Patents
Literature
35 results about "Internal ID" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
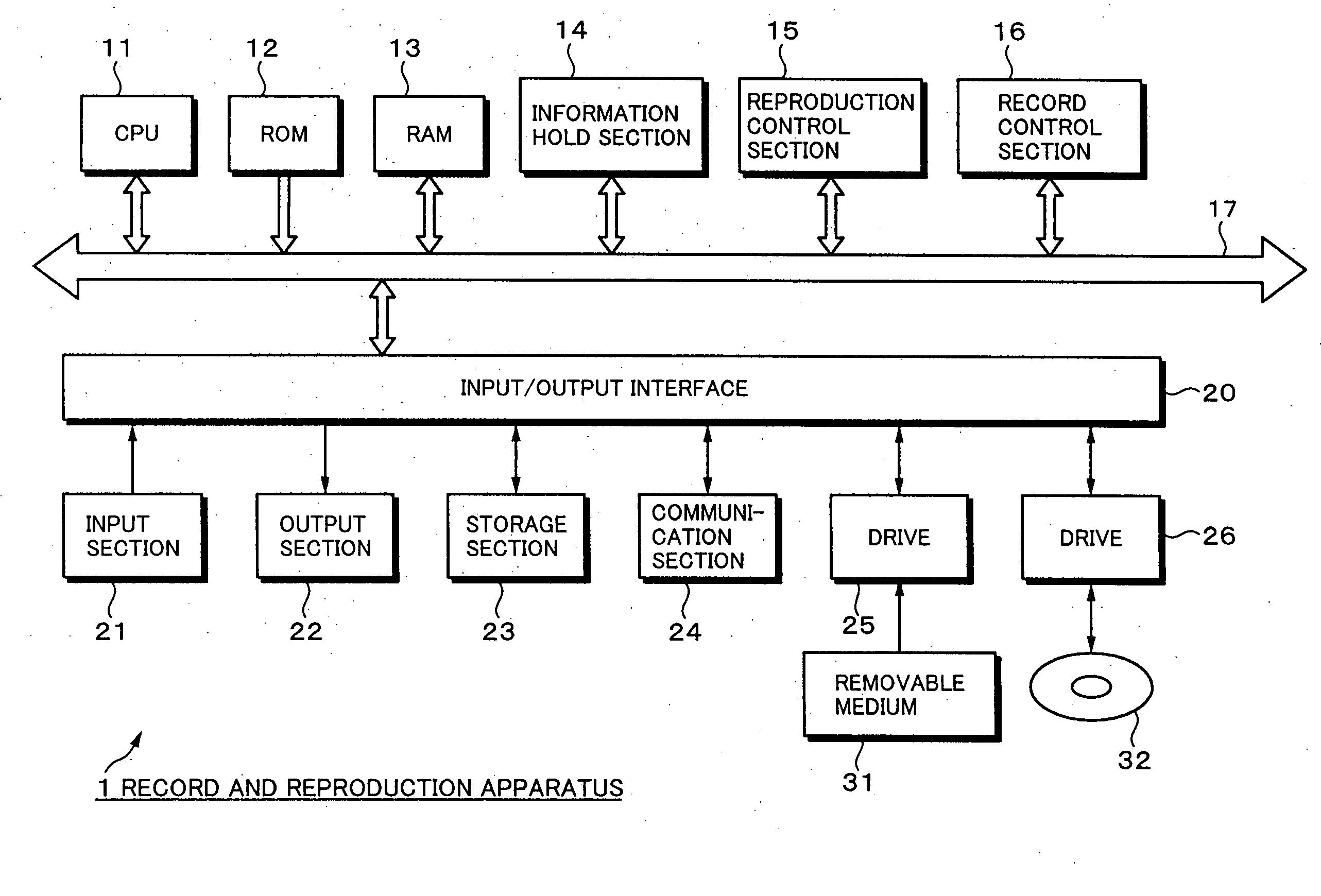
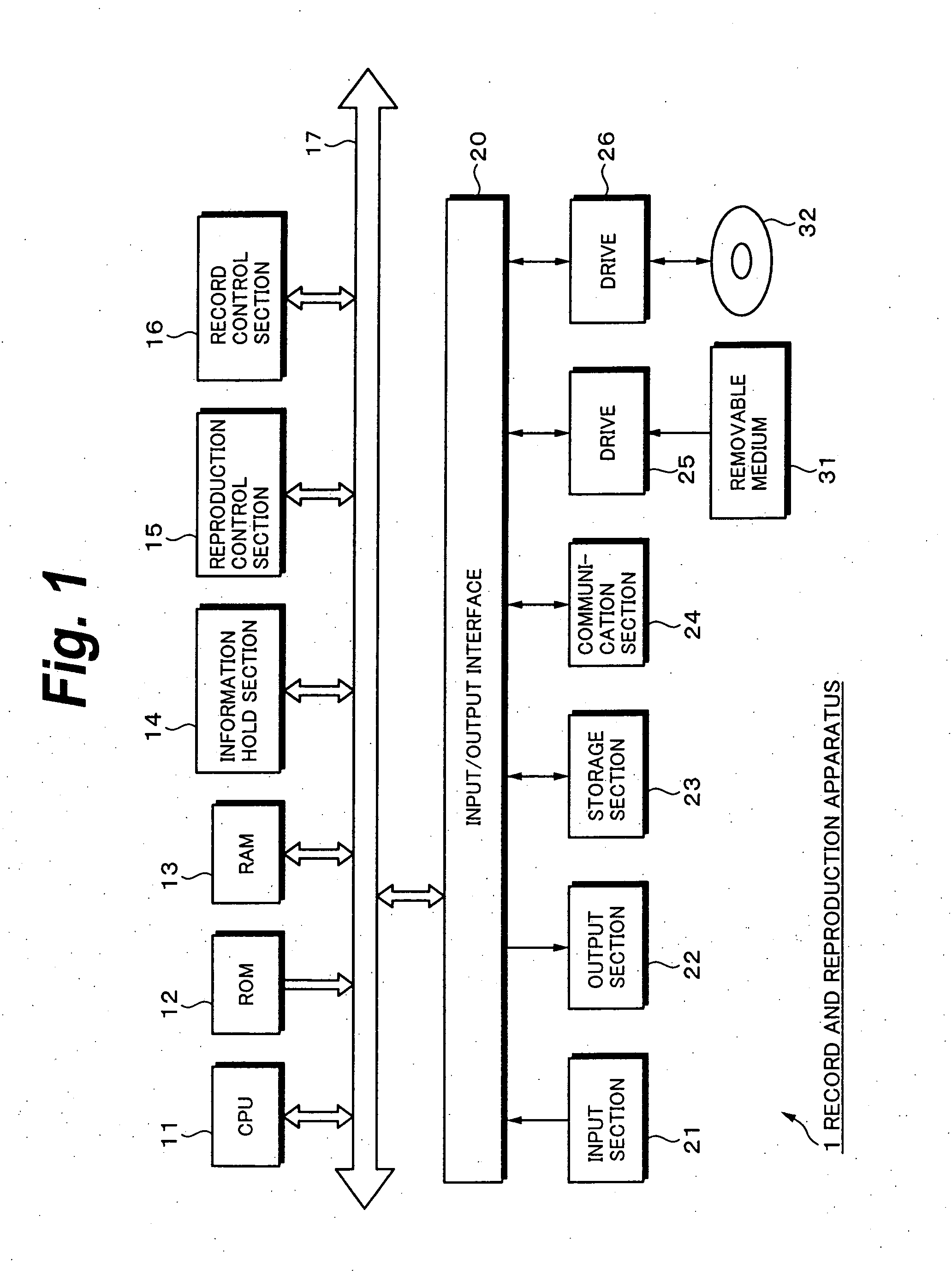
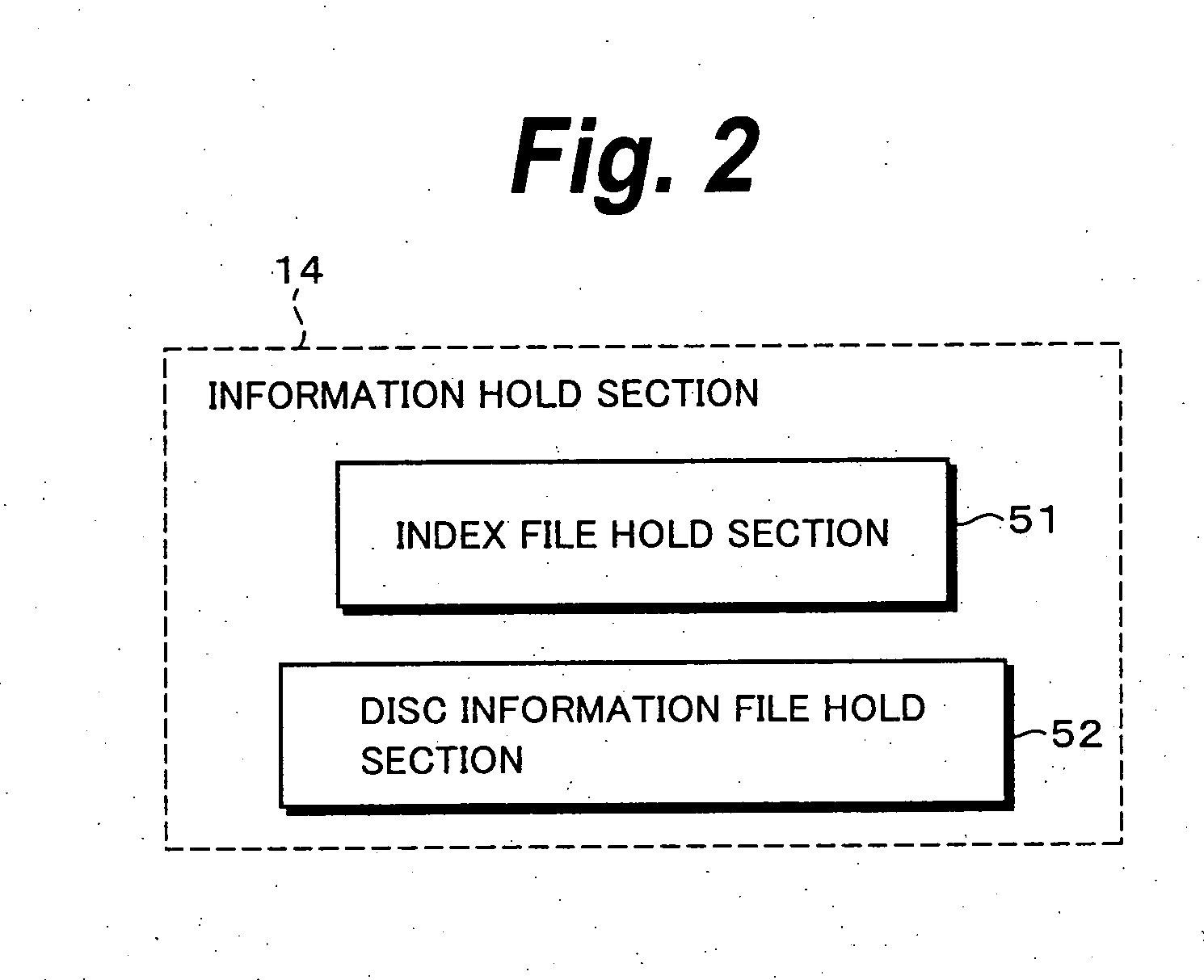
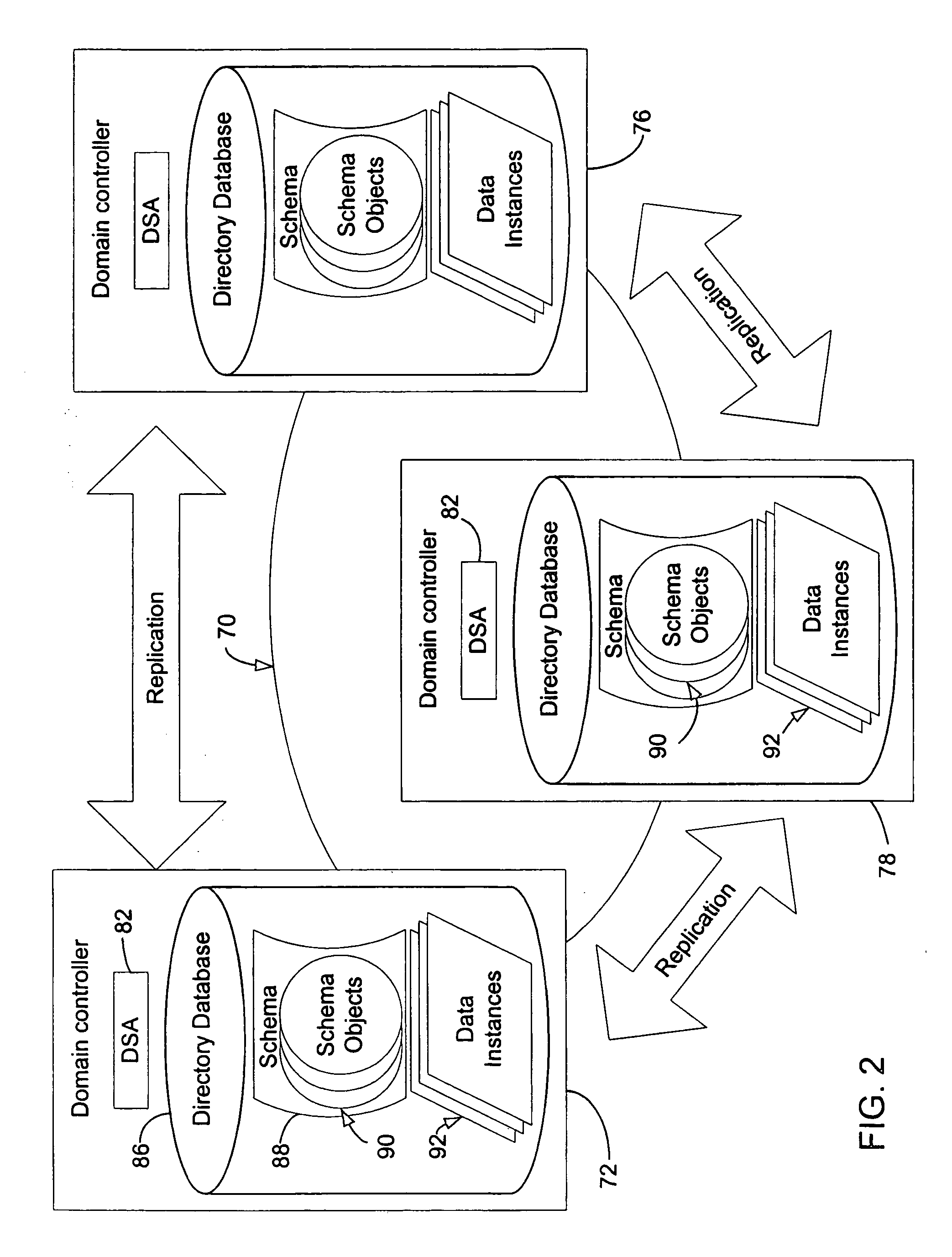
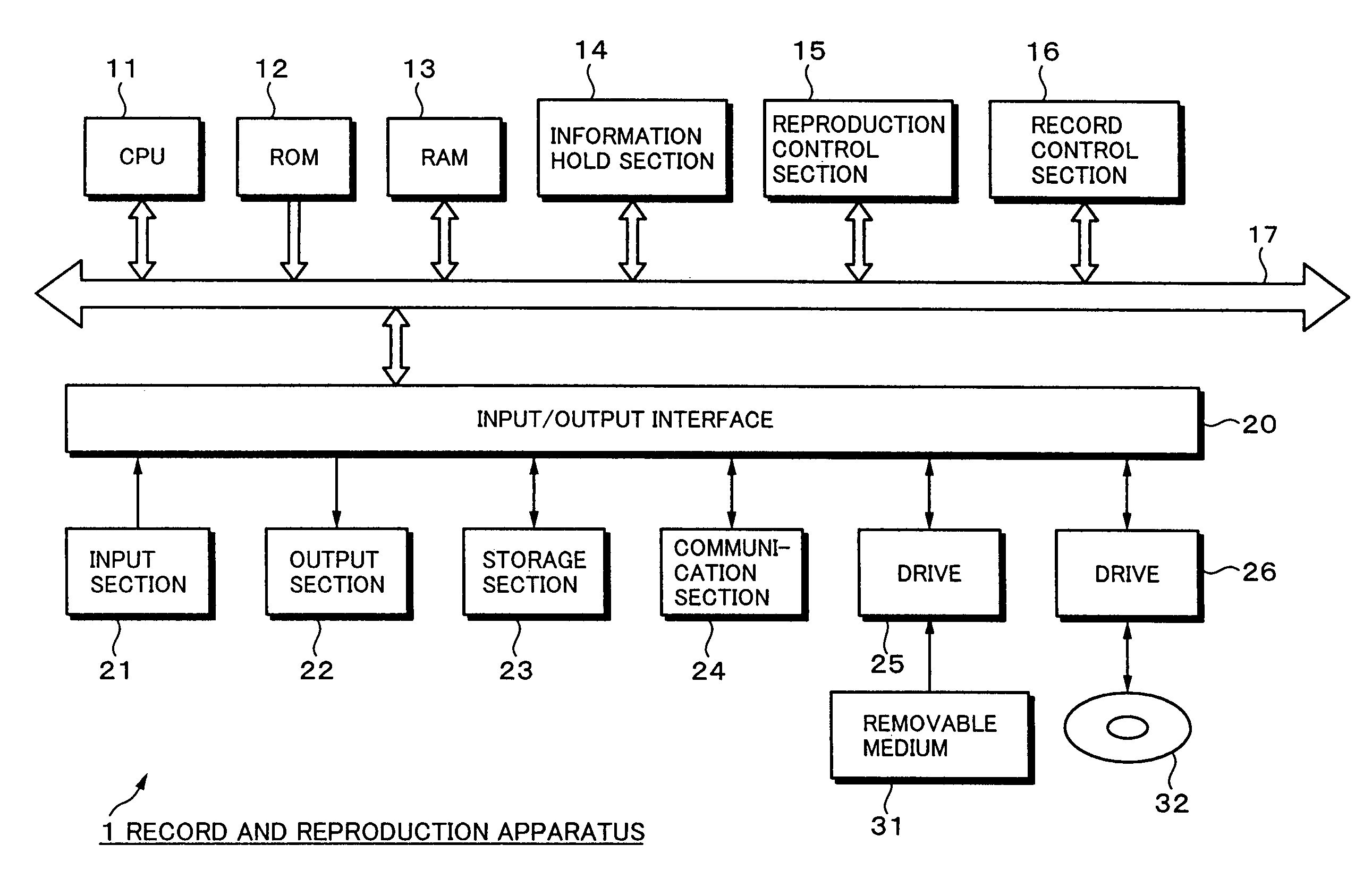
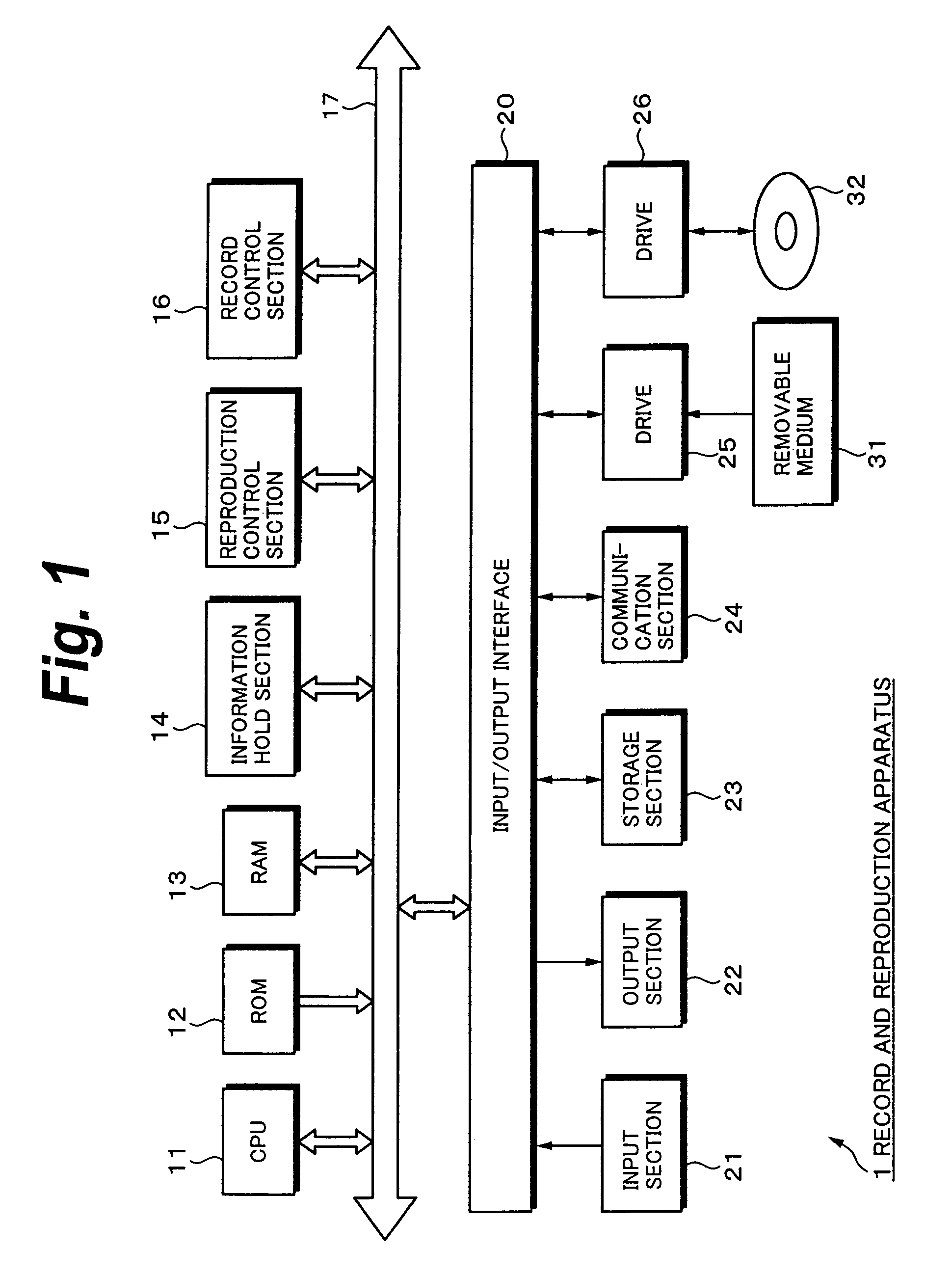
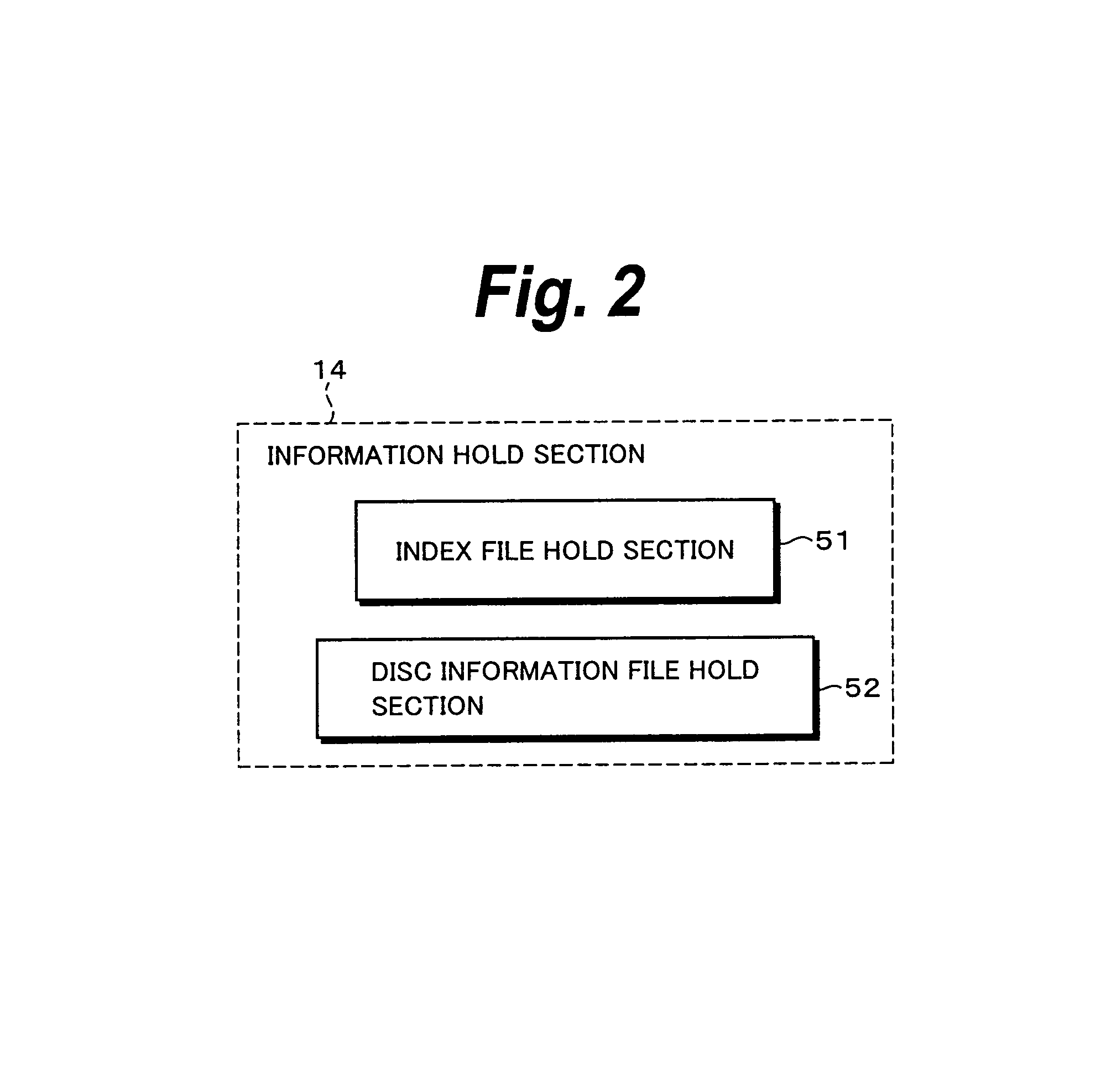
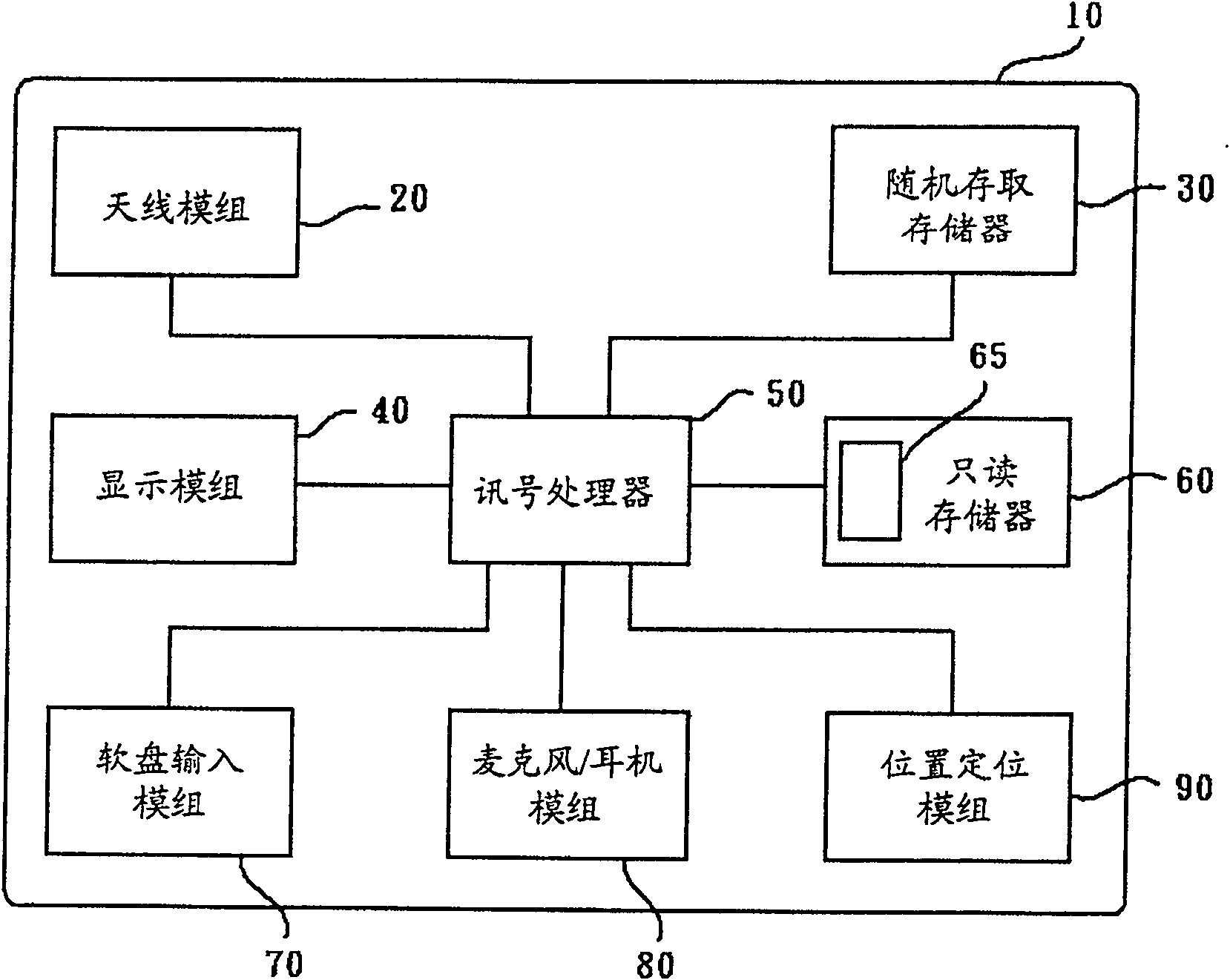
Information Process Apparatus and Method, Program, and Record Medium
InactiveUS20070206920A1Improve convenienceEasy to implementElectronic editing digitised analogue information signalsColor television signals processingCompact discInformation processing
To improve the convenience of a record medium and allow a record process and reproduction process to be more easily performed than before. When a clip edit list update process 121 that updates video data and audio data recorded on a disc 32 is executed, an index file management section 72 manages and updates an index file held in an index file hold section 51 as the video data and audio data are updated. At this point, a search section 92 searches disc internal IDs assigned to clips or edit lists contained in the index file for the maximum value. A disc internal ID generation section 91 generates a disc internal ID according to the maximum value. An index file management section 72 updates the index file with the disc internal ID generated by the disc internal ID generation section 91.
Owner:SONY CORP +1
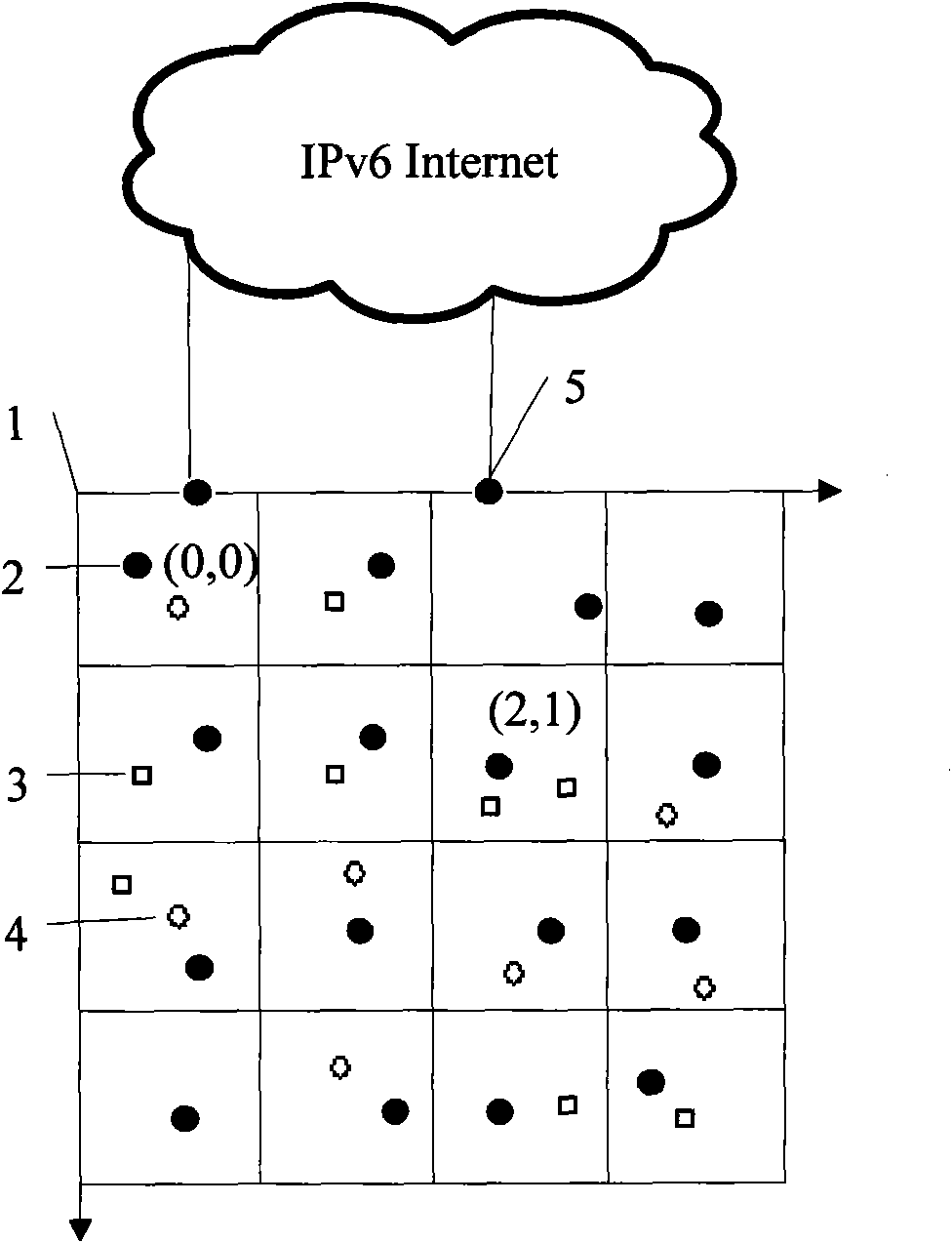
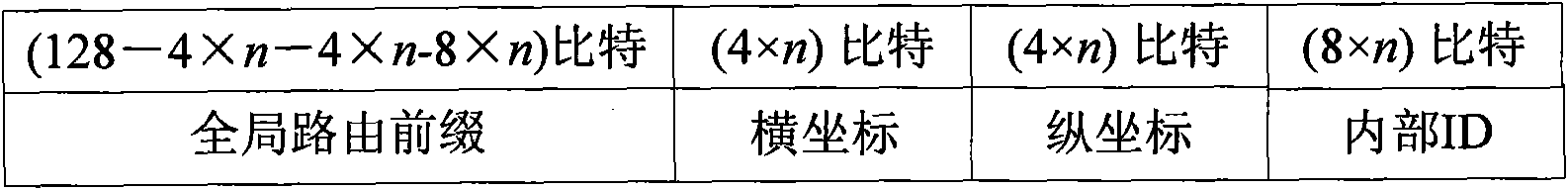
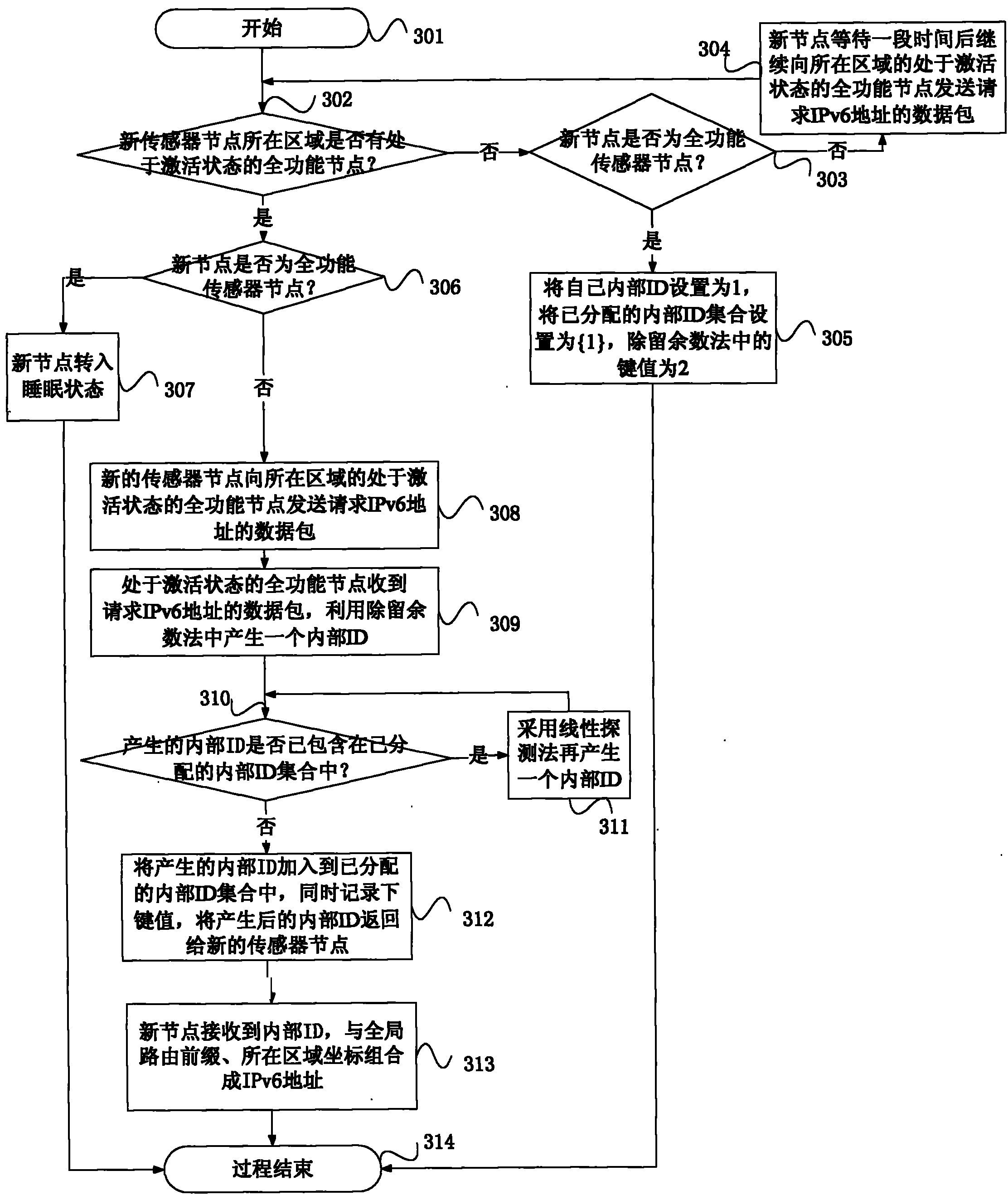
IPv6 address configuration method of wireless sensor network based on geographical position
InactiveCN101867919AReduce volumeLow priceNetwork topologiesWireless network protocolsLine sensorMobile wireless sensor network
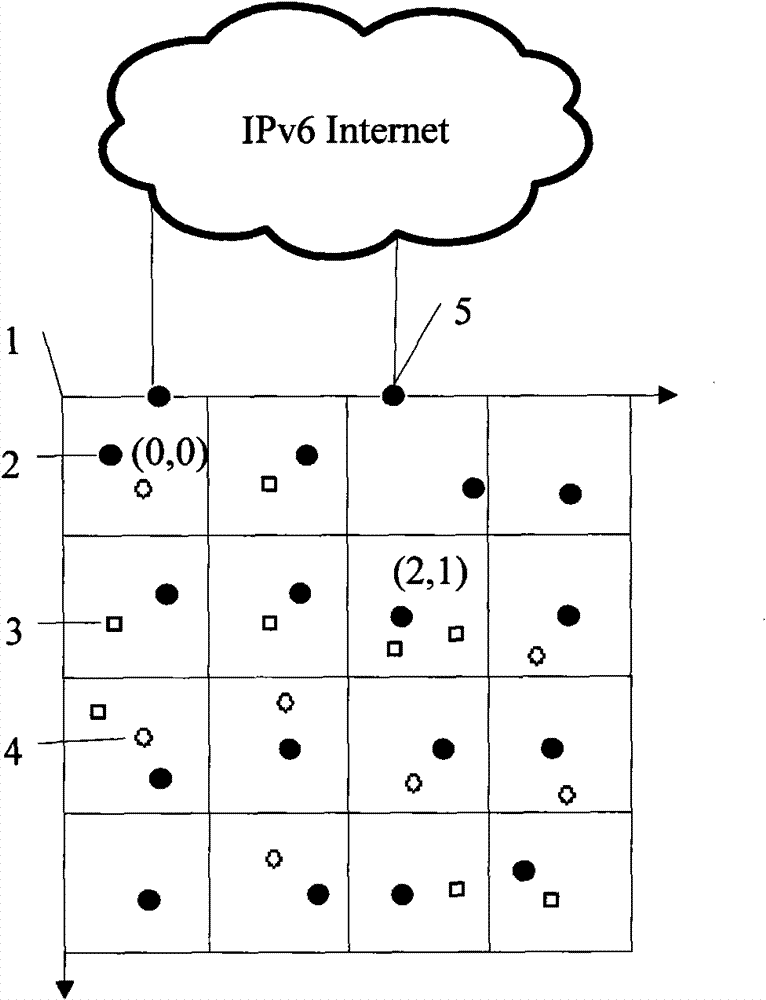
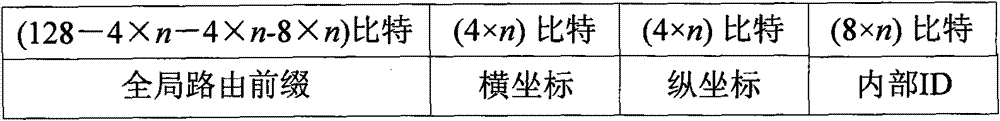
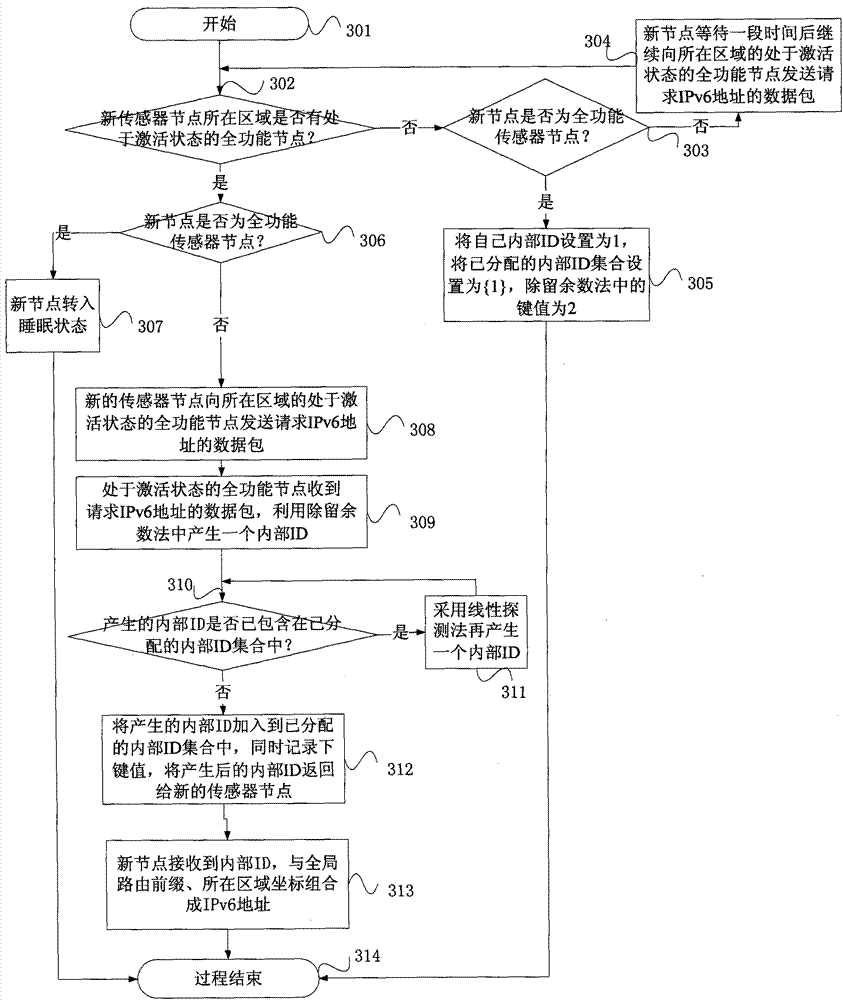
The invention provides an IPv6 address configuration method of a wireless sensor network based on a geographical position. The wireless sensor network comprises full-function sensor nodes and partial-function sensor nodes; a wireless sensor network area is divided into multiple squares with identical areas, and each square is identified by coordinates; if the multiple full-function sensor nodes are contained in one square region, then only one full-function sensor node in activated state exists at the same time; in one square region, all the sensor nodes can realize one-hop communication; access nodes used for connecting the wireless sensor network and an IPv6 network are full-function sensor nodes; at most one access node is contained in one square region; and the full-function sensor nodes in the activated state adopt the stateful address distribution scheme that the partial-function sensor nodes in the square area distribute internal ID addresses in a unified way, and adopt the division method and linear detection method to produce internal ID addresses.
Owner:JIANGSU JUNZHI SENSING TECH
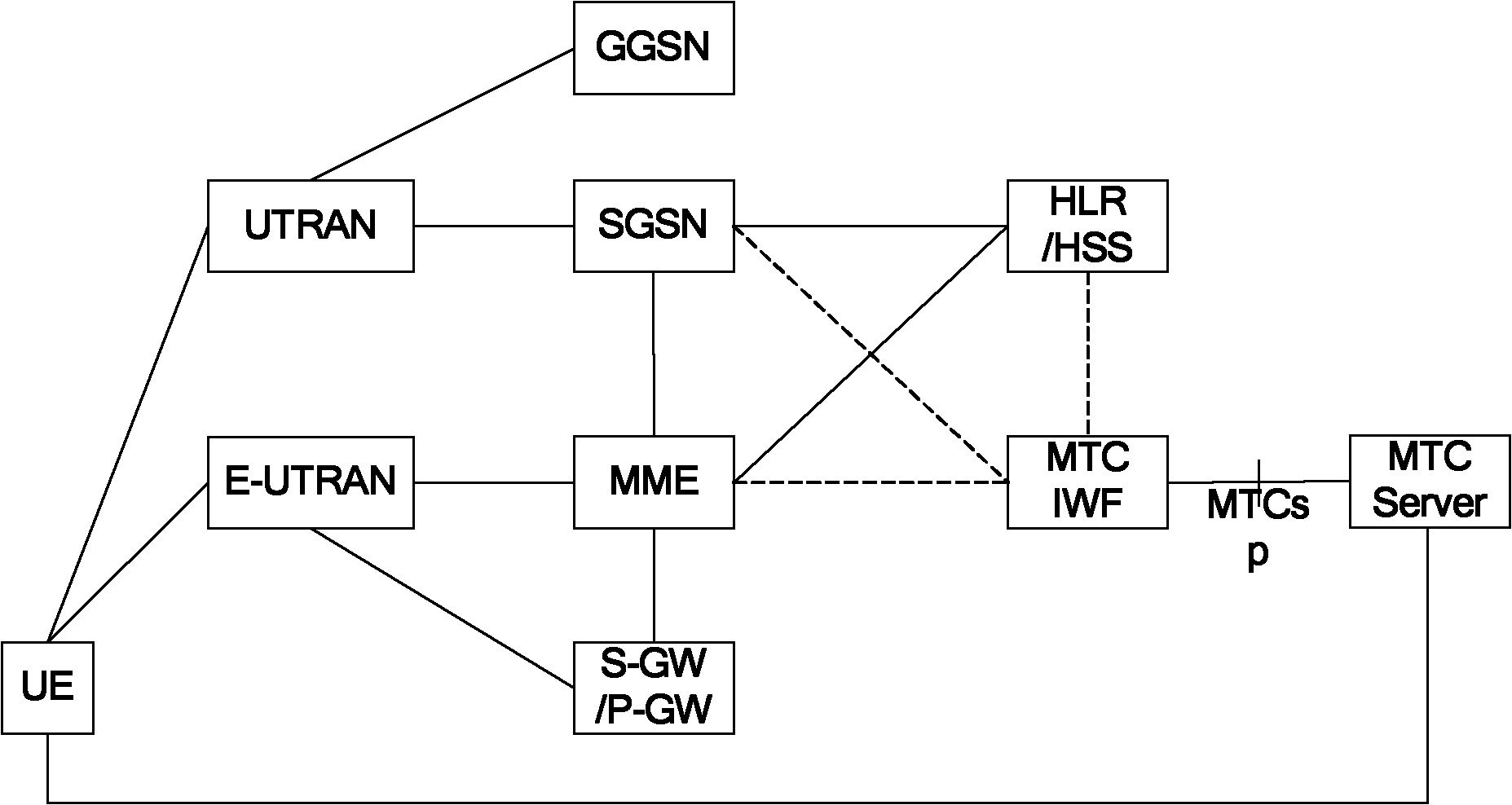
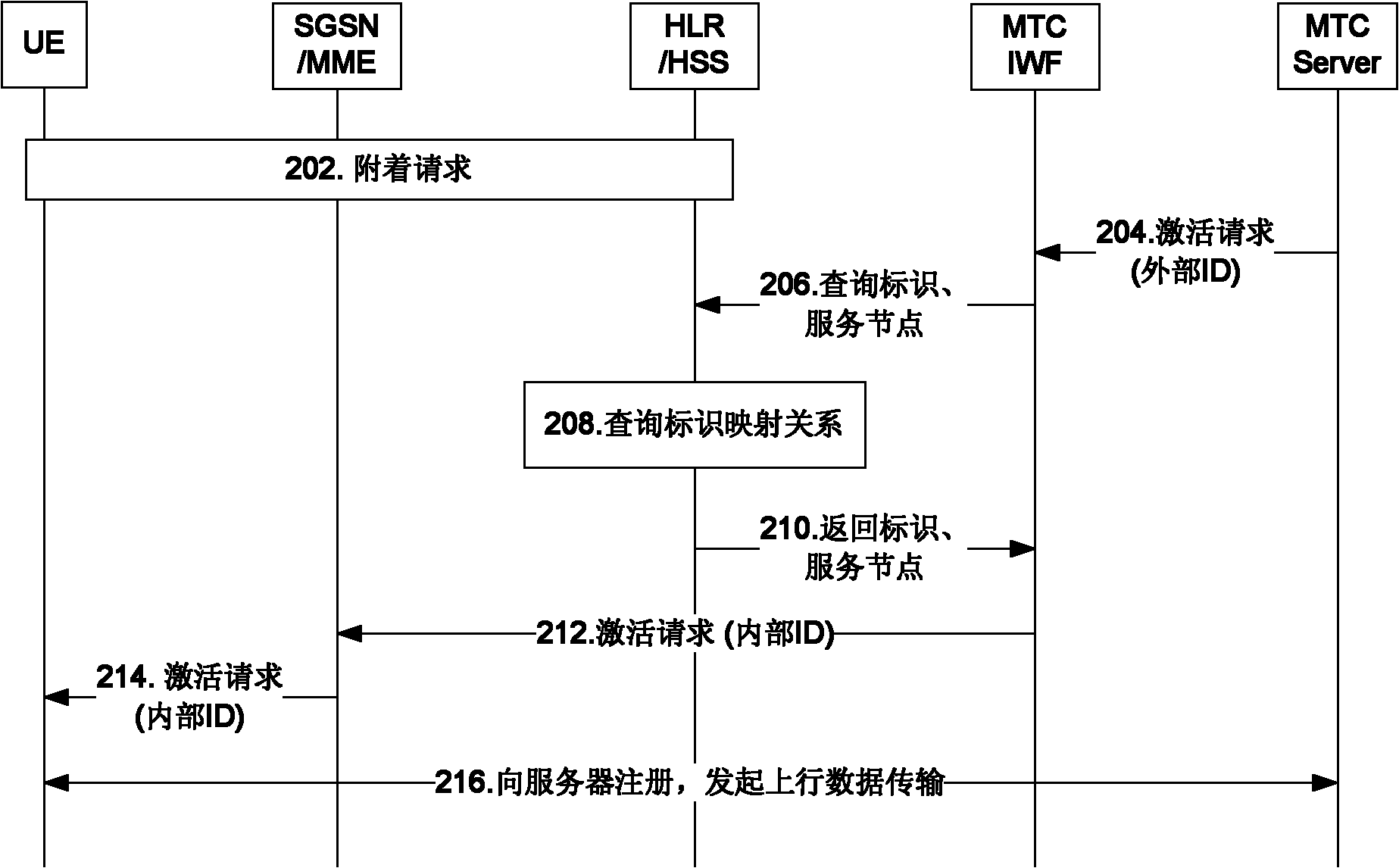
Mapping method, device and system for terminal identifications
ActiveCN102857908AAvoid couplingIncrease flexibilityNetwork data managementProtocol ApplicationComputer science
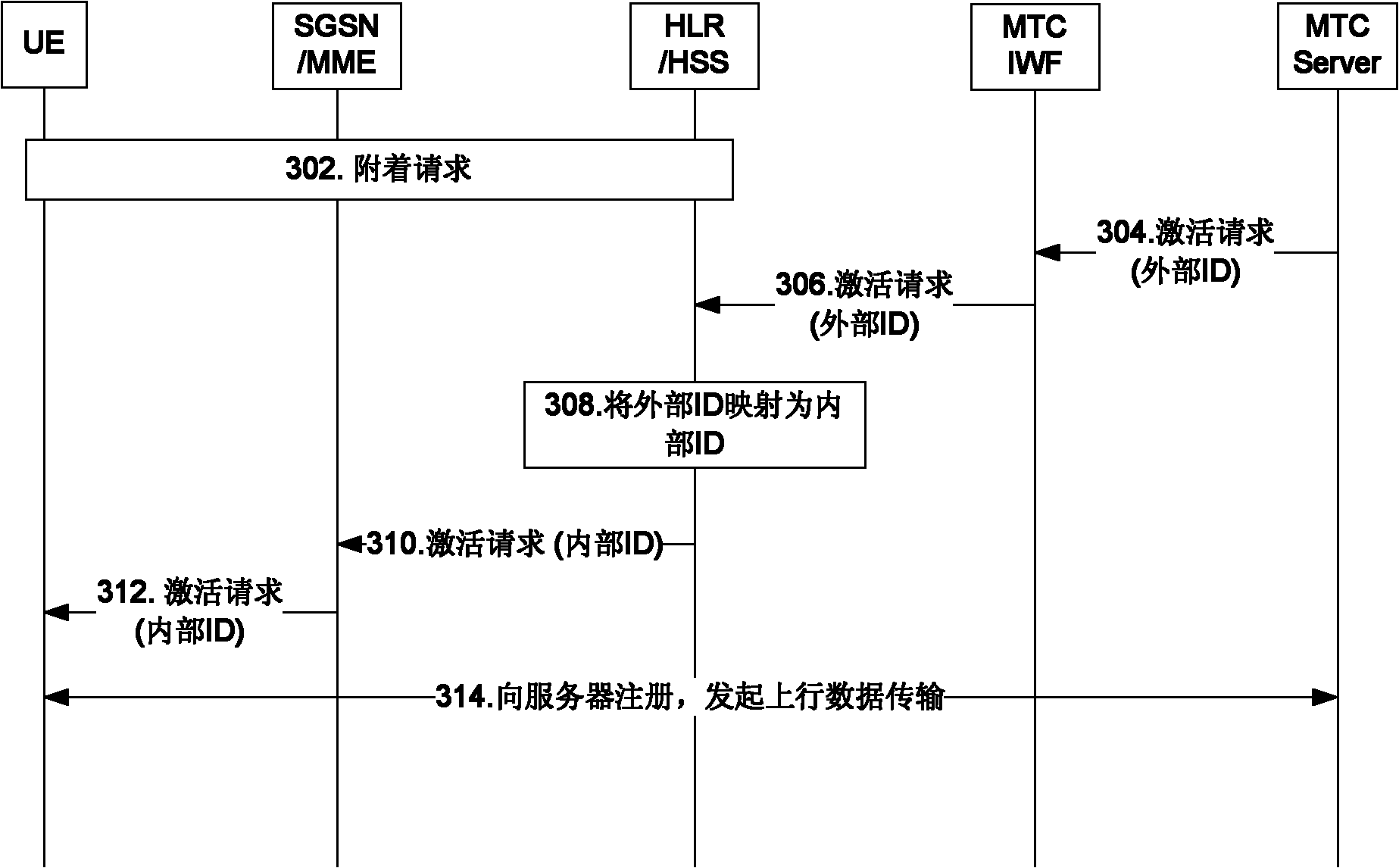
The invention discloses a mapping method, a device and a system for terminal identifications. The mapping method includes that a machine type communication interworking function (MTC IWF) stores a mapping relation between an internal identification (ID) and an external ID of user equipment (UE); and the MTC IWF completes conversion from the external ID to the internal ID of the UE according to the mapping relation while receiving information sent to the UE. By using the mapping method, the device and the system, the mapping relation of the internal ID and the external ID of the UE can be stored in the MTC IWF rather than in a home location register / home subscriber server (HLR / HSS), when the external ID of the UE is needed to change on the application layer out of certain purposes, the HLR / HSS is not needed to be informed to change signing data, therefore the external ID of the UE is prevented from being closely coupled on the internal ID of the UE, and control flexibility of the application layer on the external ID of the UE is improved.
Owner:ZTE CORP
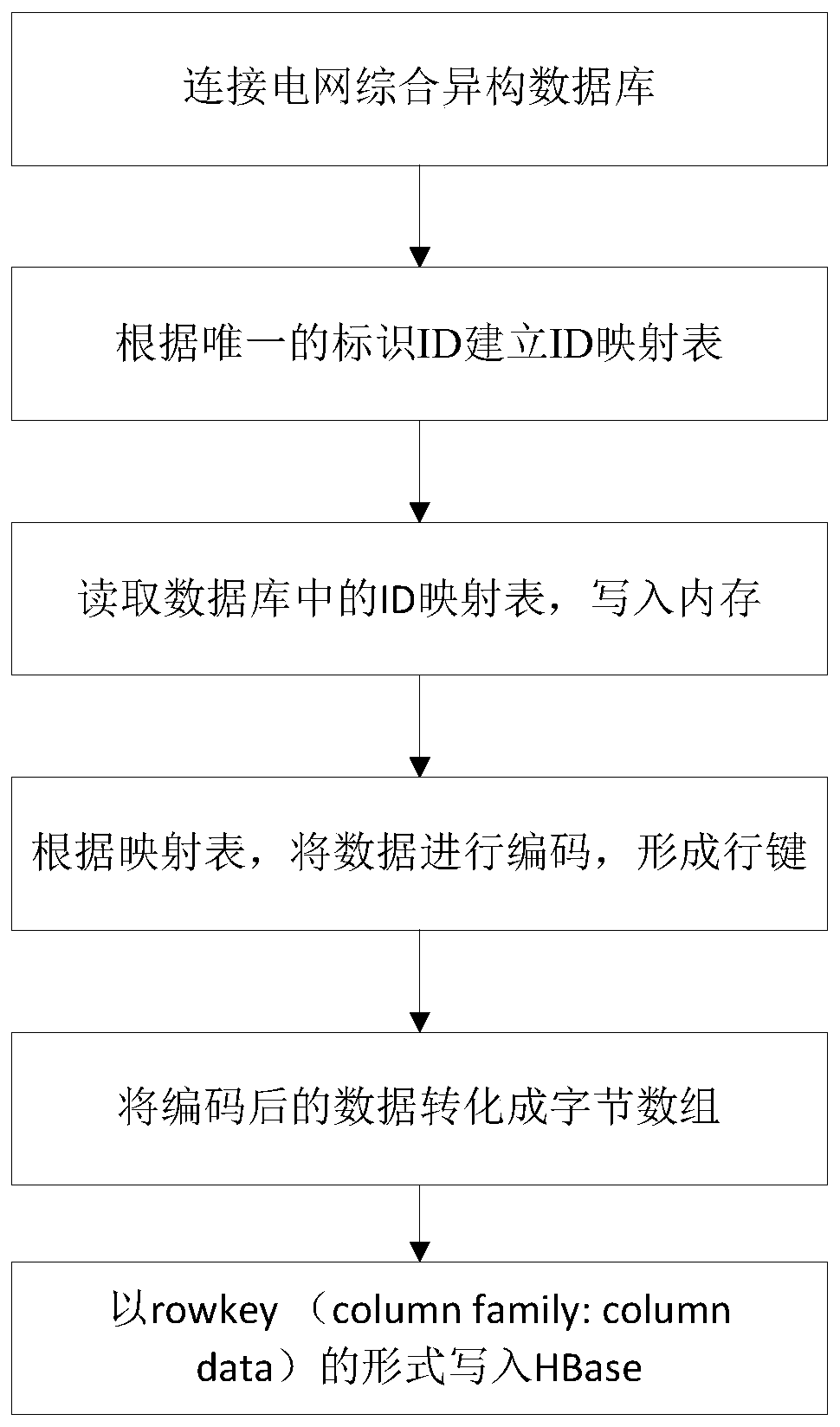
Method and system for rapidly transferring multi-source heterogeneous power grid big data to HBase
ActiveCN106528786AReduce overheadMulti-transportDatabase distribution/replicationRelational databasesArray data structureData platform
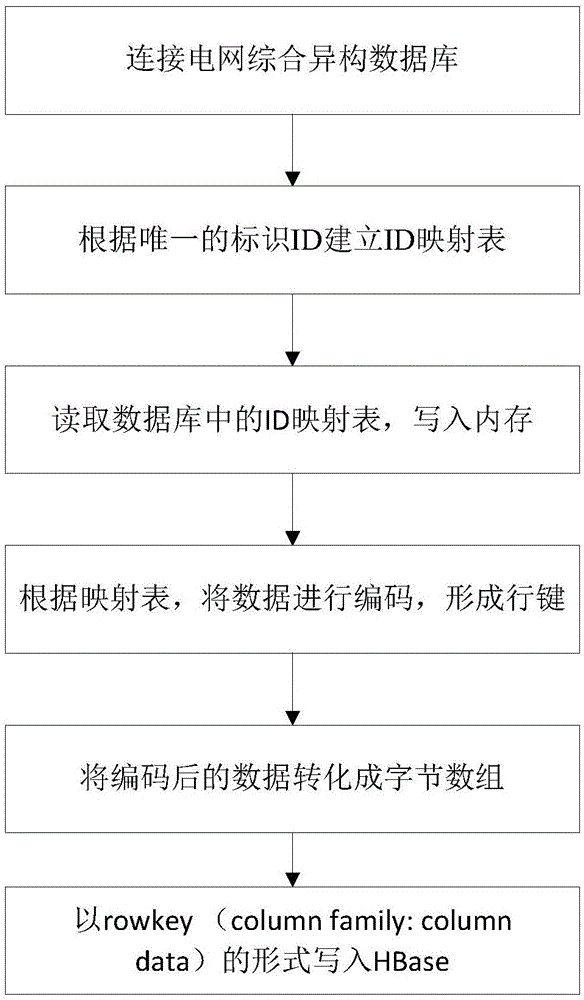
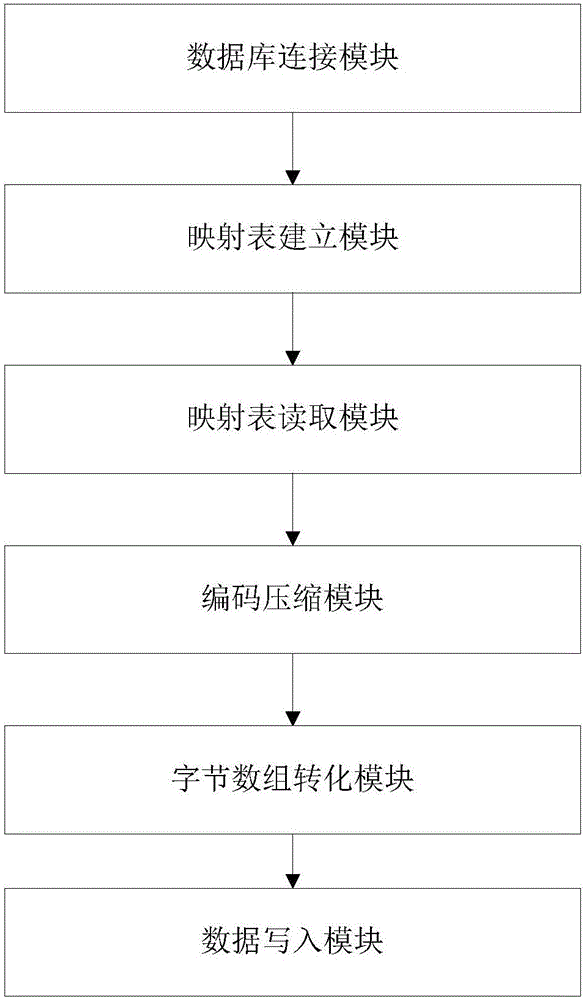
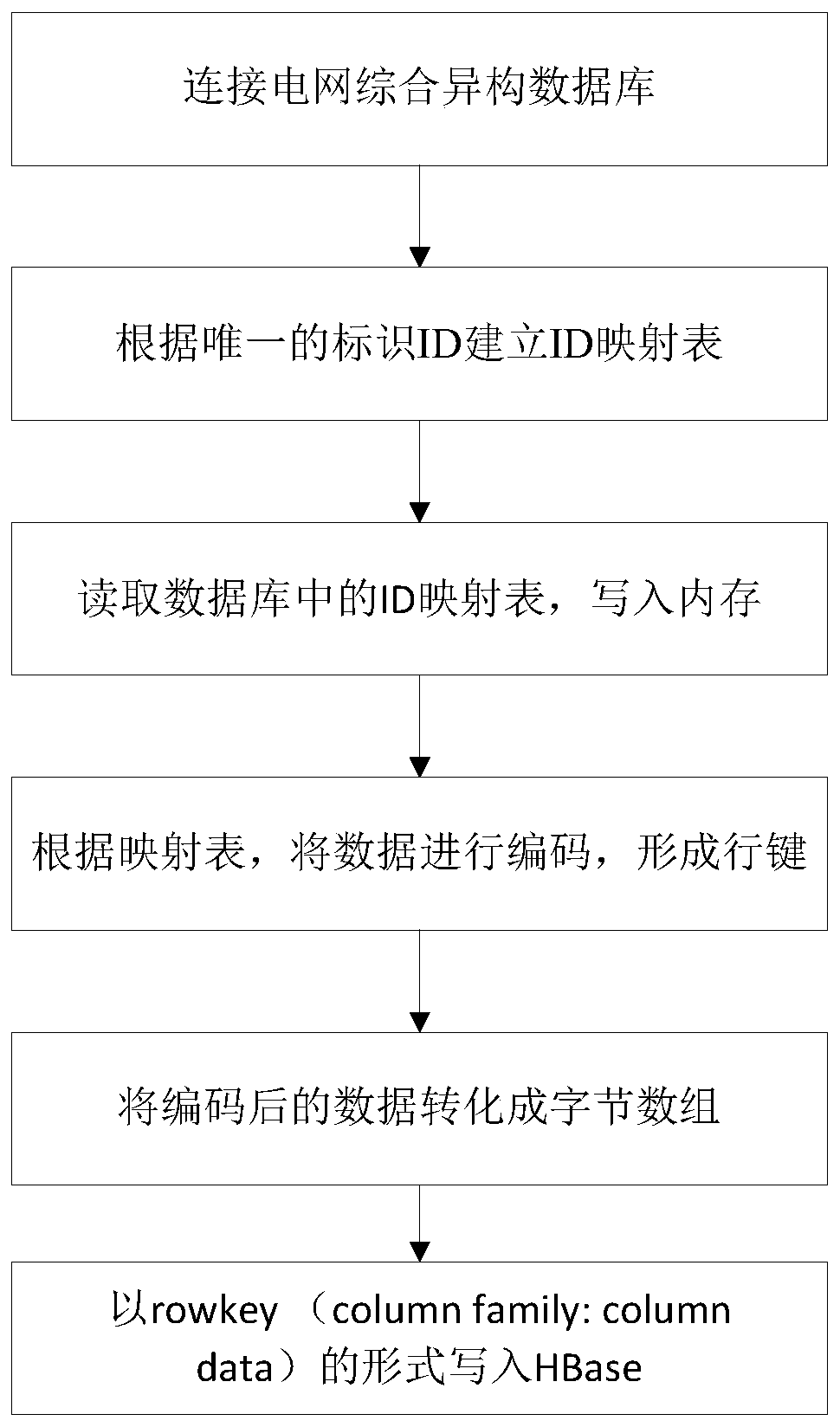
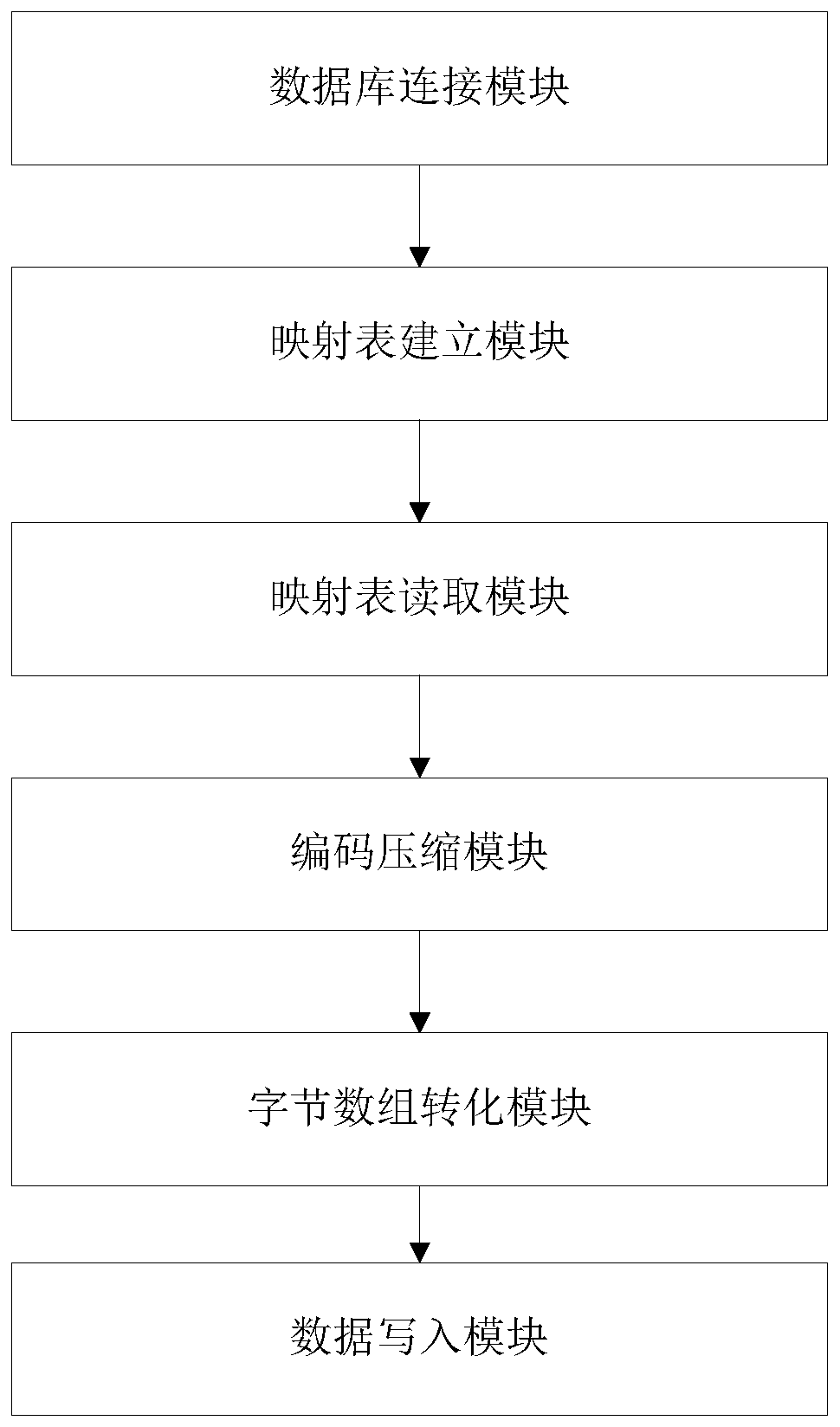
The invention discloses a method and system for rapidly transferring multi-source heterogeneous power grid big data to HBase. The method includes the following steps that a power grid database is connected with an HBase data platform; each datum in the power grid database has a unique mark ID and is composed of the mark ID and data content; according to unique mark IDs, an ID mapping table is established; after a data source is selected, the ID mapping table is read and written into a memory for residence; codes in the ID mapping table are each compressed, so that data class ID row keys and data class internal ID row keys are formed; the data class ID row keys and the data class internal ID row keys are converted into a byte array; the data class ID row keys, the data class internal ID row keys and the row name qualifier of HBase are written into an HBase table in a byte form. Rapid transferring is achieved for a complex electric power data format through the method and system.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +2
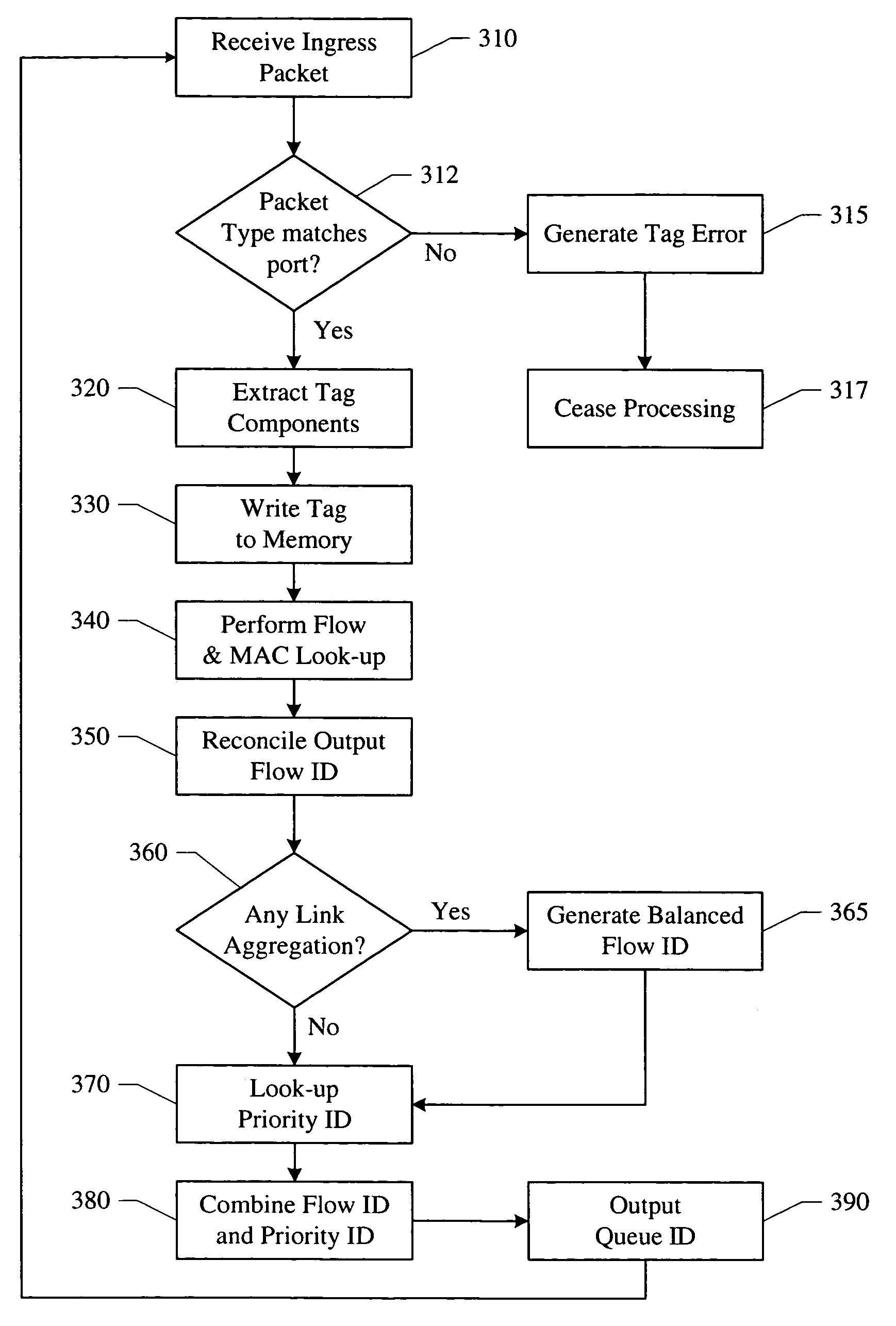
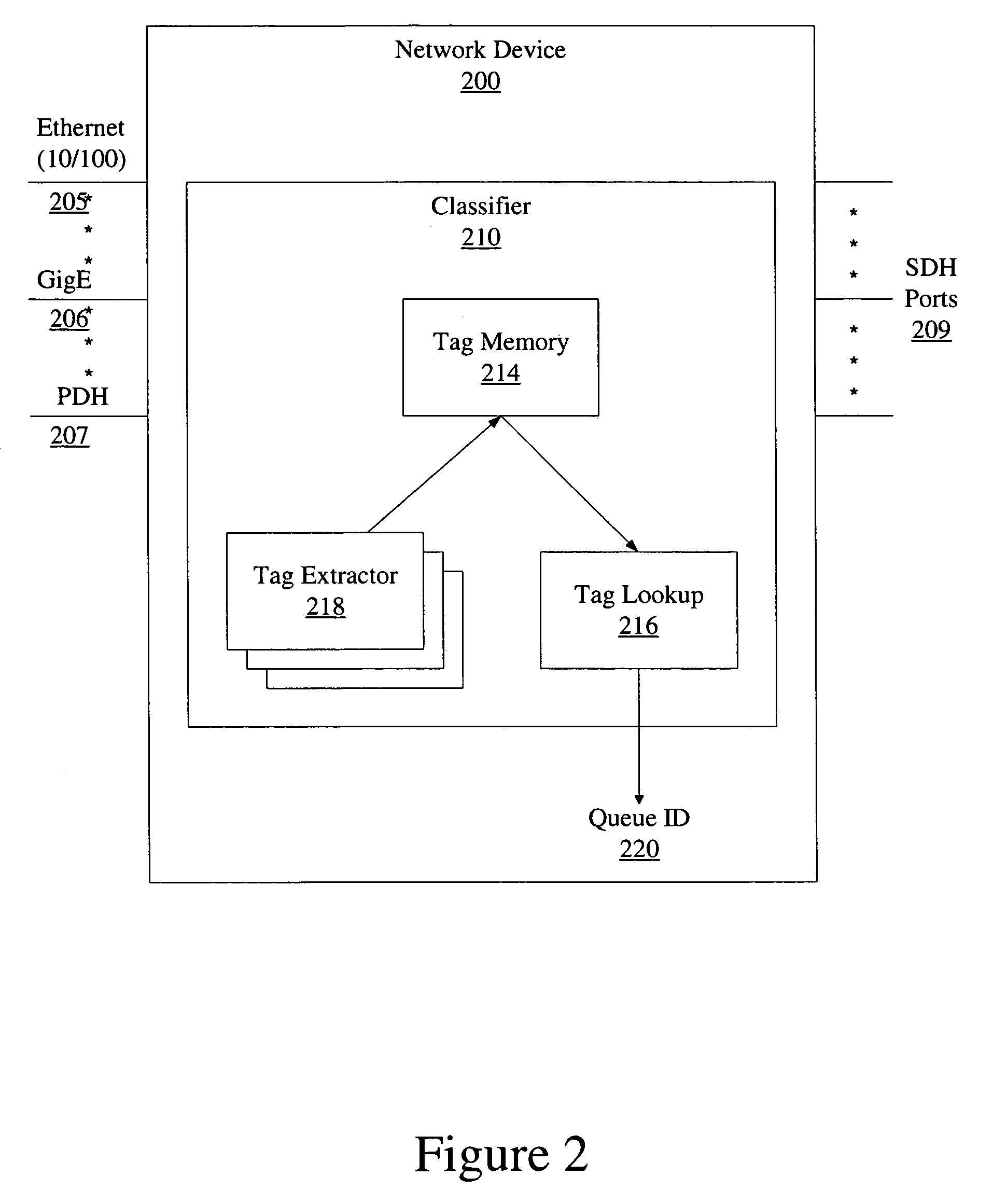
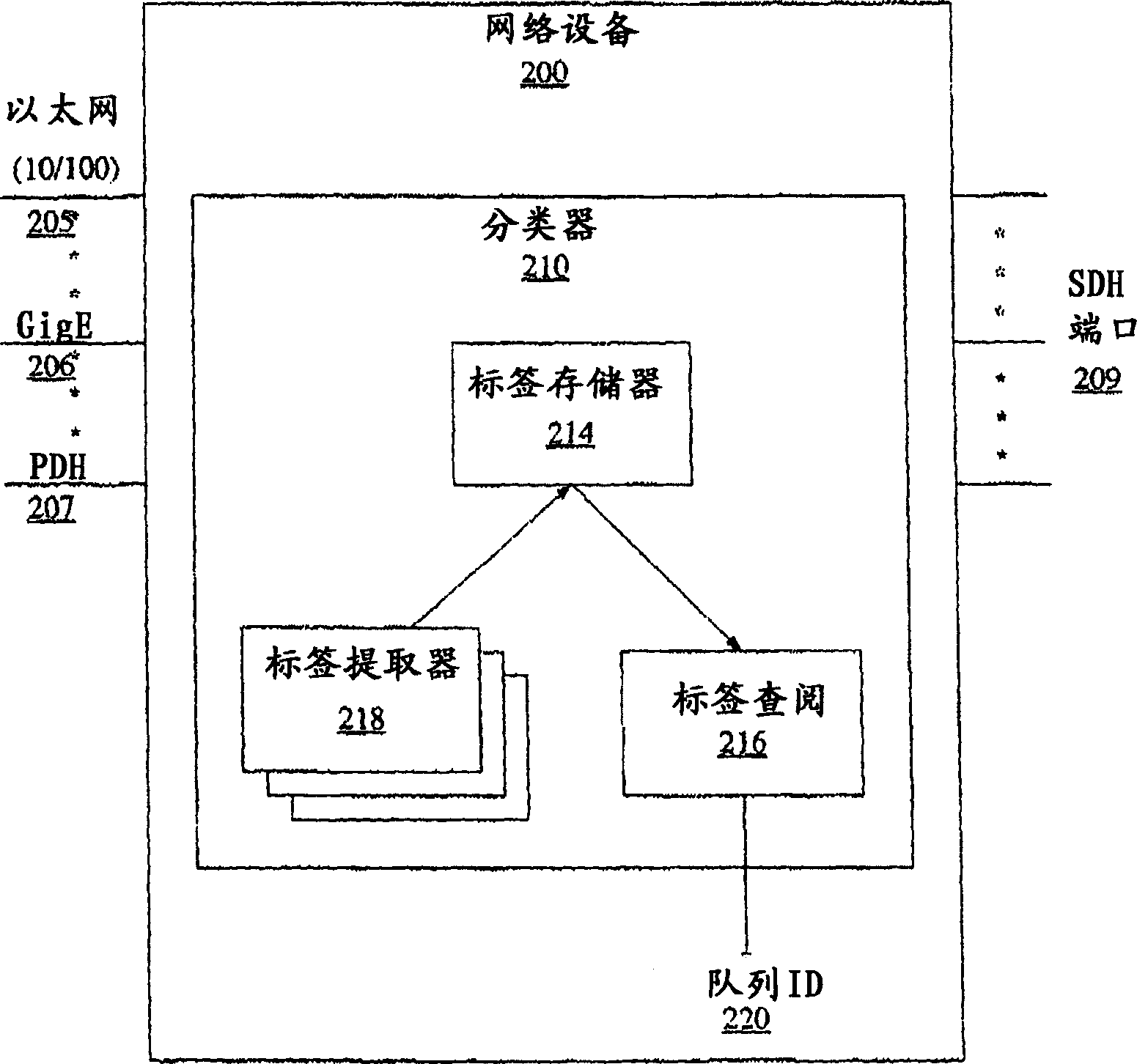
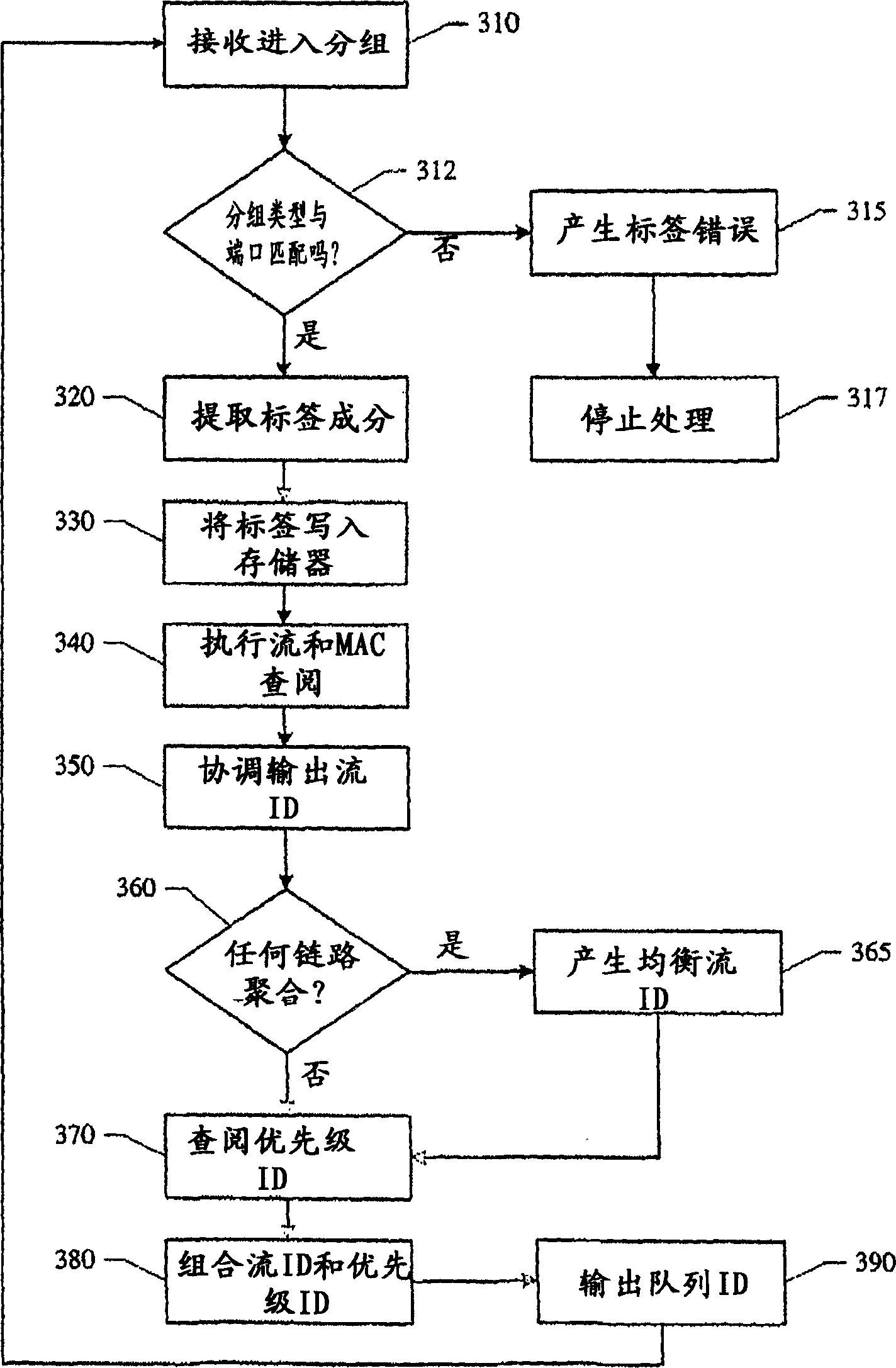
Method and device for the classification and redirection of data packets in a heterogeneous network
InactiveUS7447204B2Data switching by path configurationElectric digital data processingHeterogeneous networkDistributed computing
A system and method for classification of data units in a network device acts as a bridge in heterogeneous networks, provides many different services and provisions many different transport mechanisms. The data classifier generates an ID that is internally used by the network device in managing, queuing, processing, scheduling and routing to egress the data unit. This internal ID enables the device to accept any type of data units from any physical / logical ports or channels and output those data units on any physical / logical ports or channels that are available. The device utilizes learning on a per-flow basis and can enable the device to identify and process data units used in private line services and private LAN services.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Method and device for the classification and redirection of data packets in a heterogeneous network
InactiveCN1759574AData switching networksElectric digital data processingHeterogeneous networkDistributed computing
A system and method for classification of data units in a network device acts as a bridge in heterogeneous networks, provides many different services and provisions many different transport mechanisms. The data classifier generates an ID that is internally used by the network device in managing, queuing, processing, scheduling and routing to egress the data unit. This internal ID enables the device to accept any type of data units from any physical / logical ports or channels and output those data units on any physical / logical ports or channels that are available. The device utilizes learning on a per-flow basis and can enable the device to identify and process data units used in private line services and private LAN services.
Owner:NETLOGIC MICROSYSTEMS
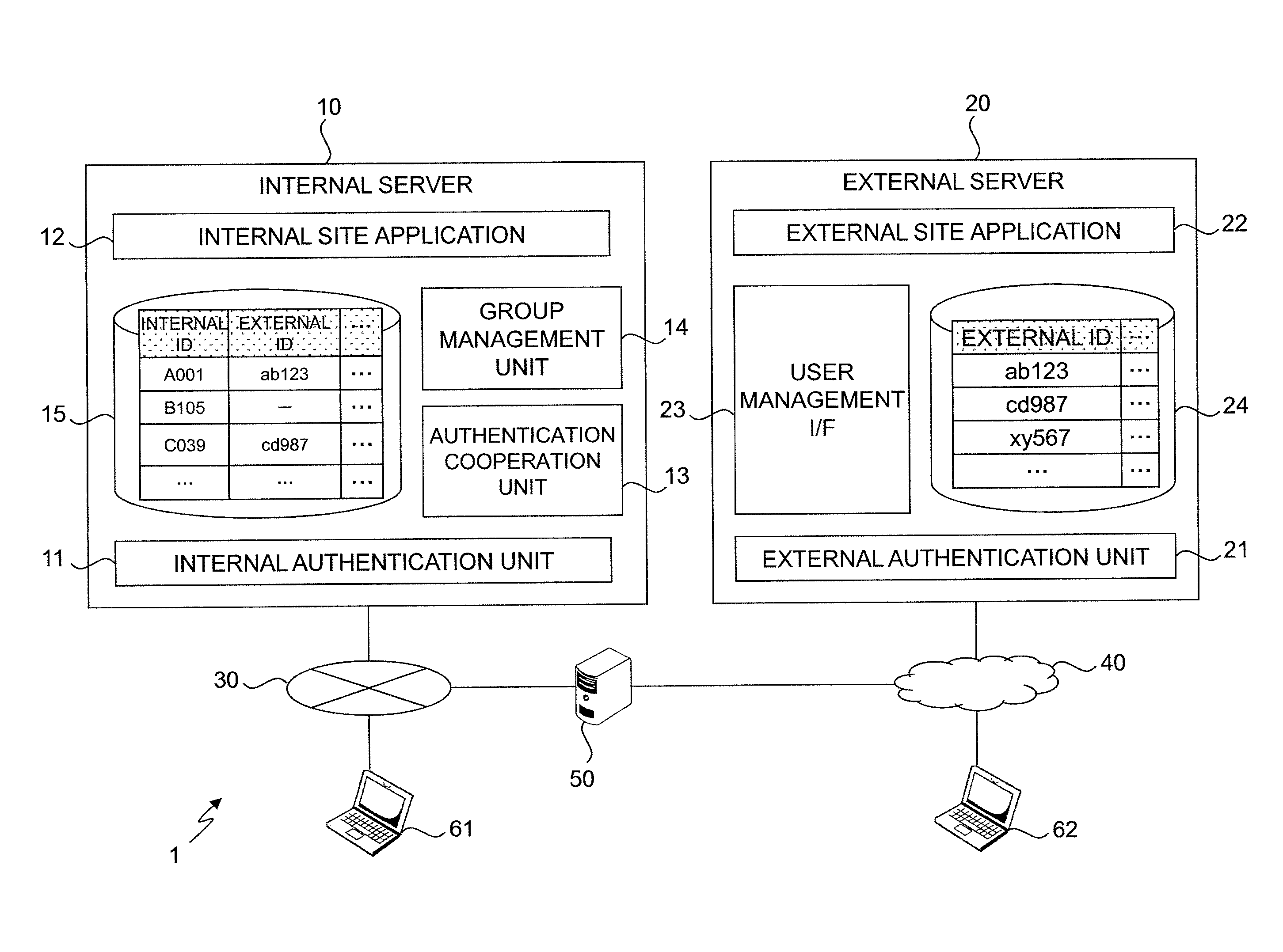
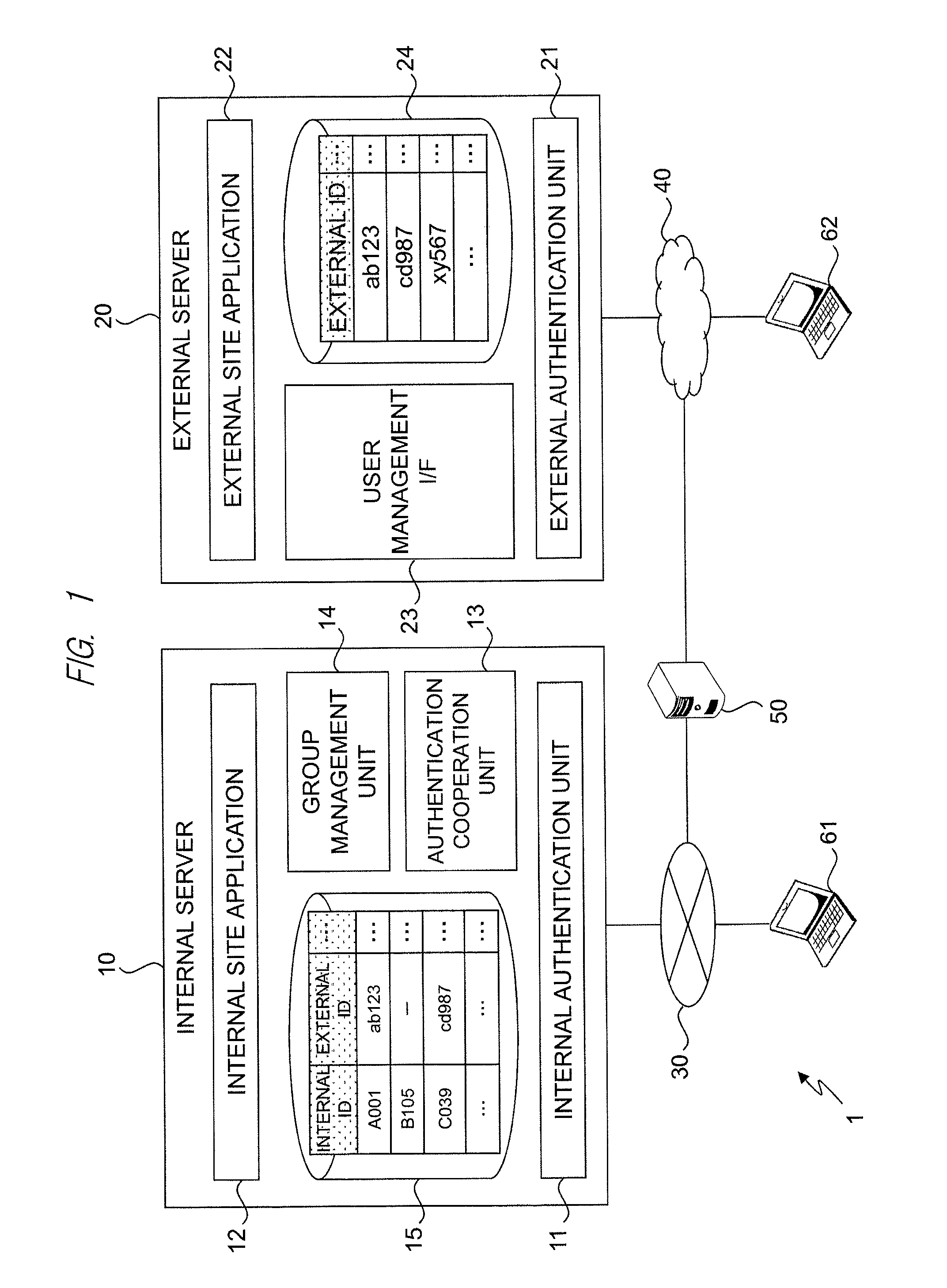
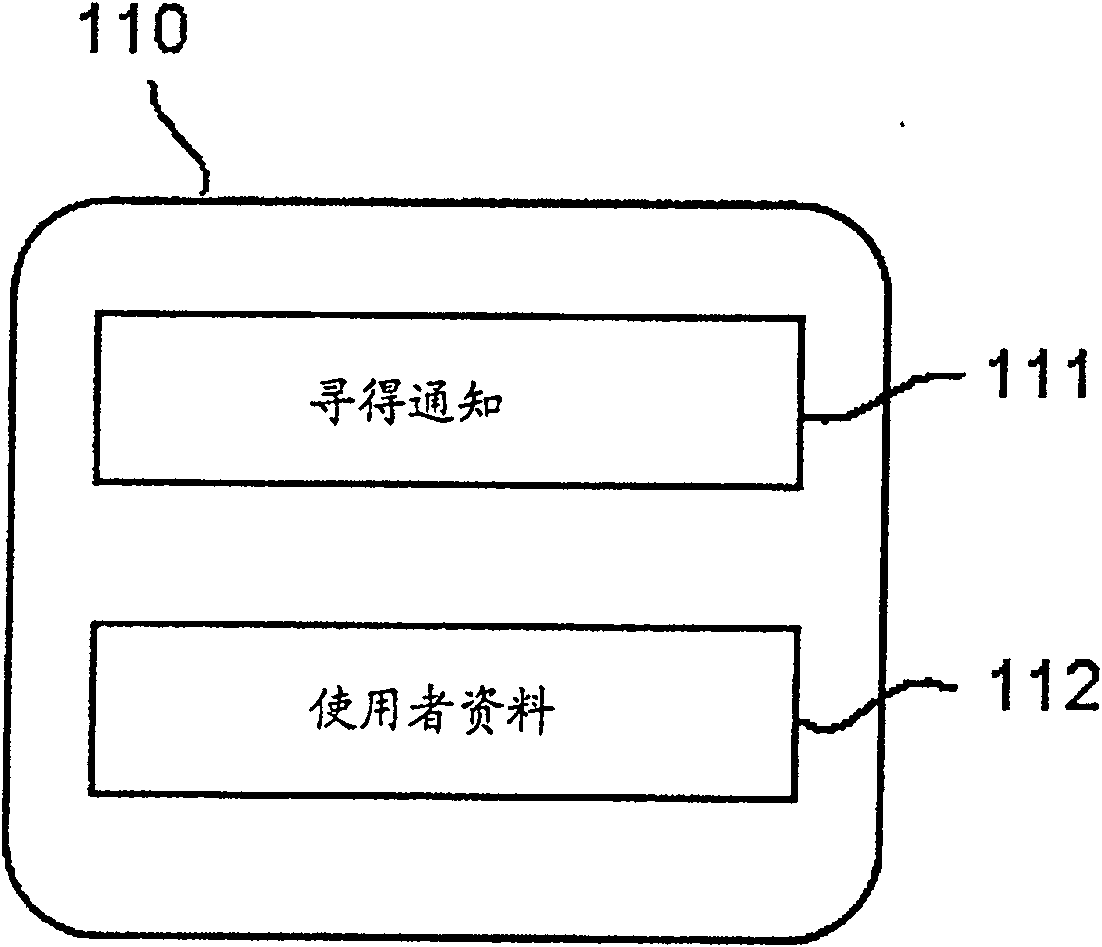
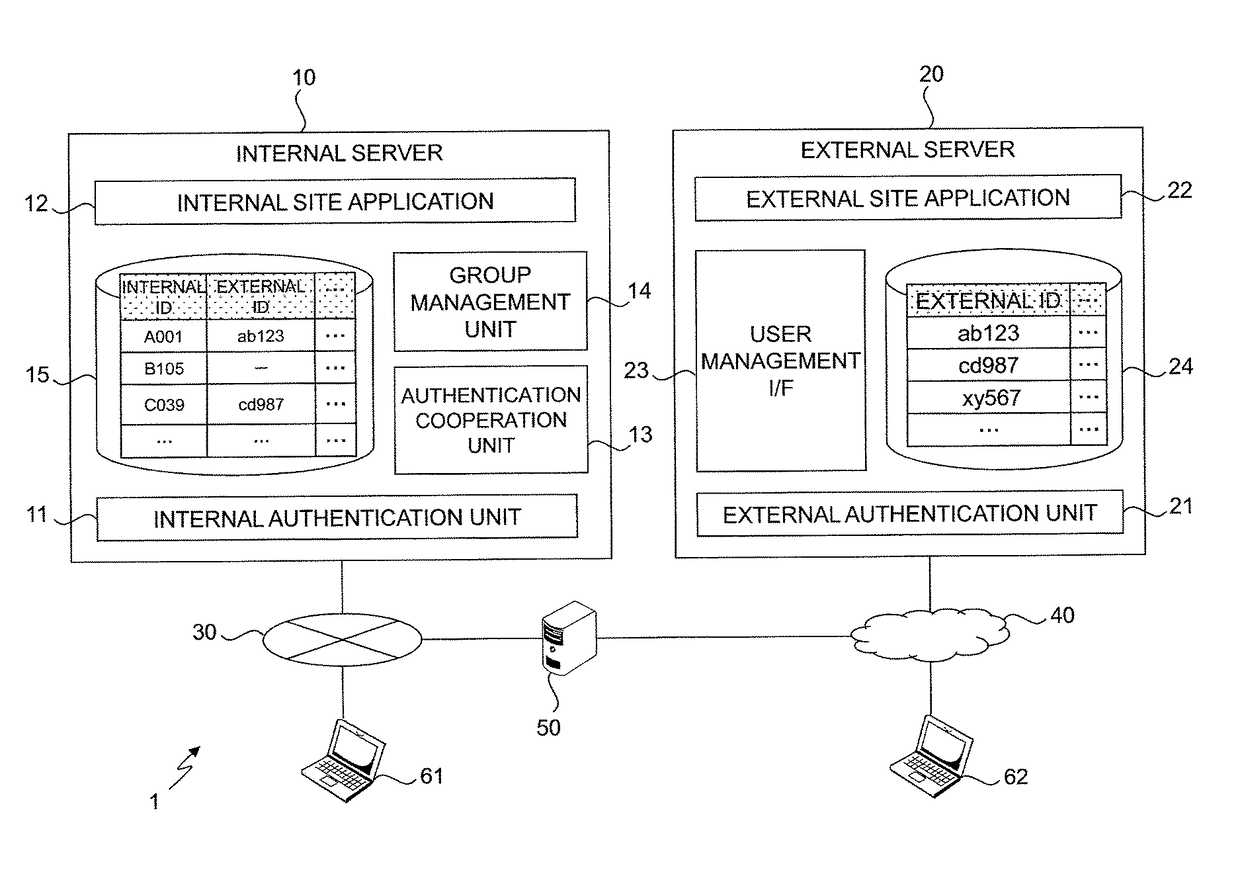
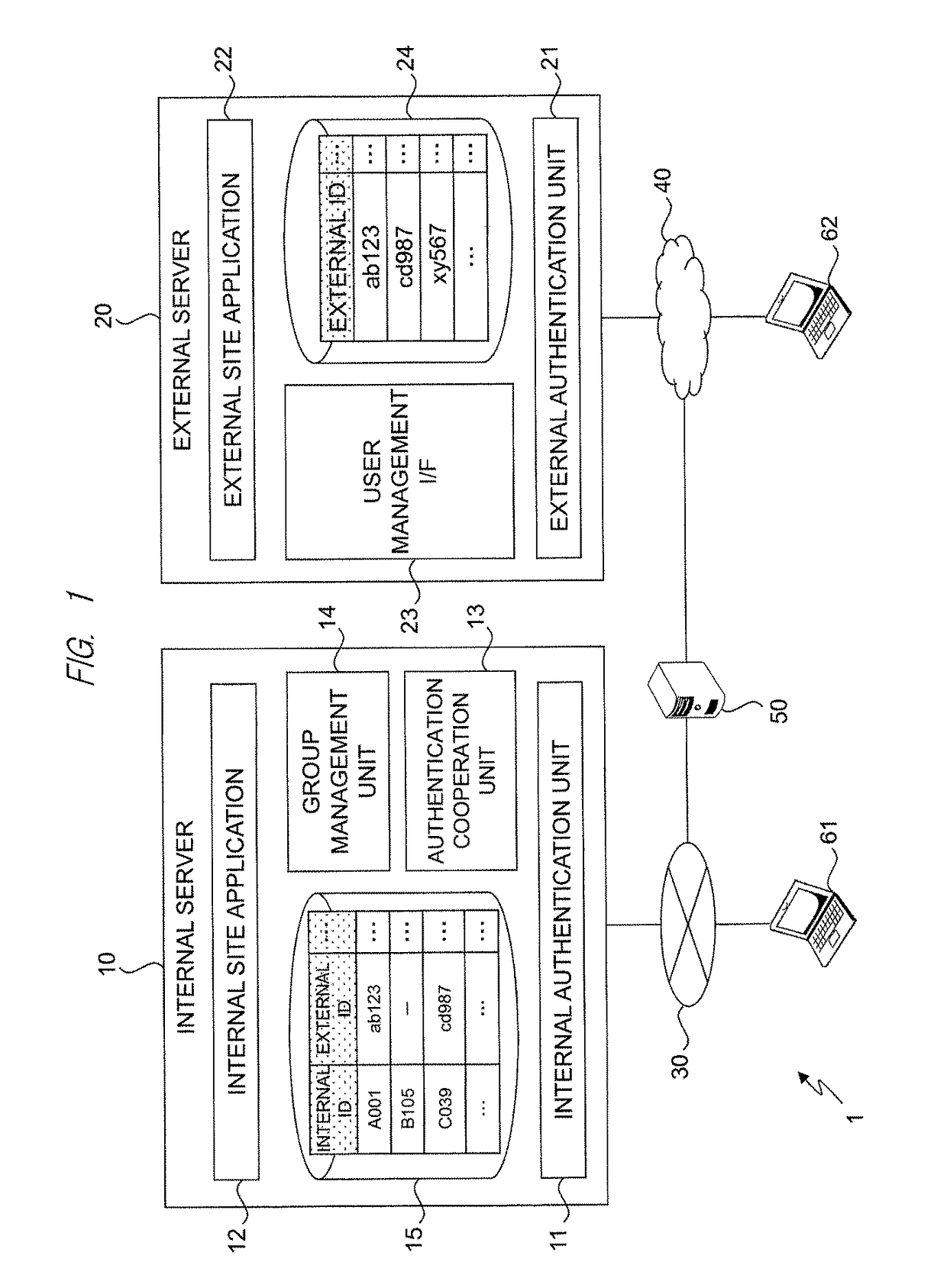
Group definition management system
ActiveUS20140189796A1Easy to getIncrease reflectionDigital data processing detailsMultiple digital computer combinationsEngineeringUser management
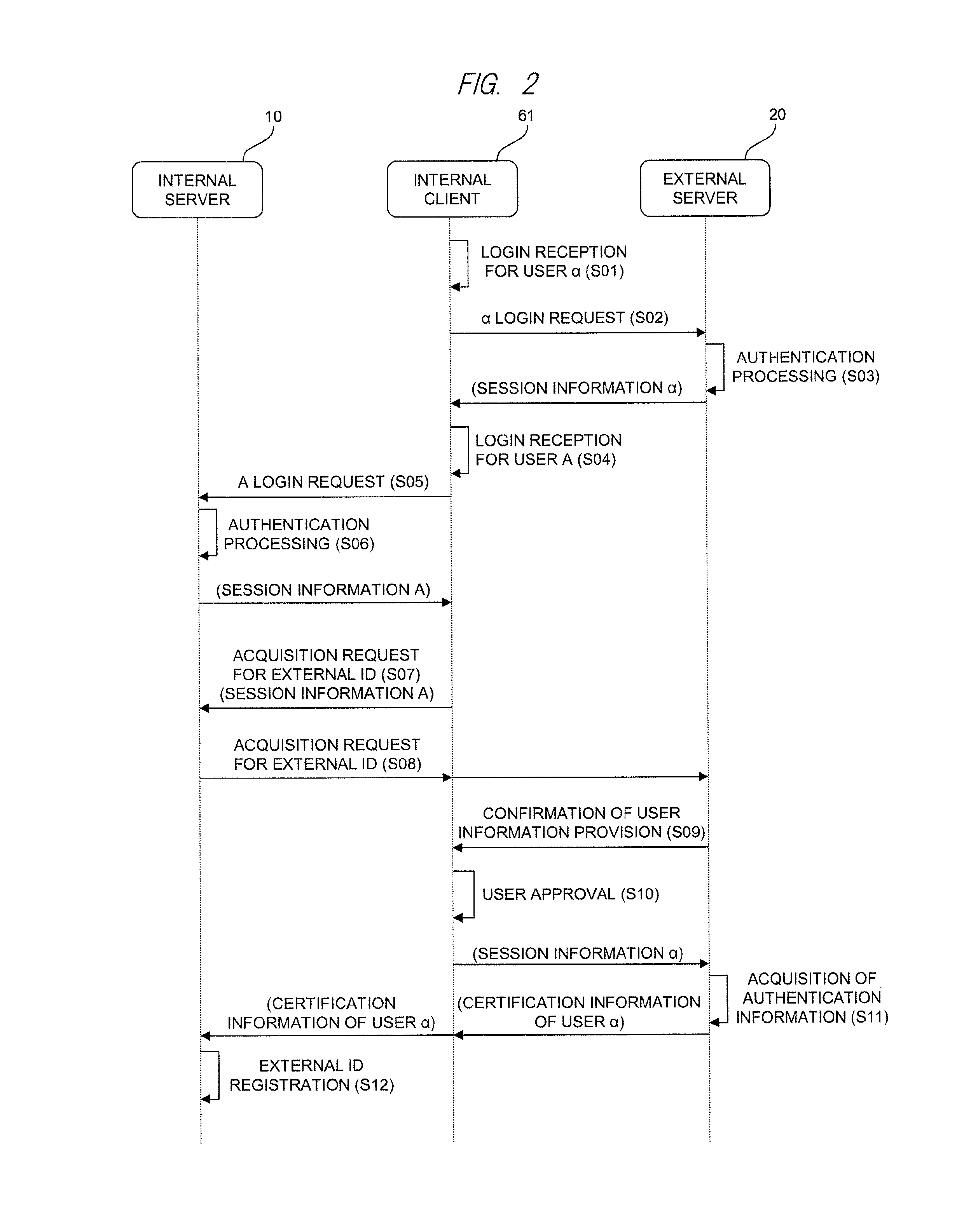
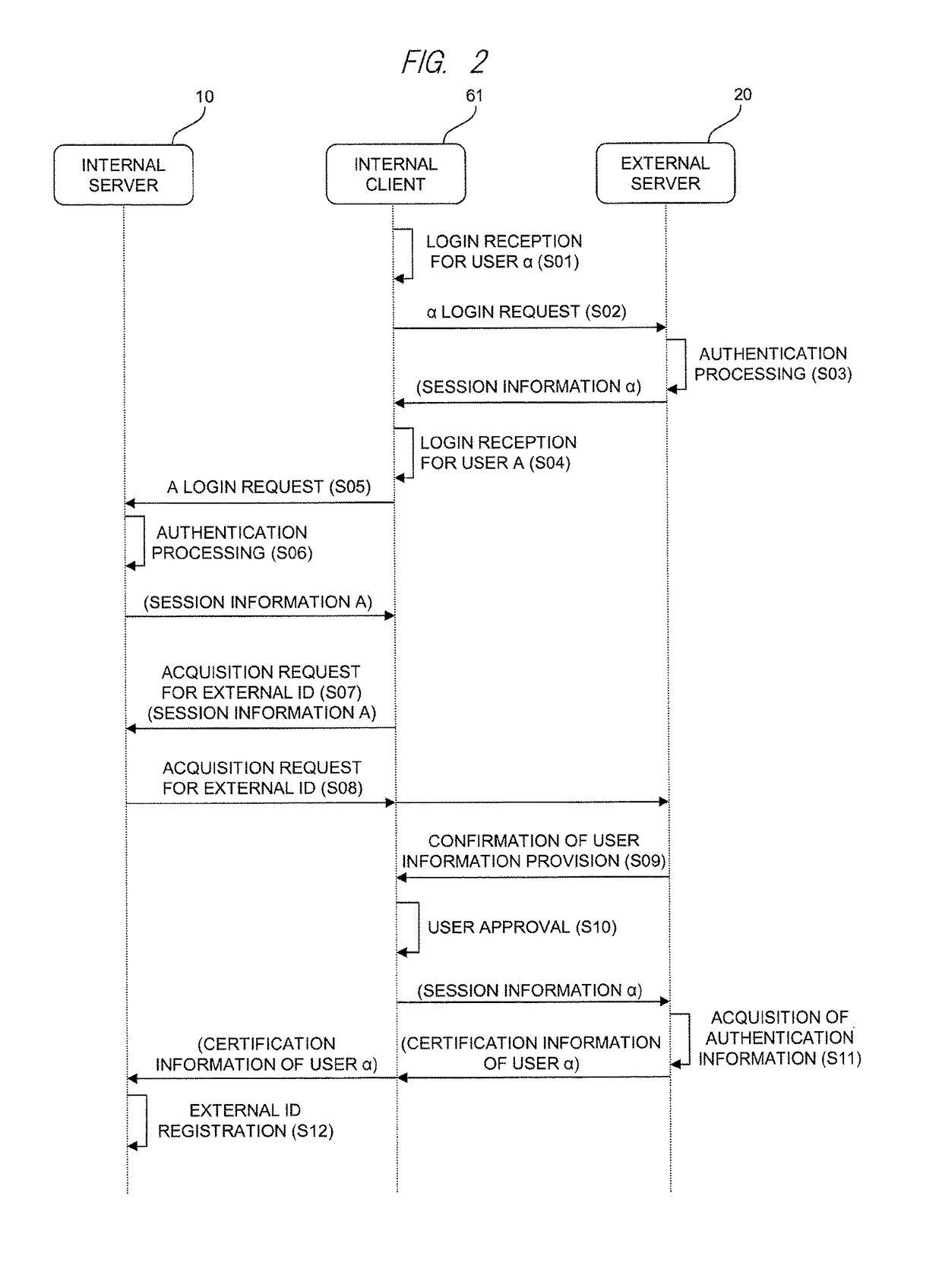
A group definition management system can easily acquire correspondence between an internal ID and an external ID and easily reflect information of a group definition for the internal ID to an external site. In a typical embodiment of the present invention, this is configured of an internal server 10, an external server 20, and a client. The internal server 10 has an internal user management table 15 and an internal authentication unit 11 that performs authentication by the internal ID. The external server 20 has an external user management table 24 and an external authentication unit 21 that performs authentication by the external ID and replies the information of the external ID in response to an inquiry for whether or not a specific user is an authentic user. The internal server 10 further has an authentication cooperation unit 13 that inquires the external server 20 about whether or not the user is the authentic user of the external server 20 in response to a request from the client used by the user authenticated by the internal authentication unit 11, and registers the replied external ID in the internal user management table 15 so as to correspond to the internal ID.
Owner:RAKUTEN GRP INC
Method and system for modifying schema definitions
ActiveUS7024434B2Data processing applicationsObject oriented databasesSchema for Object-Oriented XMLClient-side
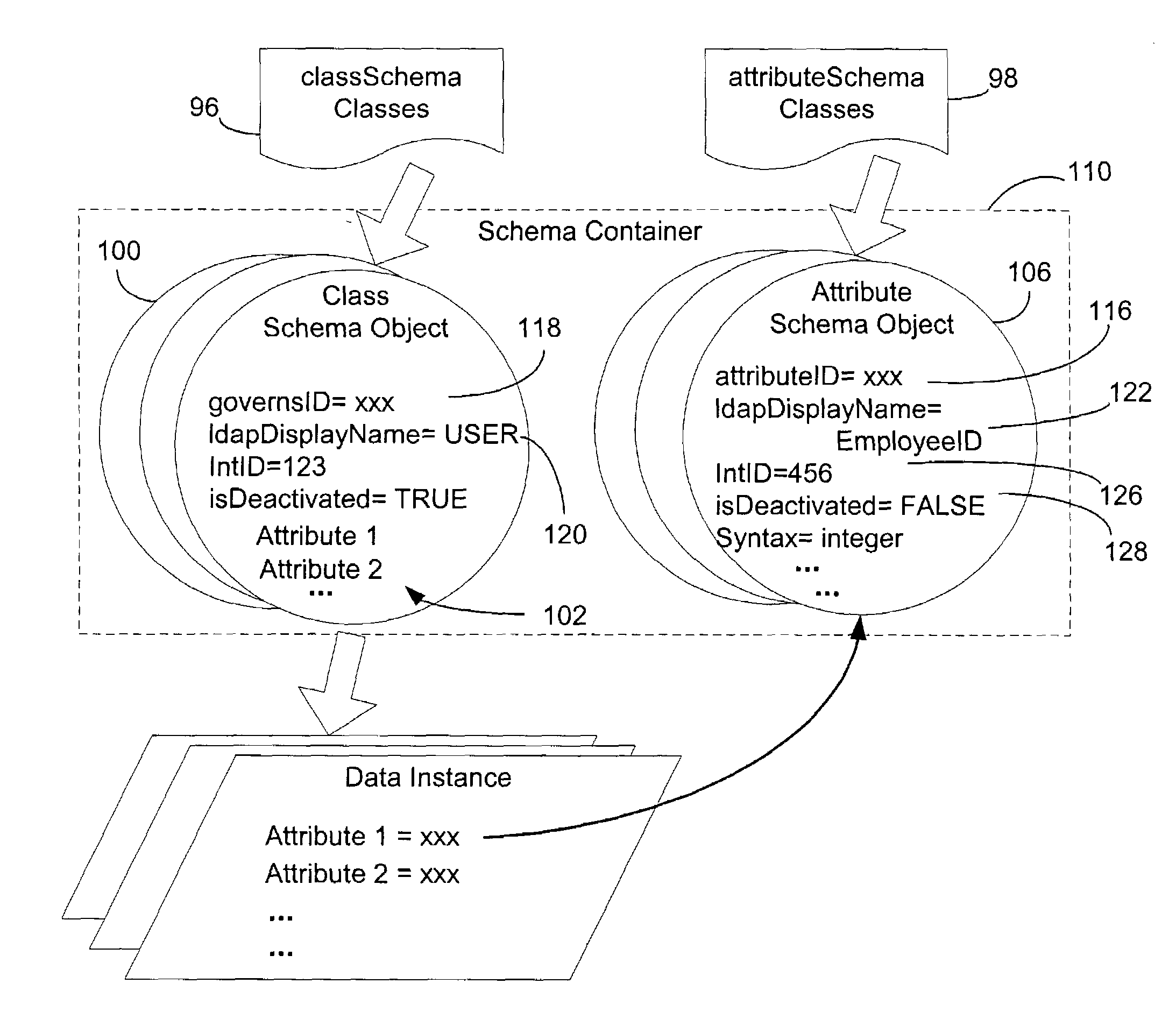
A new schema implementation enables reversible changes to be made to definitions in a schema. The definitions of attributes and classes are in the form of schema objects. Each schema object has an internal ID in addition to its unique name and object ID (OID), and a deactivation flag for indicating whether the schema object has been deactivated. To modify an attribute or class, the corresponding schema object is deactivated by setting its deactivation flag to “TRUE,” and a new schema object is created to contain the changes. The new schema object has the same unique name and OID as the old schema object but is given a different internal ID. When a client wants to access instances of the schema object by its unique name or OID, a translation is made to provide the internal ID of the new schema object such that instances of the new schema object are located instead of the old schema object. The changes to the schema can be reversed by reactivating the first schema object and deactivating the second schema object.
Owner:MICROSOFT TECH LICENSING LLC
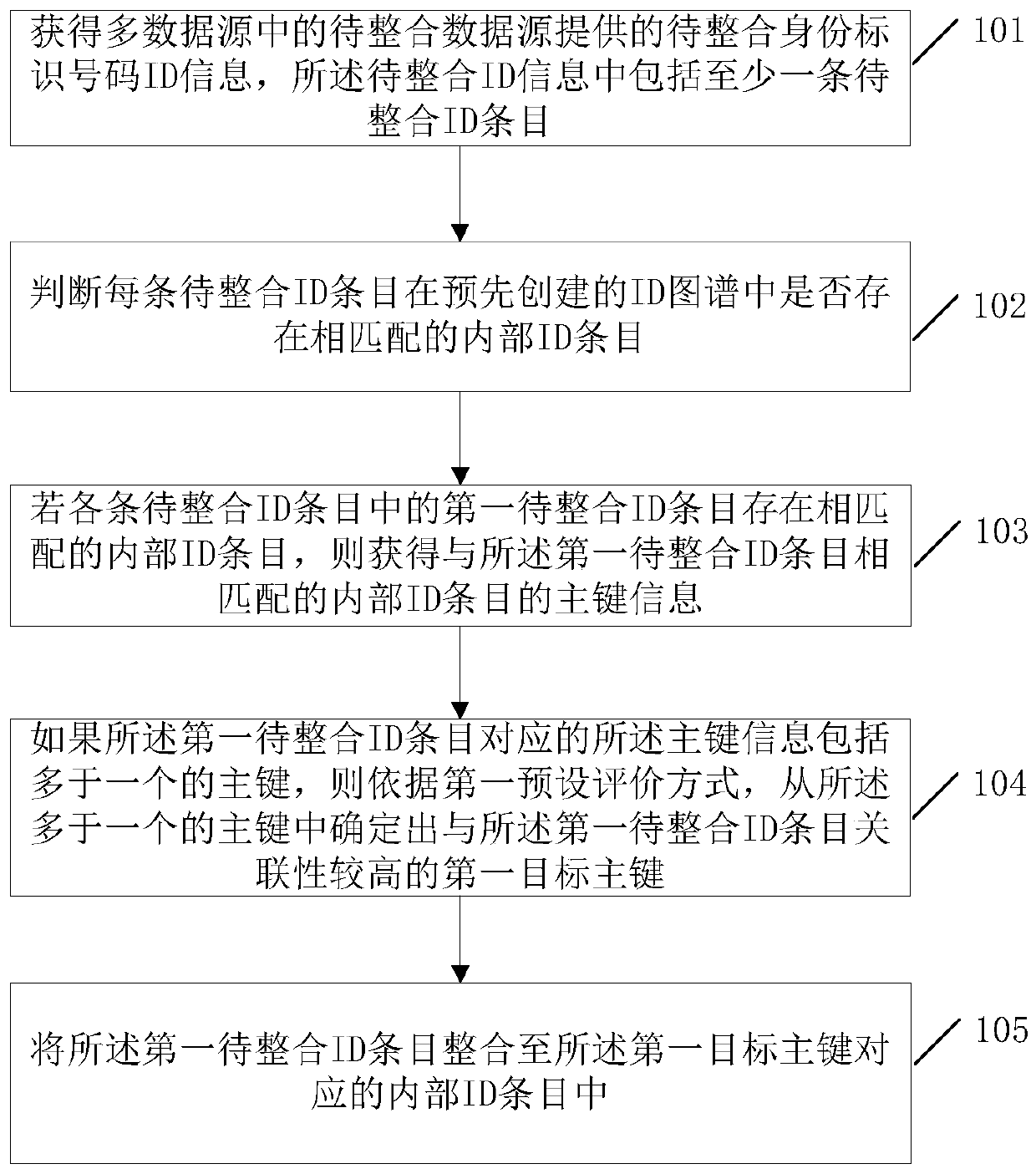
Multi-data-source user information integration method and device
ActiveCN108664480ASolving recognition problemsEfficient integrationSpecial data processing applicationsMarket data gatheringData sourceComputer science
Owner:BEIJING GRIDSUM TECH CO LTD
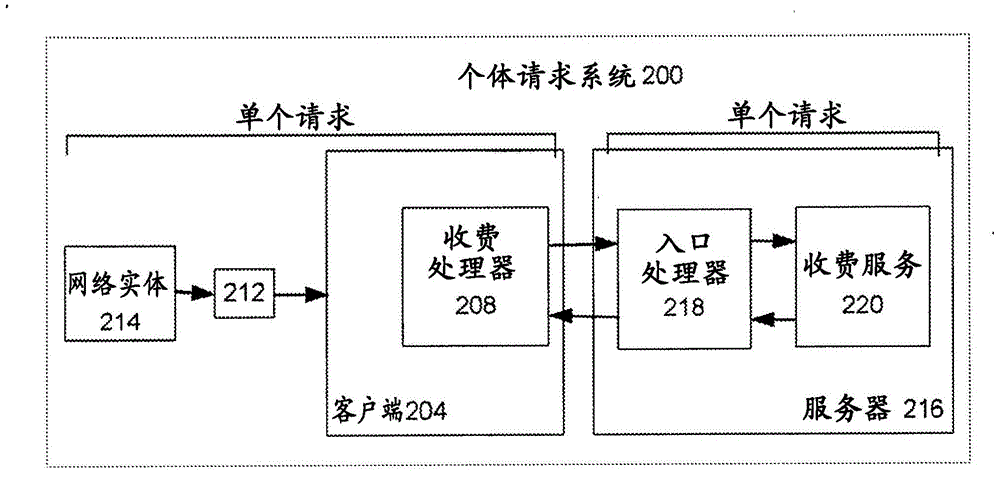
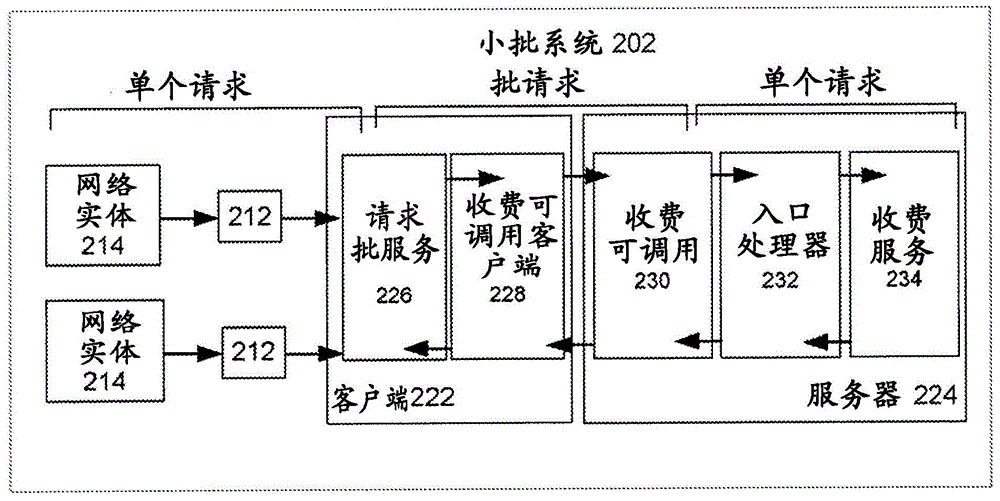
System and method for small batching processing of usage requests
In accordance with various embodiments, systems and methods that provide unified charging across different network interfaces are provided. A system for small batch processing of usage requests, can include a service broker, a plurality of servers wherein each server includes customer data, and a plurality of queues, each associated with a different server. When a usage request is received from a network entity, the service broker is configured to determine an internal ID associated with data requested by the usage request, determine on which particular server of the plurality of servers the data requested by the usage request is stored, enqueue the usage request in a particular queue associated with the particular server, and upon a trigger event, send all requests in the particular queue to the particular server in a batch.
Owner:ORACLE INT CORP
Method and system for modifying schema definitions
InactiveUS20060136439A1Data processing applicationsDigital data processing detailsClient-sideDatabase
A new schema implementation enables reversible changes to be made to definitions in a schema. The definitions of attributes and classes are in the form of schema objects. Each schema object has an internal ID in addition to its unique name and object ID (DID), and a deactivation flag for indicating whether the schema object has been deactivated. To modify an attribute or class, the corresponding schema object is deactivated by setting its deactivation flag to “TRUE,” and a new schema object is created to contain the changes. The new schema object has the same unique name and DID as the old schema object but is given a different internal ID. When a client wants to access instances of the schema object by its unique name or DID, a translation is made to provide the internal ID of the new schema object such that instances of the new schema object are located instead of the old schema object. The changes to the schema can be reversed by reactivating the first schema object and deactivating the second schema object.
Owner:MICROSOFT TECH LICENSING LLC
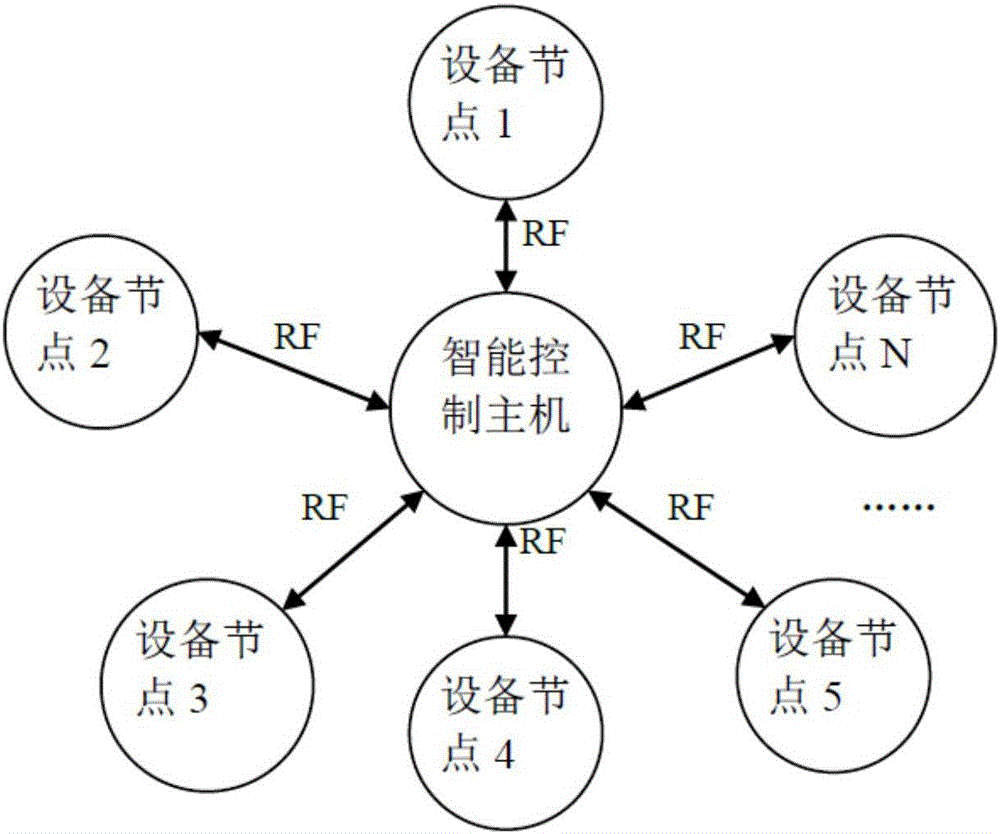
Multi-point networking communication system
InactiveCN106341292AReduce limitationsNo feeStar/tree networksHome automation networksCommunications systemRF module
The invention provides a multi-point networking communication system comprising an intelligent control host and an equipment node network. The intelligent control host and the equipment node network form a star network. Point-to-point communication is performed between the intelligent control host and the equipment node network through control instructions. The equipment node network includes countless equipment nodes. A wireless transmit-receive module is embedded in each equipment node to act as the wireless communication hardware basis. The intelligent control host comprises a host node, a core processor and an RF module. The host node is used for processing the serial port instructions of the core processor. When the host requires to communicate with the equipment, the core processor transmits the instructions to the RF module through serial ports, then the RF module wirelessly forwards the instructions to the equipment nodes, and the equipment receives information and then performs processing and feedback according to the respective attribute state. Each equipment node and the host node have a unique equipment address ID, wherein the equipment address ID uses the internal ID of the chip so as to guarantee the uniqueness.
Owner:广州华睿电子科技有限公司
Information process apparatus and method, program, and record medium
InactiveUS8437604B2Improve convenienceEasy to implementElectronic editing digitised analogue information signalsColor television signals processingInformation handlingRecording media
To improve the convenience of a record medium and allow a record process and reproduction process to be more easily performed than before. When a clip edit list update process 121 that updates video data and audio data recorded on a disc 32 is executed, an index file management section 72 manages and updates an index file held in an index file hold section 51 as the video data and audio data are updated. At this point, a search section 92 searches disc internal IDs assigned to clips or edit lists contained in the index file for the maximum value. A disc internal ID generation section 91 generates a disc internal ID according to the maximum value. An index file management section 72 updates the index file with the disc internal ID generated by the disc internal ID generation section 91.
Owner:SONY CORP +1
Authentication method, device and system for preventing lock from being duplicated, and electronic key for preventing lock from being duplicated
ActiveCN109326018ASolve the problem of artificial illegal copyingEliminate problems integrating into lock management systemsIndividual entry/exit registersManagement systemAuthentication
The invention relates to an authentication method, device and system for preventing a lock from being duplicated, and an electronic key for preventing the lock from being duplicated. The authentication method comprises the steps that the electronic key judges whether the accessed lock is an intelligent lock or not, when it is judged that the accessed lock is the intelligent lock, power supplying is conducted on the intelligent lock, and a communication secret key of the intelligent lock is obtained; whether the obtained communication secret key of the intelligent lock is correct or not is verified, and when it is verified that the obtained communication secret key of the intelligent lock is correct, the type of the intelligent lock is obtained; whether the obtained type of the intelligentlock is correct or not is judged, and when it is judged that the obtained type of the intelligent lock is correct, internal ID of the intelligent lock is obtained; and whether the obtained internal IDof the intelligent lock is correct or not is judged, and the obtained internal ID of the intelligent lock is correct and is target ID, the lock is authenticated successfully. According to the authentication method, device and system for preventing the lock from being duplicated, and the electronic key for preventing the lock from being duplicated, the problem that the intelligent lock is duplicated artificially and illegally is effectively solved, and thus the problem that a counterfeit lock or intelligent lock is merged into a lock management system is effectively eradicated.
Owner:ZHUHAI UNITECH POWER TECH CO LTD
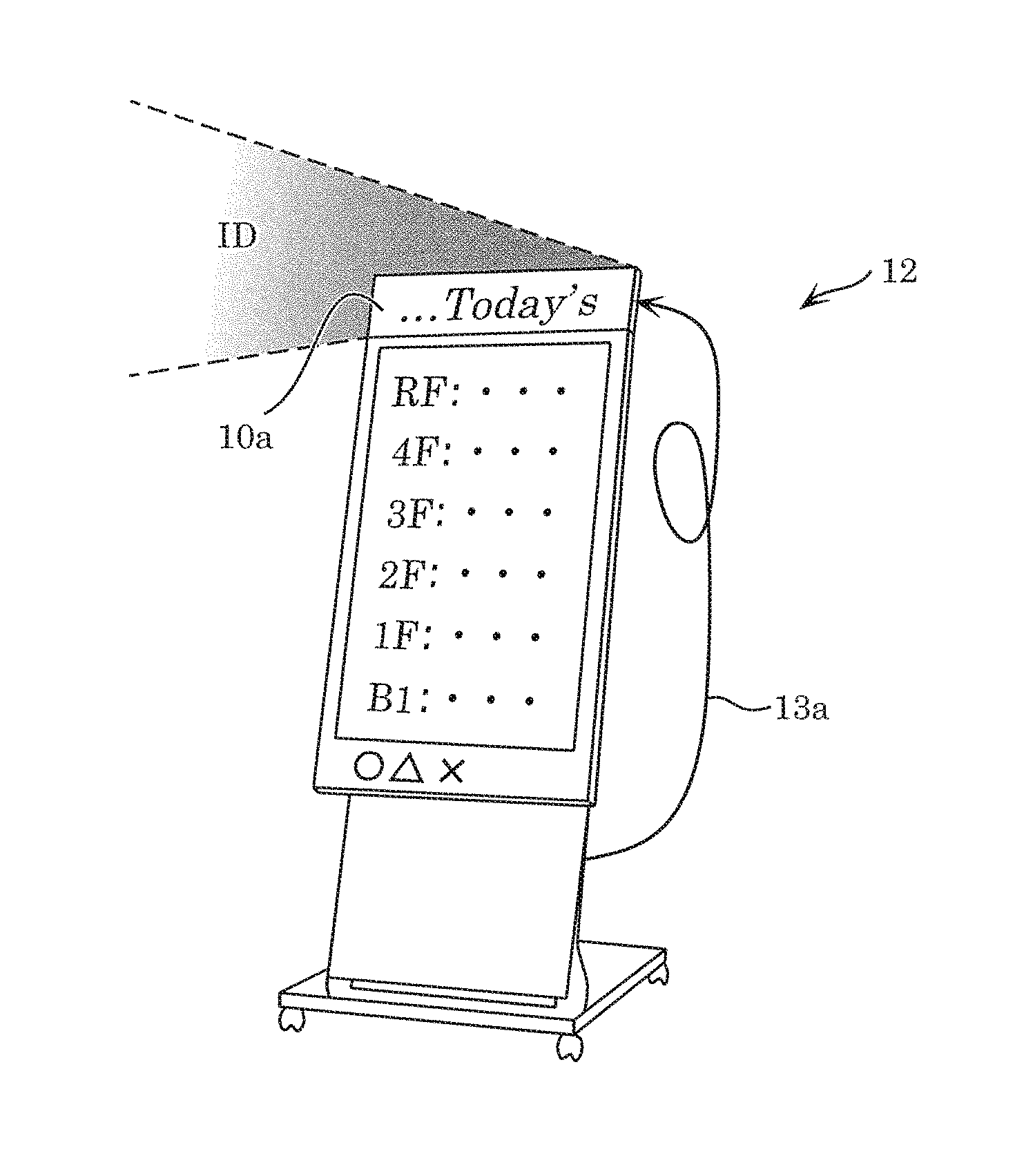
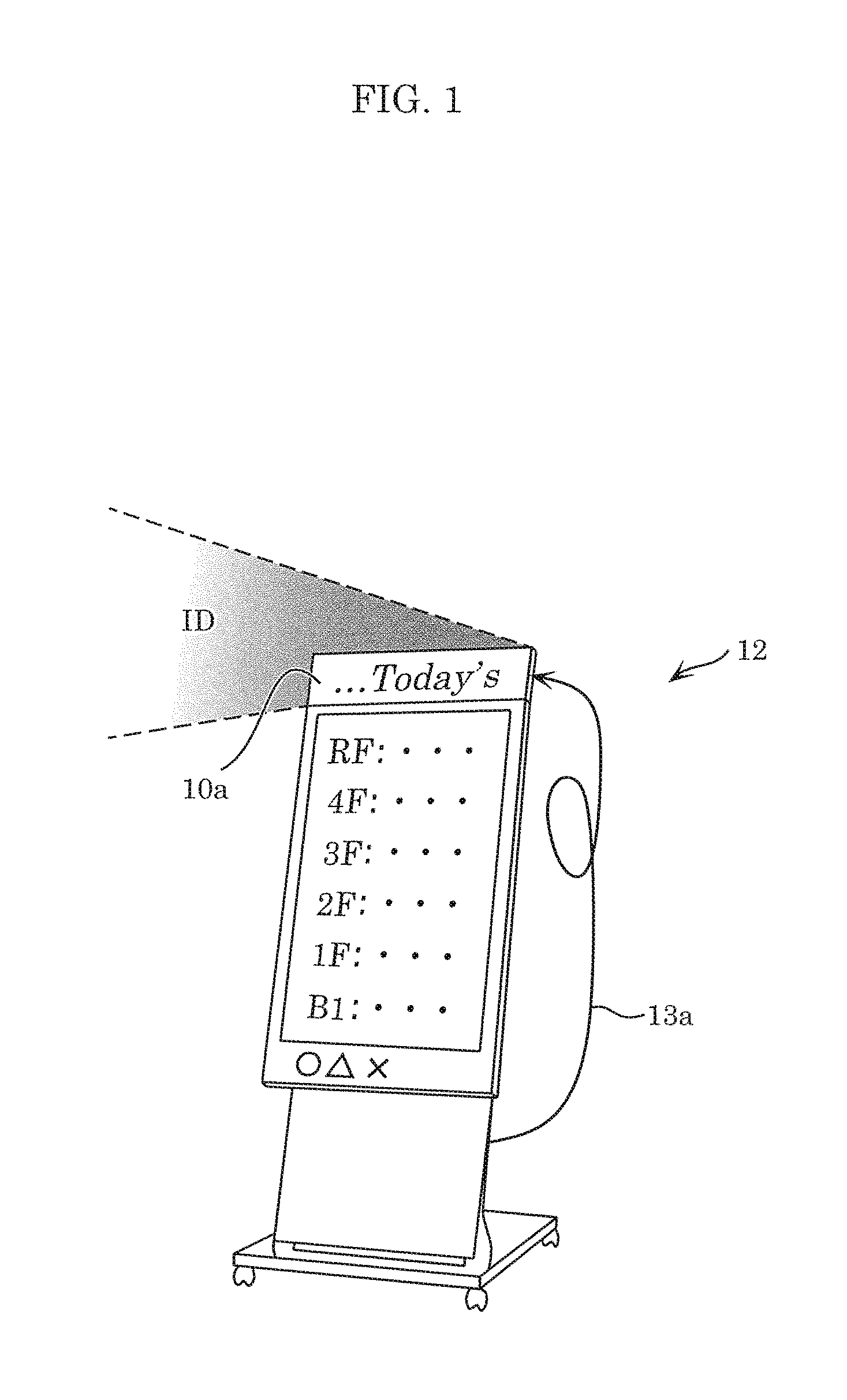
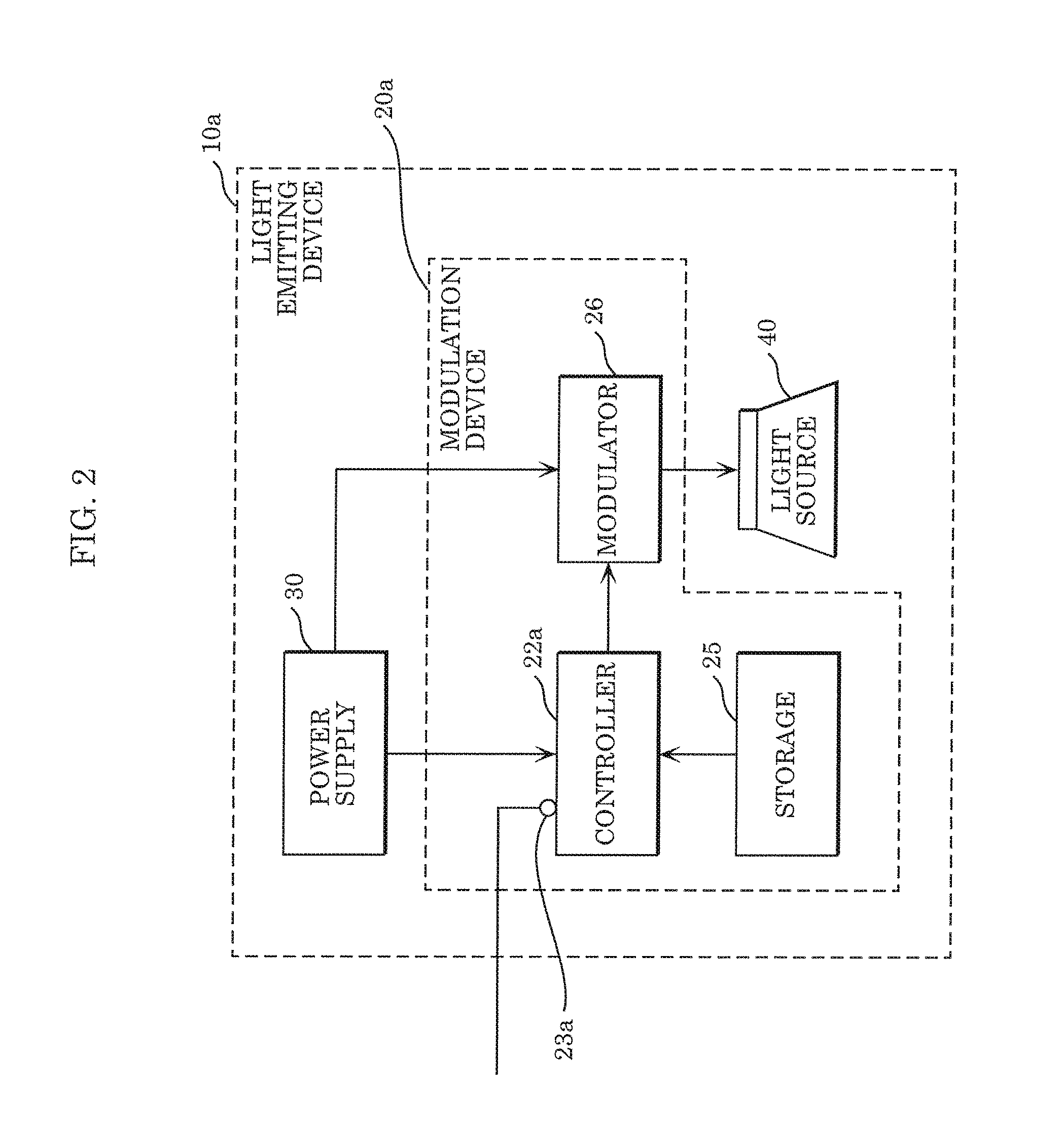
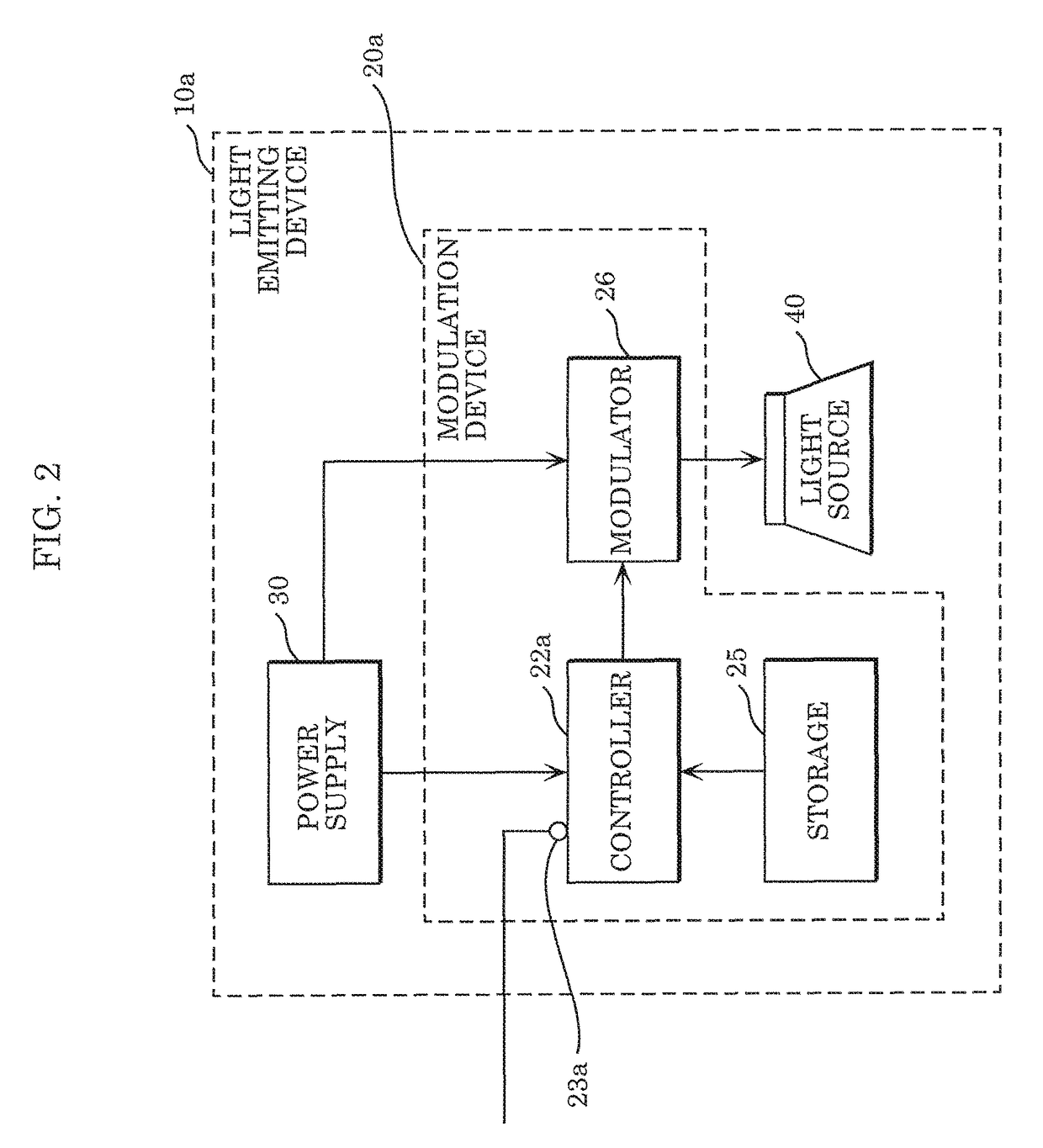
Modulation device, light emitting device, and light emission system
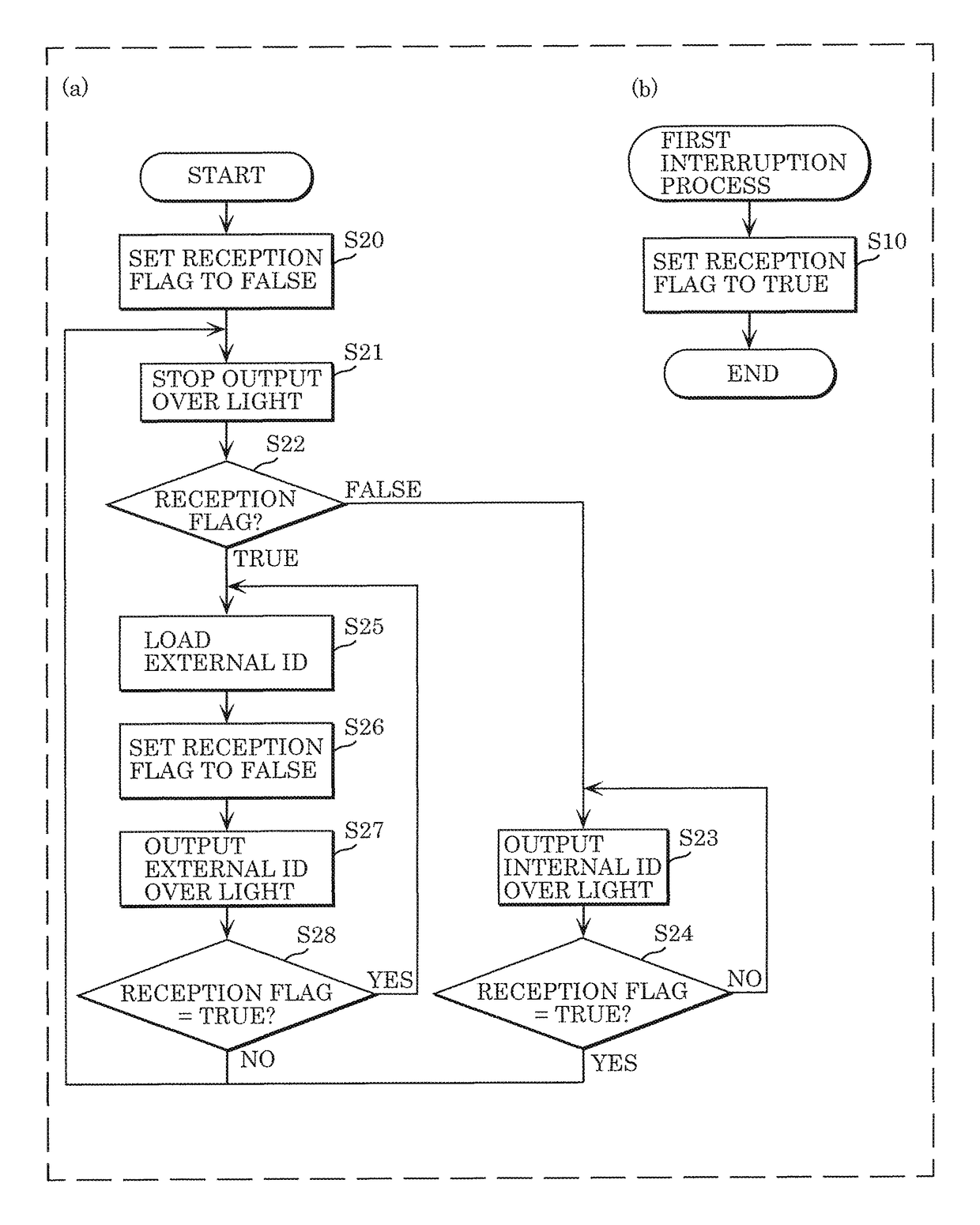
ActiveUS20160359562A1Transmission systemsSynchronisation by photonic/optical meansEngineeringControl circuit
A modulation device includes a modulator circuit that causes a light source to perform light communication, storage storing an internal ID, and a control circuit that determines whether an external ID is input into the modulation device. When the control circuit determines that the external ID is input into the modulation device, the control circuit causes the input external ID to be input, as a modulation signal, into the modulator circuit. When the control circuit determines that the external ID is not input into the modulation device, the control circuit causes the internal ID stored in the storage to be input, as a modulation signal, into the modulator circuit.
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
Method for matching Bluetooth interface with charging pile ID and two-dimensional bar code for charging piles
InactiveCN107277749AIncrease productivityCompact structureCo-operative working arrangementsDevices with bluetooth interfacesHuman powerBluetooth
Owner:ZHEJIANG UNIV OF TECH
Improvements to method and system for detecting counterfeit consumable products
The invention relates to a method and system for detecting counterfeit consumable products, comprising the use of two identifiers (ID), namely an external ID and an internal ID, in order to identify if a product is original or counterfeit. Both IDs are affixed to the surface of the product, one being exposed to the exterior and the other concealed by some type of protective layer that can only be removed by the owner of the product. In addition, the external ID provides the user with descriptive information about the product.
Owner:卡洛斯莫伊塞斯埃尔南德斯苏亚雷斯
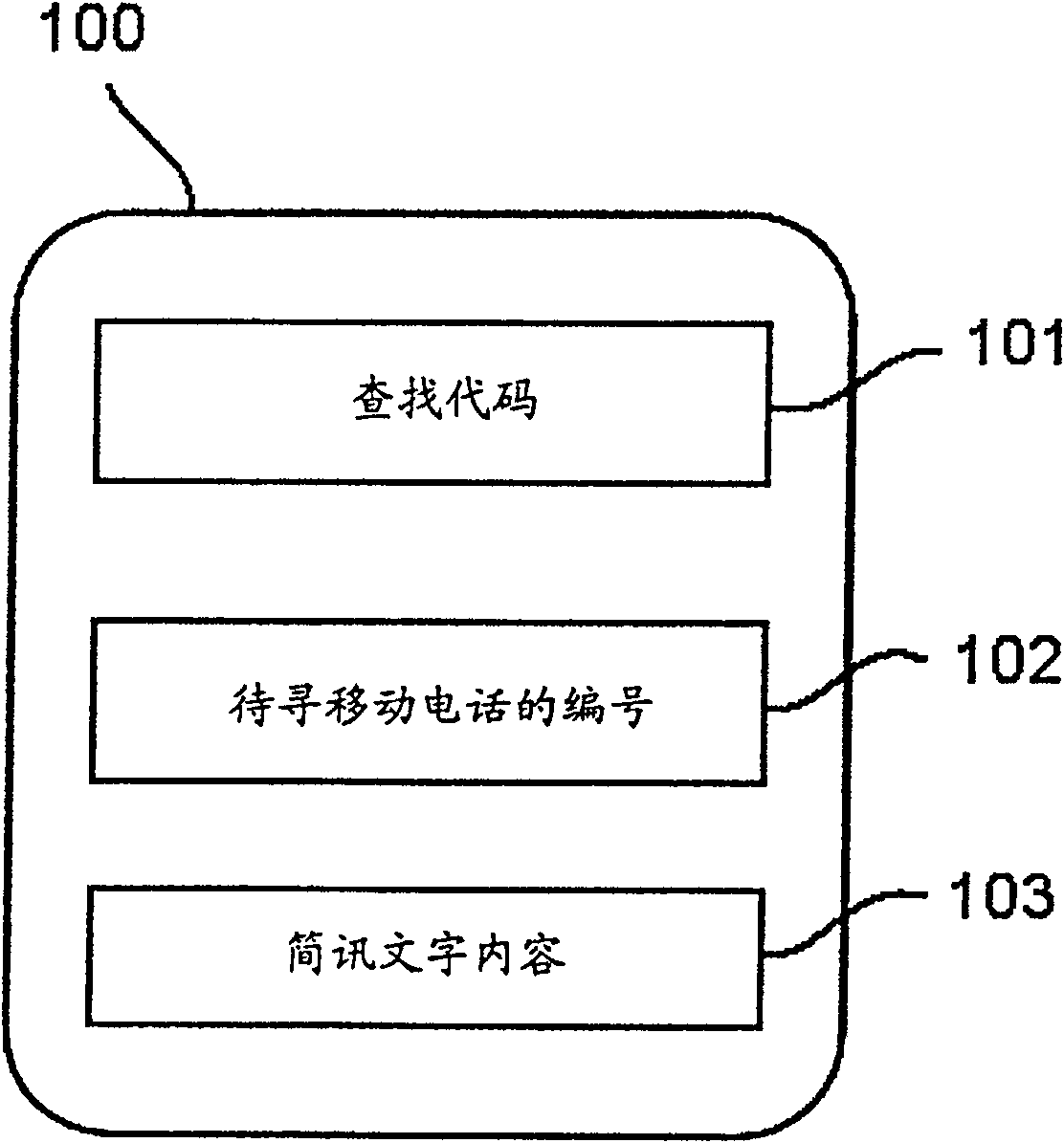
Antitheft method for mobile telephone
InactiveCN100553274CTelephonic communicationRadio/inductive link selection arrangementsGSMMobile phone
The invention relates to an anti-theft method for a mobile phone, which uses the unique internal number built in the mobile phone and cooperates with a short message filtering program to filter all the short messages received by the mobile phone; when a mobile phone search code is filtered out of the short messages, the short messages are Compare the number of the mobile phone to be searched with the local number in order to find out the door number currently used by the stolen mobile phone, and find the location of the mobile phone through the GSM mobile phone positioning or the SMS feedback system of the base station.
Owner:YINGHUADA (SHANGHAI) ELECTRONIC CO LTD
Group definition management system
ActiveUS9858399B2Easy to getIncrease reflectionDigital data processing detailsDigital data protectionInternet privacyUser management
A group definition management system can easily acquire correspondence between an internal ID and an external ID and easily reflect information of a group definition for the internal ID to an external site. In a typical embodiment of the present invention, this is configured of an internal server 10, an external server 20, and a client. The internal server 10 has an internal user management table 15 and an internal authentication unit 11 that performs authentication by the internal ID. The external server 20 has an external user management table 24 and an external authentication unit 21 that performs authentication by the external ID and replies the information of the external ID in response to an inquiry for whether or not a specific user is an authentic user. The internal server 10 further has an authentication cooperation unit 13 that inquires the external server 20 about whether or not the user is the authentic user of the external server 20 in response to a request from the client used by the user authenticated by the internal authentication unit 11, and registers the replied external ID in the internal user management table 15 so as to correspond to the internal ID.
Owner:RAKUTEN GRP INC
IPv6 address configuration method of wireless sensor network based on geographical position
InactiveCN101867919BReduce volumeLow priceNetwork topologiesWireless network protocolsMobile wireless sensor networkGeographic site
The invention provides an IPv6 address configuration method of a wireless sensor network based on a geographical position. The wireless sensor network comprises full-function sensor nodes and partial-function sensor nodes; a wireless sensor network area is divided into multiple squares with identical areas, and each square is identified by coordinates; if the multiple full-function sensor nodes are contained in one square region, then only one full-function sensor node in activated state exists at the same time; in one square region, all the sensor nodes can realize one-hop communication; access nodes used for connecting the wireless sensor network and an IPv6 network are full-function sensor nodes; at most one access node is contained in one square region; and the full-function sensor nodes in the activated state adopt the stateful address distribution scheme that the partial-function sensor nodes in the square area distribute internal ID addresses in a unified way, and adopt the division method and linear detection method to produce internal ID addresses.
Owner:JIANGSU JUNZHI SENSING TECH
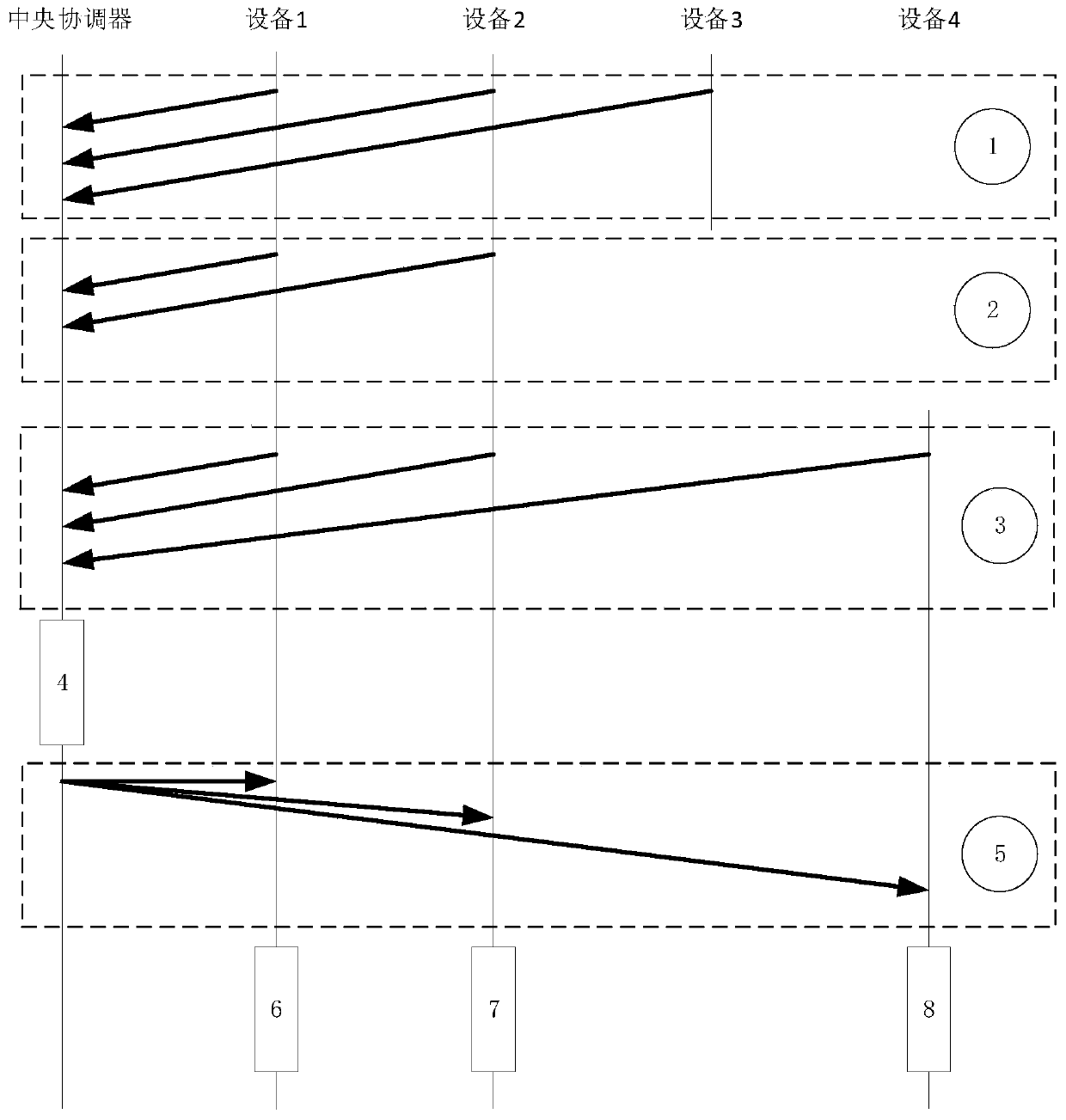
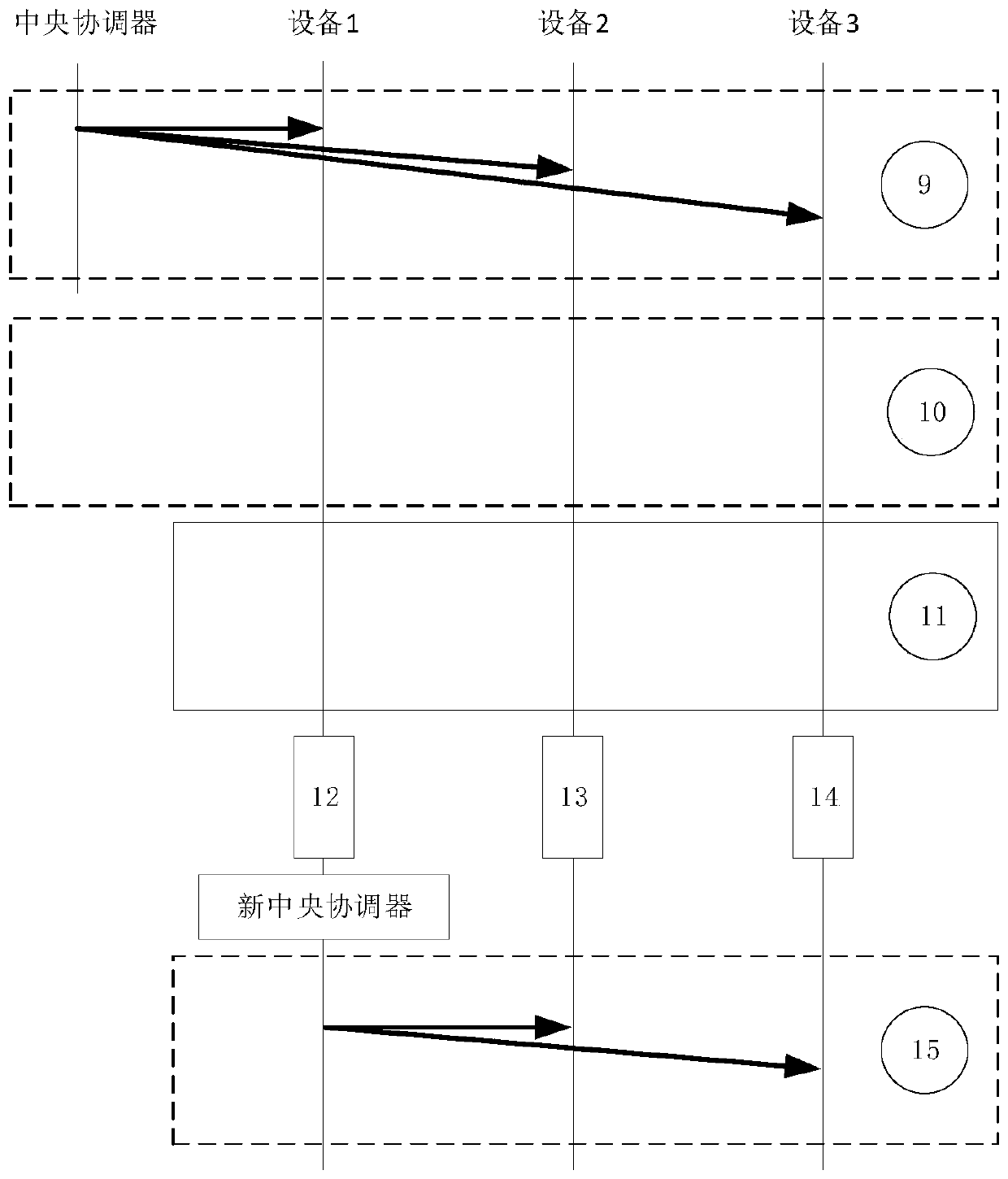
Power failure detection method of communication equipment
ActiveCN111245477AAvoid wastingGuaranteed timelinessPower distribution line transmissionPower supply for data processingCommunications systemPublic broadcasting
A power failure detection method of communication equipment comprises the following steps: a central coordinator carries MAC addresses of all devices in a current network and a network internal ID number mapping table corresponding to the MAC addresses in public broadcast information, the mapping table in the public broadcast information is updated, all the devices in the current network judge thestates of the devices in the network according to the mapping table, and then the network connection state of the devices is optimized. The state information of each device in the current network needs to be updated in time in a communication system to prevent waste of system resources, caused by occupation of network resources due to unnecessary factors, so timeliness of equipment state updatingis effectively guaranteed, unnecessary loss caused by failure of normal connection during equipment reconnection is avoided, and meanwhile, the resource utilization rate in a system network is also guaranteed.
Owner:磐基技术有限公司
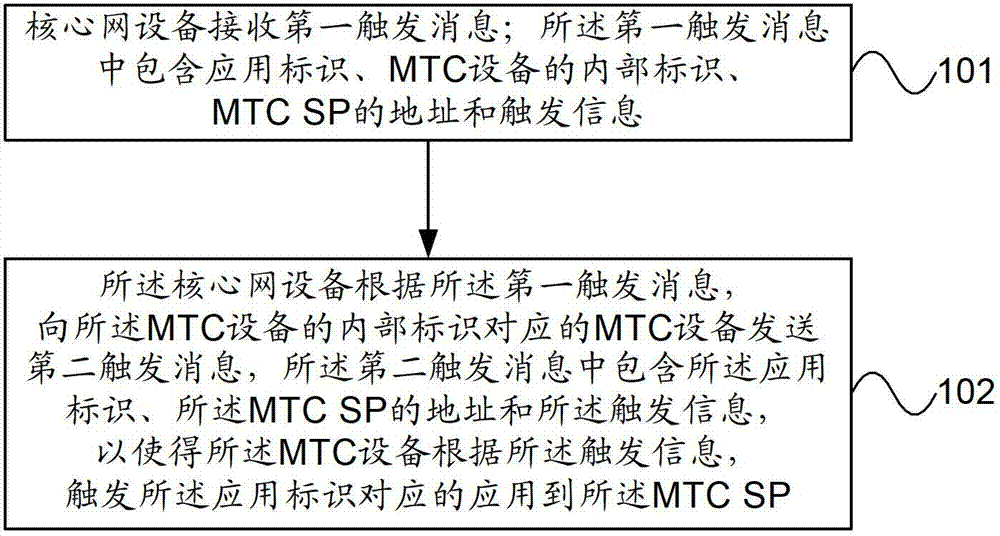
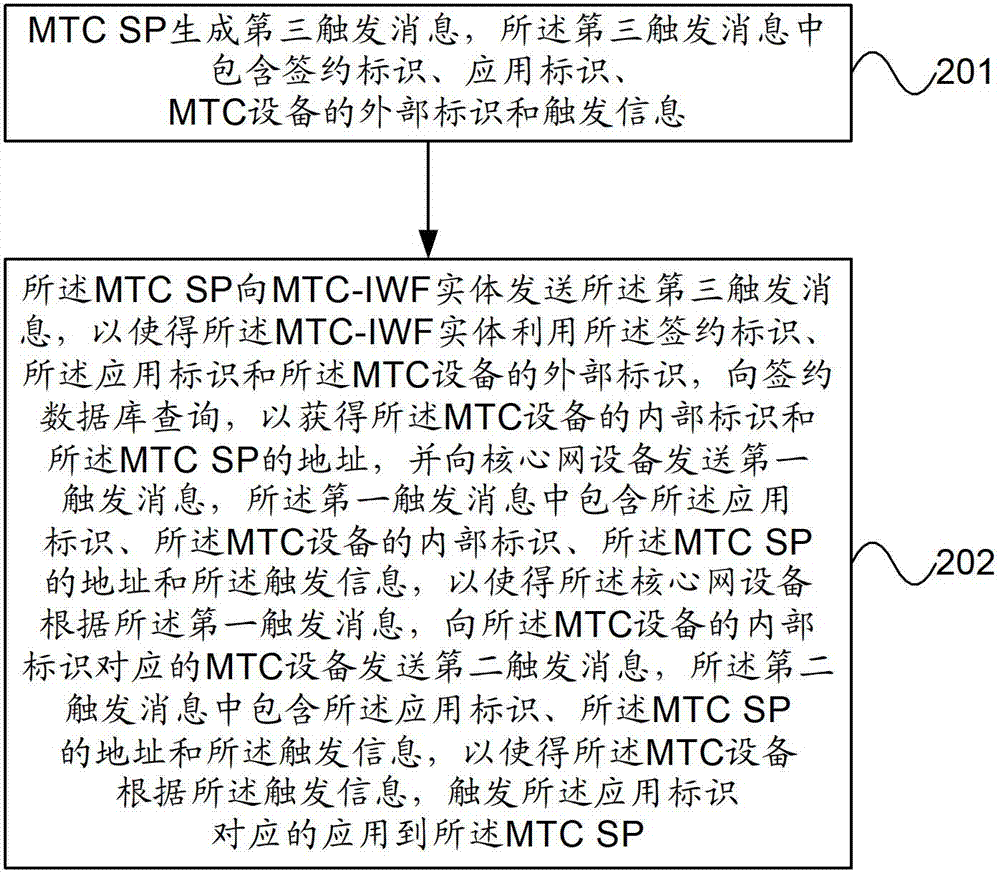
Application trigger method, device and system
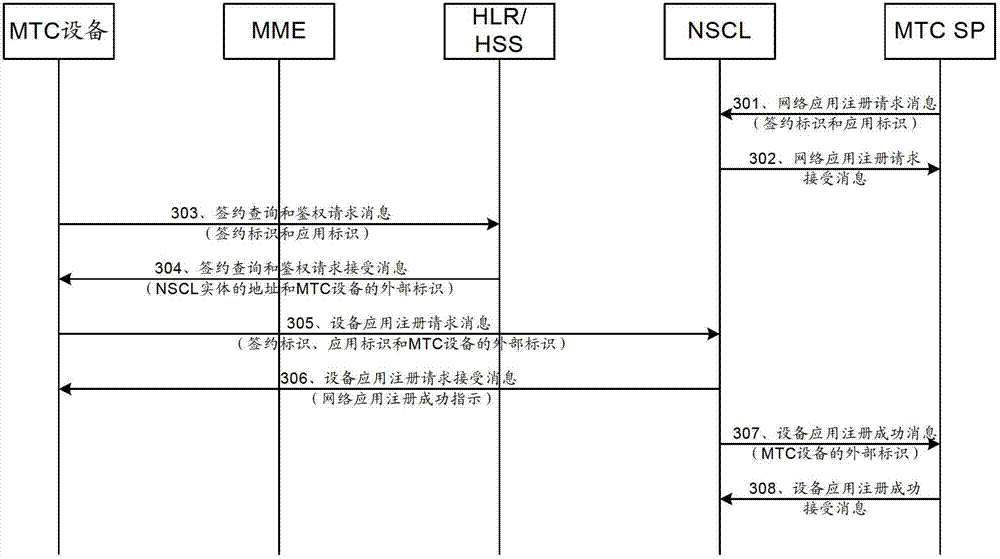
ActiveCN103685172BTransmissionMachine-to-machine/machine-type communication serviceInternal identifierSoftware engineering
This application provides an application triggering method, device, and system. In the embodiment of the present application, the MTC service is triggered by the MTC SP using the subscription ID, the application ID, and the external ID of the MTC device. Since the trigger message contains the internal ID of the MTC device and the application ID, the mobility management device can The received trigger message records the internal identifier of the MTC device and the application identifier, so that the core network device can control and manage the application triggered by the MTC device.
Owner:HUAWEI DEVICE CO LTD
An authentication method, device and system for preventing a lock from being copied, and an electronic key
ActiveCN109326018BSolve the problem of artificial illegal copyingEliminate problems integrating into lock management systemsIndividual entry/exit registersEmbedded systemAuthentication
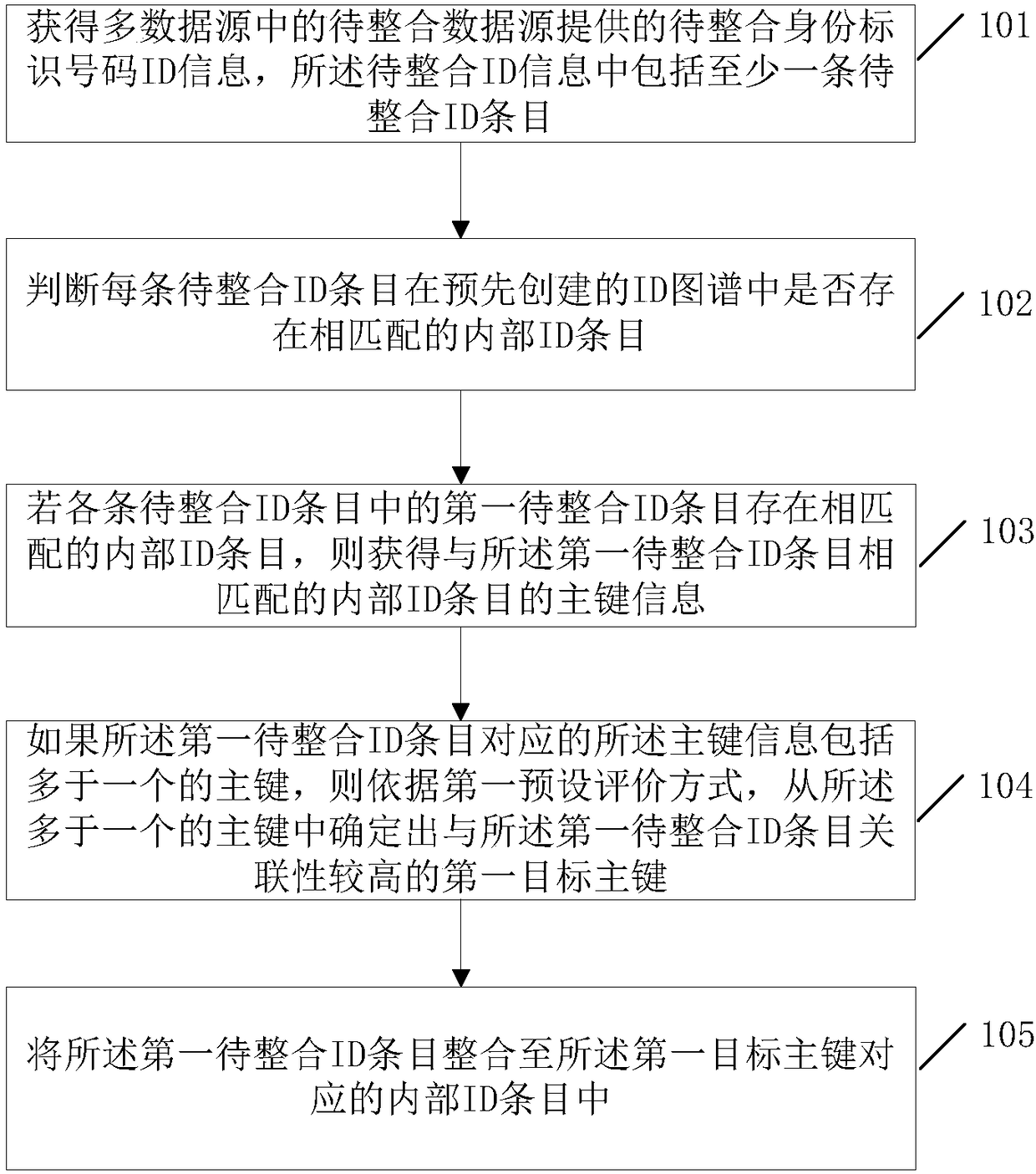
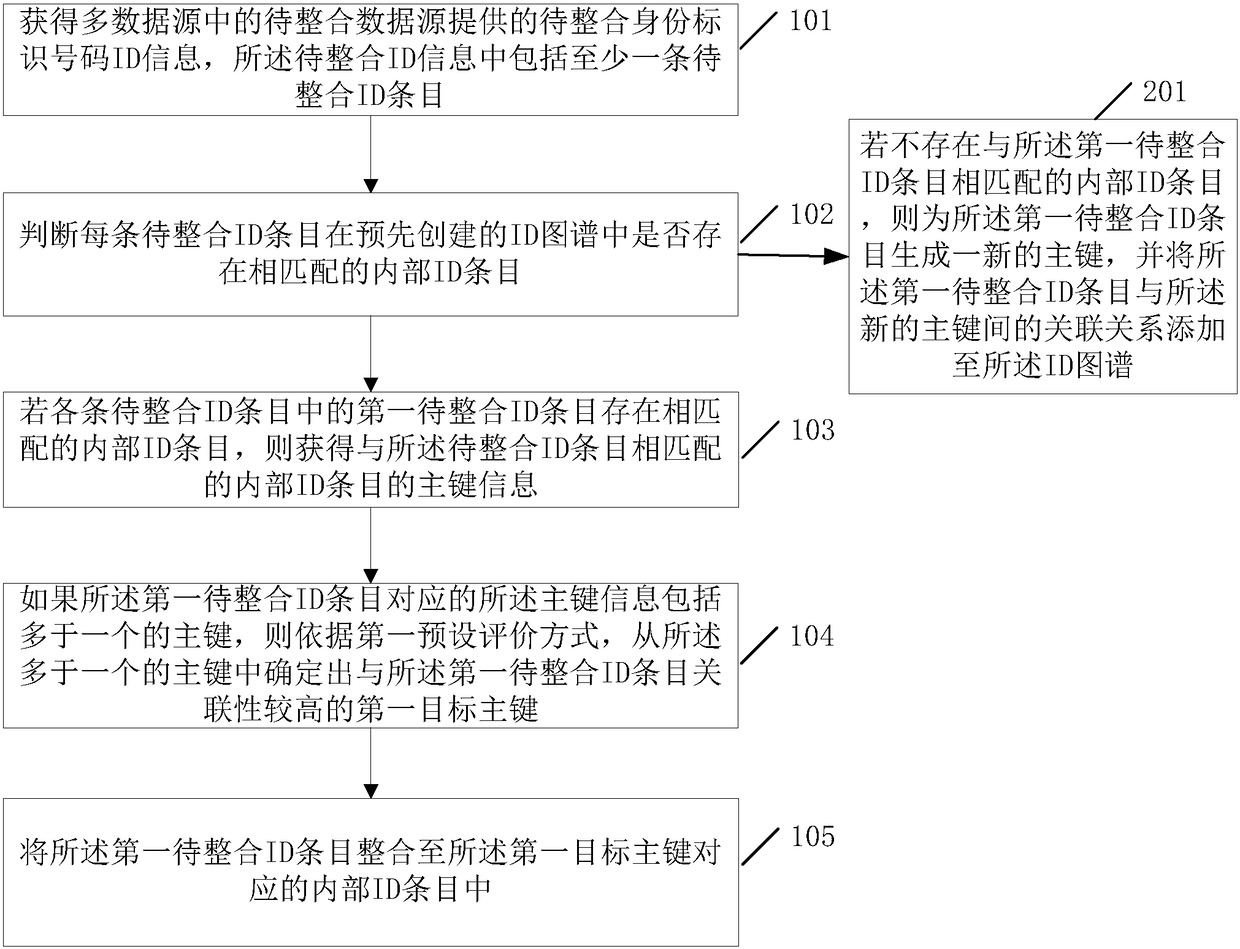
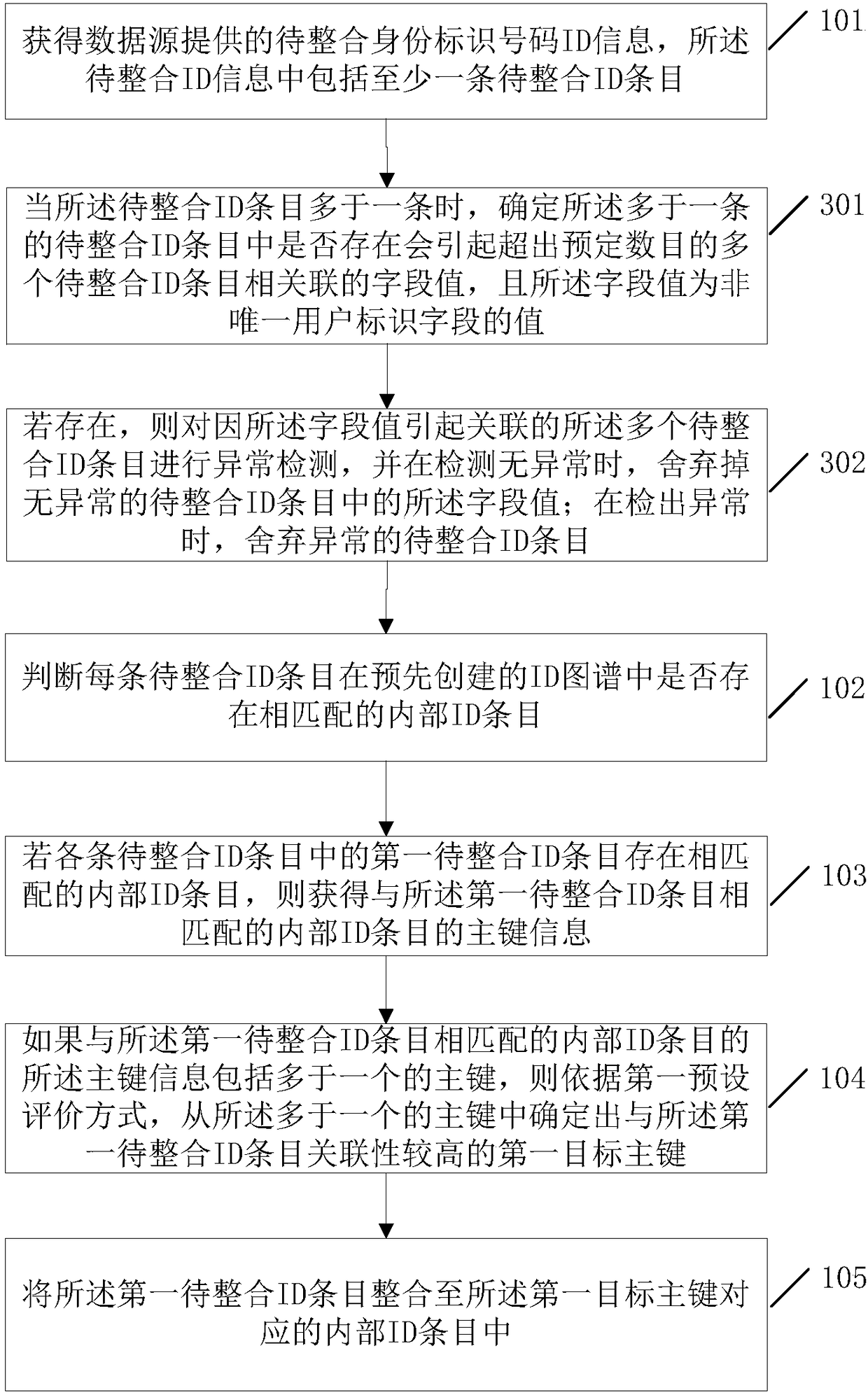
The invention relates to an authentication method, device and system for preventing a lock from being duplicated, and an electronic key for preventing the lock from being duplicated. The authentication method comprises the steps that the electronic key judges whether the accessed lock is an intelligent lock or not, when it is judged that the accessed lock is the intelligent lock, power supplying is conducted on the intelligent lock, and a communication secret key of the intelligent lock is obtained; whether the obtained communication secret key of the intelligent lock is correct or not is verified, and when it is verified that the obtained communication secret key of the intelligent lock is correct, the type of the intelligent lock is obtained; whether the obtained type of the intelligentlock is correct or not is judged, and when it is judged that the obtained type of the intelligent lock is correct, internal ID of the intelligent lock is obtained; and whether the obtained internal IDof the intelligent lock is correct or not is judged, and the obtained internal ID of the intelligent lock is correct and is target ID, the lock is authenticated successfully. According to the authentication method, device and system for preventing the lock from being duplicated, and the electronic key for preventing the lock from being duplicated, the problem that the intelligent lock is duplicated artificially and illegally is effectively solved, and thus the problem that a counterfeit lock or intelligent lock is merged into a lock management system is effectively eradicated.
Owner:ZHUHAI UNITECH POWER TECH CO LTD
Modulation device, light emitting device, and light emission system
ActiveUS9831949B2Transmission systemsSynchronisation by photonic/optical meansEngineeringControl circuit
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
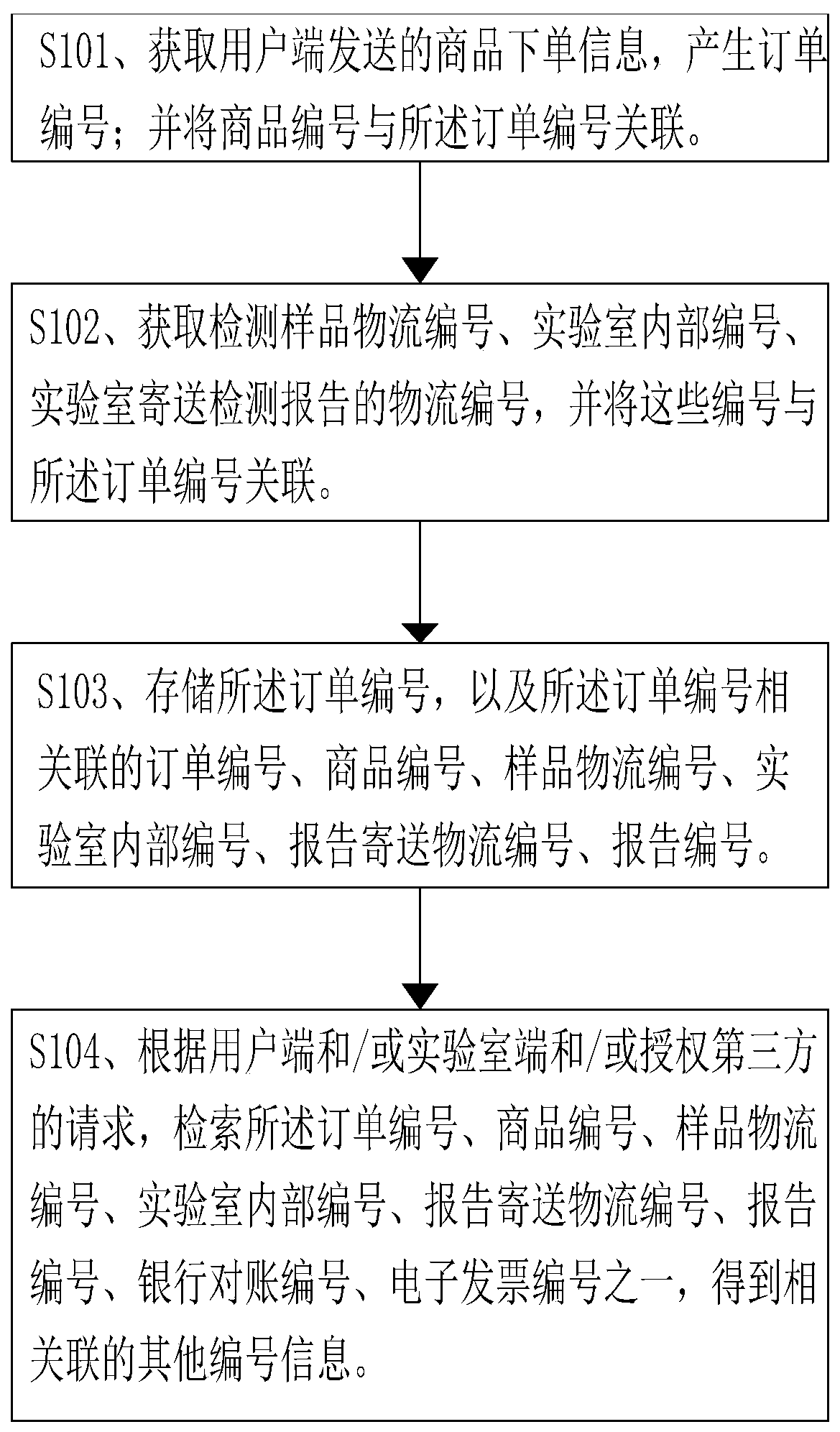
Number association method, server and user side
The invention provides a number association method, a server and a user side, and the method comprises the steps: obtaining commodity ordering information transmitted by the user side, generating an order number, and the commodity number being associated with the order number; obtaining a detection sample logistics number, and associating the detection sample logistics number with the order number; obtaining a laboratory internal number of the order compiled in the laboratory, and associating the internal number with the order number; and obtaining a logistics number of a laboratory sending detection report, and associating the logistics number with the order number. According to the number association method, number data of all links can be integrated and detected in a unified mode, and conditions of all detection processes are provided for users and laboratories in time.
Owner:上海百检网络技术有限公司
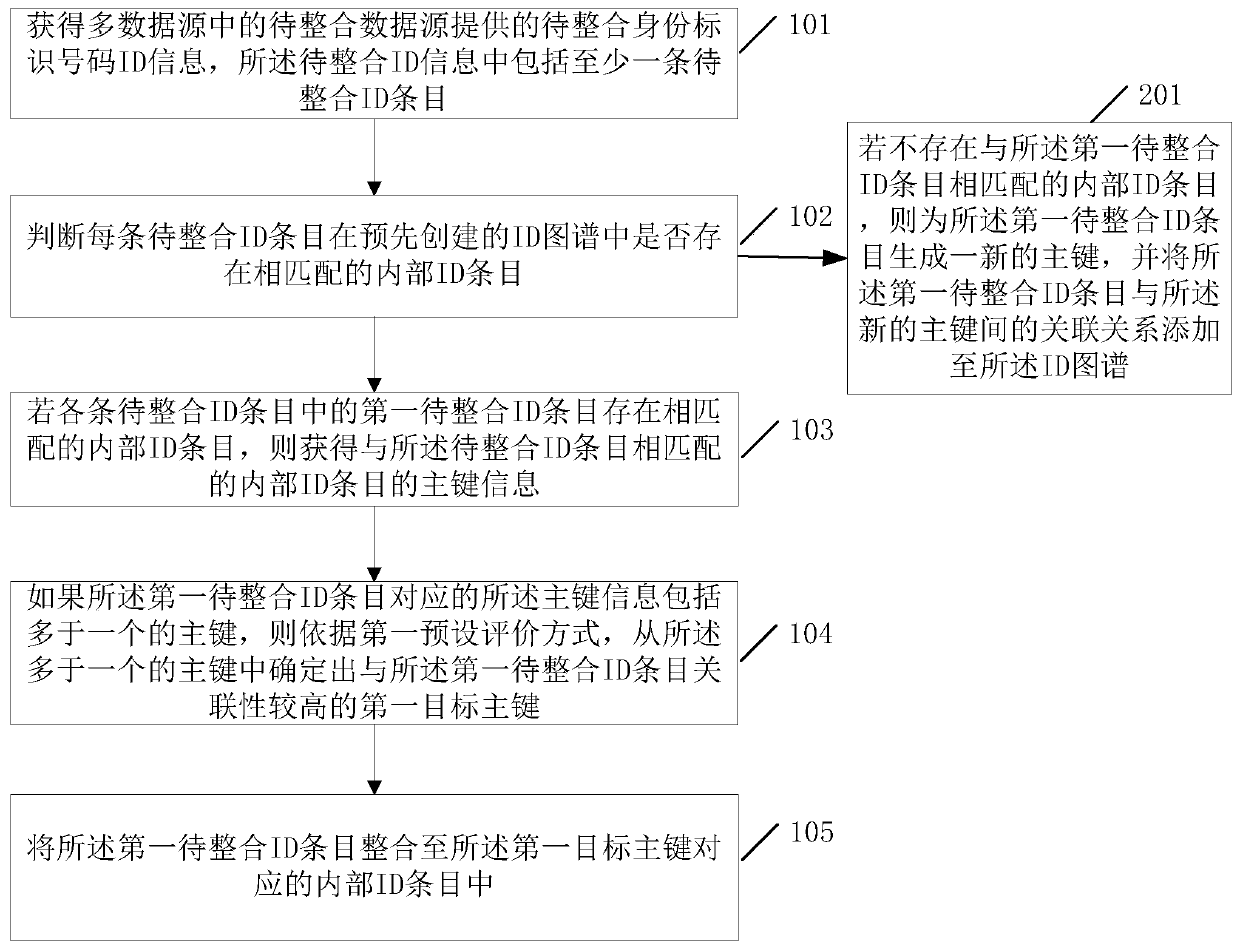
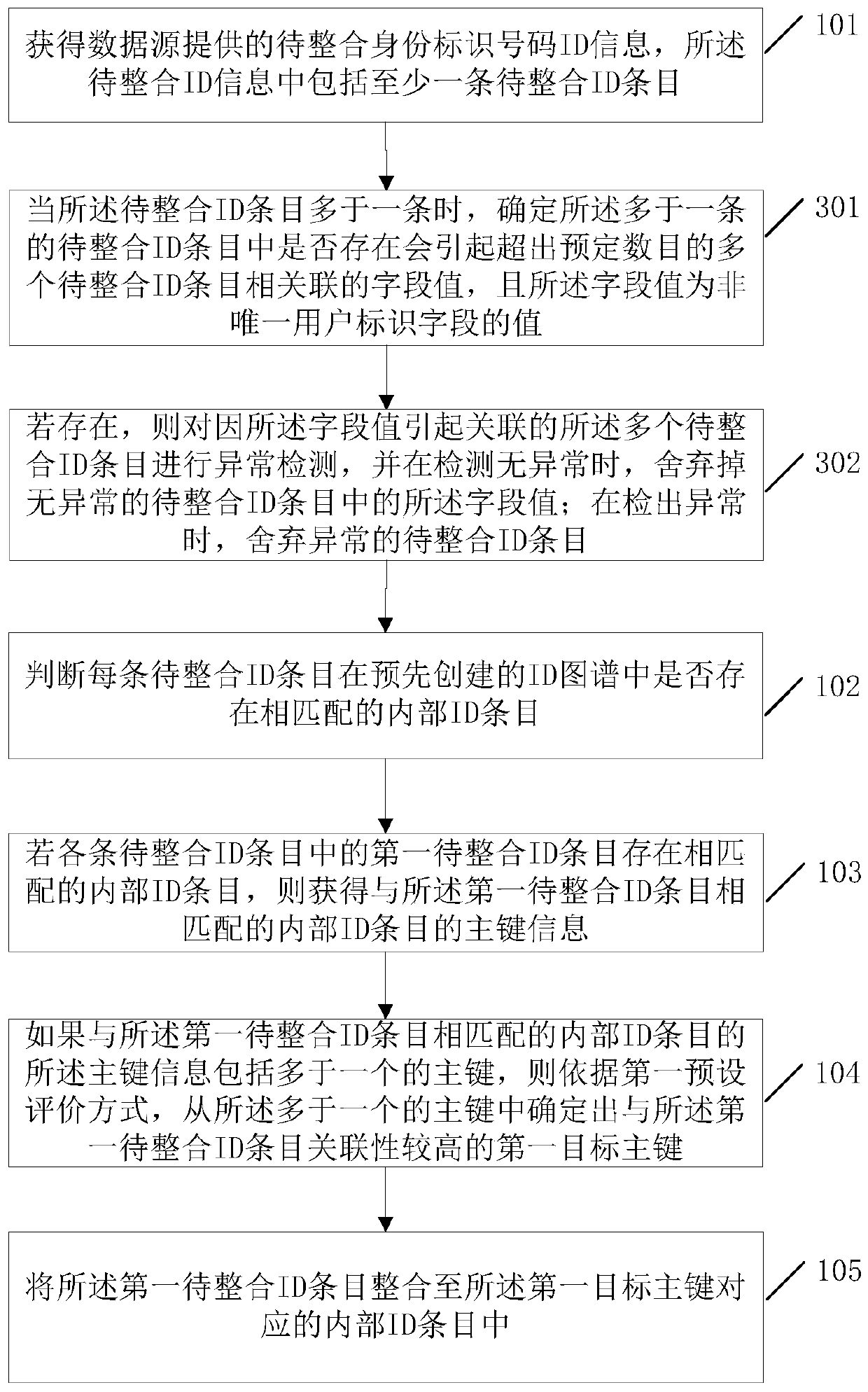
A method and device for integrating user information from multiple data sources
ActiveCN108664480BSolving recognition problemsEfficient integrationDatabase modelsSpecial data processing applicationsData sourceEngineering
The invention discloses a multi-data source user information integration method and device. In the method, when the ID entry to be integrated matches more than one primary key in the ID map, the ID entry to be integrated matches more than one primary key in the ID map. According to the first preset evaluation method, determine the first target primary key with the highest correlation with the ID entry to be integrated from the more than one primary key, and integrate the ID entry to be integrated In the internal ID entry corresponding to the first target primary key, the IDs to be integrated that are matched to more than one primary key / internal ID entry in the ID map are finally realized to be effectively integrated and associated into the ID map, Thus, the present invention solves the problem that the prior art cannot effectively integrate and normalize such entries (entries to be integrated that match multiple internal ID entries in the ID map), and on this basis, it can further effectively solve the problem of multi-data source user Identify the problem.
Owner:BEIJING GRIDSUM TECH CO LTD
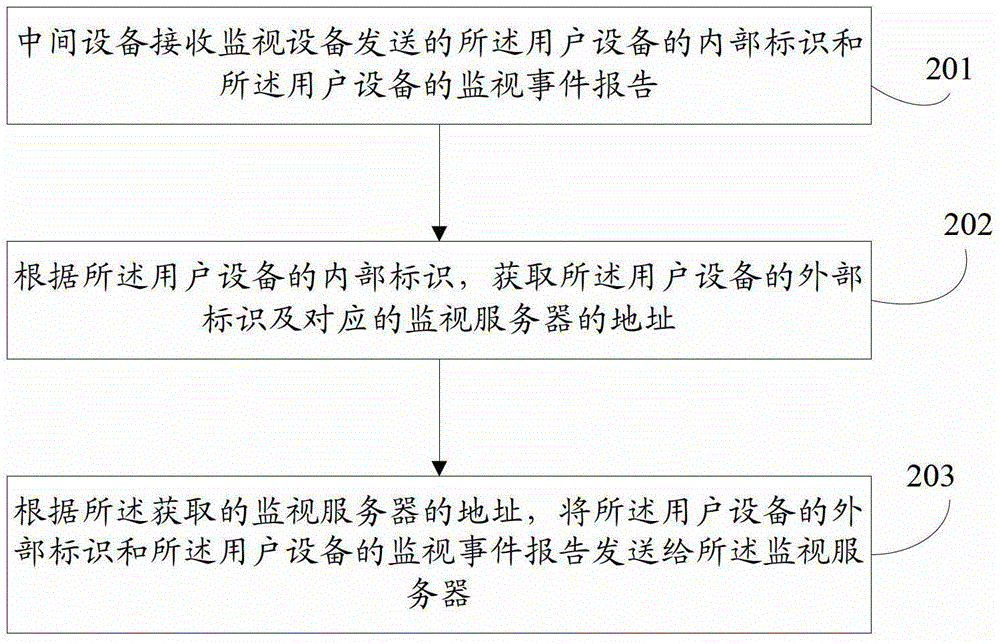
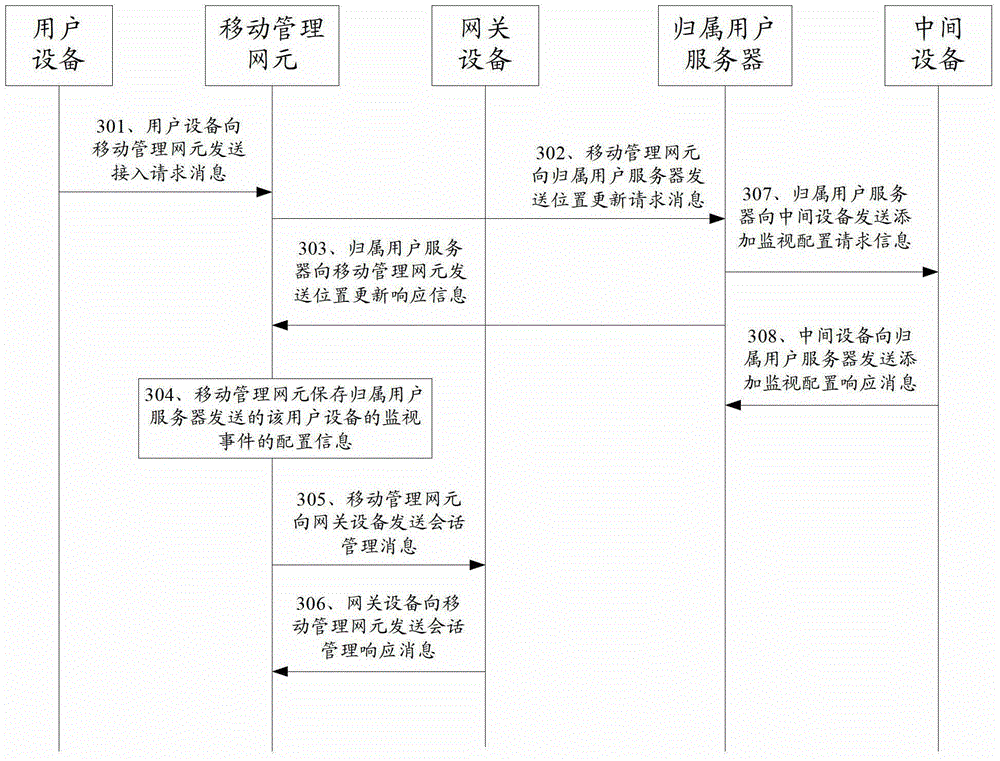
User equipment information monitoring method, device and system
ActiveCN103716833BImprove sending accuracyImprove network securityWireless communicationUser equipmentComputer science
The embodiment of the present invention discloses a user equipment information monitoring method, device, and system, wherein the method includes: the monitoring equipment detects a monitoring event of the user equipment that needs to be monitored, and generates a monitoring event report of the user equipment; according to the The internal identification of the user equipment determines the intermediate device that forwards the monitoring event report of the user equipment; sends the internal identification of the user equipment and the monitoring event report of the user equipment to the intermediate device, so that the intermediate device according to the The internal identifier of the user equipment, obtain the external identifier of the user equipment and the address of the corresponding monitoring server, and report the external identifier of the user equipment and the monitoring event of the user equipment according to the obtained address of the monitoring server Sending to the monitoring server; can improve the sending accuracy rate of the monitoring event report of the user equipment.
Owner:HUAWEI TECH CO LTD
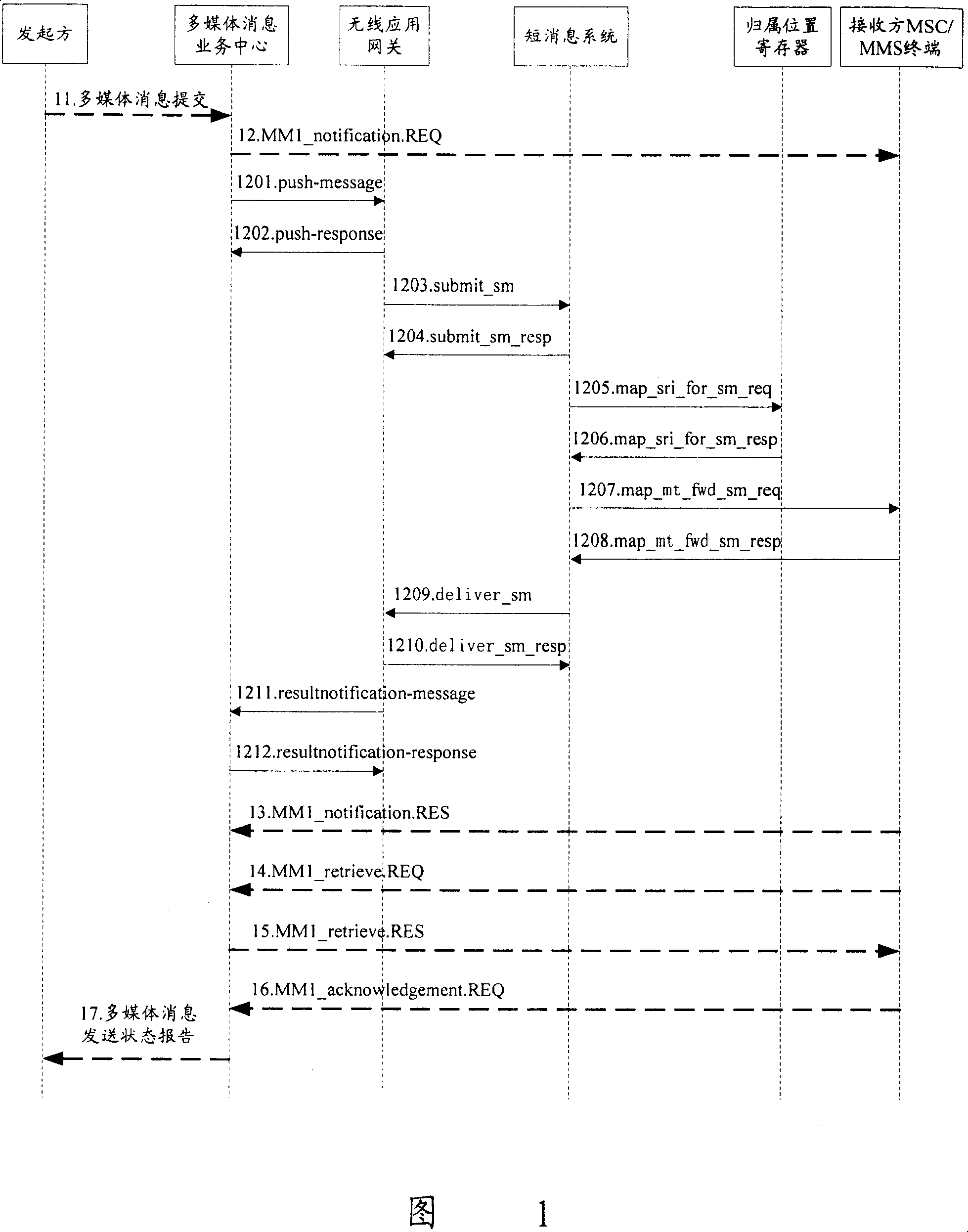
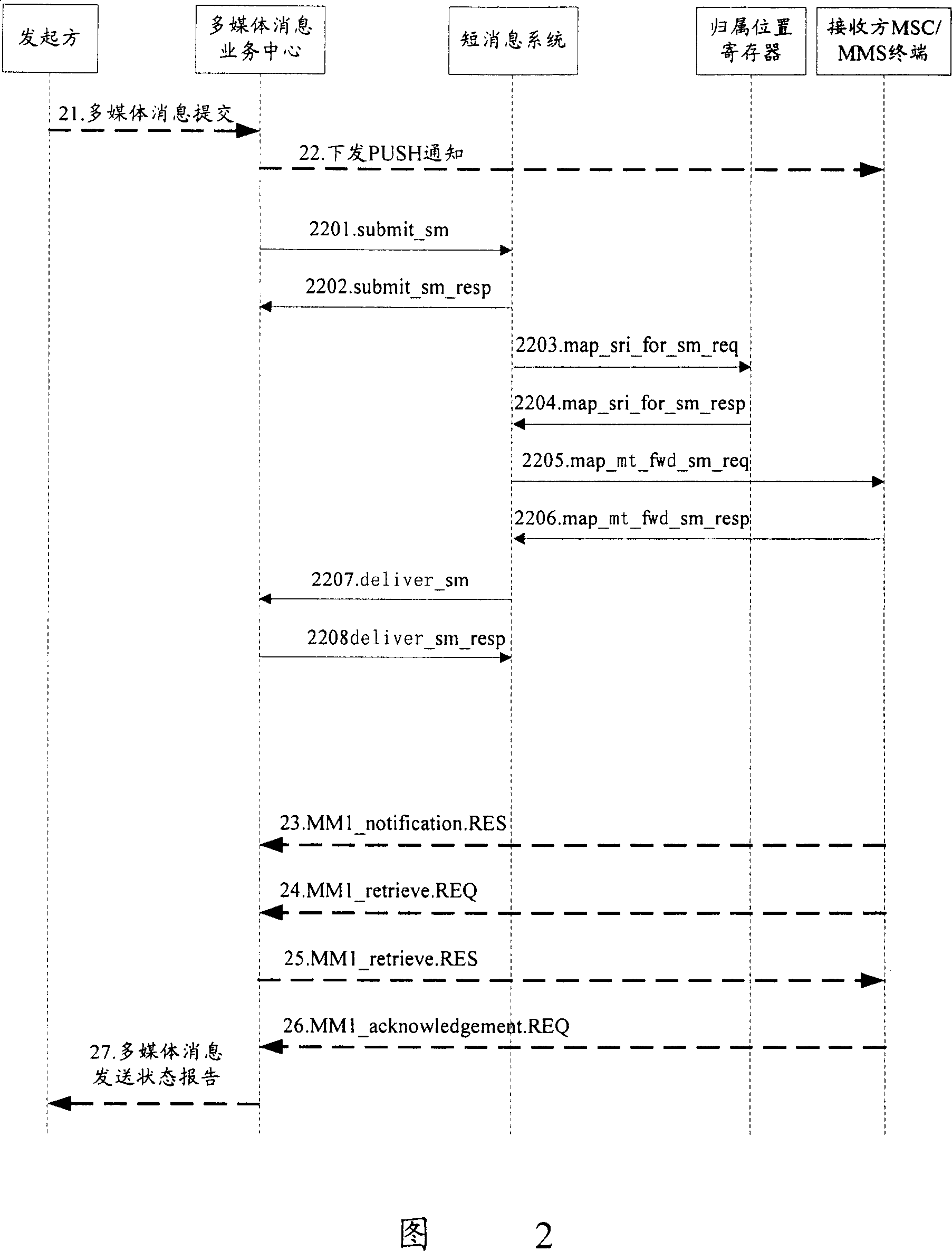
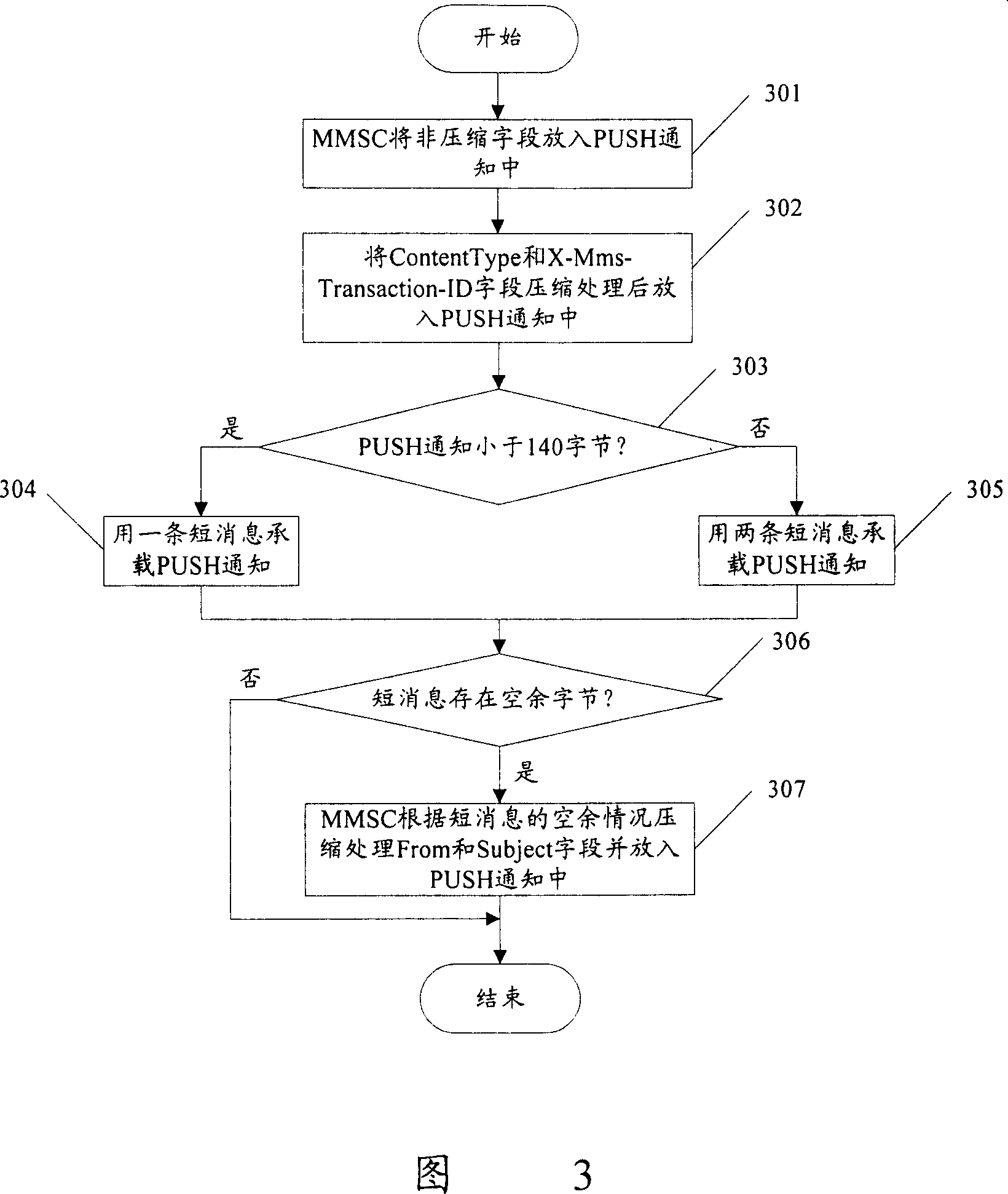
Processing method for sending out notice in multimedia message service
ActiveCN100349474CIntegrity guaranteedShorten the lengthRadio/inductive link selection arrangementsMessaging/mailboxes/announcementsMessage typeByte
The invention discloses a method for processing a PUSH notification, including: placing non-compressible fields into the Push notification and placing into the PUSH notification a field signifying message type and a field of internal ID after the fields are compressed; determining whether the PUSH notification may be carried in one short message; if yes, having the PUSH notification carried in one short message; otherwise, having the PUSH notification carried in two short messages; determining whether there are any unoccupied bytes in the short message; if yes, determining whether to place the initiator From field into the PUSH notification according to the number of the unoccupied bytes in the short message, and determining whether to compress Subject field and place the Subject field into the PUSH notification; otherwise, terminating the processing flow of the PUSH notification. The present invention may have the PUSH notifications carried in two short messages at most.
Owner:徐州博创建设发展集团有限公司
Anti-counterfeiting method for network terminal device
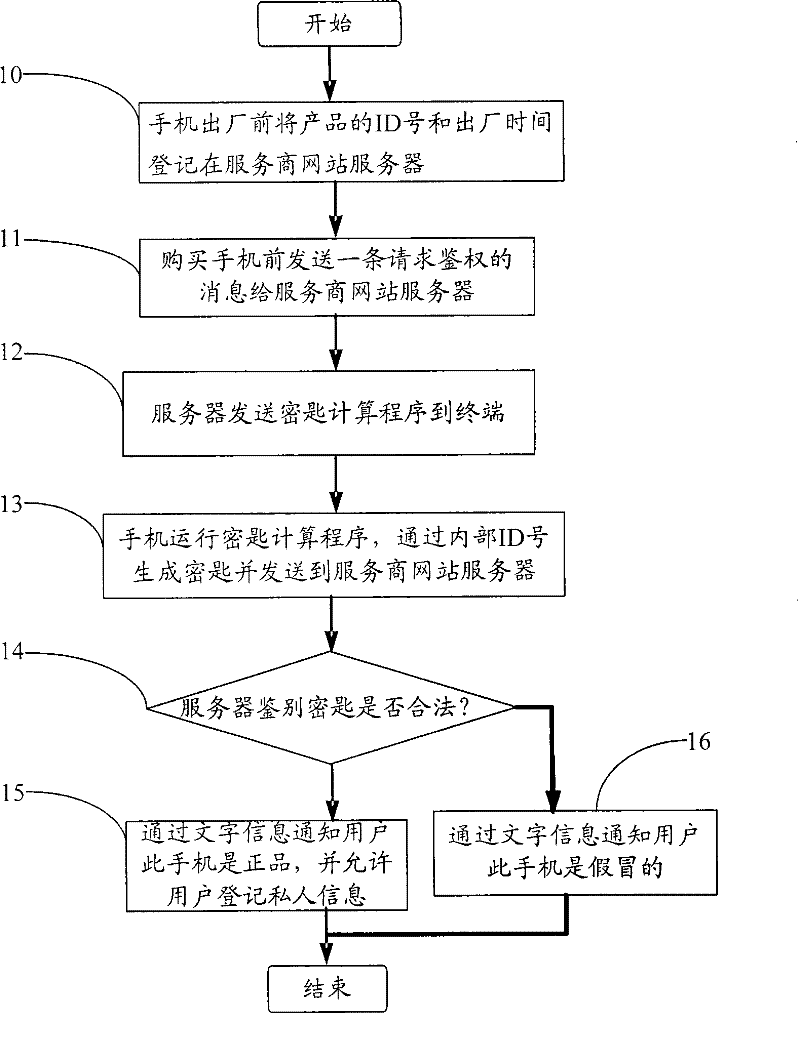
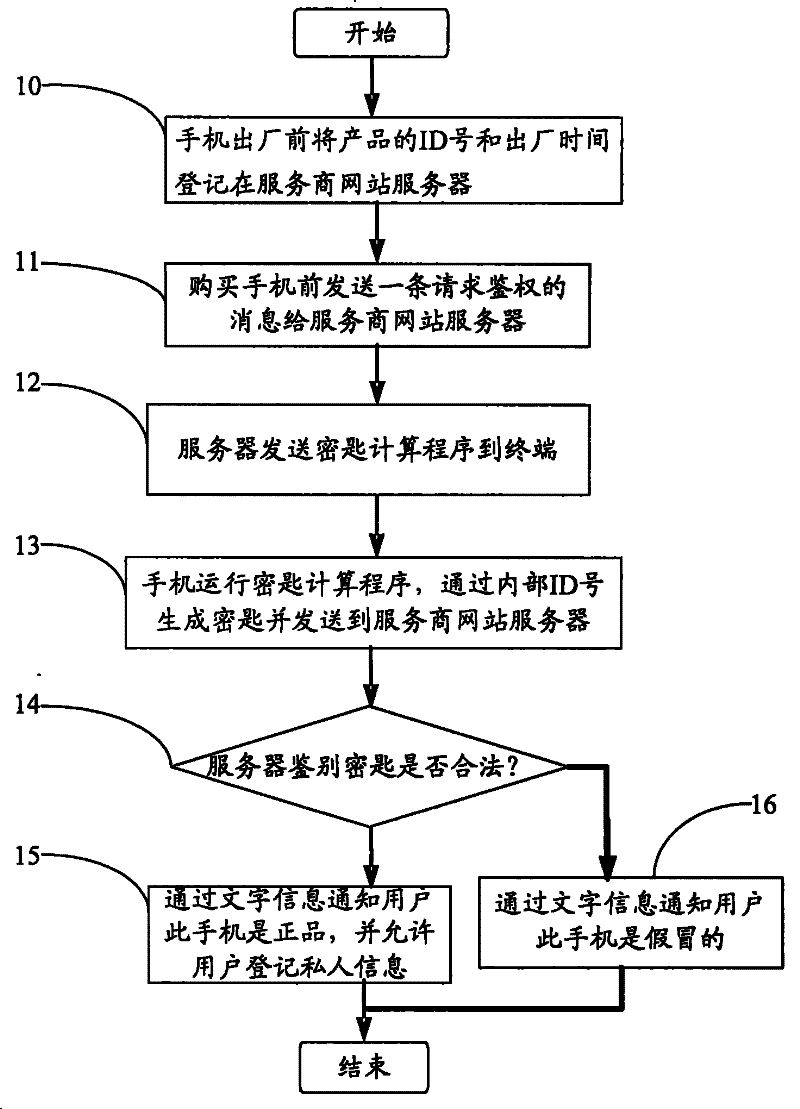
InactiveCN101730276BEnsure safetyHas practical valueUser identity/authority verificationWireless network protocolsTerminal equipmentComputer terminal
The invention provides an anti-counterfeiting method for a network terminal device. The anti-counterfeiting method comprises the following steps that: a, before the network terminal device leaves a factory, an ID number and the leave-factory time corresponding to the network terminal device are stored in the network terminal device and registered in a web server of a service provider; b, a consumer transmits a message of requesting authorization to the web server of the service provider before purchasing a mobile phone; c, the server transmits a key calculation program to the network terminaldevice; d, the network terminal device operates the key calculation program, generates a key through an internal ID number and transmits the key to the web server of the service provider; and e, the web server of the service provider identifies whether the key is legal and feeds an identification result back to the network terminal device. The anti-counterfeiting method for the network terminal device finishes the key identification through both of the network terminal device and the web server of the service provider. The anti-counterfeiting method for the network terminal device has the advantages of security guarantee and high practical value.
Owner:TCL CORPORATION
Method and system for quickly migrating multi-source heterogeneous power grid big data to hbase
ActiveCN106528786BReduce overheadMulti-transportRelational databasesDatabase distribution/replicationArray data structureData platform
The invention discloses a method and system for rapidly transferring multi-source heterogeneous power grid big data to HBase. The method includes the following steps that a power grid database is connected with an HBase data platform; each datum in the power grid database has a unique mark ID and is composed of the mark ID and data content; according to unique mark IDs, an ID mapping table is established; after a data source is selected, the ID mapping table is read and written into a memory for residence; codes in the ID mapping table are each compressed, so that data class ID row keys and data class internal ID row keys are formed; the data class ID row keys and the data class internal ID row keys are converted into a byte array; the data class ID row keys, the data class internal ID row keys and the row name qualifier of HBase are written into an HBase table in a byte form. Rapid transferring is achieved for a complex electric power data format through the method and system.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com