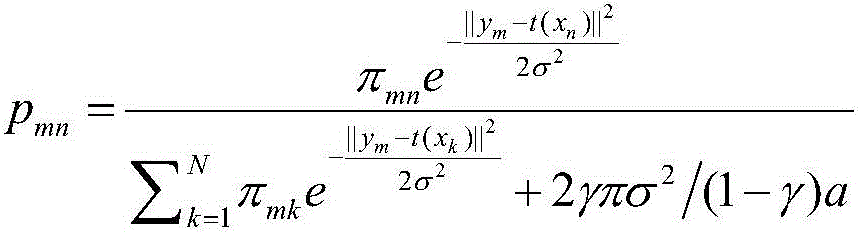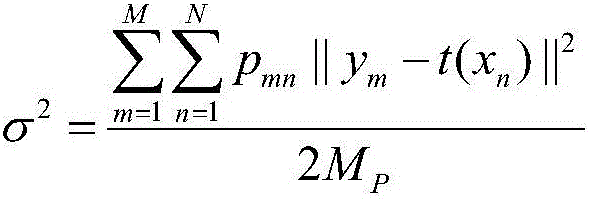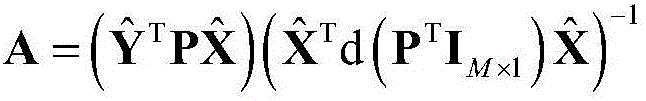Patents
Literature
48 results about "Data degradation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data degradation is the gradual corruption of computer data due to an accumulation of non-critical failures in a data storage device. The phenomenon is also known as data decay, data rot or bit rot.
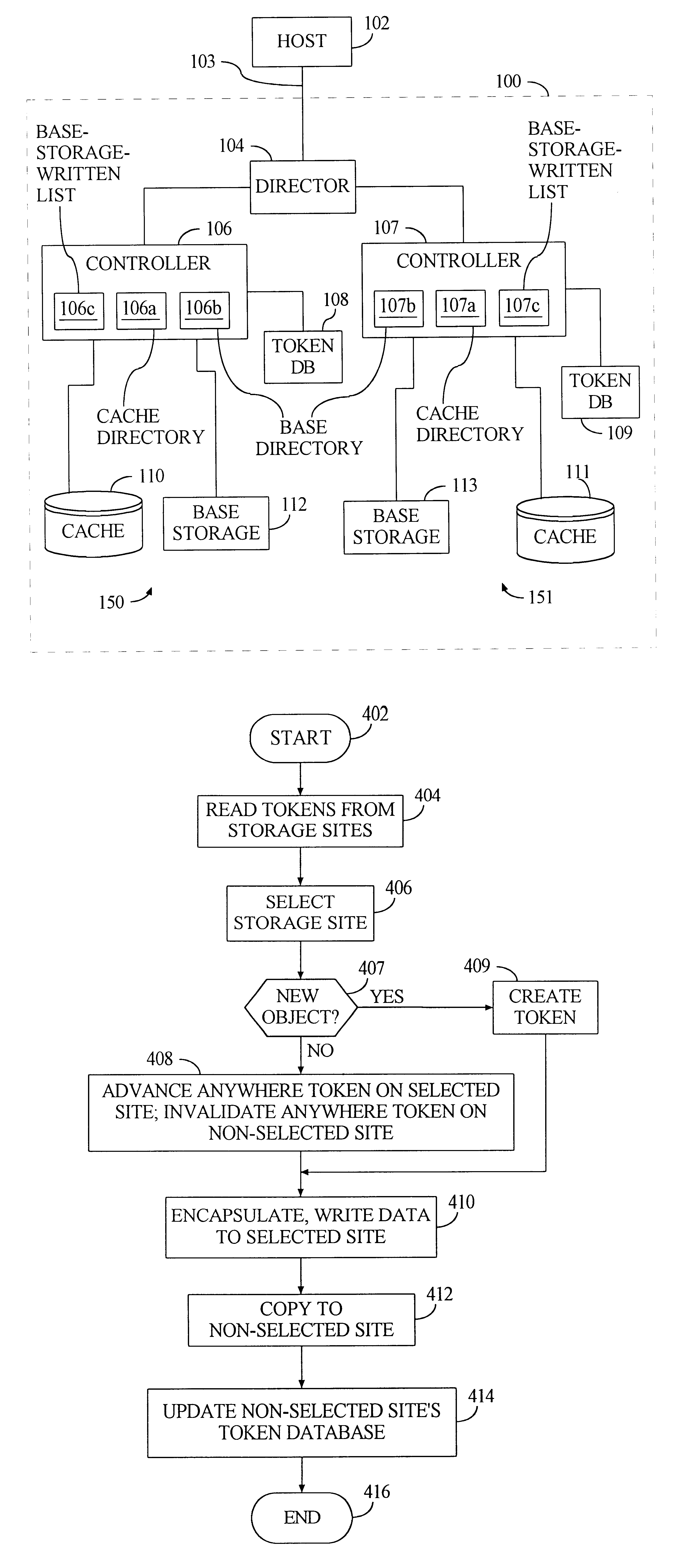
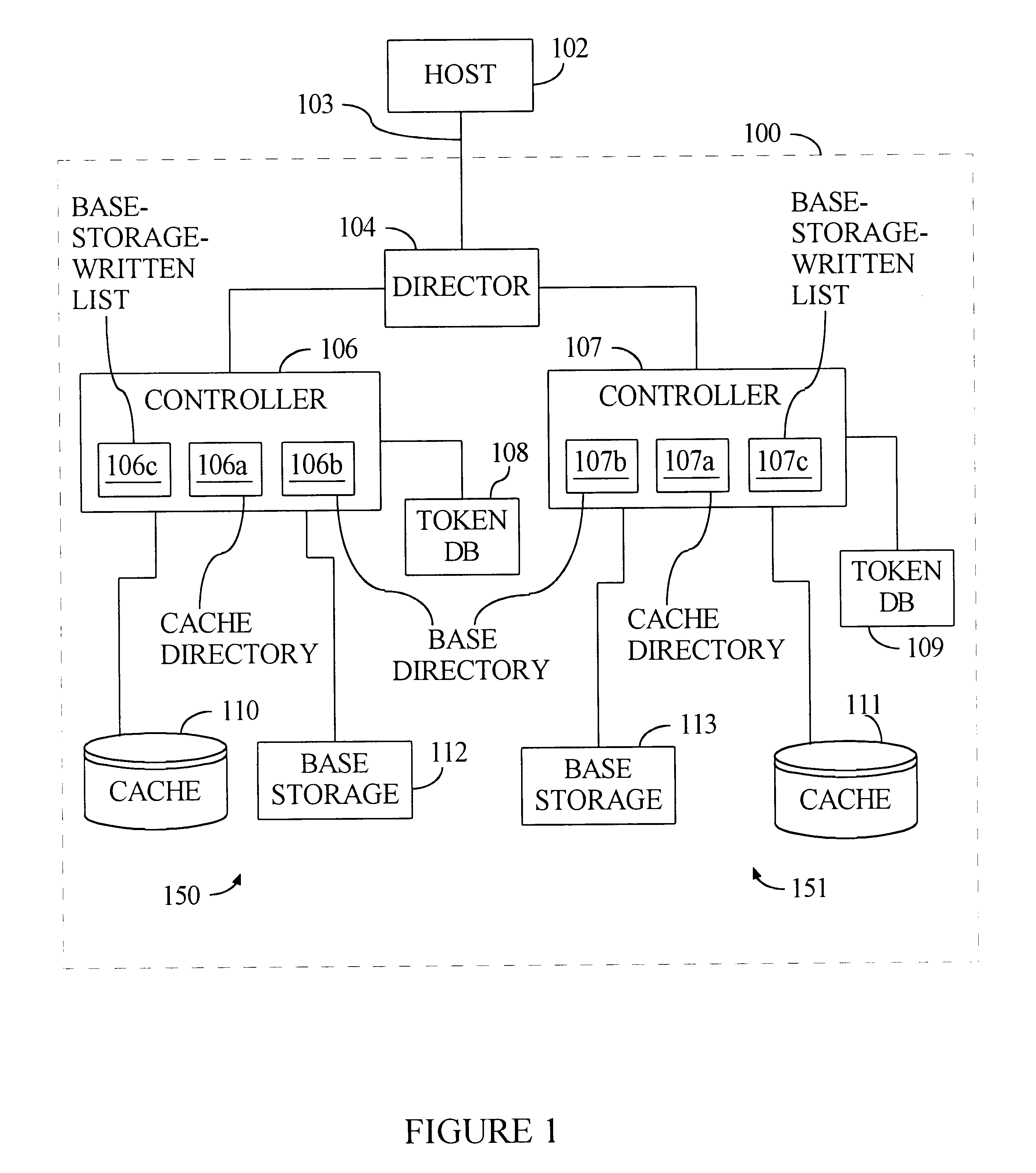
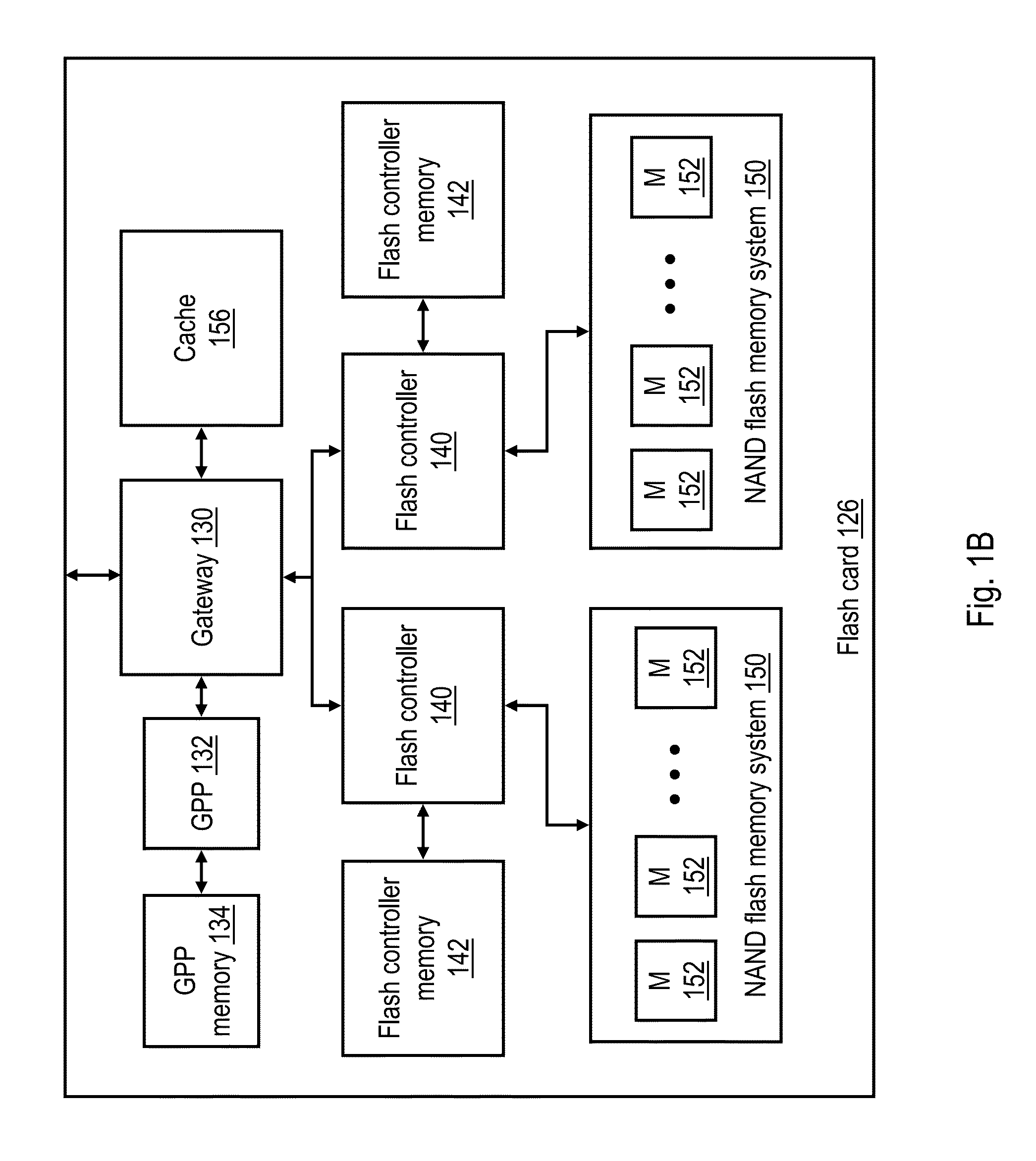
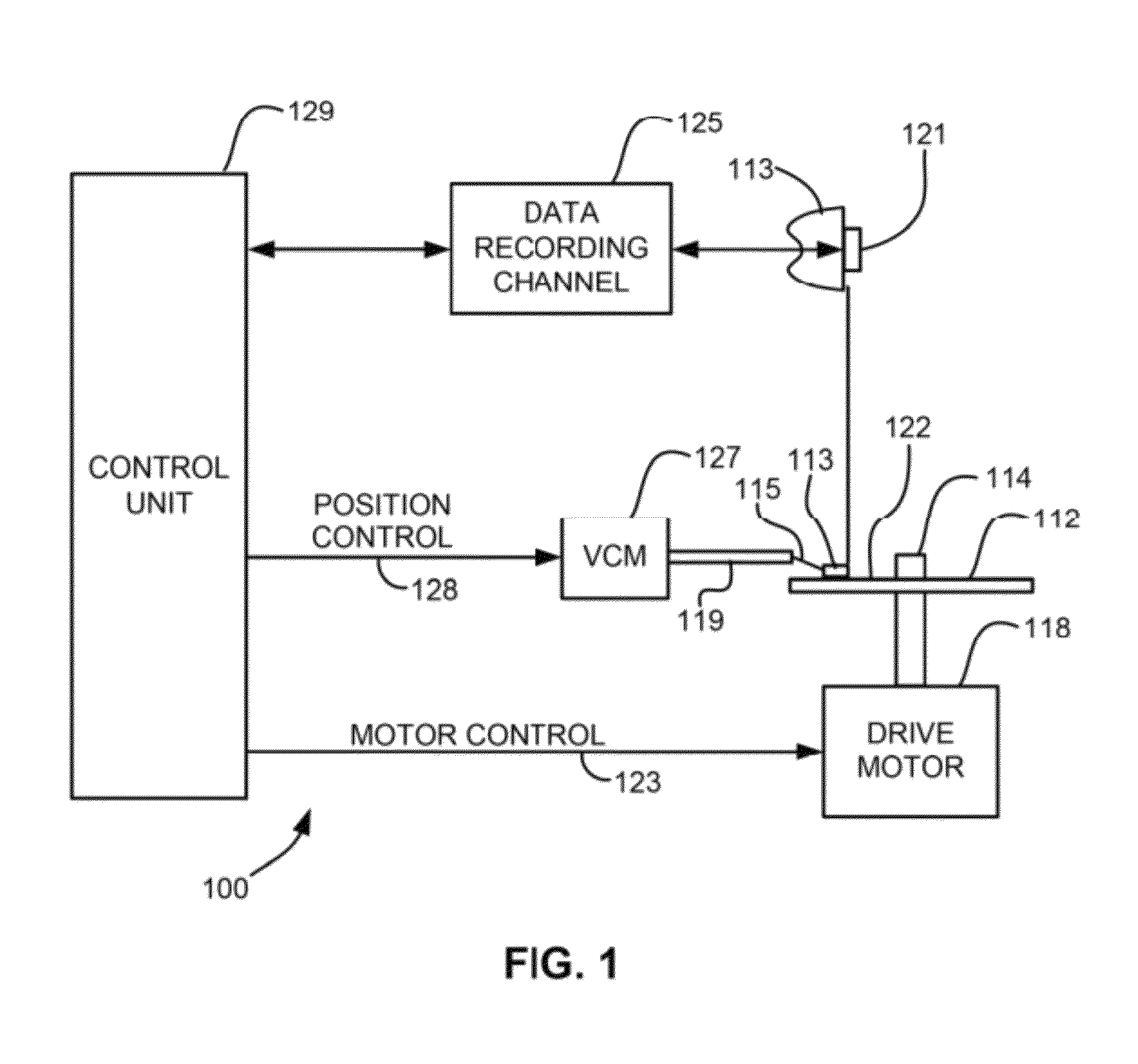
Cache management system utilizing cascading tokens
InactiveUS6691137B1Data processing applicationsMemory adressing/allocation/relocationMagnetic tapeParallel computing
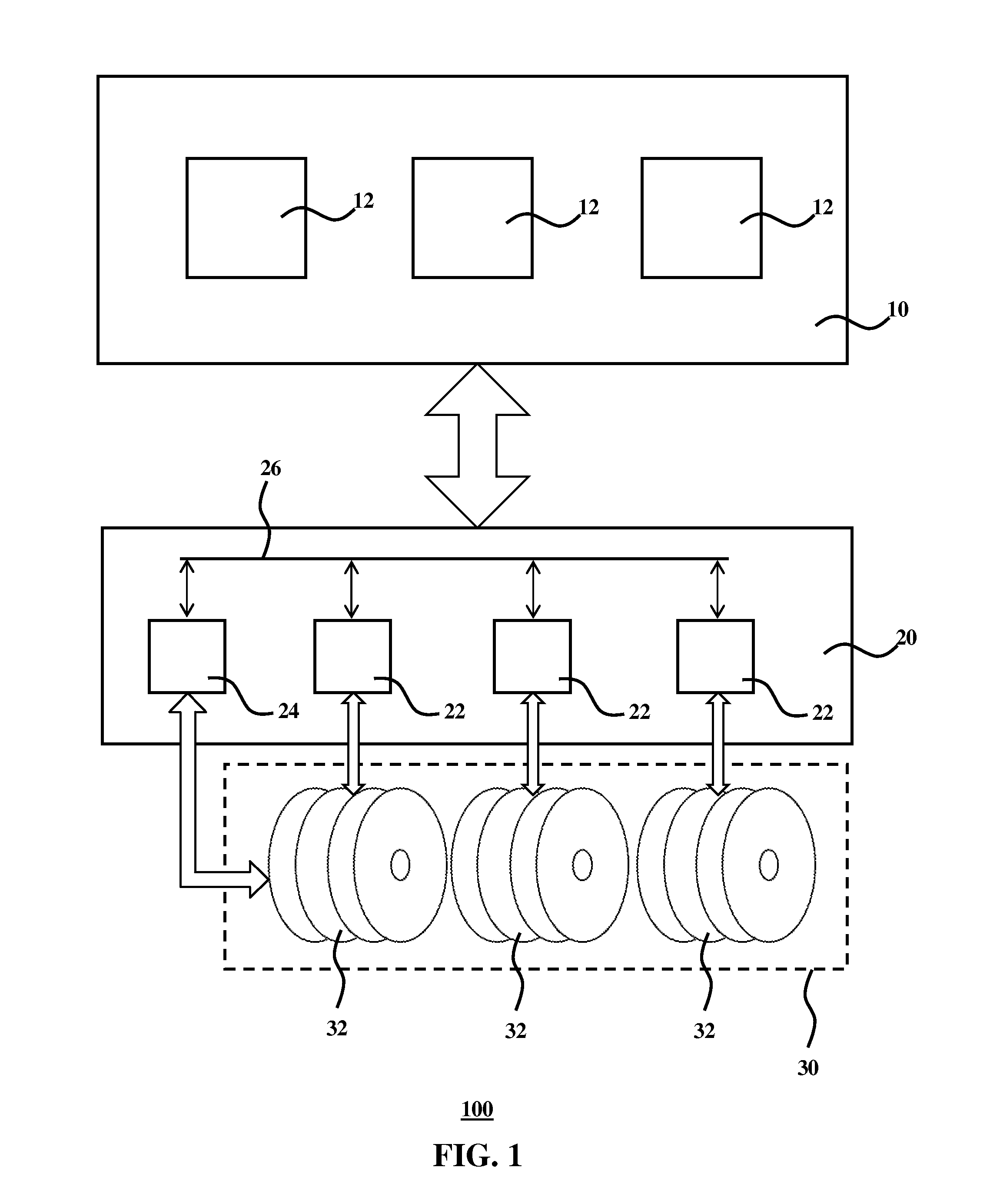
A data storage system, employing cache and base storage, assigns an "anywhere" token to each data object received for storage, whether the object is stored in cache or base storage. The anywhere token contains the latest metadata for the data object and includes at least a version code. If a data object is stored in base storage, the data object is assigned a "base" token with the same value as its anywhere token. These "cacading" tokens are available for use in tracking functions such as cache grooming, de-staging data to base storage, and processing cache miss events. All tokens are stored in a token database. For each data object, the token database lists its anywhere token and base token. If the storage system experiences a cache failure, normal storage operations are halted until the cache is repaired. Then, the controller implements a replacement token database. Namely, the controller accesses base storage to retrieve tokens of all data objects lost from cache. Using these base tokens, the controller populates a replacement token database, inserting the retrieved base tokens as both base and anywhere token for each data object lost from cache. Then, the replacement token database is used to the exclusion of the previous token database. With this procedure, the newly created token database accurately represents the contents of tape and cache. This avoids any danger of unknowingly recalling down-level data objects from tape, where their current counterpart data objects were stored on cache but lost in the cache failure.
Owner:GOOGLE LLC
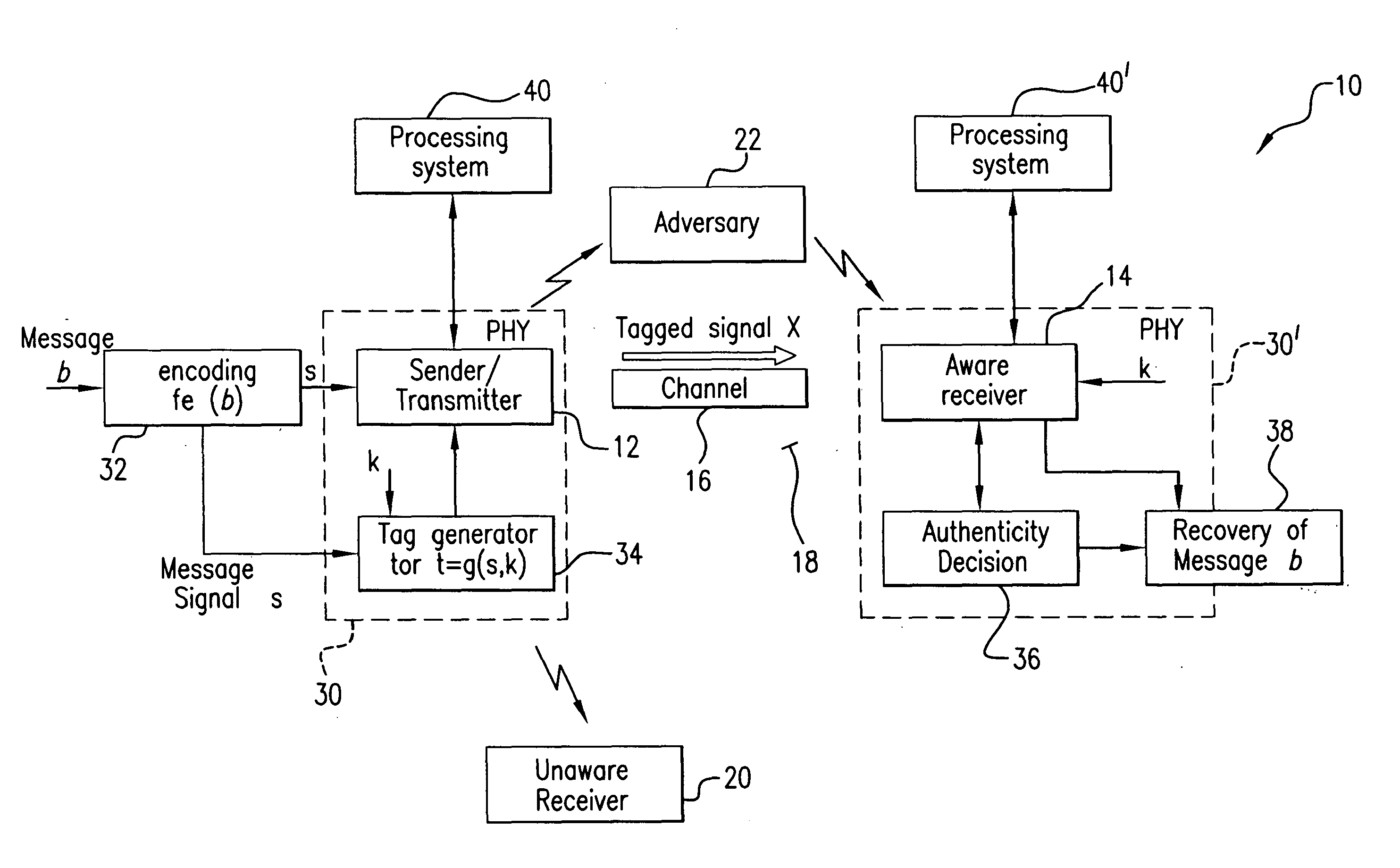
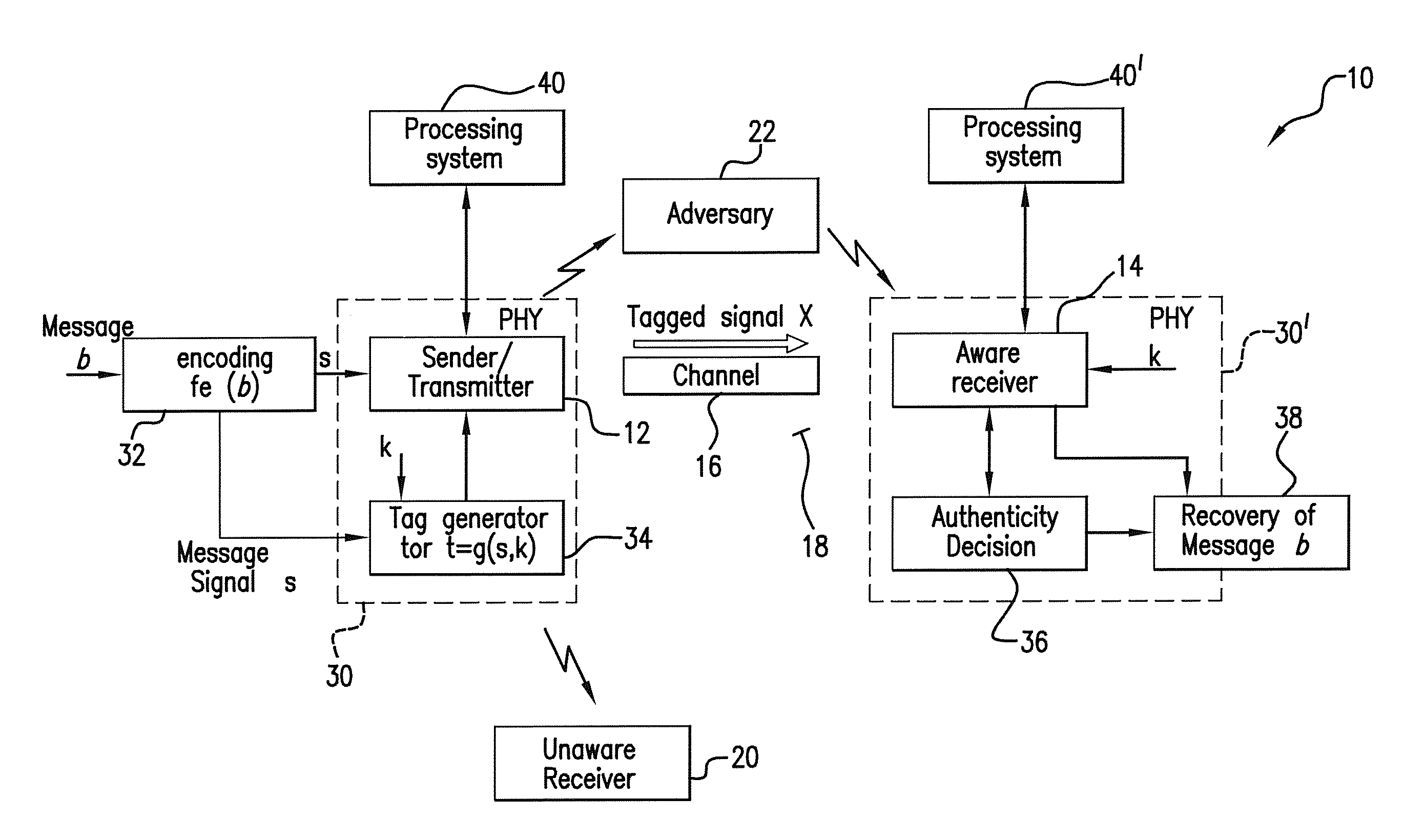
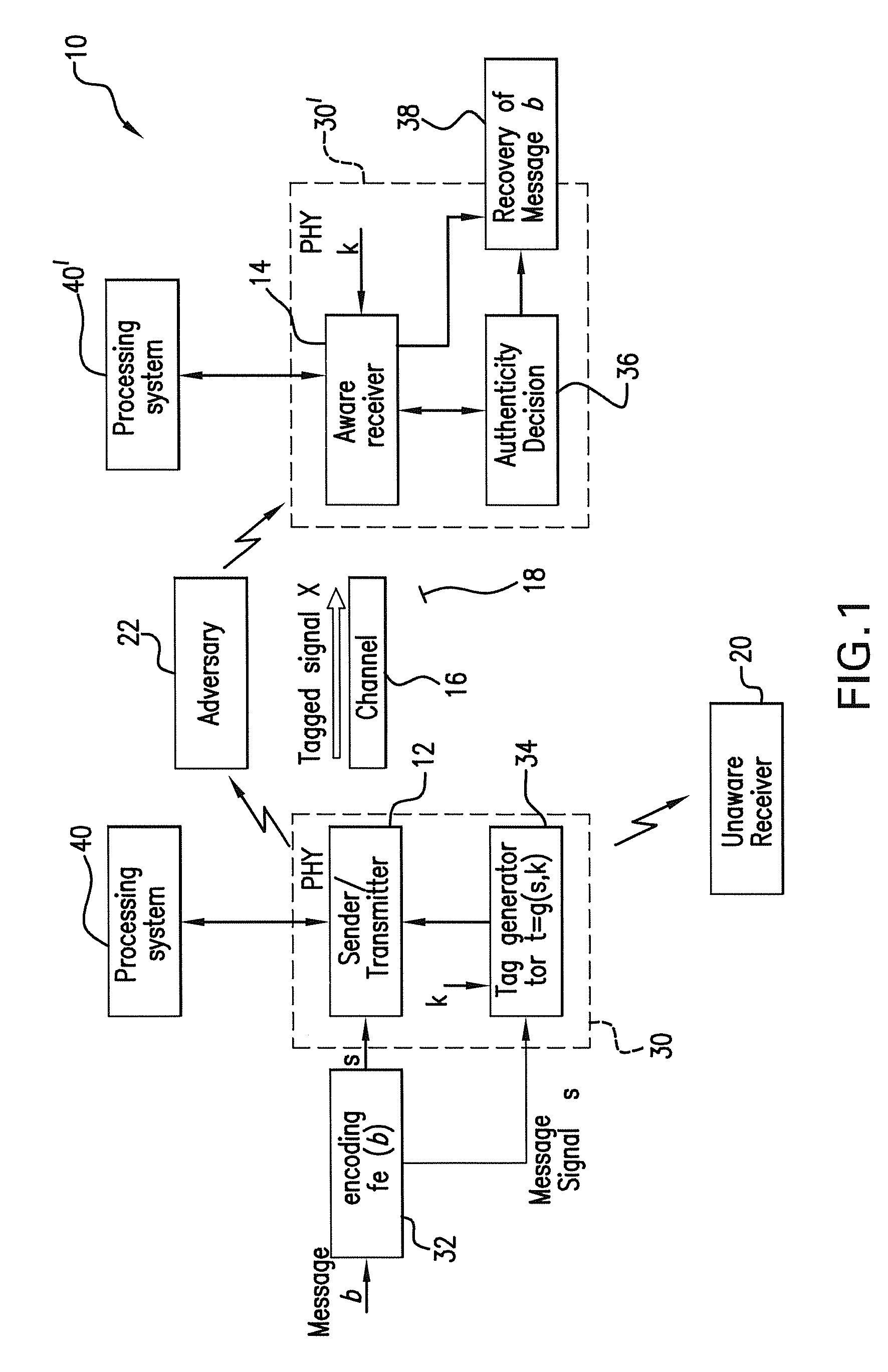
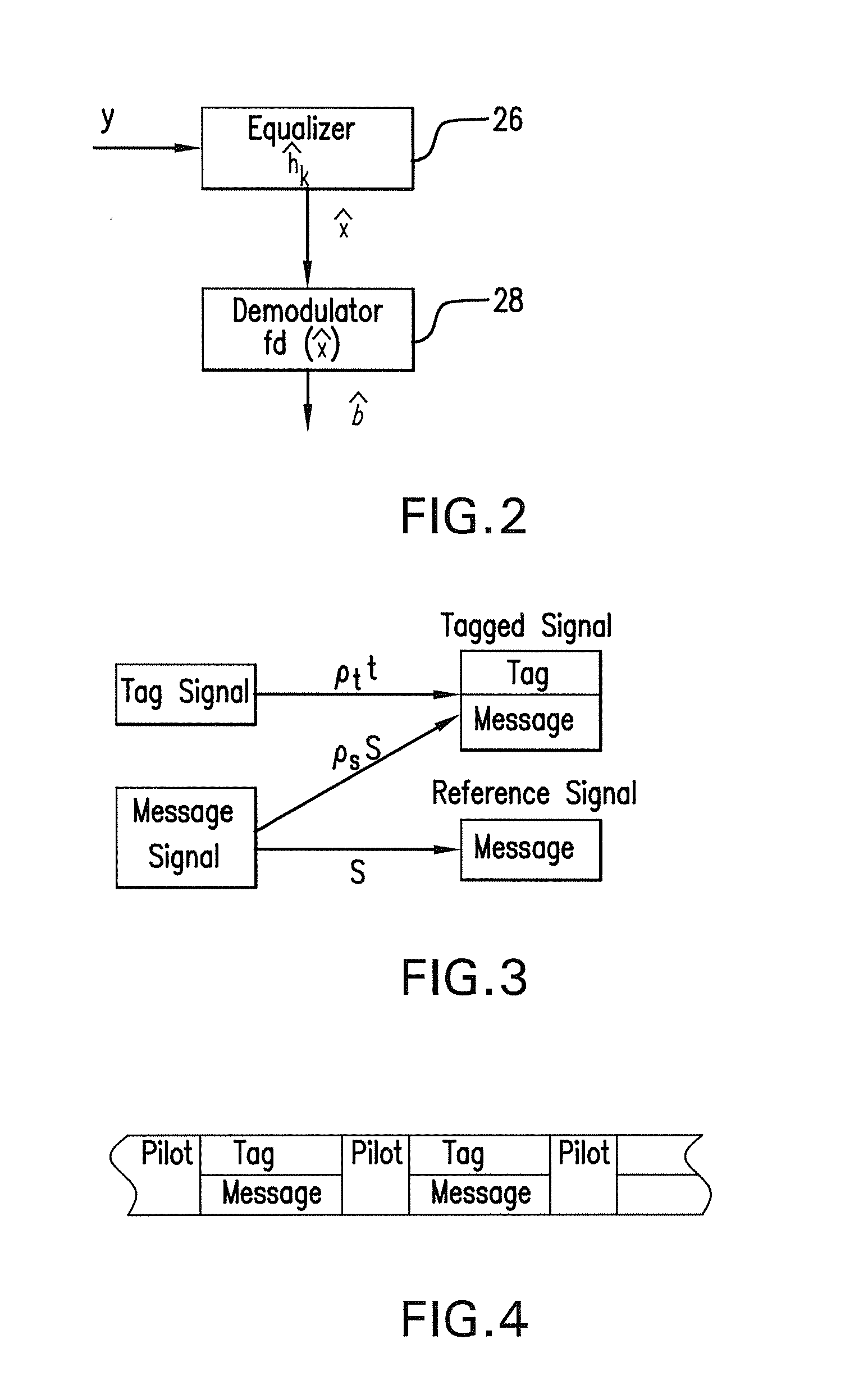
Wireless communication method and system for transmission authentication at the physical layer
InactiveUS20100246825A1Improve anti-interference abilityAuthentication securityUser identity/authority verificationSecret communicationInterference (communication)Engineering
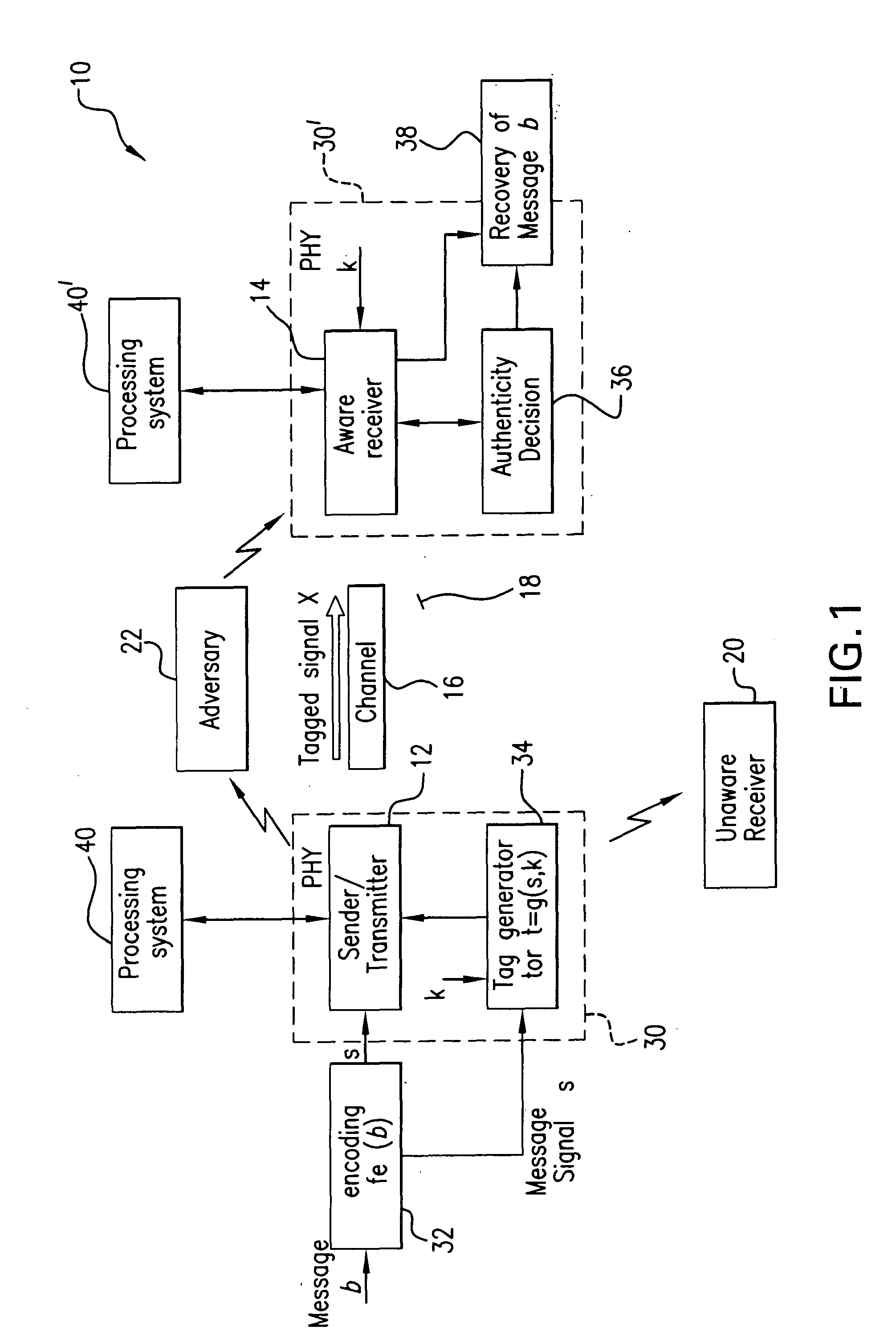
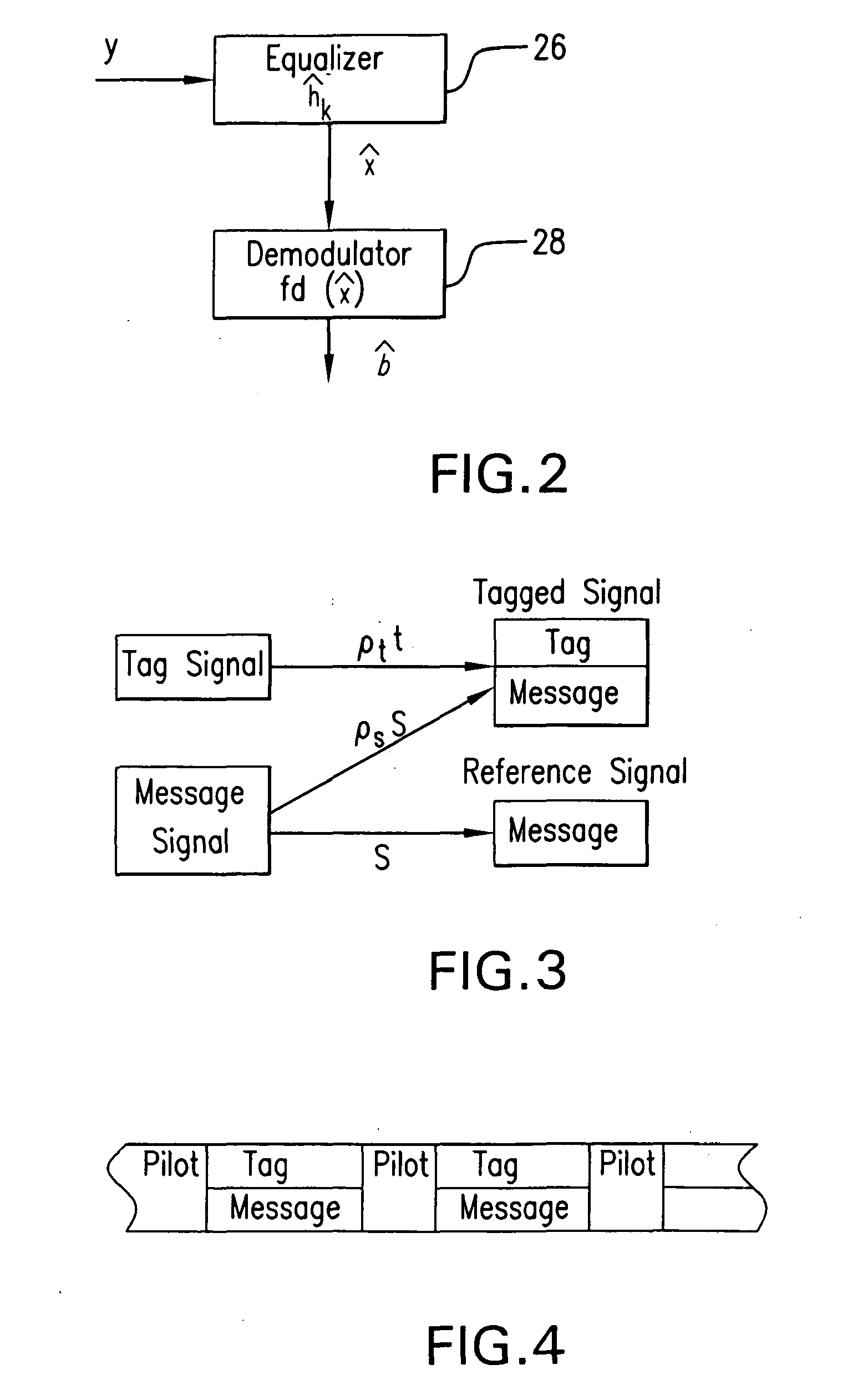
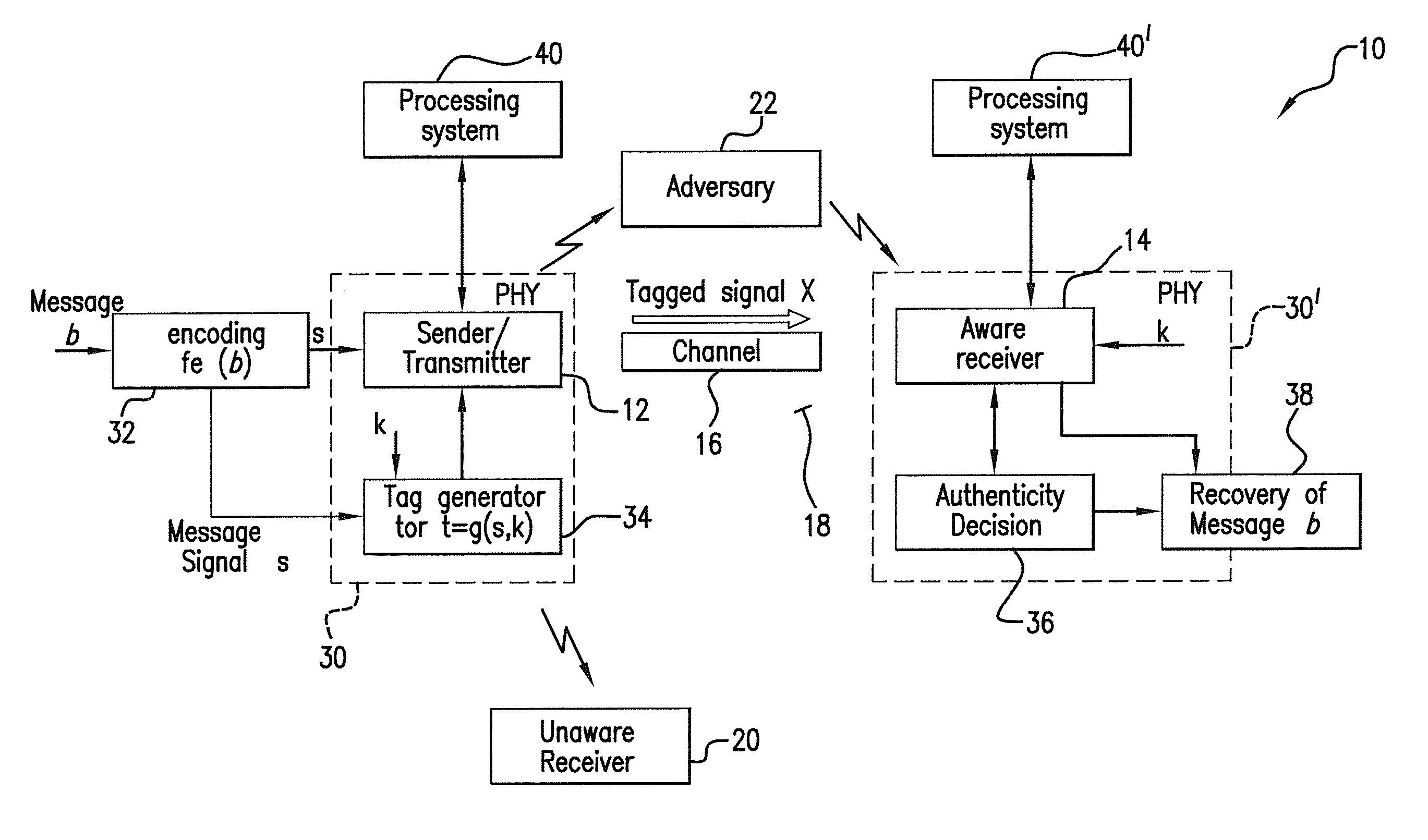
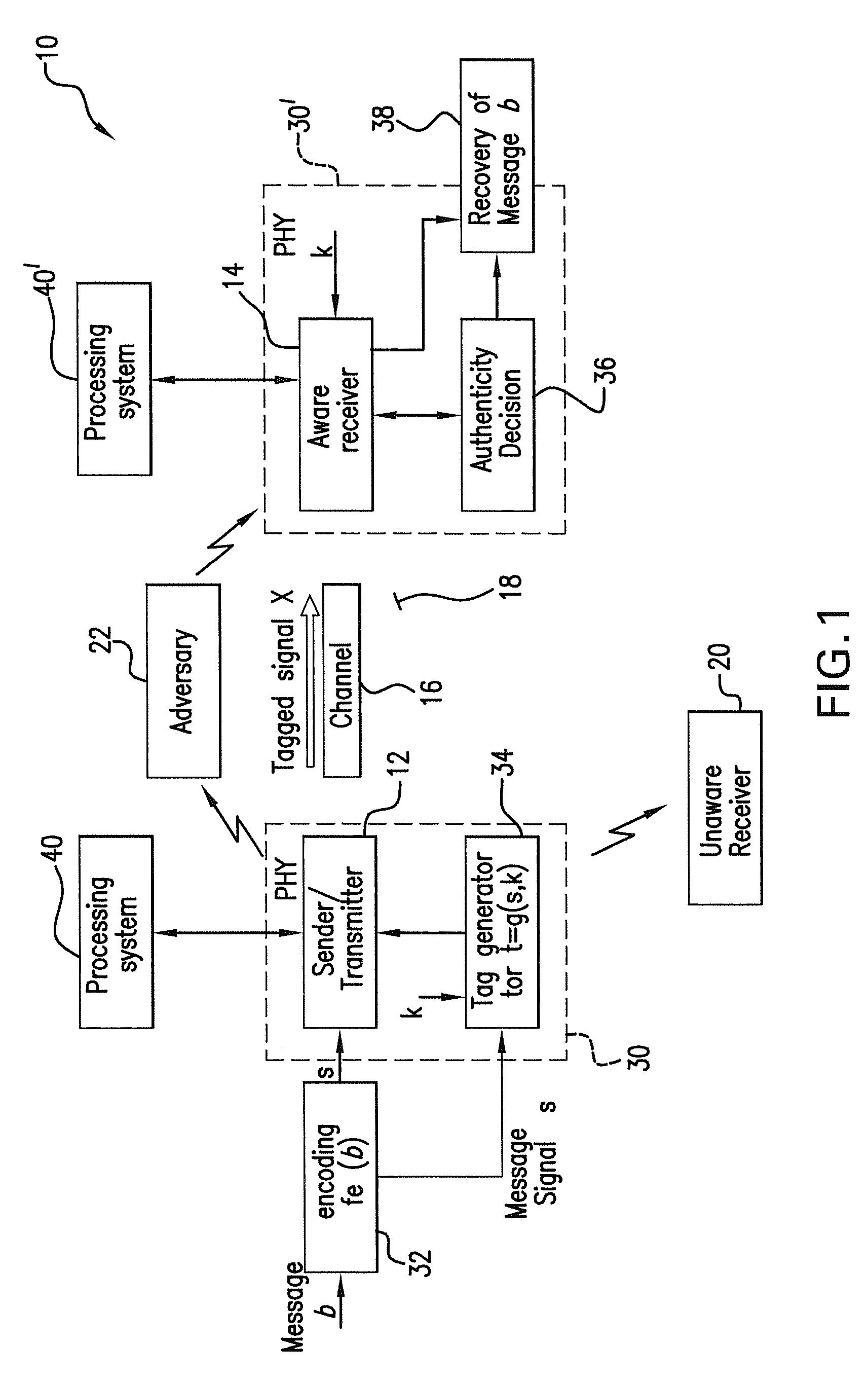
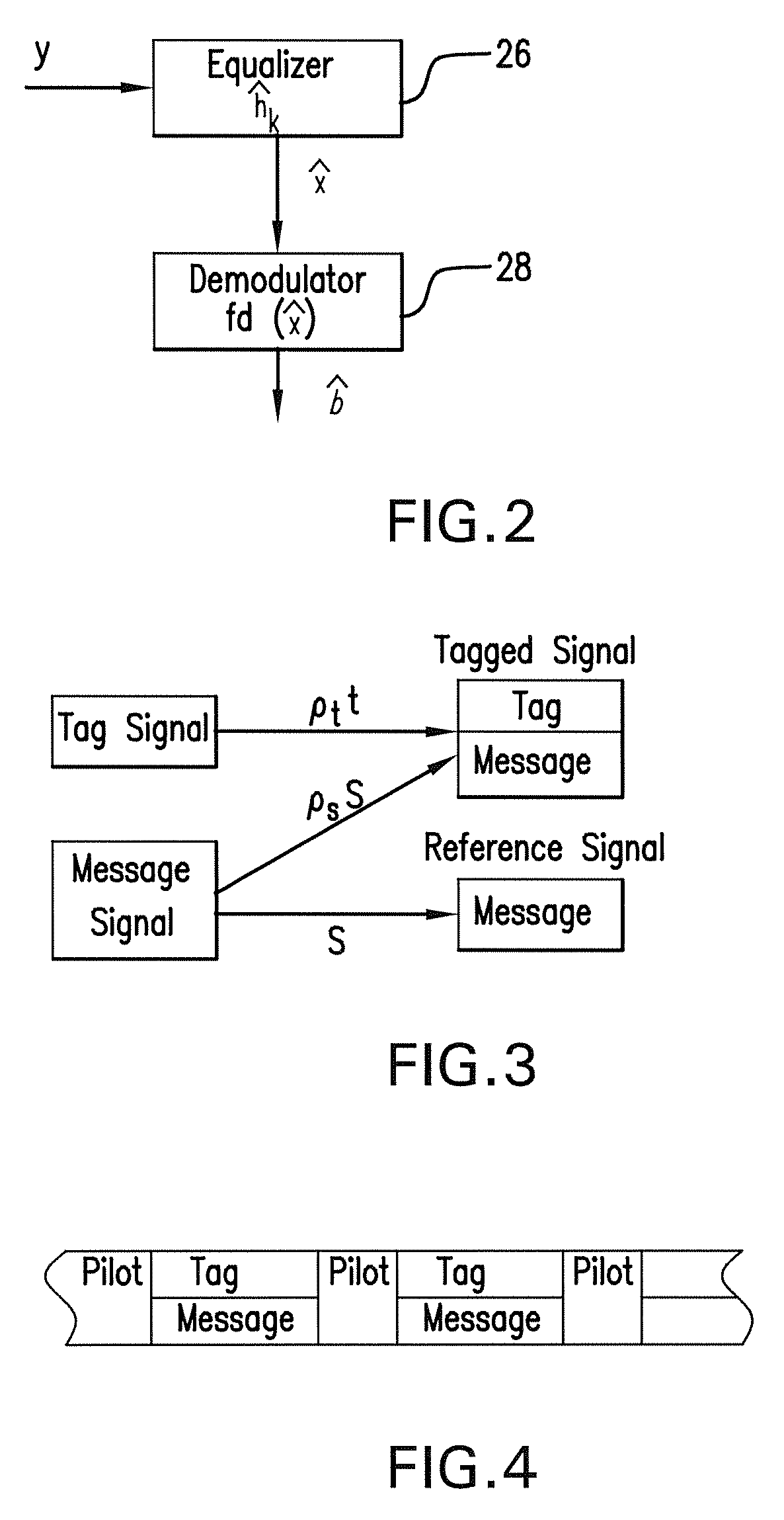
The subject authentication scheme encompasses a large family of authentication systems which may be built over existing transmission systems. By superimposing a carefully designed secret modulation on the waveforms, authentication is added to the signal without requiring additional bandwidth. The authentication information (tag signal) is sent concurrently with data (message signal). The authentication is designed to be stealthy to the uninformed user, robust to interference, and secure for identity verification. The tradeoffs between these three goals are identified and analyzed. The use of the authentication for channel estimation is also considered, and improved bit errors are demonstrated for time-varying channels. With a long enough authentication code word an authentication system is achieved with very slight data degradation. Additionally, by treating the authentication tag as a sequence of pilot symbols, the data recovery may be improved by the aware receiver.
Owner:ARMY US SEC THE THE +1
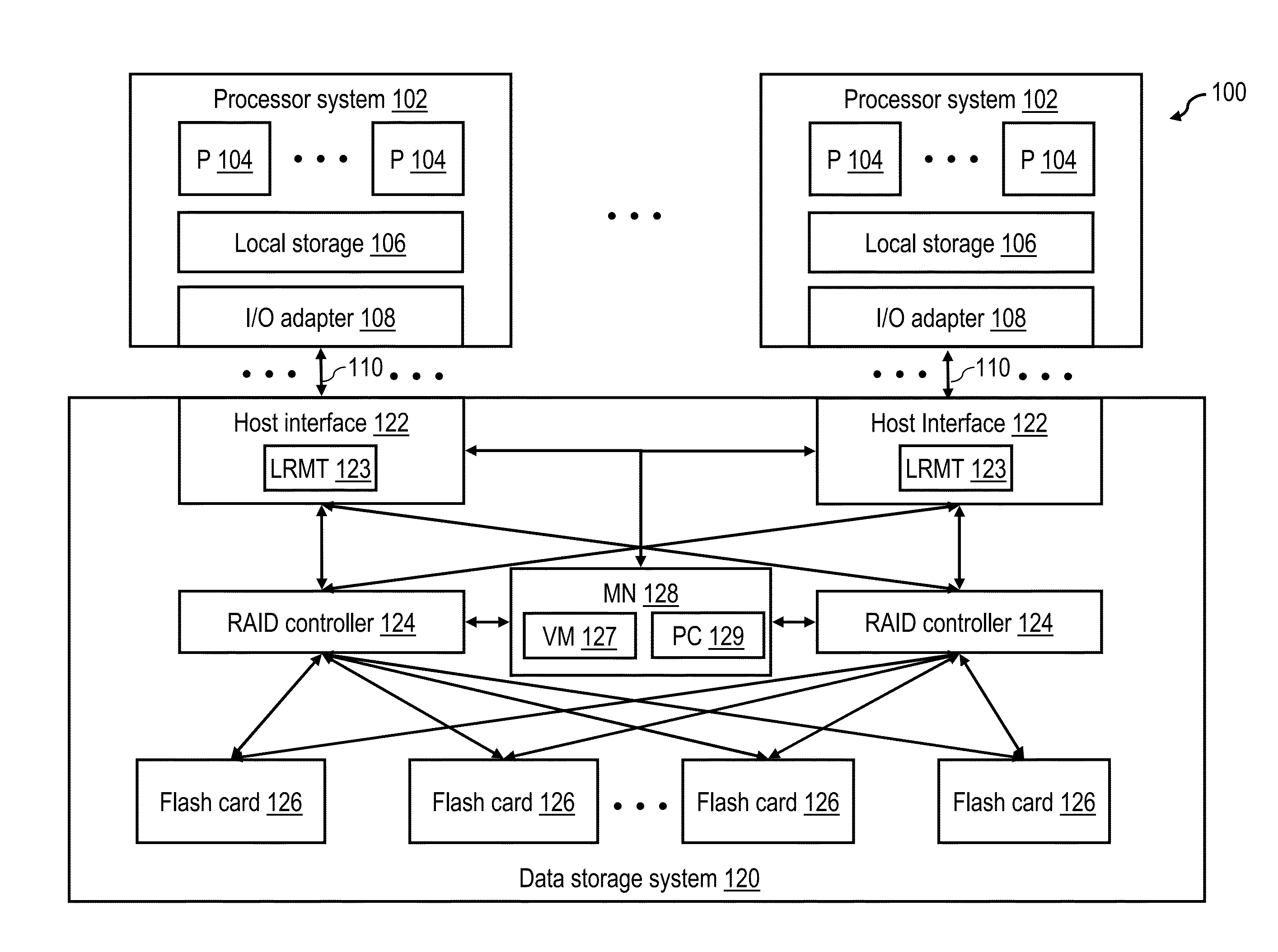
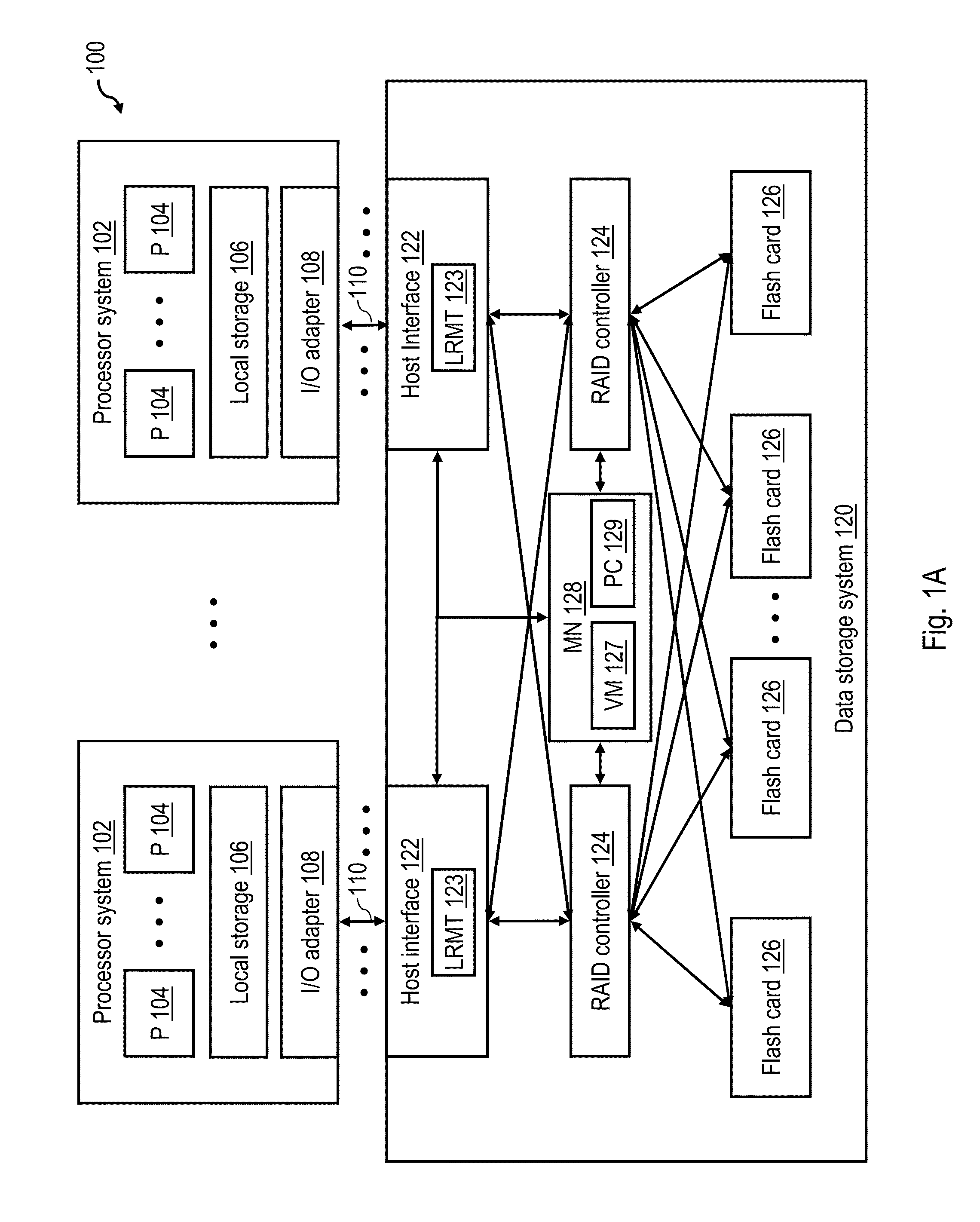
Optimizing thin provisioning in a data storage system through selective use of multiple grain sizes
ActiveUS20160188211A1Small granularityMemory architecture accessing/allocationInput/output to record carriersParallel computingThin provisioning
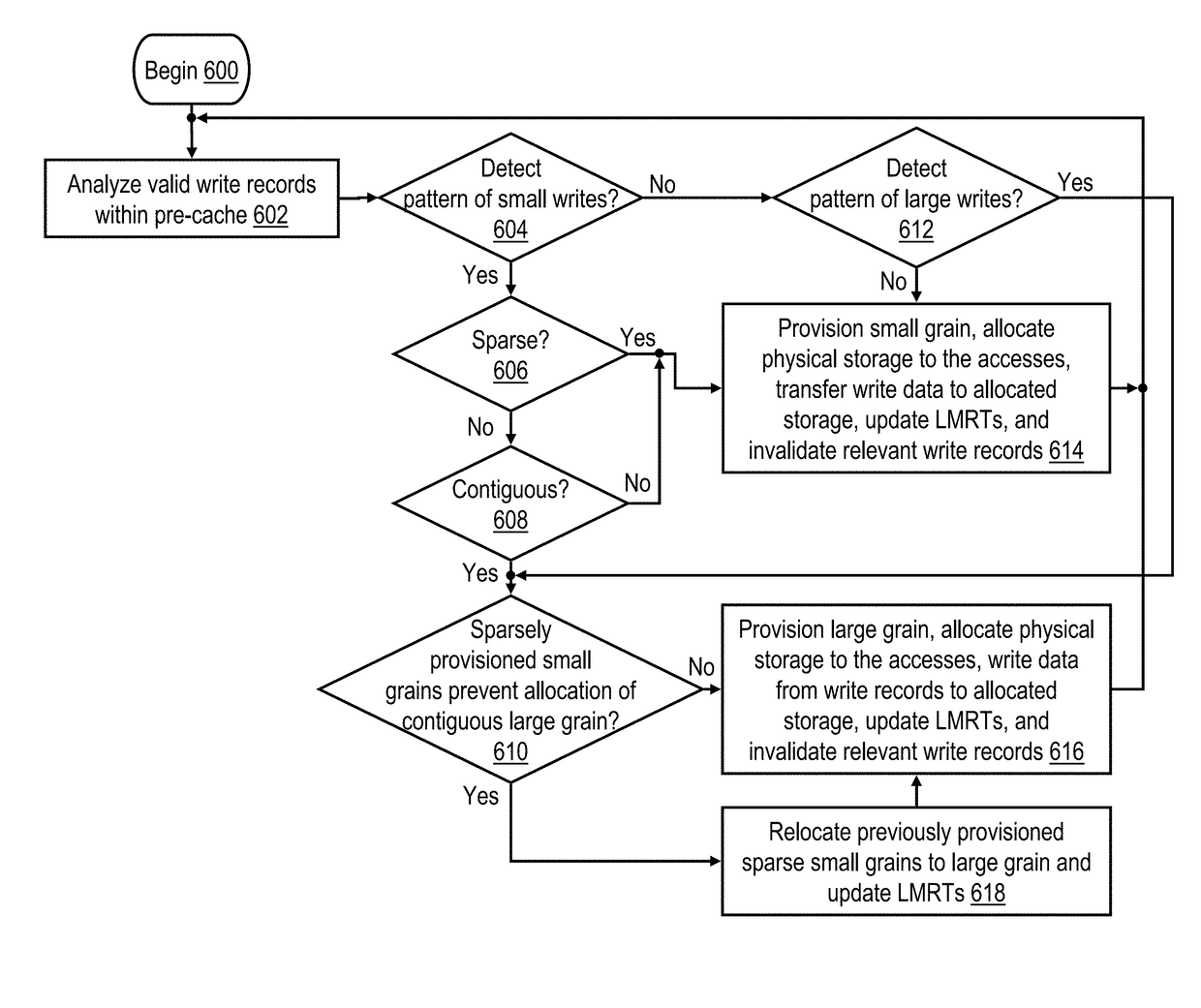
A data storage system includes a pre-cache and a plurality of storage devices across which a data storage array is distributed. In response to receipt of a write request specifying a logical address and write data, the data storage system buffers the write request among a plurality of write requests in the pre-cache without provisioning in the data storage array a physical extent corresponding to the logical address. A management node analyzes the plurality of write requests buffered in the pre-cache. In response to the analyzing identifying a first pattern of write requests, the management node provisions, in the data storage array, a first physical extent having a smaller grain size and destages the write data to the first physical extent. In response to the analyzing identifying a second pattern of write requests, the management node provisions a second physical extent having a larger grain size and destages the write data from the pre-cache to the second physical extent.
Owner:IBM CORP
Wireless communication method and system for transmission authentication at the physical layer
ActiveUS20130163761A1Improve anti-interference abilitySafety verificationBroadcast specific applicationsSecret communicationTransfer systemPhysical layer
The subject authentication scheme encompasses a large family of authentication systems which may be built over existing transmission systems. By superimposing a carefully designed secret modulation on the waveforms, authentication is added to the signal without requiring additional bandwidth. The authentication information (tag signal) is sent concurrently with data (message signal). The authentication is designed to be stealthy to the uninformed user, robust to interference, and secure for identity verification. The tradeoffs between these three goals are identified and analyzed. The use of the authentication for channel estimation is also considered, and improved bit errors are demonstrated for time-varying channels. With a long enough authentication code word an authentication system is achieved with very slight data degradation. Additionally, by treating the authentication tag as a sequence of pilot symbols, the data recovery may be improved by the aware receiver.
Owner:US SEC THE ARMY THE +1
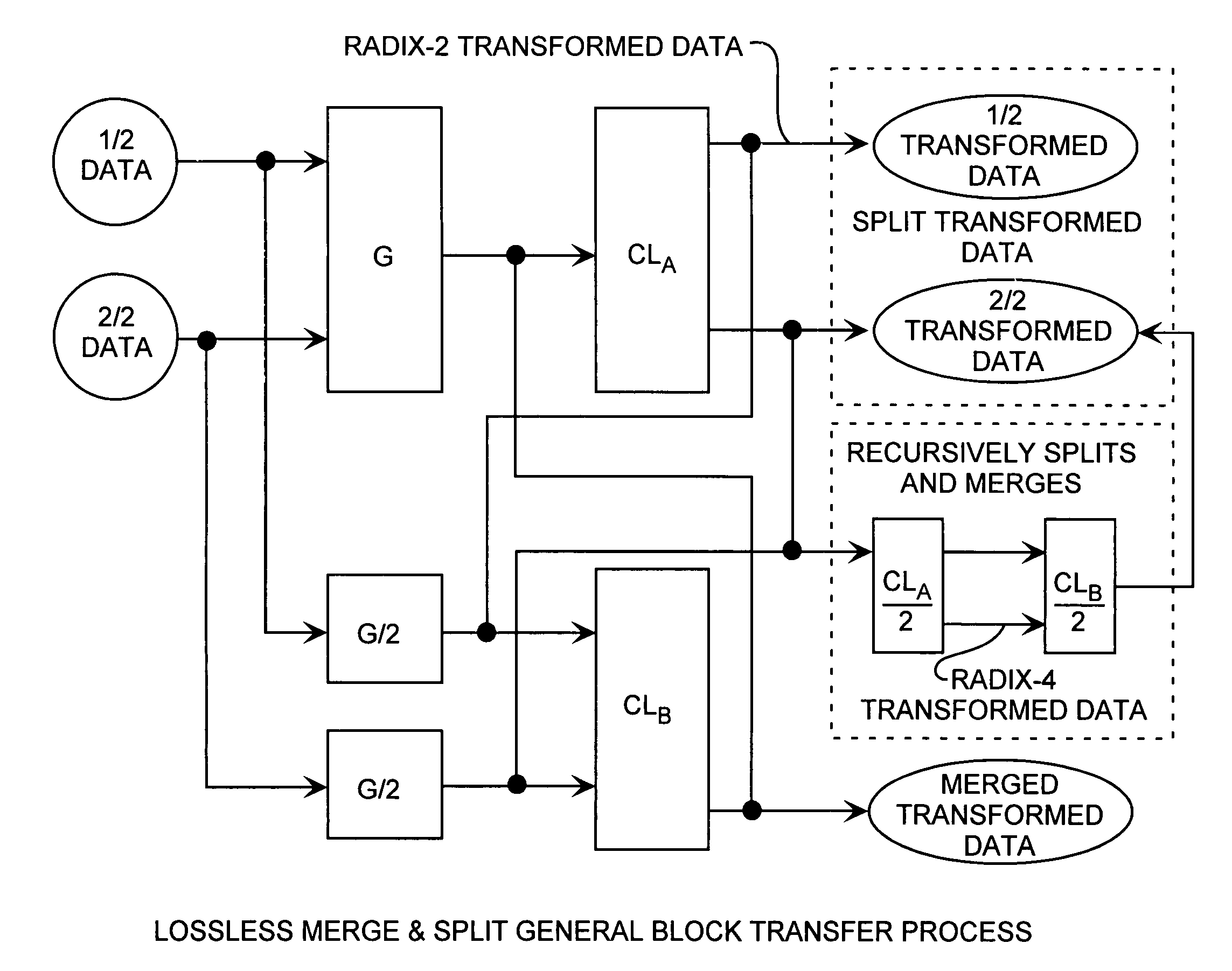
Merge and split discrete cosine block transform method
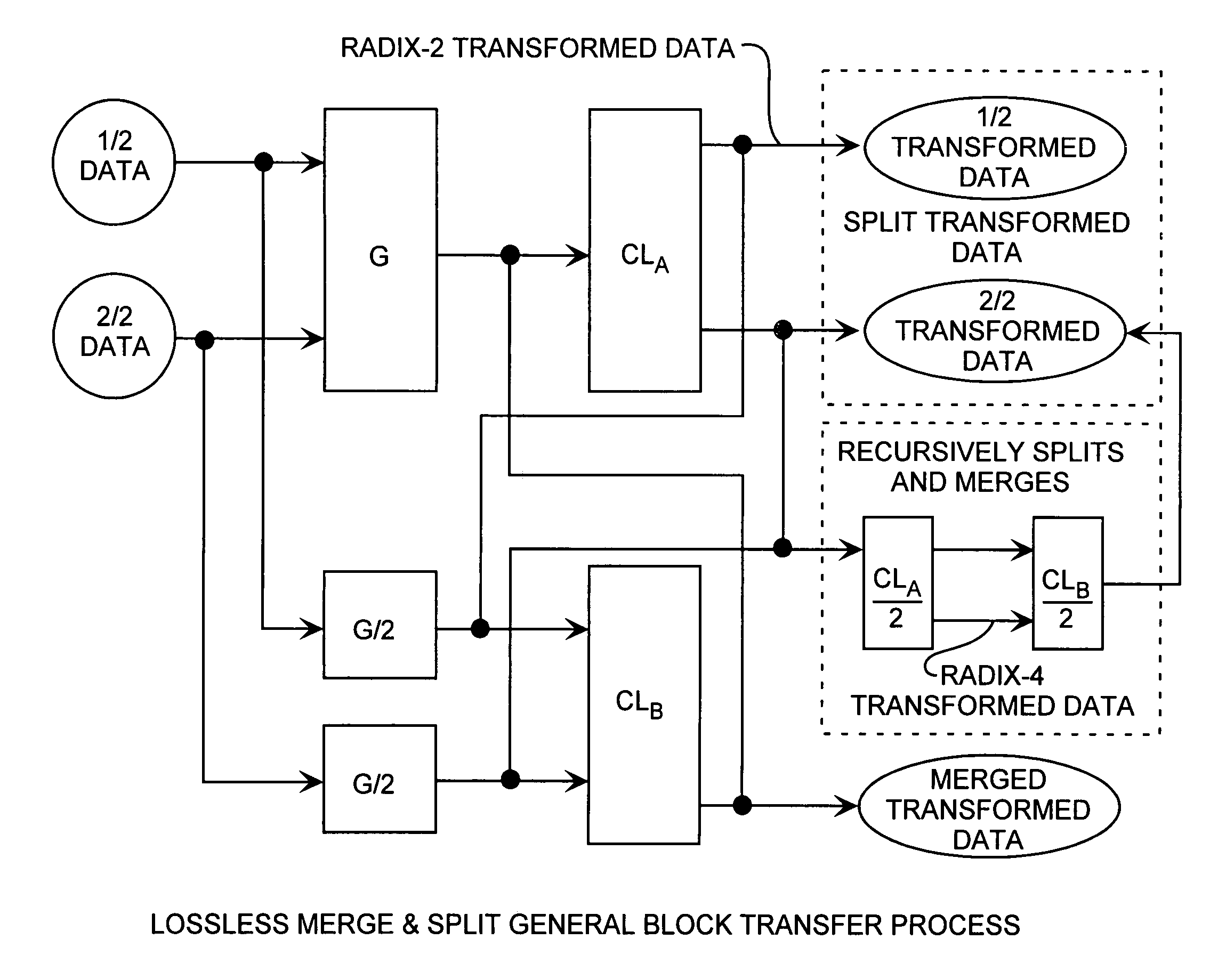
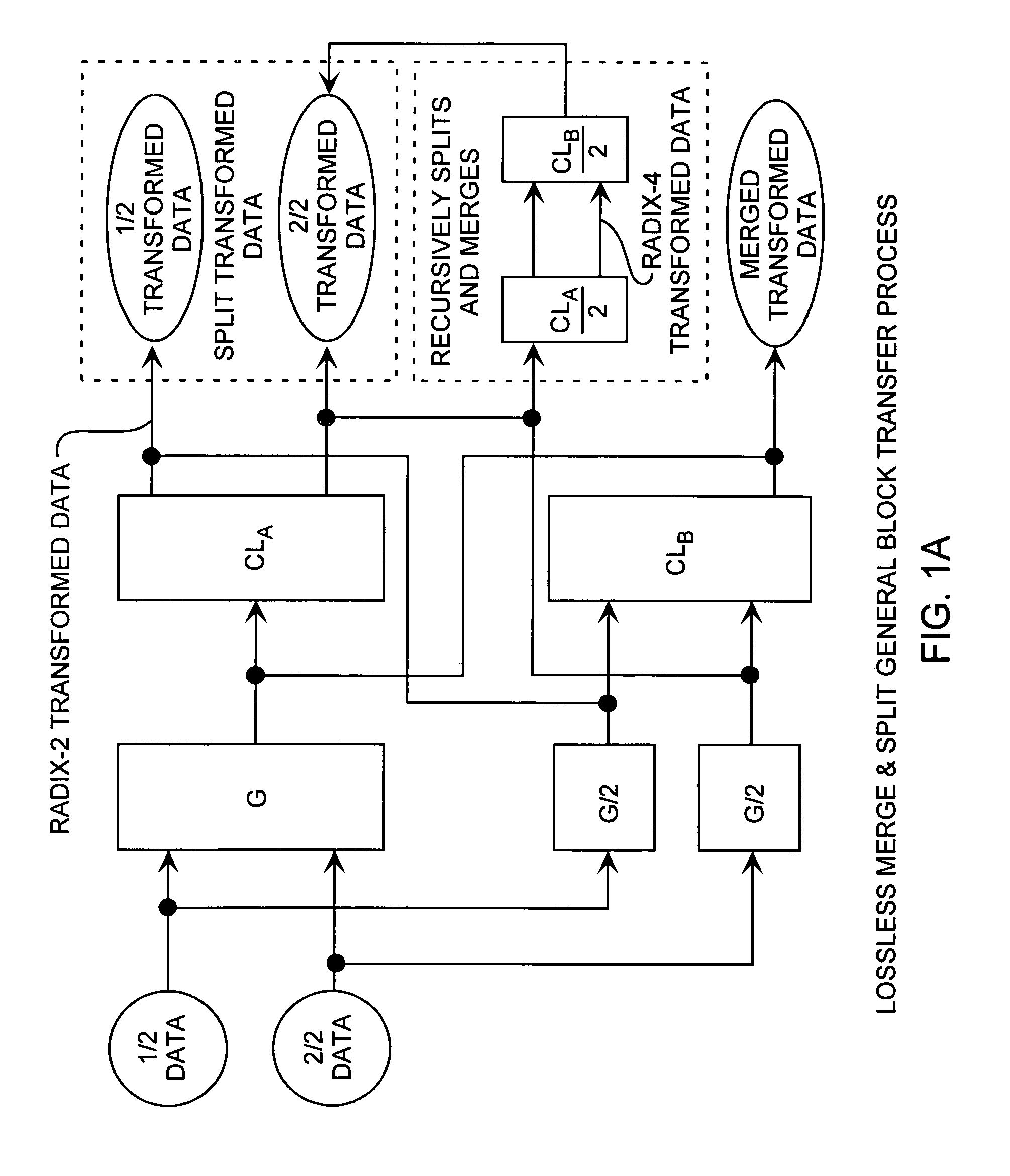
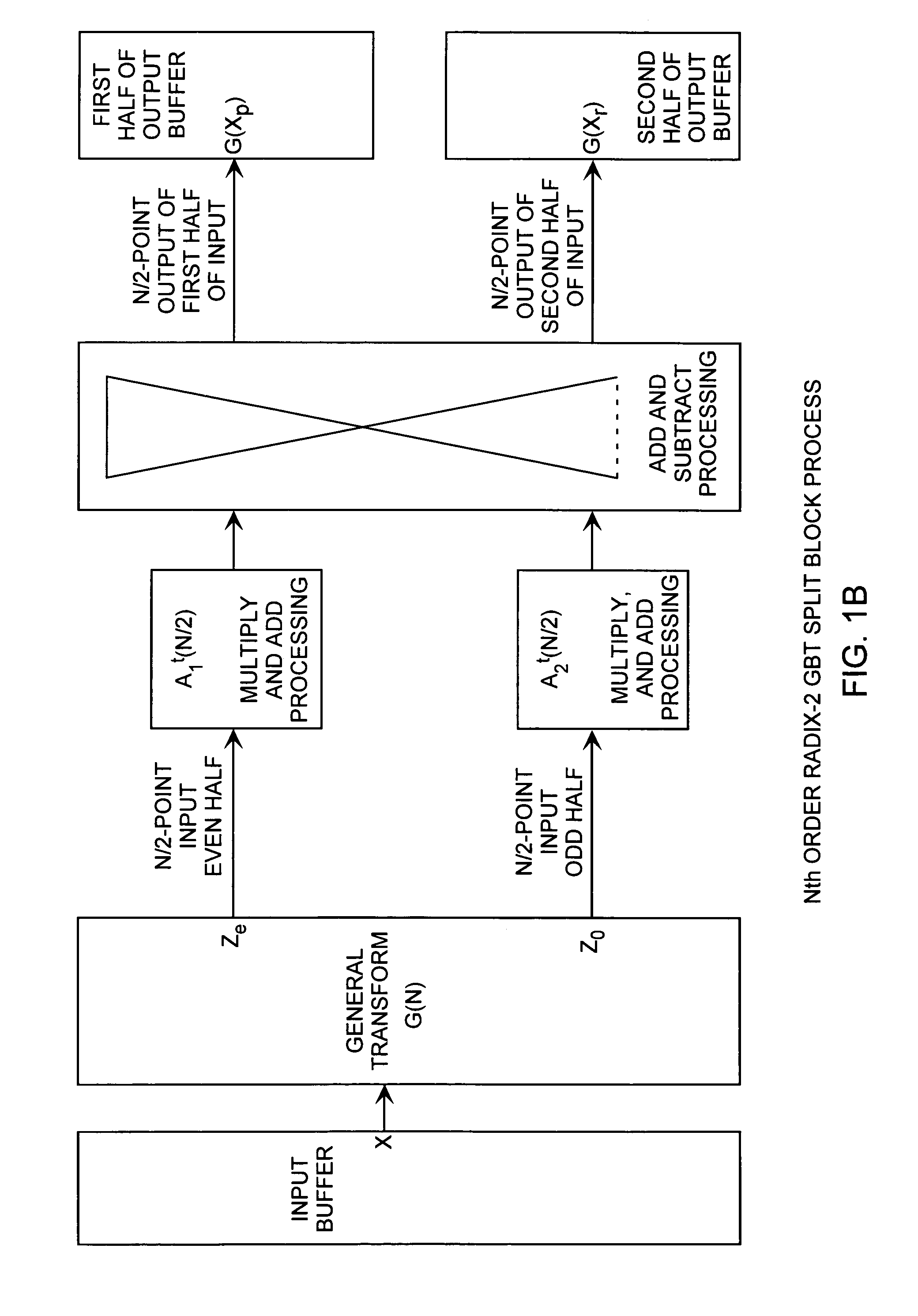
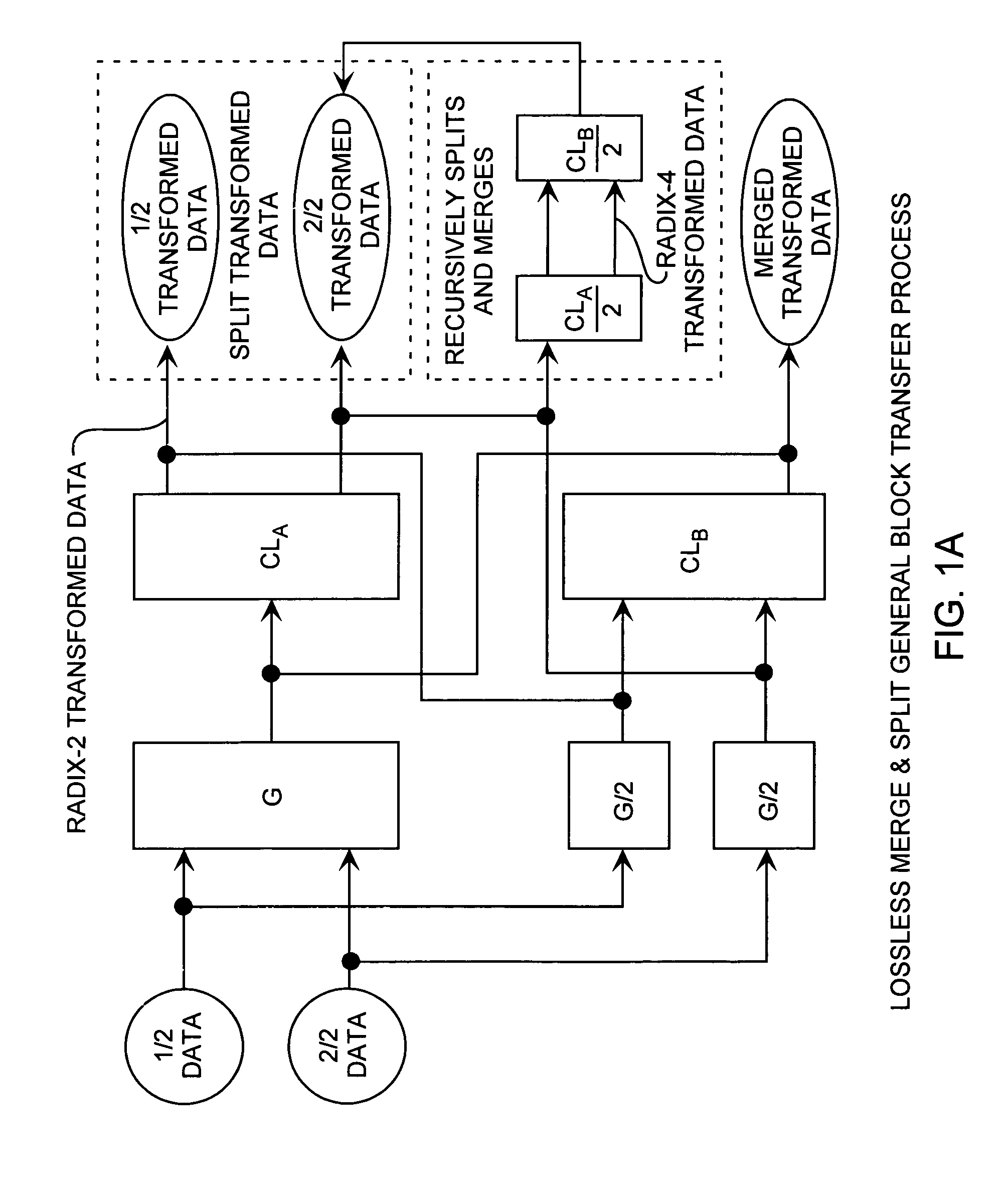
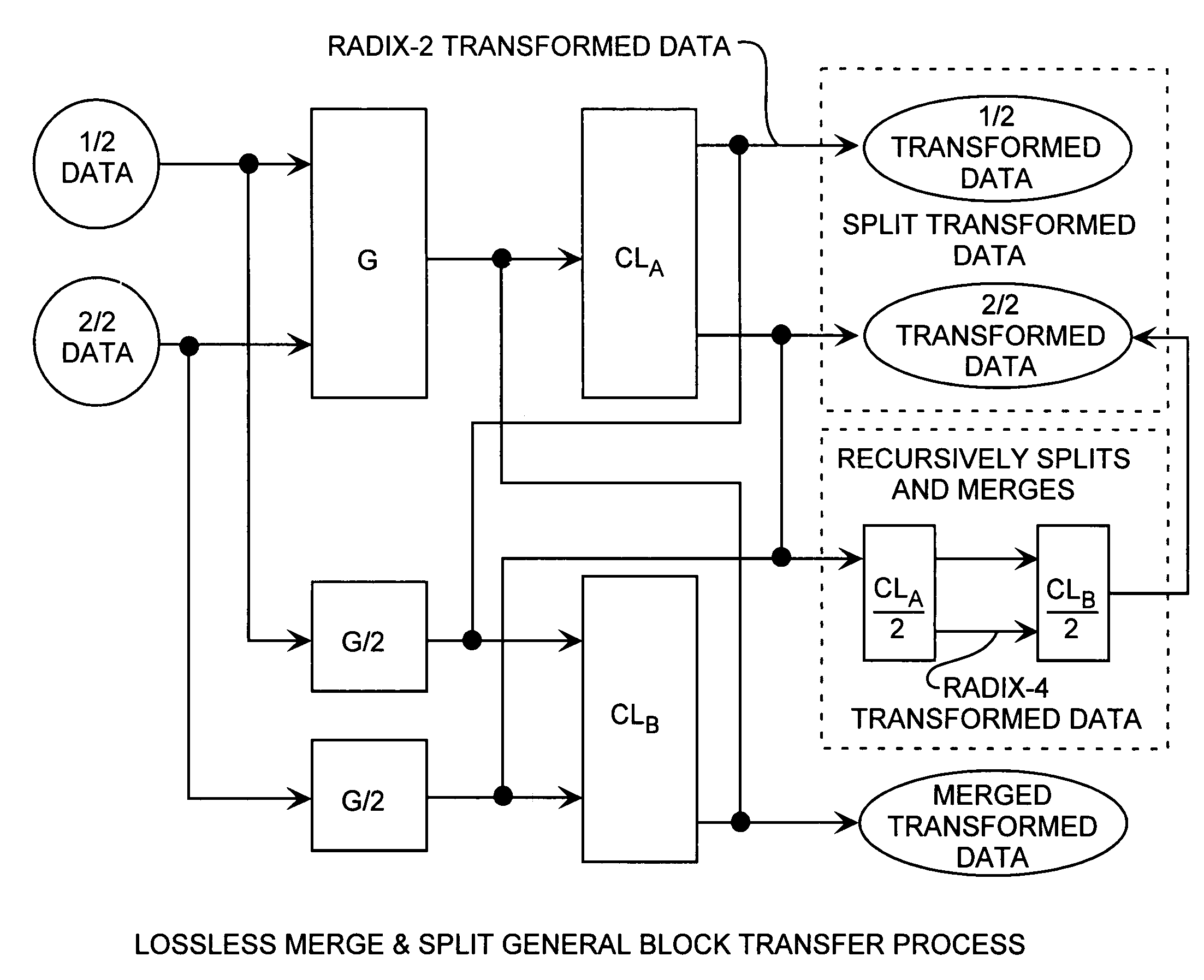
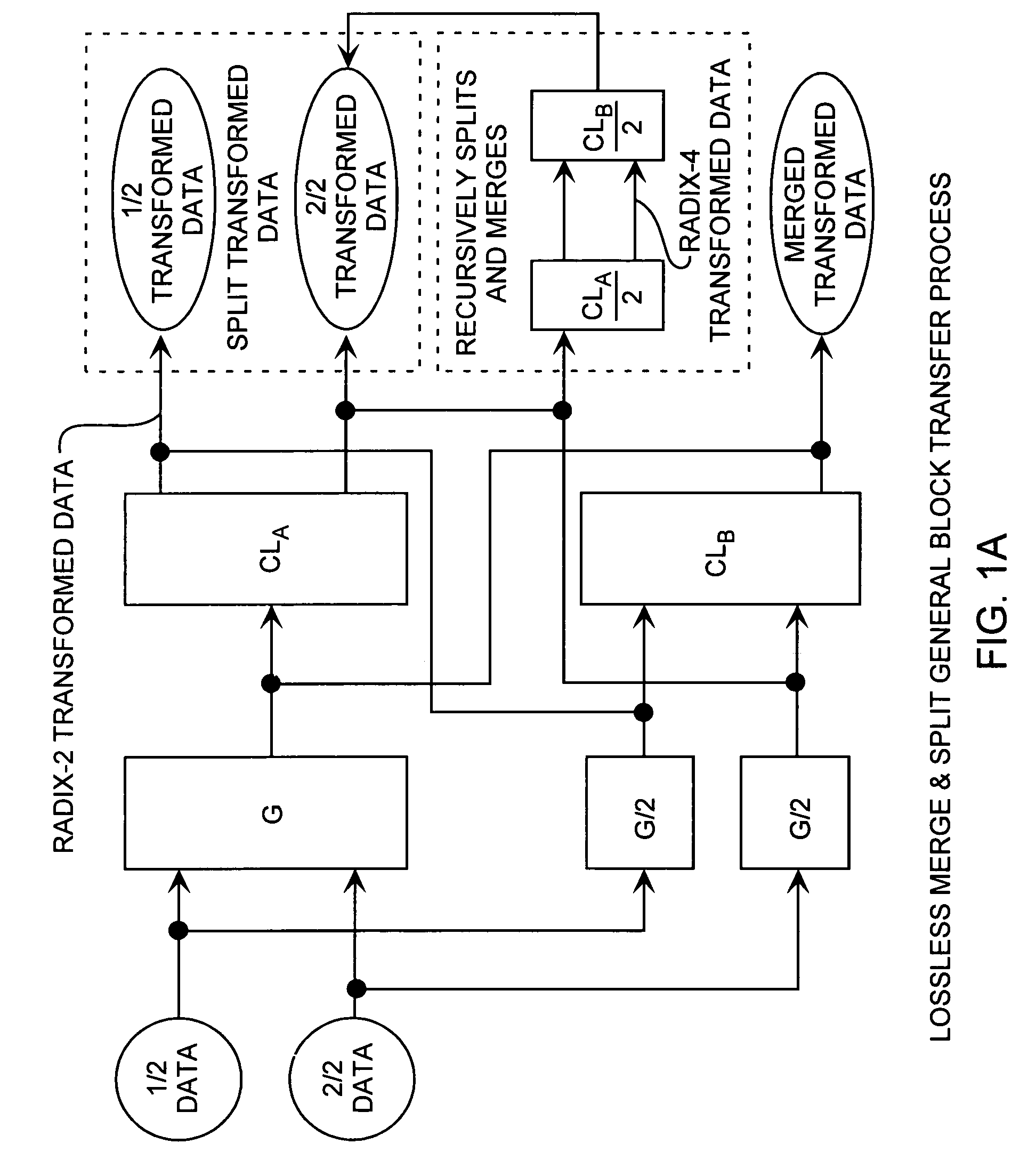
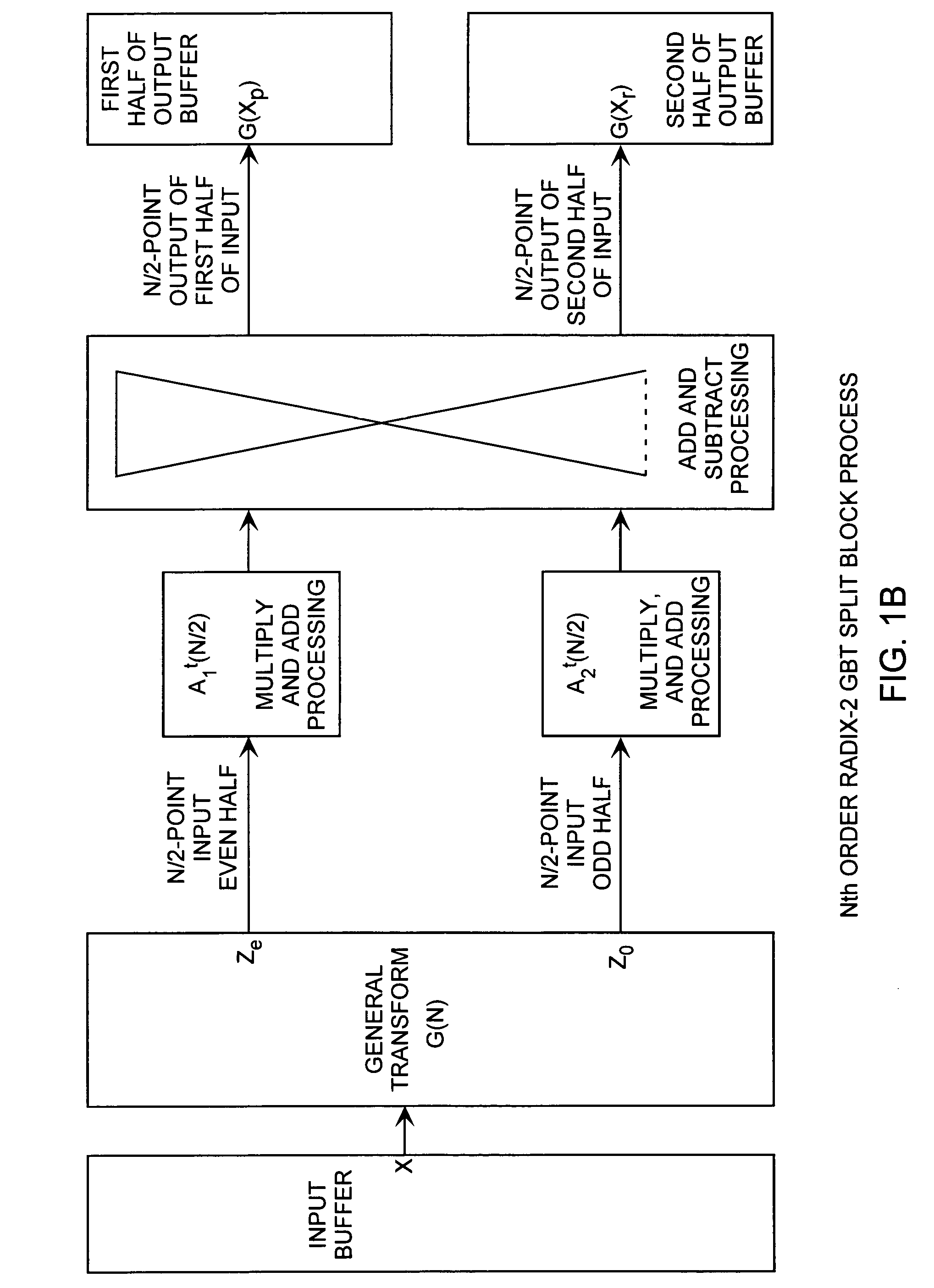
Discrete Cosine Transforms in a radix-2 block transform method enables true split and merge transform processing of equal sized data halves in the transform domain for enabling recursive merges and splits in transform domain without data degradation. Input data in the time domain or spatial domain during either the split and merge radix-2 forward transform processing is firstly transform processed followed by combinational processing. In the split transform process, whole transformed data is split using combinational processing into first and second transformed data halves in the transform domain as a true split. In the merge transform process, first and second transform halves are merged using combinational processing into a merged transformed data whole in the transform domain. In either case, time or spatial domain input data can be transformed into the transform domain in the form of split halves or merged whole. The split halves can be merged by the merge process combinational processing and the merged whole can be split by the split process combinational processing. The split and merge process combinational processing enable recursive splits and merges in the transform domain.
Owner:THE AEROSPACE CORPORATION
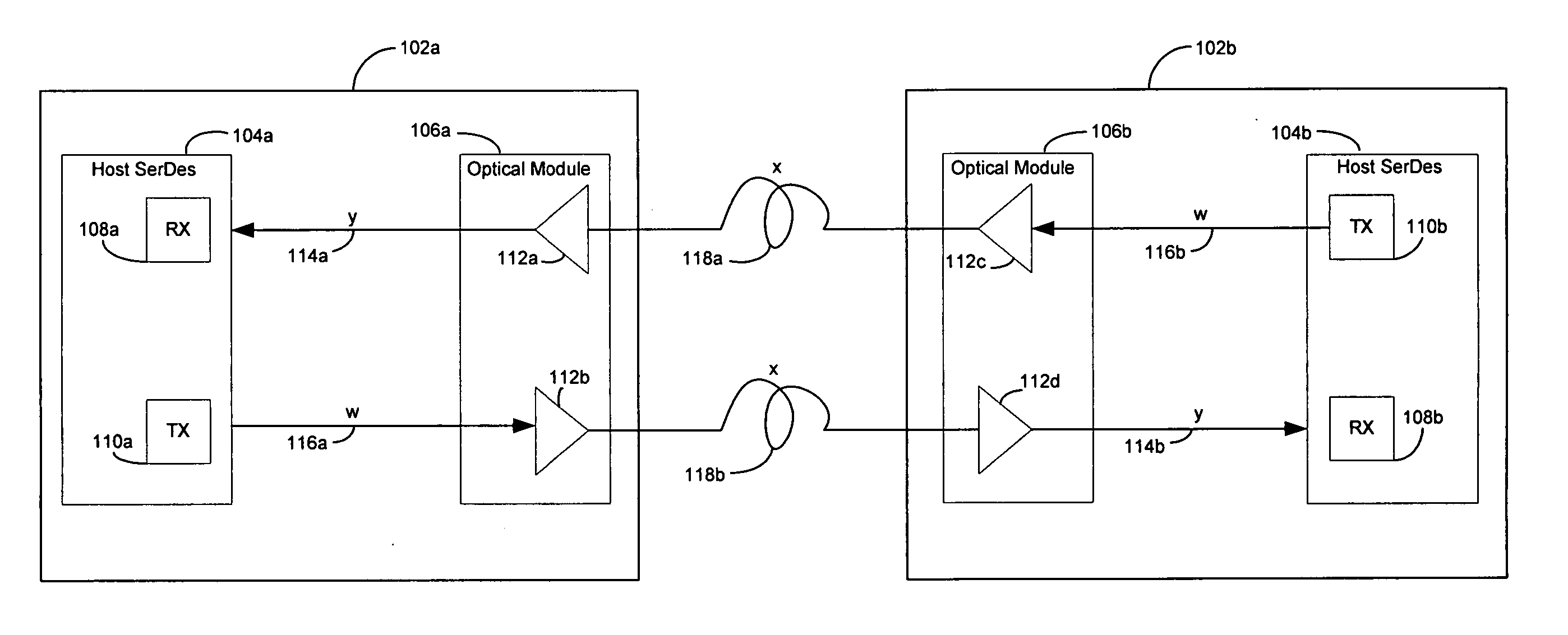
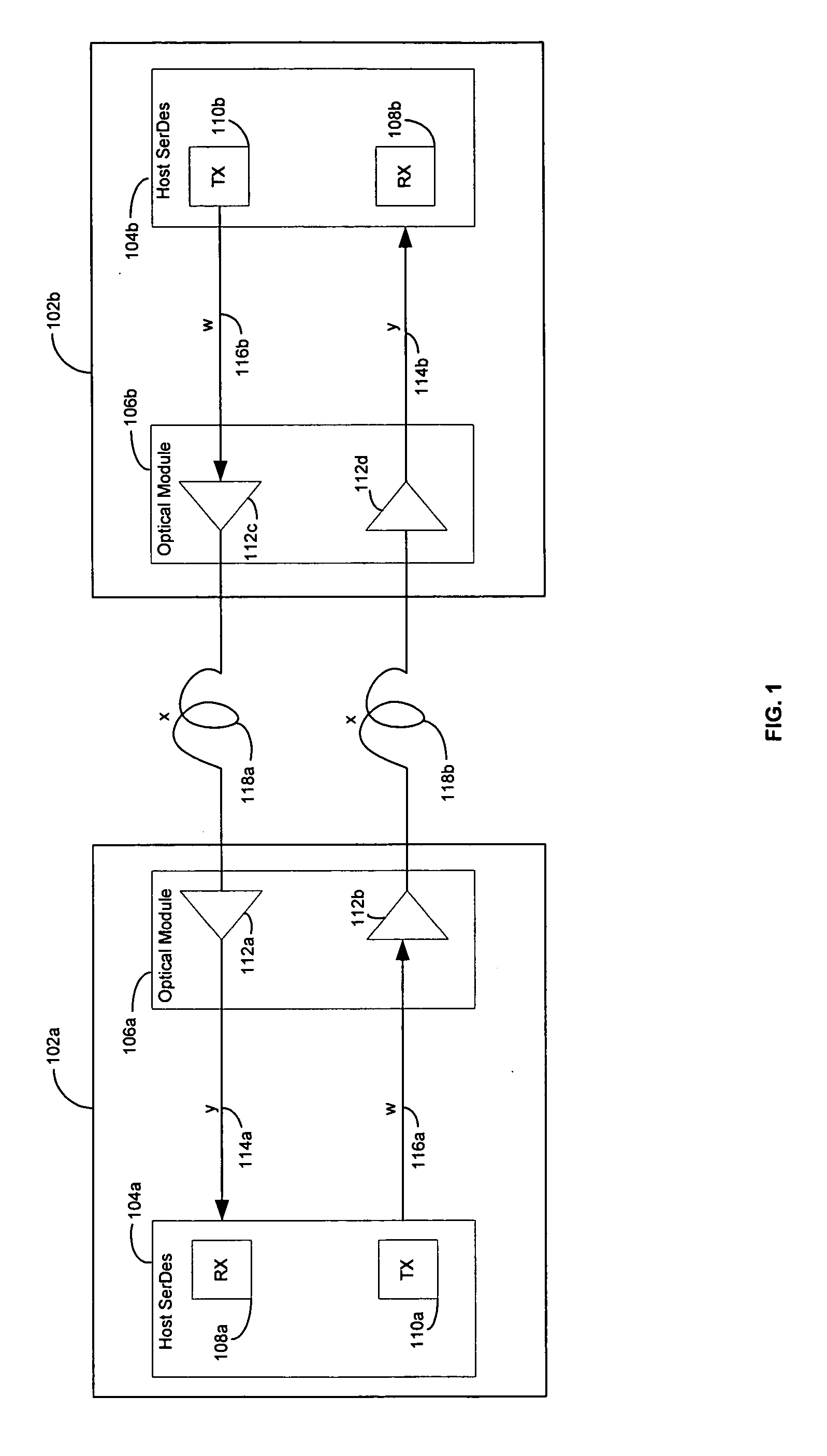
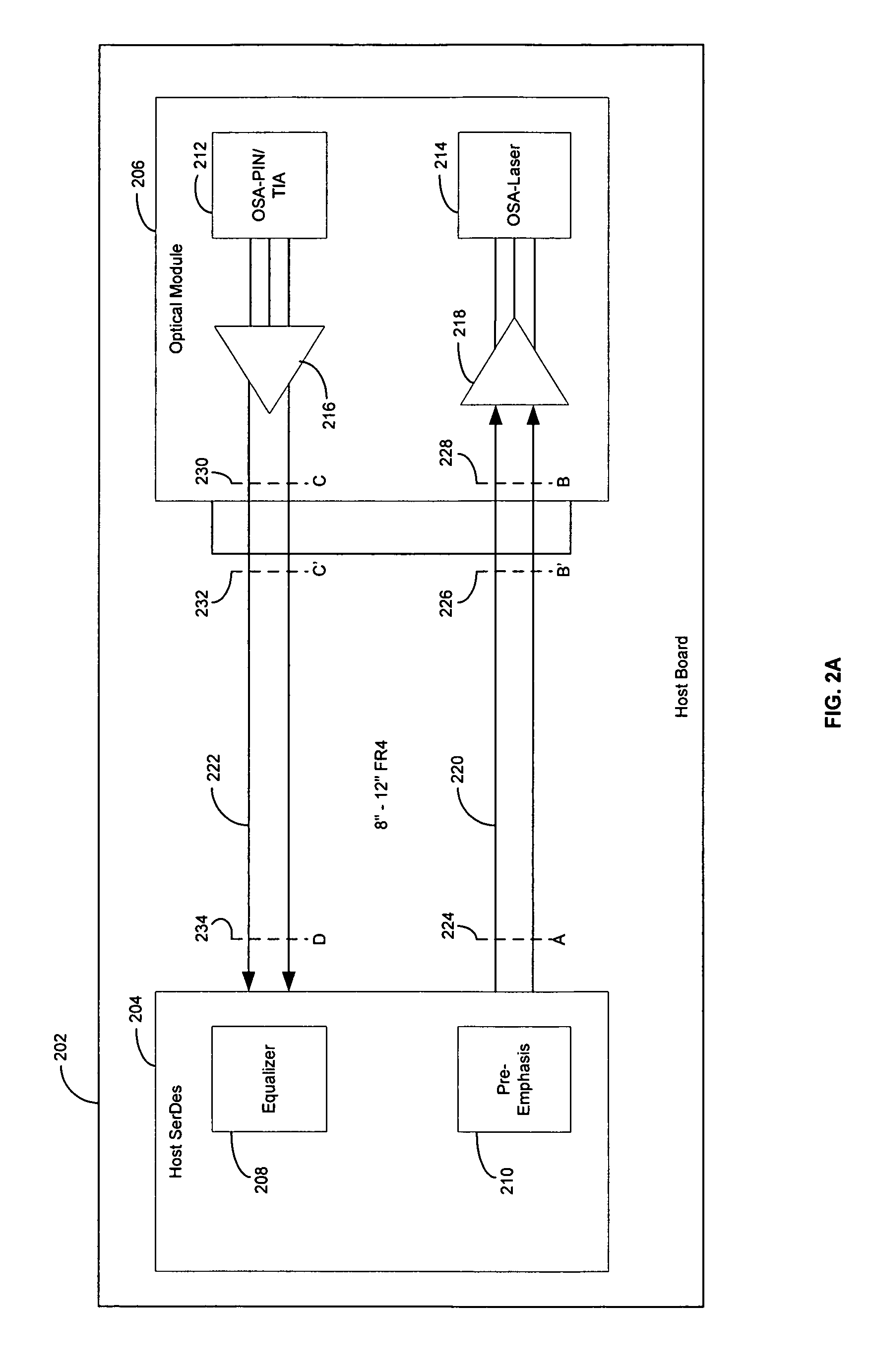
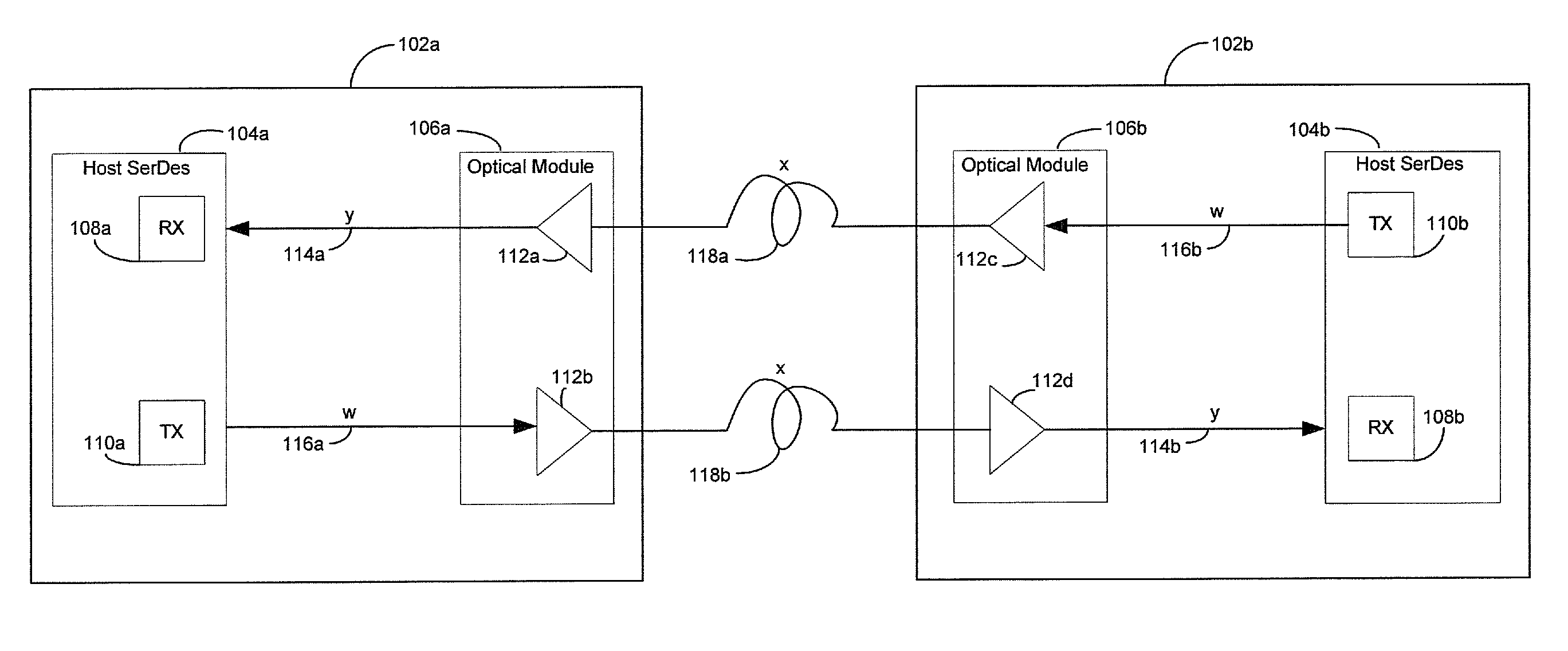
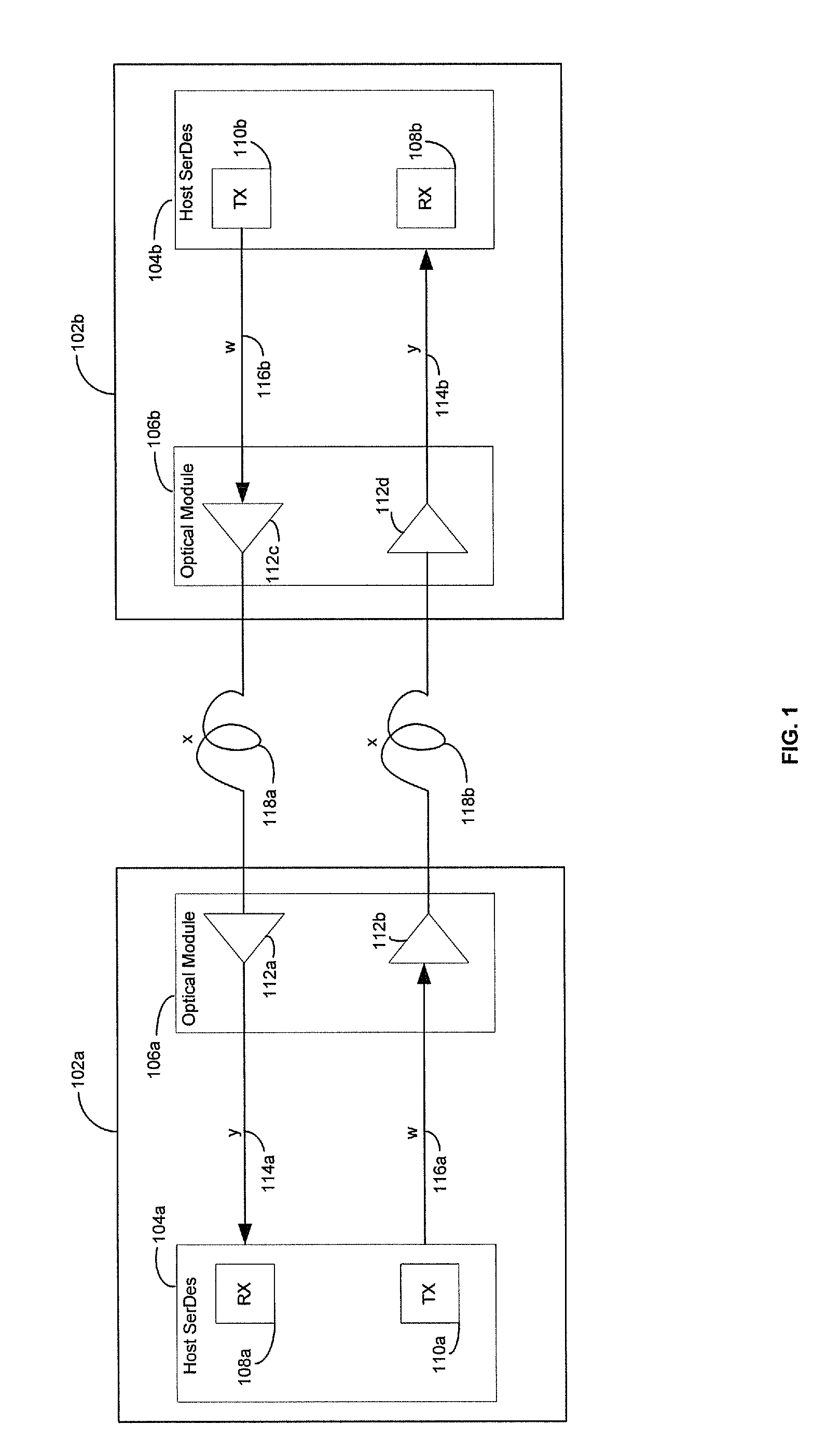
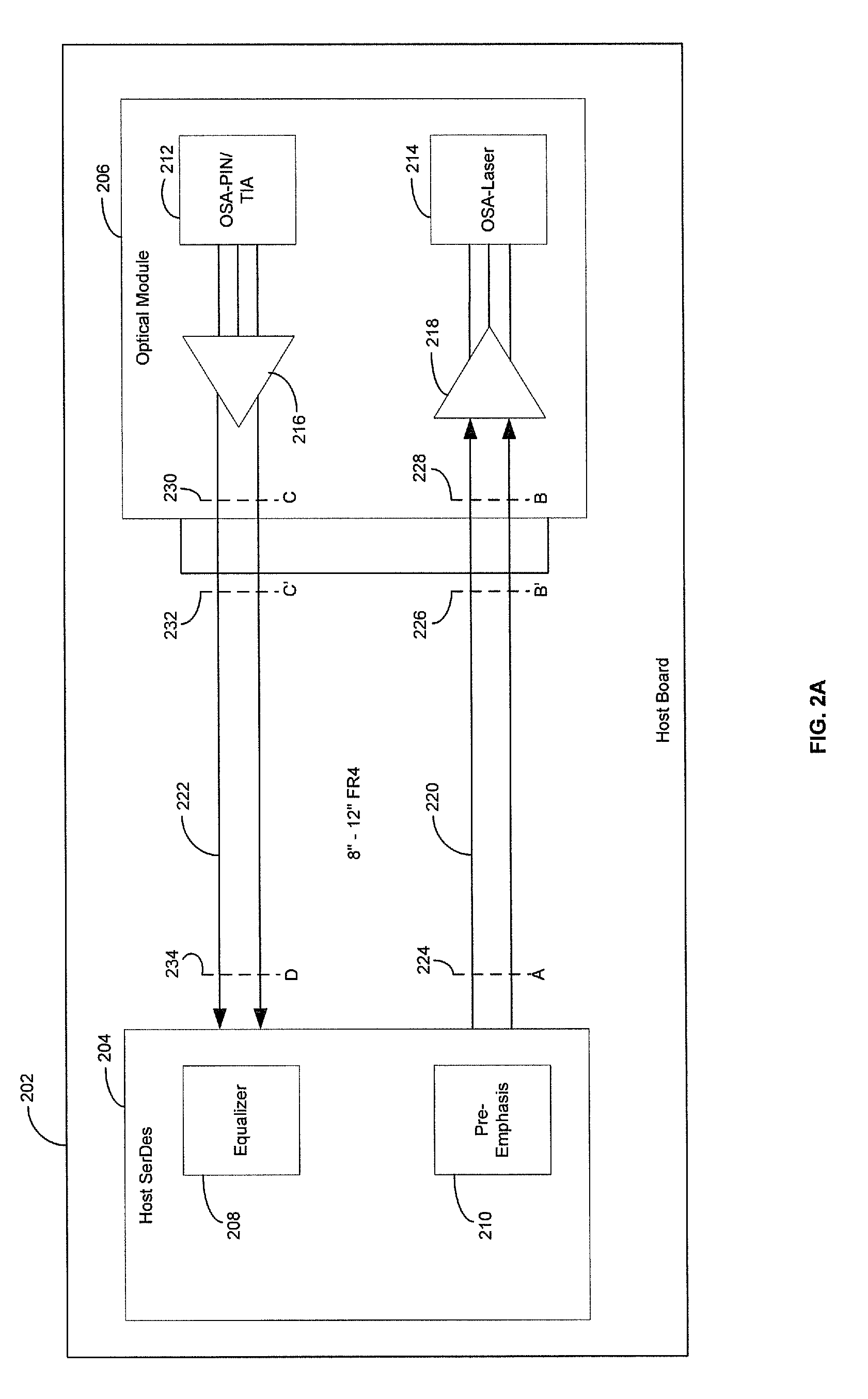
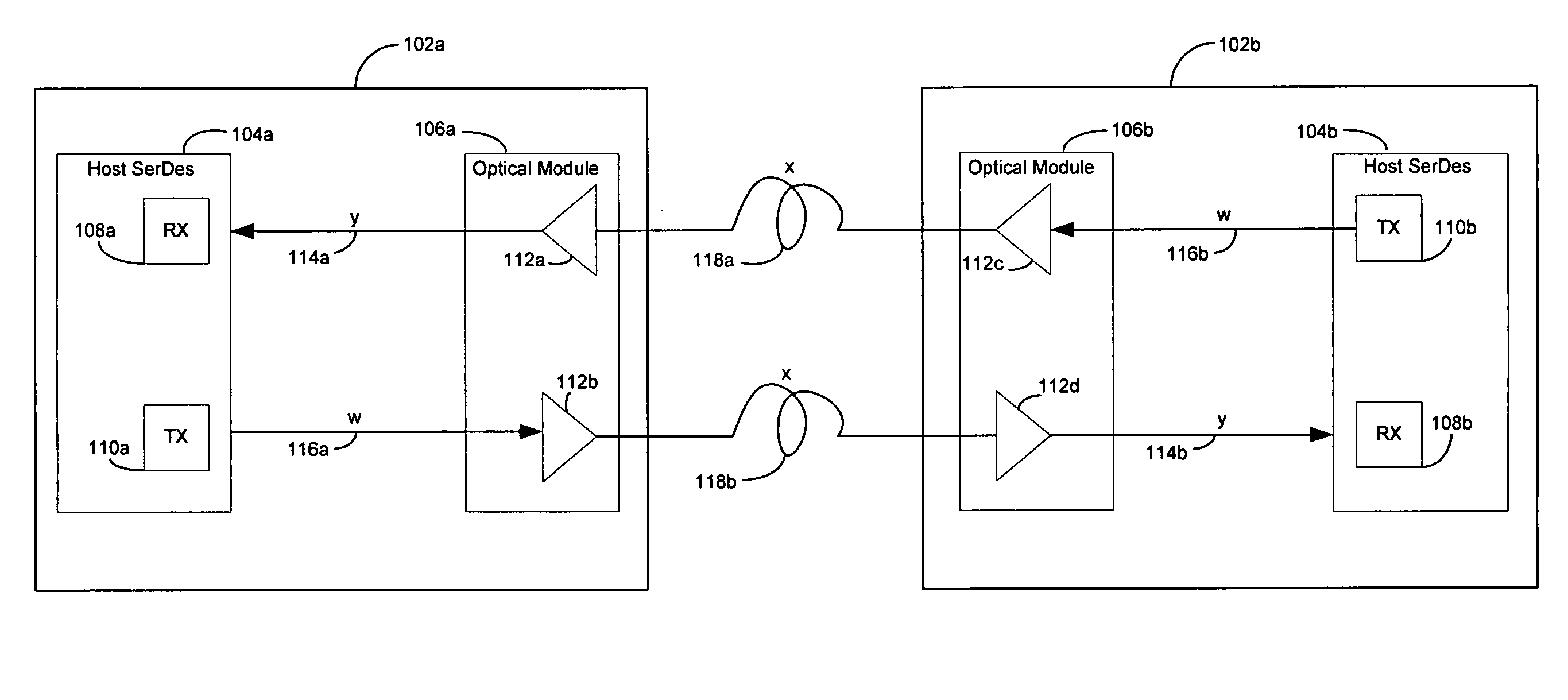
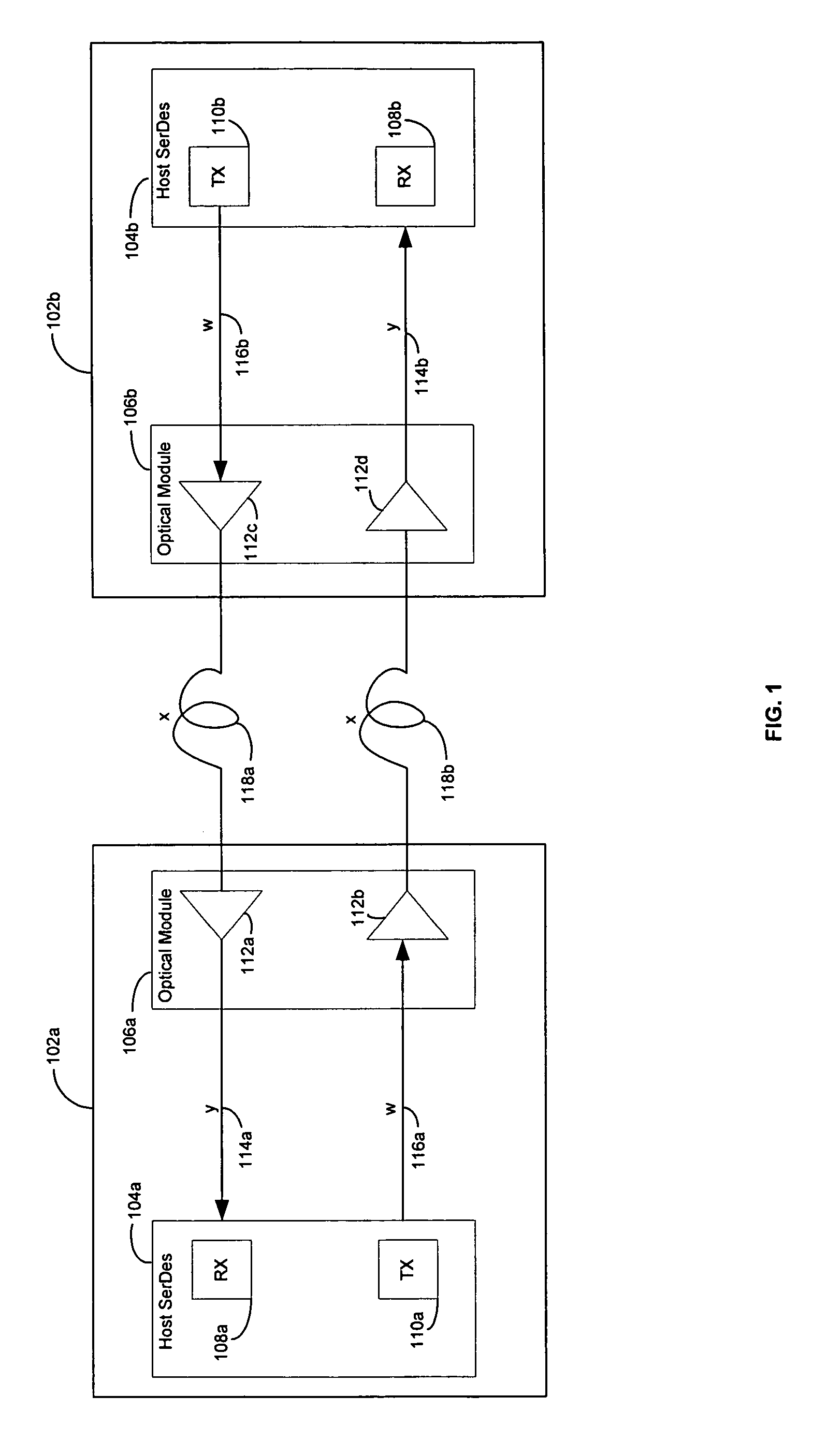
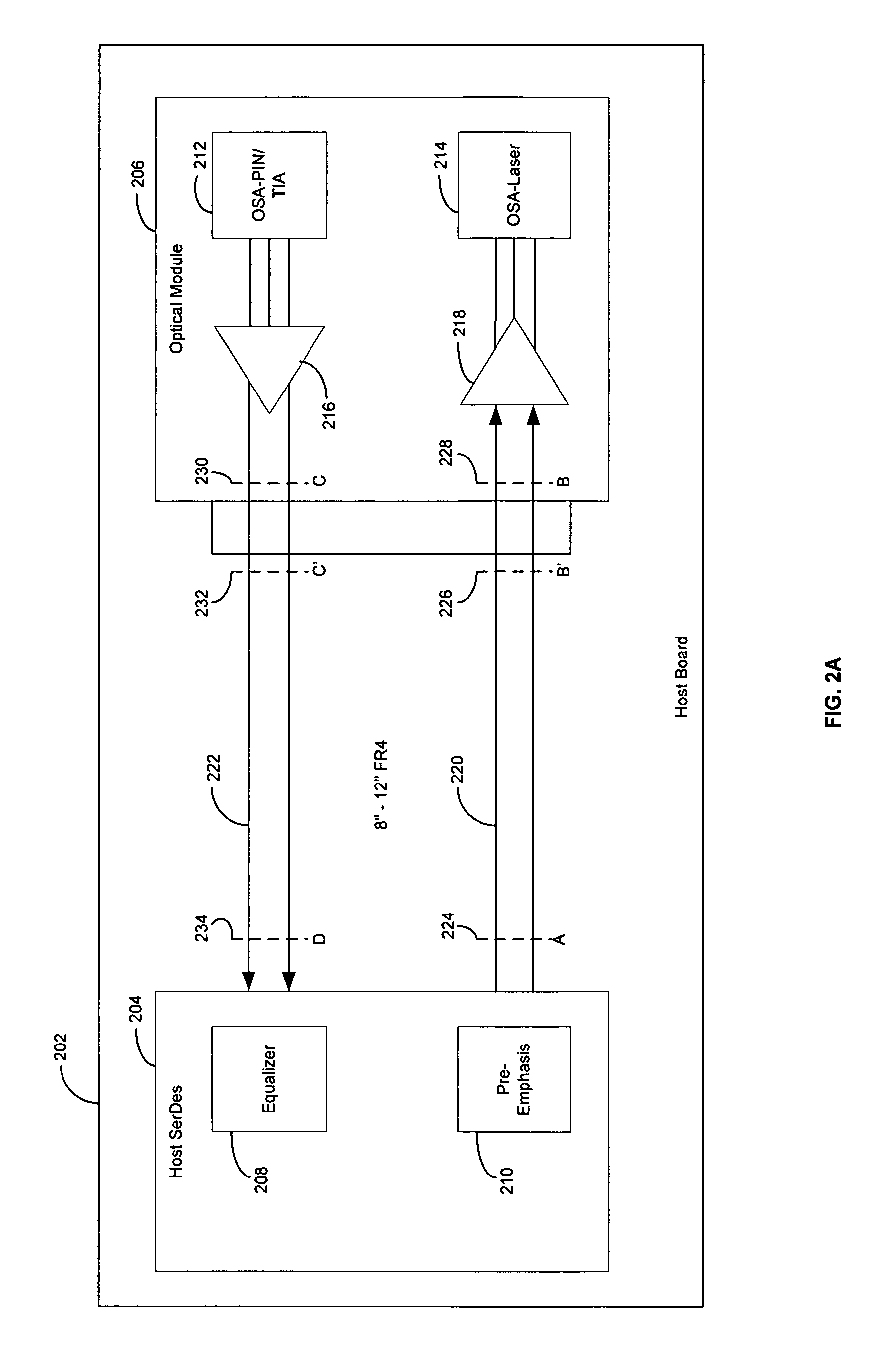
Method and system for optimum channel equalization from a SerDes to an optical module
Certain aspects of a method and system for optimum channel equalization between a host Serializer-Deserializer (SerDes) and an optical module may compensate and reduce dispersion loss along an electrical transmit path of a transmitter and an optical transmit path coupled to the transmitter via pre-emphasis. The data degradation as a result of the dispersion loss along the electrical transmit path of the transmitter and the optical transmit path coupled to the transmitter may be recovered by equalizing signals received via an electrical receive path of a receiver communicatively coupled to the transmitter.
Owner:AVAGO TECH INT SALES PTE LTD
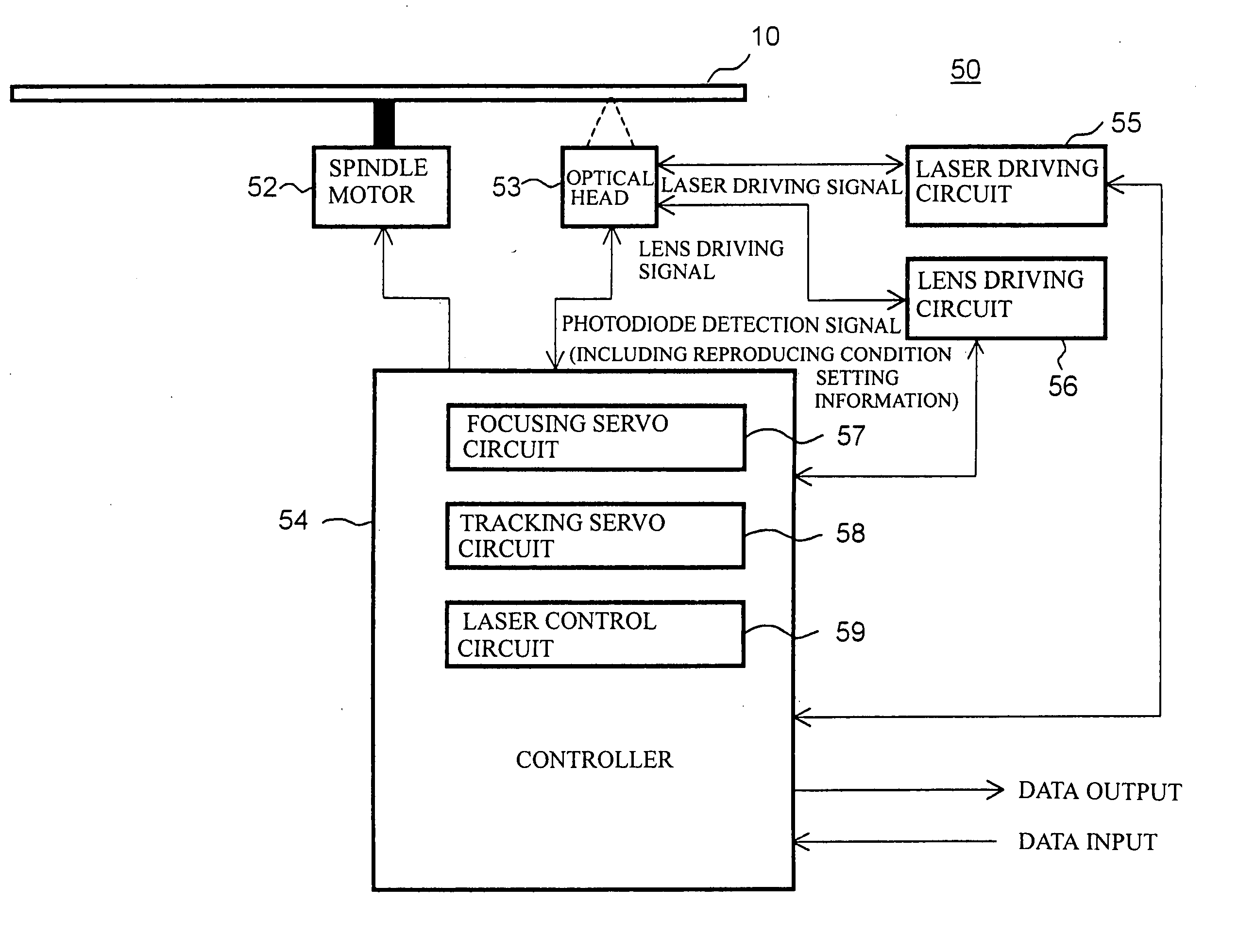
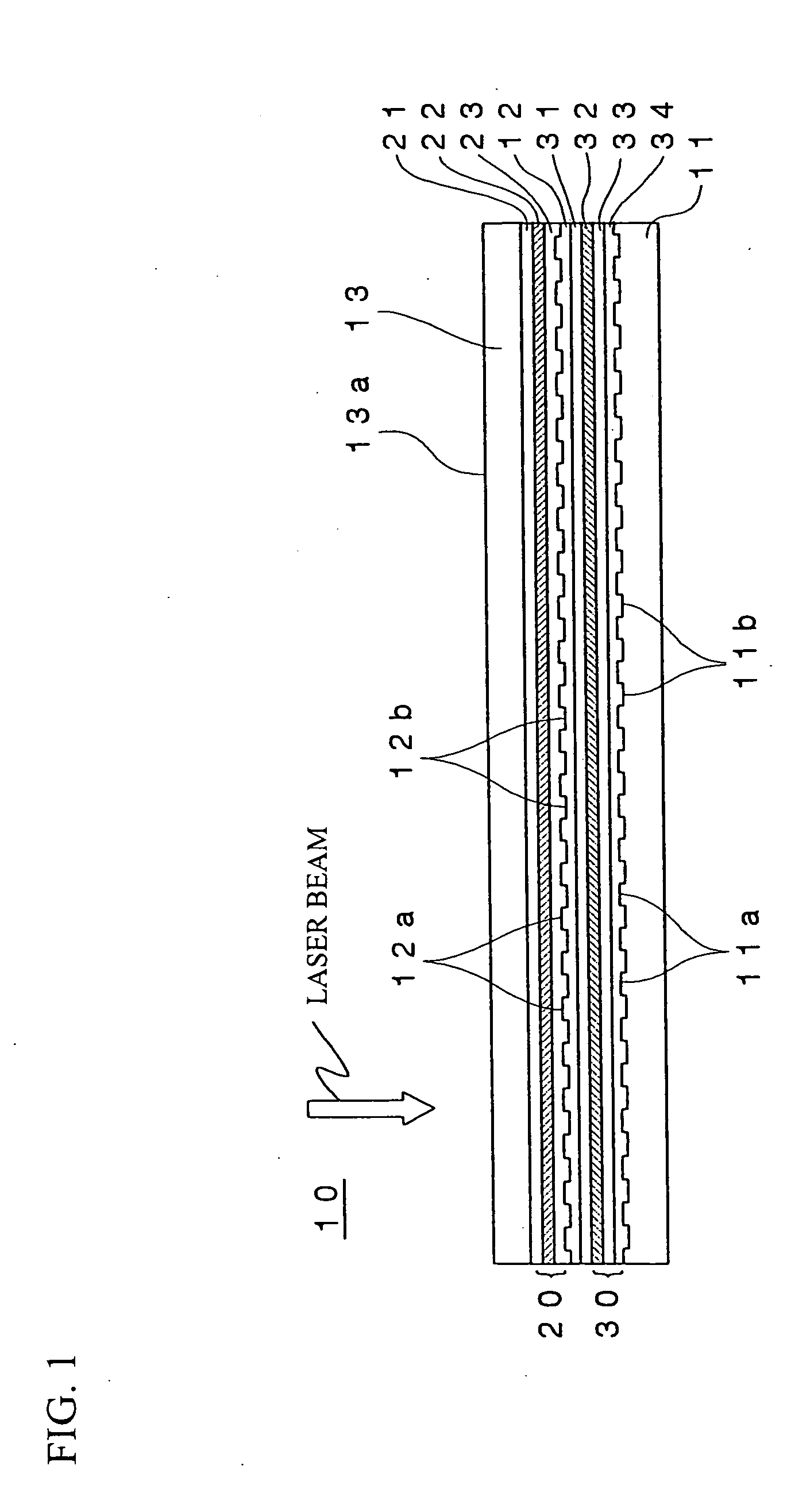
Method for reproducing information from optical recording medium, information reproducer, and optical record medium
InactiveUS20050073935A1Avoid degradationOptical beam sourcesMechanical record carriersOptical recordingLength wave
It is an object of the present invention to provide an information reproducing method for reproducing information from a data rewritable type optical recording medium having a plurality of information recording layers, which can prevent the data degradation phenomenon from occurring. The information reproducing method according to the present invention is directed to reproducing information from an optical recording medium 10 having at least a stacked L0 layer 20 and L1 layer 30 by projecting a laser beam thereonto via a light incidence plane 13a and information is reproduced by setting λ / NA to be equal to or shorter than 700 nm, where A is a wavelength of the laser beam and NA is a numerical aperture (NA) of an objective lens, and setting the laser beam to a reproducing power Pr0 when information recorded in the L0 layer 20 is to be reproduced and a reproducing power Pr1 when information recorded in the L1 layer 30 is to be reproduced.
Owner:TDK CORPARATION
Method and System for Optimum Channel Equalization From a SERDES to an Optical Module
Owner:AVAGO TECH INT SALES PTE LTD
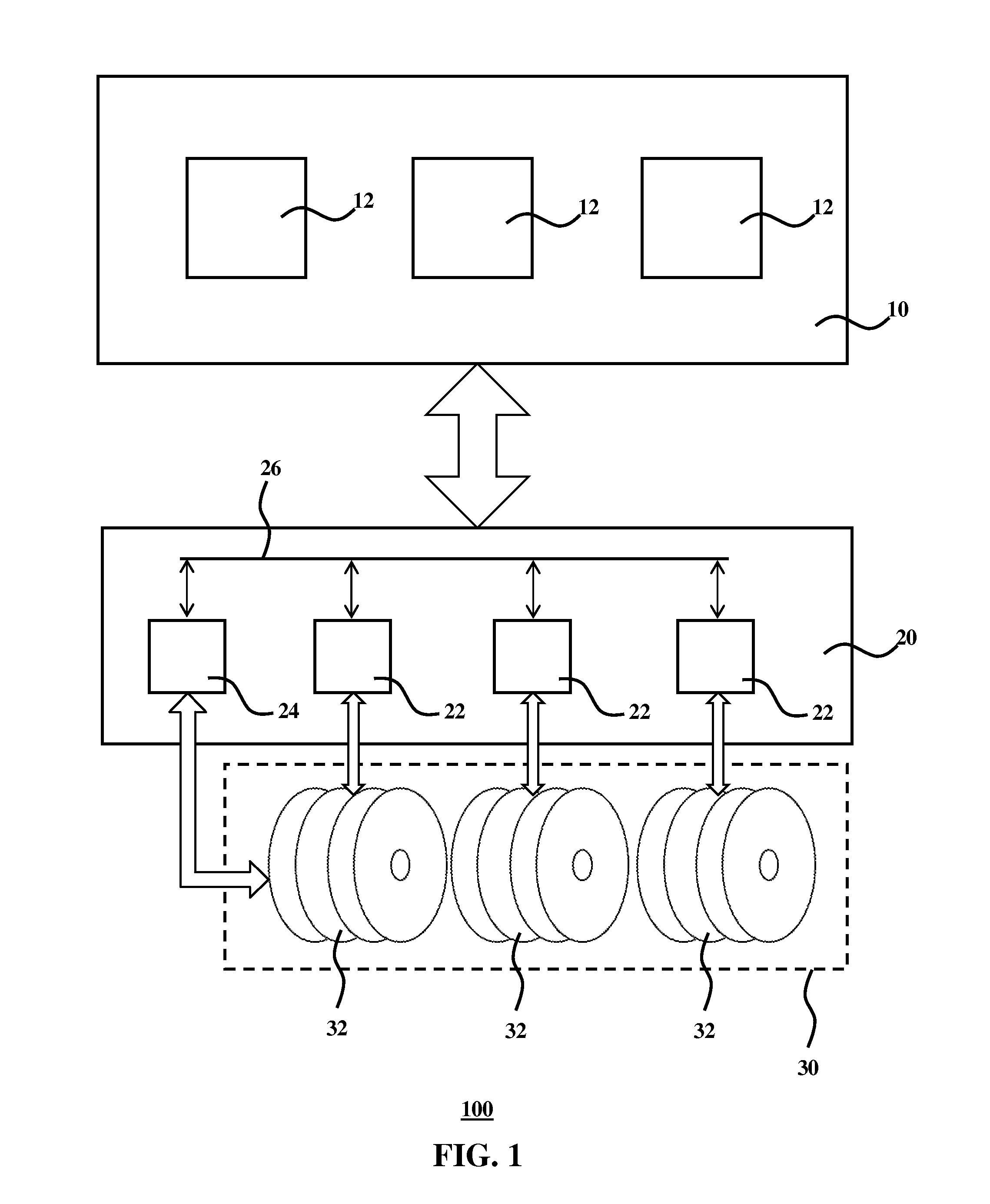
Duel controller system for dynamically allocating control of disk units
InactiveUS20050198457A1Avoid environmentImprove performanceMemory architecture accessing/allocationInput/output to record carriersAutomatic controlChange control
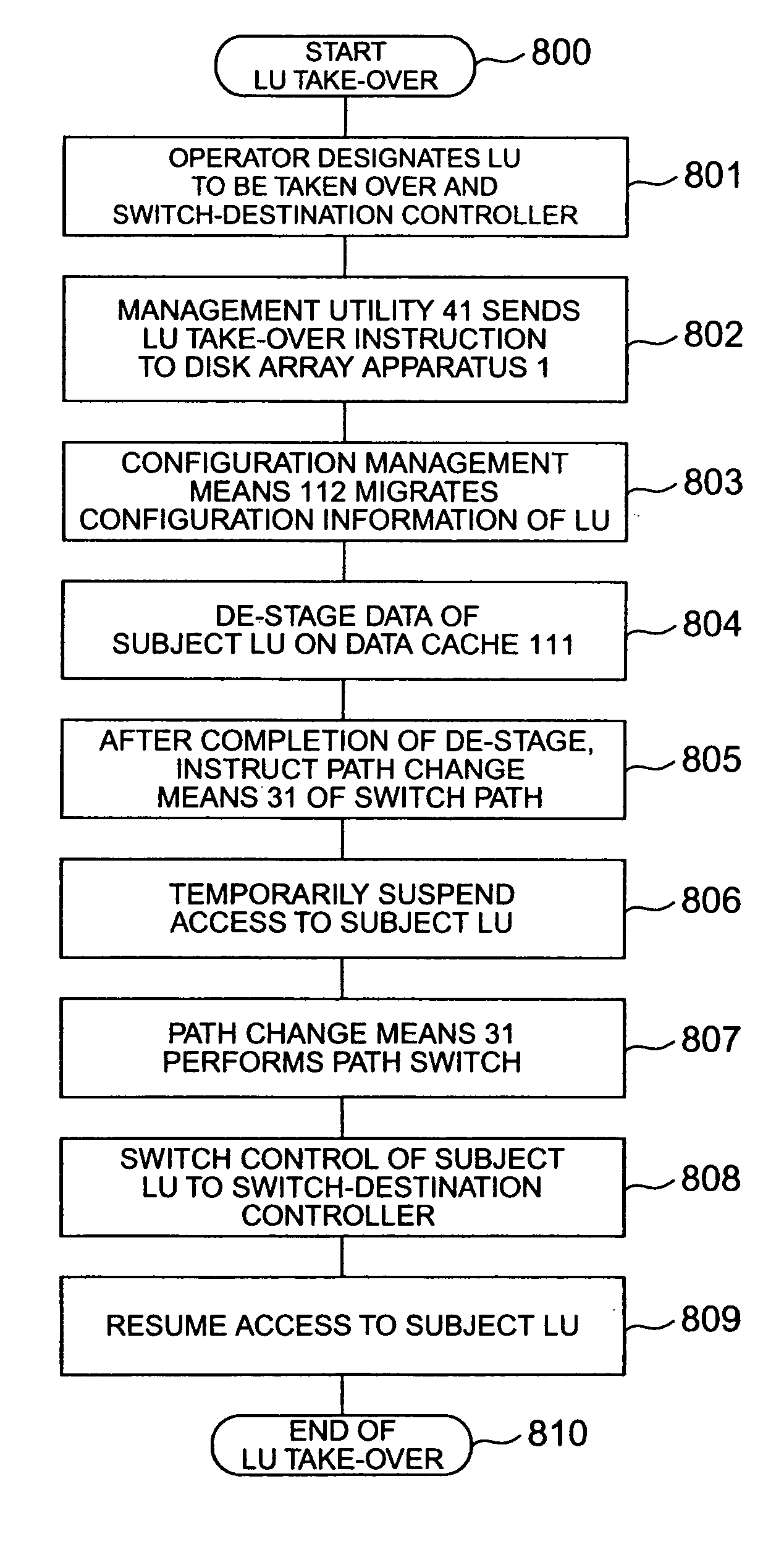
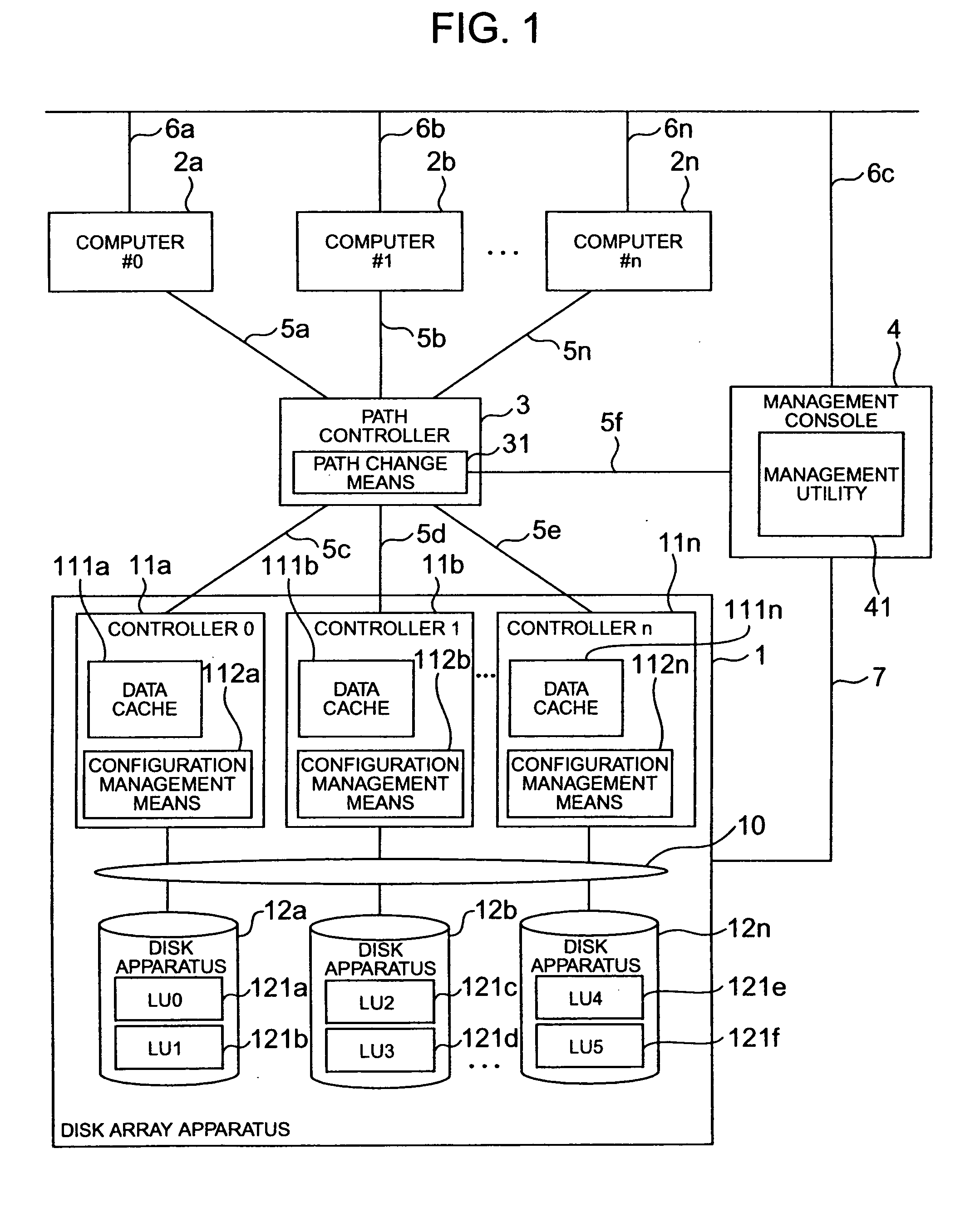
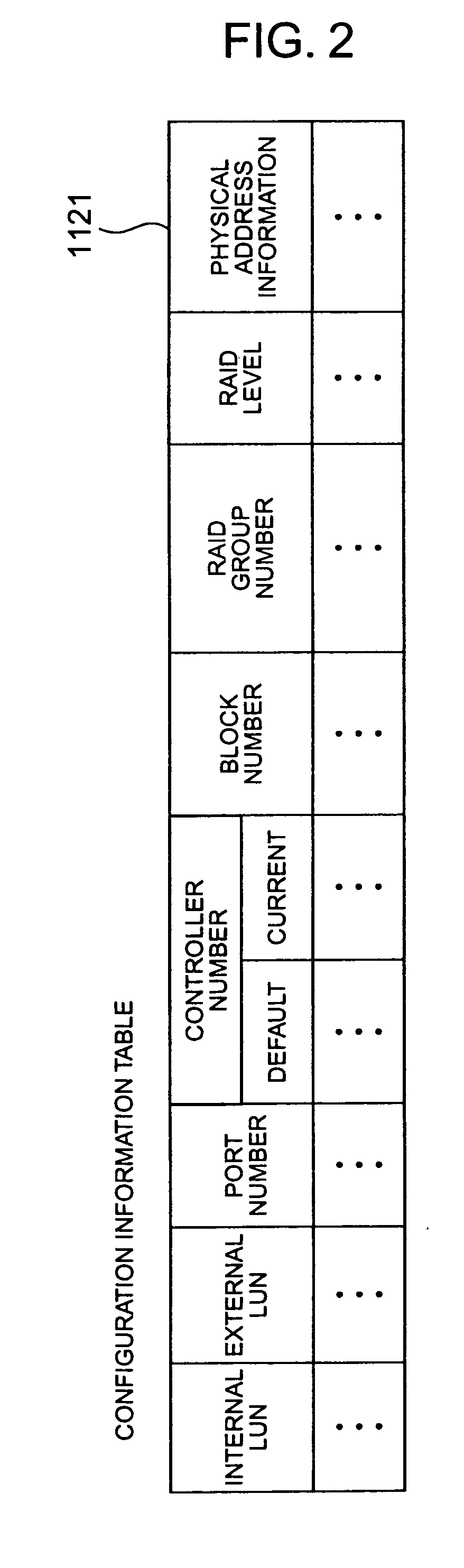
A disk array system of the type that each controller has an independent and dedicated cache. The disk array system can change control of a desired volume between desired controllers without suspending the system. When volumes are taken over between controllers, a switch-source controller de-stages data of a subject volume on the data cache to a storage subject disk to maintain the disk content reflection (coherency). Even if each controller has an independent and dedicated cache, a desired volume can be taken over between desired controllers without suspending the system. Each controller has a configuration manager which stores the controller number of a switch-destination controller to allow automatic volume take-over and automatic control by the original controller.
Owner:HITACHI LTD
Method and system for optimum channel equalization from a SerDes to an optical module
Certain aspects of a method and system for optimum channel equalization between a host Serializer-Deserializer (SerDes) and an optical module may compensate and reduce dispersion loss along an electrical transmit path of a transmitter and an optical transmit path coupled to the transmitter via pre-emphasis. The data degradation as a result of the dispersion loss along the electrical transmit path of the transmitter and the optical transmit path coupled to the transmitter may be recovered by equalizing signals received via an electrical receive path of a receiver communicatively coupled to the transmitter.
Owner:AVAGO TECH INT SALES PTE LTD
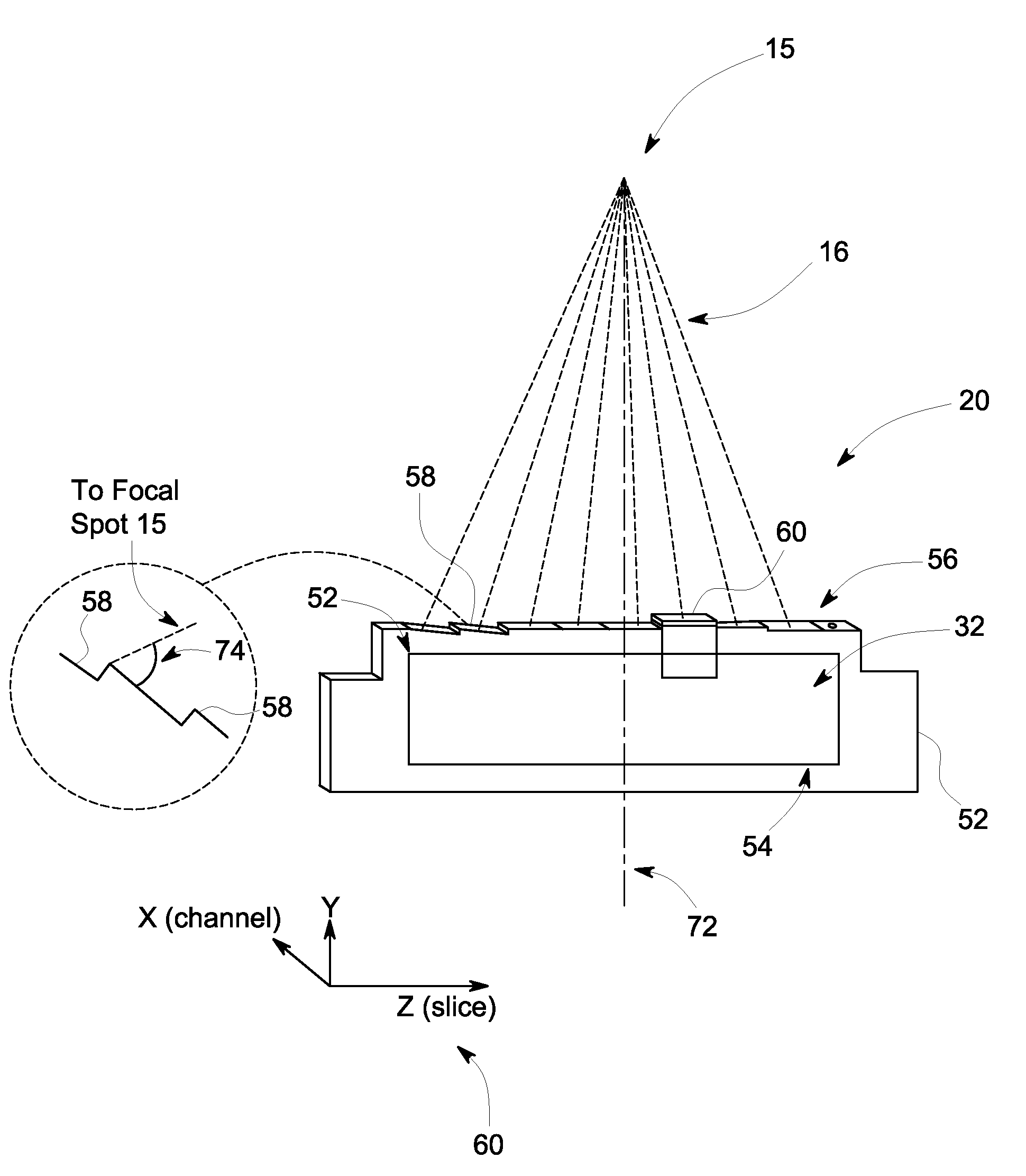
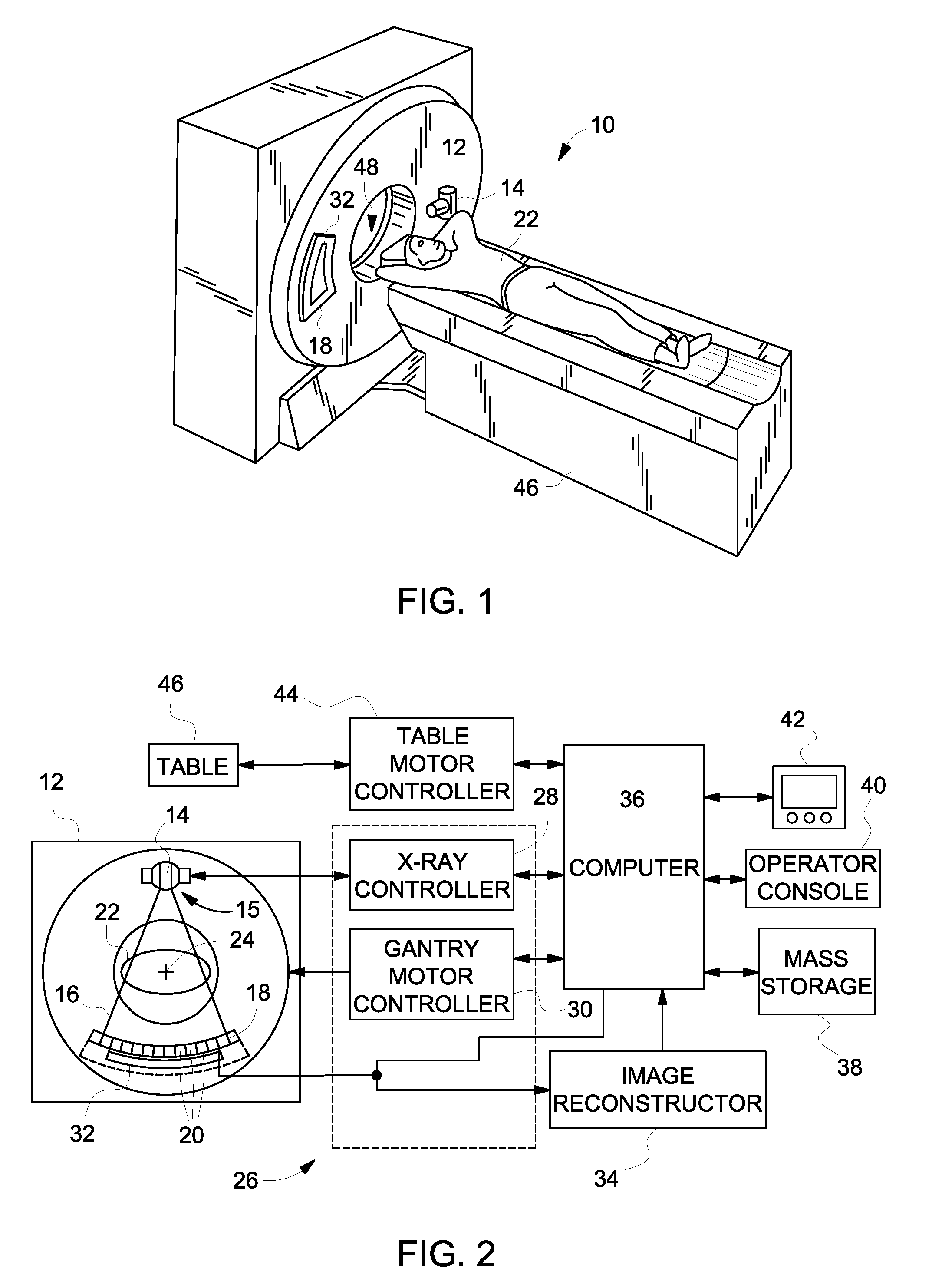
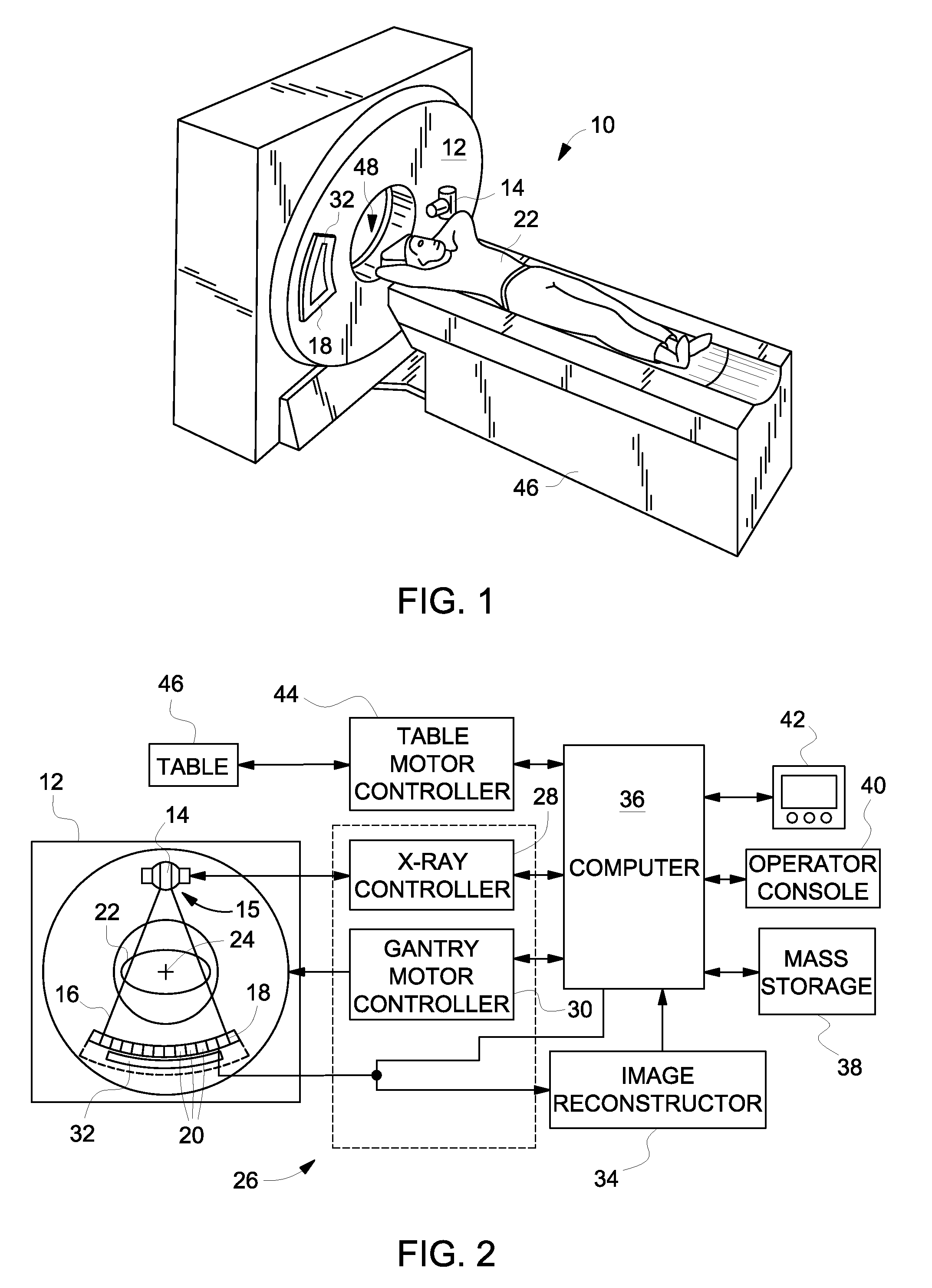
Multi-faceted tileable detector for volumetric computed tomography imaging
ActiveUS8204171B2Improve acquisitionReduce image dataMaterial analysis using wave/particle radiationRadiation/particle handlingX-rayTomography
A system and method for CT image acquisition with increased slice acquisition and minimal image data degradation is provided. The system includes an x-ray projection source positioned that projects a cone beam of x-rays from a focal spot of the x-ray projection source toward an object and a plurality of detector modules positioned on the rotatable gantry to receive x-rays attenuated by the object. Each of the detector modules includes a module frame having a top surface that includes a plurality of facets formed thereon constructed so as to be oriented at differing angles relative to the focal spot and a plurality of sub-modules positioned on the plurality of facets to receive the x-rays attenuated by the object and to convert the x-rays to electrical signals, with each sub-module being oriented at an angle relative to the focal spot based on a respective facet on which the sub-module is mounted.
Owner:GENERAL ELECTRIC CO
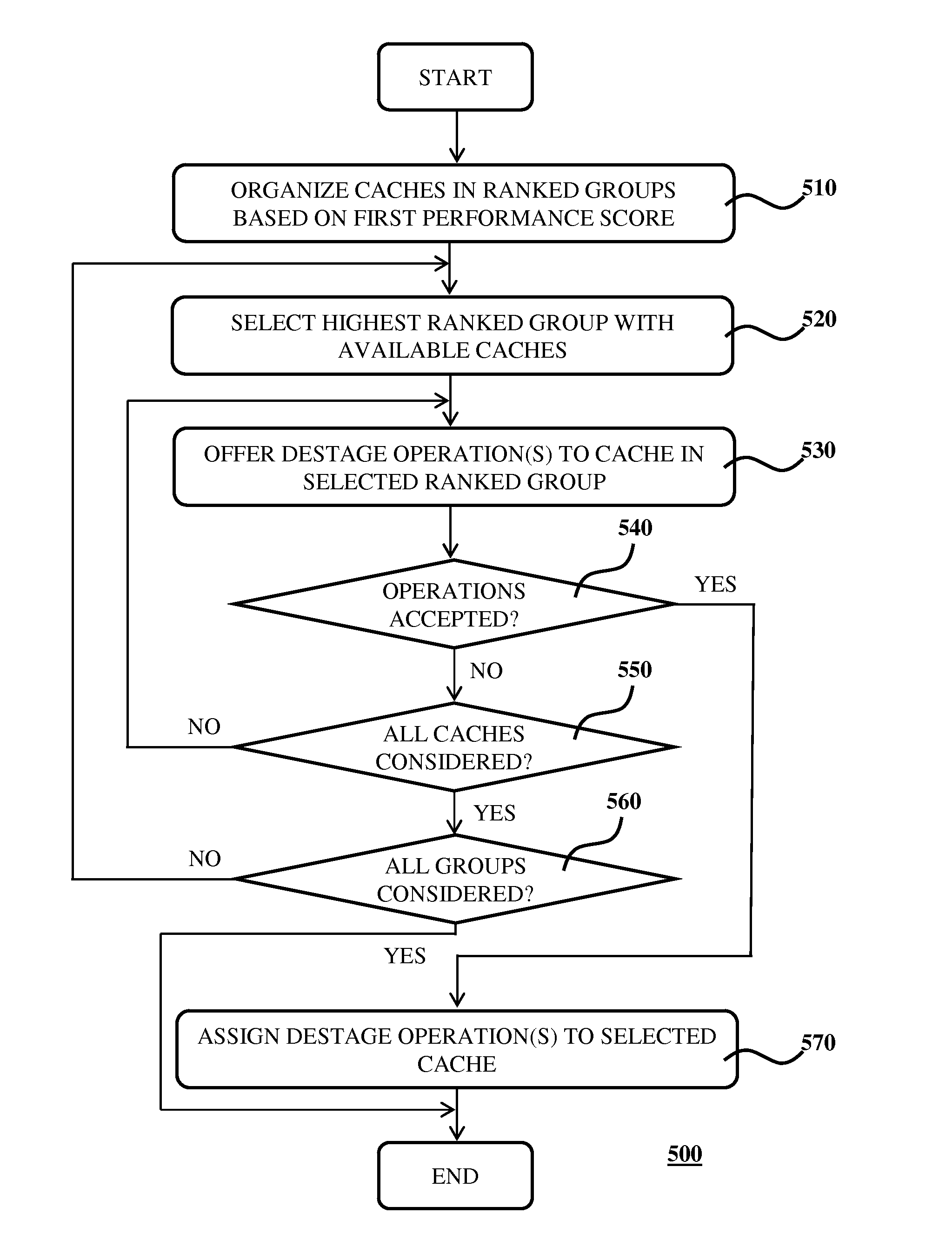
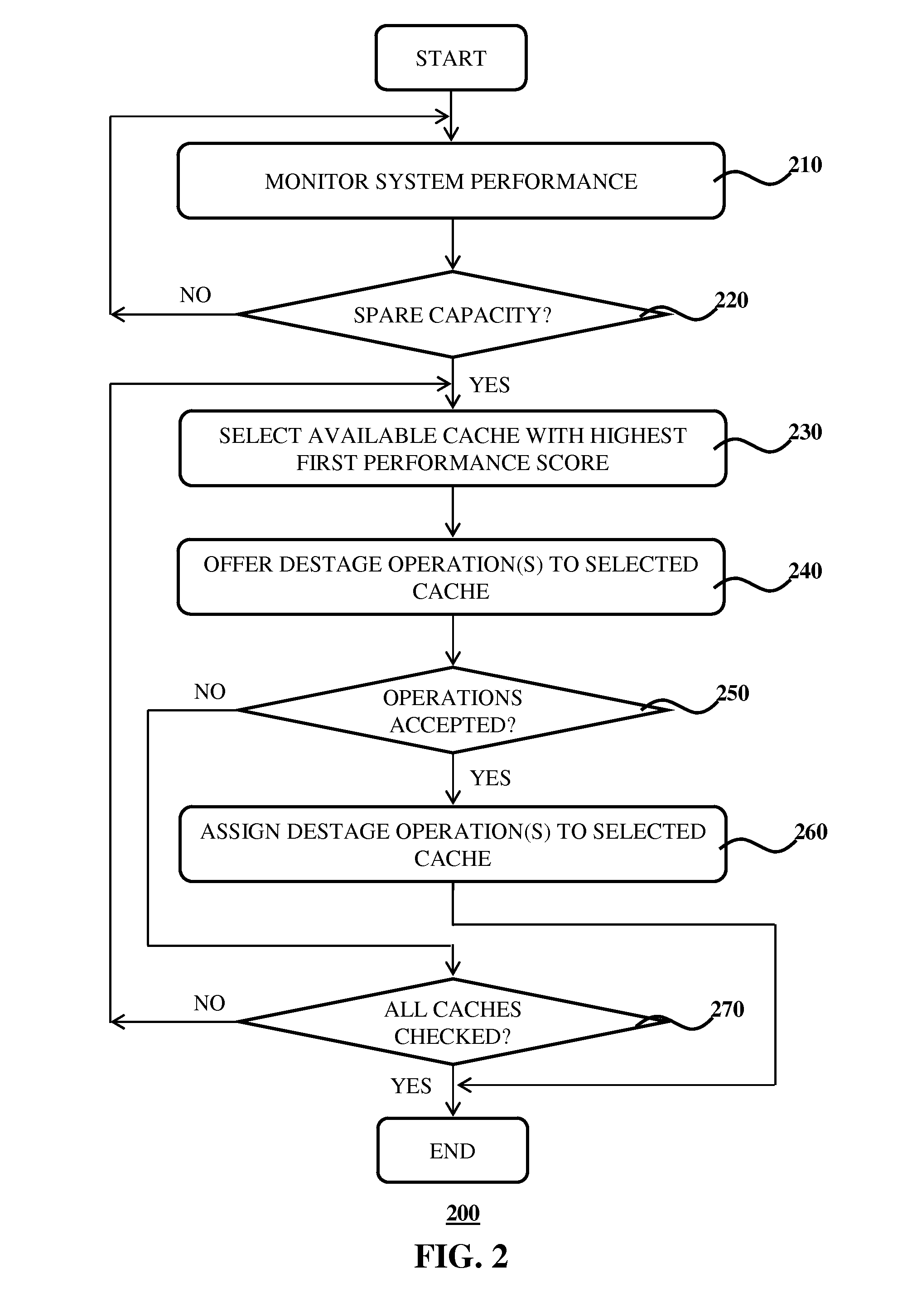
Write Cache Destaging
InactiveUS20150121008A1Memory architecture accessing/allocationMemory adressing/allocation/relocationData degradationData store
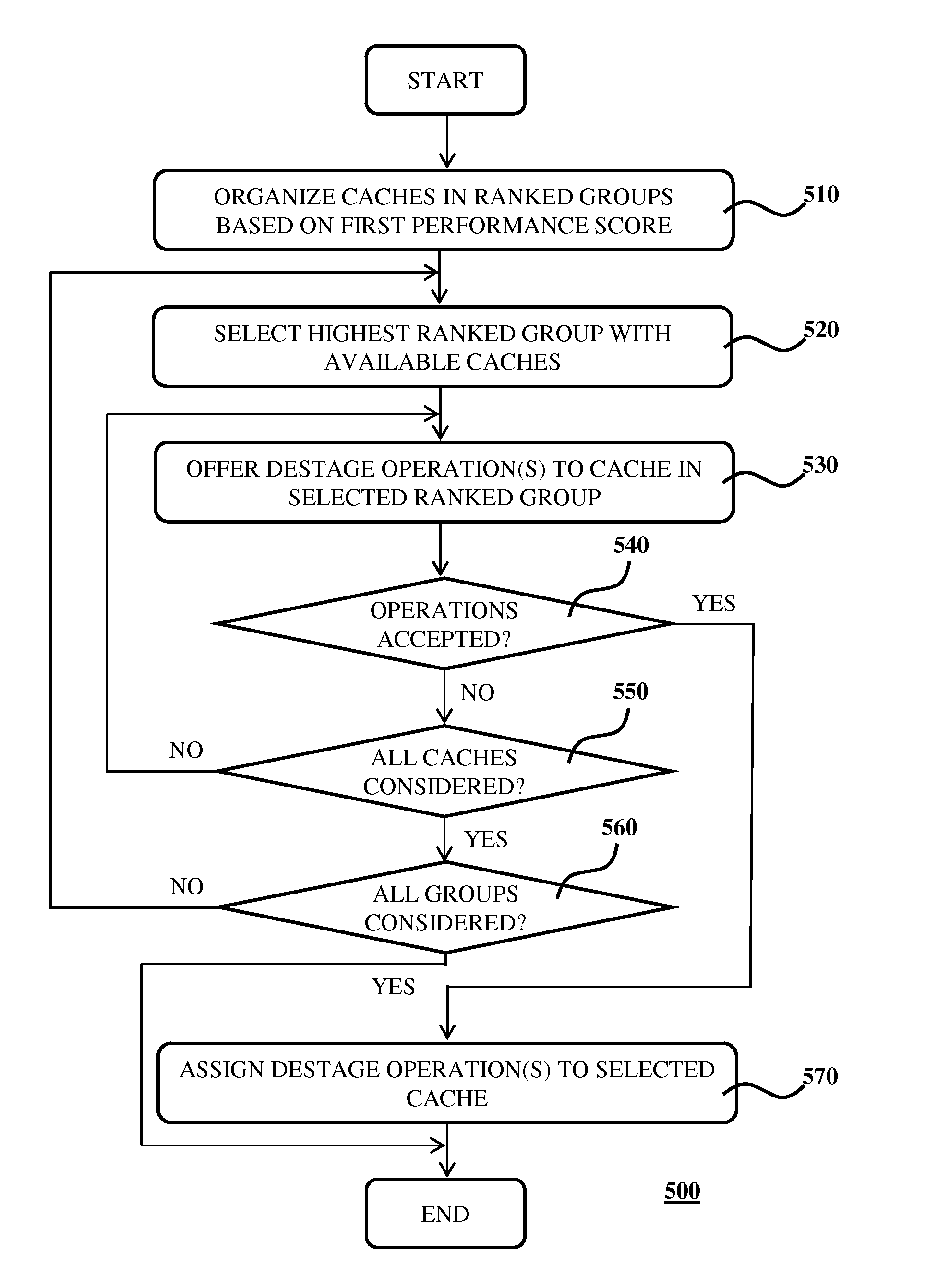
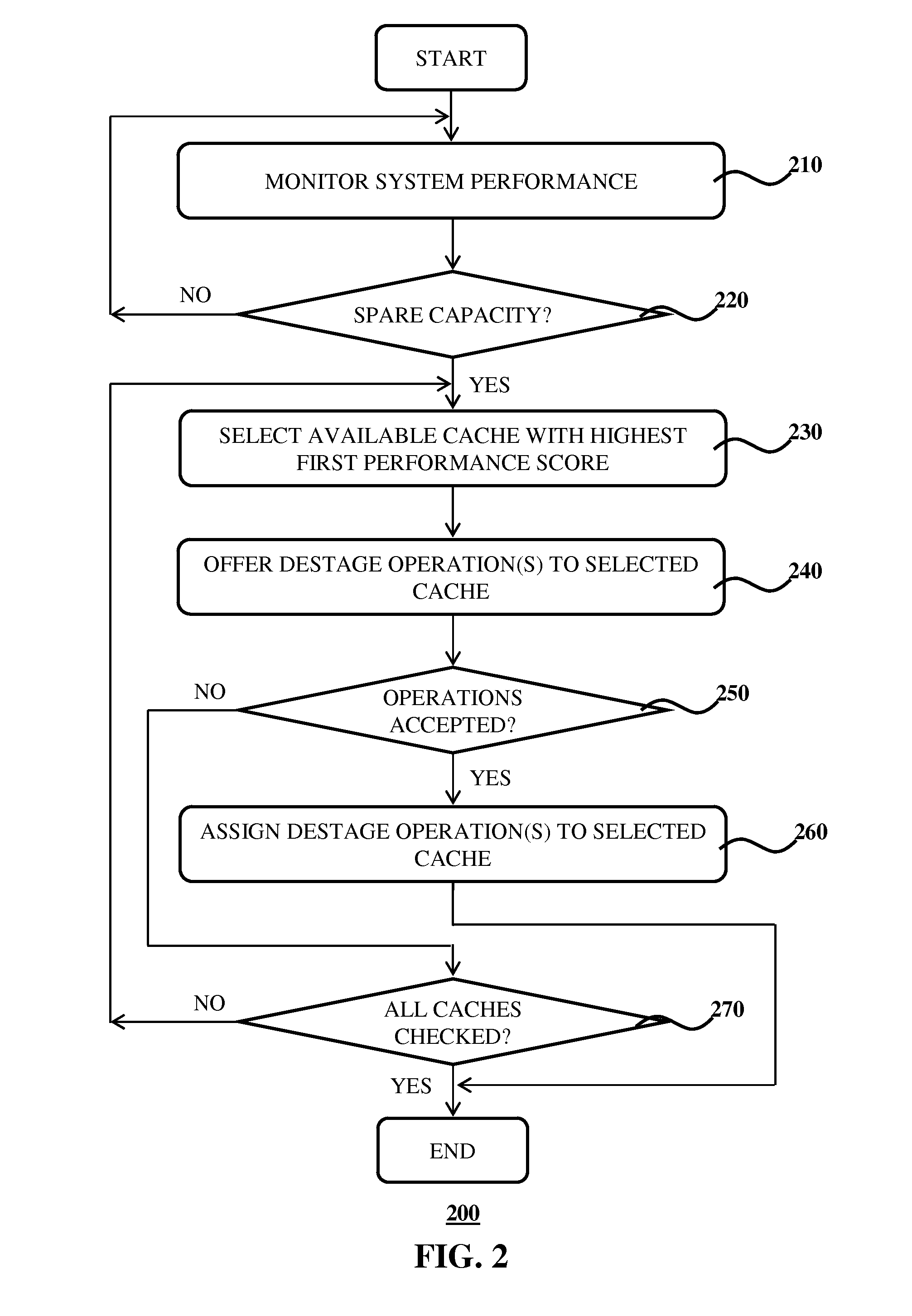
Disclosed is a system for controlling write actions to a plurality of data storage devices, the system comprising a plurality of write caches, wherein each cache is associated with a set of said data storage devices; and a controller adapted to issue write permissions to said data storage devices, said write permissions including a permission to perform a data destage operation from a cache to a data storage device; wherein each cache has a first performance score expressed as the difference between the number of data destage operations said cache has in flight and the maximum number of data destage actions said cache is permitted to issue in parallel; and wherein the controller is adapted to offer a data destage operation permission to the cache in said plurality of caches associated with the highest first performance score.
Owner:GLOBALFOUNDRIES INC
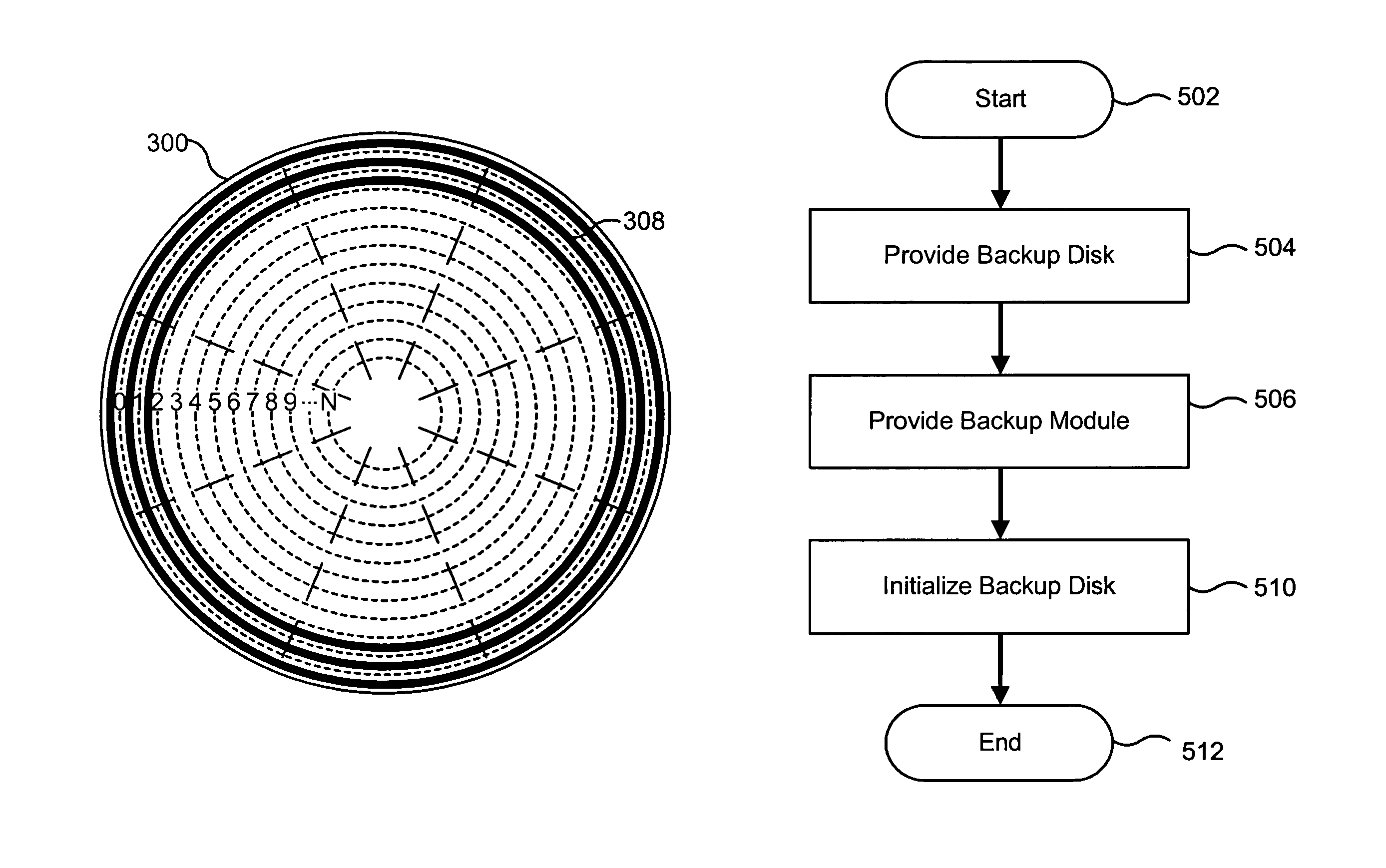
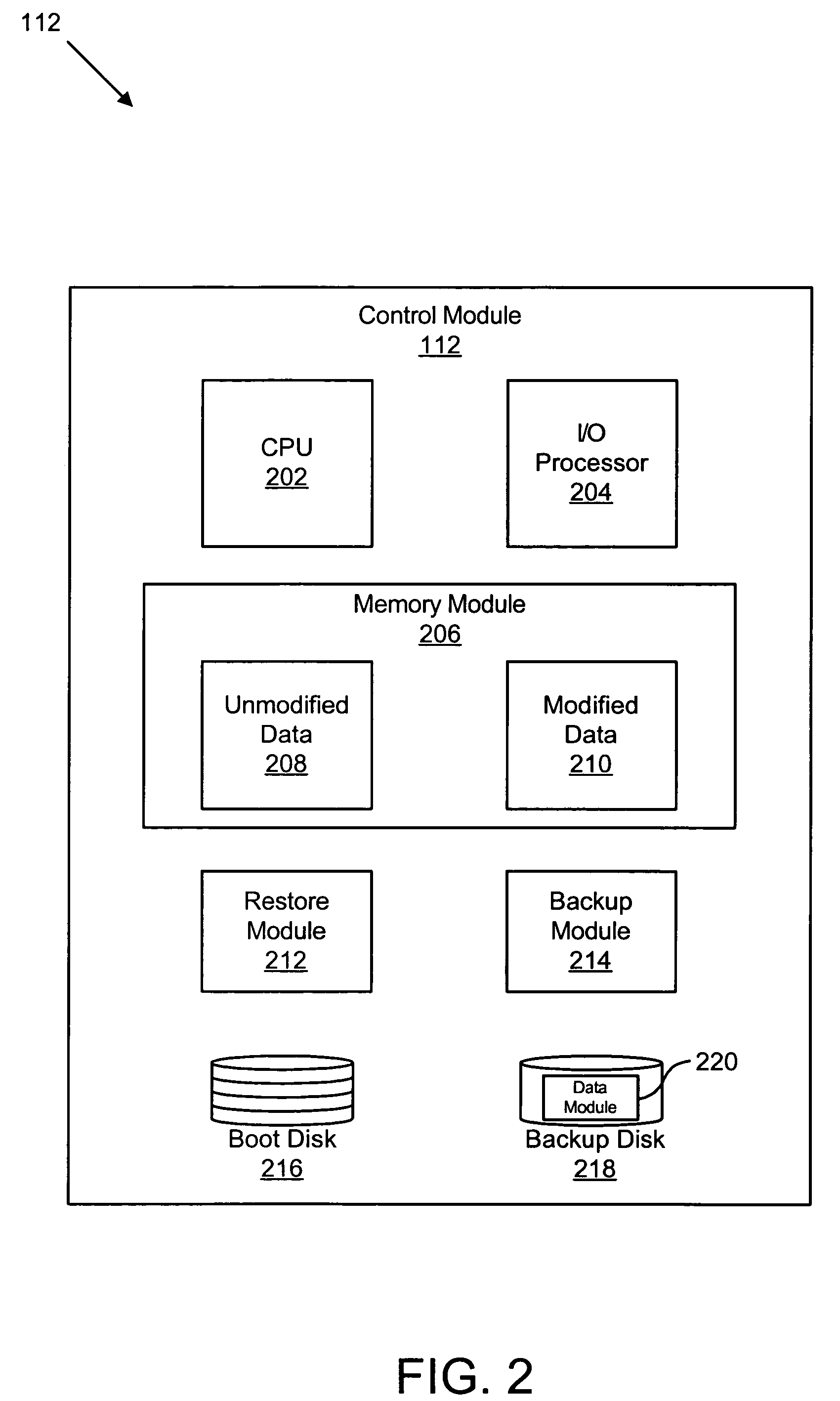
Apparatus, system, and method for emergency backup
An apparatus, system, and method quickly backs up data in an emergency situation and reduces battery backup dependence. The apparatus may include a backup module and a dedicated computer readable storage device. The backup module interfaces with system memory and selectively transmits modified data to the storage device in response to a detected system failure. The dedicated storage device stores the modified data around the outer edge of a hard disk in order to increase write performance. The system may include the backup module, the storage device, a plurality of client devices, and a plurality of storage devices. The method includes storing modified and unmodified data, detecting a system failure, and transmitting modified data stored in a memory module to a dedicated computer readable backup device. Upon rebooting the device, the method may include restoring the modified data to the system memory and destaging the modified data to the plurality of storage devices.
Owner:AIRBNB
Writer having a shield structure for adjacent and far track interference refreshment
Owner:WESTERN DIGITAL TECH INC
Write cache destaging
InactiveUS9524244B2Memory architecture accessing/allocationInput/output to record carriersData degradationData store
Disclosed is a system for controlling write actions to a plurality of data storage devices, the system comprising a plurality of write caches, wherein each cache is associated with a set of said data storage devices; and a controller adapted to issue write permissions to said data storage devices, said write permissions including a permission to perform a data destage operation from a cache to a data storage device; wherein each cache has a first performance score expressed as the difference between the number of data destage operations said cache has in flight and the maximum number of data destage actions said cache is permitted to issue in parallel; and wherein the controller is adapted to offer a data destage operation permission to the cache in said plurality of caches associated with the highest first performance score.
Owner:GLOBALFOUNDRIES INC
Dynamic cache resize taking into account underlying raid characteristics
InactiveUS20200183838A1Memory architecture accessing/allocationMemory systemsRAIDComputer architecture
A method for resizing write cache in a storage system is disclosed. In one embodiment, such a method includes maintaining, in a write cache, write data to be destaged to RAID arrays implemented on persistent storage drives. The method dynamically resizes the write cache in a way that takes into account the following: (1) an amount of battery power available to destage the write data to the persistent storage drives in the event of an emergency; and (2) underlying characteristics of the RAID arrays to which the write data is to be destaged. A corresponding system and computer program product are also disclosed.
Owner:IBM CORP
Data loss prevention method of a media storage device and media storage device
ActiveUS20070041118A1Accurate detectionSmall recording areaRecord information storageCarrier monitoringComputer hardwareData loss
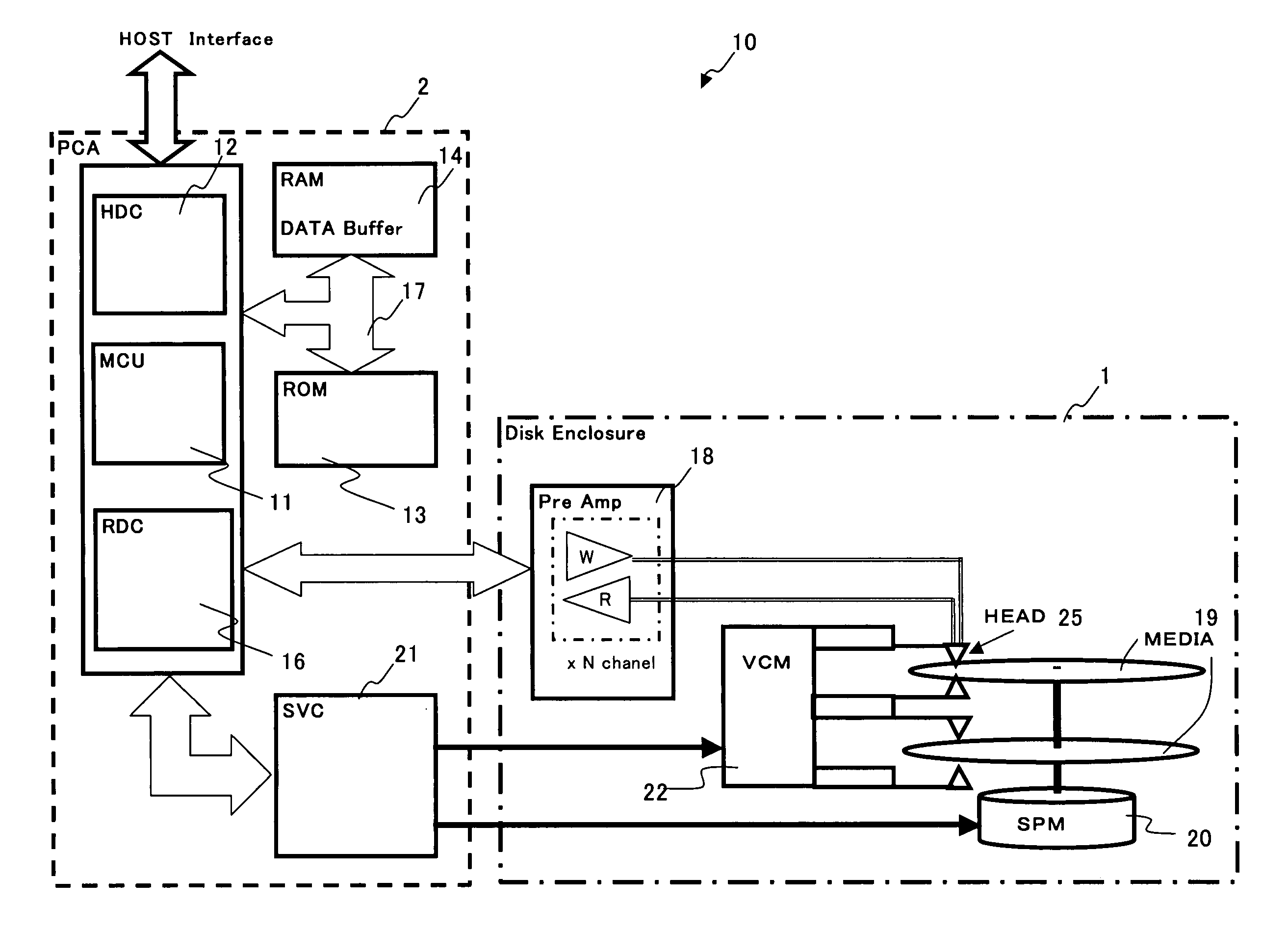
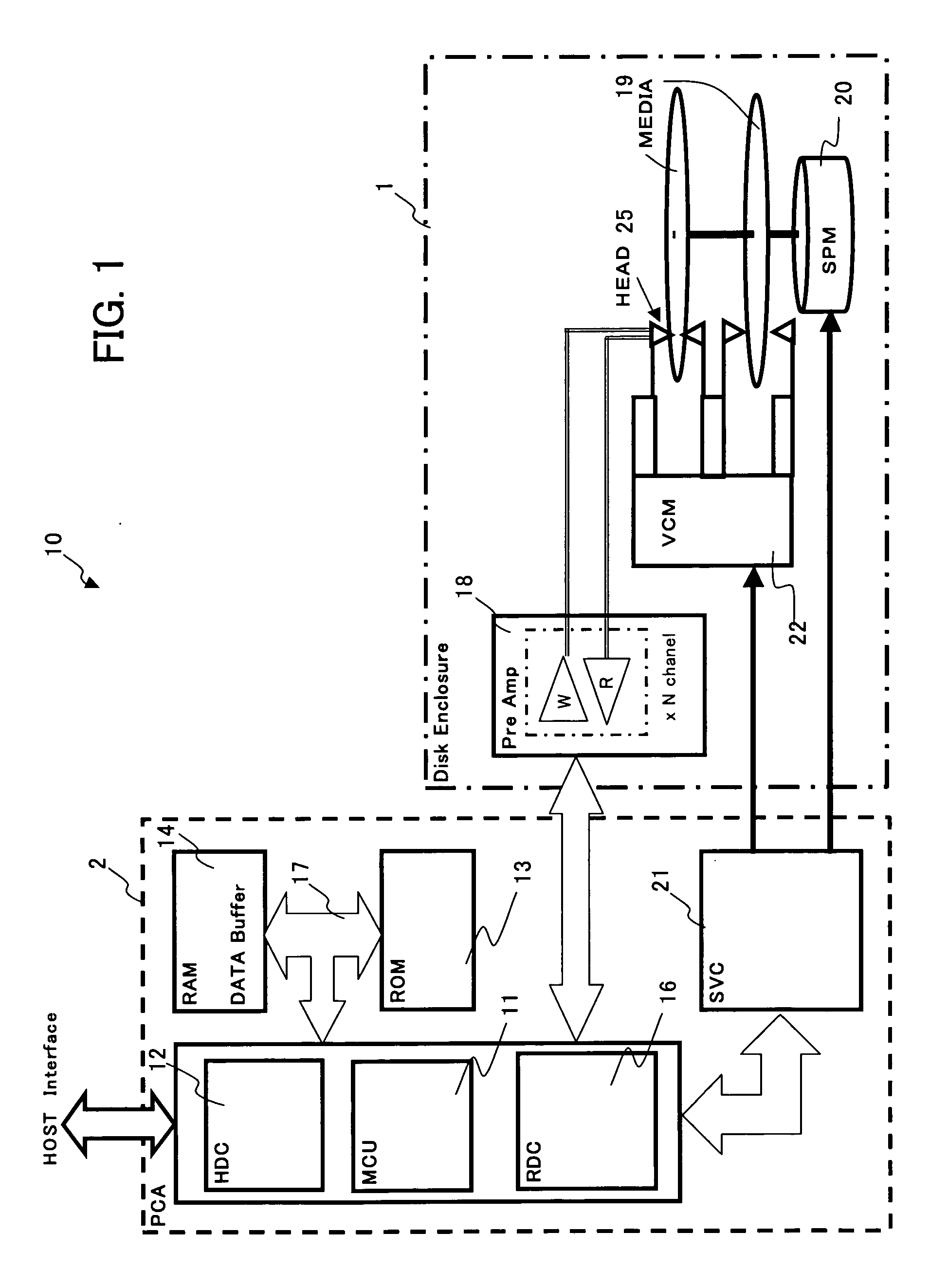
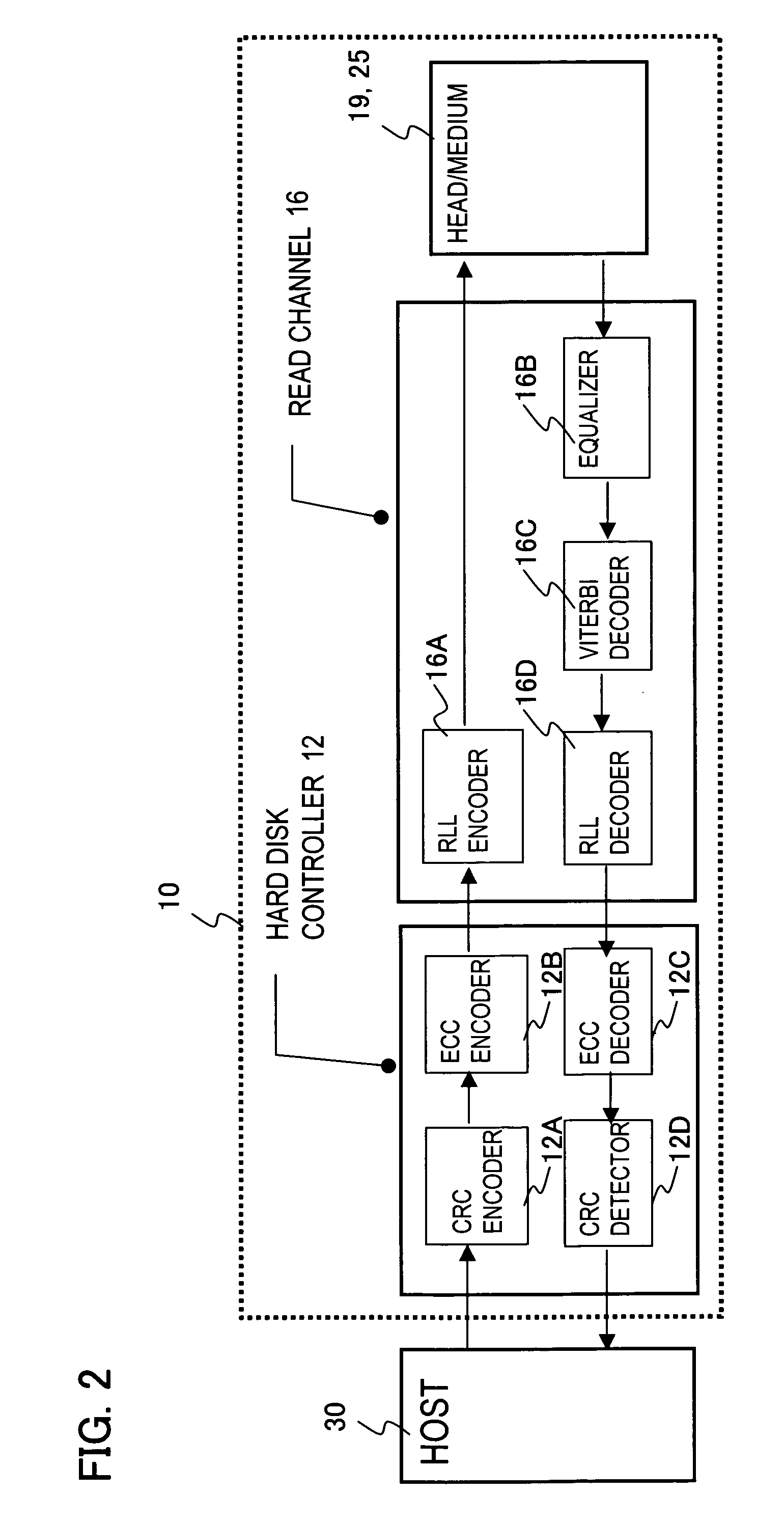
A media storage device reads and writes data from and to a storage medium using a head and prevents in advance data loss due to thermal relaxation of data recorded on the storage medium. Table stores information which is related to a read error detected by a channel circuit in record units. The channel circuit measures information which is related to a read error and updates the information in the table. Further, data degradation is judged by this information which is related to the read error. Degradation of recorded data due to thermal relaxation can be detected accurately, and data loss can be prevented.
Owner:KK TOSHIBA
Multi-faceted tileable detector for volumetric computed tomography imaging
ActiveUS20120087465A1Improve acquisitionReduce image dataMaterial analysis using wave/particle radiationRadiation/particle handlingX-rayTomography
A system and method for CT image acquisition with increased slice acquisition and minimal image data degradation is provided. The system includes an x-ray projection source positioned that projects a cone beam of x-rays from a focal spot of the x-ray projection source toward an object and a plurality of detector modules positioned on the rotatable gantry to receive x-rays attenuated by the object. Each of the detector modules includes a module frame having a top surface that includes a plurality of facets formed thereon constructed so as to be oriented at differing angles relative to the focal spot and a plurality of sub-modules positioned on the plurality of facets to receive the x-rays attenuated by the object and to convert the x-rays to electrical signals, with each sub-module being oriented at an angle relative to the focal spot based on a respective facet on which the sub-module is mounted.
Owner:GENERAL ELECTRIC CO
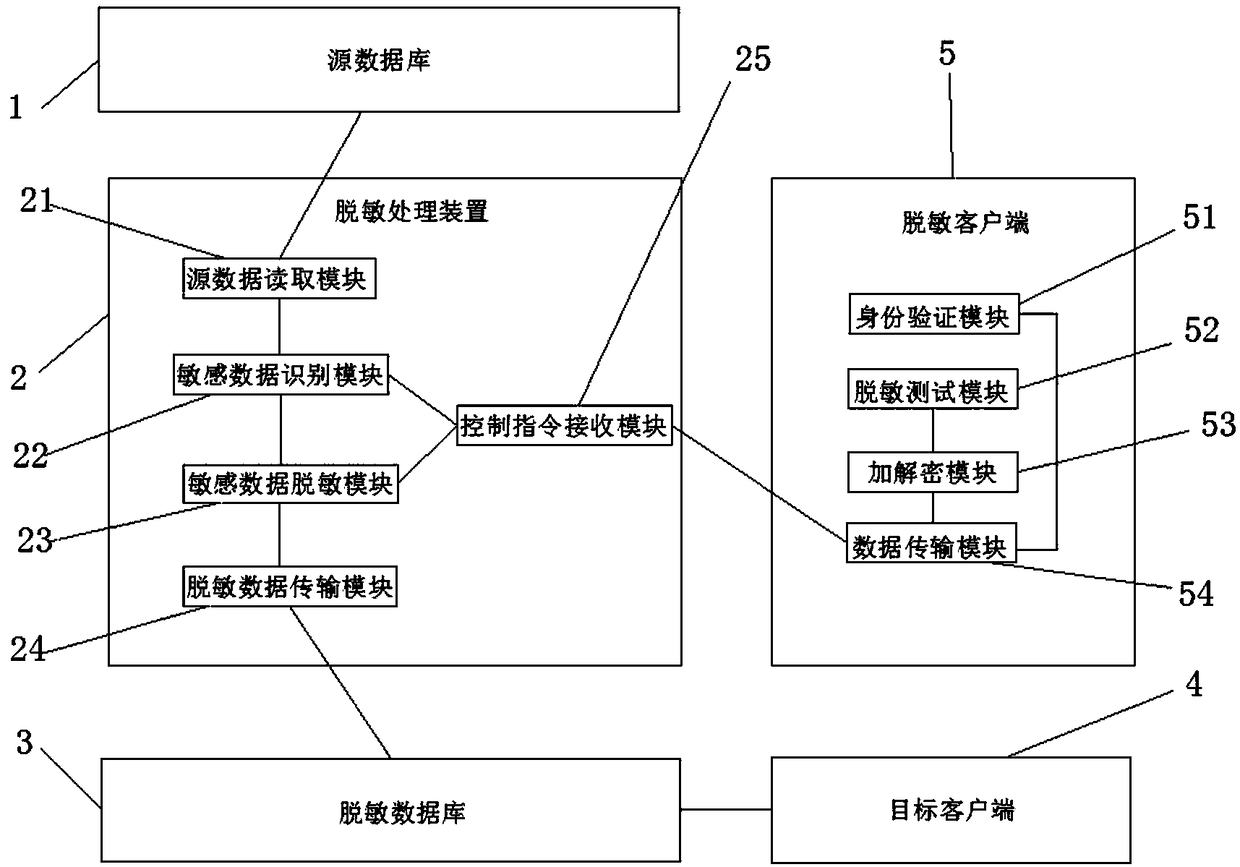
Data desensitization system
InactiveCN109190404AAvoid obstructionImprove reliabilityDigital data protectionData degradationComputer science
A data desensitization system includes a source database, a desensitization processing device, a desensitization database, a desensitization client and a target client, the source database is connected with the desensitization processing device for storing and supplying source data, the desensitization processing device is connected with the desensitization database for acquiring source data for data desensitization to generate desensitization data, the desensitization database is connected with the target client for storing the desensitization data, the target client for reading the desensitization data for use in the target environment, and the desensitization client is connected with the desensitization processing device for sending a control instruction to the desensitization processing device for modifying the desensitization method and the sensitive data standard. The invention can modify the desensitization method and the sensitive data standard in time through the desensitization client, thereby preventing the desensitization method and the sensitive data standard from leaking the sensitive data due to the poor desensitization effect caused by the improper setting or hindering the service due to the data degradation caused by the desensitization.
Owner:安徽云图信息技术有限公司
Digital data reproducing device
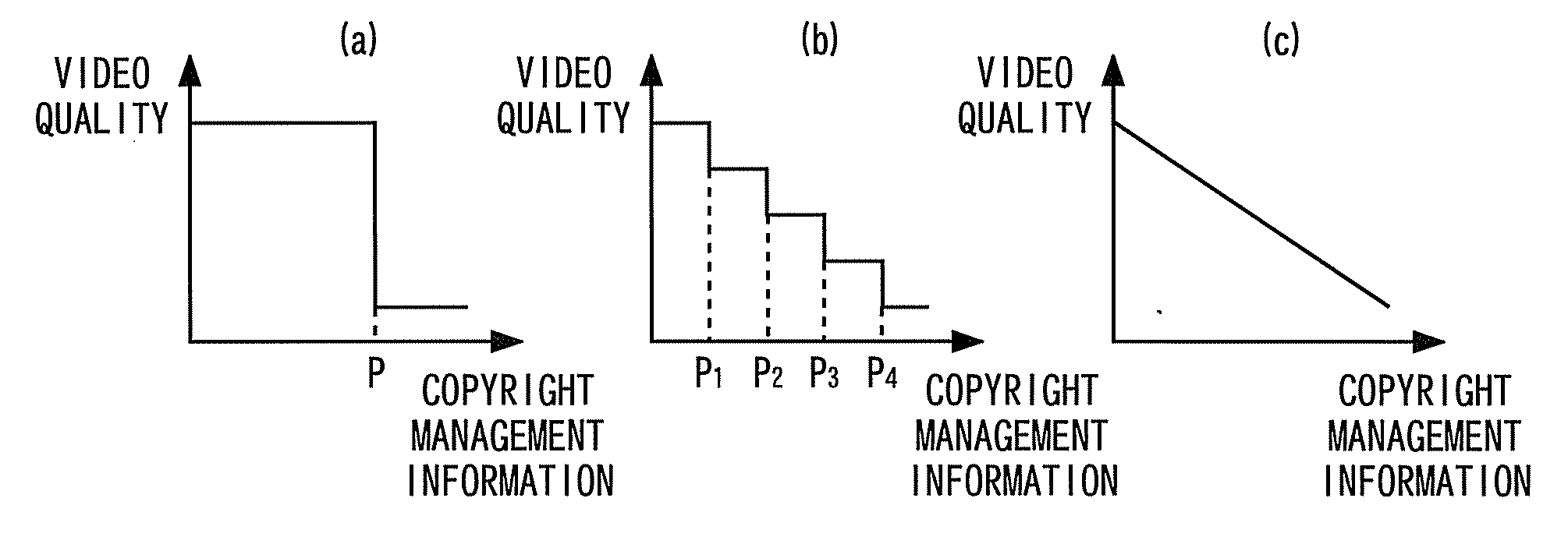
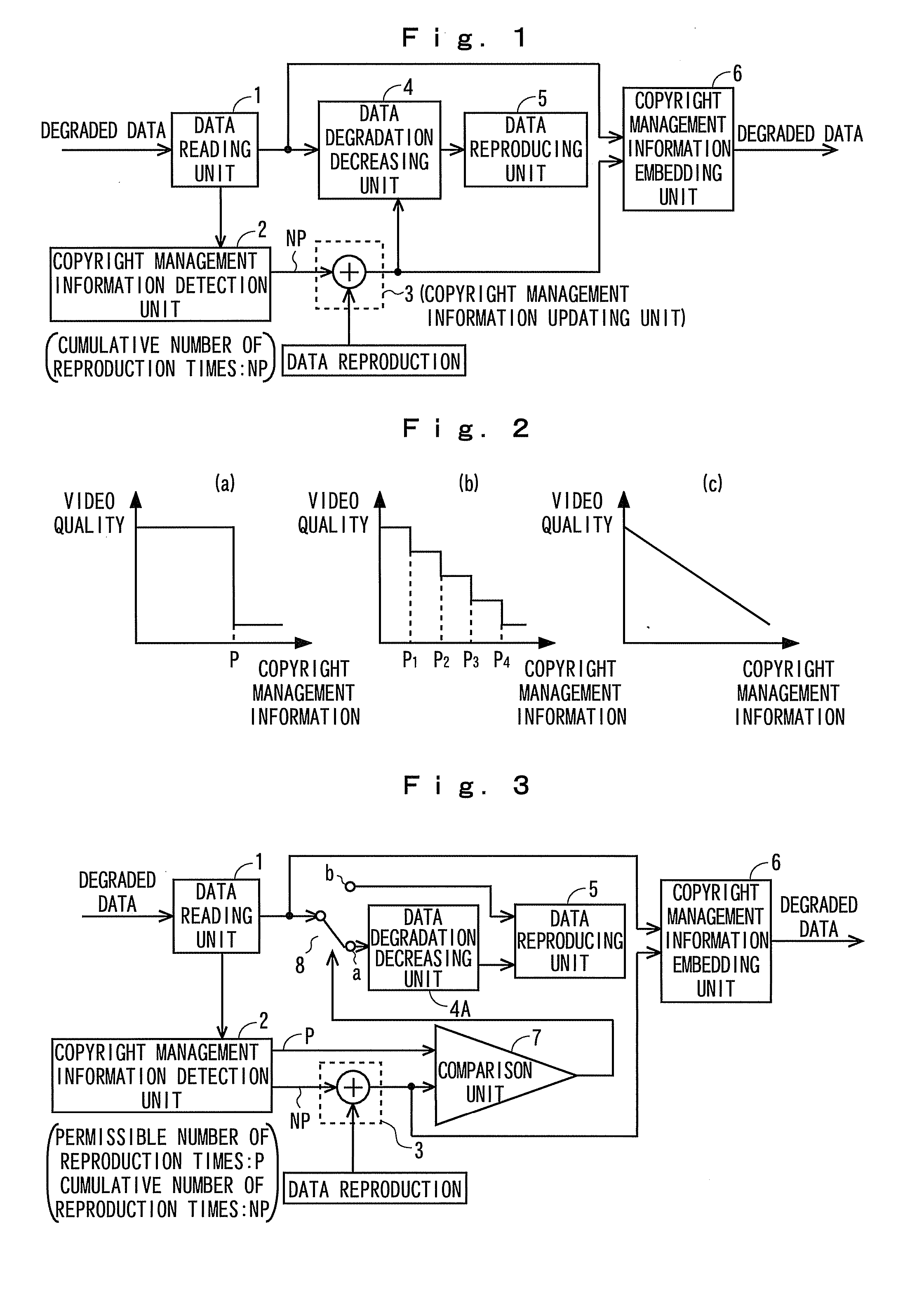
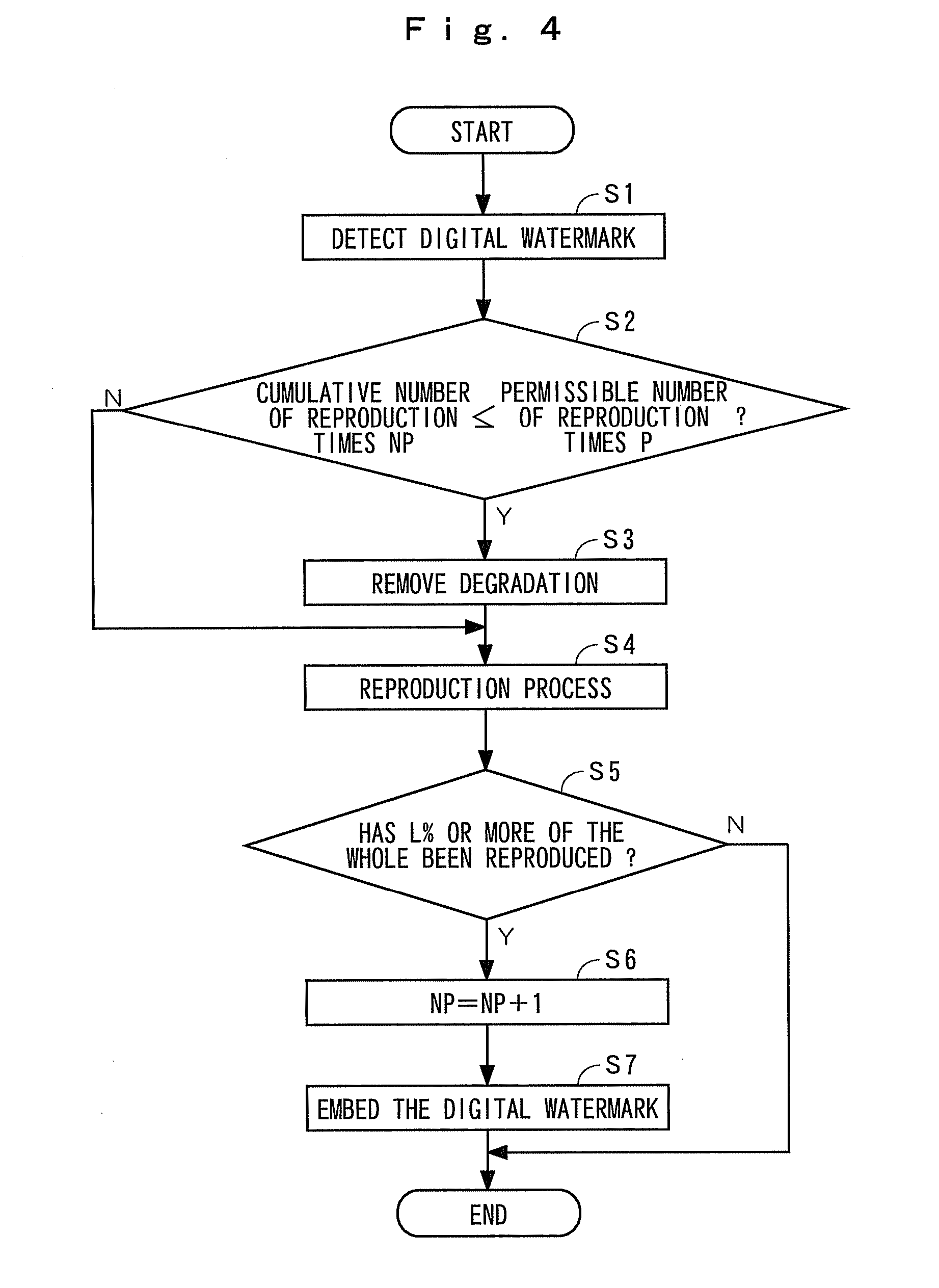
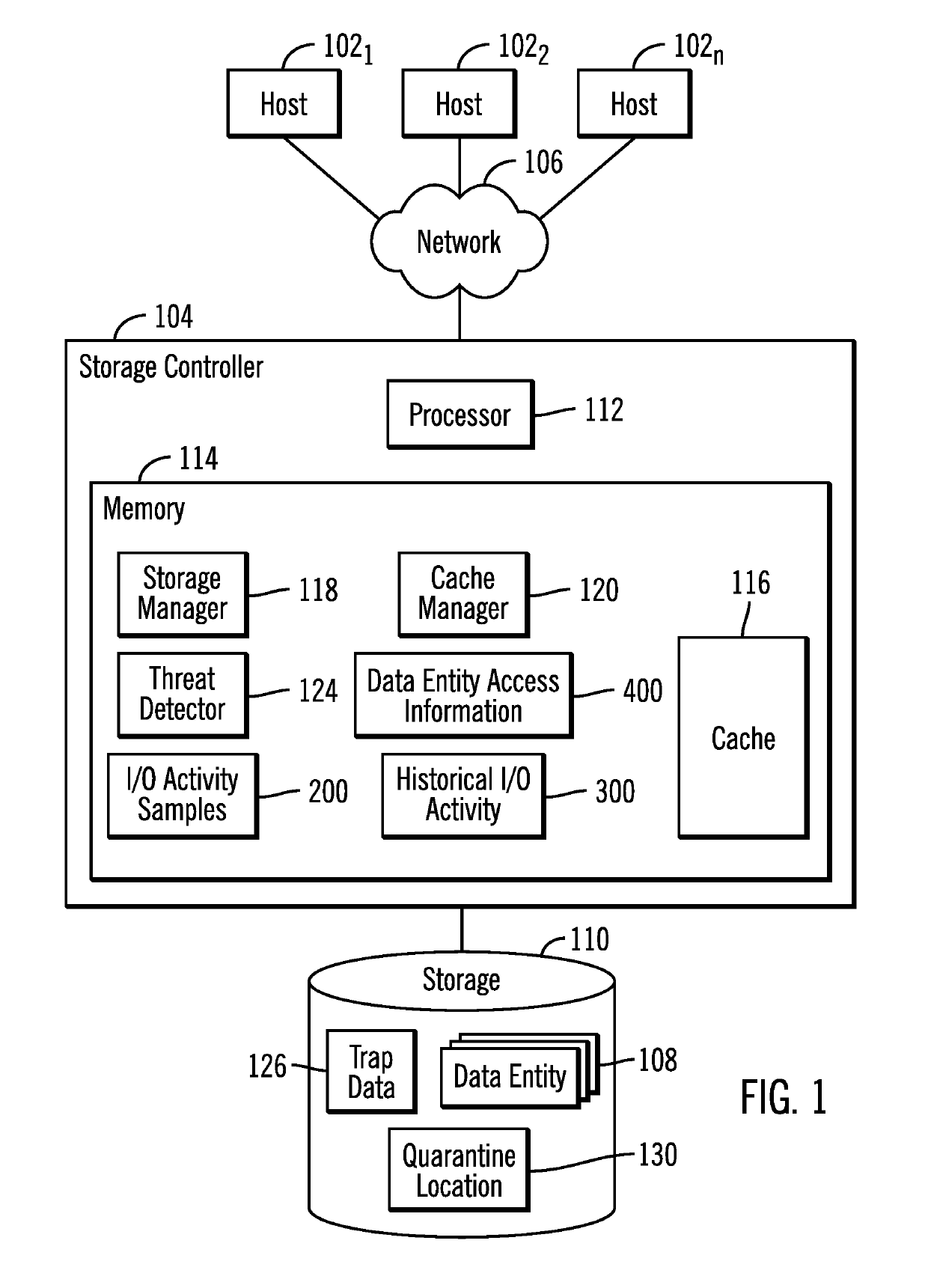
ActiveUS20090119781A1Simple configurationCopyright protectionTelevision system detailsCryptography processingDigital dataData degradation
The present invention provides a digital data reproducing device having a simple configuration and being capable of protecting copyright of digital data such as video or audio. Content provider side embeds copyright management information (cumulative number of reproduction times, permissible number of reproduction times, etc.) into digital data that has been degraded by scrambling, and provides it to a content user. A reproducing device of the content user side causes copyright management information detection unit to detect the copyright management information, decreases the data degradation depending on result of the detection, and reproduces by data reproducing unit.
Owner:KDDI CORP
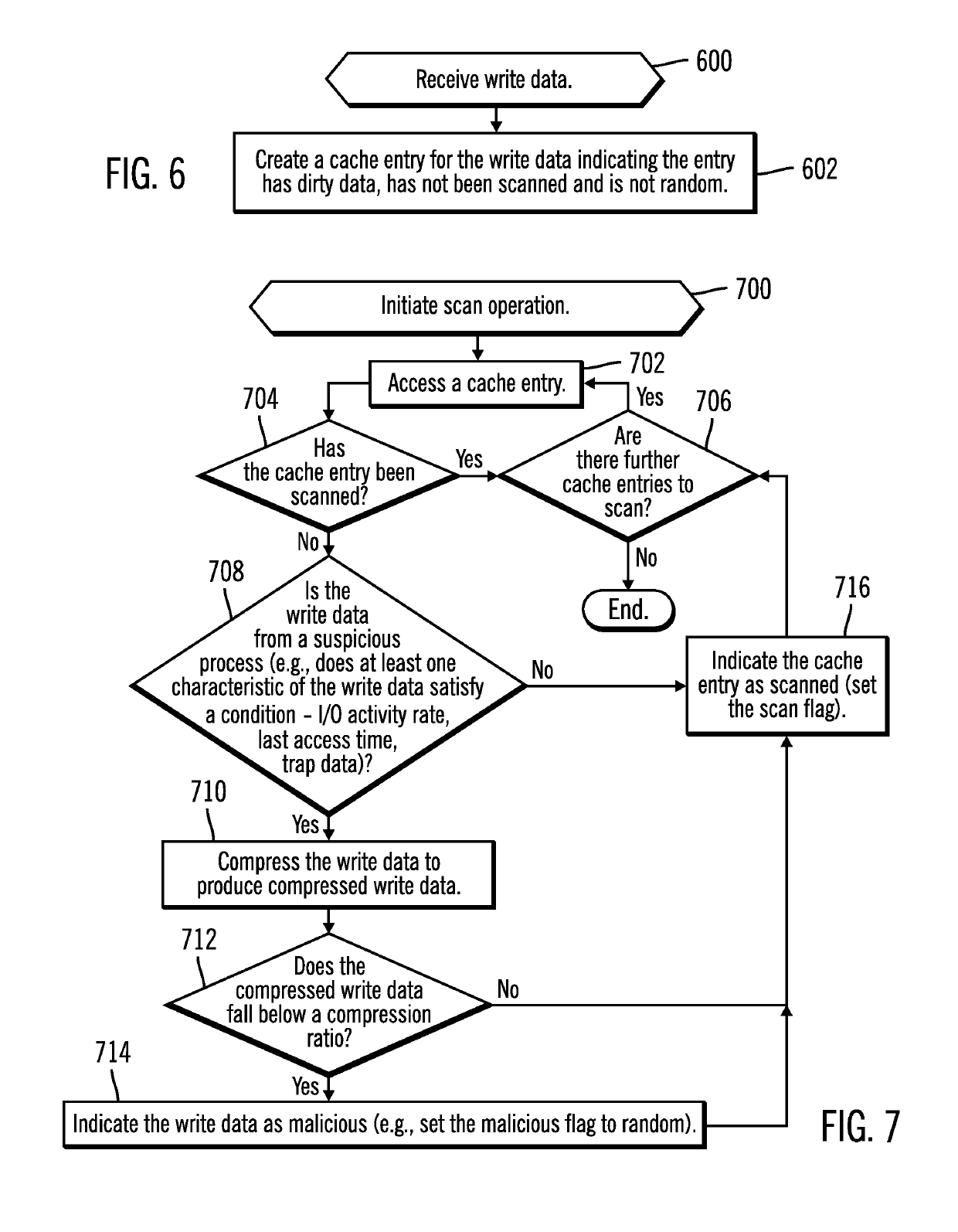
Determining whether to destage write data in cache to storage based on whether the write data has malicious data
ActiveUS10282543B2Memory architecture accessing/allocationCache memory detailsData treatmentData degradation
Provided are a computer program product, system, and method for determining whether to destage write data in cache to storage based on whether the write data has malicious data. Write data for a storage is cached in a cache. A determination is made as to whether the write data in the cache comprises random data according to a randomness criteria. The write data in the cache to the storage in response to determining that the write data does not comprise random data according to the randomness criteria. The write data is processed as malicious data after determining that the write data comprises random data according to the randomness criteria.
Owner:IBM CORP
Low-resolution face image super-resolution method for recognition.
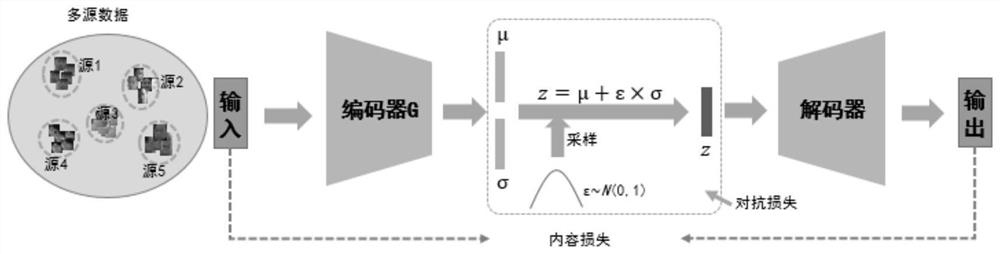
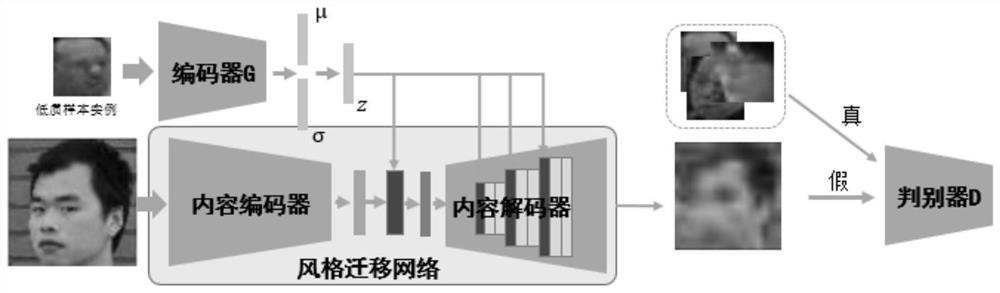
ActiveCN112288627AEffective simulationImprove recognition accuracyGeometric image transformationCharacter and pattern recognitionImage resolutionData degradation
The invention discloses a low-resolution face image super-resolution method for recognition. The method comprises the following steps: learning a degradation distribution rule of sample data by adopting a variational self-encoding network through a small number of collected monitoring scene degradation samples; on the basis of the data degradation distribution rule, expanding diverse degradation samples obeying the data degradation distribution rule through a sampling strategy; performing sample degradation simulation generation processing on the high-resolution data sample through a style migration network so as to obtain a corresponding low-resolution face sample which is distributed in the same way as the real degradation sample; and training a preset face image super-resolution networkby using the high-resolution data sample and the correspondingly generated low-resolution degraded sample until the network converges. According to the invention, the face super-resolution enhancement network not only can generate high-quality clear faces, but also pays attention to synthesis of identity information related textures. According to the method, the recognition rate of the low-resolution face image in a monitoring scene can be improved under the condition that the number of low-resolution samples is small.
Owner:WUHAN UNIV
Image registration method and system based on feature guiding GMM and edge image
The invention relates to an image registration method and system based on a feature guiding GMM and an edge image. Edge images of two to-be-matched images are calculated, feature point sets of the edge images are extracted, according to feature description vectors, a membership degree of a GMM model is set, a model corresponding to geometric transformation between to-be-matched images is established, and a model parameter is calculated by using an optimization method; a posterior probability of a matching point of a feature point in another feature point set of a feature point in the feature point set is calculated again and whether the feature points are matched points mutually is determined according to a threshold value. According to the invention, modeling is carried out for an affine transformation phenomenon between to-be-matched images; and compared with the previous optimization method, the provided method has better robustness and higher accuracy; and the performances are stable under the circumstance that the data degradation is severe.
Owner:珠海创旗科技有限公司
Merge and split fast hartley block transform method
Fast Hartley Transforms in a radix-2 block transform method enables true split and merge transform processing of equal sized data halves for enabling recursive merges and splits in Hartley transform domain without data degradation. Input data in the time domain or spatial domain during either the split and merge radix-2 forward Hartley transform processing is firstly transform processed followed by combinational processing. Whole transformed data is split using combinational processing into transformed data halves in the Hartley transform domain as a true split. The transformed halves are merged using combinational processing into whole merged transformed data in the Hartley transform domain. Time or spatial domain input data can be transformed into the Hartley transform domain in the form of split halves or merged whole. The split halves can be merged by the merge process combinational processing and the merged whole can be split by the split process combinational processing.
Owner:THE AEROSPACE CORPORATION
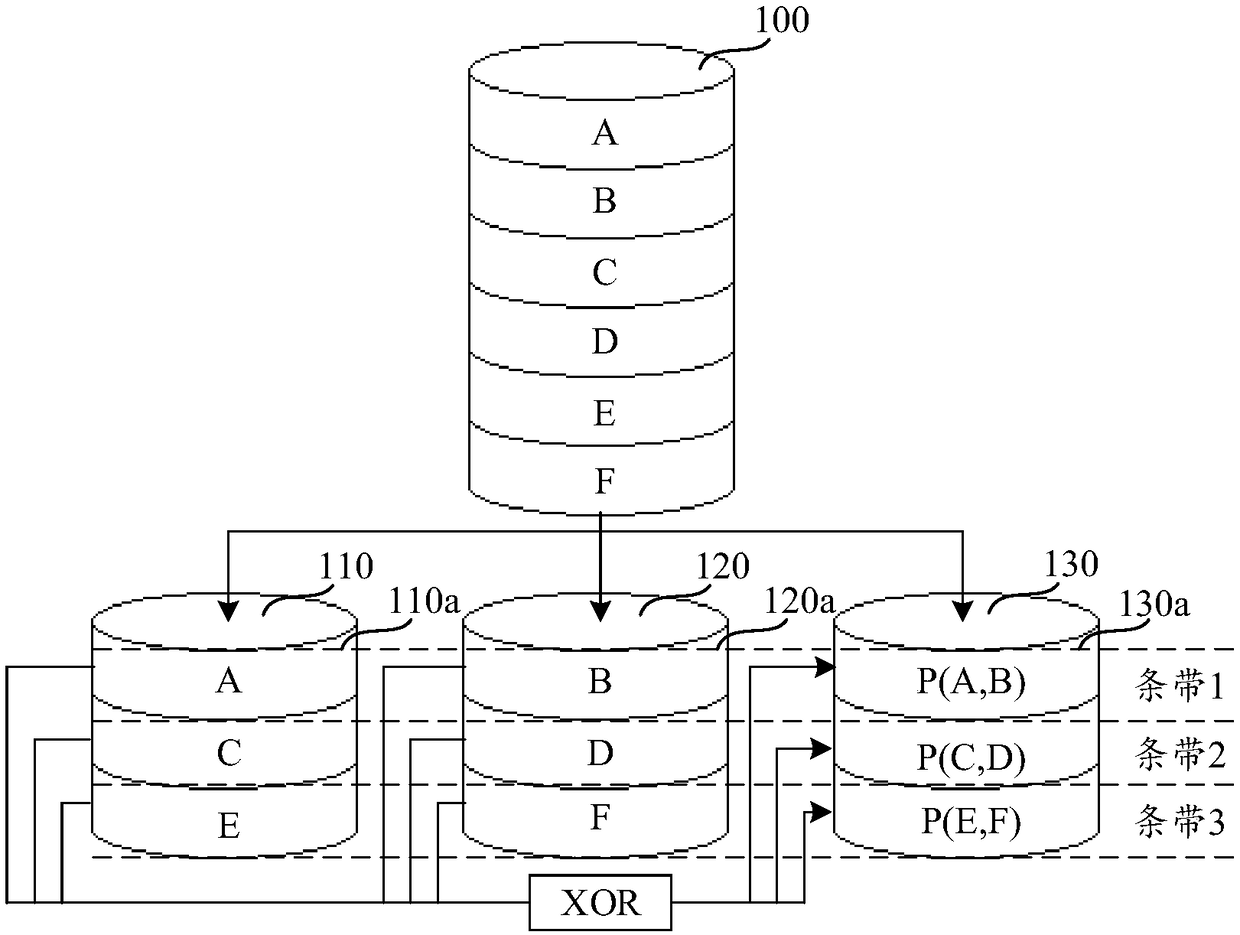
Data degradation storage method and device
ActiveCN108932176AGuaranteed recoverabilitySolve the lossRedundant data error correctionRAIDData degradation
The embodiment of the invention discloses a data degradation storage method and device and belongs to the technical field of data storage. The method includes a step of obtaining data to be stored, detecting whether an online strip exists or not, and assigning an offline strip to the data if not, a step of reallocating data blocks and check blocks in online blocks of the offline strip if the number of the online blocks in the offline strip is larger than a sum of a preset number of check blocks in each strip and 1, wherein the number of the check blocks is the preset number of the check blocksin each strip, and a step of storing the data into the offline strip. In the prior art, a RAID in a degraded state only continues to distribute and store subsequently stored data and no longer calculates and stores verification data, and once a data block has reading and writing failures, all data stored in a disk are lost and unrecoverable, according to the method and the device, the above problem is solved, and an effect that the data stored by the RAID in the degraded state can be recovered is ensured.
Owner:HANGZHOU HIKVISION DIGITAL TECH
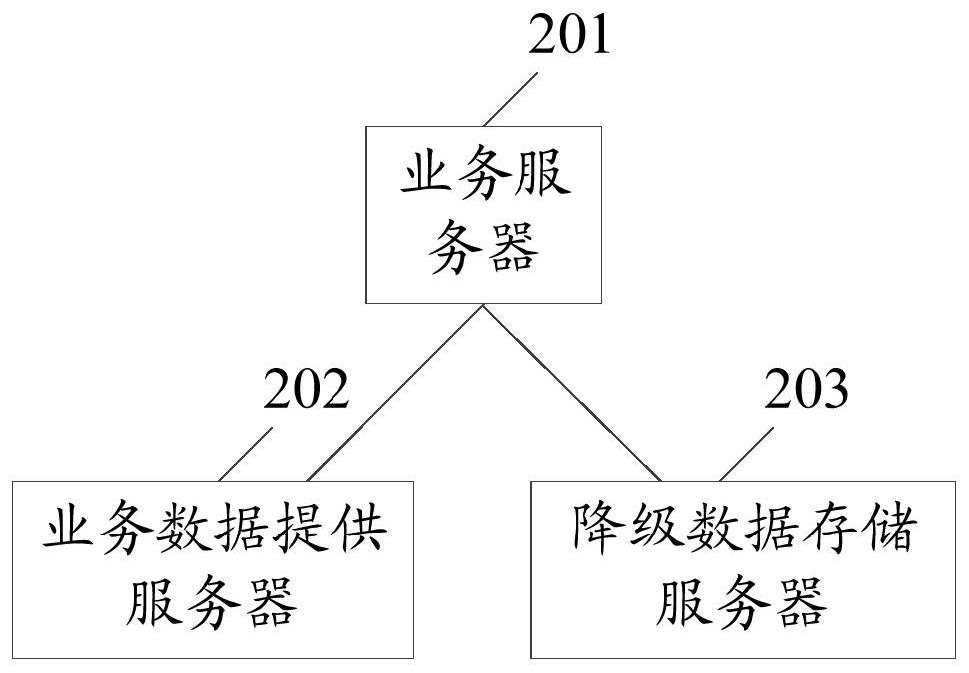
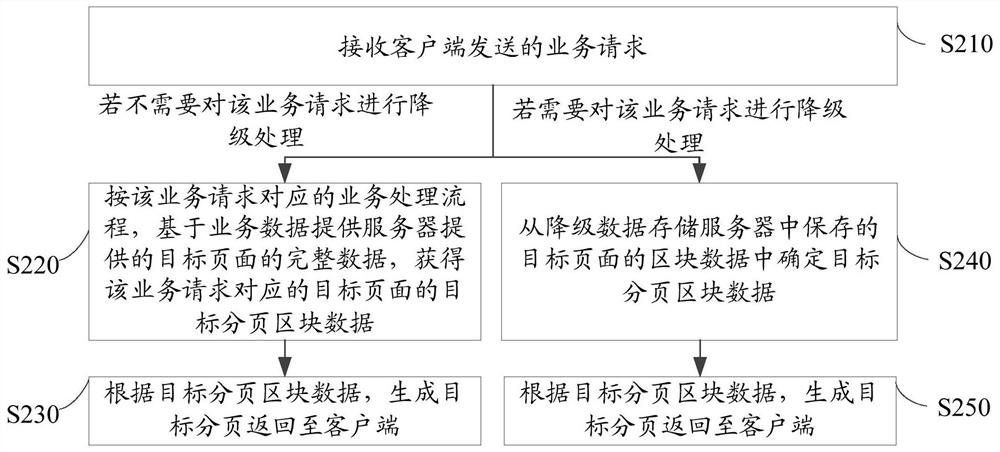
Business request processing method, device, business server and system
The embodiment of the invention provides a service request processing method, a service request processing device, a service server and a service request processing system. The service request processing method comprises the following steps: receiving a service request sent by a client; if the service request does not need to be subjected to degradation processing, generating a target page according to the target paging block data, and returning the target page to the client; if the service request needs to be subjected to degradation processing, determining target paging block data from the block data of the target page stored in the degradation data storage server; wherein the block data of the target page stored in the degradation data storage server is reported to a service server determined in advance from each service server, and the block data of the target page is stored in the degradation data storage server after the target paging block data of the target page is obtained from the service data providing server; and according to the target paging block data, generating a target page and returning the target page to the client. According to the embodiment of the invention,more business data can be sent to the client in the service degradation processing process.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
Wireless communication method and system for transmission authentication at the physical layer
InactiveUS9161214B2Improve anti-interference abilityAuthentication securityBroadcast specific applicationsSecret communicationTransfer systemPhysical layer
The subject authentication scheme encompasses a large family of authentication systems which may be built over existing transmission systems. By superimposing a carefully designed secret modulation on the waveforms, authentication is added to the signal without requiring additional bandwidth. The authentication information (tag signal) is sent concurrently with data (message signal). The authentication is designed to be stealthy to the uninformed user, robust to interference, and secure for identity verification. The tradeoffs between these three goals are identified and analyzed. The use of the authentication for channel estimation is also considered, and improved bit errors are demonstrated for time-varying channels. With a long enough authentication code word an authentication system is achieved with very slight data degradation. Additionally, by treating the authentication tag as a sequence of pilot symbols, the data recovery may be improved by the aware receiver.
Owner:US SEC THE ARMY THE +1
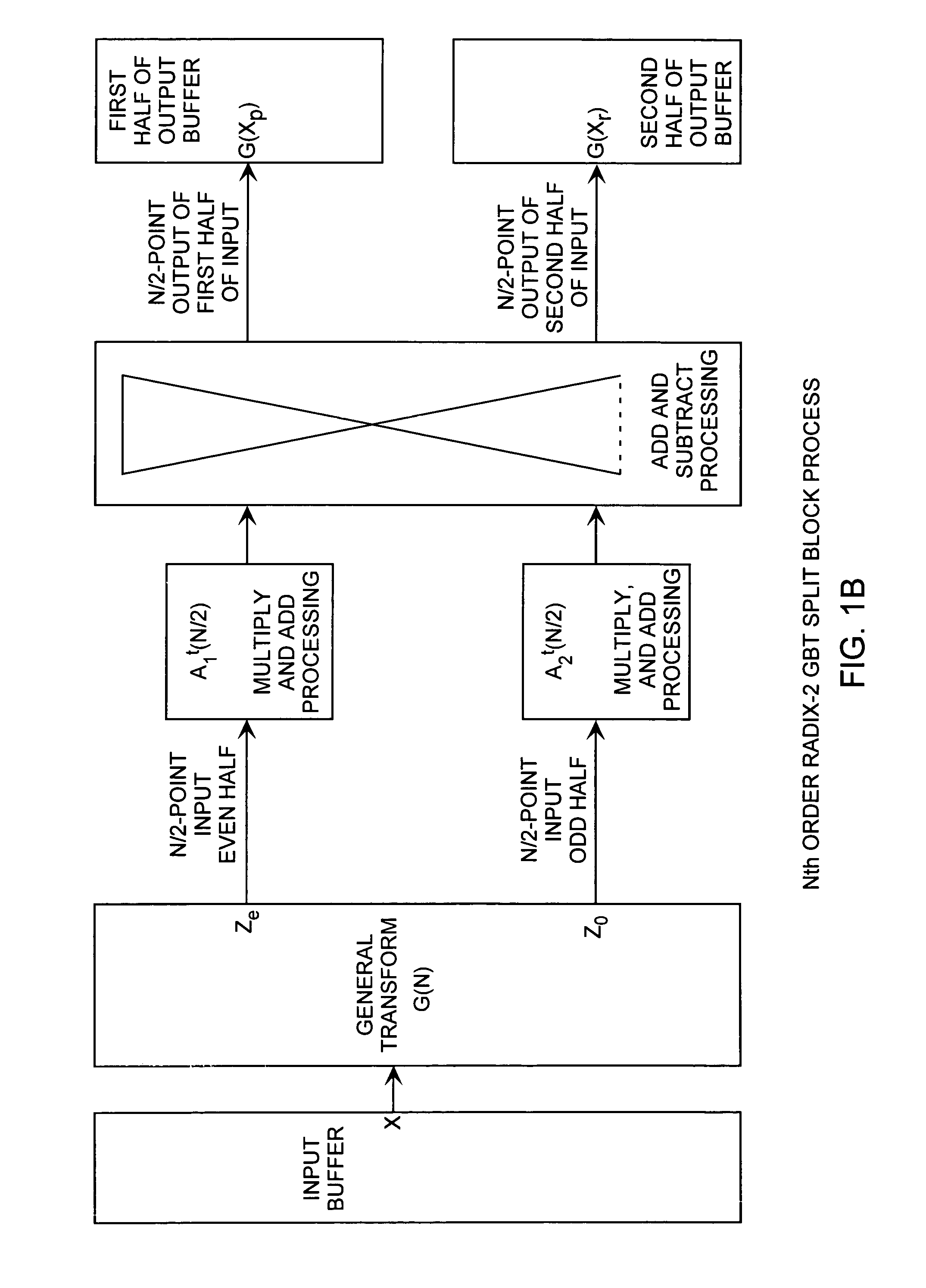
Merge and split generalized block transform method
A generalized radix-2 block transform method enables true split and merge transform processing of equal sized data halves in the transform domain enabling recursive merges and splits in transform domain data degradation. Input data in the time domain or spatial domain during either the split and merge radix-2 forward transform processing is firstly transform processed followed by combinational processing. Whole transformed data is split using combinational processing into transformed data halves in the transform domain as a true split. The transformed halves are merged using combinational processing into whole merged transformed data in the transform domain. Time or spatial domain input data can be transformed into the transform domain in the form of split halves or merged whole. The split halves can be merged by the merge process combinational processing and the merged whole can be split by the split process combinational processing.
Owner:THE AEROSPACE CORPORATION
Optimizing thin provisioning in a data storage system through selective use of multiple grain sizes
ActiveUS9785575B2Small granularityMemory architecture accessing/allocationInput/output to record carriersComputer hardwareThin provisioning
A data storage system includes a pre-cache and a plurality of storage devices across which a data storage array is distributed. In response to receipt of a write request specifying a logical address and write data, the data storage system buffers the write request among a plurality of write requests in the pre-cache without provisioning in the data storage array a physical extent corresponding to the logical address. A management node analyzes the plurality of write requests buffered in the pre-cache. In response to the analyzing identifying a first pattern of write requests, the management node provisions, in the data storage array, a first physical extent having a smaller grain size and destages the write data to the first physical extent. In response to the analyzing identifying a second pattern of write requests, the management node provisions a second physical extent having a larger grain size and destages the write data from the pre-cache to the second physical extent.
Owner:INT BUSINESS MASCH CORP
Image registration method and system based on feature-oriented gmm and edge images
An image registration method and system based on feature-oriented GMM and edge images, including calculating the edge images of the two images to be matched, extracting the feature point set of the edge images, and setting the membership degree of the GMM model based on the feature description vector set. The model corresponding to the geometric transformation between the images to be matched is used to solve the model parameters through the optimization method; the posterior probability of the matching point of the feature point in the feature point set and the feature point in the other feature point set is recalculated, and the threshold is used to determine whether the two match each other. point. The present invention models the situation where affine transformation exists between images to be matched. Compared with the previous optimal method, the method is more robust and accurate, and is especially stable when data degradation is severe.
Owner:珠海创旗科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com