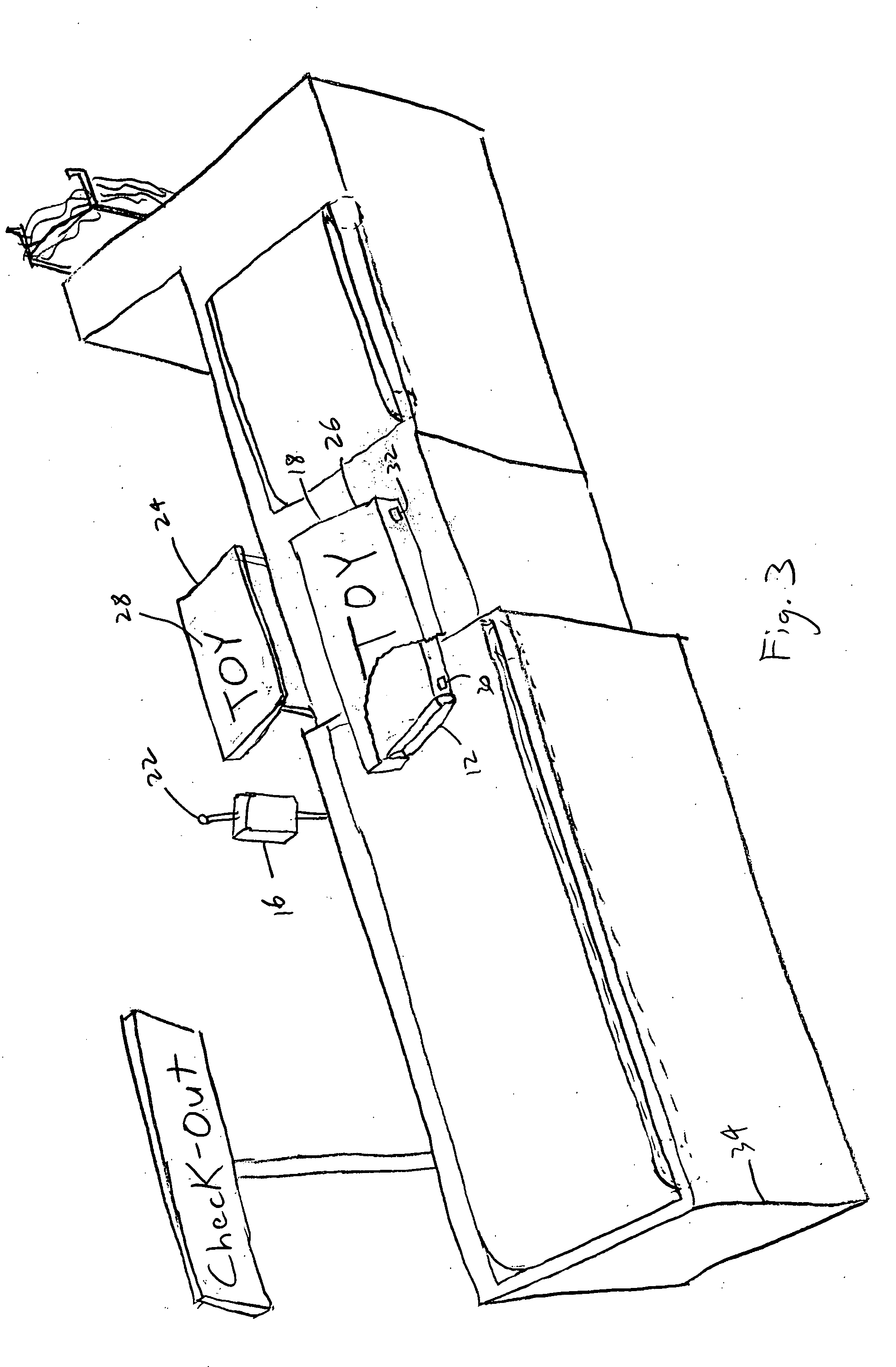
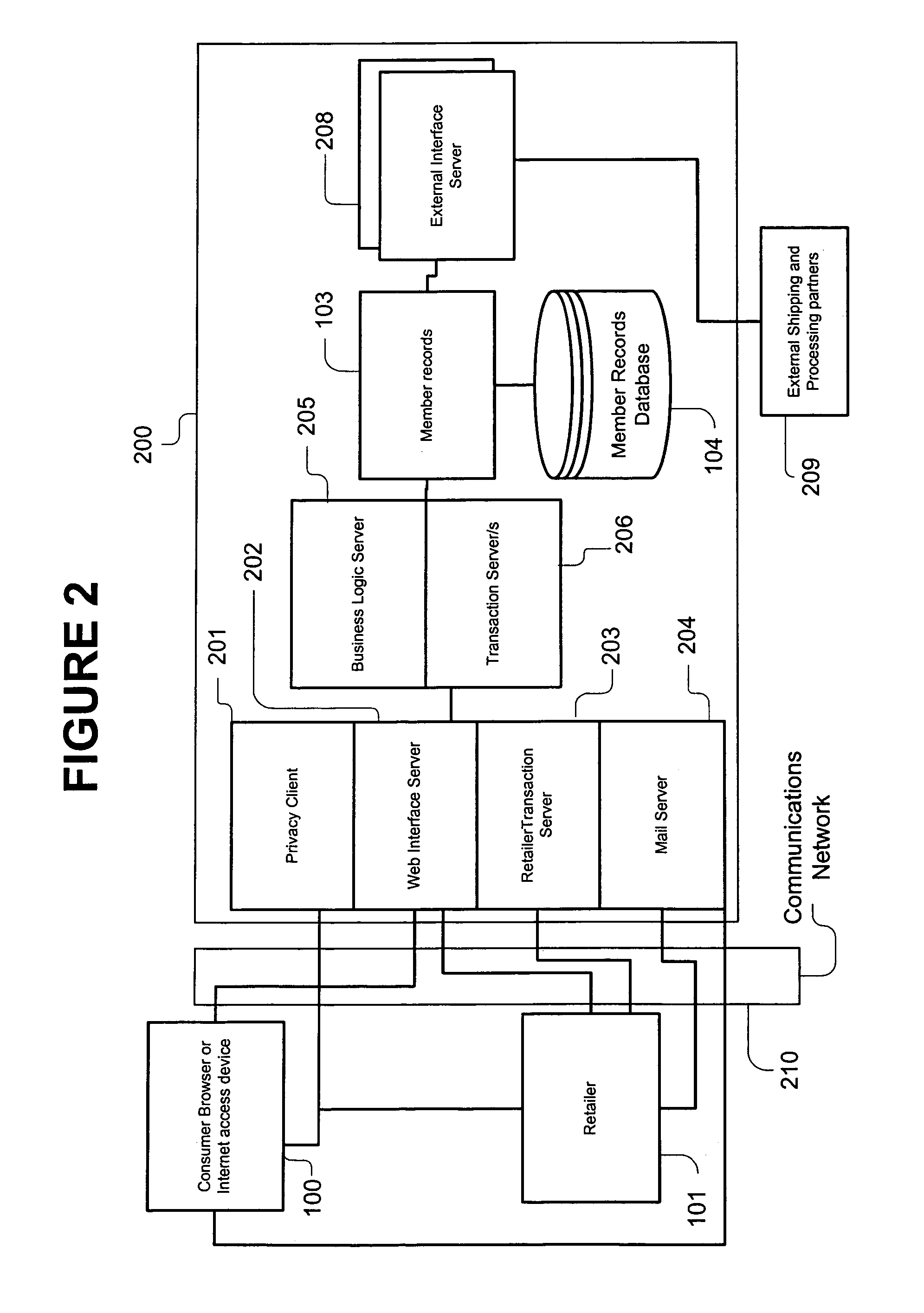
System, method, and computer program product for maintaining consumer privacy and security in electronic commerce transactions
InactiveUS7636696B1Keep it privateDisclosure is limitedComputer security arrangementsBuying/selling/leasing transactionsPaymentInternet privacy
A system, method, and computer program product for maintaining the anonymity of a consumer in a transaction with a retailer. The consumer provides payment method information and ship-to address information to a trusted third party. The consumer purchases products from a retailer by providing the trusted third party anonymous identifiers (e.g., nicknames, unique codes, or one time use codes either supplied by the consumer or by the trusted third party) corresponding to the selected payment methods and ship-to addresses. The retailer requests payment approval from the trusted third party. The trusted third party receives payment approval from a payment partner using the payment method information determined from the anonymous identifier received from the consumer. The trusted third party provides payment approval to the retailer along a transaction unique shipment identifier to place on the parcel. The trusted third party sends the same transaction unique shipment identifier and the actual shipping address determined from the anonymous identifier received from the consumer to a shipping partner who re-labels the package and delivers it to the consumer. The trusted third party acts as an e-mail conduit for messages sent to member consumers.
Owner:MEGASOFT
RFID and robots for multichannel shopping
InactiveUS9747480B2Prevent promiscuous transmissionConvenient timeLogperiodic antennasAntenna supports/mountingsComputer scienceConsumer privacy
The present invention relates to systems, methods, and devices for consumers using RFID-tagged items for multichannel shopping using smartphones, tablets, and indoor navigation, preservation of consumer's privacy related to RFID-tagged items that they leave a retail store with, and automatically reading and locating retail inventory without directly using store labor. Robots and aerial mobile automated RFID reading devices are disclosed.
Owner:ADASA
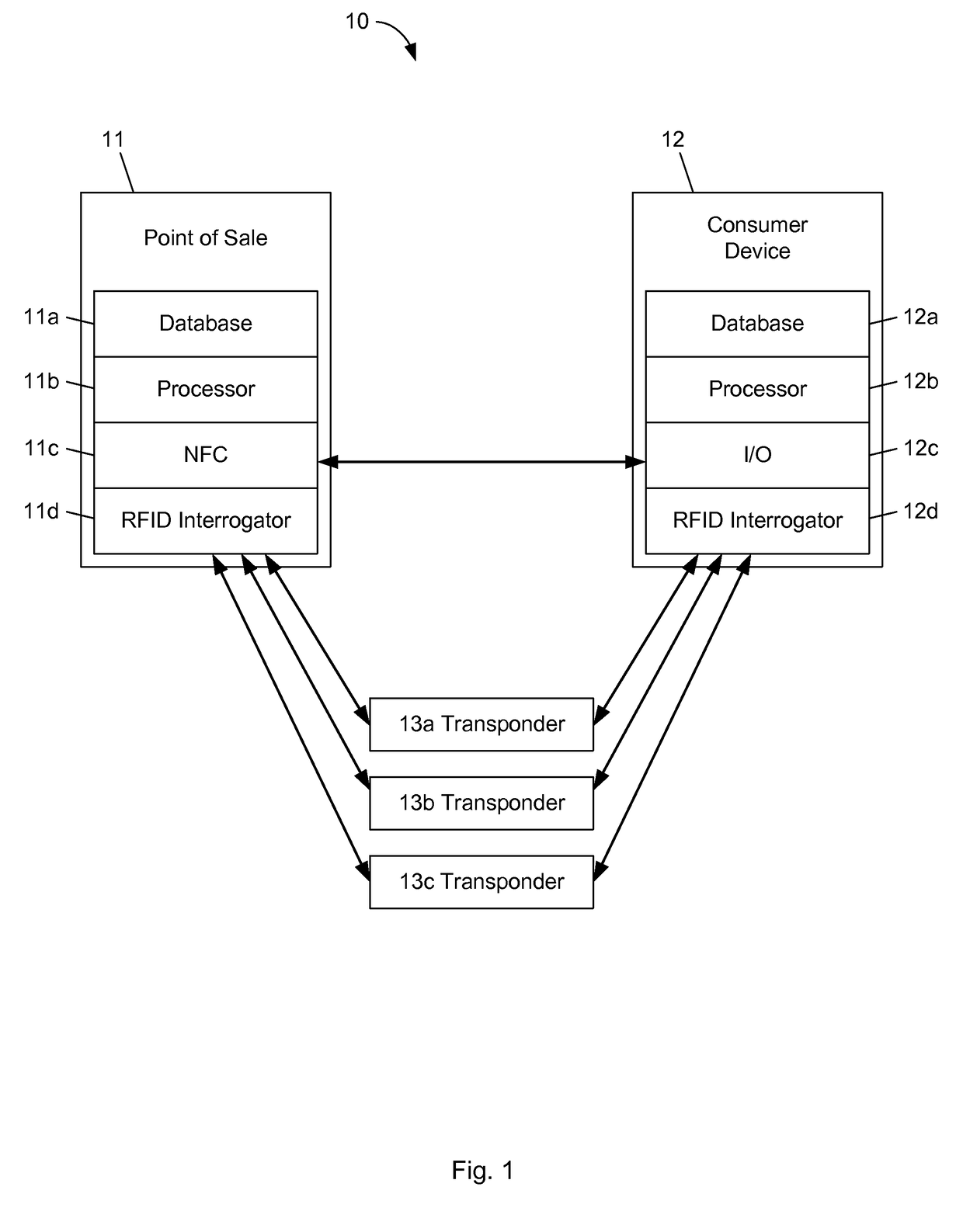
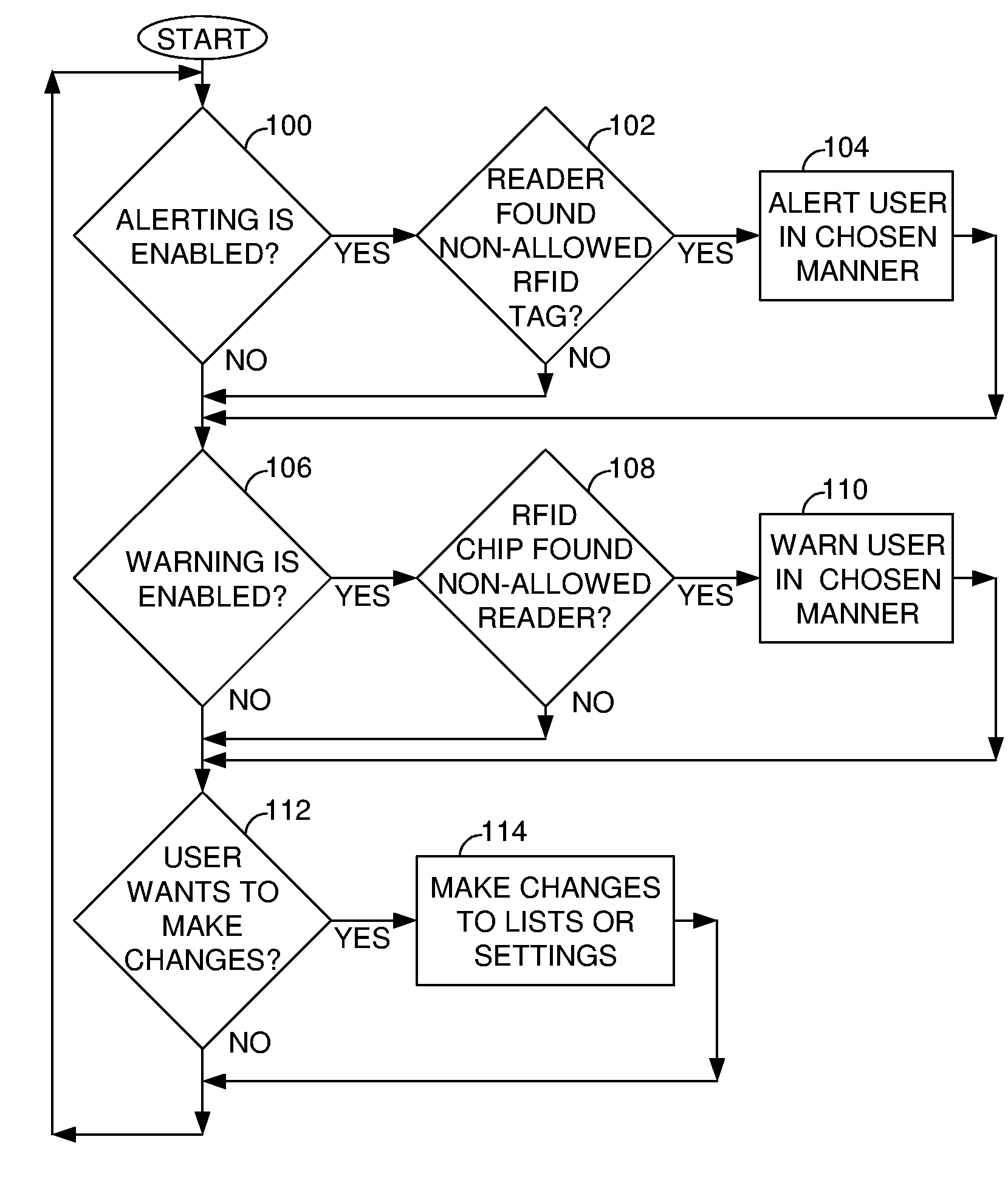
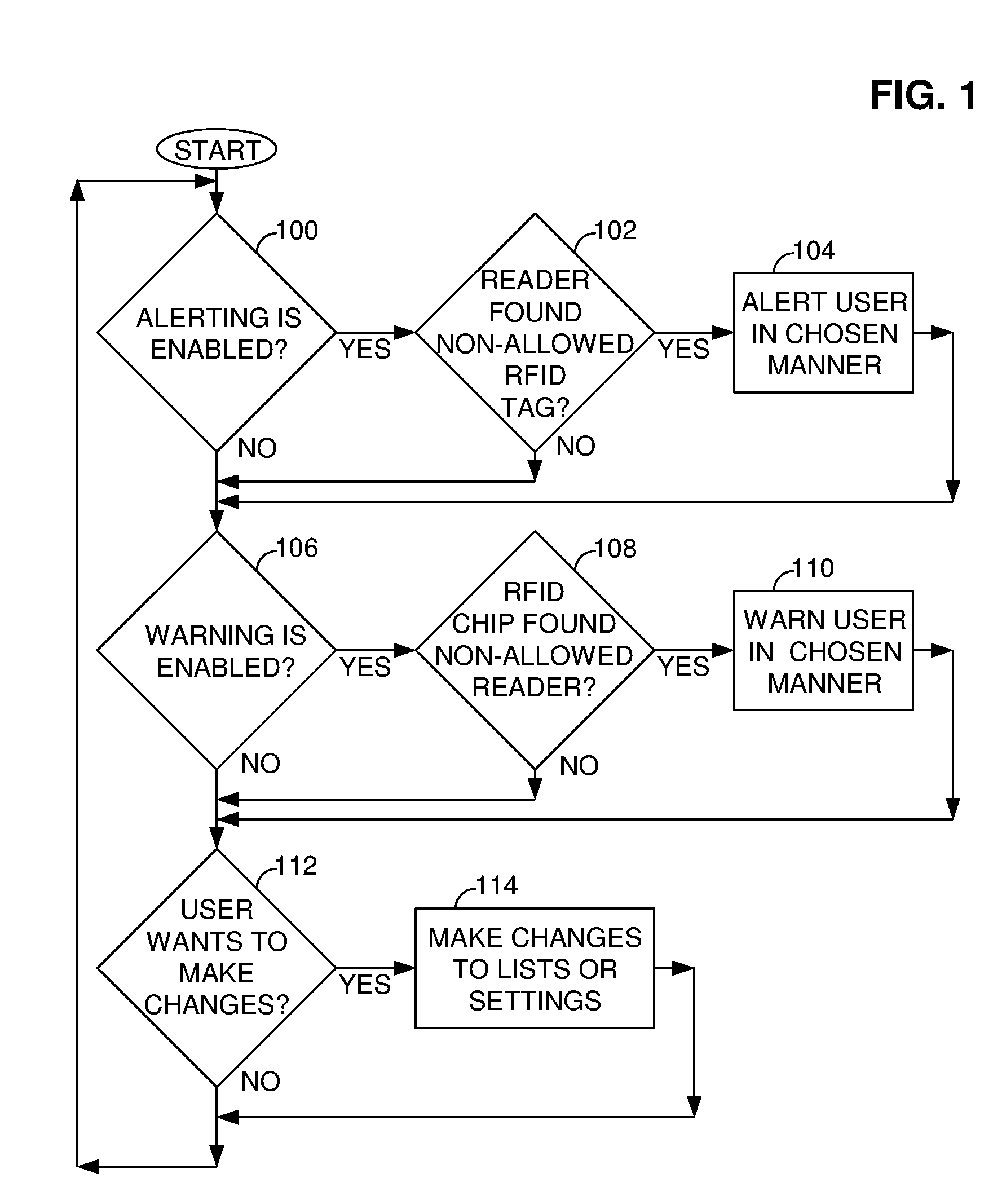
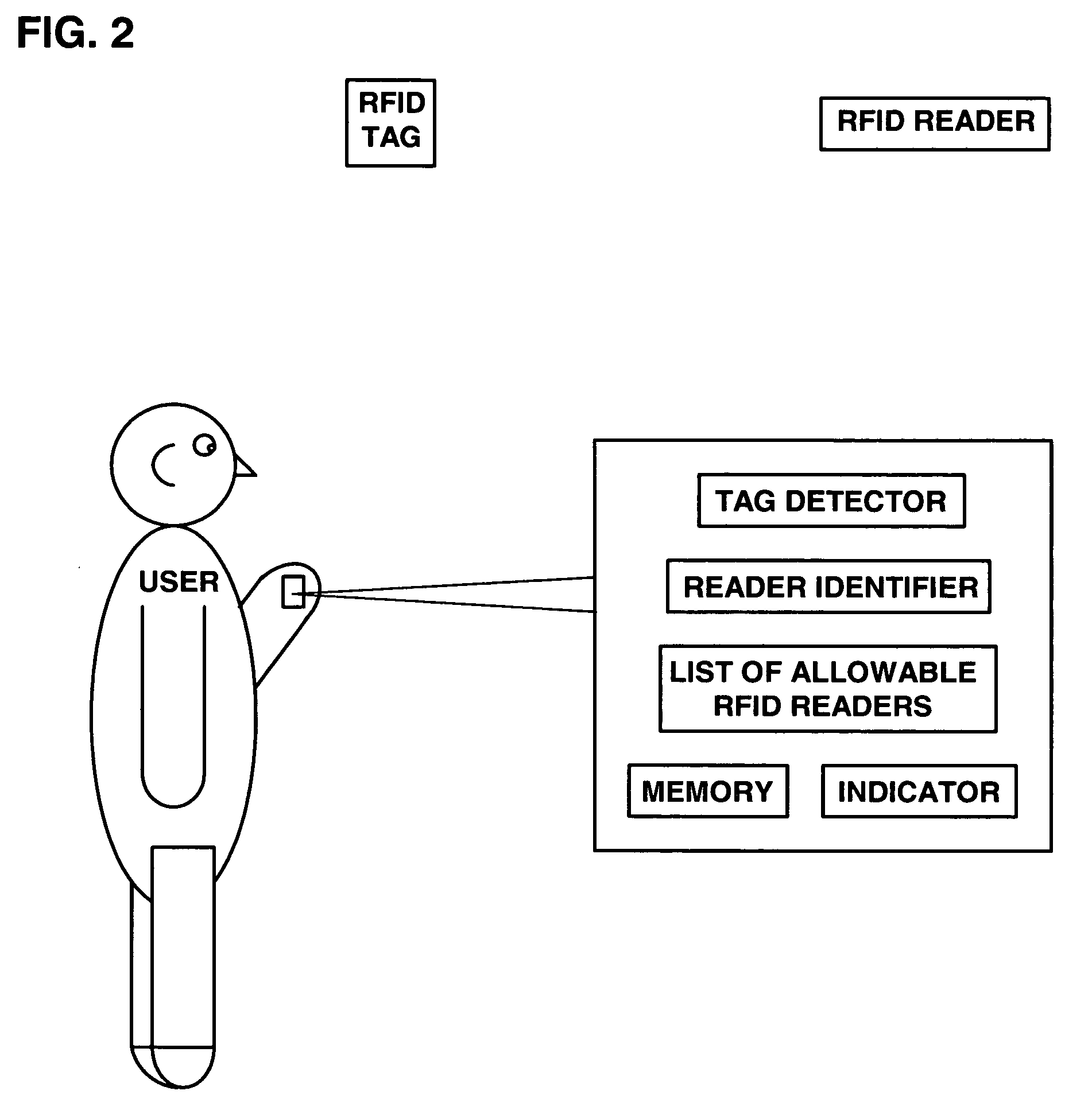
Anti-tracking system to ensure consumer privacy
ActiveUS7086587B2Memory record carrier reading problemsPayment architectureDisplay deviceUser privacy
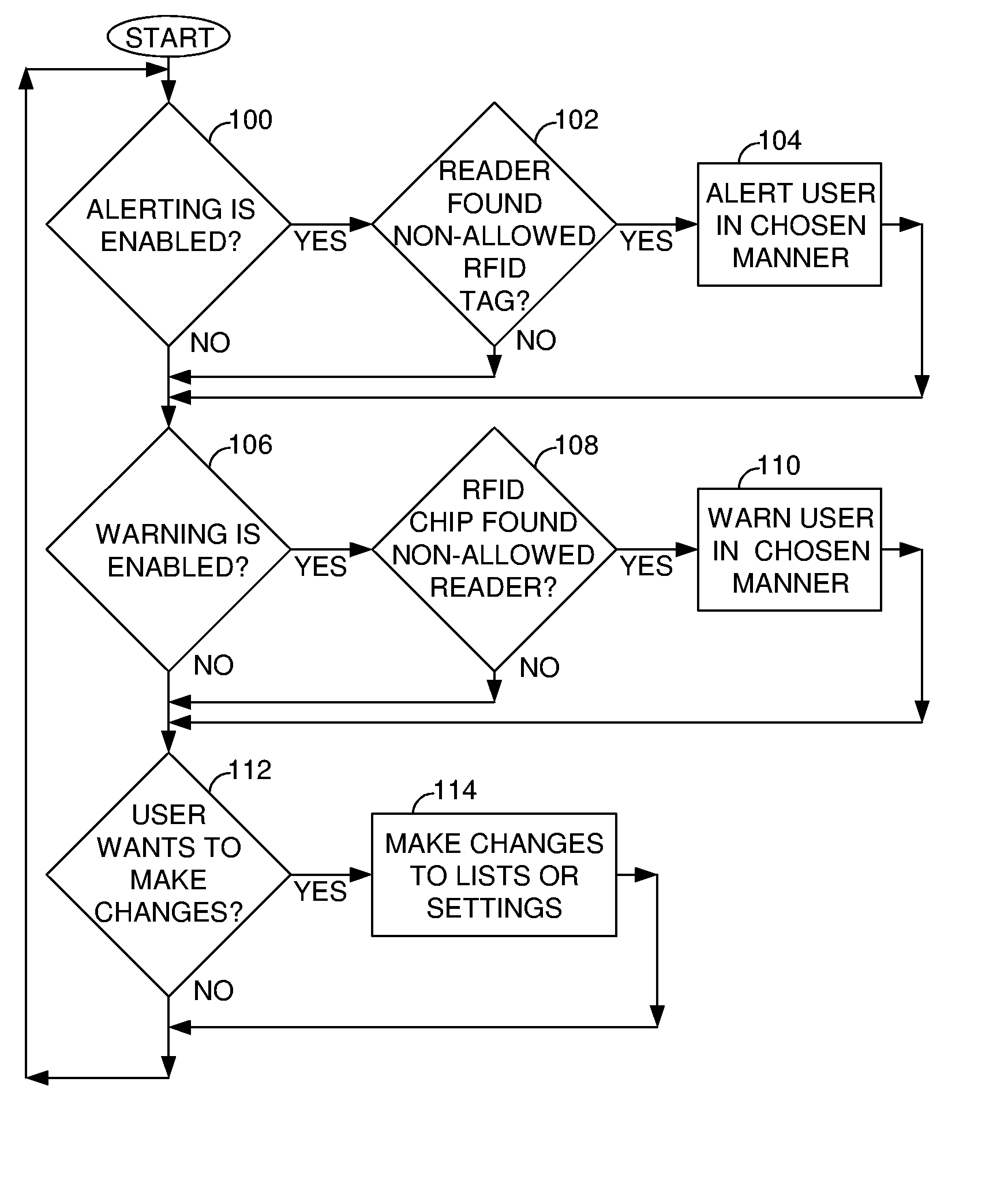
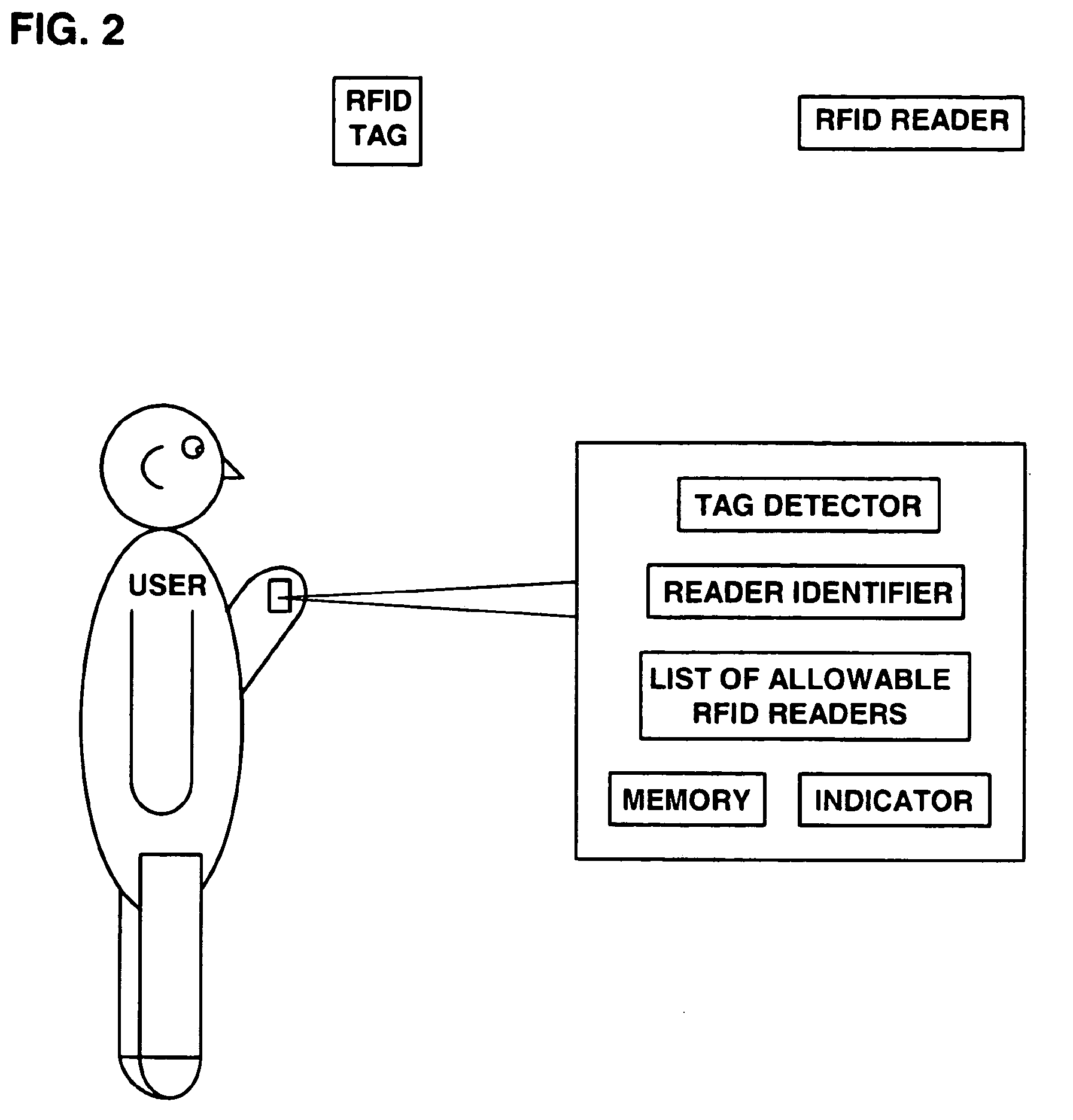
A system, method and computer program product for enabling a user to detect nearby RFID tags and identify nearby RFID readers to enhance user privacy. A portable RFID reader scans for nearby tags, and a universal RFID tag detects nearby readers. The invention can alert the user of nearby RFID tags or readers, unless the user has disabled the alerting feature or unless a particular tag or reader is already known to the user and has been deemed allowable. A memory includes editable lists of allowable tags and readers. Exemplary alerts include outputs from a sound emitter, a vibrator, a light, or a display readout. The invention thus prevents surreptitious identification and tracking of a user and a user's possessions. The invention may be integrated into items typically carried by users so that the detection and alerting may be performed without outward indication.
Owner:IBM CORP
Apparatus and Method for Bringing Offline Data Online While Protecting Consumer Privacy
ActiveUS20150081565A1Precise positioningIncreased marketingAdvertisementsComputer security arrangementsInternet privacyOnline and offline
A method and system for bringing together online and offline advertising uses anonymous links that are associated with consumer data. The anonymous links allow processing without personally identifiable information (PII) in a secure environment. Data is matched using the anonymous links, and further using identifiers that are encrypted for use in connection with individual match distribution partners. The method and system allows a marketer to utilize offline data to precisely target advertisements without the use of PII, and to perform analytics concerning the use of the online advertisements to more precisely determine the effectiveness of multichannel marketing efforts.
Owner:LIVERAMP
Individually Controlled and Protected Targeted Incentive Distribution System
A targeted information and incentive distribution system that protects consumer privacy and analyzes individuals', including individual households' or individual groups, purchase histories obtained from several retailers and other providers of goods and / or services to determine targeted information and / or incentives to deliver to individuals. Purchase history and other relevant data for each individual user are accumulated at a computer that is under the control of that user and analyzed to determine which targeted information items and / or incentives to deliver to that individual user. Purchase history data in the exemplary embodiment is only maintained at the user's computer so as to increase the privacy for the user of this extensive purchase history data that was derived from multiple sources. Abridged purchase history data that does not contain information to identify the individual to which it pertains is uploaded for comprehensive analysis to develop future purchase incentive programs.
Owner:COPE DANIEL P +1
Database clone
ActiveUS20130110770A1Digital data information retrievalData processing applicationsPaymentInternet privacy
Embodiments of the invention relate to systems and methods for cloning a production database for quality assurance (QA) by the merchant users. A QA user may request tokens, card types and other data associated with a payment device for quality assurance purposes. The payment network redirects the QA request to a go-between database that is present between the QA user and the production environment of the payment network rather than pull the information directly from the production environment. As a result, the merchant is able to use tokens for testing, without violating consumer privacy and security rules and regulations (e.g., PCI rules). The QA user does not have to create a customized testing solution.
Owner:VISA INT SERVICE ASSOC
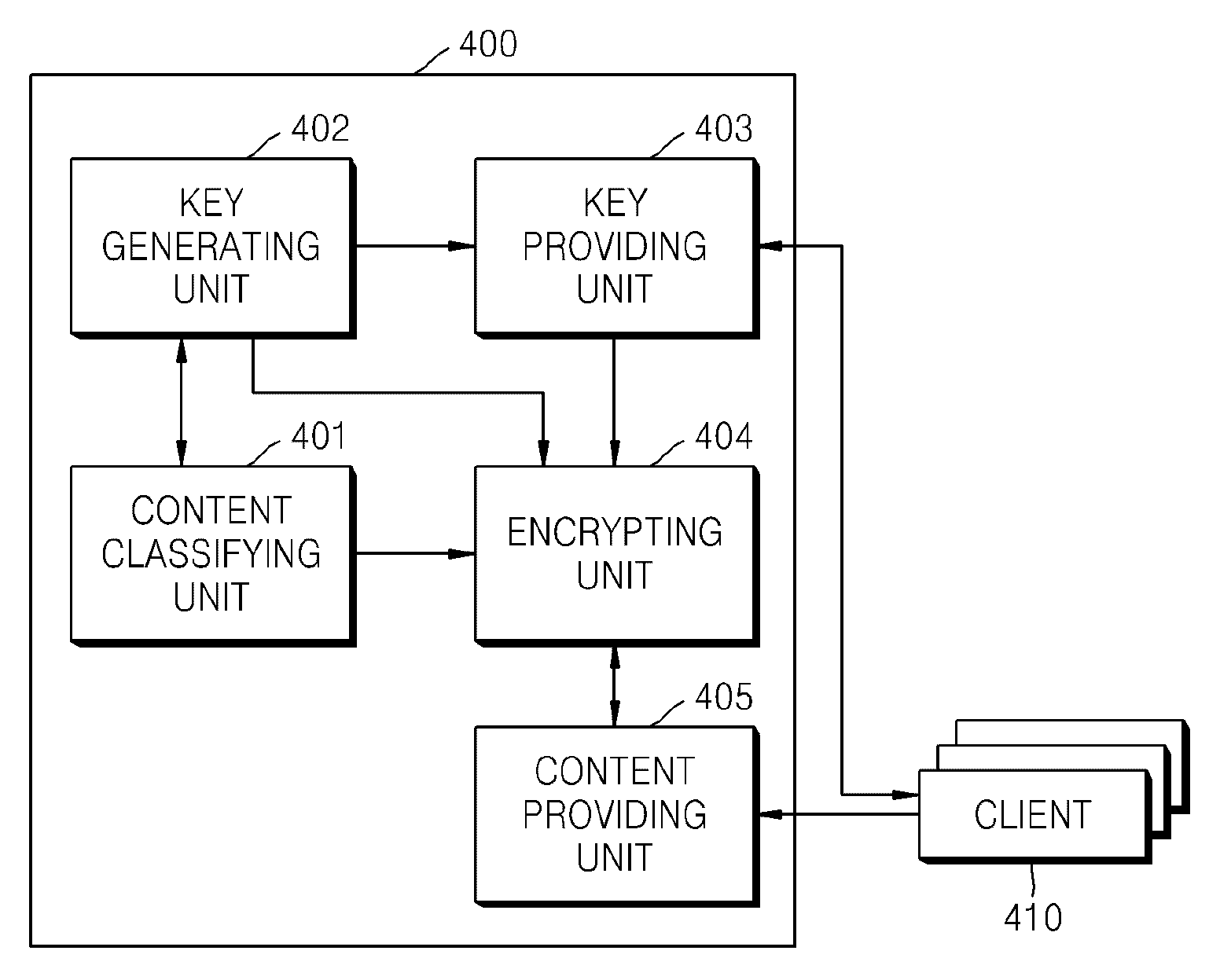
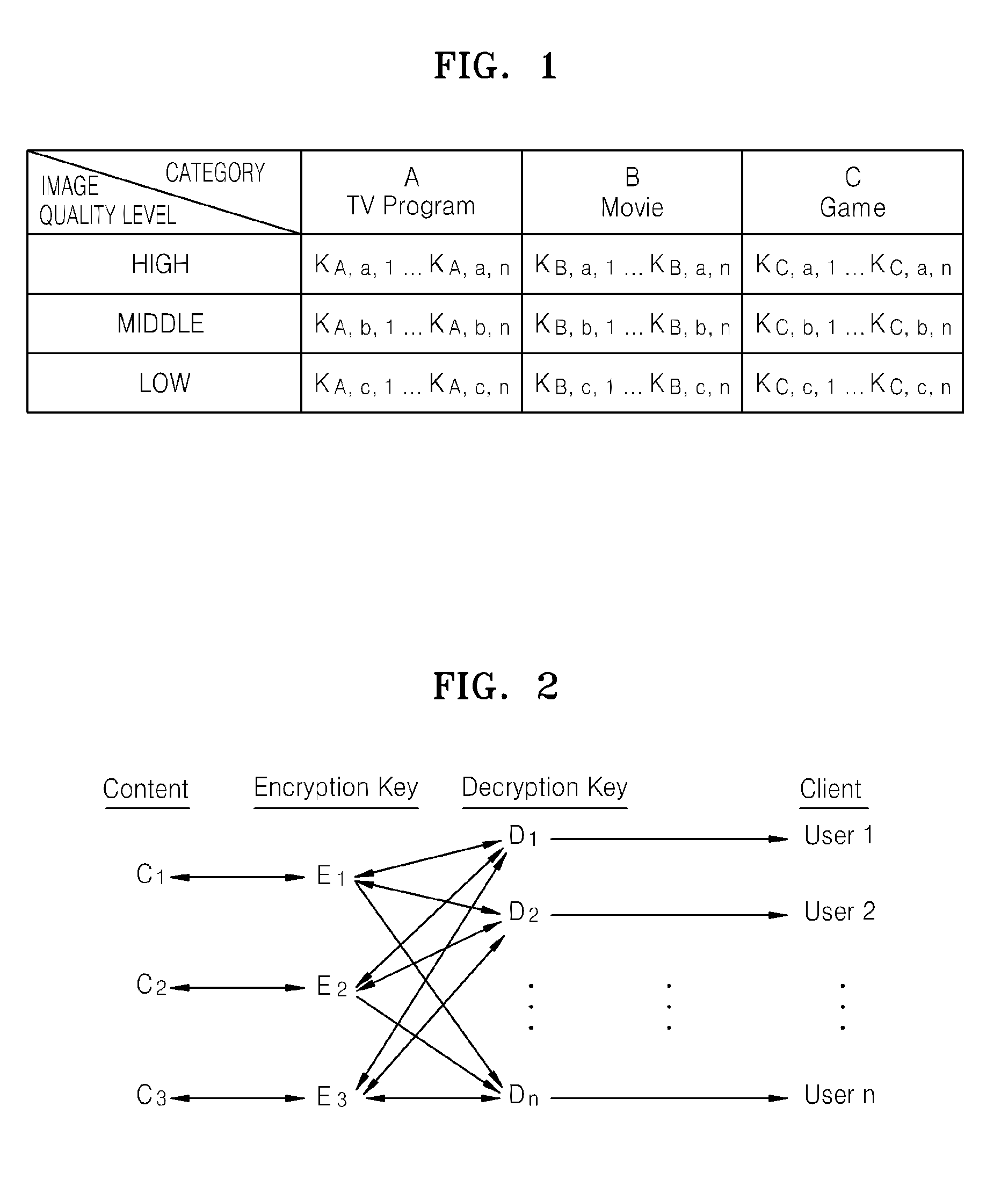
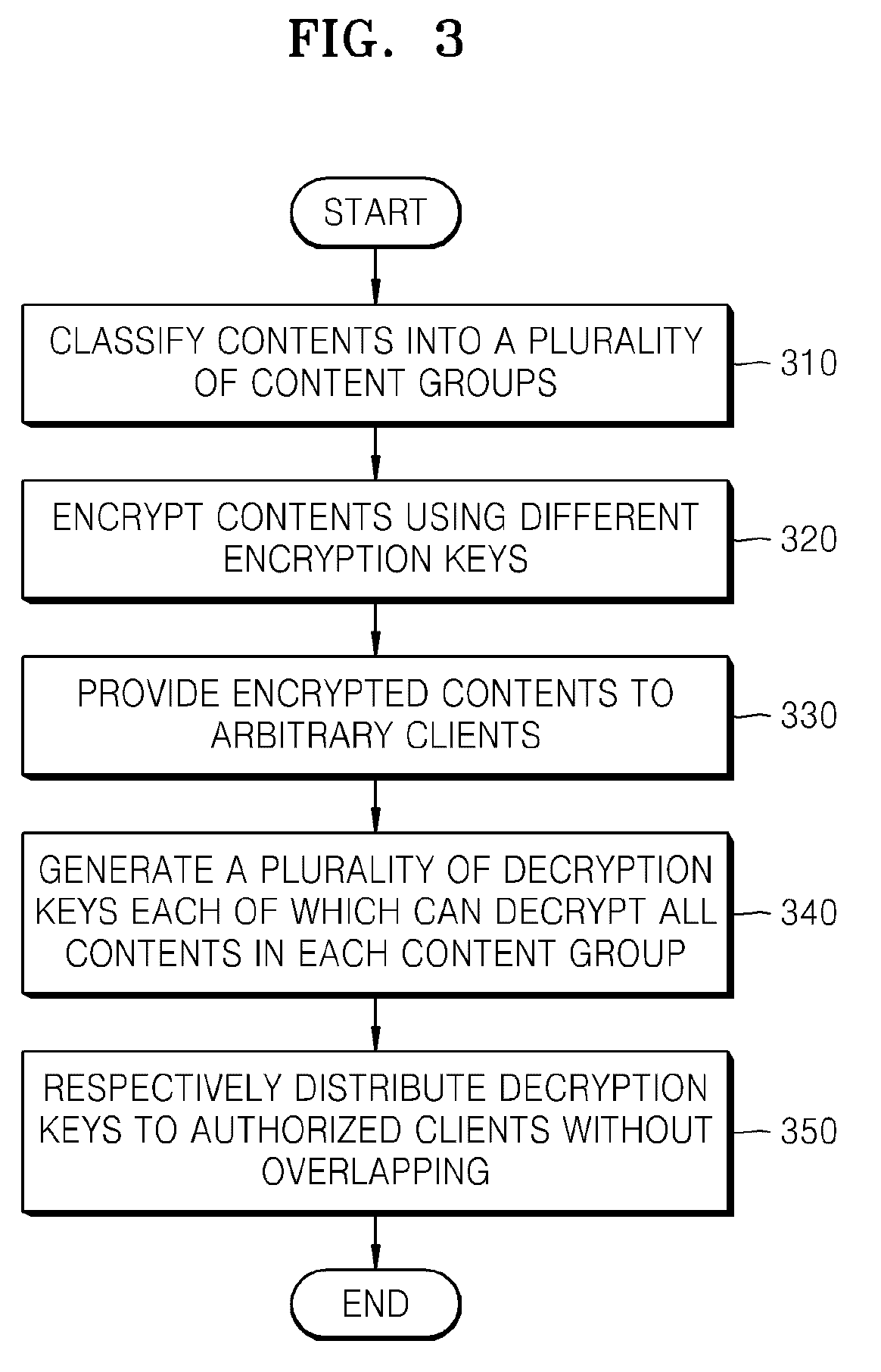
Method and apparatus for protecting content consumer's privacy
InactiveUS20090067622A1Key distribution for secure communicationMultiple keys/algorithms usageClient-sideConsumer privacy
Provided is a method of protecting a content consumer's privacy. The method includes classifying contents into content groups, encrypting the contents using different encryption keys, generating a plurality of decryption keys each of which can decrypt all contents in each of the content groups, and provides the generated decryption keys to authorized clients, wherein each client is provided with a different decryption key.
Owner:SAMSUNG ELECTRONICS CO LTD
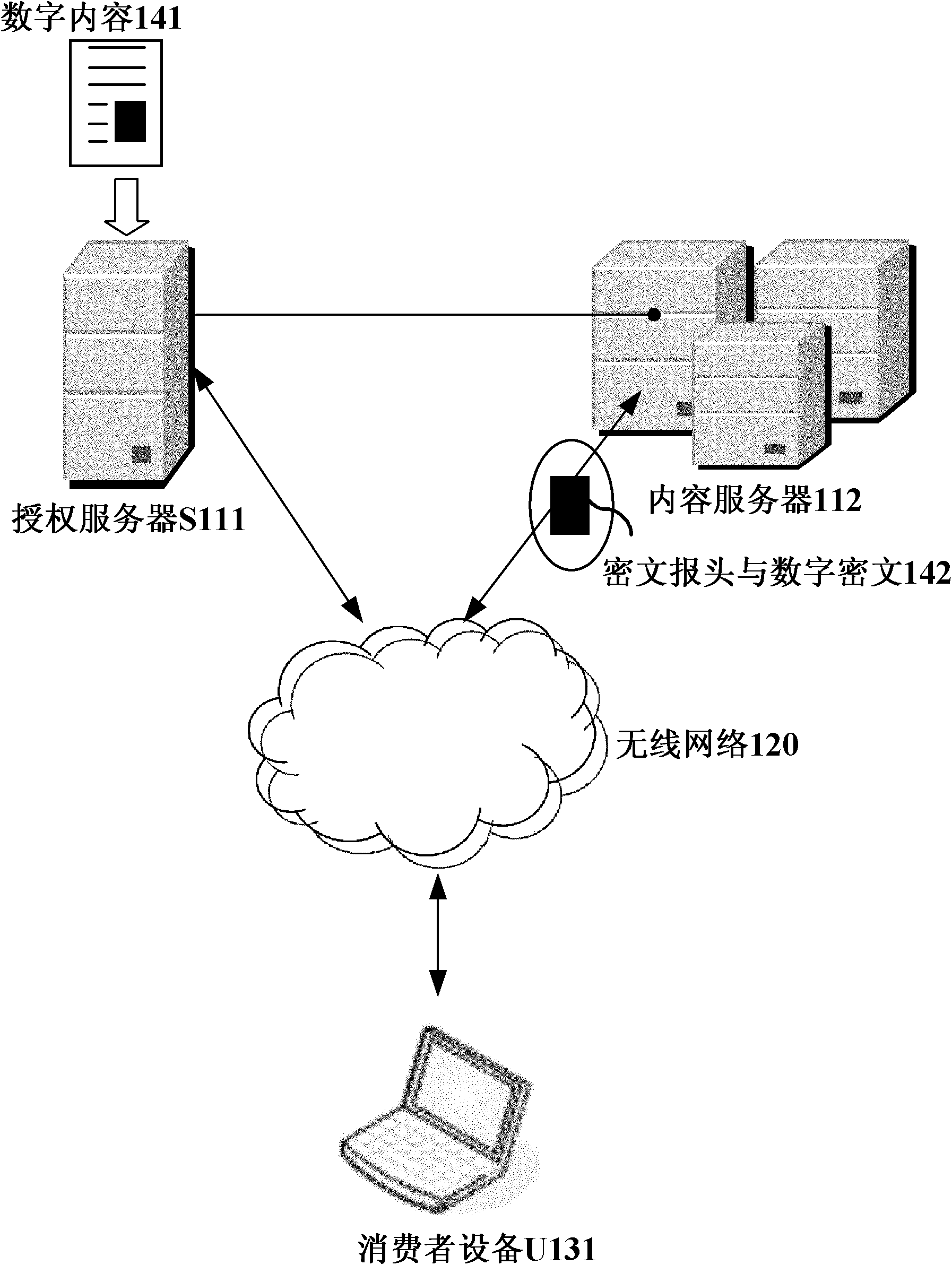
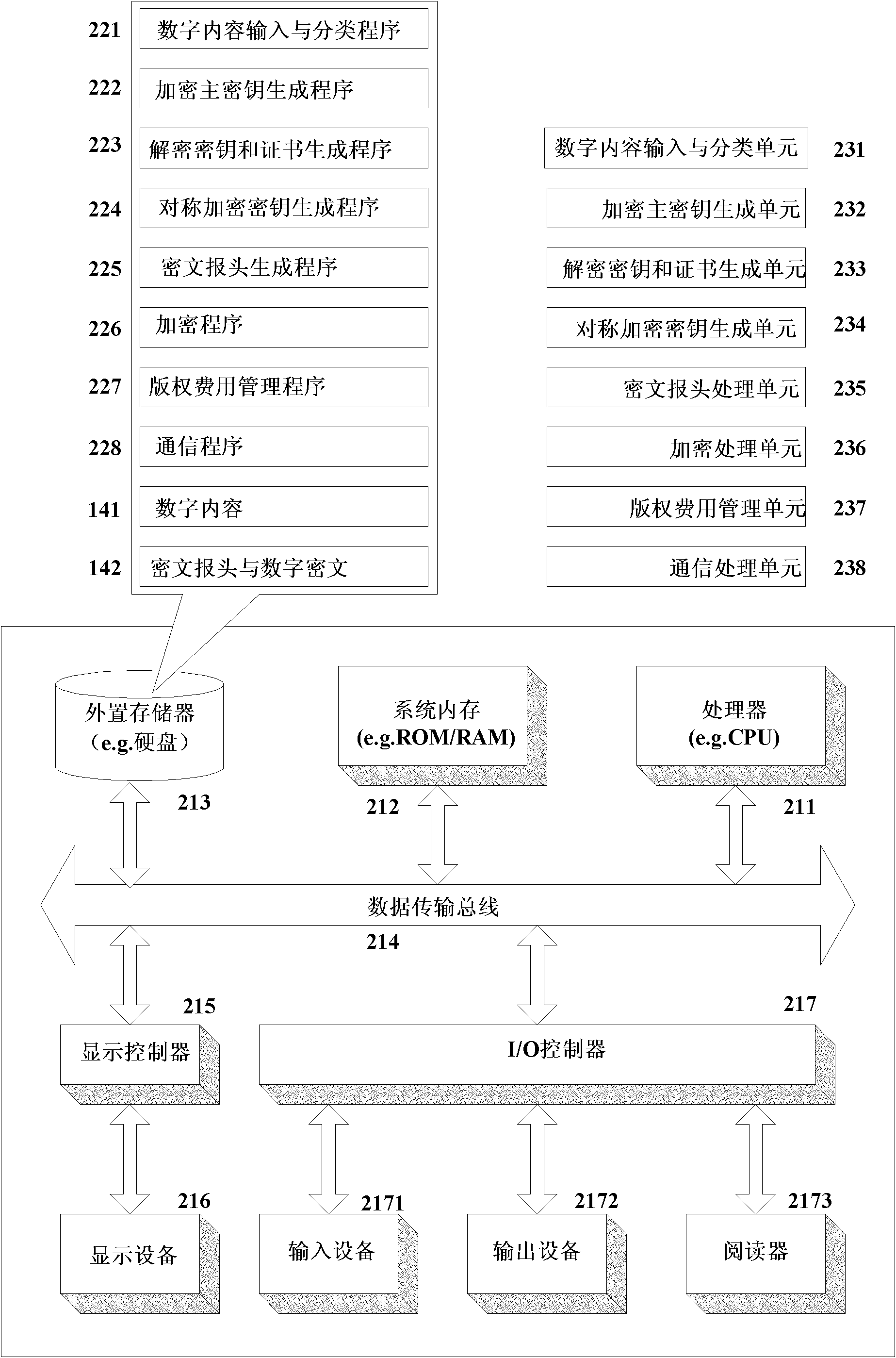
Digital copyright management method and device for protecting digital content consumer privacy
InactiveCN102025507APrivacy protectionPrevent Tampering AttacksUser identity/authority verificationProgram/content distribution protectionHash functionCiphertext
The invention discloses a digital copyright management method and device for protecting digital content consumer privacy. The method comprises the following steps: randomly generating an encrypted master key by utilizing the Chameleon hash function, and generating a copyright license; grouping the digital contents, then generating different symmetrical encrypted keys and cryptograph headers according to different groups of digital contents by adopting the Diffie-Hellman key exchange technology, encrypting the digital contents to acquire digital cryptographs, and then, storing the cryptograph headers and the digital cryptographs into a content server; and as required by users, decrypting from the cryptograph headers by utilizing the copyright license to acquire the symmetrical encrypted keys of the authorized digital contents, and then, decrypting the corresponding digital cryptographs to acquire the required digital contents. The device comprises an authorized server, a content serverand consumer equipment. Under the same security level, the invention can reduce the calculated amount, save the storage space and lower the requirements for network bandwidth.
Owner:JINAN UNIVERSITY
Anti-tracking system to ensure consumer privacy
ActiveUS20060131375A1Memory record carrier reading problemsPayment architectureUser privacySystems approaches
A system, method and computer program product for enabling a user to detect nearby RFID tags and identify nearby RFID readers to enhance user privacy. A portable RFID reader scans for nearby tags, and a universal RFID tag detects nearby readers. The invention can alert the user of nearby RFID tags or readers, unless the user has disabled the alerting feature or unless a particular tag or reader is already known to the user and has been deemed allowable. A memory includes editable lists of allowable tags and readers. Exemplary alerts include outputs from a sound emitter, a vibrator, a light, or a display readout. The invention thus prevents surreptitious identification and tracking of a user and a user's possessions. The invention may be integrated into items typically carried by users so that the detection and alerting may be performed without outward indication.
Owner:IBM CORP
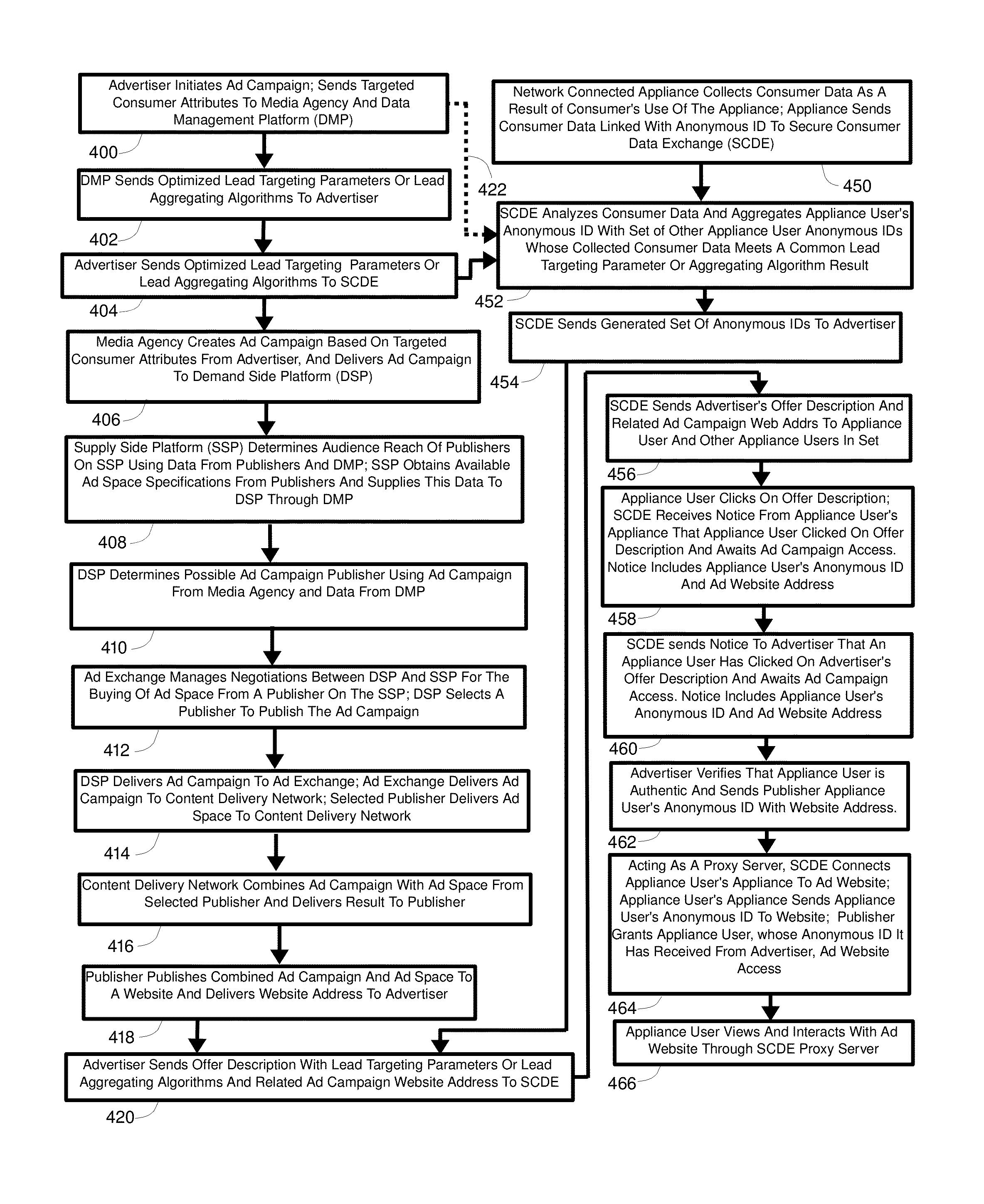
Secure consumer data exchange method, apparatus, and system therfor
InactiveUS8799053B1Enhanced anonymityEasy to followDigital data protectionTransmissionNetwork connectionInternet privacy
A method, system, and apparatus for consumer authorized collection and communication of consumer data, while facilitating compliance with government consumer privacy legislation and regulations, is provided. Authorization is obtained from a user of a network connected appliance to collect and communicate to other entities consumer data resulting from the user's use of the appliance. The data is encrypted, linked with an appliance user anonymous identifier and communicated to a first entity, where it is analyzed by the use of defined parameters. Based on this analysis, the anonymous identifier of the appliance user is aggregated with anonymous identifiers linked with the consumer data of other appliance users whose consumer data has at least one parameter in common with the consumer data of the appliance user. The aggregate set of anonymous identifiers is provisioned to a second entity by the first entity. Subsequent interaction with the first entity provides the second entity with access to the appliance user of the appliance without revealing the identity of the appliance user or providing access to the appliance user's consumer's data.
Owner:GOLDBERG PAUL R
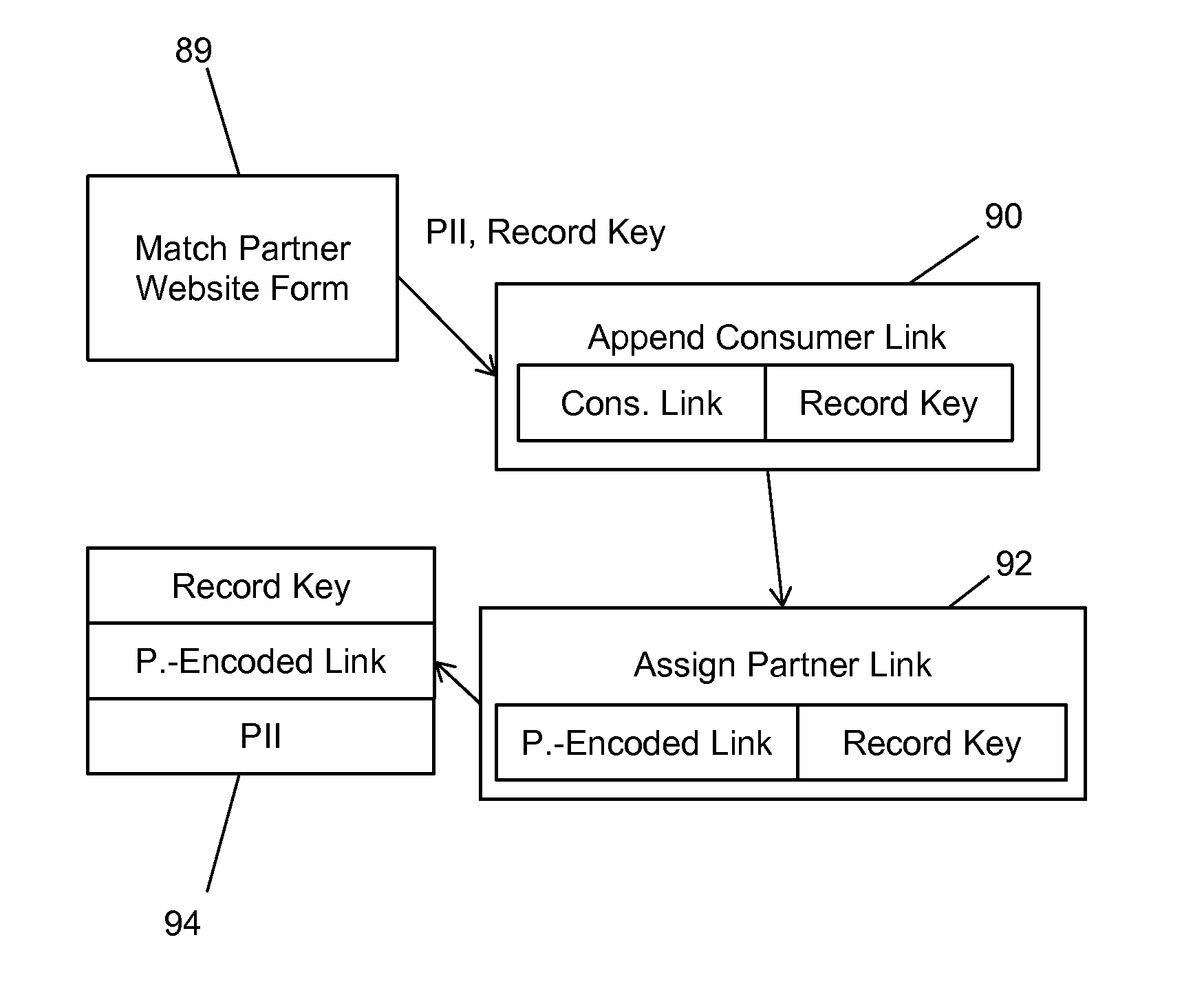
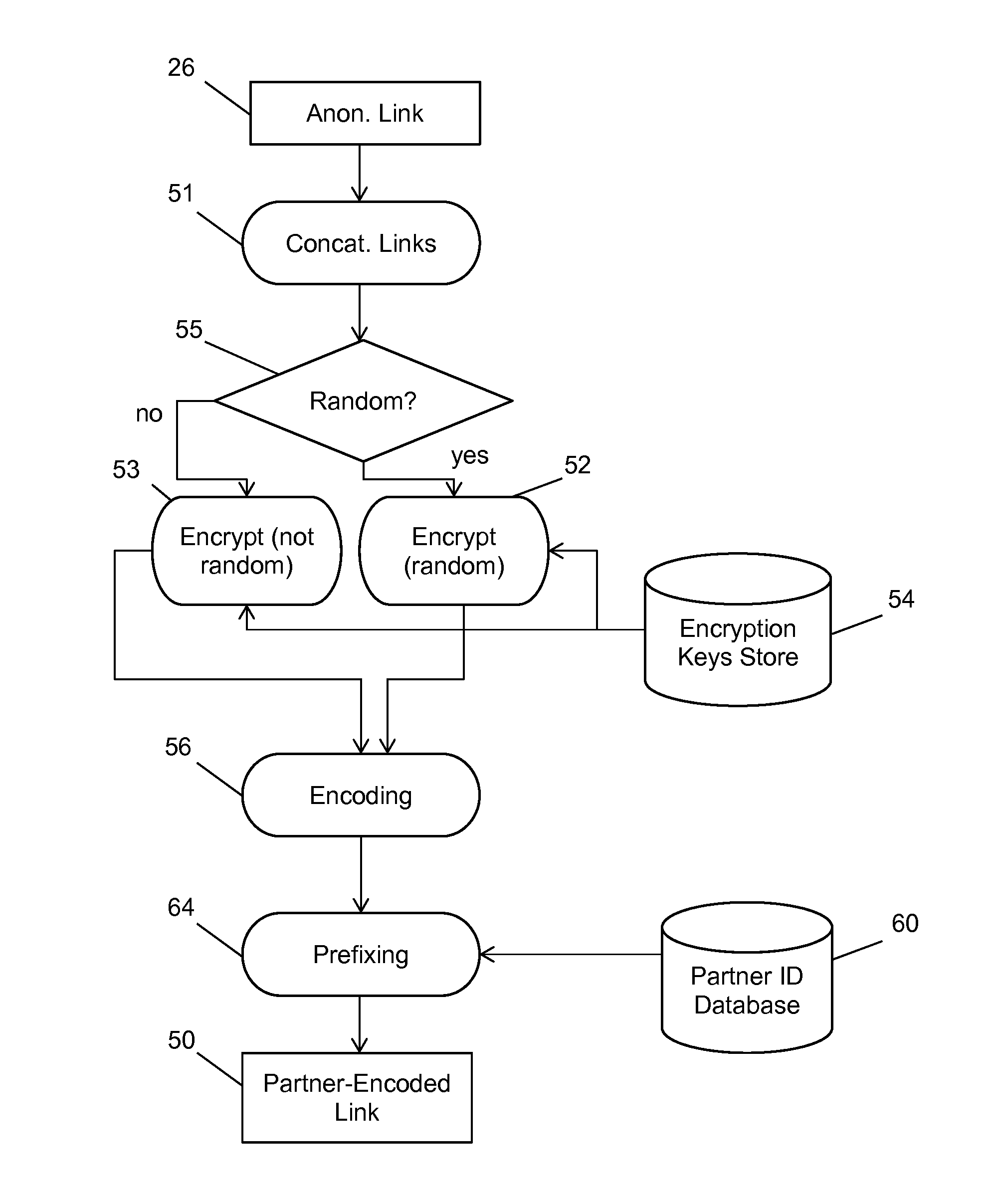
Partner Encoding of Anonymous Links to Protect Consumer Privacy
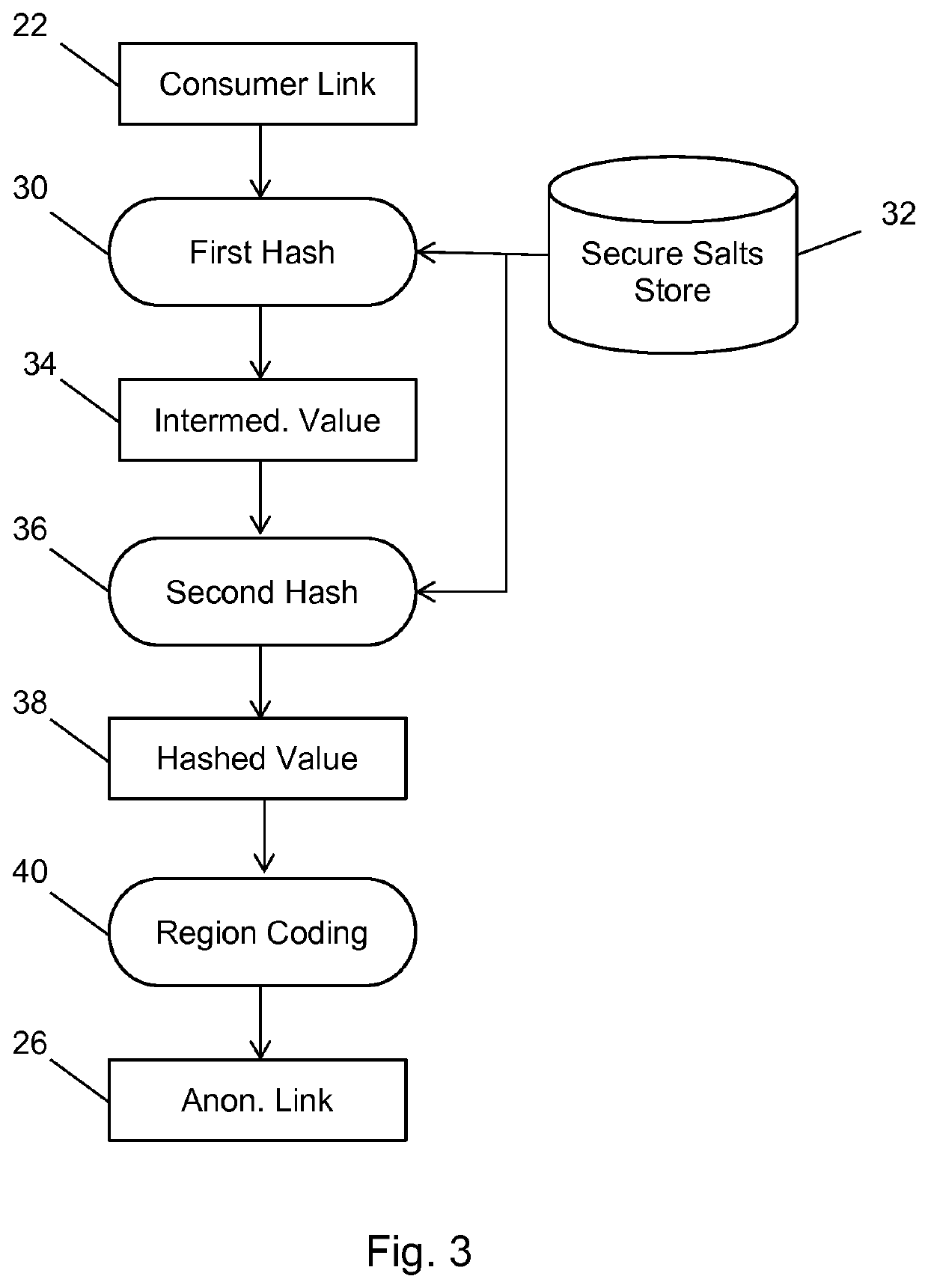
ActiveUS20150081562A1Precise positioningIncreased marketingKey distribution for secure communicationCryptography processingInternet privacyOnline advertising
A method and system for bringing together online and offline advertising uses partner-encoded anonymous links that are associated with consumer data. The partner-encoded anonymous links allow processing without personally identifiable information (PII) in a secure environment. Data is matched using identifiers that are encrypted for use in connection with individual match distribution partners. The method and system allows a marketer to utilize offline data to precisely target advertisements without the use of PII, and to perform analytics concerning the use of the online advertisements to more precisely determine the effectiveness of multichannel marketing efforts.
Owner:LIVERAMP
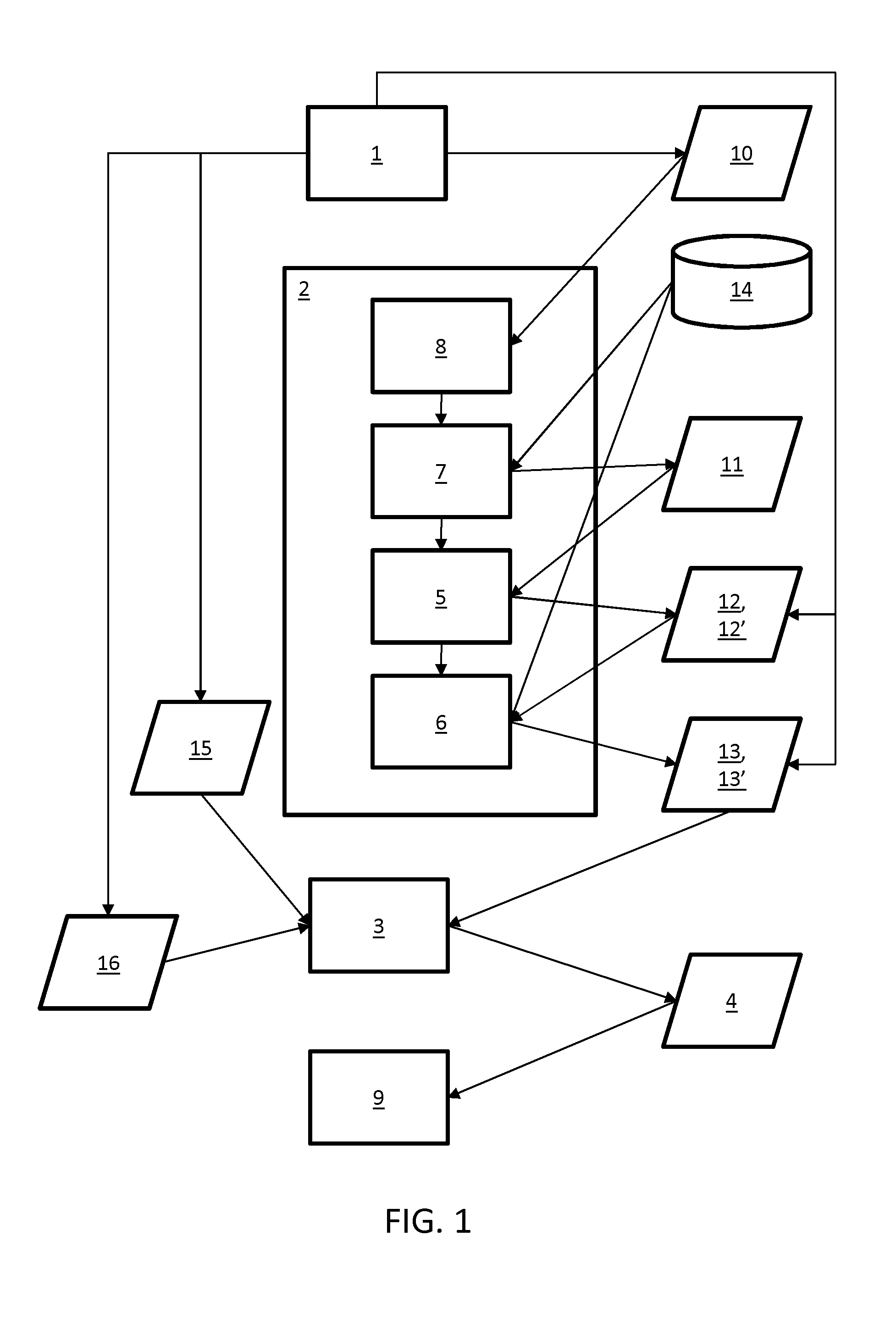
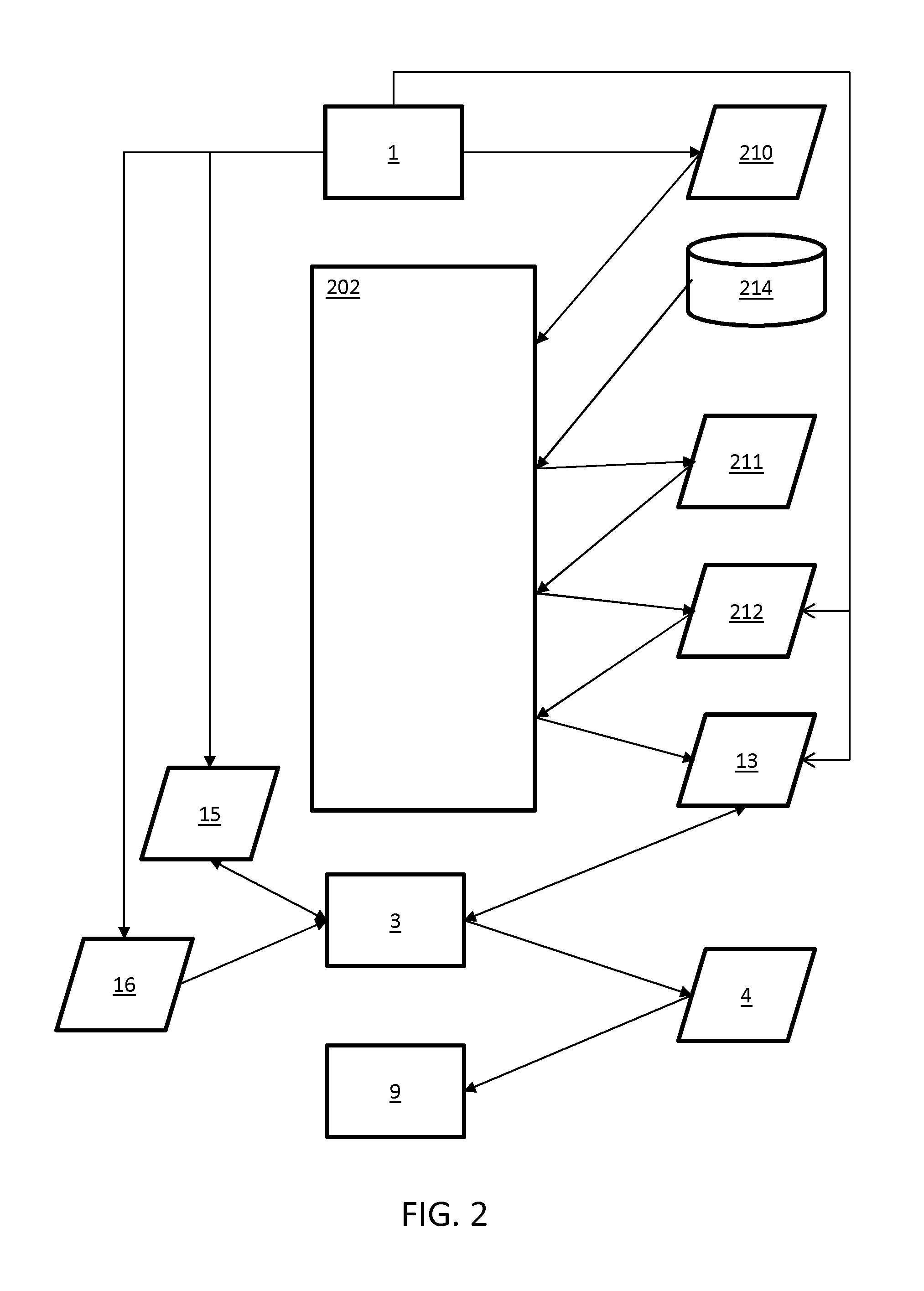
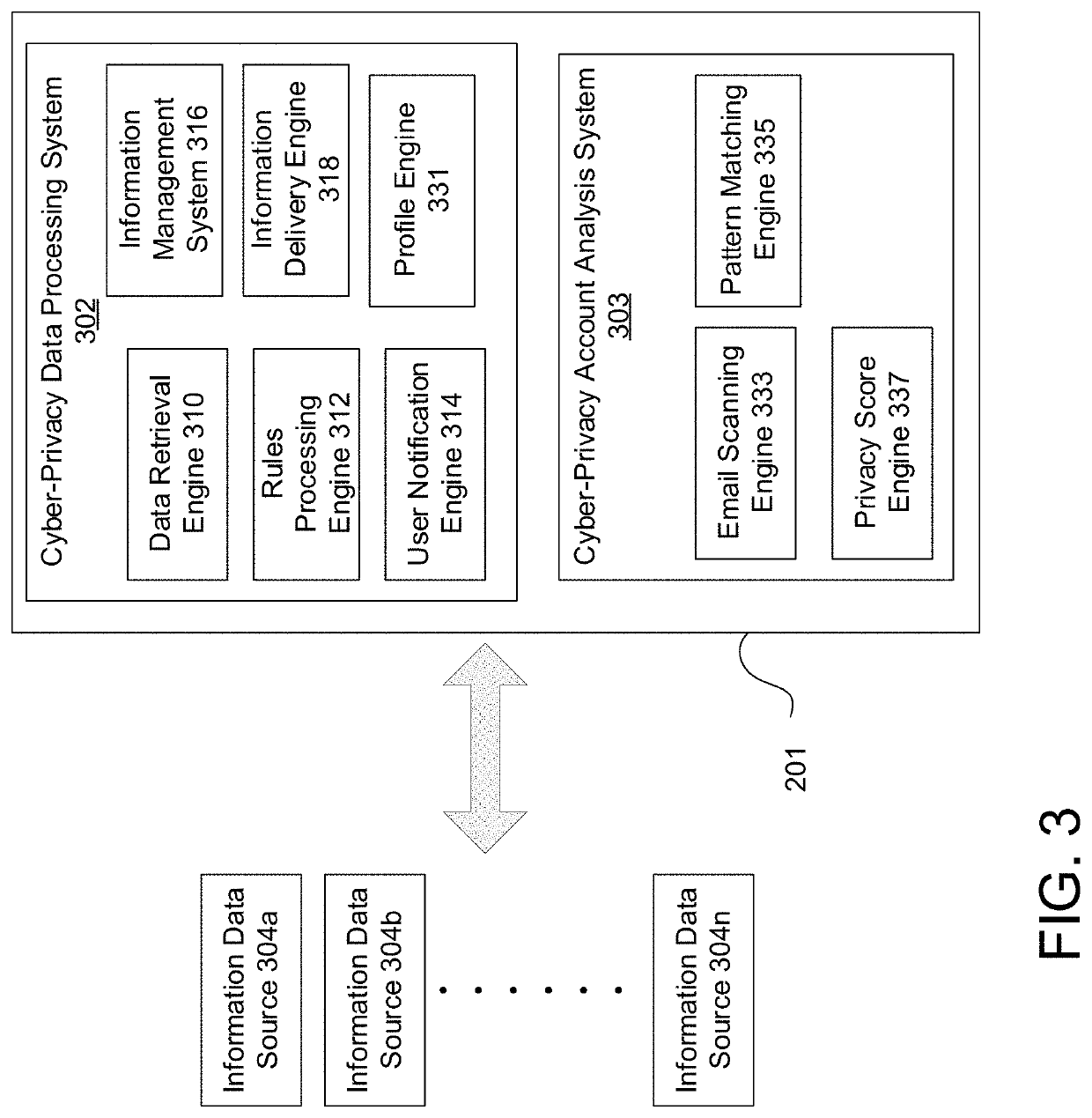
Creating an Access Control Policy Based on Consumer Privacy Preferences
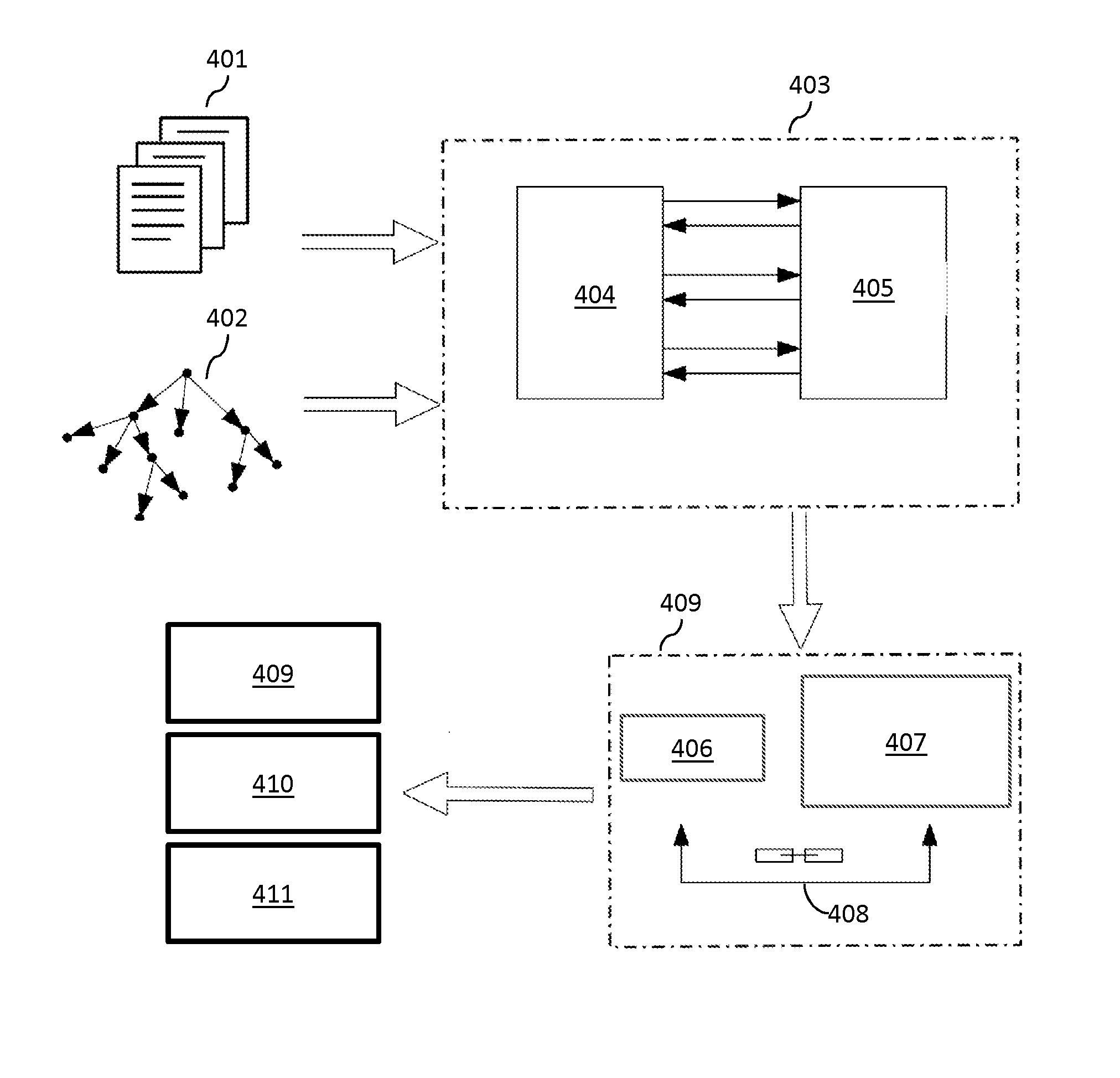
ActiveUS20130312060A1Accurately determineEasy for userData processing applicationsDigital data protectionDocumentationConsumer privacy
A system for generating an access control policy comprises a user interface (1) for enabling a user to indicate a topic (10) and a set of permissions (15). A document analyzer (2) analyzes the content of a plurality of documents (11) to find a set of documents (13) relating to the topic (10). A property finder (5) analyzes the content of a plurality of documents (11) to find at least one distinguishing property (12) of documents relating to the topic (10). A document selector (6) selects the set of documents (13), based on the distinguishing property (12). An associating subsystem (3) associates the set of permissions (15) with the set of documents (13) to obtain an access control policy (4).
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Anonymous Links to Protect Consumer Privacy
ActiveUS20150082050A1Precise positioningIncreased marketingDigital data processing detailsUnauthorized memory use protectionOnline and offlineSystem usage
A method and system for bringing together online and offline advertising uses anonymous links that are associated with consumer data. The anonymous links allow processing without personally identifiable information (PII) in a secure environment. Data is matched using the anonymous links. The method and system allows a marketer to utilize offline data to precisely target advertisements without the use of PII, and to perform analytics concerning the use of the online advertisements to more precisely determine the effectiveness of multichannel marketing efforts.
Owner:LIVERAMP
Logistics information transmission method, device and system
ActiveCN104253691AReduce Privacy LeakageData processing applicationsUser identity/authority verificationLogistics managementInformation transmission
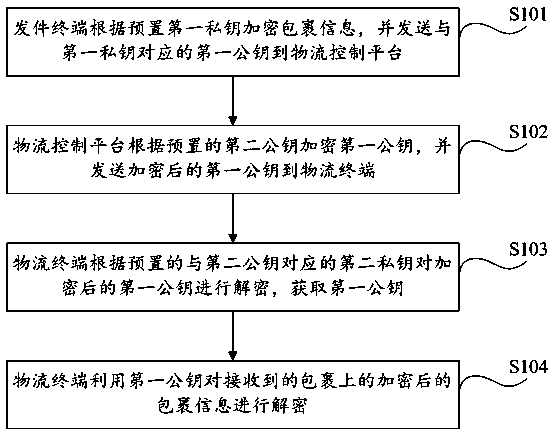
The invention provides a logistics information transmission method. The method includes the steps: a transmitting terminal encrypts packet information according to a first privacy key preset and transmits ta first public key, corresponding to the first privacy key, to a logistics control platform; the logistics control platform encrypts the first public key according to a second public key preset and transmits the first pubic key encrypted, to a logistics terminal; the logistics terminal decrypts the first encrypted public key according to the second privacy key which is preset and which corresponds to the second public key, so as to obtain the first public key; the logistics terminal decrypts the encrypted packet information of a received packet through the first public key. The embodiment further provides a logistics information transmission device and system. The keys are used for encryption and decryption, only legitimate users can acquire address information of a receiver, and chances that privacy of consumers leaks are slimmed.
Owner:SHENZHEN AUDAQUE DATA TECH
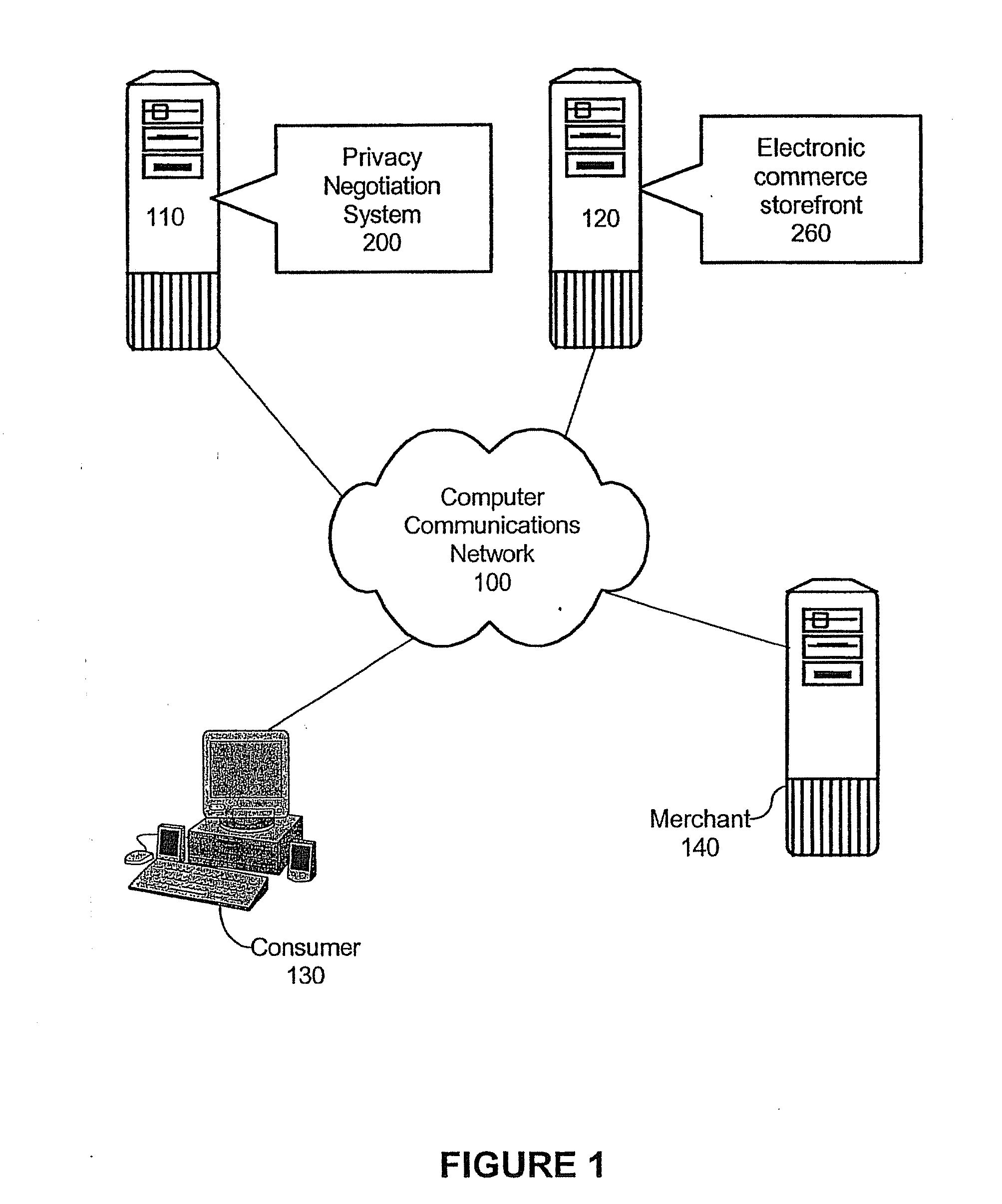
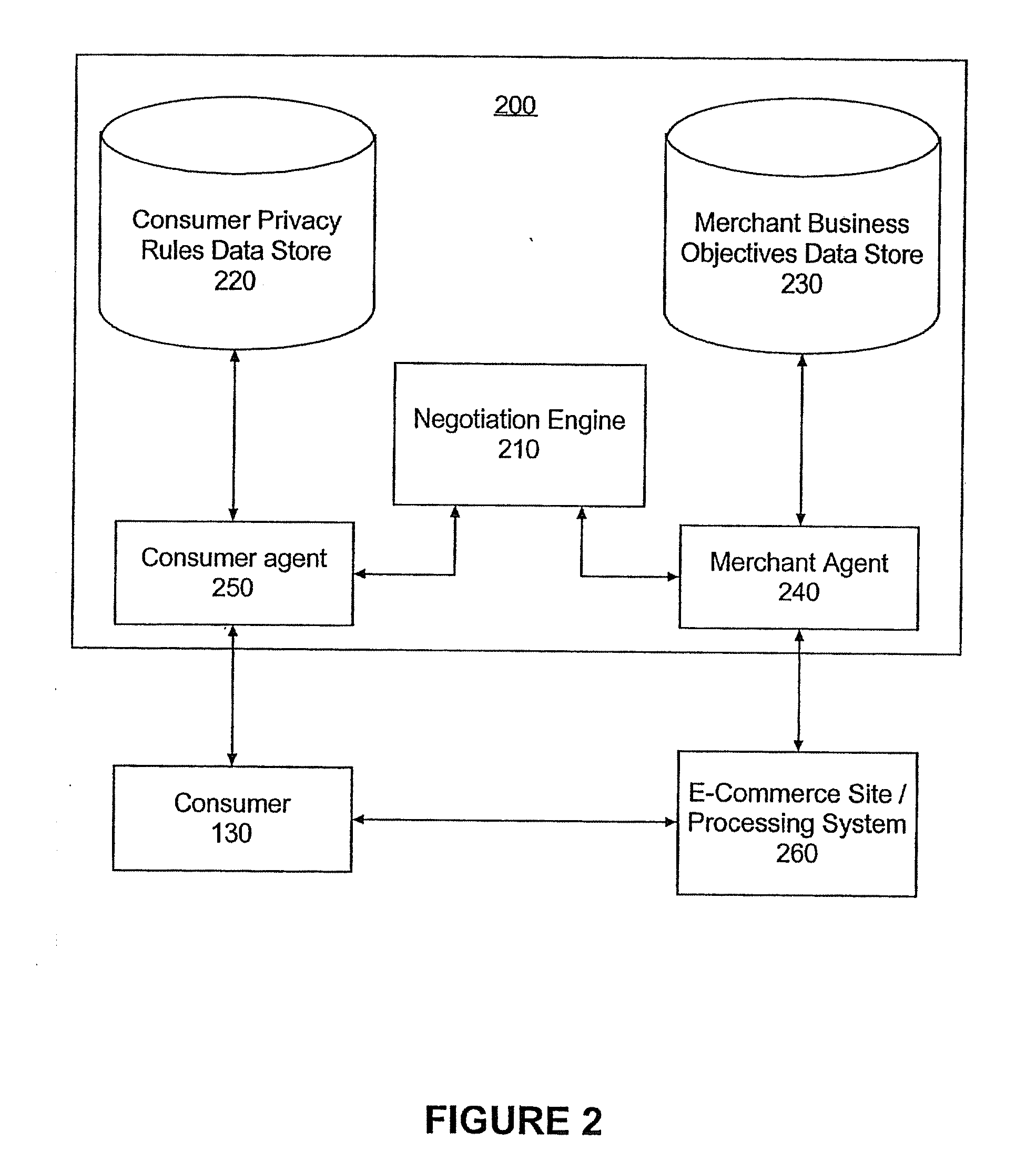
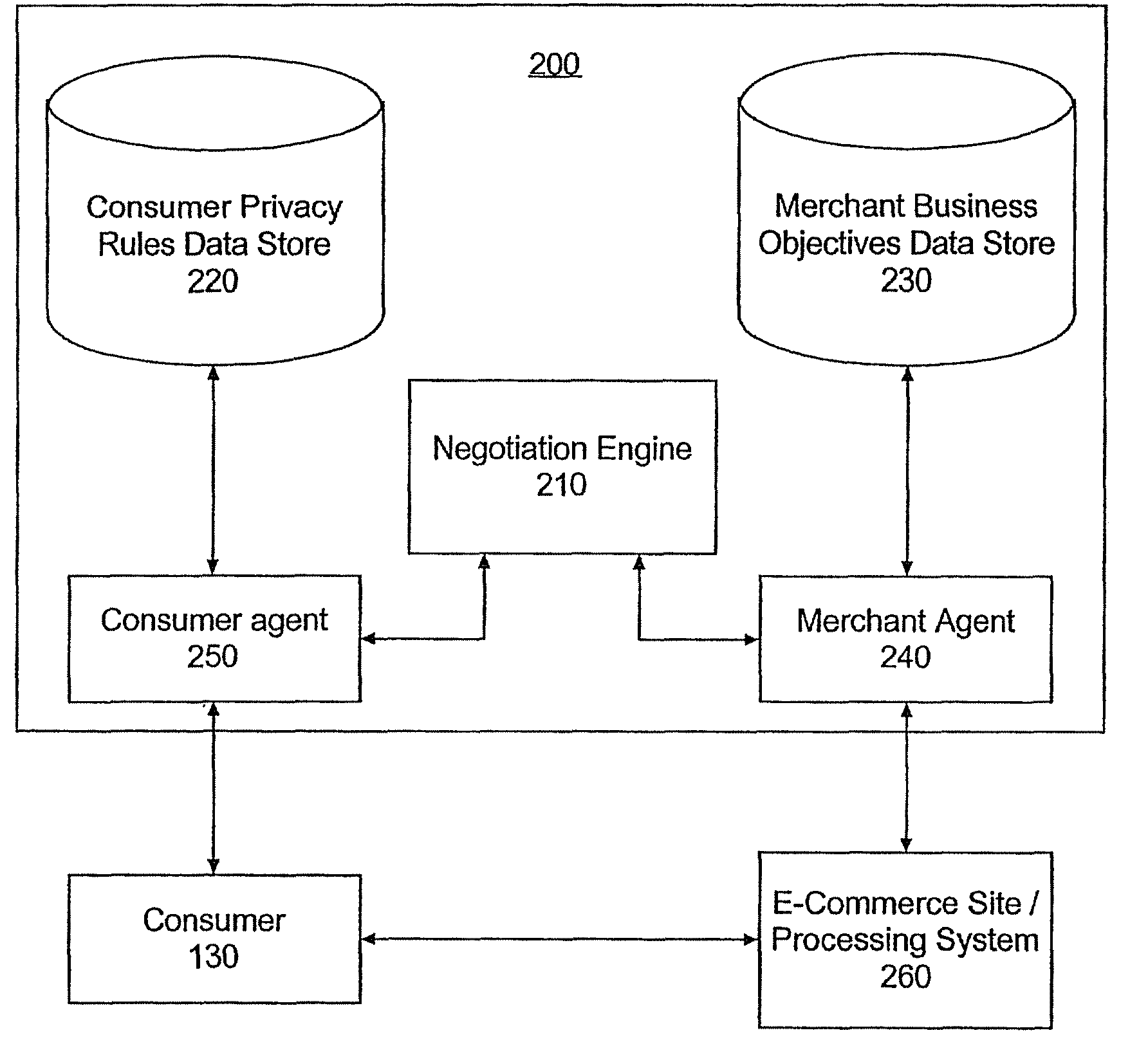
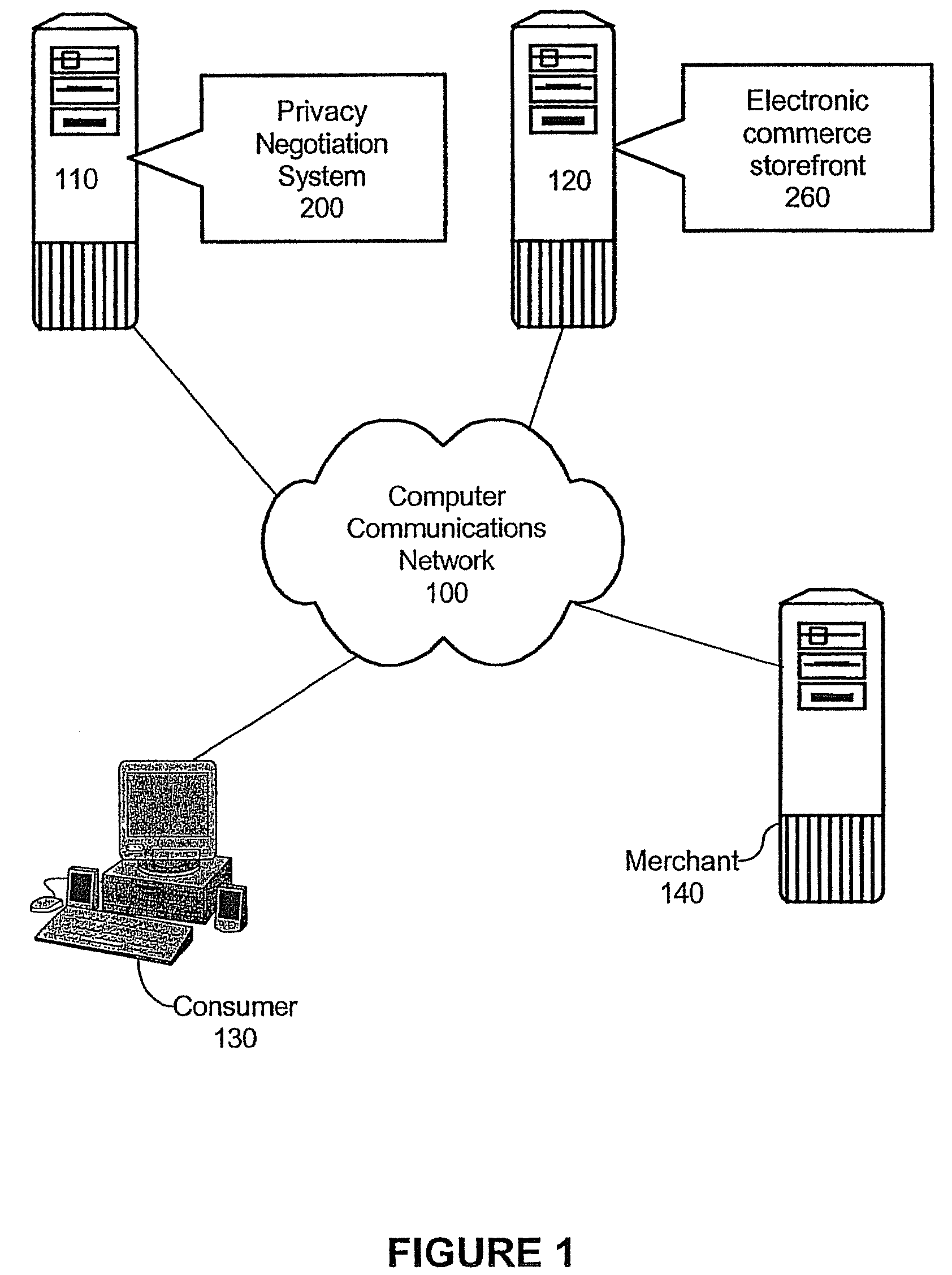
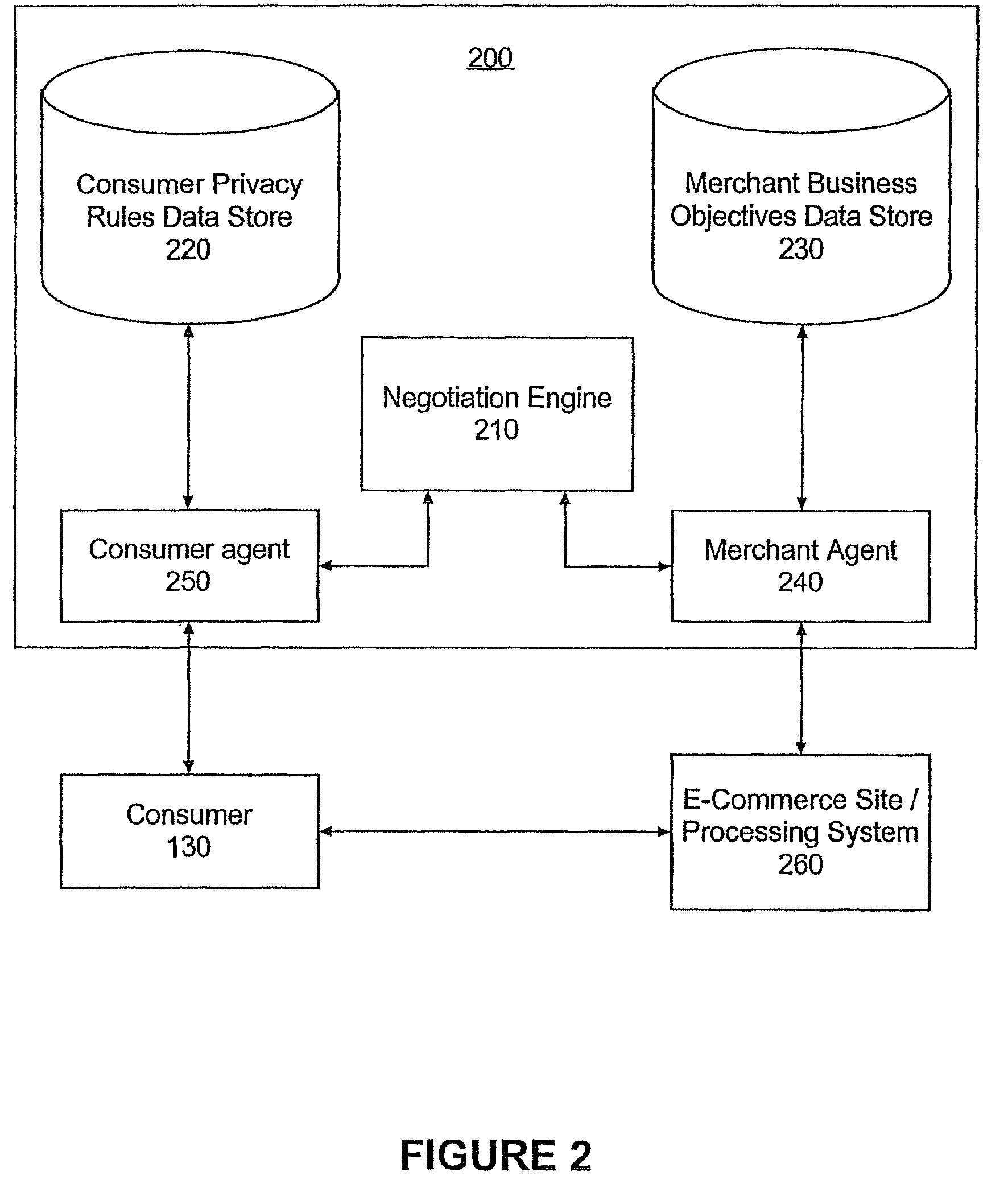
Method and apparatus for privacy negotiation
InactiveUS20090106166A1Payment architectureBuying/selling/leasing transactionsE-commerceConsumer privacy
A method of negotiating an electronic commerce (e-commerce) transaction for the sale of a selected good can include identifying an asking price for the selected good and retrieving from memory merchant business objectives (MBOs) and consumer privacy rules (CPRs). The MBOs can specify incentive information corresponding to a proposed exchange of consumer information and the CPRs can specify asking prices corresponding to the proposed exchange of consumer information. The MBOs can be compared to the CPRs to determine if an agreement can be reached for the sale of the selected good with an incentive based upon the proposed exchange of consumer information. The e-commerce transaction for the sale of the selected good with the incentive can be consummated if in the comparing step it is determined that an agreement can be reached.
Owner:IBM CORP
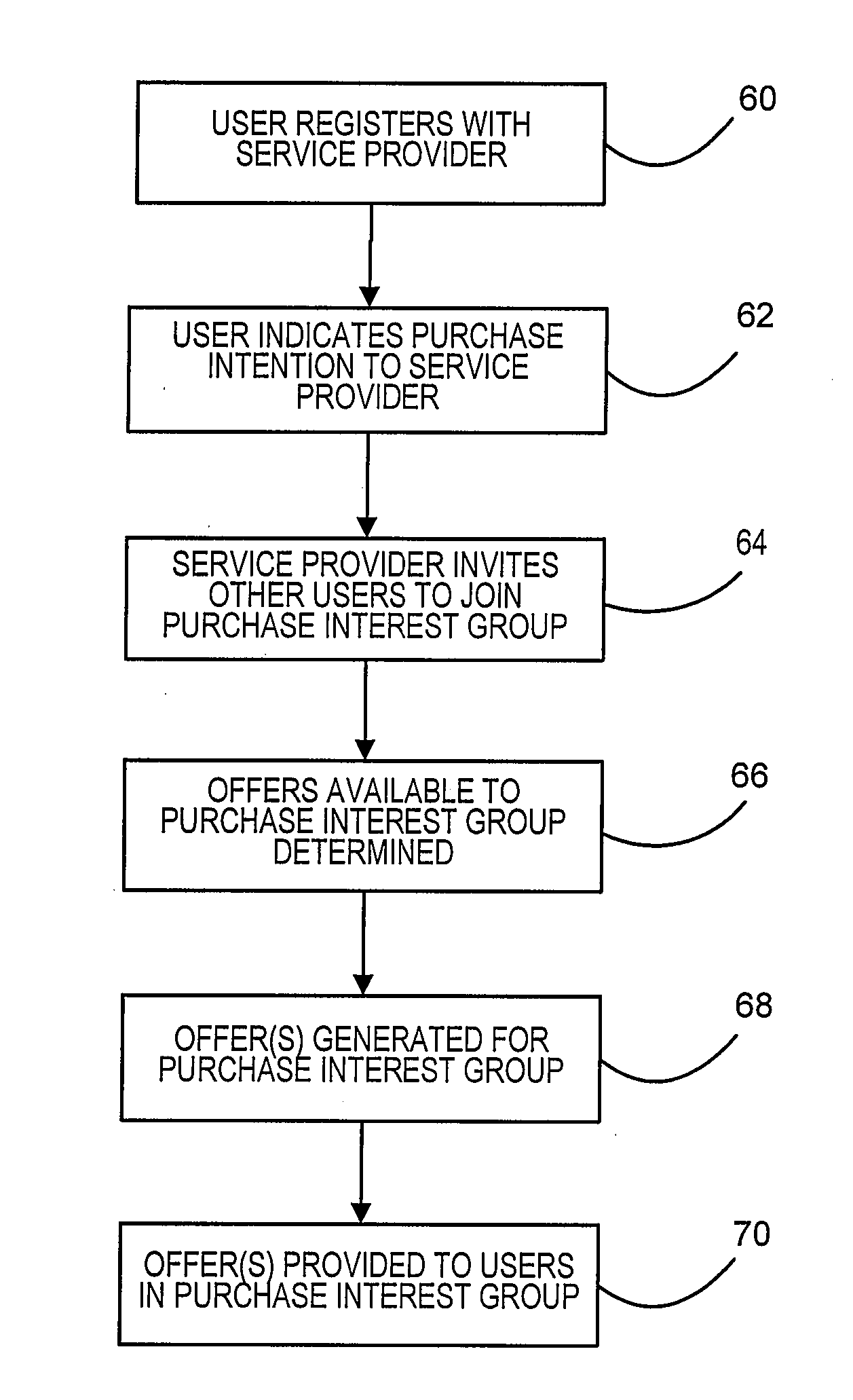
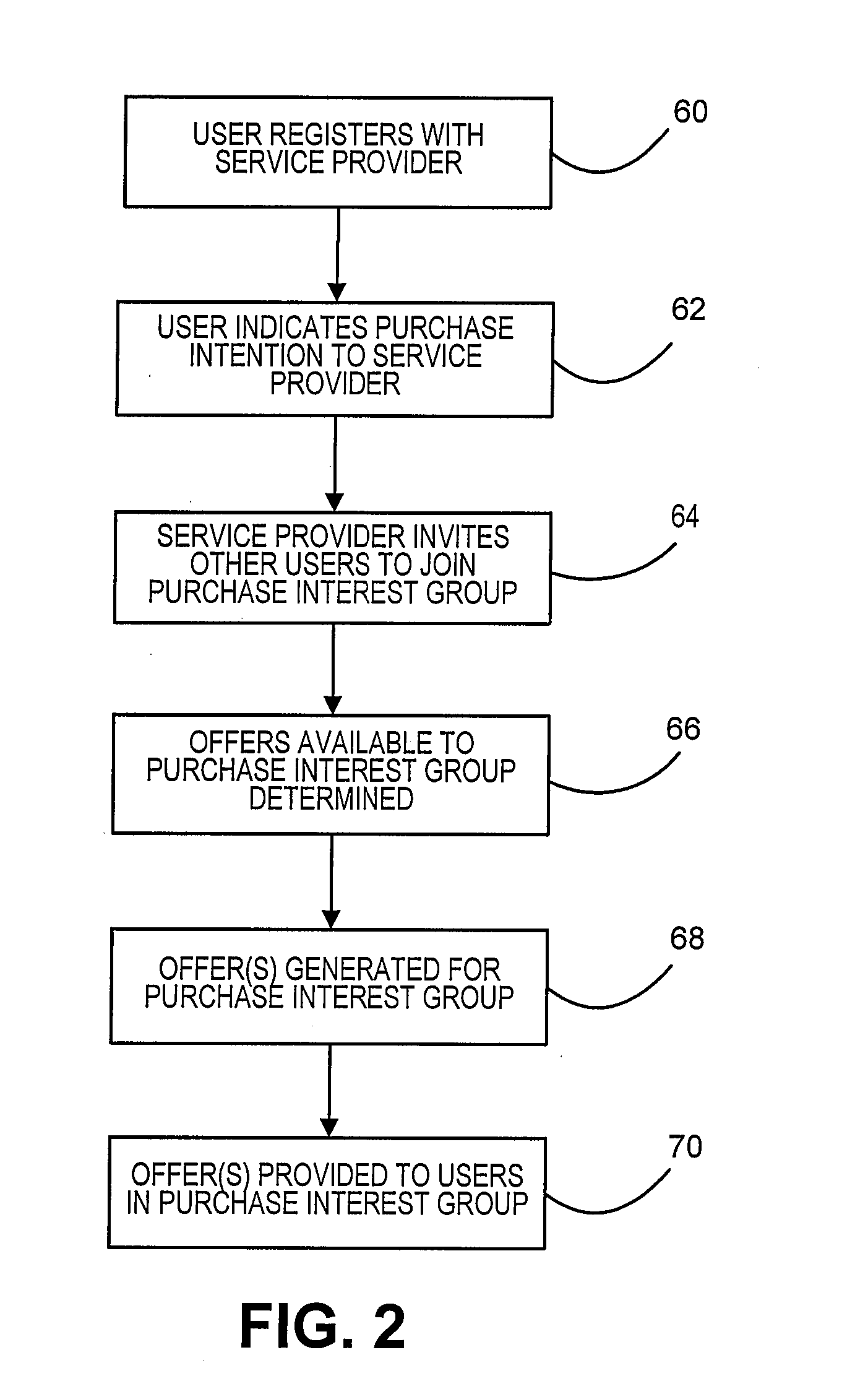
Method and system for negotiating group offers while maintaining privacy of consumers
A method and system for maintaining the privacy of consumers wishing to make a purchase while enabling them to benefit from a group discount is provided. Consumers register with a service provider that maintains their personal information in private. When a consumer is interested in purchasing a product or patronizing a traditional “brick and mortar” establishment, the consumer provides information to the service provider regarding such interest. The service provider can query other registered consumers to determine if there are others that have a similar interest. Using the leverage of all the consumers that respond to the query, the service provider can negotiate with one or more merchants to provide some type of group offer, without having to disclose the consumers' personal information. Upon successful negotiation of a group offer, the consumers will be provided with the offer.
Owner:PITNEY BOWES INC
Method and apparatus for privacy negotiation
InactiveUS8655721B2Payment architectureBuying/selling/leasing transactionsE-commerceConsumer privacy
Owner:INT BUSINESS MASCH CORP
Method for protecting consumer privacy when generating coupon
InactiveCN107742084ASolve the disadvantages of easy disclosure of personal privacyPrivacy protectionDigital data protectionBuying/selling/leasing transactionsInternet privacyConsumer privacy
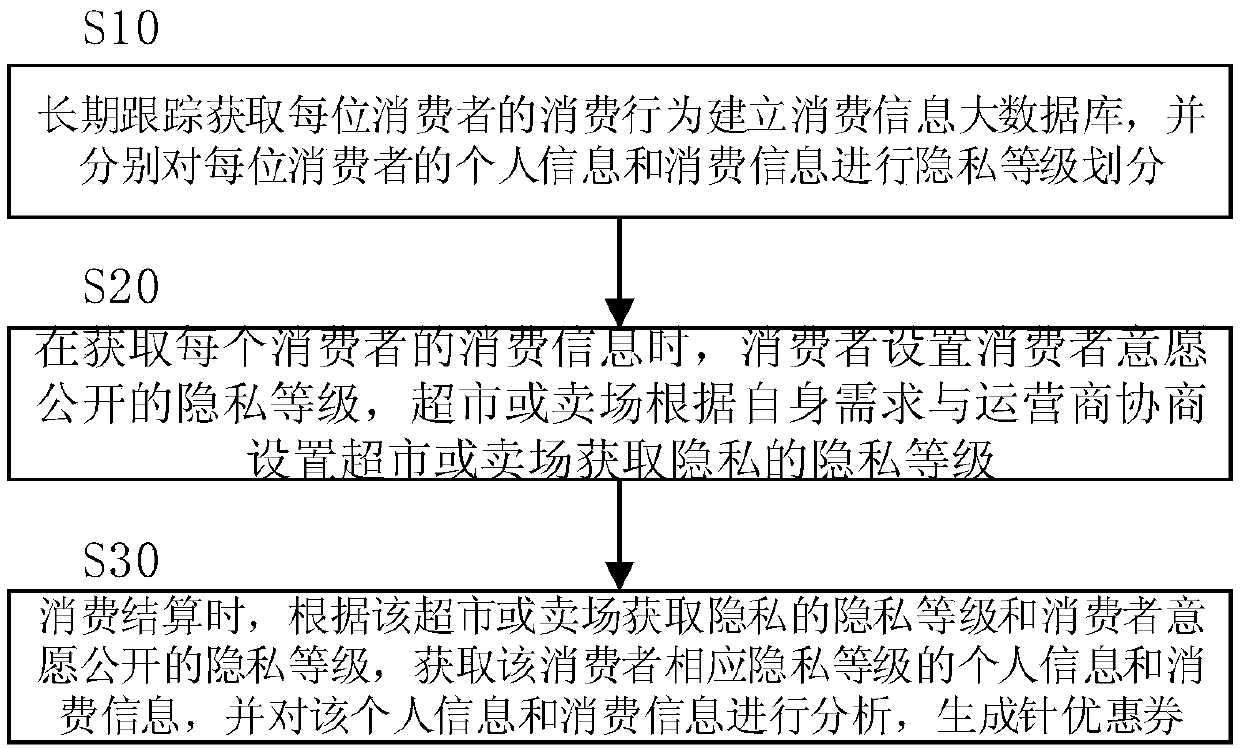
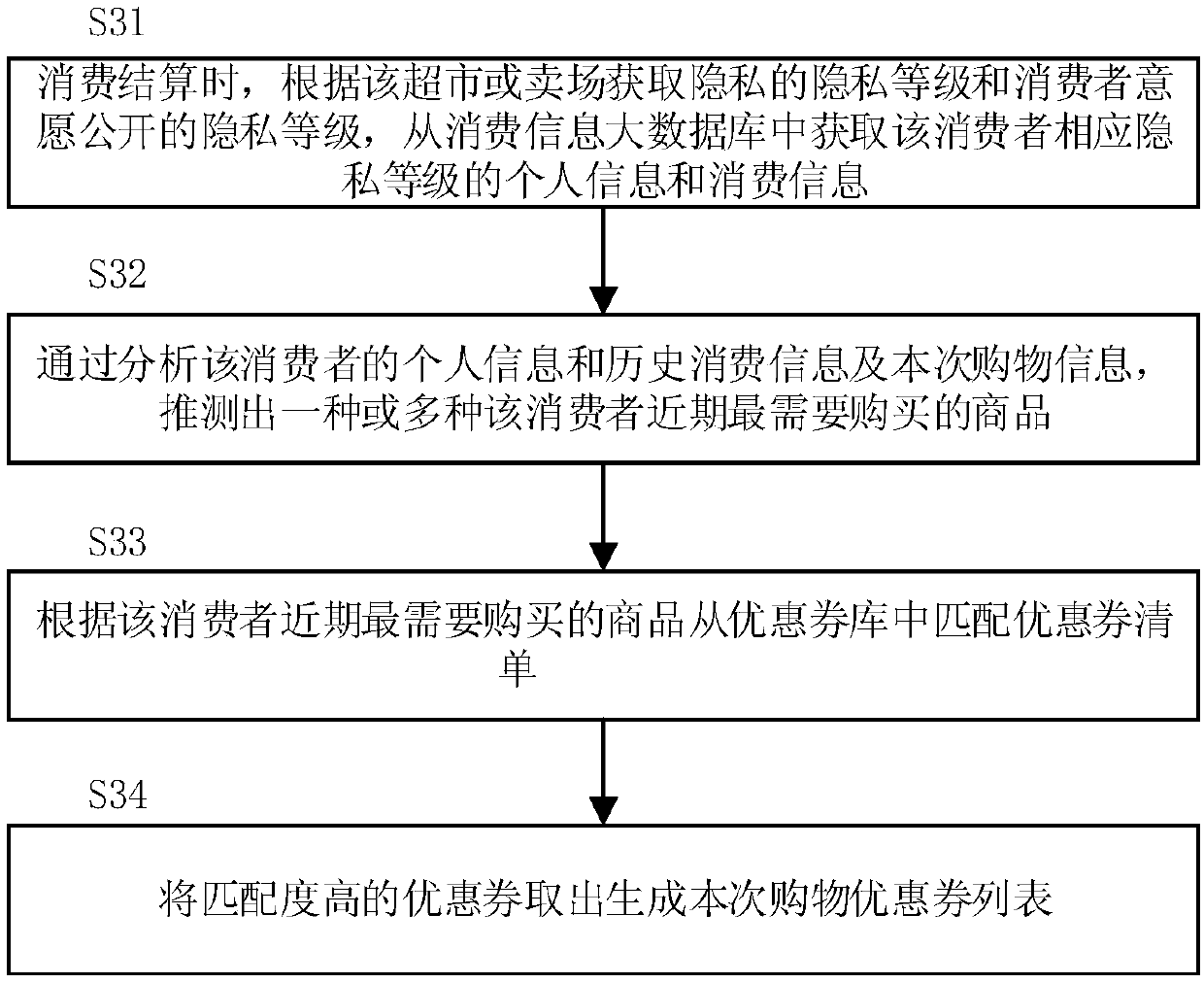
The invention discloses a method for protecting consumers' privacy when generating coupons, which includes: long-term tracking and acquisition of each consumer's consumption behavior to establish a large database of consumption information, and separately carry out personal information and consumption information of each consumer Classification of privacy levels; when obtaining consumption information, consumers set the privacy level that the consumer wishes to disclose, and the supermarket or store negotiates with the operator to set the privacy level for the supermarket or store to obtain privacy; The privacy level of the consumer and the privacy level that the consumer wishes to disclose, obtain the personal information and consumption information of the corresponding privacy level of the consumer, analyze the obtained personal information and consumption information, and generate a coupon for the consumer: the invention solves Eliminates the drawbacks of the coupon intelligent generation scheme based on a large database that easily leaks personal privacy, effectively protects consumer privacy, and improves consumer consumption experience.
Owner:北京翰宁智能科技有限责任公司
Big data correlation analysis method and system for protecting consumer privacies in electronic transaction
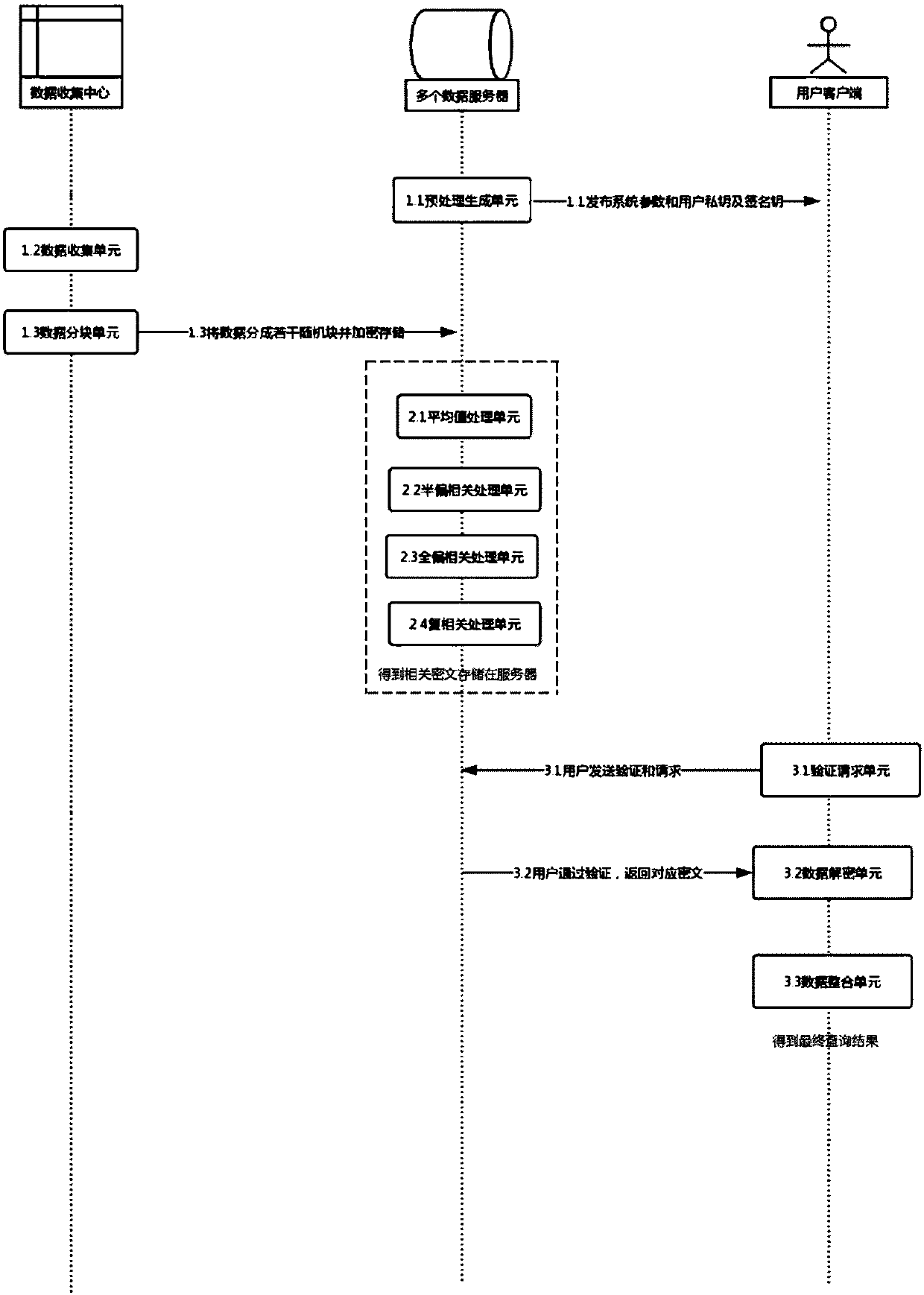
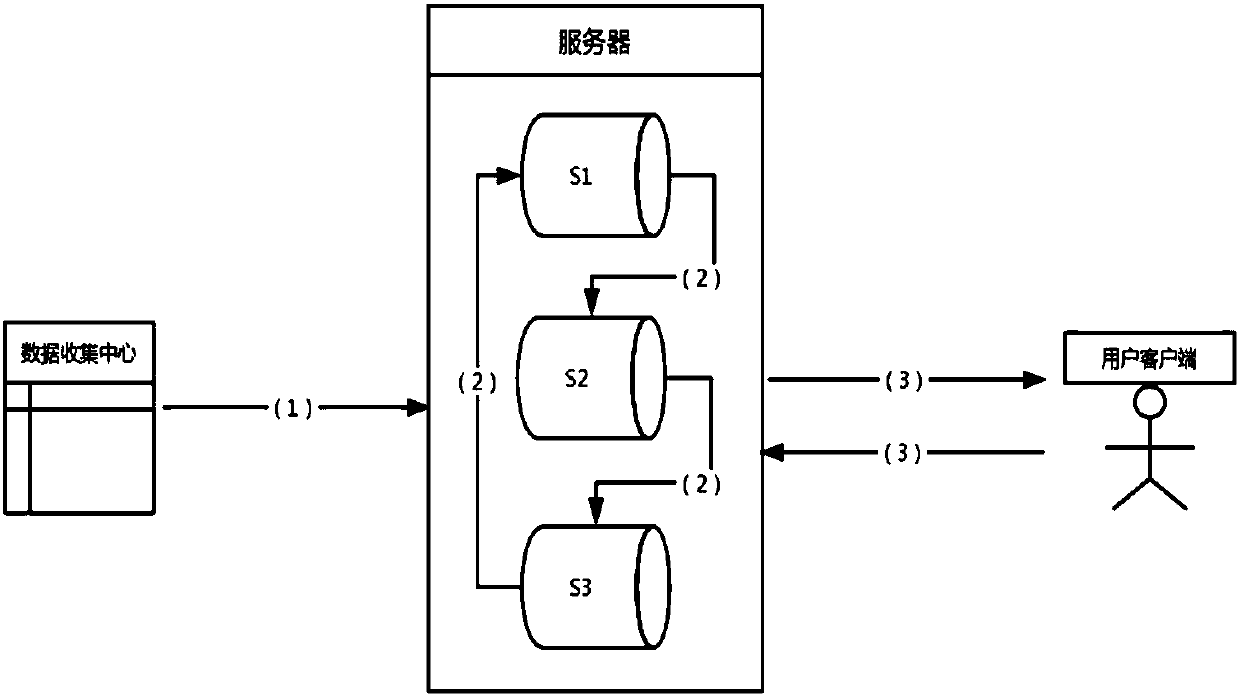
ActiveCN108171076AEnsure safetyPrevent insider attacksDigital data protectionPayment protocolsAnalysis dataStatistical analysis
The invention discloses a big data correlation analysis method and system for protecting consumer privacies in electronic transaction. The method comprises the steps of data storage, data statisticalprocessing, access query and the like; the system comprises a data storage module used for initializing the system, randomly dispersing data, secretly processing the data, converting the data into ciphertexts and storing the ciphertexts in data servers, a data statistical processing module used for performing data processing of related statistical analysis calculation on the ciphertexts, and an access query module used for performing decryption calculation on the ciphertexts in a client after a user passes an access request. By using the big data correlation analysis method and system for protecting the consumer privacies in the electronic transaction, consumer information is subjected to correlation analysis favorable for market adjustment under the condition of not harming the consumer privacies. The big data correlation analysis method and system assists the user (such as, an administrator, a merchant and a researcher) to analyze the data and does not leak the data.
Owner:深圳市崇晸实业有限公司
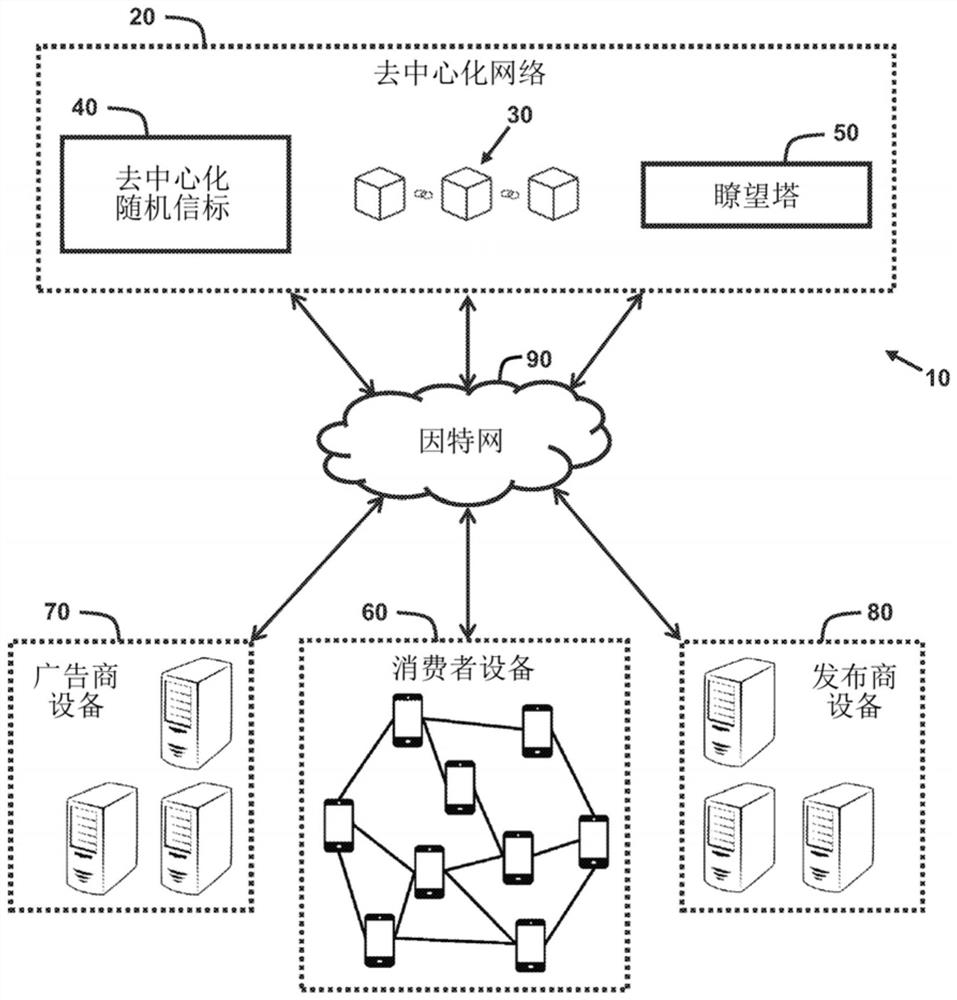
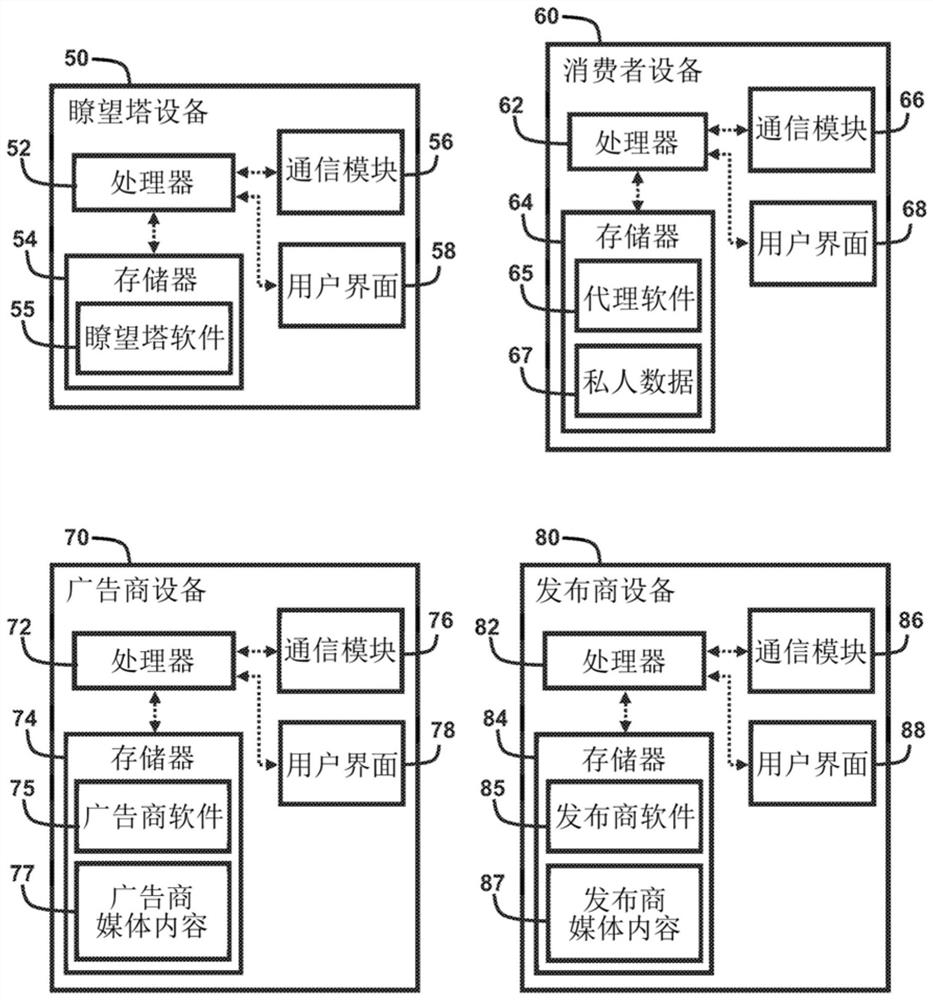
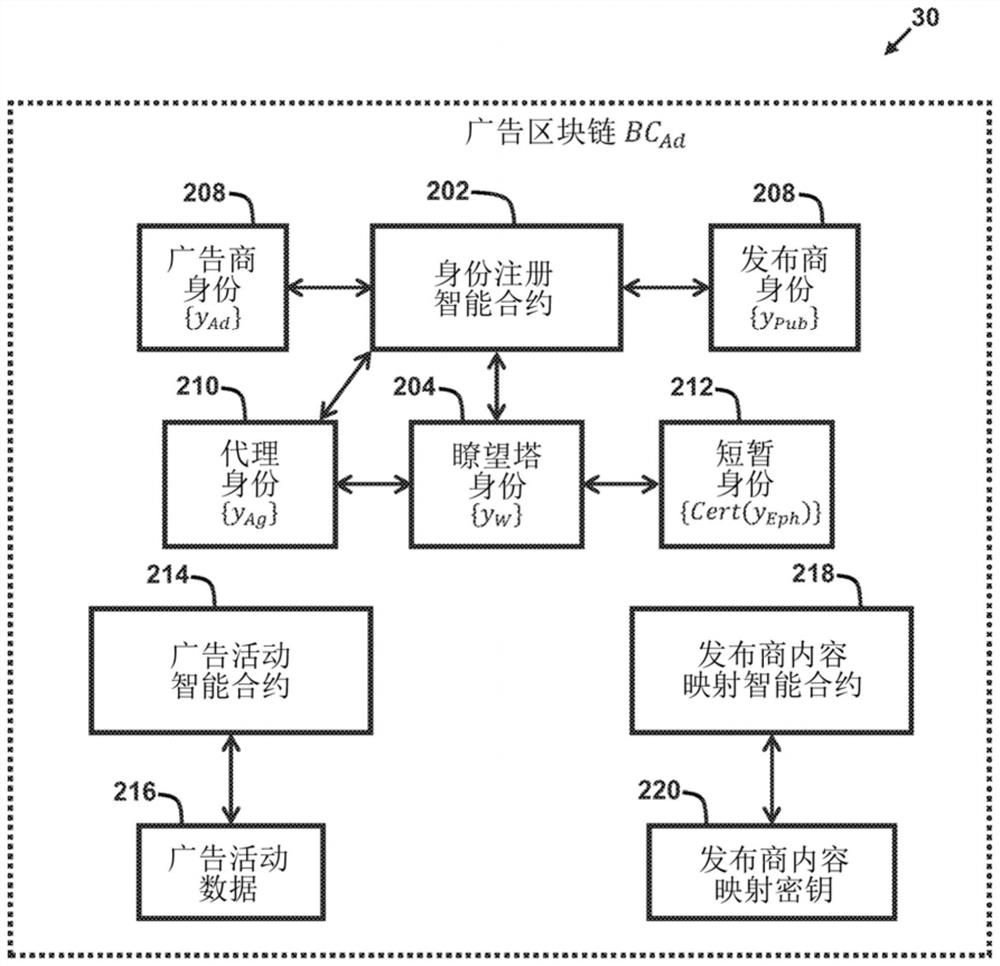
Methods and system for serving targeted advertisements to consumer device
A system and a method are disclosed that enable advertisers, publishers, and consumers to interact to provide the well-targeted advertisement impressions, while preserve consumer privacy. Particularly, the system and the method enable the accurate and reliable targeting of advertisements without the need for privacy-invasive tracking and collection of the consumer information by the advertisers or publishers. Instead, the consumer retains complete control of his or her own private information, even while the private information is used for programmatic targeting of advertisements. The system and the method disclosed herein advantageously utilize a block chain as a tool for arbitrating data, which accounts for and helps to eliminate fraud, costly arbitrage, and brand safety concerns by providing the programmatic advertising ecosystem with trust, permanence. transparency, and auditability.
Owner:爱丽丝网基金会
Partner encoding of anonymous links to protect consumer privacy
ActiveUS11157944B2Precise positioningIncreased marketingKey distribution for secure communicationCryptography processingInternet privacyOnline and offline
Owner:LIVERAMP
Split chip
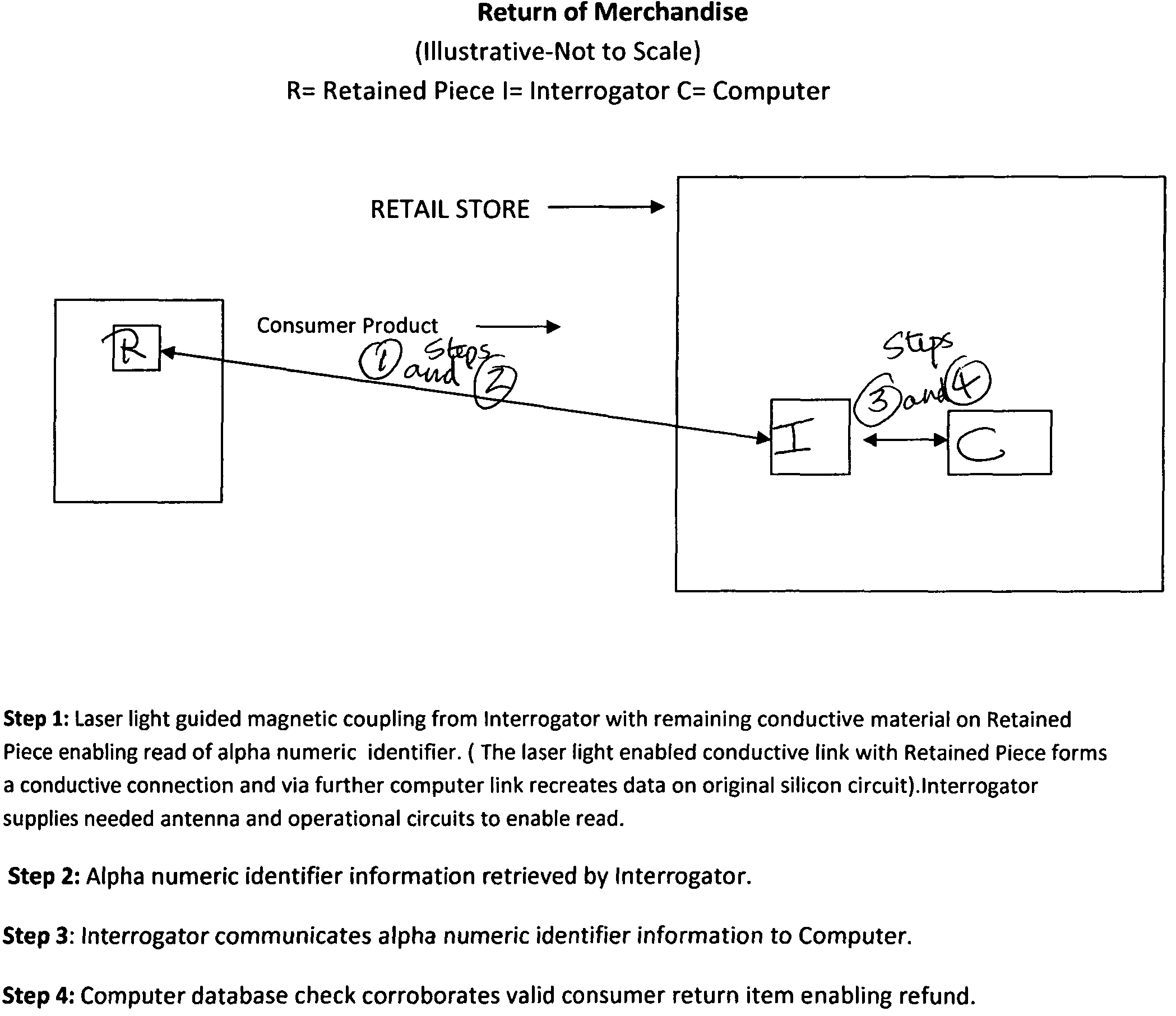
InactiveUS7741971B2Low costIncreasing range and selectivityTransistorSemiconductor/solid-state device detailsElectricityOriginal data
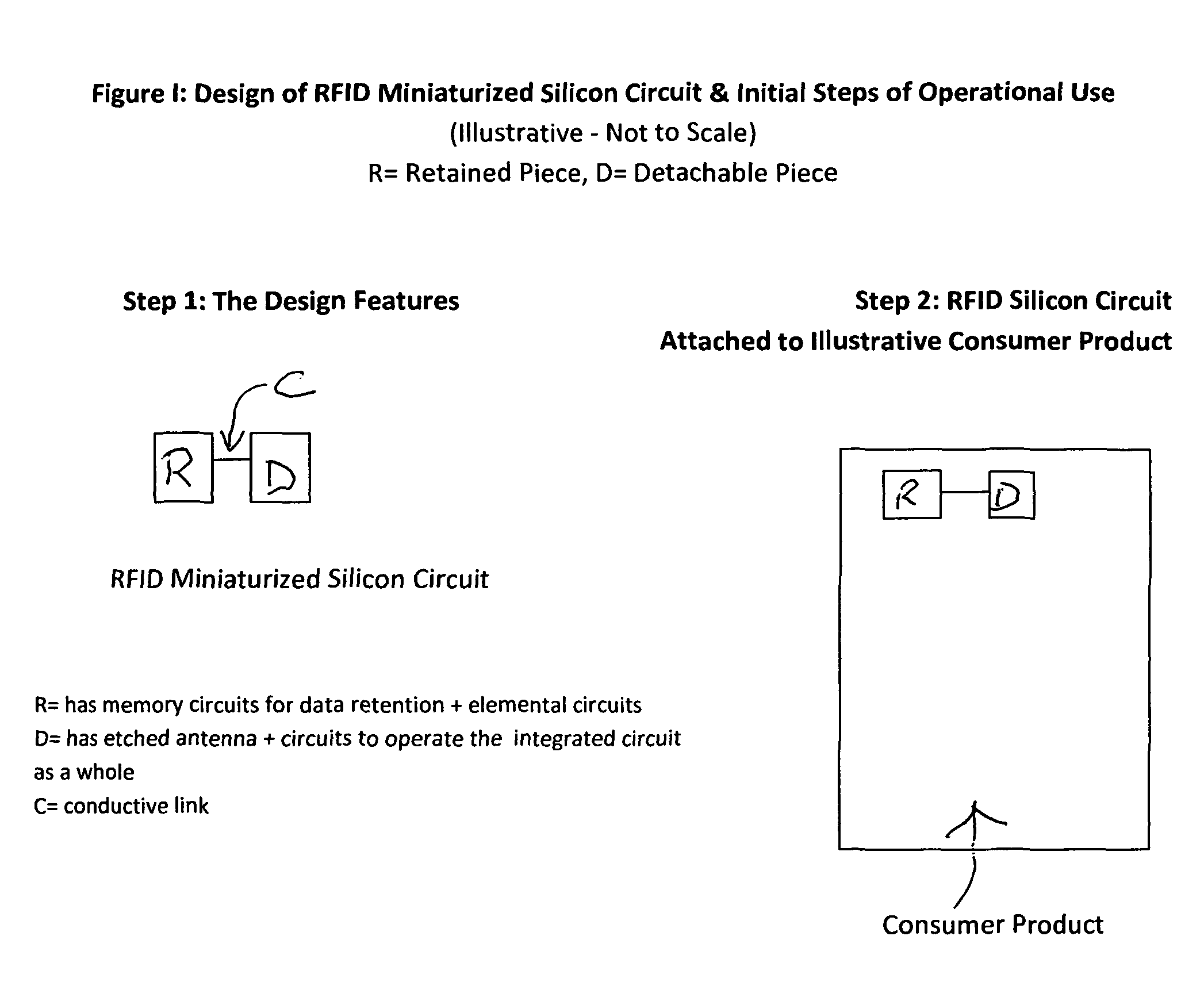
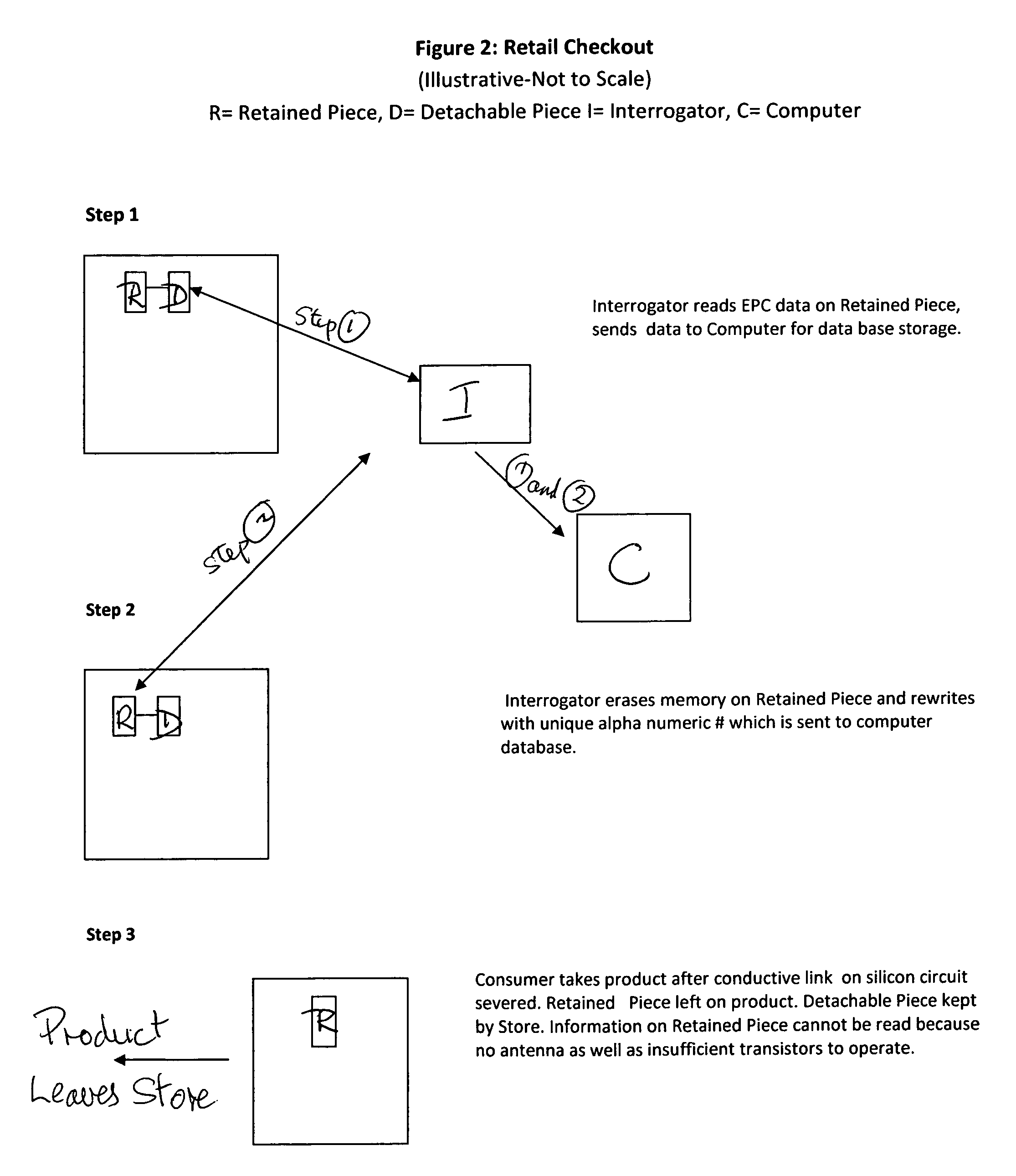
The Invention, titled the “Split Chip” by the Inventor, contemplates an RFID enabled consumer oriented tracking system which protects consumer privacy by splitting a miniaturized silicon RFID transponder circuit into a retained piece and a detached piece. The two pieces are electrically connected by a fine piece of conductive material. Each piece is dependent upon the other in order to disgorge data. The electrical connection between the two pieces can be severed by the consumer by tearing the fine piece of conductive material at a designated spot on the substrate making the Split Chip moribund. Upon a return or refund of the consumer item the original data can be recovered through a laser guidance system which connects the retained piece and its alpha numeric identifier to a back end host computer administration network.
Owner:RODGERS JAMES NEIL
Privacy Score
Methods, computer-readable media, software, and apparatuses may calculate and inform a consumer of company privacy scores corresponding to companies with which the consumer has a corresponding account, or for a company associated with a website that a consumer may visit. A consumer privacy score may also be determined, based on the company privacy scores. The company privacy scores may be based on a calculation including elements of a privacy practice of the corresponding company and elements of a privacy policy of the corresponding company.
Owner:ALLSTATE INSURANCE +1
Creating an access control policy based on consumer privacy preferences
ActiveUS9892279B2Accurately determinedEasy for userData processing applicationsDigital data information retrievalConsumer privacyUser interface
A system for generating an access control policy comprises a user interface (1) for enabling a user to indicate a topic (10) and a set of permissions (15). A document analyzer (2) analyzes the content of a plurality of documents (11) to find a set of documents (13) relating to the topic (10). A property finder (5) analyzes the content of a plurality of documents (11) to find at least one distinguishing property (12) of documents relating to the topic (10). A document selector (6) selects the set of documents (13), based on the distinguishing property (12). An associating subsystem (3) associates the set of permissions (15) with the set of documents (13) to obtain an access control policy (4).
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com