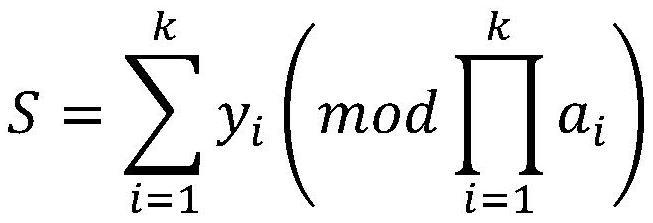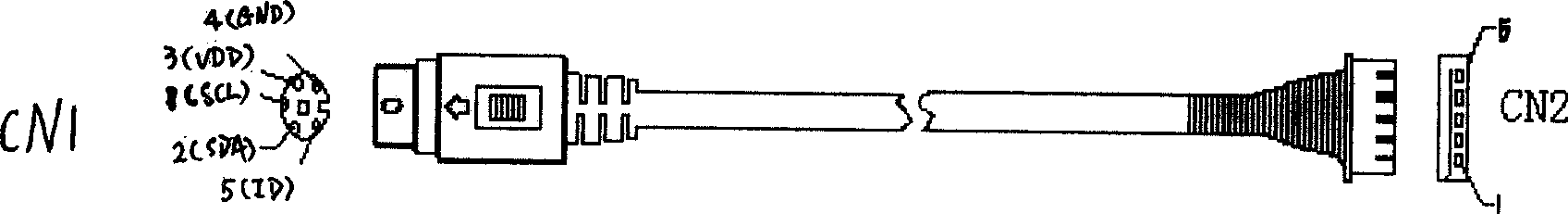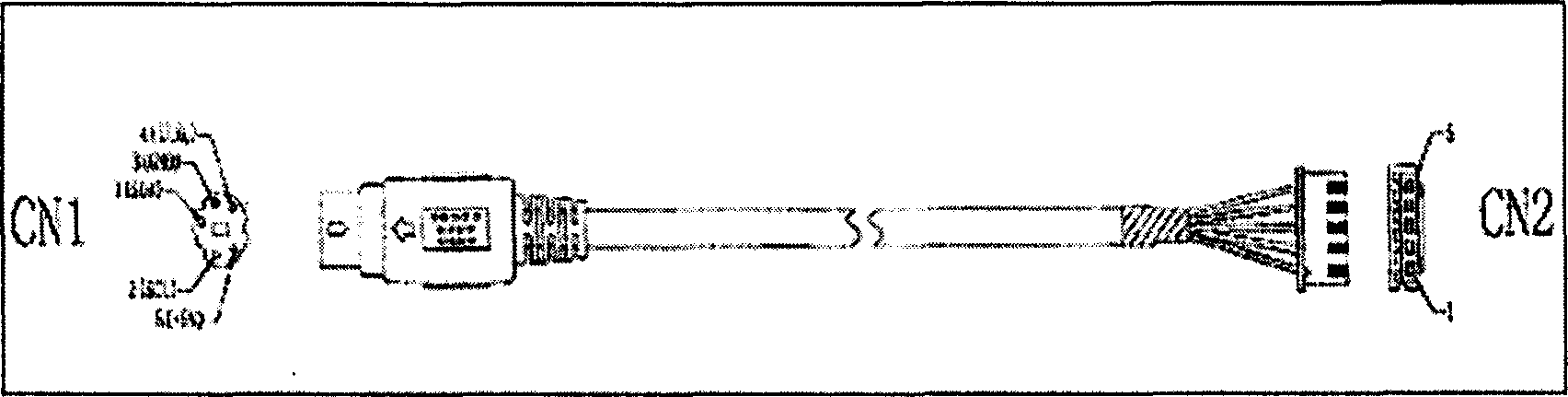Patents
Literature
33results about How to "Prevent random modification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
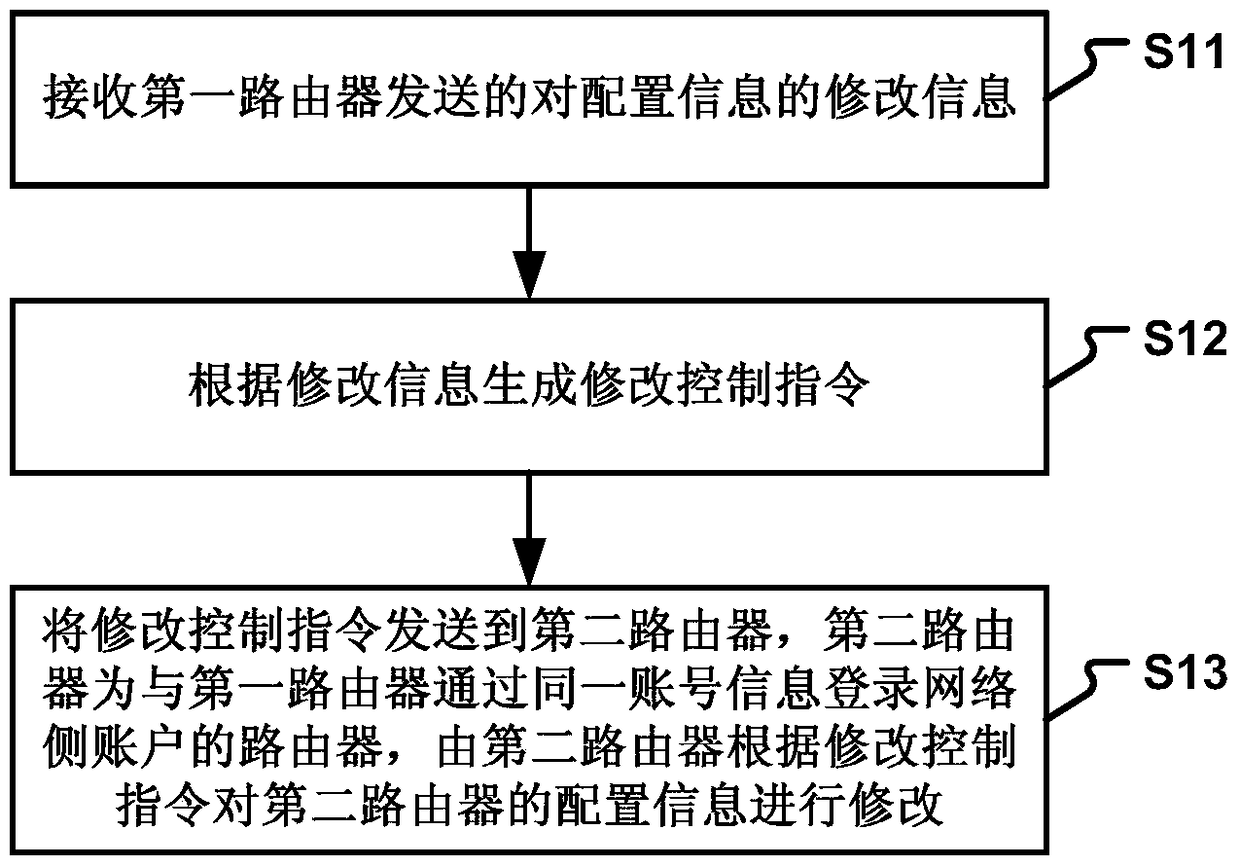
Patent Type
Patent Status
Application Year
Inventor
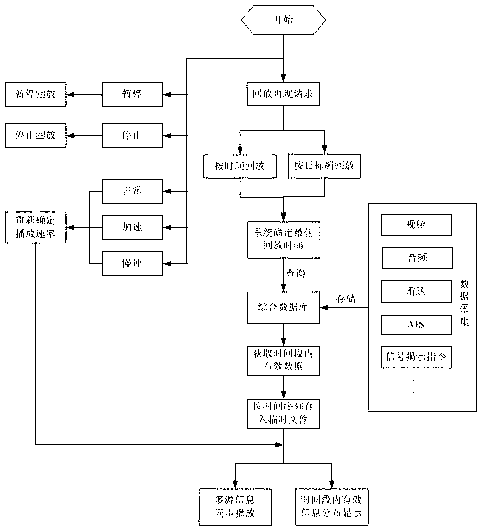
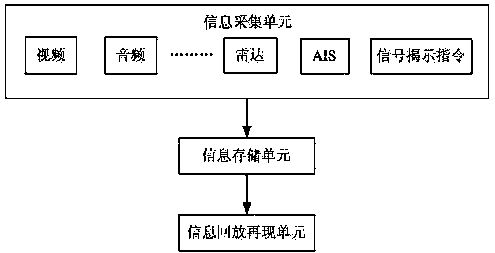
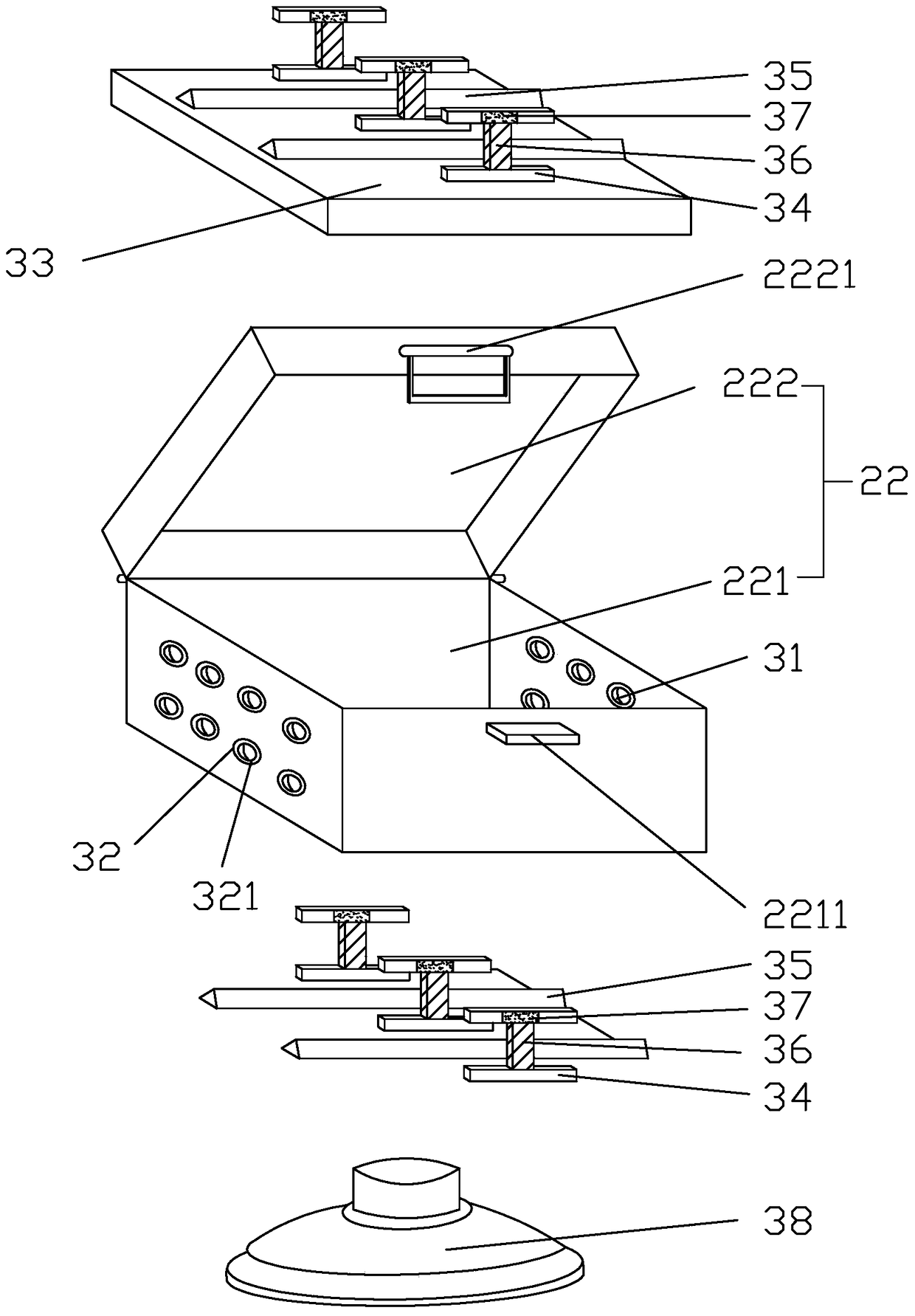
Reappearing method and system controlling river reach ship traveling dynamic and signal revealing process
ActiveCN103065503AAccurately grasp risky behaviorPrevent random modificationMarine craft traffic controlVIT signalsVery high frequency
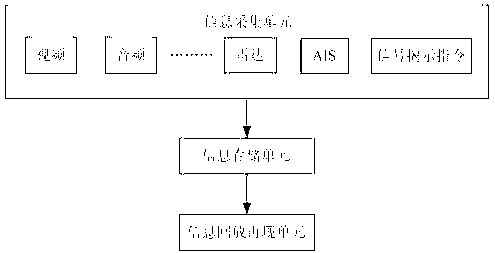
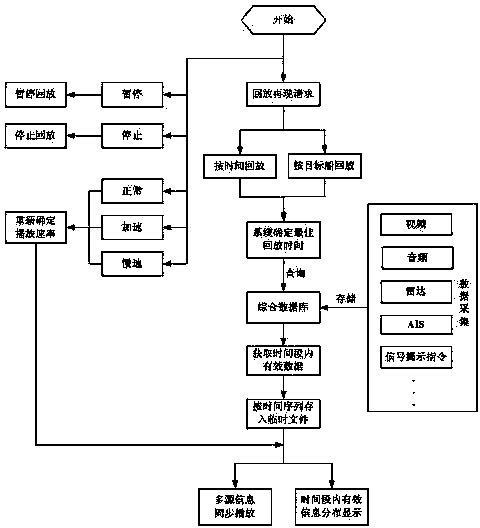
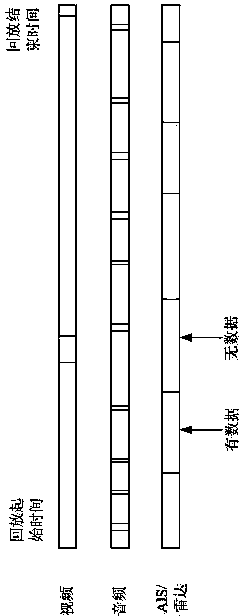
The invention discloses a reappearing method and a system for controlling river reach ship traveling dynamic and signal revealing process. The reappearing method comprises the following steps: collecting real-time information of dynamic and static information (automatic identification system (AIS) data and radar data) and videos of a traveling ship, very high frequency (VHF) call voice, signal tower command information and the like; compressing and storing the collected real-time information; and receiving reappearing orders, starting playback reappearing procedures, selecting a ship or a time quantum for playback reappearing, loading historical information, synchronously displaying information of ship positions corresponding to audios and videos, ship dynamic historical route, signal revealing time point, and the like. According to the reappearing method and the system, historical information of arbitrary come-and-go ships or within a time quantum can be found and used for synchronous playback, original record information of the audios and videos, ship dynamic tracks, signal revealing orders, and the like can be synchronously displayed in the whole course, and thus dynamic relevant evidence of the ship traveling dynamic and the signal revealing process is formed and can be used as a basis of accident analysis after an accident and signalman command effect evaluation.
Owner:CHONGQING UNIV +1
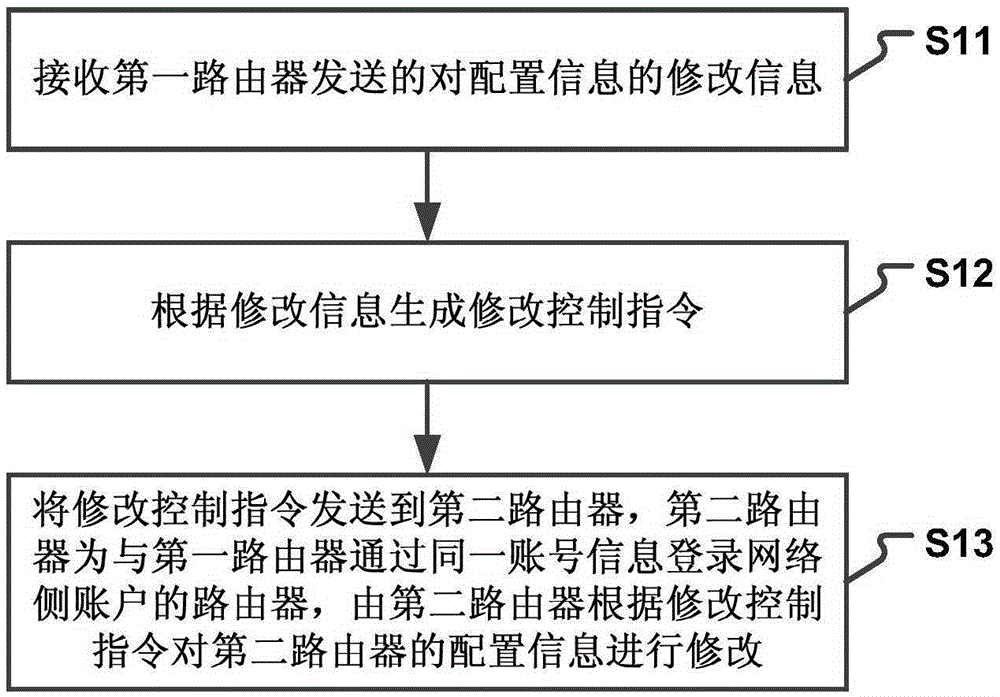
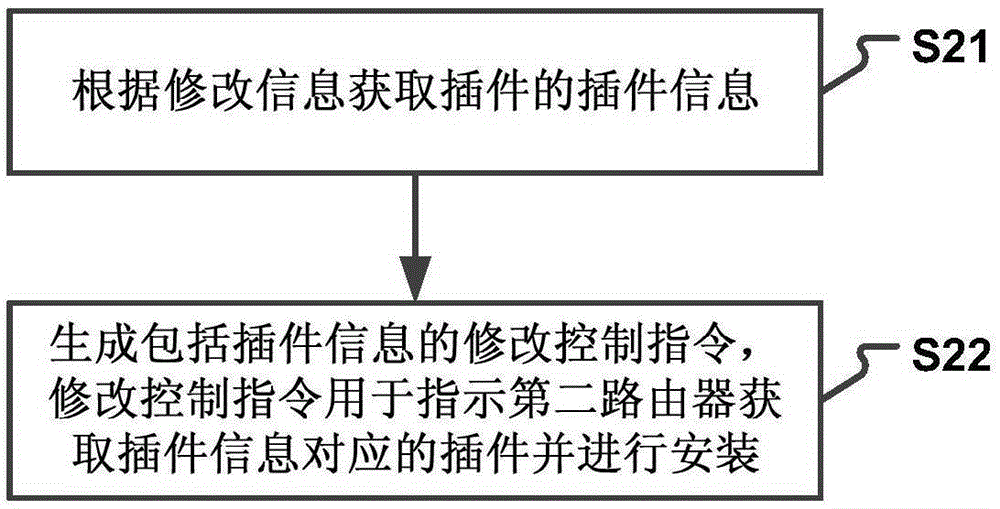
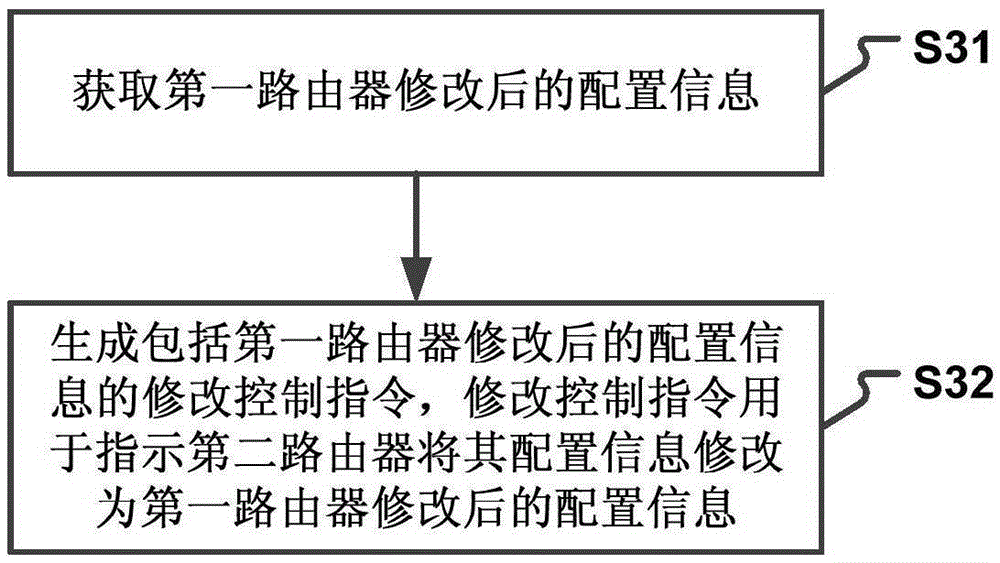
Router configuration information modifying method and device
The invention provides a router configuration information modifying method and device. The method comprises the steps that configuration information modifying information sent by a first router is received; a modifying control command is generated according to the modifying information; the modifying control command is sent to a second router, wherein the second router is a router which logs a network side account through the same account information with the first router; and the second router modifies the configuration information of the second router according to the modifying control command. According to the technical scheme, the configuration accuracy of multiple routers is improved; the router configuration complexity is reduced; user operations are simplified; the time spent by a user to modify the configuration of multiple routers is reduced; and the user experience is improved.
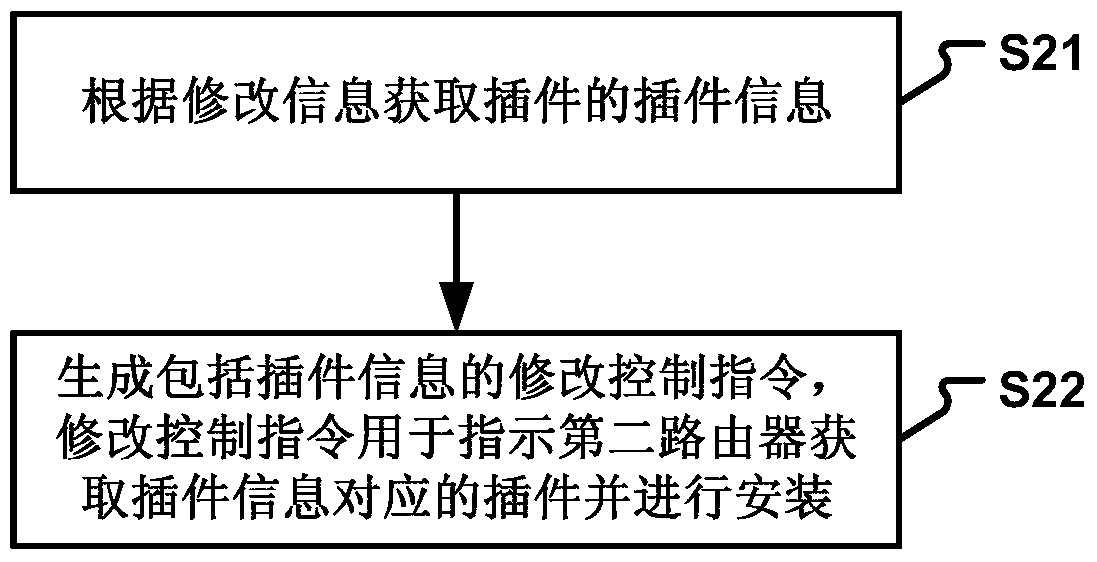
Owner:XIAOMI INC
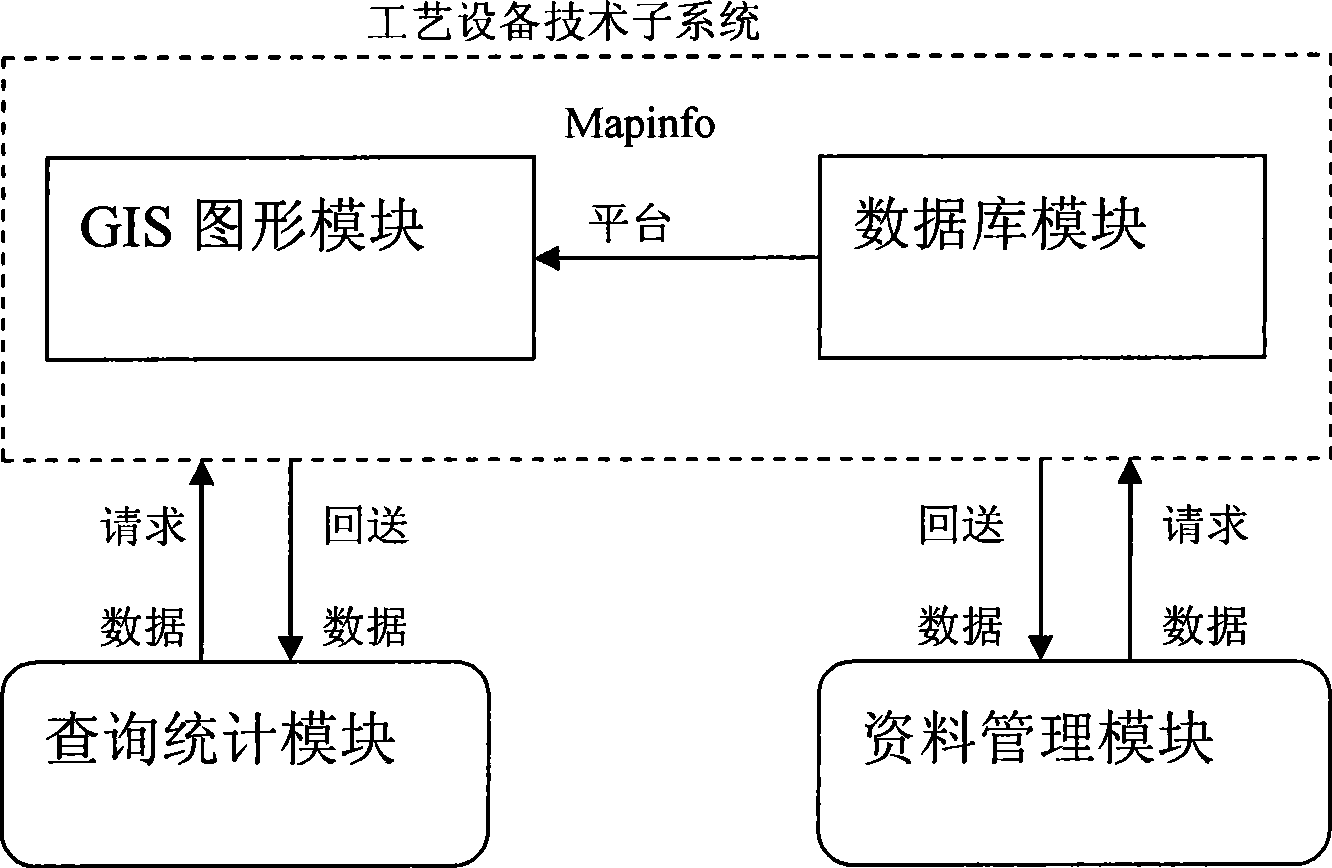
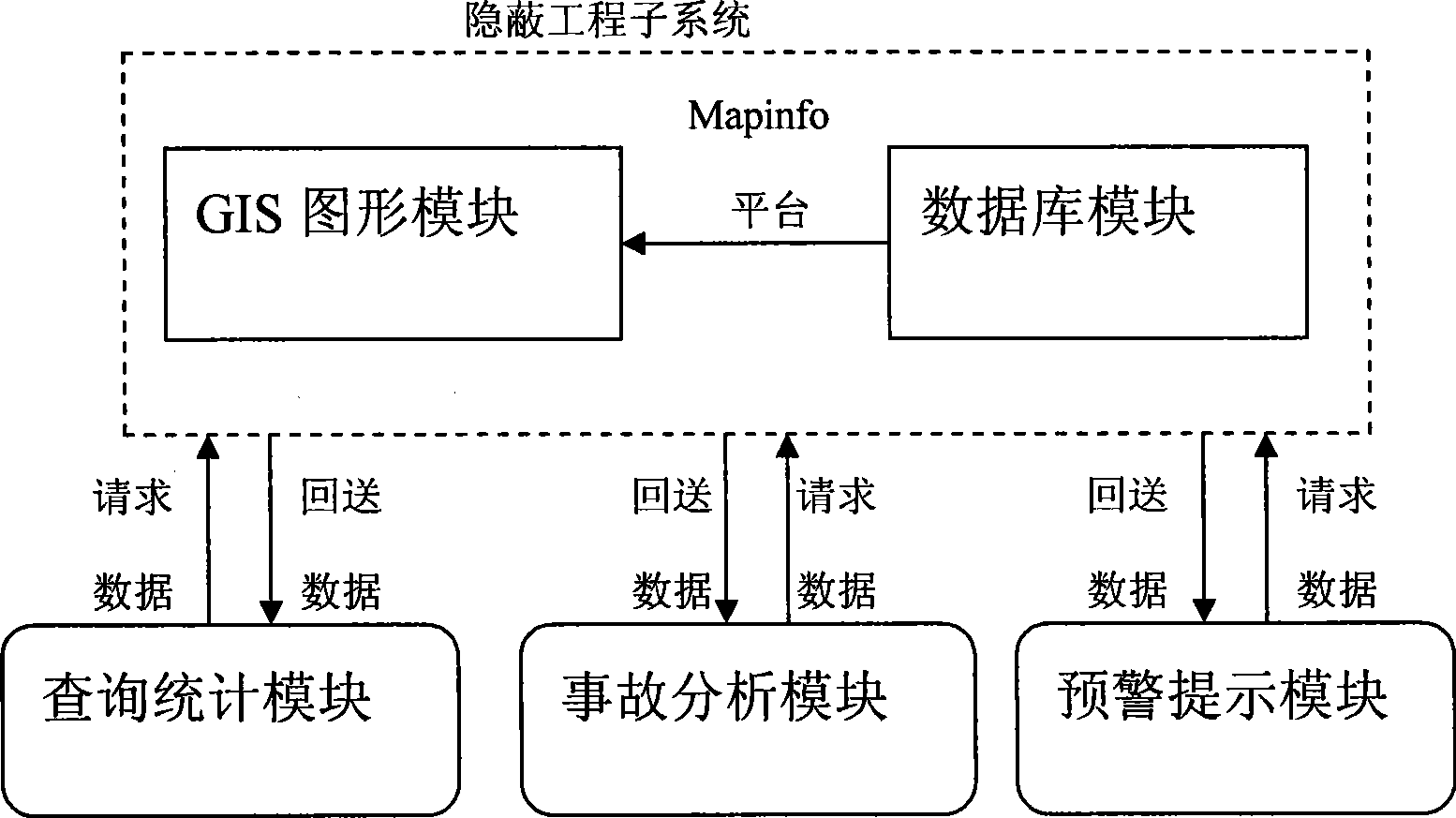
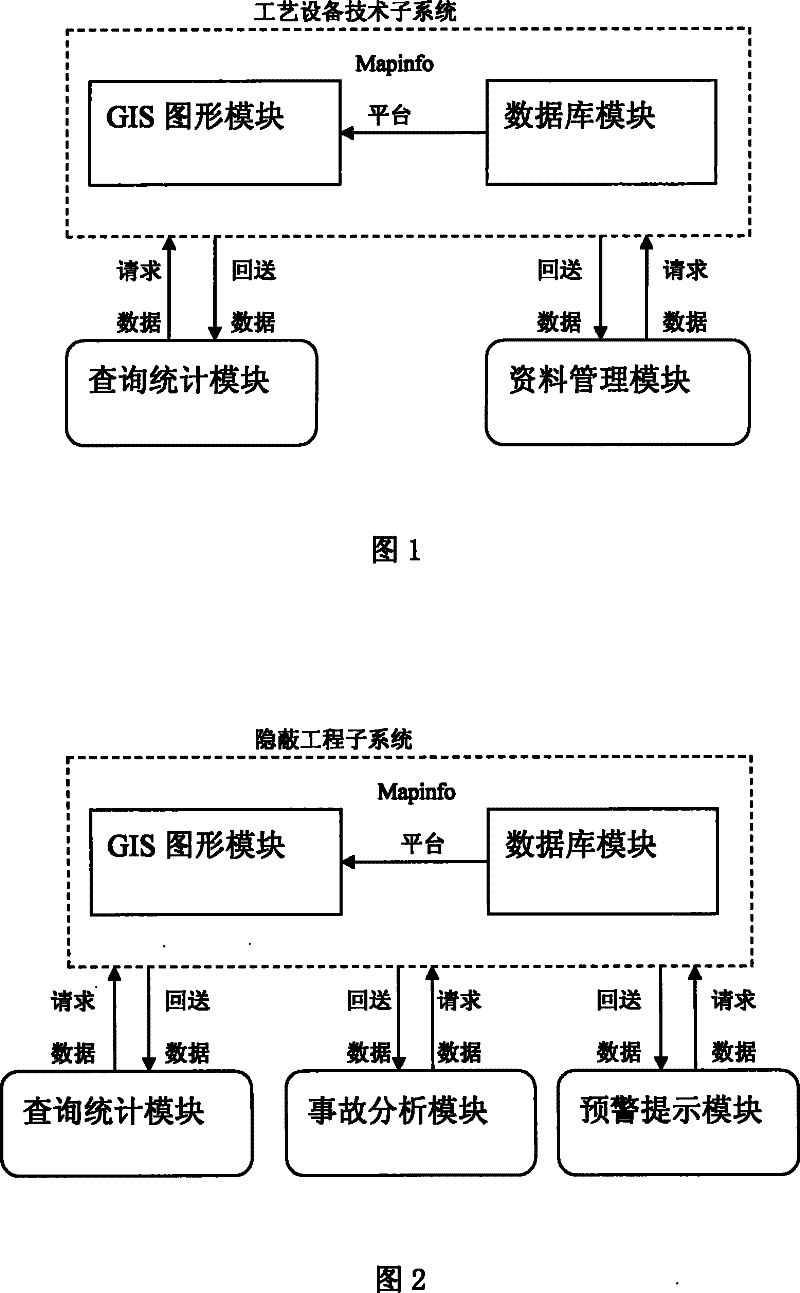
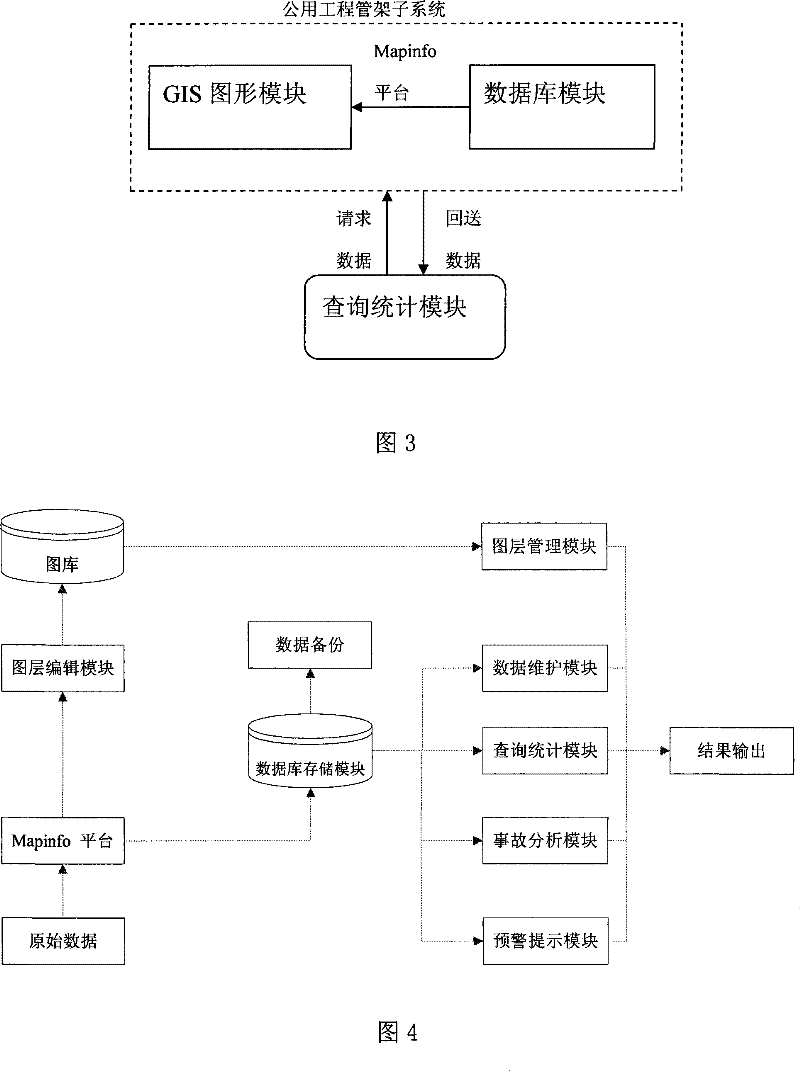
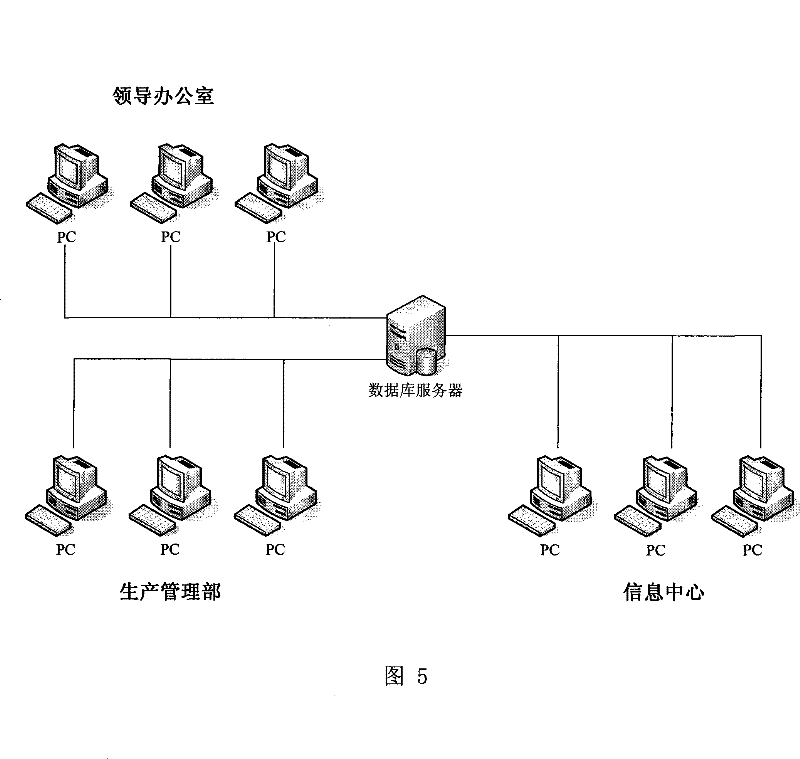
Information system for managing chemical industry data
InactiveCN101442456AImprove work efficiencyImprove good performanceData switching by path configurationChemical industryProcess equipment
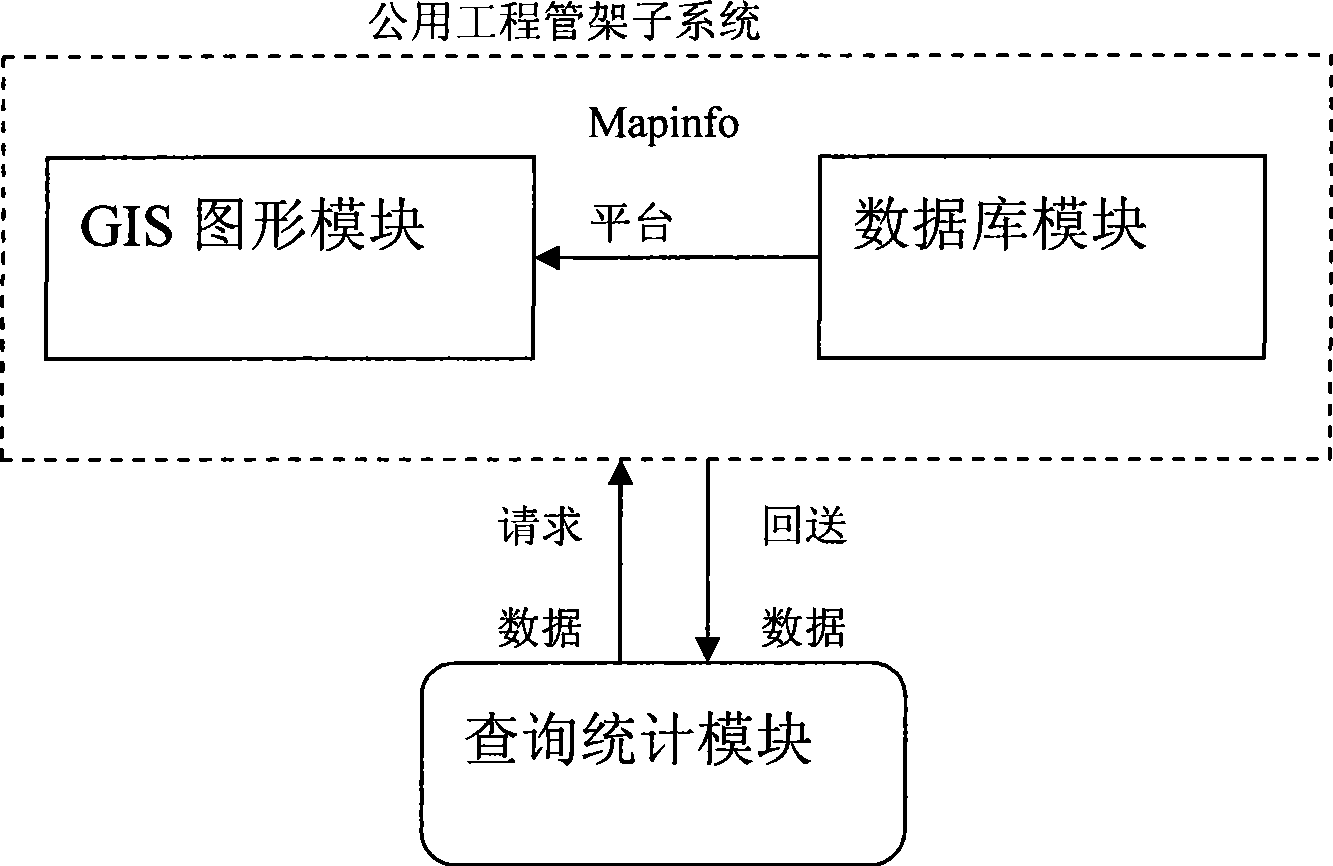
The invention discloses a chemical data management information system. The structure of the system comprises a client computer, an application server and a database server which are connected through a network. A software system comprises three independent subsystems, namely, a process equipment technical subsystem, a concealed engineering subsystem and a common pipe frame subsystem. The chemical data management information system is characterized in that a module part inside the database server comprises a Mapinfo platform for receiving external original data, wherein the Mapinfo platform is connected with a layer editor module and a database storage module respectively; the layer editor module is connected with a gallery for storing information on the map layer of the entire system, and the gallery can also be connected with a layer management module capable of outputting map information; moreover, besides being connected with a data backup module ensuring data security of the entire system, the database storage module is respectively connected with a data maintenance module, a query statistical module, an accident analysis module and an early warning prompting module which are for server data processing and information output.
Owner:SHANGHAI WUJING CHEM
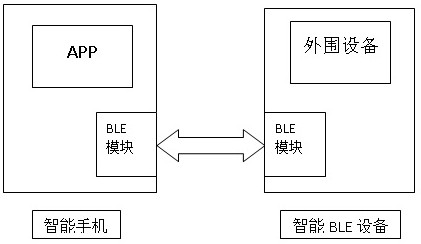
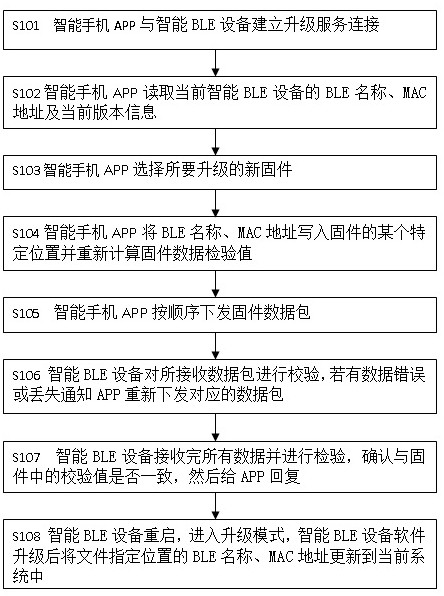
Method for reserving BLE name and MAC address in Bluetooth firmware upgrading
ActiveCN109951842ASolve the technical problem of brushing offImprove securityShort range communication serviceSoftware deploymentData terminalNetwork packet
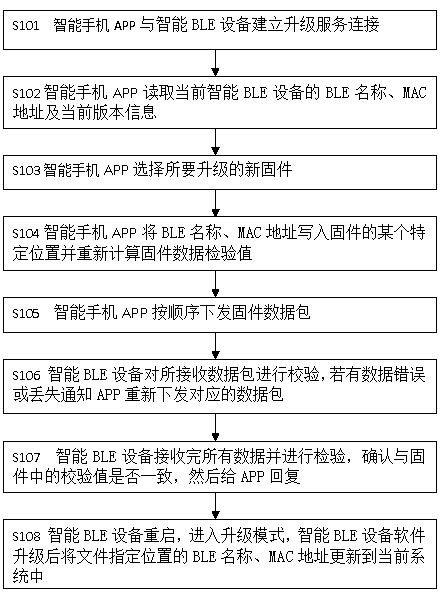
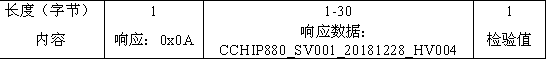
The invention relates to the technical field of wireless communication, in particular to a method for reserving a BLE name and a MAC address in Bluetooth firmware upgrading, comprising the following specific steps: step 1(S101), establishing an upgrading service connection between a mobile intelligent data terminal and an intelligent BLE device; step 2(S102) the mobile intelligent data terminal reads the BLE name, the MAC address and the current version information of the connected intelligent BLE device; step 3(S103), the mobile intelligent data terminal selects new firmware to be upgraded; step 4(S104) the mobile intelligent data terminal writes the BLE name and the MAC address into a certain specific position of the firmware and recalculates a firmware data inspection value; and step 5(S105) the mobile intelligent data terminal issues the firmware data packet and the like in sequence. The method has the advantages that the technical problem that in the prior art, due to the fact that firmware of the intelligent BLE device is updated, the BLE name and the MAC address are brushed away is solved, the safety of data writing is improved, random modification and tampering of data areavoided, and the upgrading cost is effectively reduced.
Owner:厦门市思芯微科技有限公司
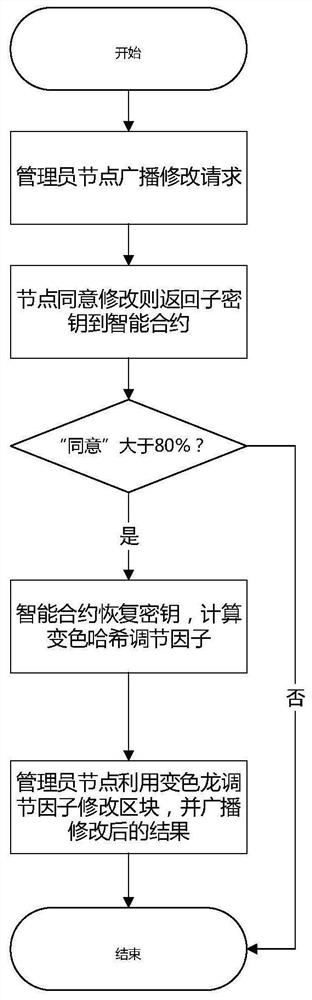
Blockchain editing method based on distributed key management
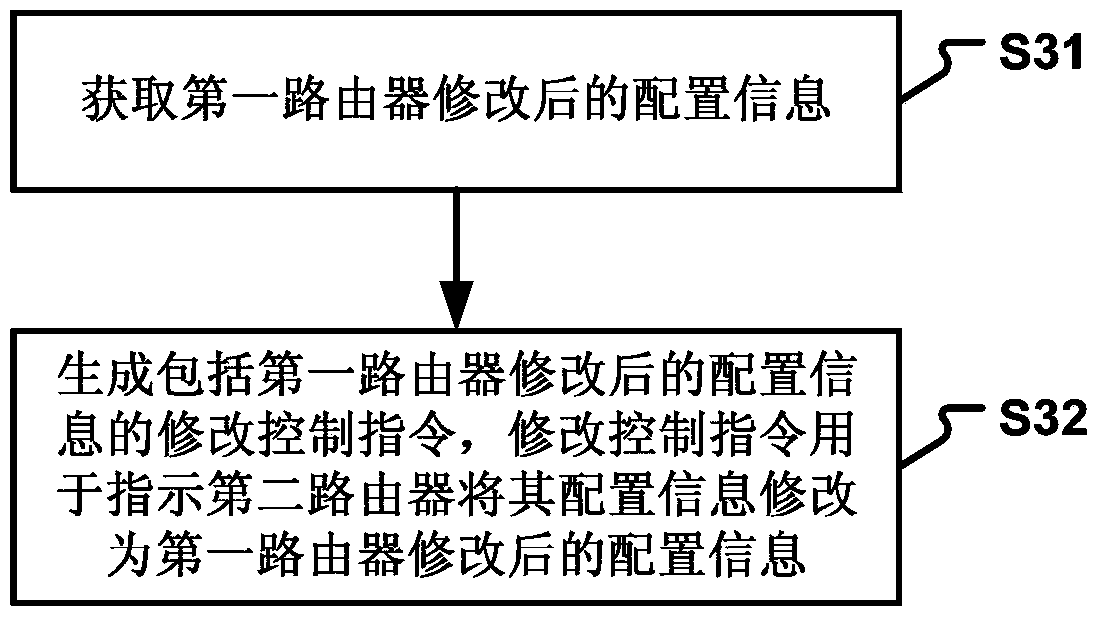
InactiveCN112437069AImplement modificationAccurate timingKey distribution for secure communicationFinanceComputer networkHash function
The invention provides a blockchain editing method based on distributed key management, which comprises the following steps: generating a key through a chameleon hash function based on identity information, and then dividing the secret into a plurality of sub-secrets through a threshold segmentation scheme; deploying an intelligent contract at the management node, wherein the intelligent contractis responsible for calculation operation of the secret key; enabling the management node to broadcast a block modification request to other nodes; enabling the other nodes to return the sub-keys to the management node after receiving the request; enabling the management node to perform asymmetric decryption on the received sub-key and recovers the complete key; enabling the management node to callan intelligent contract, and enabling the intelligent contract to perform random number calculation according to the information of the management node; and enabling the supervision node to completeblock editing according to the calculated random number and broadcast an edited result to other nodes. Compared with the prior art, the blockchain editing method based on distributed key management provided by the invention is high in key distribution management and security and easy to implement.
Owner:HUNAN TIAN HE GUO YUN TECH CO LTD +1
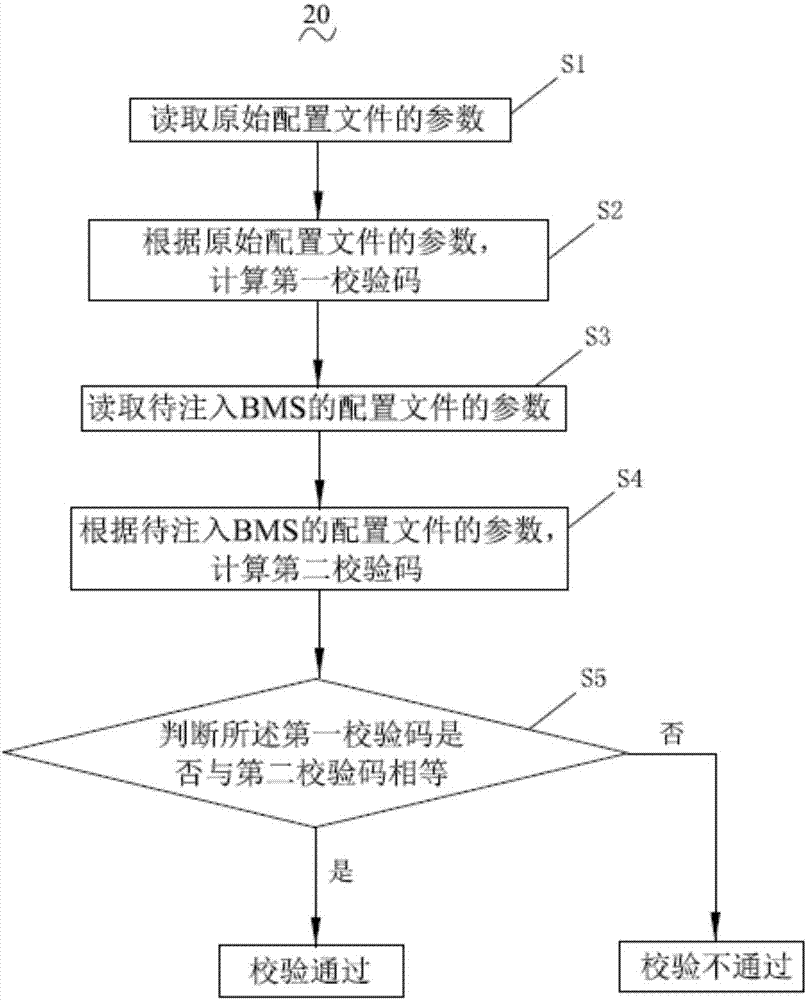
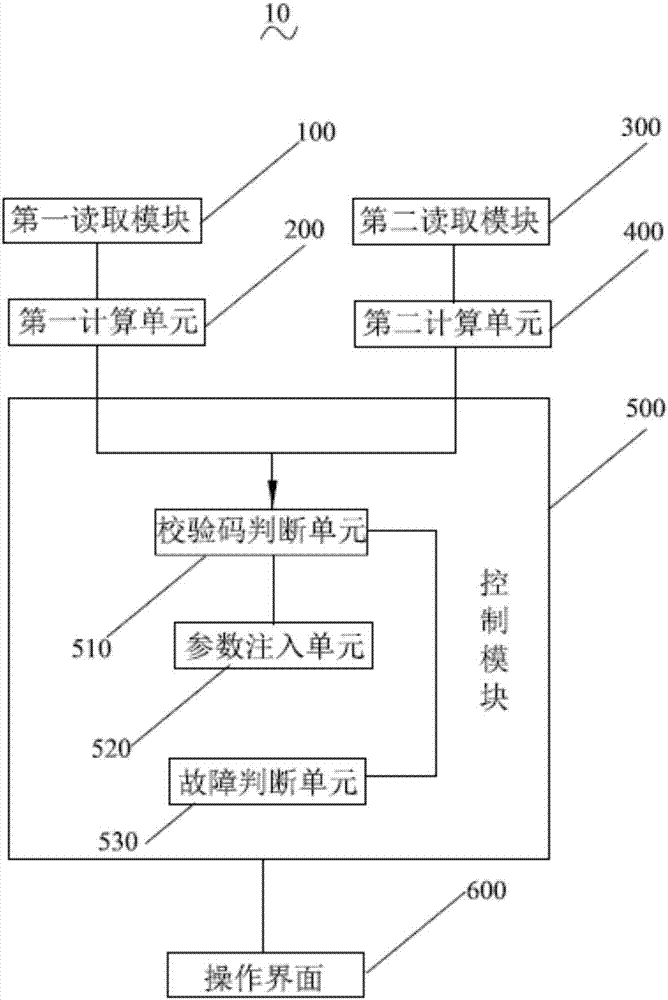
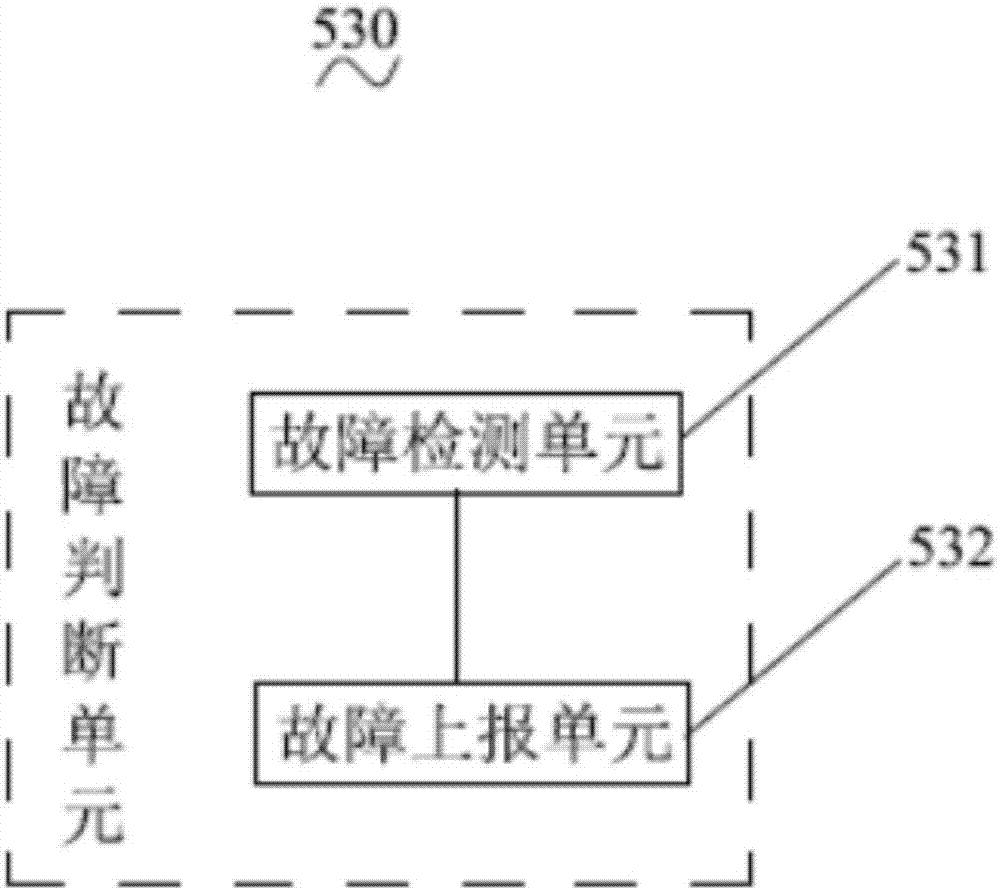
Method and system for preventing configuration document from being tampered and monitoring upper computer
InactiveCN106874777APrevent tamperingPrevent random modificationDigital data protectionProgram loading/initiatingProtection ProfileSoftware engineering
The invention discloses a method and a system for preventing a configuration document from being tampered and a monitoring upper computer. The method comprises the following steps: S1) reading parameters of an original configuration document; S2) calculating a first check code according to the parameters of the original configuration document; S3) reading the parameters of the configuration document to be injected with BMS; S4) calculating a second check code according to the parameters of the configuration document to be injected with BMS; S5) judging if the first check code is equal to the second check code, if so, passing the verification, and if not, failing to pass the verification. In order to solve the problem that the parameters can be randomly updated onsite, the invention provides the method and the system for preventing the configuration document from being tampered, so that the configuration document can be protected from being tampered and the onsite technician can be prevented from randomly altering the parameters of the configuration document and injecting the fault parameters of the configuration document into BMS. The parameters of the configuration document can be prevented from being tampered, the onsite debugging support staff can be prevented from altering the parameters to result in incorrect system configuration and disordered parameters and the system safety can be promoted.
Owner:HUIZHOU BNET TECH CO LTD
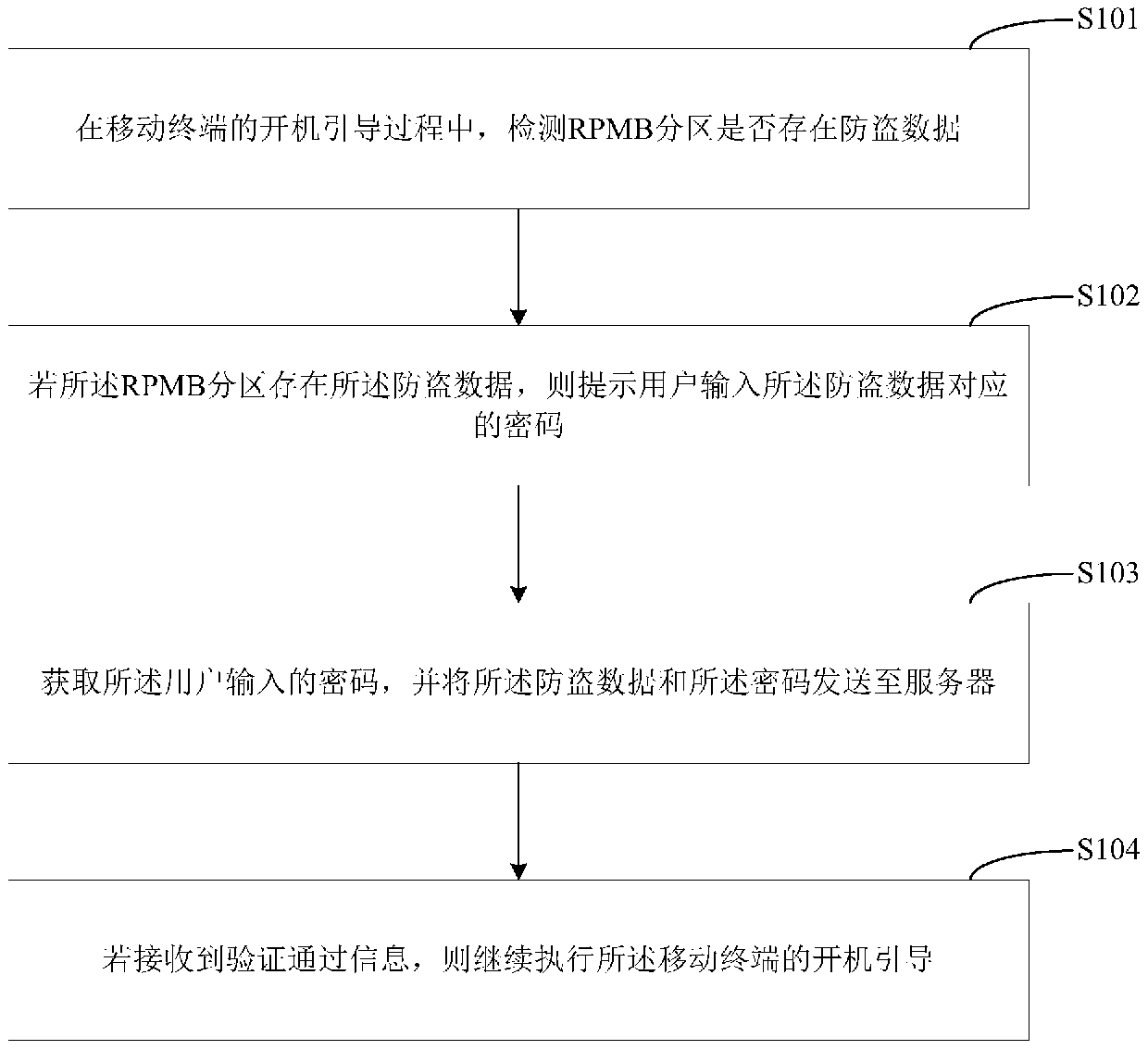
Information protection method, information protection device and mobile terminal
ActiveCN110598384AReal-time protectionAchieve protectionUser identity/authority verificationInternal/peripheral component protectionPasswordUser input
The invention is suitable for the technical field of mobile communication, and provides an information protection method, an information protection device and a mobile terminal, and the method comprises the steps: detecting whether there is antitheft data in a replay protected memory block RPMB partition or not in a start-up guide process of the mobile terminal; if the RPMB partition has the antitheft data, prompting a user to input a password corresponding to the antitheft data; obtaining the password input by the user, and sending the anti-theft data and the password to a server; and if theverification passing information is received, continuing to execute the startup guidance of the mobile terminal. According to the invention, the information in the mobile terminal can be protected under the condition that the mobile terminal is lost or stolen.
Owner:OPPO CHONGQING INTELLIGENT TECH CO LTD
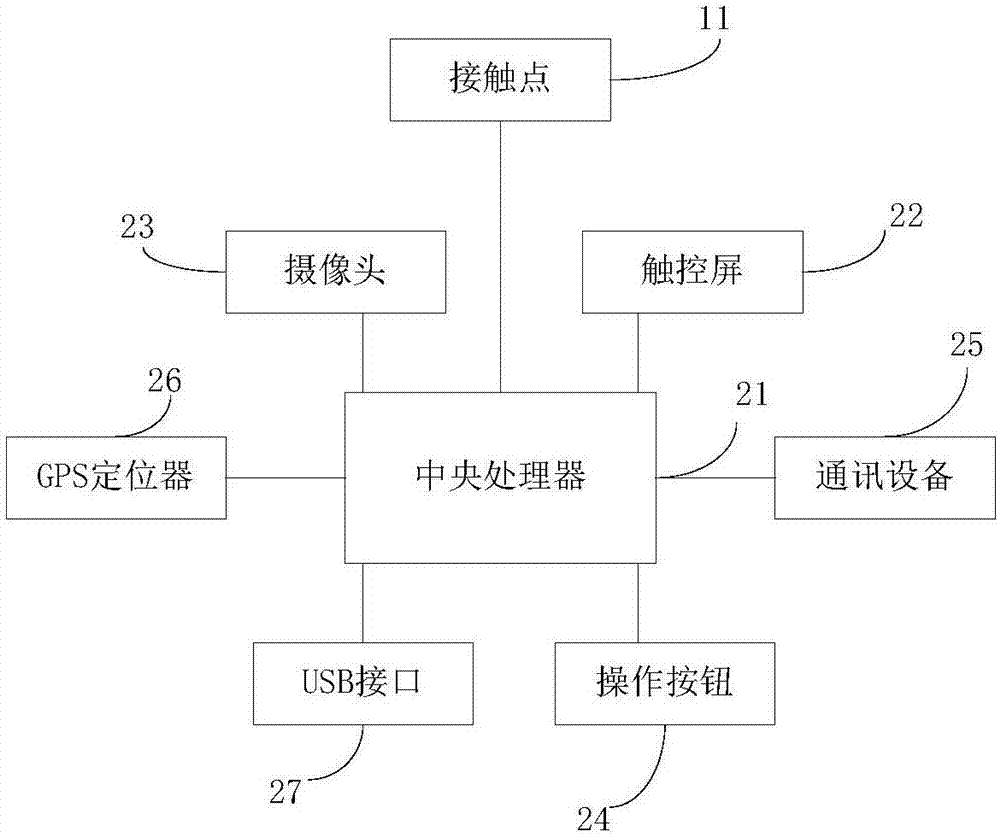
Intelligent key and control system thereof
InactiveCN107103669AMeet environmental requirementsMeet the use requirementsIndividual entry/exit registersControl systemComputer terminal
The invention discloses an intelligent key, which comprises a mobile terminal and a key head installed at the top of the mobile terminal. The mobile terminal comprises a casing, a touch screen is installed on the front surface of the casing, operating buttons are installed on the lower side of the touch screen, a camera is installed on the back surface of the casing, a central processor and an accumulator are installed inside the casing, the touch screen, the operating buttons and the camera are in circuit connection with the central processor, a communication apparatus is installed inside the casing and is in circuit connection with the central processor, and a contact point is installed on the key head and is in circuit connection with the central processor. In addition, the invention discloses a control system of the intelligent key. The intelligent key of the invention integrates a mobile terminal and an electronic key, and has two ways of communication unlocking and touch unlocking. The control system of the intelligent key records unlocking actions, and effectively ensures security and traceability.
Owner:NINGBO HI-TECH DISTRICT RUIAO OPTOELECTRONIC TECH CO LTD
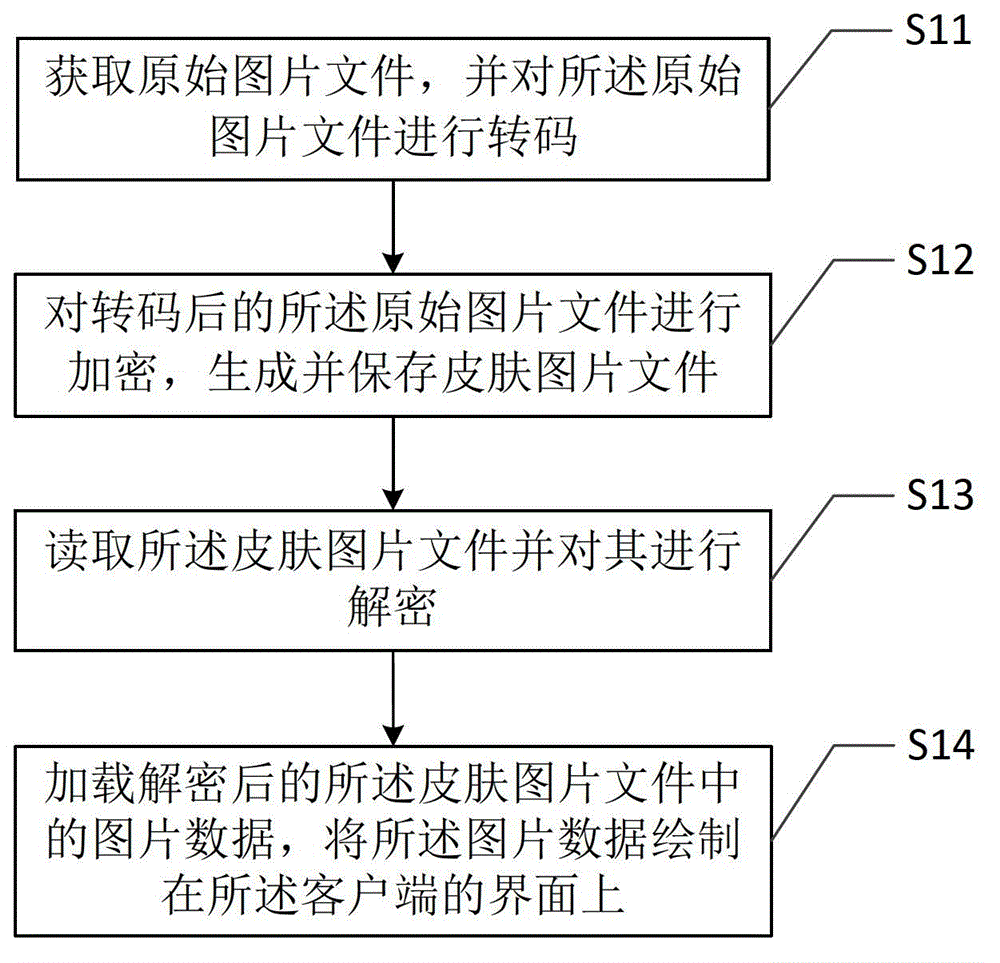
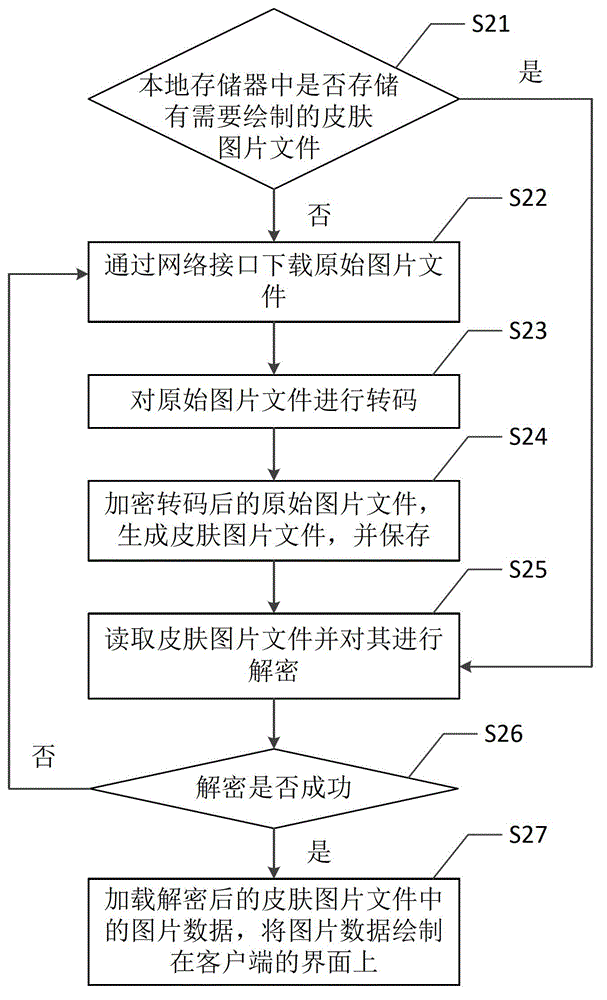
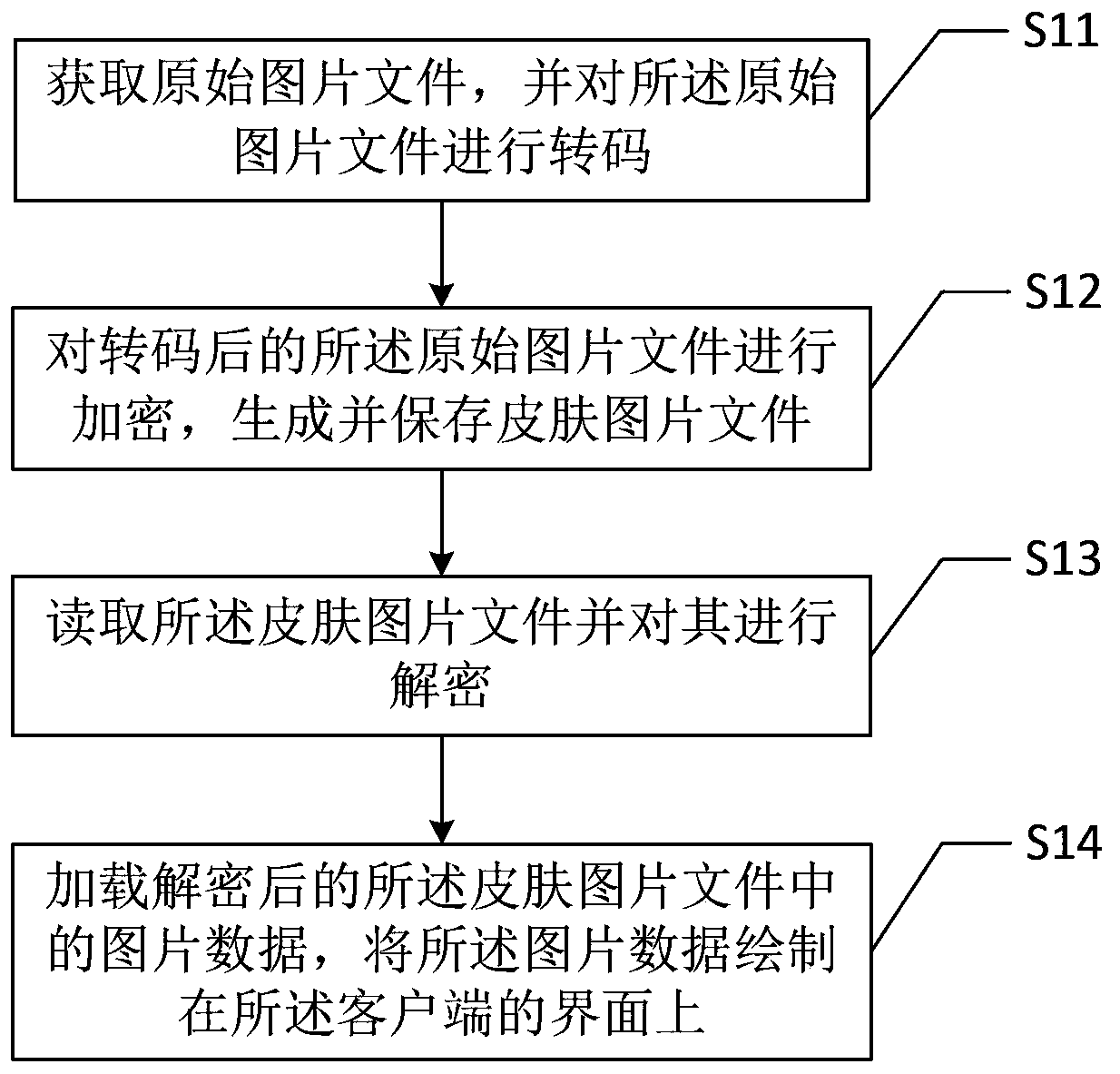
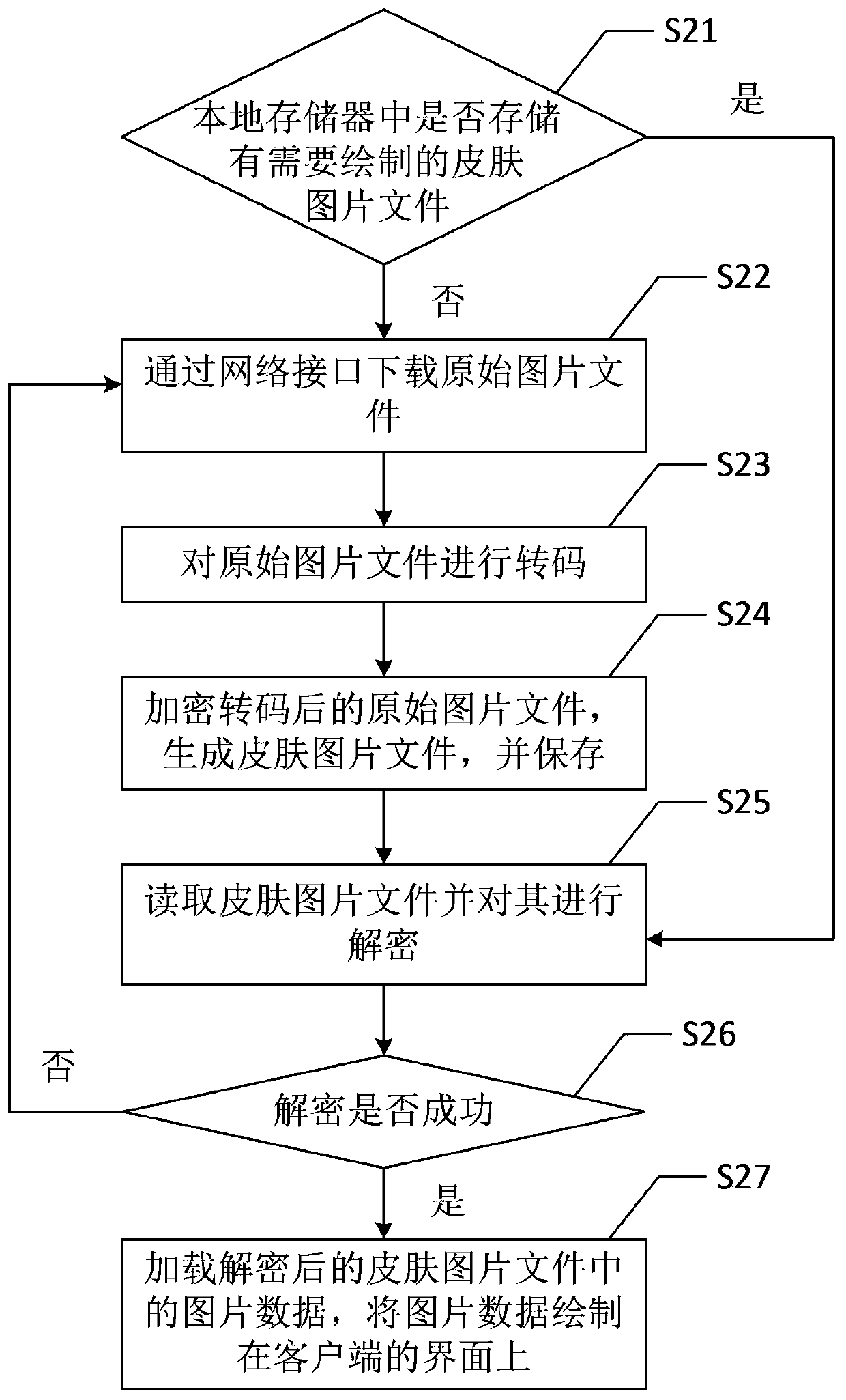
Client skin picture drawing method and client skin picture drawing device
ActiveCN104102504AImprove drawing efficiencyPrevent random modificationProgram loading/initiatingProgram/content distribution protectionClient-sideComputer graphics (images)
The invention provides a client skin picture drawing method. The method comprises the following steps: acquiring an original picture file and transcoding the original picture file; encrypting the transcoded original picture file and generating a skin picture file; reading the skin picture file and decrypting the skin picture file; loading picture data in the decrypted skin picture file and drawing the picture data on an interface of a client. Furthermore, the invention also provides a client skin picture drawing device. The client skin picture drawing method and the client skin picture drawing device have higher efficiency in drawing client skin pictures, and can be used for effectively protecting the picture data of the client skin picture file.
Owner:TENCENT TECH (SHENZHEN) CO LTD
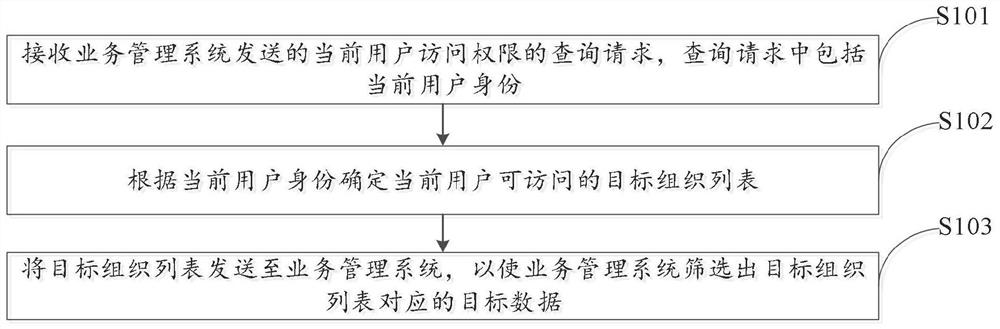
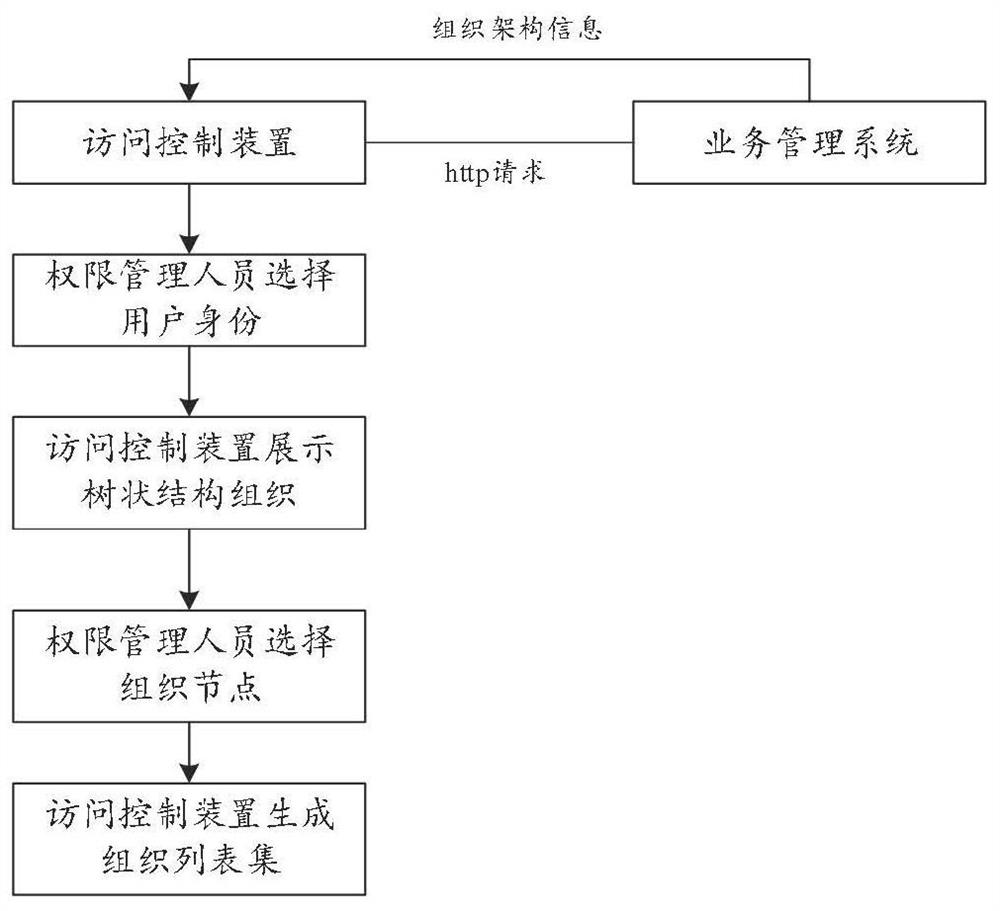
User access permission control method and device, electronic equipment and storage medium
PendingCN114065248AAvoid data breachesAvoid security issuesDigital data protectionBusiness managementEngineering
The invention relates to a user access permission control method and device, electronic equipment and a storage medium. The method comprises the steps of: receiving a query request of the access permission of a current user sent by a business management system, the query request comprising the identity of the current user; determining a target organization list which can be accessed by the current user according to the identity of the current user; and sending the target organization list to the business management system, so as to enable the business management system to screen out target data corresponding to the target organization list. The problems of data leakage and low data security of the business management system caused by the fact that a user randomly modifies the target organization list or maliciously modifies the target organization list by adopting other malicious tools are avoided.
Owner:GUANGZHOU PINWEI SOFTWARE
Animal electronic ear tag
InactiveCN109275586ASimple structurePrevent random modificationAnimal husbandryMemory chipWireless transmission
The invention discloses an animal electronic ear tag. The animal electronic ear tag comprises a main tag, an auxiliary tag and cover plates with clamping feet, wherein an ear tag head is arranged on an ear tag neck on the back surface of the main tag, the ear tag head is of a cone structure, and an annular groove is formed in the bottom of the ear tag head; the ear tag head is embedded in the auxiliary tag, the clamping feet of the cover plates are connected in the groove in a clamped mode, and the cover plates and the auxiliary tag are locked tightly; a chip mounting slot is formed in the front surface of the main tag, an electronic identifier is arranged in the chip mounting slot, and the outer side of the electronic identifier is covered with a baffle; a clamping slot is formed in the part, located on the outer side of the baffle, of the inner wall of the chip mounting slot, sealing plastic is disposed at the slot mouth of the chip mounting slot and is clamped in the clamping slot,and the electronic identifier includes a memory chip, a wireless transmission module and an encoder; and the memory chip is connected to the wireless transmission module through the encoder. The animal electronic ear tag has a simple structure, convenience and practicability.
Owner:吴绍飞
Medal of patent certificate
ActiveCN103110246BImprove seismic performanceMoisture-proof and anti-magneticMedalBadgesPatent CertificationIntellectual property
The invention discloses a medal of a patent certificate. The medal is characterized in that a hanging fastener is arranged at the back of a medal body; a data interface is formed in the side of the medal body; the patent certificate and other information of the patent are stored in the medal body; colors and image-text for a cover of the paper patent certificate are shown on the front surface of the medal body; a pendant is connected below the medal body by a connection buckle; the medal of the patent certificate is applied for a state intellectual property office by an applicant; the medal is issued by the state intellectual property office; data stored by the medal body is recorded by the state intellectual property office in an encryption mode; and the applicant can update the data stored by the medal by virtue of a representative office of the state intellectual property office, connects the pedal of the patent certificate with a computer, inputs a password to read out contents by virtue of the computer and wears the medal on an important occasion, so that the medal is convenient to carry, a plurality of patent certificates and patent information are convenient to manage, the patent certificates and patent contents are convenient to display, the honor of the applicant and an inventor is improved, and the practicability is high.
Owner:SUZHOU BIJIA INTERNET TECH CO LTD
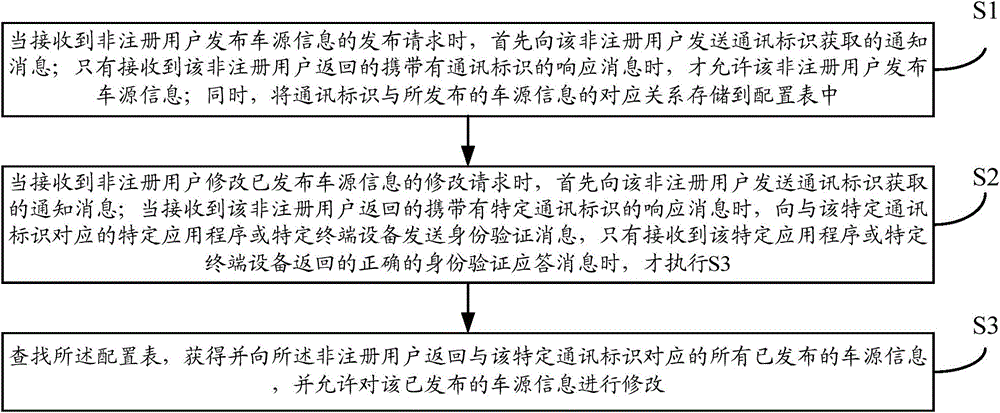
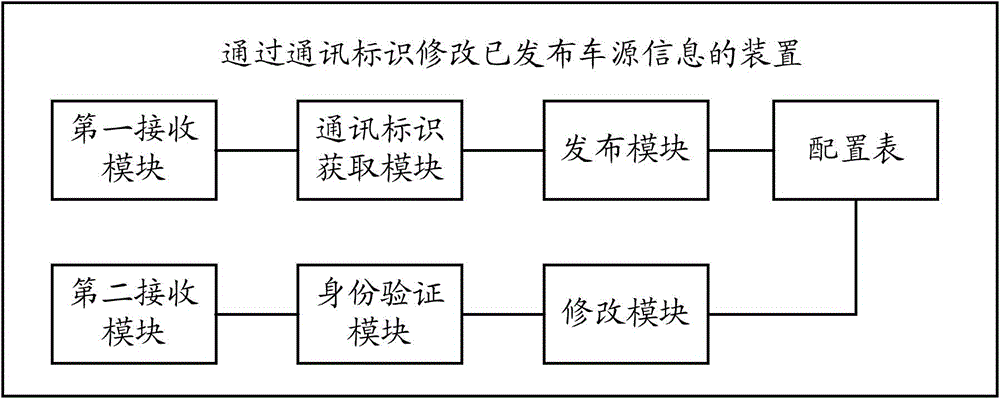
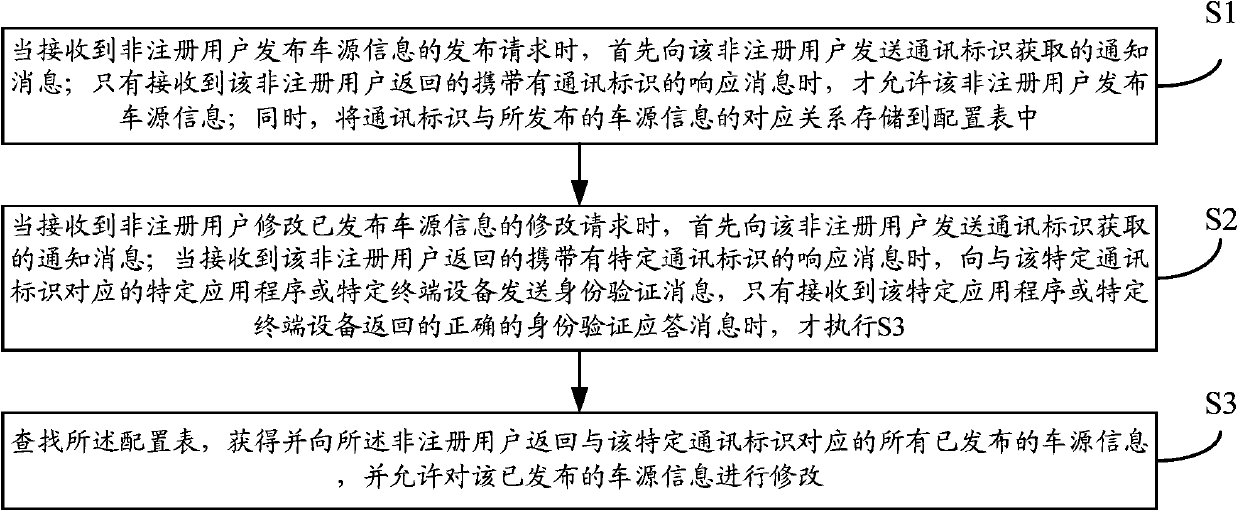
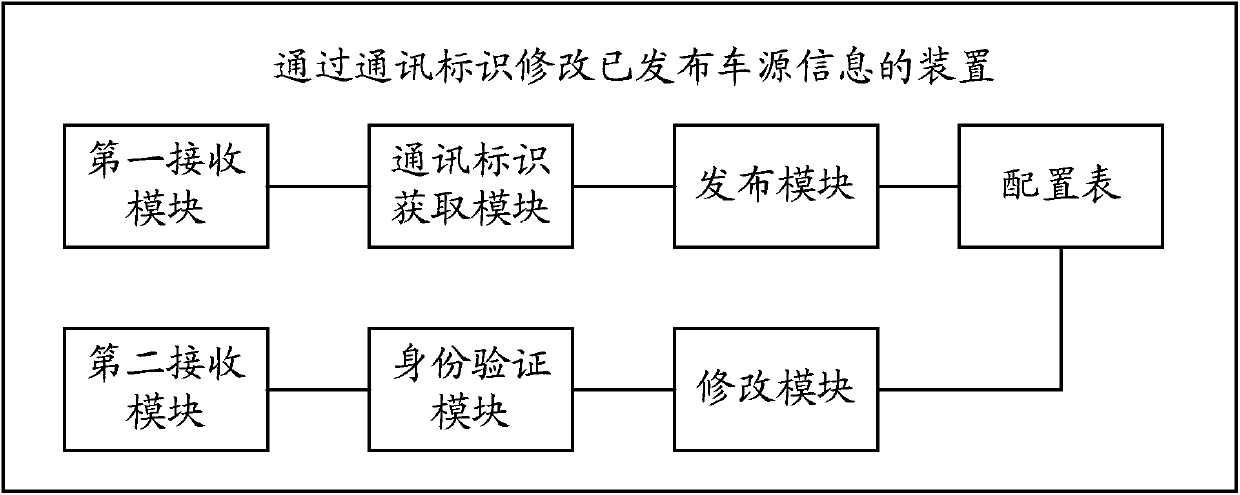
Method and device for modifying released vehicle source information through communication identifiers
ActiveCN104468480AEasy to operatePrevent random modificationData switching networksReal-time computingRegistered user
The invention provides a method and a device for modifying released vehicle source information through communication identifiers. The method comprises the following steps: the corresponding relationship between communication identifiers and released vehicle source information is stored in a configuration table; when a request of a non-registered user for modifying released vehicle source information is received, a notification message acquired by a communication identifier is sent to the non-registered user; when a response message carrying a specific communication identifier returned by the non-registered user is received, an identity authentication message is sent to a specific application program or specific terminal device corresponding to the specific communication identifier; and only when a correct identity authentication response message returned by the specific application program or specific terminal device is received, the configuration table is queried, all released vehicle source information corresponding to the specific communication identifier is obtained and returned to the non-registered user, and the non-registered user is allowed to modify the released vehicle source information. The method and the device of the invention enable non-registered users to conveniently modify vehicle source information released on websites, and have the advantage of simple and convenient operation.
Owner:BEIJING QIERBULAITE TECH
Animal ear tag with mosquito and fly repellent function
InactiveCN106305475ASimple structurePrevent random modificationAnimal husbandryWireless transmissionEar tag
The invention discloses an animal ear tag with a mosquito and fly repellent function. The animal ear tag comprises a main tag, an auxiliary tag and a cover plate with a clamp pin, wherein an ear tag head is arranged on an ear tag neck arranged at the back side of the main tag; the ear tag head is of a conical structure; an annular groove is formed in the bottom of the ear tag head; the ear tag head is embedded in the auxiliary tag; the clamp pin of the cover plate is clamped and connected in the groove; in addition, the cover plate and the auxiliary tag are tightly locked; a chip installing groove is formed in the front side of the main tag; an electronic recognizer is arranged in the chip installing groove; a baffle plate covers the outer side of the electronic recognizer; a clamp groove is formed in the inner wall of the chip installing groove and is positioned at the outer side of the baffle plate; encapsulation plastic cement is arranged at the notch position of the chip installing groove, and is clamped in the clamp groove; the electronic recognizer comprises a storage chip, a wireless transmission module and an encoder; the storage chip is connected with the wireless transmission module through an encoder; a round hole is formed in the ear tag neck; volatile mosquito repellent medicine is put in the round hole.
Owner:BEIHAI YUNXIN ELECTRONICS TECH
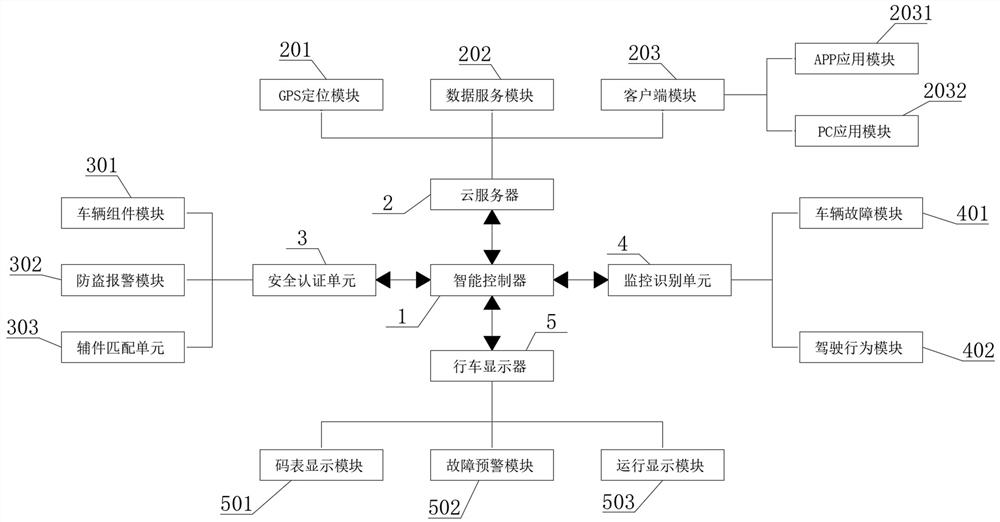
Safety electric control system of electric vehicle
PendingCN114291103AConvenient remote security monitoringPrevent random modificationTransmission systemsElectric/fluid circuitDisplay deviceElectric cars
The invention discloses an electric vehicle safety electronic control system, which comprises an intelligent controller, a cloud server, a safety certification unit, a monitoring identification unit and a driving display, and is characterized in that the intelligent controller is electrically connected with the safety certification unit, the monitoring identification unit and the driving display through wires. With the adoption of the structure, the intelligent controller is adopted to control the cloud server, so that a user can conveniently carry out remote safety monitoring on a vehicle, and the intelligent controller is adopted to control the safety certification unit, so that safety certification can be conveniently carried out on components and vehicle accessories of the vehicle; the intelligent controller is adopted to control the monitoring and identifying unit, so that whether the running state of a vehicle is safe or not can be conveniently monitored, and the intelligent controller is adopted to control the driving display, so that man-machine interaction active reminding display can be conveniently carried out; therefore, through the electronic control system, the vehicle safety and the personal safety of the user can be guaranteed conveniently.
Owner:LIMA VEHICLE IND GRP
Method for modifying published vehicle source information through communication identification
ActiveCN104468480BEasy to modifyEasy to operateData switching networksTerminal equipmentLookup table
The present invention provides a method and device for modifying published vehicle source information through communication identification, including: storing the corresponding relationship between communication identification and released vehicle source information in a configuration table; When requesting modification of source information, firstly send a notification message of communication identification acquisition to the non-registered user; The program or a specific terminal device sends an authentication message, and only when it receives the correct identity verification response message returned by the specific application program or specific terminal device, it searches the configuration table, obtains and returns the specific communication ID to the non-registered user Corresponding to all published vehicle source information, and allows modification of the published vehicle source information. It is convenient for non-registered members to modify the vehicle source information published on the website, and has the advantage of simple and convenient operation.
Owner:BEIJING QIERBULAITE TECH
Animal ear tag and installation method
The invention discloses an animal ear tag and an installation method. The animal ear tag comprises a main tag, an auxiliary tag and a cover plate, wherein the cover plate is provided with clamping pins; an ear tag head is arranged on the ear tag neck at the back face of the main tag; the ear tag head is of a conical structure; an annular groove is formed in the bottom part of the ear tag head; the ear tag head is embedded in the auxiliary tag; the clamping pins of the cover plate are clamped in the groove, and the cover plate is locked with the auxiliary tag; the front face of the main tag is provided with a chip installation groove; the chip installation groove is internally provided with an electronic identifier; the outer side cover of the electronic identifier is provided with a baffle plate; a clamping groove is formed in the inner wall, positioned at the outer side of the baffle plate, of the chip installation groove; packaging plastic is arranged at the groove opening of the chip installation groove, and is clamped in the clamping groove; the electronic identifier comprises a memory chip, a wireless transmission module and an encoder; the memory chip is connected with the wireless transmission module through the encoder. The animal ear tag has the advantages of simple structure, convenience and practicability.
Owner:BEIHAI YUNXIN ELECTRONICS TECH
Electronic ear tag for animals
InactiveCN109548678ASimple structurePrevent random modificationAnimal husbandryEar tagWireless transmission
The invention discloses an electronic ear tag for animals. The electronic ear tag comprises a main tag, an auxiliary tag and a cover plate with a clamp foot. An ear tag head is arranged on an ear tagneck on the back surface of the main tag and is of a conical structure, an annular groove is formed in the bottom of the ear tag head, the ear tag head is inlaid in the auxiliary tag, the clamp foot of the cover plate is clamped in the groove, the cover plate is locked with the auxiliary tag, a chip mounting groove is formed in the front surface of the main tag, an electronic identifier is arranged in the chip mounting groove, a barrier covers the electronic identifier, a clamp groove is formed in the inner wall of the chip mounting groove and is particularly formed in the outer side of the barrier, and encapsulation plastic is arranged at a notch of the chip mounting groove and is clamped in the clamp groove; the electronic identifier comprises storage chips, wireless transmission modulesand encoders, and the storage chips are connected with the wireless transmission modules by the encoders. The electronic ear tag has the advantages of simple structure, convenience and practicality.
Owner:南京誉凯电子科技有限公司
A method for retaining ble name and mac address in bluetooth firmware upgrade
ActiveCN109951842BSolve the technical problem of brushing offImprove securityShort range communication serviceSoftware deploymentData terminalData pack
The present invention relates to the technical field of wireless communication, in particular to a method for reserving a BLE name and a MAC address in a Bluetooth firmware upgrade. The specific steps include: step 1 (S101), establishing an upgrade service connection between a mobile smart data terminal and a smart BLE device; step 2 (S102), the mobile smart data terminal reads the BLE name, MAC address and current version information of the connected smart BLE device; Step 3 (S103), the mobile smart data terminal selects the new firmware to be upgraded; Step 4 (S104), The mobile intelligent data terminal writes the BLE name and MAC address into a specific location of the firmware and recalculates the firmware data inspection value; Step 5 (S105), the mobile intelligent data terminal sends firmware data packets in sequence, etc. Beneficial effects: Solve the technical problem of BLE name and MAC address being wiped out due to smart BLE device firmware update in the existing related technologies, improve the security of data writing, prevent data from being modified and tampered at will, and effectively reduce upgrade costs .
Owner:厦门市思芯微科技有限公司
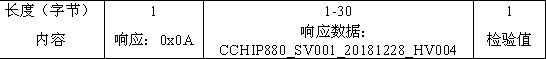
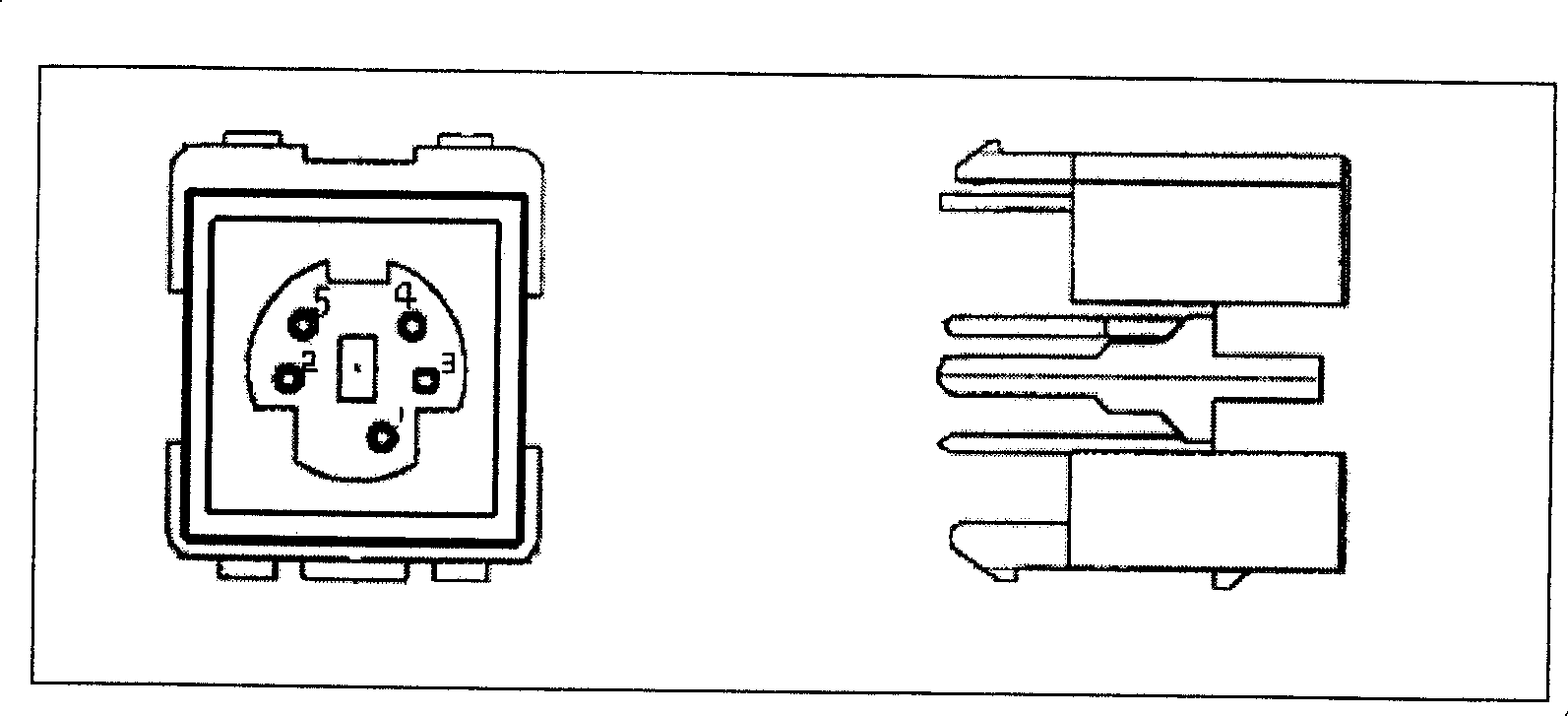
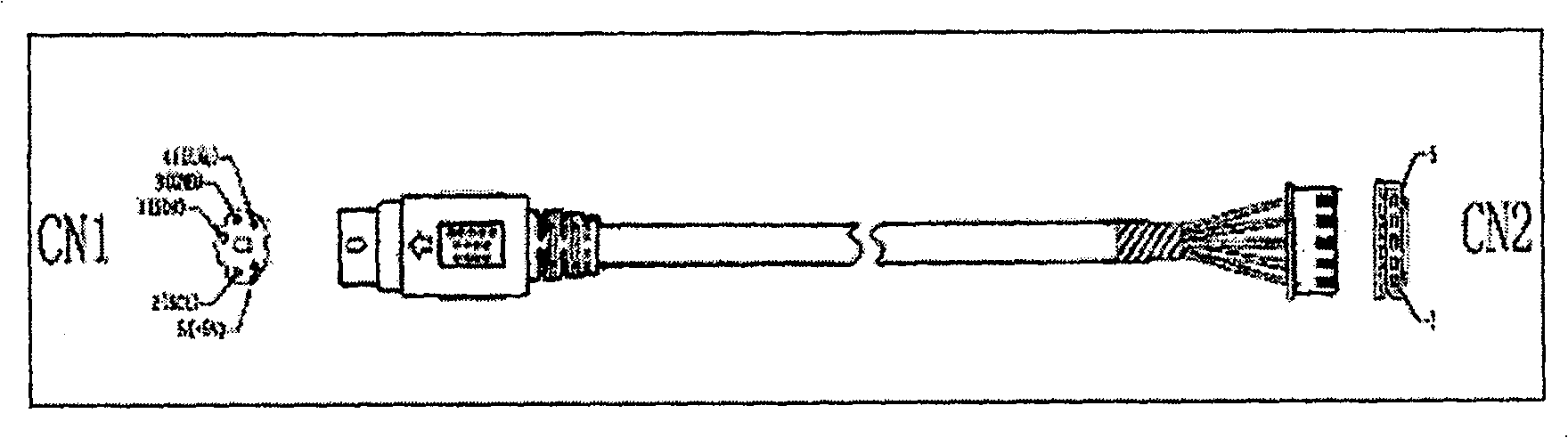
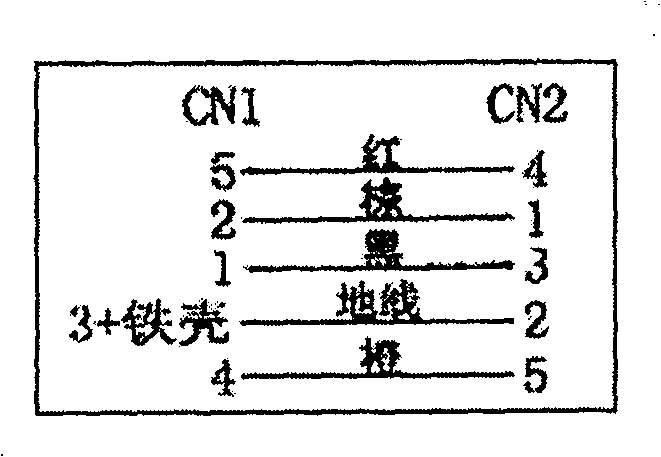
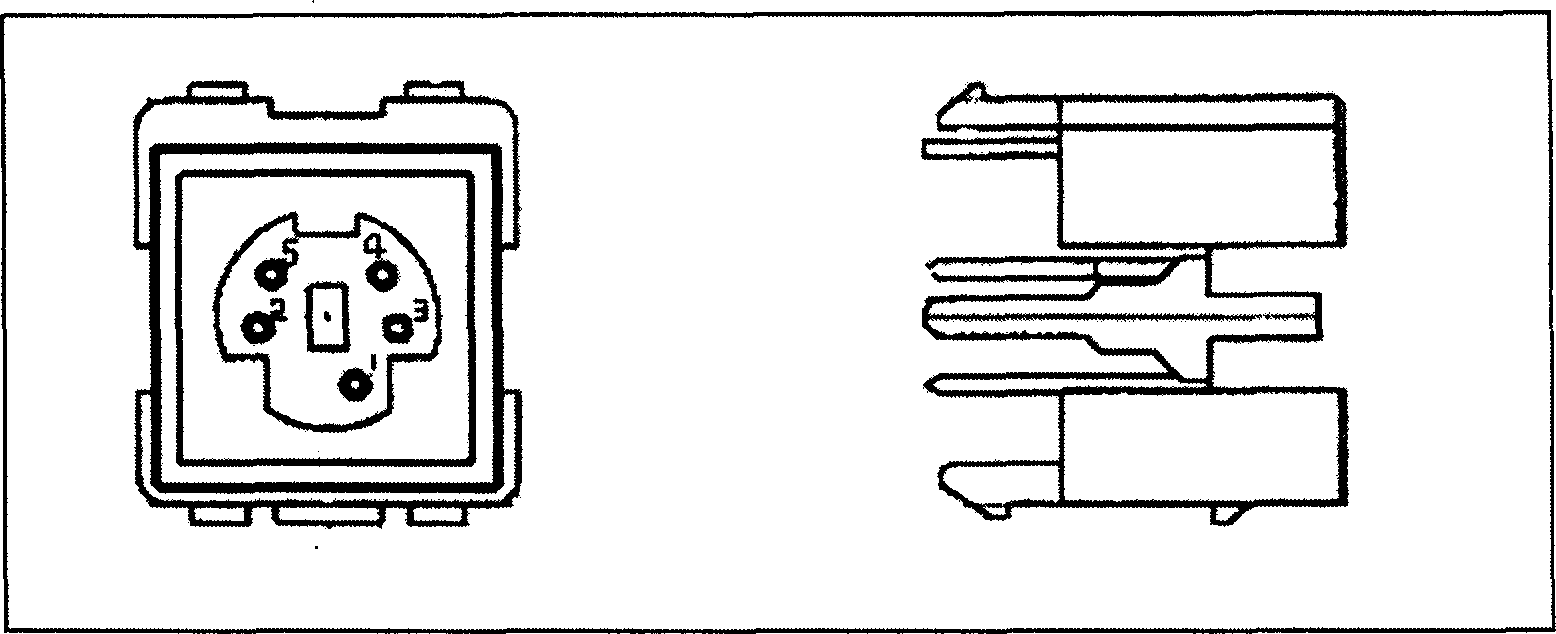
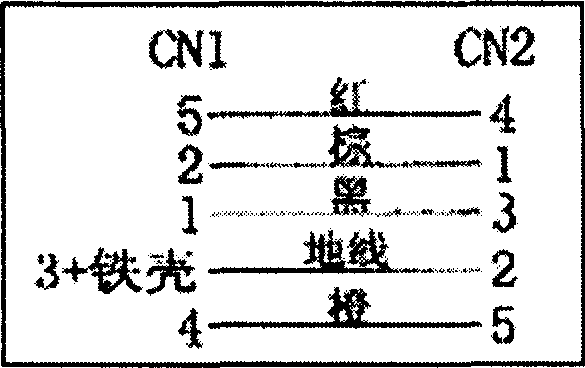
Interface apparatus based on I2C bus and read-write apparatus employing the same
The invention relates to an interface device based on I2C bus and relative read-write equipment, wherein the interface device comprises: SCL terminal, SDA terminal, VCC terminal, GND terminal, and ID terminal; the cable meeting the I2C bus interface connects the I2C bust with the external memory via said interface device, to process the read-write operation; and via connecting the interface device to MCU, the data memory can form read-write equipment, to read-write data quickly, to support the system upgrade and debug data modification of electric product.
Owner:SHENZHEN TCL NEW-TECH CO LTD
A client skin picture drawing method and drawing device
ActiveCN104102504BImprove drawing efficiencyPrevent random modificationExecution for user interfacesProgram/content distribution protectionComputer graphics (images)
The invention provides a client skin picture drawing method. The method comprises the following steps: acquiring an original picture file and transcoding the original picture file; encrypting the transcoded original picture file and generating a skin picture file; reading the skin picture file and decrypting the skin picture file; loading picture data in the decrypted skin picture file and drawing the picture data on an interface of a client. Furthermore, the invention also provides a client skin picture drawing device. The client skin picture drawing method and the client skin picture drawing device have higher efficiency in drawing client skin pictures, and can be used for effectively protecting the picture data of the client skin picture file.
Owner:TENCENT TECH (SHENZHEN) CO LTD
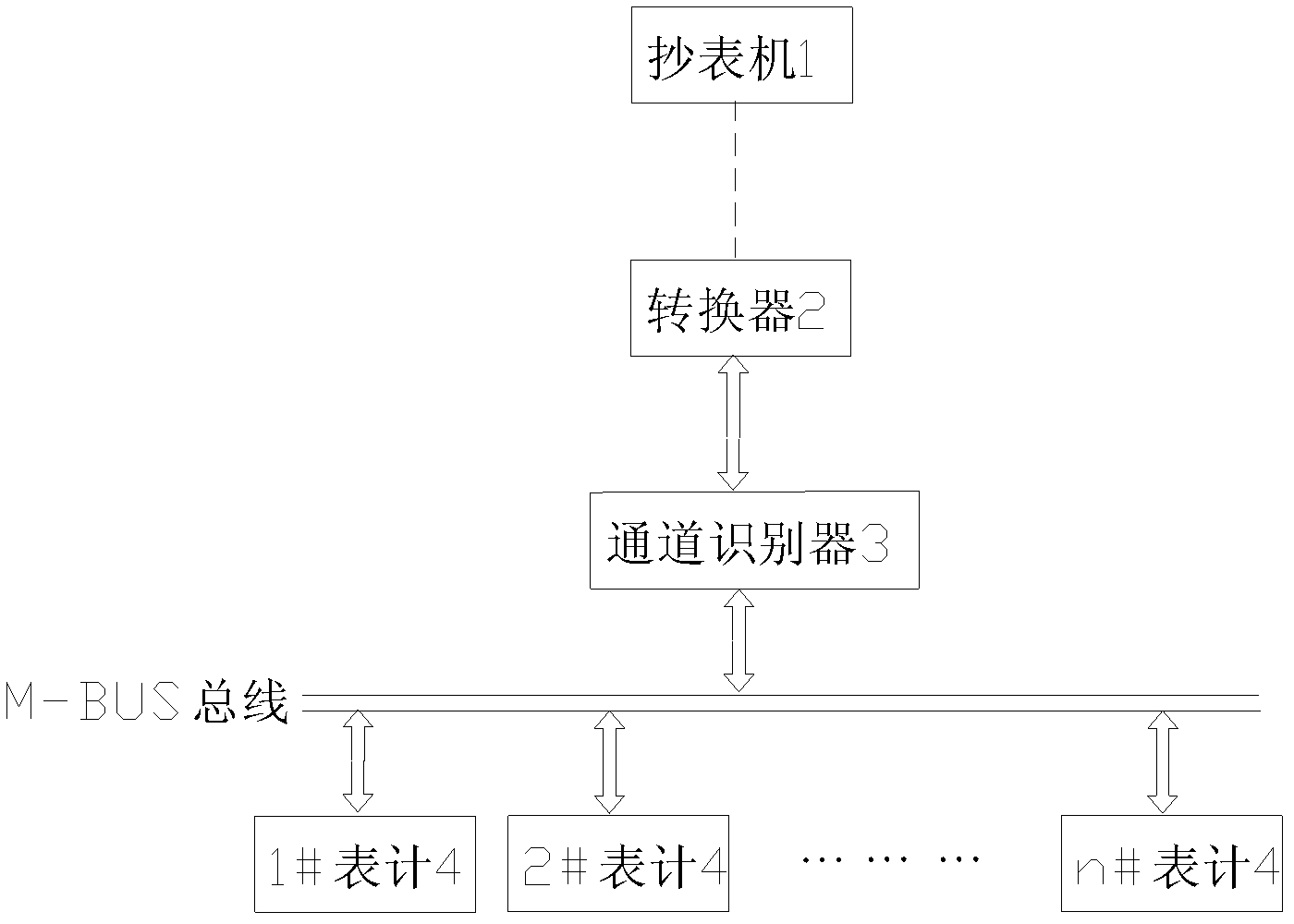
Semiautomatic meter reading device and meter reading method thereof
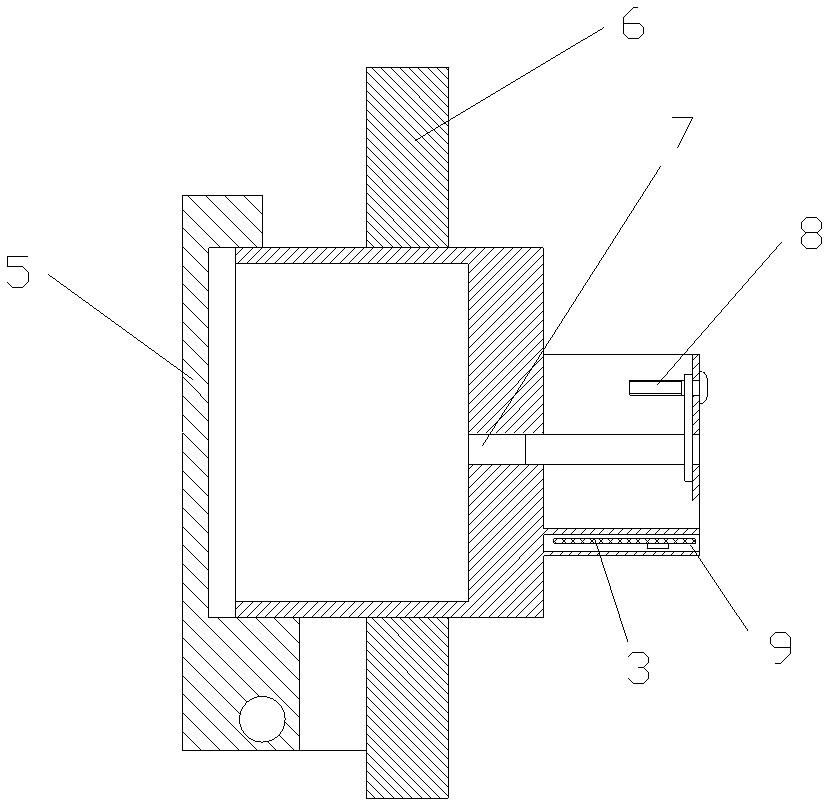
ActiveCN102419903BReduce construction difficultySolve the problem of difficult meter reading and household registrationElectric signal transmission systemsComputer scienceEnergy consumption
The invention relates to a meter reading device and a meter reading method, in particular to a semiautomatic meter reading device and a meter reading method thereof. The meter reading device comprises a meter, a converter and a meter reading machine, and also comprises a socket for the converter to be plugged, wherein the socket is connected with the meter in a M-BUS bus way, and the converter is wirelessly connected with the meter reading machine; a channel recognizer is installed inside the socket, and the channel recognizer is connected with the socket through a conducting wire; the channel recognizer comprises a micro-control unit, an identity identifier and a program for automatically generating a meter address list are embedded in the micro-control unit, and a memory unit for storing the identifier and the meter address list is also arranged inside the micro-control unit. When the meter is read, pins of the converter are connected with the socket, and an address list is generated by the channel recognizer so as to read the meter. Due to the adoption of the meter reading way, the problem that the meter reading device is difficult to acquire electricity and is difficultly grounded can be solved, the system operation energy consumption can be reduced, the size of the socket is small, and the installation space is saved.
Owner:QINGDAO IESLAB ELECTRONICS CO LTD
Reappearing method and system controlling river reach ship traveling dynamic and signal revealing process
ActiveCN103065503BAccurately grasp risky behaviorPrevent random modificationMarine craft traffic controlTime informationRadar
The invention discloses a reappearing method and a system for controlling river reach ship traveling dynamic and signal revealing process. The reappearing method comprises the following steps: collecting real-time information of dynamic and static information (automatic identification system (AIS) data and radar data) and videos of a traveling ship, very high frequency (VHF) call voice, signal tower command information and the like; compressing and storing the collected real-time information; and receiving reappearing orders, starting playback reappearing procedures, selecting a ship or a time quantum for playback reappearing, loading historical information, synchronously displaying information of ship positions corresponding to audios and videos, ship dynamic historical route, signal revealing time point, and the like. According to the reappearing method and the system, historical information of arbitrary come-and-go ships or within a time quantum can be found and used for synchronous playback, original record information of the audios and videos, ship dynamic tracks, signal revealing orders, and the like can be synchronously displayed in the whole course, and thus dynamic relevant evidence of the ship traveling dynamic and the signal revealing process is formed and can be used as a basis of accident analysis after an accident and signalman command effect evaluation.
Owner:CHONGQING UNIV +1
Encryption and decryption method and device for numerical value and storage medium
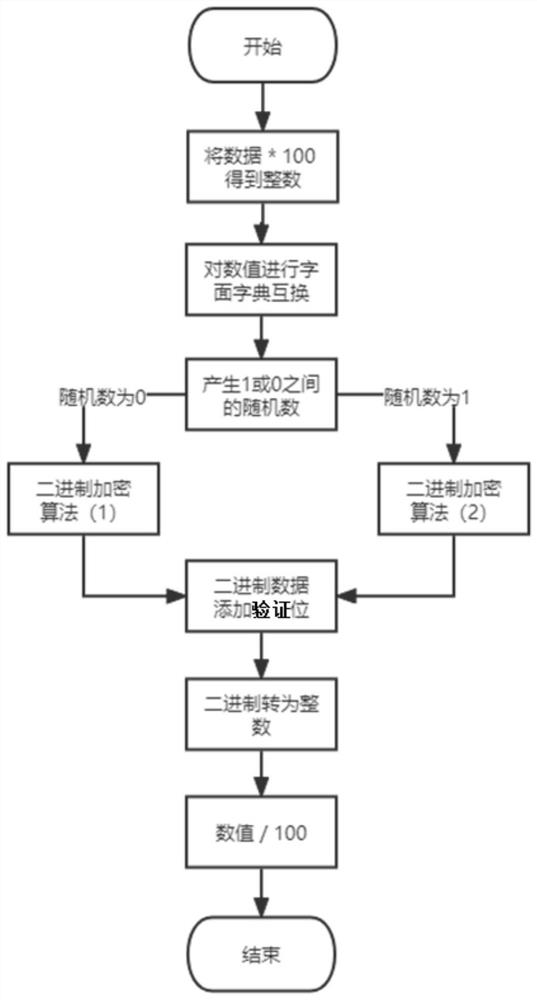
PendingCN114329530AAvoid crackingNo design changes requiredRandom number generatorsDigital data protectionAlgorithmSource Data Verification
The invention discloses a numerical value encryption and decryption method and device, and the encryption method comprises the steps: multiplying to-be-encrypted data by the M power of 10 to obtain a first integer value, carrying out the literal dictionary exchange of the first integer value, and converting the first integer value after the literal dictionary exchange into first binary data, M being 0 or a natural number; generating a random number 0 or 1, and performing binary encryption processing on the first binary data according to the random number to obtain second binary data; a verification bit and an algorithm bit are added to the right side of the second binary data; and converting the result added with the verification bit and the algorithm bit into a second integer value, dividing the second integer value by M power of 10, and converting the second integer value into an encryption value to obtain an encrypted result. According to the method, the original numerical value is converted into another effective numerical value to facilitate use and transmission by performing various means such as dictionary conversion, random binary data conversion encryption algorithm and data verification bit addition on the numerical value. In the decryption process, verification and reverse operation are carried out on the encrypted data to obtain an original value with unchanged precision.
Owner:深圳市米软科技有限公司
Method and device for modifying router configuration information
ActiveCN105245382BEasy to operateReduce configuration timeData switching networksSoftware engineering
The invention provides a router configuration information modifying method and device. The method comprises the steps that configuration information modifying information sent by a first router is received; a modifying control command is generated according to the modifying information; the modifying control command is sent to a second router, wherein the second router is a router which logs a network side account through the same account information with the first router; and the second router modifies the configuration information of the second router according to the modifying control command. According to the technical scheme, the configuration accuracy of multiple routers is improved; the router configuration complexity is reduced; user operations are simplified; the time spent by a user to modify the configuration of multiple routers is reduced; and the user experience is improved.
Owner:XIAOMI INC
Method for updating data of electronic product
InactiveCN100552627CEasy to changeLow costTelevision system detailsColor television detailsExternal storage
The invention relates to a method for refreshing the data of electric product, which uses special I2C bus plug to lead internal signal outside the product, and uses relative cable; and uses said plug to connect the I2C bus with external memory eraser; then uses external eraser to process the data of memory. The invention has low cost, and simple operation, to improve the working efficiency.
Owner:SHENZHEN TCL NEW-TECH CO LTD
A production platform monitoring system with information protection function
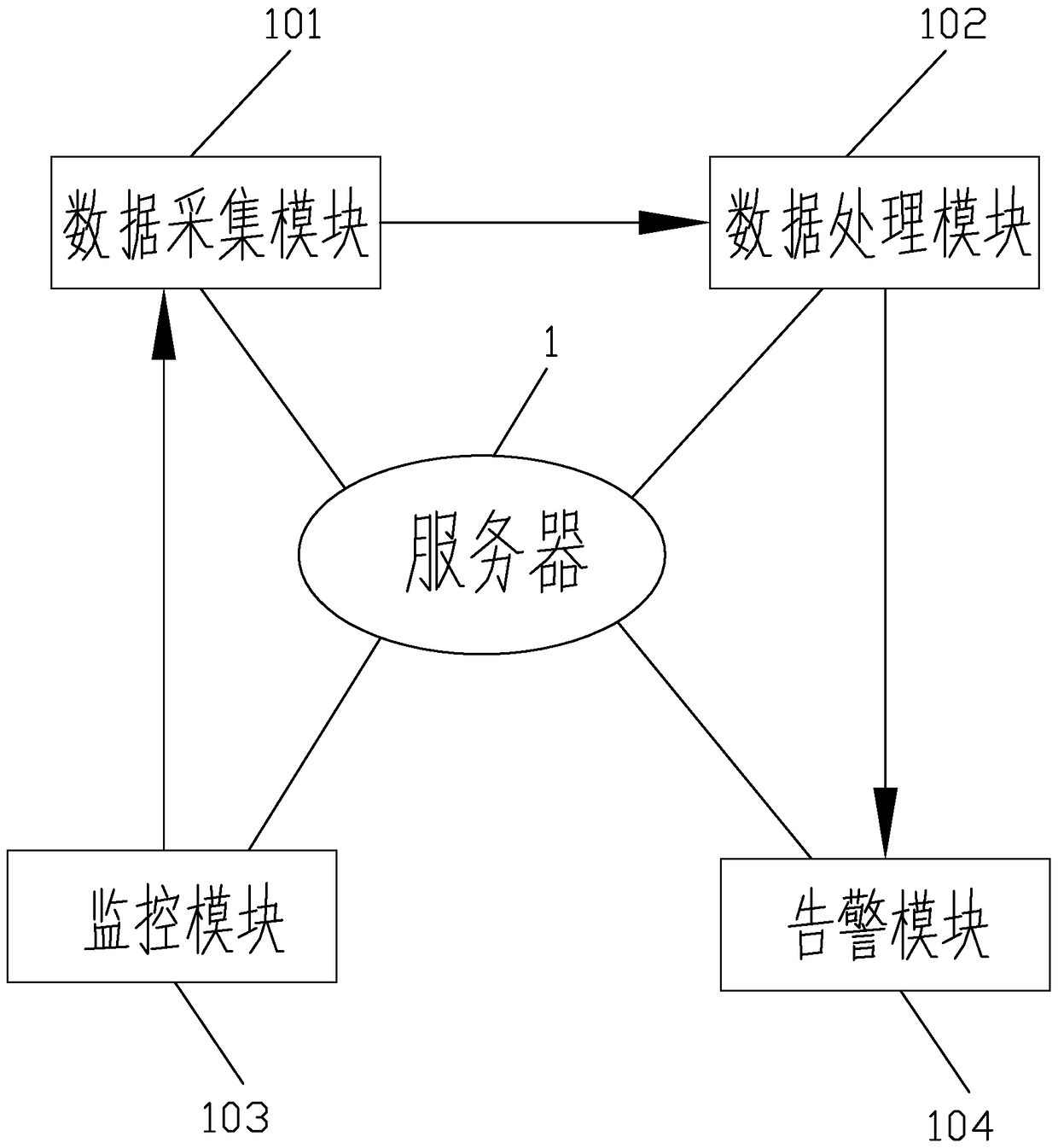
ActiveCN105334791BAvoid entanglementAvoid watchingProgramme controlComputer controlMonitoring systemData acquisition
The invention mainly discloses a production platform monitoring system with the information protecting function. According to the technical scheme, the system comprises a data acquisition module, a data processing module, a monitoring module, a warning module and a server. The data acquisition module acquires data through the monitoring module and stores the data to a background database. The data processing module processes the data to obtain warning data. The warning module is used for warning the warning information. A wire collecting device is arranged on the back side of the server and comprises a distributor plate and a wiring box, the distributor plate is provided with a distributor ring, the wiring box is provided with a winder, and the winder is provided with a label. The monitoring module comprises an exhibition platform, the front side of the exhibition platform is provided with a groove and a fingerprint switch, the groove is provided with a sealing plate, a button, a touch display screen and a driving device, and the driving device is connected with the sealing plate and the fingerprint switch. Automatic management is achieved, all objects are monitored, the data are acquired, alarm processing is immediately conducted once the data are abnormal, safety is high, and management and maintenance are convenient.
Owner:CHINA TOBACCO ZHEJIANG IND
Information system for managing chemical industry data
InactiveCN101442456BImprove work efficiencyImprove good performanceData switching by path configurationChemical industryProcess equipment
The invention discloses a chemical data management information system. The structure of the system comprises a client computer, an application server and a database server which are connected through a network. A software system comprises three independent subsystems, namely, a process equipment technical subsystem, a concealed engineering subsystem and a common pipe frame subsystem. The chemicaldata management information system is characterized in that a module part inside the database server comprises a Mapinfo platform for receiving external original data, wherein the Mapinfo platform isconnected with a layer editor module and a database storage module respectively; the layer editor module is connected with a gallery for storing information on the map layer of the entire system, andthe gallery can also be connected with a layer management module capable of outputting map information; moreover, besides being connected with a data backup module ensuring data security of the entire system, the database storage module is respectively connected with a data maintenance module, a query statistical module, an accident analysis module and an early warning prompting module which are for server data processing and information output.
Owner:SHANGHAI WUJING CHEM
Interface apparatus based on I2C bus and read-write apparatus employing the same
The invention relates to an interface device based on I2C bus and relative read-write equipment, wherein the interface device comprises: SCL terminal, SDA terminal, VCC terminal, GND terminal, and ID terminal; the cable meeting the I2C bus interface connects the I2C bust with the external memory via said interface device, to process the read-write operation; and via connecting the interface device to MCU, the data memory can form read-write equipment, to read-write data quickly, to support the system upgrade and debug data modification of electric product.
Owner:SHENZHEN TCL NEW-TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com