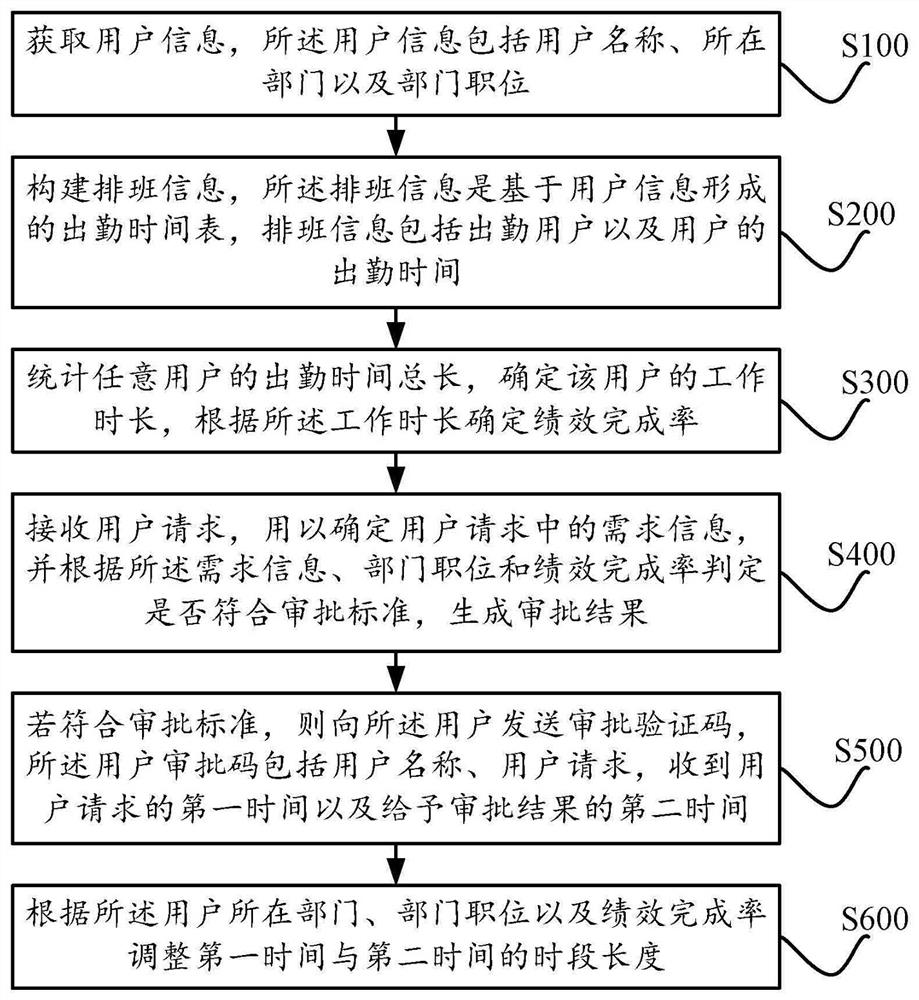
Patents
Literature
30 results about "Information sector" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
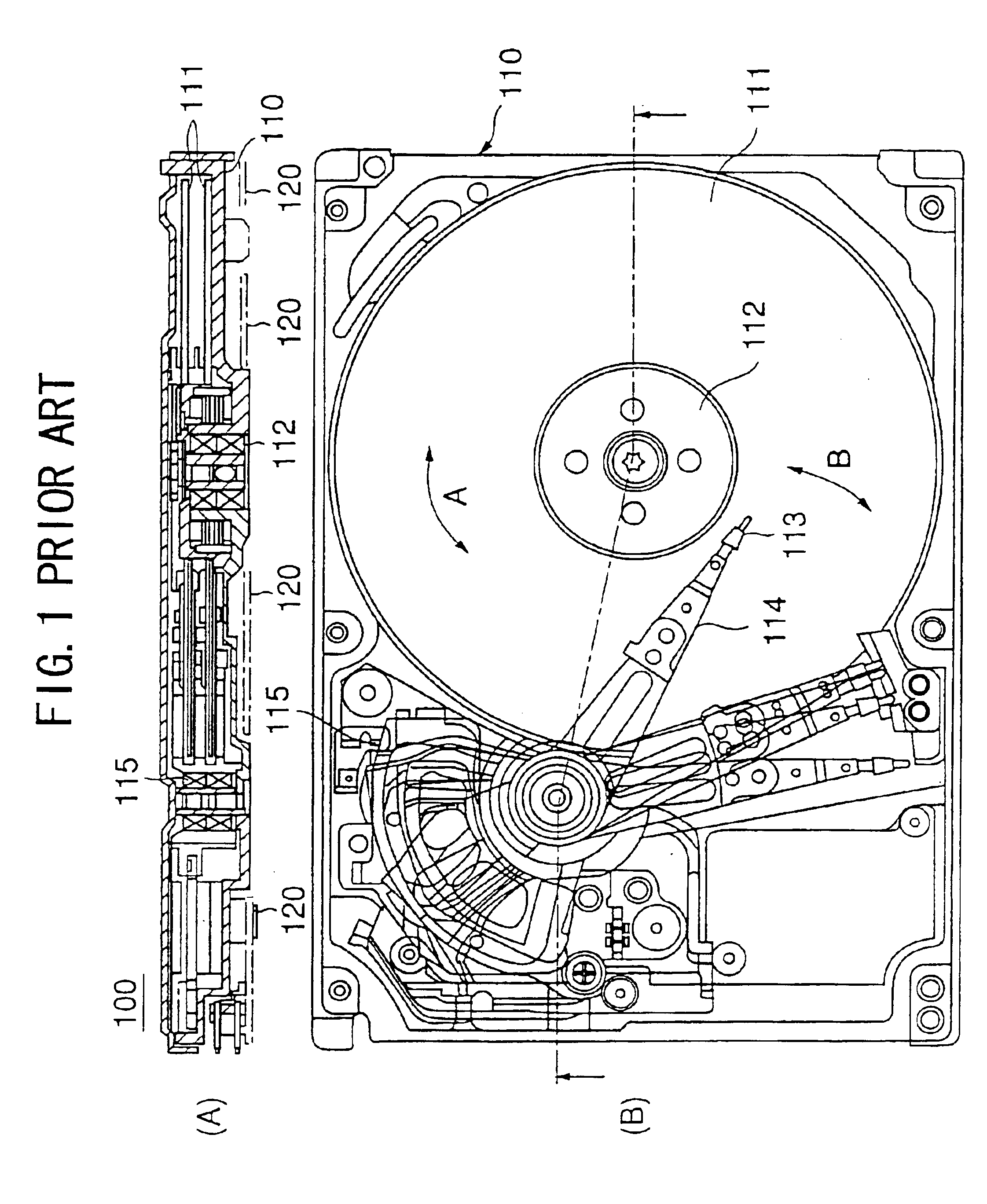
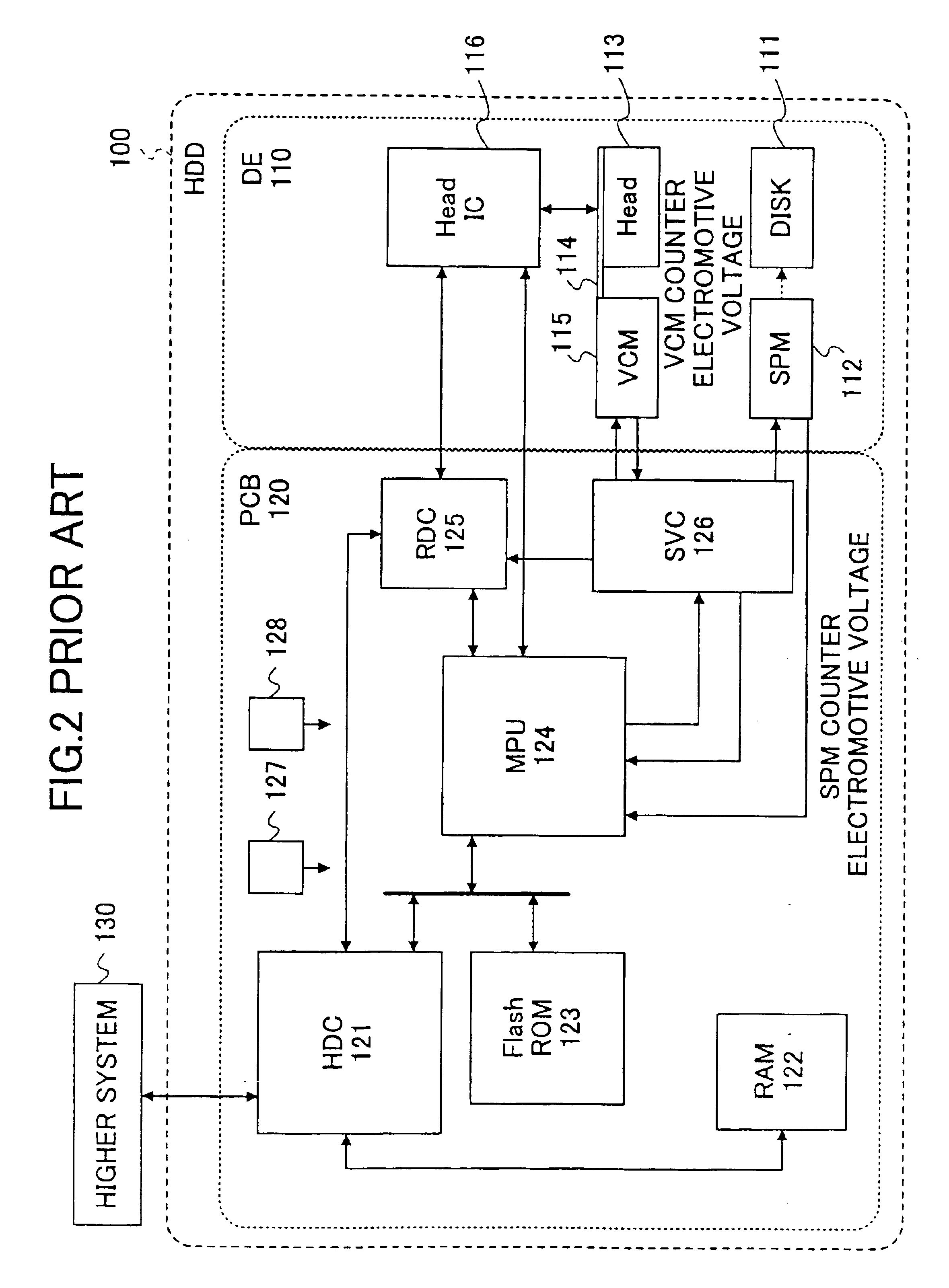
The Information Technology Sector is central to the nation's security, economy, and public health and safety as businesses, governments, academia, and private citizens are increasingly dependent upon Information Technology Sector functions.
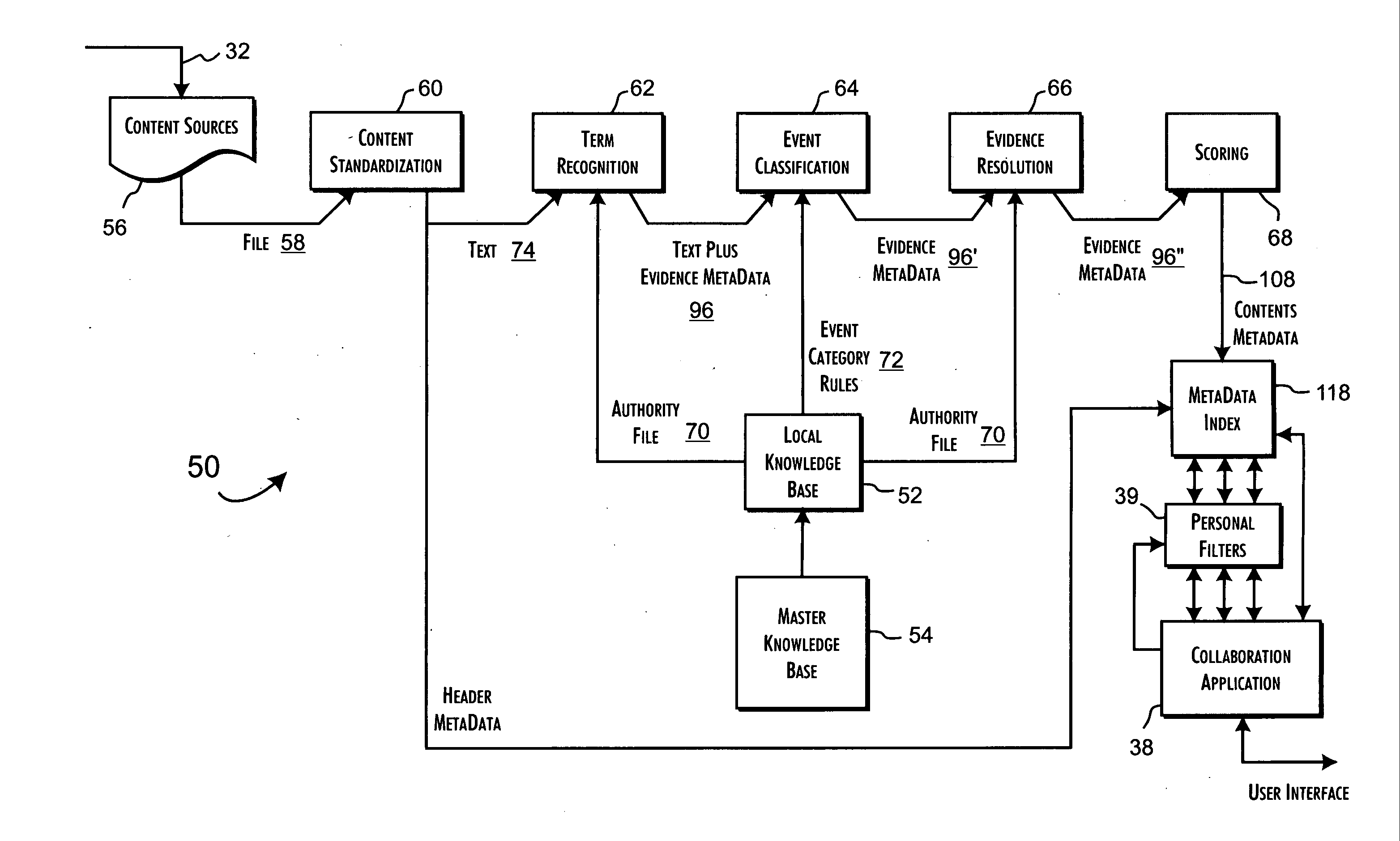
Sector content mining system using a modular knowledge base
InactiveUS20050131935A1Accurate identificationEfficient analysisDigital data information retrievalNatural language data processingStructured contentInformation sector
A content mining system and process utilizes a combination of term recognition and rules-based activity-event classification, performed using a modular database that defines one or more vertical markets or information sectors, to identify sector relevant evidence. The primary elements of the identified evidence are scored in a manner that rates the relevance of a content item with respect to a set of identified nominative entities, a set of activity-based event categories, further associated as sets of entity-event pairs. A database constructed of the scored information provides a relevancy indexed repository of the original unstructured content items.
Owner:GREEN RIDGE SYST
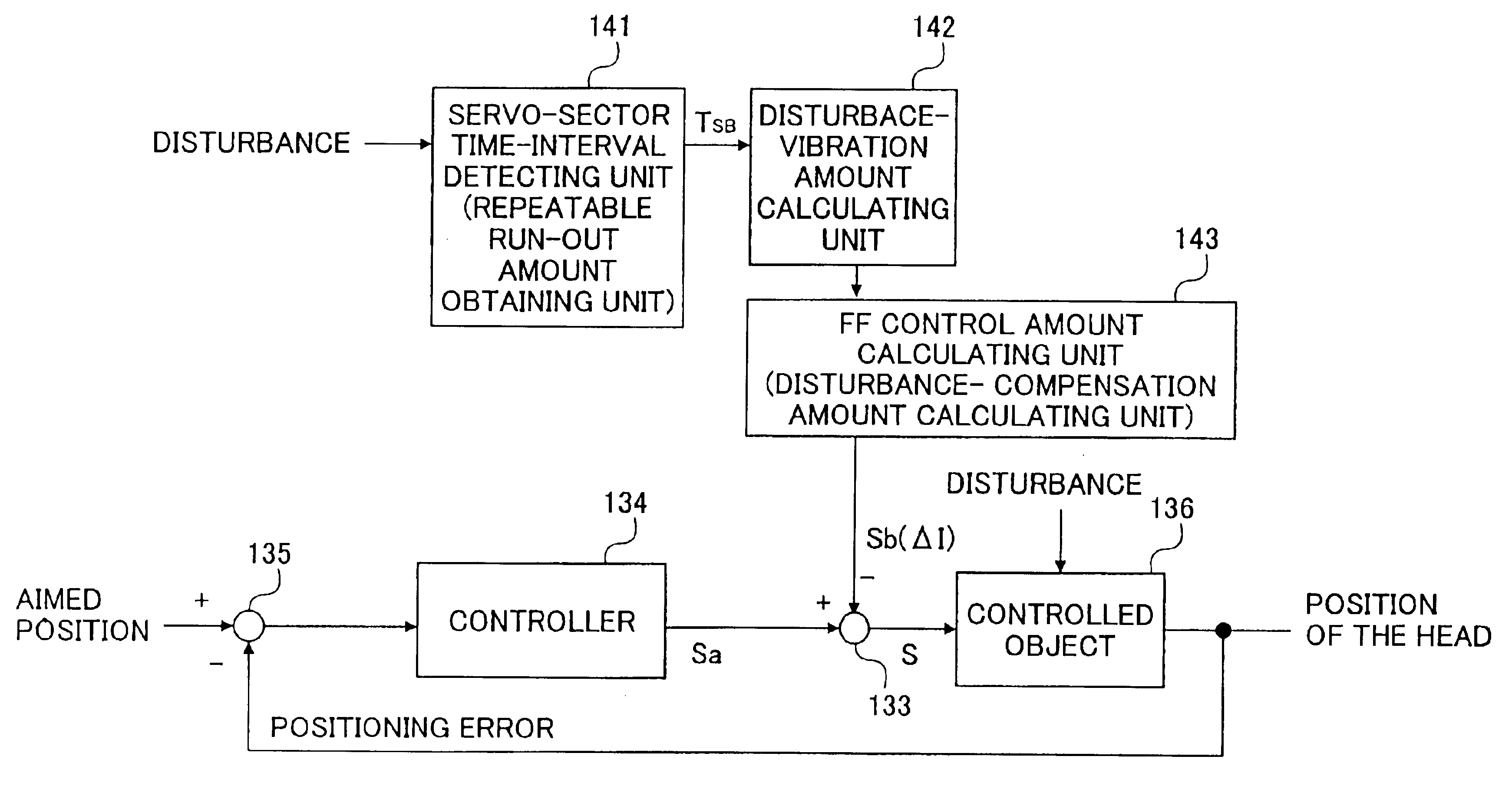
Disk device conducting a disturbance compensation based on a time-interval measurement in reading servo sectors recorded on a disk
Owner:TOSHIBA STORAGE DEVICE CORP
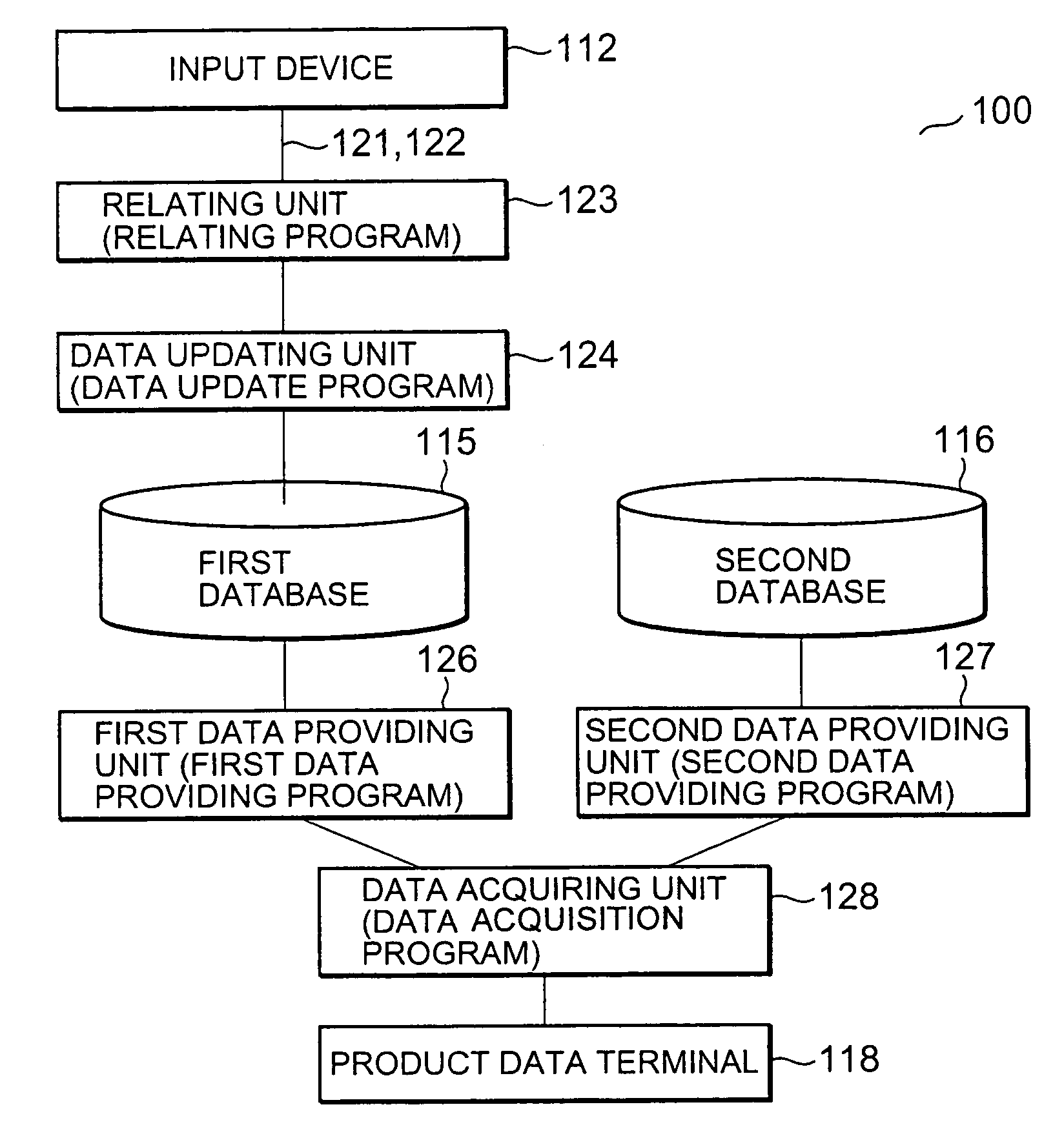
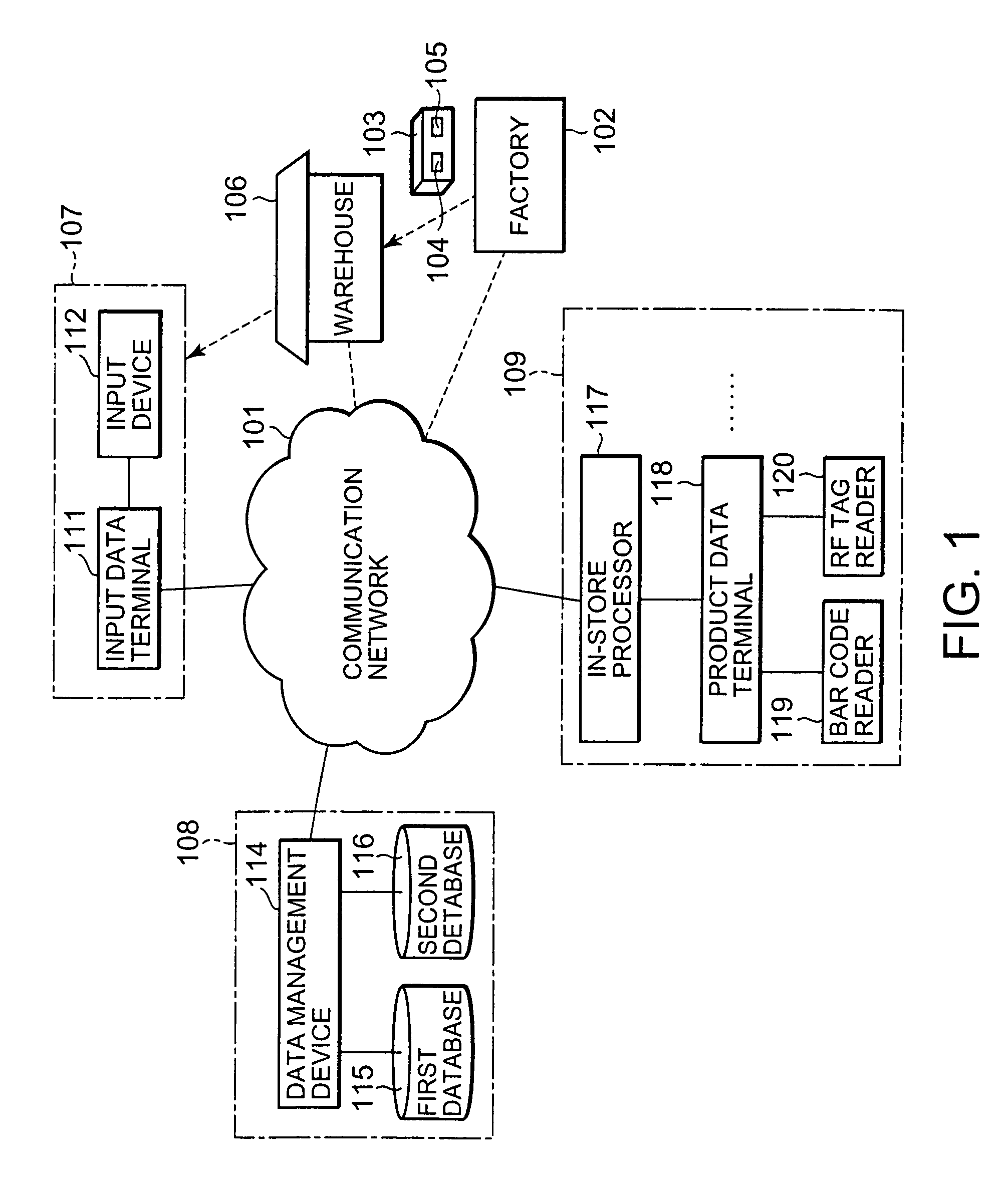
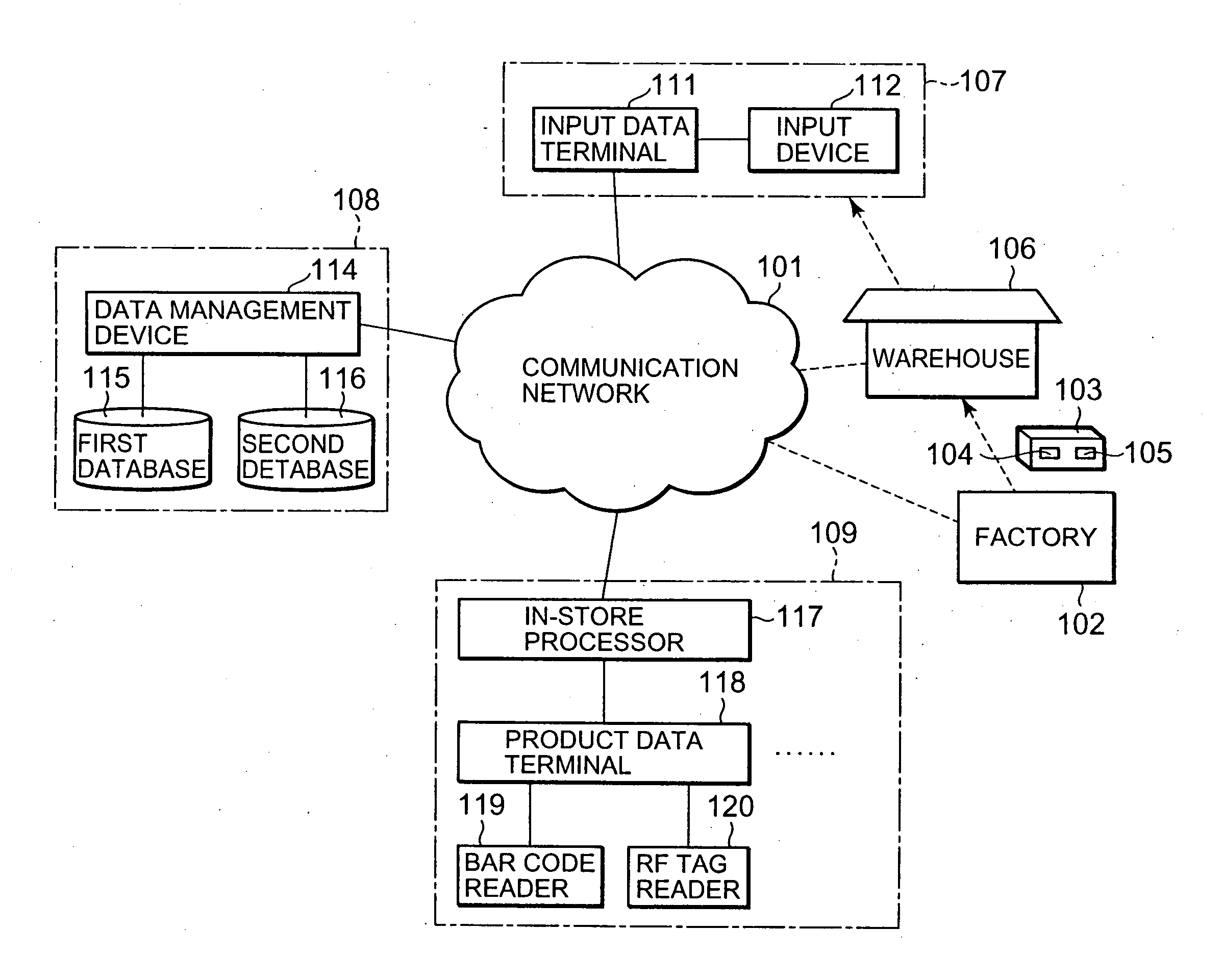
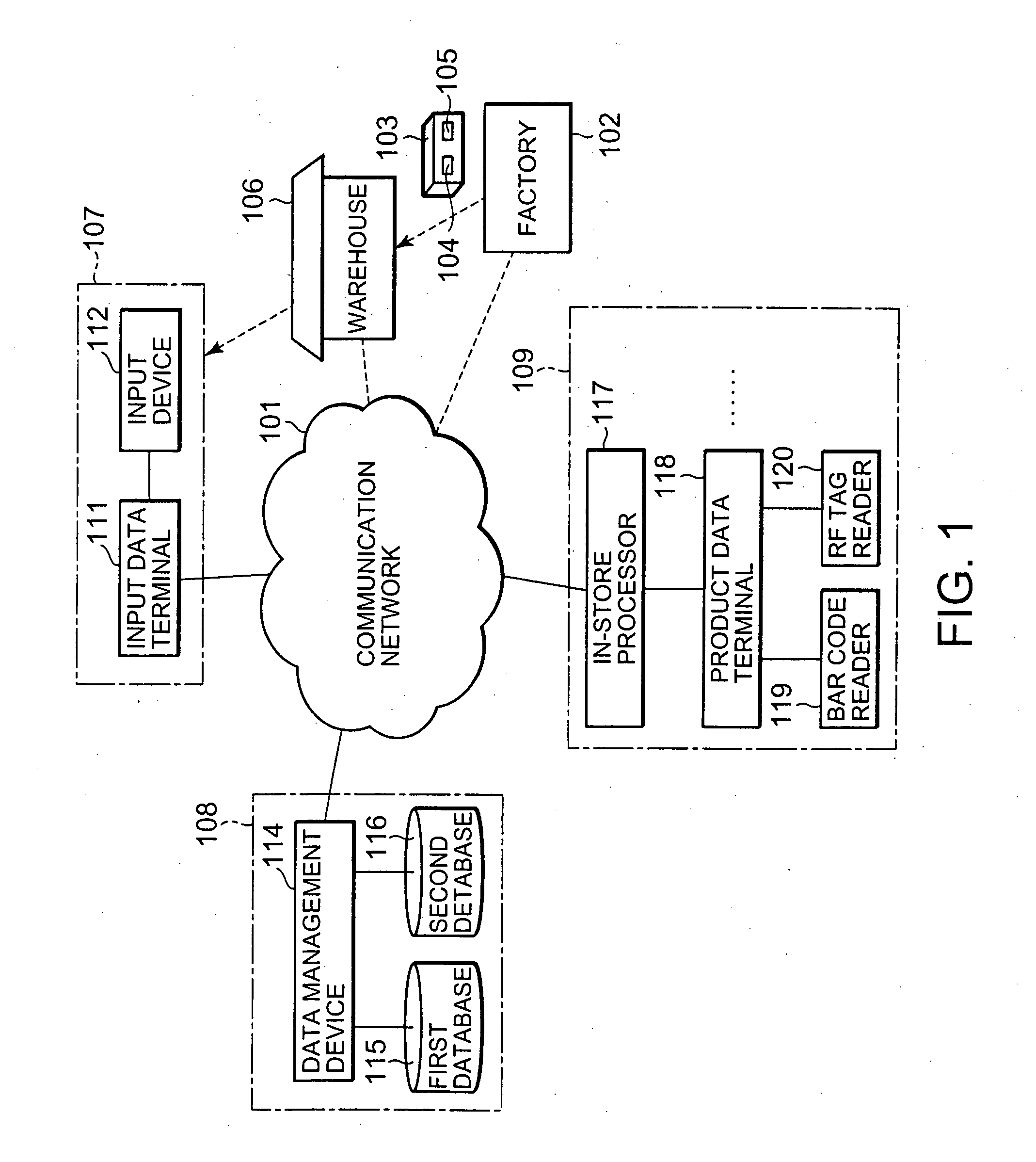
Product identification data management system and product identification data management method
ActiveUS7416122B2ConsistencyCheck consistencyCo-operative working arrangementsCash registersBarcodeInformation sector
The present invention relates to a product identification data management system and method. According to the present invention, an input device of a purchasing department reads a bar code and an RF tag as data of two identification data systems added to a product such that the identification data of the two identification data systems are related with each other. The read bar code data and RF tag data are stored and managed in first and second databases of a information department, respectively. When a user terminal such as a product data terminal issues a request to acquire predetermined data on the basis of the bar code data of the product, the predetermined data is retrieved from either or both of the first and second databases. The acquired data is returned to the user terminal. The consistency between identification data added to each product can also be checked.
Owner:NEC CORP
Information recording medium, information recording method, information recording apparatus, information reproduction method, and information reproduction apparatus
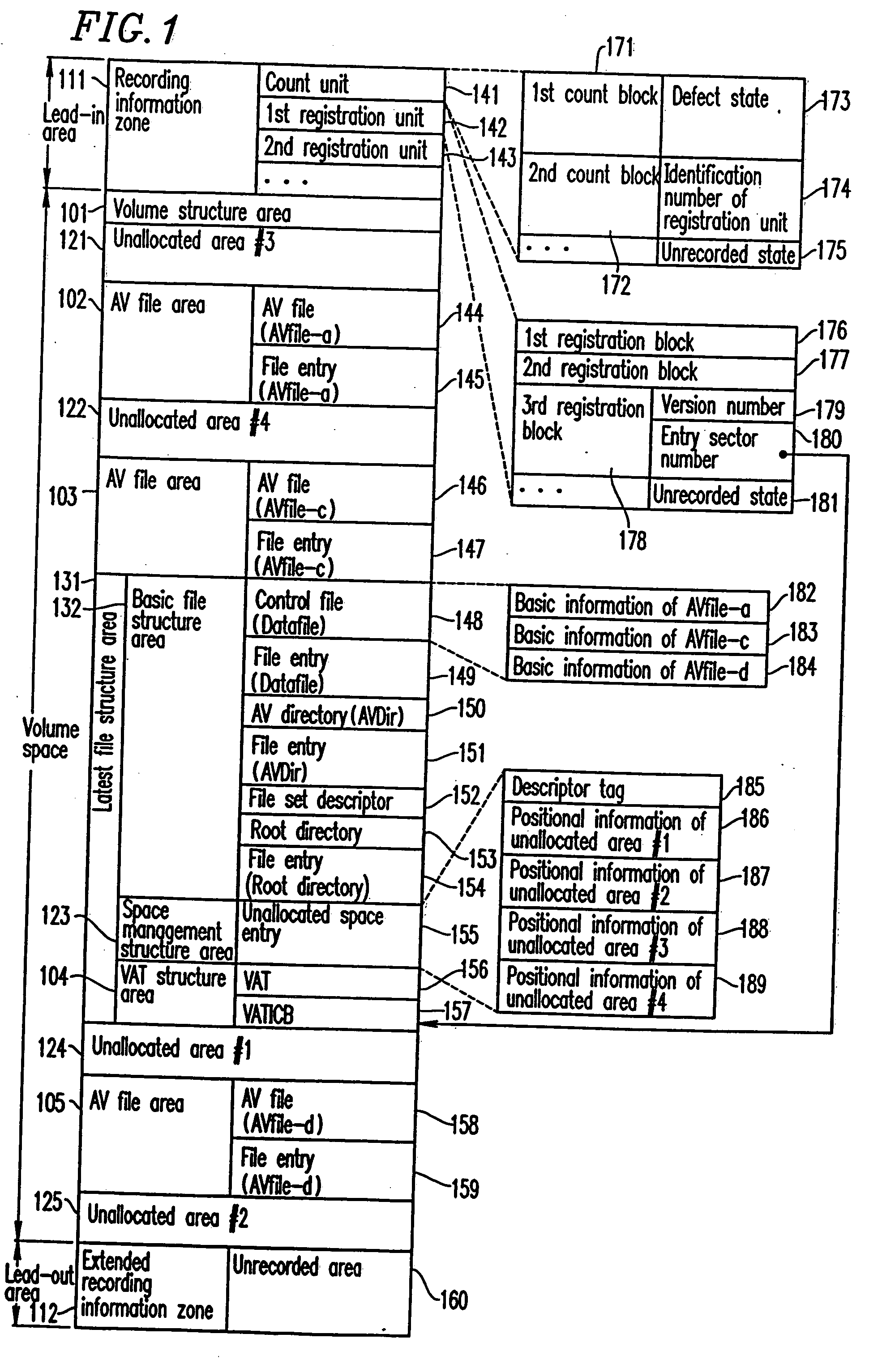
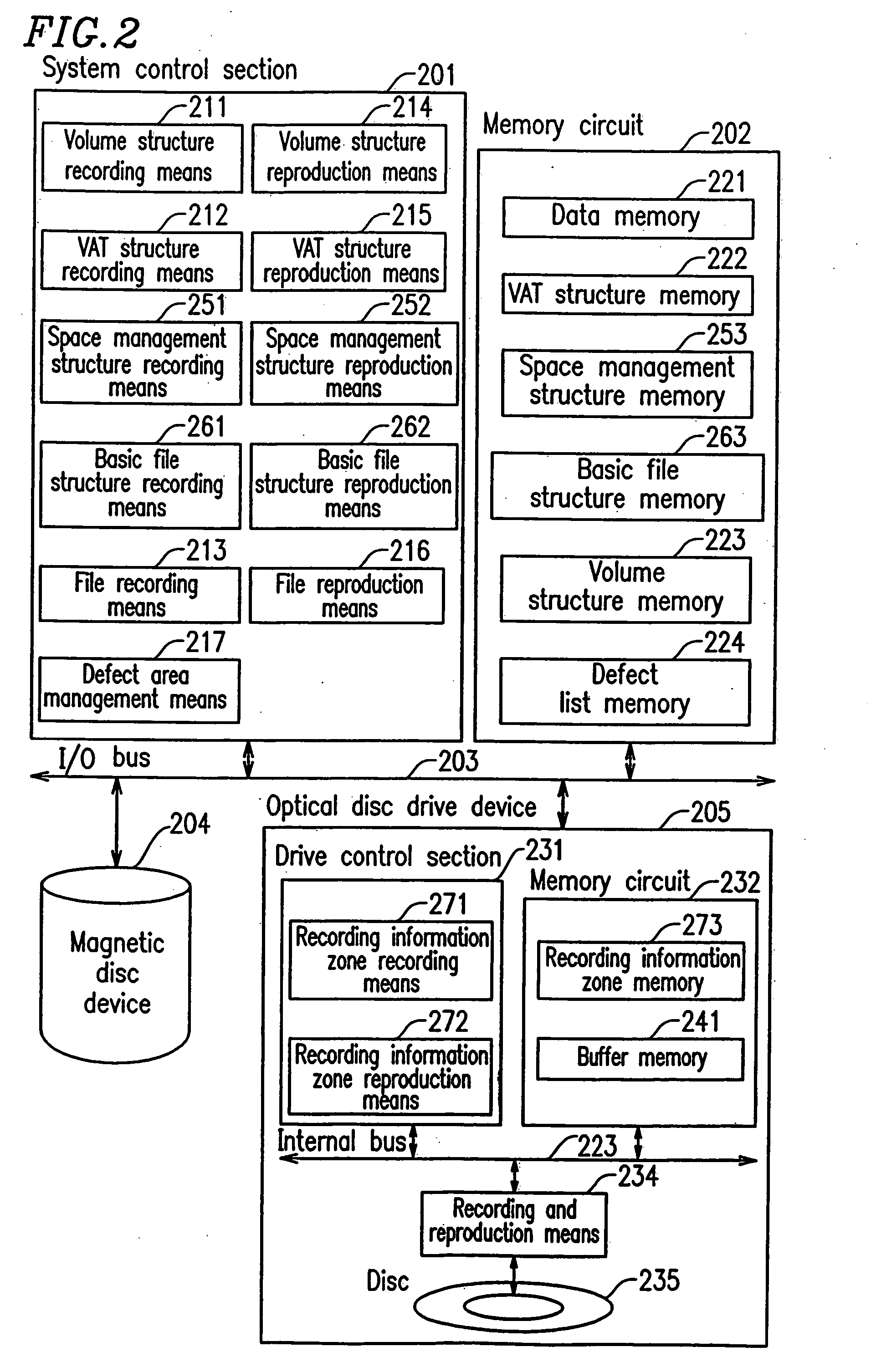
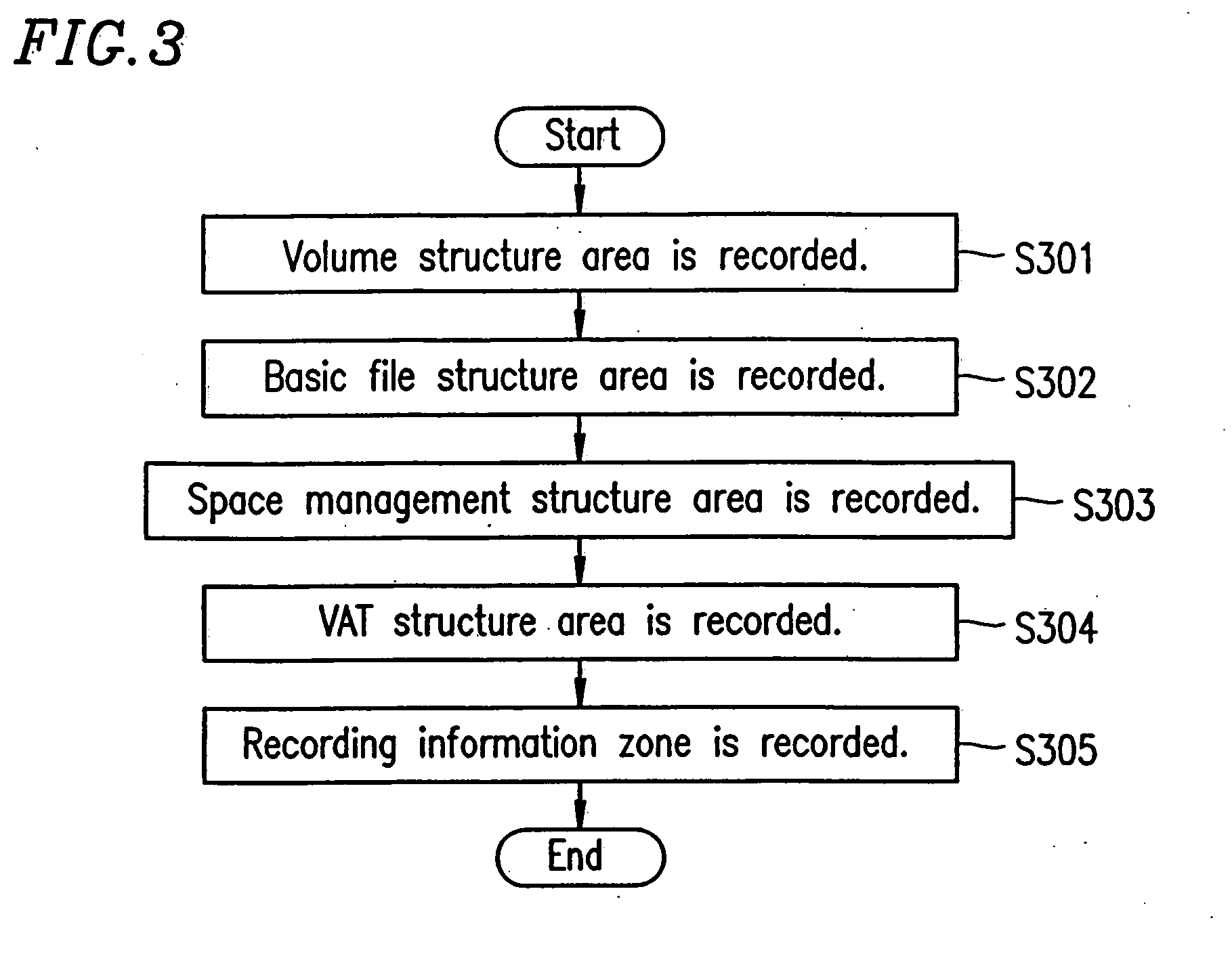
InactiveUS7024534B2Electronic editing digitised analogue information signalsRecord information storageInformation sectorData recording
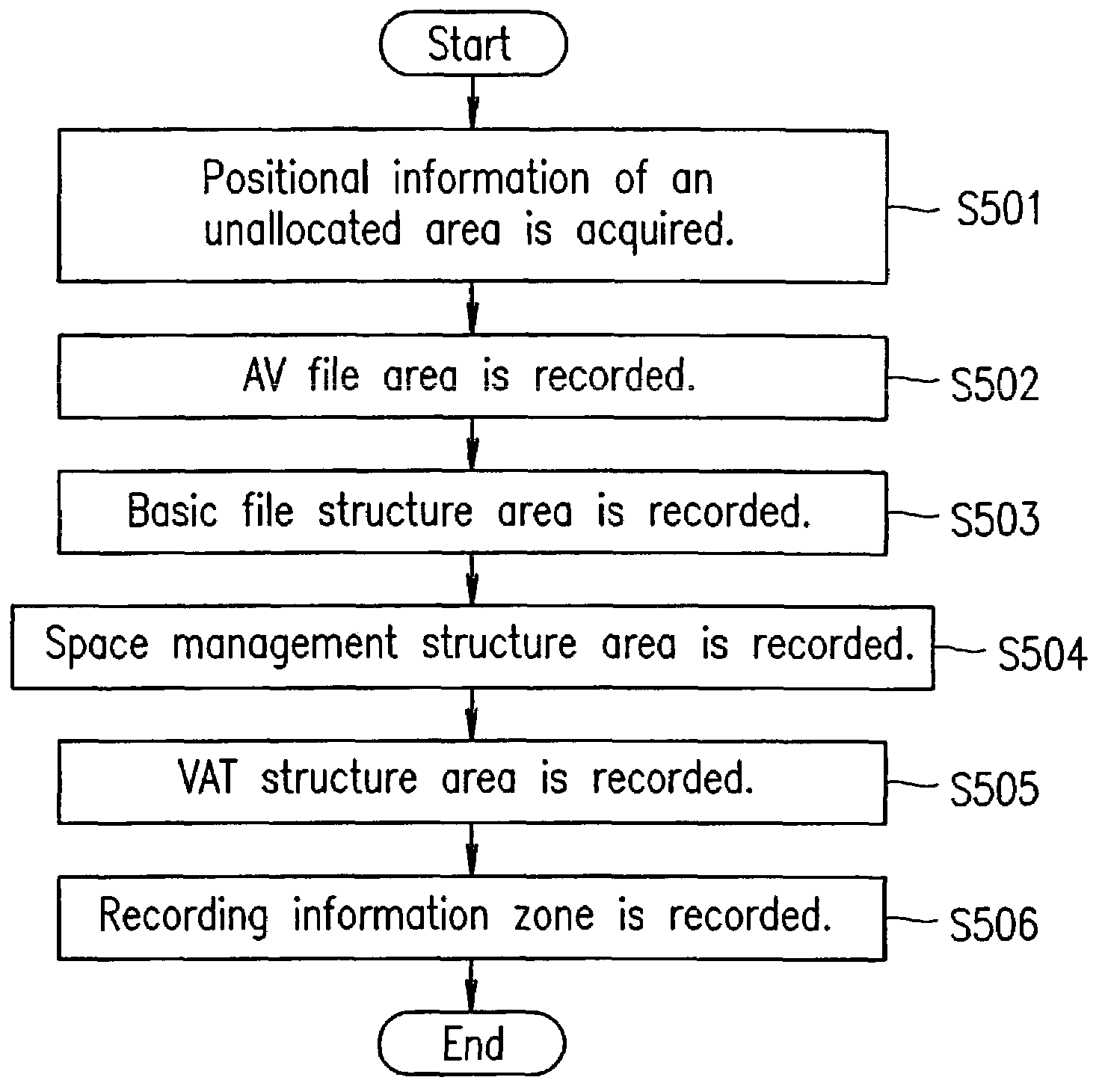
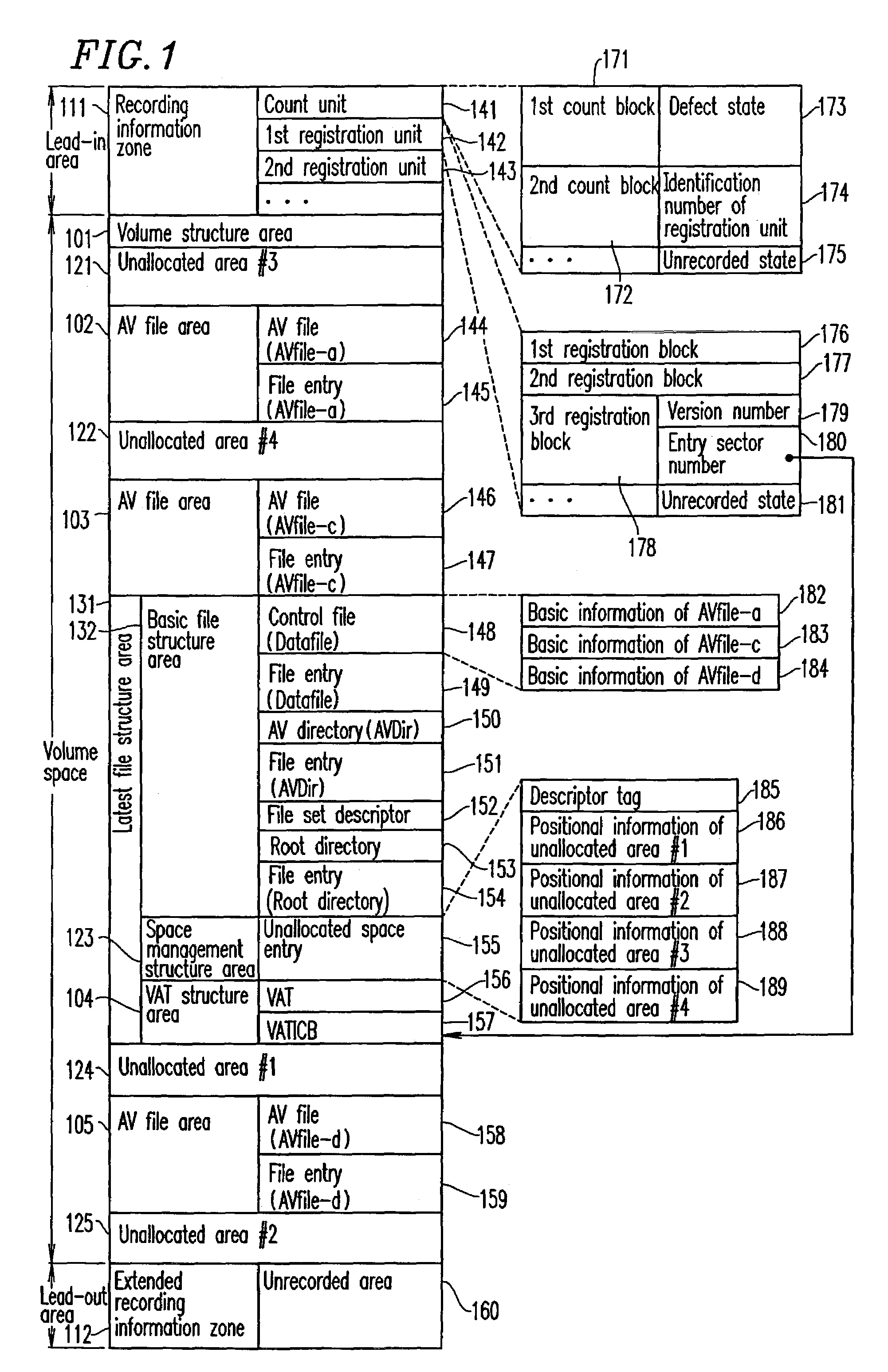
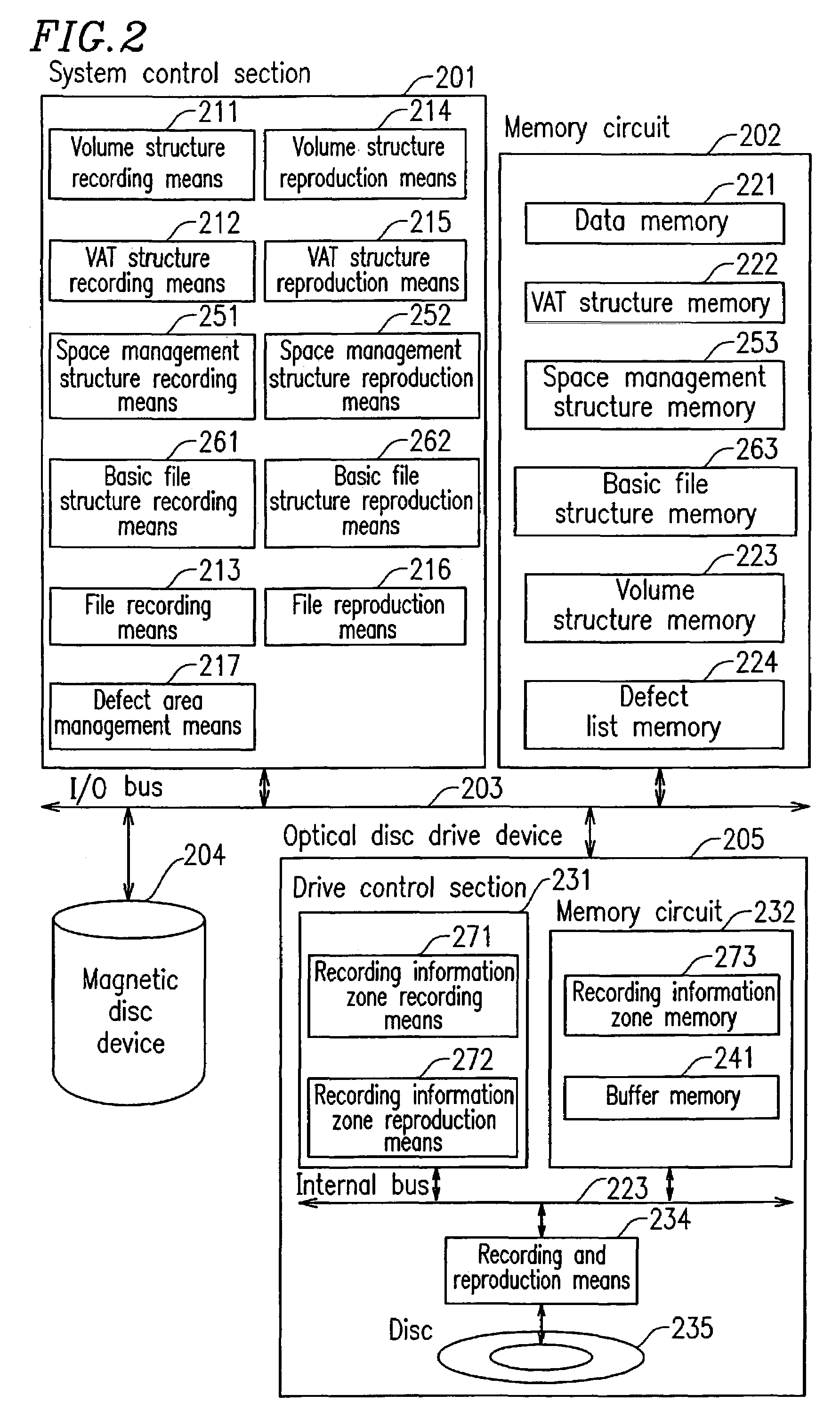
According to a recording method for a conventional rewritable disc, the latest data is recorded by rewriting data in an identical area. In the case of a disc of which the number of times of data rewrite is limited, this causes a problem that a defect block is easily generated. The present invention has an objective of providing an information recording medium, an information recording and reproduction method, and an information recording and reproduction system apparatus, by which data is recorded sequentially from an unallocated area after an entry sector number, and data recording is sequentially repeated from an inner portion to an outer portion.
Owner:PANASONIC CORP
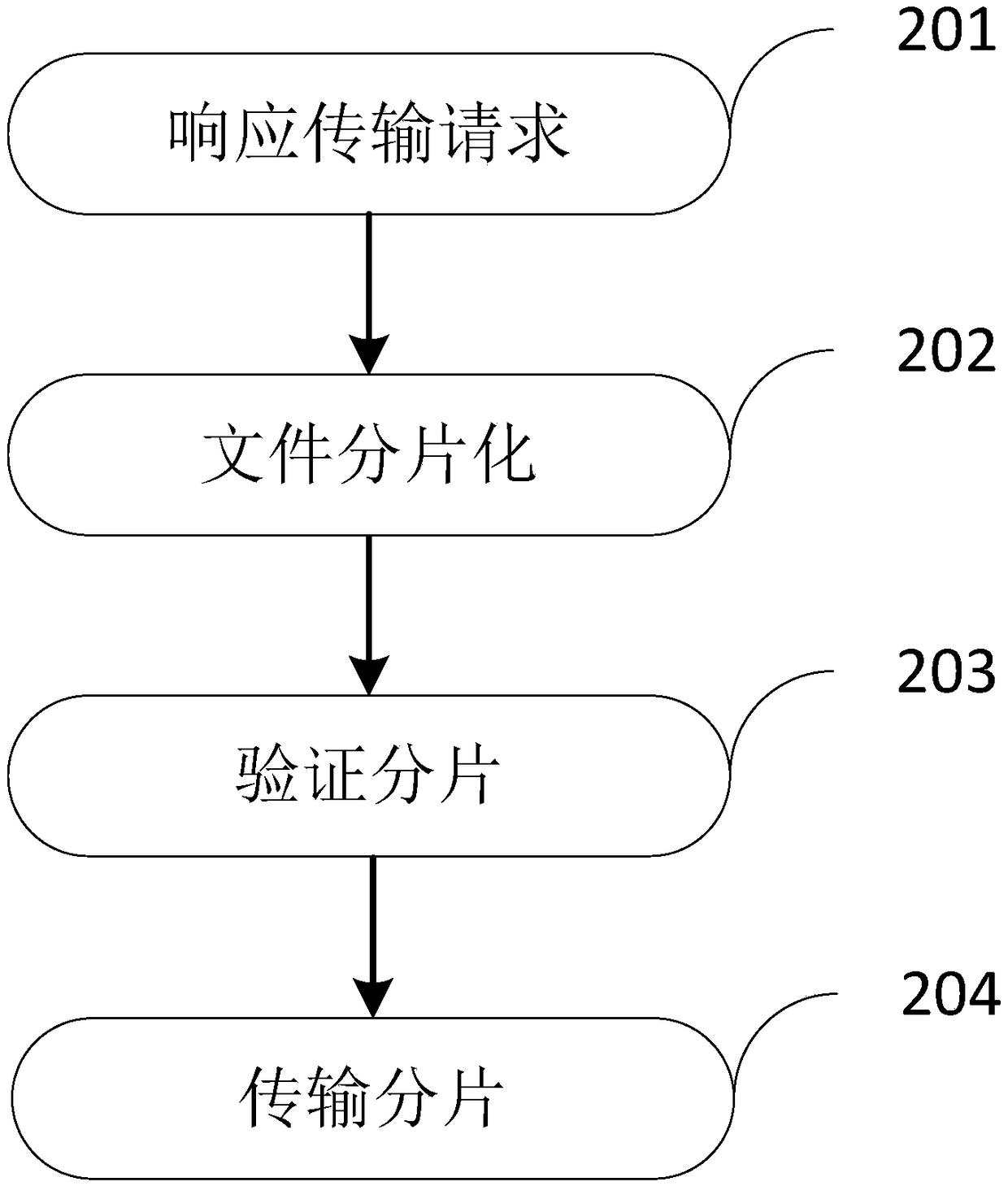
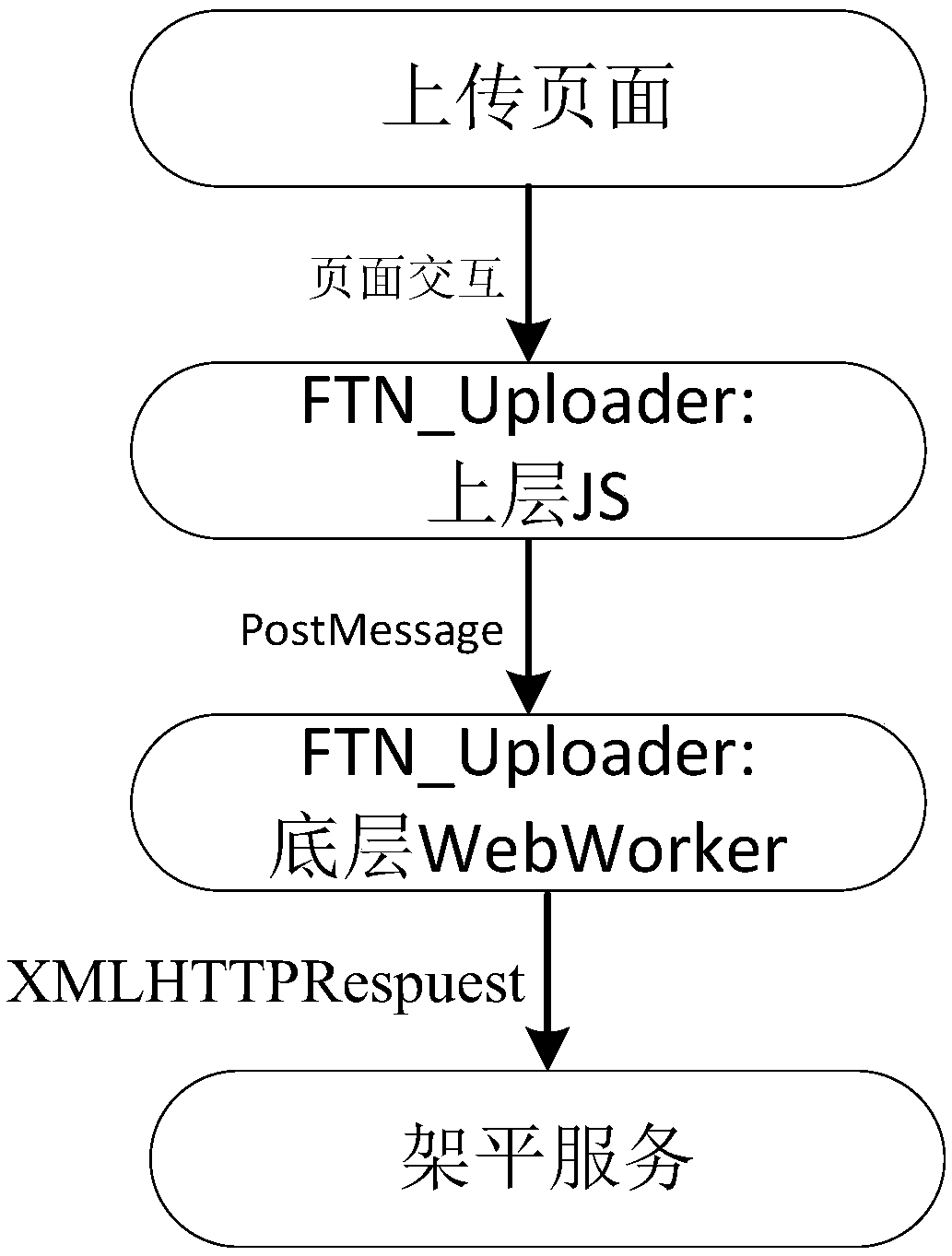
Browser-based file transfer method and device
InactiveCN109361754ATroubleshoot issues that require restarting transfersUser identity/authority verificationOperational systemManaged file transfer
The invention relates to file transfer technologies for the field of Internet, in particular to a browser-based file transfer method and device. In response to a file transfer request sent by a user,a browser carries out fragmentation on a target file and respectively transfers all fragments, and all fragment files are finally reintegrated into the transferred file, so that the problem that a large file needs to be retransferred after a transfer failure is solved. The method and device provided by the invention is applicable for large file transfer among multiple browsers and among multiple browser versions, is particularly applicable to a multi-operation system environment of government agencies or large enterprise information departments, adopts file fragment uploading, and totally supports an application client clustering or load balancing environment, so that high efficiency and a high success rate of large file uploading on the browser are ensured.
Owner:CGN POWER CO LTD +2
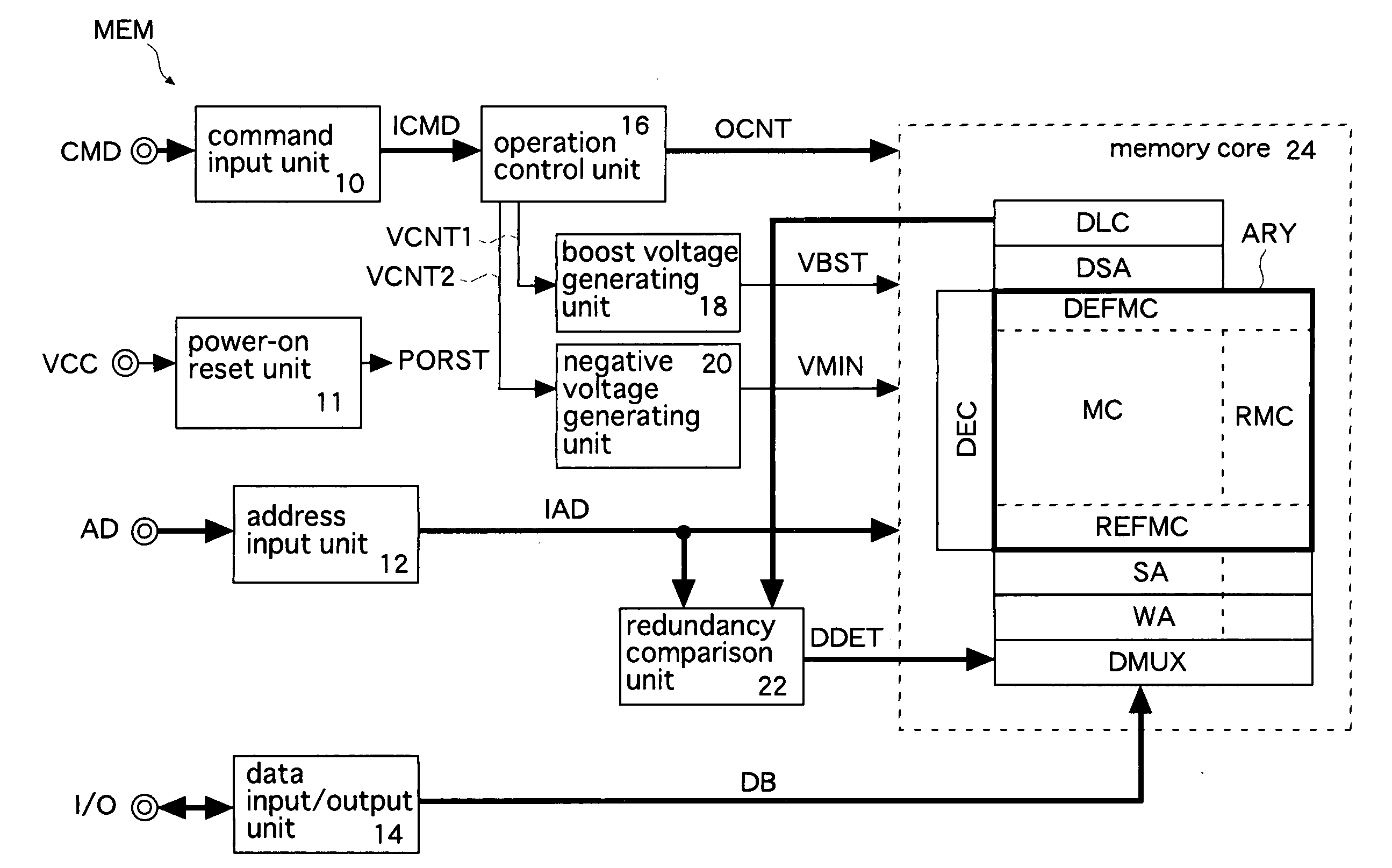
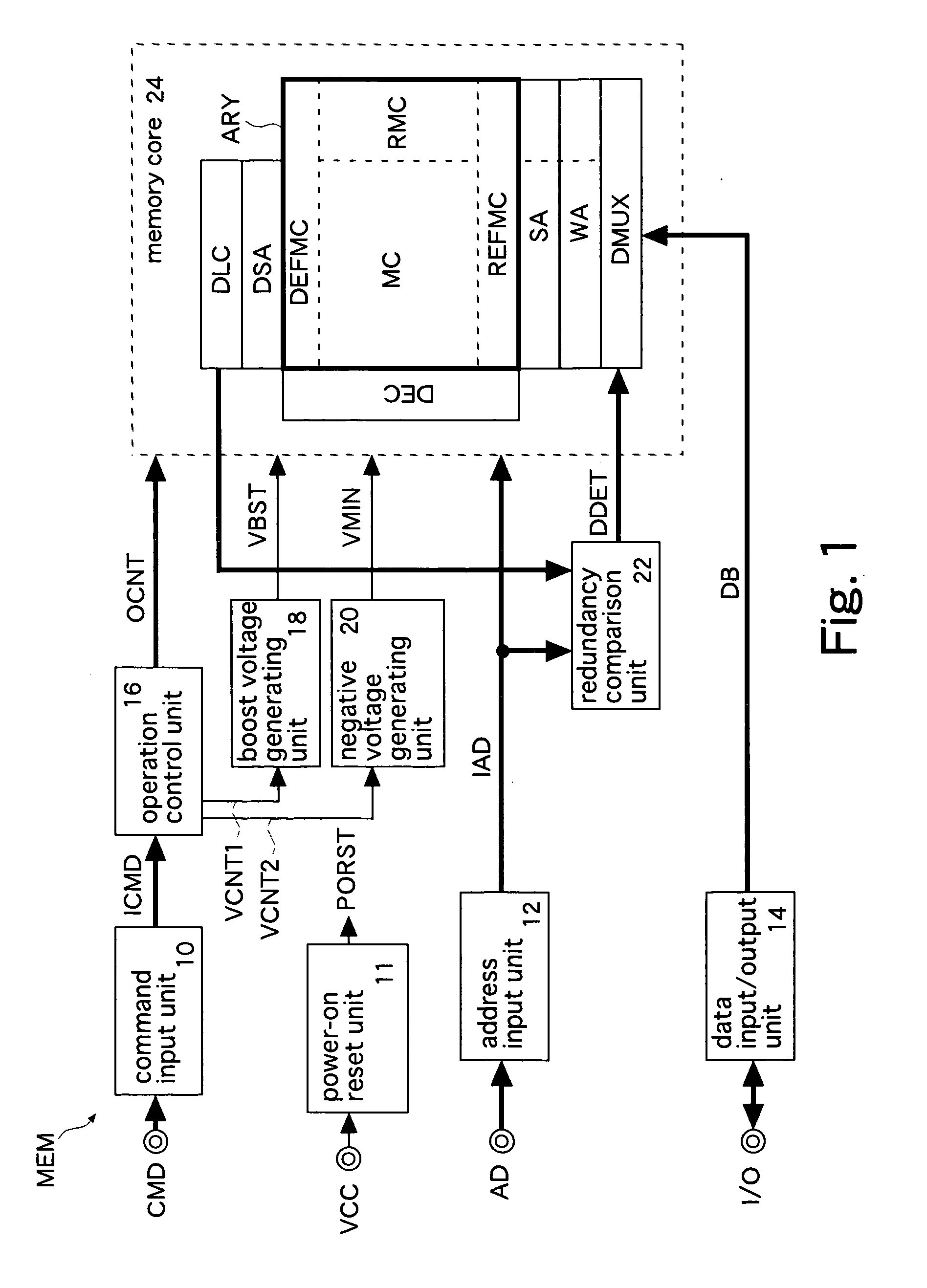
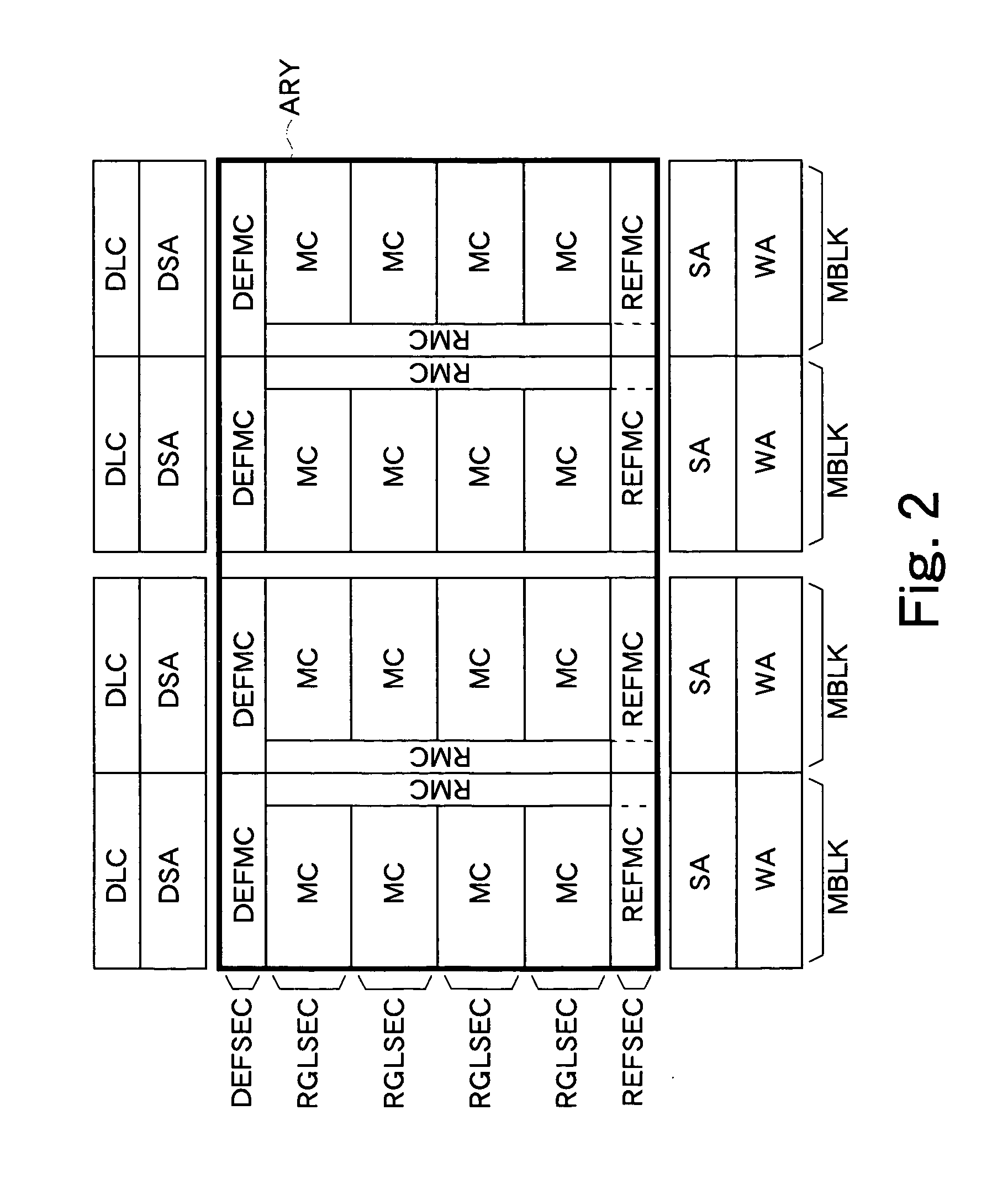
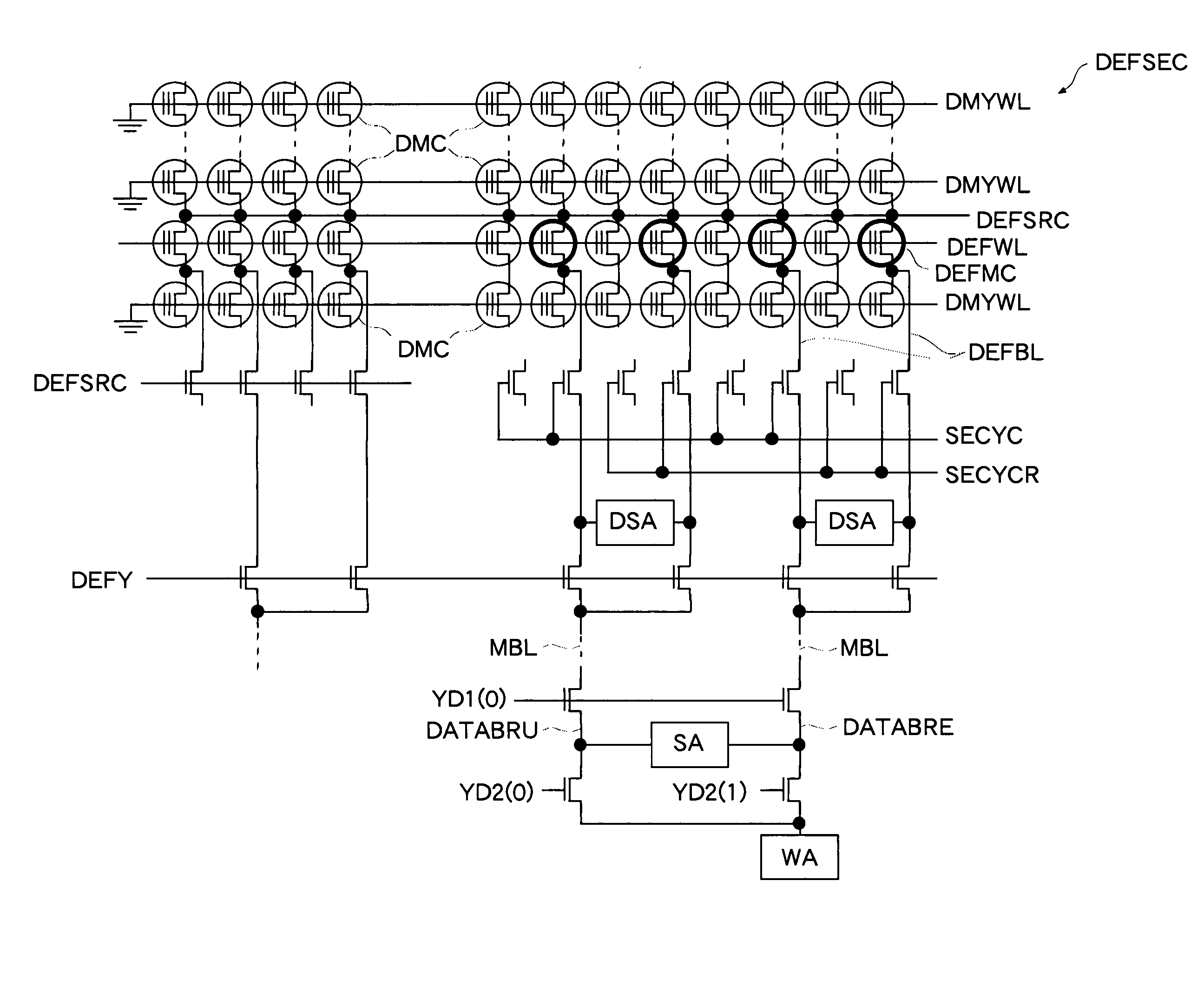
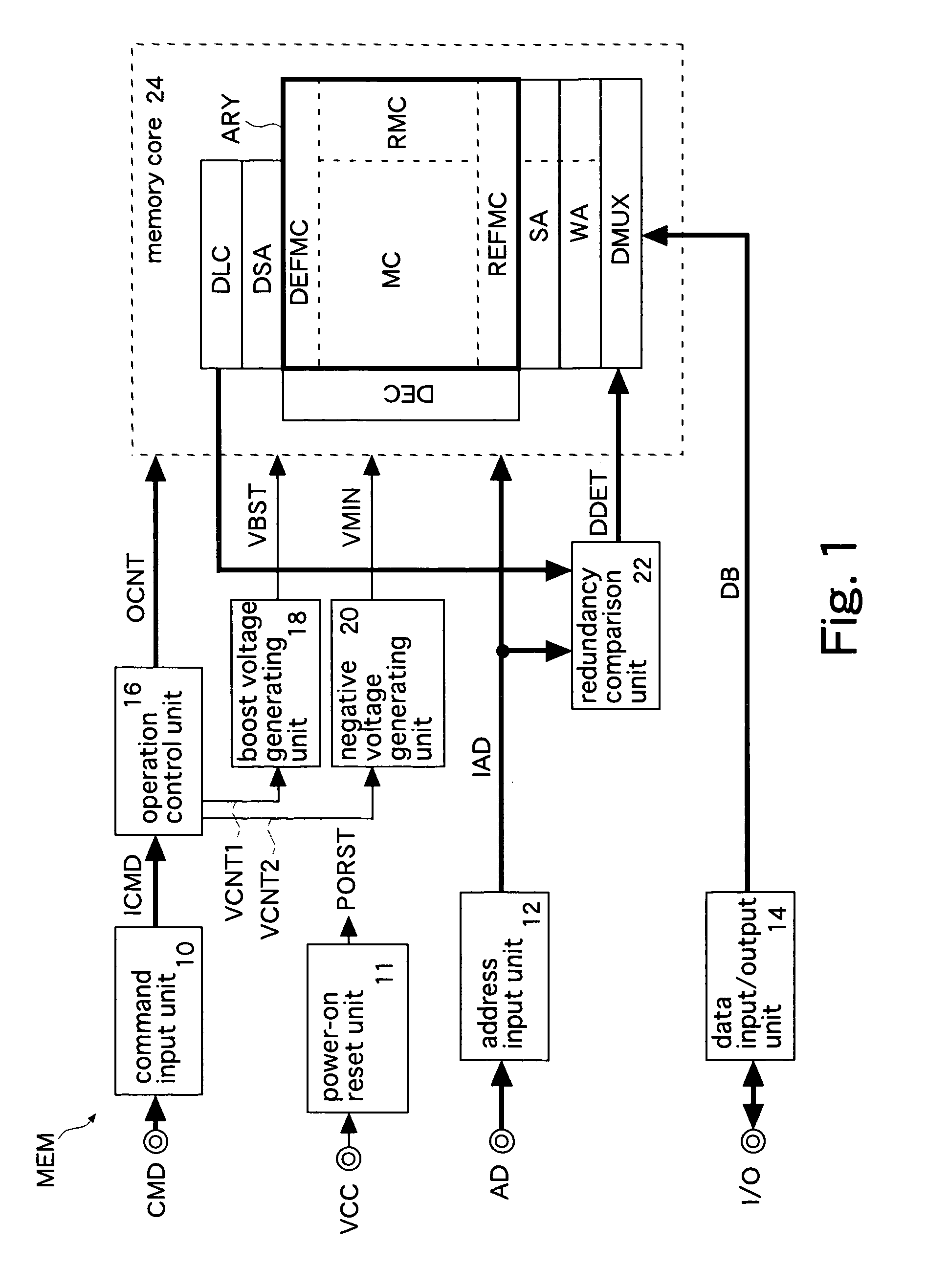
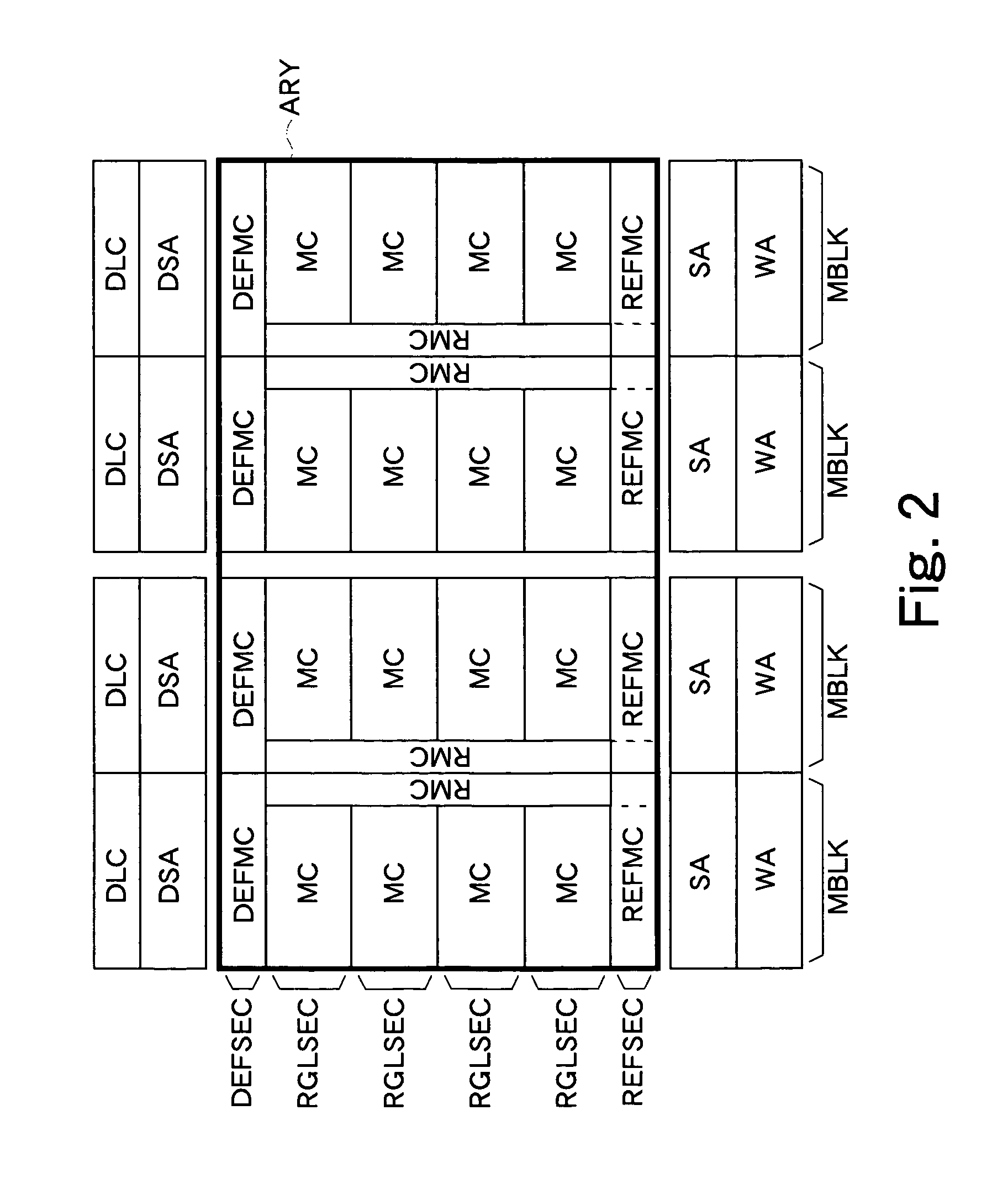
Nonvolatile semiconductor memory
InactiveUS20070230263A1Small circuit scaleExtended access timeDigital storageAudio power amplifierInformation sector
A regular sense amplifier and a defect-information sense amplifier are provided for each regular sector and each defect-information sector, respectively. This can prevent an excess load from being applied to a read path, and minimize the access time. A write amplifier is provided in common to the regular sector, the reference sector, and the defect-information sector. Generally, the write operation time of a nonvolatile semiconductor memory is long, so that an increase in a wiring load on a data transmission path and an increase in a load on a switch do not affect the write operation time much. As a result, the circuit scale can be made smaller without lengthening the read access time, and thereby the fabrication cost of the nonvolatile semiconductor memory can be reduced.
Owner:SOCIONEXT INC
Product identification data management system and product identification data management method
ActiveUS20050139665A1Efficient data structureConsistencyCo-operative working arrangementsCash registersBarcodeInformation sector
Owner:NEC CORP
Data protection method
InactiveUS20070124648A1Efficient accessReduce in quantityStatic storageForward error control useData setData information
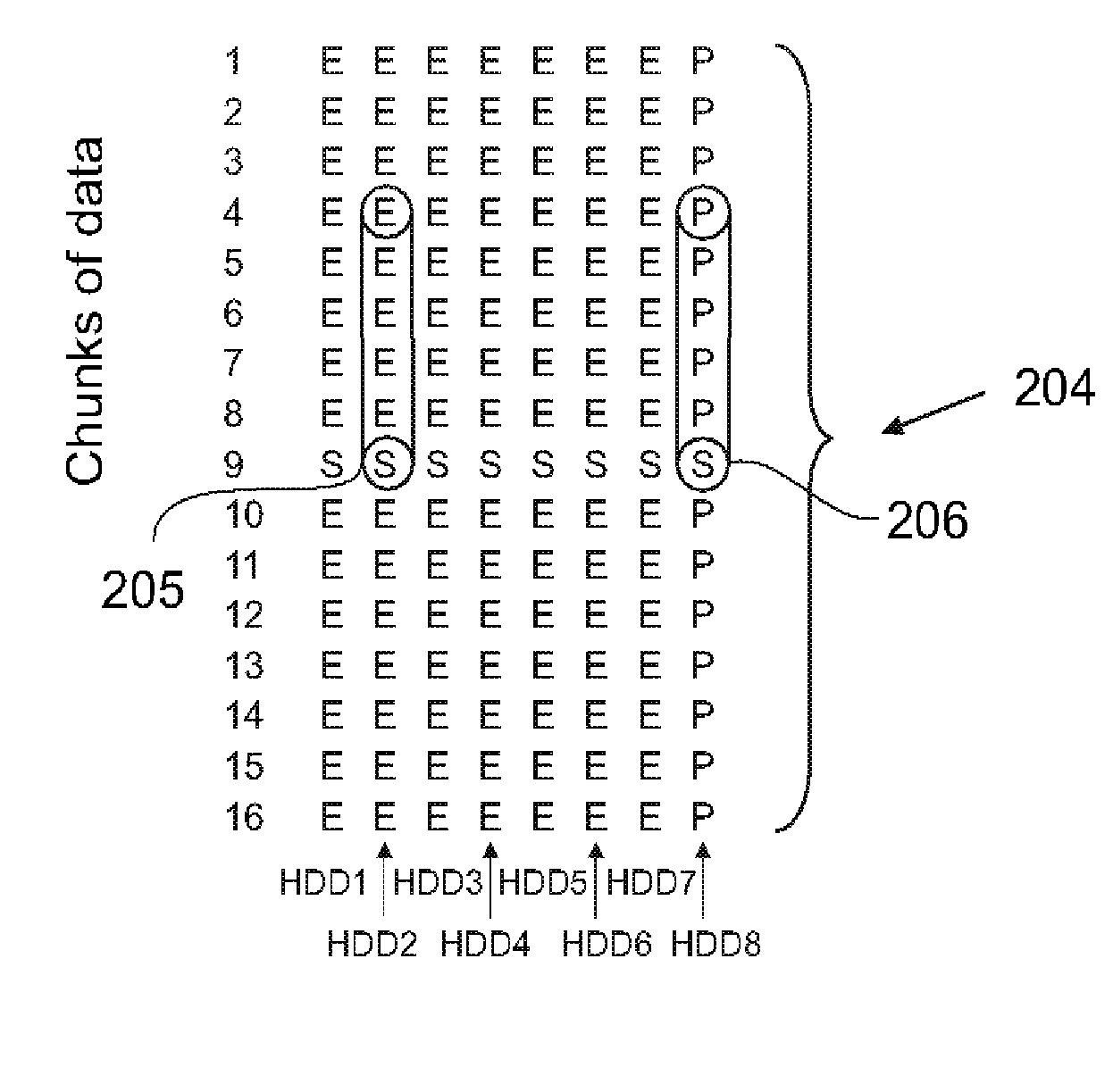
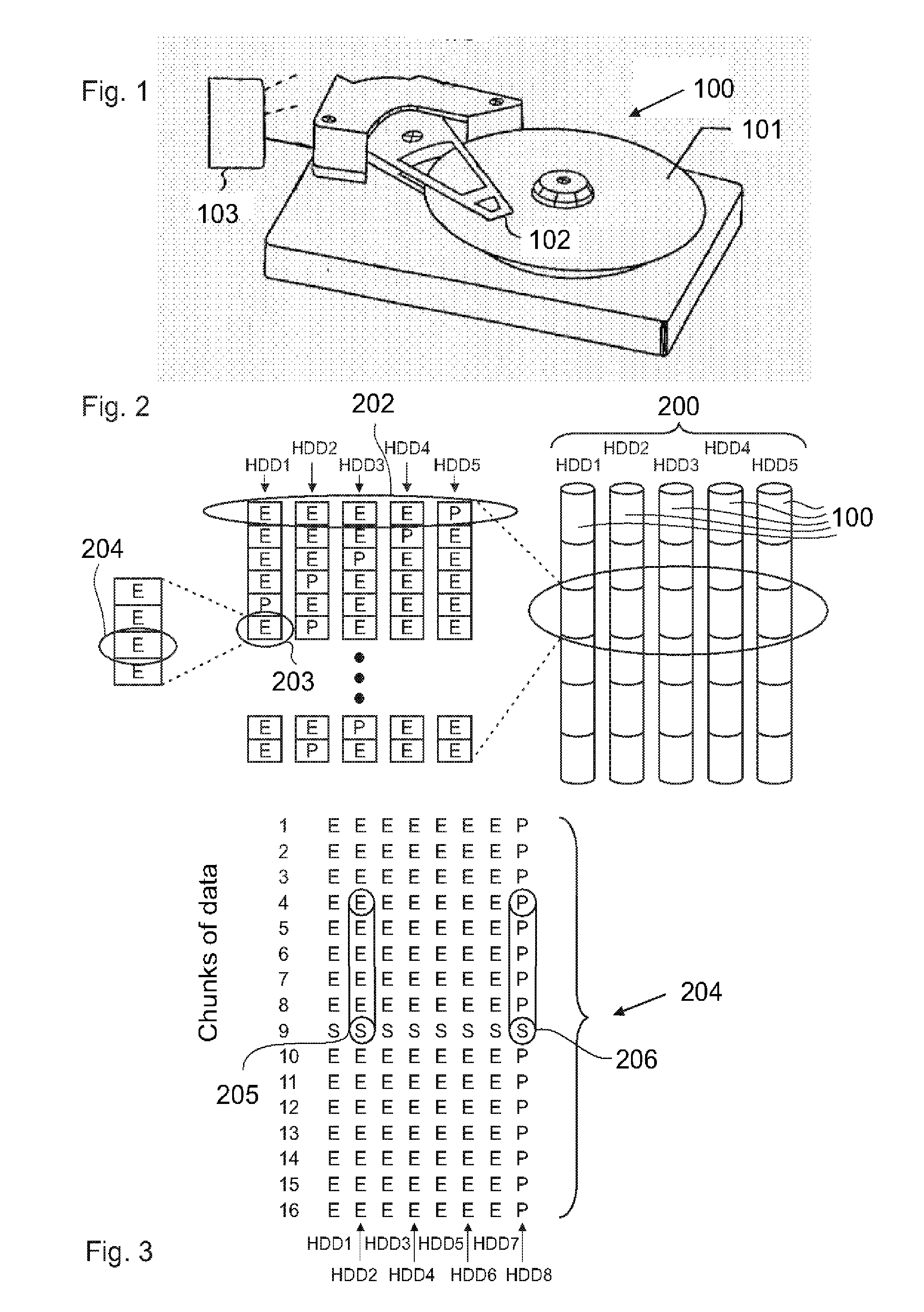
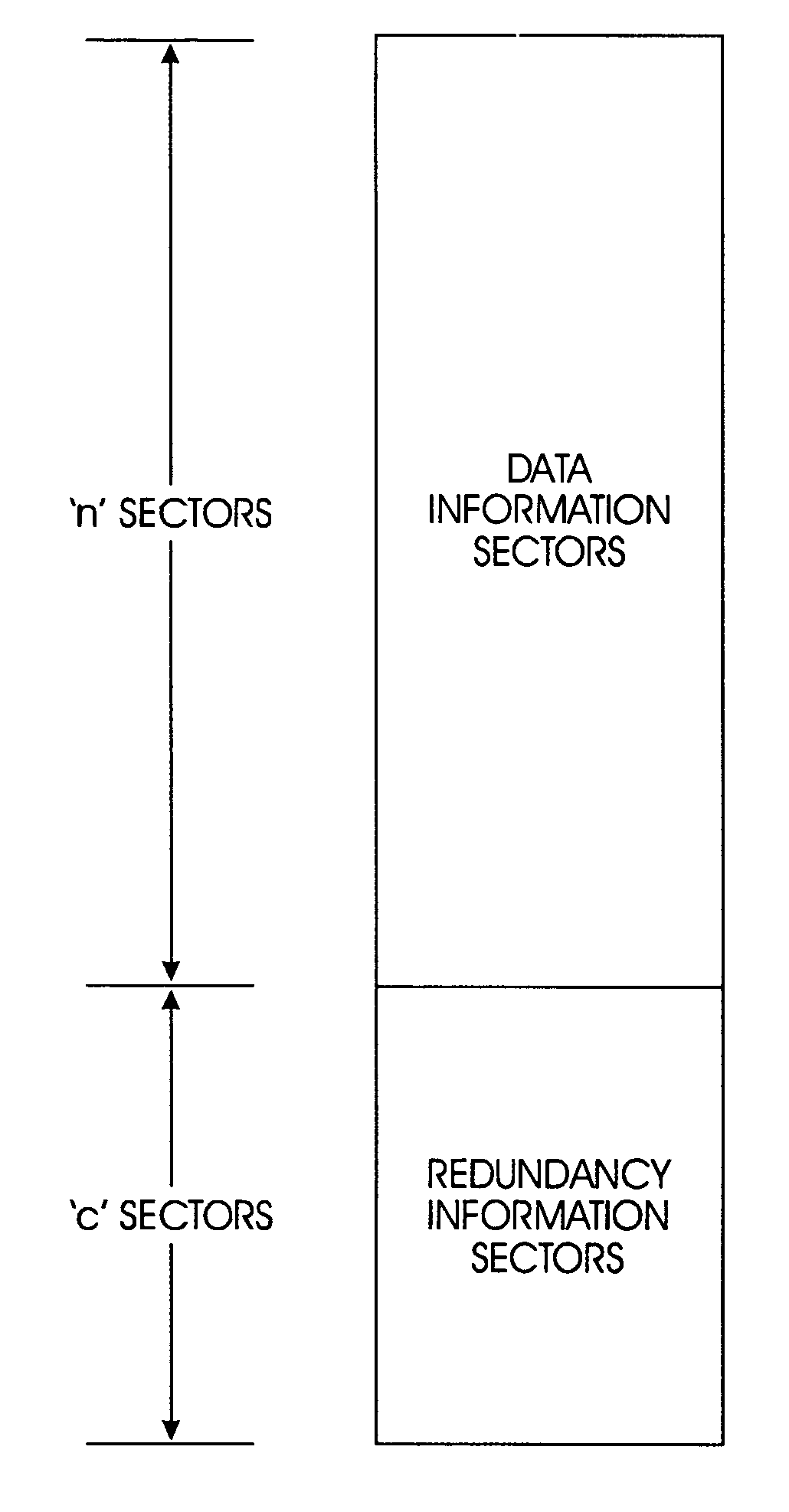
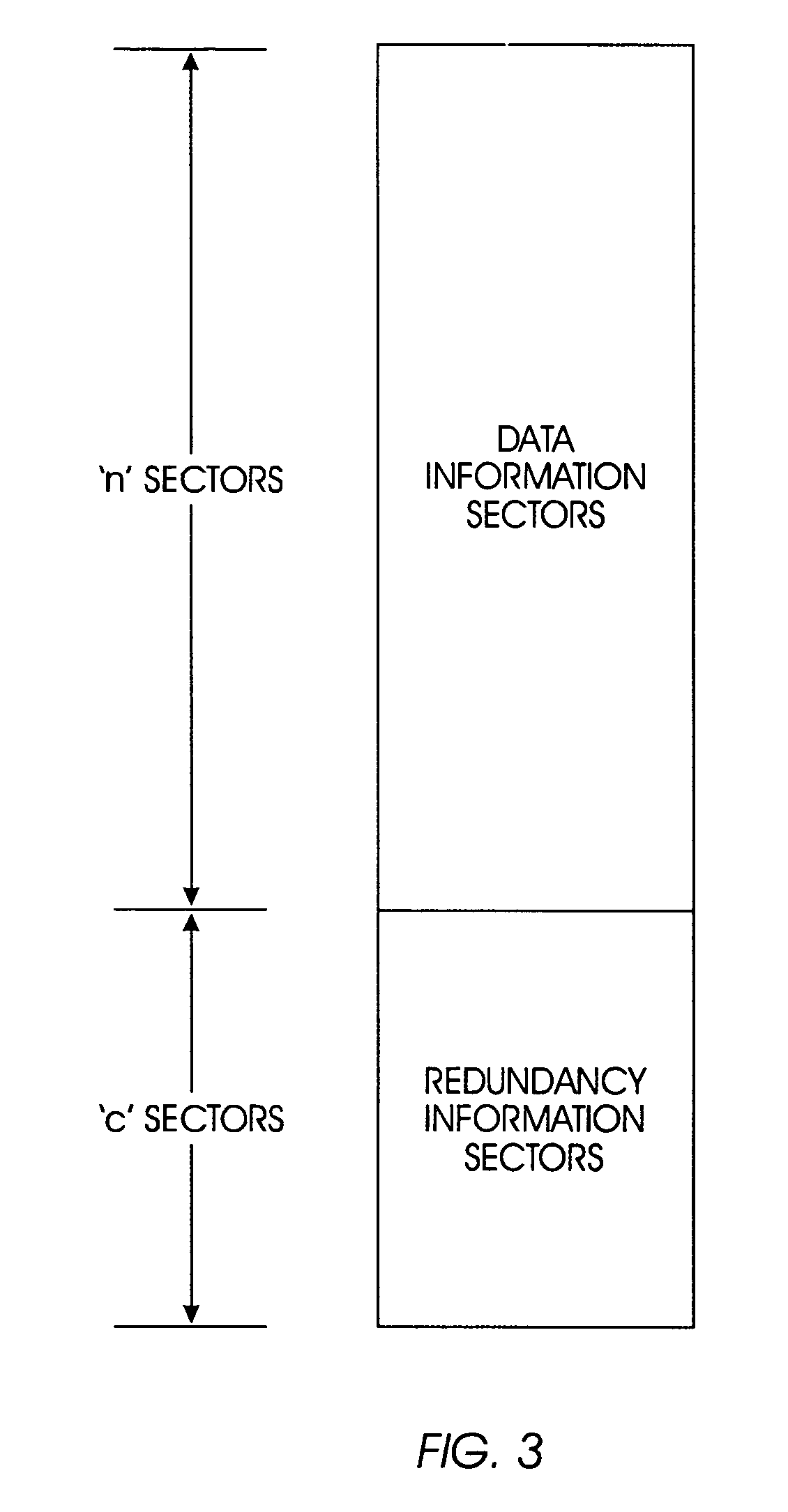
One embodiment disclosed is method for protecting data stored on at least one storage unit against uncorrectable media errors. The method includes associating a given redundancy set of at least one redundancy information sector (R) with a given data set of at least two data information sectors (D). The information content of the redundancy set is computed dependent on the information content of the data set. A storing operation stores the information content of the redundancy set consecutively with the information content of the data set forming a segment such that the redundancy set is placed logically in between a first part and a second part of the data set, and accessing at least one data information sector (D) in the data set by reading and / or writing the information content of the at least one data information sector (D) and at least one redundancy information sector (R) in the redundancy set with a single request.
Owner:IBM CORP
SVG (scalable vector graphics) imaging modeling-based method for realizing information resource monitoring and positioning
An SVG (scalable vector graphics) imaging modeling-based method for realizing information resource monitoring and positioning comprises the steps of imaging a modeling tool according to information equipment, establishing three layers of physical space position and logic hierarchical model of information resource, performing bidirectional binding on modeling and the equipment to support monitoring on different types of the same equipment and different equipment of the same type, designing a monitoring model, wherein configuration parameters, resource type, monitoring data items, data alarm threshold values and the like for monitoring need to be configured when the model is related to the equipment, performing real-time monitoring and customizing on the information equipment according to a real-time attention model by dimensions, concerned by a user, of application, the information resource, the resource type and the like, and performing statistics, analysis and summarizing on the alarm data according to the data and the alarm rule which are collected by monitoring. The SVG imaging modeling-based method has the characteristics of easiness in configuration, maintenance and expansibility and strong suitability and is suitable for the information department of a company to configure and monitor the equipment.
Owner:STATE GRID CORP OF CHINA +1
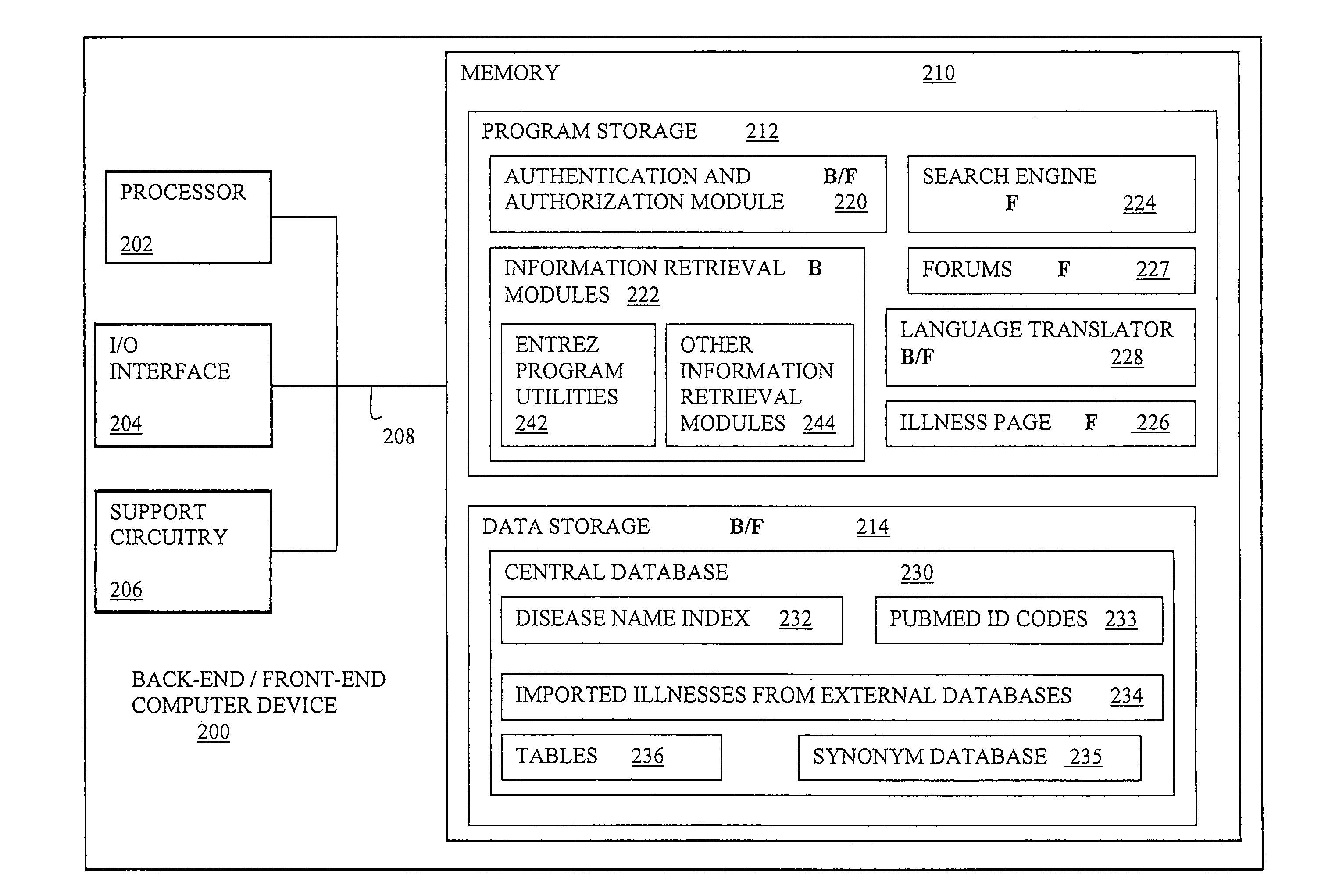
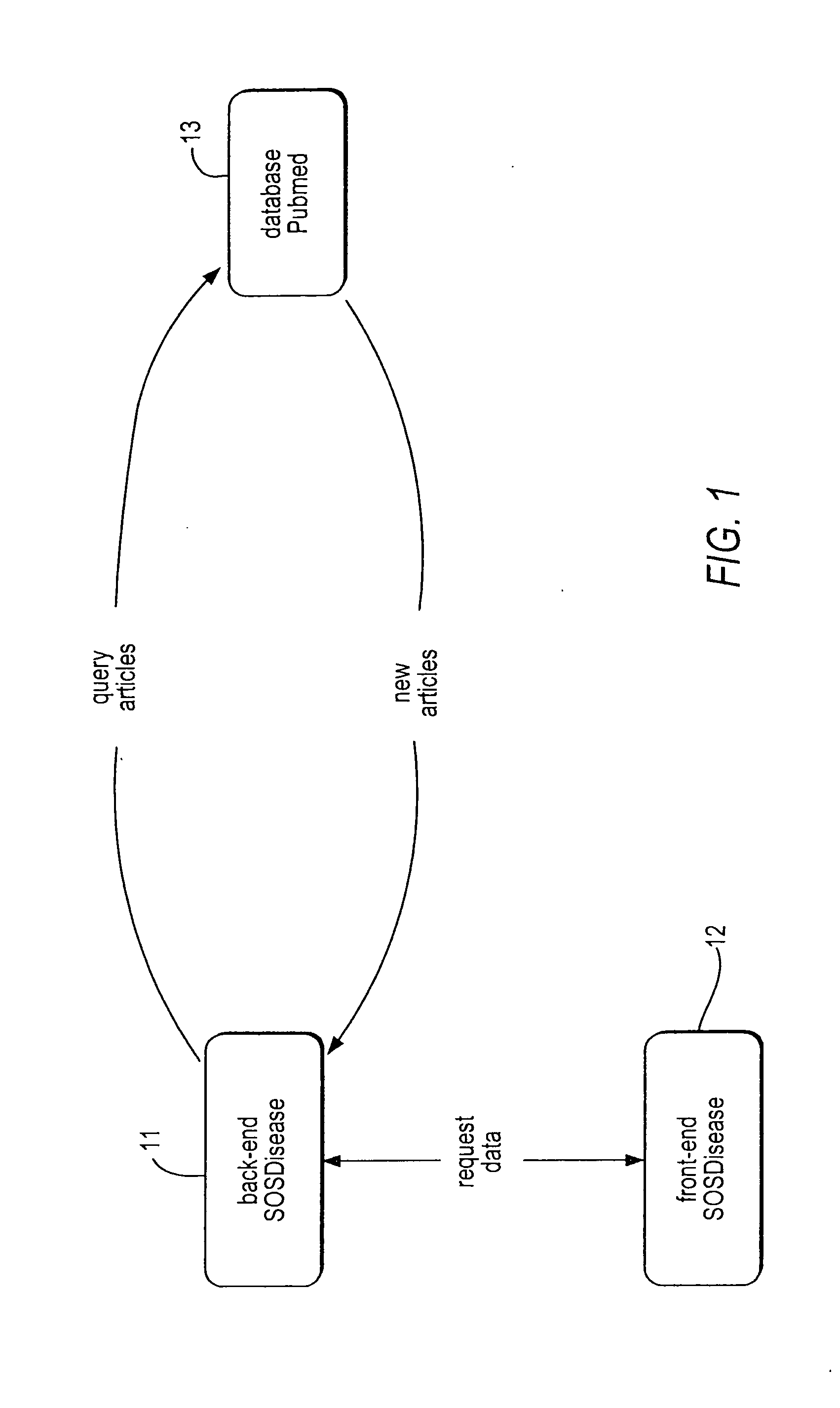
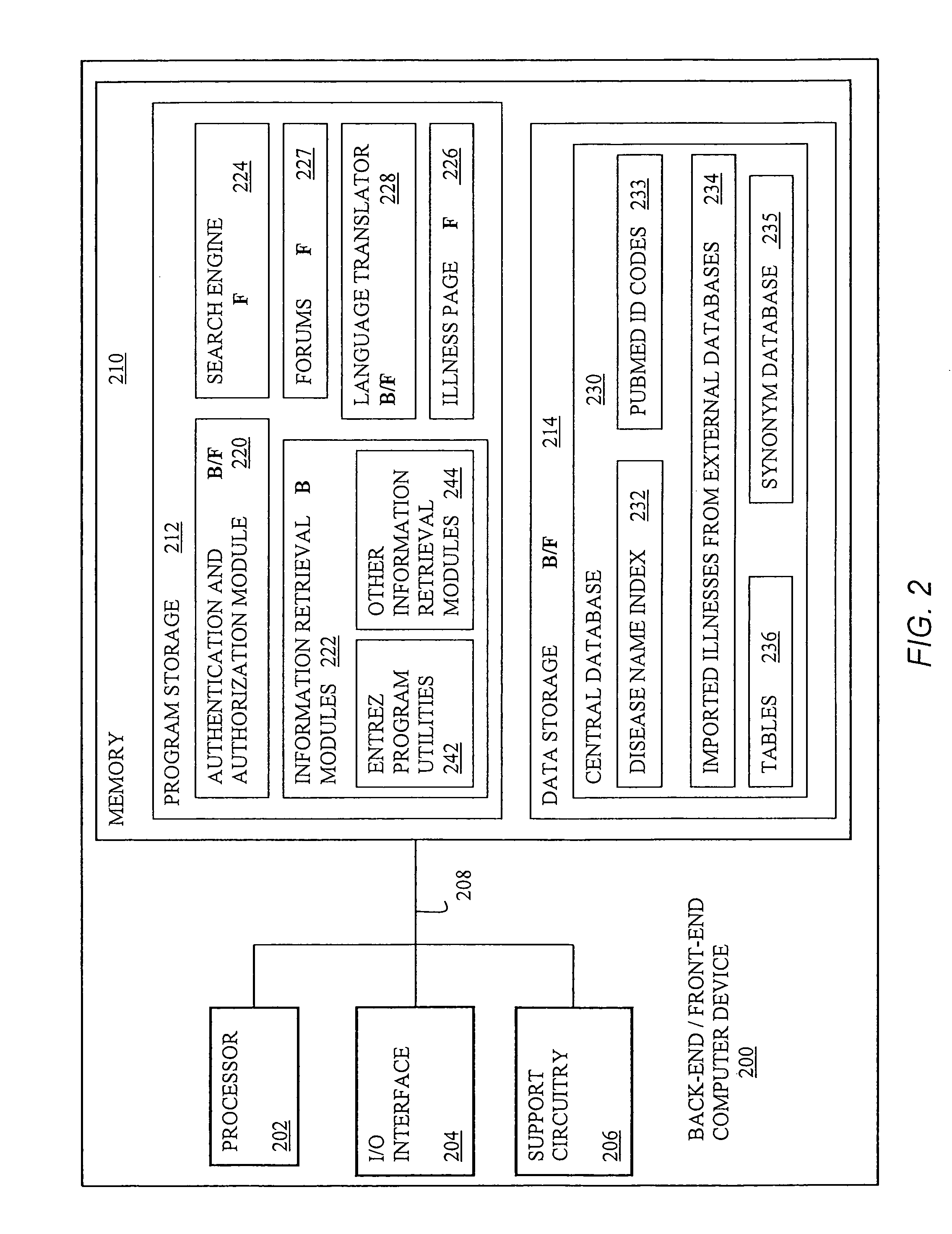
Electronic system for a social -network web portal applied to the sector of health and health information
InactiveUS20100306183A1Overcome disadvantagesMedical data miningDigital data processing detailsHealth related informationElectronic systems
A system for retrieving health-related information includes at least one processor coupled to memory; a back-end subsystem for storing in the memory, illness and health-related information imported from external data-base sources. An information retrieval program stored in the memory is executable by the processor to search the external data-base sources for illness and health-related terms and definitions; organize the illness and health-related information in an internal data-base stored in the memory by categories according to illness names, and include an aggregation of synonyms of scientific and unofficial terms identifying the illness names in different languages; search in each category for health-related articles in at least one predetermined international scientific data-base; and populate the internal data-base with information related to the articles. A front-end subsystem includes a search engine for searching the internal data-base for illness names; and an illness-page module for displaying the results including illness and health-related information and articles.
Owner:ECONFIDENCE SRL
Nonvolatile semiconductor memory
InactiveUS7379359B2Small scaleExtension of timeRead-only memoriesDigital storageAudio power amplifierAccess time
A regular sense amplifier and a defect-information sense amplifier are provided for each regular sector and each defect-information sector, respectively. This can prevent an excess load from being applied to a read path, and minimize the access time. A write amplifier is provided in common to the regular sector, the reference sector, and the defect-information sector. Generally, the write operation time of a nonvolatile semiconductor memory is long, so that an increase in a wiring load on a data transmission path and an increase in a load on a switch do not affect the write operation time much. As a result, the circuit scale can be made smaller without lengthening the read access time, and thereby the fabrication cost of the nonvolatile semiconductor memory can be reduced.
Owner:SOCIONEXT INC
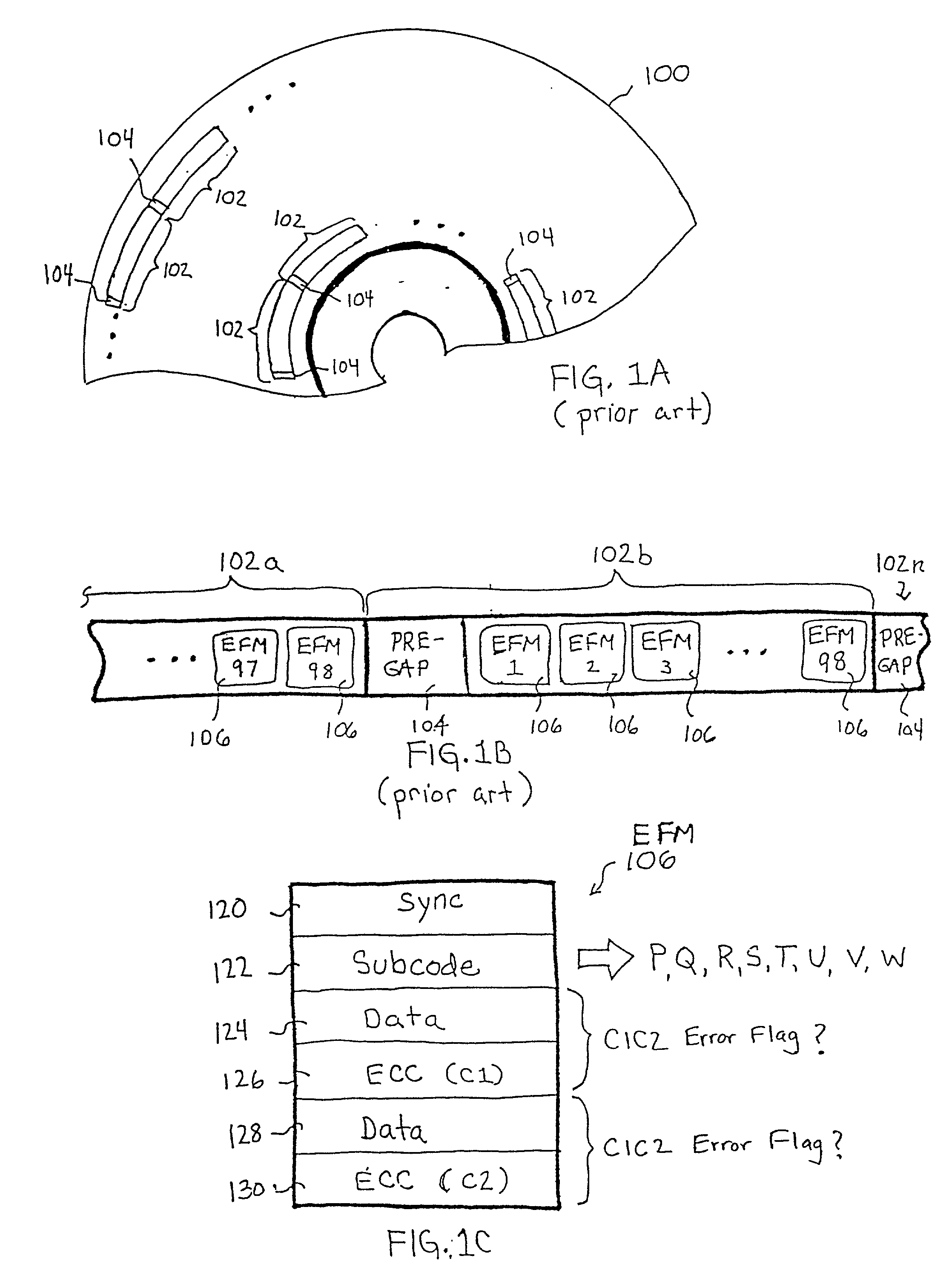
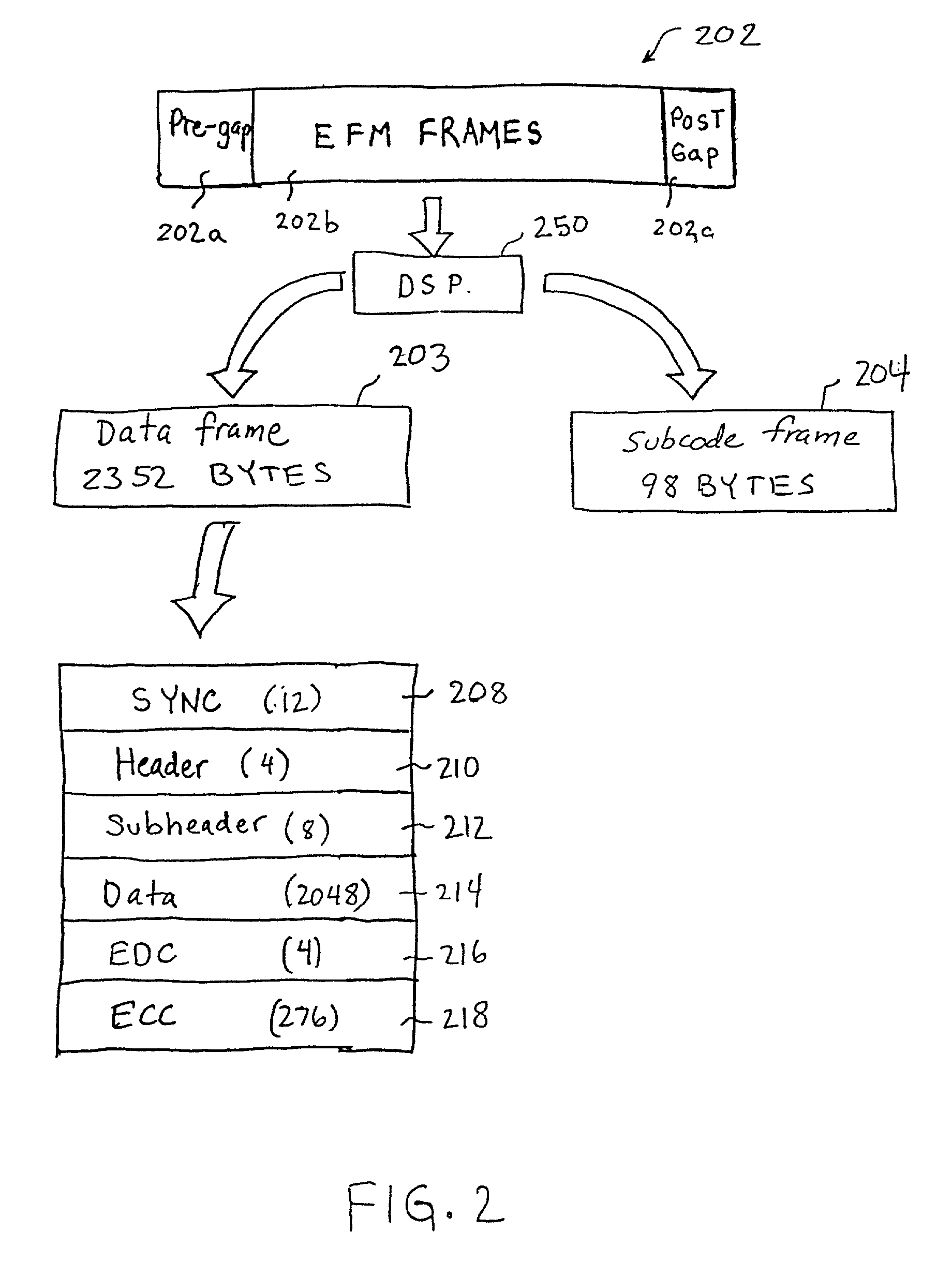
Methods and apparatus for delayed block release in compact disc systems
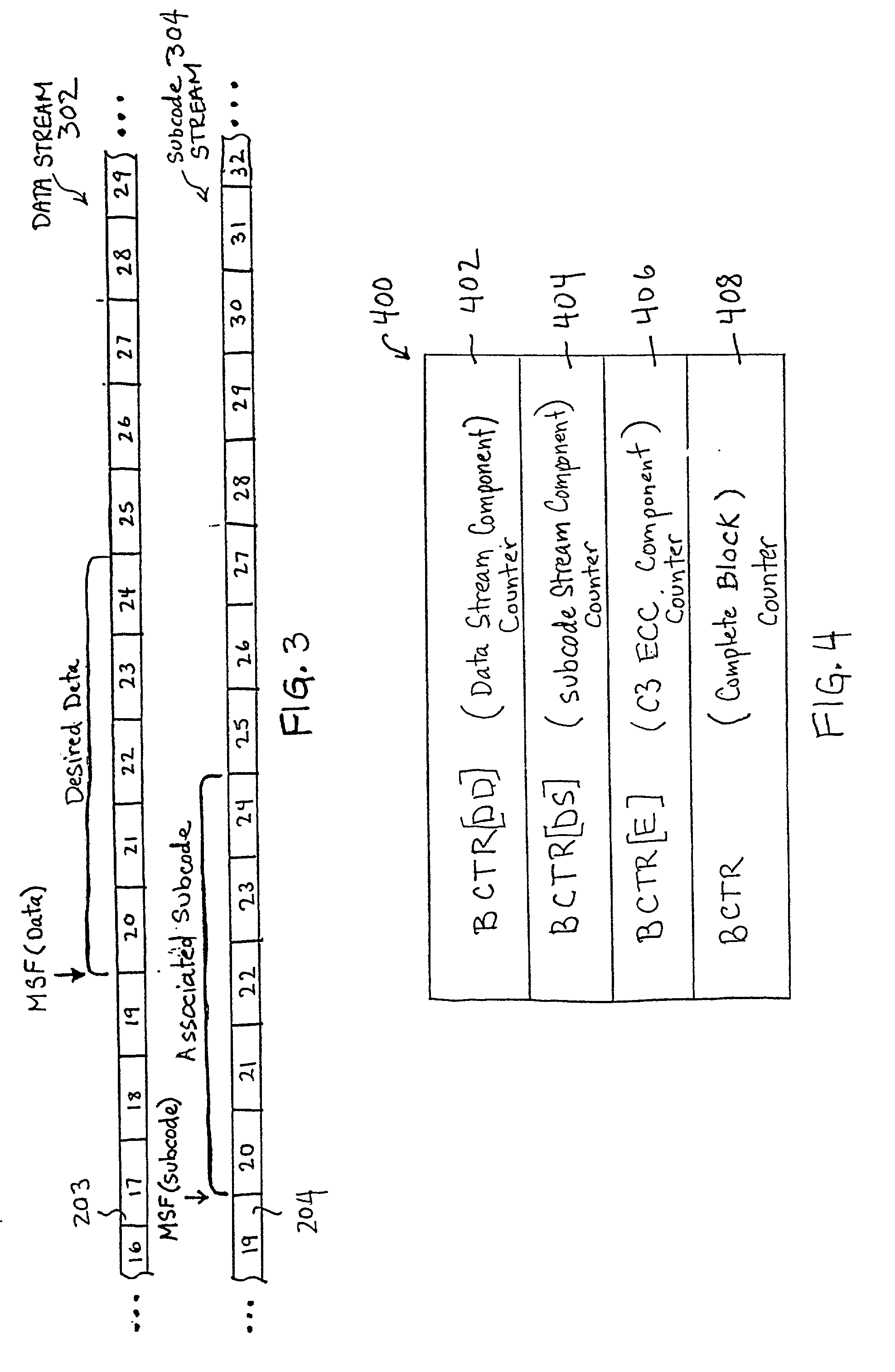
InactiveUS6373794B2Television system detailsData buffering arrangementsCompact discInformation sector
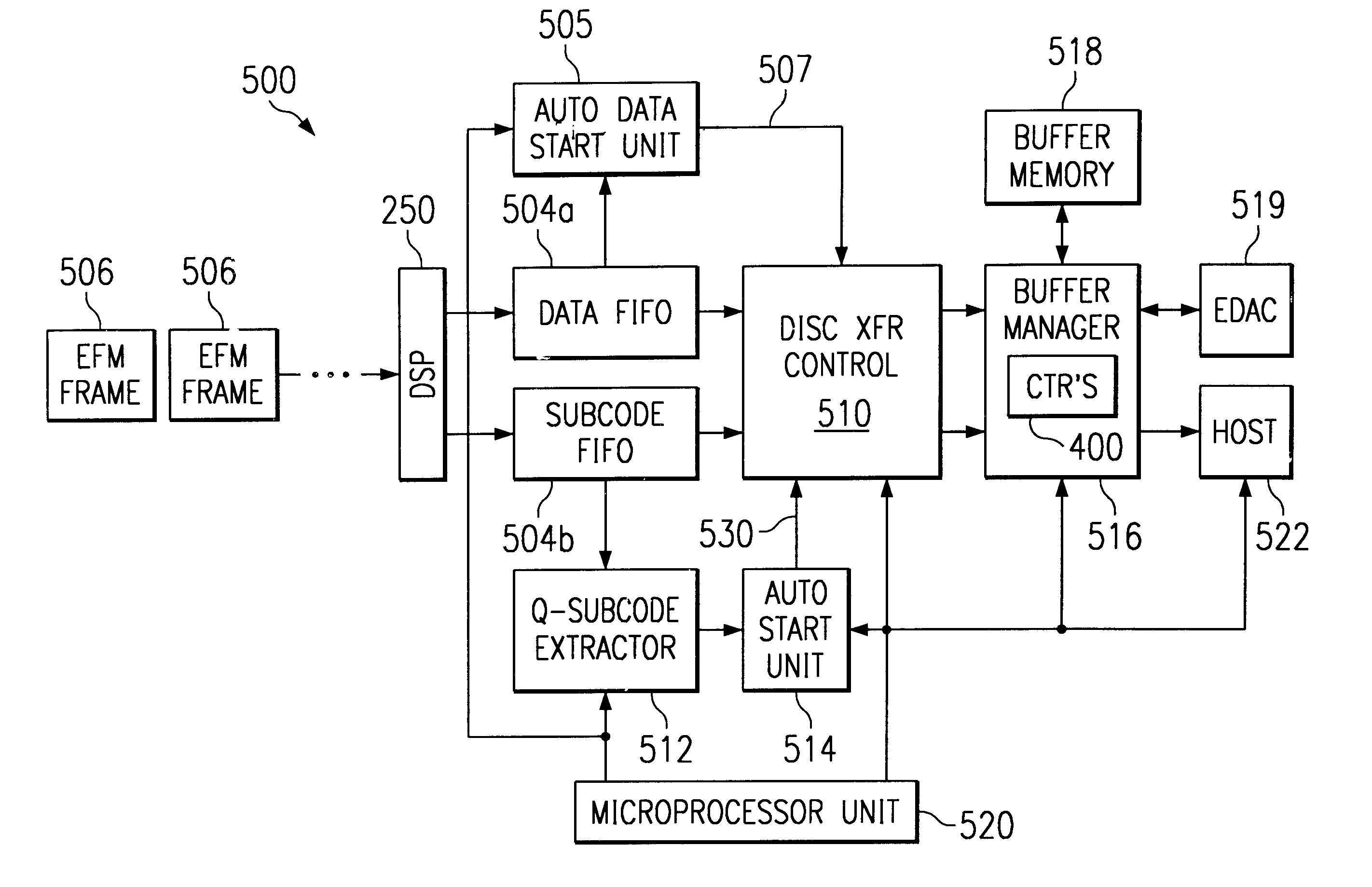
Disclosed is a disc drive system that includes a digital signal processor for processing information sectors read from a CD media. The digital signal processor is configured to parse the information sectors into data frames and subcode frames. A data auto-start unit for triggering a data transfer to a buffer memory when a desired data frame is detected. A subcode auto-start unit for triggering a subcode transfer to the buffer memory when a desired subcode frame is detected. Preferably, the desired data frame and the desired subcode frame have a same MSF. The disc drive system further includes a buffer manager having a plurality of counters that are configured to track the number of data frames and the number of subcode frames being transferred to the buffer memory, and releasing a block including one of the data frames and one of the subcode frames when the counters indicate that the block is complete.
Owner:STMICROELECTRONICS SRL
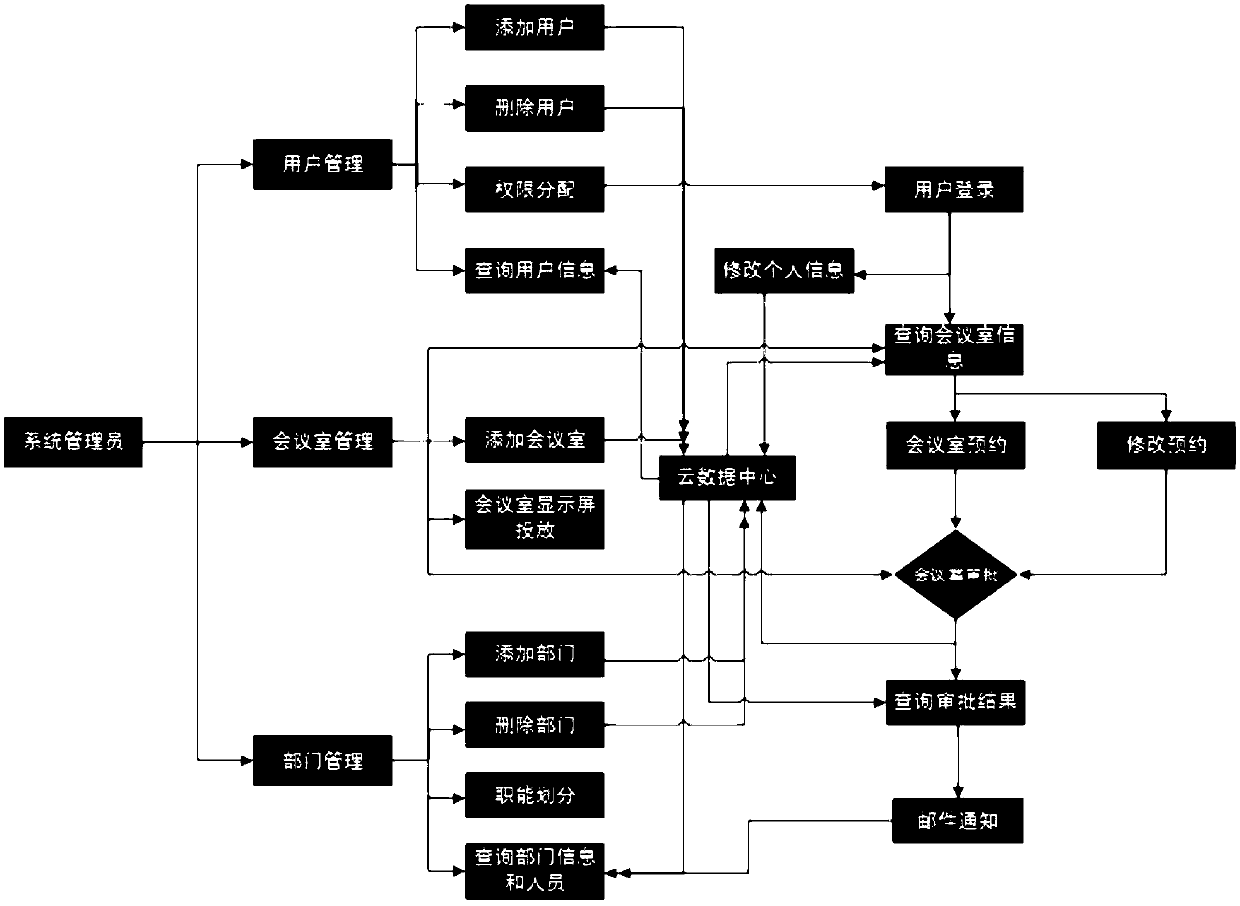
Cloud computing-based conference room on-line reservation management system and cloud computing-based conference room on-line reservation method
InactiveCN107633314AAvoid using conflictsReduce labor costsReservationsOffice automationResource managementLibrary science
The present invention provides a cloud computing-based conference room on-line reservation management system and a cloud computing-based conference room on-line reservation method. According to the present invention, by the user management, the conference room resource management, the department information management and the user reservation audit activities, the conference participation personnel, the conference room resources and the conference time are coordinated fully, the conference room resource usage conflicts and the manpower cost needed by using the conference rooms are reduced, andthe conferencing efficiency is improved. By constructing the keywords for the user information, the conference room information, the department information and the conference room reservation results, users can query the needed information conveniently and more rapidly, and the conference room reservation efficiency is improved. According to the present invention, various resources are called according to the demands, more costs are saved for the enterprises, the conference room reservation randomness and the resource waste are avoided, and the management levels of the enterprises take new steps.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
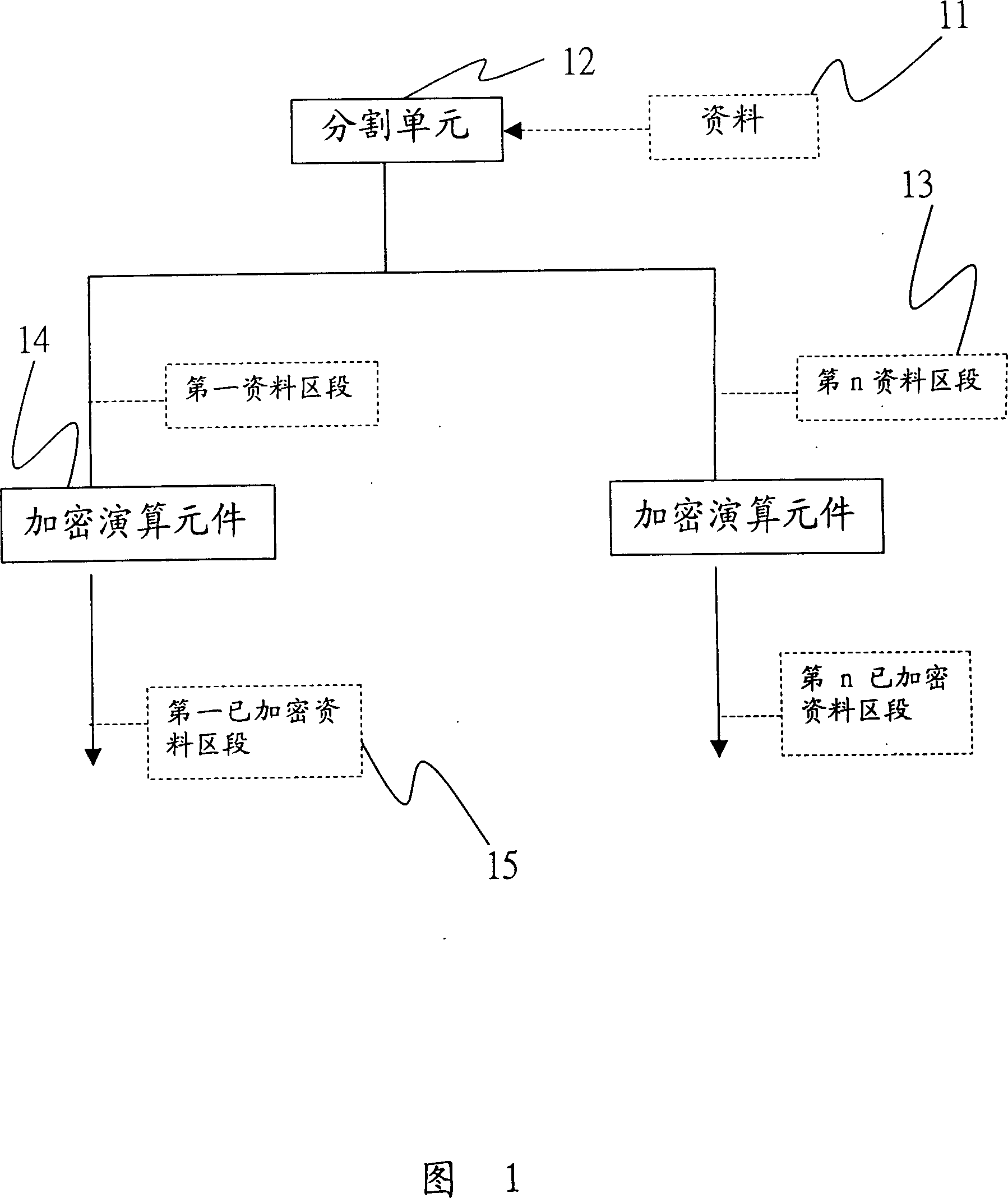
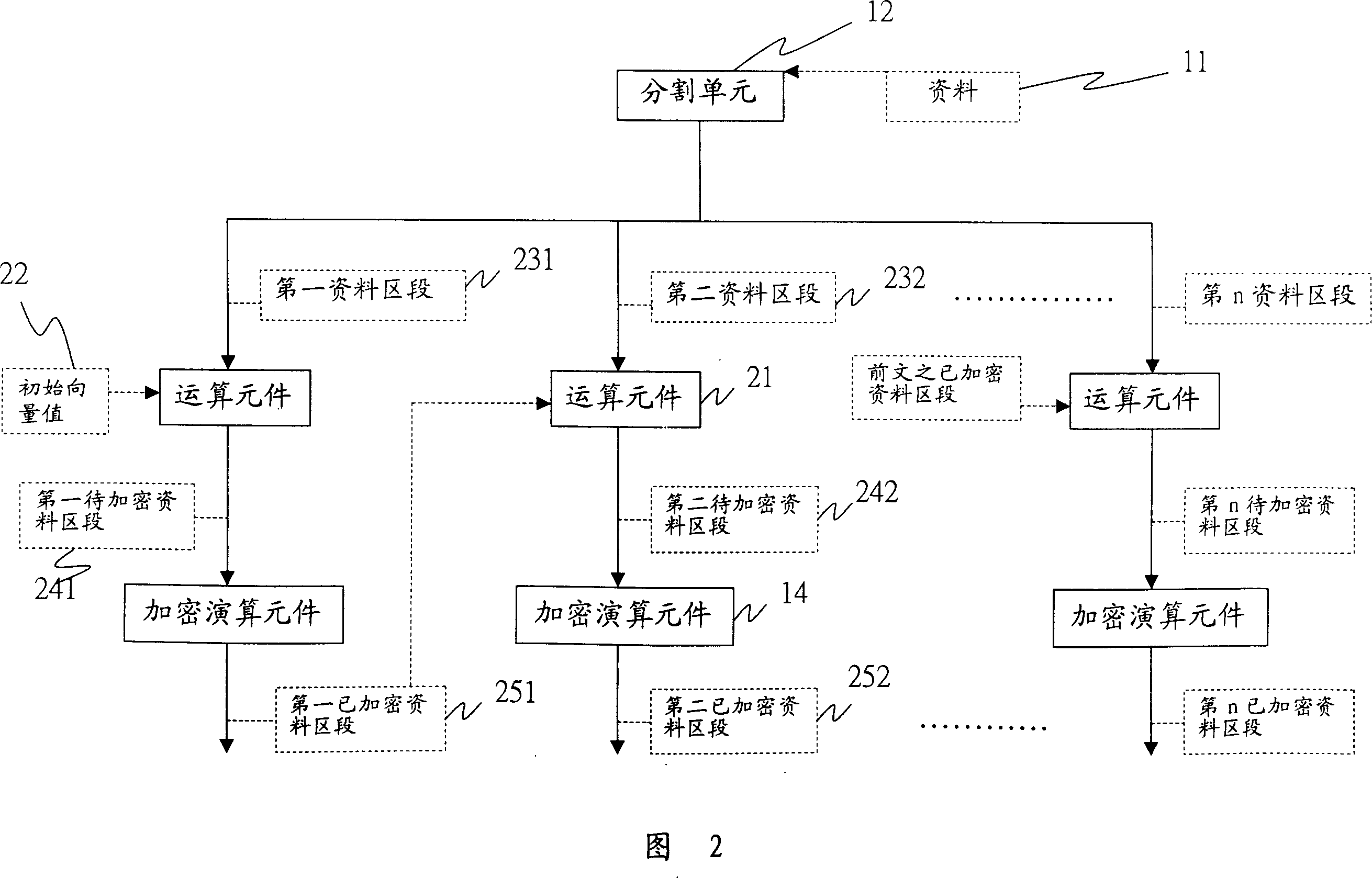
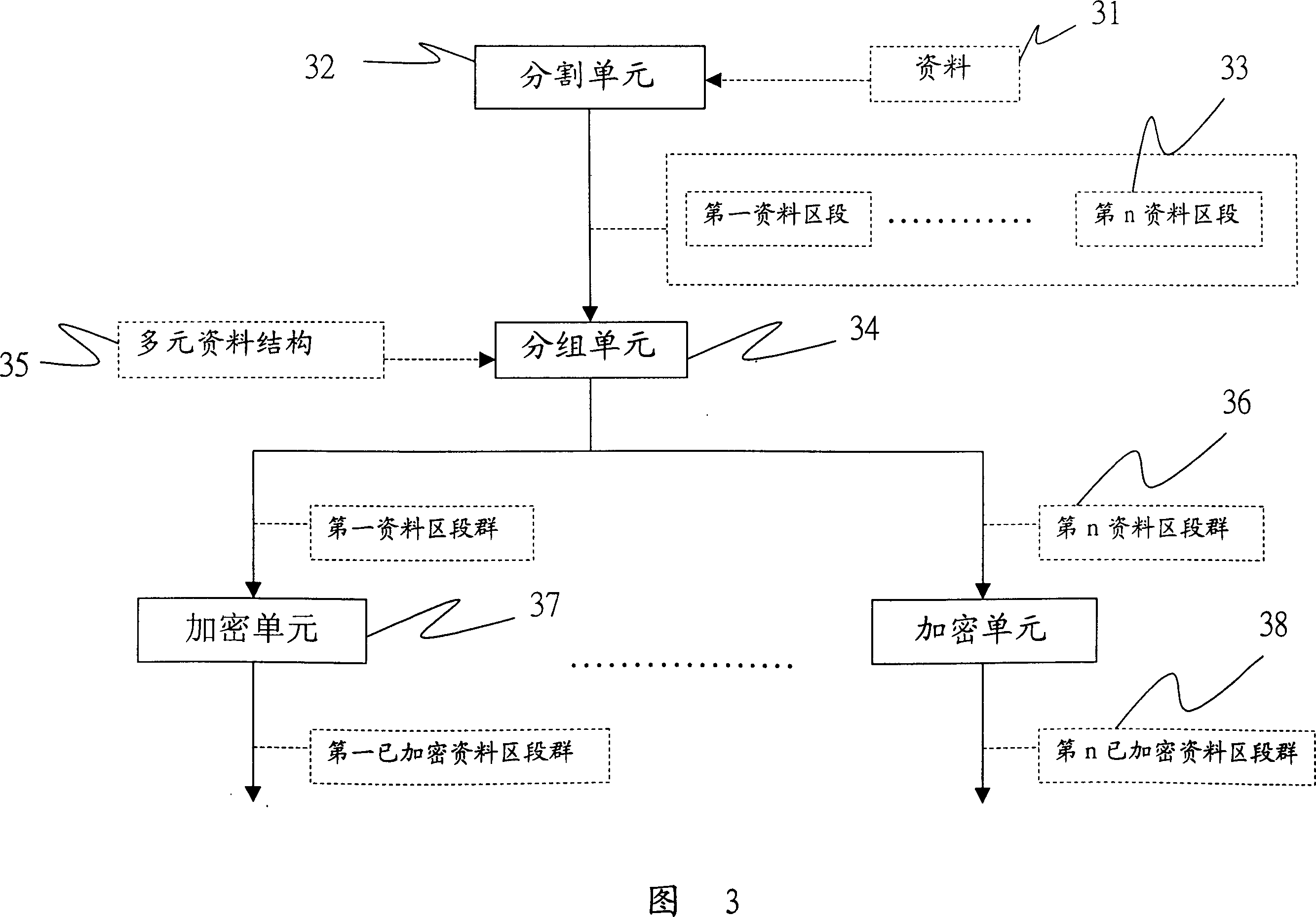
Encryption mode combined with file structure
InactiveCN1992588AShorten the timeTake security into considerationMultiple keys/algorithms usageComputer hardwareInformation sector
This invention discloses an encryption mode of combinated of information structure. This mode includes a separate unit, a group unit and the plural encryption modules. The separate unit separates a document into plural information sections. According to a multiple-element information structure, the group unit divides the information section into plural information section group. Finally, it uses the plural encryption modules for computing the encryption algorithms in order to generate the encrypted information sector group. Thereby, it achieves to shorten the encryption time and improve the encryption speed.
Owner:BEST WISE INT COMPUTING
Encryption and decryption method and system capable of aiming at disk data memory area
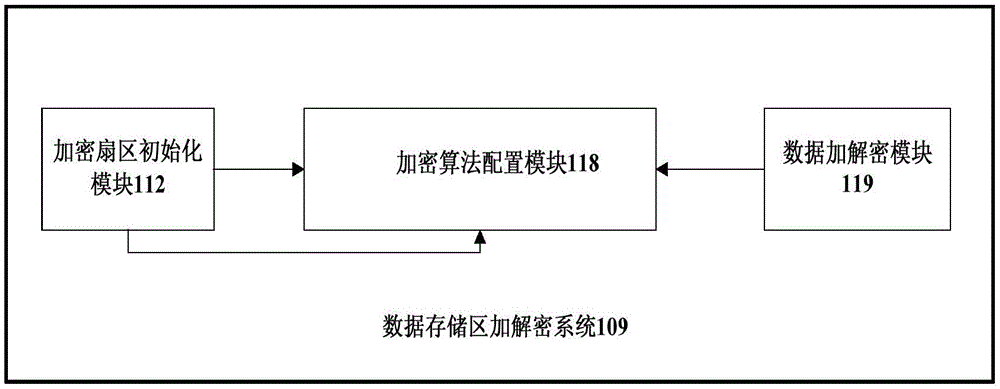
InactiveCN106709380AEfficient encryption and decryption frameworkImprove securityInternal/peripheral component protectionFile systemComputer module
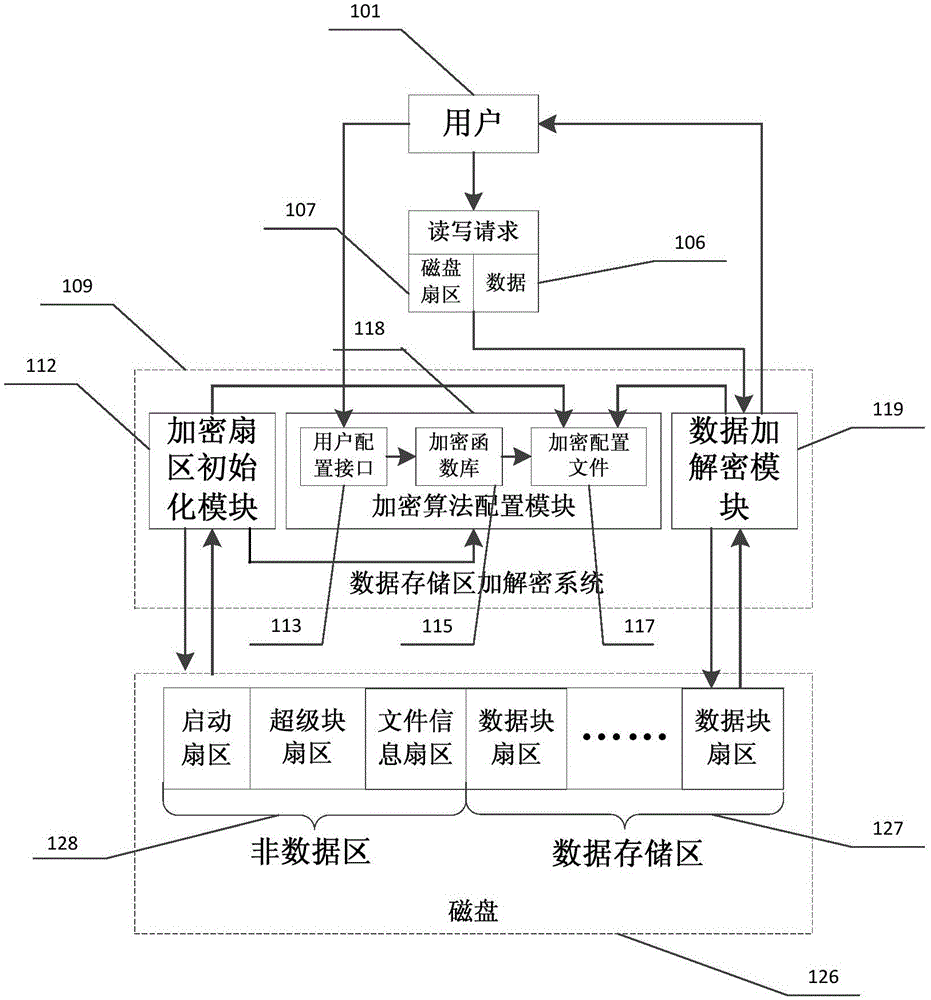
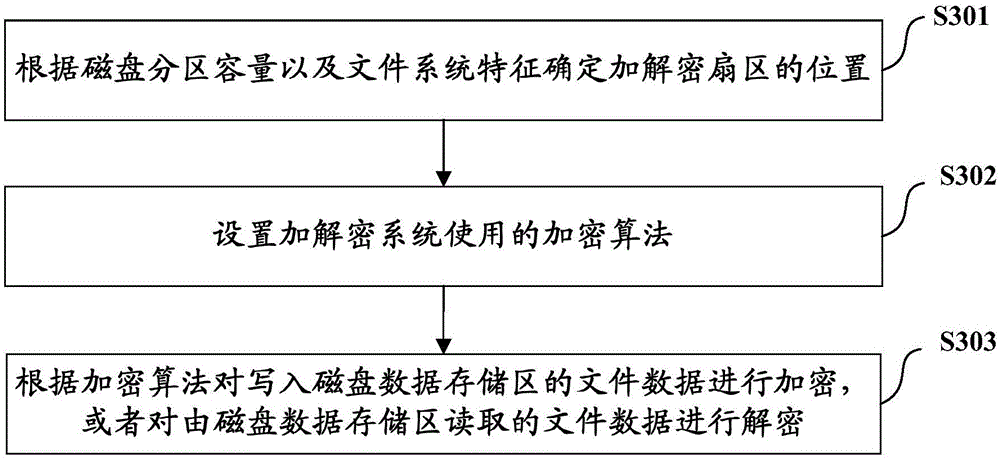
The invention relates to an encryption and decryption method and system capable of aiming at a disk data memory area. The system comprises an encryption algorithm configuration module (118), an encryption sector initialization module (112) and a data encryption and decryption module (119), wherein the encryption sector initialization module (112) is used for setting a sector which needs to be encrypted and decrypted according to the partitioned memory capacity of a disk and file system characteristics; the encryption algorithm configuration module (118) is used for setting an encryption algorithm used by the system; and the data encryption and decryption module (119) is used for encrypting file data written into the disk data memory area according to the encryption algorithm and carrying out decryption on the file data read via the disk data memory area. By use of the system, decryption and encryption processing for the disk data memory area is realized, but the boot sector of the disk and the super block sector and the file information sector of the disk file system are not subjected to the encryption and decryption processing, and an efficient disk encryption and decryption frame is realized.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI +1
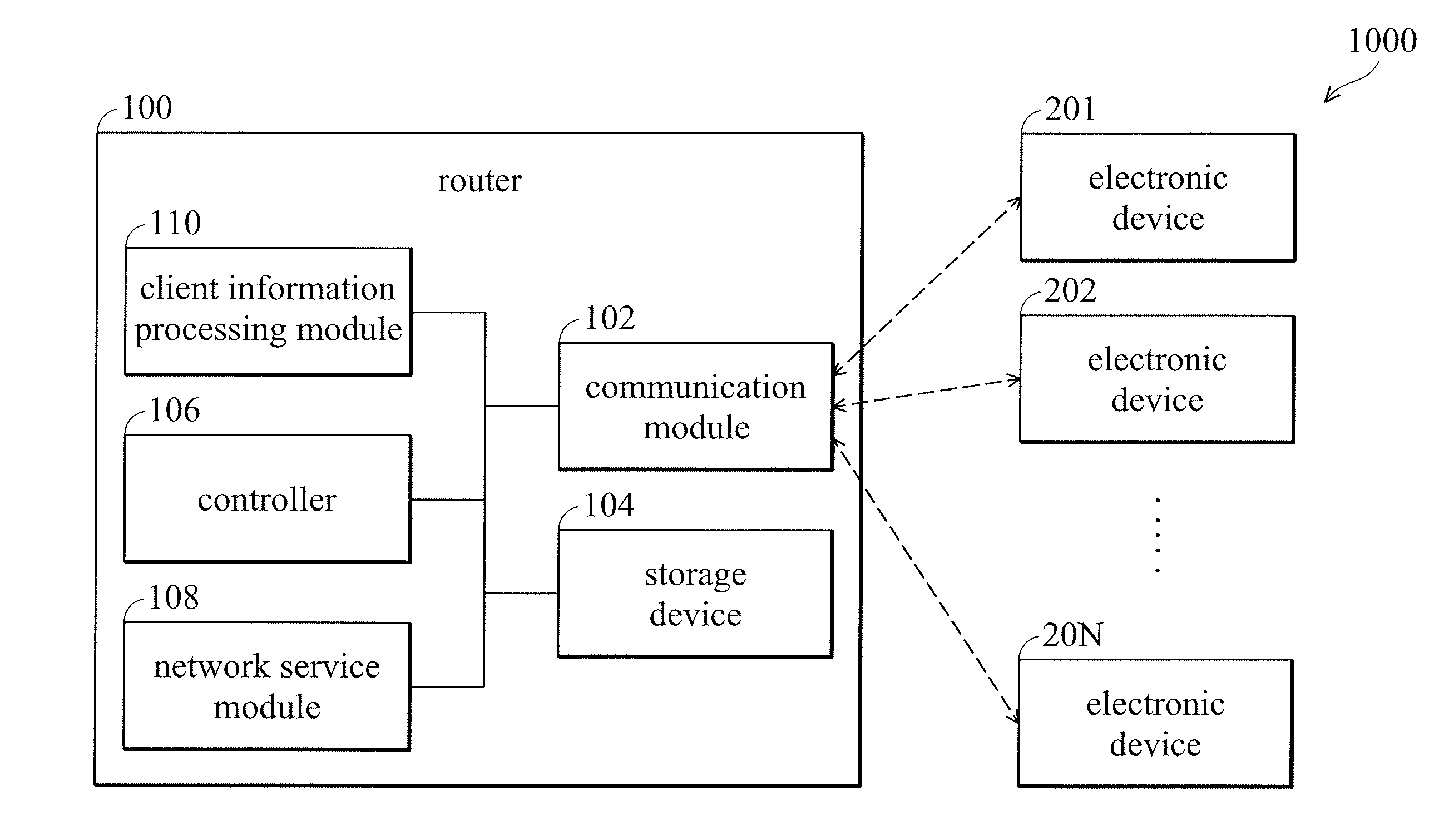
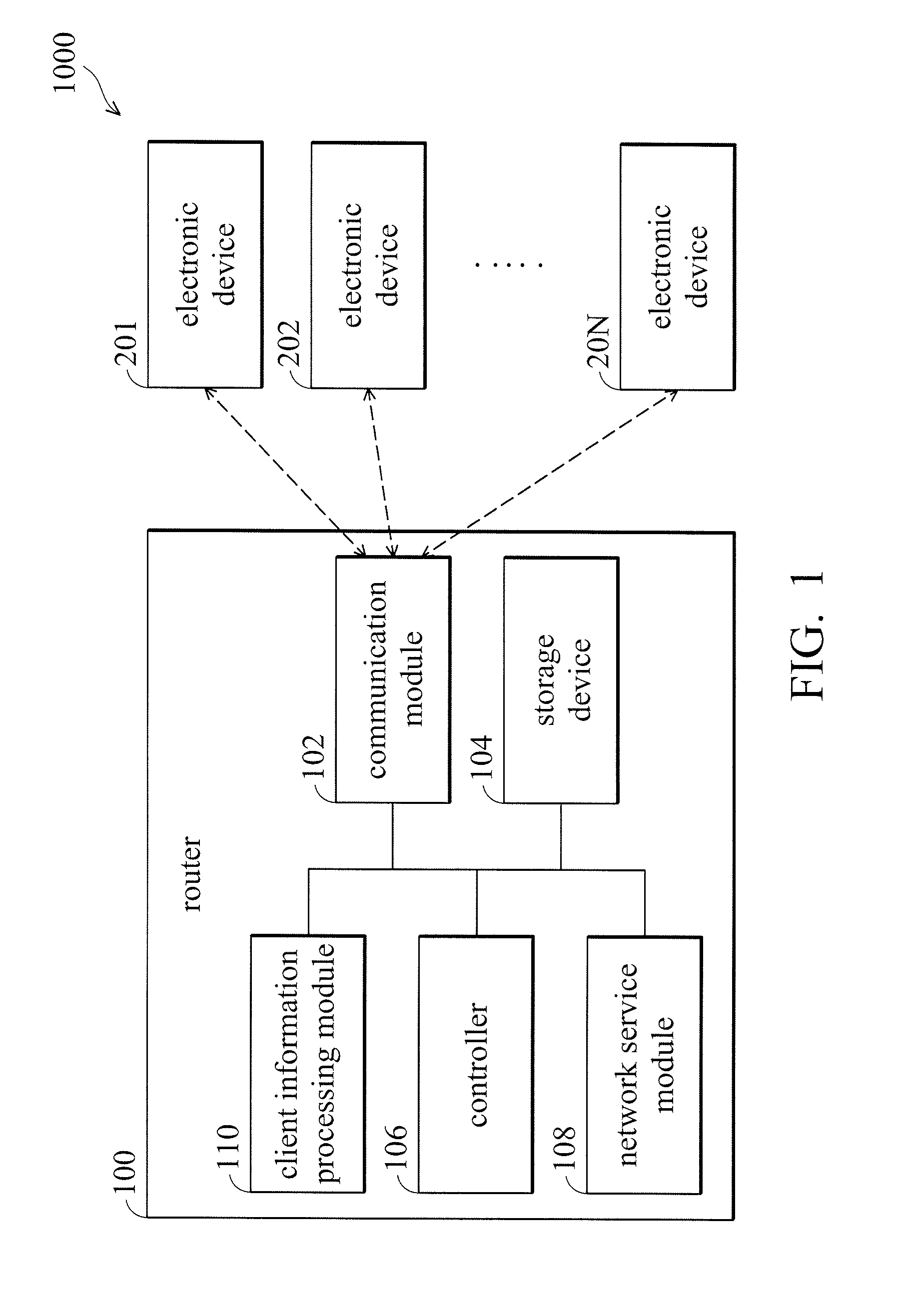
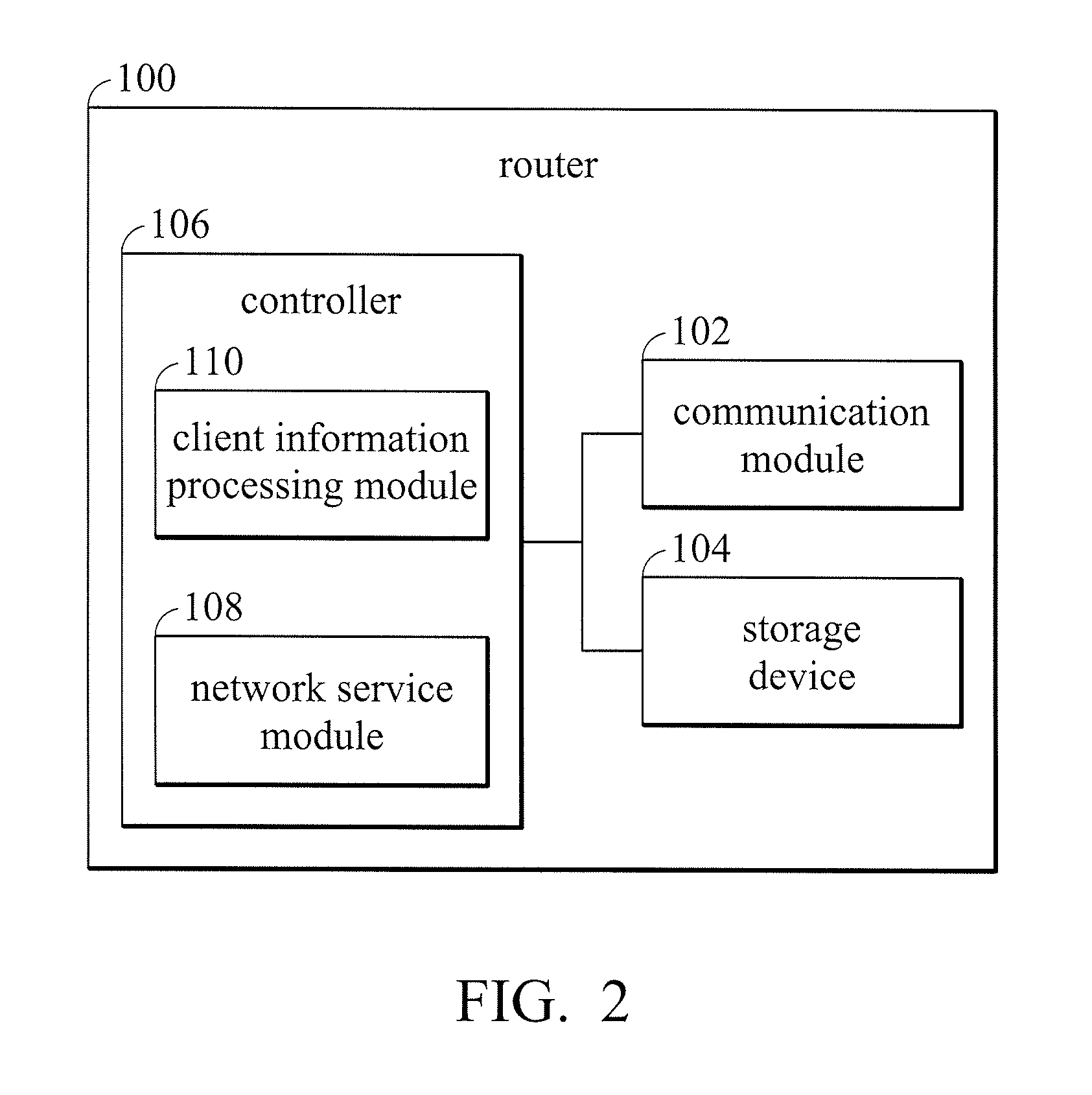
Router and information-collection method thereof
The present invention provides a router including a storage device, a communication module, and a controller. The storage device stores a web-page code corresponding to a graphical user interface, wherein the web-page code includes an information-gathering code. The controller enables the communication module to transmit the web-page code to the first electronic device coupled in response to a predetermined web-page request received from the first electronic device, wherein the information-gathering code is arranged to collect an environment information sector of the first electronic device and transmit the environment information sector of the first electronic device to the router.
Owner:WISTRON NEWEB
Enterprise information operation, maintenance and management method
InactiveCN105825275AReal-time monitoring of operationReal-time monitoring inputOffice automationData centerButt joint
An enterprise information operation, maintenance and management method relates to the information management technology field. The method has the following working flows of deploying an EICM information management system in an enterprise data center; initializing the enterprise internal information via the information department personnel; recording or importing the new information, such as the personnel, the asset, the budget, the project, the contract, etc.; configuring the equipment monitoring; receiving the fault reports coming from other departments in a telephone or self-service manner, and noticing the related officials automatically and timely to follow and serve; supplementing the reports that are not generated automatically by a management system of the scheme via the related personnel and in the management system; managers checking the above information via a webpage or a WeChat official account to instruct. The enterprise information operation, maintenance and management method of the present invention is an information management platform that is customized for an enterprise information department omni-directionally, technically supports all current mainstream platforms, integrates the technology management and the working management as a uniform working and cooperation platform, and can in butt joint with a conventional relevant system.
Owner:GUANGZHOU JIA HE TECH CO LTD
Application network management and control method combining in-band management and out-of-band management of a power grid company
The invention provides an application network management and control method combining in-band management and out-of-band management of a power grid company, and the method comprises the steps: settingan acquisition server and a client plug-in, enabling the acquisition server to be divided into an in-band acquisition server and an out-of-band acquisition server, and enabling the in-band acquisition server to be accessed to a network in a non-intrusive mode; accessing the out-of-band acquisition server to the network to realize convergence of out-of-band monitoring data and internal monitoringdata, and the client plug-in is installed on a monitored object to acquire performance indexes in real time and integrate the performance indexes with the out-of-band performance indexes to form finalperformance data of the monitored object; and enabling the collected information to enter a server area system, and the server area system monitor and analyze all sessions entering the application and tracks database access actions caused by clicking of the user. According to the monitoring method for monitoring the availability and the performance of each service system in real time from the perspective of the terminal user, faults and hidden dangers of the system can be found in time, and rapid analysis and processing of an information department are facilitated.
Owner:STATE GRID LIAONING ELECTRIC POWER RES INST
Methods and apparatus for delayed block release in compact disc systems
InactiveUS20010002894A1Television system detailsData buffering arrangementsCompact discInformation sector
Disclosed is a disc drive system that includes a digital signal processor for processing information sectors read from a CD media. The digital signal processor is configured to parse the information sectors into data frames and subcode frames. A data auto-start unit for triggering a data transfer to a buffer memory when a desired data frame is detected. A subcode auto-start unit for triggering a subcode transfer to the buffer memory when a desired subcode frame is detected. Preferably, the desired data frame and the desired subcode frame have a same MSF. The disc drive system further includes a buffer manager having a plurality of counters that are configured to track the number of data frames and the number of subcode frames being transferred to the buffer memory, and releasing a block including one of the data frames and one of the subcode frames when the counters indicate that the block is complete.
Owner:STMICROELECTRONICS SRL
Intelligent bank card with hospital general treatment function
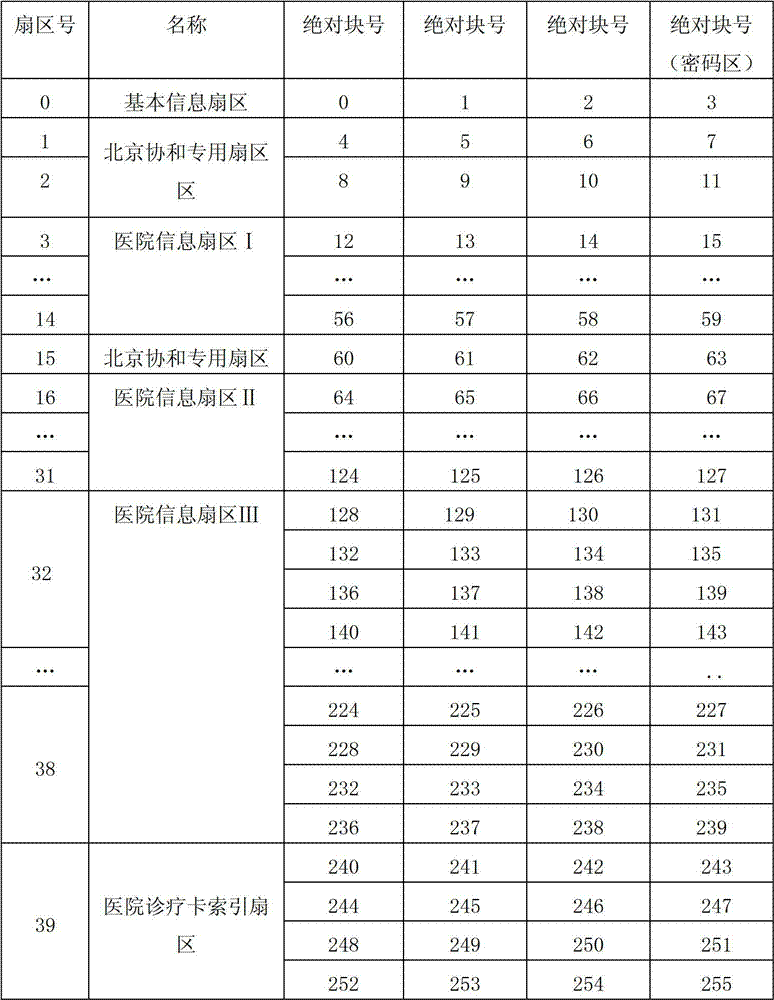
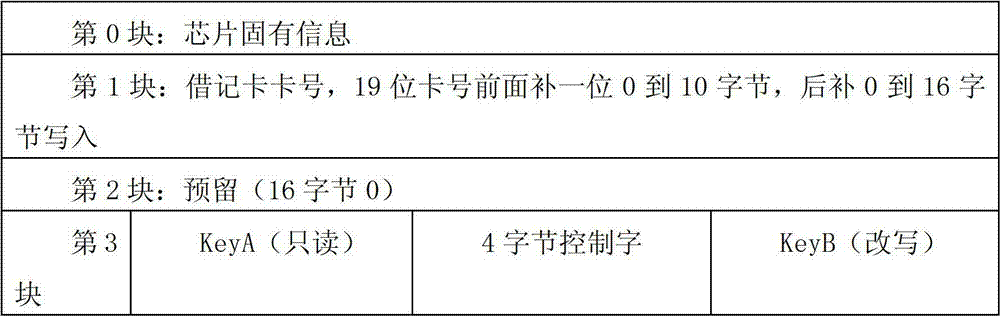
InactiveCN102855517ARealize the universal use of one cardRecord carriers used with machinesSpecial data processing applicationsPaymentMedical expenses
The invention discloses an intelligent bank card with a hospital general treatment function. The intelligent bank card comprises an intelligent card body and an integrated chip (IC), wherein a storage unit is arranged in the IC chip and comprises a basic information sector, a plurality of hospital information sectors and a hospital medical card index sector; the basic information sector consists of at least one sector; each hospital information sector consists of at least one sector positioned behind the basic information sector; and the hospital medical card index sector is arranged behind the hospital information sectors. The intelligent bank card with the hospital general medical function can be used on accept terminals such as doctor working stations, artificial windows and self-service medical suggestion equipment which are registered and activated, has financial functions of borrowing accounts and keeping accounts and can pay medical cost and other medical expenses; and an effect that one card realizes seeing doctors and payment in a plurality of hospitals can be achieved.
Owner:BANK OF CHINA
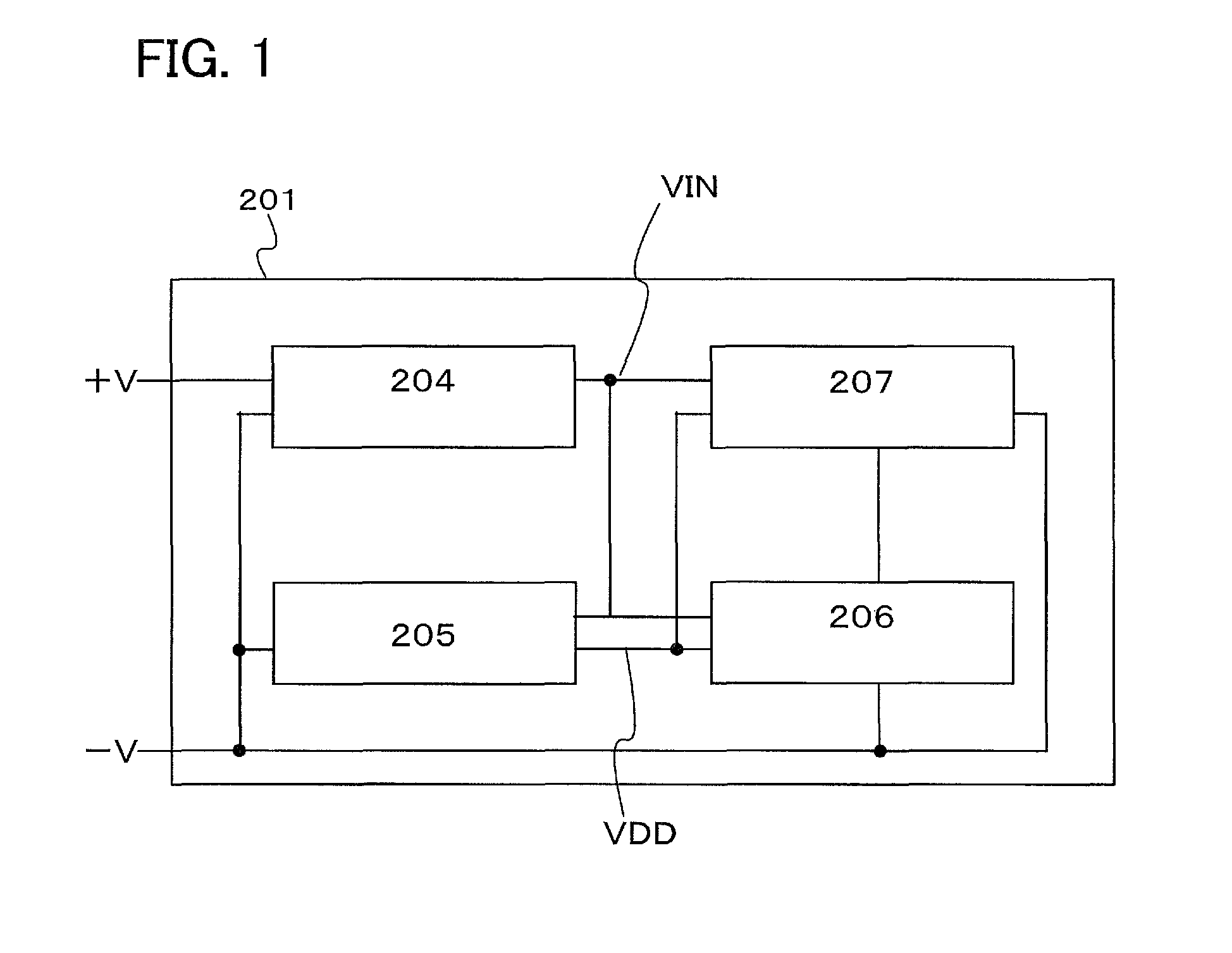
Semiconductor device and driving method the same
InactiveUS20110055463A1Prevent tamperingAvoid dataMemory architecture accessing/allocationMemory adressing/allocation/relocationPower semiconductor deviceComputer hardware
It is an object to prevent miswriting by radio in a relatively easy way in a semiconductor device which is capable of data communication (reception / transmission) through wireless communication, in particular, in an RFID tag provided with an OTP memory or a write-once memory. Alternatively, it is an object to prevent data from being tampered. Further alternatively, it is an object to inhibit access to a memory in a relatively easy way and to inhibit reading of data in a semiconductor device which is capable of data communication (reception / transmission) through wireless communication. In a semiconductor device including a control circuit and an OTP memory, a memory includes at least a sector for preventing additional writing and an information sector. When data for preventing additional writing is written to the sector for preventing additional writing and information is written to the information sector which is electrically connected to the sector for preventing additional writing, additional writing to the information sector to which the information is written is impossible.
Owner:SEMICON ENERGY LAB CO LTD
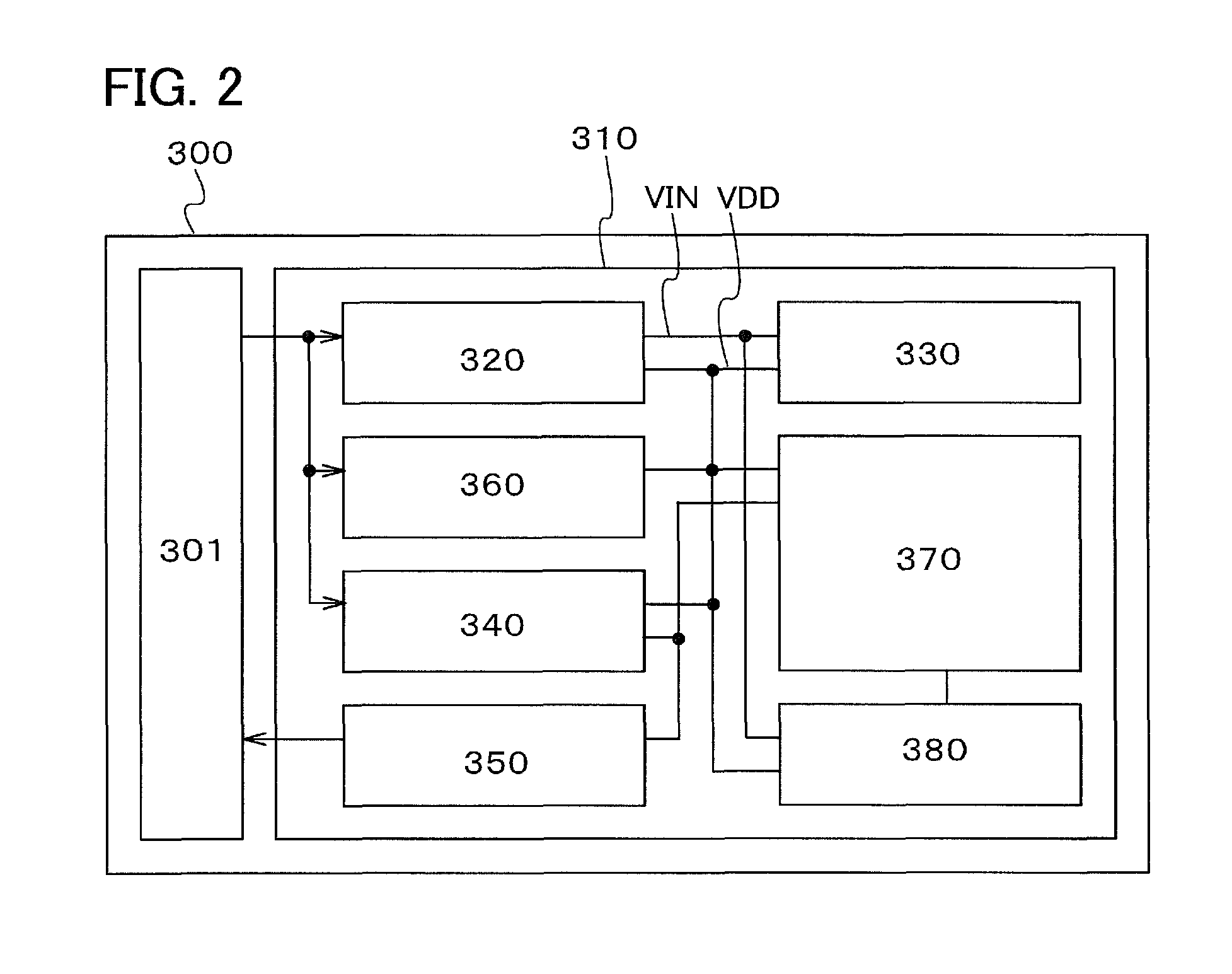
Semiconductor device and driving method the same
InactiveUS8825943B2Prevent tamperingAvoid dataMemory architecture accessing/allocationMemory adressing/allocation/relocationElectricityInformation sector
In a semiconductor device including a control circuit and a memory, the memory includes at least a sector for preventing additional writing and an information sector. When data for preventing additional writing is written to the sector for preventing additional writing and information is written to the information sector which is electrically connected to the sector for preventing additional writing, additional writing to the information sector is impossible.
Owner:SEMICON ENERGY LAB CO LTD
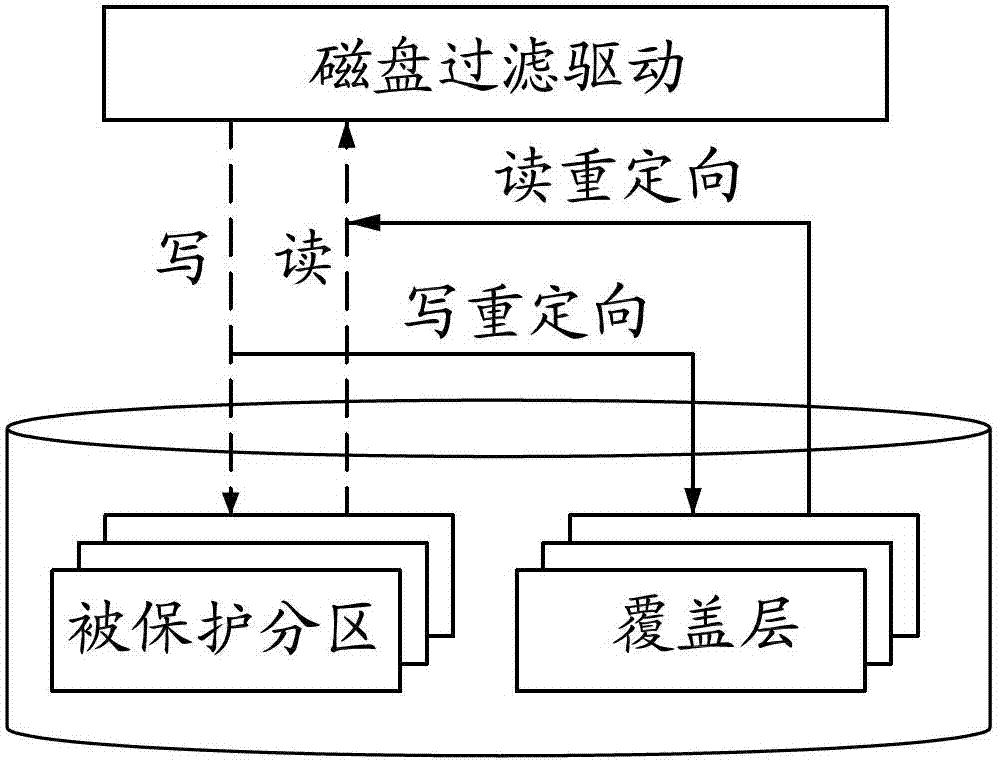
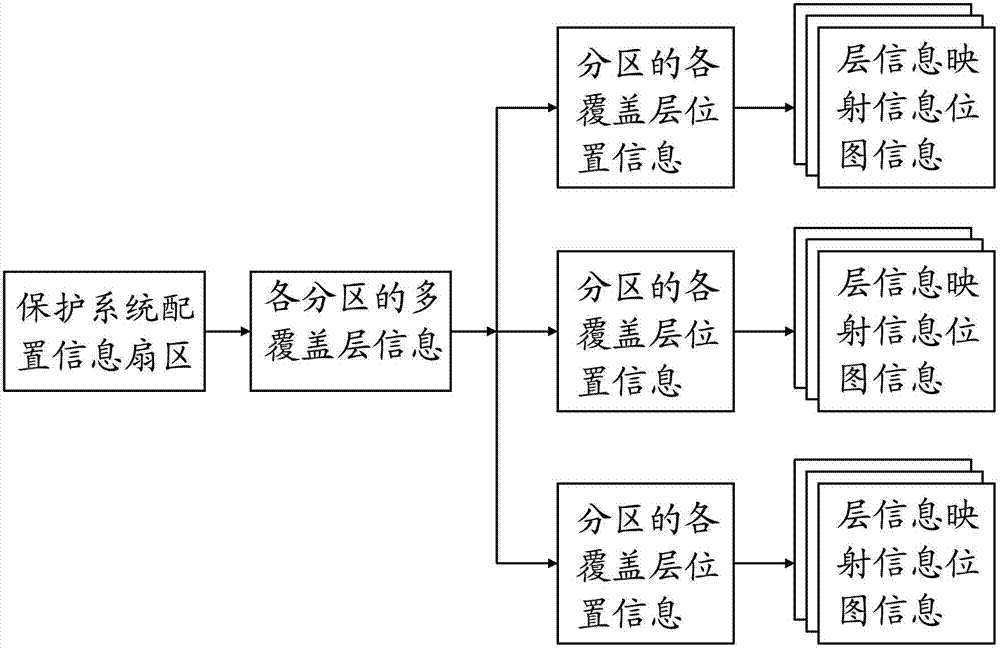
Disk protection system of tree-form multilayer cover layer of sector increment and implementing method thereof
ActiveCN102799542BImplement read and write redirectionPrivacy protectionUnauthorized memory use protectionLevel structureComputer module
The invention provides a disk protection system of a tree-form multilayer cover layer of a sector increment and an implementing method thereof. The disk protection system and the implementing method comprise a disk filter drive, a configuration information module, a current layer and a history cover layer, wherein the disk filter drive is used for implementing reading-writing redirections to writing filter data of a protected partition through the current layer and the history cover layer, the configuration information module is used for storing a configuration information structure which consists of multiple levels structures; the multiple levels of structures include a disk protection system configuration information sector, multiple cover layer information of each partition, position information of each cover layer of the partition and a layer information sector in turn; the address of the next level of structure is stored in the front level of structure, and the tree-form hierarchical structure of multiple layers of cover layers can be analyzed only through the disk protection system configuration information sector. According to the disk protection system and the implementing method, multiple layers of covering layers are effectively organized through a configuration information structure so as to support multiple functions of the cover layers, each cover layer is of a tree-form organization structure, and the privacy and the safety of the data in each cover layer can be protected.
Owner:FUJIAN CENTM INFORMATION
Information recording medium, information recording method, information recording apparatus, information reproduction method, and information reproduction apparatus
InactiveUS20050169603A1Television system detailsElectronic editing digitised analogue information signalsInformation sectorData recording
According to a recording method for a conventional rewritable disc, the latest data is recorded by rewriting data in an identical area. In the case of a disc of which the number of times of data rewrite is limited, this causes a problem that a defect block is easily generated. The present invention has an objective of providing an information recording medium, an information recording and reproduction method, and an information recording and reproduction system apparatus, by which data is recorded sequentially from an unallocated area after an entry sector number, and data recording is sequentially repeated from an inner portion to an outer portion.
Owner:PANASONIC CORP
Process and arrangement for writing binary data onto glass masters
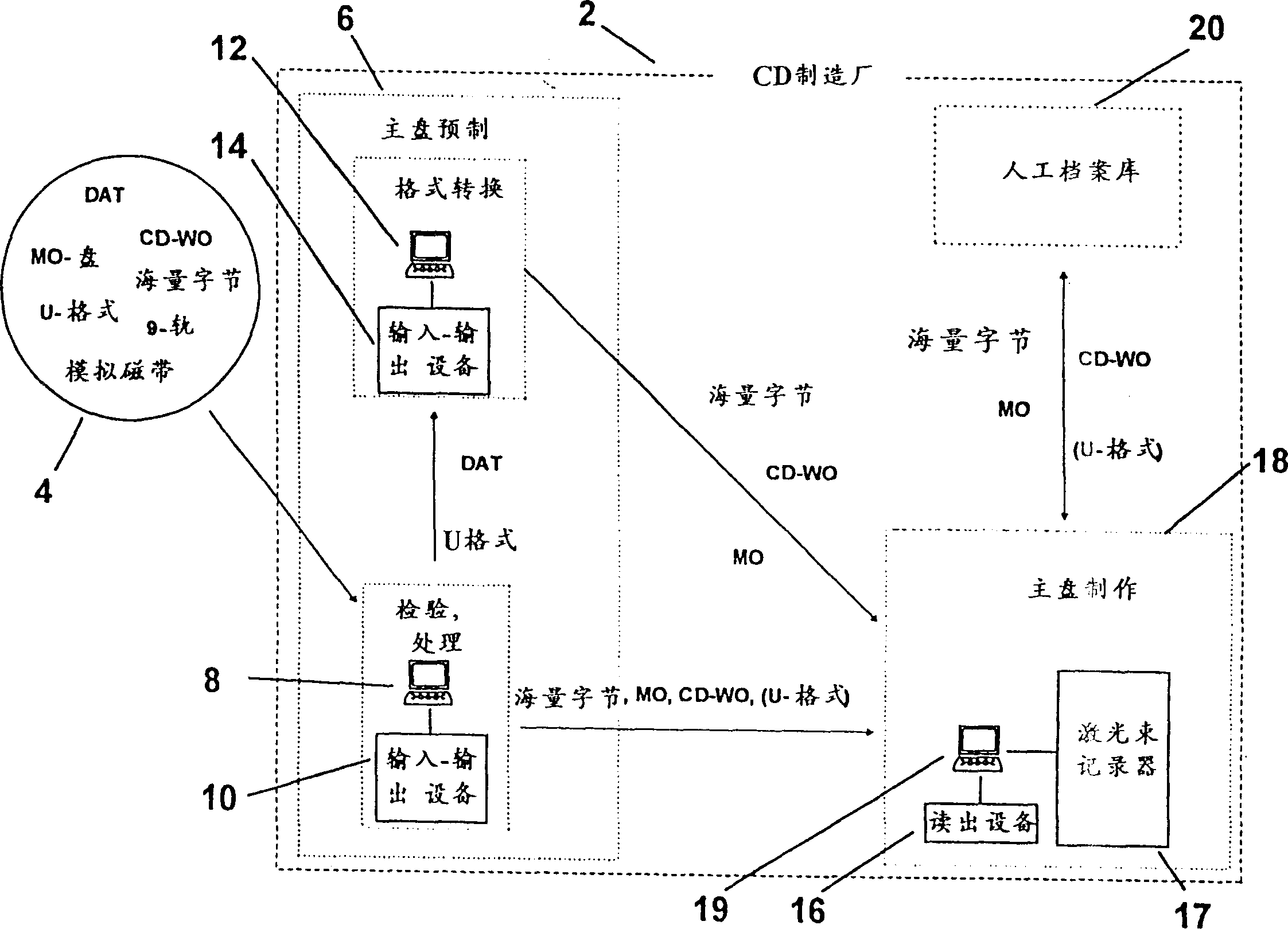
InactiveCN1099113CHigh speedImprove stabilityRecord information storageWrite-once discsMass storageData stream
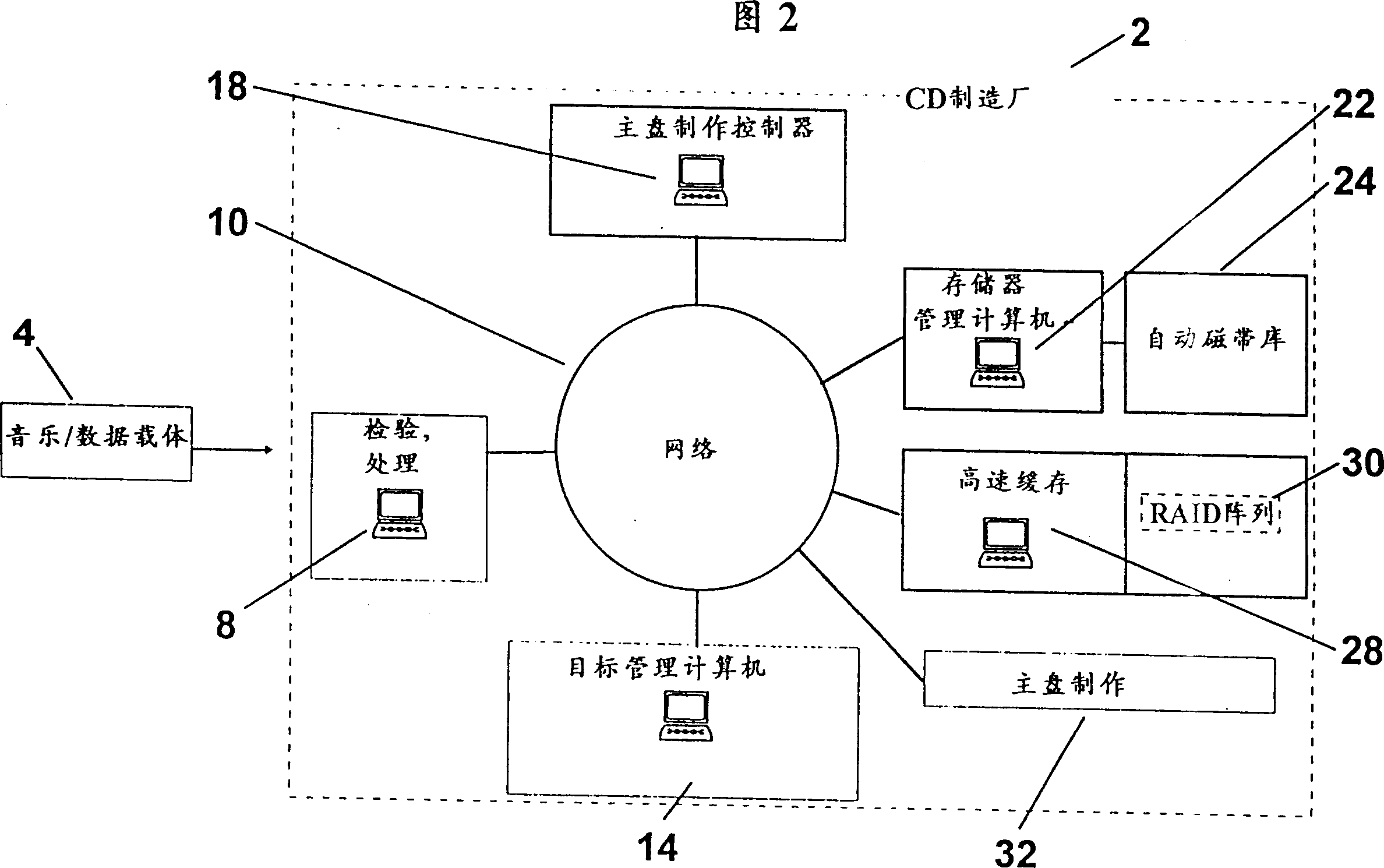
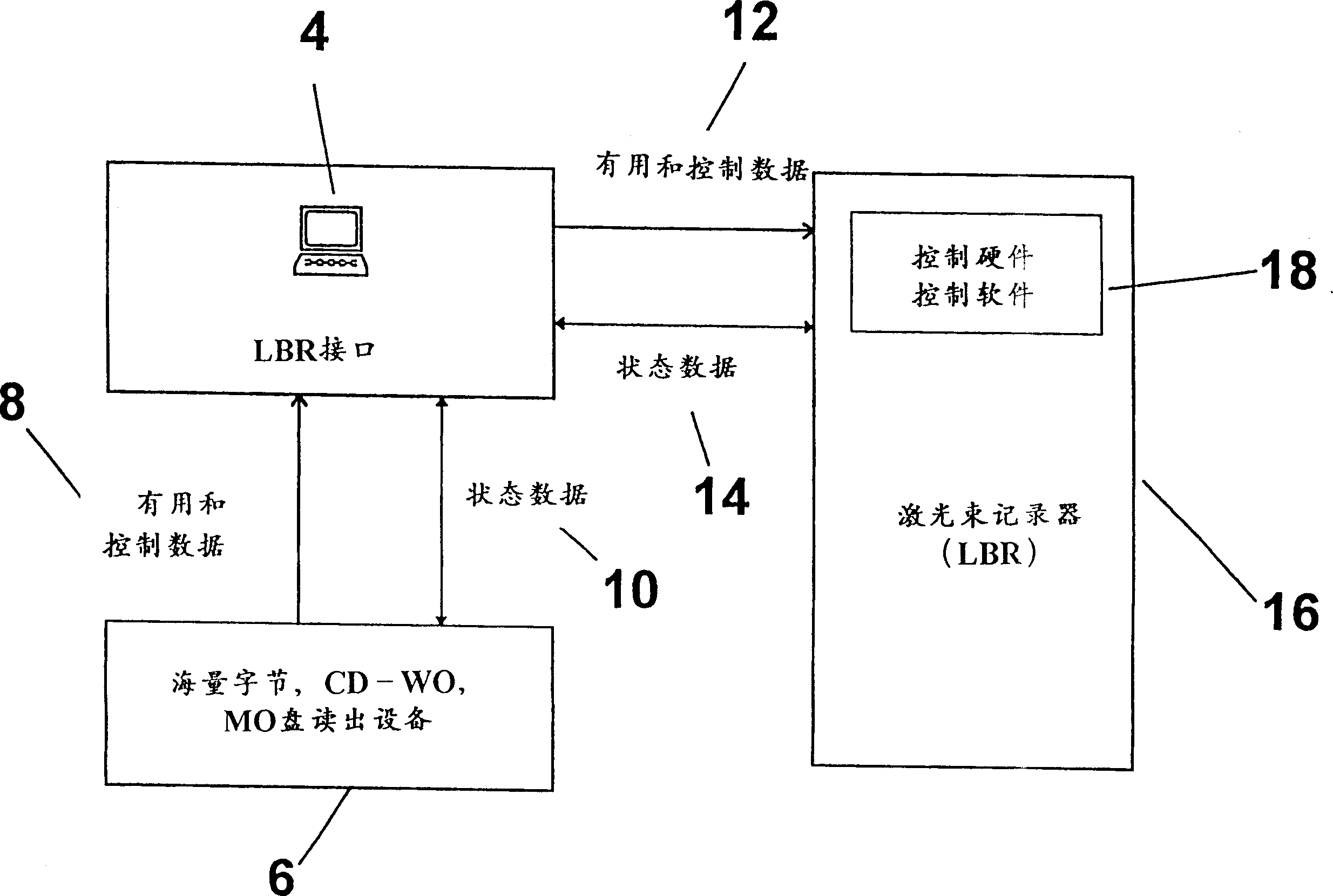
A system concept and the components integrated therein for storing useful and control information as well as feature items, general components for data flow control of all components integrated in the system concept as well as special components for data flow and process control of interface systems for laser-beam recorders permit handling of useful and control information as well as feature items independently of physical music / data carriers within premastering and the production of glass masters (mastering) in CD plants. All the various types of information are stored in on-line compatible mass storages and automatically transferred into the sectors calling for the information concerned by general data flow control components. Requests for information can be generated manually or automatically. The time needed to transfer to the requesting sectors or machines is shortened, the premastering expense reduced, the mastering actions automated with the aid of special control components and considerably speeded up as compared to conventional methods by using a network as the carrier medium.
Owner:索诺普莱斯声音和信息载体制品有限公司
Method to protect data on a disk drive from uncorrectable media errors
ActiveUS8645622B2Effective protectionMemory loss protectionRedundant data error correctionRAIDBase code
Owner:INT BUSINESS MASCH CORP
Method for establishing error encoding scheme and equipment for reducing data loss
InactiveCN1959648BReduce lossesForward error control useRedundant data error correctionData setData information
Owner:GLOBALFOUNDRIES INC
Data processing system based on monitoring information
InactiveCN114298697AAccurate judgmentImprove approval efficiencyOffice automationData processing systemUser needs
Owner:XIEHE HOSPITAL ATTACHED TO TONGJI MEDICAL COLLEGE HUAZHONG SCI & TECH UNIV
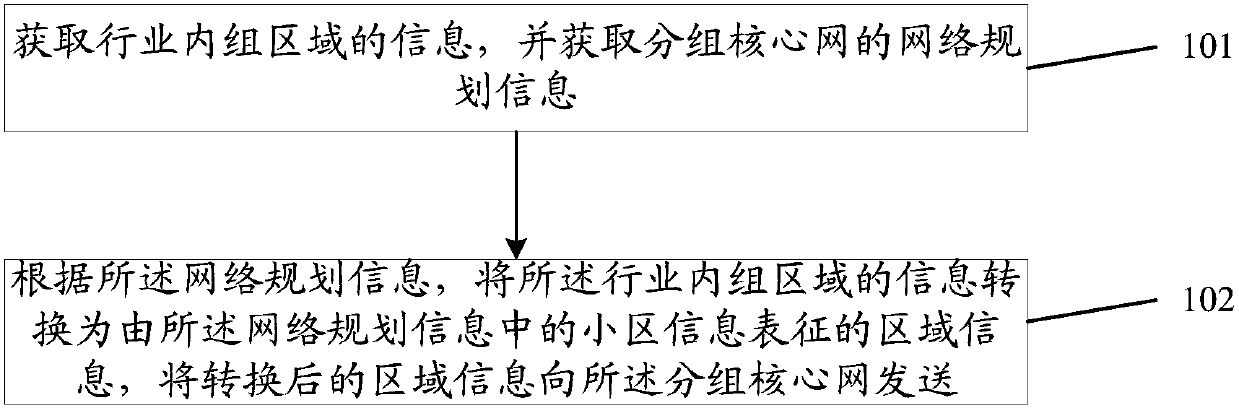
Group region setting method and device and group region updating method and device
InactiveCN107708122ASolve the problem of inconsistent settingsMeet needsNetwork traffic/resource managementNetwork planningInformation sectorComputer science
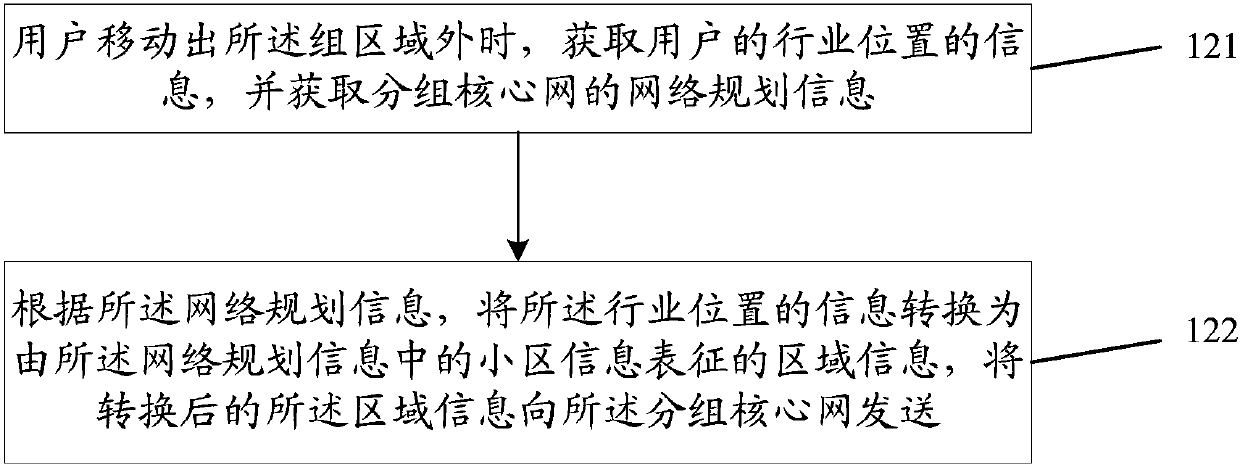
The invention discloses a group region setting method. The group region setting method comprises the following steps: acquiring information of a group region in the industry, and acquiring network planning information of an evolved packet core; and converting the information of the group region in the industry into region information represented by cell information in the network planning information according to the network planning information, and transmitting the converted region information to the evolved packet core. The invention also discloses a group region setting device and a groupregion updating method and device.
Owner:ZTE CORP
Method for solving overdue payment of patent tax fees
InactiveCN101551877ACompressed spaceSolve the problem of overdue paymentData processing applicationsMessaging/mailboxes/announcementsPaymentInformation sector
The invention relates to a method for solving overdue payment of patent tax fees, which is characterized in that a charging party arranges or entrusts other persons and a communication department to arrange a payment preannouncing system by utilizing the existing communication conditions, facilities and equipment to preannounce tax payers, patentees and applicants to pay correlative fees on time, thus the overdue payment cannot be caused because of forgetting the time of paying the fees, heavy losses such as late fees, patent reinstatement fees, even patent failures and the like of the tax payers and patent fee payers are avoided, the charging party can efficiently collect the tax fees on time with full amount of money, a payment scroll network file is established and payment detail automatic preannouncing information is programmed to preannounce the fee payers to pay the correlative fees on time and bring convenience for an information department to expand the operating service space, improve the short message quality, compress the development space of junk short messages and enable mobile phone short messages to play a role in bringing profits for the modern fee payers and the whole society so as to reduce the bad effects of the junk short messages on the society.
Owner:易美春
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com