Patents
Literature
40results about How to "Remove burden" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
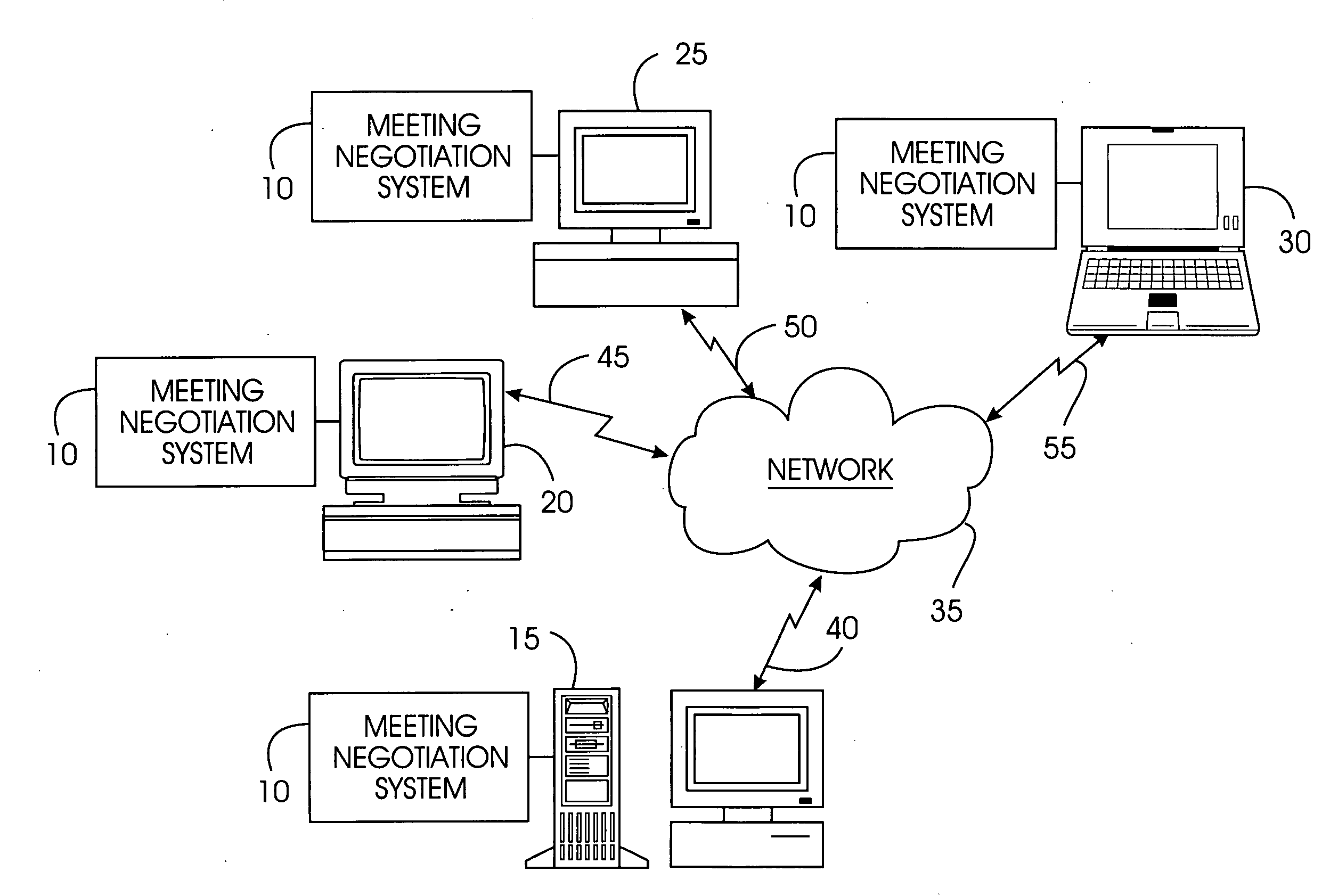
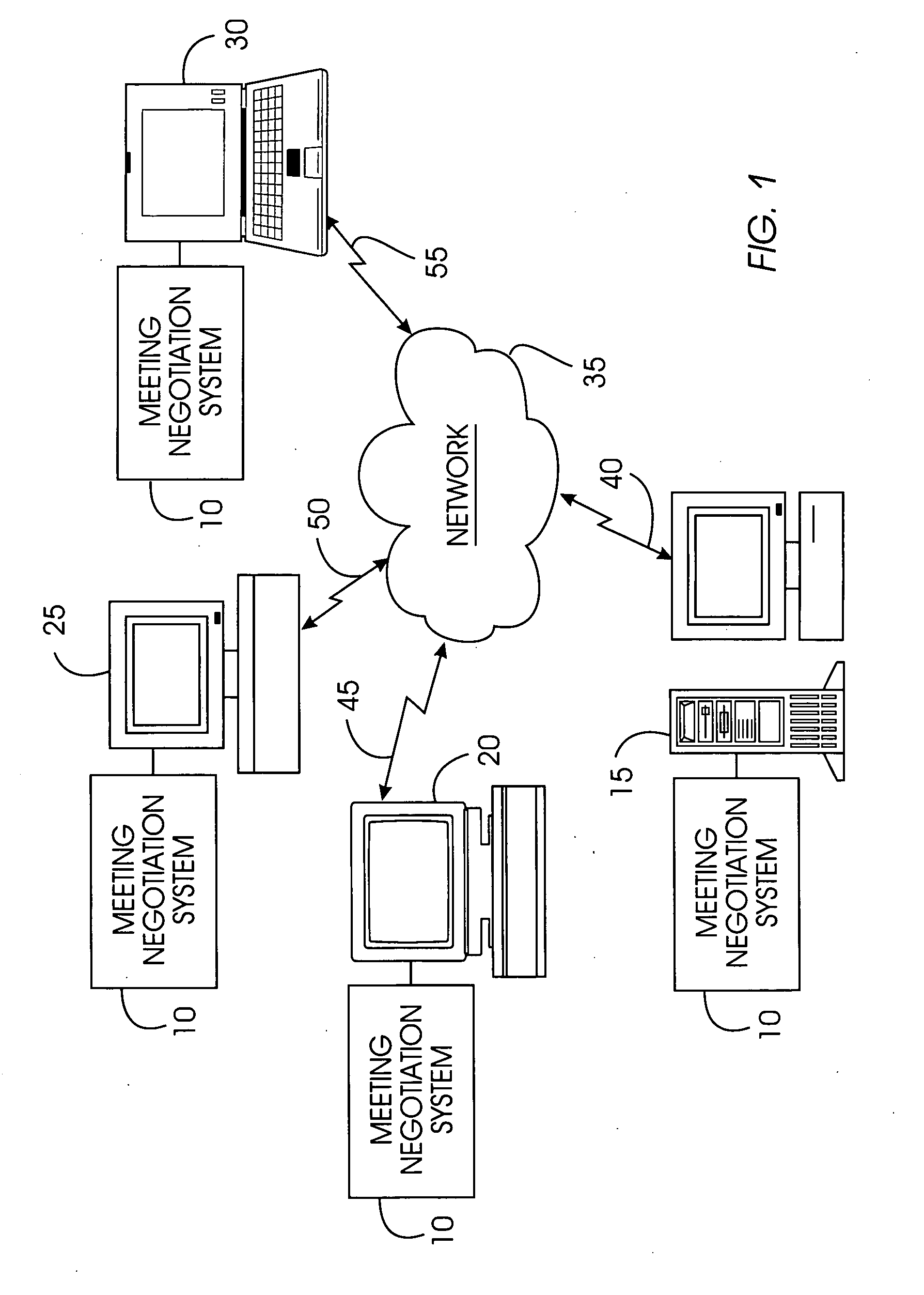
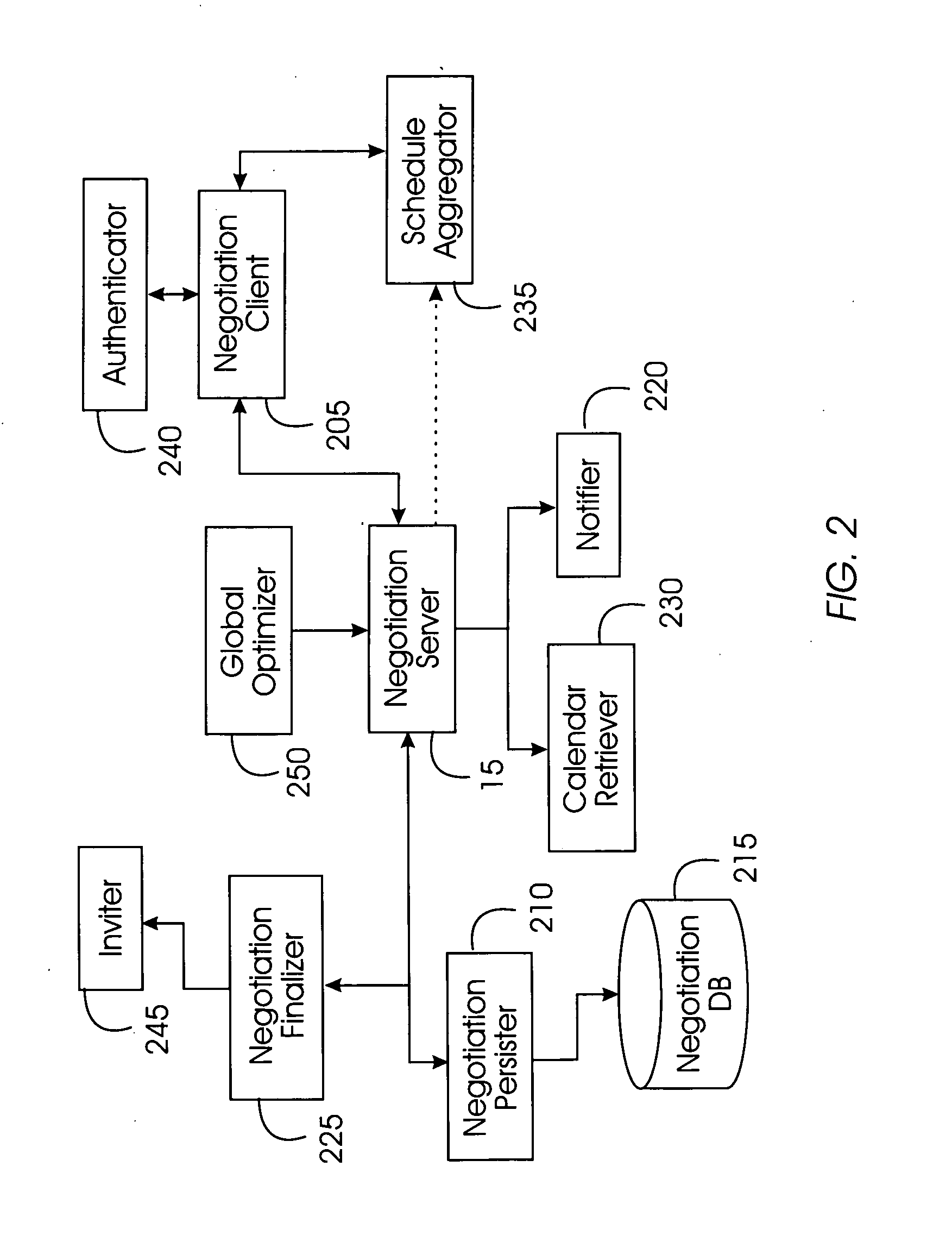
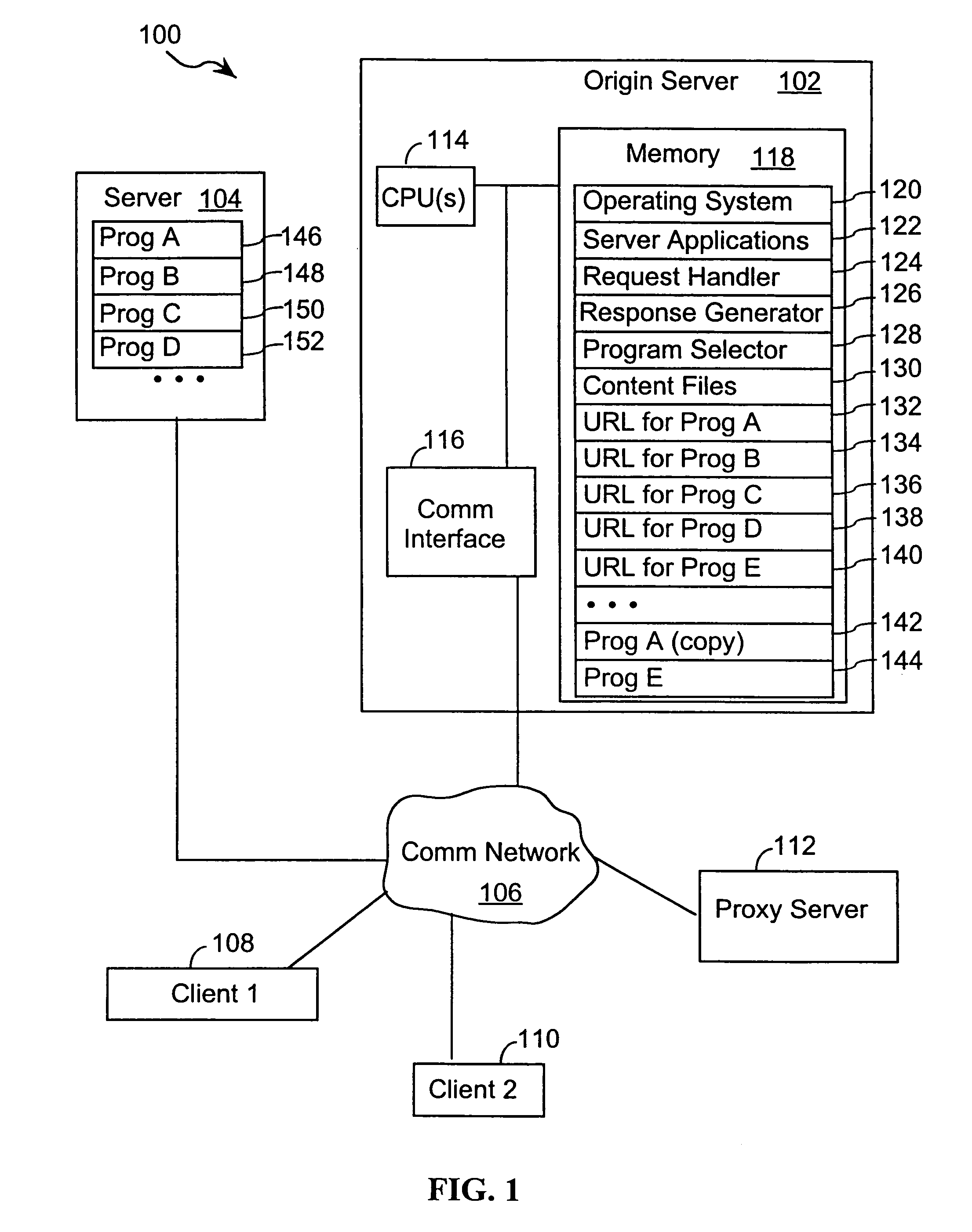
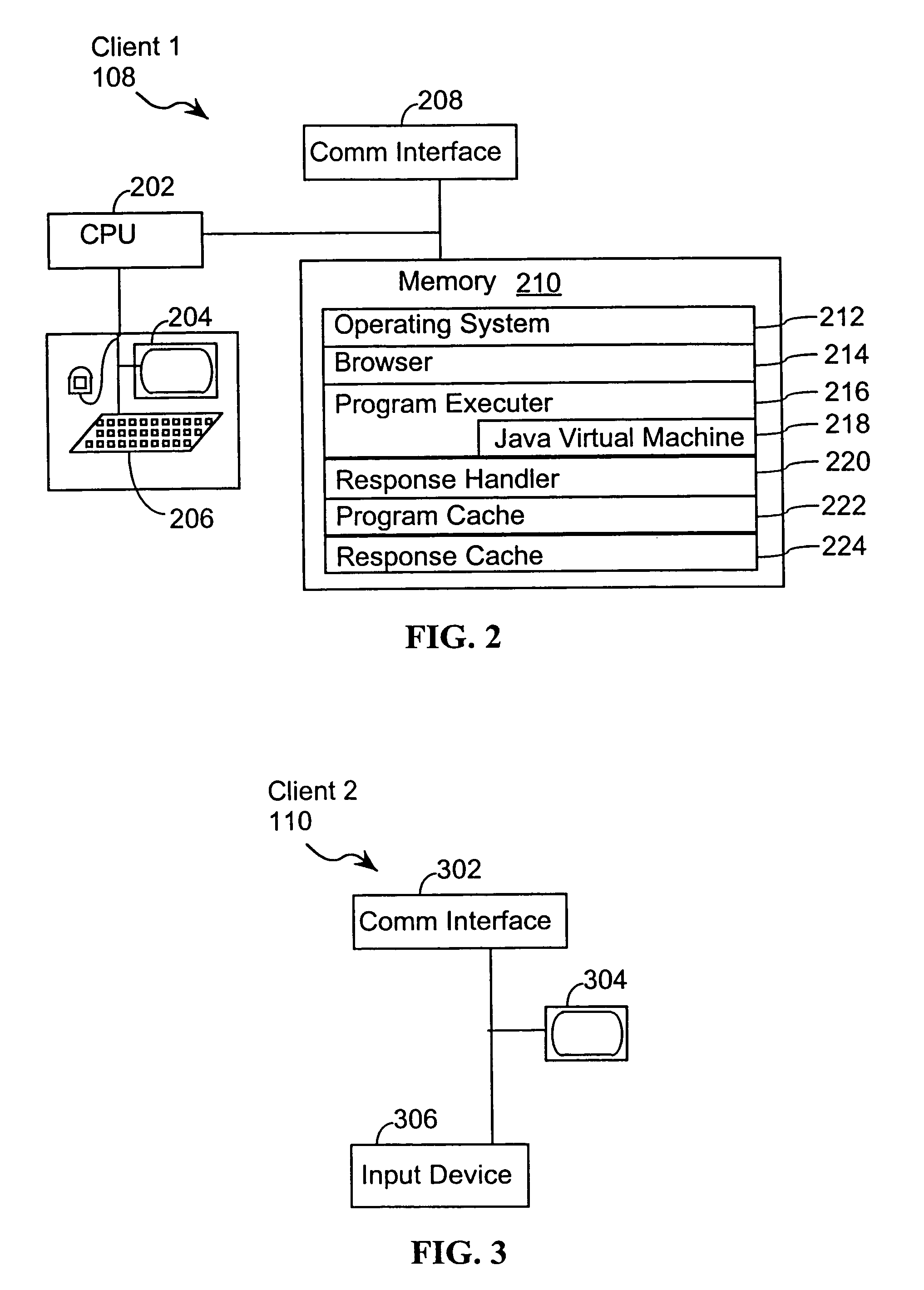
System, method, and service for negotiating schedules while preserving privacy through a shared representation
InactiveUS20050102245A1Large basePrivacy protectionDigital computer detailsPayment architectureTime scheduleBusy time
A meeting negotiation system provides a new approach to scheduling events by negotiating schedules while preserving privacy through a shared representation that separates the meeting negotiation from the meeting invitation. The negotiation system integrates all scheduling-related information such as times users can meet, location, etc. and reduces dependency on designations of time as free or busy by a potential meeting attendee. Consequently, the negotiation system enables time preferences richer than just free or busy, allowing potential meeting attendees to designate preference in addition to time available. The negotiation system supports annotations and comments as a discussion mechanism, giving feedback to the meeting scheduler before the meeting invitation is issued. Possible times provided for the meeting are provided in the form of a bounded negotiation; participants may select the best time for them to attend a meeting from the bounded negotiation. The meeting organizer finalizes the meeting time from the responses provided by participants.
Owner:IBM CORP
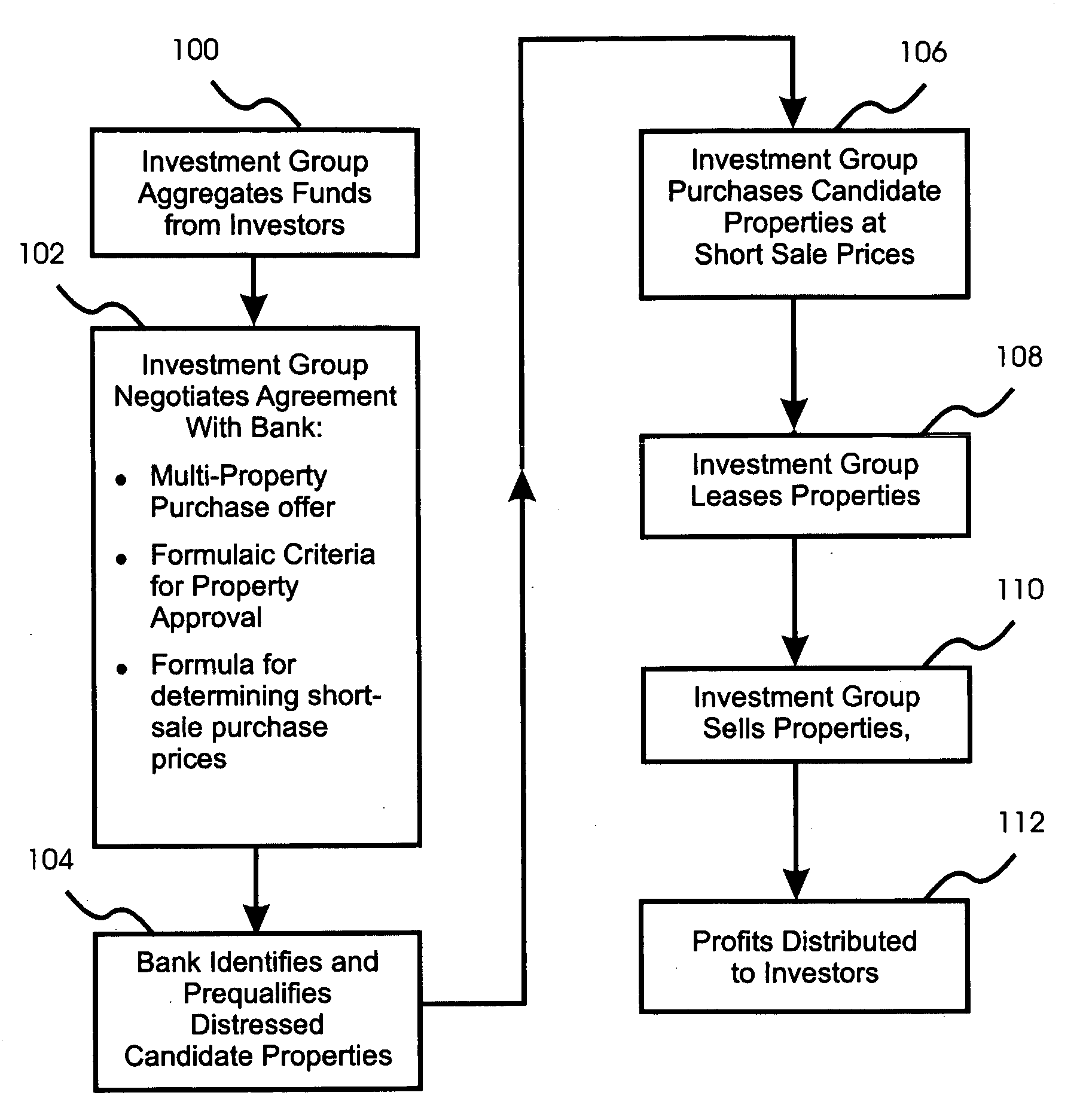
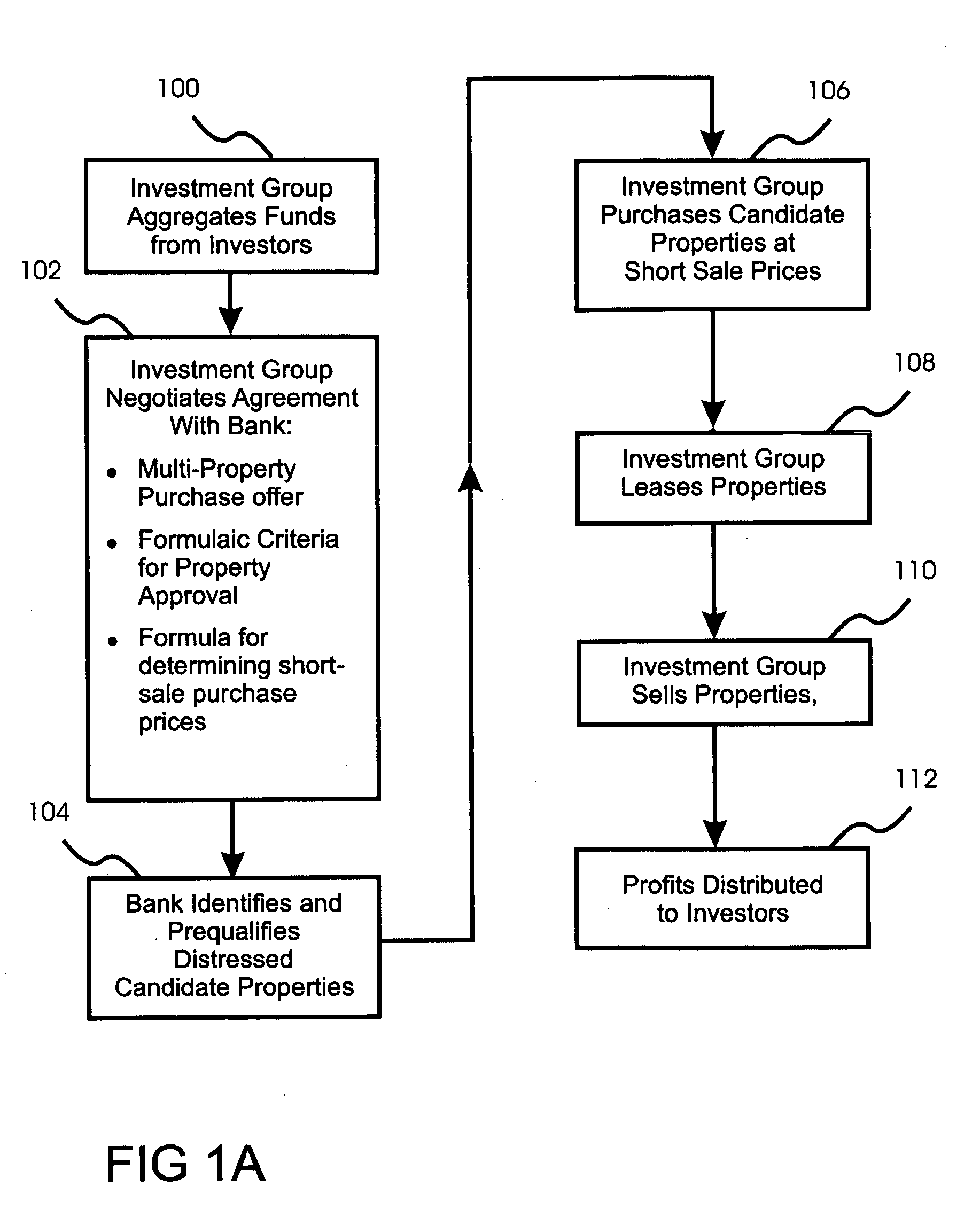
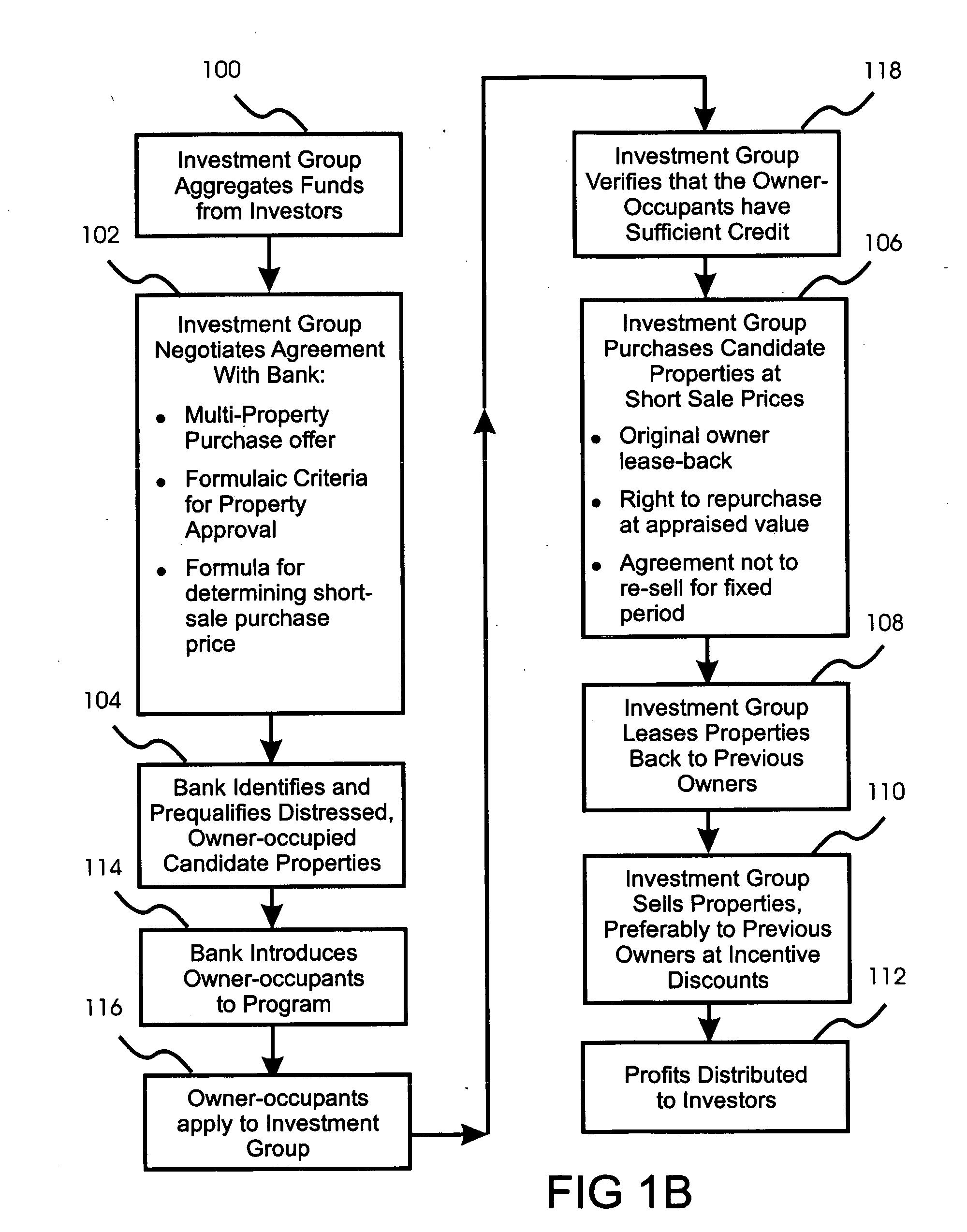
Real estate investment method for purchasing a plurality of distressed properties from a single institution at formula-derived prices
InactiveUS20100293114A1Remove the burdenRemoval can be quite burdensomeFinanceSpecial data processing applicationsSupport groupService provision
A real estate investing method is disclosed in which aggregated investment capital is used to purchase a plurality of properties from a single lending institution at short-sale prices calculated using a pre-negotiated formula. The lending institution agrees to identify and qualify properties, and accept the short-sale prices, in return for selling a plurality of distressed properties under a single agreement. Owners avoid foreclosure and consequent damage to their credit. Investors aren't burdened by property selection and / or maintenance. In preferred embodiments, owner-occupied homes are purchased, leased back to their occupants, and eventually resold to the occupants if their finances recover. Repurchase credit incentives can be offered to occupants, providing limited participation in property appreciation and motivating occupants to maintain the properties and strive to repurchase them. During leases, landlord services are provided under contract by local service providers and / or regional warranty providers. A central support group can provide centralized tenant support.
Owner:KHAN MOHAMMED SALAHUDDIN +1
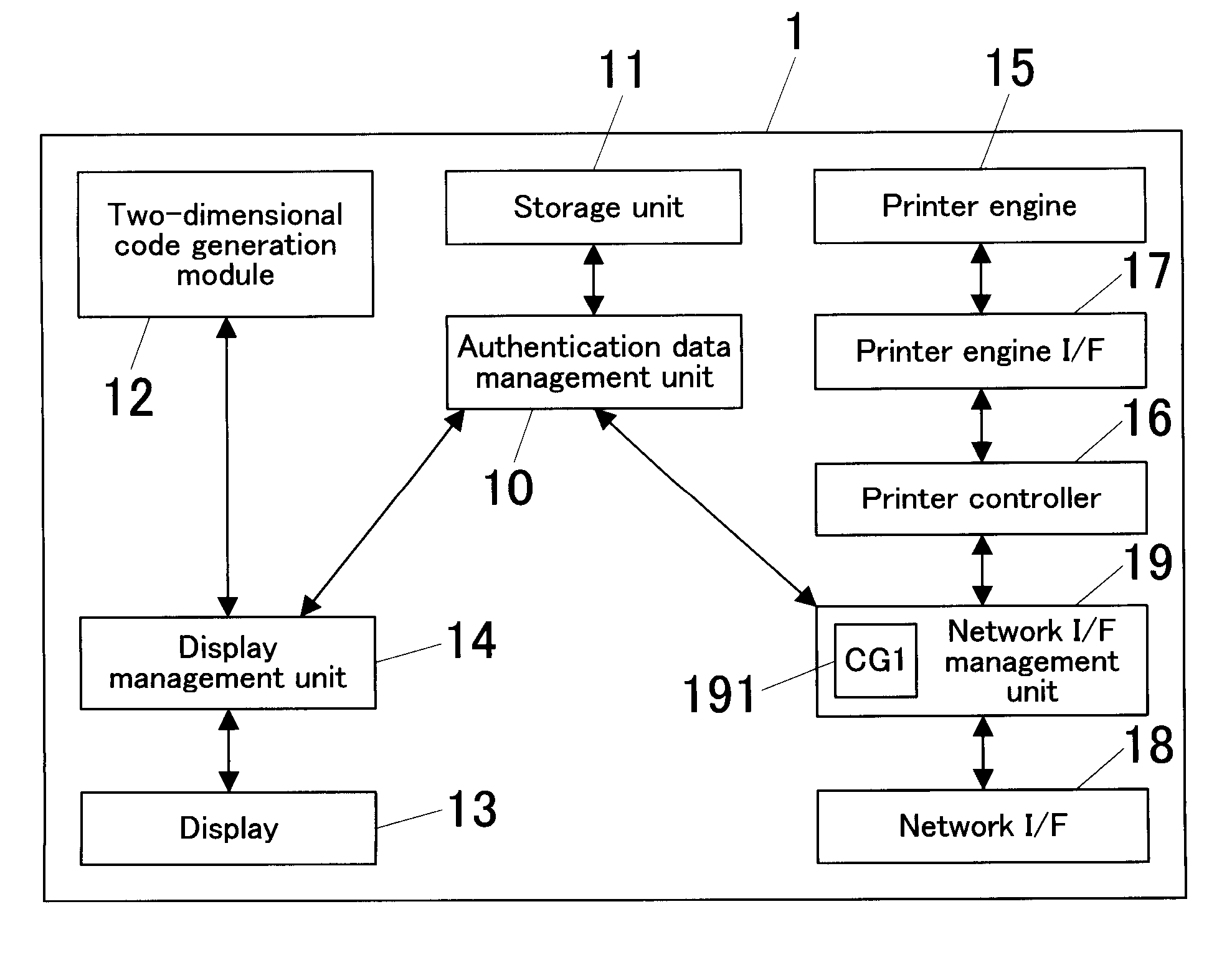
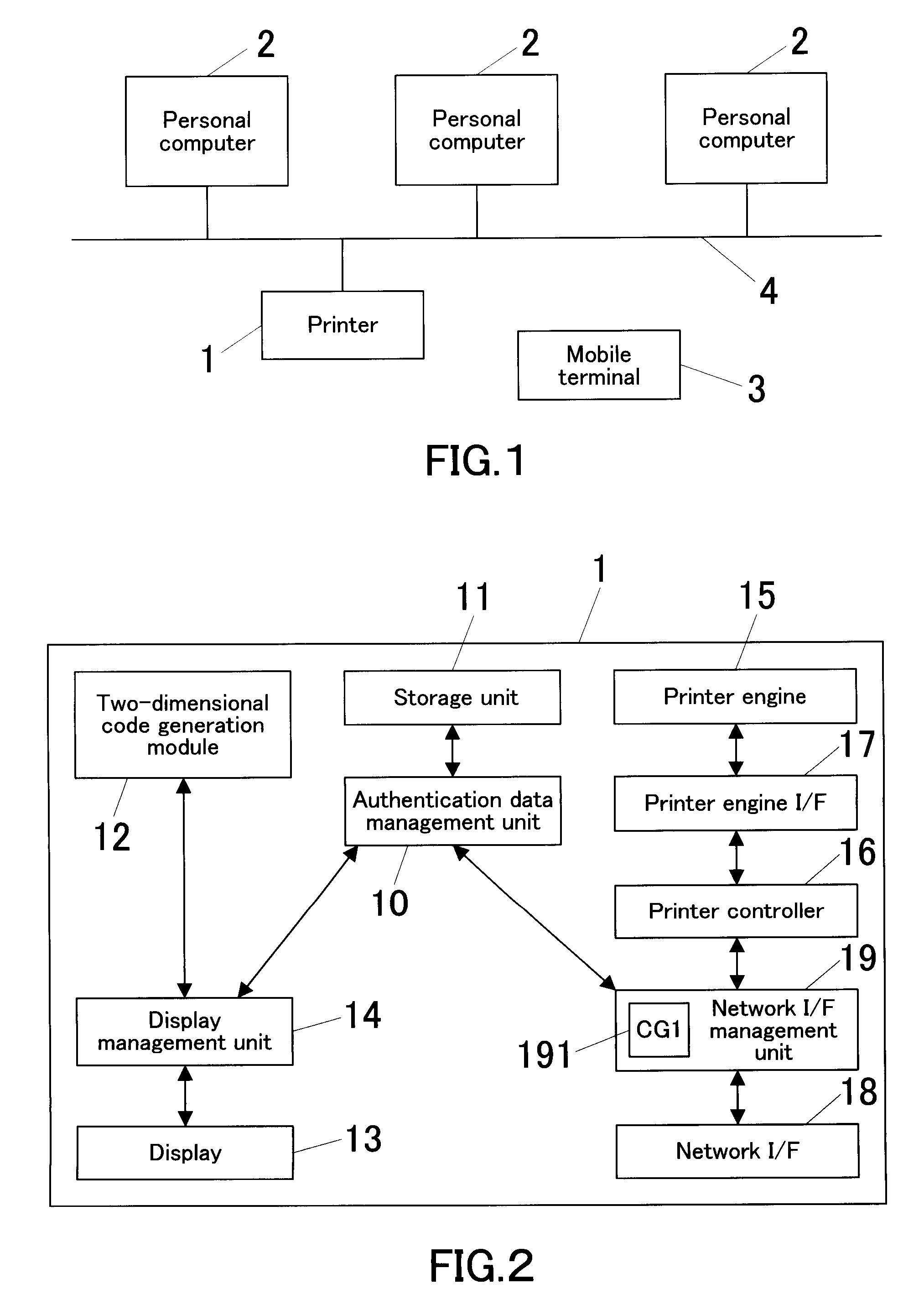
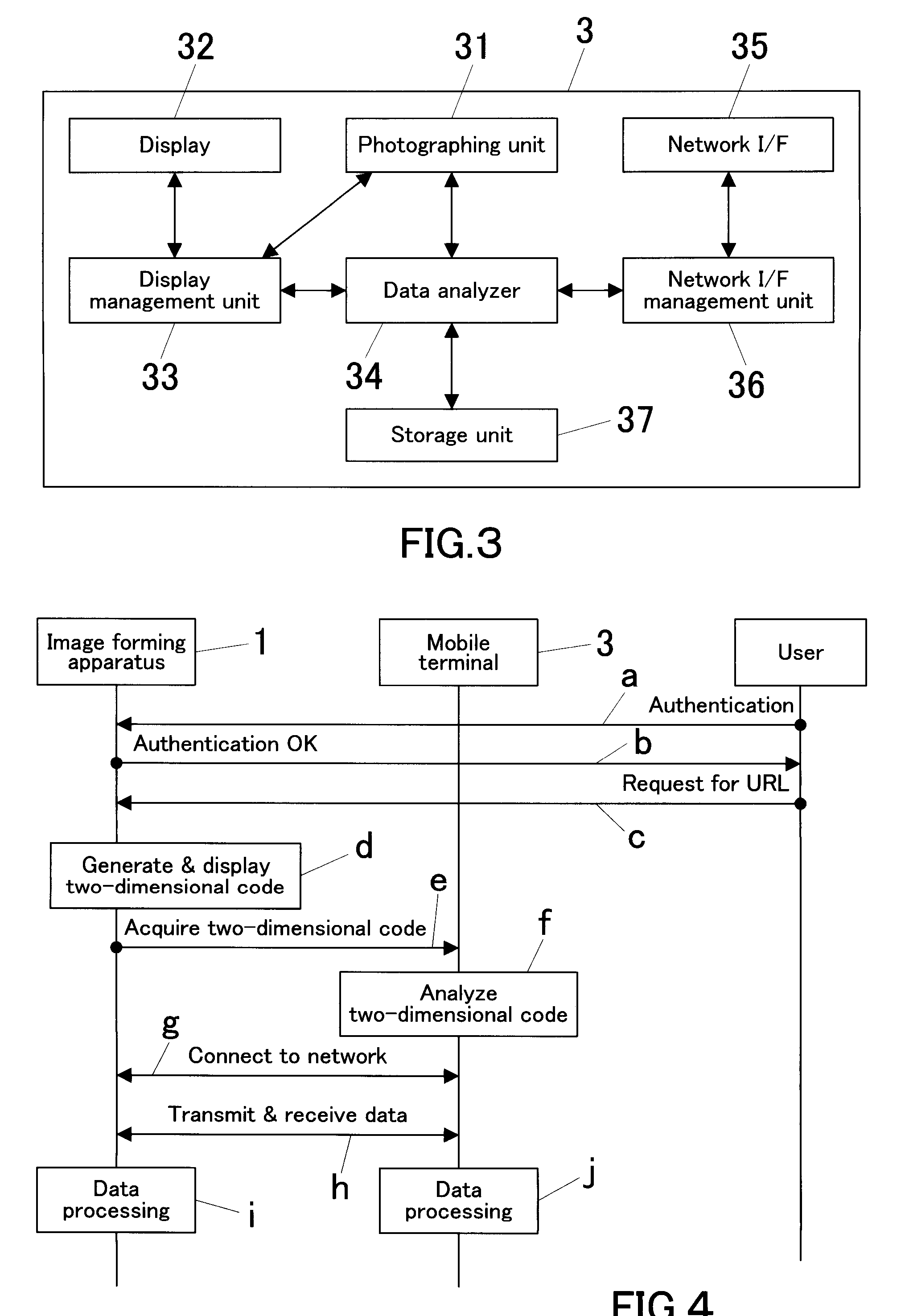
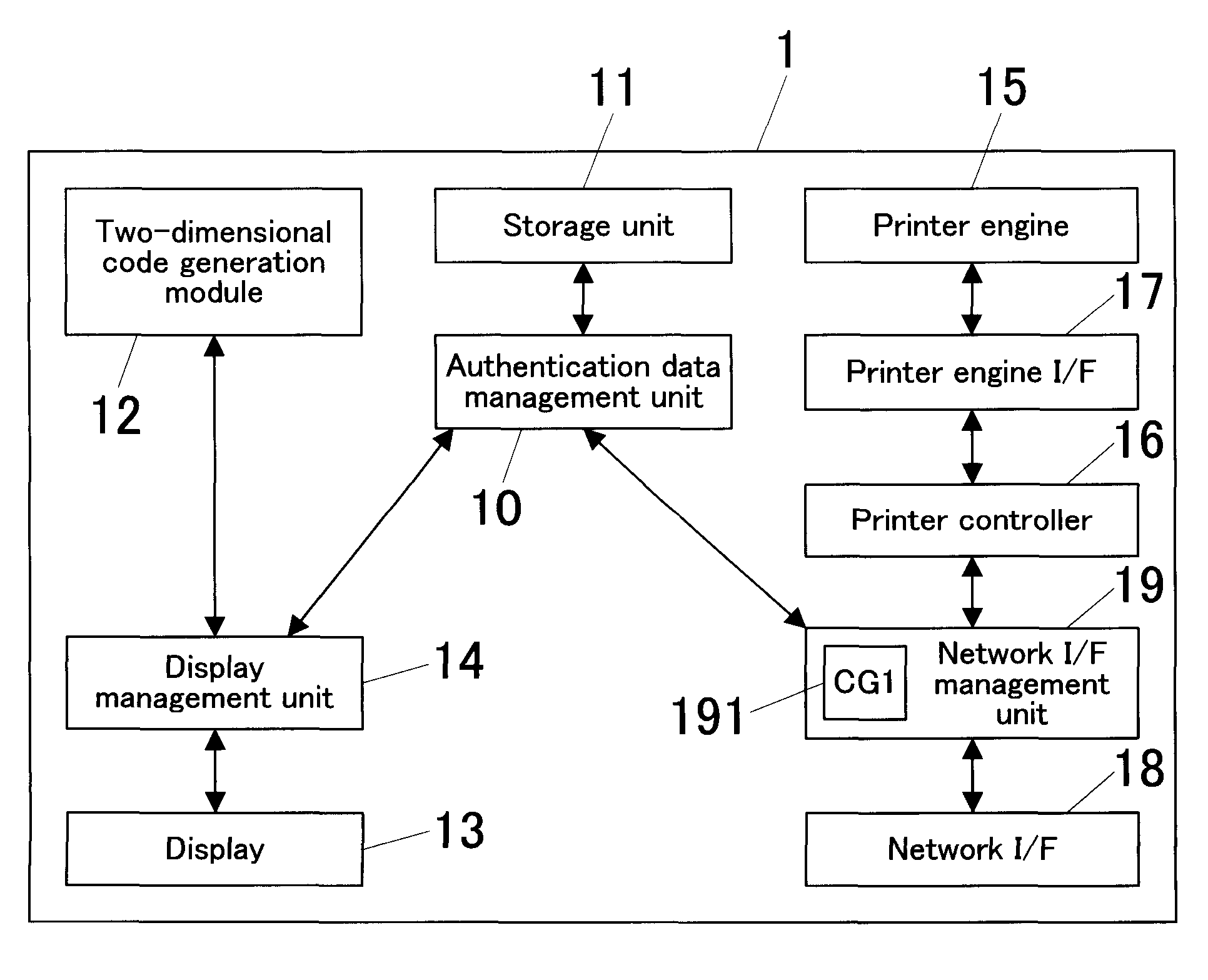
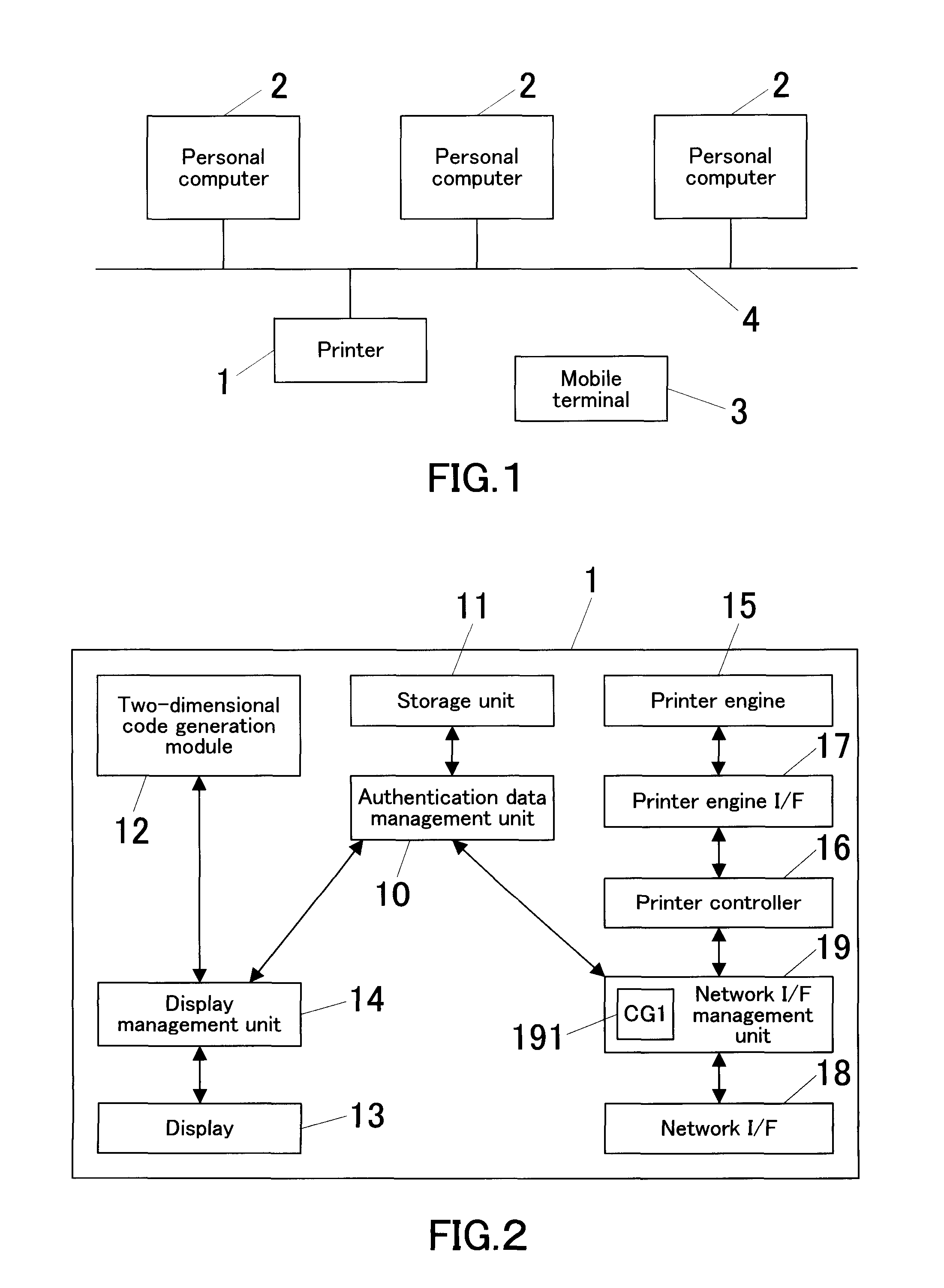
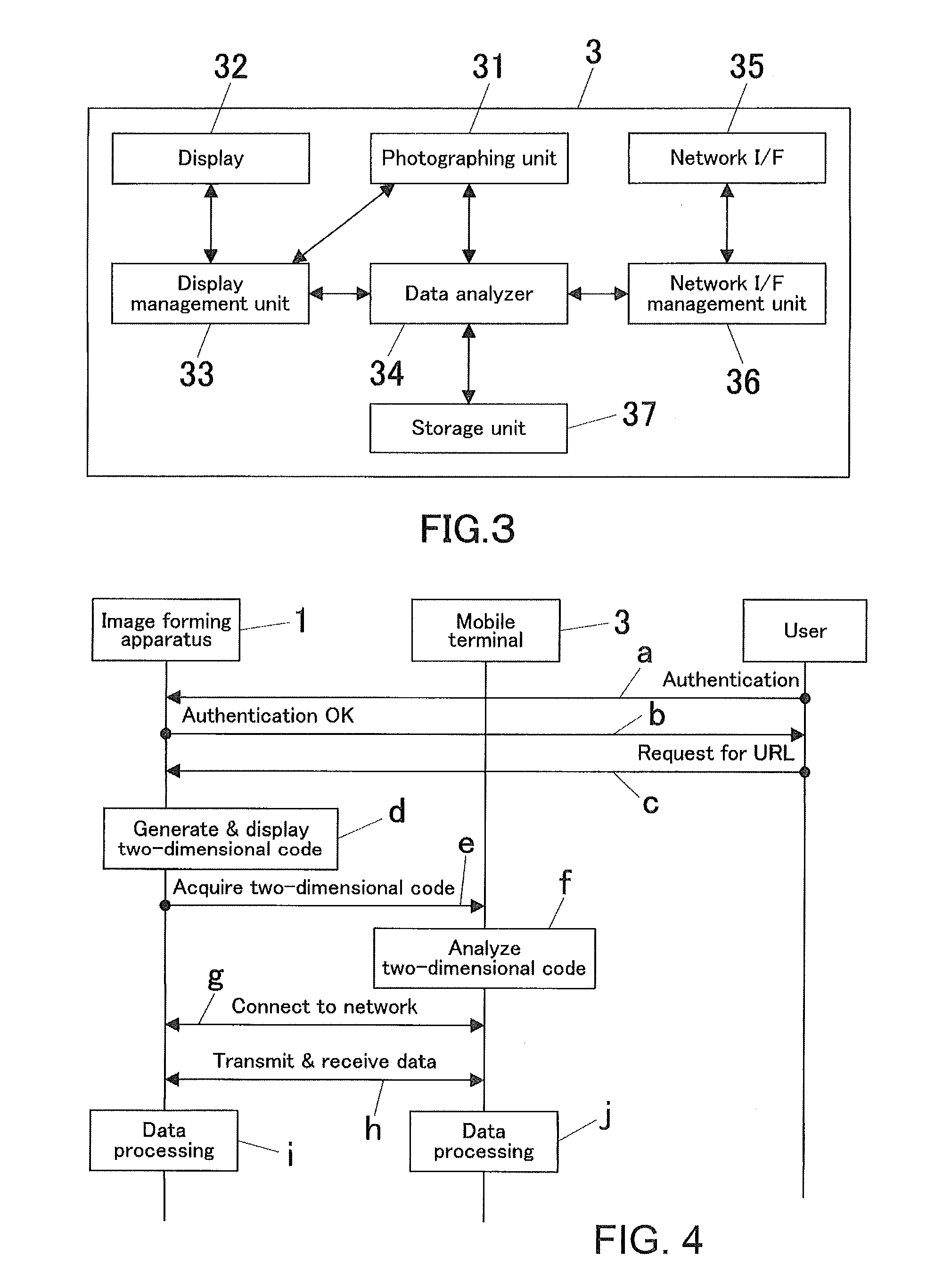
Image Forming System, Image Forming Apparatus, And Image Forming Processing Method
ActiveUS20070019232A1Remove burdenEasy to operateVisual presentationPictoral communicationCommunication unitImage formation
An image forming system includes an image forming apparatus and a mobile terminal. The image forming apparatus includes: a two-dimensional code output unit for outputting a two-dimensional code into which address information of the image forming apparatus is converted; and a job execution unit for executing a job transmitted from the mobile terminal that has accessed the image forming apparatus based on address information into which the two-dimensional code obtained by photographing an image of the two-dimensional code outputted from the image forming apparatus by the mobile terminal is inversely converted. The mobile terminal includes: a photographing unit for photographing an image of the two-dimensional code; an inverse converter for inversely converting the photographed two-dimensional code into address information; and a communication unit for accessing an address of the image forming apparatus, which address is obtained through the inverse conversion, to transmit a job.
Owner:KONICA MINOLTA BUSINESS TECH INC
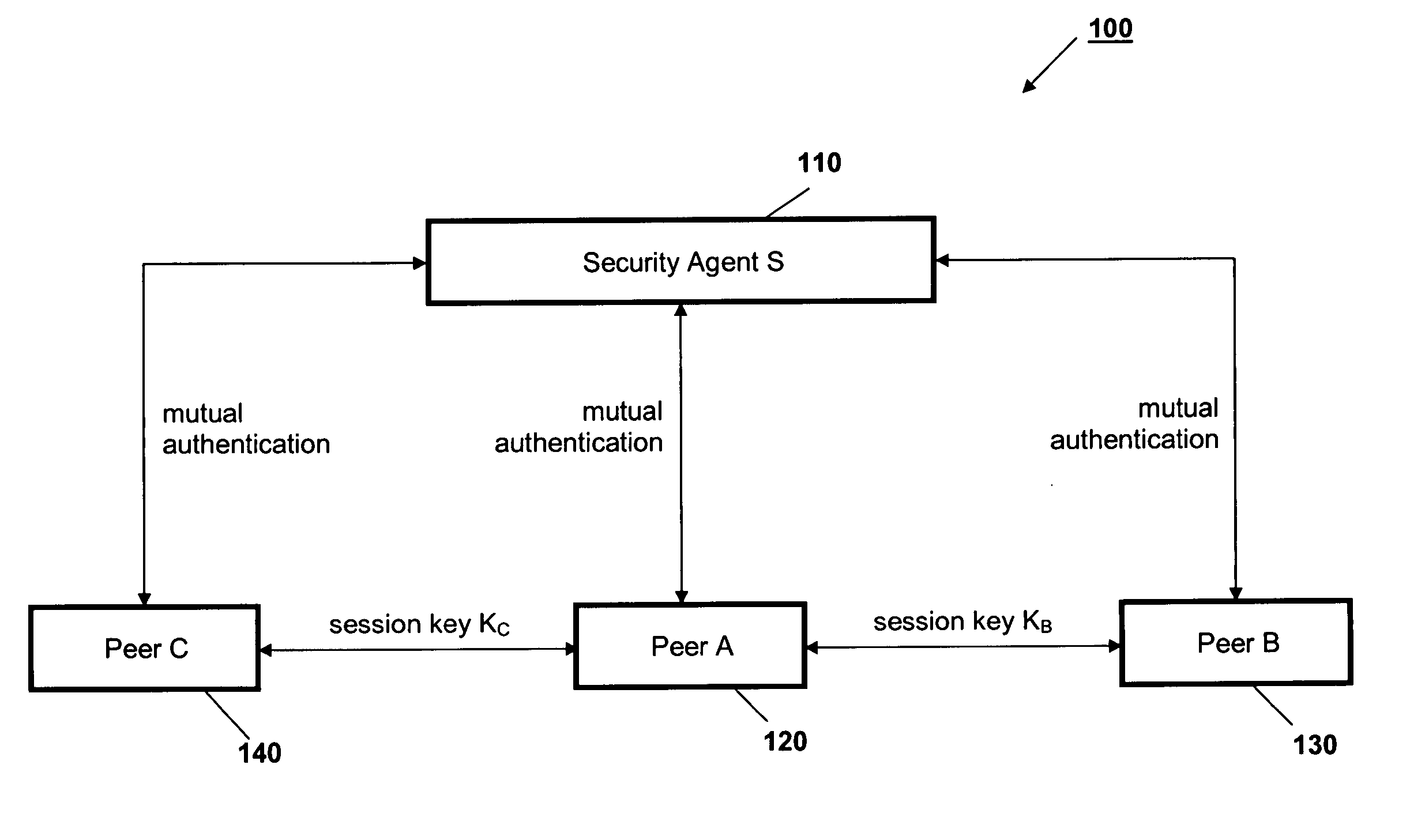
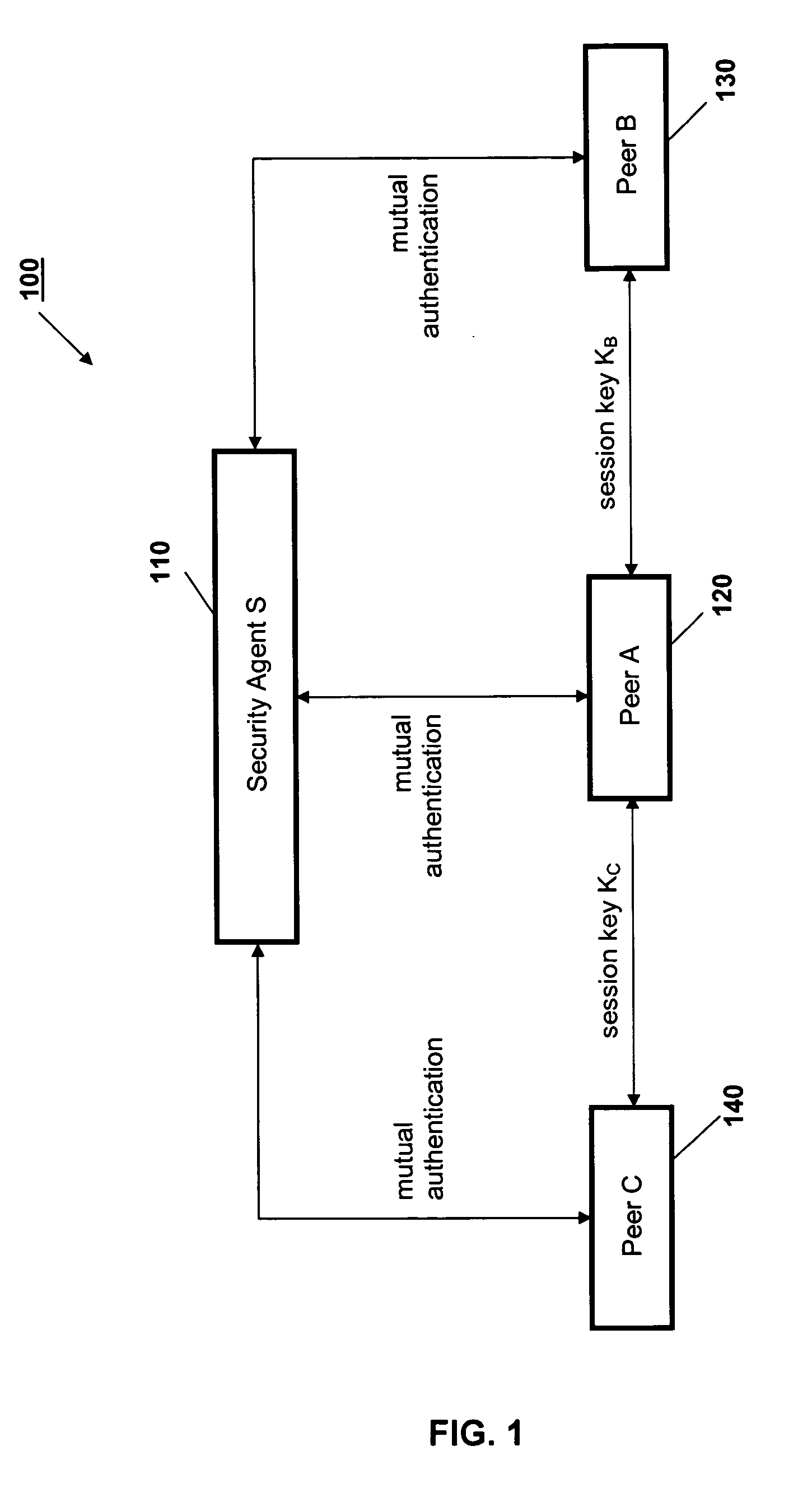
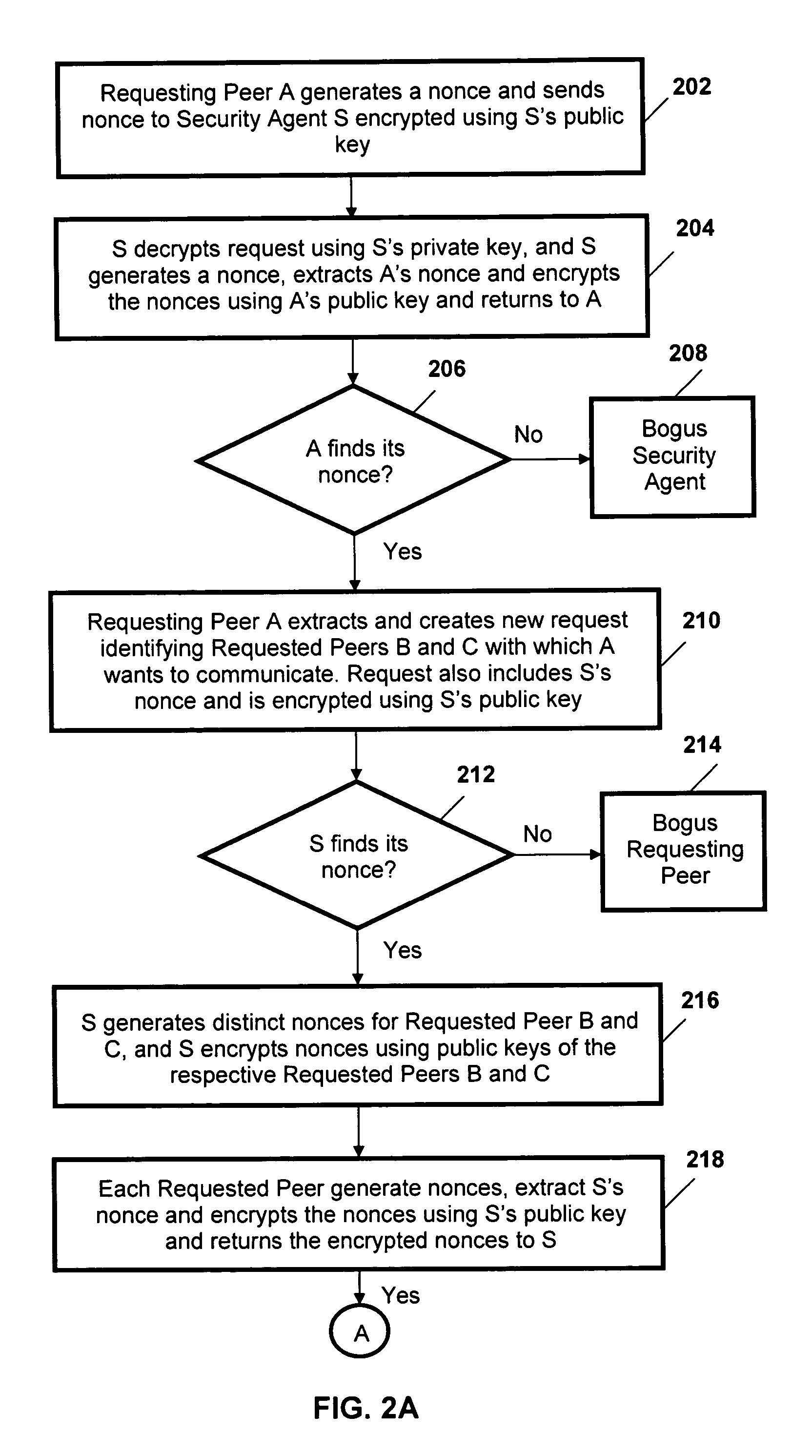
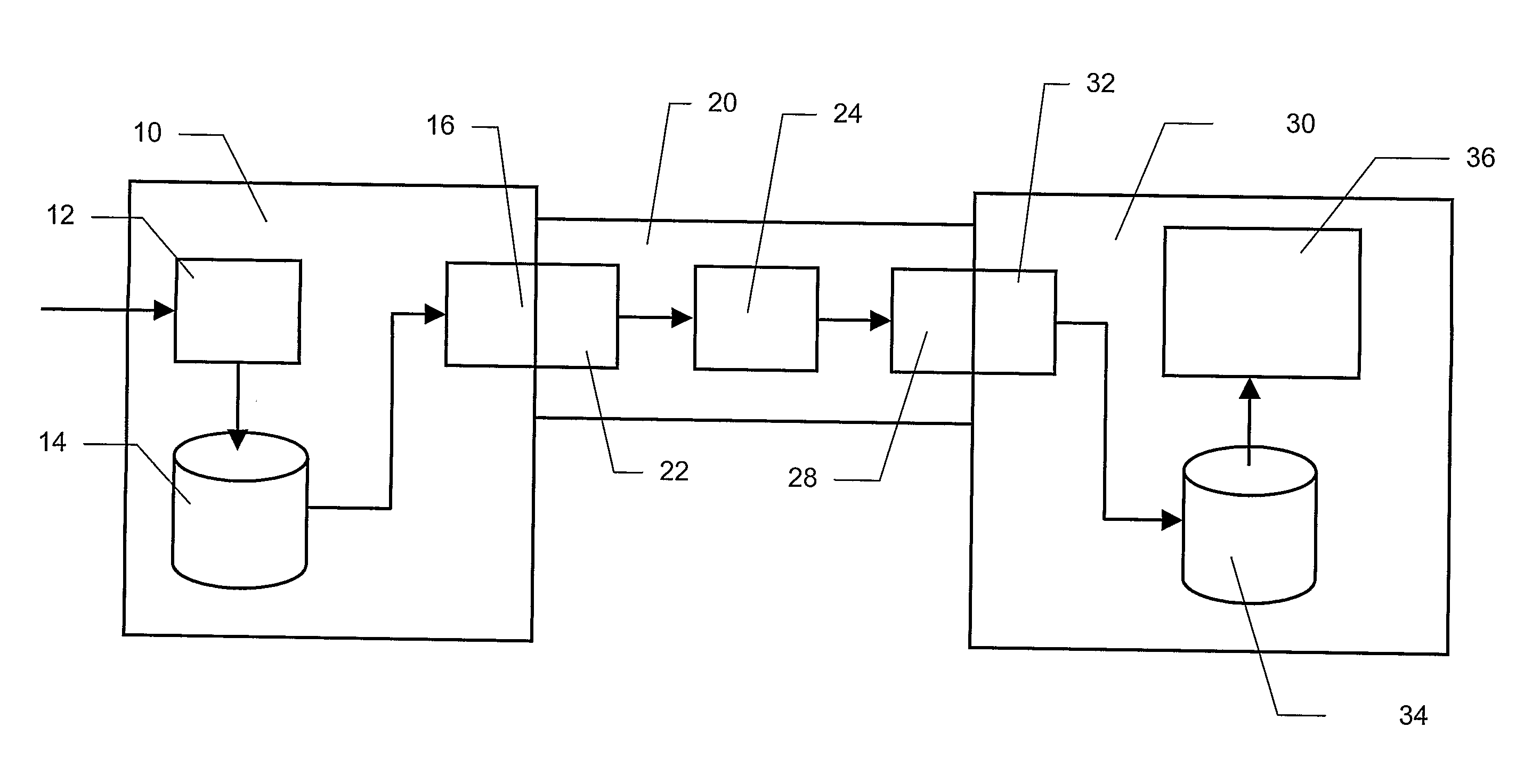
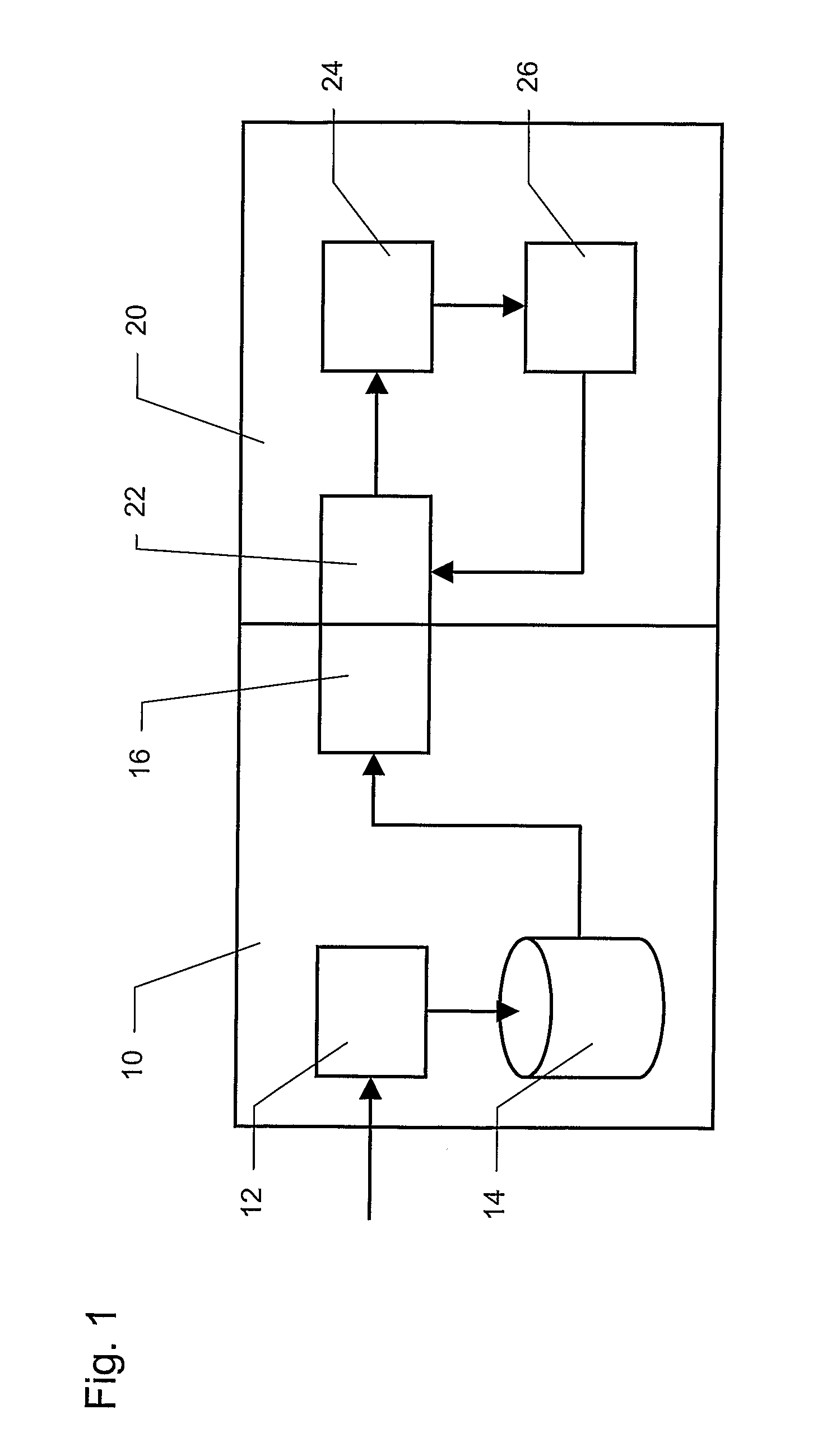
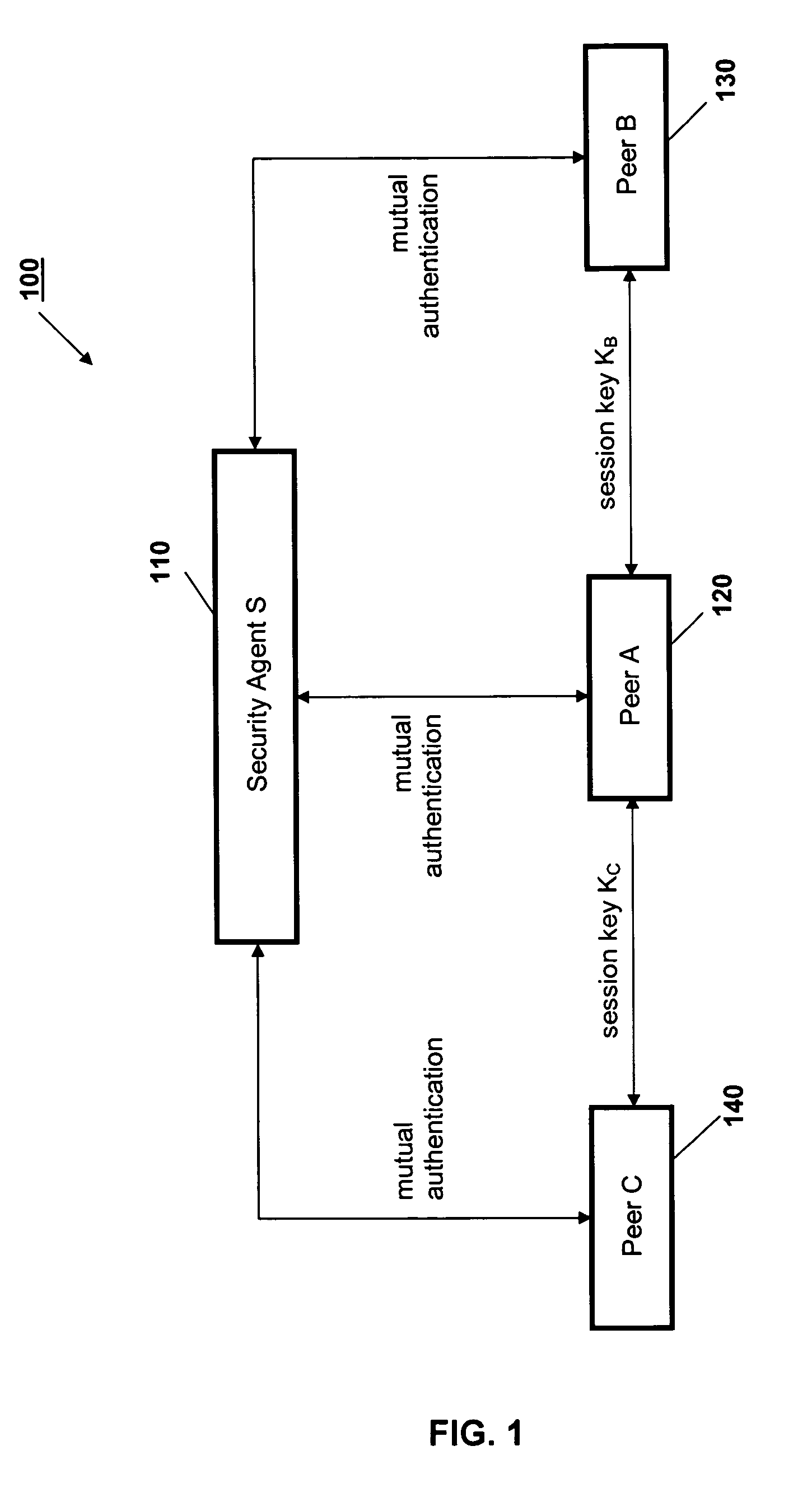
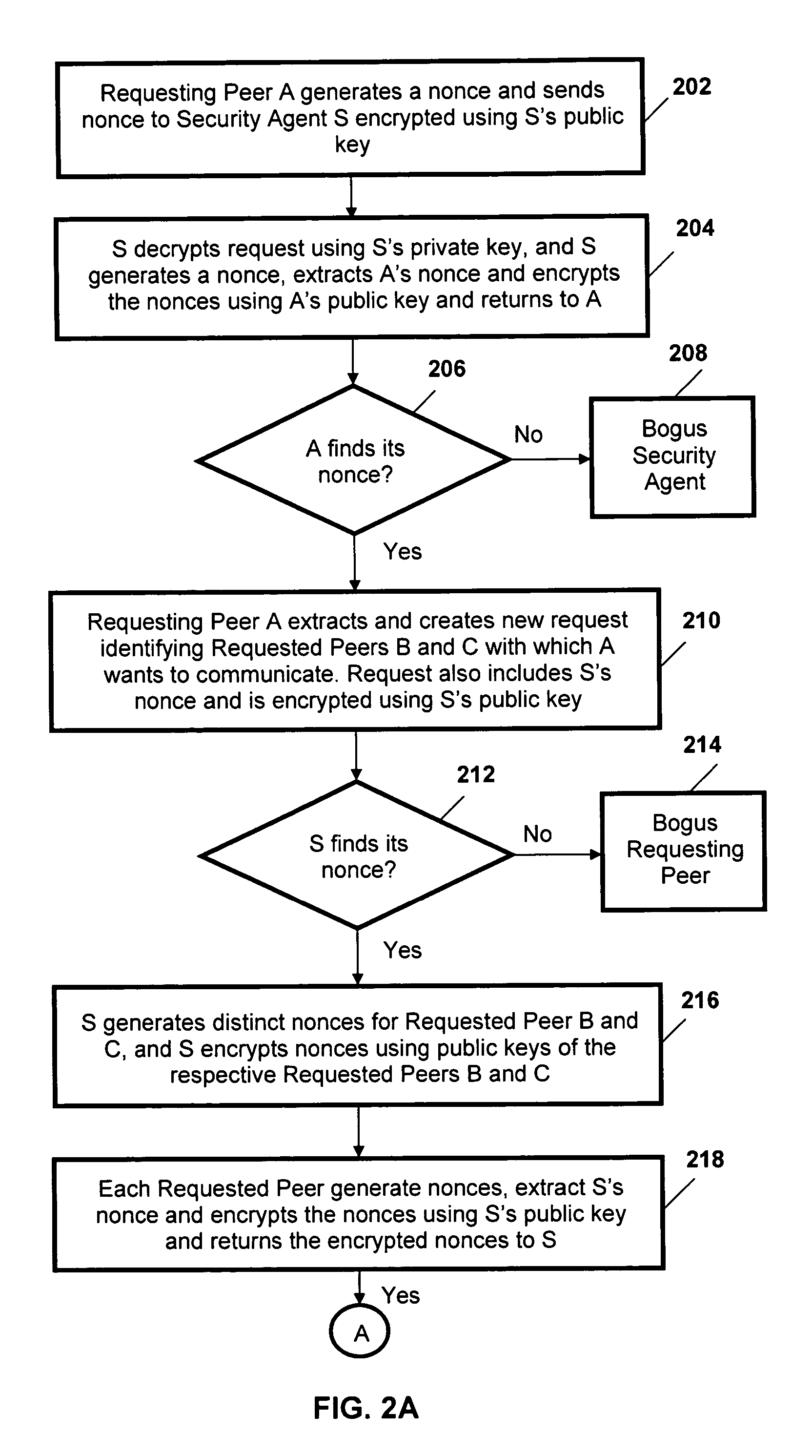
Peer-to-peer communications
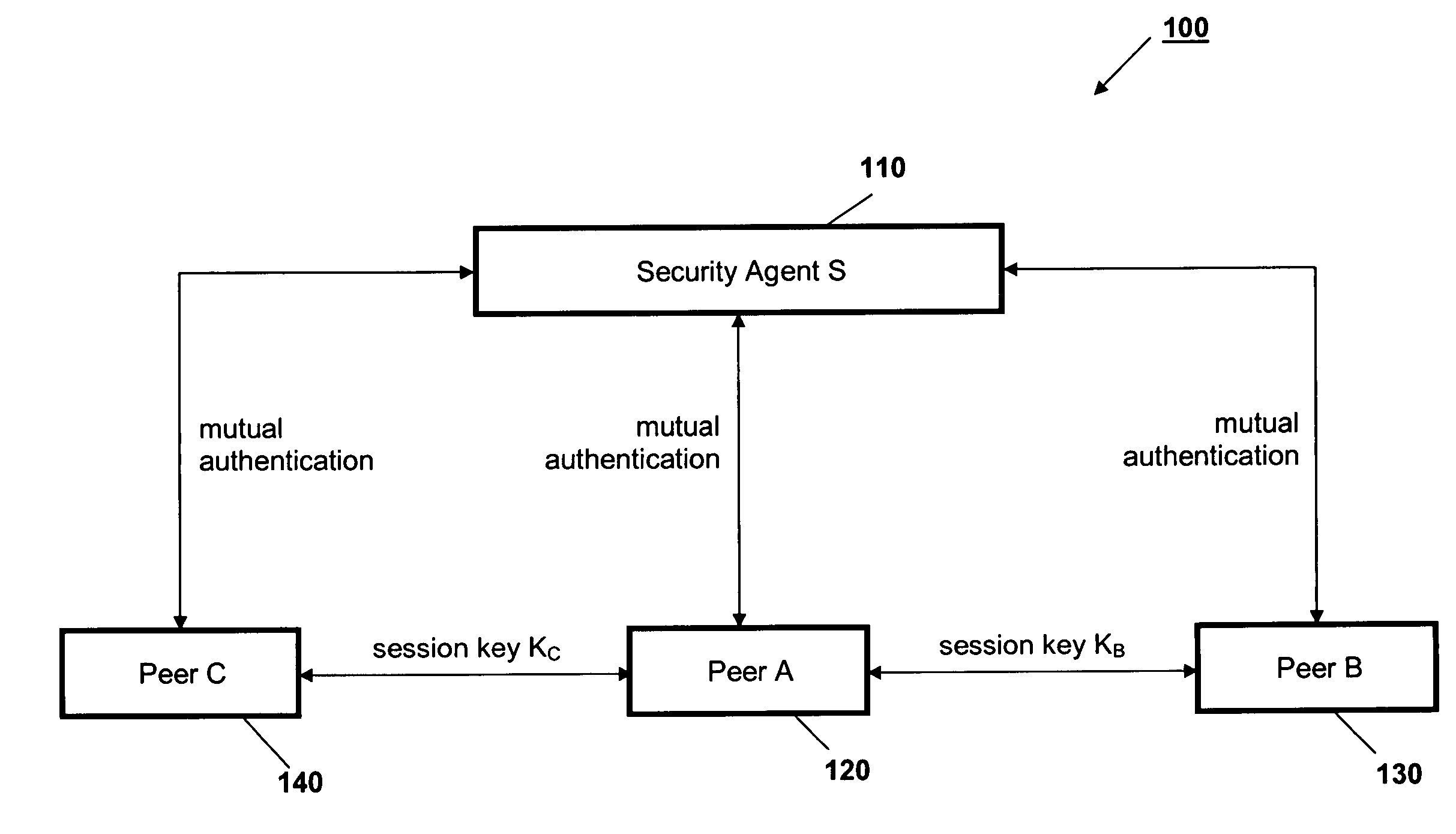
ActiveUS20060053289A1Lighter network trafficRelieving peers of much of the burden of managing securityUser identity/authority verificationPeer-to-peerSession key
A protocol for secure peer-to-peer communications is established based on existing cryptographic techniques and encryption algorithms. The peers (120, 130, 140) and a central security agent (110) undergo mutual authentication. A newly generated nonce is used for authentication, and a random session key is used for a session. The security agent (110) generates unique session keys for communication between peers (120, 130, 140). The security agent (110) removes the burden of mutual authentication between requested peer (130, 140) and the requesting peer (120), as the security agent (110) independently authenticates the requesting peer (120) and the requested peer (130, 140). The requested peer (130, 140) and the requesting peer (120) are sent a session key by the security agent (110).
Owner:KYNDRYL INC
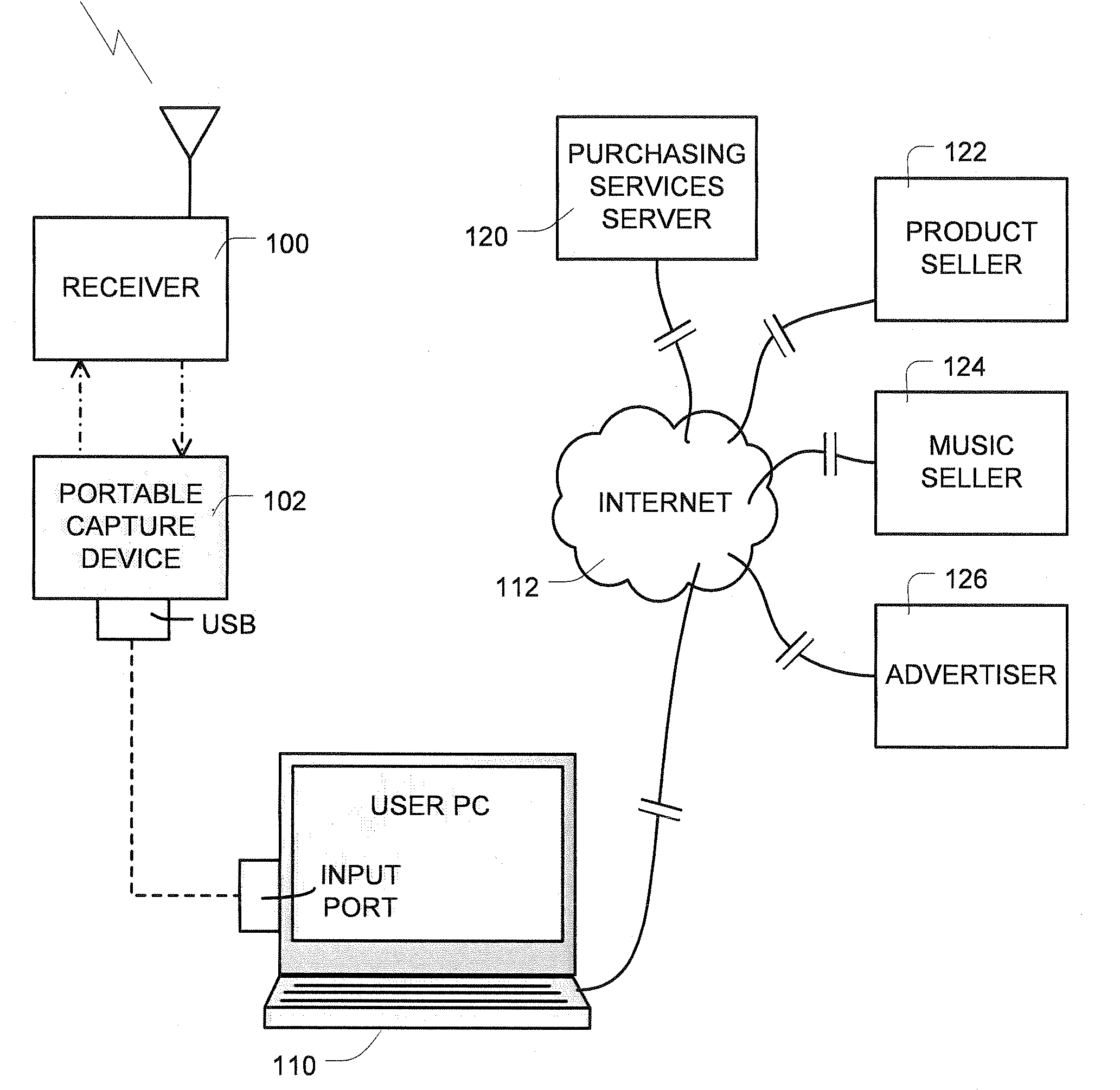
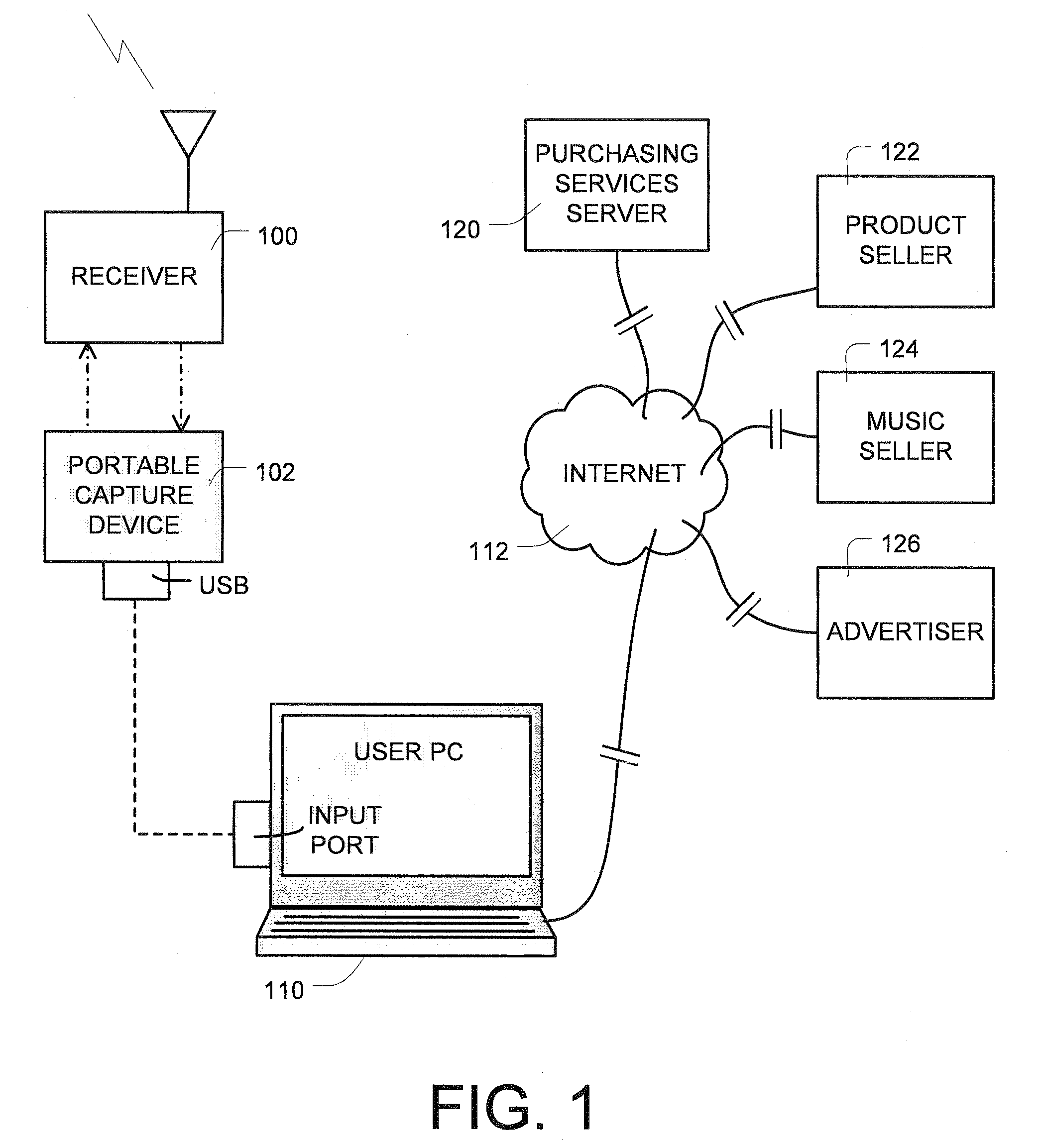
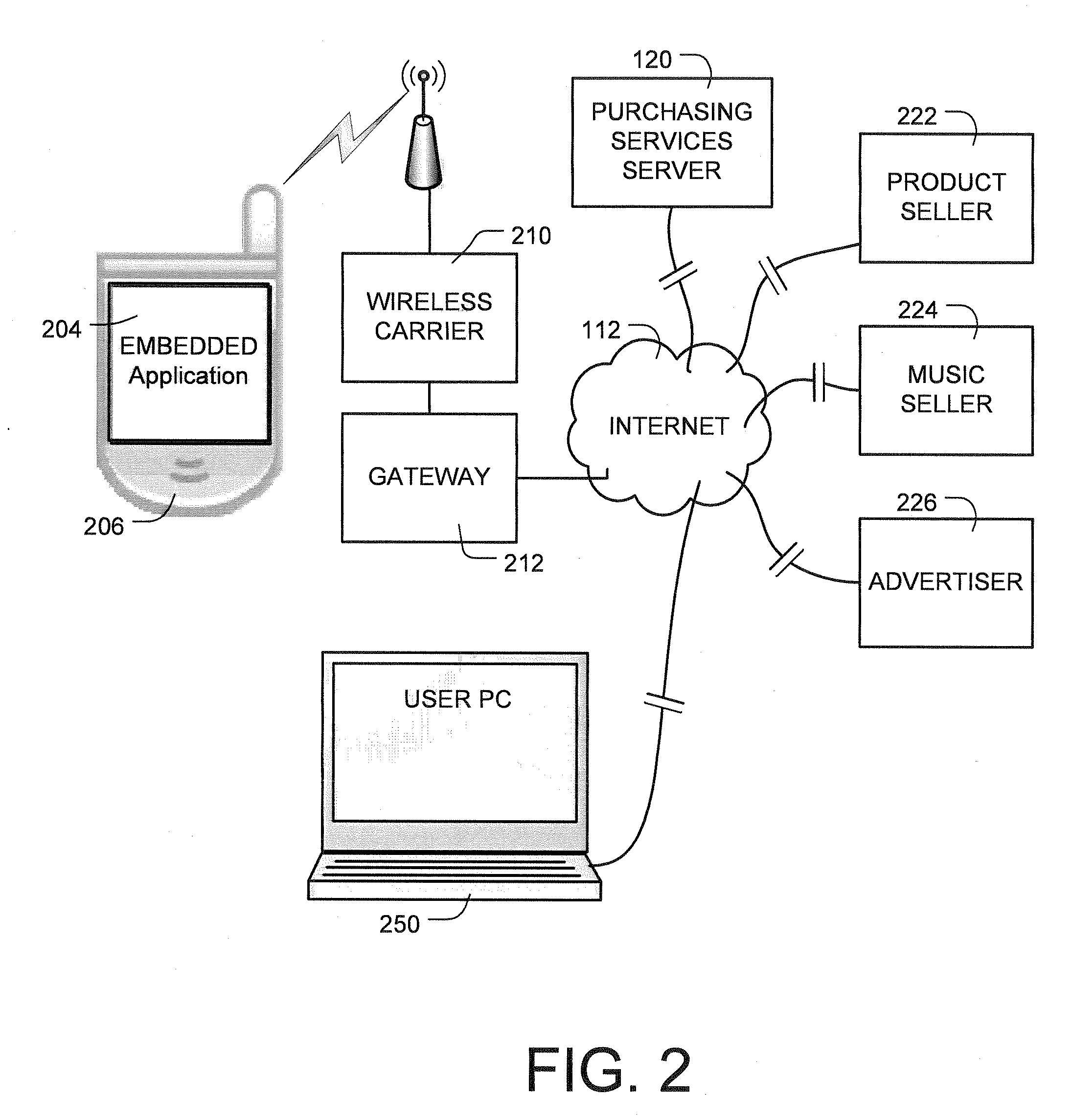
Digital content download associated with corresponding radio broadcast items
ActiveUS20080214236A1Remove burdenRemove the burdenError preventionBroadcast information characterisationData shippingApplication software
A portable device is used to capture, in real time, data sufficient to identify an item, such as a product or service promoted, or a music track played, on a broadcast medium such as radio or television. The capture device can be a standalone implementation, or an application program executable on a personal communication device such as a cell phone or Blackberry. The capture device communicates the captured data to a remote server via a selected wired or wireless channel, or the internet, and the server provides services to support the user in responding to the radio or television broadcast item that corresponds to the captured data. The server on demand downloads to the user additional digital content associated with the identified radio broadcast item.
Owner:HARB JOSEPH
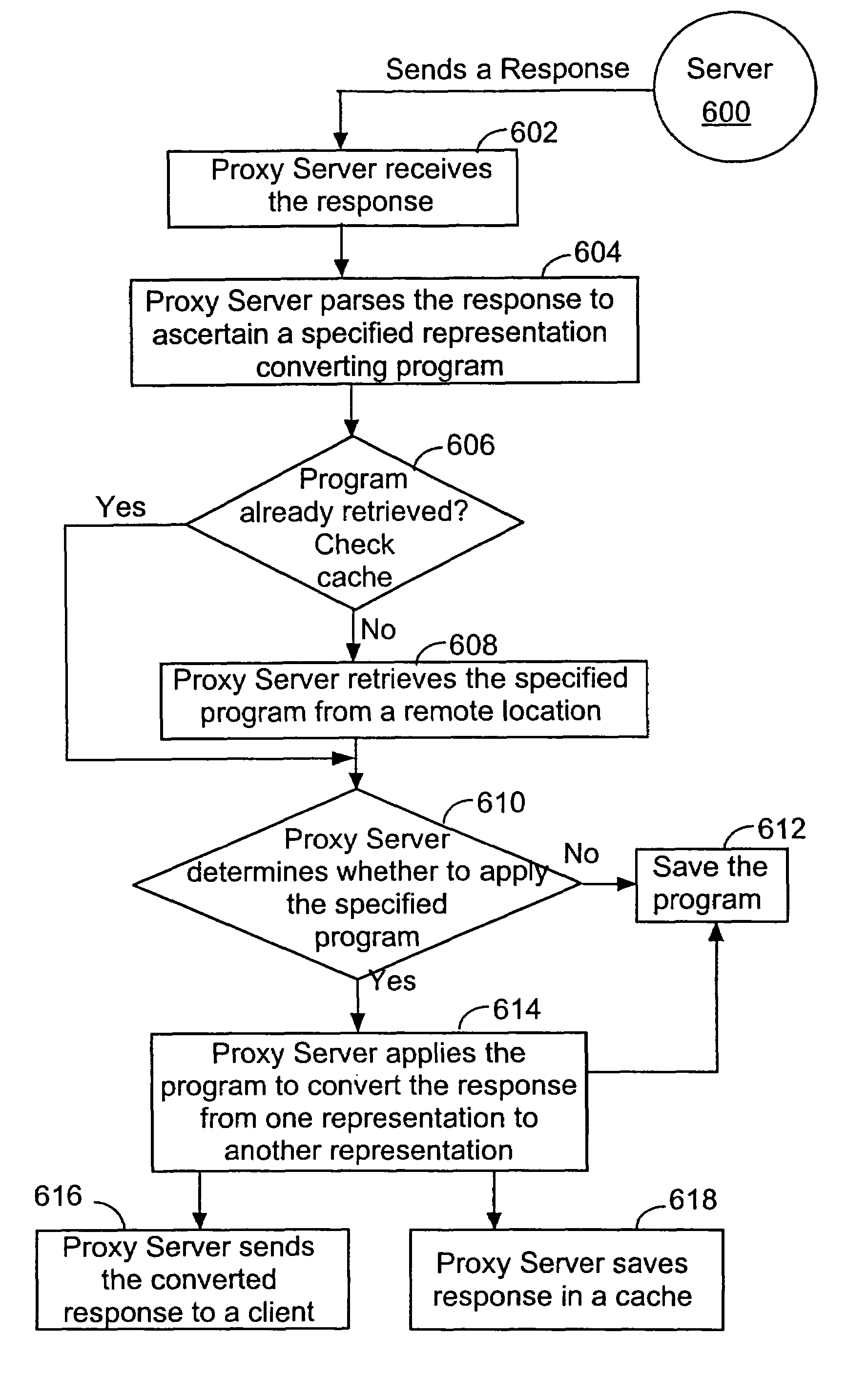
Explicit server control of transcoding representation conversion at a proxy or client location
InactiveUS7287094B2Improve efficiencyMinimize time of retrievalMultiple digital computer combinationsTransmissionComputer graphics (images)Transcoding
Information returned by a server to a client includes instructions, executable by either a proxy server or the client, for converting the returned information from a first representation to a second representation. The representation conversion may be made by a proxy server, for example, to make transmission of the returned information to the client more efficient, and / or to render the returned information in a format suitable for display by the client. By having the server embed representation conversion information in the query response, the representation conversion can take into account the type and other characteristics of information being returned, as well as the computational and display characteristics of the client.
Owner:HEWLETT PACKARD DEV CO LP
Media Transcoding Device and Method
InactiveUS20090080870A1Remove burdenReduced Power RequirementsTelevision system detailsPulse modulation television signal transmissionComputer hardwareCode converter
A transcoding device includes an interface for receiving a media file in a first format, a transcoder for transcoding the media file to the second format, and output means for outputting the media file in a second format. The interface is preferably suitable for connection to a media file store, such as a PVR, so as to receive and transcode the media file to the second format for output to a portable media player (PMP).
Owner:SKY UK
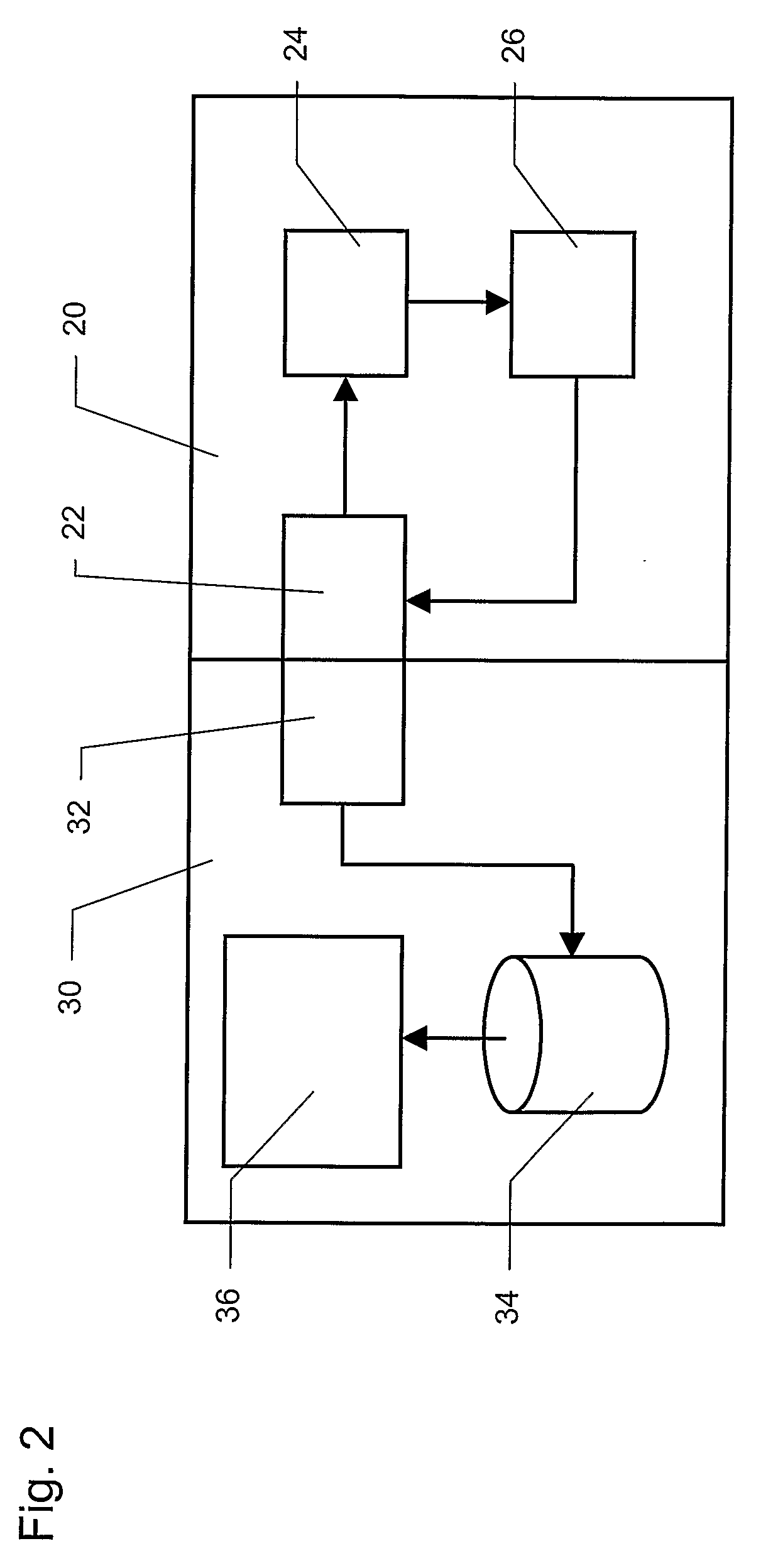
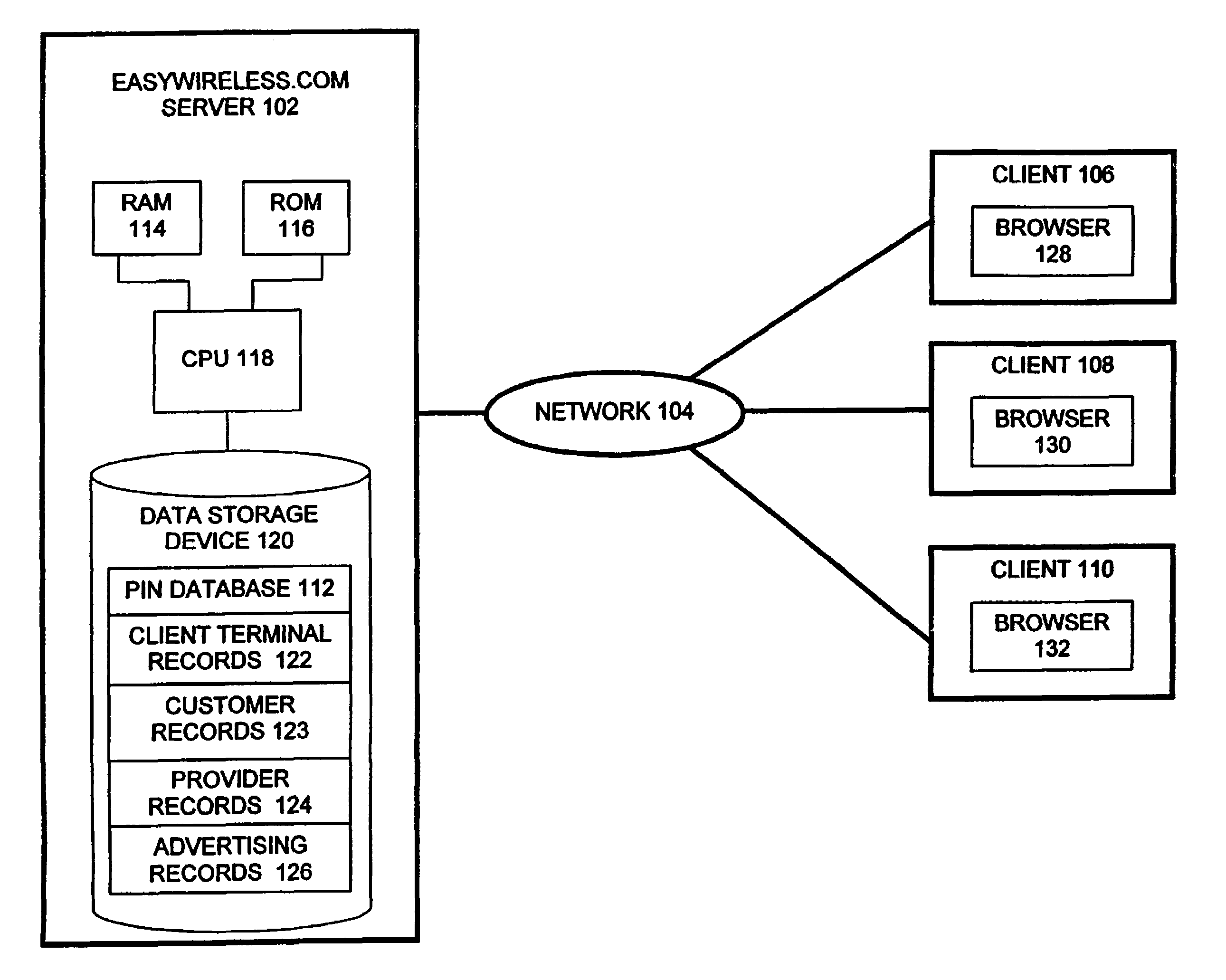
System and method for distributing personal identification numbers over a computer network
InactiveUS7522716B2Removal costEliminating taskAccounting/billing servicesPrepayment with automatic account/card rechargingPersonal identification numberOn demand
The present invention comprises a system and method for providing a personal identification number (PIN) to a client terminal over a computer network. In accordance with one aspect of the present invention, a server receives a request for a PIN over a network, the request originating from a user at a client terminal. The request is associated with a requested monetary unit and a requested provider. The server retrieves from a database a PIN associated with the requested monetary unit and requested provider. The server transmits the retrieved PIN to the client terminal over the network, wherein the PIN is transmitted to the client terminal on-demand in response to the customer's request.
Owner:EWI HLDG
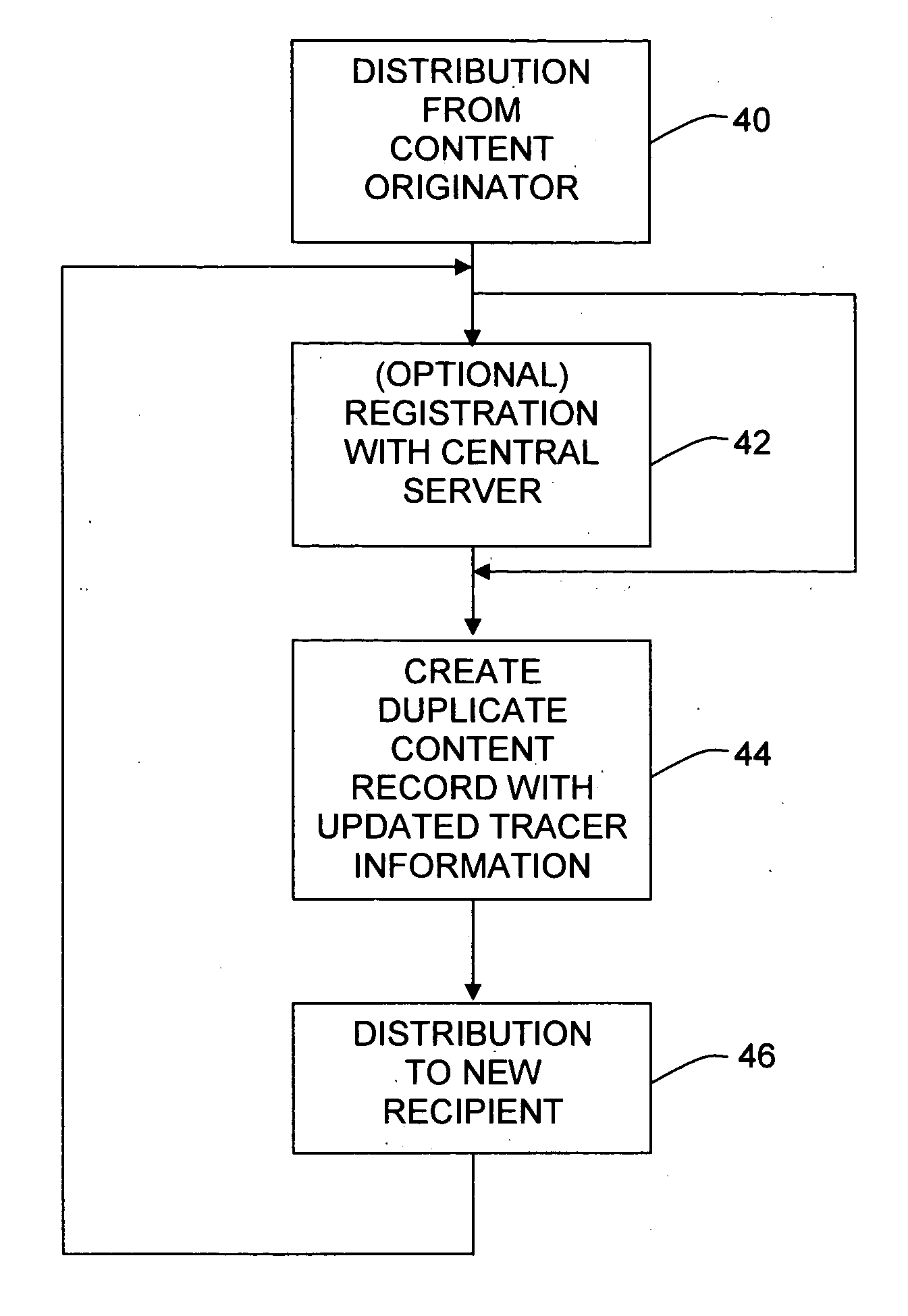
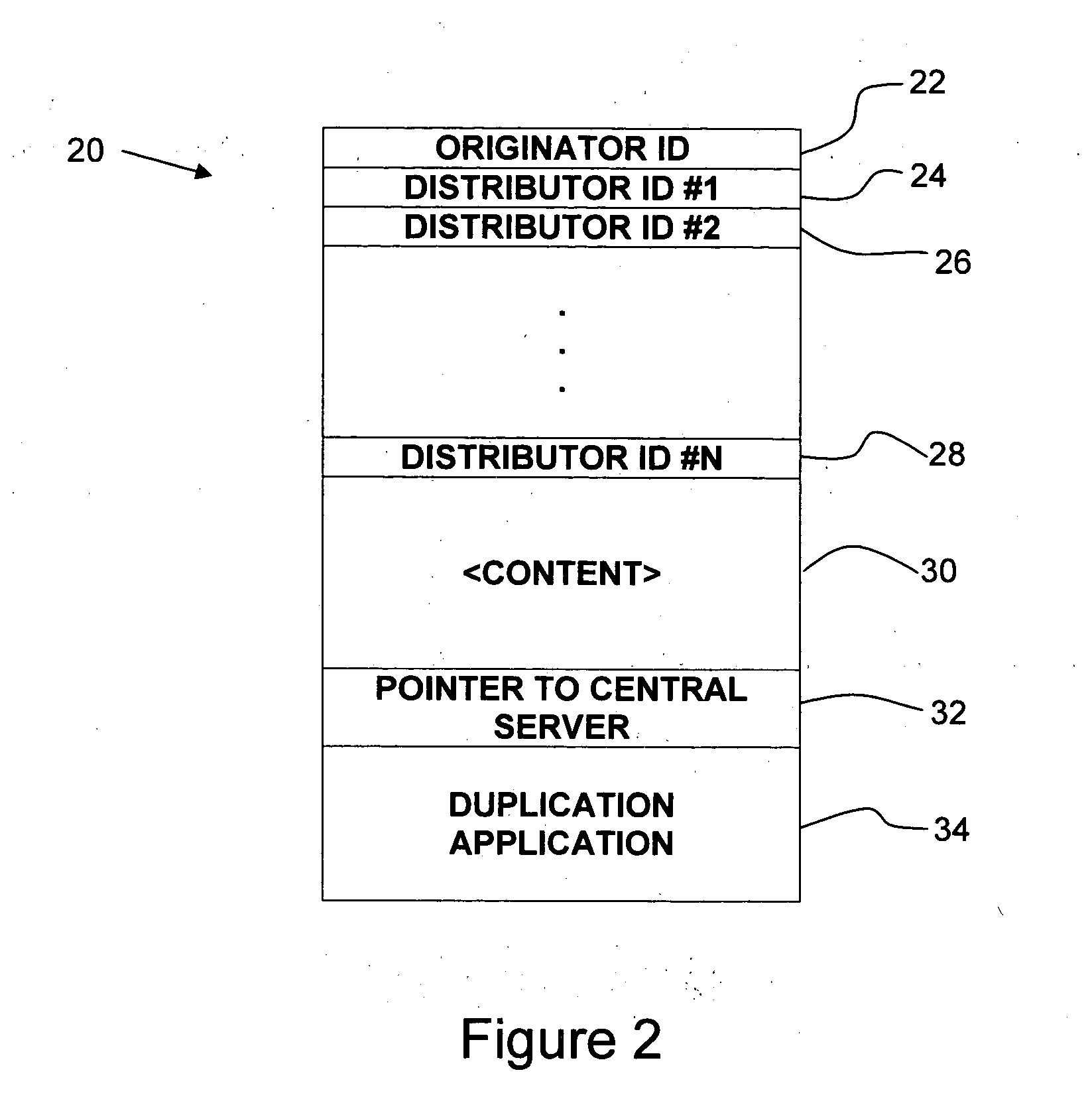
System and method for distribution and tracking of digital content
InactiveUS20050138139A1Reduce materialReduce labor costsMultiple digital computer combinationsTransmissionDigital contentDistribution chain
A system and method for distribution of content is disclosed in which the content in the form of a content record is distributed from a content originator through a series of intervening recipients of copies of the content record. Each recipient of a copy of a content record is capable of making further copies for distribution to other recipients. Each content record includes certain tracer information for tracking the distribution of the content and preferably uniquely identifying each recipient along the distribution chain.
Owner:SPARKART GRP
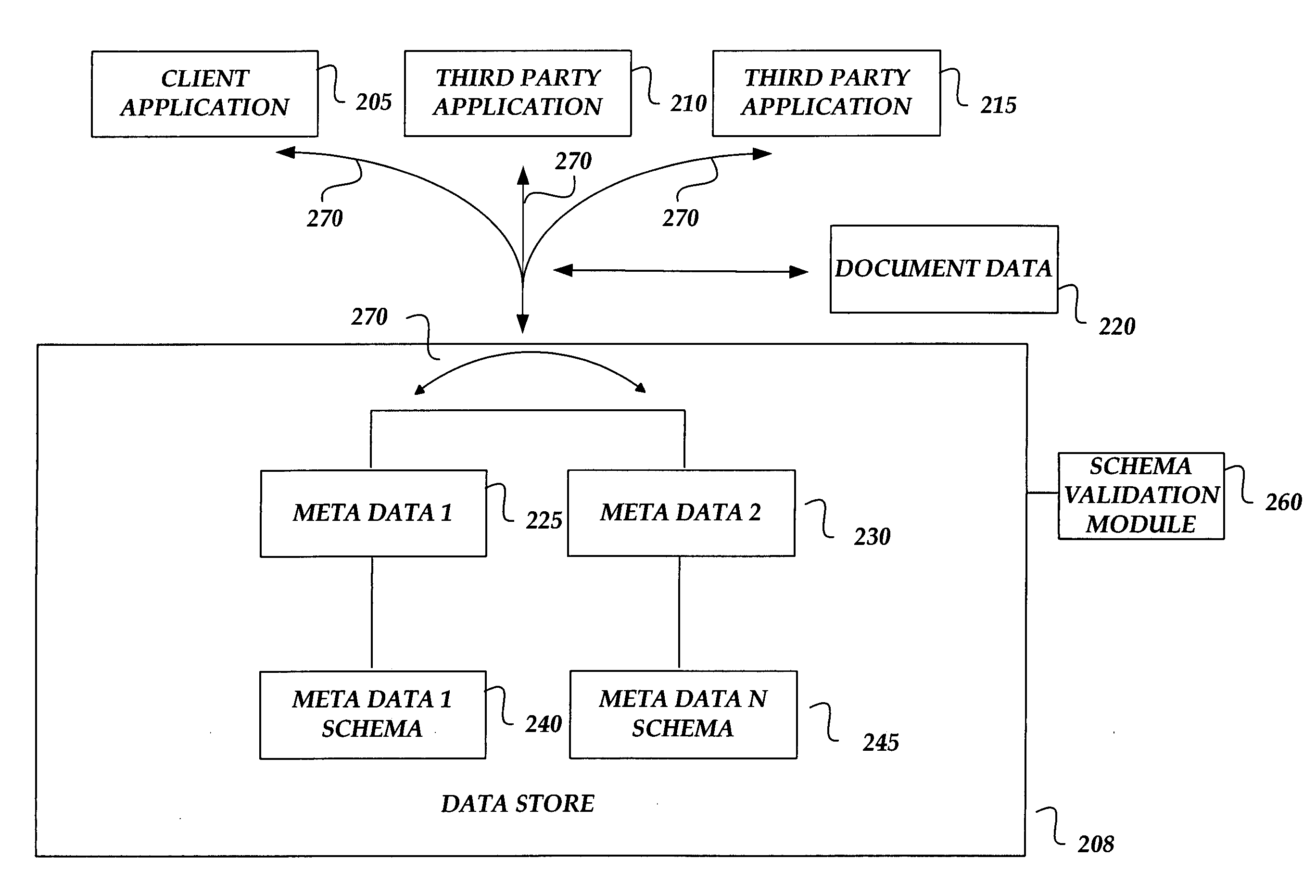
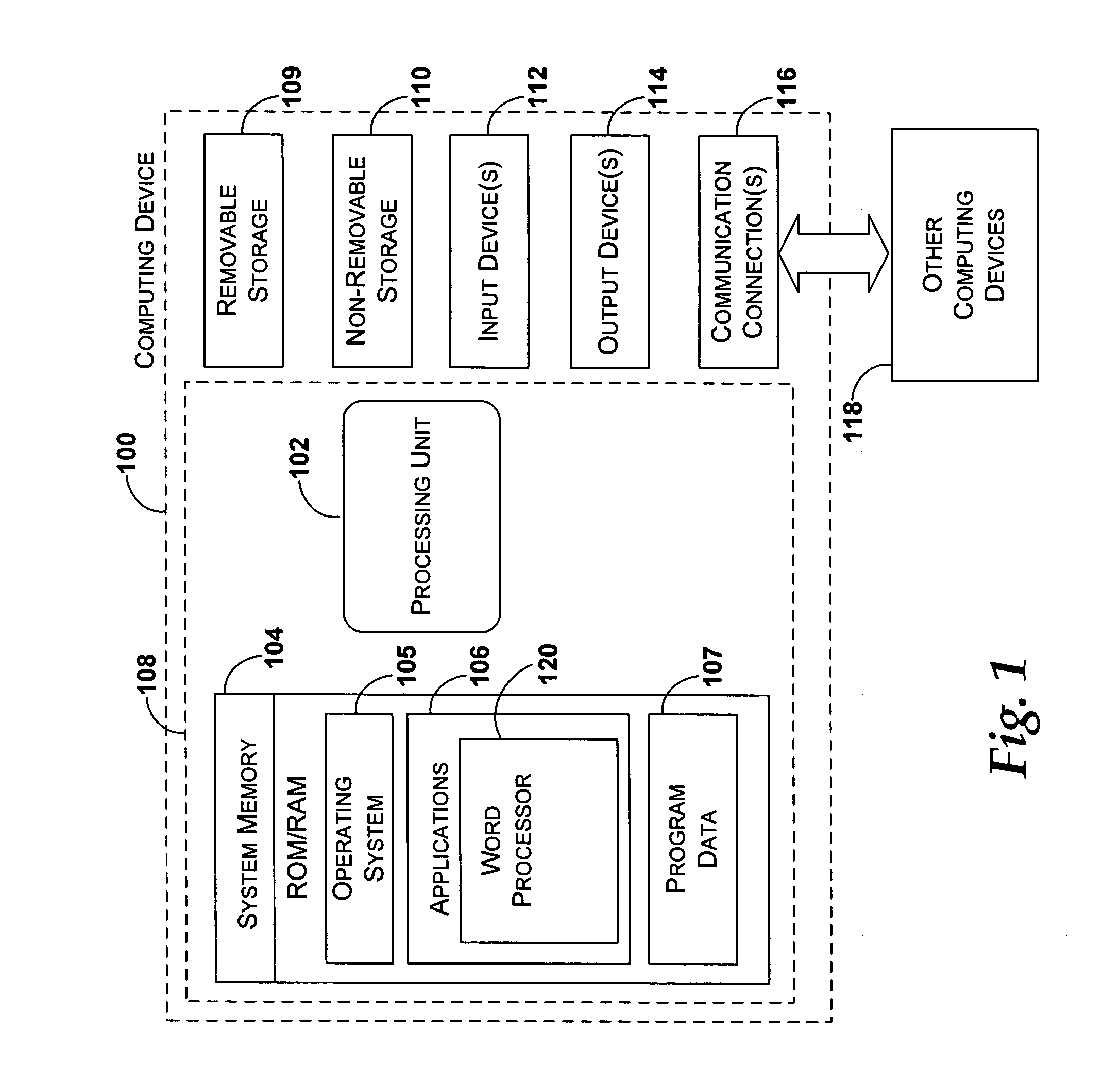
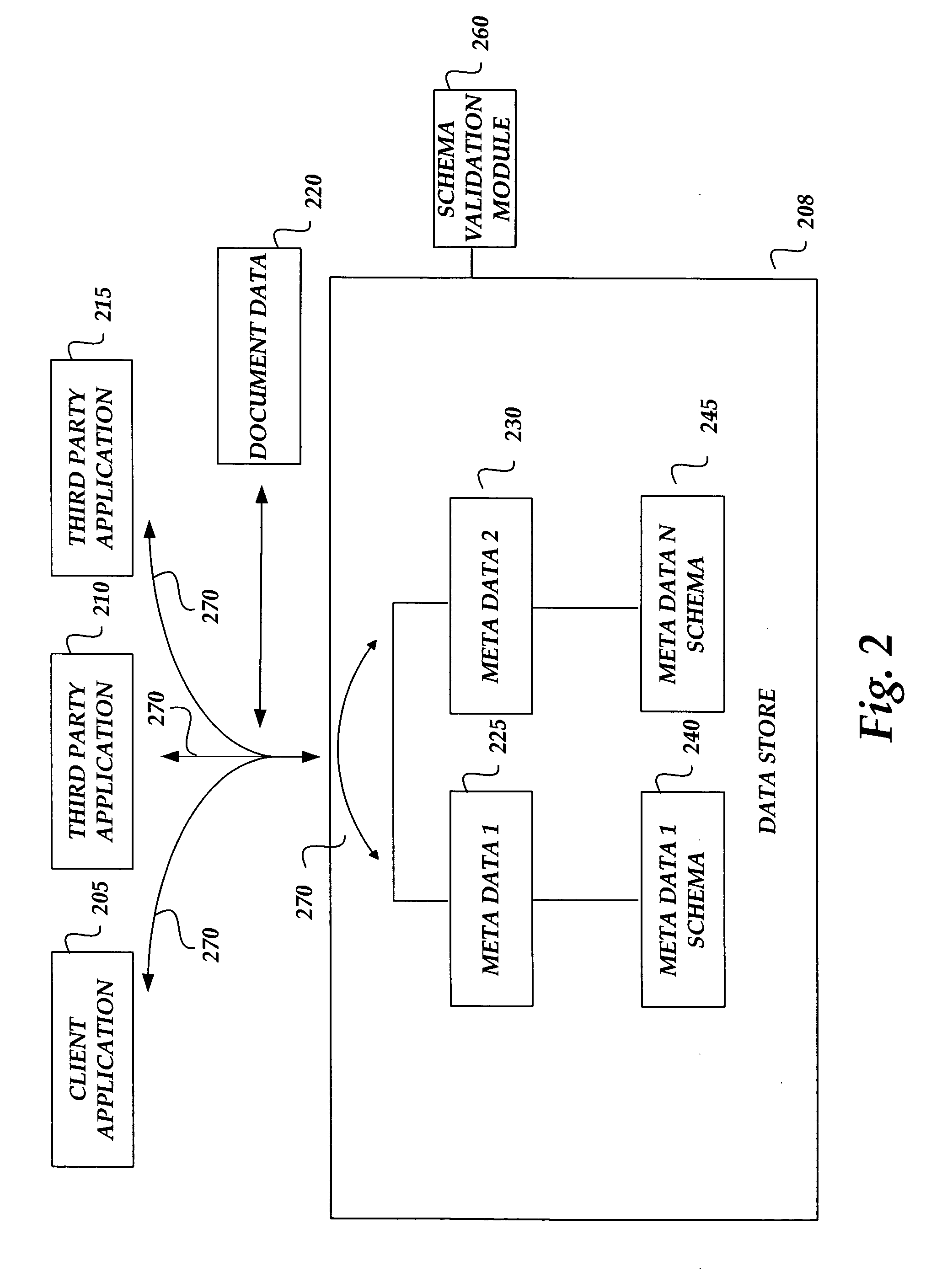
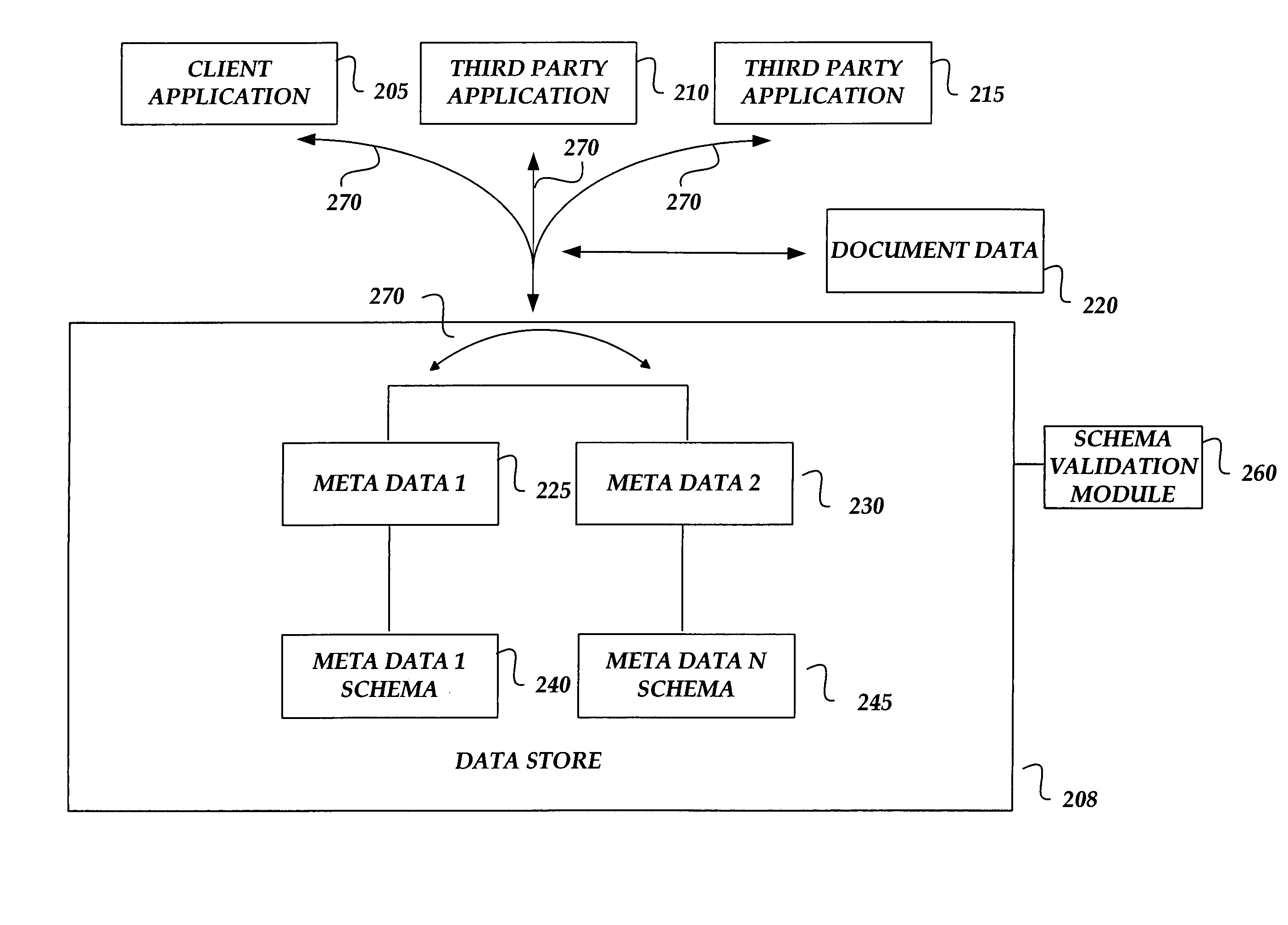
Data store for software application documents
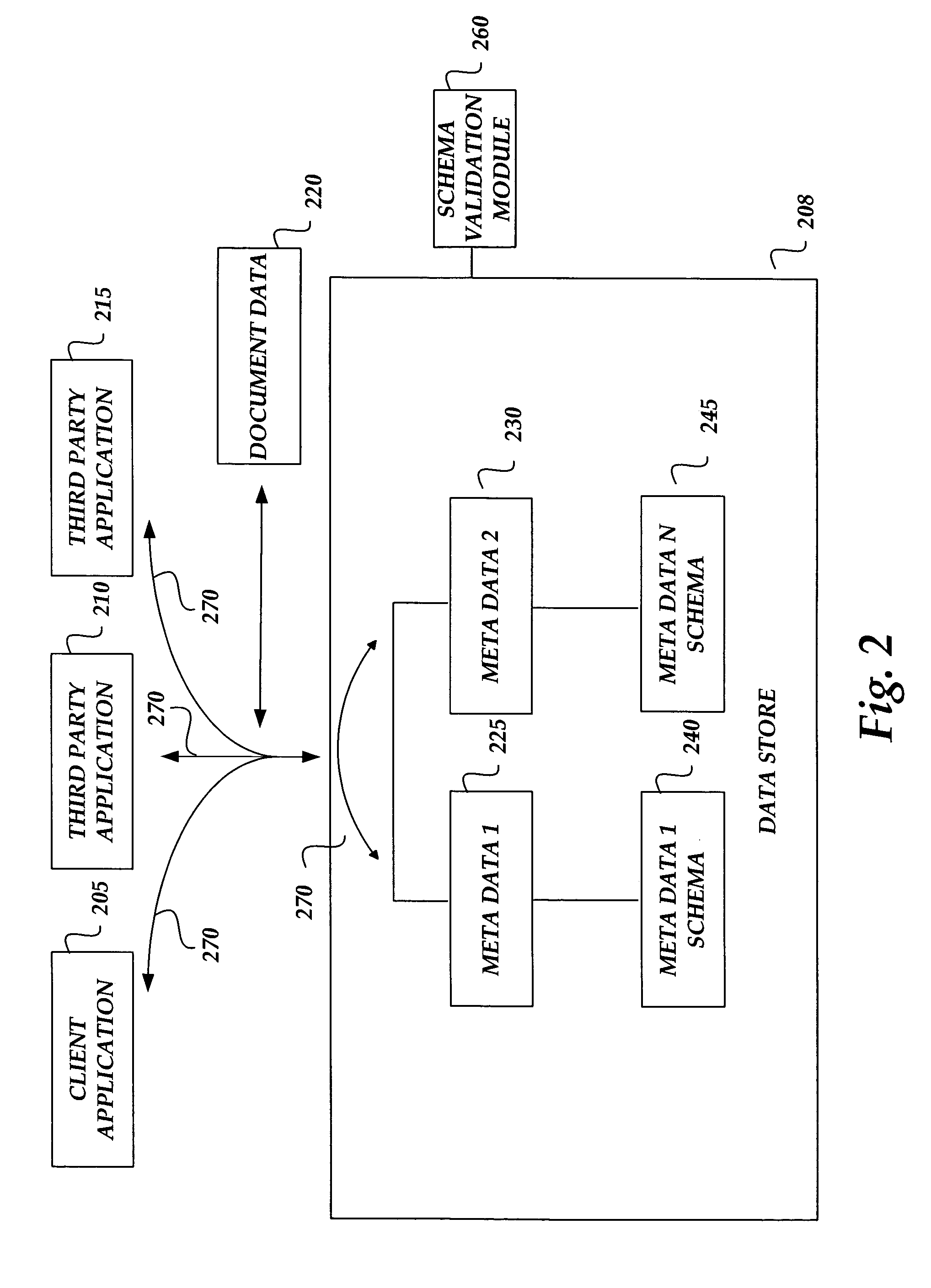
ActiveUS20060195777A1Remove the burdenRemove burdenUnstructured textual data retrievalNatural language data processingXML schemaData segment
A data store is provided for storing, relating and for allowing use of data associated with a computer-generated document. Data for structuring information associated with a document, such as document metadata, is maintained in the data store where relationships between different pieces of data are maintained in a location distinct from the surface level view of a document. The data store exposes interfaces to the various pieces of data in the data store for allowing different applications to access and operate on one or more of the data pieces. The pieces of data may be structured according to a markup language such as the Extensible Markup Language (XML), and XML schemas may be associated with each piece of data for allowing the data store to validate the structure applied to the data based on an XML schema associated with a given piece of data.
Owner:MICROSOFT TECH LICENSING LLC
Data store for software application documents
ActiveUS7668873B2Remove burdenDigital data processing detailsUnstructured textual data retrievalXML schemaSurface level
Owner:MICROSOFT TECH LICENSING LLC
Professional service management using project-based point system
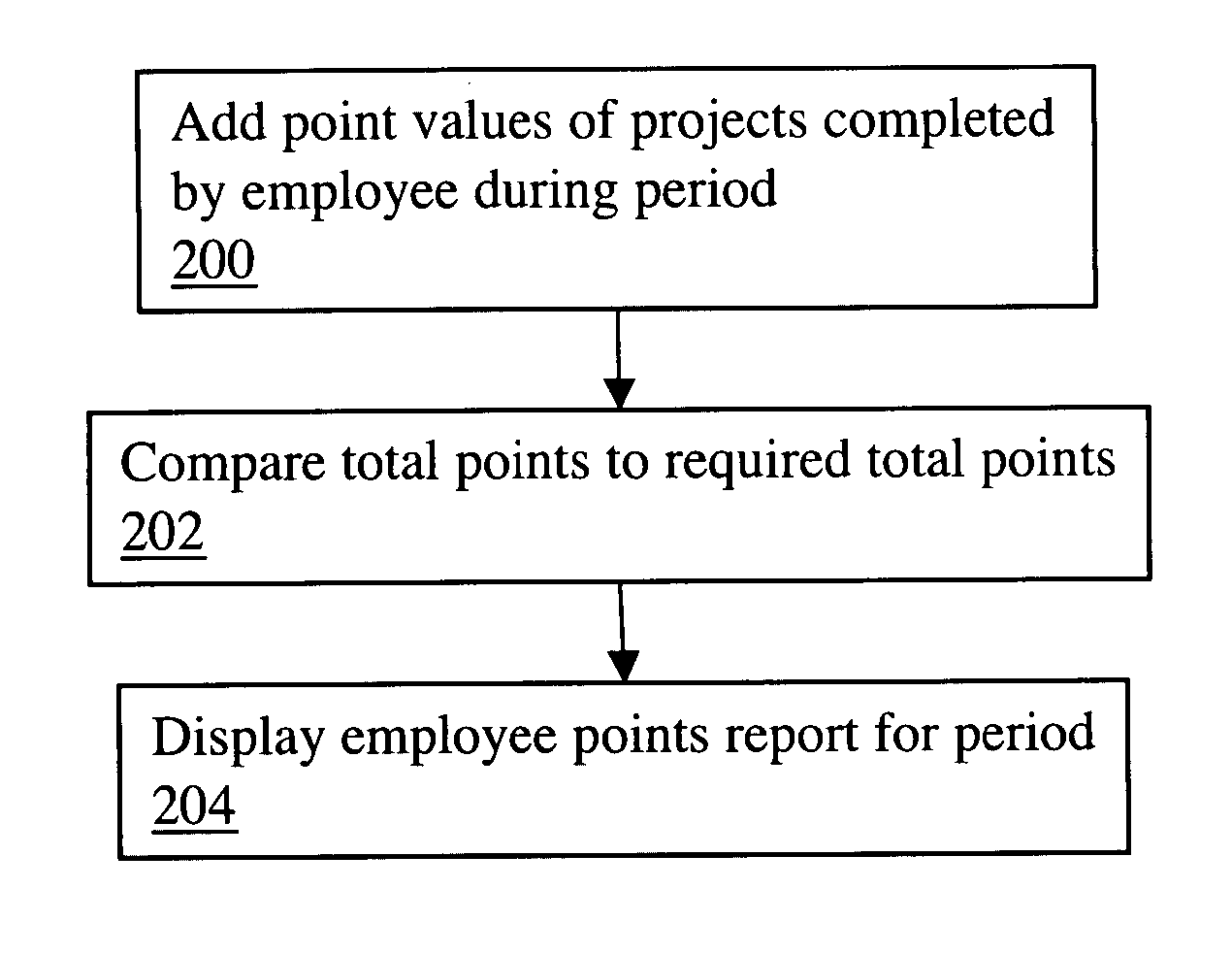
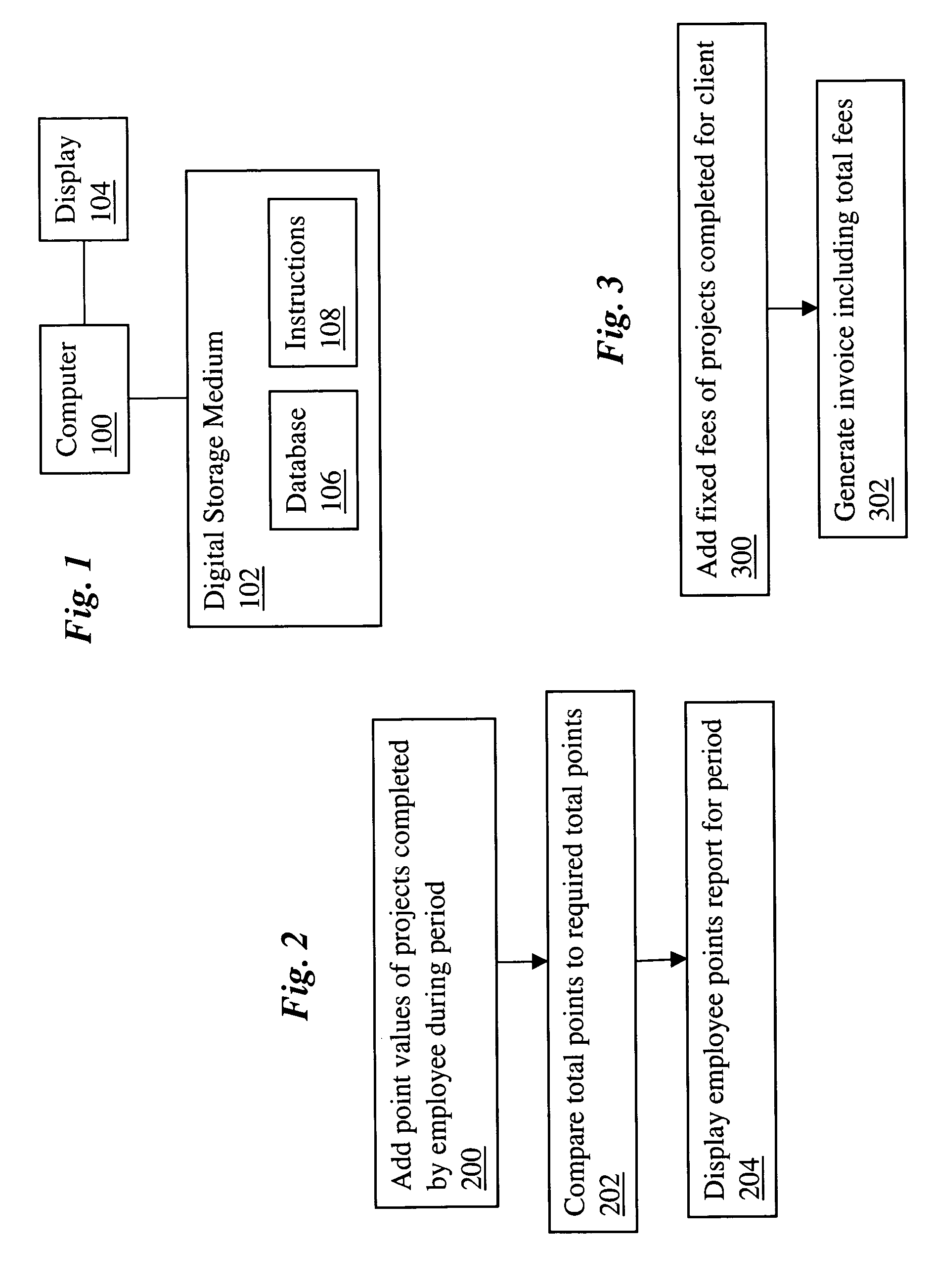
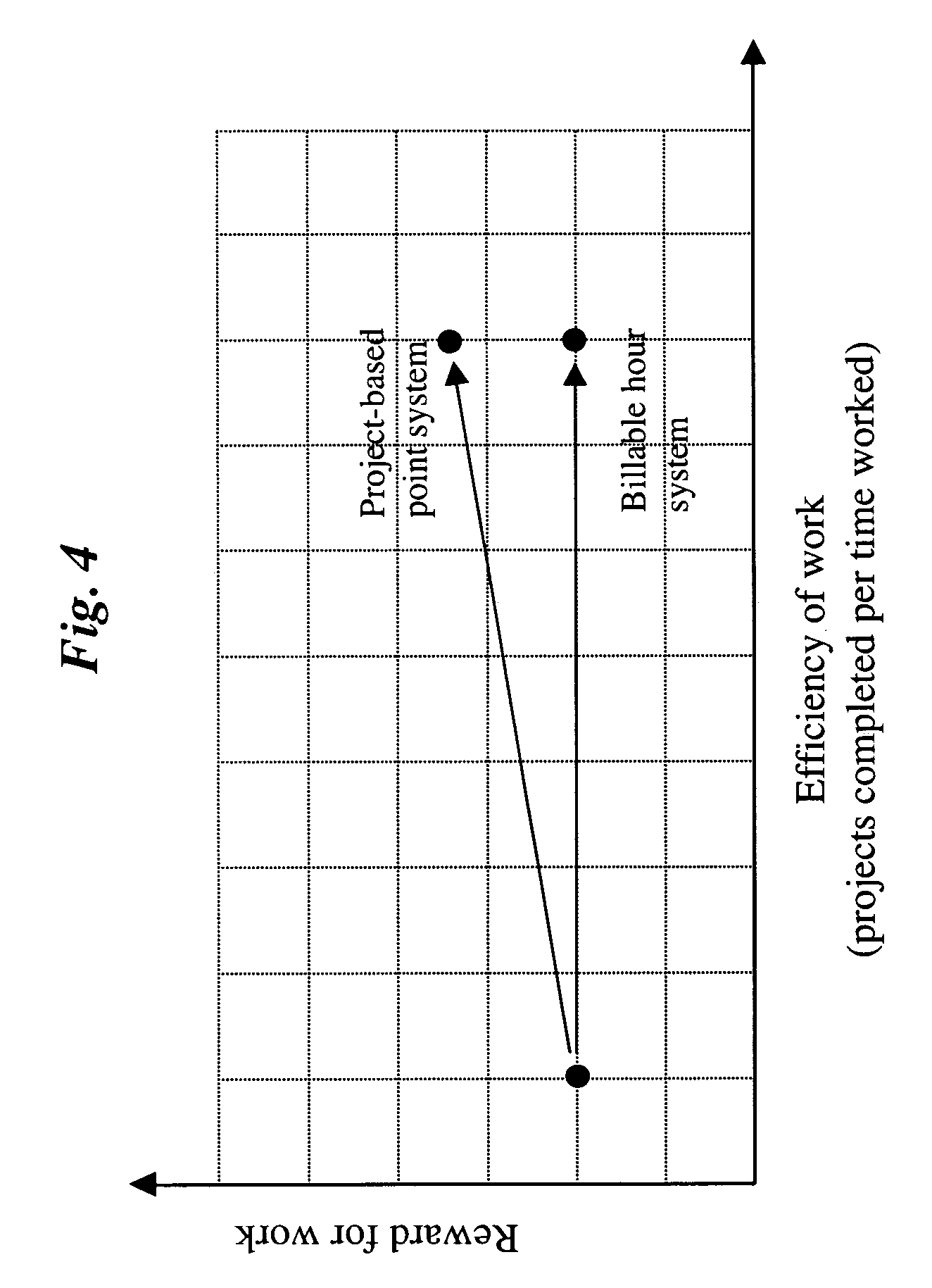
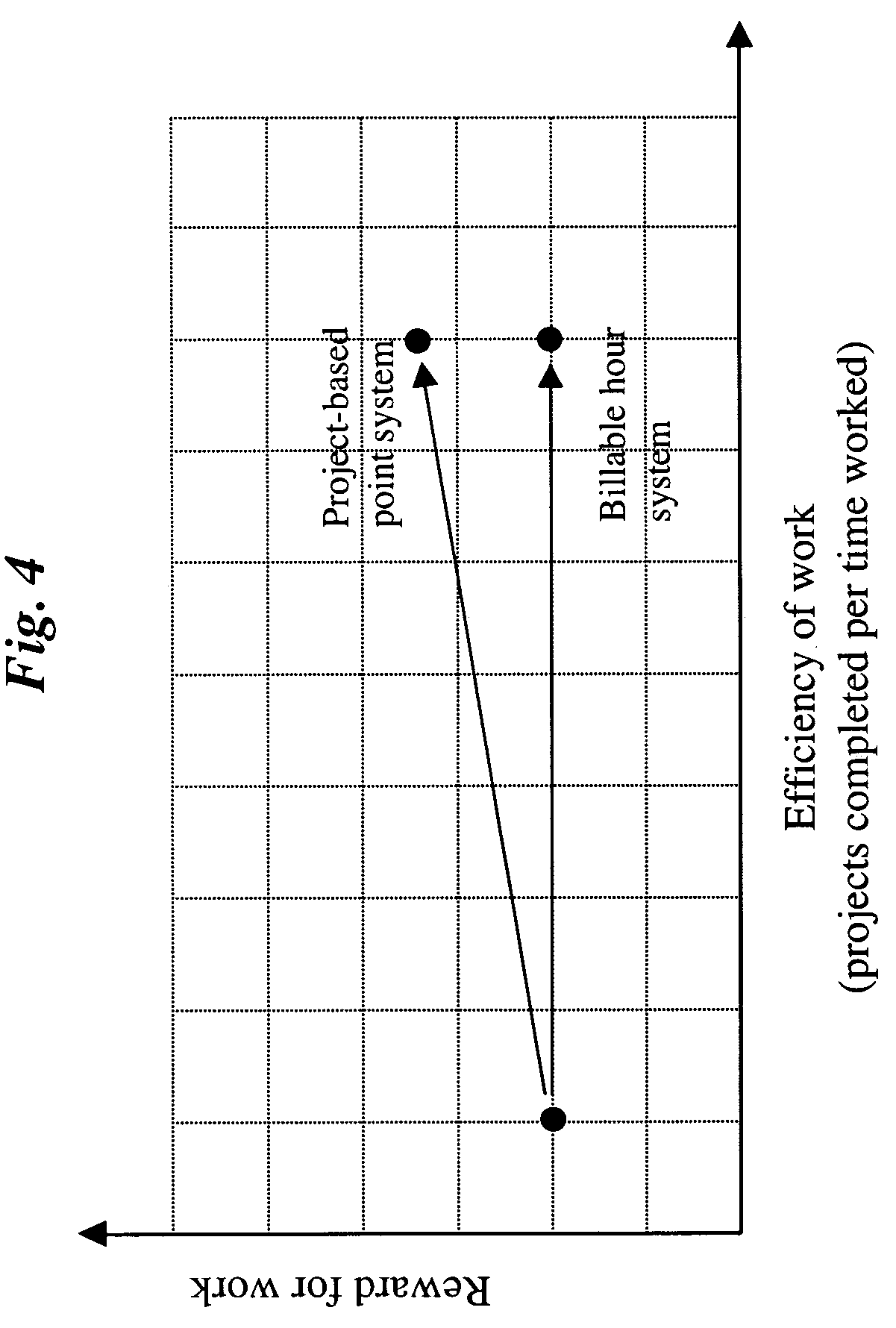
InactiveUS20070022001A1Clear processReduce demandHardware monitoringResourcesFixed chargeProject based
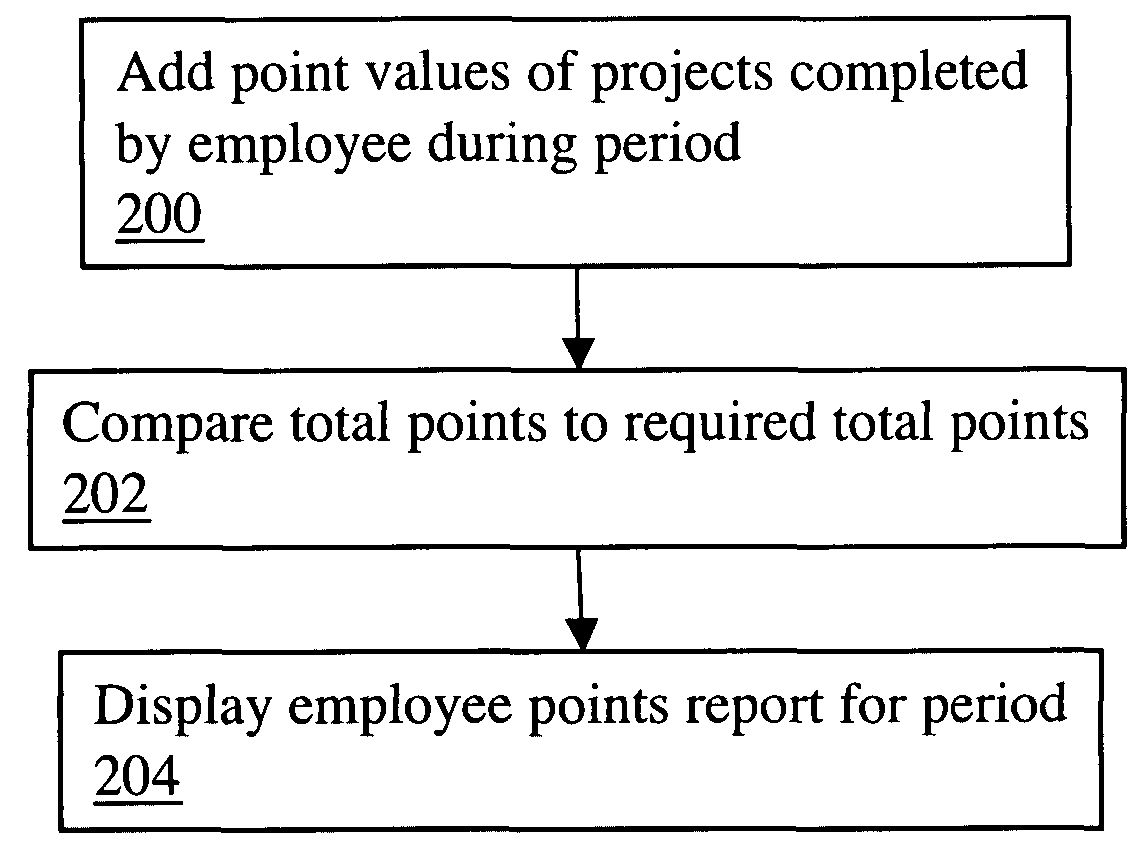
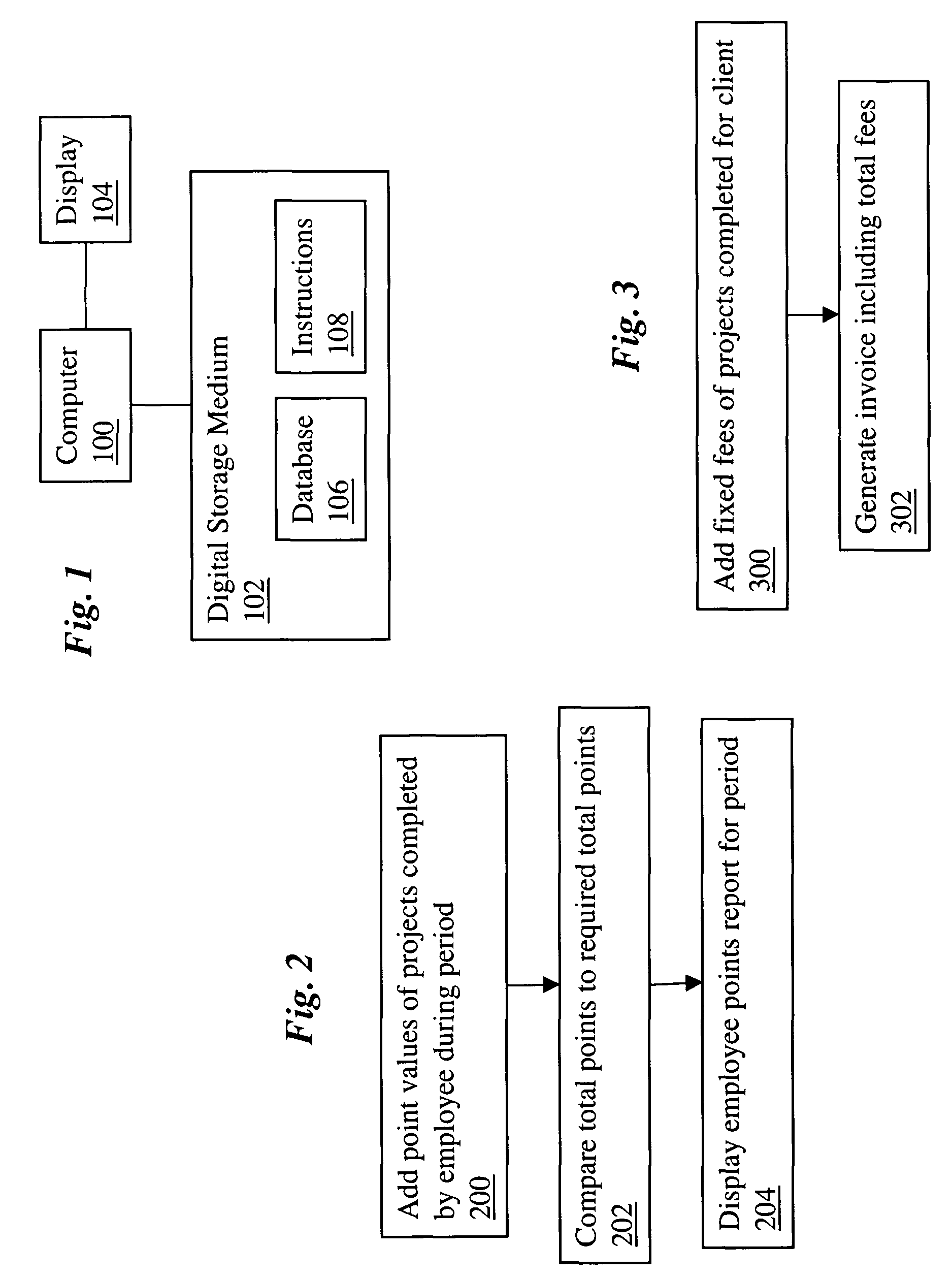
A computer-implemented project-based point system for professional services uses a database including a list of professional employees, a menu of project codes, and an assignment of a point value to each of the project codes. The method calculates total points earned by a professional by adding point values assigned to project codes of completed projects, which may be billable and / or non-billable projects. The calculated total points earned by the professional may be compared to a point requirement, whereby the performance of the professional may be evaluated. In addition, the method may calculate a total charge to a client for professional services by adding fixed fees assigned to project codes of completed billable projects.
Owner:LUMEN PATENT FIRM
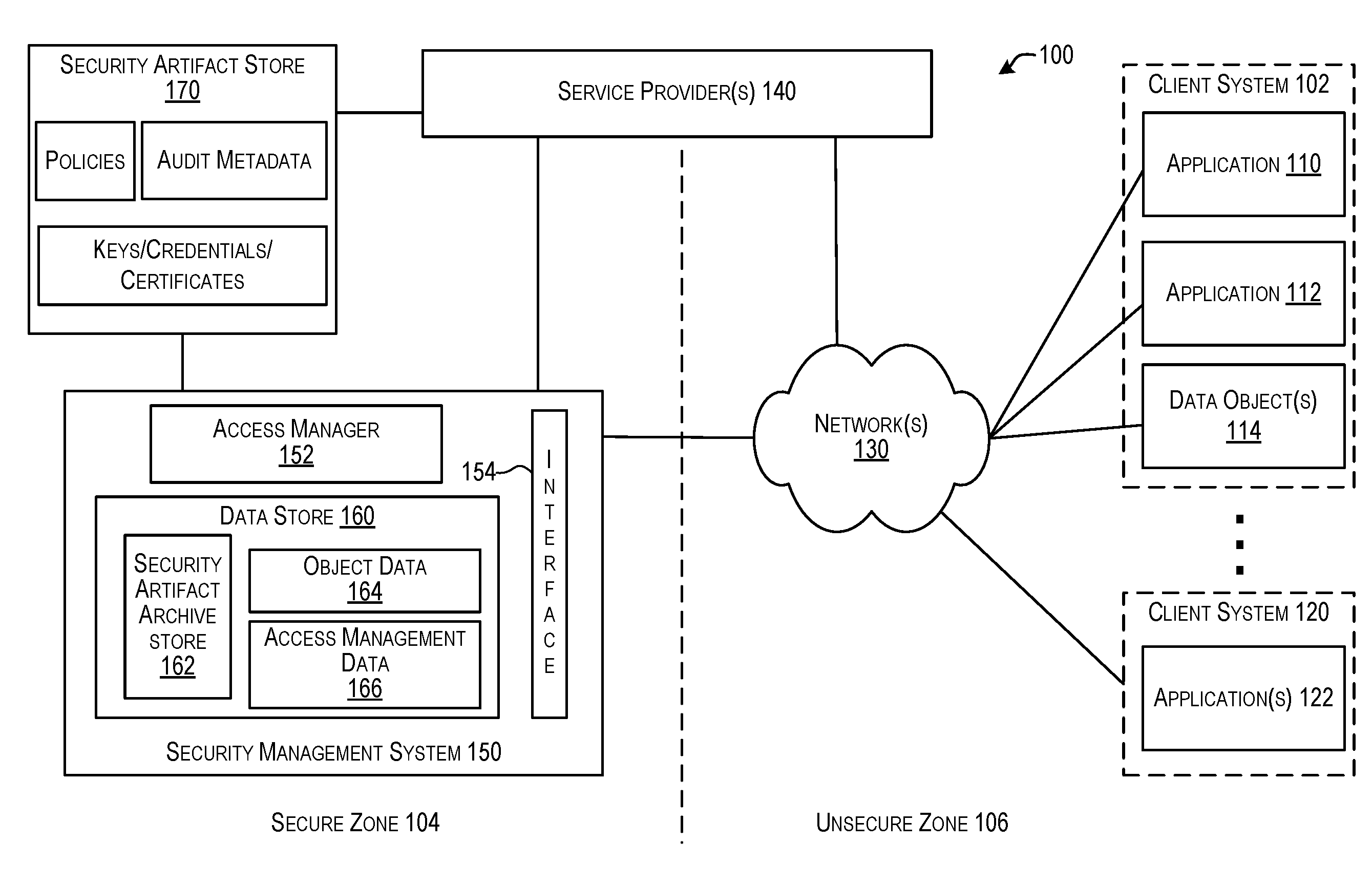
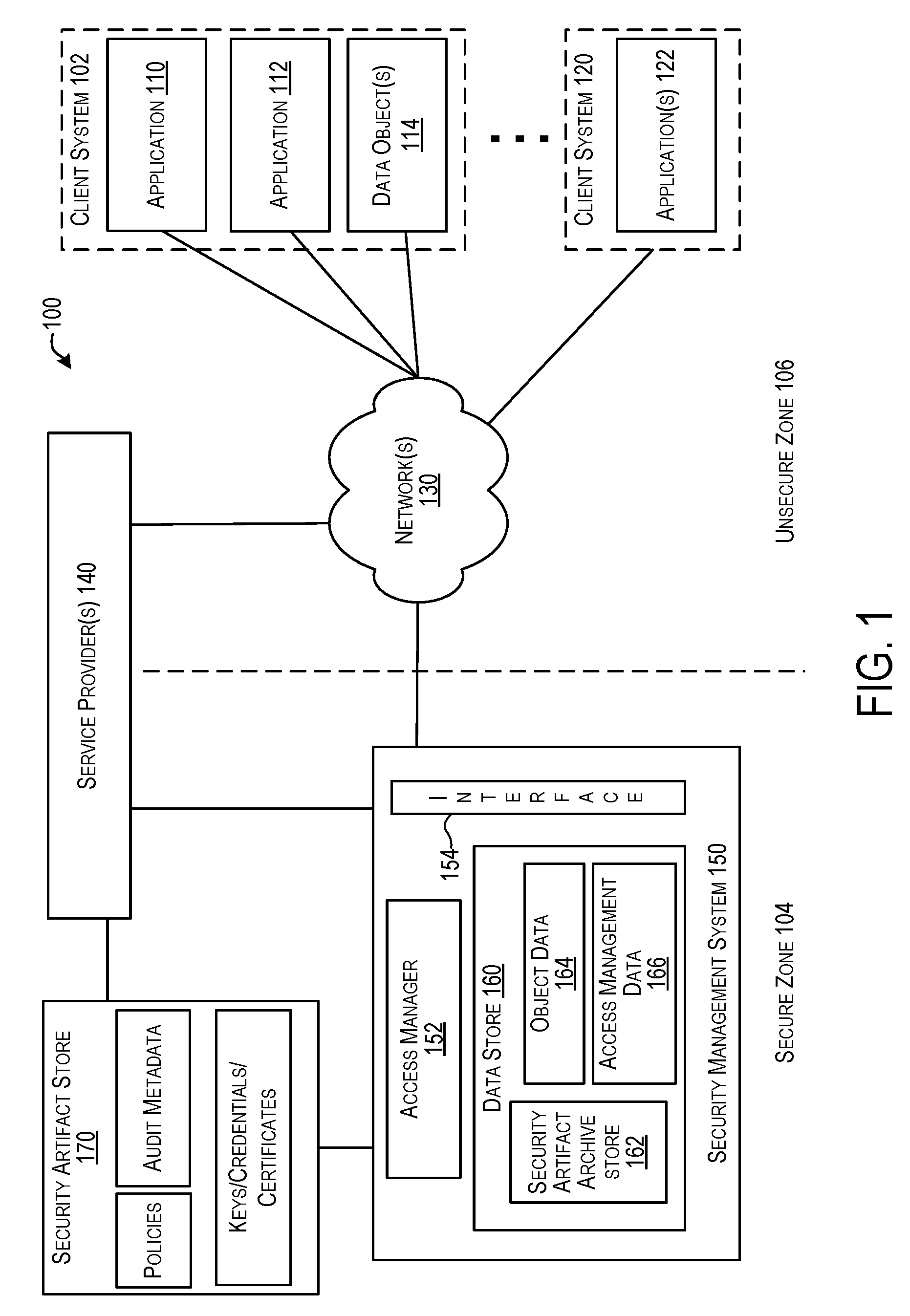
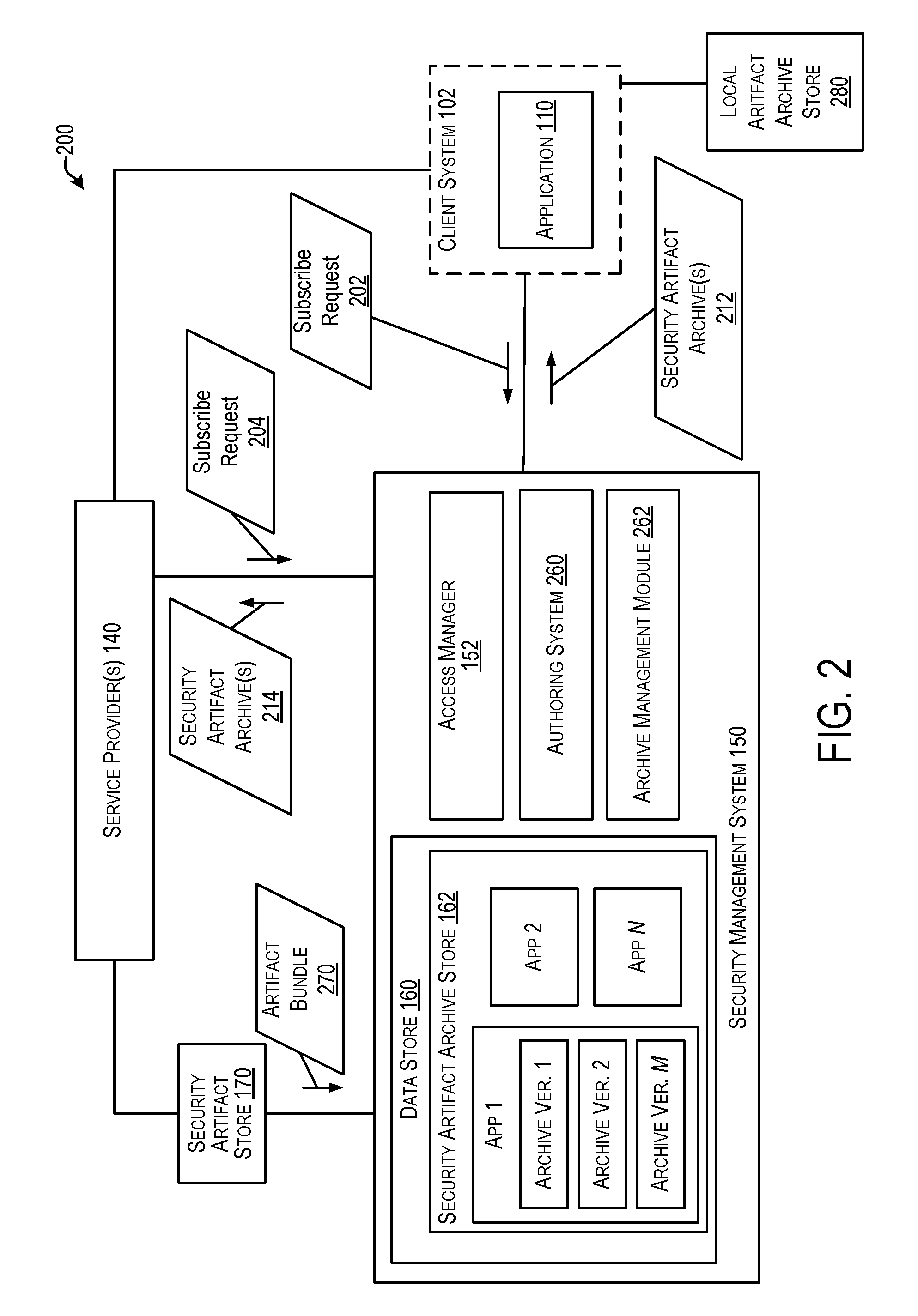
Techniques for security artifacts management
Techniques are provided to manage security artifacts. Specifically, a security management system is disclosed for implementing security artifact archives to manage security artifacts. A security artifact archive may include information for managing one or more security artifacts that can be referenced or included in the security artifact archive. The security management system can create, edit, read, send, and perform other management operations for security artifact archives. Objects can be bundled in an object-specific security artifact archive. Security artifact archives may be named, versioned, tagged and / or labeled for identification. Security artifact archives may be transmitted to a destination (e.g., a service provider or a client system) that provides access to an object whose access is dependent on security artifacts. The destination may can manage access to the object using a security artifact archive that includes relevant and current security artifacts for the object.
Owner:ORACLE INT CORP
Peer-to-peer communications
ActiveUS7596690B2Relieving peers of much of the burden of managing securityRemove burdenUser identity/authority verificationPeer-to-peerSession key
A protocol for secure peer-to-peer communications is established based on existing cryptographic techniques and encryption algorithms. The peers (120, 130, 140) and a central security agent (110) undergo mutual authentication. A newly generated nonce is used for authentication, and a random session key is used for a session. The security agent (110) generates unique session keys for communication between peers (120, 130, 140). The security agent (110) removes the burden of mutual authentication between requested peer (130, 140) and the requesting peer (120), as the security agent (110) independently authenticates the requesting peer (120) and the requested peer (130, 140). The requested peer (130, 140) and the requesting peer (120) are sent a session key by the security agent (110).
Owner:KYNDRYL INC
Digital Asset Delivery Network
InactiveUS20210049600A1Remove the burdenReduce transmission costsKey distribution for secure communicationCryptography processingDigital signatureEngineering
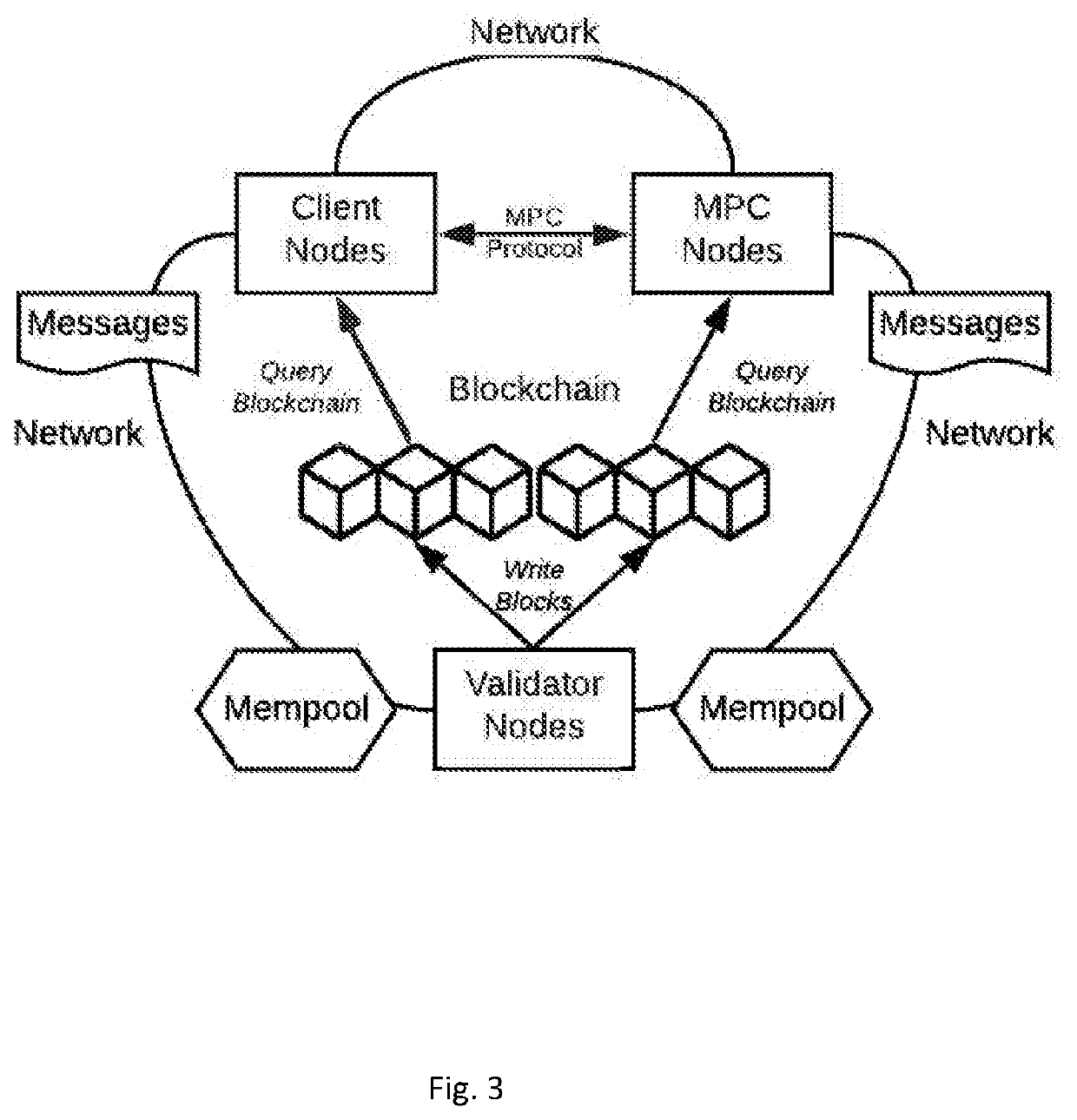
A digital asset delivery network that consists of a cryptographic scheme and a decentralized network that runs on a blockchain. The decentralized network consists of a computer program that interact with the network by issuing electronic messages, computer programs that validate those messages as entries into blockchain and agree on blocks to publish next, and computer programs that run cryptographic multi-party computation protocols. The multi-party computation protocol generates public keys necessary to create cryptocurrency or crypto asset wallets, and also generates the digital signatures necessary to create a transaction for submission to the crypto asset's underlying decentralized network and blockchain.
Owner:QREDO
Method for admixing plant essential oils to coatings for the purpose of repelling insects
The Federal EPA has consistently limited the use of known toxicants (insecticides) to preclude their admixture into paints and coatings by contractors or homeowners for the purpose of repelling or killing insects on the dried or cured coating. The current invention is a method to repel, rather than kill, insects, arachnids, and other arthropods, utilizing materials taken from the EPA's GRAS (Generally Recognized as Safe) List, obviating onerous Federal Insecticide, Fungicide, and Rodenticide Act (FIFRA) regulations and greatly extending the useful life of the insect-repellant materials by binding them into the dried film solids—greatly slowing their evaporation and degradation and creating a timed release of insect repellant material. Furthermore, the current invention utilizes the insect repellant nature of these materials to repel insects from the surrounding area during coating application, thereby eliminating the need for applying insect repellants, such as DEET, to the skin.
Owner:CTA PROD GRP
Energy measuring apparatus and energy measurement information labeling system using same
ActiveUS20150233984A1Remove the burdenReduce time delayCircuit monitoring/indicationElectric devicesData setPattern matching
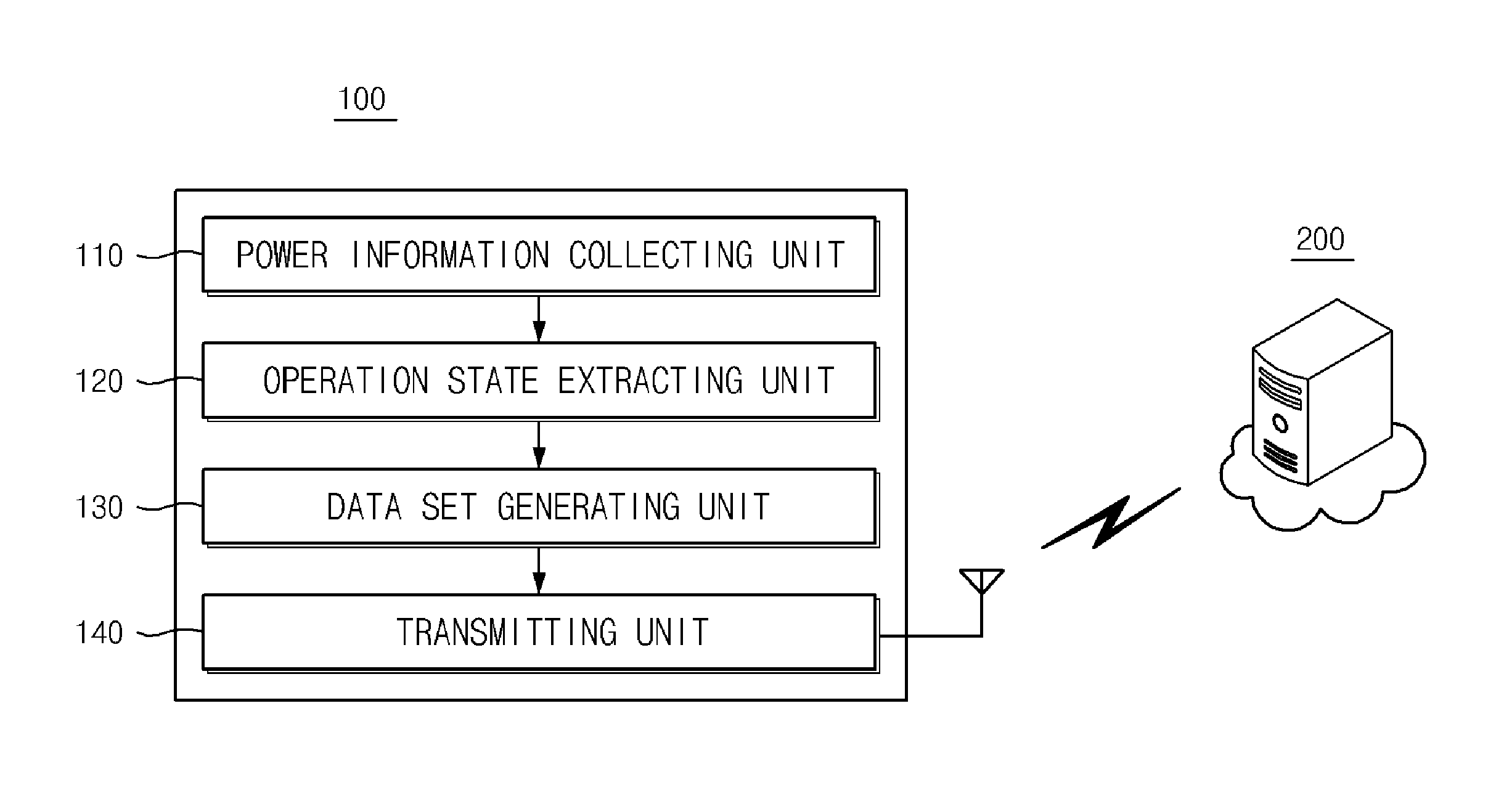
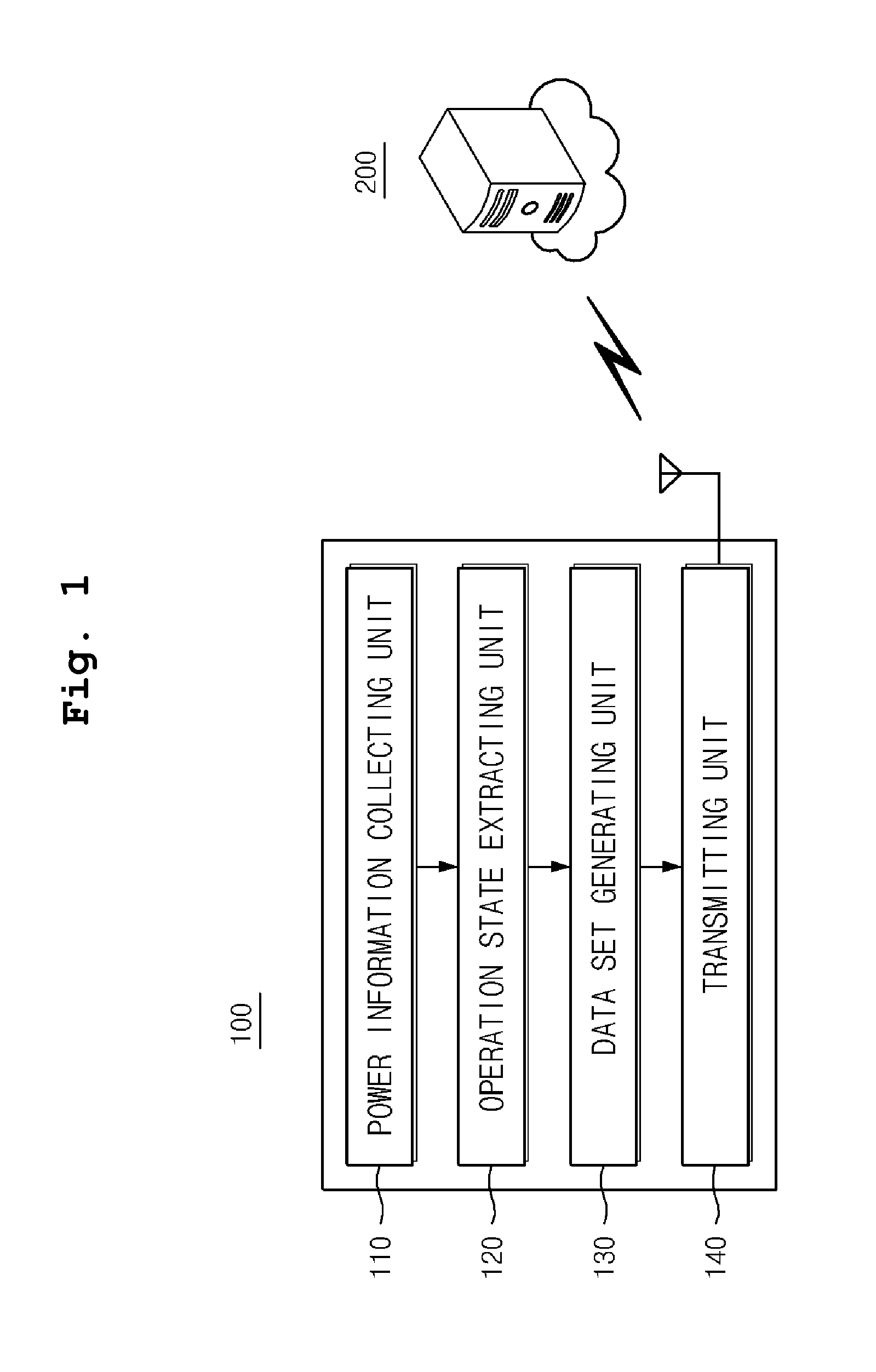
An energy measuring apparatus includes: a power information collecting unit for collecting the power information including the power signal at least one penetration point of power for the multiple facility equipments; an operating state extracting unit for extracting the operating state or the changing pattern of the operating state of facility equipments by classifying the normal state and the transitional state of the power change from the collected power information; and a data set generating unit for generating data sets for the individual facility equipment matching with operating state or the changing pattern of operating state through the signal correlations according to the power consumption characteristic of individual facility equipments.
Owner:ENCORED TECH
Method for admixing plant essential oils to coatings for the purpose of repelling insects
ActiveUS20090155394A1Remove the burdenLessening human health riskBiocideDead animal preservationToxicantEvaporation
The Federal EPA has consistently limited the use of known toxicants (insecticides) to preclude their admixture into paints and coatings by contractors or homeowners for the purpose of repelling or killing insects on the dried or cured coating. The current invention is a method to repel, rather than kill, insects, arachnids, and other arthropods, utilizing materials taken from the EPA's GRAS (Generally Recognized as Safe) List, obviating onerous Federal Insecticide, Fungicide, and Rodenticide Act (FIFRA) regulations and greatly extending the useful life of the insect-repellant materials by binding them into the dried film solids—greatly slowing their evaporation and degradation and creating a timed release of insect repellant material. Furthermore, the current invention utilizes the insect repellant nature of these materials to repel insects from the surrounding area during coating application, thereby eliminating the need for applying insect repellants, such as DEET, to the skin.
Owner:CTA PROD GRP
Instant customer service feedback system
ActiveUS20160125484A1Low transparencyHigh transparencyTransmissionMarketingDisplay deviceClient-side
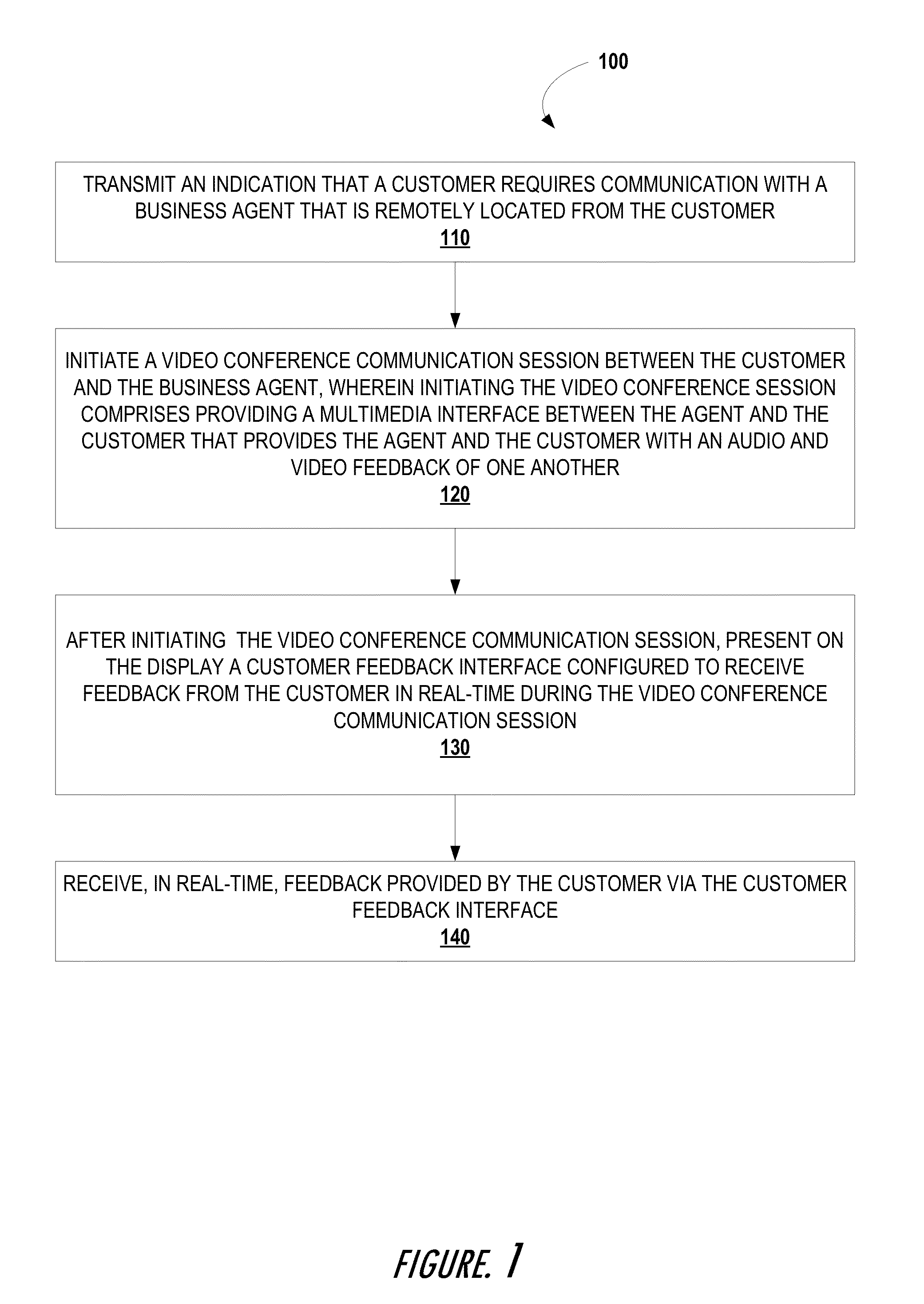
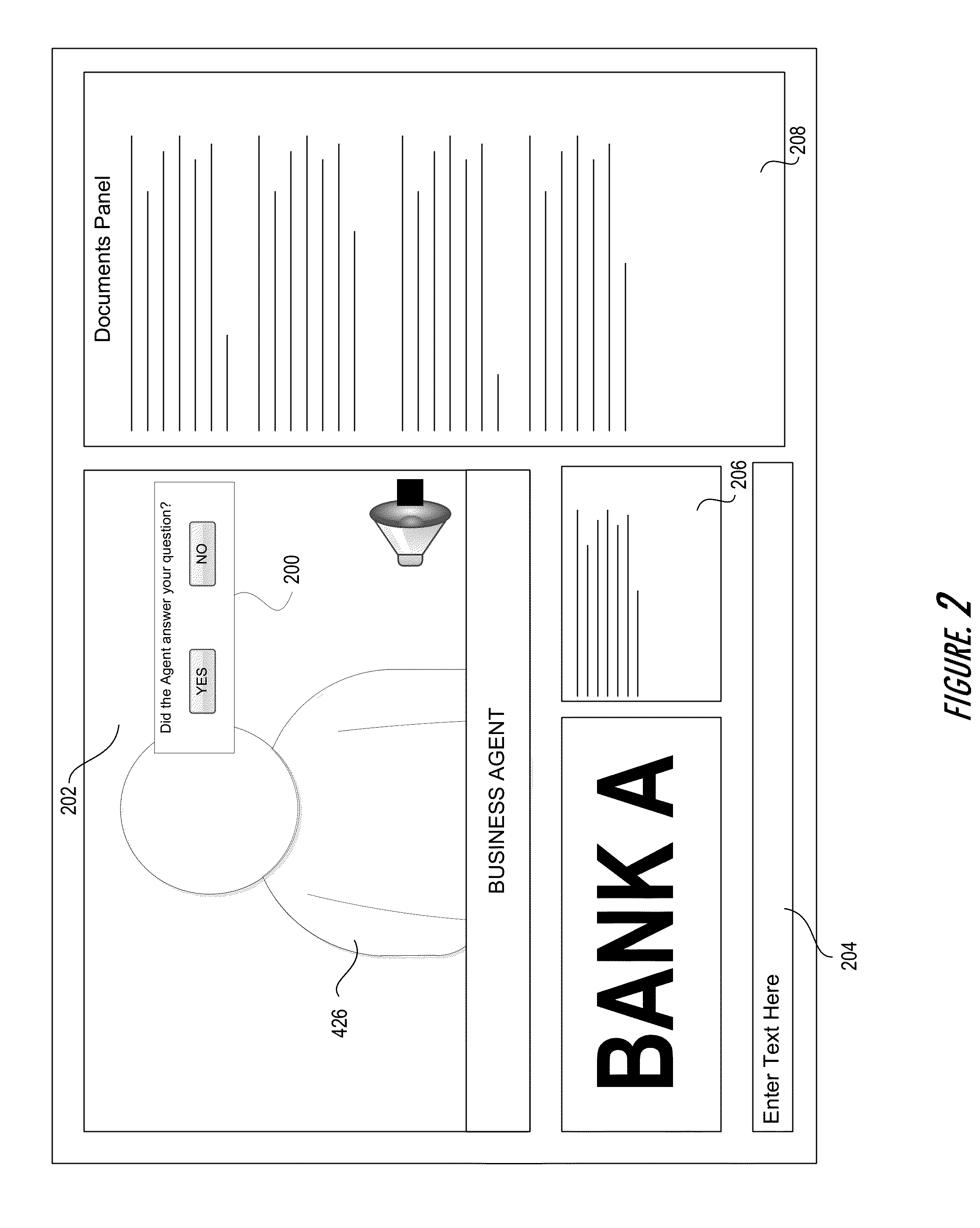
Embodiments of the invention provide instant customer service feedback during a communication session with the customer. The system initiate a video conference communication session between the customer and the business agent that comprises providing a multimedia interface between the agent and the customer that provides the agent and the customer with an audio and video feedback of one another. After initiating the video conference communication session, a customer feedback interface configured to receive feedback from the customer in real-time during the video conference communication session is presented on the display of the customers apparatus such that the system may receive, in real-time, feedback provided by the customer via the customer feedback interface.
Owner:BANK OF AMERICA CORP
Professional service management using project-based point system
InactiveUS7756738B2Reduce demandRemove burdenMultiprogramming arrangementsResourcesFixed billFixed charge
A computer-implemented project-based point system for professional services uses a database including a list of professional employees, a menu of project codes, and an assignment of a point value to each of the project codes. The method calculates total points earned by a professional by adding point values assigned to project codes of completed projects, which may be billable and / or non-billable projects. The calculated total points earned by the professional may be compared to a point requirement, whereby the performance of the professional may be evaluated. In addition, the method may calculate a total charge to a client for professional services by adding fixed fees assigned to project codes of completed billable projects.
Owner:LUMEN PATENT FIRM
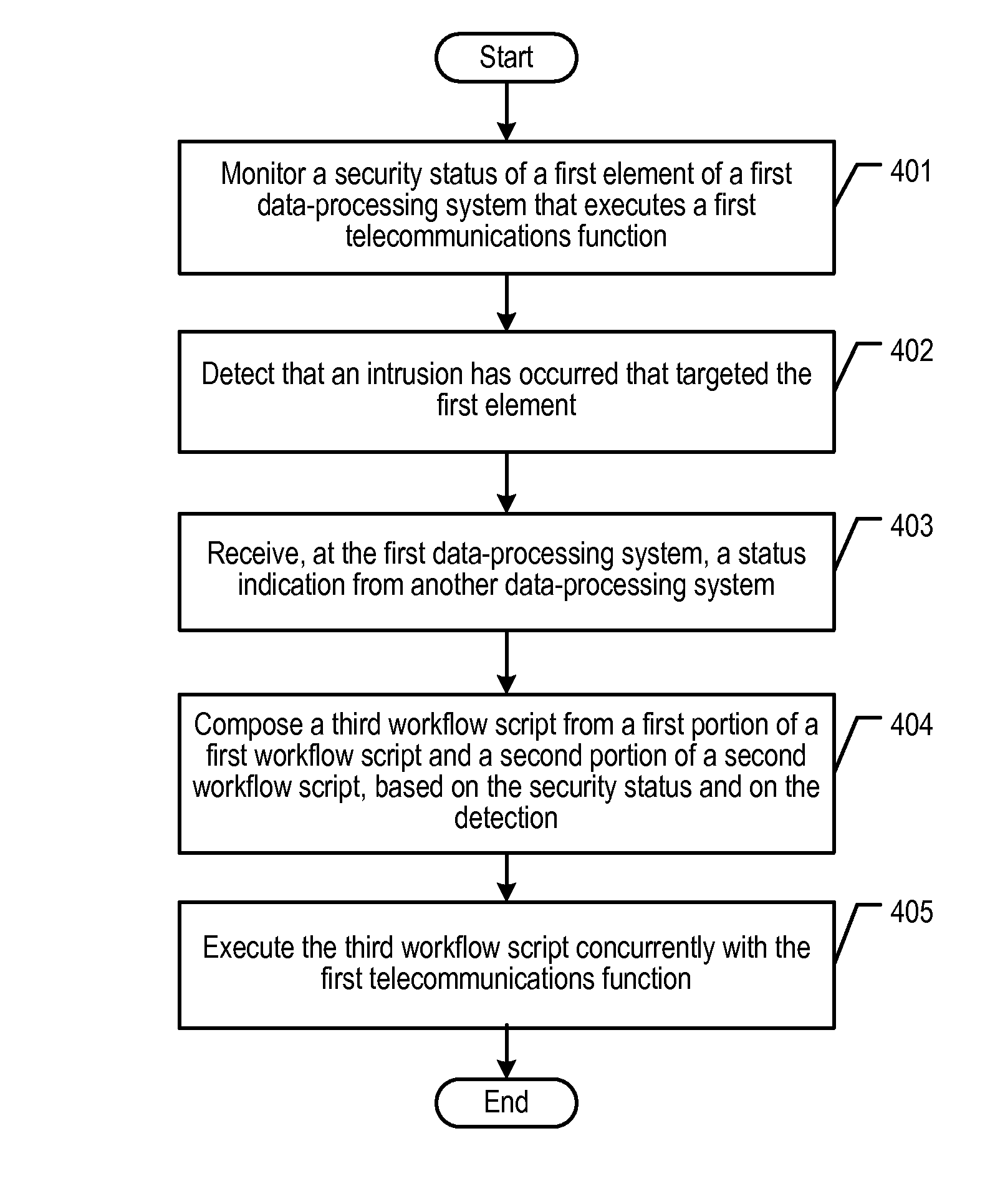
Self-Operating Security Platform
InactiveUS20080127343A1Remove the burdenRemove burdenMemory loss protectionError detection/correctionMonitoring systemOrchestration
A platform is disclosed that enables security monitoring and protection across a plurality of related telecommunications devices. The self-operating security platform of the present invention is based on a collection of security adapters that are tied together and are coupled with an orchestration engine that loads and executes workflow scripts. Workflow scripts have been used for business applications, but their usage in real-time telecommunications devices is relatively new. Each security adapter monitors a different aspect of the system for intrusions or other security threats. The specific security protection rules are taught to the security platform in a basic profile; as the security platform runs, it builds up the actual profile of how the telecommunications device performs in a normal state. In other words, the security platform “composes” new workflow scripts from basic workflow scripts. The self-expanding nature of the workflow enables the telecommunications device to learn the behavioral patterns of its users.
Owner:AVAYA INC
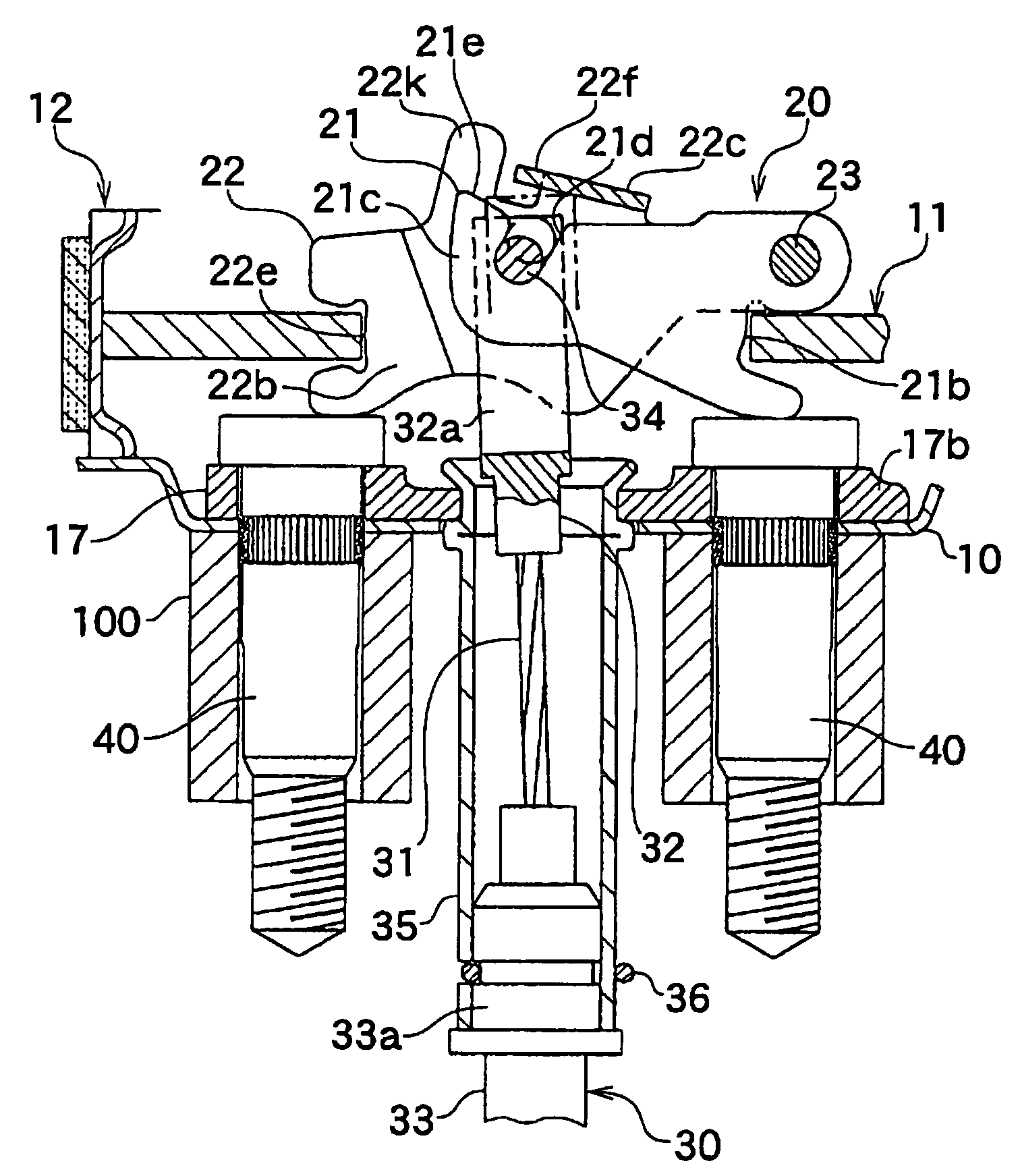
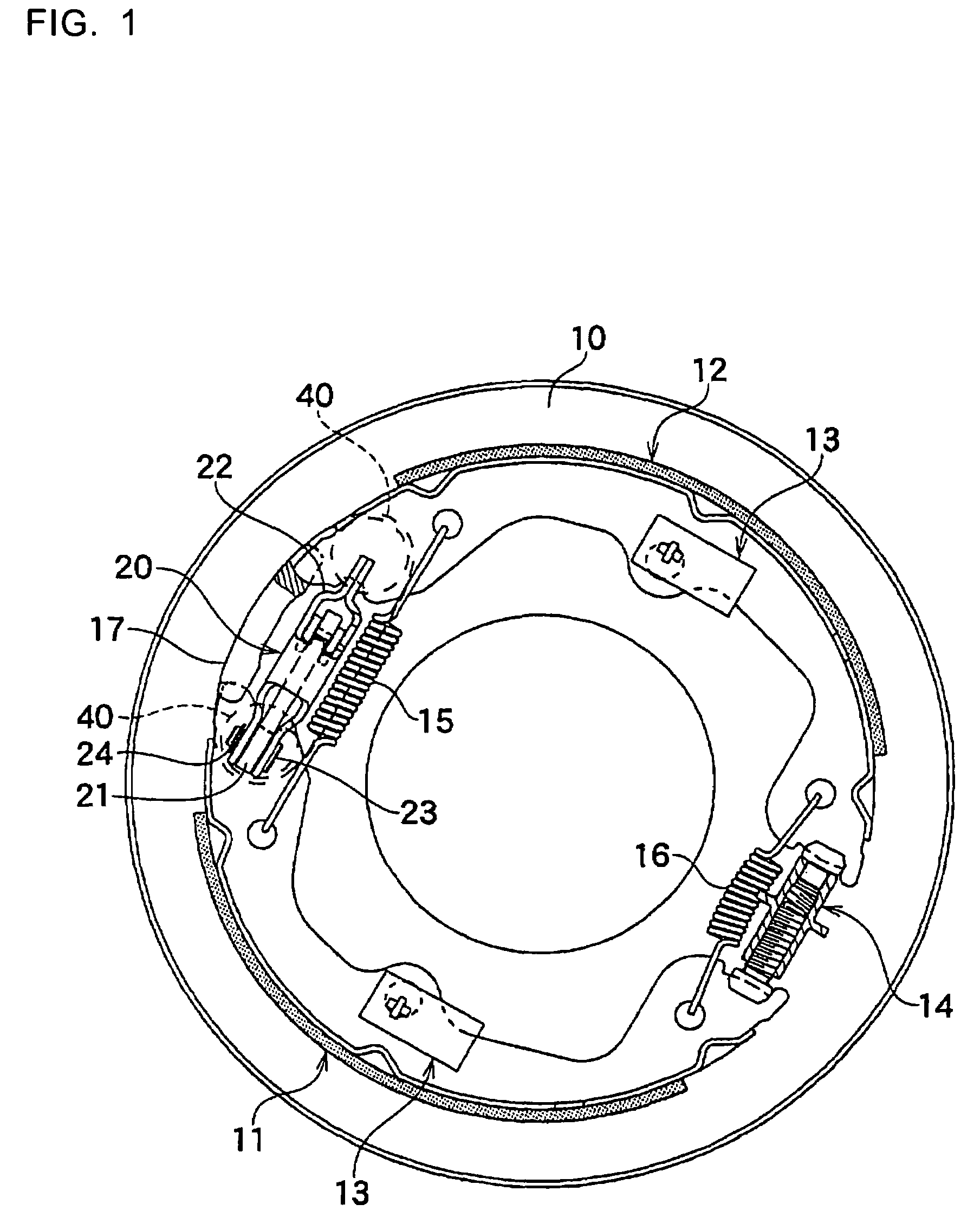
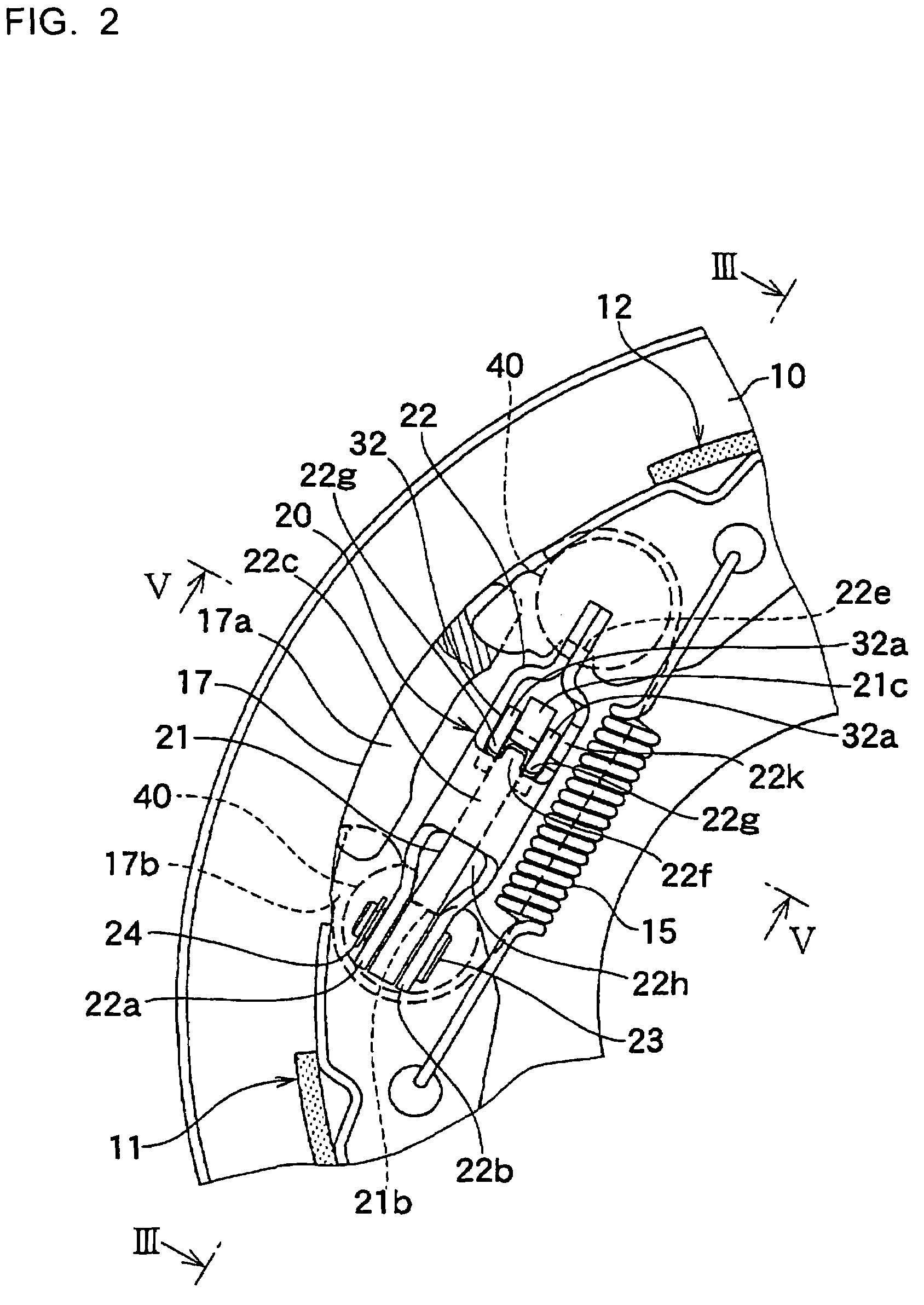
Brake cable connecting apparatus
InactiveUS7434668B2Reduce the burden onRemove burdenBraking element arrangementsDrum brakesInsertion depthEngineering
Owner:NISSHINBO IND INC
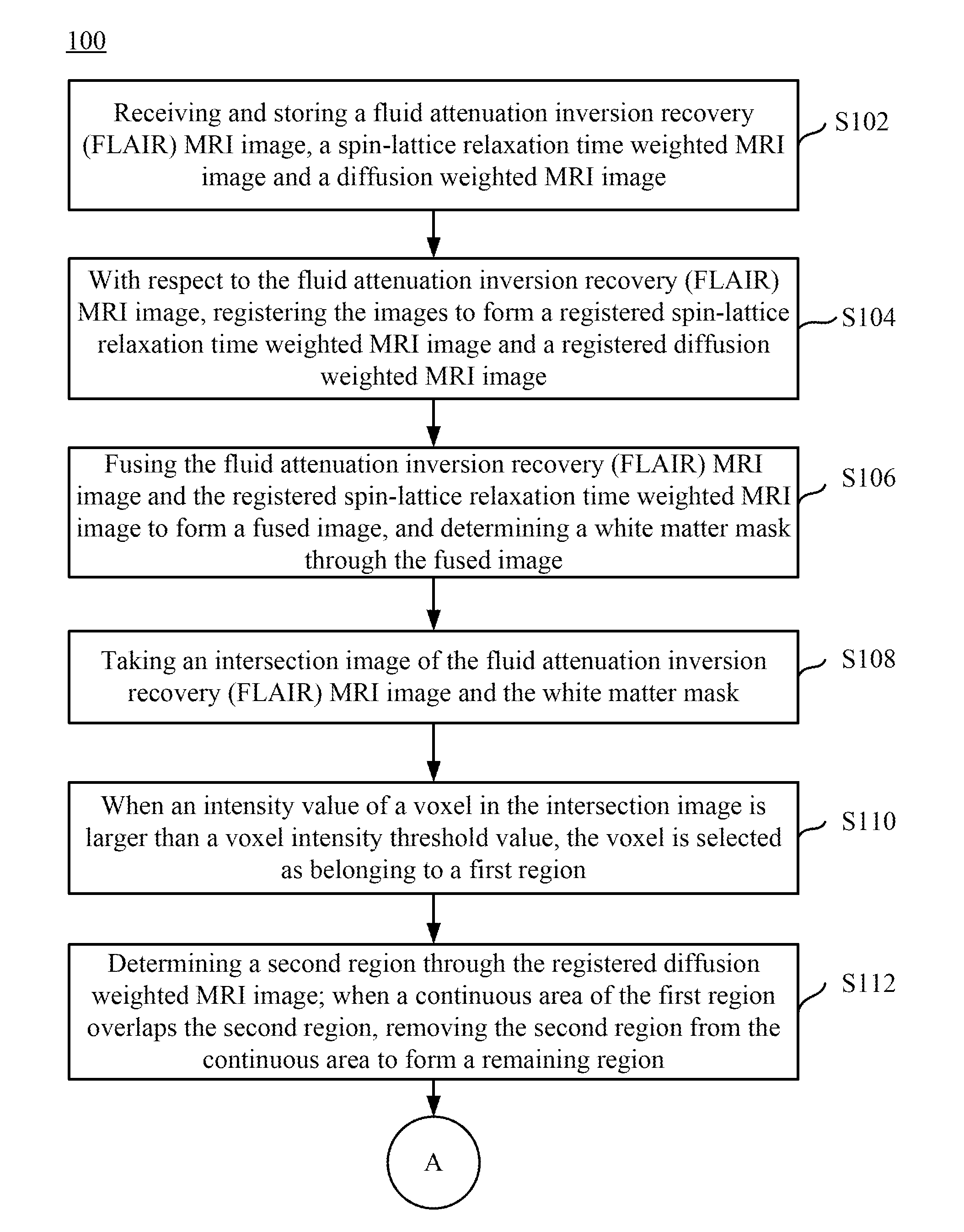
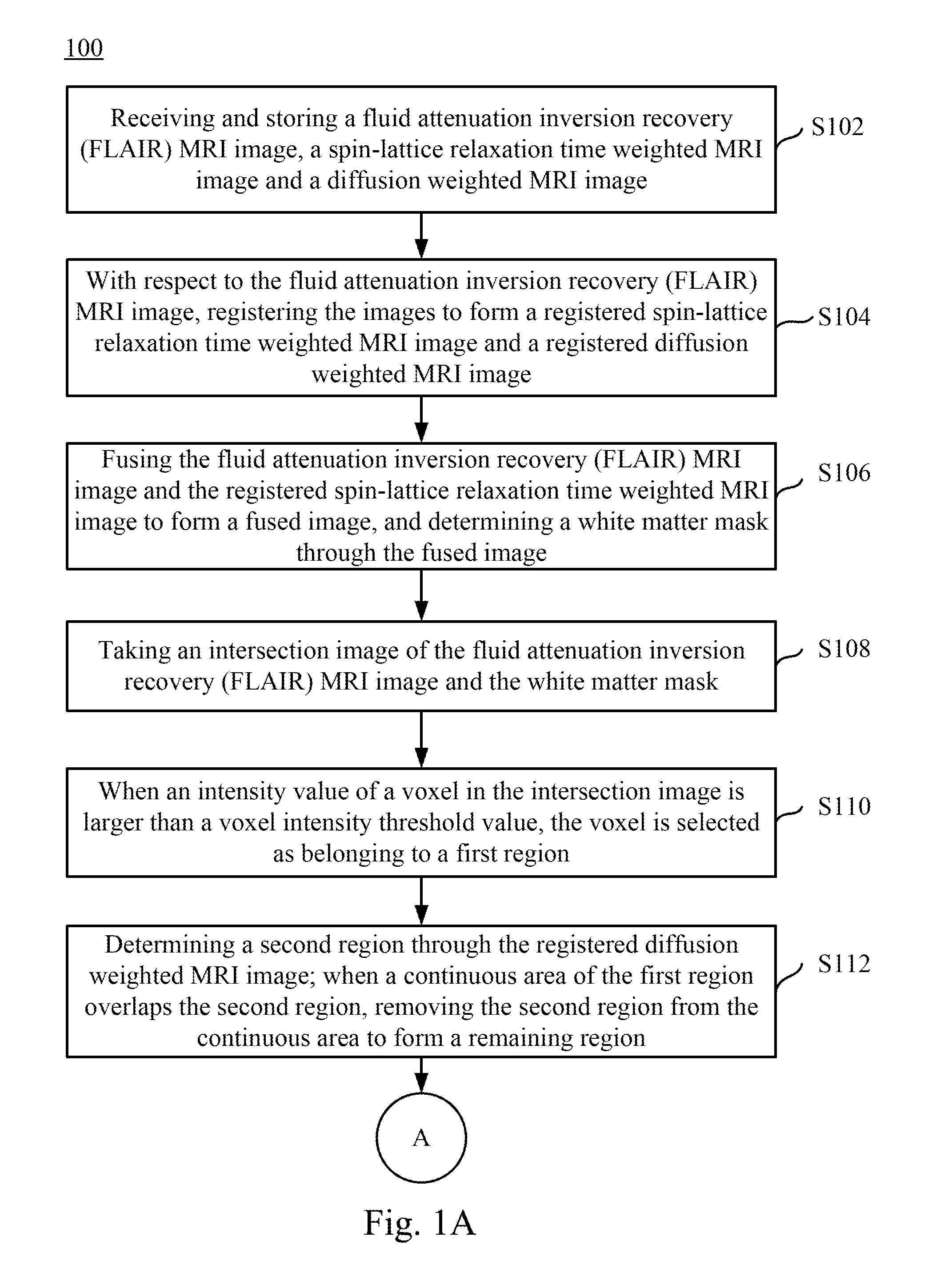
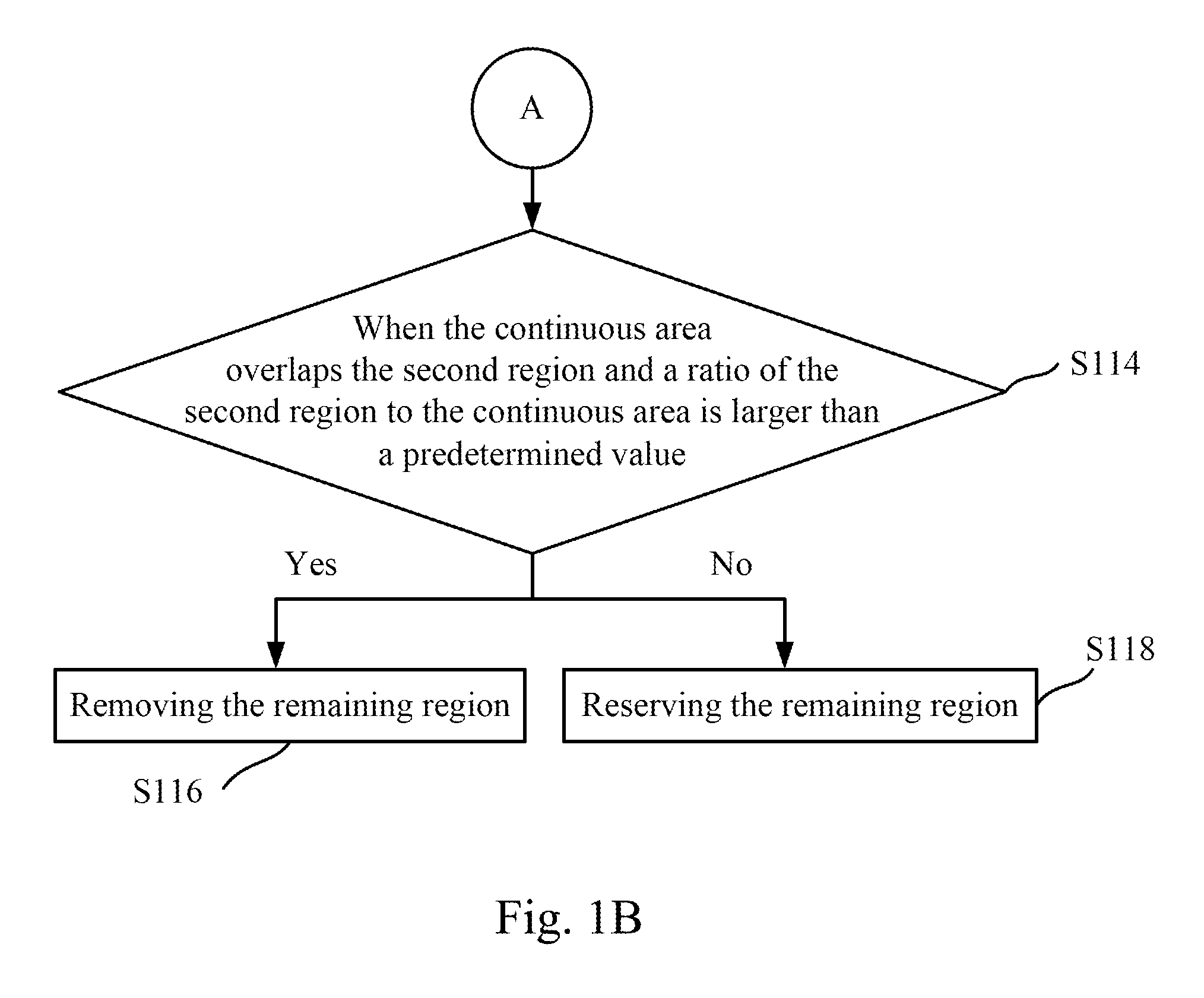
Magnetic resonance imaging white matter hyperintensities region recognizing method and system
ActiveUS20160196644A1Remove burdenImprove recognition efficiencyImage enhancementImage analysisWhite matterMri image
A magnetic resonance imaging white matter hyperintensities region recognizing method and system are disclosed herein. The white matter hyperintensities region recognizing method includes receiving and storing a FLAIR MRI image, a spin-lattice relaxation time weighted MRI image, and a diffusion weighted MRI image. Registration and fusion are preformed, and a white matter mask is determined. An intersection image of the FLAIR MRI image and the white matter mask is taken, a first region is determined after normalizing the intersection image, a cerebral infarct region is removed from the first image through the diffusion weighted MRI image, and then a determination is made as to whether to remove a remaining region in order to form a white matter hyperintensities region in the FLAIR MRI image.
Owner:NAT CENT UNIV +1
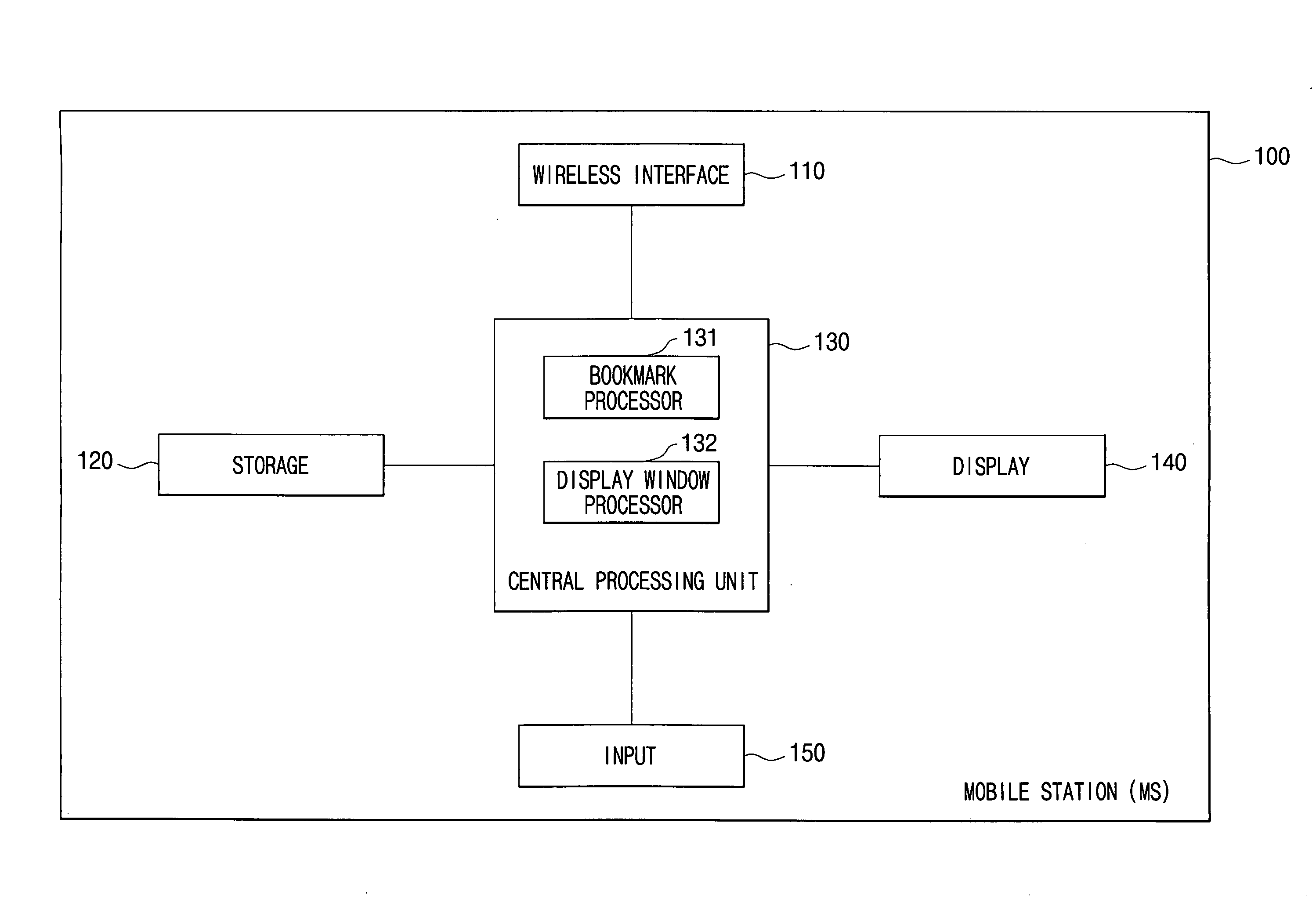
Method and apparatus of displaying output of mobile station
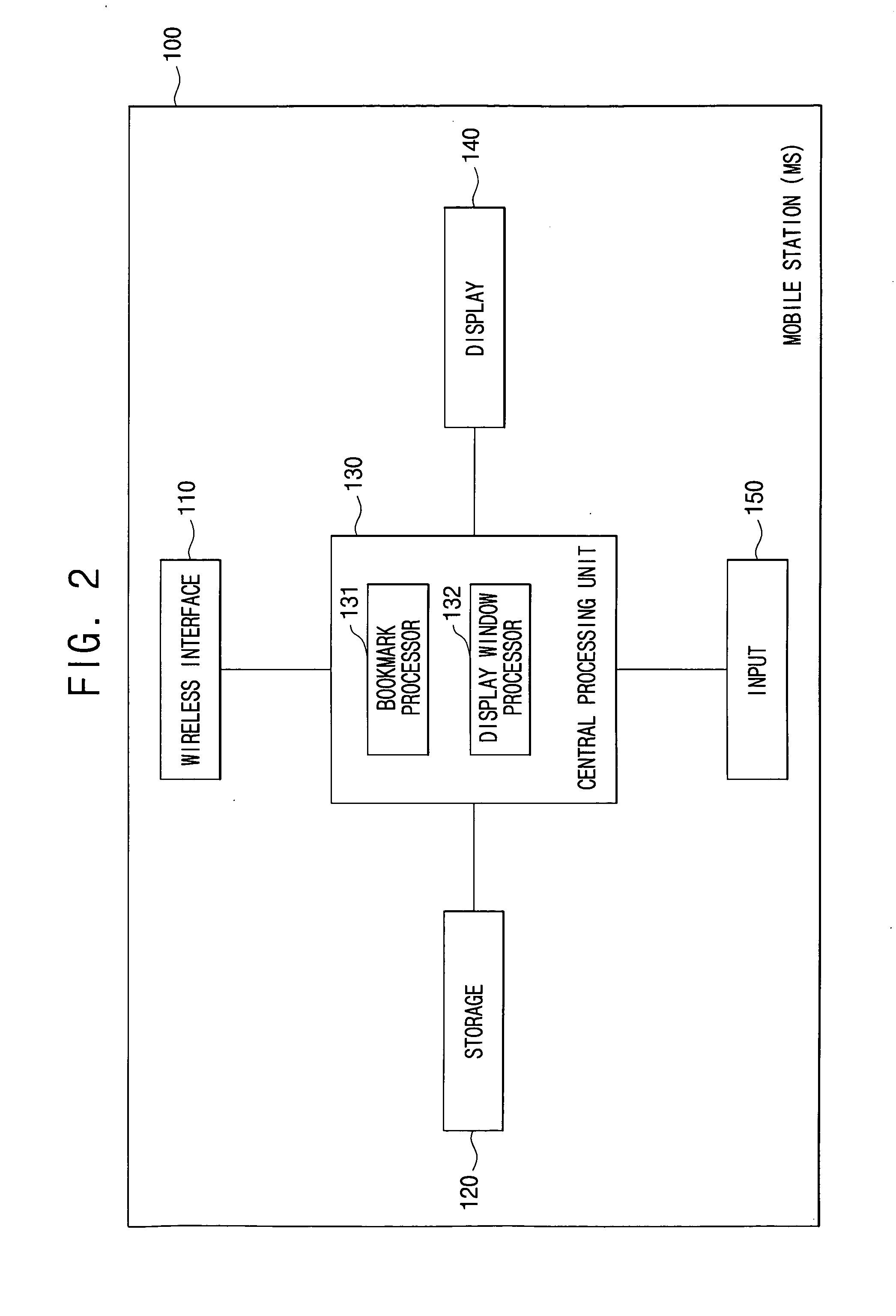
ActiveUS20090131118A1Remove burdenEliminating trouble causedSubstation equipmentTransmissionMobile communication networkWeb page
A mobile station includes a wireless interface, which gains wireless access to Internet via a BTS of a mobile communication network, a storage, which stores bookmark information including information on a title, a URL, or a display mode of at least one WAP page / Web page, a display, which displays the WAP / Web page, an input, which receives the information on the title, the URL, or the display mode of the WAP / Web page, and a central processing unit, which stores the bookmark information, including the information on the title, the URL, or the display mode of the WAP / Web page input through the input, in the storage, and displays the WAP / Web page, based on data downloaded from a server on the Internet accessed through the wireless interface, through the display using the display mode information corresponding to the title information or the URL information of the WAP / Web page.
Owner:SAMSUNG ELECTRONICS CO LTD
Image forming system, image forming apparatus, and image forming processing method
ActiveUS8243303B2Remove burdenEasy to operateVisual presentationPictoral communicationCommunication unitImage formation
Owner:KONICA MINOLTA BUSINESS TECH INC
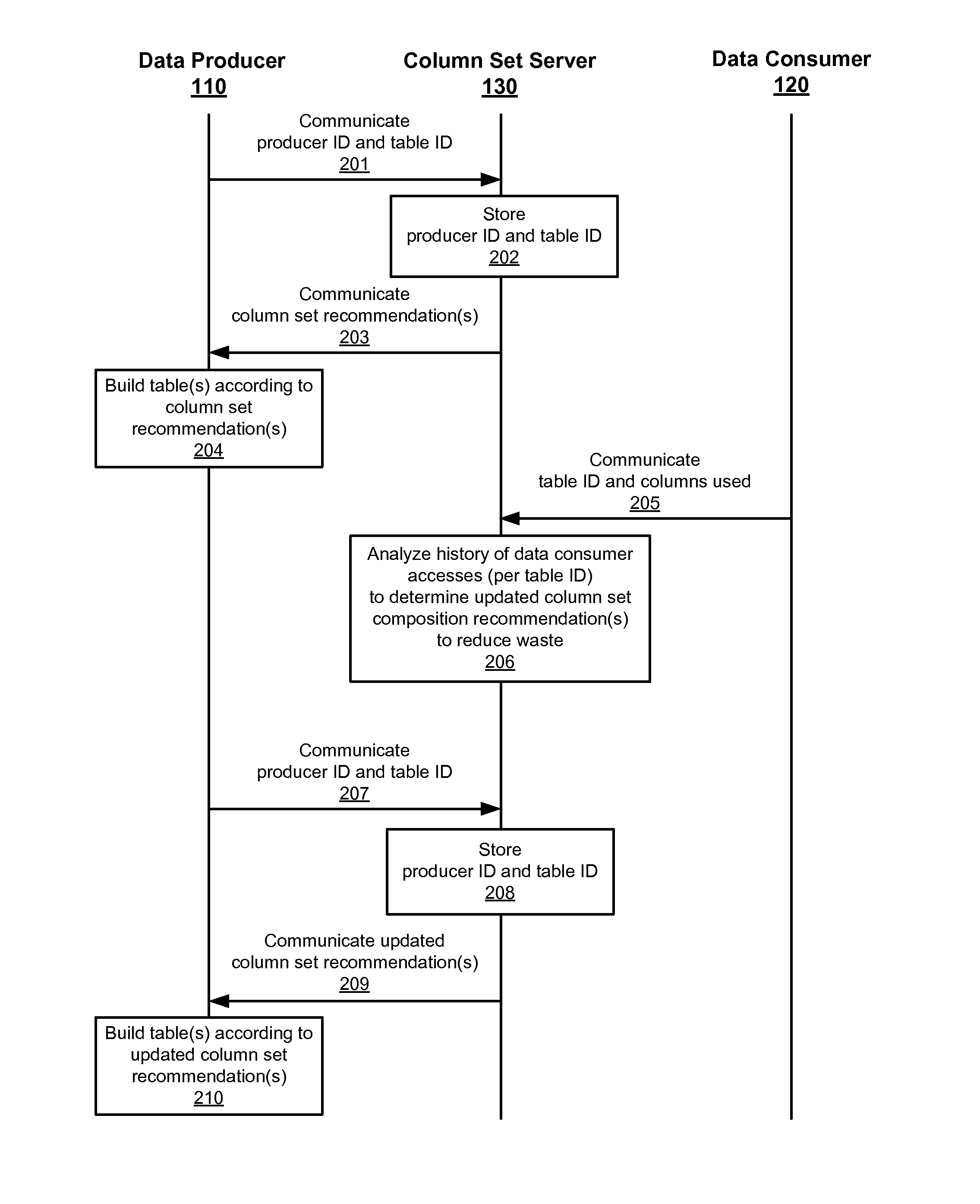
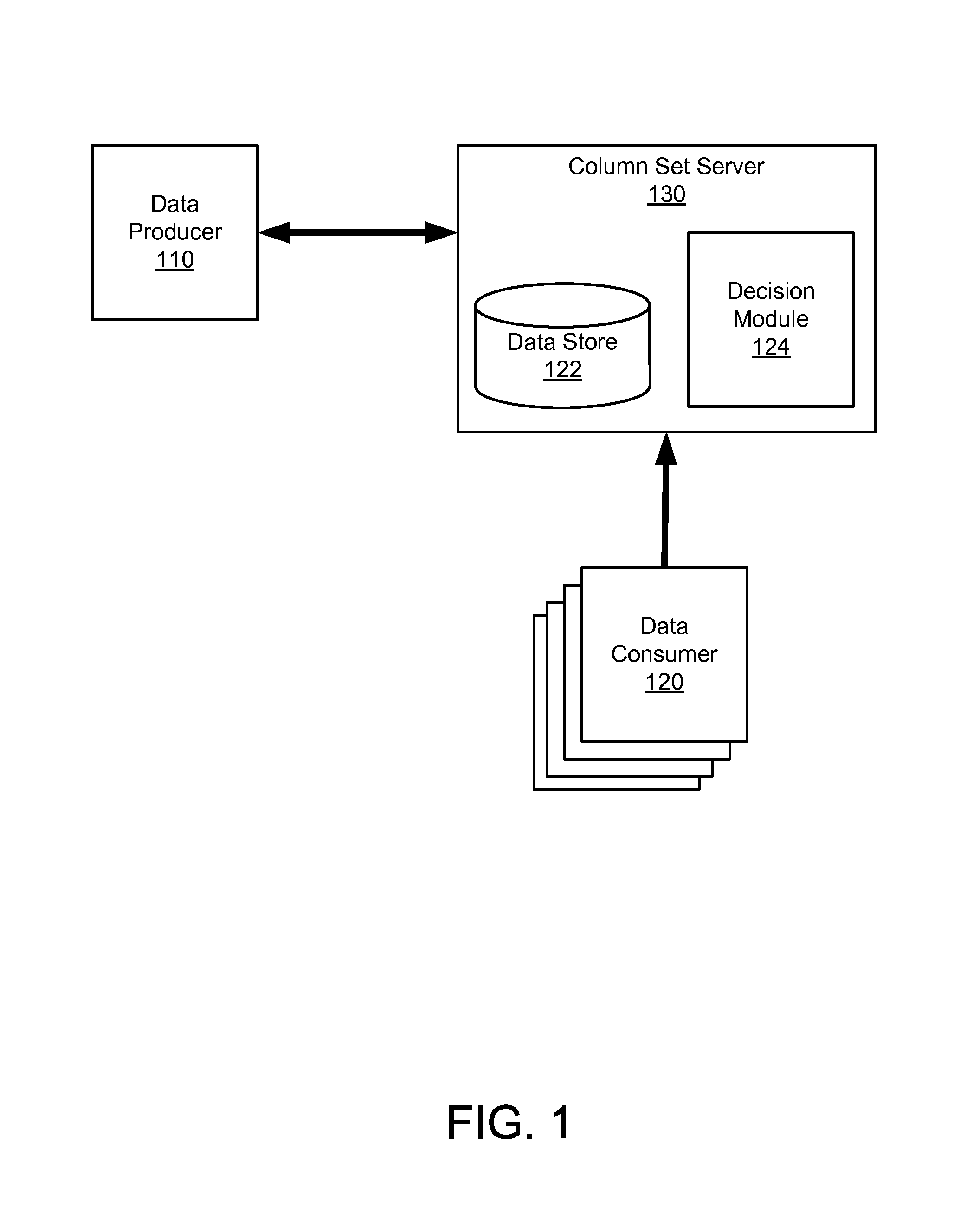
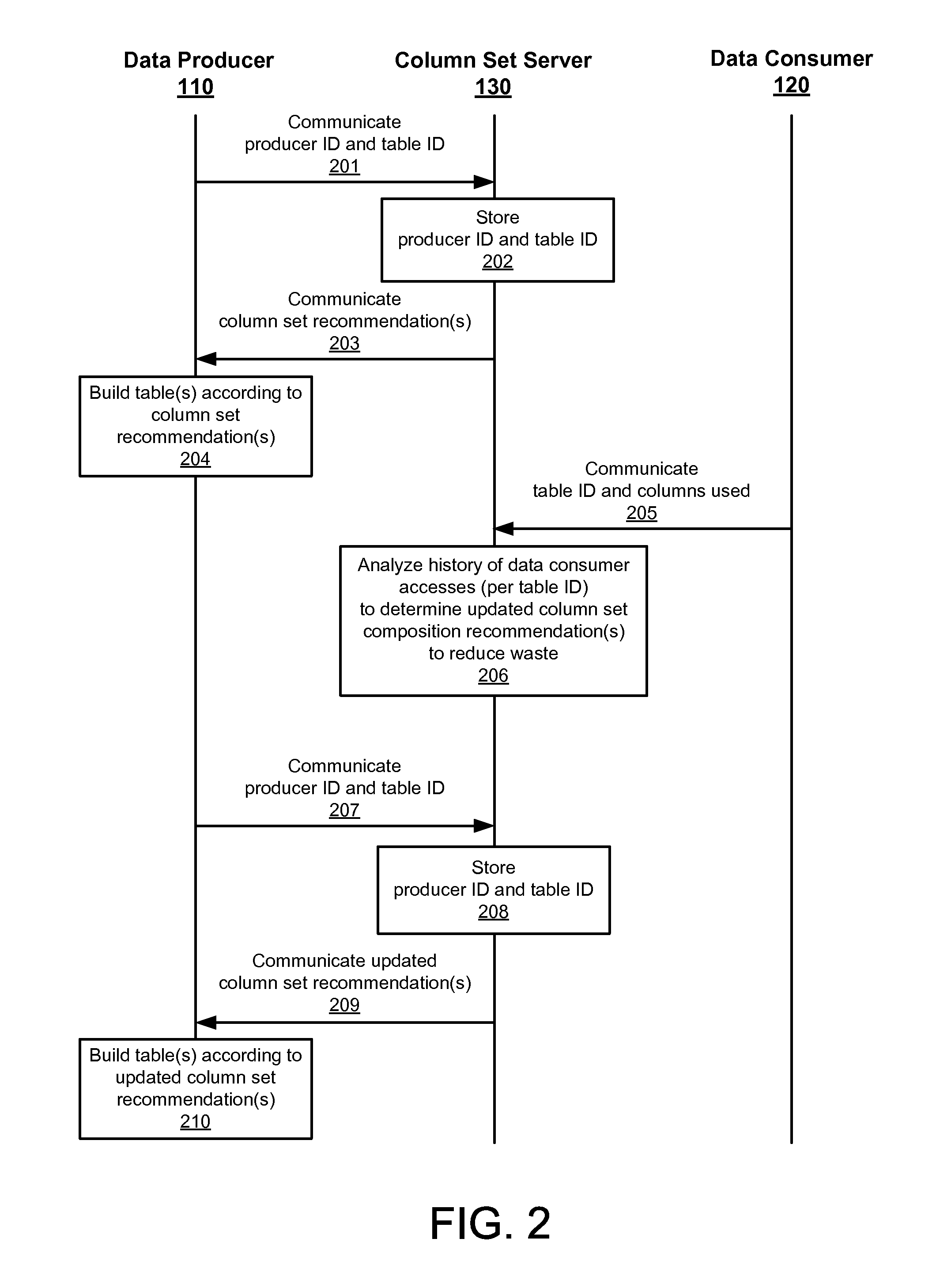
Adaptive column set composition
ActiveUS9141651B1Relieves developerRemove the burdenDigital data information retrievalSpecial data processing applicationsData setDatabase
A column set server adapts to data use patterns by data consumers by modifying how a table produced by a data producer is partitioned into separate column sets to reduce the waste incurred in accessing the data by multiple consumers of the data. For example, the column set server adjusts a column set distribution when a new consumer process is added, when one is retired, or when relative data set size ratios change.
Owner:QUANTCAST CORP
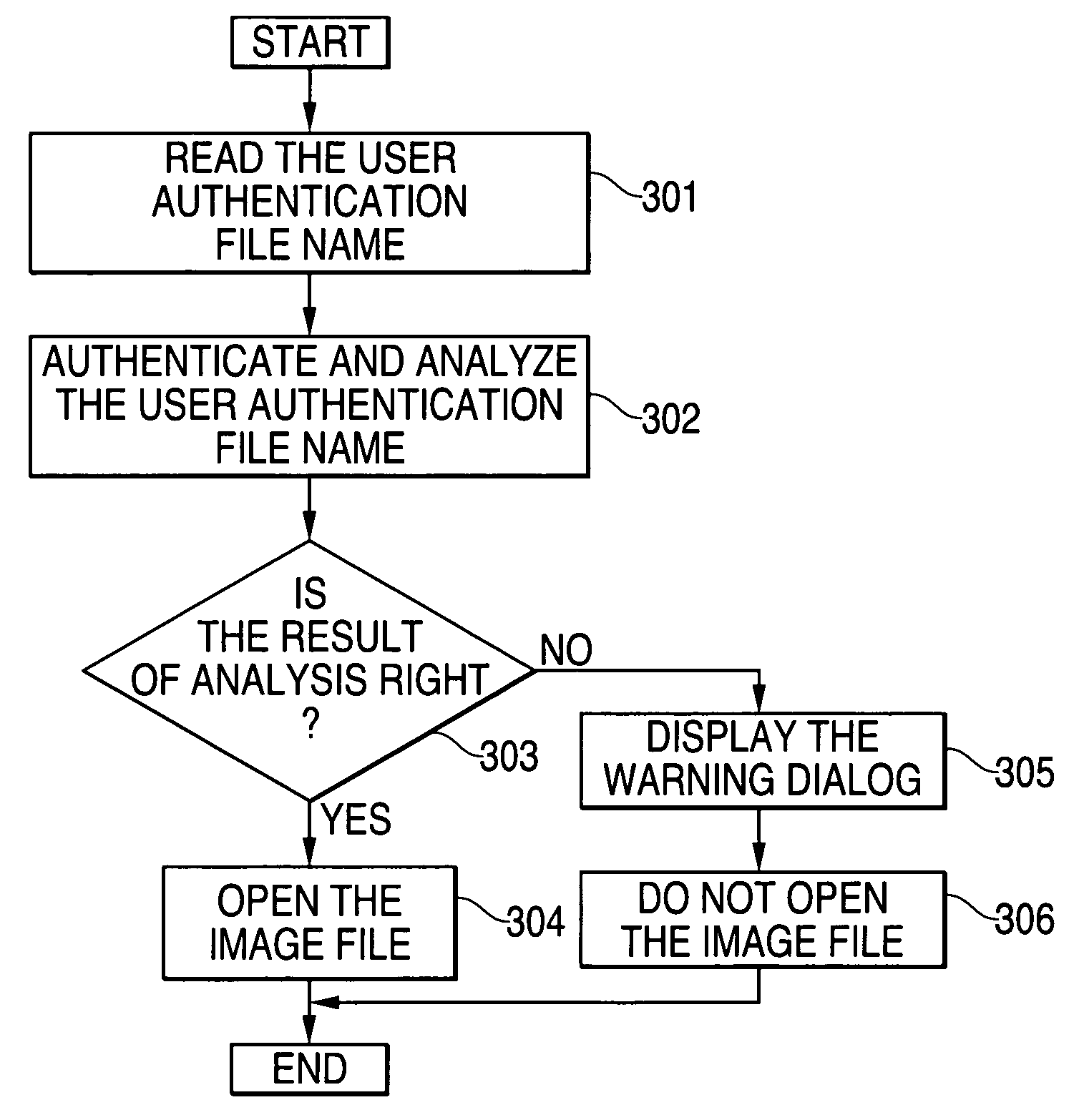
Authentication apparatus and authentication method
InactiveUS20050223223A1Controlling illegal copyingEliminate concernsDigital data processing detailsUnauthorized memory use protectionAuthenticationProcess control
In order to solve concerns about processes performed on a display screen for an authentication program which limits access to each file, the authentication program has an authentication process to request authentication of each file at the time of using the files. The authentication process controls a computer to execute operations of analyzing the authentication character-string input for the file name, determining whether the result of analysis is right or wrong, and opening and closing the file to enable use of the file when the result of analysis is right and to disable use of the file when the analysis result is wrong.
Owner:FUJITSU LTD
Method for admixing plant essential oils to coatings for the purpose of repelling insects
ActiveUS7514102B1Remove the burdenLessening human health riskBiocideInorganic active ingredientsToxicantEvaporation
The Federal EPA has consistently limited the use of known toxicants (insecticides) to preclude their admixture into paints and coatings by contractors or homeowners for the purpose of repelling or killing insects on the dried or cured coating. The current invention is a method to repel rather than kill insects, arachnids, and other arthropods utilizing materials taken from the EPA's GRAS (Generally Recognized as Safe) List, obviating onerous Federal Insecticide, Fungicide, and Rodenticide Act (FIFRA) regulations and greatly extends the useful life of the insect-repellant materials by binding them into the dried film solids—greatly slowing their evaporation and degradation and creating a timed release of insect repellant material. Furthermore, the current invention utilizes the insect repellant nature of these materials to repel insects from the surrounding area during coating application, thereby eliminating the need for applying insect repellants such as DEET to the skin.
Owner:CTA PROD GRP
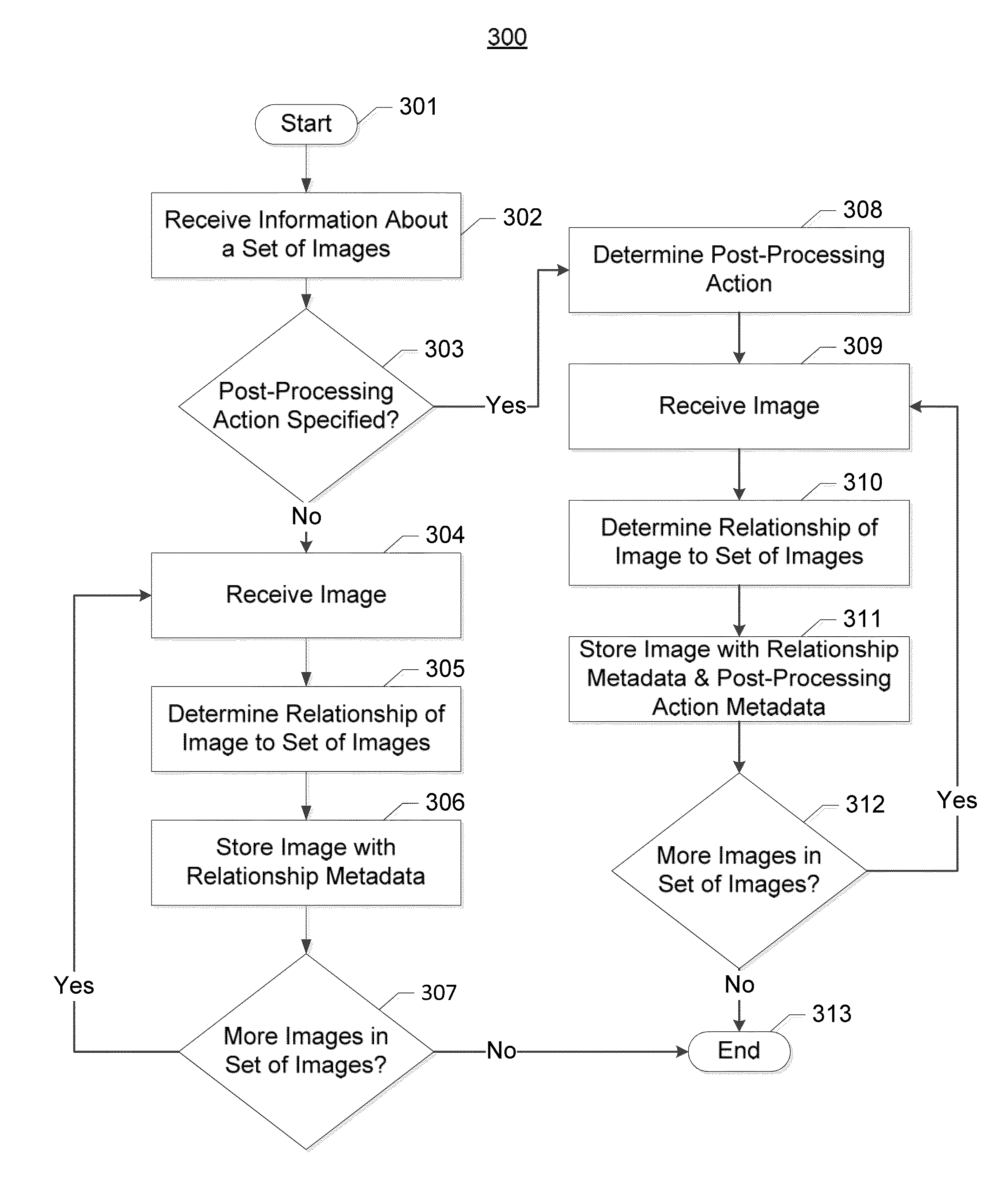
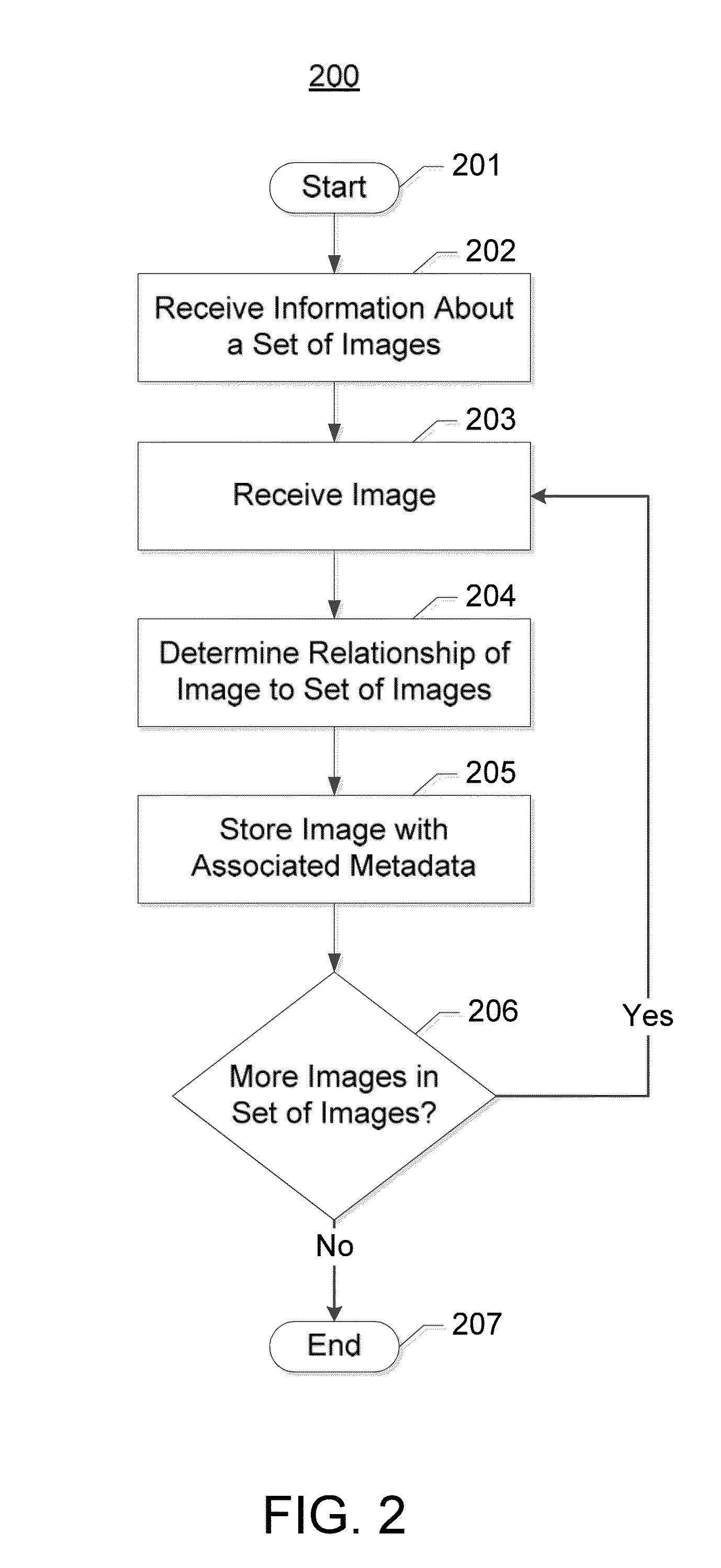
Method and apparatus for determining the relationship of an image to a set of images
InactiveUS20140193083A1Reduce and eliminate identificationRemove burdenCharacter and pattern recognitionSpecial data processing applicationsComputer visionMetadata
A method, apparatus, and computer program product are disclosed to determine the relationship of an image to a set of images. In the context of a method, information about a set of images is received. The method also receives an image from the set of images. The method determines, by a processor, information about a relationship of the image to the set of images. The method also causes storage of the image in conjunction with metadata about the image. The metadata includes the information about the relationship of the image to the set of images. The method may also repeat the above operations until a determined number of images have been stored in conjunction with respective metadata, in which case the information about the relationship of the image to the set of images includes a parameter specifying the number of images in the set of images.
Owner:NOKIA TECHNOLOGLES OY
Wireless Communication Terminal and Control Method Threrof
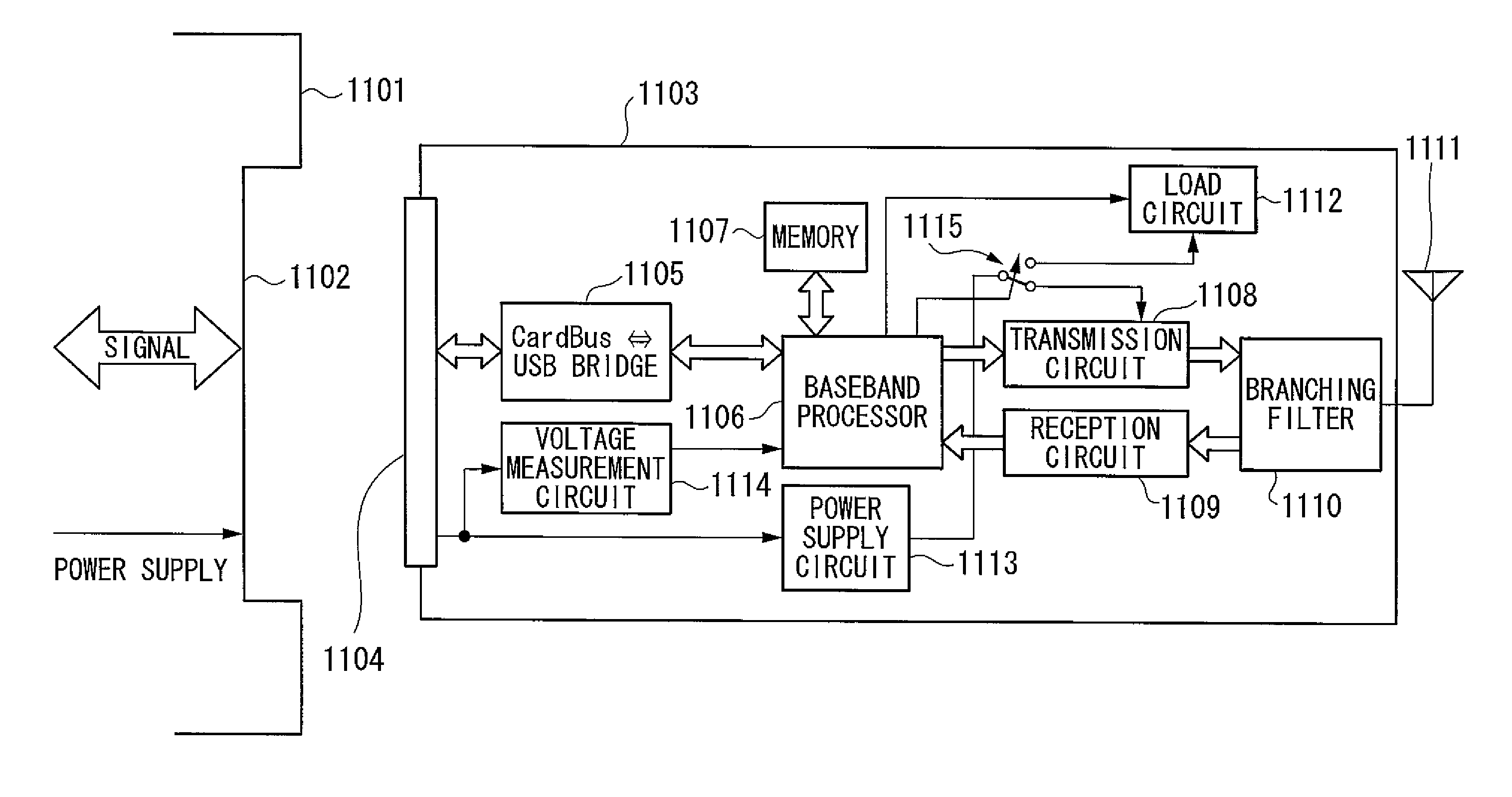
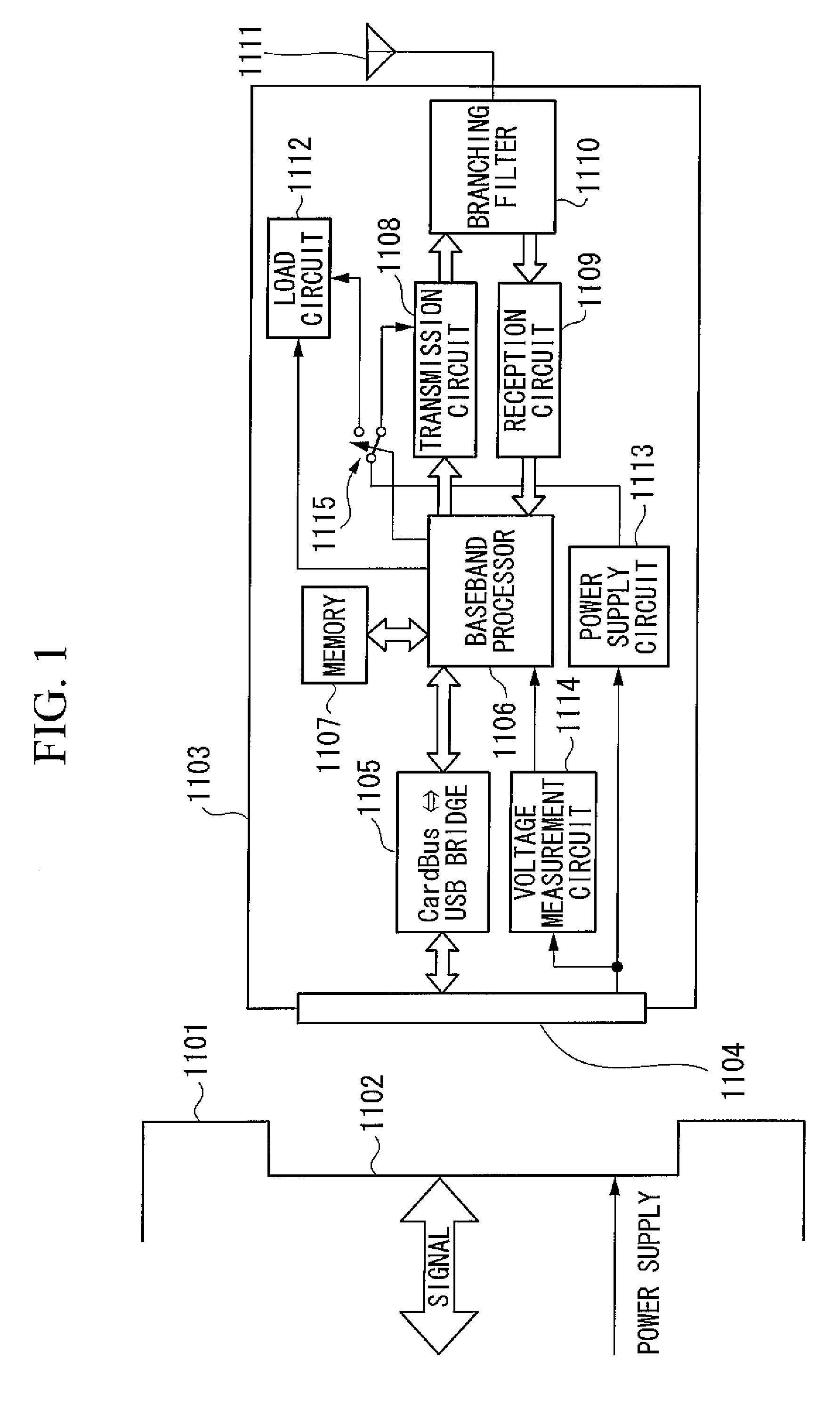
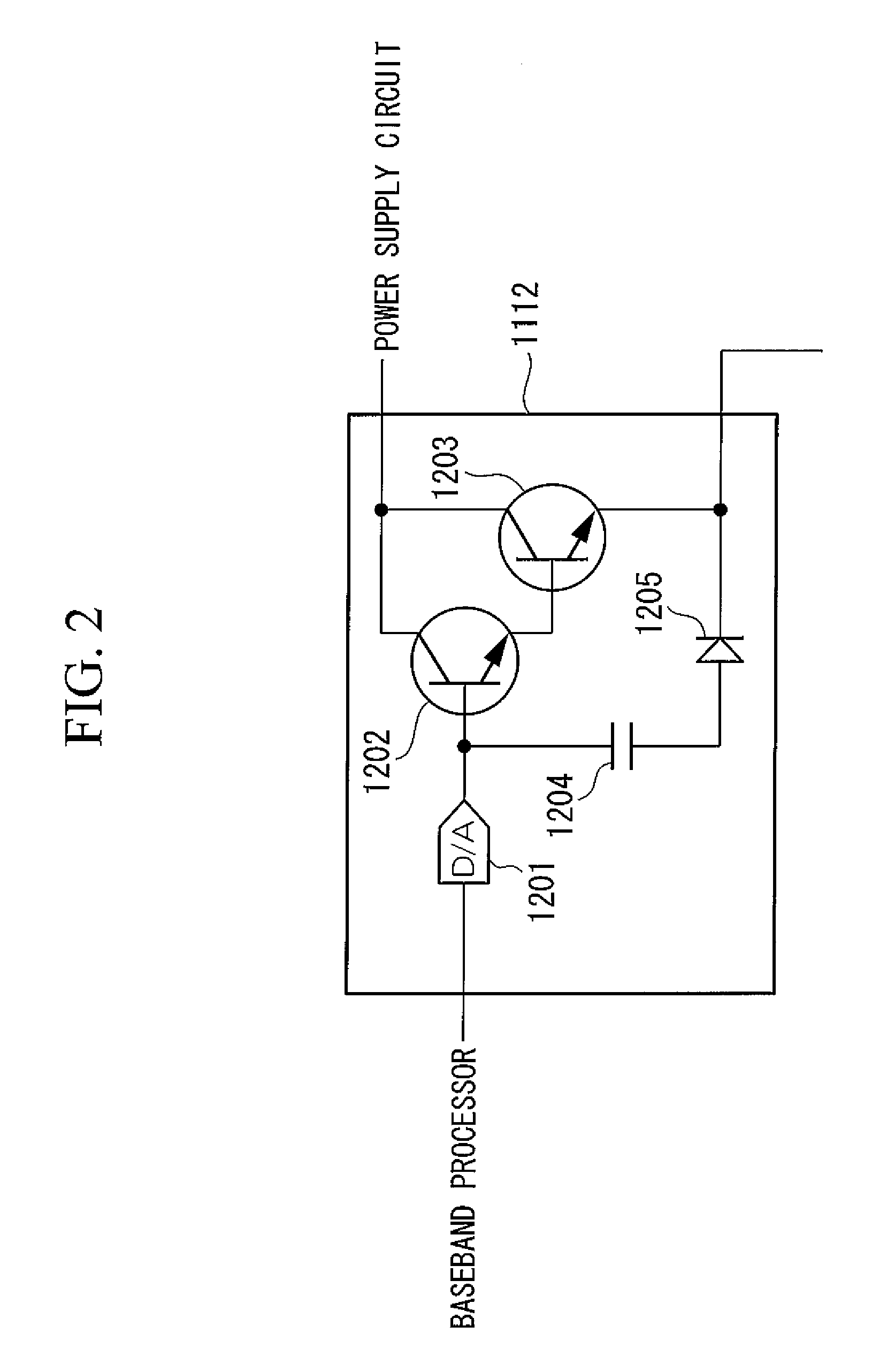
InactiveUS20080058025A1Operational reliability is increasedReduce stepsPower managementResonant long antennasLoad circuitVoltage drop
In a PC card communication terminal that operates supplied with power from a host device, problems such as malfunctions due to a supply voltage drop at the time of high transmission output are prevented from occurring. A baseband processor (1106) selects a transmission-power upper-limit measurement mode when a PC card terminal (1103) is to be controlled for the first time. A supply voltage drop is measured by a voltage measurement circuit (1114) while a load value of a load circuit (1112) is being changed. The load value of the load circuit (1112) when the supply voltage decreases to a permissible lowest supply voltage is obtained. Using a conversion table stored in a memory (1107), the load value is converted into a transmission output and is set as a transmission-output upper limit. In a normal communication mode, a maximum transmission output is restricted based on this transmission-output upper limit.
Owner:GE TECH DEV INC GETD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com