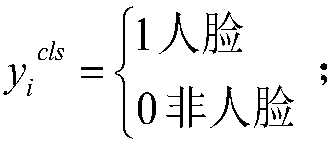Patents
Literature
521 results about "Method cascading" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In object-oriented programming, method cascading is syntax which allows multiple methods to be called on the same object. This is particularly applied in fluent interfaces.
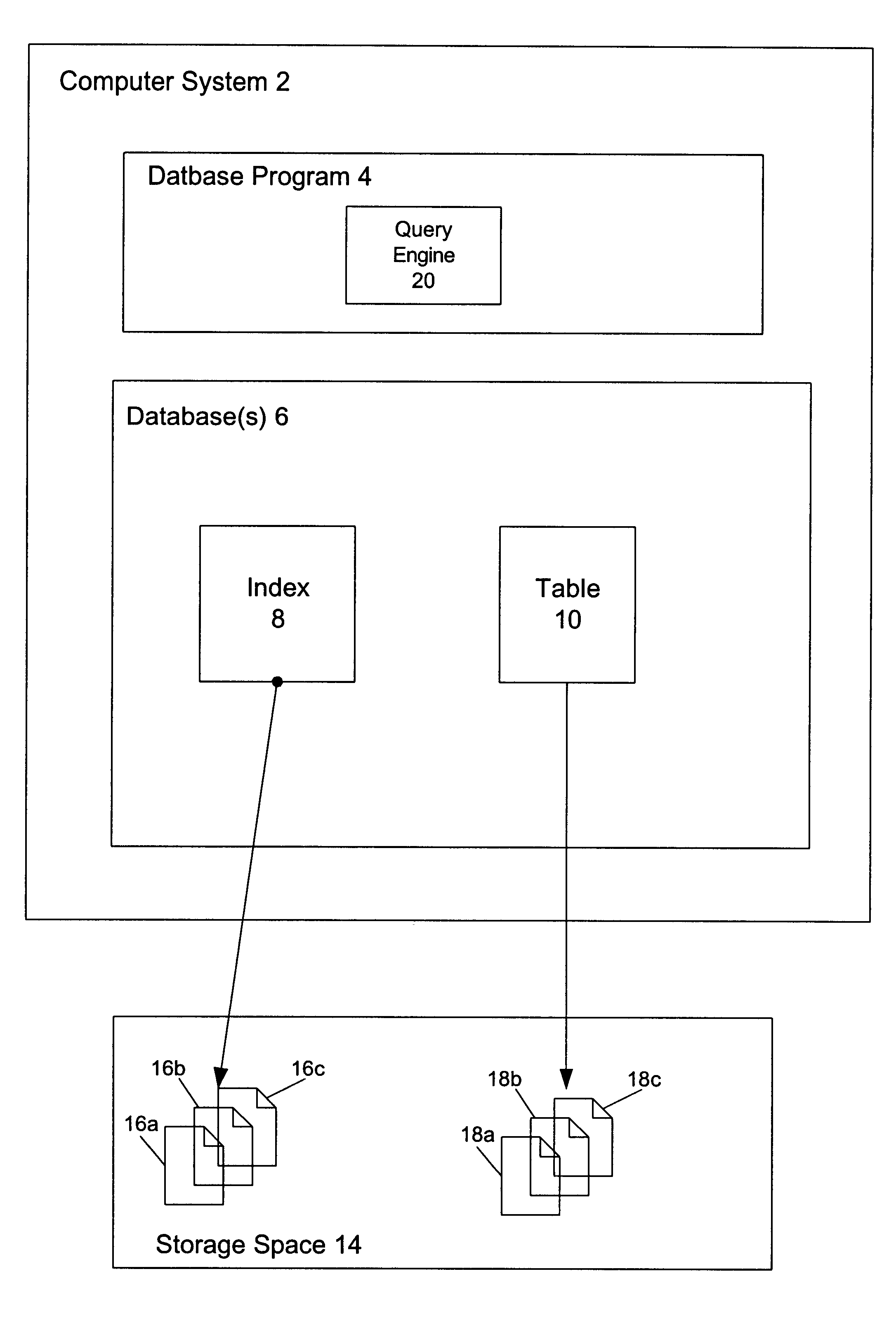
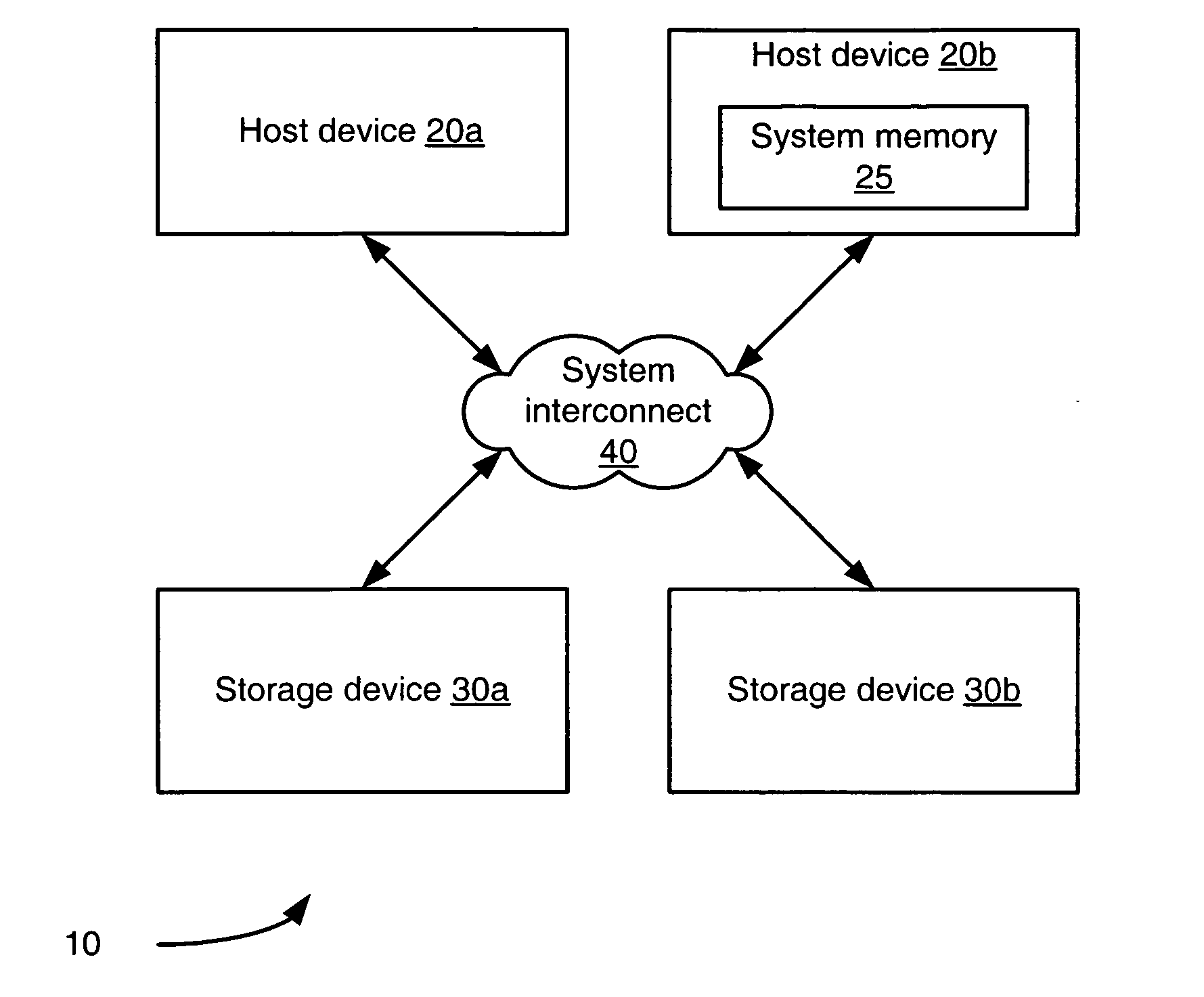
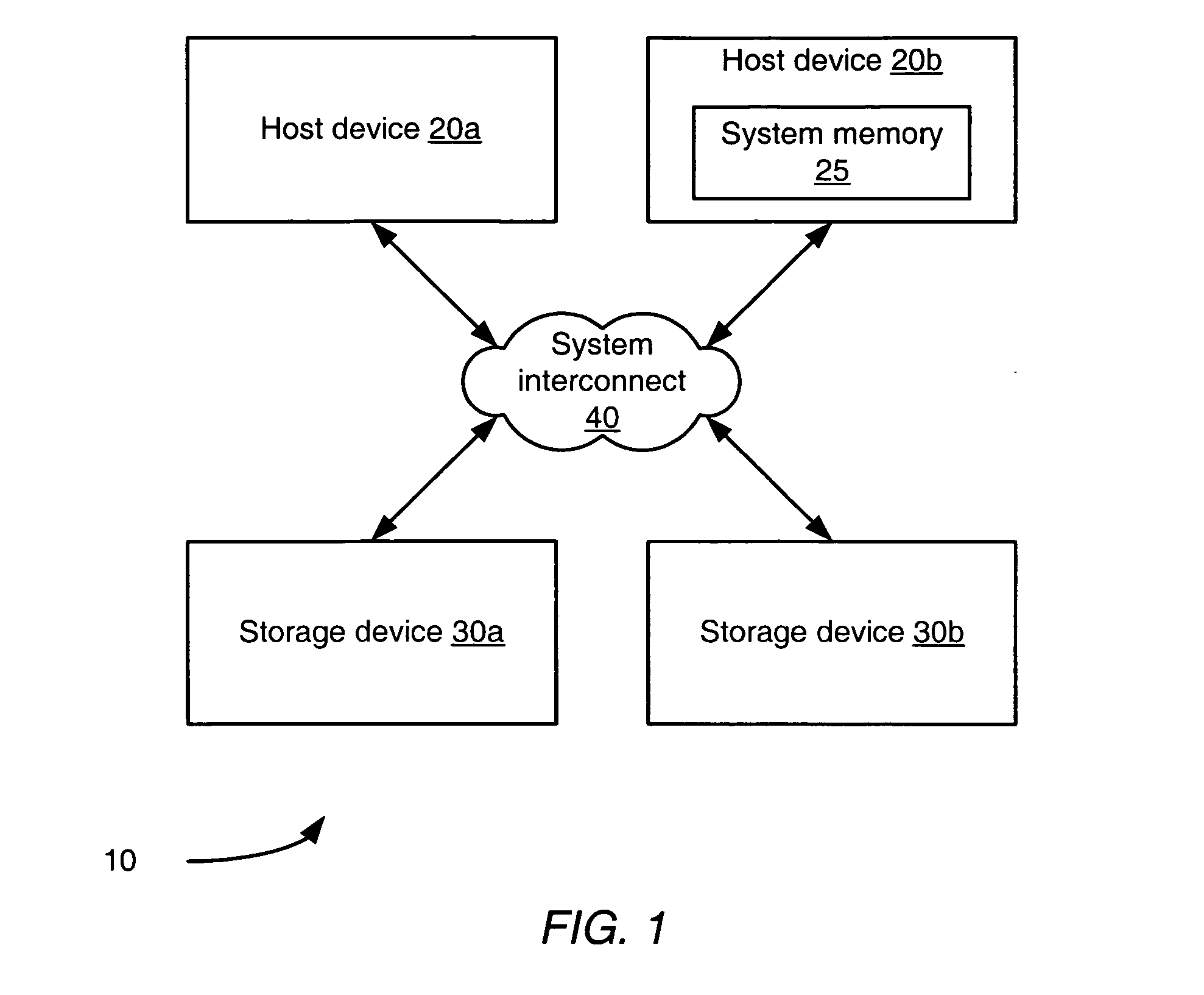
Method and apparatus for cascading data through redundant data storage units
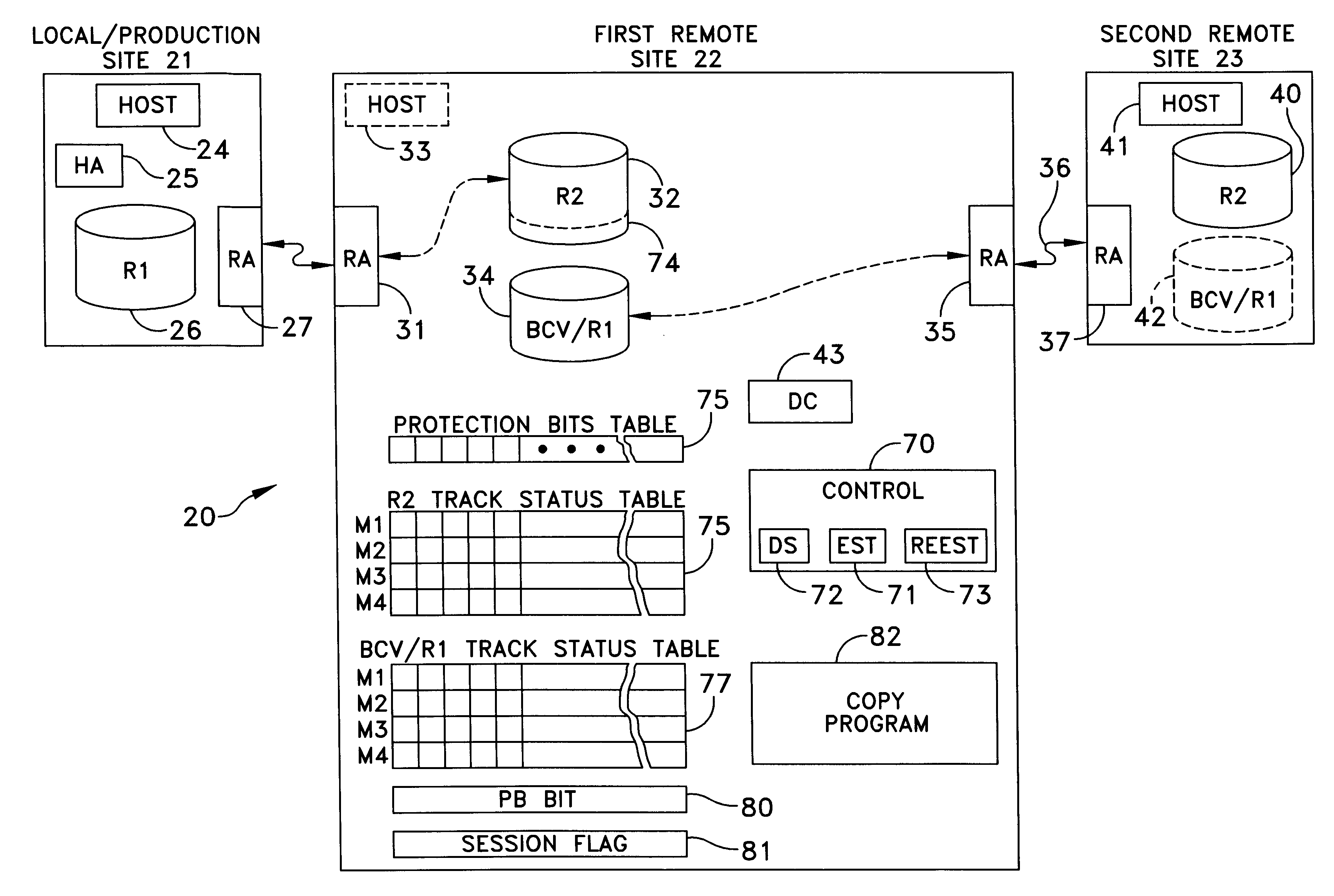
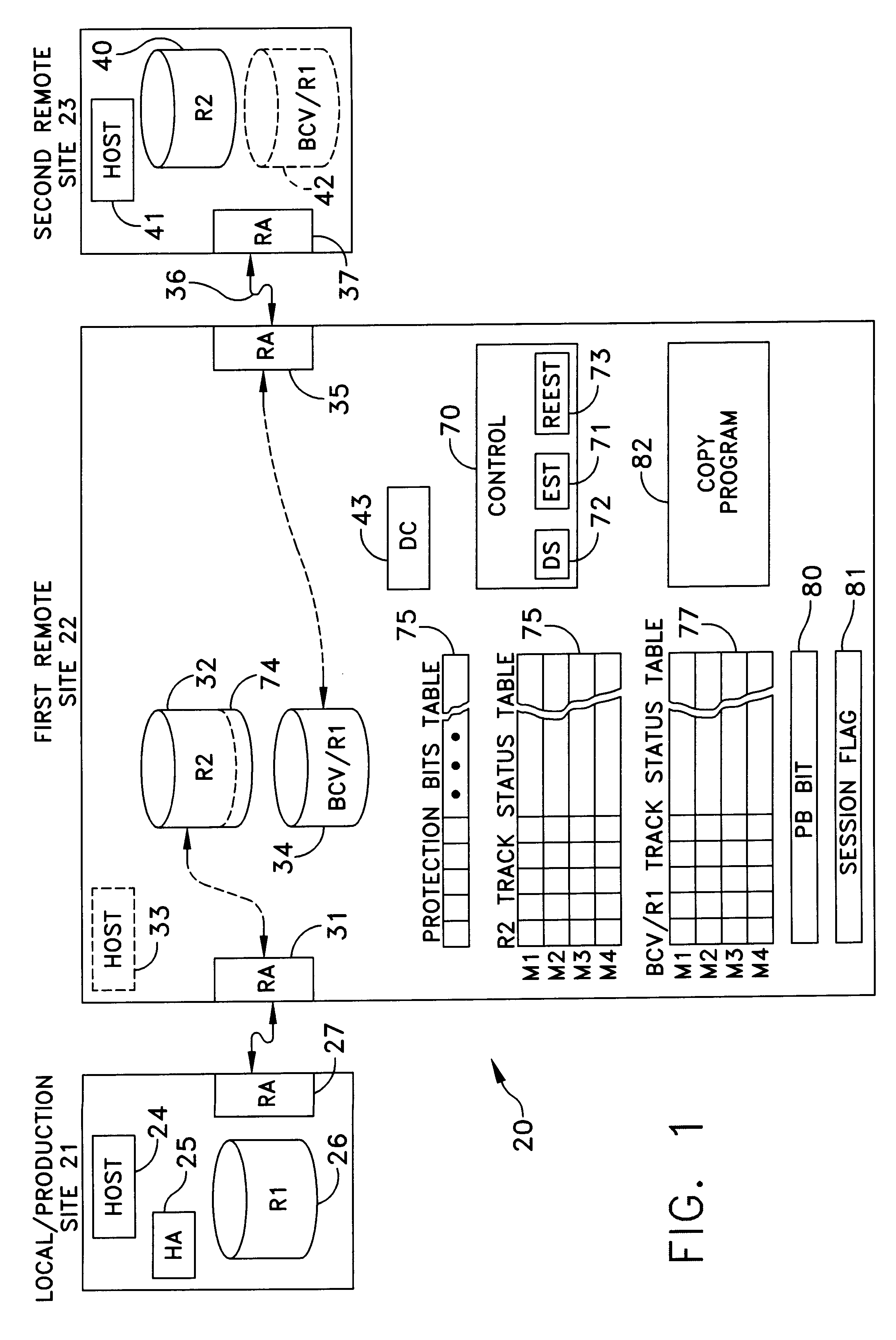
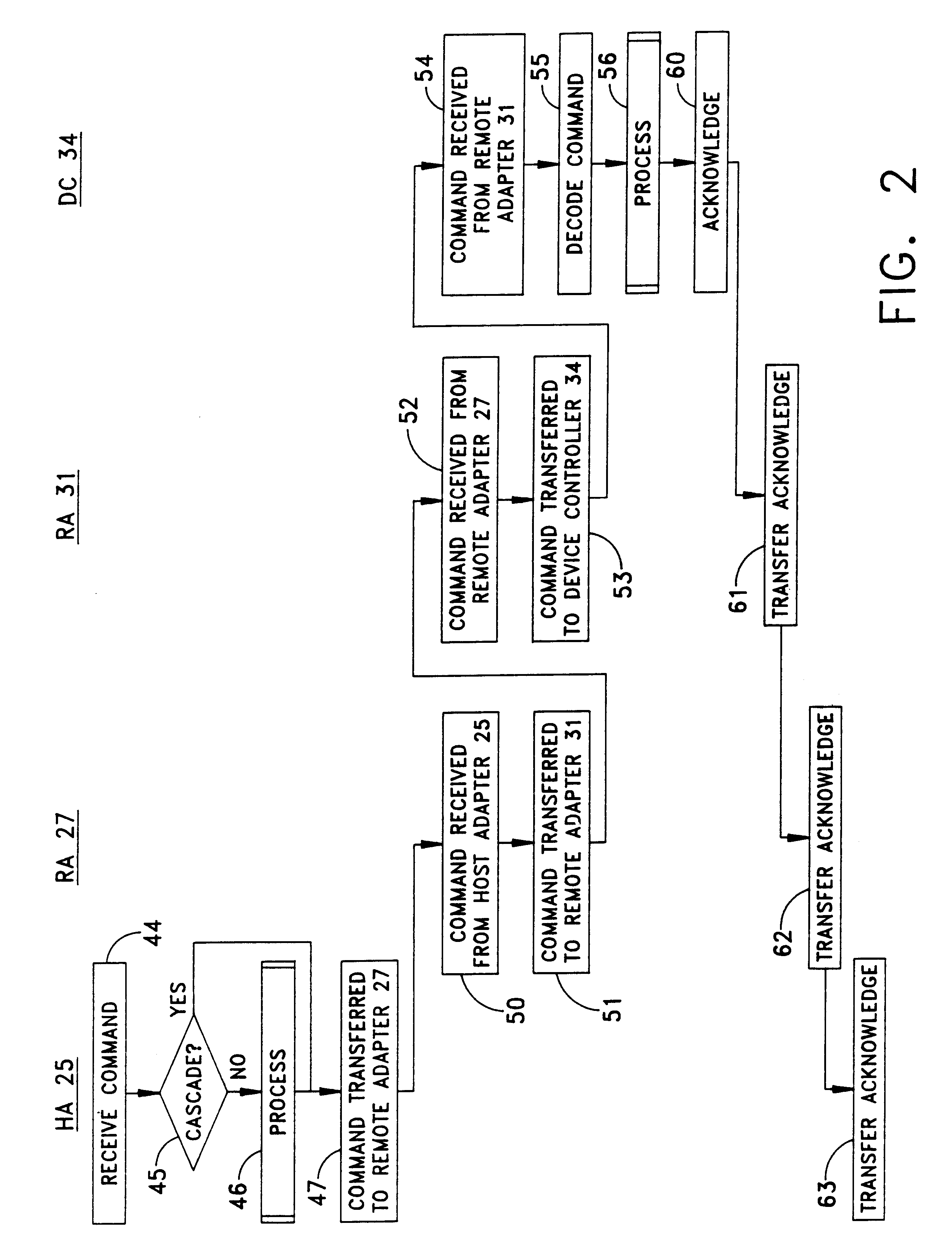
A data storage facility for transferring data from a data altering apparatus, such as a production data processing site to a remote data receiving site. The data storage facility includes a first data store for recording each change in the data generated by the data altering apparatus. A register set records each change on a track-by-track basis. A second data store has first and second operating modes. During a first operating mode the second data store becomes a mirror of the first data store. During a second operating mode the second data store ceases to act as a mirror and becomes a source for a transfer of data to the data receiving site. Only information that has been altered, i.e., specific tracks that have been altered, are transferred during successive operations in the second operating mode. Commands from the local production site initiate the transfers between the first and second operating modes.
Owner:EMC IP HLDG CO LLC
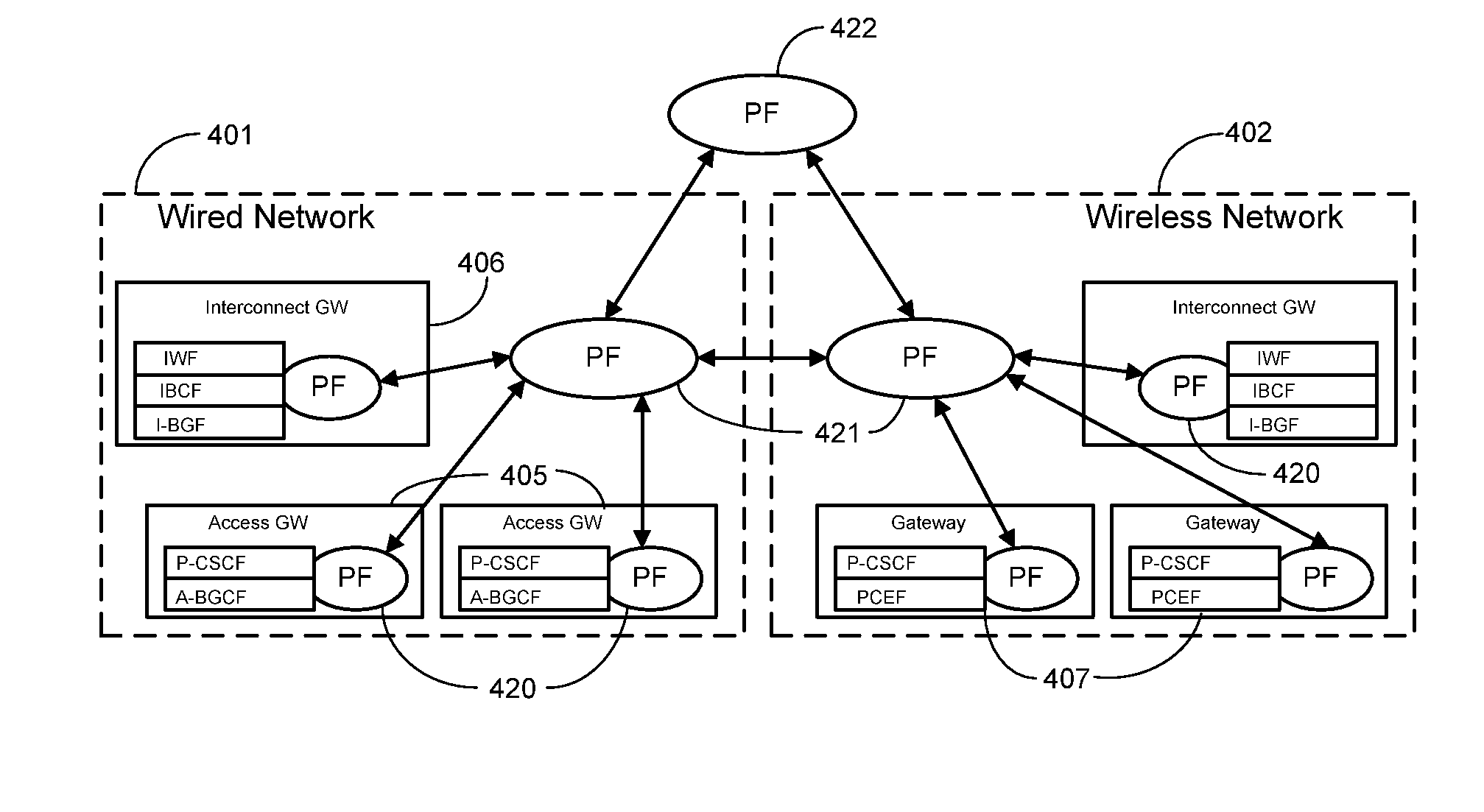
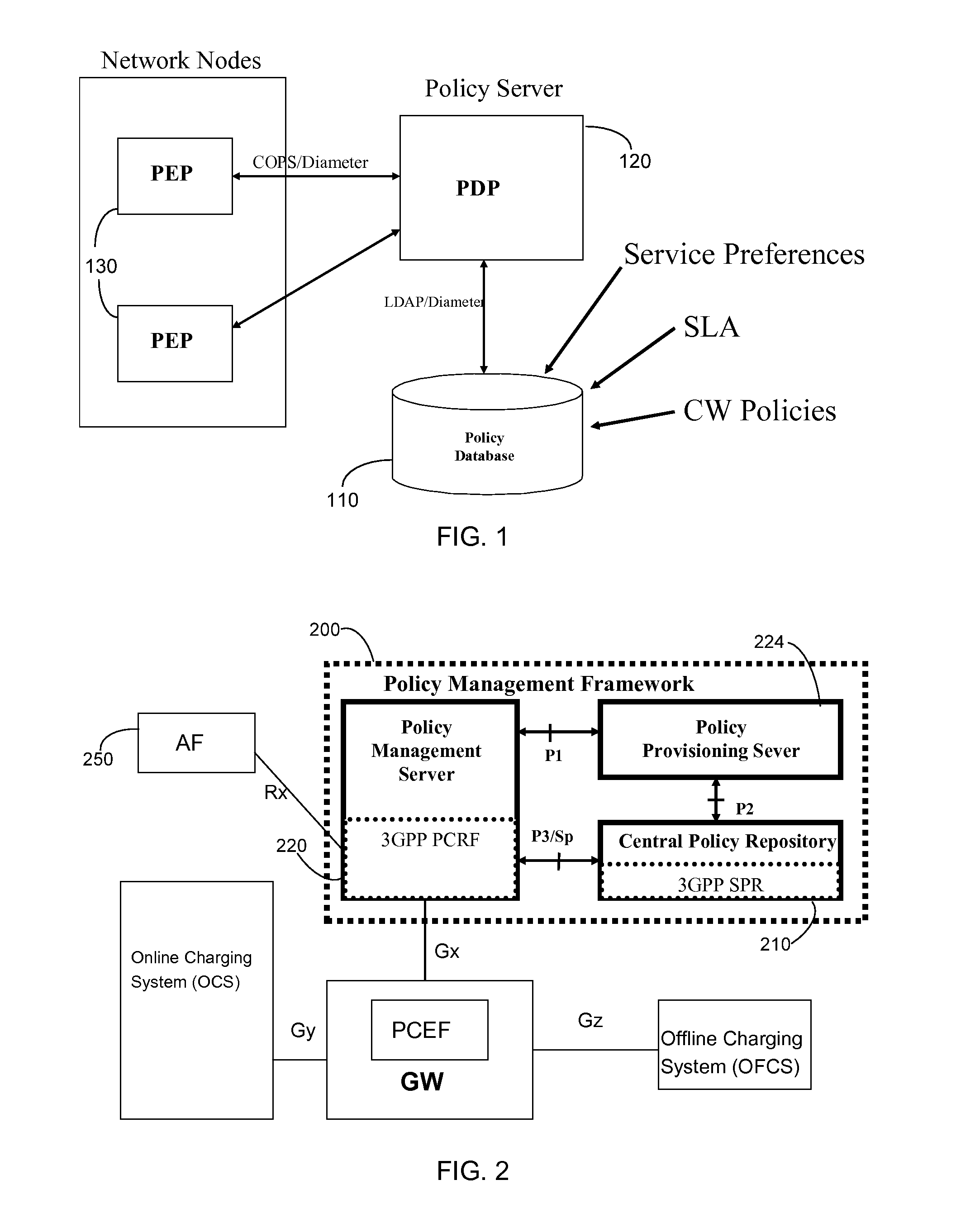
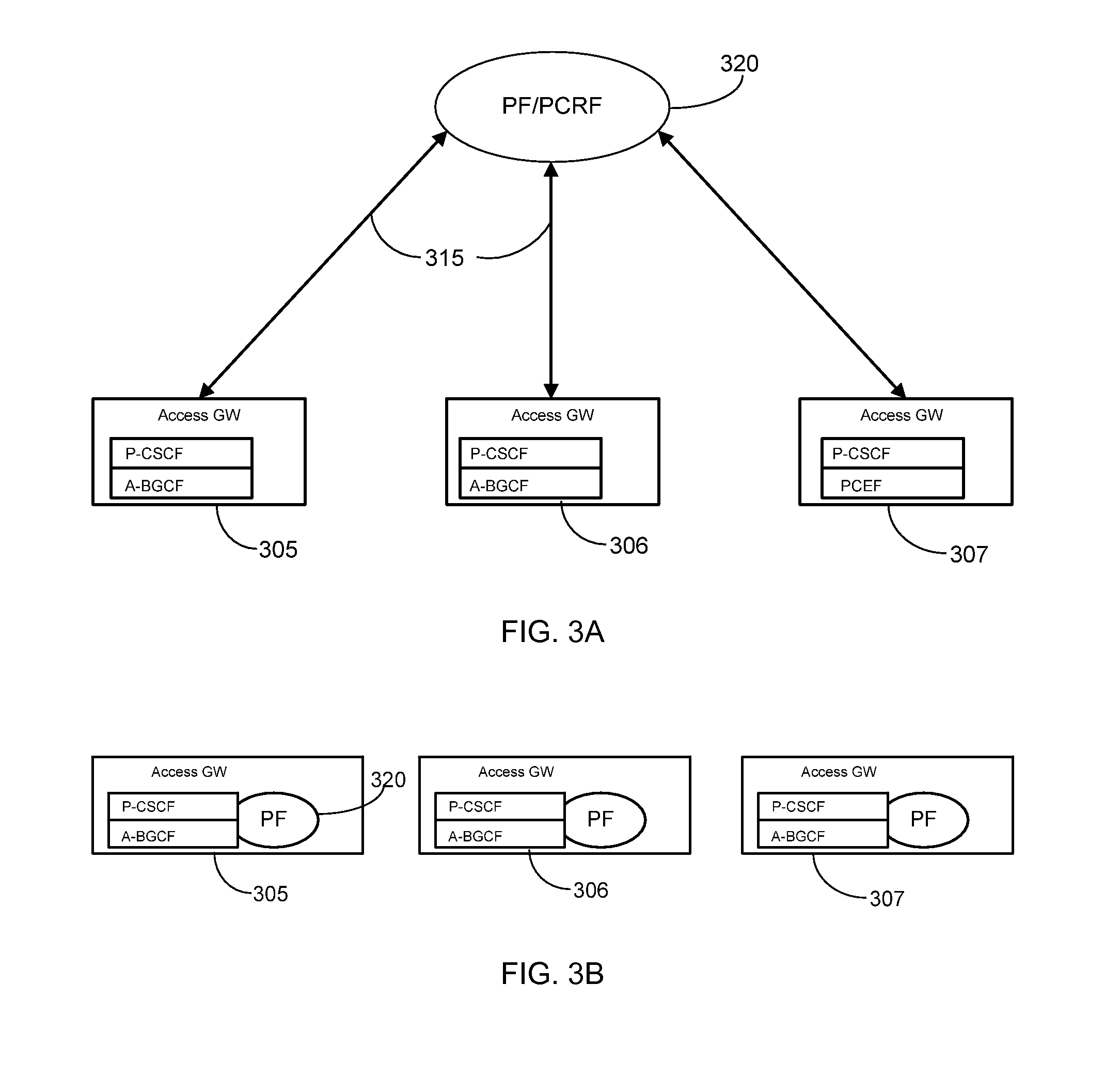
Cascading Policy Management Deployment Architecture
InactiveUS20090113514A1Improve performanceLimitation is enforcedError preventionTransmission systemsPolicy decisionWireless mesh network
Systems and methods are provided to implement a dynamic and efficient cascading policy management framework architecture for both wired and wireless networks. A plurality of Policy Functions (PFs) are assigned to a plurality of Policy Enforcement Points (PEP). The PFs make decisions regarding local policy control at the specific PEP. The PFs then delegate the policy requests or IP flows to a separate PEP that is more conducive to enforcing that policy request. Thus, policy decisions are made at the point where the most information is available, leading to fewer policy requests traversing back and forth across a network. Additionally, this cascading Policy Management Framework Architecture allows for unified policy management across multiple types of networks, including wired (Internet) and wireless (UMTS).
Owner:AT&T MOBILITY II LLC
System and method of performing speech recognition based on a user identifier
InactiveUS7451081B1Natural language data processingSpeech recognitionData fieldBackground information
Owner:NUANCE COMM INC
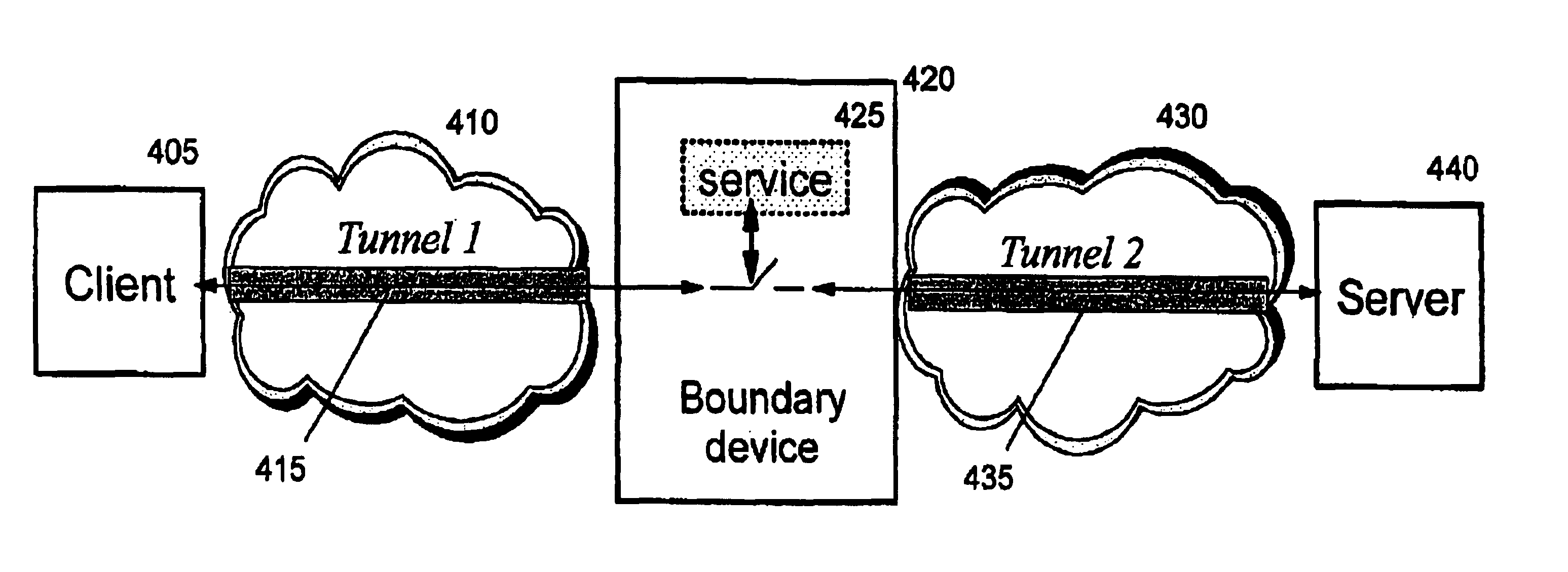
Establishing consistent, end-to-end protection for a user datagram
A method, system, and computer program product for providing consistent, end-to-end protection within a computer network for user datagrams (i.e. packets) traveling through the network. The network may comprise network segments that are conventionally assumed to be secure (such as those found in a corporate intranet) as well as network segments in non-secure networks (such as the public Internet or corporate extranets). Because security breaches may in fact happen in any network segment when datagrams are unprotected, the present invention discloses a technique for protecting datagrams throughout the entire network path by establishing cascaded tunnels. The datagrams may be exposed in cleartext at the endpoints of each tunnel, thereby enabling security gateways to perform services that require content inspection (such as network address translation, access control and authorization, and so forth). The preferred embodiment is used with the “IPSec” (Internet Protocol Security Protocol) and “IKE” (Internet Key Exchange) protocols, thus providing a standards-based solution.
Owner:IBM CORP
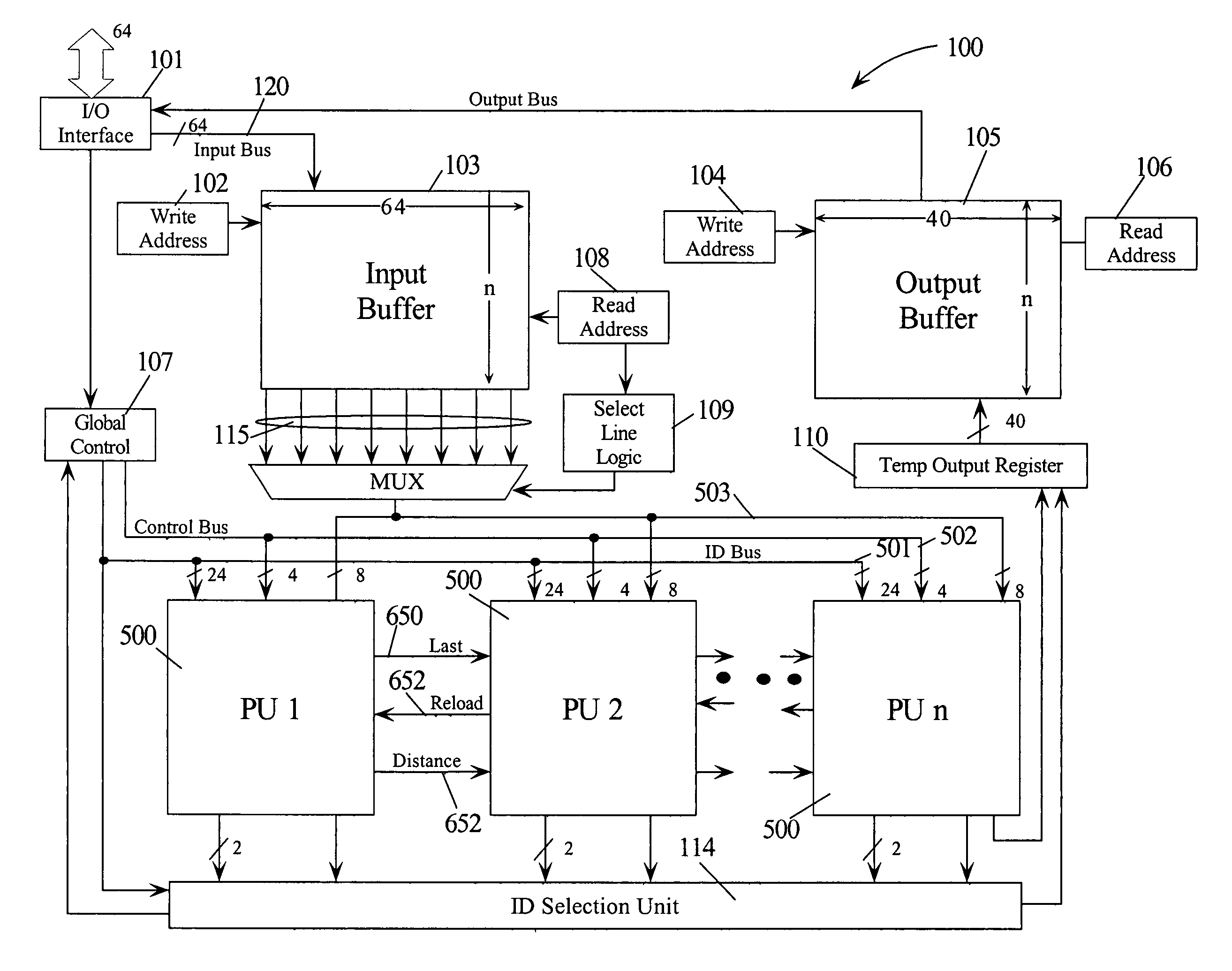
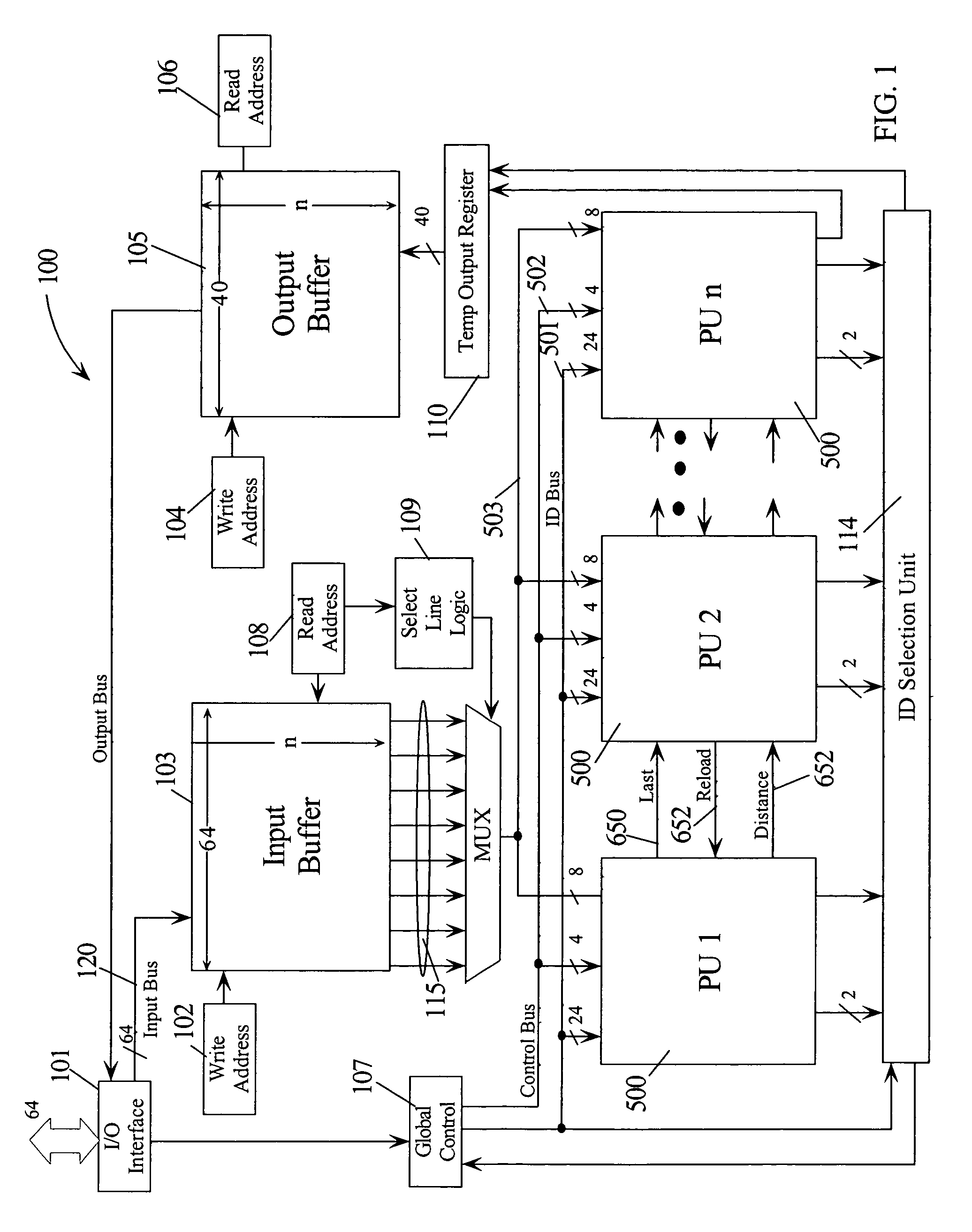
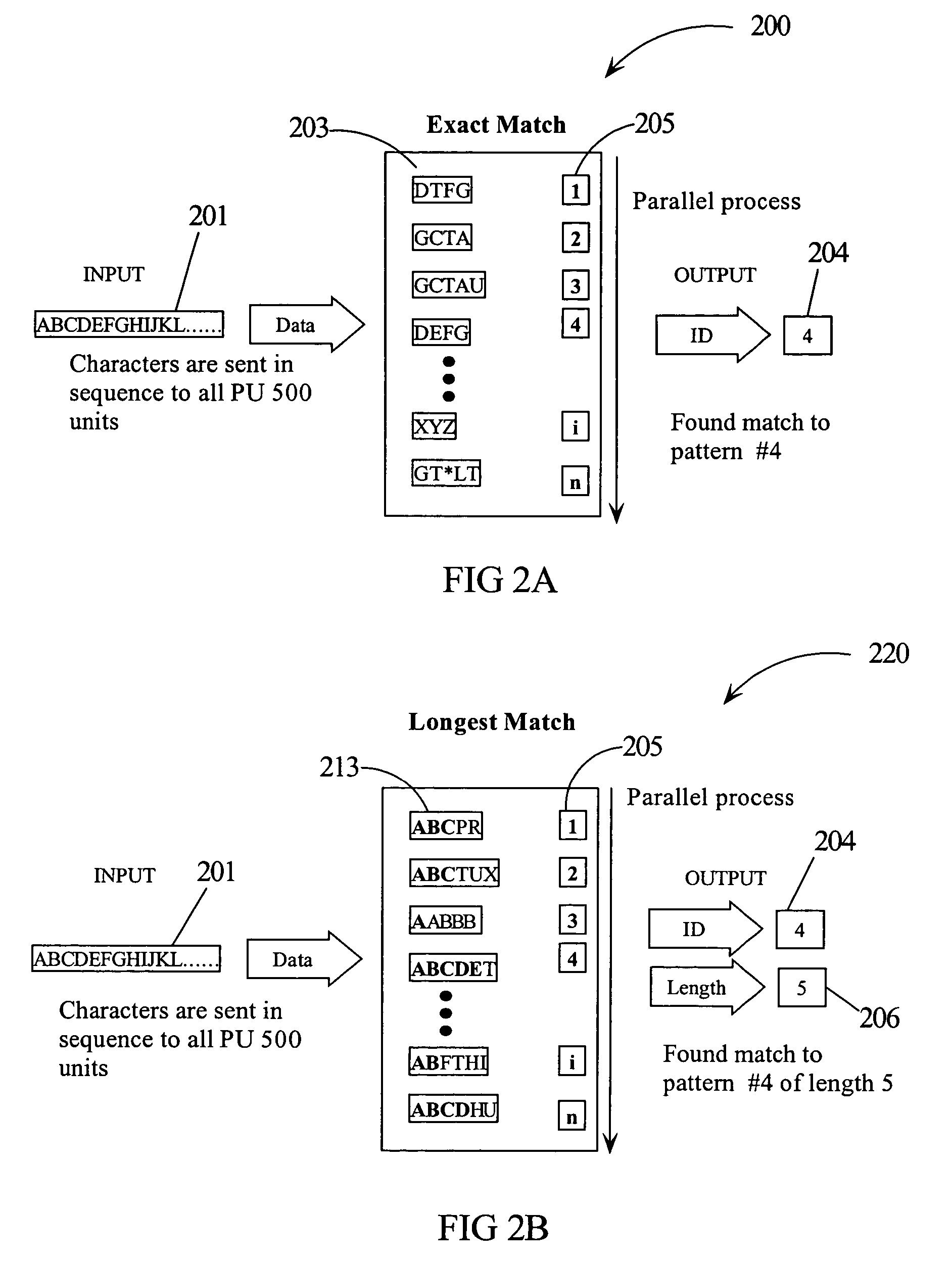
Intrusion detection using a network processor and a parallel pattern detection engine
InactiveUS7487542B2Improve scalabilityMemory loss protectionDigital data processing detailsData streamPattern matching
An intrusion detection system (IDS) comprises a network processor (NP) coupled to a memory unit for storing programs and data. The NP is also coupled to one or more parallel pattern detection engines (PPDE) which provide high speed parallel detection of patterns in an input data stream. Each PPDE comprises many processing units (PUs) each designed to store intrusion signatures as a sequence of data with selected operation codes. The PUs have configuration registers for selecting modes of pattern recognition. Each PU compares a byte at each clock cycle. If a sequence of bytes from the input pattern match a stored pattern, the identification of the PU detecting the pattern is outputted with any applicable comparison data. By storing intrusion signatures in many parallel PUs, the IDS can process network data at the NP processing speed. PUs may be cascaded to increase intrusion coverage or to detect long intrusion signatures.
Owner:TREND MICRO INC
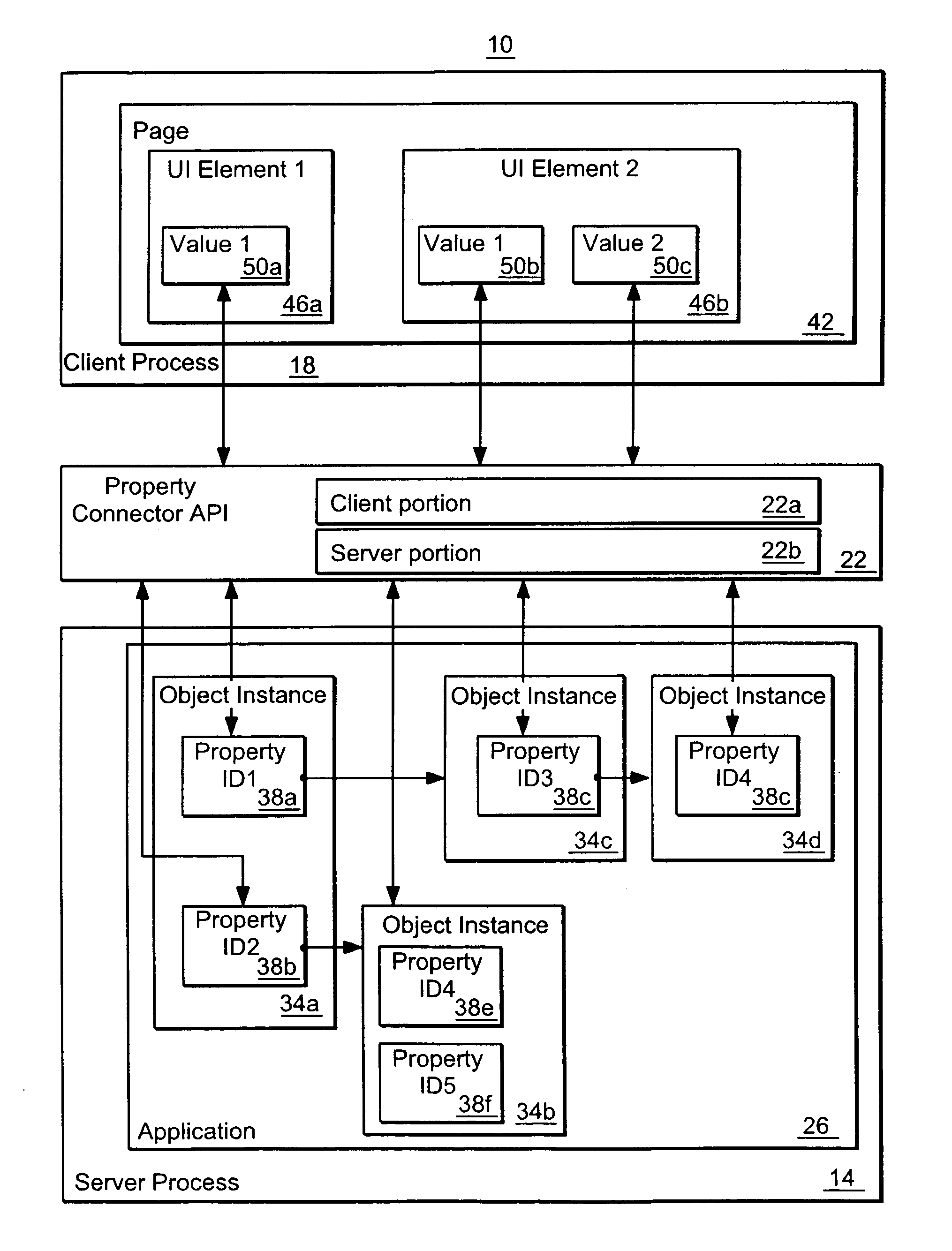
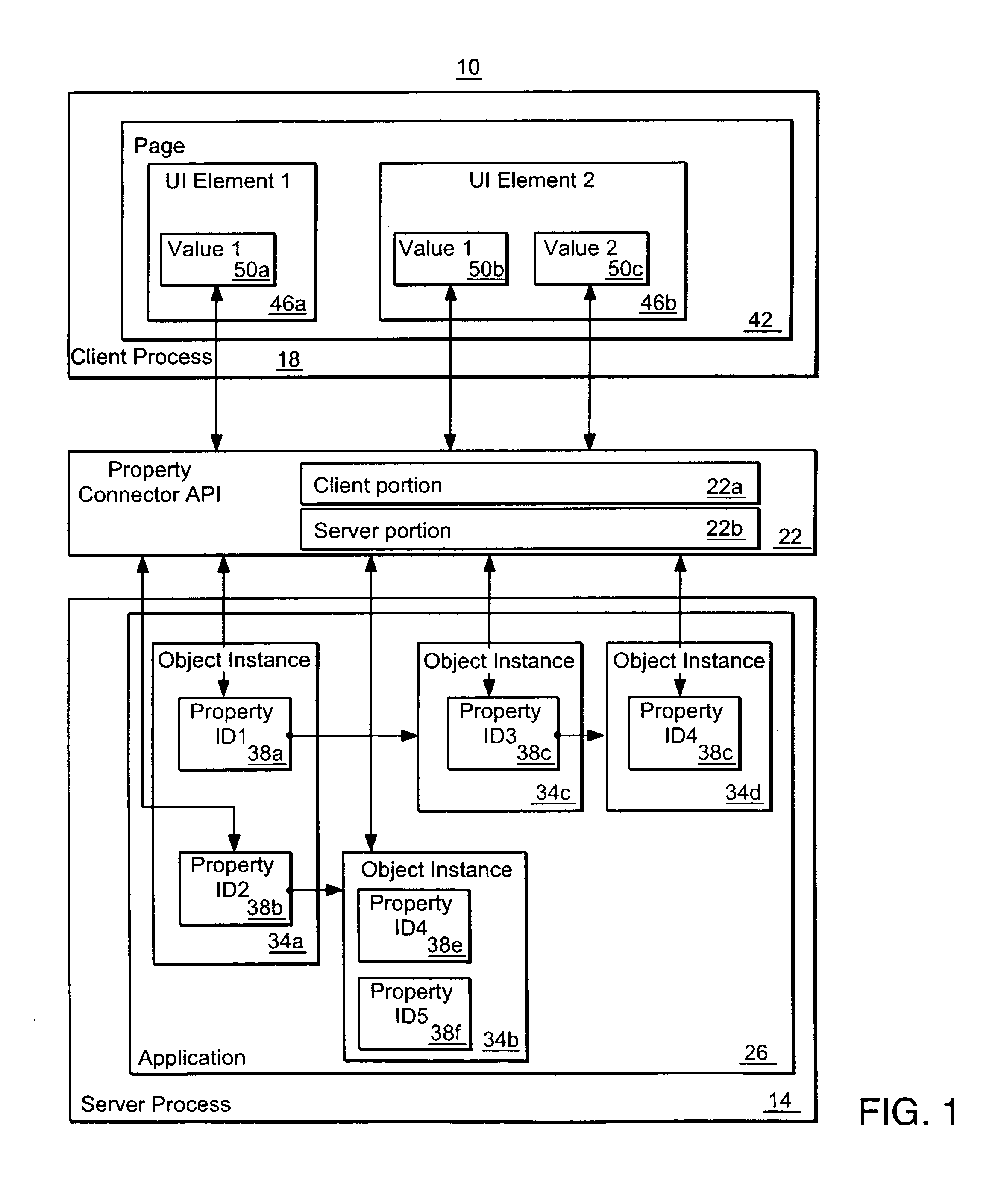
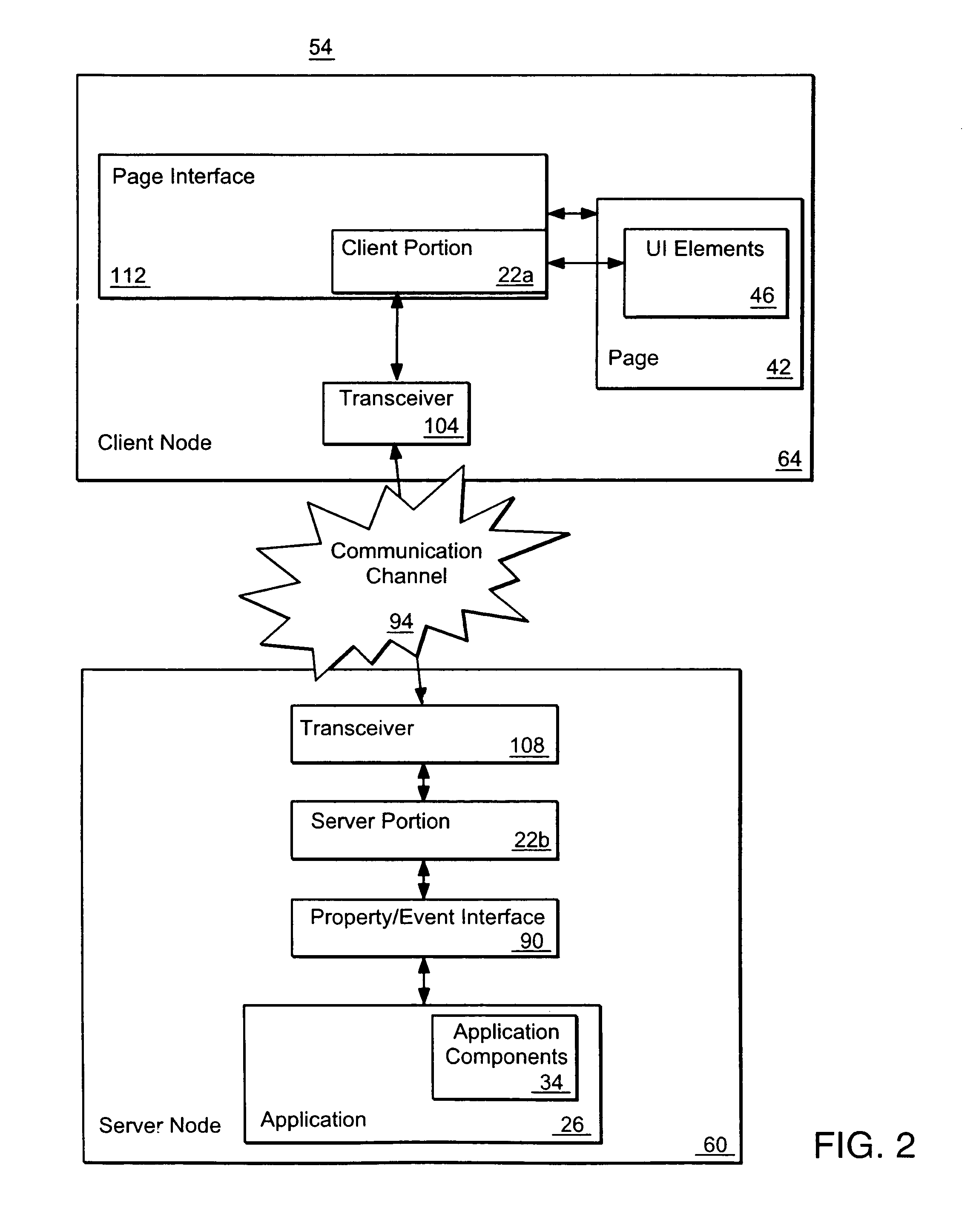
Methods and apparatus for communicating changes between a user interface and an executing application using property paths
InactiveUS7194743B2Simple designReduce latencySoftware engineeringMultiprogramming arrangementsApplication softwareComputer science
In one aspect the invention relates to a method of associating an element of a user-interface to a current state of a property in a system including an application having a plurality of components, wherein at least one component has a property, wherein each property is identified with an identifier. The method comprises associating the element of the user-interface with a property path, the property path including a concatenation of a plurality of identifiers, the concatenation of identifiers defining a path through the components of the application to a property at the end of the concatenation, and mapping the property path to a current state of the property at the end of the path defined by the concatenation of identifiers, to associate the element of the user-interface with the current state of that property.
Owner:CITRIX SYST INC
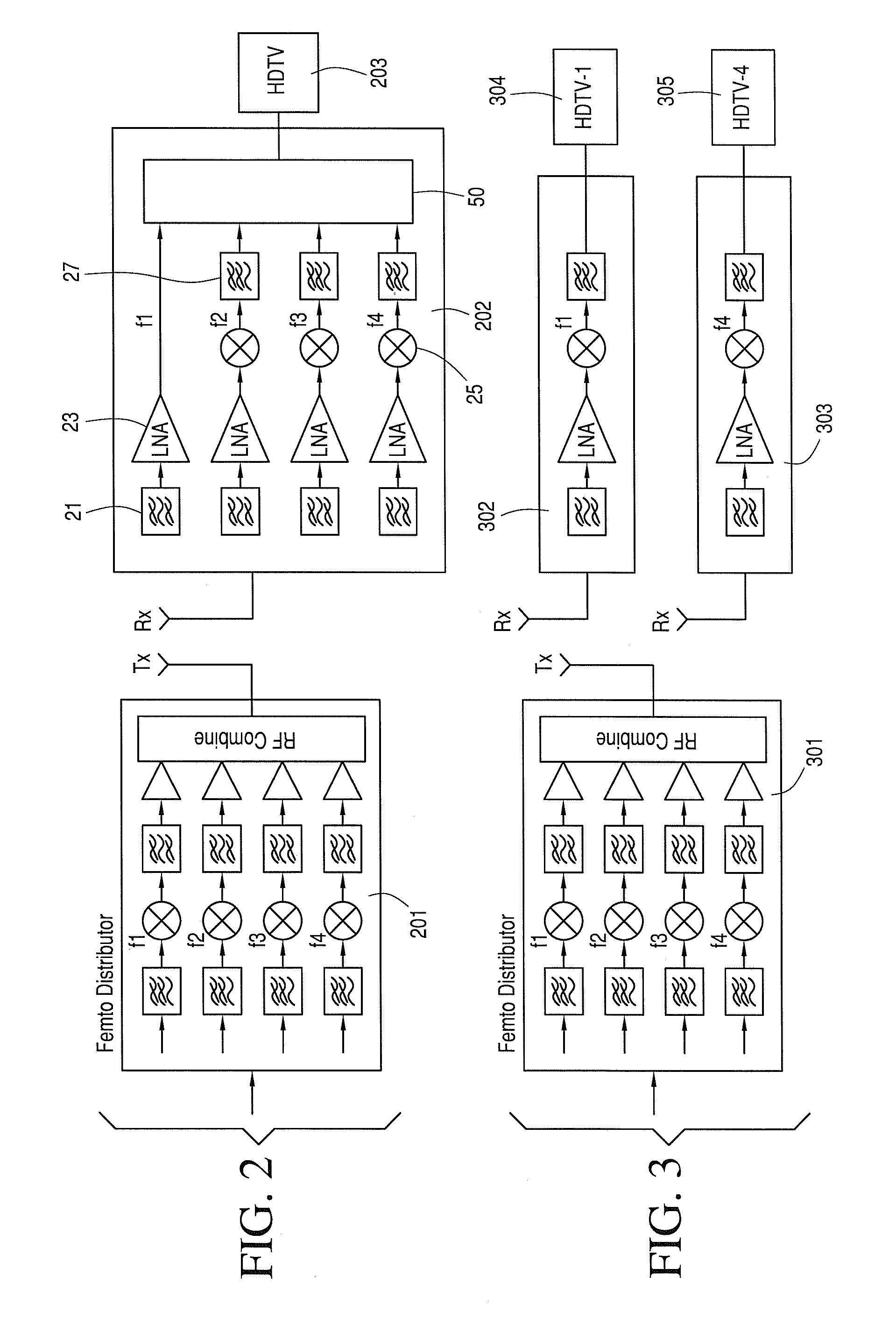
System and apparatus for cascading and redistributing HDTV signals
InactiveUS20120212628A1Change is minimalEffective wireless redistributionResource management arrangementsPlural information simultaneous broadcastFrequency spectrumVIT signals
Redistribution of multimedia signals or the like within a service area is performed by identifying one or more pieces of white space in the VHF / UHF spectrum, selecting a carrier frequency for each piece of white space spectrum, parsing the signal into a like number of components and modulating each component over a carrier frequency. The receiving device performs the reverse operation for reconstructing the signal.
Owner:TAIWAN SEMICON MFG CO LTD
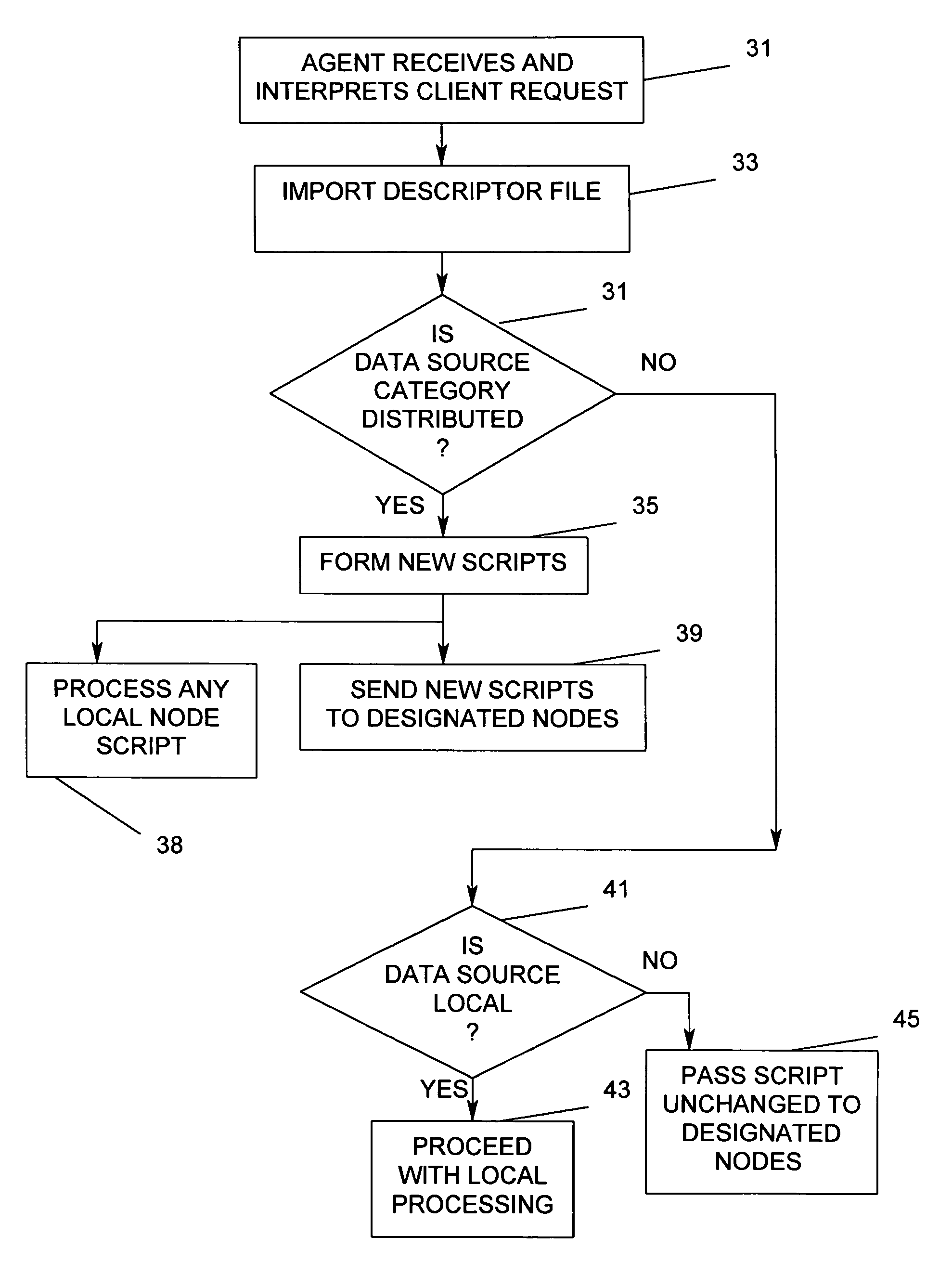
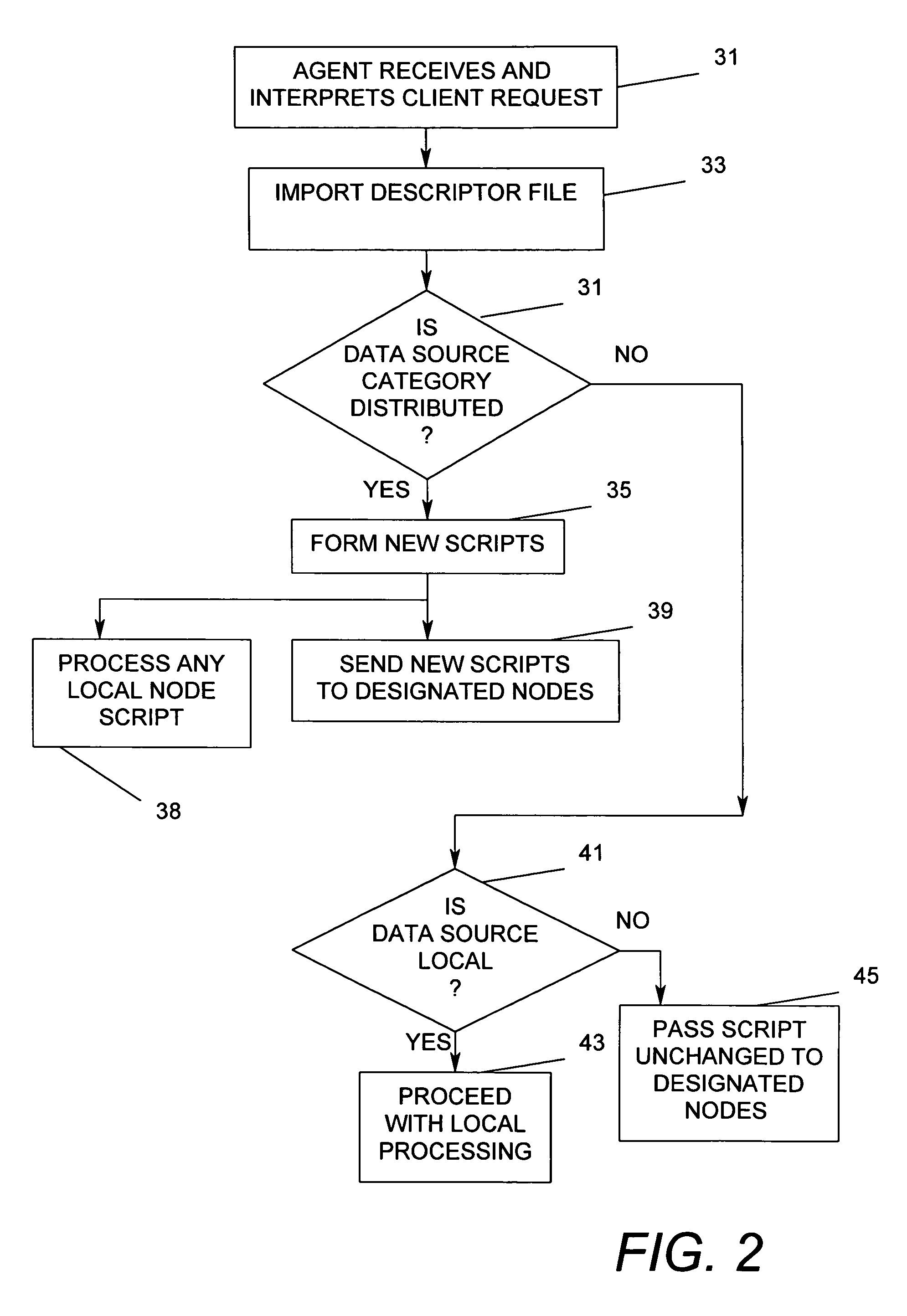
Method and apparatus for automatic execution of concatenated methods across multiple heterogeneous data sources
Heterogeneous data at a plurality of remote nodes is accessed automatically in parallel at high speed from a user site using a simple script request containing a data source object name wherein the heterogeneous data is treated as a single data source object, the script further containing at least one method to be performed on the data source object and at least a second method to be automatically performed on the results of executing the first method. A user site agent breaks the user-generated script into new scripts appropriate for execution at the remote nodes and determines whether the second method should be executed at the remote nodes or at the user site. A messenger process transmits the new scripts to the appropriate remote nodes where respective agent processes respond to automatically access the appropriate data and to automatically execute the specified methods.
Owner:UNISYS CORP
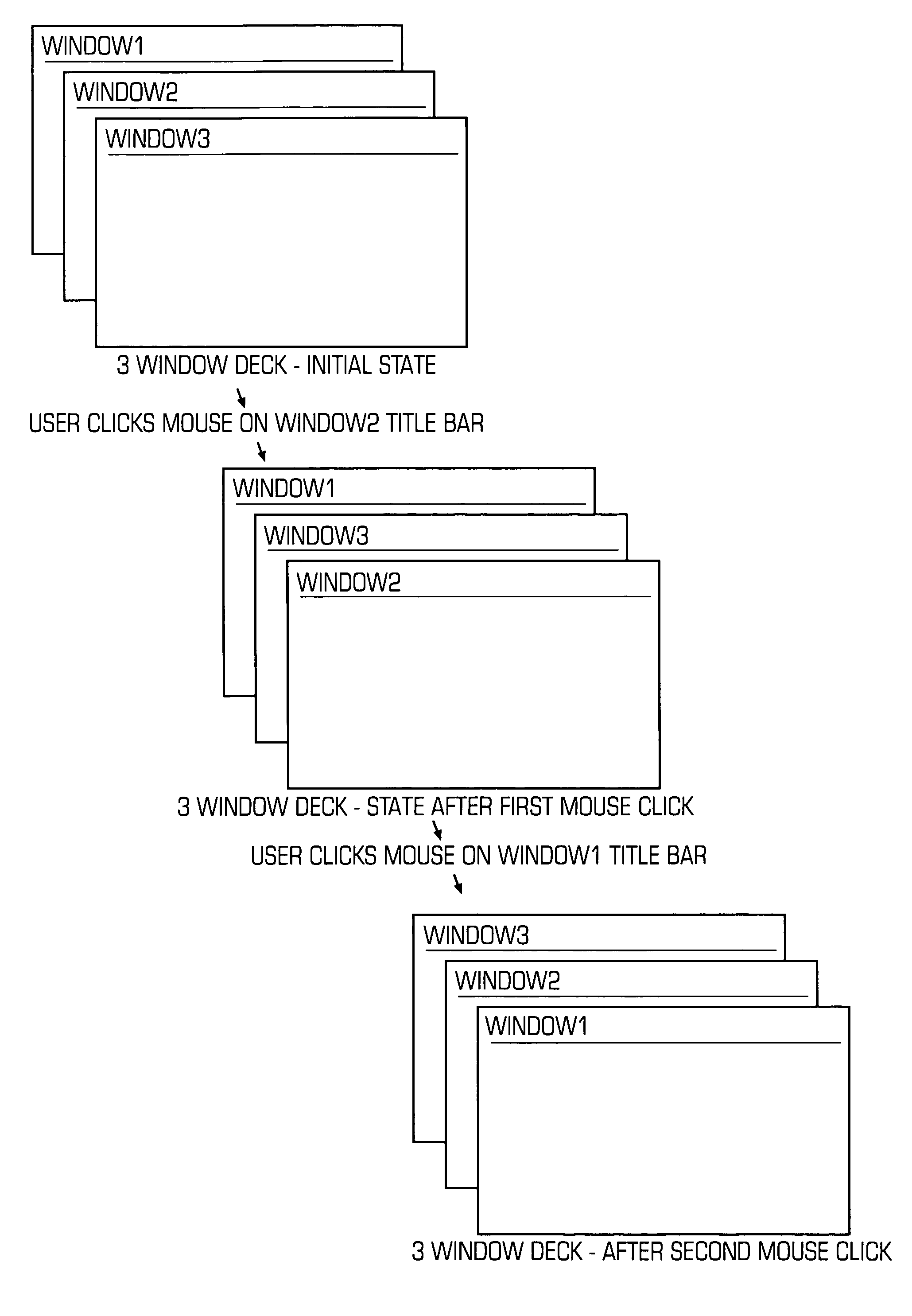
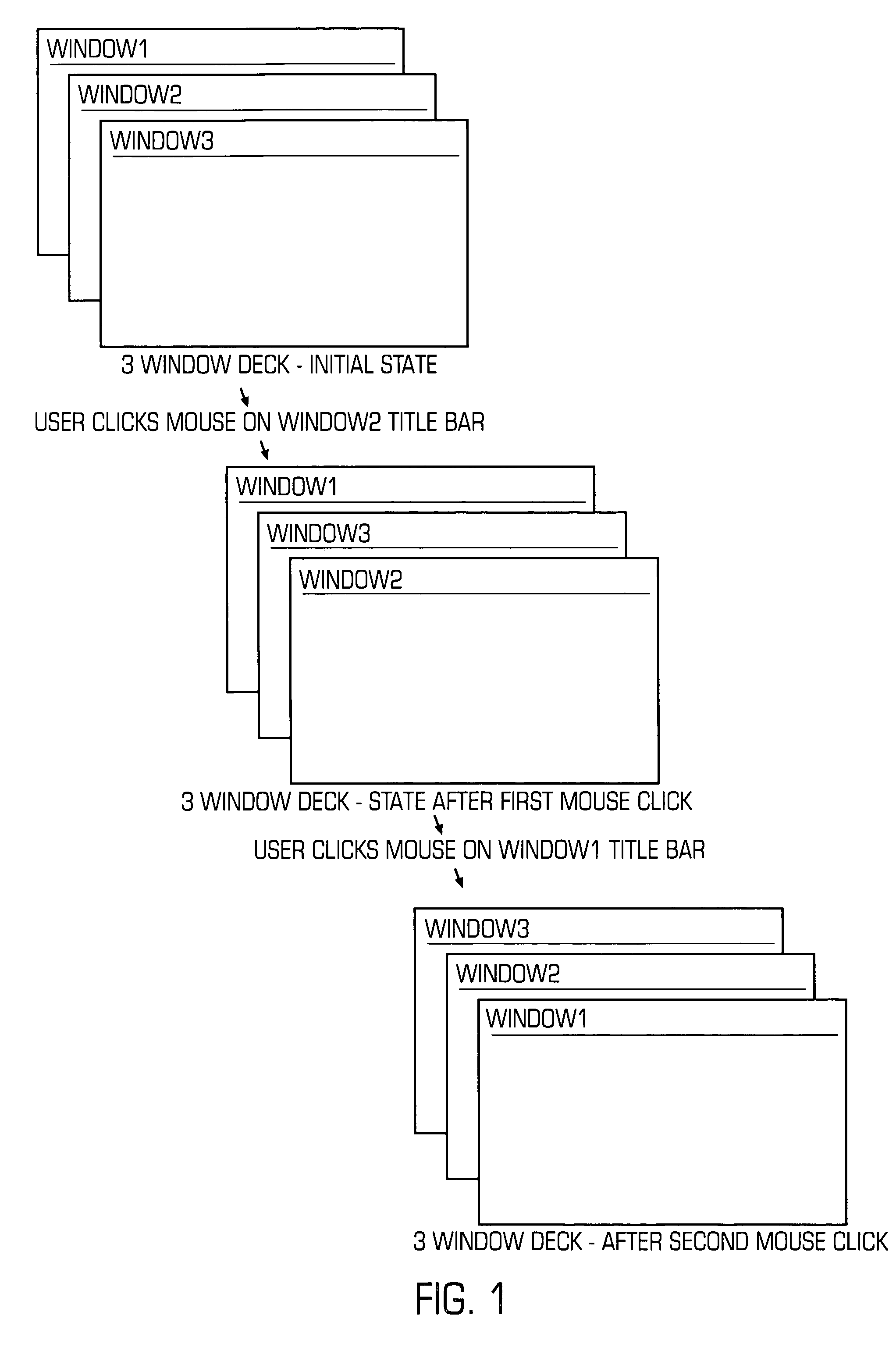
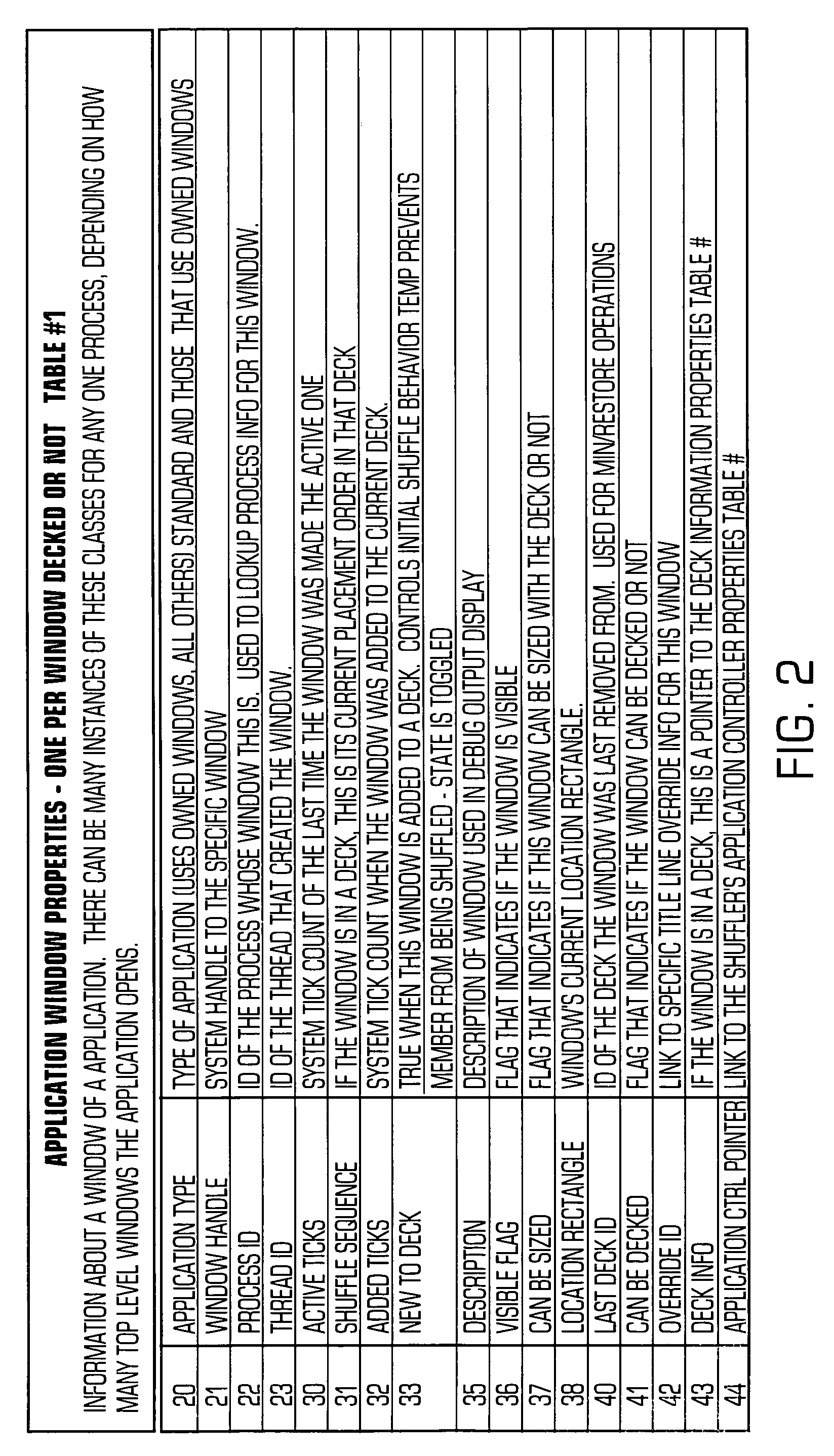
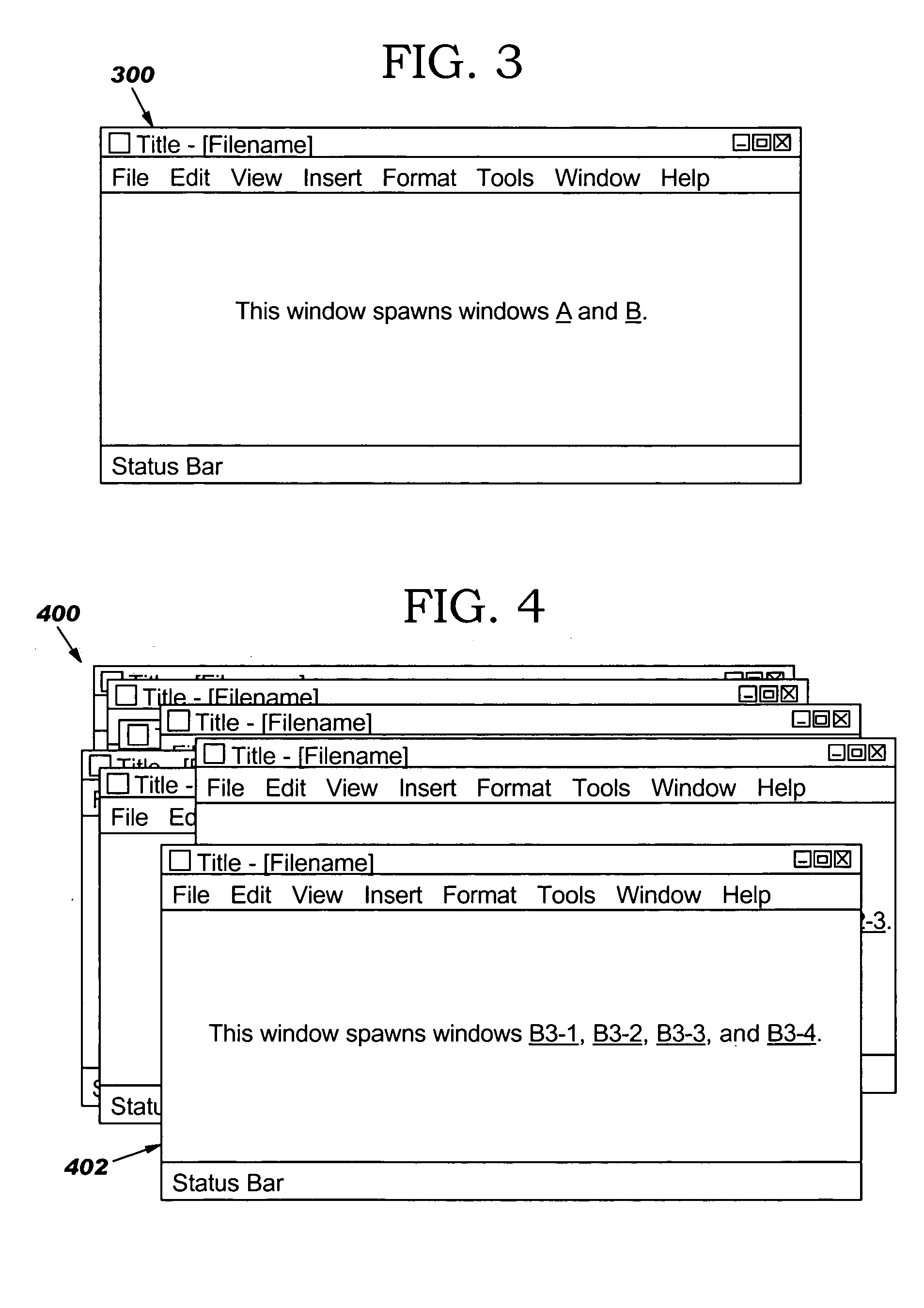
Method and system for controlling cascaded windows on a GUI desktop on a computer
ActiveUS7159189B2Automatic resizing of all windowsEasy and quick for userCathode-ray tube indicatorsInput/output processes for data processingThe InternetPlaying card
The present invention provides a method and system of maintaining and controlling the ordering and placement for display of individual GUI windows into groups or “decks” similar to a deck of playing cards on a desktop area of a computer display. The decks comprise collections of cascaded windows. The method and system control the decks such that the title bars of all windows of the deck are always simultaneously visible to the user no matter which window is selected as the active window. The act of moving the current top window back into a new position in the deck is defined as “shuffling” the windows. The method and system further provide auto-deck processes that automatically cascade defined applications, such as Internet Explorer windows, into a deck. In addition, the method and system may also include user-definable options as to the order of the shuffle, and includes the ability to drag the active window out of the deck and to drag any window into the deck. Also, the method and system may allow for the automatic resizing of all windows in a deck by just resizing the active window, and for a predetermined grouping of different applications into the same deck.
Owner:ALPHABASE SYST
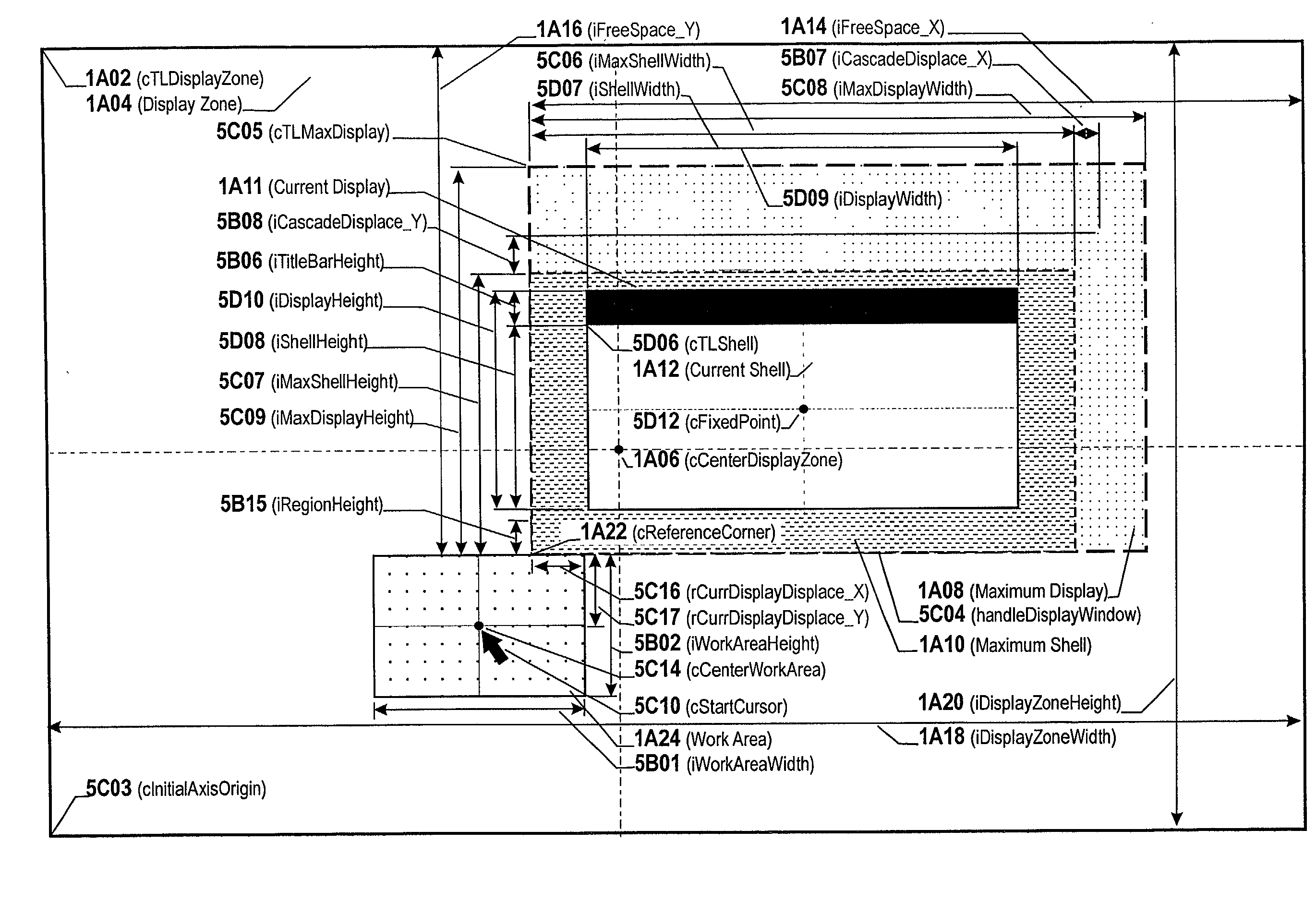
Method to display and manage computer pop-up controls
InactiveUS20030112278A1Cathode-ray tube indicatorsExecution for user interfacesHuman–machine interfaceReverse order
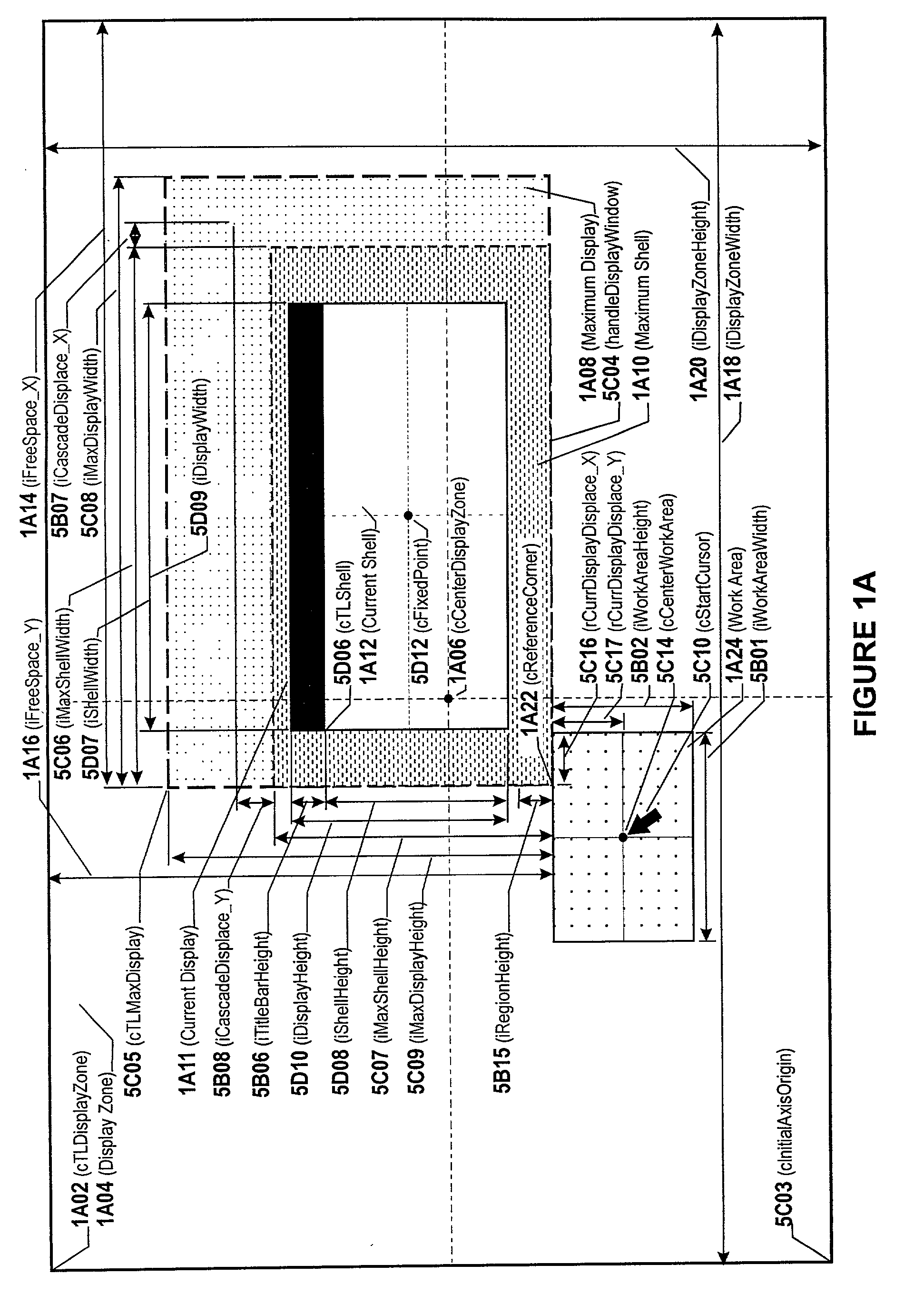
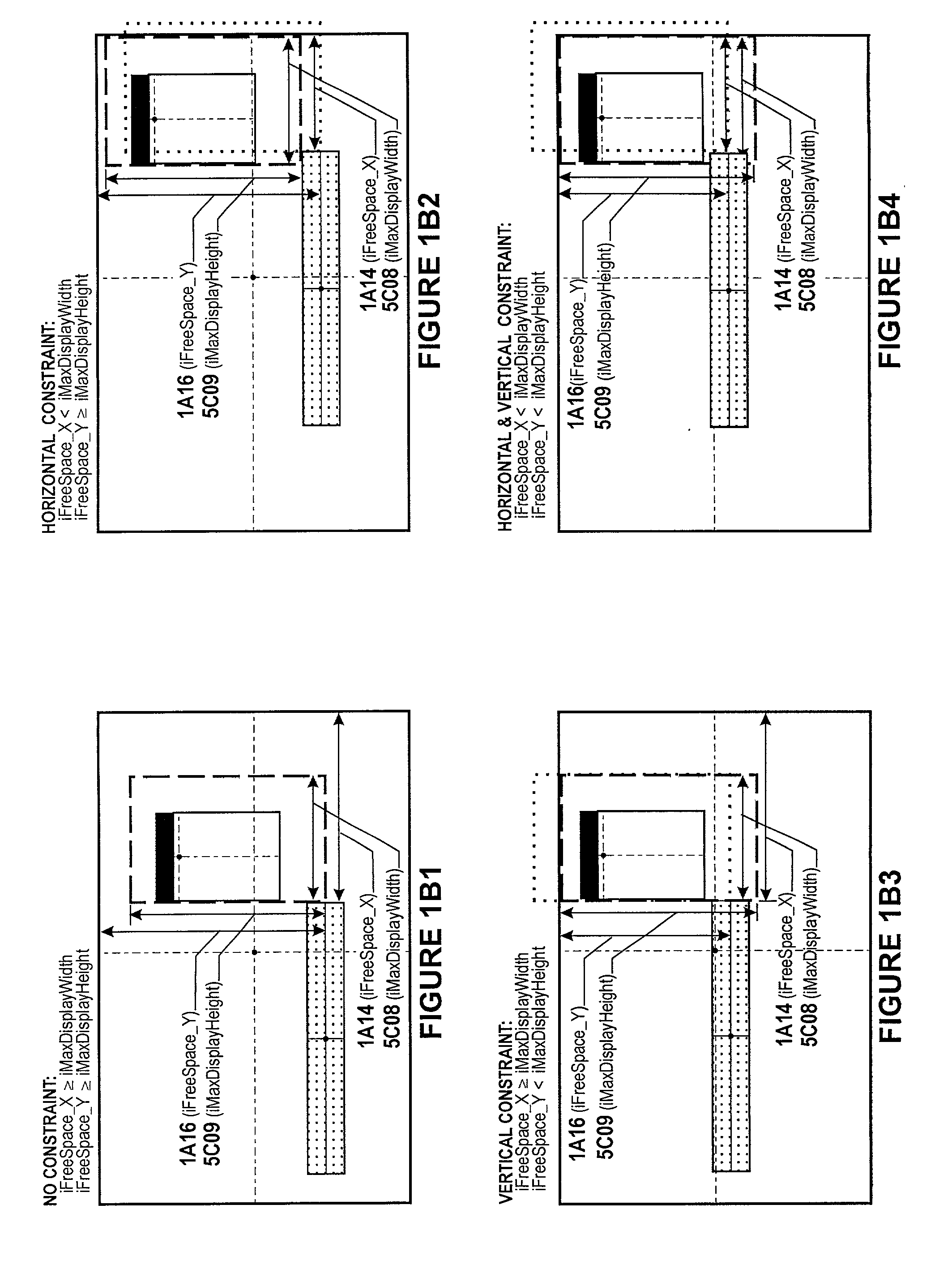
This invention enhances the usability of the human-computer interface by disclosing a technique for the display of single and multi-generation pop-up controls at a location that best meets the user's criterion of an optimal display location. The technique determines the minimum size of a rectangle capable of displaying the actual or likely maximum size of pop-up controls requested during any given activation of the subsystem that manages display of requested controls. The invention then identifies a location that assures the said rectangle either has no overlay or a minimum overlay of the screen area of current interest to the user while avoiding display clipping. A fixed-point is now determined within said rectangle based on physical characteristics of the controls to be displayed that permits display of descendant controls in a backward cascade that enables the user to maintain visual focus at a fixed screen location while manipulating successive controls. The invention provides the user with the ability to redisplay any previously displayed control irrespective of control type as well as provide a "Done" capability for appropriately designed controls that permits the user to convert a single selection control into a multi-selection control. As an adjunct to the reverse order the invention provides four capabilities that permit the user to undo and redo arbitrary services via performed via redisplay of ancestor controls.
Owner:DRISKELL STANLEY W
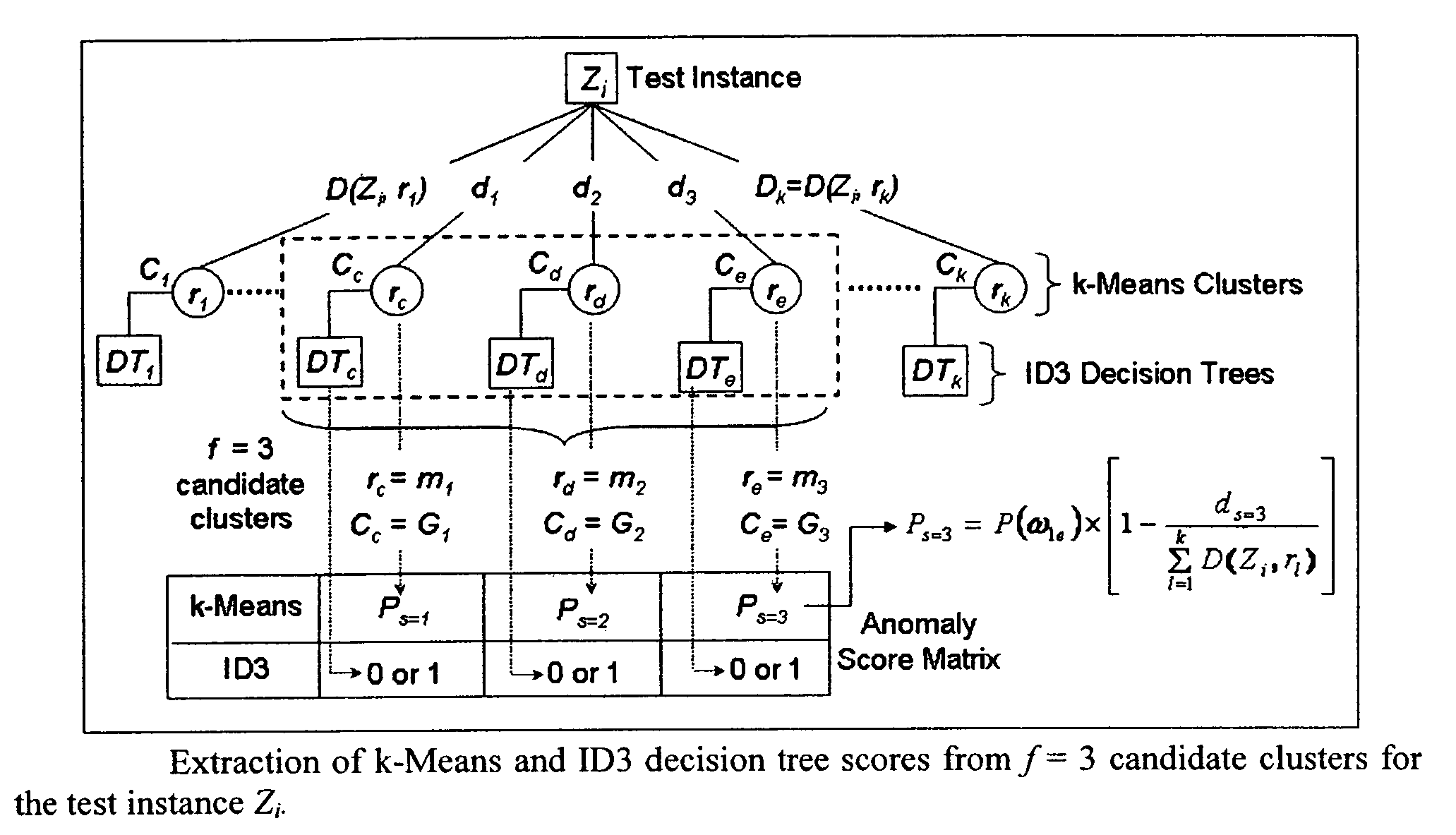
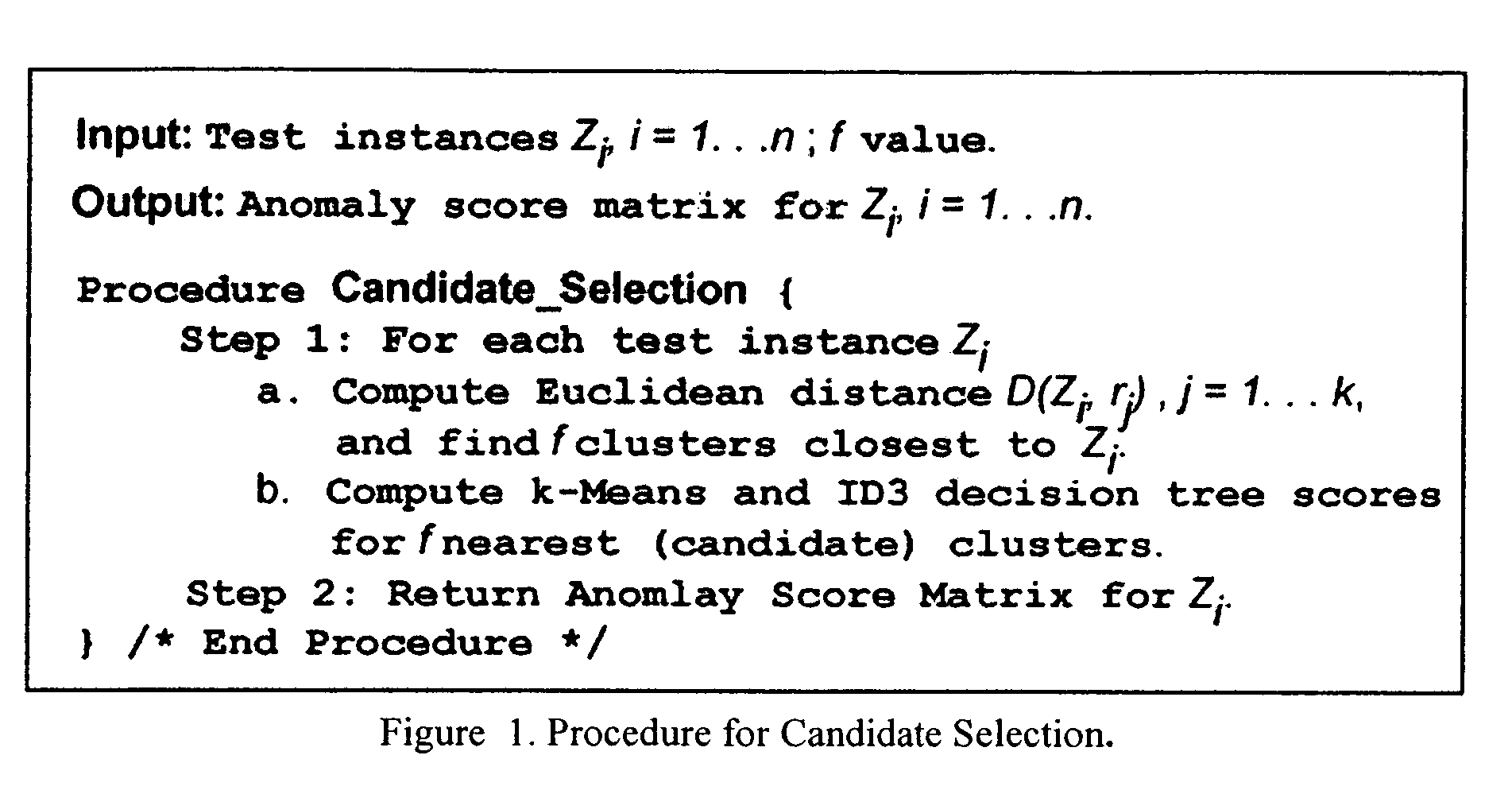
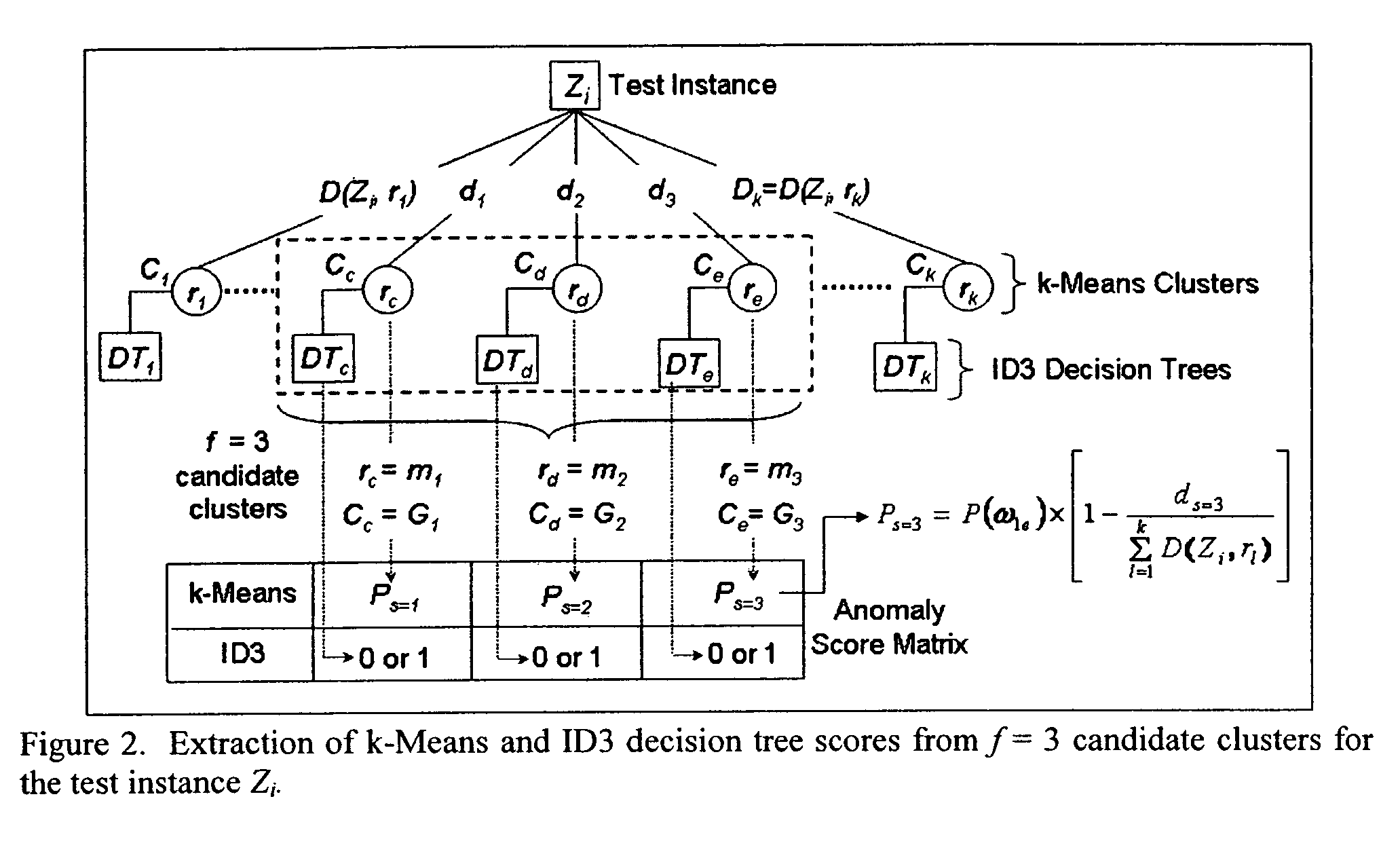
Method to indentify anomalous data using cascaded K-Means clustering and an ID3 decision tree
The invention is a computer implemented technique for id entifying anomalous data in a data set. The method uses cascaded k-Means clustering and the ID3 decision tree learning methods to characterize a training data set having data points with known characterization. The k-Means clustering method first partitions the training instances into k clusters using Euclidean distance similarity. On each training cluster, representing a density region of normal or anomaly instances, the invention builds an ID3 decision tree. The decision tree on each cluster refines the decision boundaries by learning the sub-groups within the cluster. A test data point is then subjected to the clustering and decision trees constructed form the training instances. To obtain a final decision on classification, the decisions of the k-Means and ID3 methods are combined using rules: (1) the Nearest-neighbor rule, and (2) the Nearest-consensus rule.
Owner:LOUISIANA TECH RES CORP
Use of a bulk-email filter within a system for classifying messages for urgency or importance
InactiveUS7565403B2Diminishing its filtering abilityIncrease powerProgramme controlData processing applicationsCombined useElectronic mail
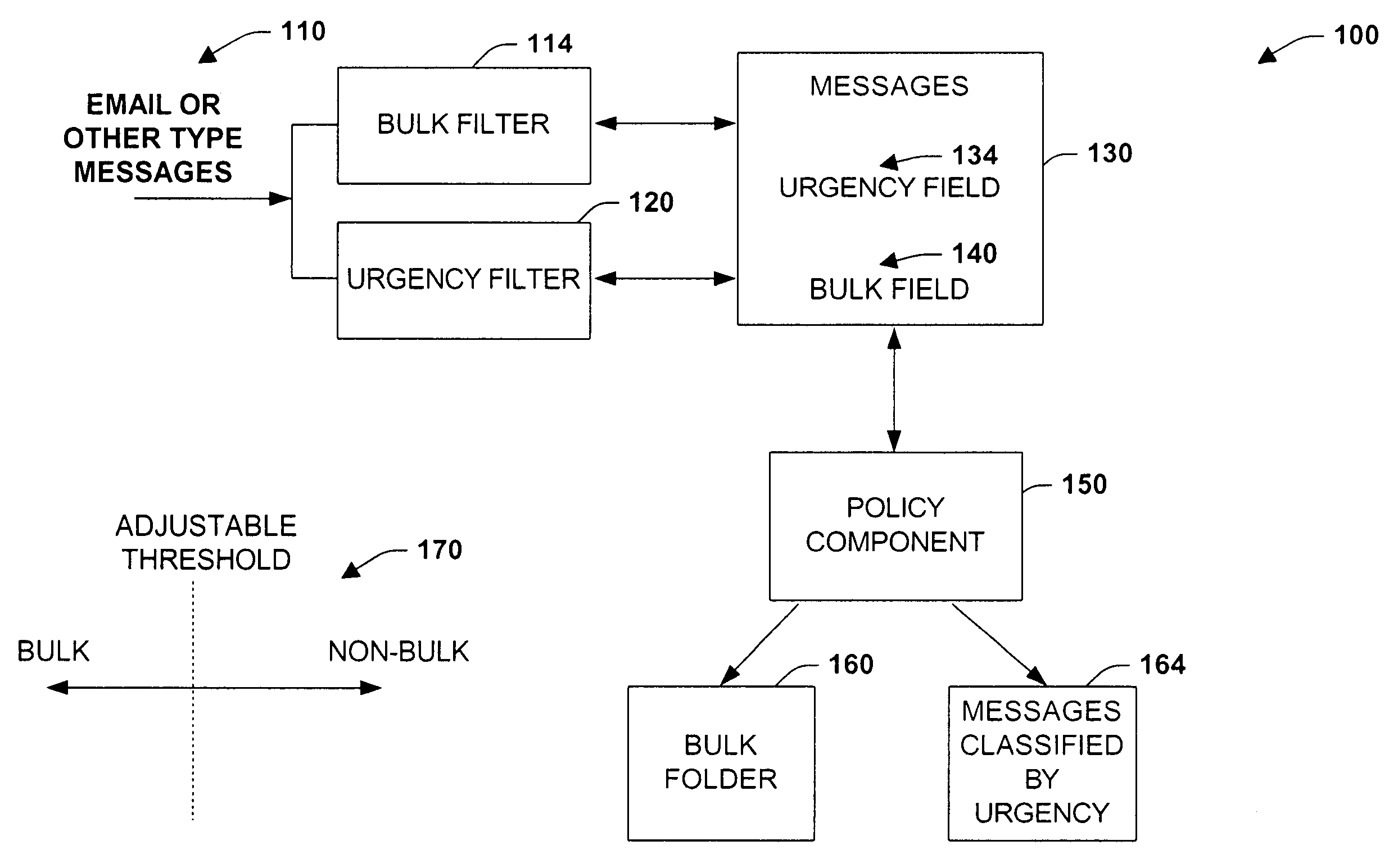
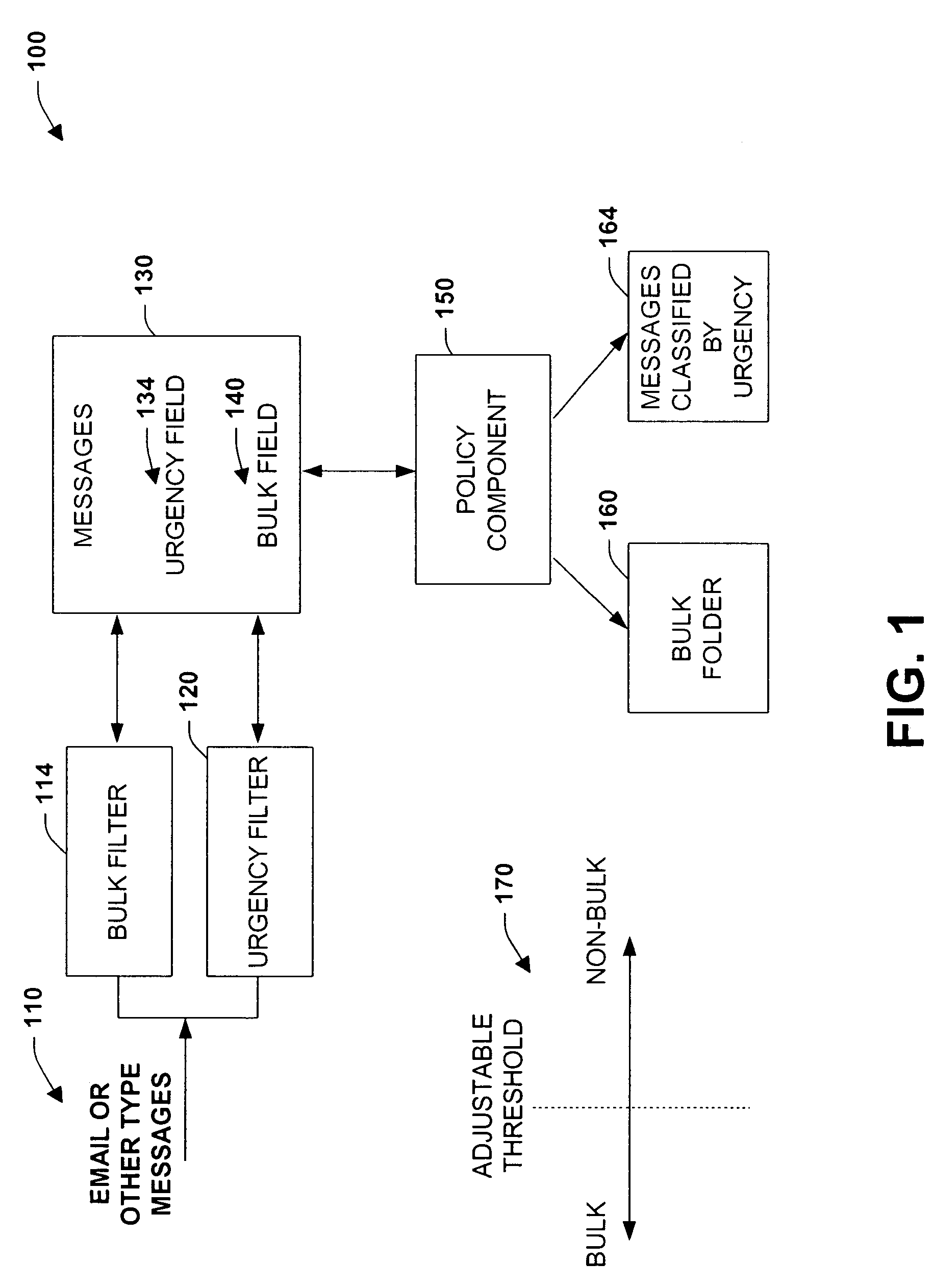
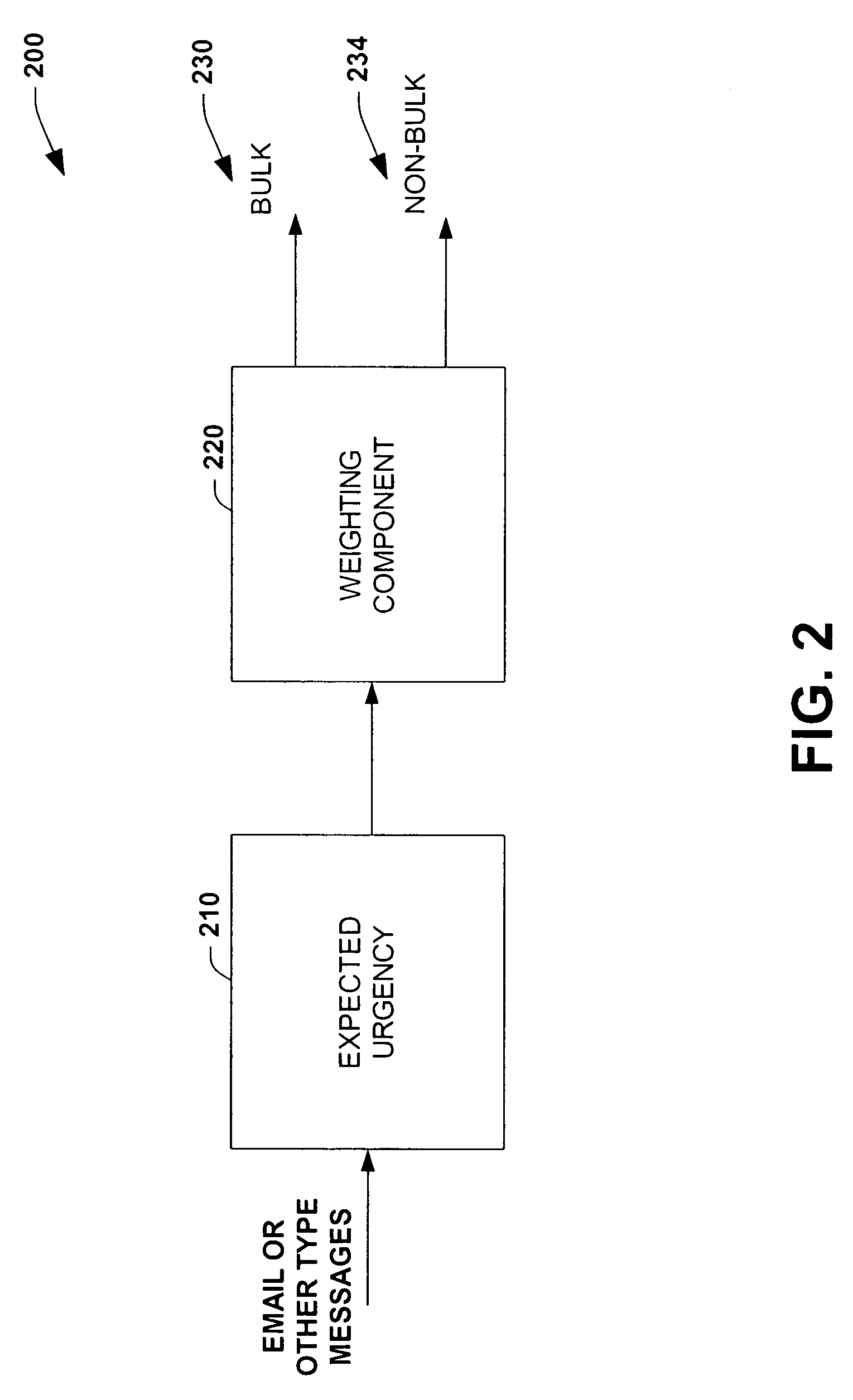
The present invention relates to a system and method to facilitate efficient and automated processing of messages. A bulk filter is provided to categorize one or more received messages according to a range of classification, the range spanning from at least a bulk classification of values to at least a non-bulk classification of values. A second filter is provided to further classify the received messages in order to automatically facilitate processing of the messages. The range of classification includes a continuum of values based on a likelihood that the received messages are determined to tend toward or fall within the bulk classification of values or toward / within the non-bulk classification of values. Also, the bulk filter or filters can include an adjustable threshold setting to determine or define differences between the bulk classifications and the non-bulk classifications. Various combinations of filters are possible including multiple filter arrangements, parallel arrangements, cascaded arrangements, and other arrangements to facilitate filtering and sorting of messages in order that users can more efficiently process such information in a timely manner. Applications include the enhancement of classification procedures for identifying urgent or important email from non-urgent or non-important email, with the combination of bulk-email filters with urgency or importance filters in cascaded and parallel filtering methodologies.
Owner:MICROSOFT TECH LICENSING LLC
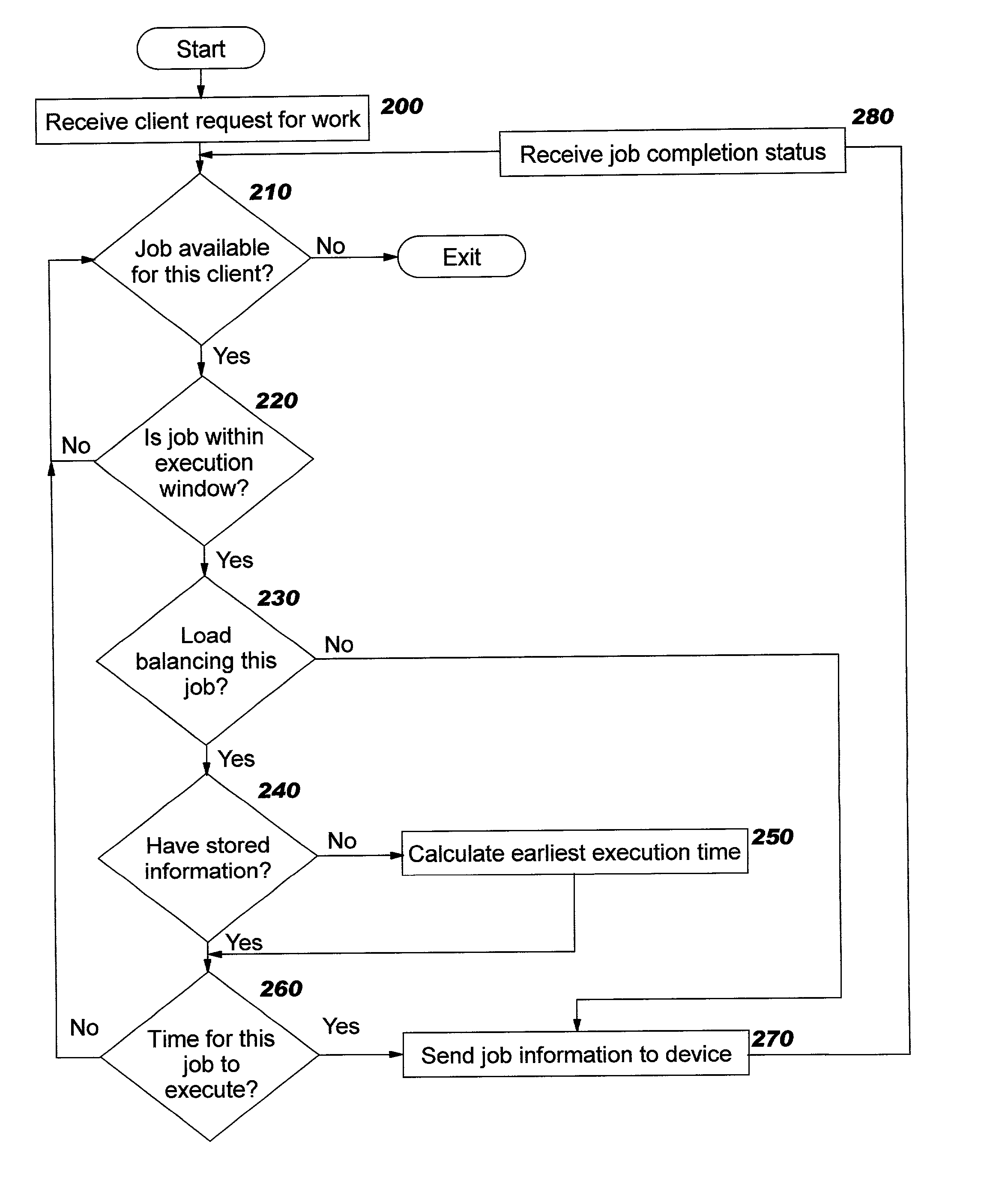
Technique for scheduling execution of jobs for or by network-connected devices
ActiveUS20020198923A1Limitations of prior art device management systems are avoidedAvoid restrictionsResource allocationMemory systemsCascading failureStart time
Methods, systems, computer program products, and methods of doing business by improving the scheduling of execution of jobs for or by network-connected devices, thereby enabling the job execution process to scale more easily, efficiently, and effectively to support large numbers of devices and / or users. Examples of jobs include, but are not limited to, distribution of resources (including software, configuration information, images, and other types of content) to a device, fetching a device's inventory information, backing up a device's contents, and so forth. Jobs are programmatically scheduled based upon a specified time internal, according to a class of the requester. Only if an earliest start time after which the job may be executed for this requester has been reached will the job be executed; otherwise, the job execution is delayed. The disclosed techniques lessen the need for additional servers to handle spikes in processing load, reduce the likelihood of reaching system overload, and reduce the likelihood of cascading failures that may occur when systems are overloaded.
Owner:TWITTER INC
Methods and systems for a dynamic networked commerce architecture
InactiveUS20060095343A1Easy accessEasy to useDiscounts/incentivesBuying/selling/leasing transactionsClient-sideClient machine
One embodiment of the present invention provides systems and methods, which allow a more efficient shopping experience. A cascading commerce menu provides access to a plurality of product, service, and / or content categories. In one embodiment, the cascading commerce menu is stored on a client computer, thereby providing quick access to the menu.
Owner:LOCAL COM LTD
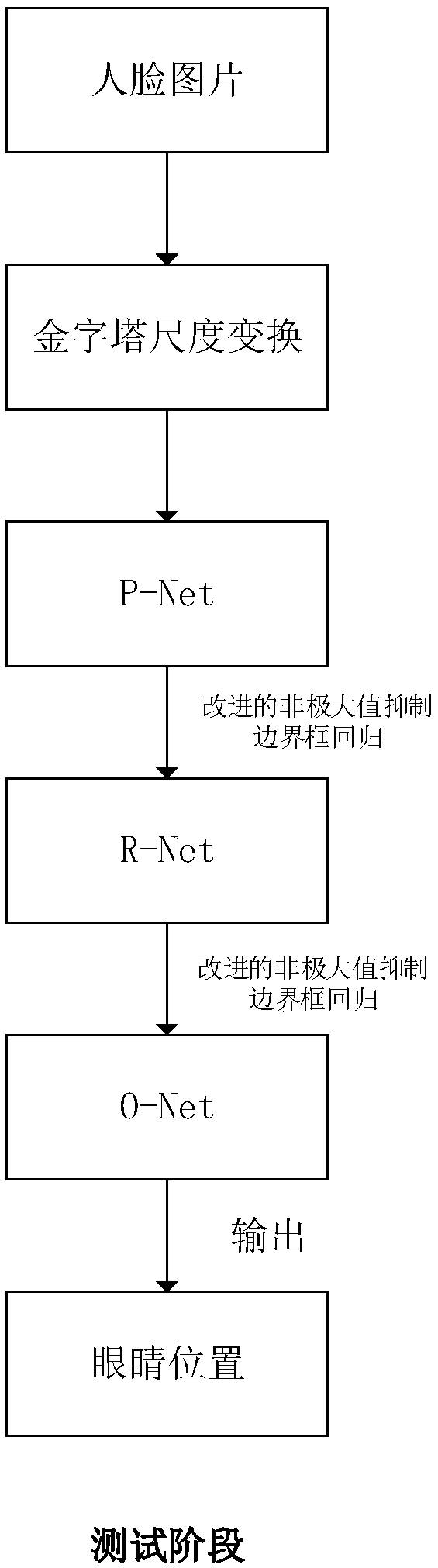
Multi-pose eye positioning algorithm based on cascaded convolutional neural network
InactiveCN107748858AGood effectEfficient multi-pose face detectionCharacter and pattern recognitionNeural learning methodsFace detectionNerve network
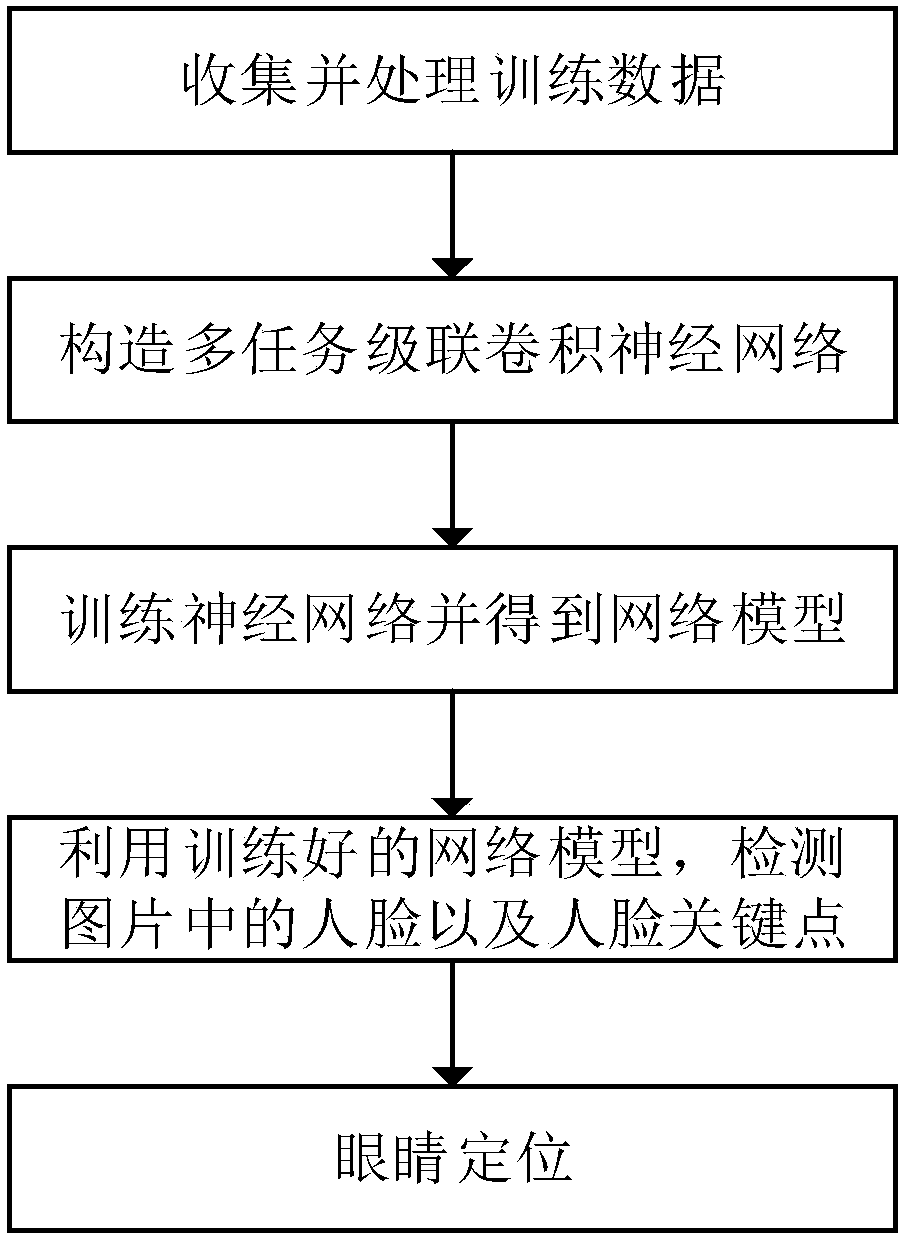
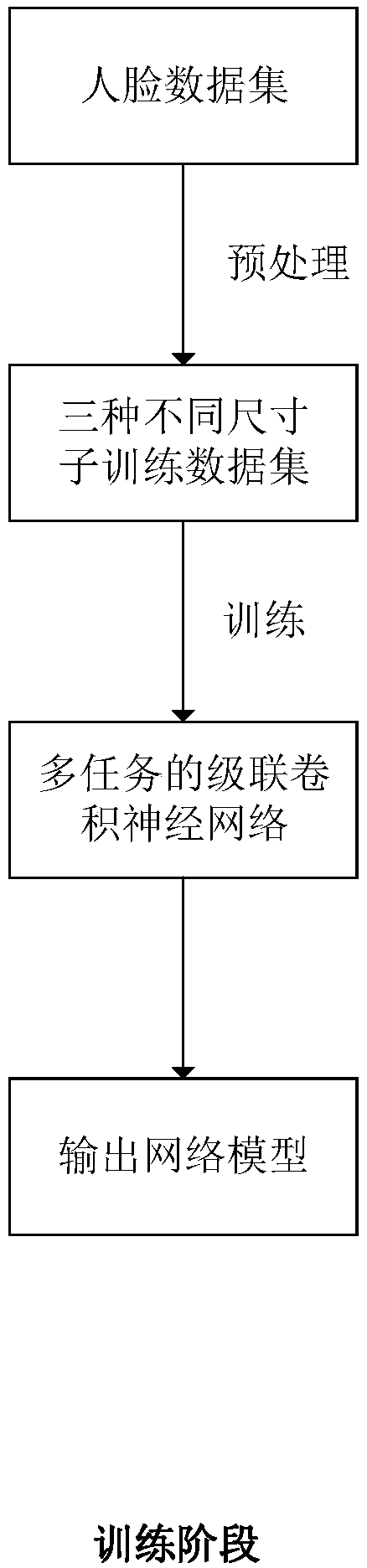
The invention discloses a multi-pose eye positioning algorithm based on the cascaded convolutional neural network, belongs to the machine learning and computer vision field and is suitable for intelligent systems such as face recognition, sight tracking and driver fatigue detection. The method comprises steps that face pictures marked with various types of information are collected to form a training data set; the multi-task cascaded convolutional neural network is constructed; the training data set is utilized to train the network to acquire a network model; and lastly, the network model is utilized to detect faces and face key points of the pictures, and the smallest rectangular box containing the eye key points is selected as the eye positioning result. The method is advantaged in thatthe multi-task cascading convolutional neural network is utilized to accomplish face detection and face key point detection, so the multi-pose eye positioning effect is obviously improved.
Owner:SOUTH CHINA UNIV OF TECH
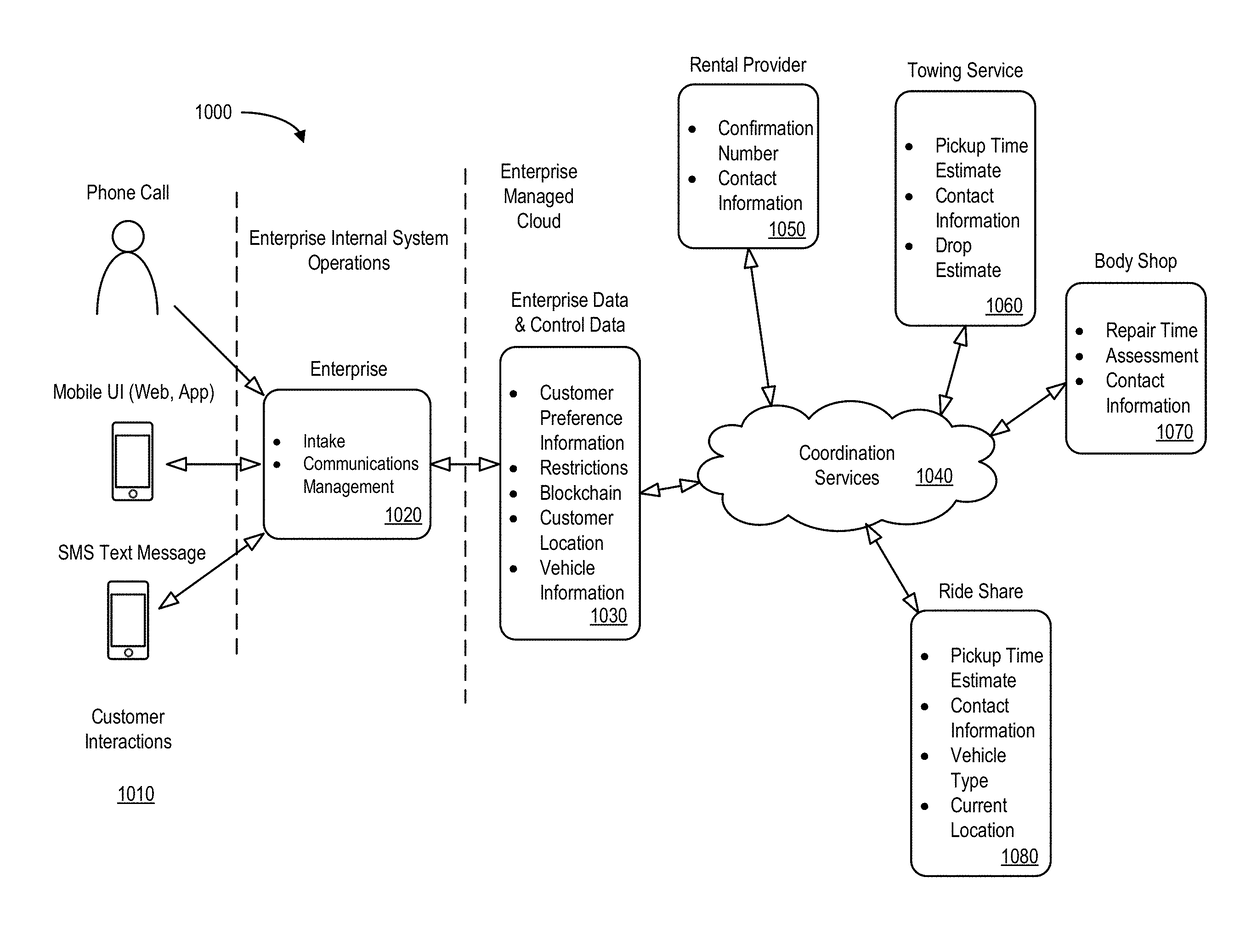
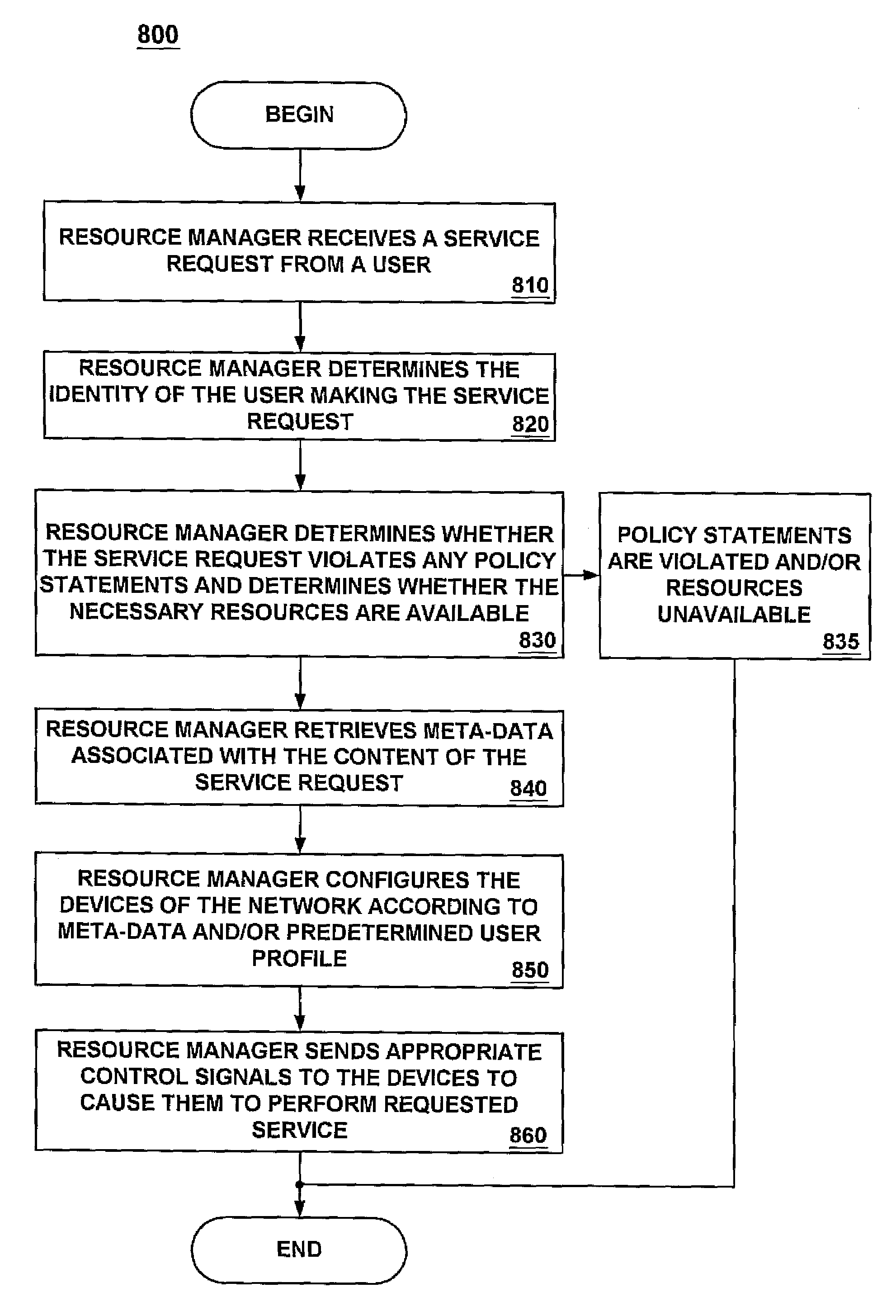
Automated service management system with rule-based, cascading action requests
InactiveUS20170220998A1Faster and efficient performanceFacilitate communicationFinanceOffice automationService product managementIT service management
A system may generate action requests for a service management system. A user preference data store may contain electronic records for a set of users, including, for example, at least one user preference value. A back-end application computer server may receive, from a remote user mobile device, an indication associated with an event. The server may then determine at least one location coordinate associated with the event and select a sub-set of service providers from a service provider data store based on the location and at least one user preference value. The server may generate an action request for a designated one of the sub-set of service providers in accordance with logic based rules and transmit information about the action request to the designated service provider and the remote user mobile device. The server may receive an action request update and transmit a modified action request to another service provider.
Owner:HORN GREGORY WILLIAM +1
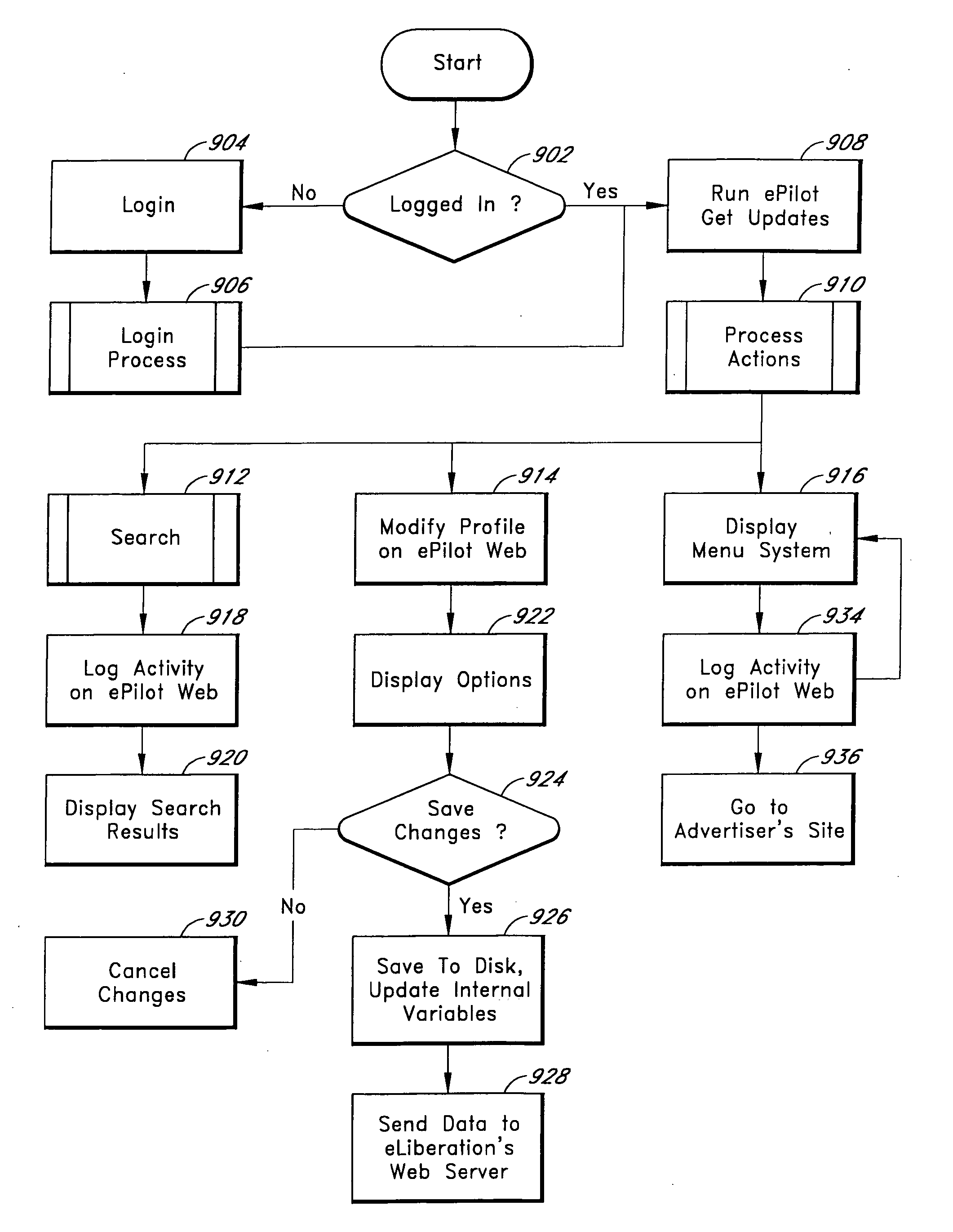
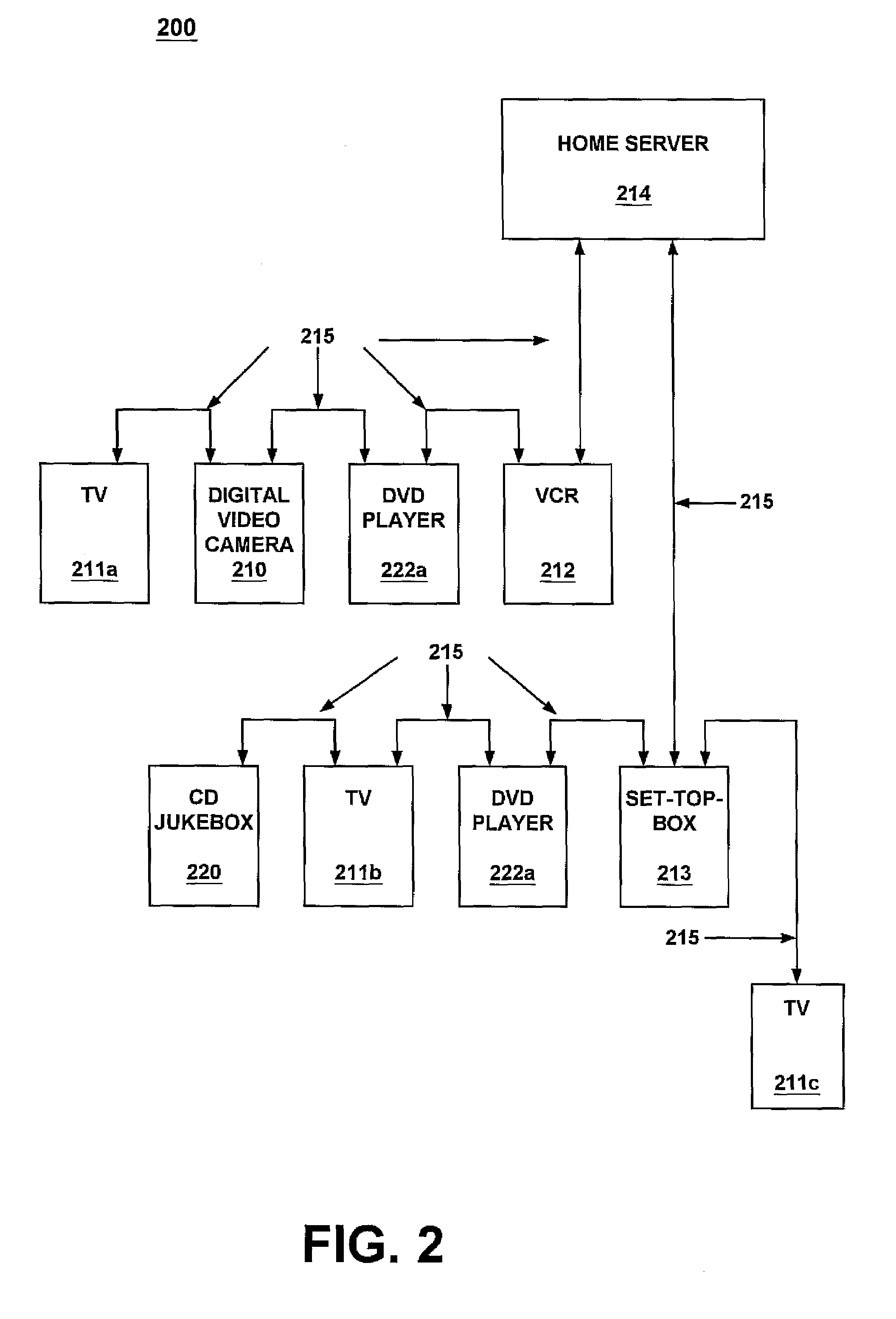
Request event manager and event lists for home and office systems and networks
InactiveUS7412538B1Multiple digital computer combinationsNetwork connectionsNetwork activityApplication software
A request event manager for a network of consumer electronic devices. In one embodiment, the request event manager maintains a database of home network services, and allows the home network services to be scheduled for execution over time. Home network services herein refer to high-level abstractions of a consumer electronic device's functionalities, and also content that is available from the consumer electronic device. The request event manager of the present invention also creates and maintains a service request list (SRL) which details the service actions in a hierarchical fashion. By maintaining a database of home network services, the request event manager of the present invention allows user applications to specify and schedule concatenated or hierarchical events such that different network activity across interconnected heterogeneous consumer electronic devices can be synchronized without requiring complicated logic to be implemented. The request event manager of the present invention may be implemented as part of a middleware infrastructure for a home network, and may reside within a home server.
Owner:SONY CORP +1
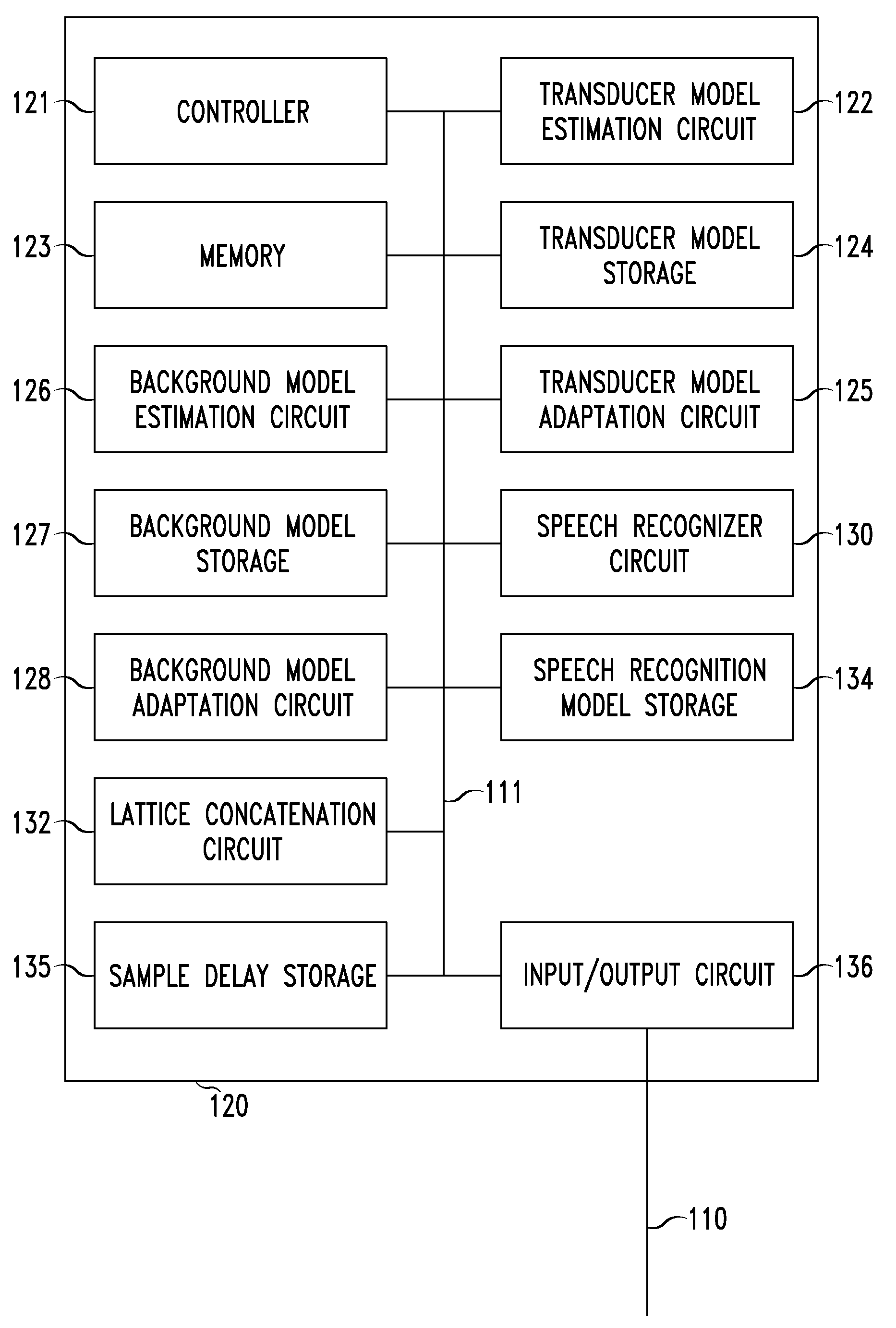
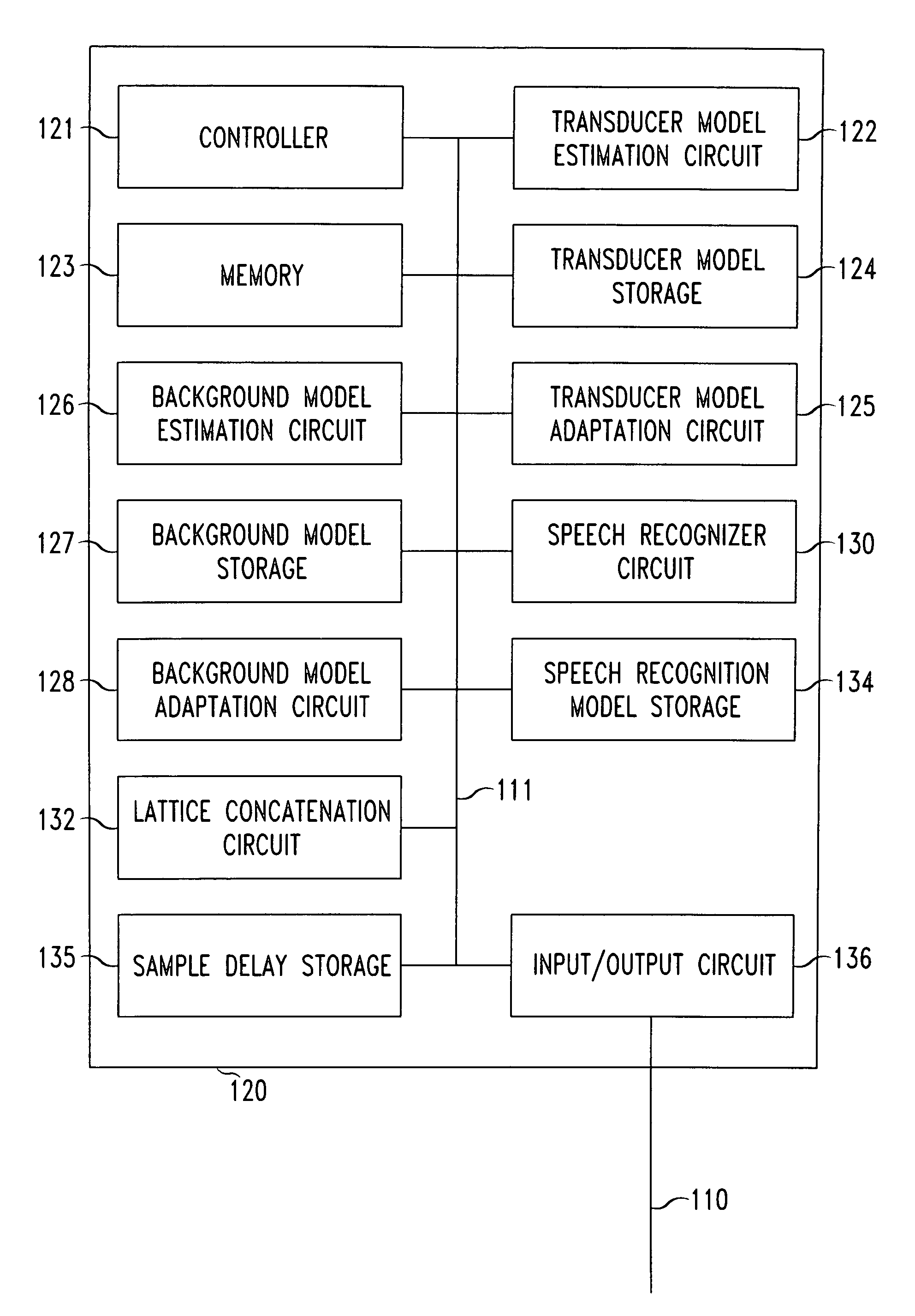
Systems and methods for dynamic re-configurable speech recognition
ActiveUS7209880B1Digital computer detailsNatural language data processingData fieldBackground information
Speech recognition models are dynamically re-configurable based on user information, application information, background information such as background noise and transducer information such as transducer response characteristics to provide users with alternate input modes to keyboard text entry. Word recognition lattices are generated for each data field of an application and dynamically concatenated into a single word recognition lattice. A language model is applied to the concatenated word recognition lattice to determine the relationships between the word recognition lattices and repeated until the generated word recognition lattices are acceptable or differ from a predetermined value only by a threshold amount. These techniques of dynamic re-configurable speech recognition provide for deployment of speech recognition on small devices such as mobile phones and personal digital assistants as well environments such as office, home or vehicle while maintaining the accuracy of the speech recognition.
Owner:NUANCE COMM INC
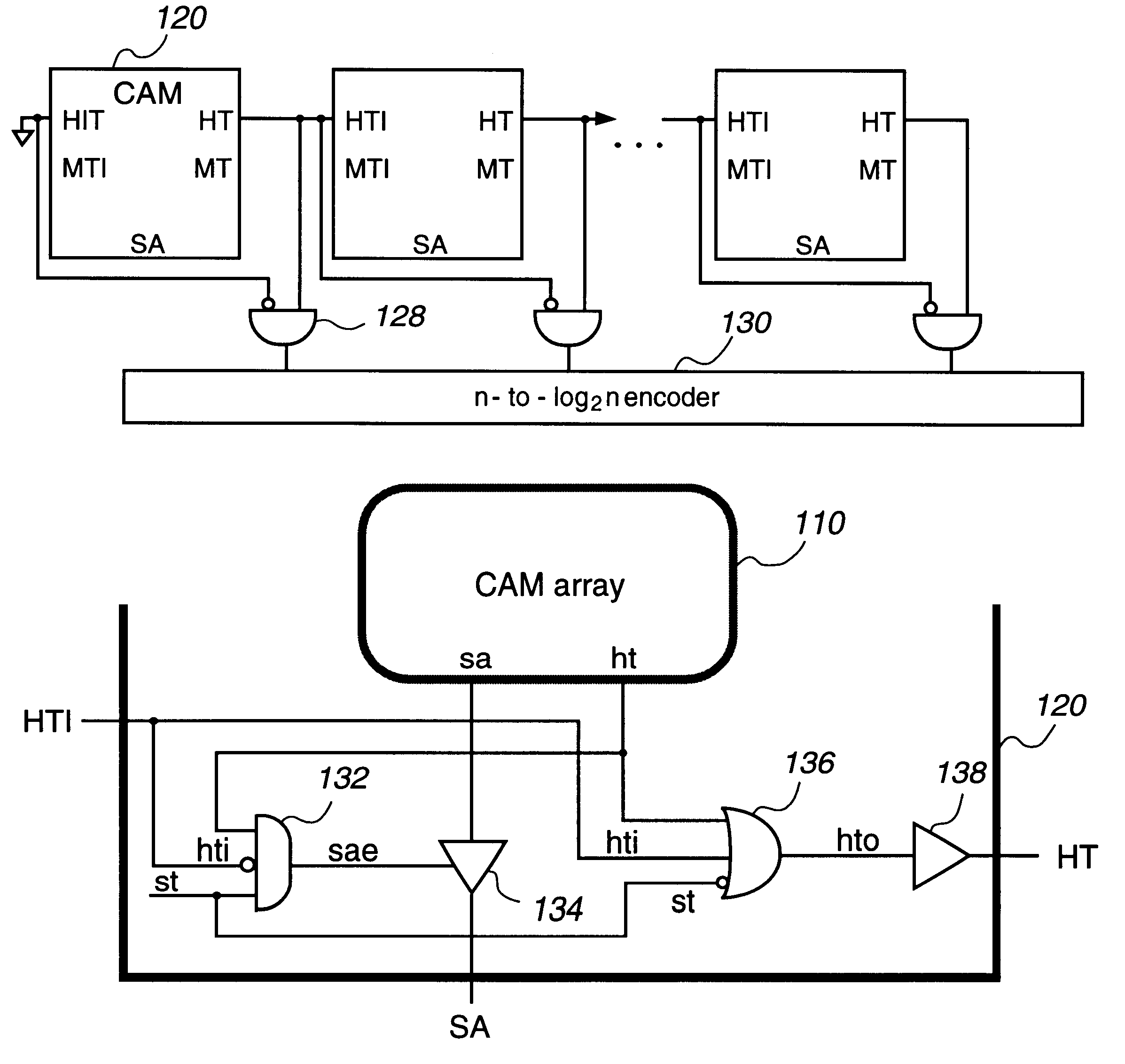
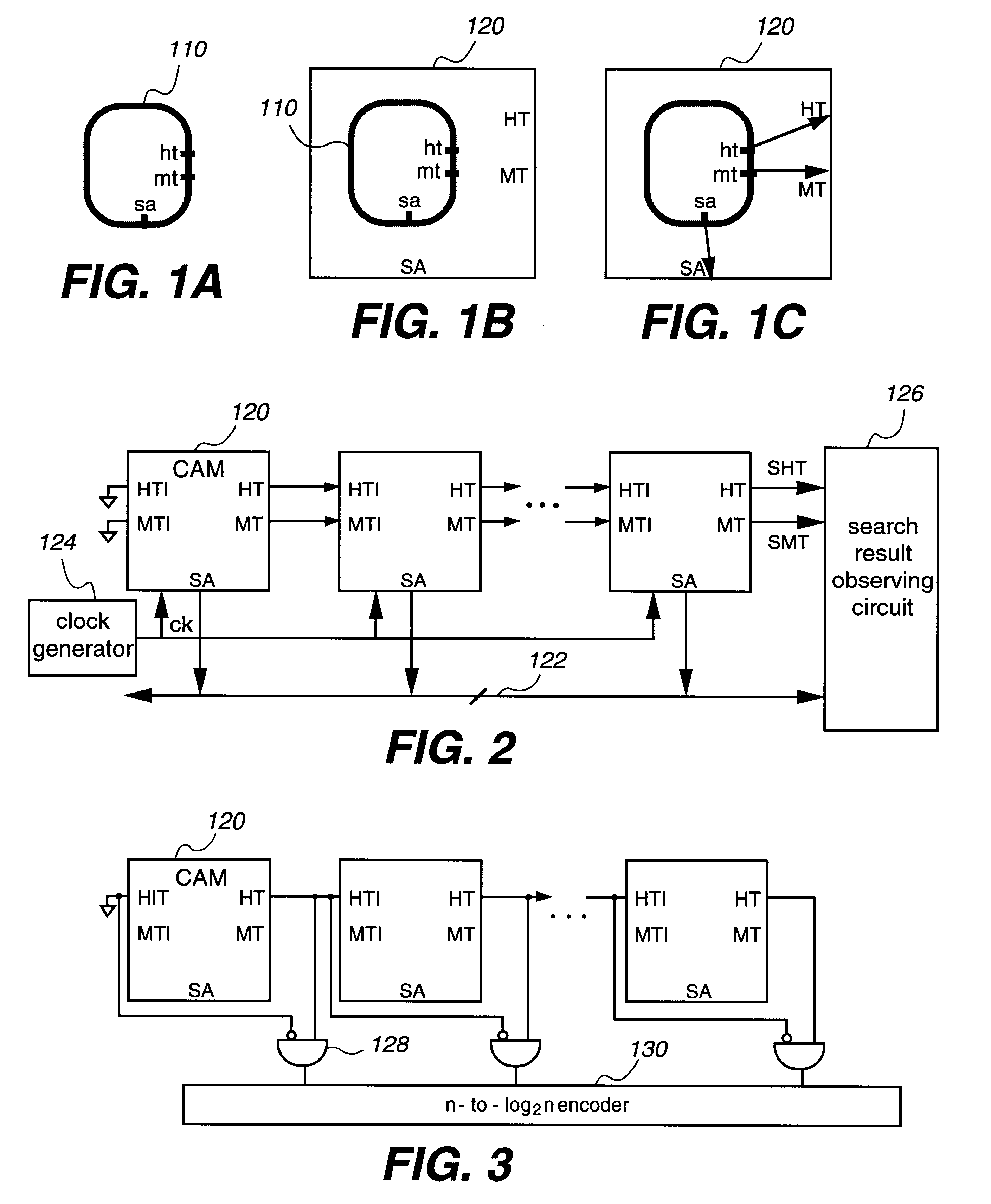
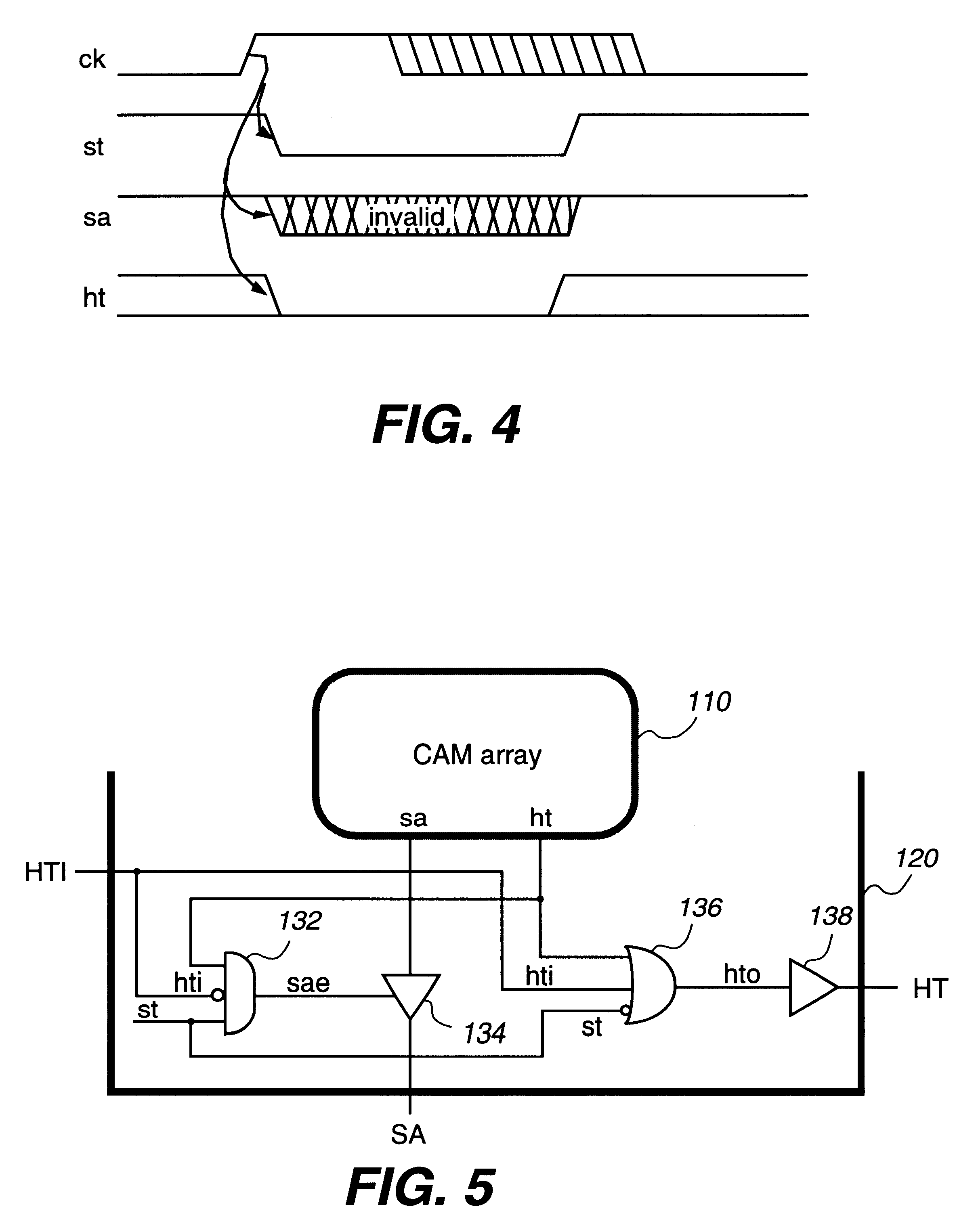
Content addressable memory system with cascaded memories and self timed signals
InactiveUS6301636B1Memory adressing/allocation/relocationDigital storageHemt circuitsSignal generator
A system includes cascaded content addressable memory (CAM) chips connected to a common bus. Each CAM chip includes a CAM array, a self-timed signal generator and hit propagation and match address transfer circuits. Each CAM array including an array of core cells provides, through its encoder, hit and match address signals resulting from a search operation in response to a clock signal. Each match address transfer circuit transfers the match address signal to the common bus, in response to a self-timed signal, the hit signal and a propagation-in hit signal provided from an upstream CAM chip, so that more than one CAM chip is prevented from providing the match address signal to the common bus simultaneously. Each hit propagation circuit provides a propagation-out hit signal to a downstream CAM chip, in response to the self-timed signal, the hit signal and the propagation-in hit signal from the upstream CAM chip, so that a hit signal is propagated from an upstream CAM chip to a downstream CAM chip. Each CAM chip may include an extra row for providing a modelmiss signal or a modelhit signal which is used for a generating self-timed signal. Each word may be divided into two halves and two match lines of the two halves are coupled by a logic circuit. The system may also observe a multiple match status and the highest priority chip indicating a match.
Owner:FOOTHILLS IP LLC +1
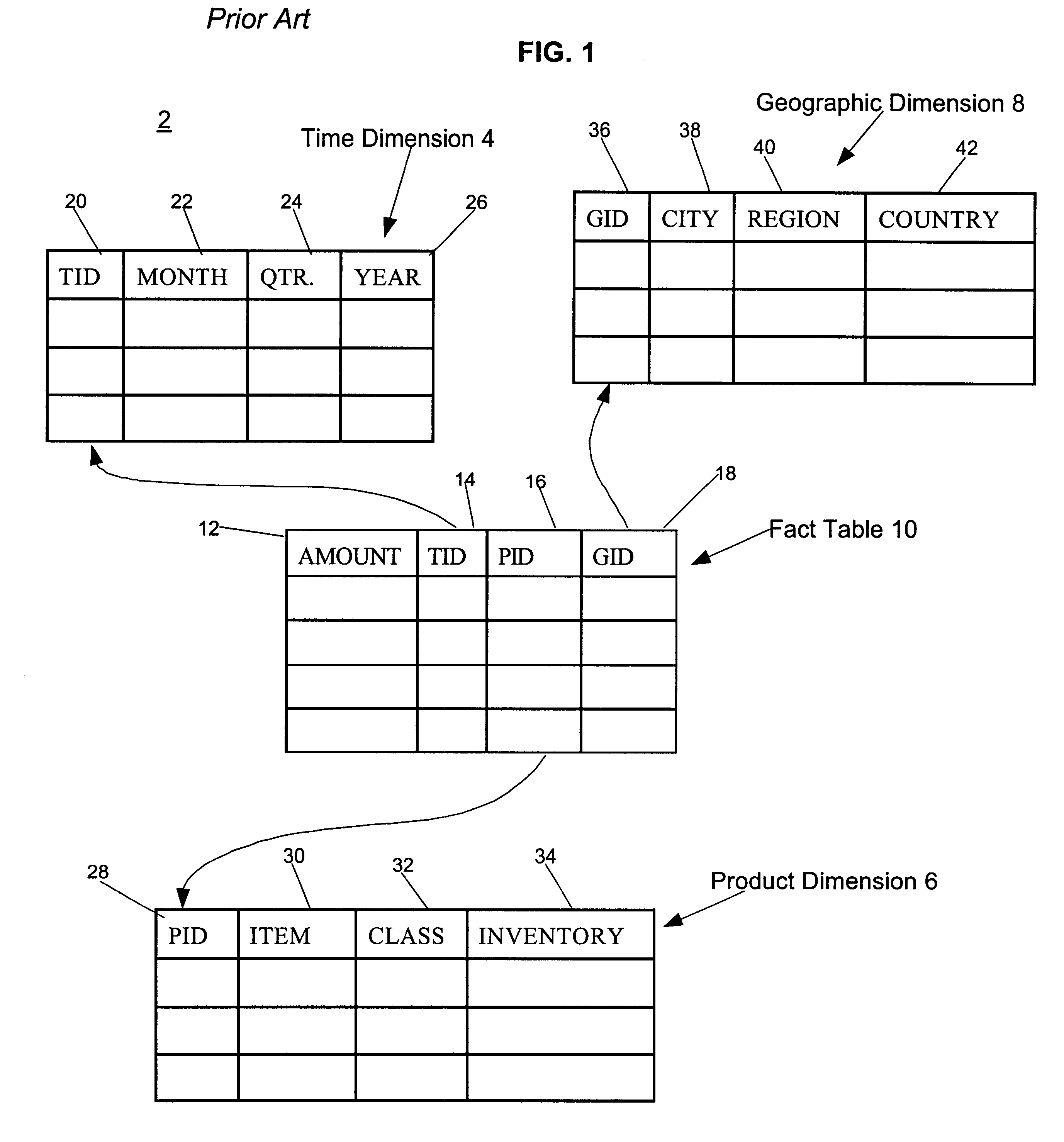
Method, system, and program for performing a join operation on a multi column table and satellite tables
InactiveUS6446063B1Avoid searchingData processing applicationsDigital data information retrievalConcatenationComputer science
Disclosed is a system, method, and program for performing a join operation on a multi-column table and at least two satellite tables having a join condition. Each satellite table is comprised of multiple rows and at least one join column. Each multi-column table is comprised of multiple rows and at least one column corresponding to the join column in each satellite table. A join operation is performed on the rows of the satellite tables to generate a first join result comprising concatenations of the rows of the satellite tables. Less than all the concatenated rows in the first join result that satisfy the join condition are then selected. The selected concatenated rows in the first join result are then joined to the multi-column table.
Owner:IBM CORP
Accounting allocation method
InactiveUS6014640AQuantity minimizationEasy and efficient implementationComplete banking machinesFinanceDistribution methodParallel computing
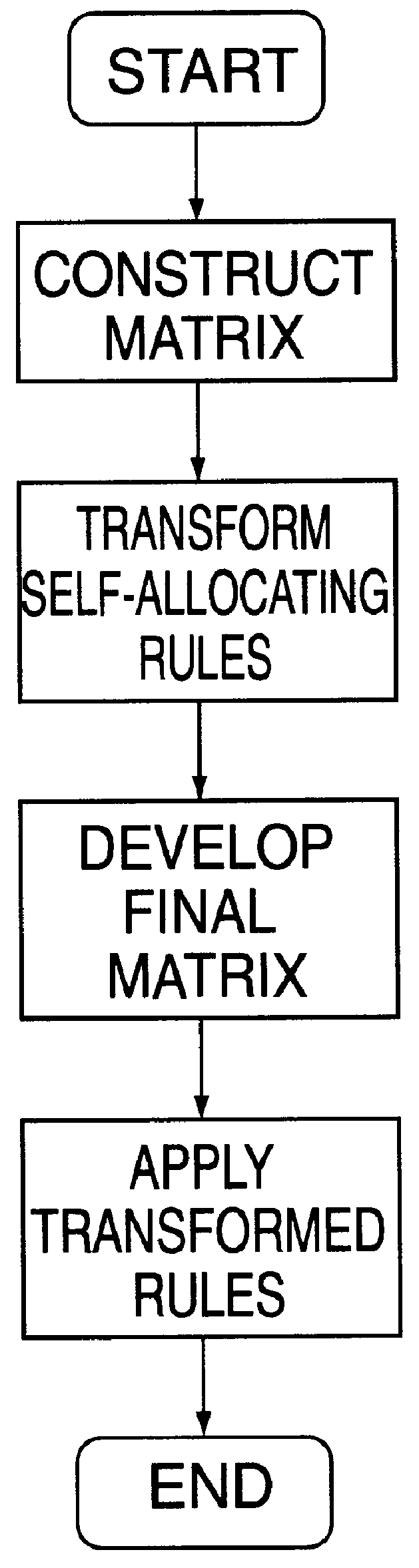
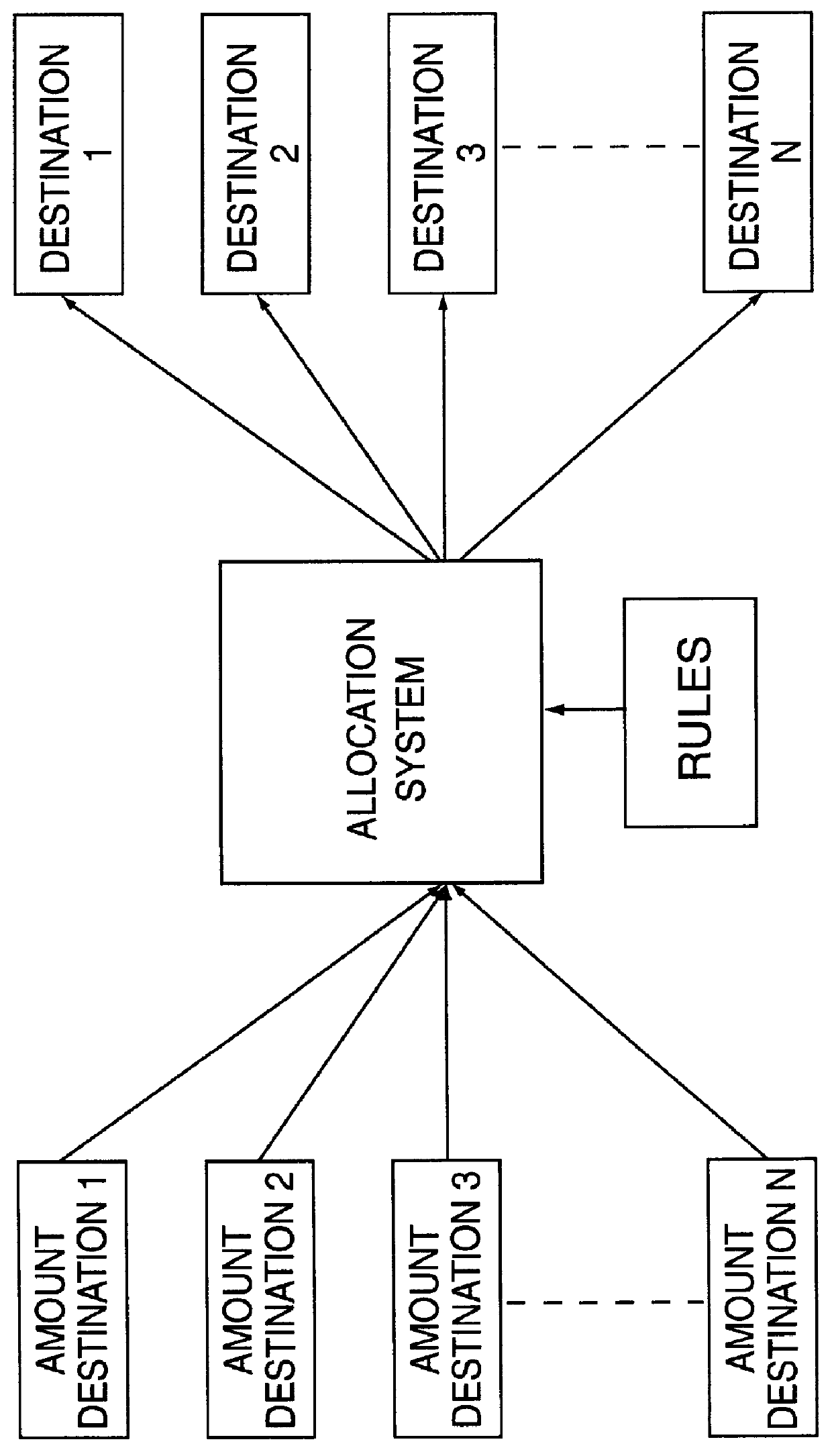
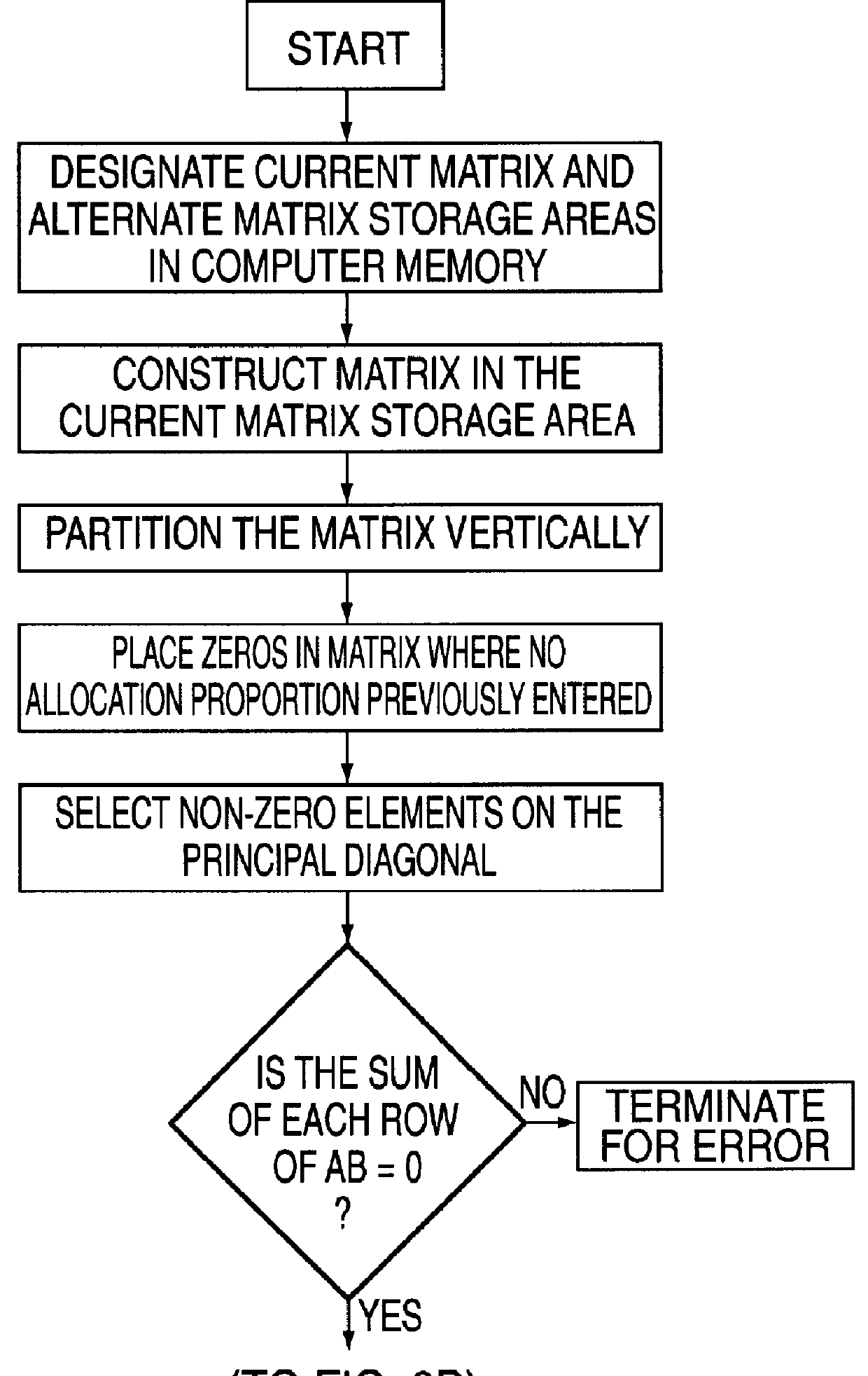
An expense allocation method utilizes matrix multiplication to transform a set of reciprocal or cascading allocation rules into a new set of one-step allocation rules. The new set of rules reallocates amounts directly to the ultimate destination without going through numerous intermediate levels of reallocation. By taking advantage of the specific structure of the matrix, and partitioning the matrix into four (4) subparts, the matrix multiplication process is greatly simplified. The expense allocation method can be easily and efficiently implemented on a computer system, including computers based upon parallel or vector architectures. This invention permits most allocation work to be done before the end of an accounting period, allowing end-of-period accounting work to be completed sooner. Alternatively, expenses can be allocated as they occur, rather than waiting until the end of a period.
Owner:BENT KIRKE M
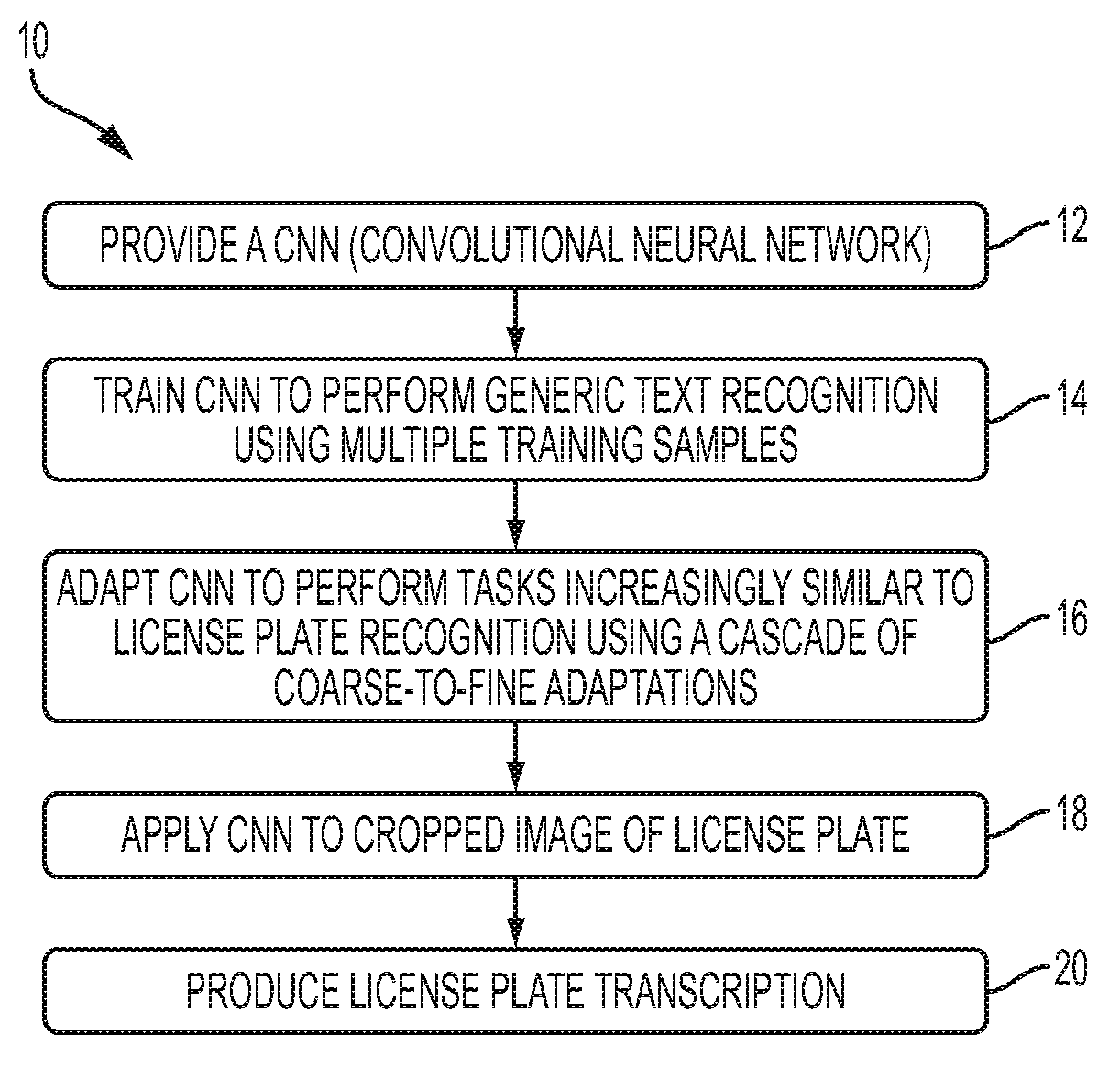
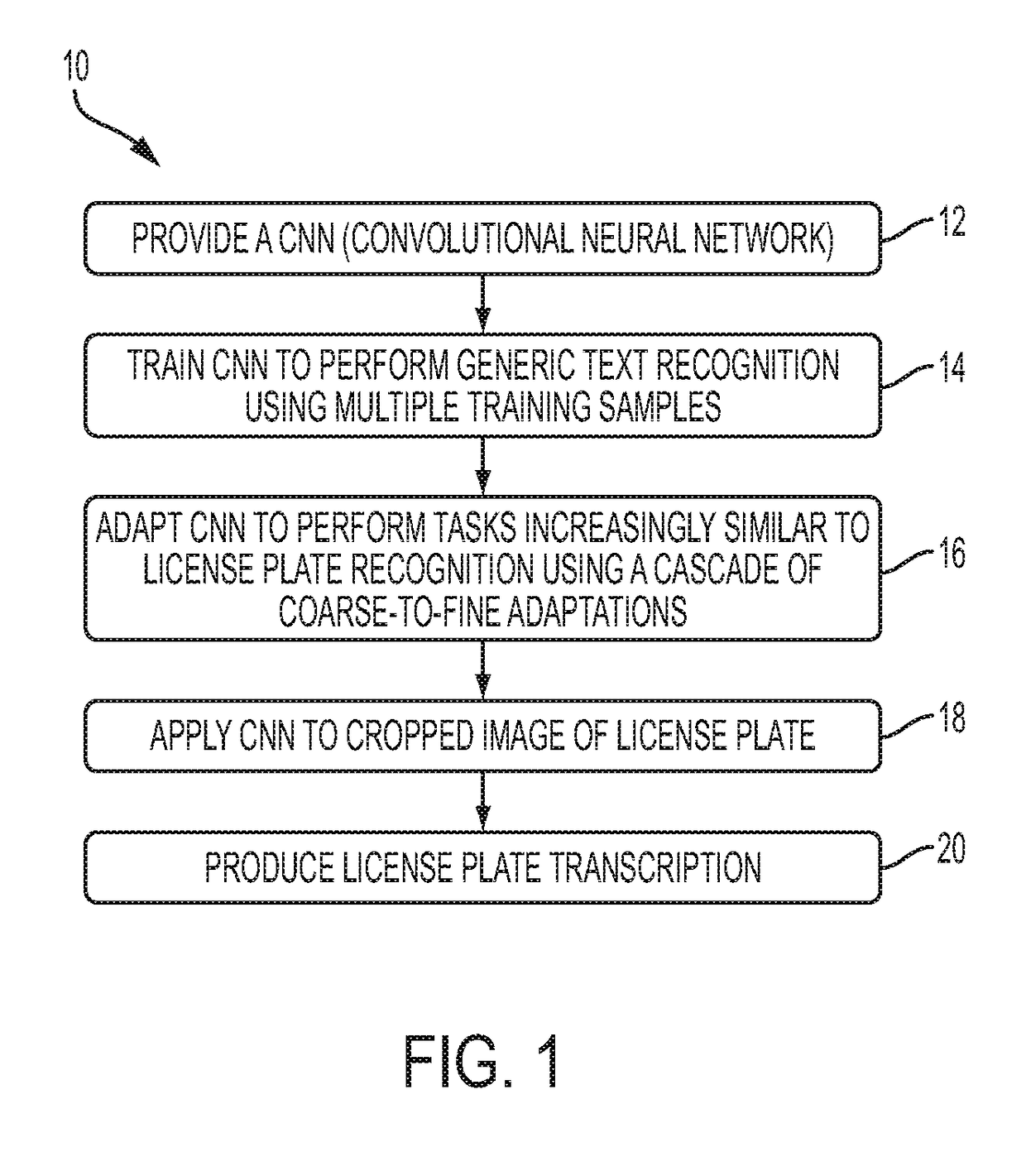
Coarse-to-fine cascade adaptations for license plate recognition with convolutional neural networks
Methods and systems for license plate recognition utilizing a trained neural network. In an example embodiment, a neural network can be subject to operations involving iteratively training and adapting the neural network for a particular task such as, for example, text recognition in the context of a license plate recognition application. The neural network can be trained to perform generic text recognition utilizing a plurality of training samples. The neural network can be applied to a cropped image of a license plate in order to recognize text and produce a license plate transcription with respect to the license plate. An example of such a neural network is a CNN (Convolutional Neural Network).
Owner:CONDUENT BUSINESS SERVICES LLC
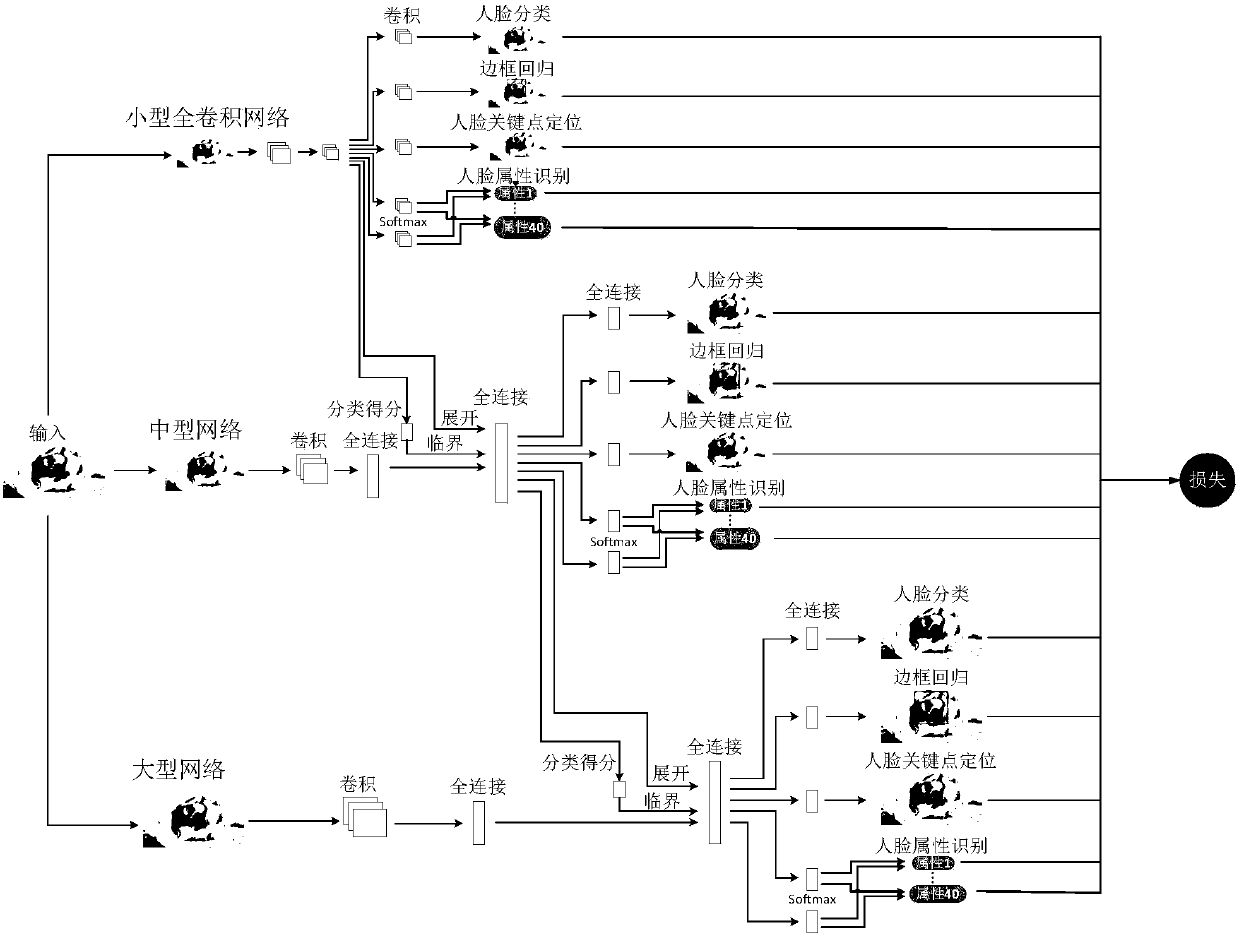
Face attribute recognition method of deep neural network based on cascaded multi-task learning
ActiveCN108564029APromote resultsThe result of face attribute recognition is improvedCharacter and pattern recognitionNeural architecturesVisual technologyCrucial point
The invention provides a face attribute recognition method of a deep neural network based on cascaded multi-task learning and relates to the computer vision technology. Firstly, a cascaded deep convolutional neural network is designed, then multi-task learning is used for each cascaded sub-network in the cascaded deep convolutional neural network, four tasks of face classification, border regression, face key point detection and face attribute analysis are learned simultaneously, then a dynamic loss weighting mechanism is used in the deep convolutional neural network based on the cascaded multi-task learning to calculate the loss weights of face attributes, finally a face attribute recognition result of a last cascaded sub-network is used as the final face attribute recognition result based on a trained network model. A cascading method is used to jointly train three different sub-networks, end-to-end training is achieved, the result of face attribute recognition is optimized, different from the use of fixed loss weights in a loss function, a difference between the face attributes present is considered in the invention.
Owner:XIAMEN UNIV
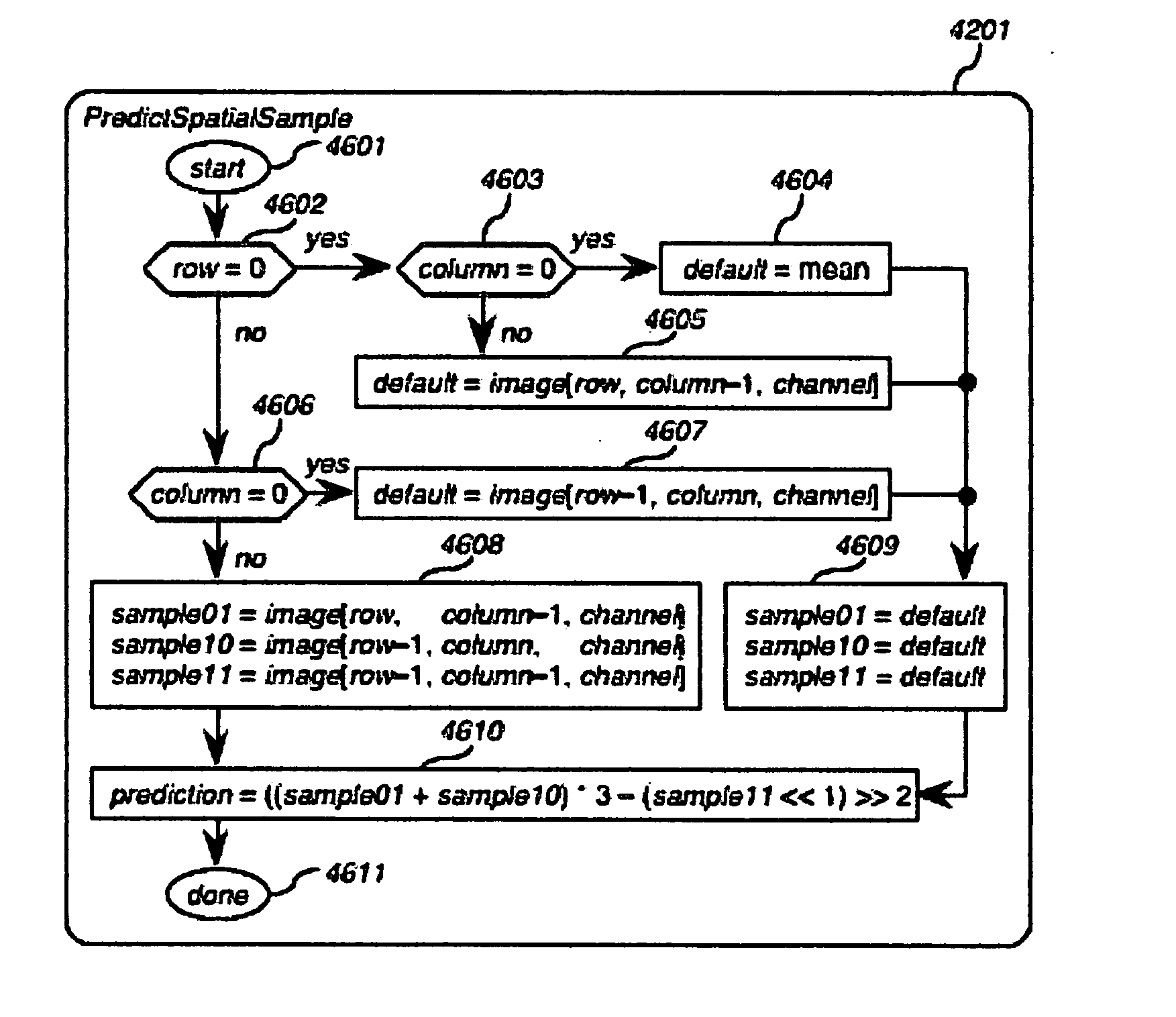
Method and apparatus for faster-than-real-time lossless compression and decompression of images
InactiveUS20080219575A1Maximize compression ratioMinimized on demandCharacter and pattern recognitionDigital video signal modificationFrequency spectrumContext independent
The present invention is a method and apparatus for compressing and decompressing data. In particular, the present invention provides for (de-)compressing naturalistic color-image and moving-image data, including high-precision and high-definition formats, with zero information loss, one-sample latency and in faster than real time on common computing platforms, resulting in doubled transmission, storage, and playback speed and doubled transmission bandwidth and storage capacity, and hence in doubled throughput for non-CPU-bound image-editing tasks in comparison with uncompressed formats. The present invention uses a nearly symmetrical compression-decompression scheme that provides temporal, spatial, and spectral compression, using a reversible condensing / decondensing filter, context reducer, and encoder / decoder. In the preferred embodiment of the invention, the compression filter is implemented as a cascade of quasilinear feedforward filters, with temporal, multidimensional spatial, and spectral stages, where appropriate, in that order, whose support consists of adjacent causal samples of the respective image. The decompressor cascades quasilinear feedback inverse filters in the reverse order. The filters can be implemented with mere integer addition, subtraction, and either one-dimensional table lookup or constant multiplication and binary shifting, depending on the computing environment Tables permit the data precision to be constrained throughout to that of the image samples. The encoder uses a table of prefix codes roughly inversely proportional in length to their probability, while the decoder uses chunked decode tables for accelerated lookup. In the fastest and simplest mode, the code tables are context-independent. For greater power, at the cost of a reduction in speed, the code tables are based on the temporal, multidimensional spatial, and spectral adjacent causal residue samples, where contexts with similar probability distributions are incoherently collapsed by a context reducer using one-dimensional lookup tables followed by implicitly multidimensional lookup tables, to minimize the overall table size. The invention's minimal resource requirements makes it ideal for implementation in either hardware or software.
Owner:WITTENSTEIN ANDREAS
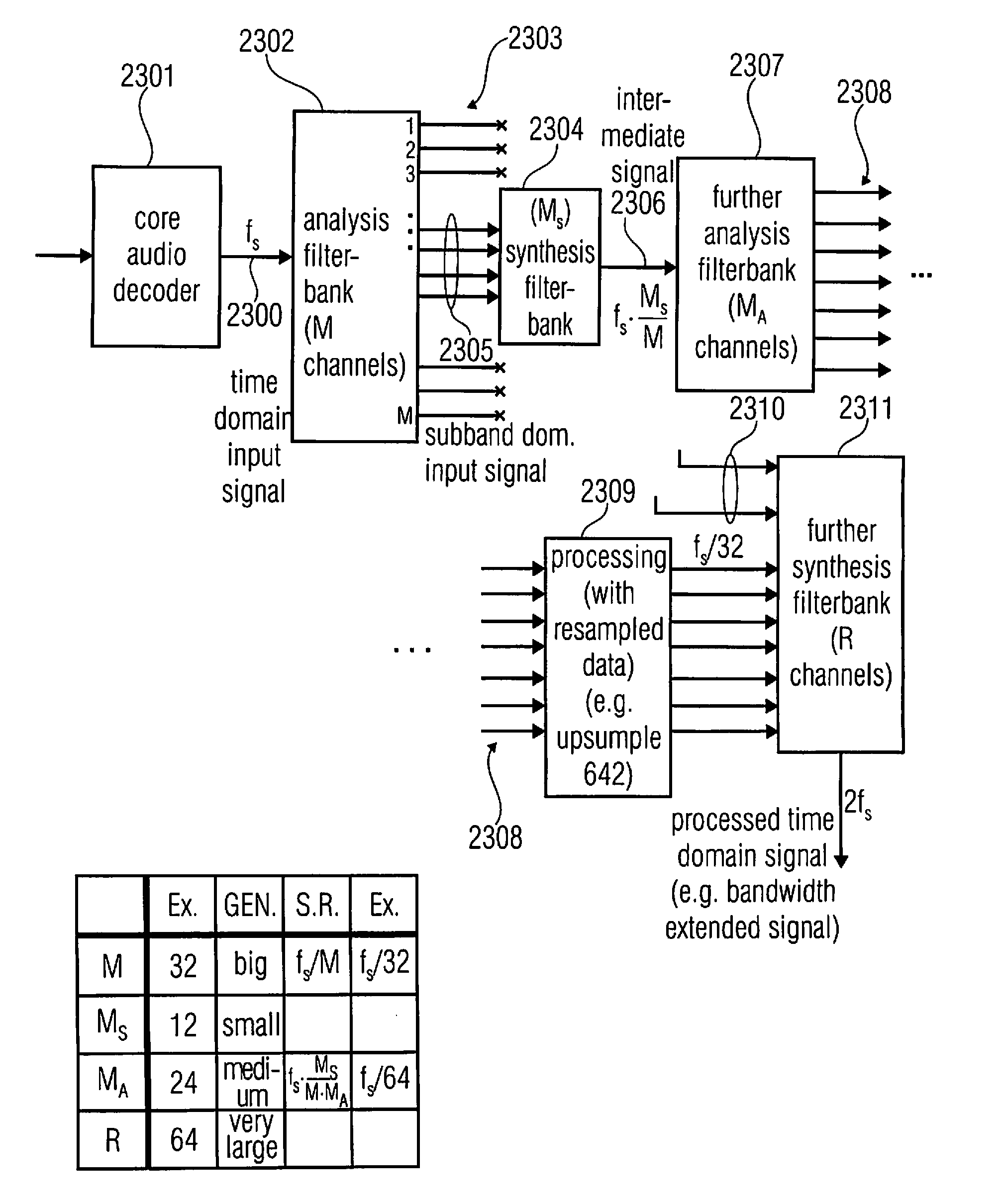
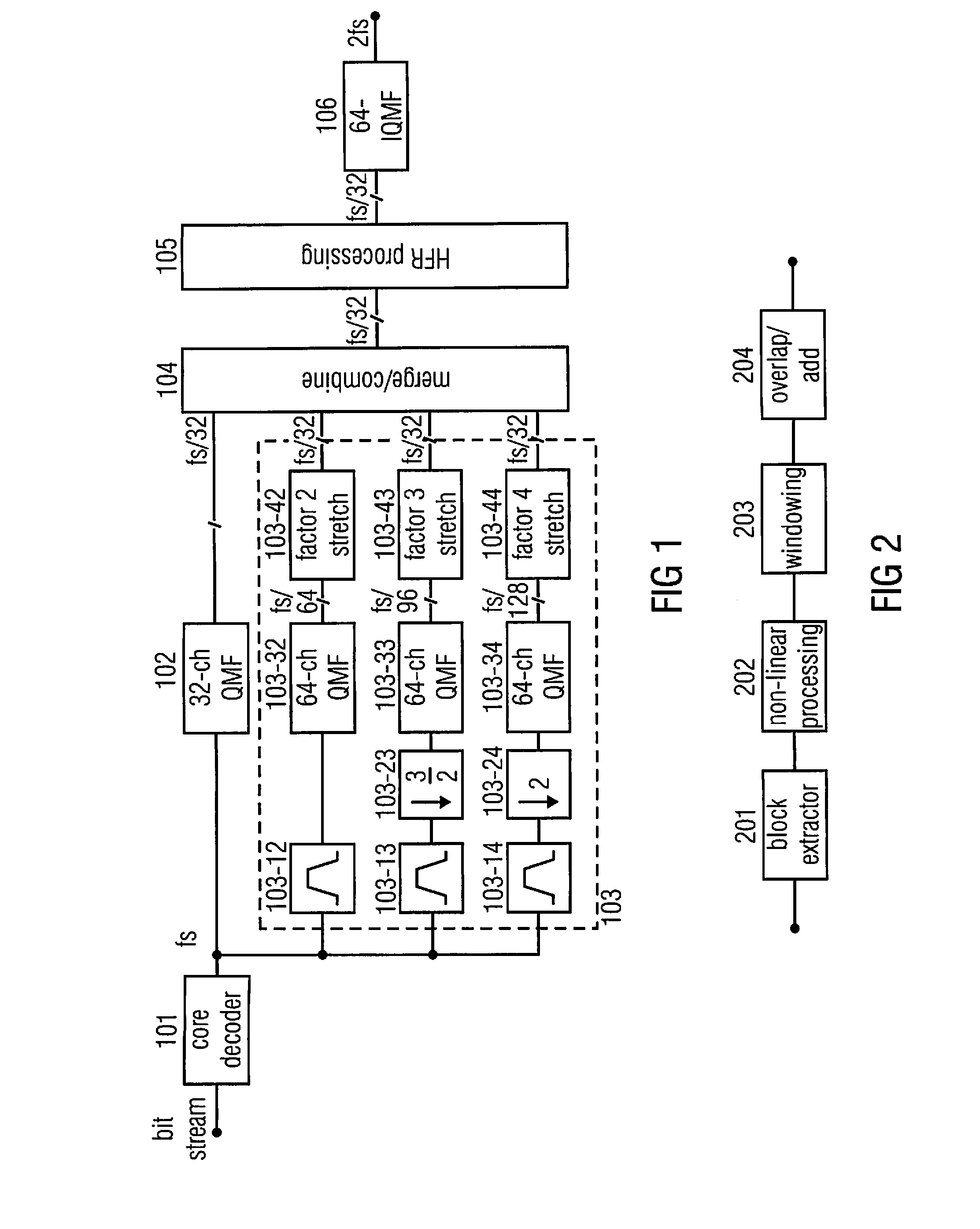
Apparatus and method for processing an input audio signal using cascaded filterbanks
ActiveUS20130090933A1Influence the complexity of the audio processing algorithmOperation moreSpeech analysisAudio frequencyComputer science
An apparatus for processing an input audio signal relies on a cascade of filterbanks, the cascade having a synthesis filterbank for synthesizing an audio intermediate signal from the input audio signal, the input audio signal being represented by a plurality of first subband signals generated by an analysis filterbank, wherein a number of filterbank channels of the synthesis filterbank is smaller than a number of channels of the analysis filterbank. The apparatus furthermore has a further analysis filterbank for generating a plurality of second subband signals from the audio intermediate signal, wherein the further analysis filterbank has a number of channels being different from the number of channels of the synthesis filterbank, so that a sampling rate of a subband signal of the plurality of second subband signals is different from a sampling rate of a first subband signal of the plurality of first subband signals.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV +1
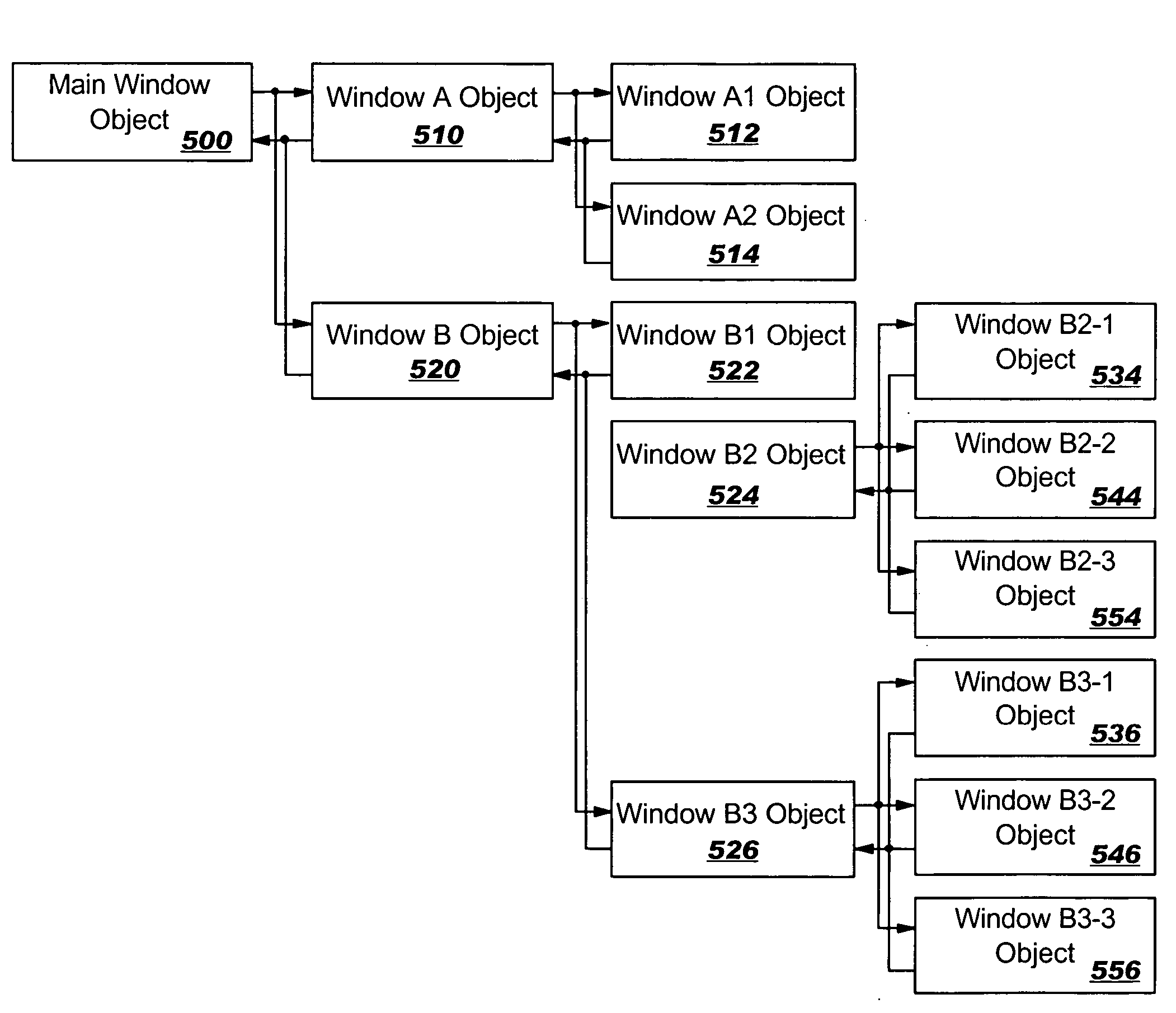
Global window management for parent/child relationships
InactiveUS20060184894A1Recognize disadvantageSpecial data processing applicationsInput/output processes for data processingInternet privacyWorld Wide Web
A mechanism is provided for maintaining some global windowing context to parent / child relationships. When a current window spawns a child window, a data structure stores the parent / child relationship within the window hierarchy. A cascading menu indicates to the user the contextual relationship of a current window to related windows. The user may then navigate among related windows using the cascading menu.
Owner:IBM CORP
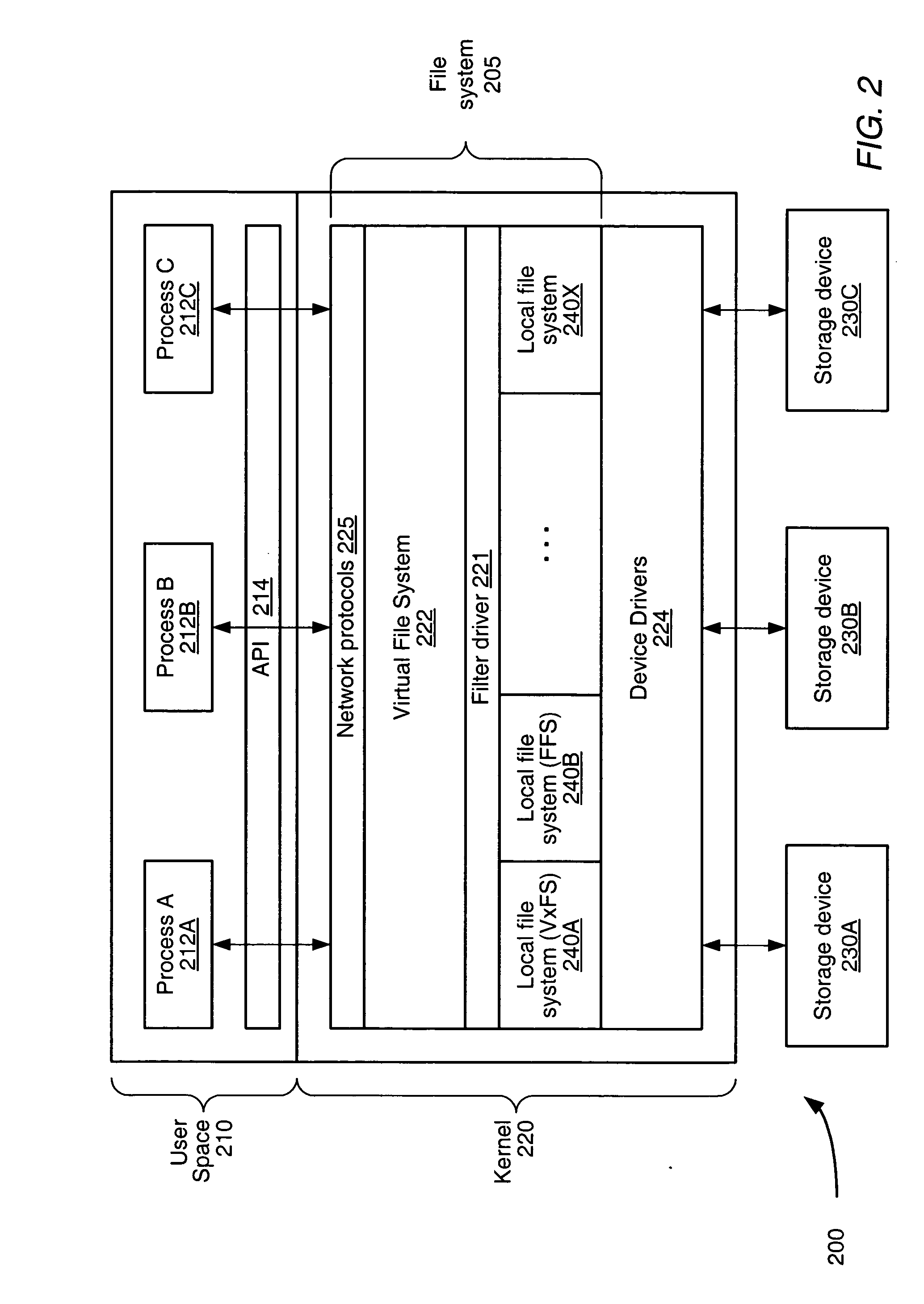
System and method for detecting file content similarity within a file system
InactiveUS20050114290A1Data processing applicationsDigital data information retrievalFile systemConcatenation
A system and method for detecting file content similarity within a file system. The system may include a storage device configured to store a plurality of files and a file system configured to manage access to the storage device. The file system may be configured to compute a compressed size of at least a portion of a given file, and to store an indication of the compressed size in a named stream corresponding to the given file. In one specific implementation of the system, the file system may be further configured to determine a value of a file harmony metric from the compressed size of the concatenation of a first and second file and the compressed sizes of the first and second files, where the compressed sizes of the first and second files may be stored in a corresponding one of a plurality of respective named streams.
Owner:SYMANTEC OPERATING CORP
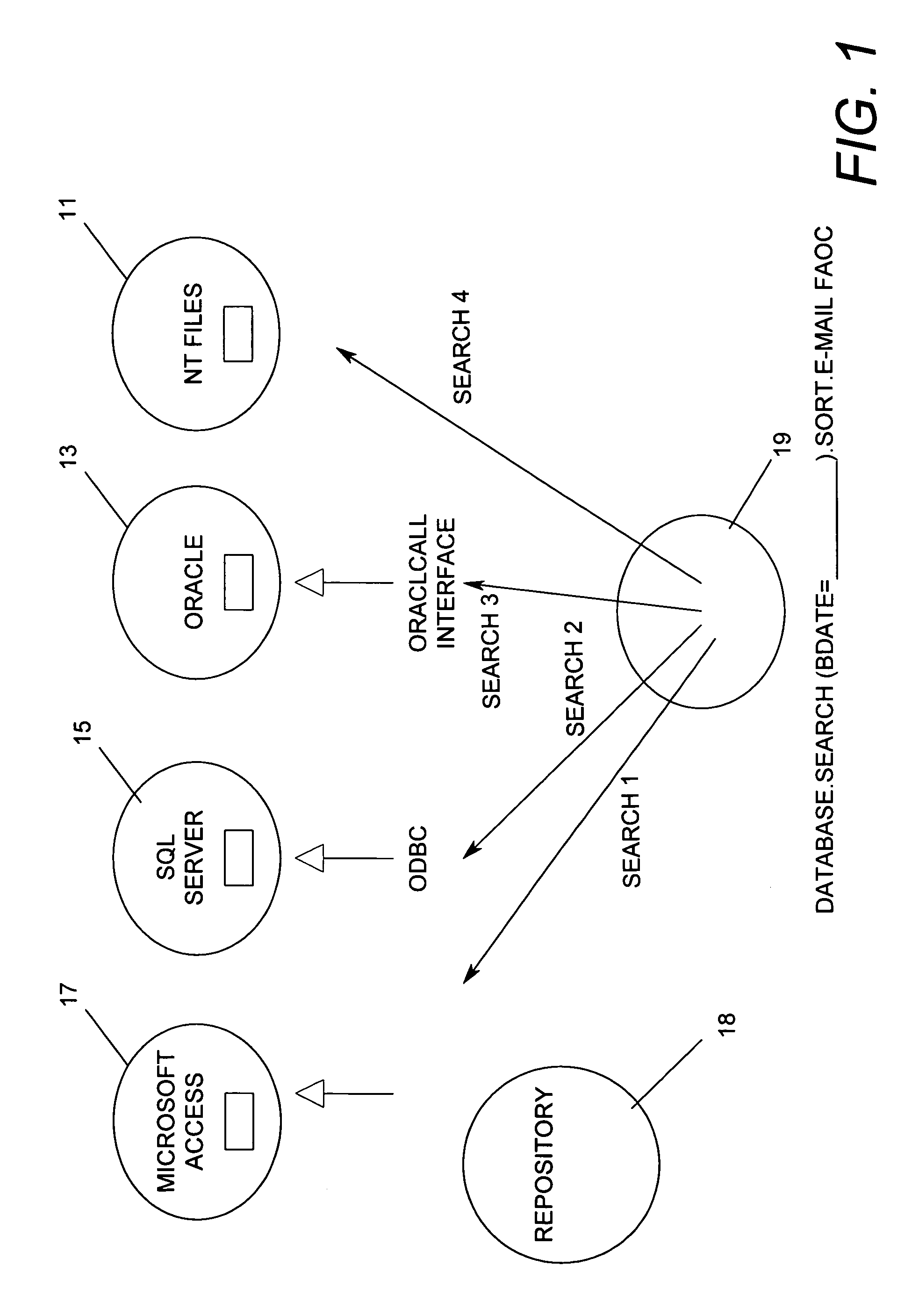
Sequential subset catalog search engine
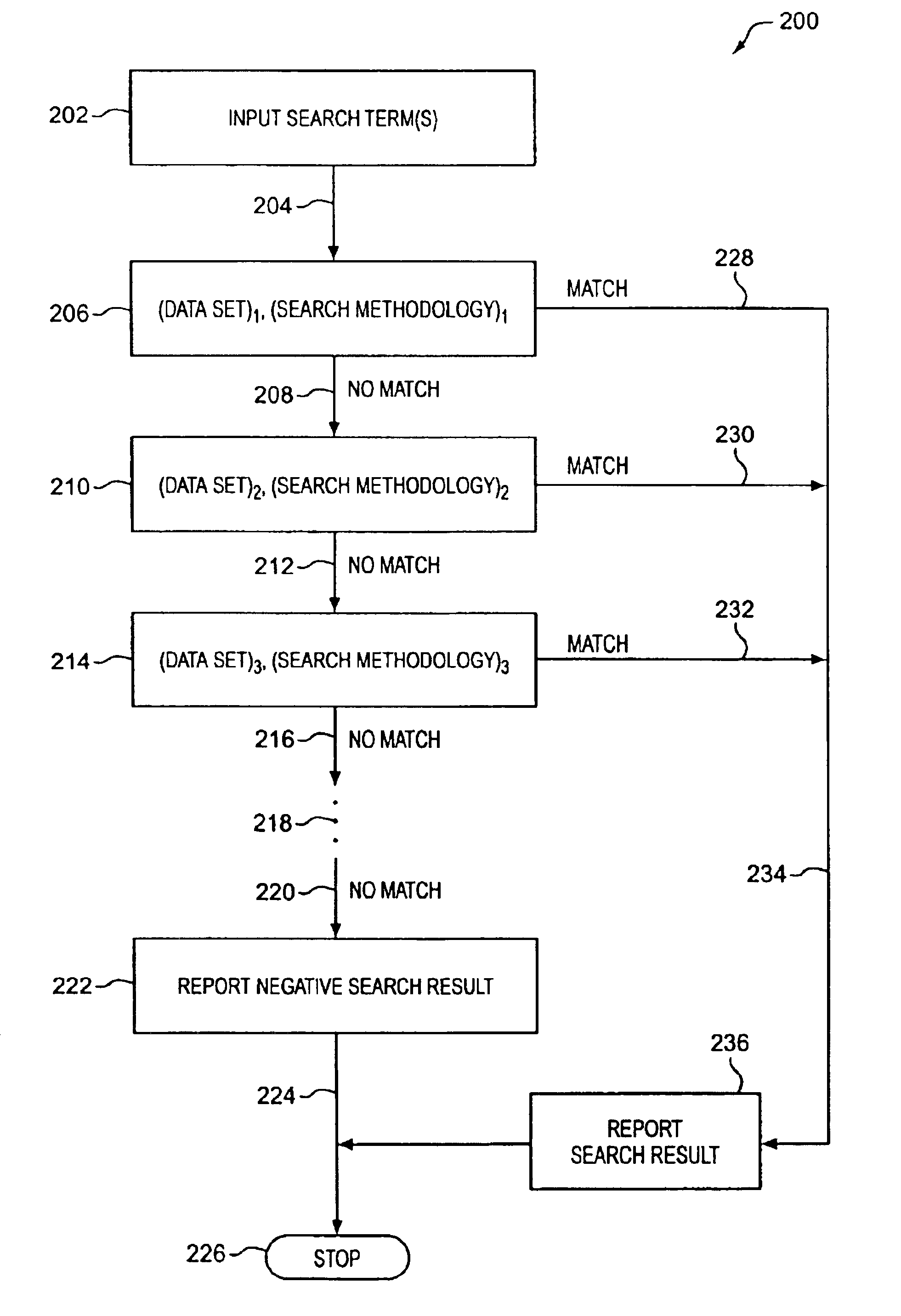
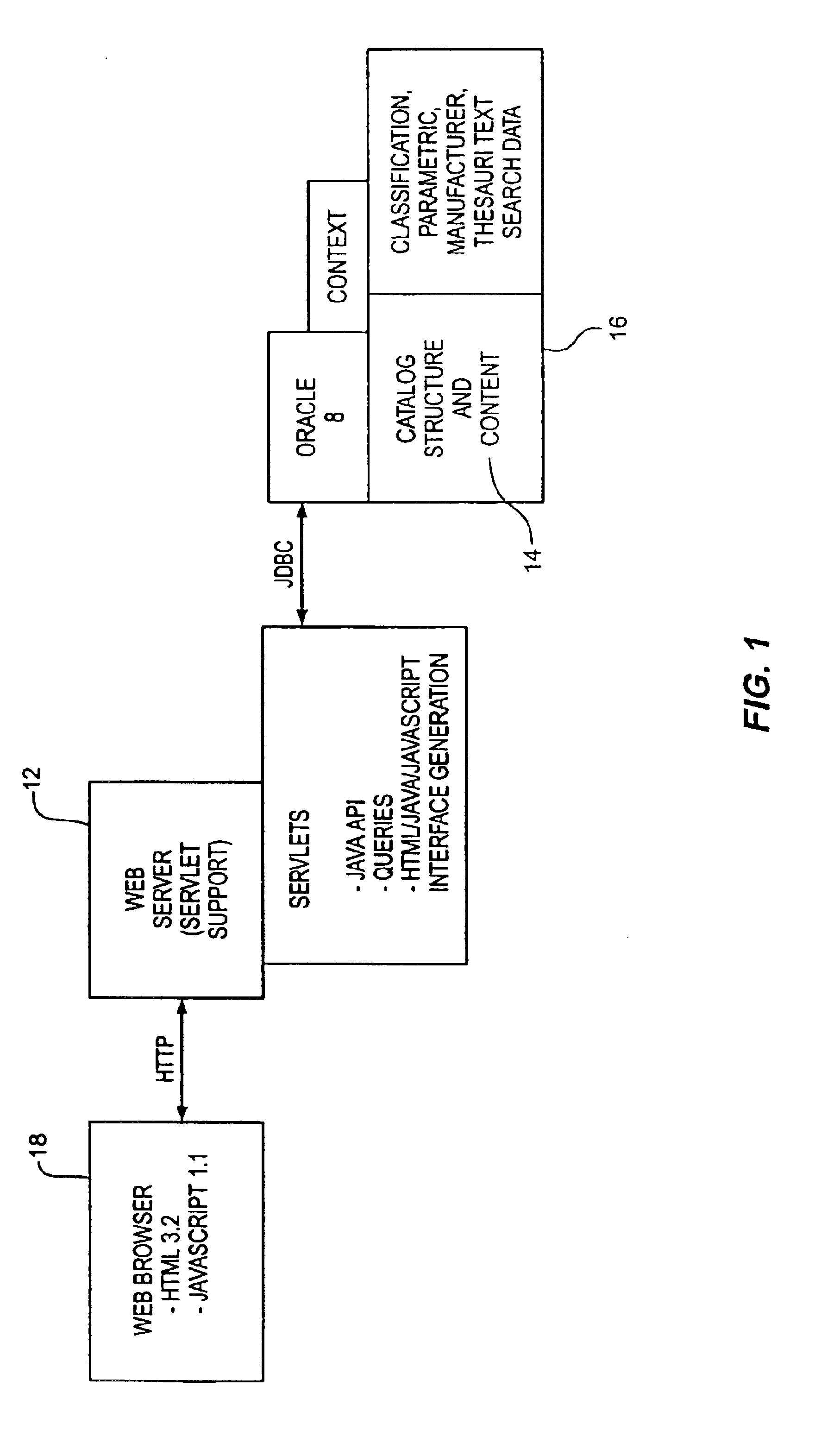
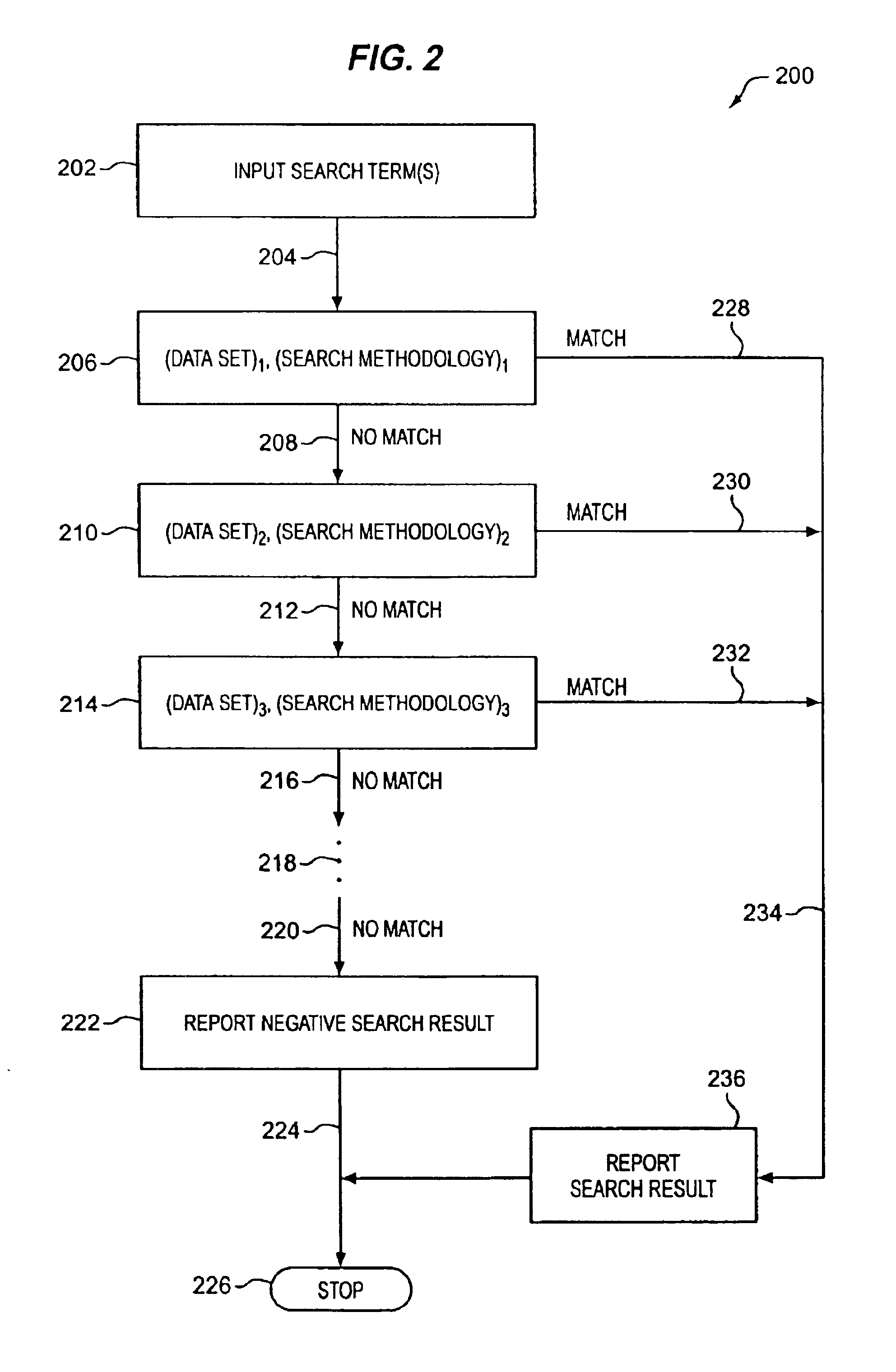
InactiveUS6907424B1The process is convenient and fastImprove efficiencyData processing applicationsWeb data indexingGraphicsData set
A method and apparatus are described to perform cascading search methodologies on one or more data sets from one or more databases. A graphical user interface for setting up the searching is also described. In one embodiment, the invention can include designating a first strategy comprising a search string applied to operate upon data records in a first database, designating a second search strategy comprising the search string applied to operate upon data records in a second database, and forming a search hierarchy comprised of the first search strategy followed by the second search strategy. In another embodiment, the invention can include a graphical user interface comprising a first area to select a database, a second area to select a search type, and a third area to select an attribute from the selected database upon which to execute the selected search type.
Owner:IBM CORP
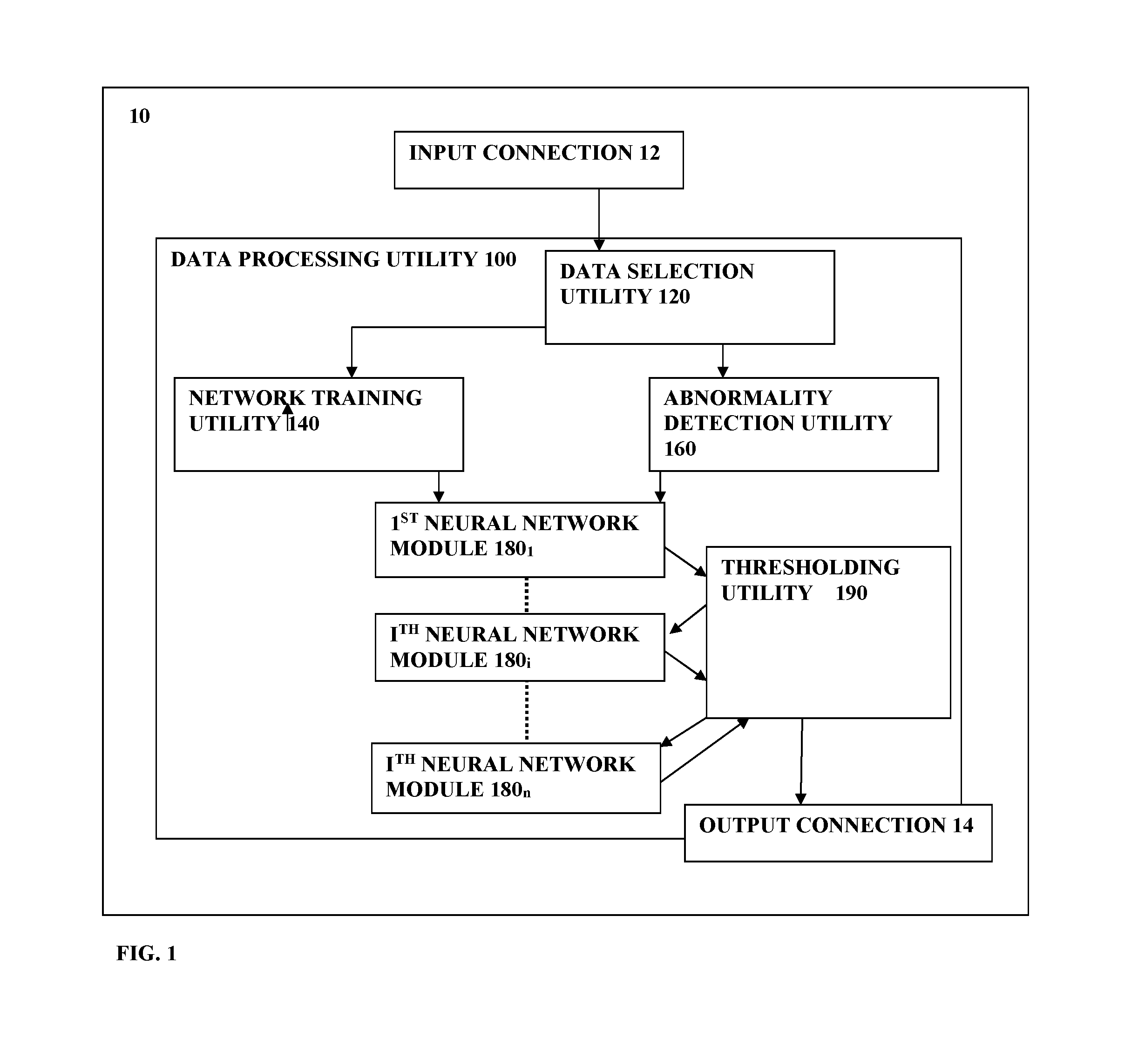
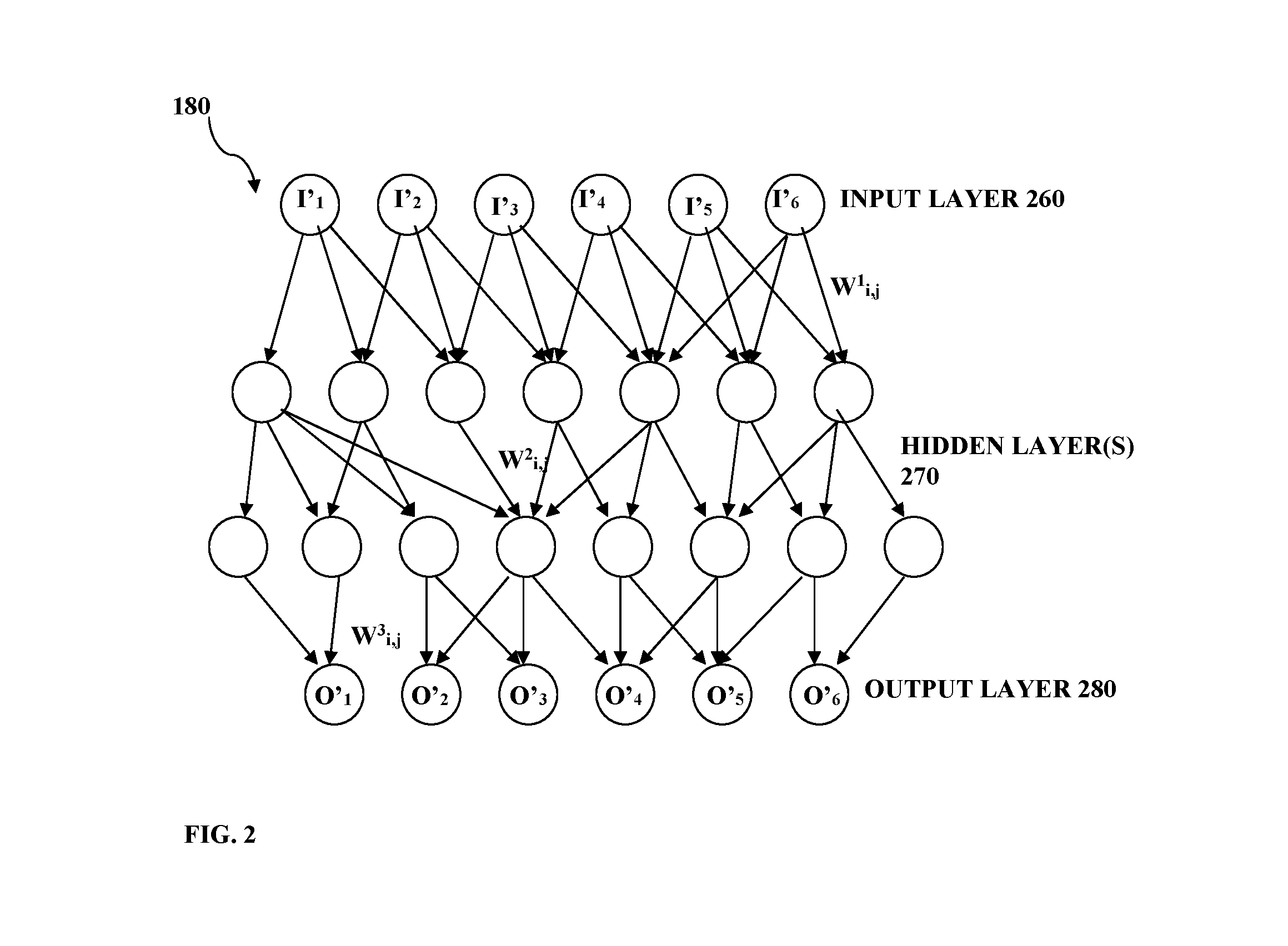
System and method for abnormality detection
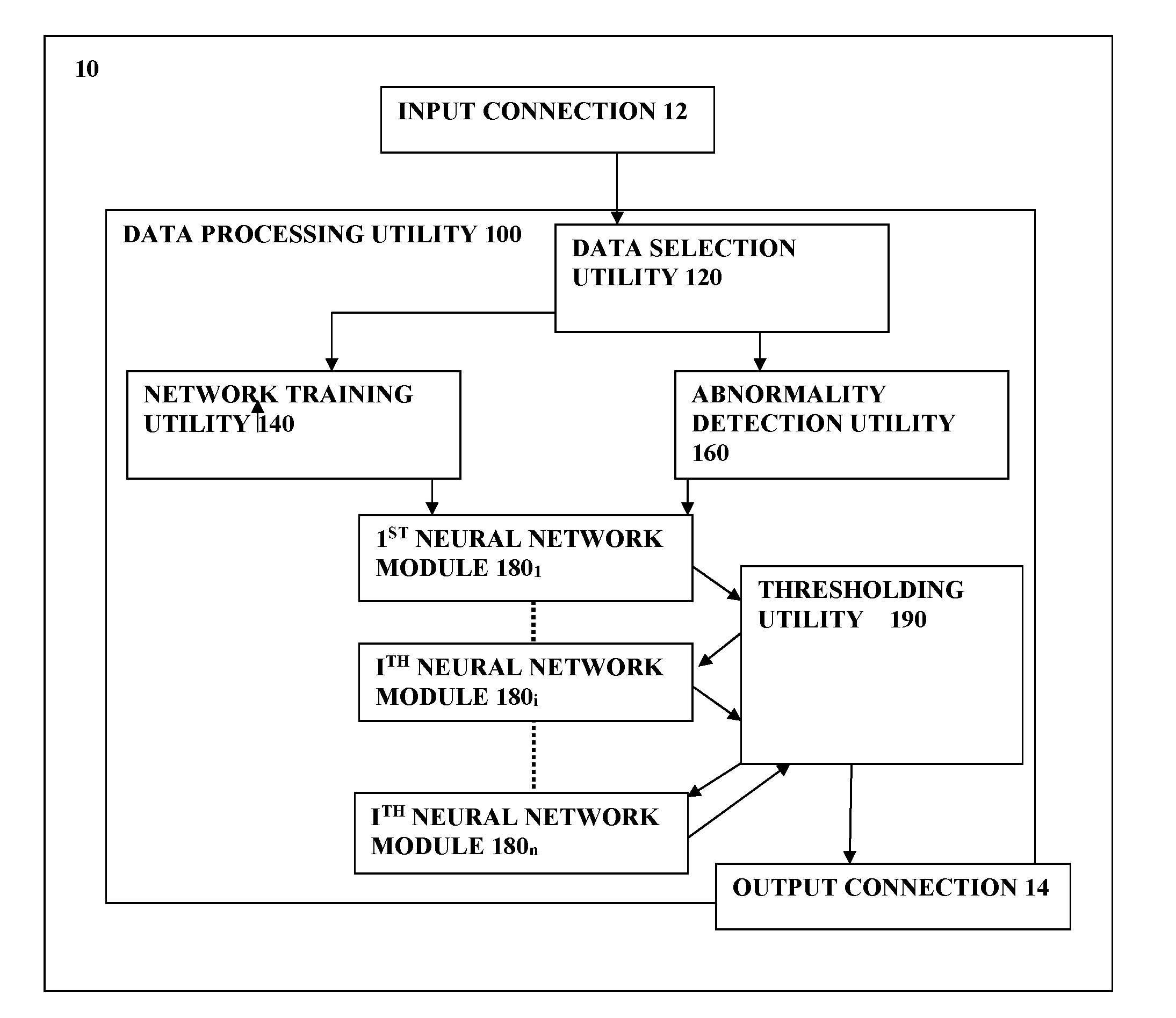
ActiveUS20160139977A1Accurately determineReduce the error valueCharacter and pattern recognitionNon-redundant fault processingComputer moduleMachine learning
A system and method for use in data analysis are provided. The system comprises a data processing utility configured to receive and process input data, comprising: plurality of neural network modules capable for operating in a training mode and in a data processing mode in accordance with the training; a network training utility configured for operating the neural network modules in the training mode utilizing selected set of training data pieces for sequentially training of the neural network modules in a cascade order to reduce an error value with respect to the selected set of the training data pieces for each successive neural network module in the cascade; and an abnormality detection utility configured for sequentially operating said neural network modules for processing input data, and classifying said input data as abnormal upon identifying that all the neural network modules provide error values being above corresponding abnormality detection thresholds.
Owner:AGENT VIDEO INTELLIGENCE
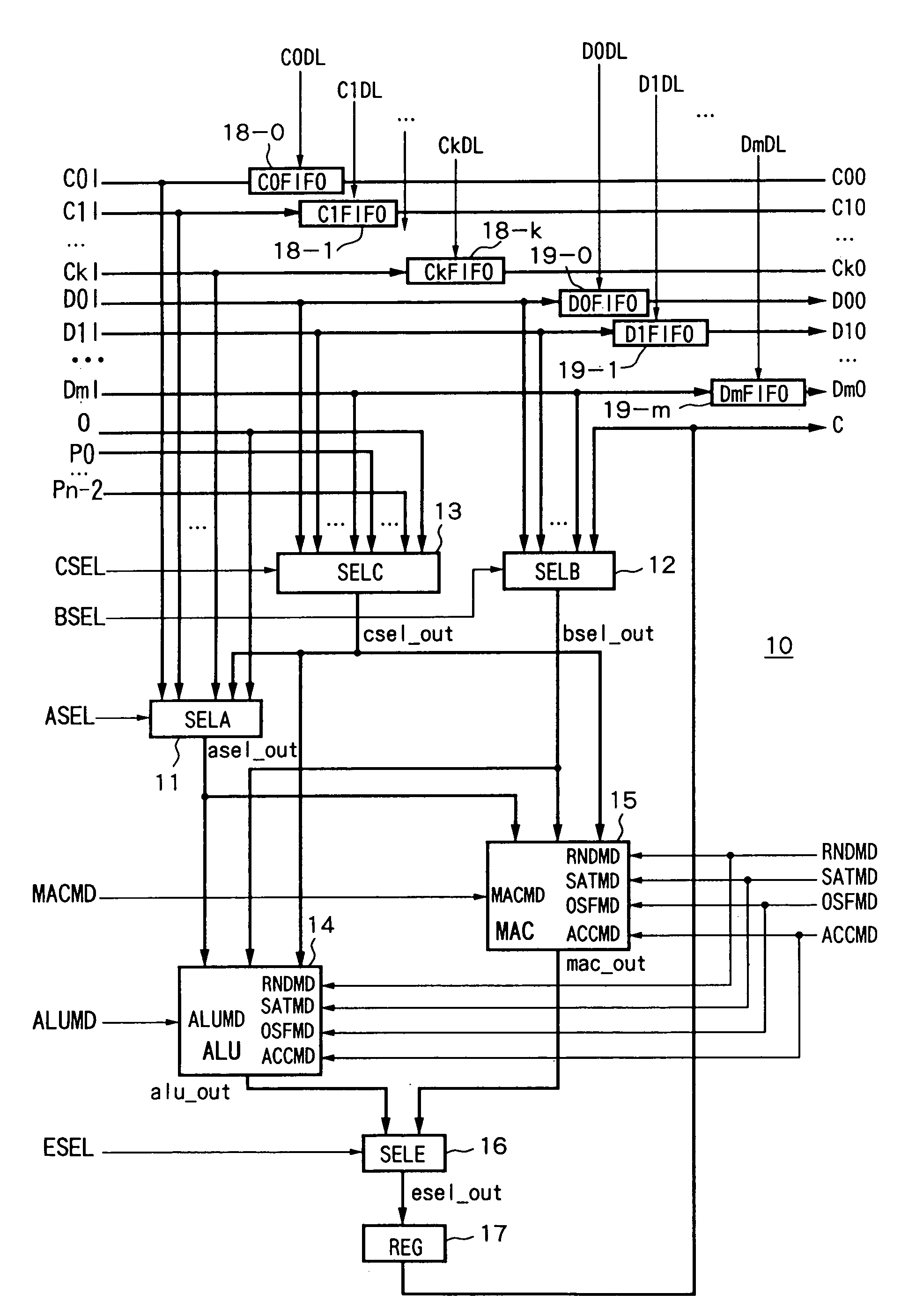
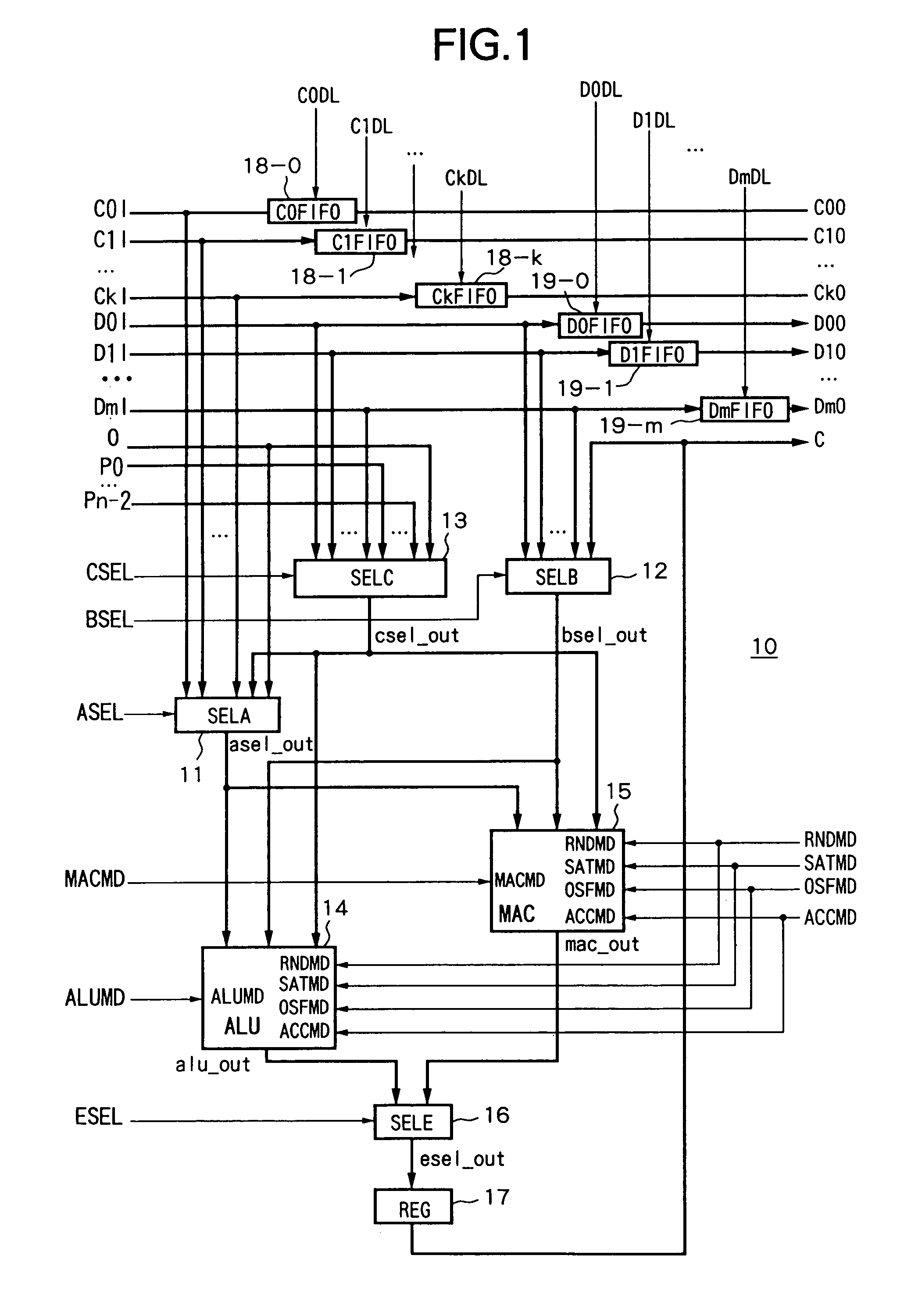
Reconfigurable arithmetic device and arithmetic system including that arithmetic device and address generation device and interleave device applicable to arithmetic system
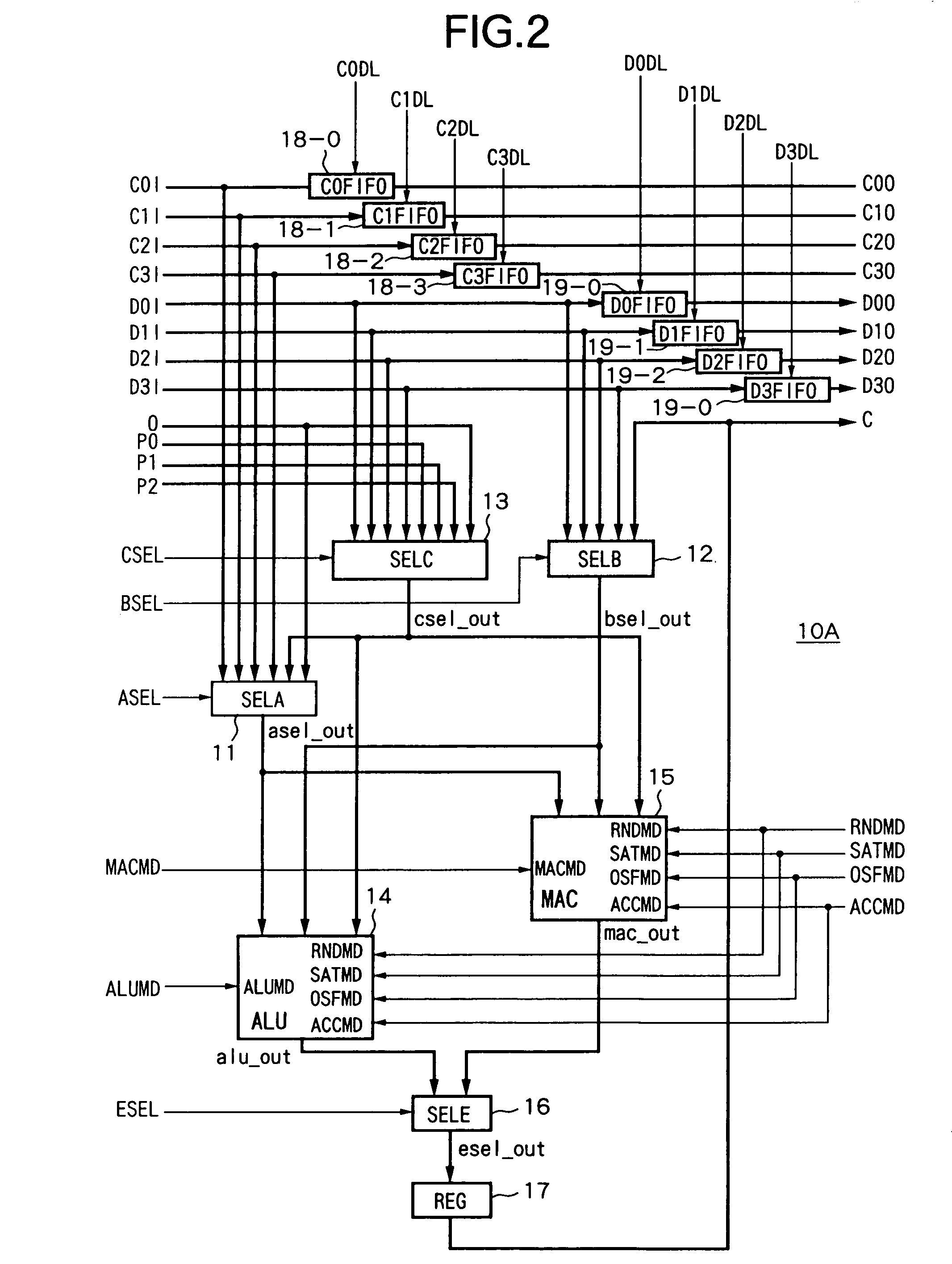
ActiveUS7020673B2Level of optimizationAvoid elevationComputation using denominational number representationControl signalLogical operations
An arithmetic device able to optimize the logic level, able to prevent an increase in the component data, able to prevent the area efficiency as an integrated operation efficiency, and circuit, achieving an improvement in the achieving a reduction power consumption, provided with a first selection device for selecting coefficient inputs C0I to CkI in accordance with a control signal ASEL, a second selection device for selecting data inputs D0I to DmI in accordance with a control signal BSEL, a third selection device for selecting cascade inputs P0 to Pn−2 in accordance with a control signal CSEL, an ALU for receiving as input the output signal of the first to third selection devices and performing a logic operation in accordance with instructions of the control signals ALUMD etc., a MAC for receiving as input the output signals of the first to third selection devices and performing operation in accordance with instructions of
Owner:SONY CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com